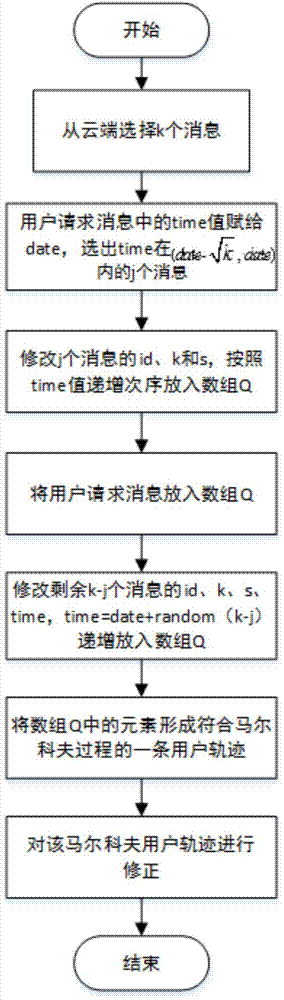
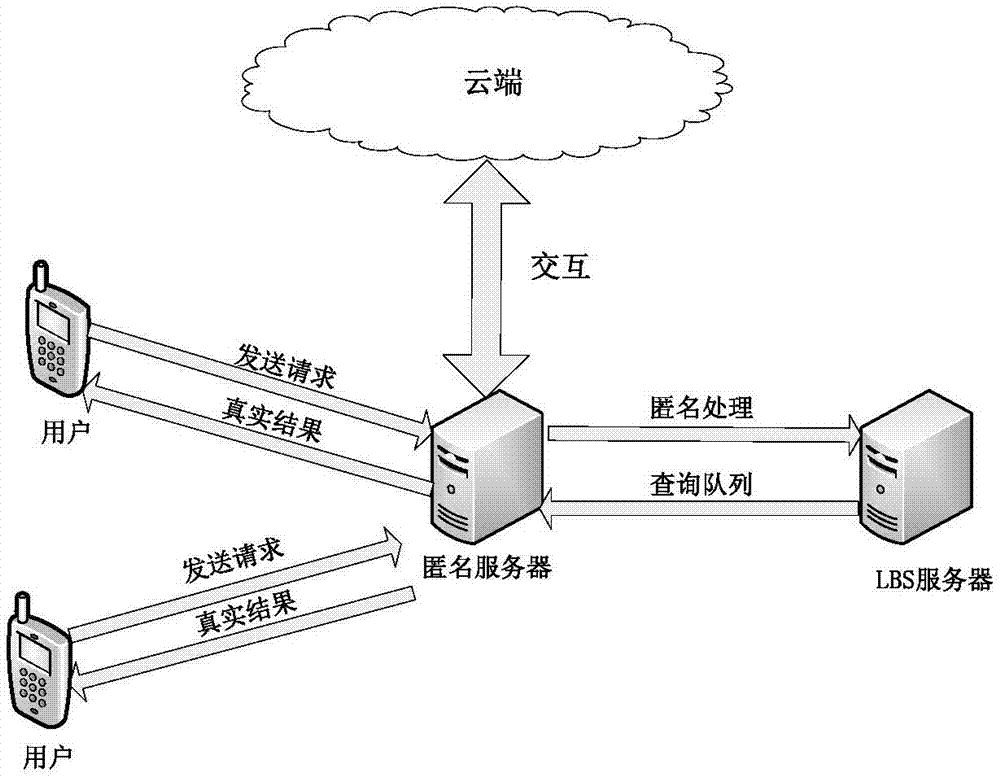
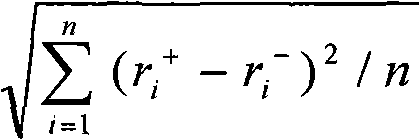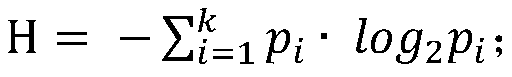Patents
Literature
71 results about "K-anonymity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
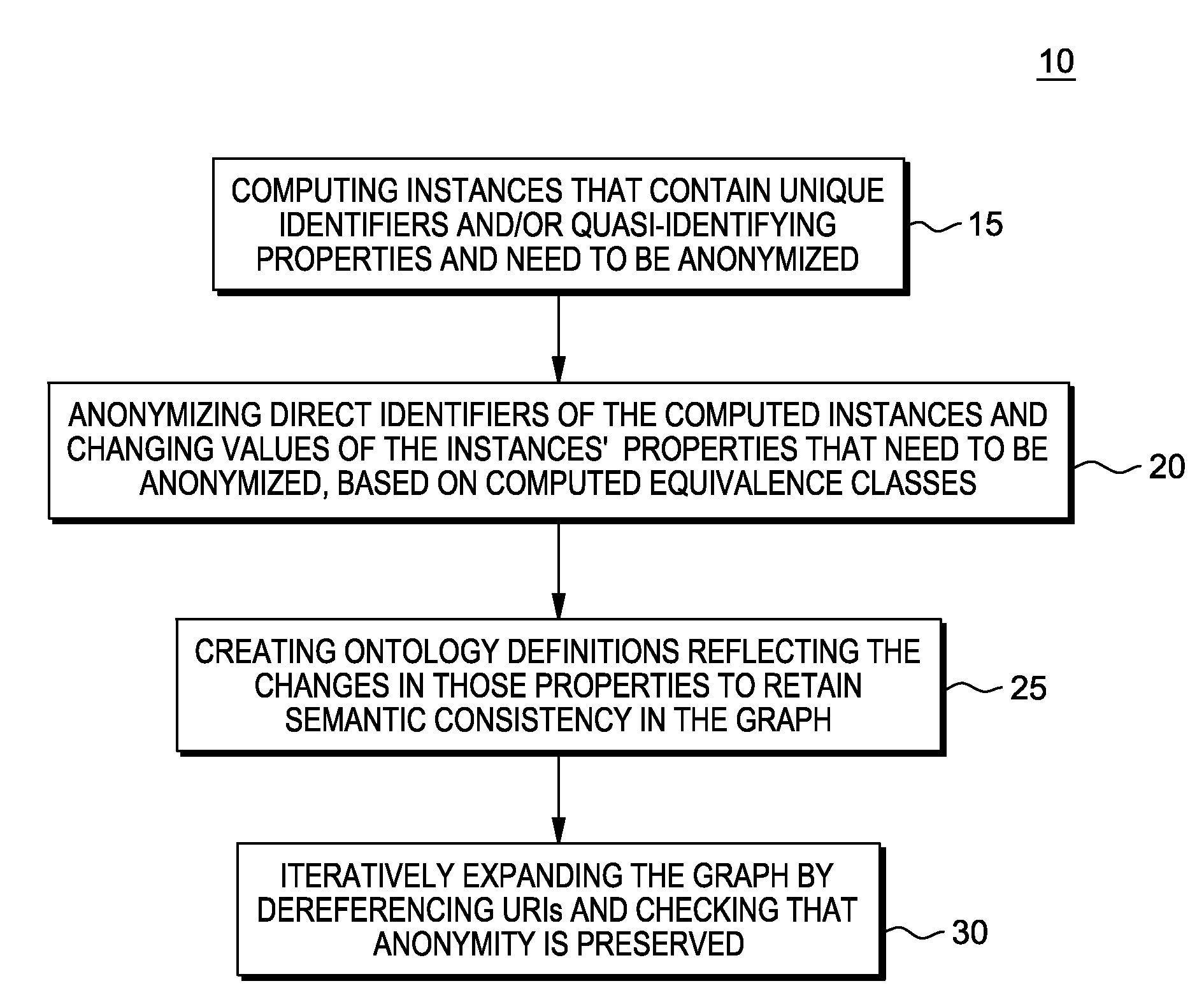
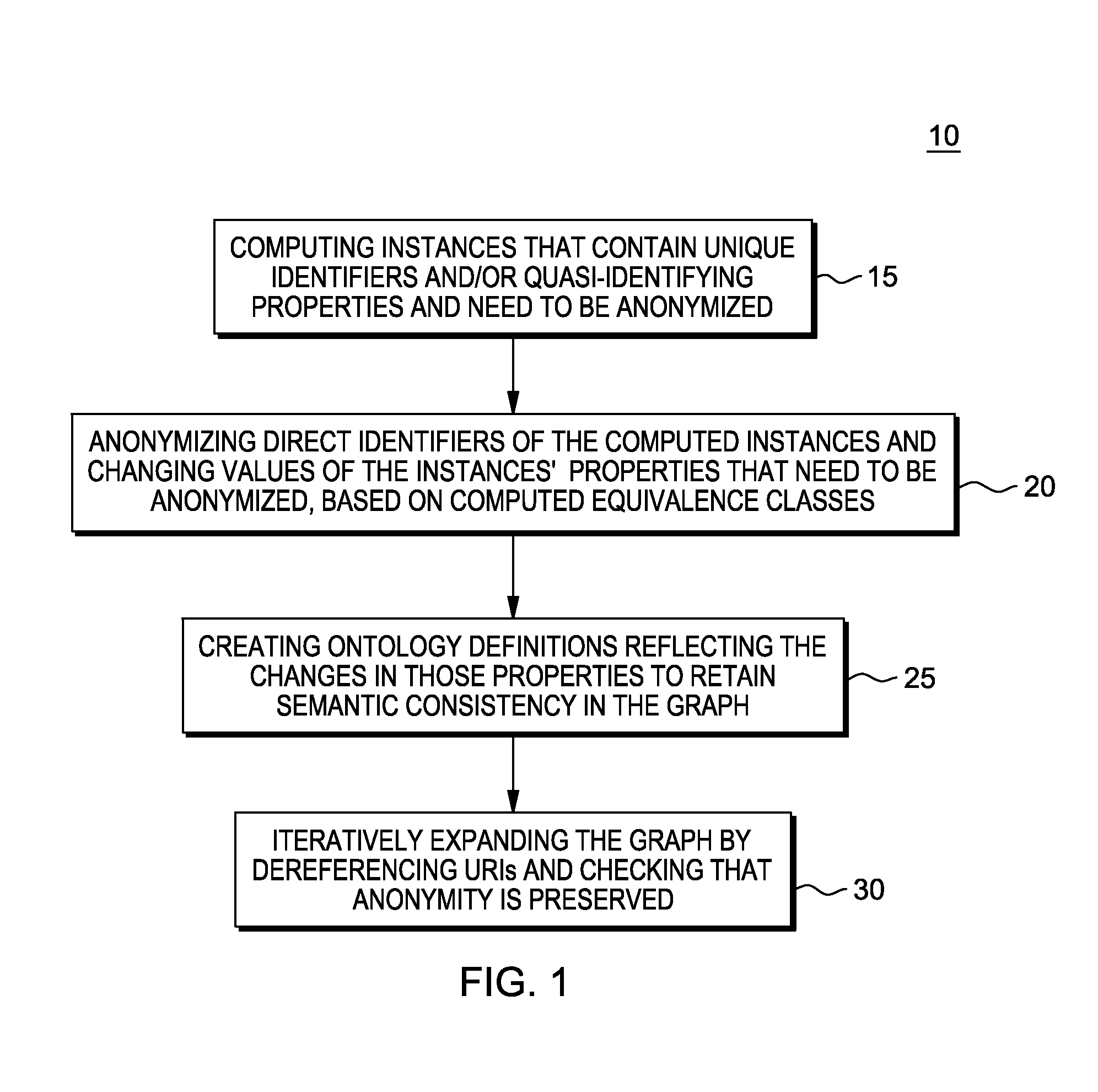
K-anonymity is a property possessed by certain anonymized data. The concept of k-anonymity was first introduced by Latanya Sweeney and Pierangela Samarati in a paper published in 1998 as an attempt to solve the problem: "Given person-specific field-structured data, produce a release of the data with scientific guarantees that the individuals who are the subjects of the data cannot be re-identified while the data remain practically useful."
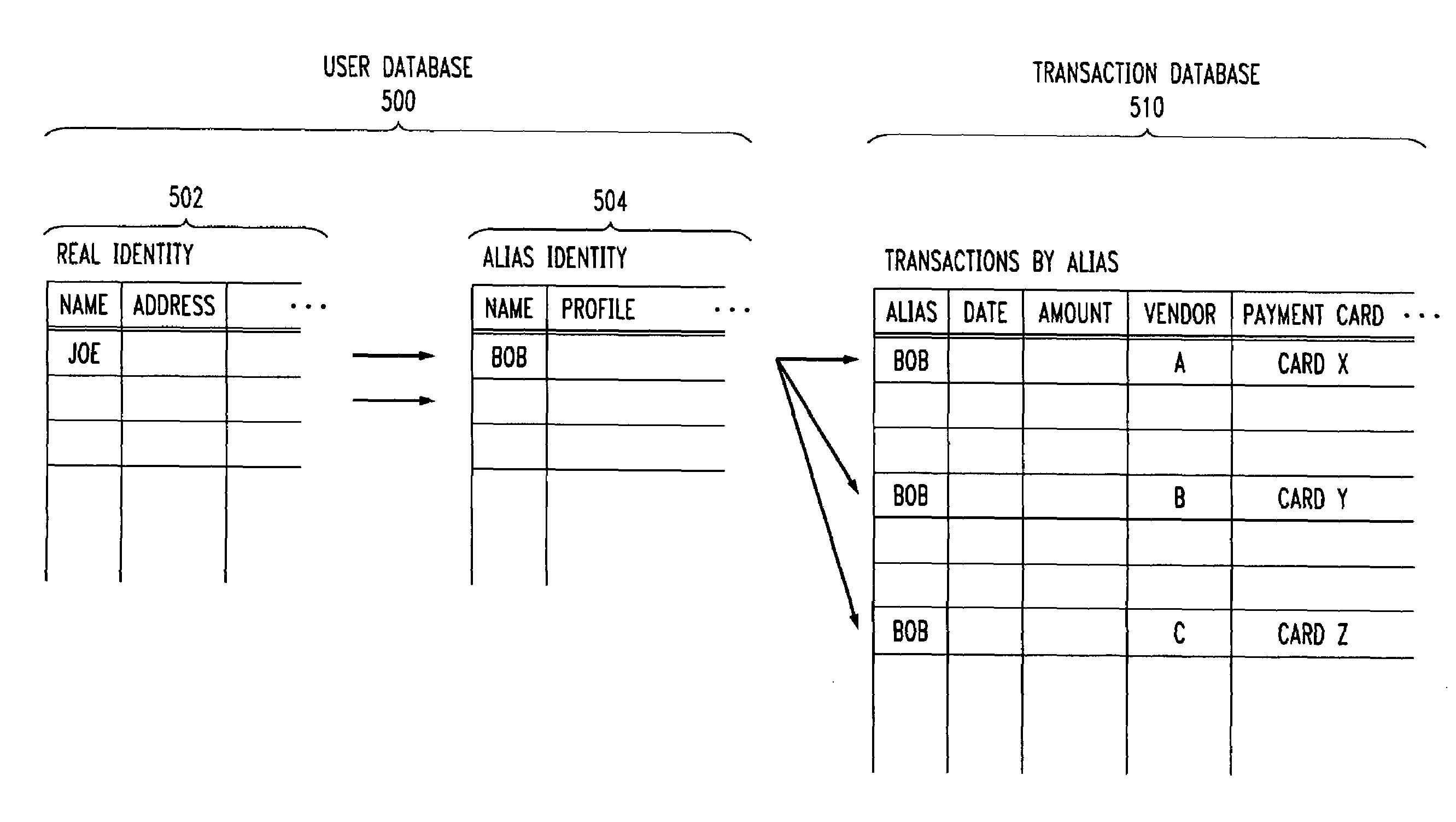
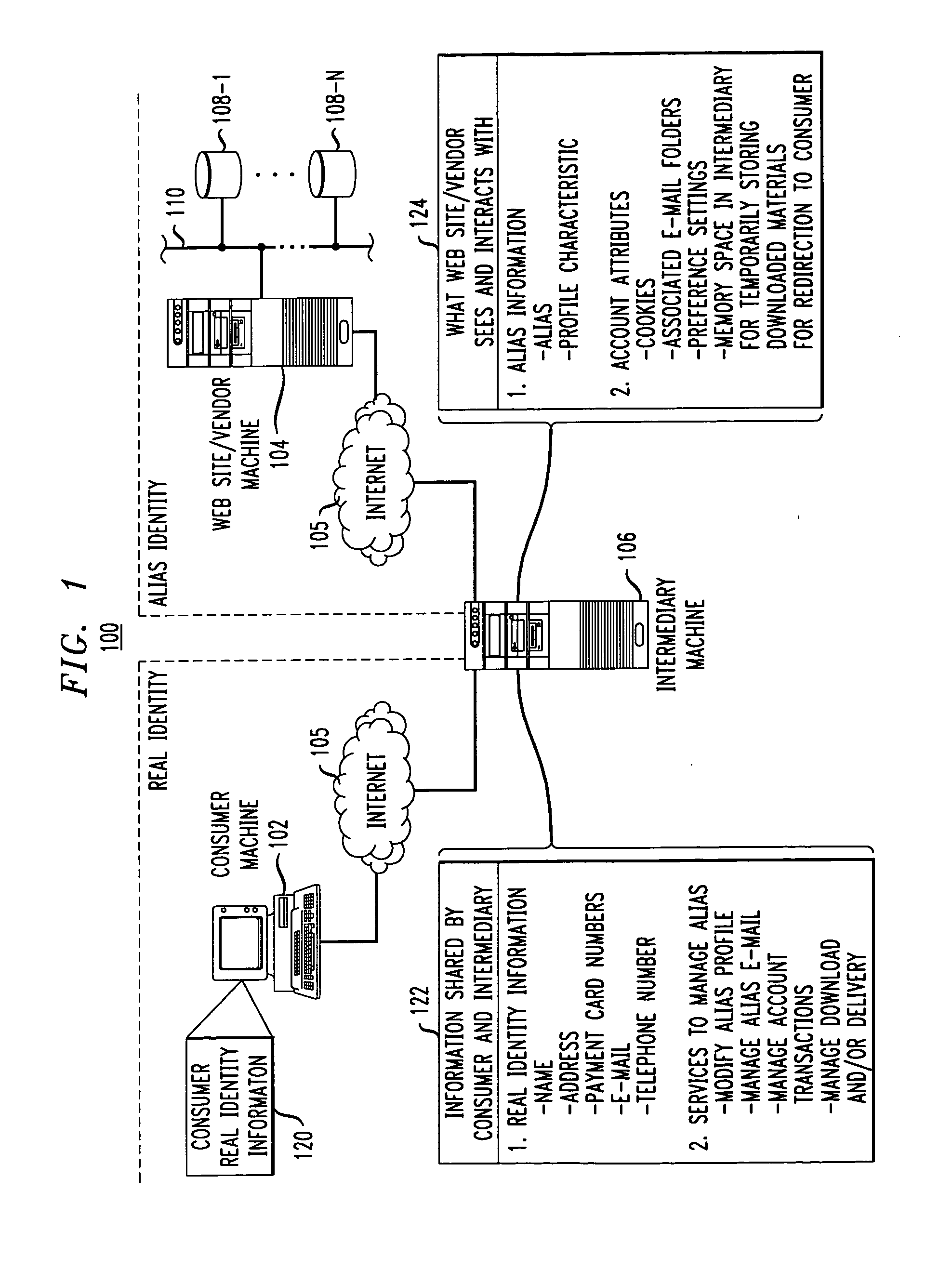
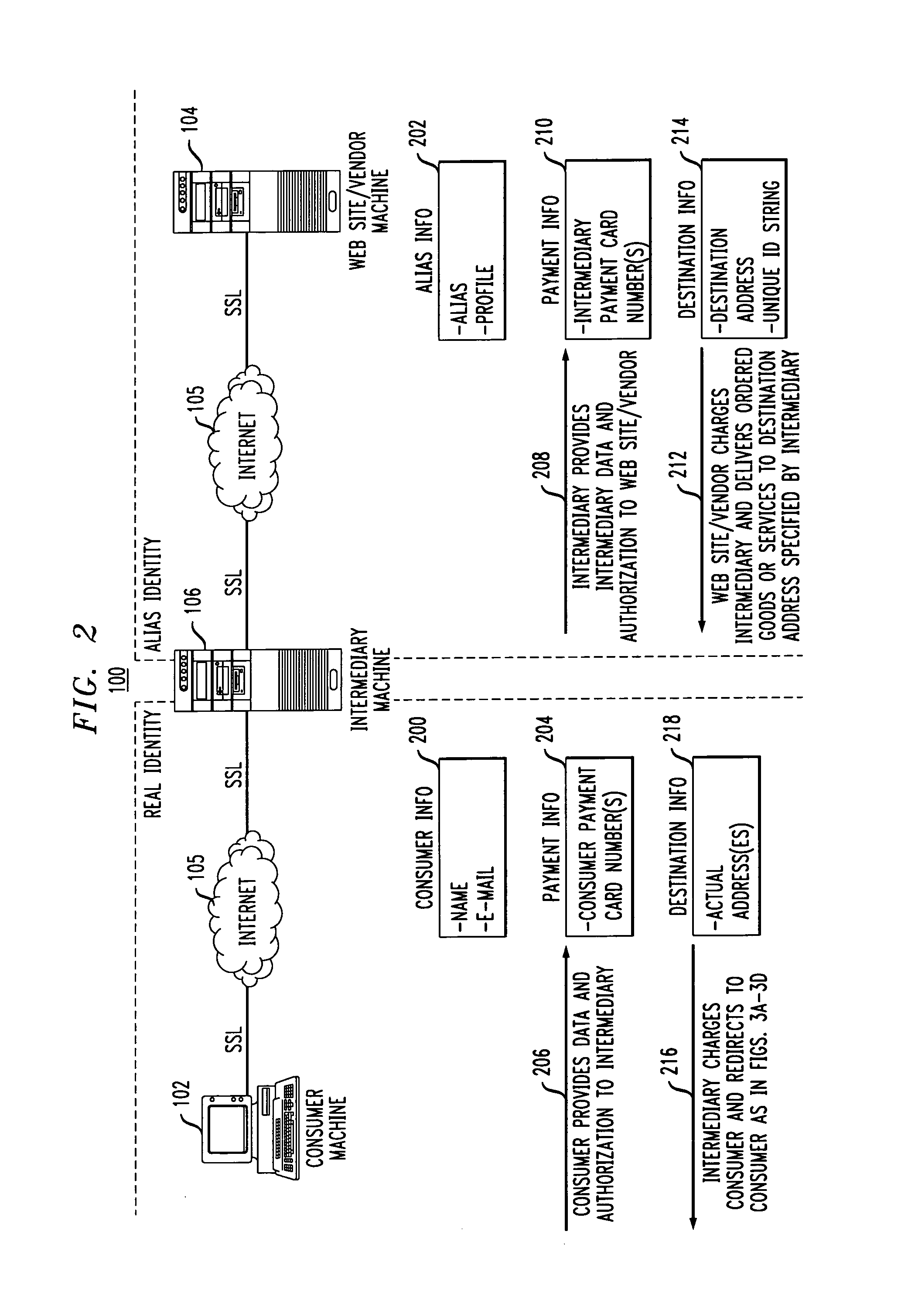
Methods and apparatus for providing user anonymity in online transactions
InactiveUS7203315B1Maintaining anonymityLimit fraud riskDigital data processing detailsMultiple digital computer combinationsWeb siteThird party
End-to-end user anonymity is provided in electronic commerce or other types of online transactions through the use of an intermediary. An intermediary machine, which may be implemented in the form of a set of servers or other type of computer system, receives communications from a consumer or other user, and generates and maintains an alias for that user. Connections between the user machine and any online vendor or other web site are implemented through the intermediary using the alias. When the user desires to make a purchase from a given online vendor, the intermediary may present the user with a number of options. For example, the user may be permitted to select a particular payment card number and real destination address as previously provided to the intermediary. The intermediary then communicates with the online vendor and supplies intermediary payment information, e.g., a payment card number associated with the intermediary rather than the user, along with appropriate authorizing information and an alias destination address, e.g., a third party physical shipping address for deliverable goods, an alias electronic address for downloadable material, etc. The online vendor charges the purchase to the intermediary, and redirects the delivery of the goods or services to the destination address provided by the intermediary. The intermediary charges the payment card number of the user, and arranges for the redirection of the delivery to the real user address. In this manner, the invention provides complete end-to-end anonymity for the user, even when the user desires to enter transactions involving purchase and receipt of deliverable goods and services.
