Patents
Literature
54results about How to "Maintaining anonymity" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Anonymous authenticated communications
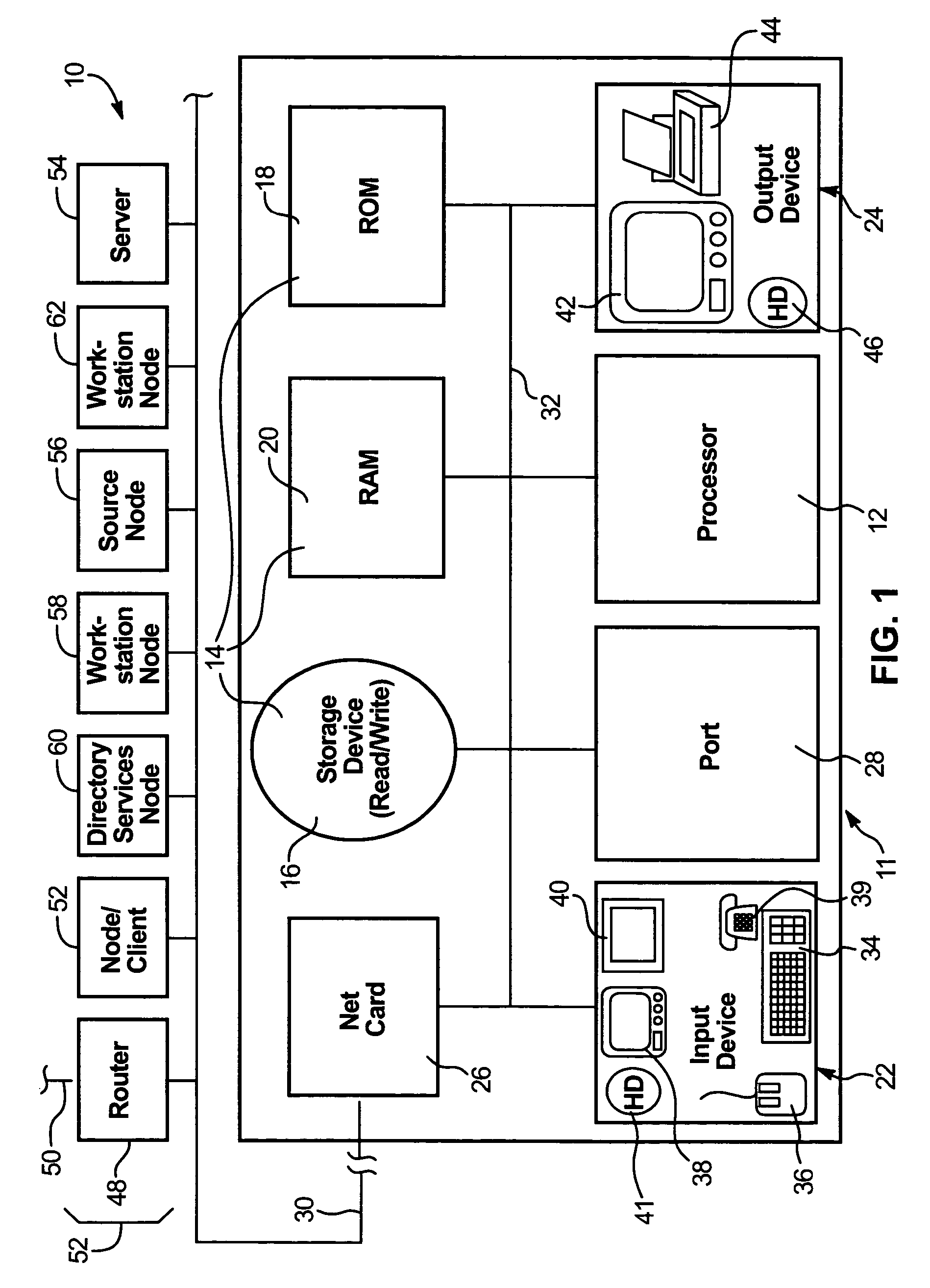
InactiveUS7234059B1Maintaining anonymityKey distribution for secure communicationPublic key for secure communicationComputer networkElectronic communication
Owner:SANDIA NAT LAB
Methods and apparatus for providing user anonymity in online transactions
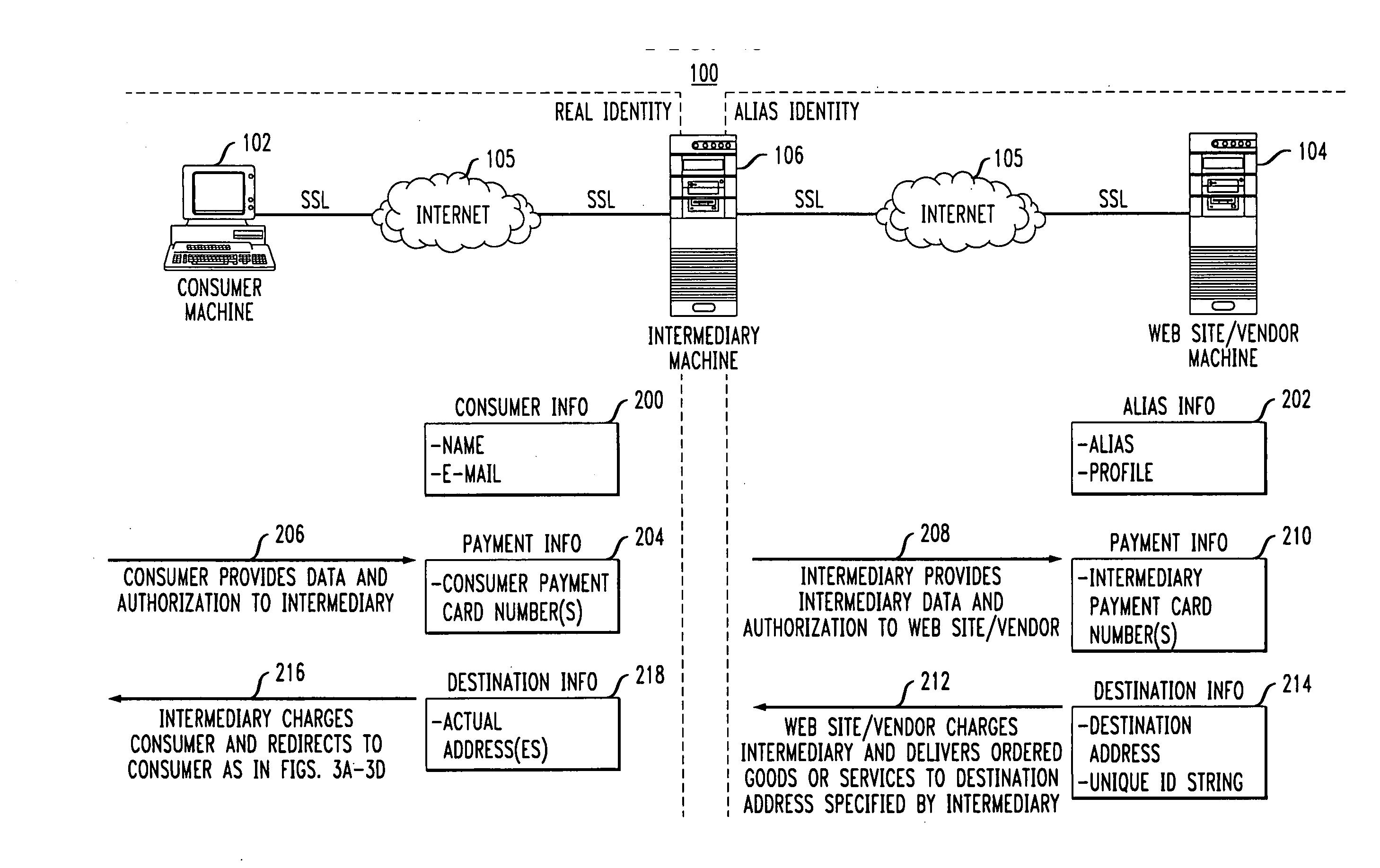
