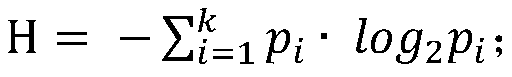K-anonymity-based personalized position privacy protection method
A privacy protection, fake location technology, applied in the field of information security, can solve the problems of small indistinguishability of k locations, not considering the actual needs of users, affecting the quality of query request service, etc., to achieve abbreviated location diversity and resist location distribution attacks. and background information attack, to achieve the effect of diversity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and specific embodiments. It should be understood that these examples are used to illustrate the present invention and not to limit the scope of the present invention. The implementation conditions used in the examples can be further adjusted according to the conditions of specific manufacturers, and the implementation conditions not indicated are usually the conditions in routine experiments.
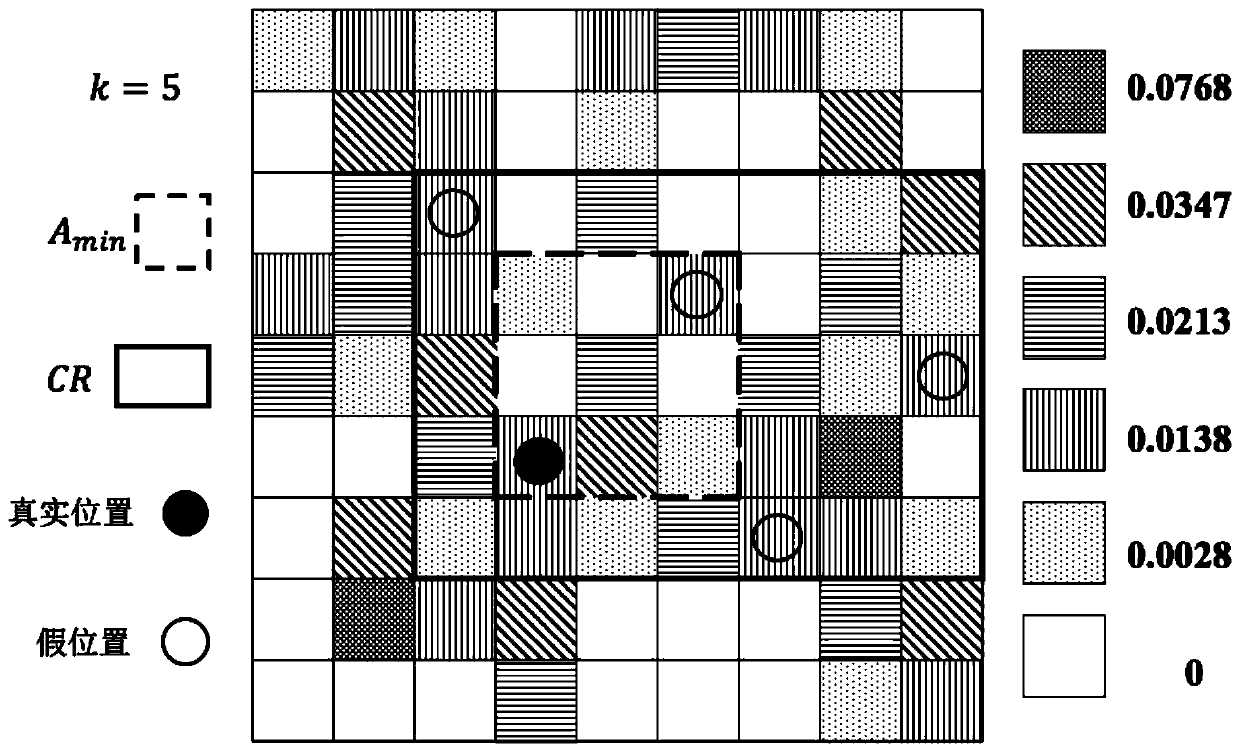
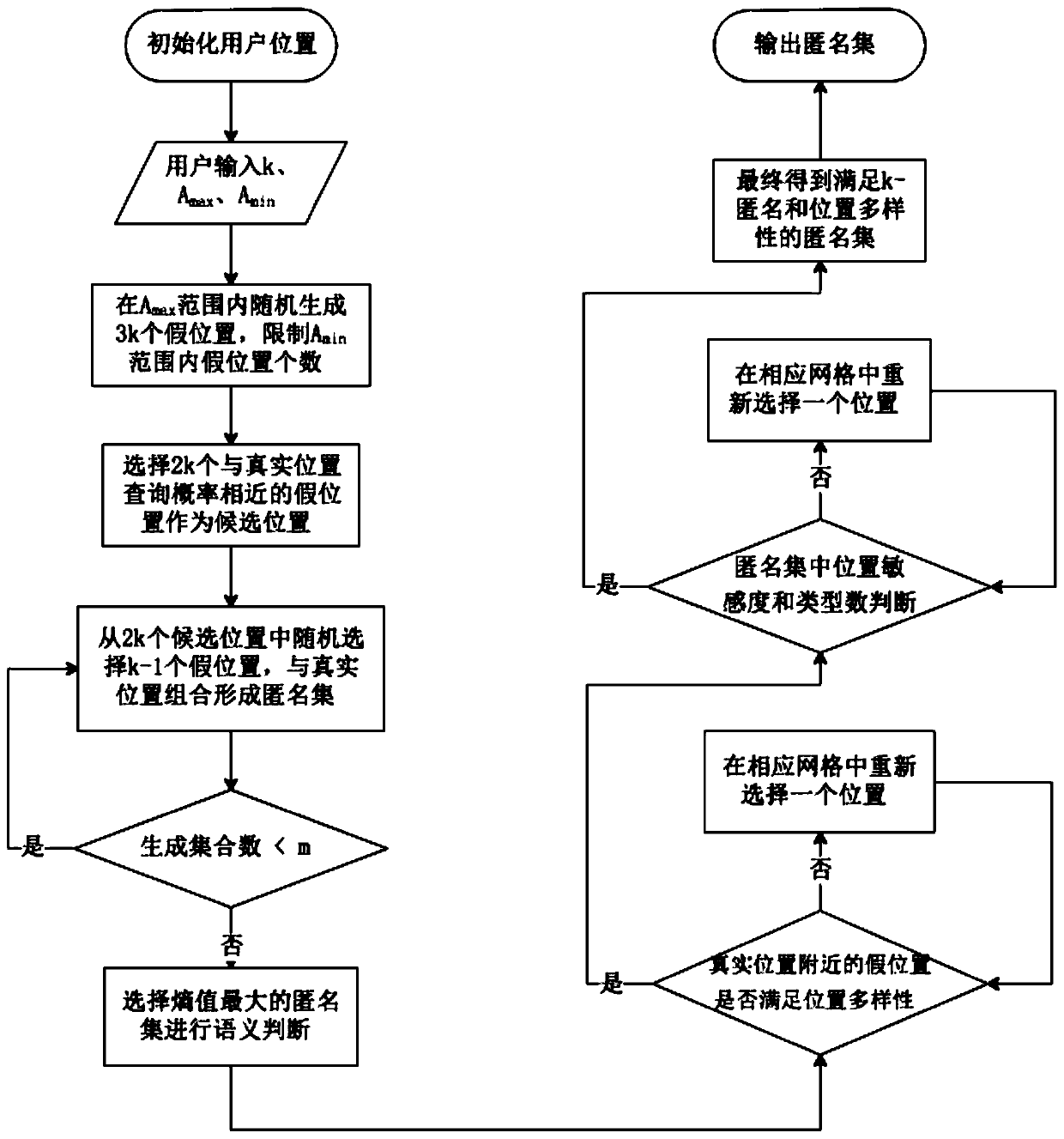
[0030] In the location privacy protection process of LBS, users need to obtain their current location through the positioning system first, and then generate k-1 effective fake locations through a personalized fake location generation algorithm, and construct an anonymous area CR in combination with the user's real location. Such as figure 1 As shown in , the shades of different cells in the rightmost column represent different query probabilities; this...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com