Owner:PRIVACY LABS
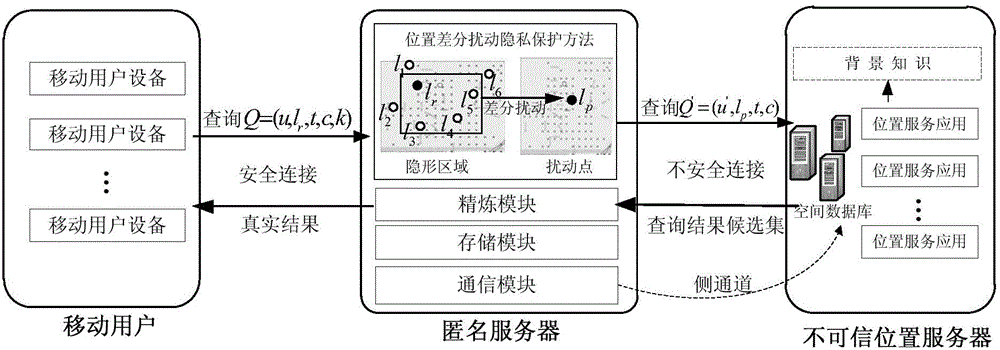
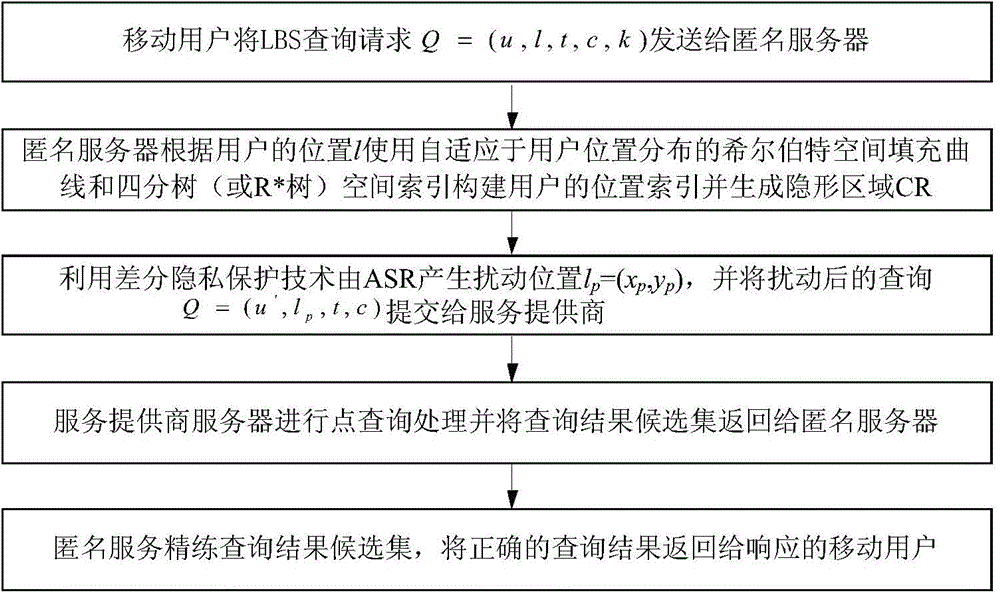
High-efficiency difference disturbance location privacy protection system and method
ActiveCN104394509AGenerate efficientlyGuaranteed correctnessTransmissionLocation information based serviceK-anonymitySide information
The invention discloses a high-efficiency difference disturbance location privacy protection system and a method, considering that the attacker has the challenge to the location privacy protection method based on the location disturbance and fuzzy technology about the background knowledge of the user side information, the difference privacy protection technology is guided to the location fuzzy privacy protection method, the Hilbert space filling curve capable of self-adaption transition on the user location according to the distributed change features in the geographic space of the mobile user and the current fashionable quadtree or R tree spatial index are used for forming the location index for all mobile users in the geographic space, and the K anonymity contact area satisfying the principle of reciprocity is effectively generated. Then, the difference privacy protection technology is used for generating the location disturbance point reasonable near user real location of k location points of the contact area as the query location of LBS user for requesting service from the LBS service provider, the problems and deficiencies of the existing method can be overcome.
Owner:XI AN JIAOTONG UNIV
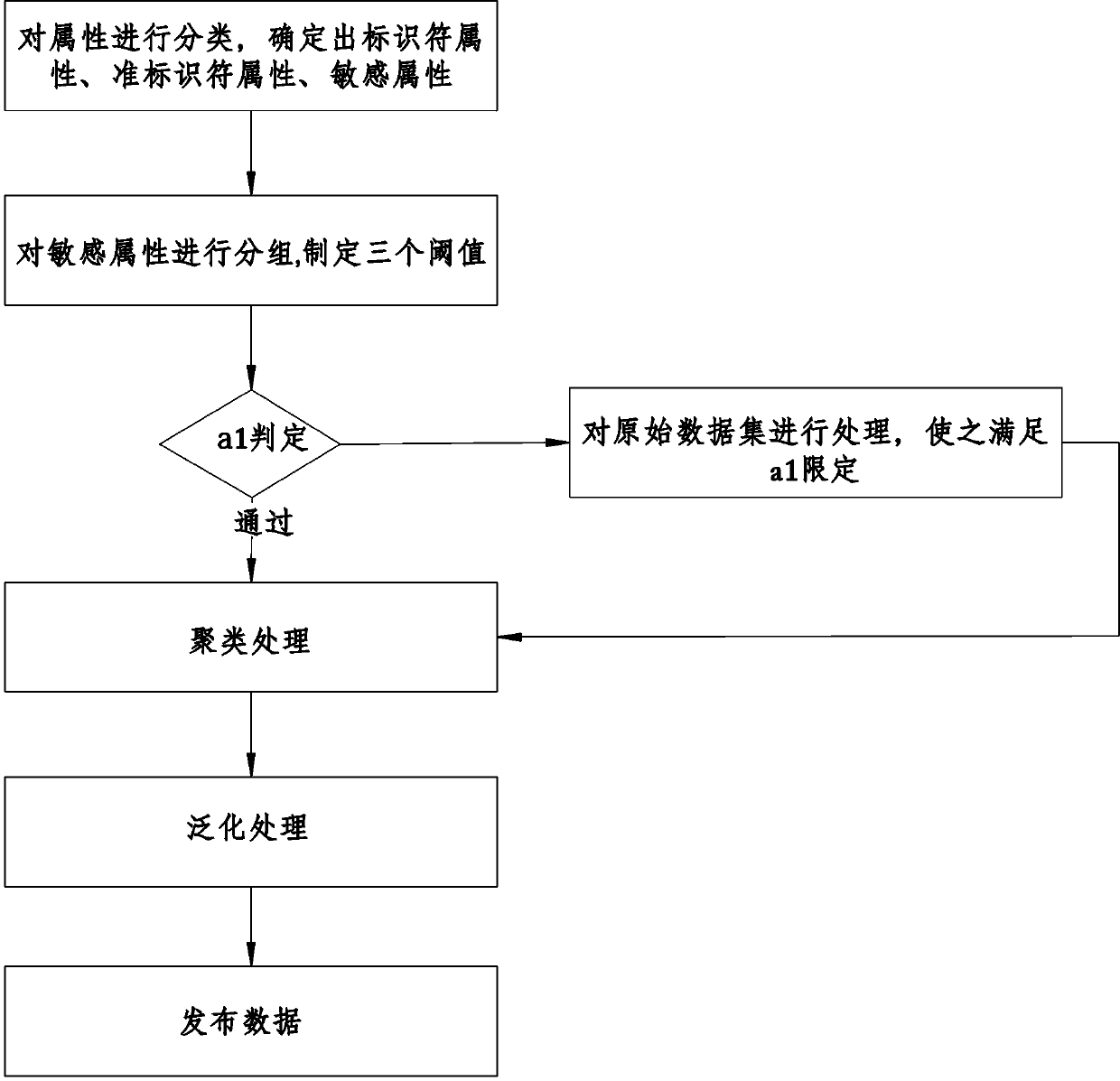
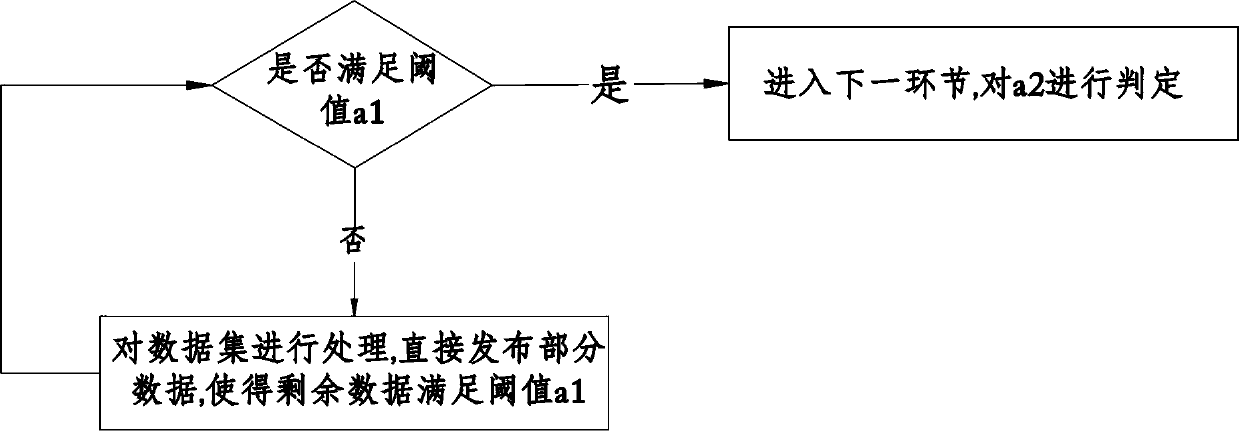
Health data privacy protection method based on K-anonymity
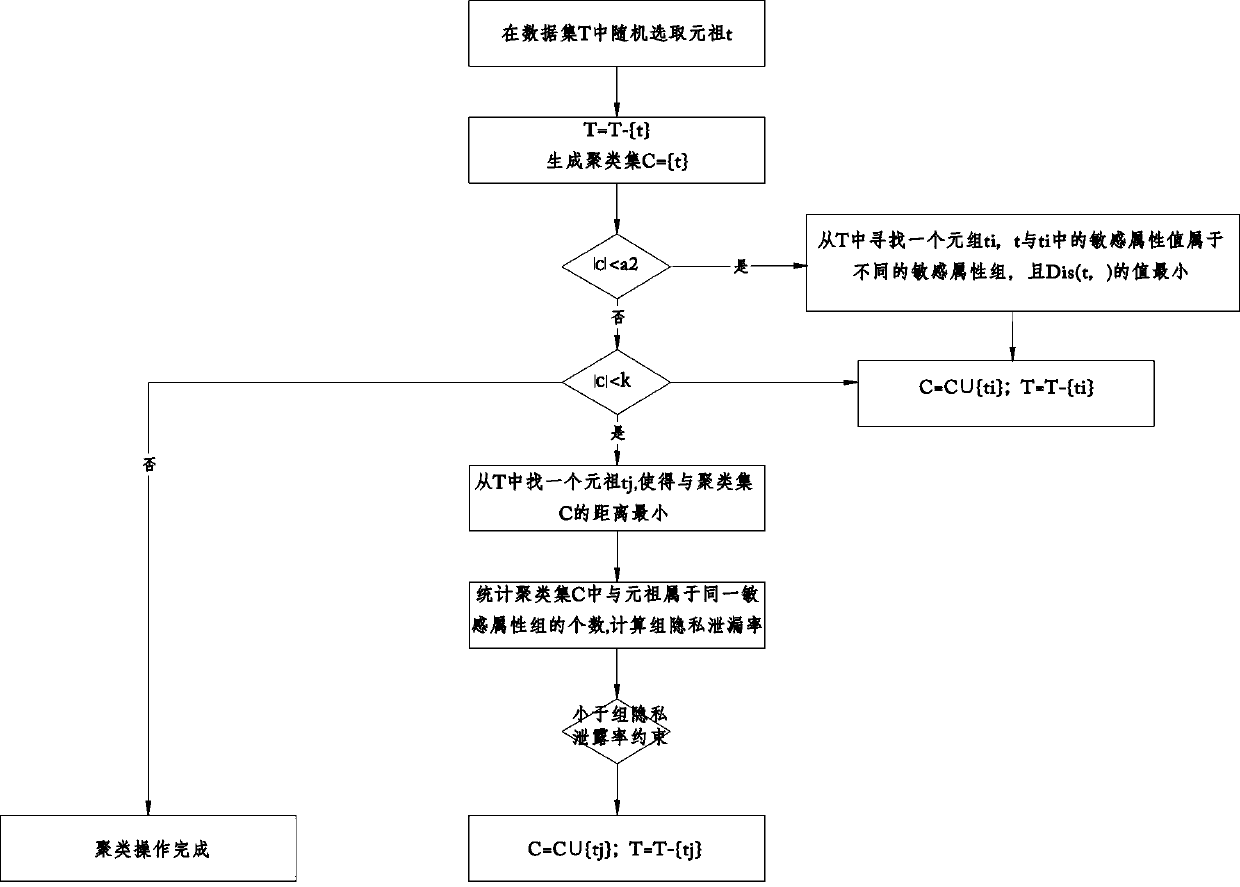
ActiveCN105512566APrevent Consistency AttacksFlexible handling of anonymityDigital data protectionData setK-anonymity
The invention relates to a health data privacy protection method based on the K-anonymity. The health data privacy protection method comprises that (1) sensitive information is divided into groups, the privacy leakage rate of each group is set for restraint; (2) statistics is carried out to the tuple number of different sensitive attribute values in the data set; (3) whether clustering operation is directly carried out to data or only part of the data is processed is judged in dependence on a threshold a1; (4) whether the number of the sensitive attribute values is larger than a2 is judged, if the number of the sensitive attribute values is larger than a2, the next step is executed, otherwise the process is stopped; (5) clustering processing is carried out to the data; and (6) generalization processing is carried out to the data. According to the invention, K-anonymity processing is carried out to the data, and therefore the processed data can resist linking attack, and consistency attack can be effectively prevented.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA +1
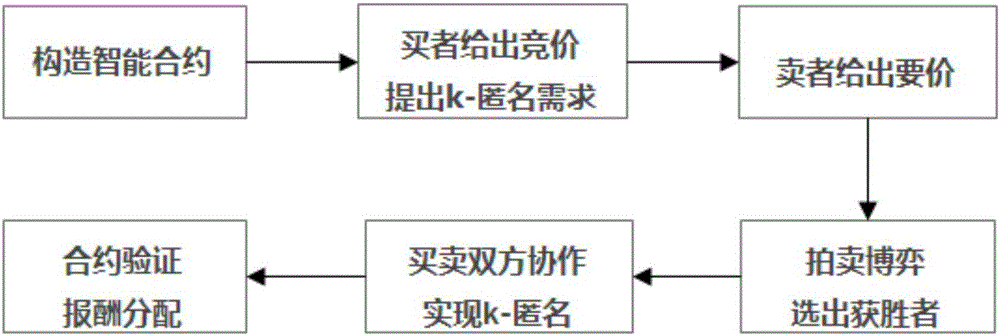
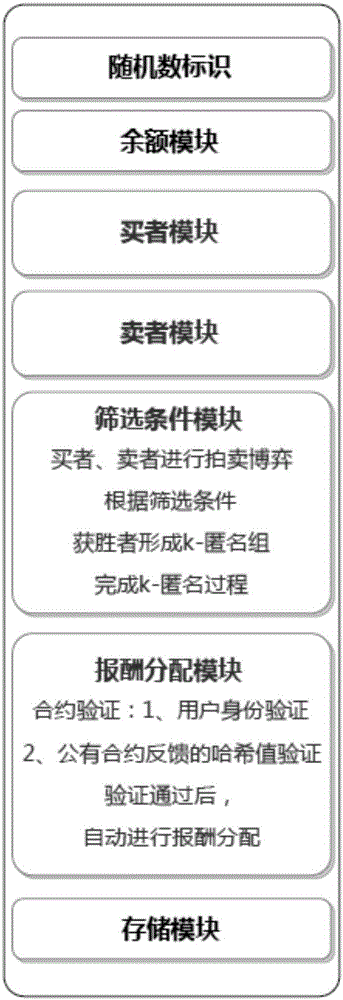
Blockchain-based personalized k-anonymity privacy protection motivation method
ActiveCN107483211AAvoid safety hazardsMeet privacy level requirementsUser identity/authority verificationCommercePersonalizationThird party
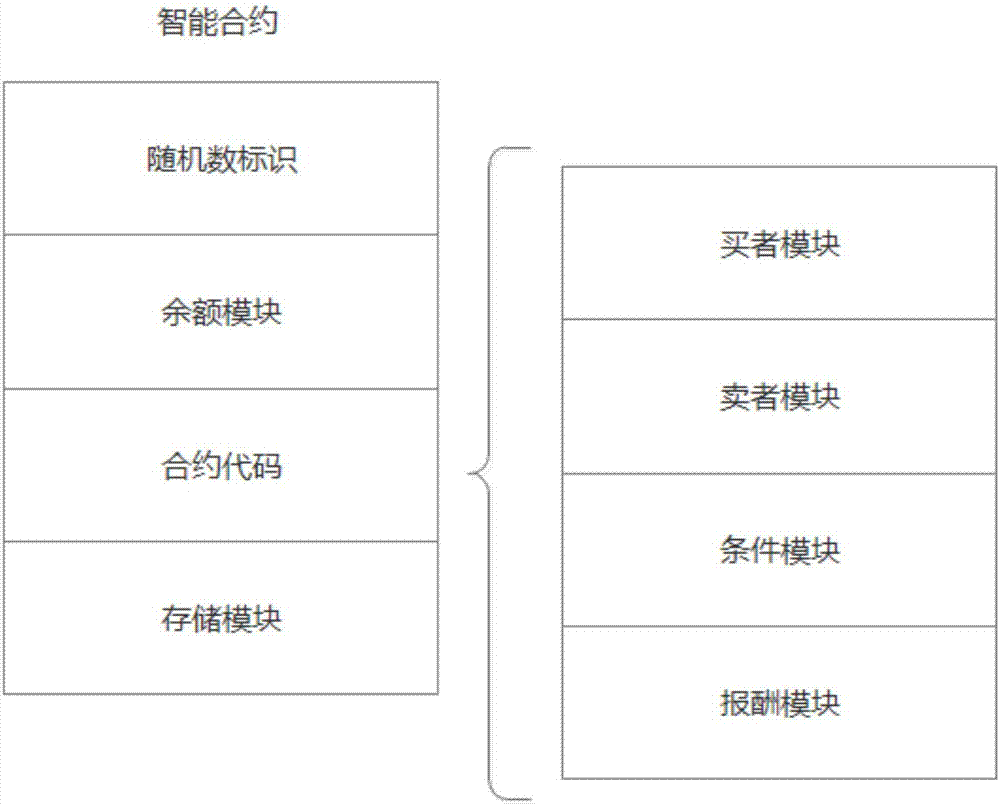
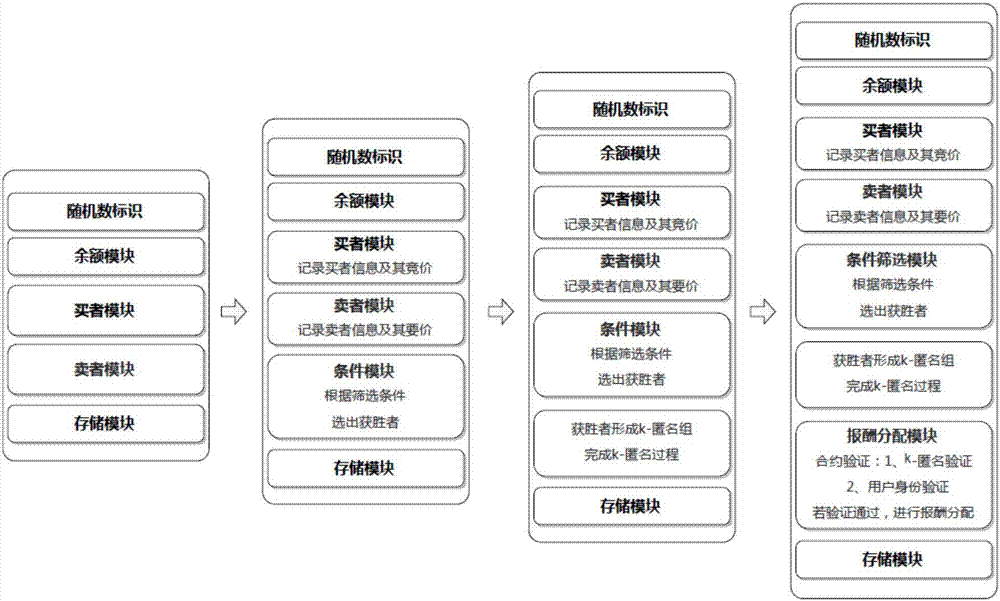
The invention relates to a blockchain-based personalized k-anonymity privacy protection motivation method. When the privacy levels of clients are same, buyer clients and seller clients conduct an auction game according to the screening conditions in a smart contract, the winning buyer clients and seller clients are selected out to form an anonymity group, and the clients in the anonymous groups upload the positions of the clients and query requests to a server side together to achieve the k-anonymity process. When the privacy levels of the clients are different, the buyer clients are divided into multiple groups according to the sequence that the privacy levels needed by the buyer clients are increased, an anonymity group is formed by the buyer clients screened out from the buyer client groups of which the numbers n of the buyer clients are larger than k+1, and a k-anonymity group is formed by the seller clients and buyer clients in the other groups. According to the method, the privacy level requirements of different users can be met to complete different privacy levels of k-anonymity privacy protection, and by applying the decentralized smart contract, the security hazards of a trusted third party are avoided.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
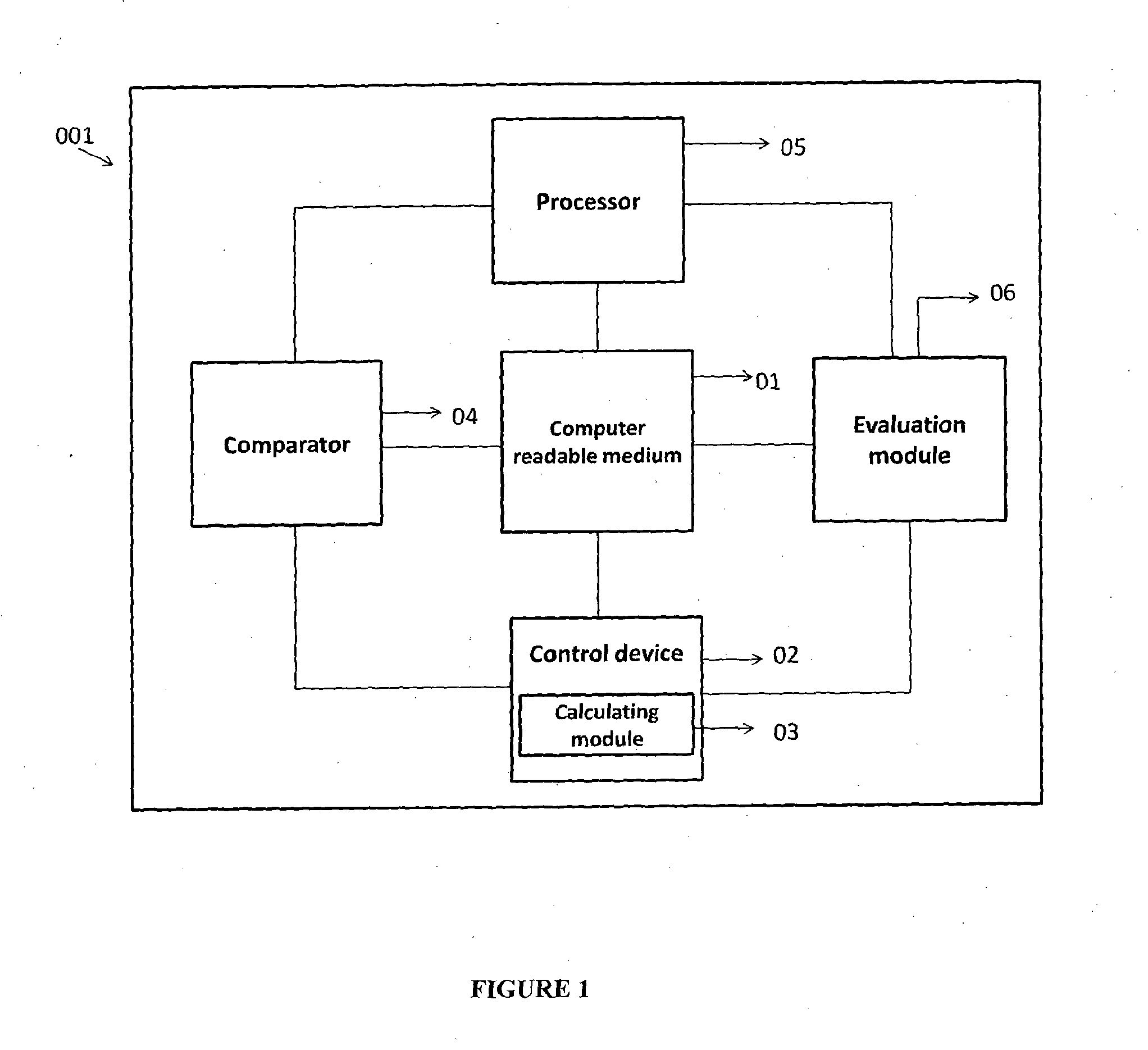
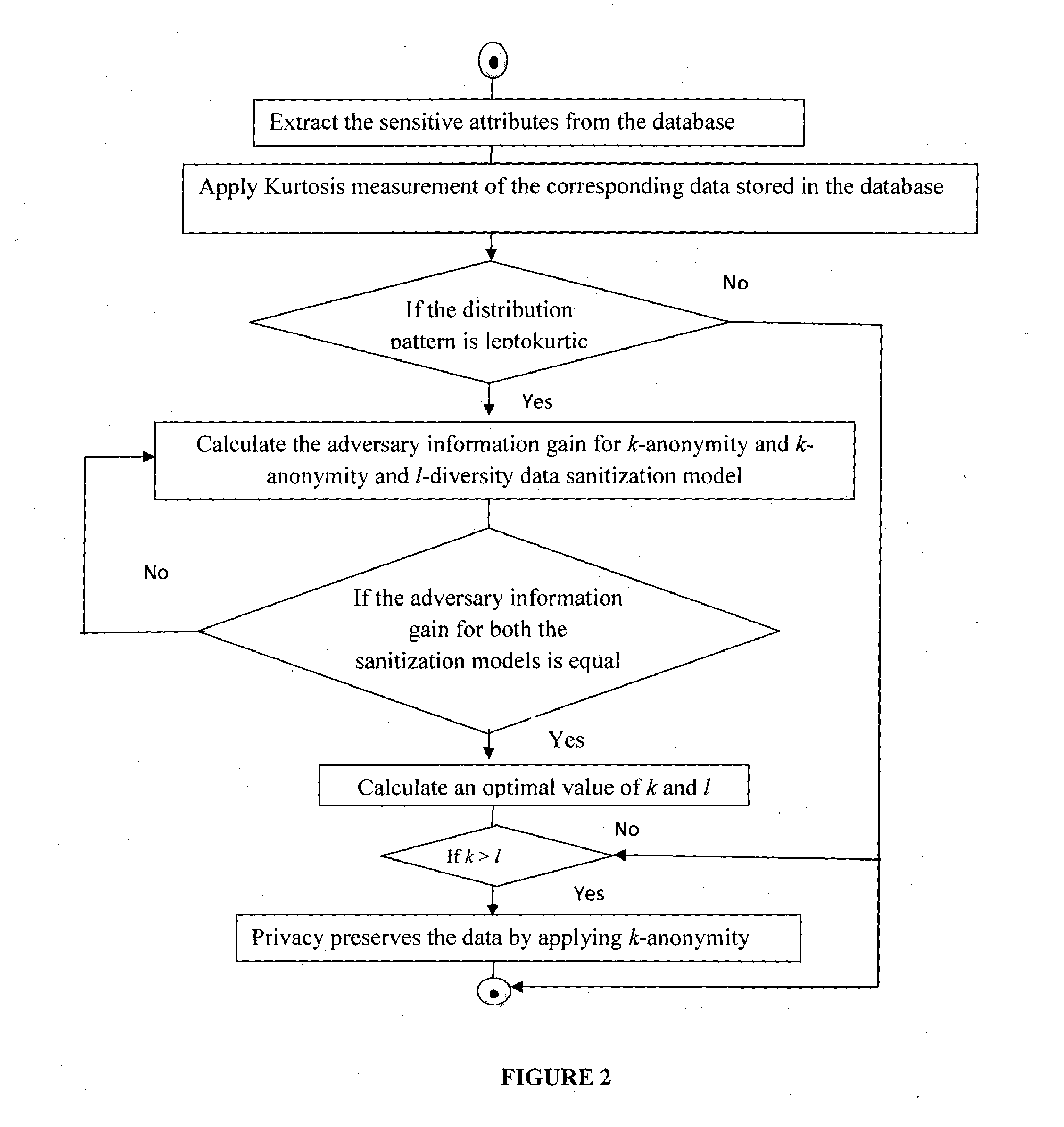
System and method for database privacy protection
ActiveUS20140237620A1Reduce complexitySame quantityDigital data processing detailsAnalogue secracy/subscription systemsK-anonymityAdversary