InactiveUS7203315B1Maintaining anonymityLimit fraud riskDigital data processing detailsMultiple digital computer combinationsWeb siteThird party
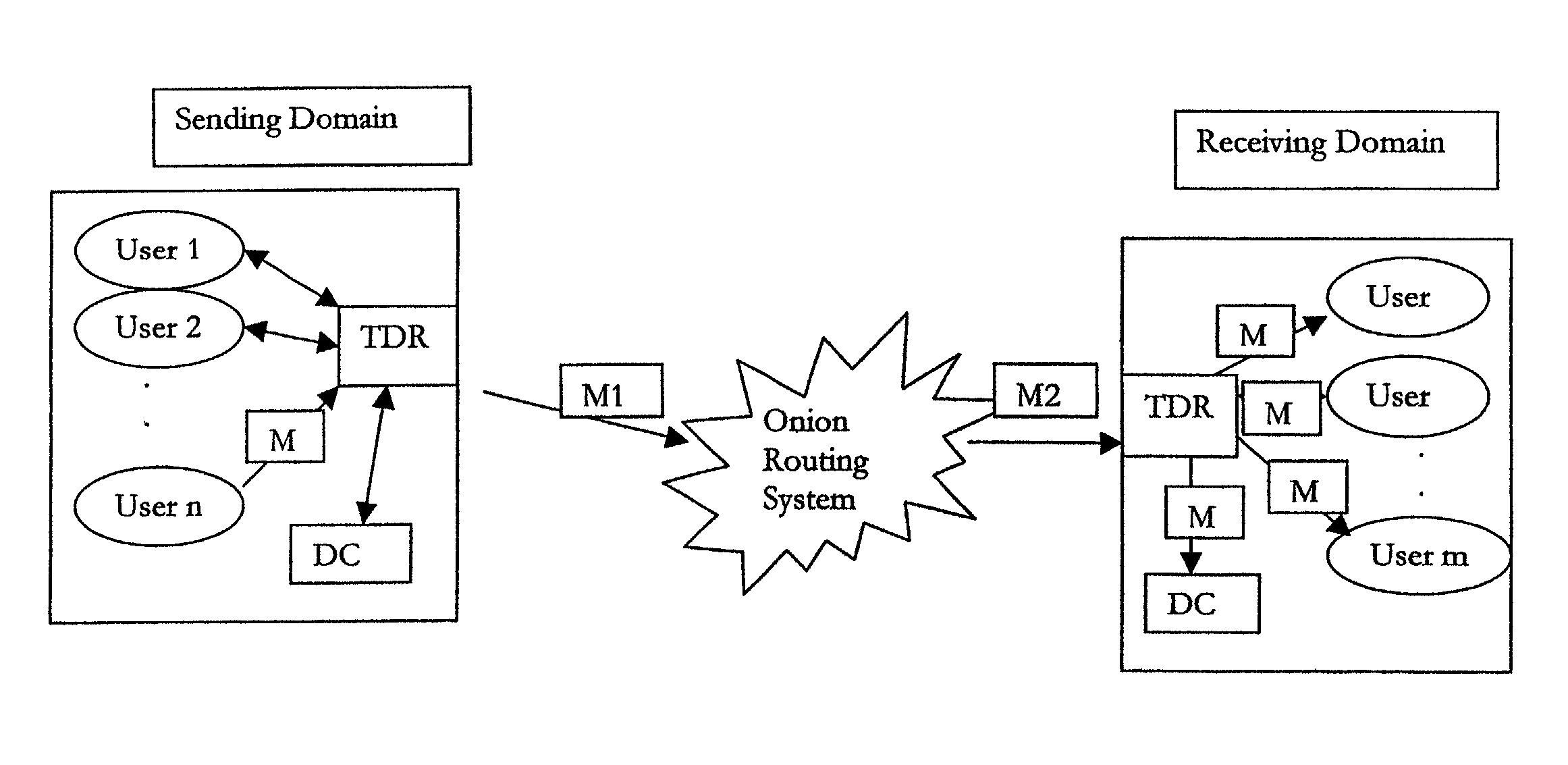
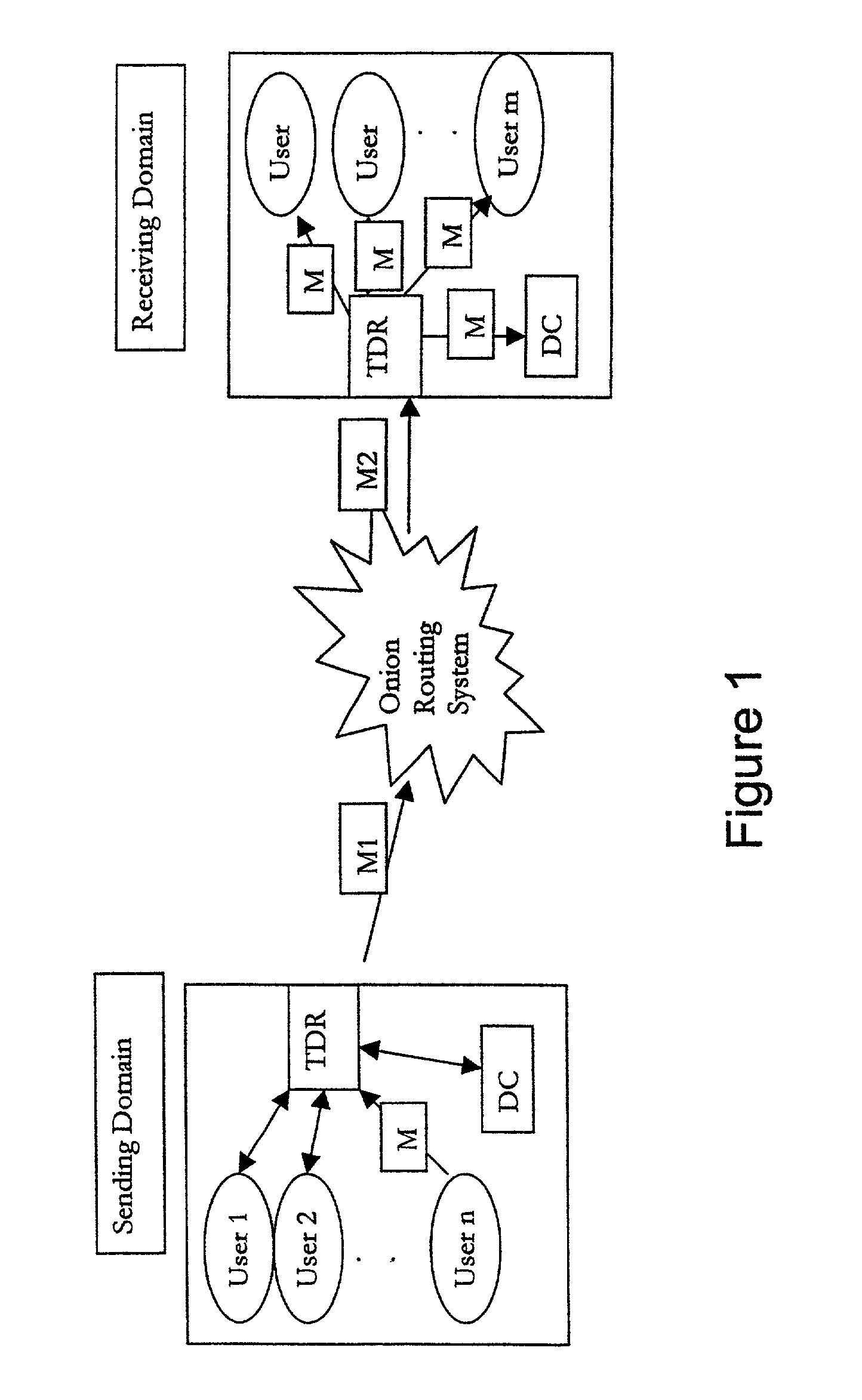
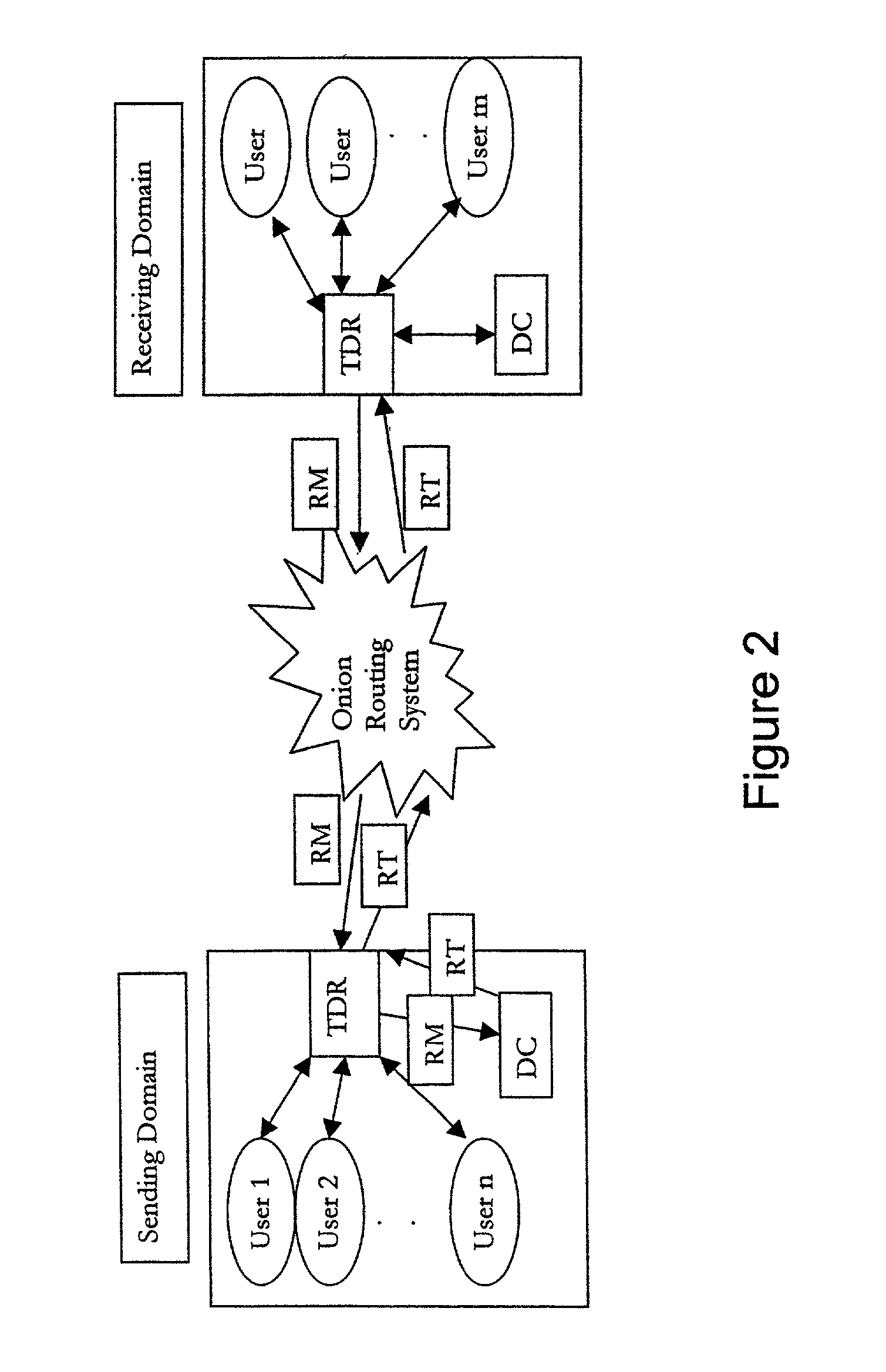
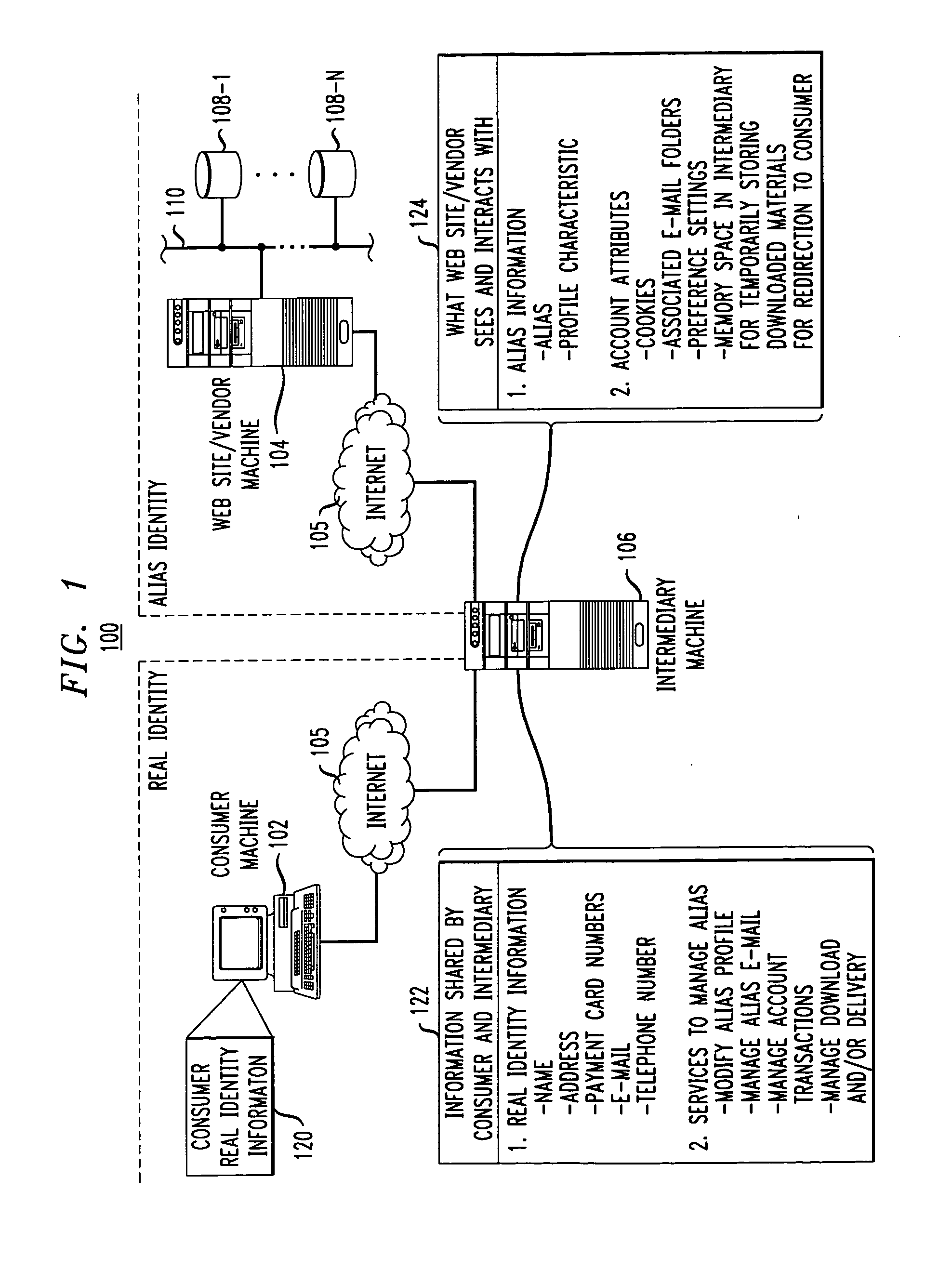
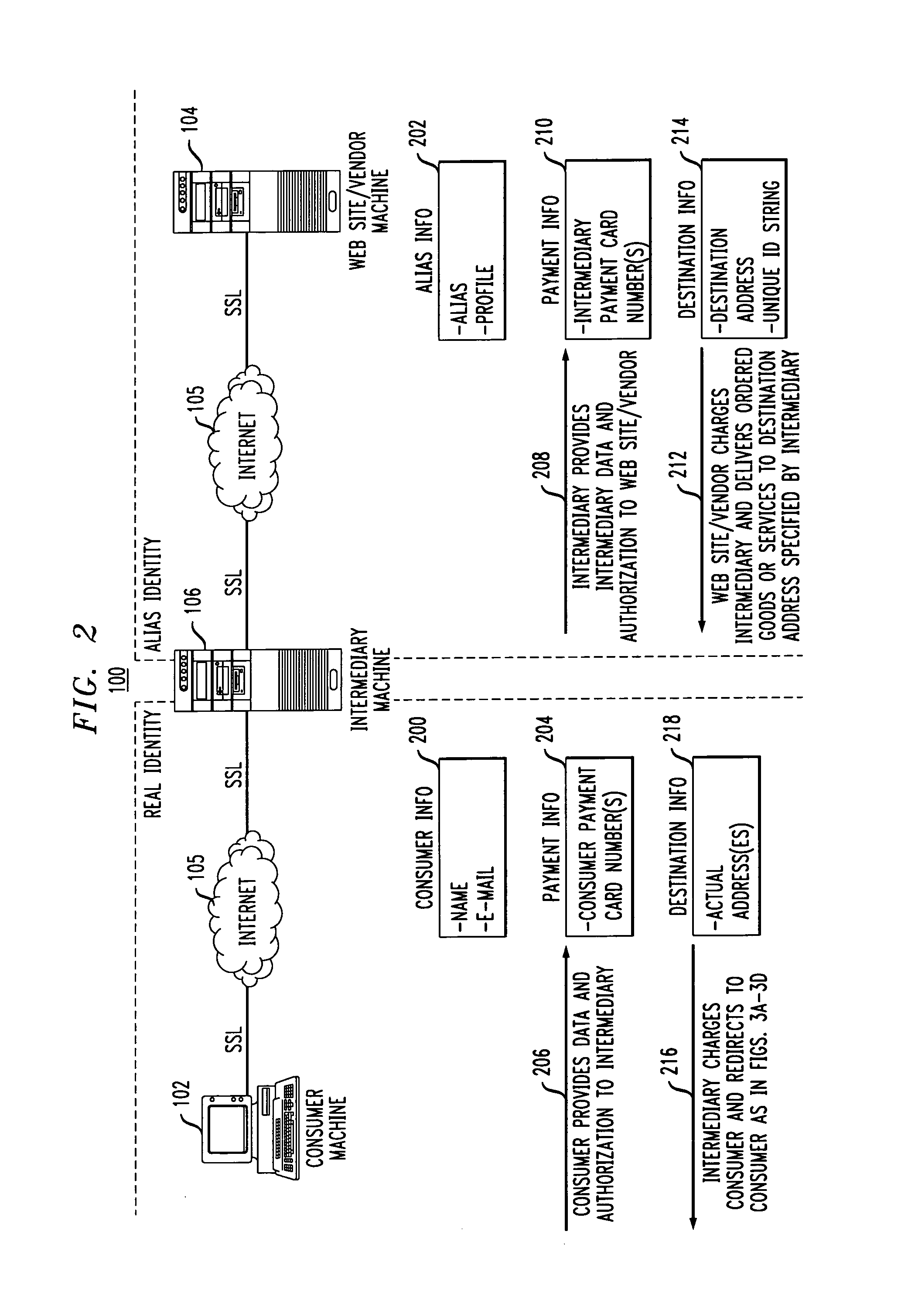
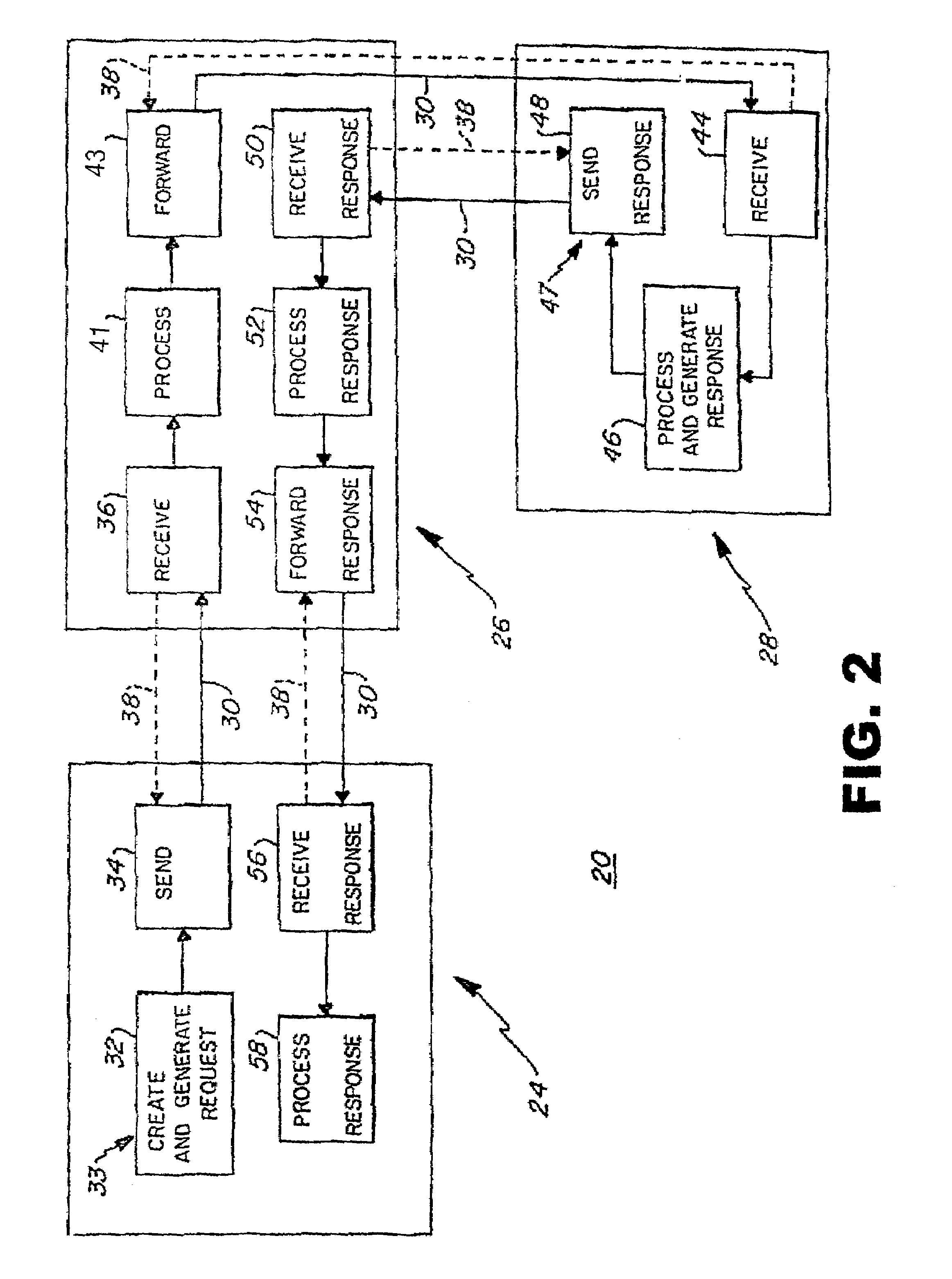
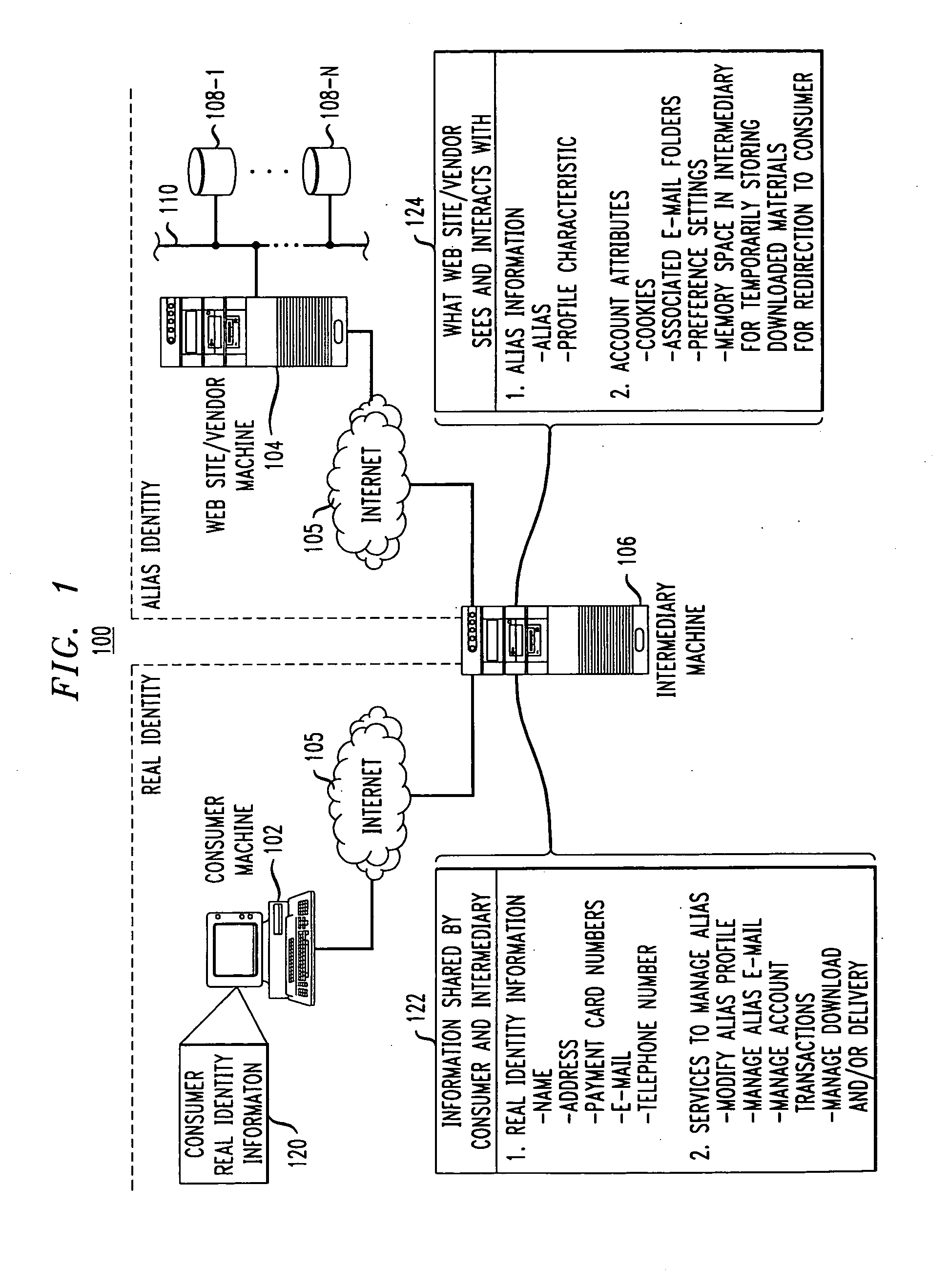
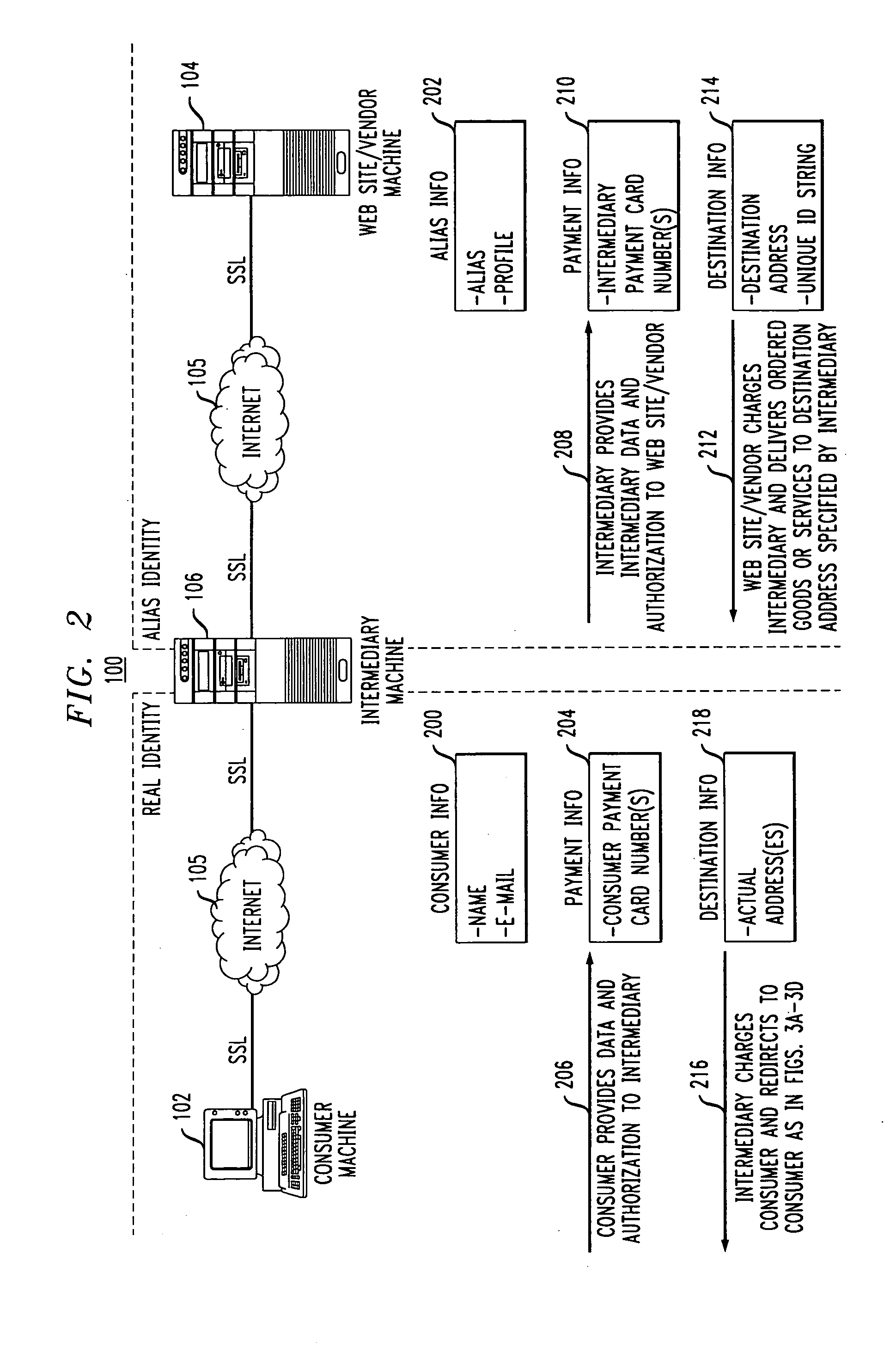
