Anonymous region construction method based on query range
A construction method and a technology of query scope, applied in the field of information security, can solve the problems of too large anonymity area and reduced service quality, achieve the effect of small query area, improve service quality, and solve the problem of location privacy security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] In order to make the purpose, technical method and advantages of the present invention clearer, the present invention will be further described in detail below.
[0029] The application principle of the present invention will be described in detail below in conjunction with the accompanying drawings.
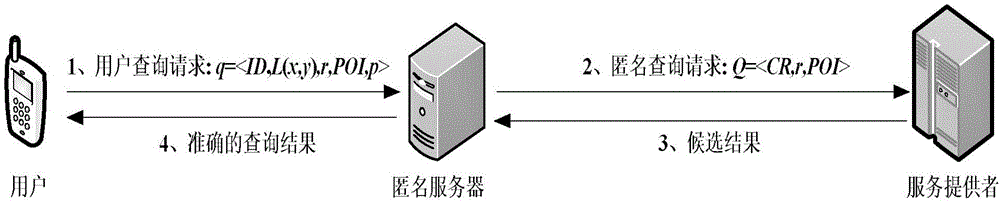
[0030] refer to figure 1 , the use scenario of the present invention is a K-anonymous centralized system, including three parts of user, anonymous server and service provider LSP, which is mainly used for location-based service LBS, and the working principle of the system is as follows:
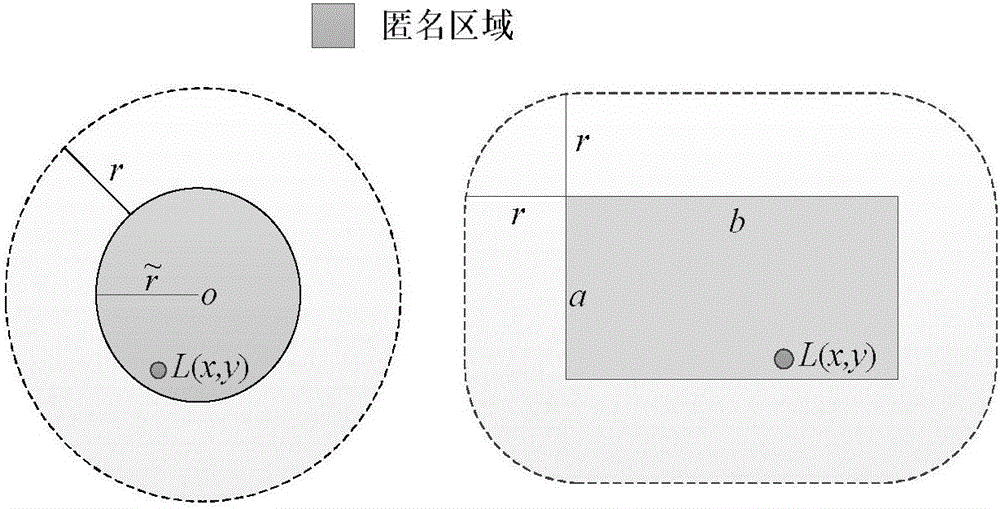
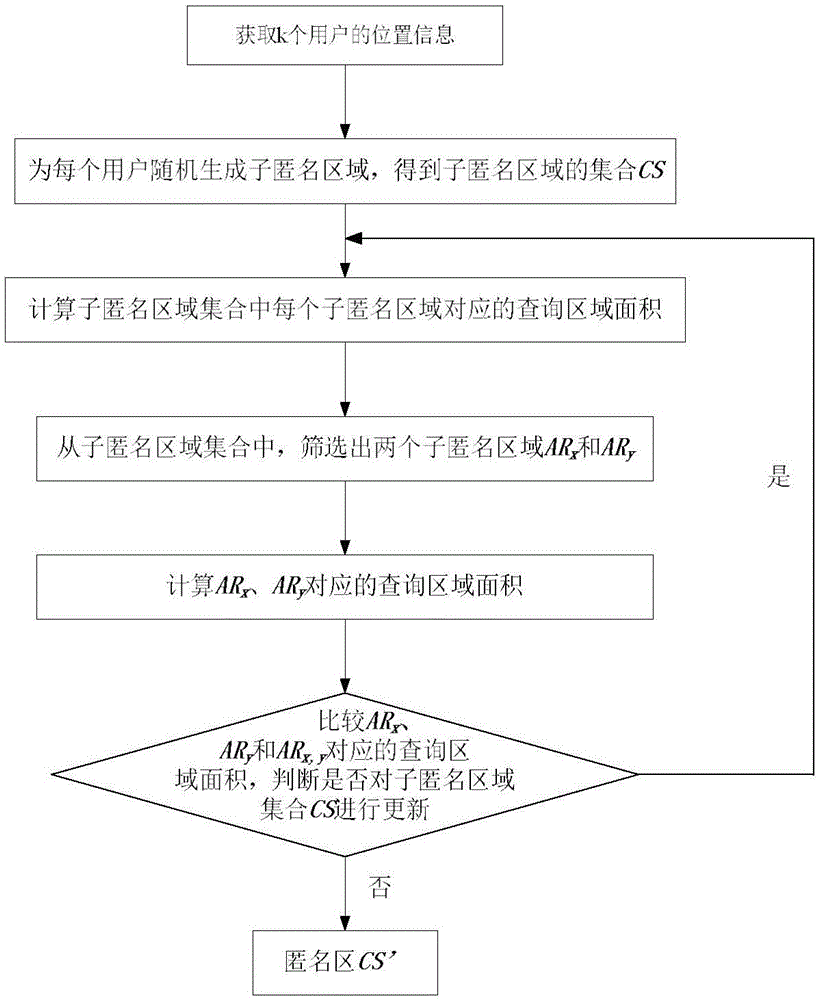
[0031] Assuming that there is a secure communication channel between the user and the anonymous server, when the user queries nearby POIs, the query request q= will be passed through the secure channel first. Channels are sent to trusted anonymous servers. Among them, ID represents the identity of the user; L (x, y) represents the position coordinates of the user; r represents the quer...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com