The invention relates to a system and a method for privacy preservation of sensitive attributes stored in a database. The invention reduces the complexity and enhances privacy preservation of the database by determining the distribution of sensitive data based on Kurtosis measurement. The invention further determines and compares the optimal value of k-sensitive attributes in k-anonymity data sanitization model with the optimal value of l sensitive attributes in l diversity data sanitization model using adversary information gain. The invention reduces the complexity of the method for preserving privacy by applying k anonymity only, when the distribution of the sensitive data is leptokurtic and optimal value of k is greater than the optimal value of l.
Owner:TATA CONSULTANCY SERVICES LTD
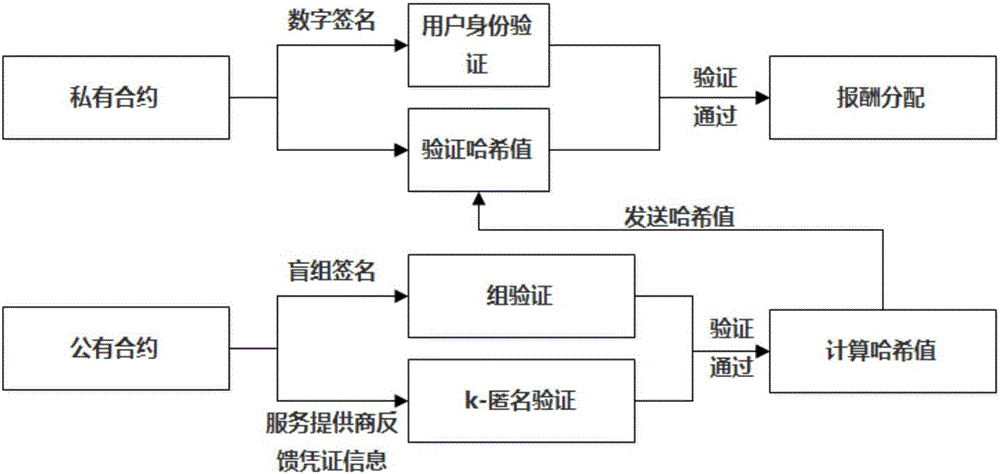
User privacy protection method based on secure smart contract k-anonymity incentive mechanism
ActiveCN107528835AIncrease success rateAvoid safety hazardsKey distribution for secure communicationUser identity/authority verificationK-anonymityUser privacy
The invention relates to a user privacy protection method based on a secure smart contract k-anonymity incentive mechanism. According to the method, contracts are divided into public contracts and private contracts, the private contracts can be seen only by users in an anonymous group, the public contracts are encrypted through group keys to be prevented from being viewed by outsiders, and the private contracts and the public contracts are jointly verified, such that the security when the users request service is effectively guaranteed. According to the invention, the users can be encouraged to join the k-anonymous group and apply decentralized smart contracts such that potential security risks in a trusted center can be avoided; a part of information of the public contracts is encrypted by use of the group keys so that transaction relations are hidden; and joint verification is carried out by use of the private contracts and the public contracts and group verification is performed by use of a blind group signature such that the k-anonymous success rate is improved while the security is guaranteed.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
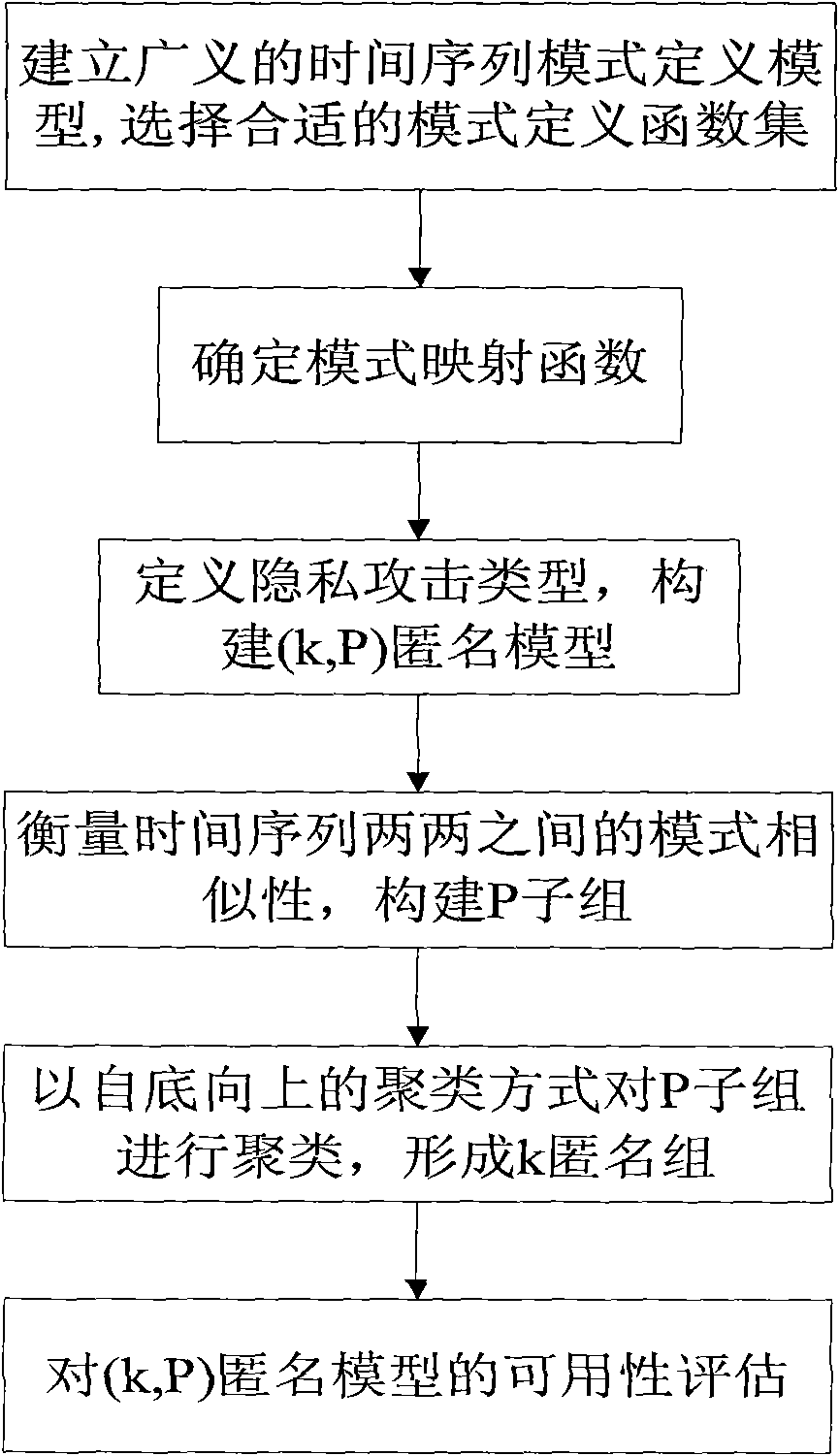
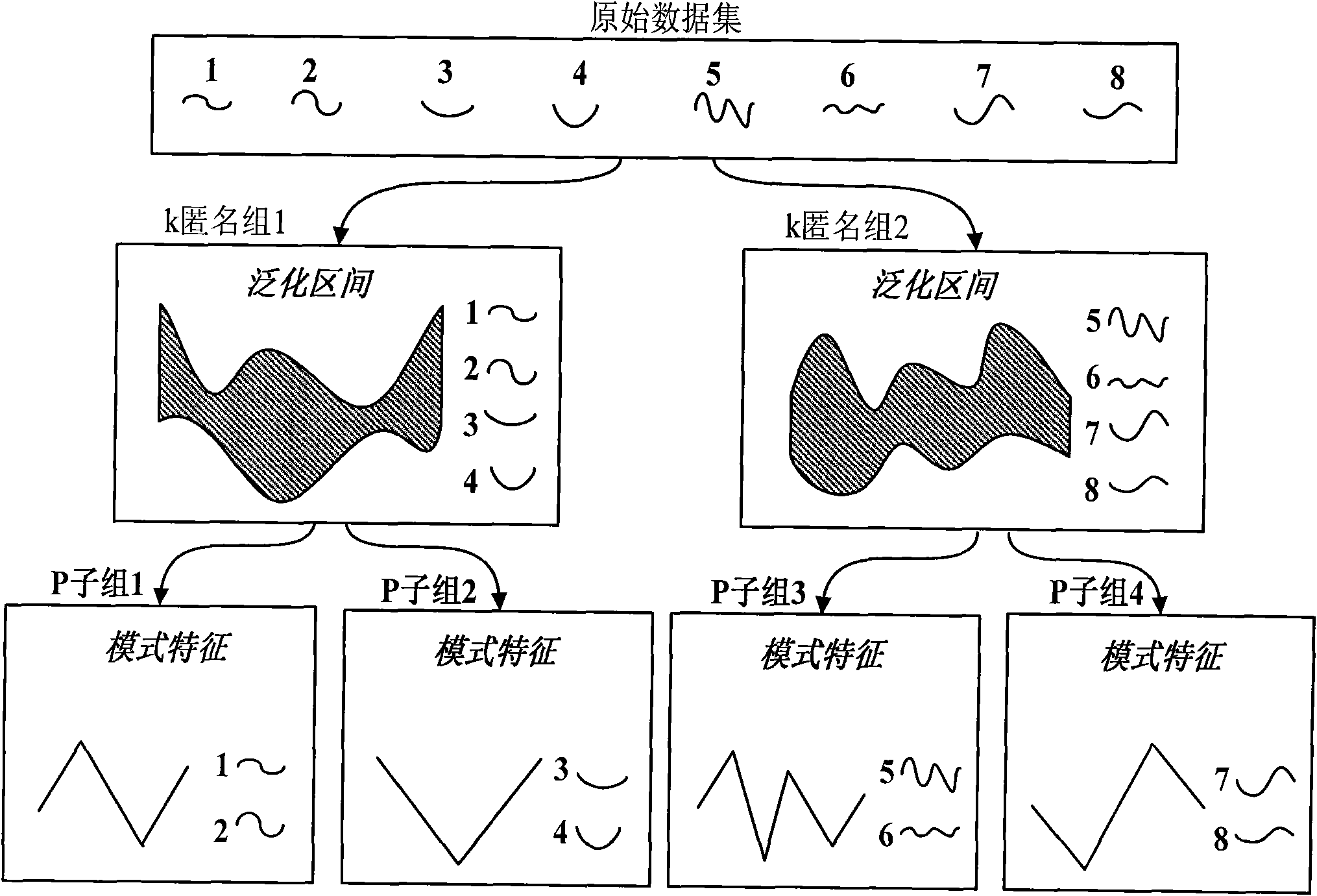
Privacy protection method for mode information loss minimized sequence data
InactiveCN101964034AGuaranteed availabilityDigital data protectionSpecial data processing applicationsK-anonymityData privacy protection
The invention discloses a privacy protection method for mode information loss minimized sequence data. The method comprises the following steps of: confirming a model defined function set based on a generalized mode definition model and a practical application requirement, based on which selecting a mode mapping function capable of realizing minimized mode information loss so as to extract a mode feature, confirming the privacy attack type based on the background knowledge of an attacker, and exerting a (k, P) anonymity mode on a QI attribute value of a time sequence and the mode feature based on a k anonymity technique, wherein the mode separately releases the attribute generalized region of the time sequence and the mode feature, minimizes the mode information loss of the time sequence based on ensuring the data privacy and ensures the usability of the data. The (k, P) anonymity mode is compatible with various mode definition ways and has a set of complete usability evaluating system, the integrity and effectiveness of which results in that the (k, P) anonymity mode is extremely relied and widely applied.
Owner:ZHEJIANG UNIV
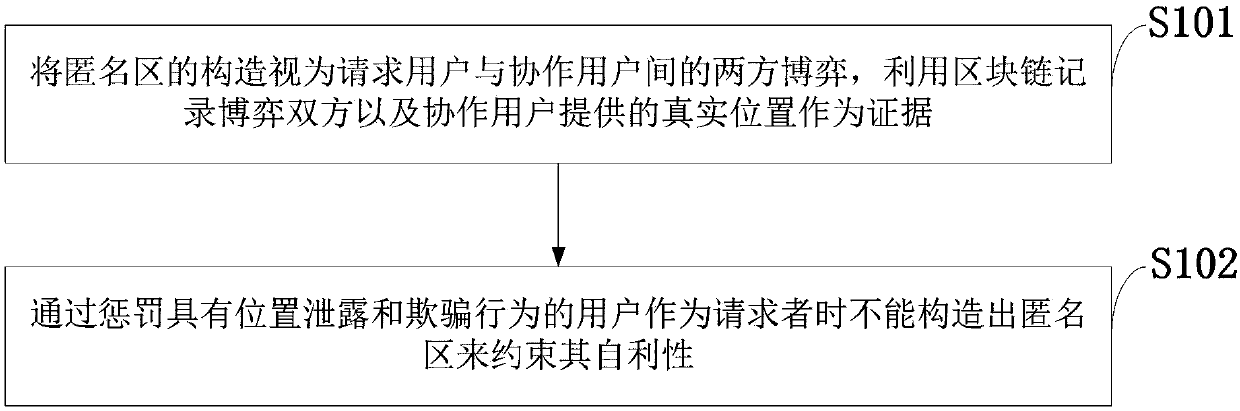
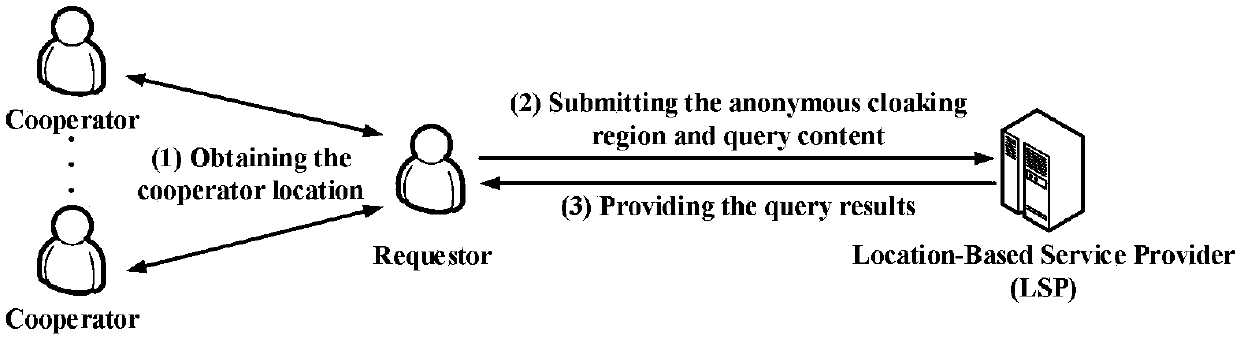
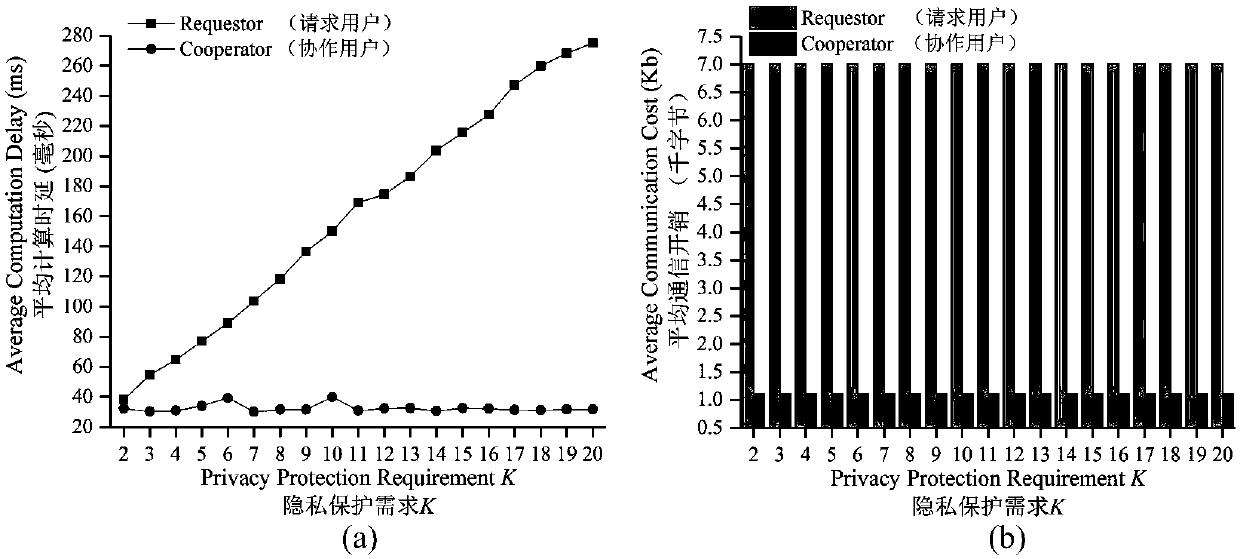
Block chain-based distributed anonymous area cooperative construction method capable of achieving privacy keeping
ActiveCN108173805AGenerate efficientlyProtect location privacyUser identity/authority verificationDigital data protectionK-anonymityBlockchain
The invention belongs to the technical field of privacy protection, and discloses a block chain-based distributed anonymous area cooperative construction method capable of achieving privacy keeping. Construction of an anonymous area is regarded as a two-party game between a request user and cooperative users, the two game parties and locations provided by the cooperation users are recorded by a block chain to serve as evidences, the user having location leakage and cheating behaviors is punished to be not capable of constructing the anonymous area when serving as the requester to restrain theself-interest of the user, and then the block chain-based distributed anonymous area cooperative construction method capable of achieving privacy keeping is proposed. According to the method, the condition that the request user leaks location information of the cooperation users can be prevented, the anonymous area can be efficiently generated while the cooperation users are motivated to provide real locations to participate in anonymous area construction, and the location privacy of the users in distributed K anonymity-based LBS querying is effectively protected.