End-to-end user anonymity is provided in electronic commerce or other types of online transactions through the use of an intermediary. An intermediary machine, which may be implemented in the form of a set of servers or other type of computer system, receives communications from a consumer or other user, and generates and maintains an alias for that user. Connections between the user machine and any online vendor or other web site are implemented through the intermediary using the alias. When the user desires to make a purchase from a given online vendor, the intermediary may present the user with a number of options. For example, the user may be permitted to select a particular payment card number and real destination address as previously provided to the intermediary. The intermediary then communicates with the online vendor and supplies intermediary payment information, e.g., a payment card number associated with the intermediary rather than the user, along with appropriate authorizing information and an alias destination address, e.g., a third party physical shipping address for deliverable goods, an alias electronic address for downloadable material, etc. The online vendor charges the purchase to the intermediary, and redirects the delivery of the goods or services to the destination address provided by the intermediary. The intermediary charges the payment card number of the user, and arranges for the redirection of the delivery to the real user address. In this manner, the invention provides complete end-to-end anonymity for the user, even when the user desires to enter transactions involving purchase and receipt of deliverable goods and services.
Owner:PRIVACY LABS
Anonymous transaction authentication
InactiveUS7264152B2Easy to centralizeMaintaining anonymityNon-ionic surface-active compoundsCredit registering devices actuationCredit cardPersonal details
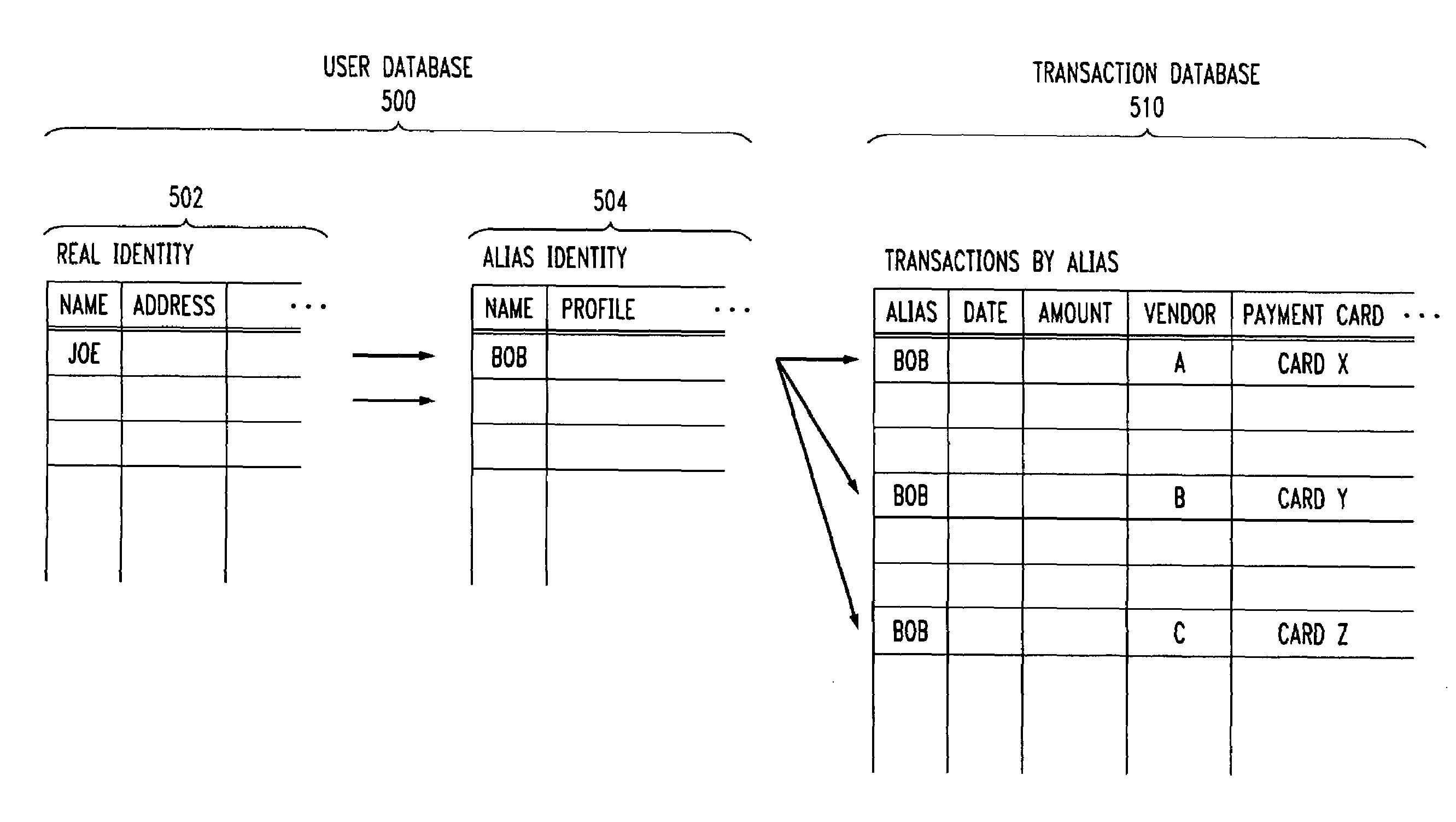
An automated system for the confirmed efficient authentication of an anonymous subscriber's profile data. The system is comprised of software / hardware interface to facilitate centralized access and exchange to easily and inexpensively allow the confirmed authentication of subscriber profiles of customers wishing to blind their transactions, while maintaining current services. In one aspect the system allows a subscriber to anonymously accomplish credit card transactions without associating any aspect of the transaction with any information associated with the true identity of the subscriber.
