Privacy protection method for mobile terminal during running position-based service
A technology for operating location and privacy protection, applied in the field of privacy protection, can solve problems such as the difficulty of technology and solutions to meet user requirements, and achieve the effect of shortening time, reducing burden, and improving service accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] The present invention will be further described below in conjunction with the accompanying drawings and embodiments.
[0018] The privacy protection method of the mobile terminal when running the location service according to the present invention includes the following basic definitions:
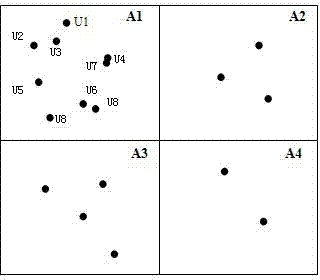
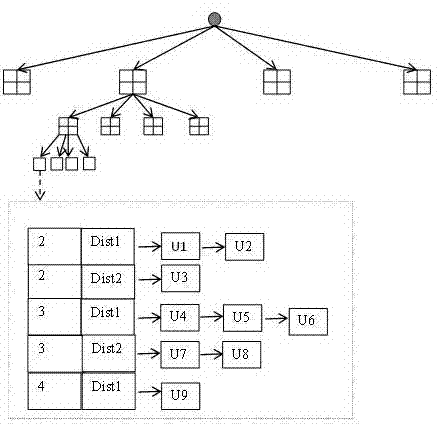
[0019] Privacy protection system structure: The central anonymous server structure is the most common system structure in the location privacy protection model, which is suitable for processing large quantities of service requests. The structure consists of 3 parts: user, location anonymity server and location server.
[0020] Location privacy requirement Q: The location privacy requirement Q is defined in the form of a triple {Pos(x,y),k,dist}, where Pos(x,y) is the user's location coordinates in the plane space; the degree of anonymity k represents The anonymous area contains the minimum number of users. If the user satisfies the anonymity principle of position k, the probability ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com