Owner:XIDIAN UNIV
LBS (Location Based Service) privacy protecting method based on position semantics K-anonymity
ActiveCN104754509AEffective response to privacy attacksIdentity privacy is protected at the same timeLocation information based serviceSecurity arrangementK-anonymityData set
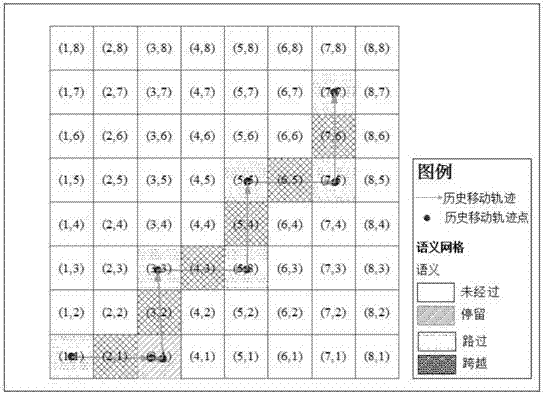
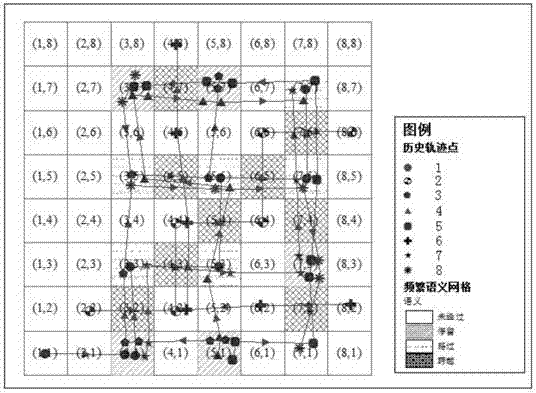
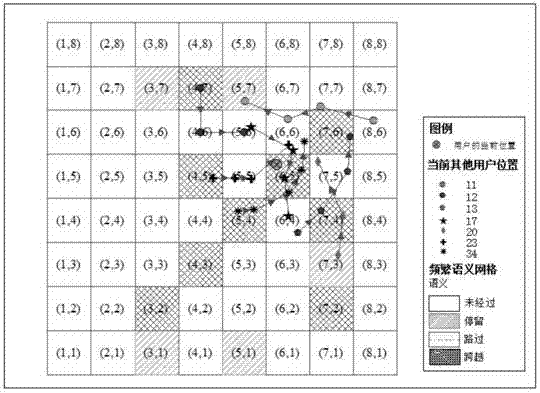
The invention provides an LBS (Location Based Service) privacy protecting method based on position semantics K-anonymity. The method comprises the steps of adopting a collaborative filtering method, and taking a space division grid as a unit to extract position semantic information included by a plurality of movement path data, i.e. obtaining position semantics through analyzing a time-space relationship between the space division grid and the historical data of the user movement; secondly, generating an anonymous data set which realizes simultaneously protecting position semantics privacy, position privacy, identification privacy and inquiry privacy based on the position semantics of the grid. The protecting method provided by the invention has the following advantages: the LBS privacy protecting method can be more conveniently integrated with a traditional time-space K-anonymous method by adopting the method of dividing the space grid to carry out position semantics statistics and expression; furthermore, four semantics, such as remaining, passby, crossing, no-passing and the like, can be generated by analyzing the historical data of the user movement tracks in an LBS analyzation, and the position semantics are more real.
Owner:NANJING UNIV OF POSTS & TELECOMM
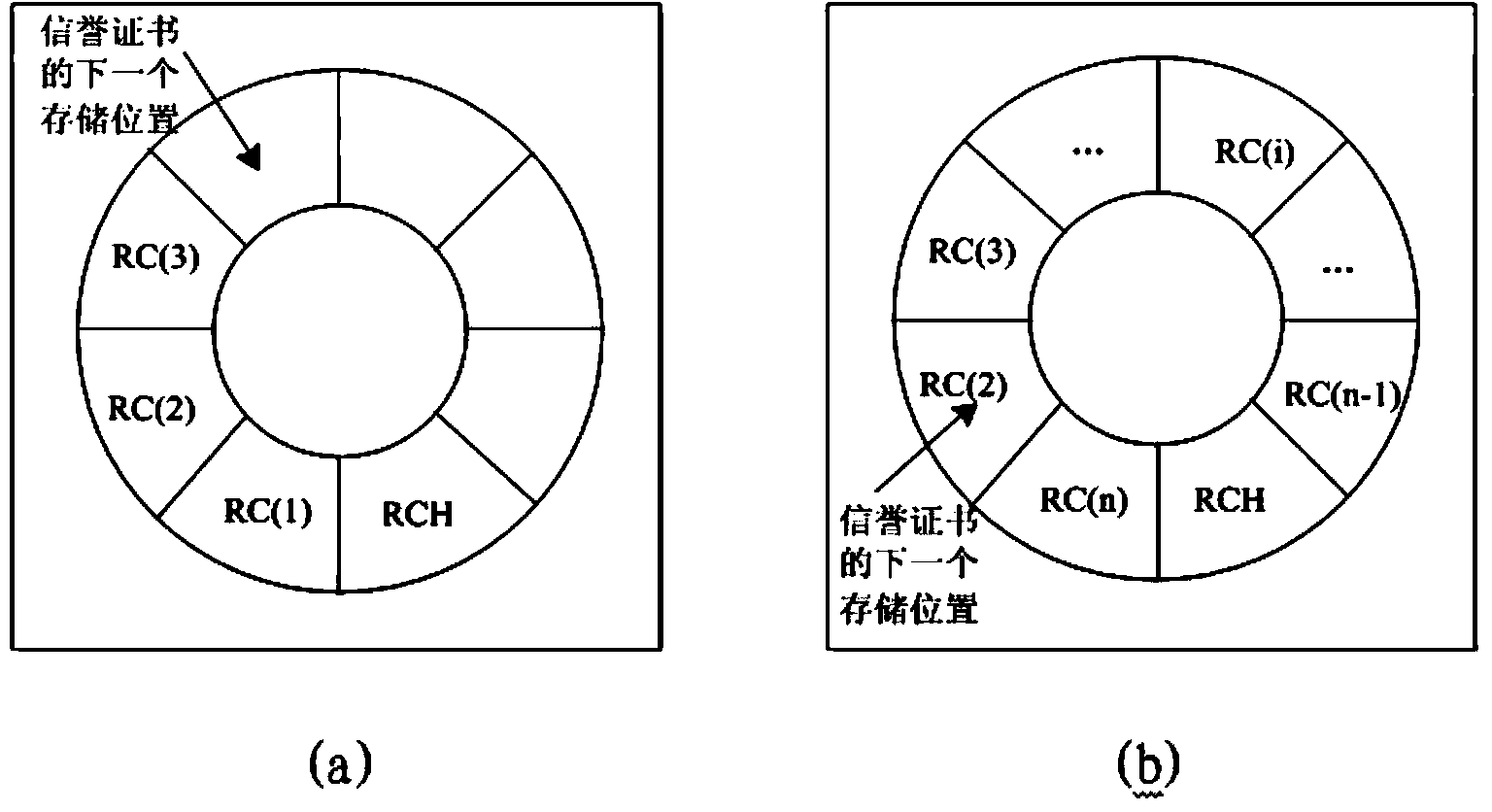
K-anonymity incentive mechanism based on local reputation storage
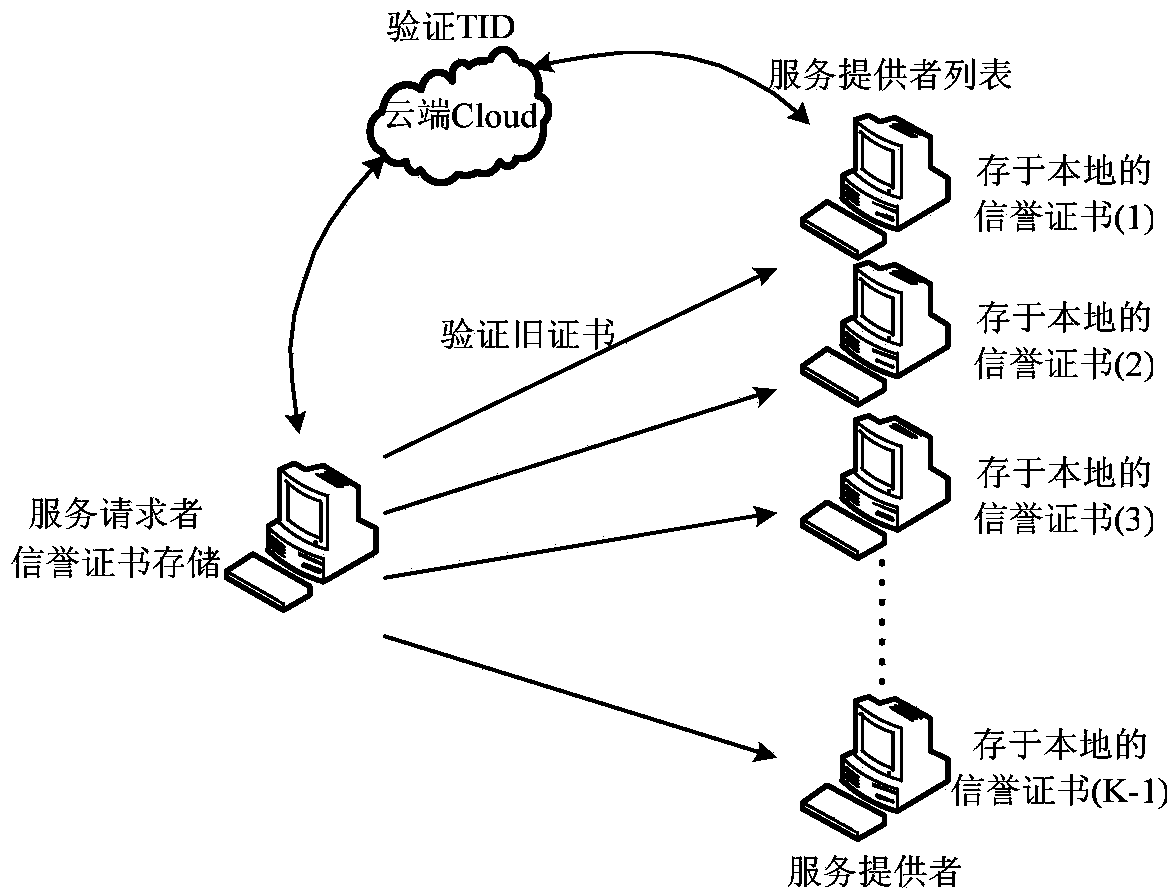
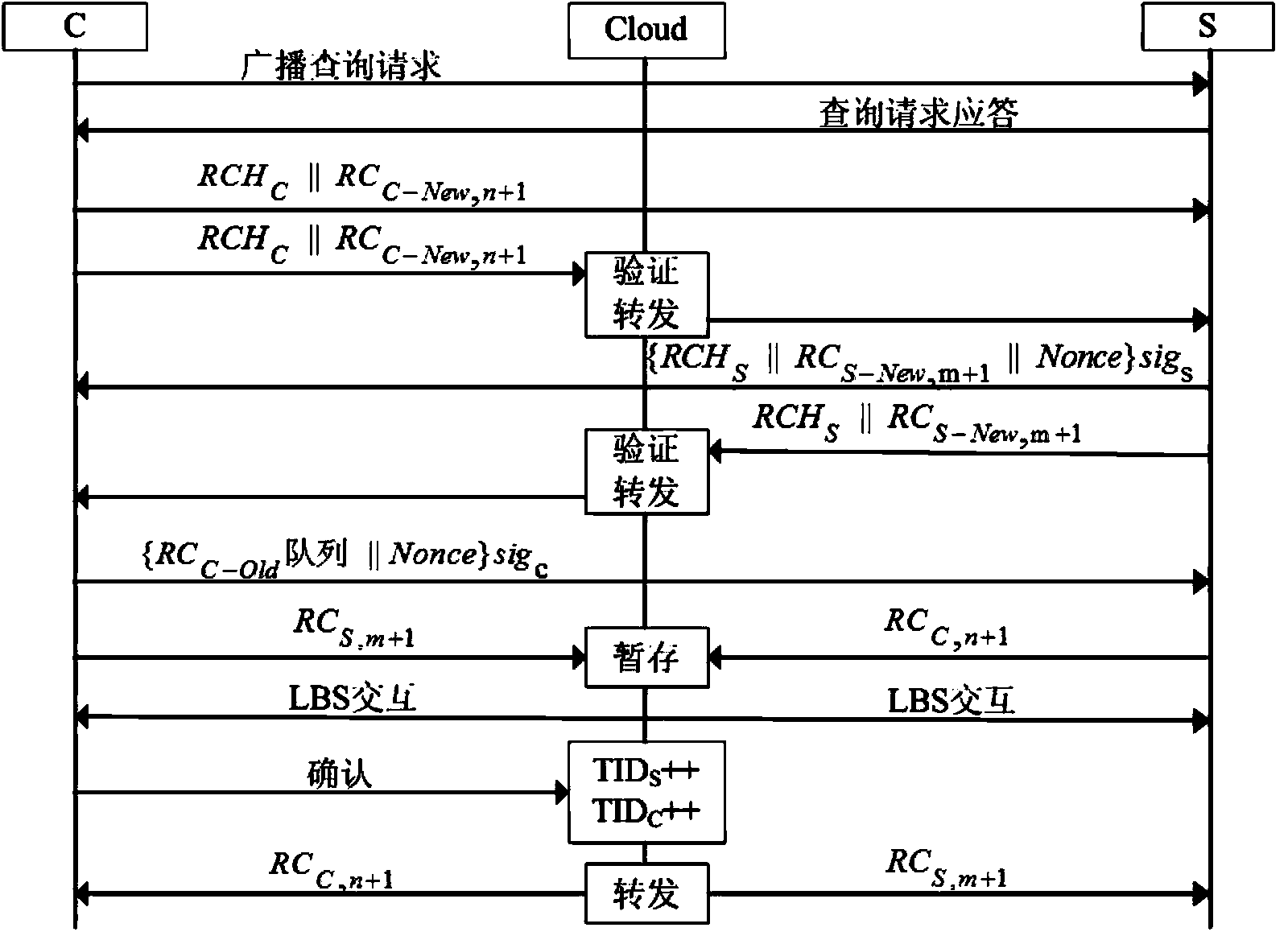
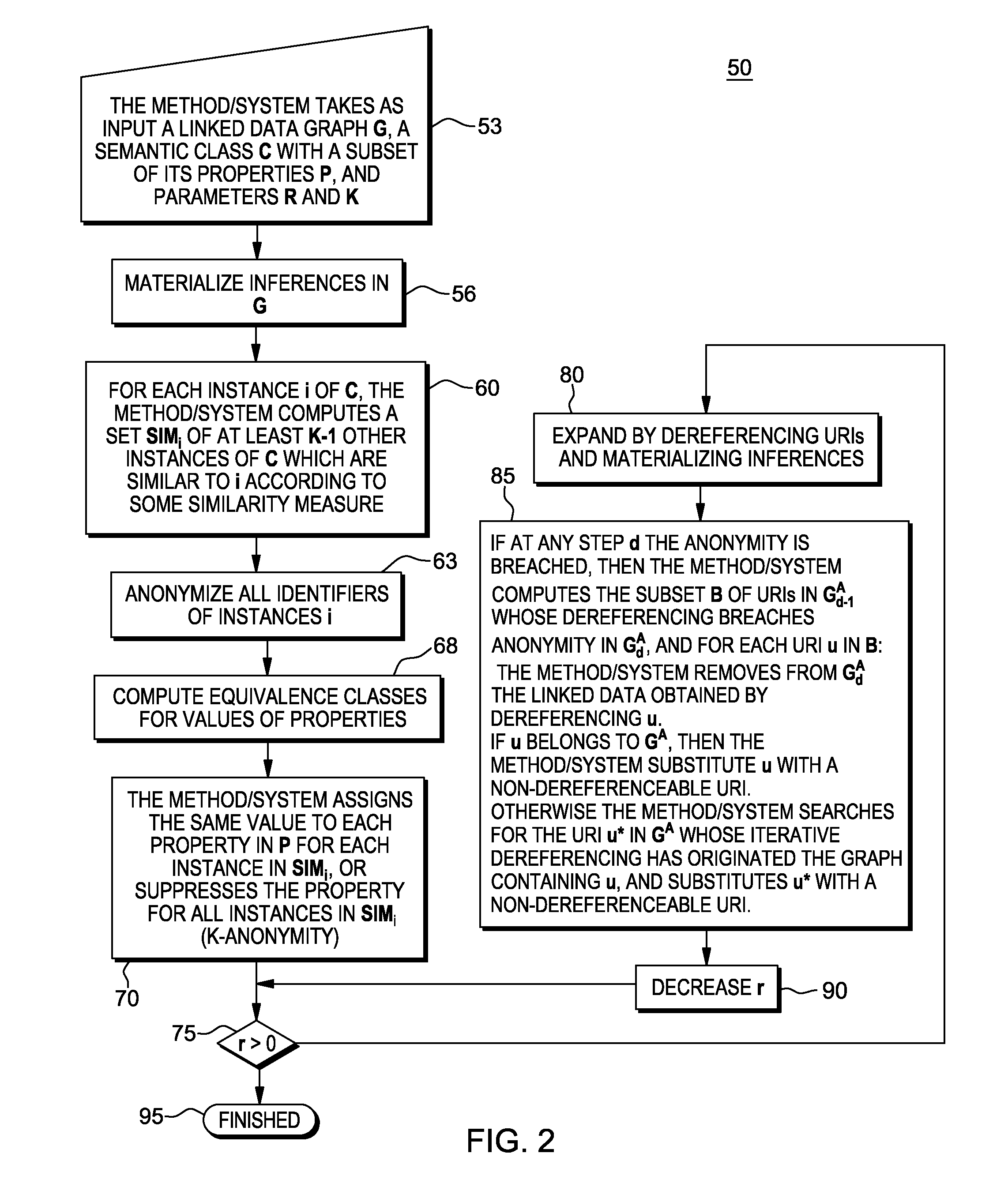
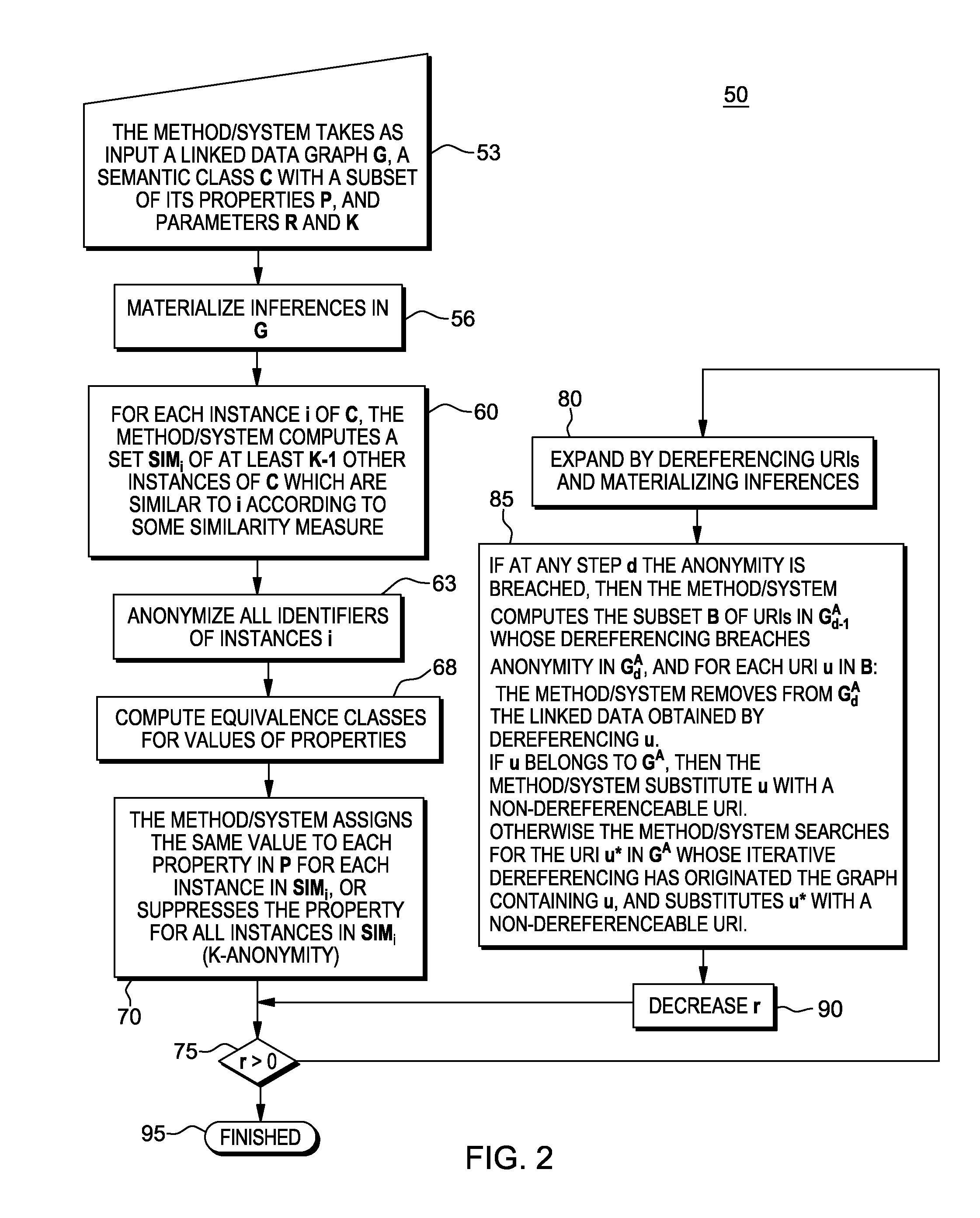
ActiveCN104168563AIncrease motivationTo achieve the effect of continuous motivationLocation information based serviceSecurity arrangementThird partyK-anonymity
The invention discloses a K-anonymity incentive mechanism based on local reputation storage. When a user requests an LBS needing privacy protection, a request for taking part in forming an anonymity region is sent to nearby users in a broadcasting mode, and a service provider list is obtained through returned information; through a third party cloud server, both parties send newly generated reputation certificates to each other and achieve verification, and a service provider verifies all old certificates of the service requester; after the verification is passed, the anonymity region is formed; after an inquiry service is finished, the both parties perform evaluation mutually, a public key is attached to the received reputation certificates of the other party, and then the certificates are sent back to be stored by the other party after signature, so that reputation values are accumulated. Reputation of all nodes is stored locally in a reputation certificate mode, reputation is obtained through providing anonymity services for the adjacent nodes and accumulated, in the future trade, and the anonymity services can be provided for the nodes only after the nodes reach certain reputation threshold values.
Owner:XIDIAN UNIV
False location- and geometry-based location privacy protecting method in location service
ActiveCN104796858ALarge entropyReduce exposureLocation information based serviceSecurity arrangementK-anonymitySide information
The invention provides a false location- and geometry-based location privacy protecting method in a location service and belongs to the technical field of information safety. The method has the advantages that the method is based on a DLS algorithm and uses entropy to allow anonymization degree to be constant, side information which may be mastered by attackers is considered, and the relevance, namely semantic coefficient of locations and inquiry contents and time is also considered; meanwhile, whether the real location of a user contains in the location information in the request message generated by the method or not can be selected freely; due to the fact that the side information which may be utilized by the attackers and the relevance of the locations and inquiry contents and time are considered during false location selection, K anonymity can be achieved, the user can acquire the large-enough entropy, and the exposing probability of the real location of the user is lowered.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
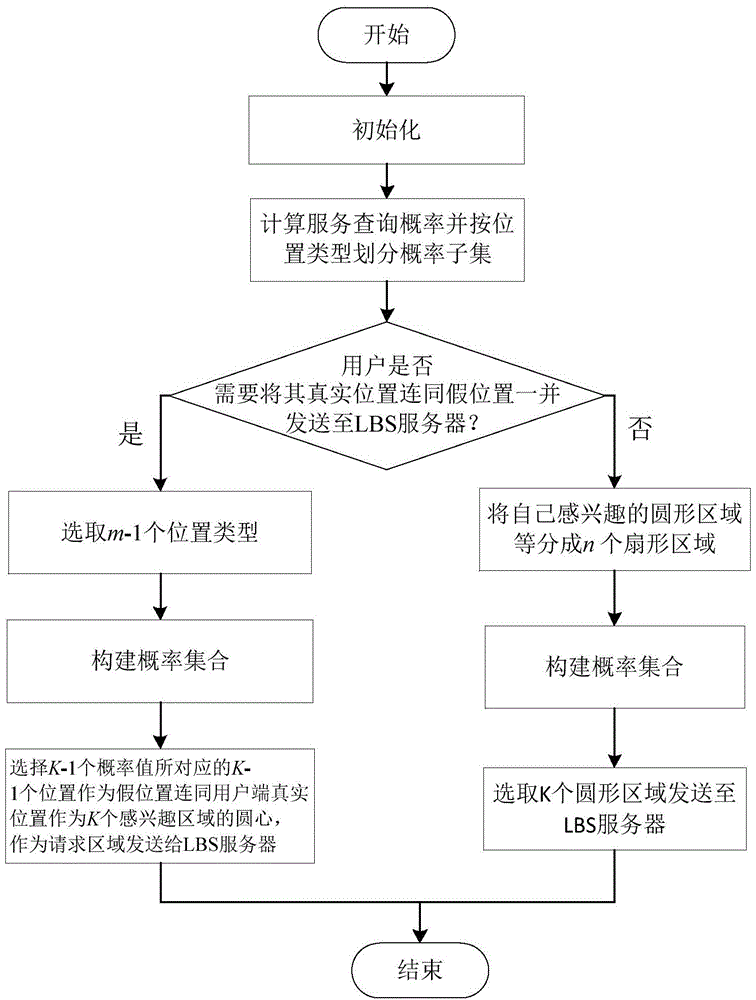
Personalized dual hiding method based on location-based service privacy protection
ActiveCN104184742ARealize double privacy protectionAvoid security issuesLocation information based serviceTransmissionPersonalizationK-anonymity
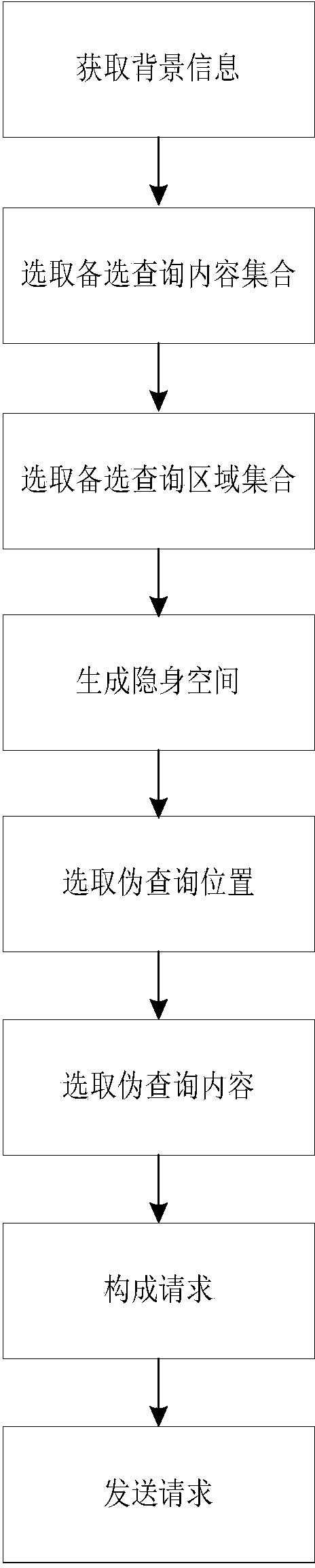
The invention discloses a personalized dual hiding method based on location-based service privacy protection. The personalized dual hiding method overcomes the defects that single-point leakage is caused by the adoption of a trusted third party in the prior art and location privacy or inquiry privacy is achieved singly. The personalized dual hiding method comprises the following steps of (1) obtaining background information, (2) selecting an alternative inquiry content set, (3) selecting an alternative inquiry region set, (4) generating a hiding space, (5) selecting a false inquiry location, (6) selecting false inquiry content, (7) constituting a request, and (8) sending the request. By the adoption of the k-anonymity technology, the 1-diversification technology and the space hiding technology, personalized dual privacy protection of location privacy and inquiry privacy of a mobile object is achieved.
Owner:XIDIAN UNIV
LBS (location-based service) track privacy protecting method
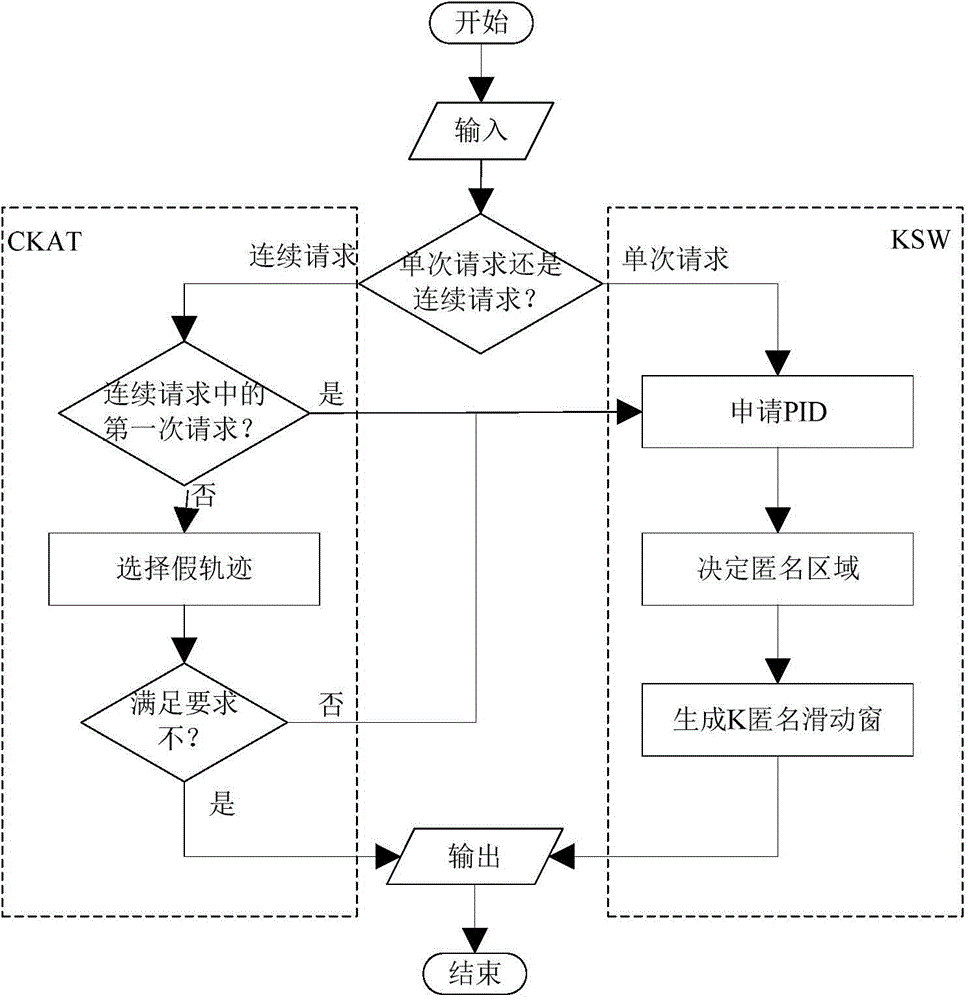
ActiveCN104618897AProtect track privacy and securityTrajectory privacy security enhancementSecurity arrangementK-anonymityInternet privacy
The invention discloses a simple and effective track privacy protecting method and belongs to the technical field of information safety. The track privacy protecting method is low in calculating cost and high in practicality. The track privacy protecting method is based on the DLS (dynamic list scheduling) algorithm, introduces the definition of side track probability and comprehensively takes single request and continuous request of LBS into consideration, and accordingly can effectively protect the location privacy of users under the condition of single request and effectively protect the track privacy of the users under the condition of continuous request. The track privacy protecting method solves associated privacy safety problems caused by traditional K-anonymity technology applied to the LBS continuous request.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
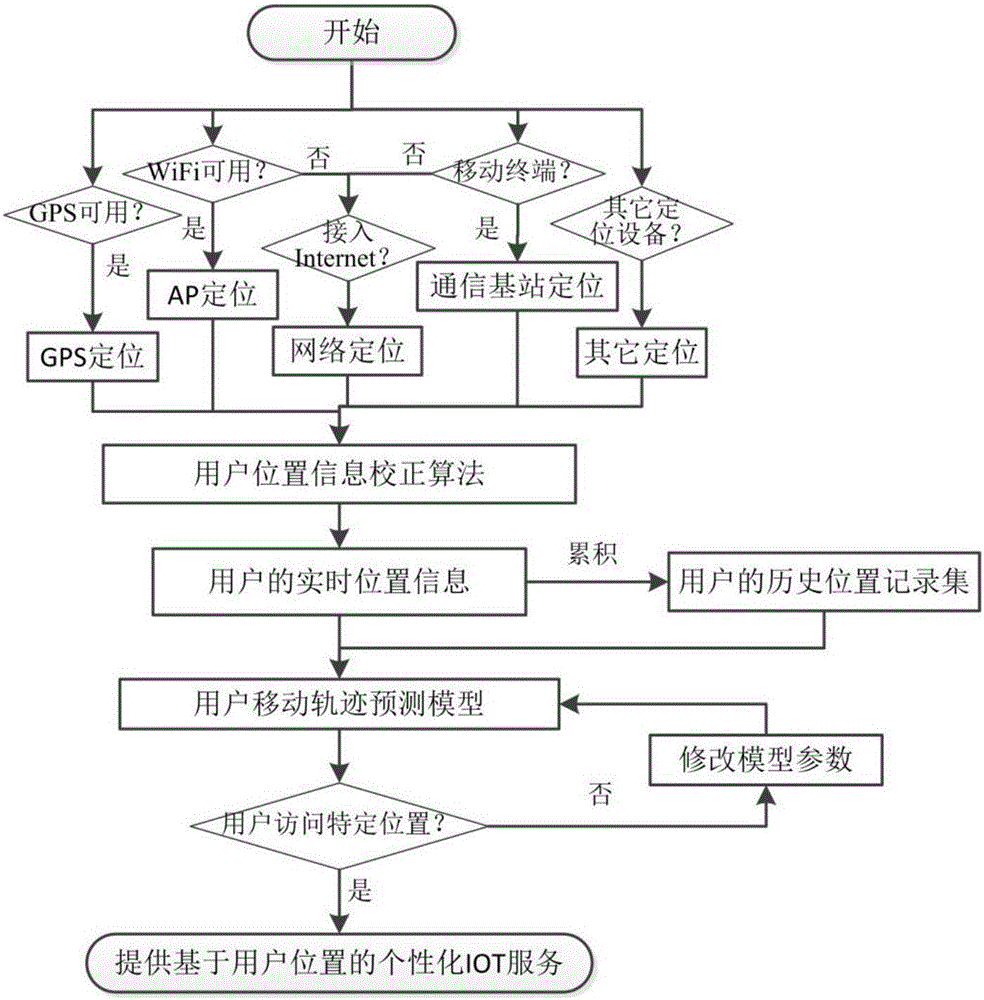
Location based individual internet of things service system user privacy protection method
ActiveCN105930738AConvenient query processingAvoid location privacy leaksDigital data protectionSpecial data processing applicationsK-anonymityRegression analysis
The invention belongs to the technical field of application of the internet of things, and relates to a location based individual internet of things service system user privacy protection method. An k-anonymity of a current location and hiding of a movement path of a user can be achieved based on the k-anonymity of regression analysis, a user location of information pre-fetching, and a movement path hiding method; a mobile user can adopt a protection measure in real time according to the demands of privacy protection of locations of the mobile user, and can determine a protection level of the location of the mobile user; a system starts a corresponding privacy protection mode according to the type of a service application program used by the user, and allows the mobile user to automatically control the level and the time of location hiding while the mobile user uses a location service; and the user can protect his privacy information to the great extent while enjoying conveniences brought by a location based individual internet of things service.
Owner:QINGDAO UNIV OF SCI & TECH
Mixed randomization privacy protection method of social network data dissemination
ActiveCN103902924ADoes not affect the natureDoes not affect qualityData processing applicationsDigital data protectionThird partyK-anonymity
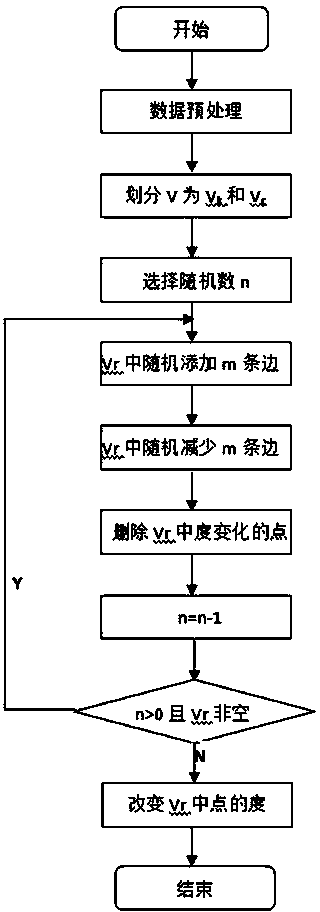
The invention discloses a mixed randomization privacy protection method of social network data dissemination. The mixed randomization privacy protection method includes the steps that top points V of an undirected graph G(V,E) for expressing social network data are divided into a set Vk and a set Vr according to degree numbers with k-anonymity as a condition, wherein the set Vk comprises the points with the degree numbers meeting the k-anonymity condition, and the set Vr comprises the points with the degree numbers not meeting the k-anonymity condition; the points in the set Vk are not processed; randomization protection processing is carried out on the points in the set Vr. According to the mixed randomization privacy protection method, an existing k-anonymity method and an existing randomization method are combined, the number of users of the social network is not changed, influences on the nature and the quality of data provided for third parties are small, the processing process is simple, and the processing speed is high; after processing is carried out, the social network data of each person can be in one of the two following protection states: the degree natures are not changed, and the social network data of the person are located in other at least k persons same as the person in degree nature, or the degree natures are changed; relocation attacks with structure background knowledge can be prevented through the protection, and the demands of the users of the social network for the privacy safety are met.
Owner:北京睿航至臻科技有限公司
Privacy protection encryption method based on homomorphic encryption, information data processing terminal
InactiveCN109039578AReduce computing costReduce communication costsKey distribution for secure communicationEncryption apparatus with shift registers/memoriesK-anonymityHash function
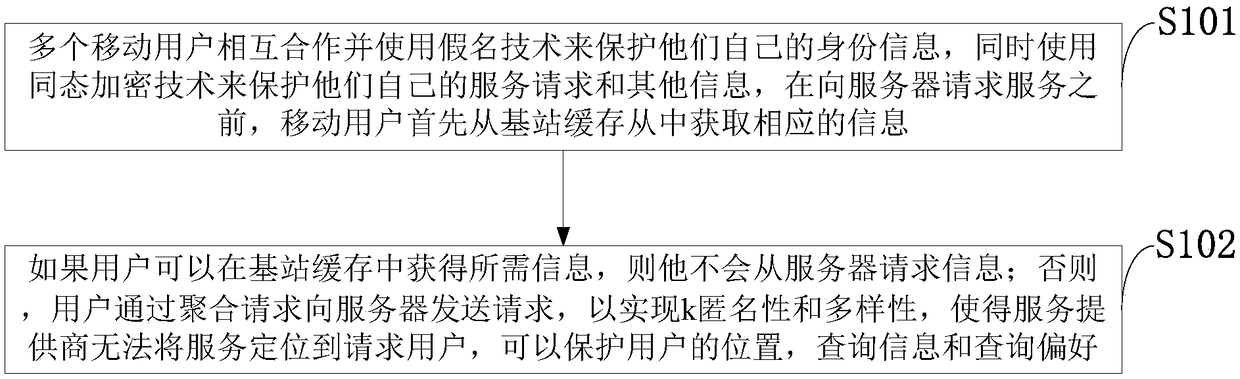
The invention belongs to the technical field of data processing characterized by protocol, and discloses a privacy protection encryption method based on homomorphic encryption, and an information dataprocessing terminal. The method includes: selecting hash function and a secure symmetrical encryption algorithm such as AES as encryption, using public-private key pair to enhance privacy protection,and realizing the request service to multiple users. The invention enables multiple mobile subscribers to cooperate with each other and to use pseudonym techniques to protect their own identity information, at the same time, homomorphic encryption technology is used to protect their own service requests and other information, if the user can get the required information in the base station cache,he will not request the information from the server, which can reduce the risk of exposing the sensitive information of the user; Otherwise, the user sends the request to the server through the aggregation request to realize k anonymity and diversity, which makes it impossible for the service provider to locate the service to the requesting user, which can protect the user's location, query information and query preferences.
Owner:CHONGQING UNIV OF EDUCATION
Trajectory privacy protection method in road network environment
InactiveCN106650486AHigh Anonymous Success RateImprove data availabilityCharacter and pattern recognitionDigital data protectionK-anonymityUndirected graph
The invention discloses a trajectory privacy protection method in a road network environment, and relates to the technical field of trajectory privacy protection methods. The method includes the following steps of trajectory data preprocessing, wherein original trajectory data is divided into equivalence class trajectories with the same trajectory cross-domain time quantum; trajectory graph construction, wherein the equivalence class trajectories are constructed into a trajectory graph according to the s-space overlapping concept; trajectory graph division, wherein the trajectory graph is divided into multiple subgraphs with the greedy algorithm, each subgraph contains at least k trajectory graph vertexes, and thus a trajectory k-anonymity set is just formed. According to the method, the trajectory data is simulated into an undirected graph, trajectory k-anonymity is achieved through k-node division of the graph, and the anonymity success rate is high; besides, the availability of data obtained after privacy protection is high.
Owner:HEBEI UNIVERSITY OF ECONOMICS AND BUSINESS
Location tag based LBS track privacy protection method
ActiveCN104936141AProtect location privacyProtect track privacyLocation information based serviceSecurity arrangementK-anonymityInformation security
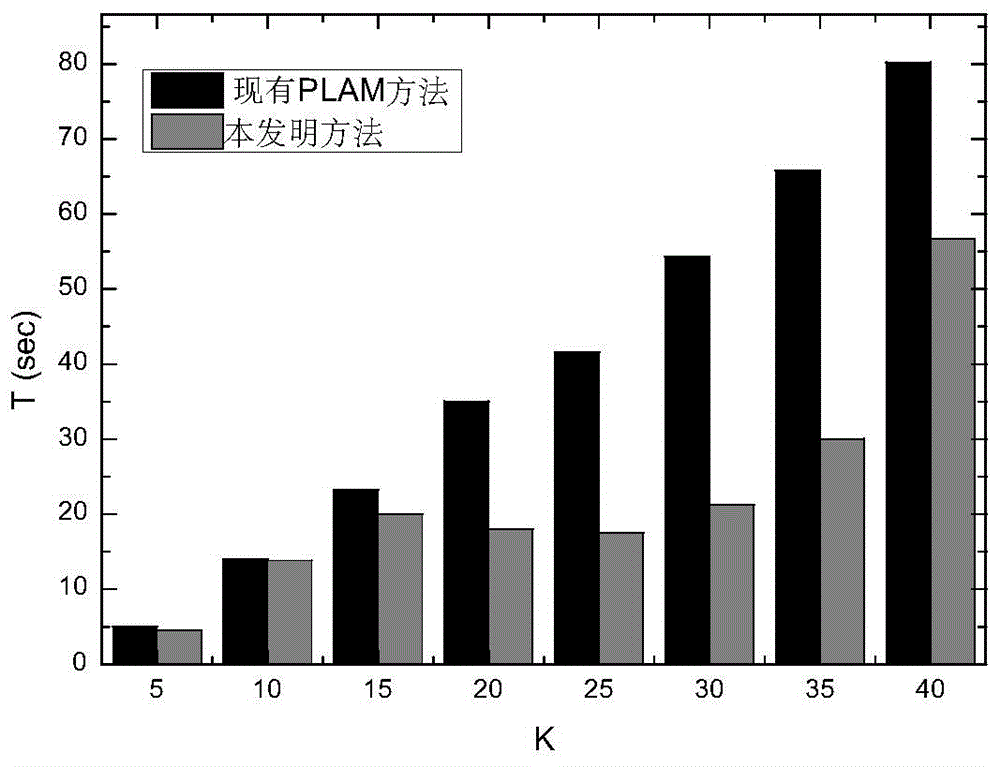
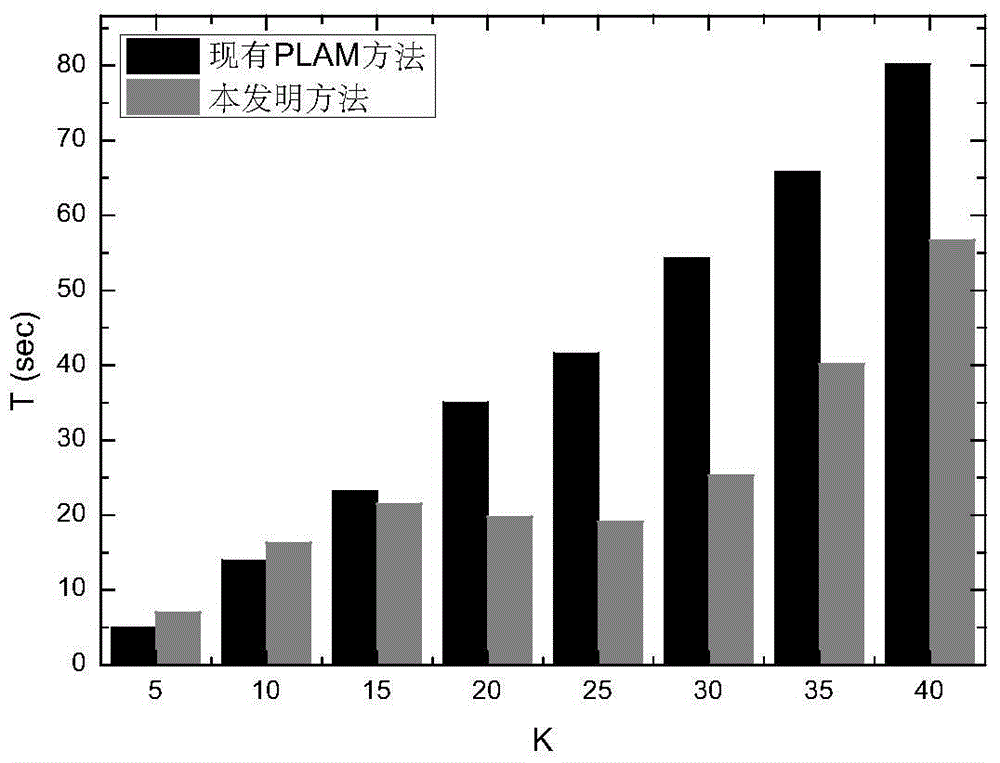
The invention provides a location tag based LBS track privacy protection method, and belongs to the technical field of information safety. The track privacy protection method based on a PLAM method combines K anonymity with L diversification, sensitive locations are divided from common locations in a service are of an LBS system, the user identity is prevented from being identified by an attacker by utilizing a PID exchange method, linkage between a user and the track is cut off, and thus, the track privacy of the user is protected. The method of the invention is low in calculation cost, the capability of privacy protection is high, and the method is completely suitable for the LBS system which serves large amount of clients.
Owner:UNIV OF ELECTRONIC SCI & TECH OF CHINA
A k-anonymity-based Location and Data Privacy Protection Method in Population Intelligence Perception
ActiveCN109214205AProtect personal locationGuaranteed Privacy of OwnershipDigital data protectionPlatform integrity maintainanceSensing dataK-anonymity
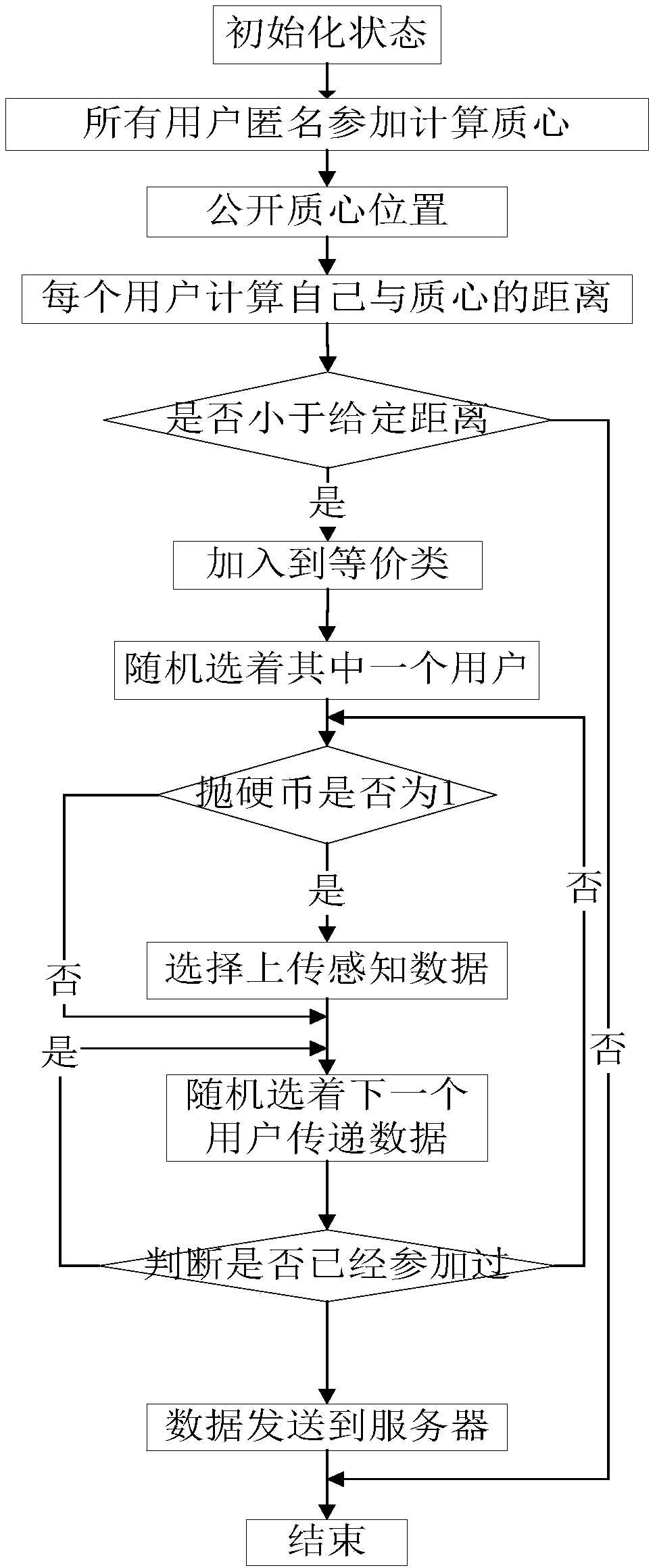
The invention discloses a population intelligence perception method based on k-anonymous location and data privacy protection method comprises the following steps of: (1) constructing an equivalent class: an equivalent class is a group composed of N users, each user has the functions of sensing data and uploading data directly to a server; in the equivalent class, all users are independent and donot trust each other; (2) Data iteration: a user is randomly selected as the first user in the equivalent class, and the user judges whether to upload perceptual data in the form of flipping a coin. If the user uploads the perceptual data, the perceptual data and the transmitted data are transmitted to the next random user, and if the user does not upload, the transmitted data is only transmittedto the next randomly selected user. And so on until all the users in the equivalent class are active and all the data is uploaded to the server. The invention can effectively protect the privacy of the perceived user's personal position and the data privacy from being disclosed.
Owner:ANHUI NORMAL UNIV
Privacy protection method for mobile terminal during running position-based service
InactiveCN104754506AShorten the timeImprove service accuracyLocation information based serviceSecurity arrangementK-anonymityTree (data structure)
The invention discloses a privacy protection method for a mobile terminal during running position-based service. The privacy protection method makes an attacker cannot distinguish the position of a user through a k-anonymity principle so as to protect the position privacy. An anonymous server constructs a quad-tree data structure, a plane space is recursively divided into four square zones with the same area, each user in each square zone sends a position privacy requirement Q {Pos (x, y), k, dist} to the anonymous server, the anonymous server constructs a data structure for each leaf node of the quad-tree according to the anonymous privacy requirements of the users, wherein the position privacy requirements of all the users in each square zone are stored in the anonymous server, and the anonymous server can quickly query the users who meet the anonymity degree k and space tolerance dist in the zone with the user according to the data structure maintained by the leaf node of the user and form an anonymous zone.
Owner:CHANGSHU RES INSTITUE OF NANJING UNIV OF SCI & TECH
Position privacy protection method combining k-anonymity and cloud end
ActiveCN104717292AQuality improvementWithout compromising accuracyTransmissionLocation information based serviceK-anonymity
The invention discloses a position privacy protection method combining k-anonymity and the cloud end. The method is based on position k-anonymity, the cloud end technology is adopted, and by means of a large number of data of the cloud end, it is guaranteed that the situation that anonymity of an anonymous server fails due to the fact that the k value is not reaches is avoided. The method is simple and easy to achieve, distribution position information precision does not need to be reduced while mobile user position privacy is protected, and a user obtains satisfying position service. Even if the anonymous server is attacked by an attacker, the attacker only obtains useless or false information stored at the cloud end and can not obtain real information of the user, and position privacy of the user is further protected.
Owner:NANJING UNIV OF POSTS & TELECOMM
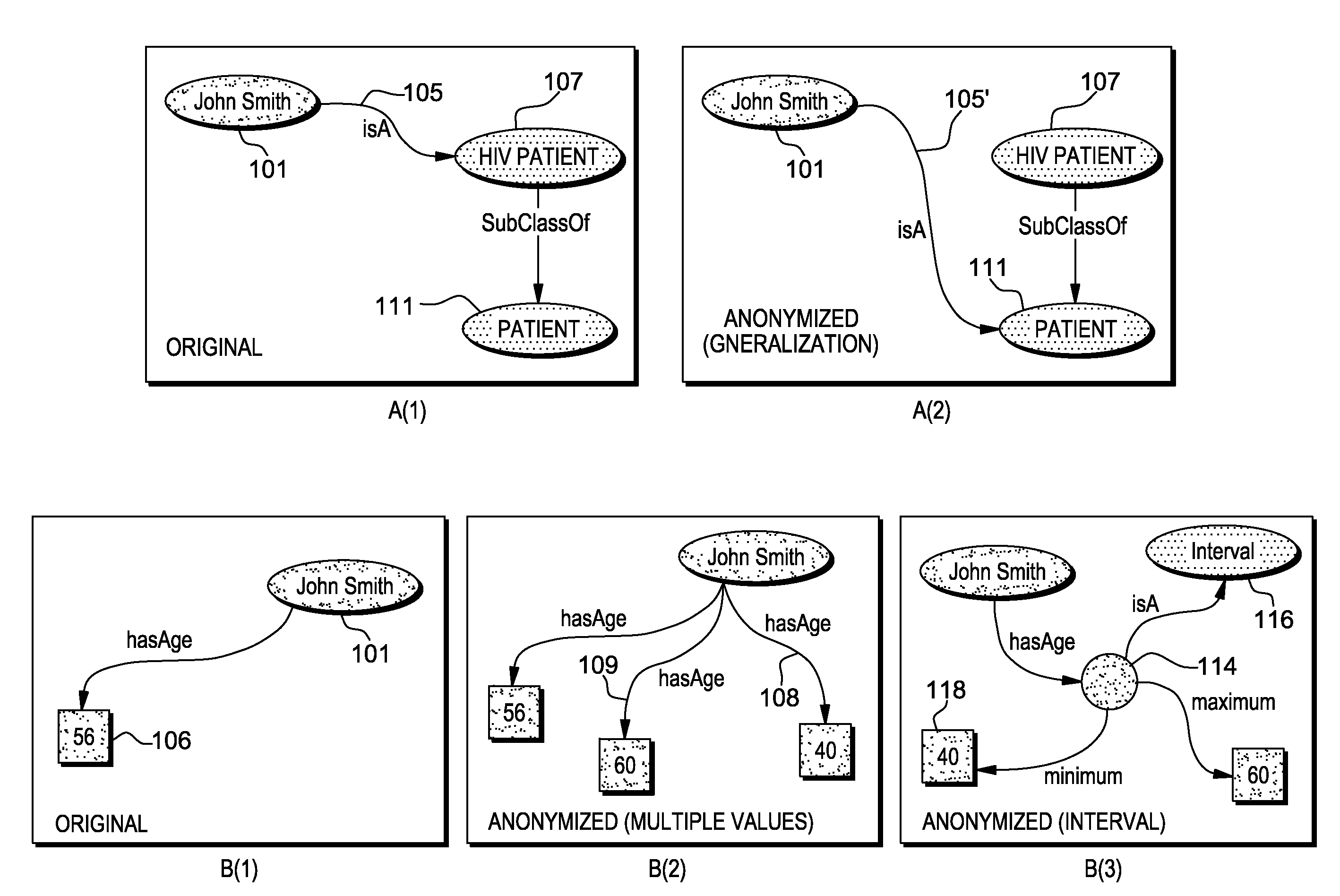
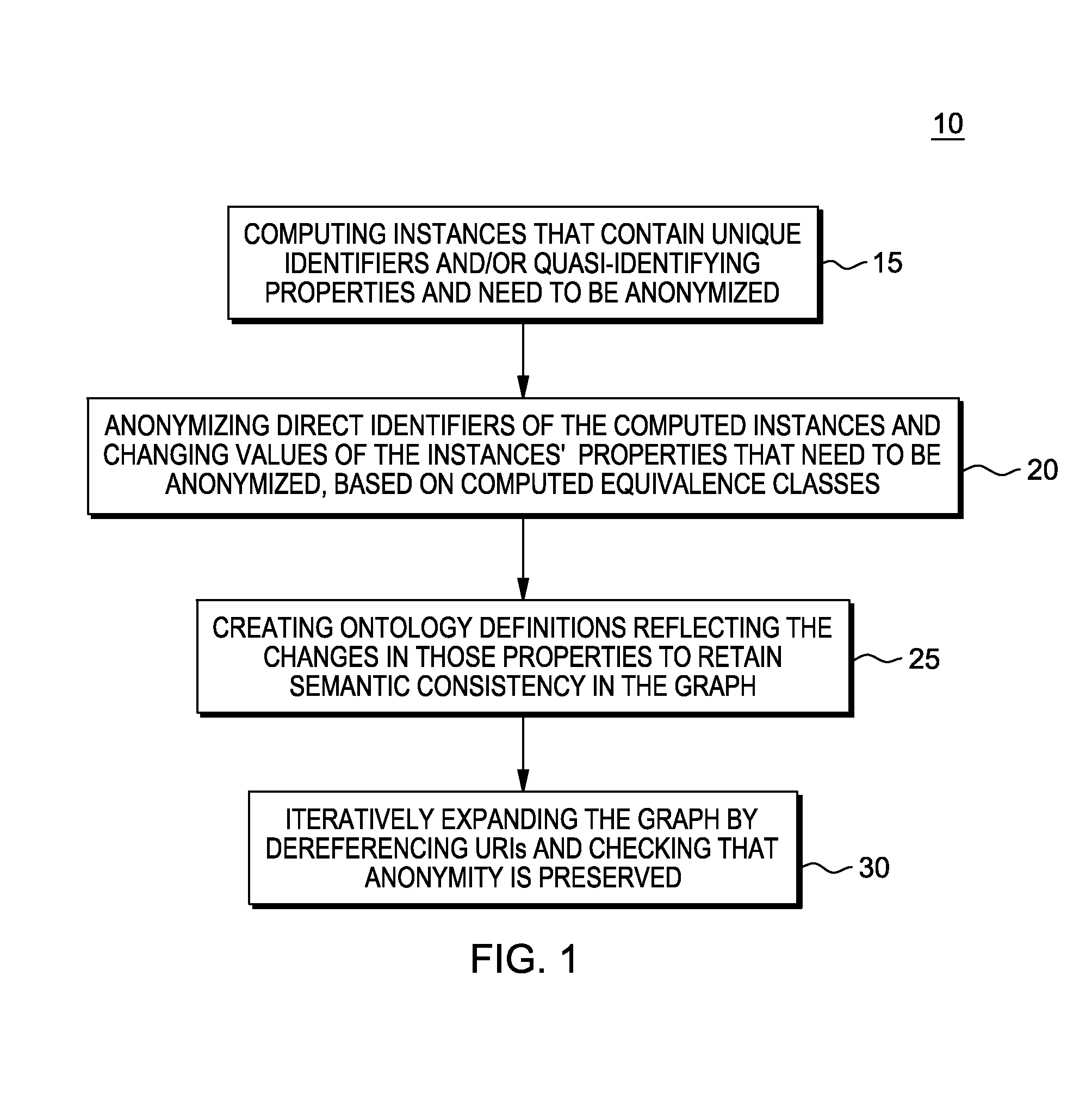
Guaranteeing anonymity of linked data graphs
A method, system and computer program product for transforming a Linked Data graph into a corresponding anonymous Linked Data graph, in which semantics is preserved and links can be followed to expand the anonymous graph up to r times without breaching anonymity (i.e., anonymity under r-dereferenceability). Anonymizing a Linked Data graph under r-dereferenceability provides privacy guarantees of k-anonymity or l-diversity variants, while taking into account and preserving the rich semantics of the graph.
Owner:IBM CORP
Guaranteeing anonymity of linked data graphs
InactiveUS20140325666A1Digital data processing detailsAnalogue secracy/subscription systemsK-anonymitySemantics
A system and computer program product for transforming a Linked Data graph into a corresponding anonymous Linked Data graph, in which semantics is preserved and links can be followed to expand the anonymous graph up to r times without breaching anonymity (i.e., anonymity under r-dereferenceability). Anonymizing a Linked Data graph under r-dereferenceability provides privacy guarantees of k-anonymity or l-diversity variants, while taking into account and preserving the rich semantics of the graph.
Owner:IBM CORP
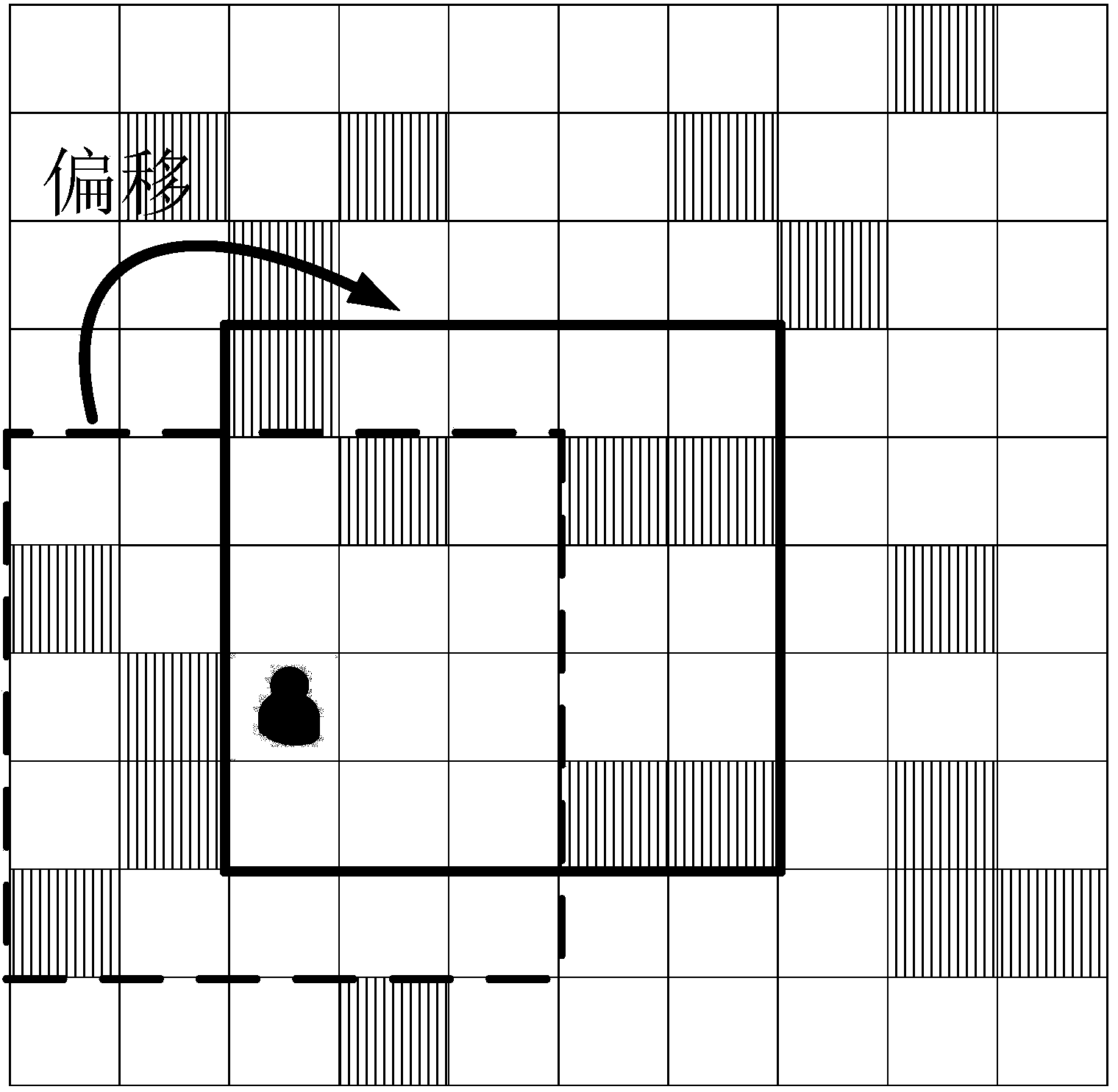
Dynamically adjustable k-anonymity position privacy protection method in VANET (Vehicular Ad hoc Network)
ActiveCN106992991ATo meet the different needs of service qualityMeet different needsTransmissionQuality of serviceK-anonymity
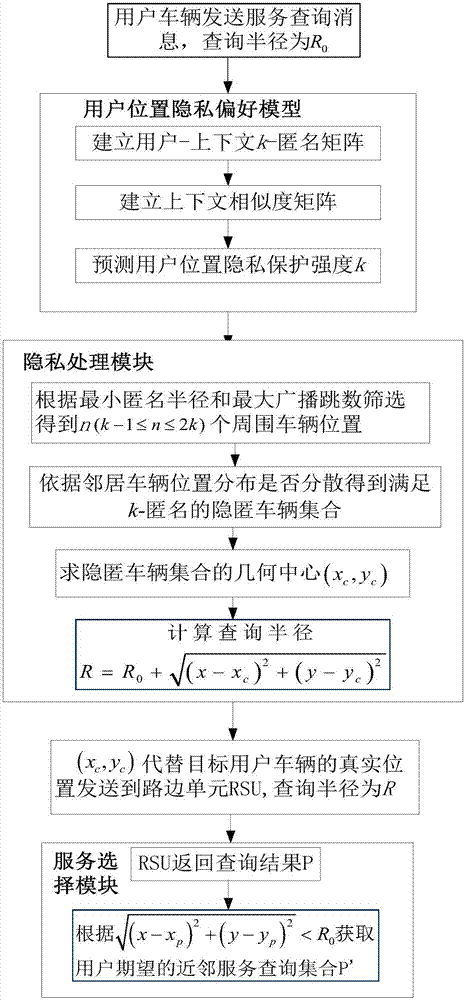
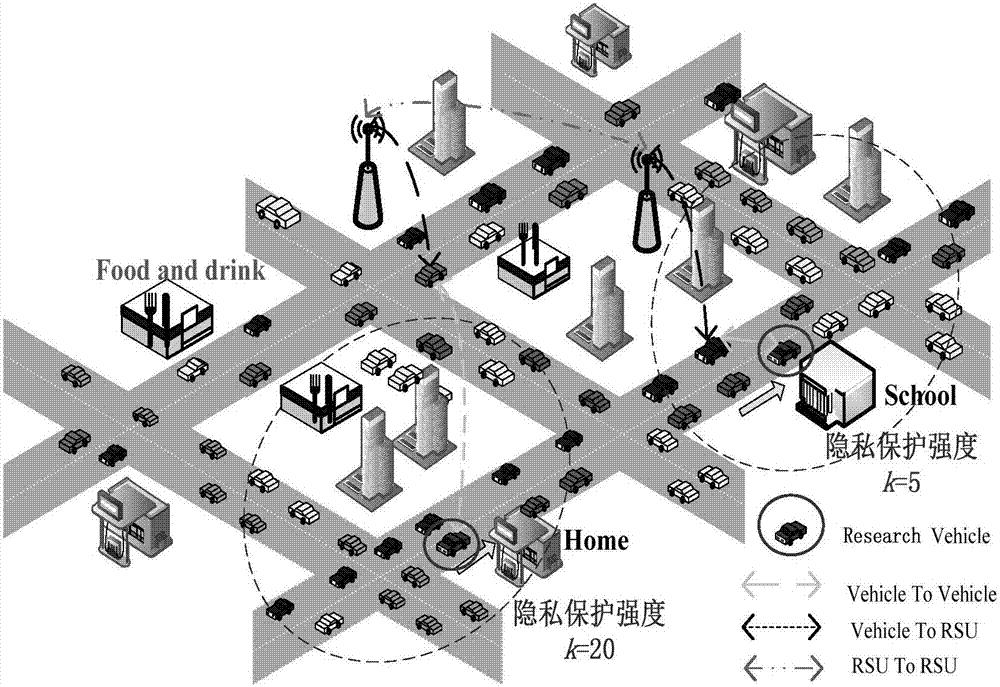
The invention discloses a dynamically adjustable k-anonymity position privacy protection method in a VANET (Vehicular Ad hoc Network). Position privacy preferences of users are discovered by mining history behavior data of the users; a position privacy preference model is established and is used for predicting the position privacy preferences of the target users in different contexts; different demands of the users for the quality of service are satisfied by dynamically adjusting position privacy protection degree k values; and through analysis of specific features of the VANET, user vehicles can obtain neighbor vehicle position information through broadcast messages and a trusted third party in a traditional LSB system structure is removed, so the communication cost is reduced, the search efficiency is improved, and a single-point attack is avoided. A cloaked vehicle set satisfying k-anonymity is obtained according to whether the distribution of the neighbor vehicle positions obtained by the user vehicles through the broadcast messages is dispersed or not, an area of a cloaked region CR is improved, and a position privacy protection level is improved.
Owner:HUNAN UNIV
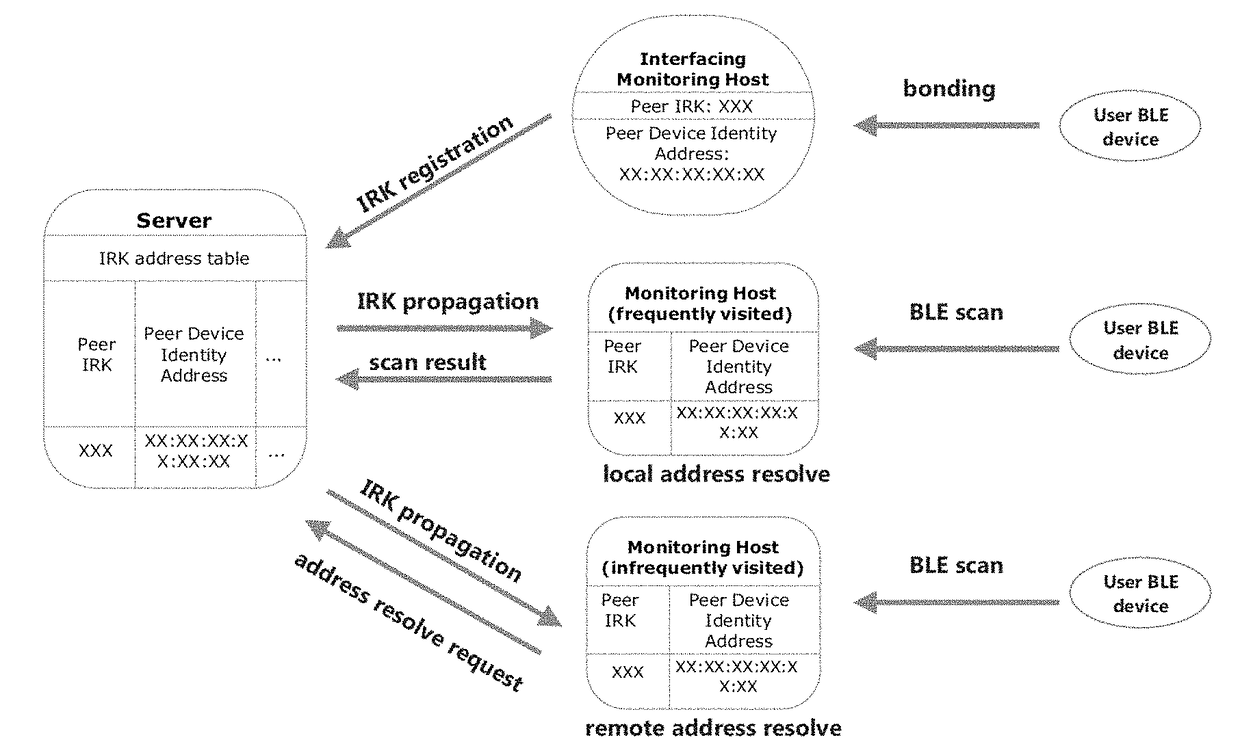
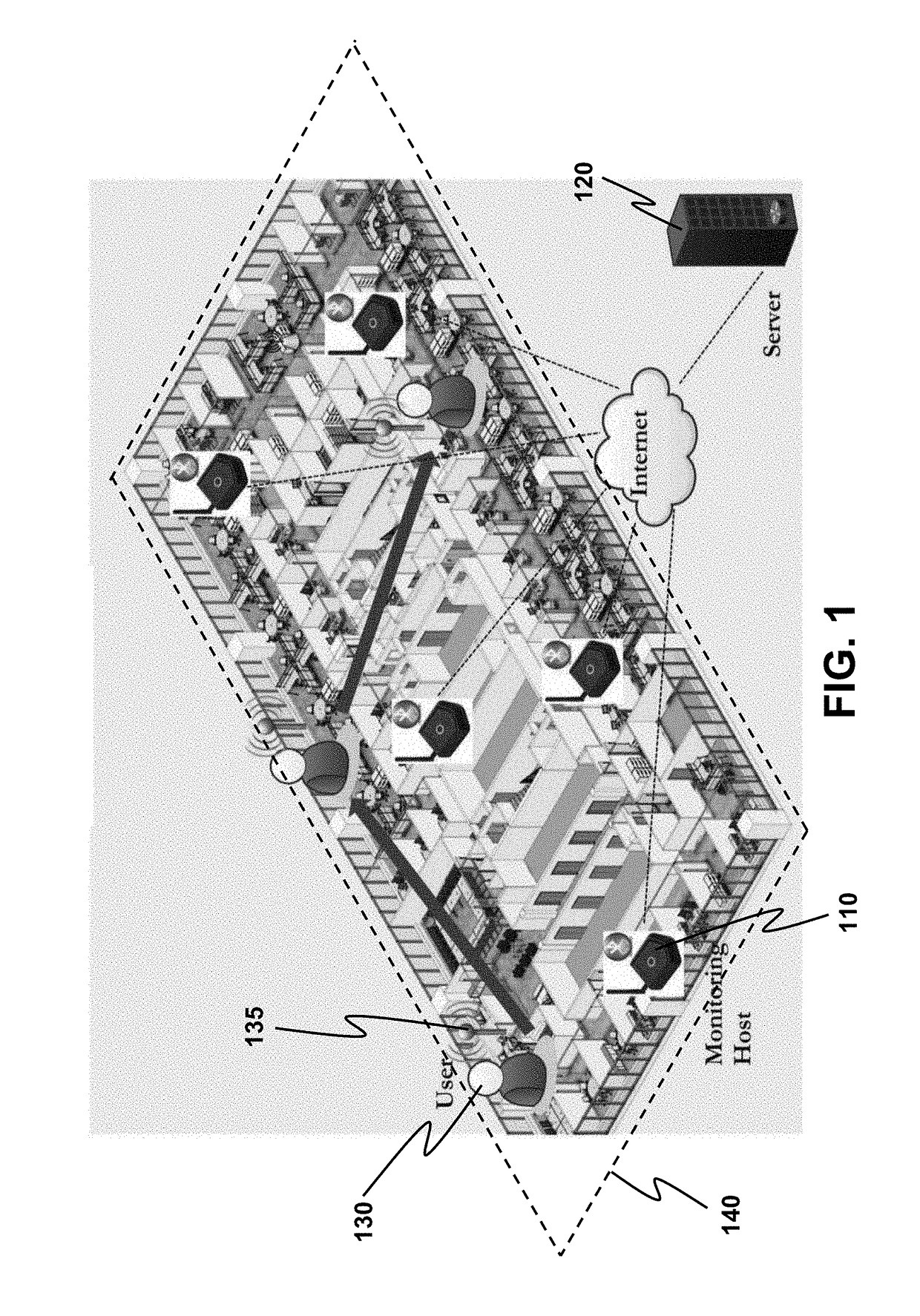
Privacy-preserving large-scale location monitoring
A privacy-preserving location monitoring system is provided, comprising monitoring hosts and a server. Immense resource requirement in large-scale location monitoring is lessened by allowing peripheral devices of users to bond to only one host. A peripheral device's one or more identity resolving keys (IRKs) retrieved by the host are sent to the server so as to register the IRKs to the server. The server propagates the IRKs to all other hosts. Furthermore, each host only stores the IRKs of peripheral devices frequently visiting the host. An incoming IRK not known by the host is sent to the server for resolving an identity of a peripheral device sending this IRK. The system is implementable in Bluetooth Low Energy (BLE) technology. Based on privacy features of BLU, different privacy protection mechanisms, including opt-in / out, k-anonymity and granularity-based anonymity, are provided.
Owner:TWINLY MARKETING TECH LTD
Method for retrieving personalized privacy information on basis of data mapping
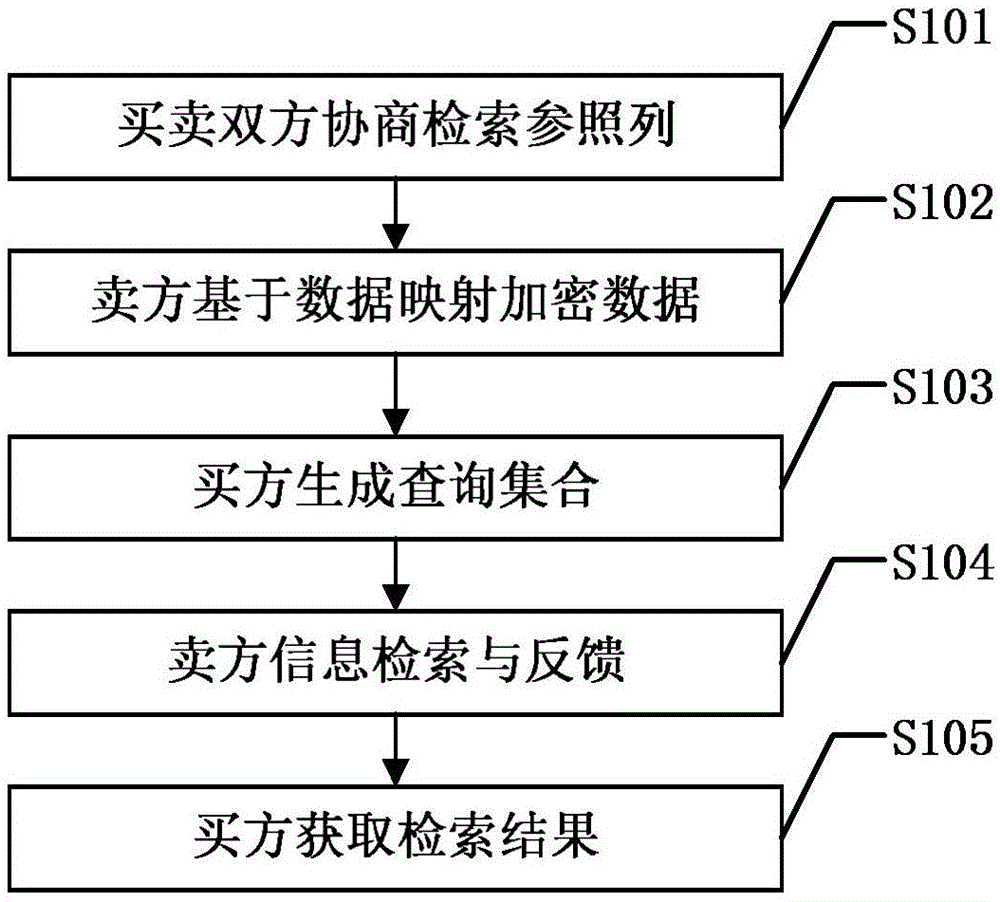
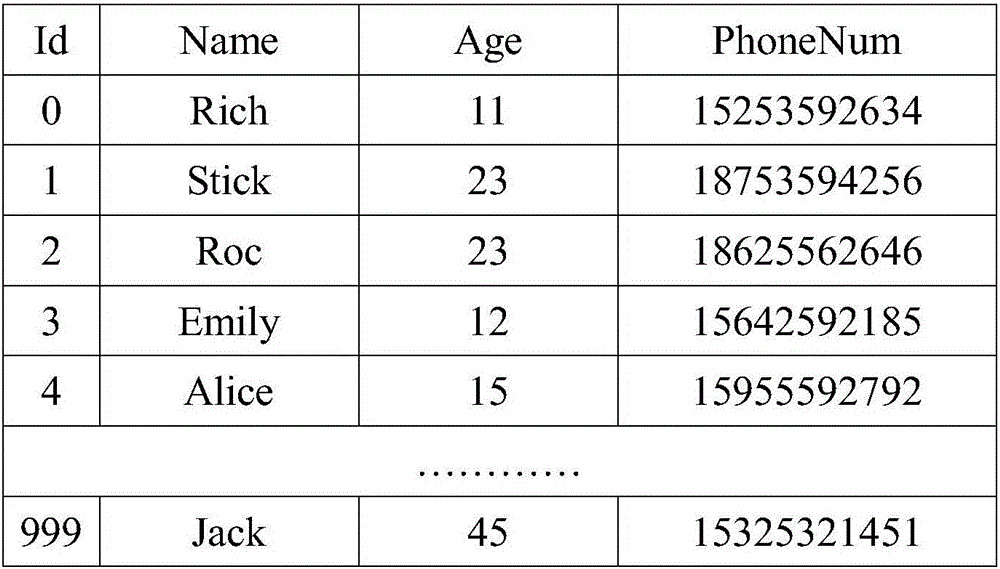
ActiveCN106844599AProtectDigital data protectionSpecial data processing applicationsPersonalizationK-anonymity
The invention discloses a method for retrieving personalized privacy information on the basis of data mapping. The method includes acquiring retrieval reference columns by means of negotiation between buyers and sellers of data exchange platforms; carrying out pseudo-ID (identification) numbering on data records by the aid of the sellers and mapping data; carrying out encryption by the aid of irreversible encryption algorithms to obtain cipher texts of data of the reference columns; transmitting the cipher texts to the buyers; acquiring corresponding pseudo-ID by means of inquiry; generating (k-1)*M pieces of false pseudo-ID according to privacy requirement parameters; constructing k anonymity sets from the (k-1)*M pieces of false pseudo-ID and pseudo-ID corresponding to M required-to-be-retrieved data and transmitting the k anonymity sets to the sellers; transmitting data record sets to the buyers by the aid of the sellers; screening required-to-be-retrieved records from retrieval record sets according to pseudo-ID corresponding to data of real retrieval reference columns by the aid of the buyers so as to obtain retrieval results. The data record sets transmitted to the buyers are obtained by means of retrieval. The method has the advantage that retrieval contents and intention privacy of the buyers can be effectively protected by the aid of the method.
Owner:EAST CHINA NORMAL UNIV
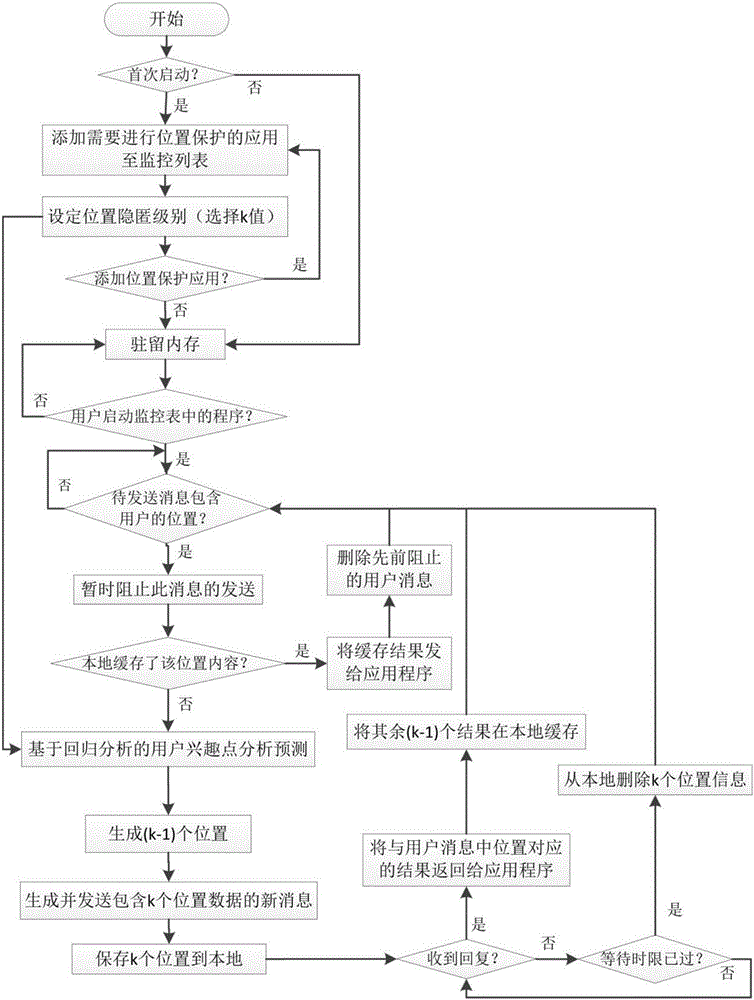
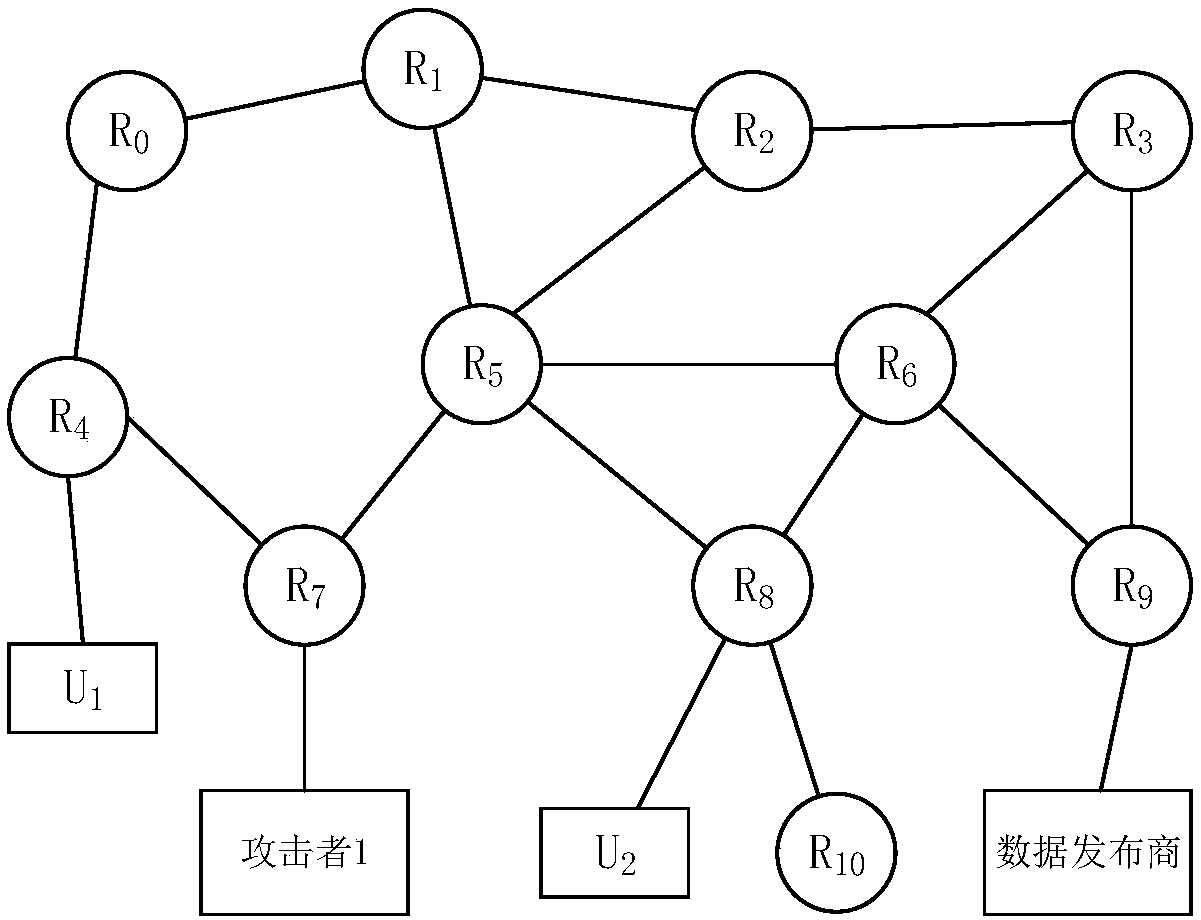
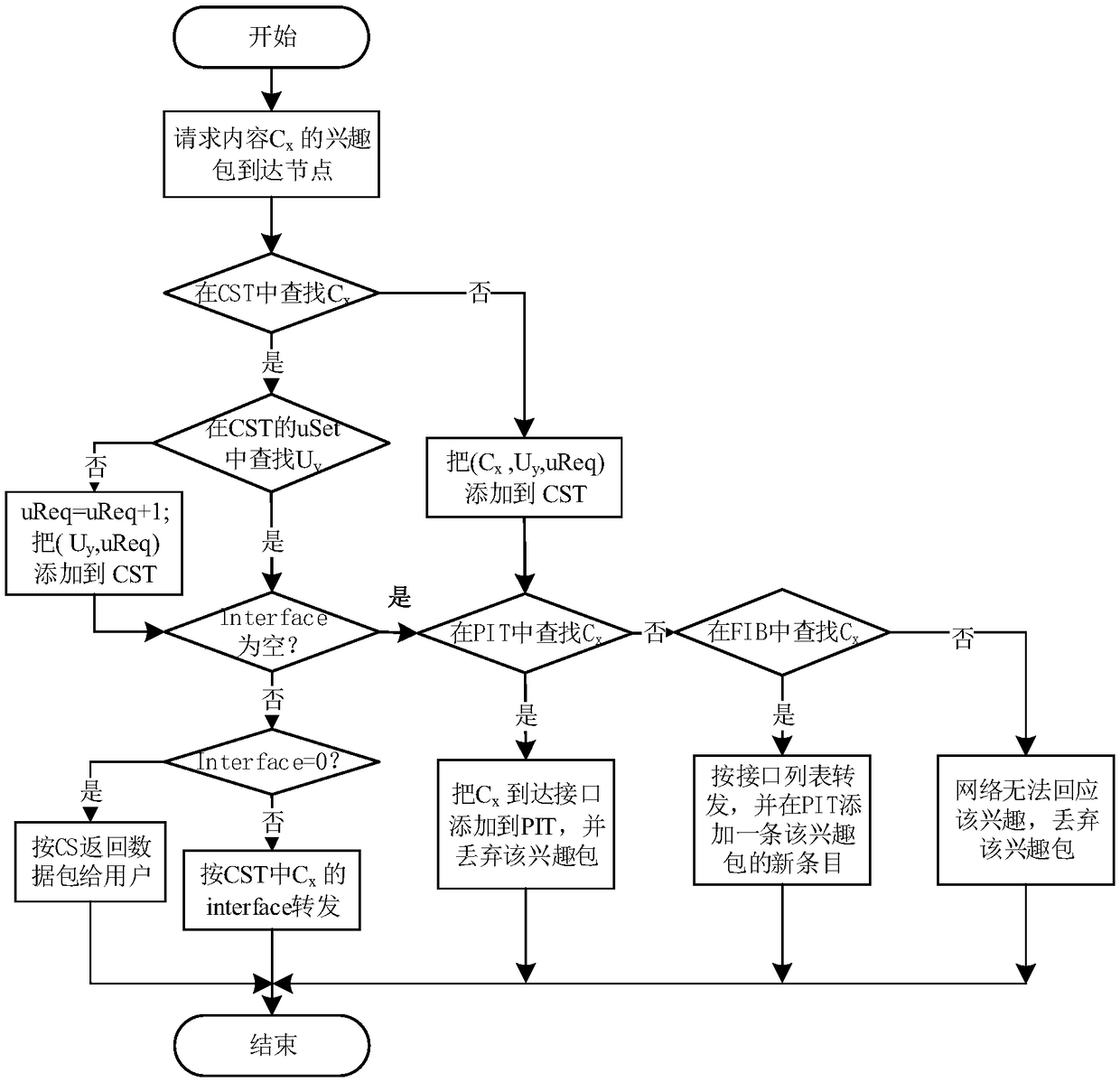
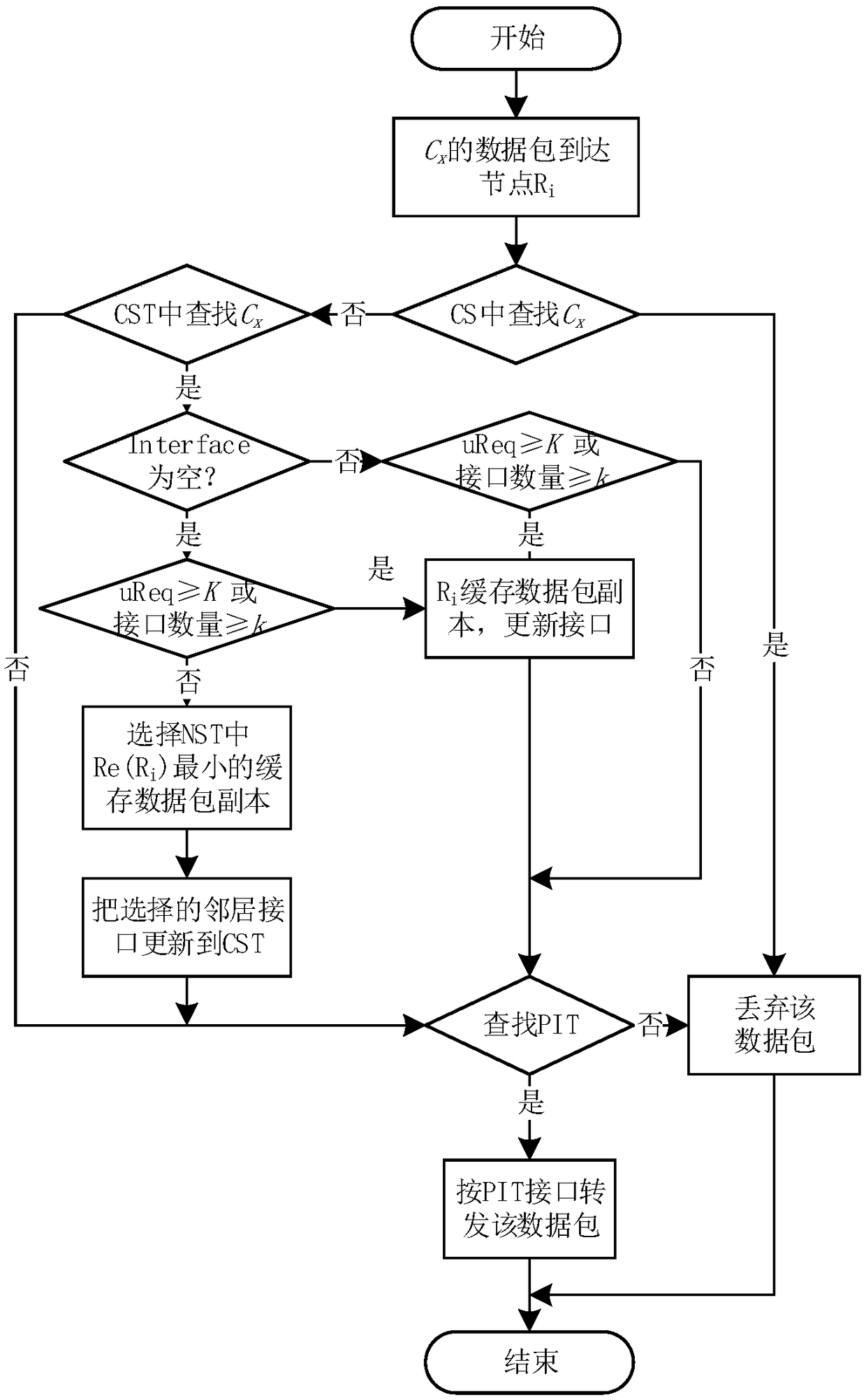
Cache decision method for privacy protection of named data network based on k-anonymity
The invention relates to a cache decision method for privacy protection of named data network based on k-anonymity. The cache decision is only made at a node where a user sends a request, and a neighboring node to which the cache is to be cached is determined by the cache replacement rate of the node. Even if an attacker can know that someone has accessed the content recently, the attacker can notinfer which user accessed the content recently through which router because of the caching cooperation in the area, so the attacker can avoid detecting the privacy information of the requester, and the privacy of the requester can be effectively protected. Furthermore, the cache privacy is protected by extending the user anonymous area through neighbor cooperative caching. The router does not need to construct the anonymous area, and does not need to search the data in the anonymous area, which reduces the implementation difficulty of the anonymous area and the time delay for local users to obtain the data.
Owner:GUANGDONG UNIV OF TECH
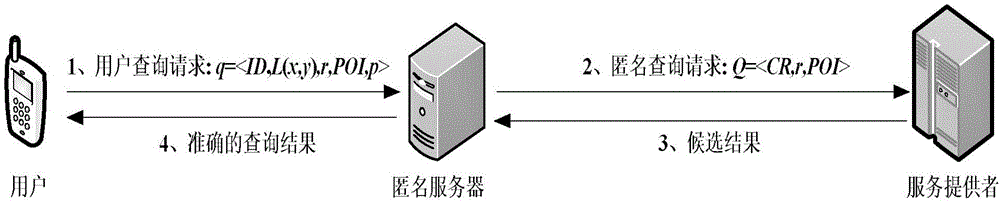
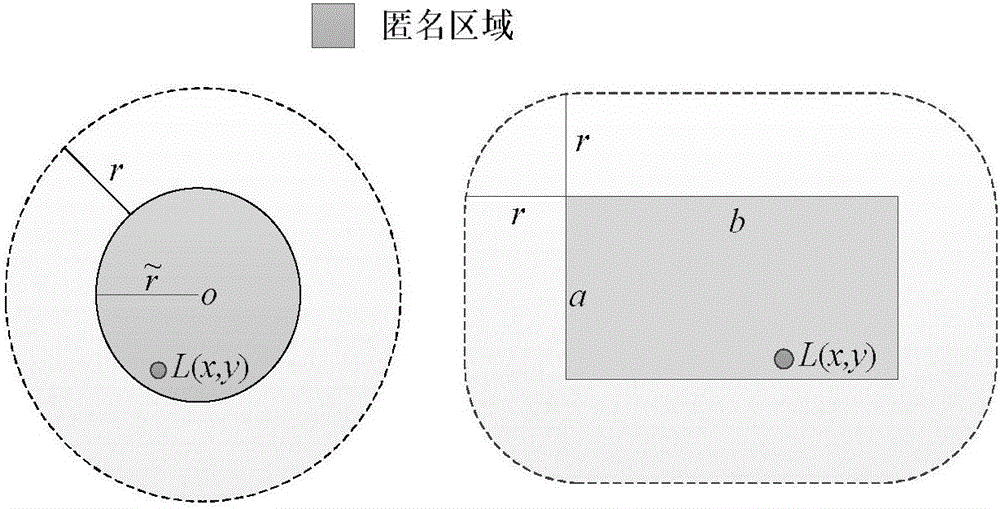
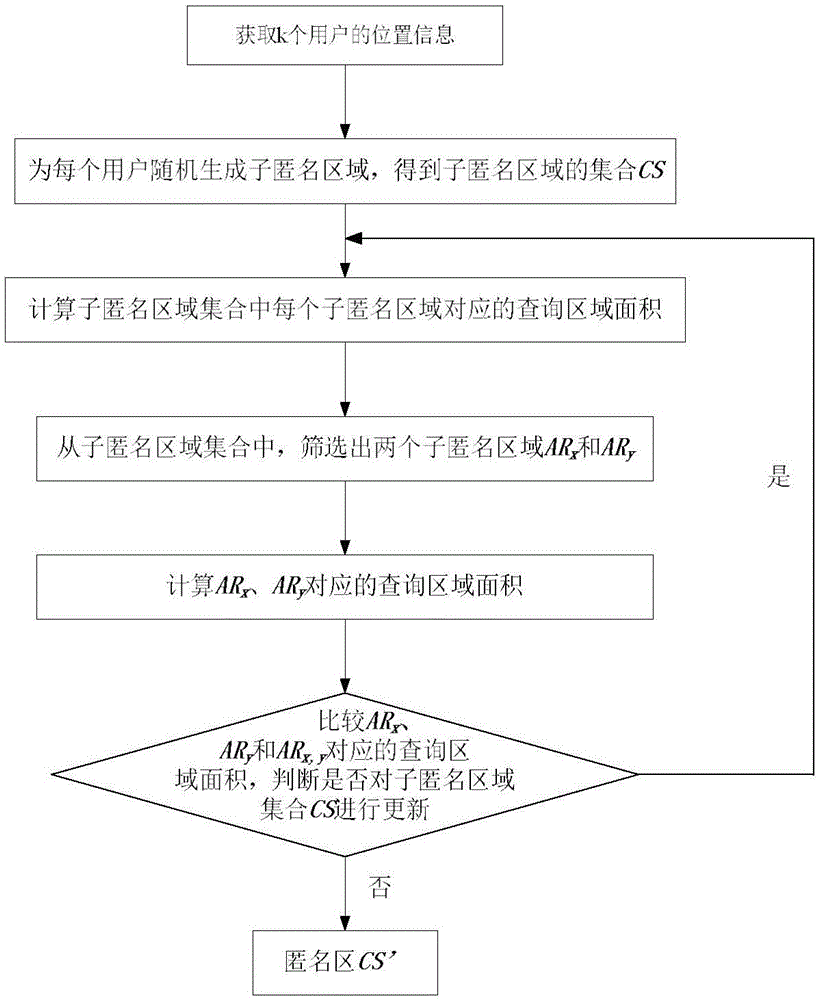
Anonymous region construction method based on query range
ActiveCN106803825ASolve the problem of location privacy securityReduce areaTransmissionLocation information based serviceQuality of serviceK-anonymity
The invention discloses an anonymous region construction method based on a query range, which mainly solves a problem that a conventional K-anonymity technique is large in anonymous region and causes degradation of the service quality in location-based service. The method comprises 1) an anonymous server generates a sub-anonymous region set CS that satisfies a user privacy protection requirement; 2) updating the sub-anonymous region set CS by using the query region area of a service provider as a criterion; 3) repeating the step 2) until the update condition of the sub-anonymous region set CS is not satisfied, and ultimately constructing an anonymous region CS'. The anonymous region construction method can meet the privacy requirement of the user, and an experiment shows that the query region area of the service provider is reduced, the delay for the user to obtain service is reduced, the service quality is improved, and the method can be used for the protection for user location privacy based on the location-based service.
Owner:XIDIAN UNIV
Track privacy protection method based on position service
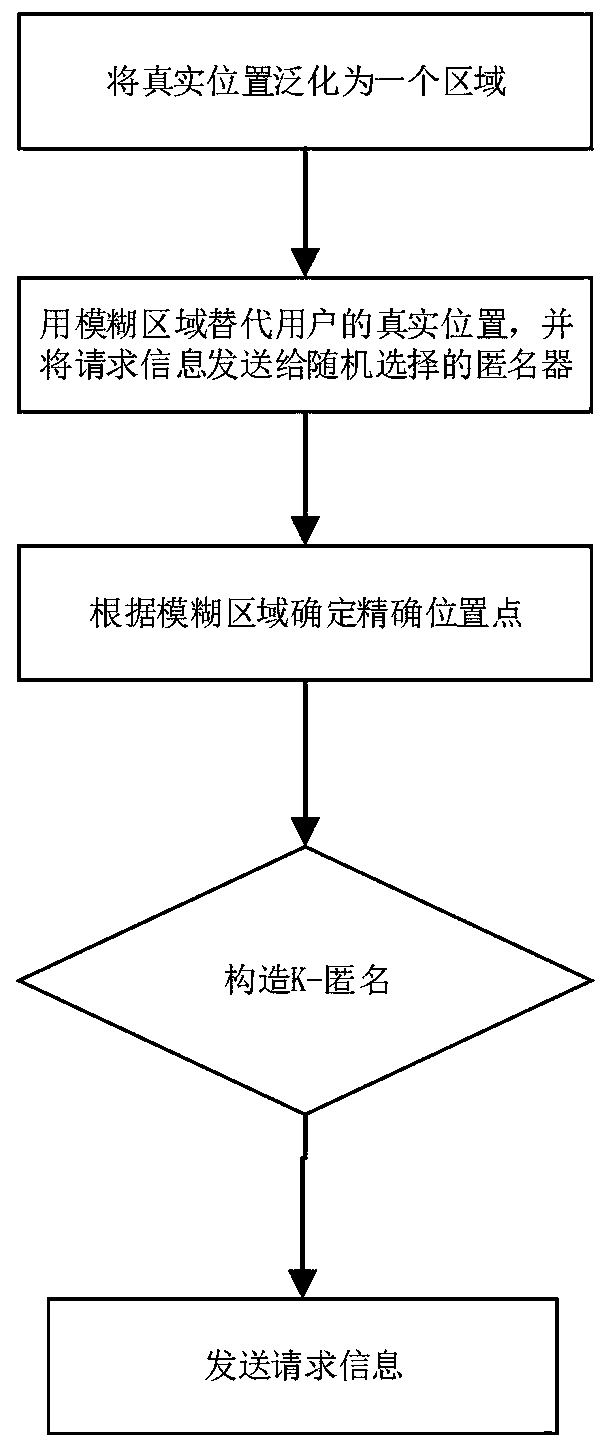
ActiveCN110602145AAvoid gettingReduce the risk of privacy breachesTransmissionK-anonymityRoad networks
The invention discloses a track privacy protection method based on position service. The method comprises the following steps: step 1, generating a fuzzy region BA according to a real position location of a user; 2, replacing the real position location of the user with a fuzzy region BA, randomly selecting an anonymous server from a plurality of anonymizers, and sending a query request (id, BA, t,query, k) to the anonymous server; 3, after the anonymous server receives the request information sent in the step 2, a selecting position point Li in a fuzzy area BA according to a road network; 4,enabling the anonymous server to generate an anonymous query request according to the Li generated in the step 3; and step 5, sending an anonymous query request to the location service provider. The real-time trajectory privacy protection method is researched on the basis of a multi-anonymizer system structure privacy protection model, and a method of combining location ambiguity and K-anonymity is provided, so that the purposes of enhancing trajectory privacy protection and ensuring data availability are achieved.
Owner:HARBIN ENG UNIV
K-anonymity-based personalized position privacy protection method
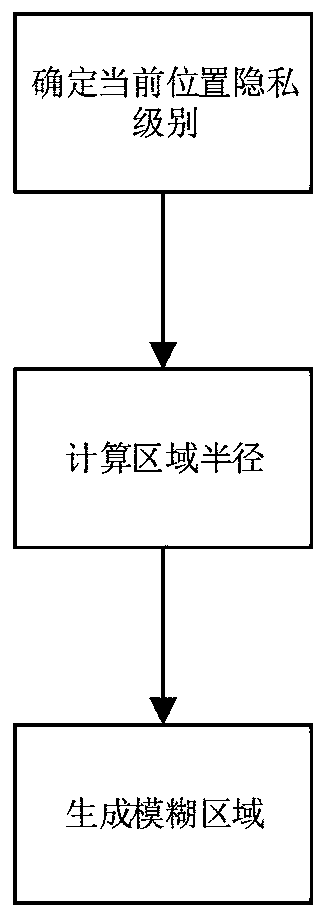
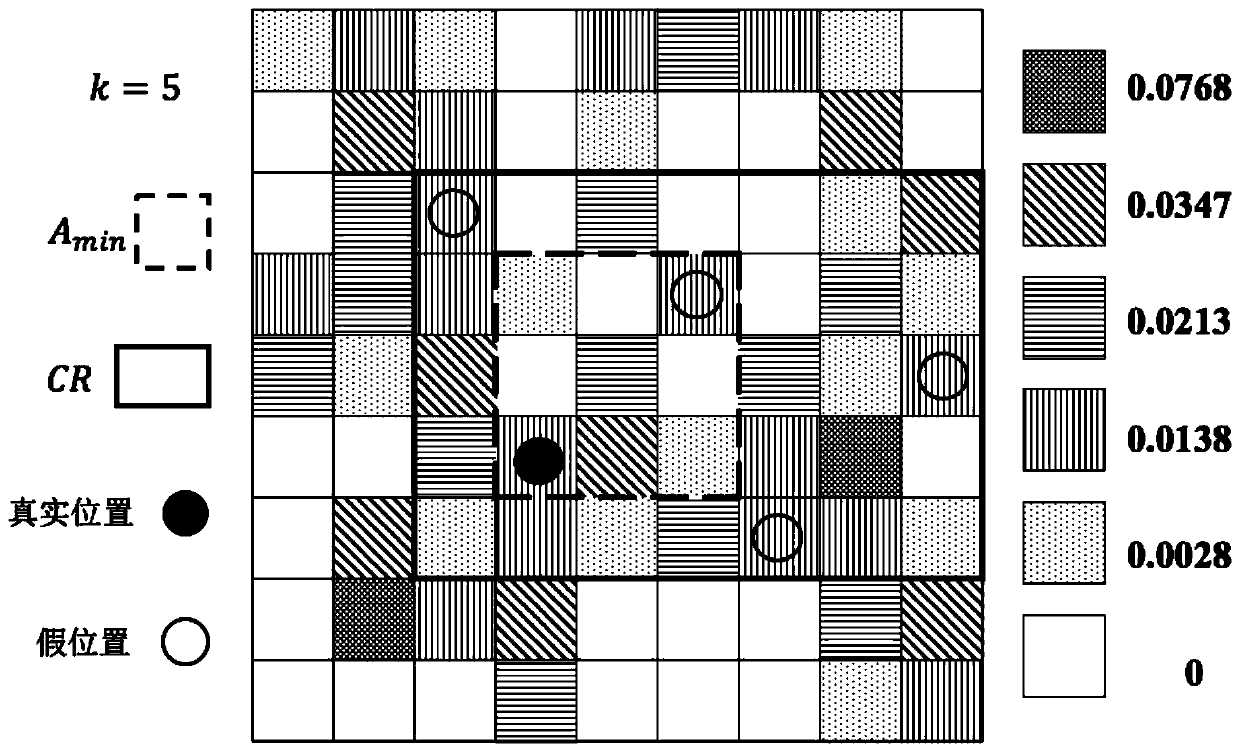
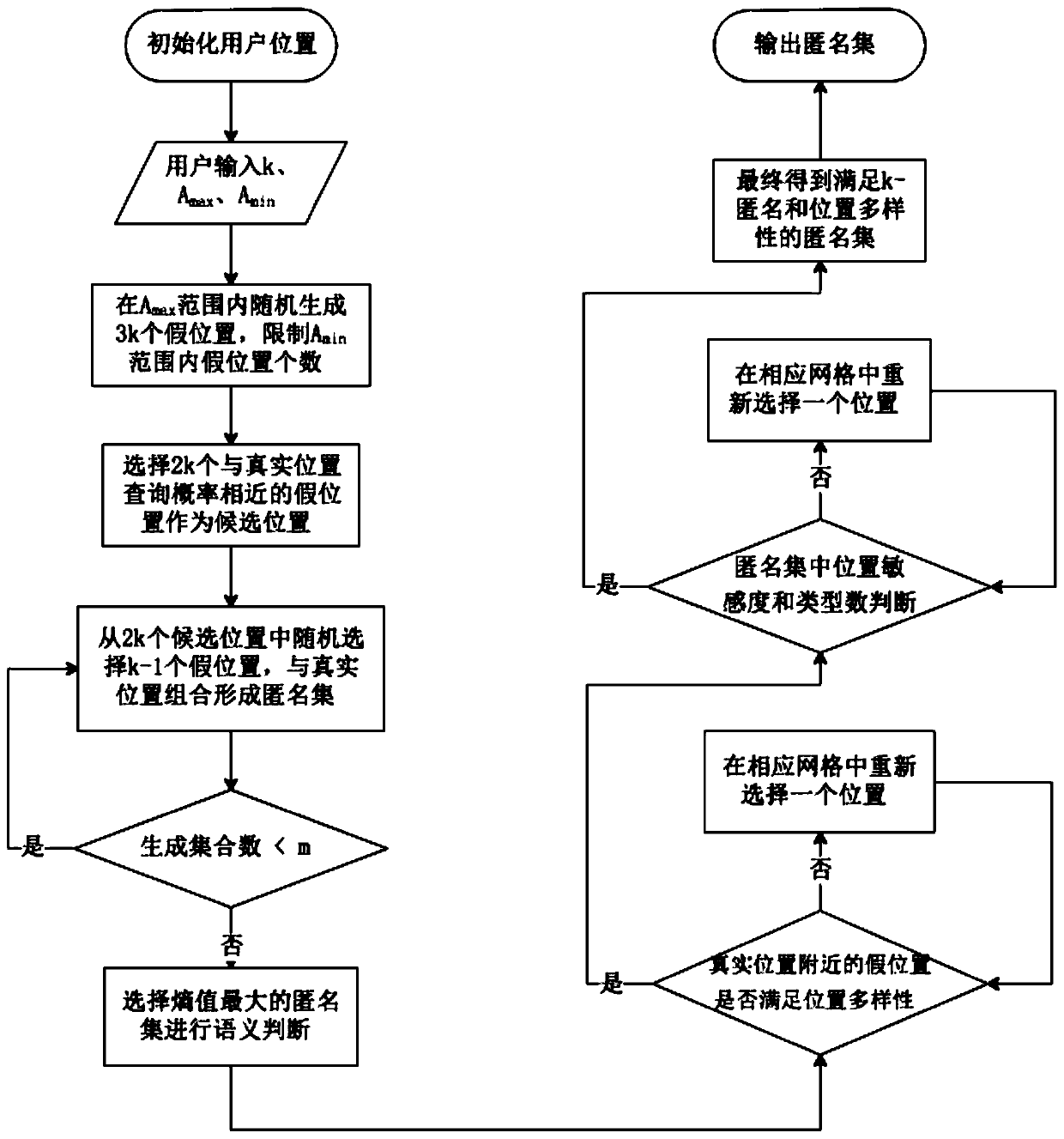
ActiveCN110062324ARealize individual needsIncrease diversityLocation information based serviceSecurity arrangementPersonalizationK-anonymity
The invention discloses a K-anonymity-based personalized position privacy protection method, and belongs to the field of information security. The method includes: generating an efficient k- anonymousset by a personalized false position generation algorithm; using the anonymous set to replace a real position and sending the anonymous set to a service provider, so that the position privacy of theuser is protected when the user sends a request based on the position service (LBS), and the user can define the anonymous degree and the service demand according to the actual condition to obtain a query result meeting the privacy protection demand. The method is suitable for services of a single discrete request, such as interest point retrieval.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com