Owner:FIRST DATA
System and method for utilizing connected devices to enable secure and anonymous electronic interaction in a decentralized manner
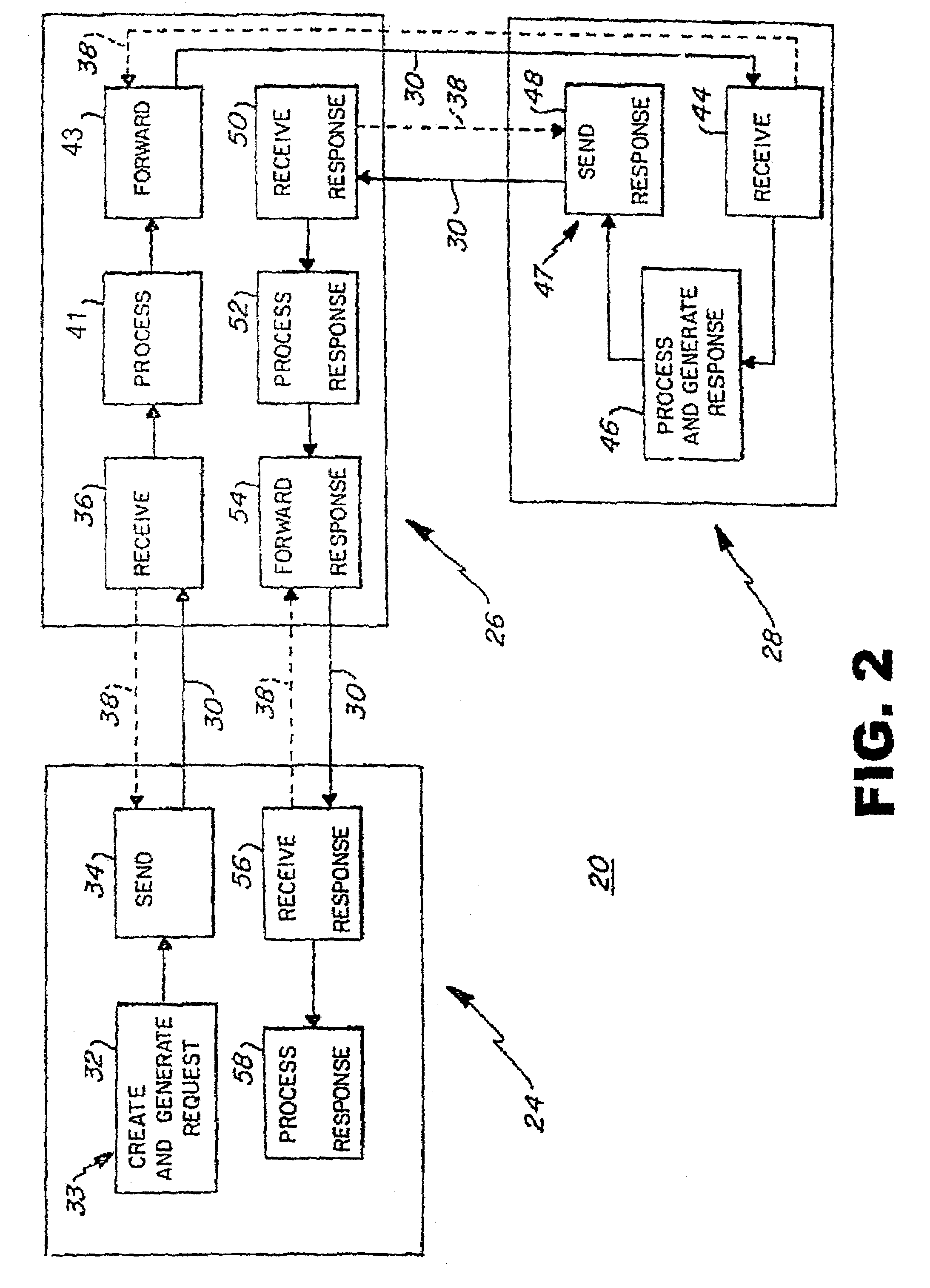
ActiveUS20180343126A1Maintaining anonymityPublic key for secure communicationUser identity/authority verificationPublic key infrastructureBlockchain
A system and method for utilizing connected devices to enable secure and anonymous electronic interaction in a decentralized manner without the need for usernames and passwords. The method comprises Blockchain, Merkle Trees and Public Key infrastructures and methods that utilize peer-to-peer network protocols. The methods include interactions of two self-sovereign identity groups; persons and devices, with each having their own authorization layer. The devices employ two domains of identity and authorization with each said device having its own self-assigned machine identity. There are three domains of Identity, Authentication and Authorization employed for persons. The final linking of the two groups requires access to be granted by the device in a distributed autonomous manner.
Owner:NXM TECH INC
Credit management for electronic brokerage system
InactiveUS6985883B1Maintaining anonymitySpecial service provision for substationFinanceConfidentialityData mining
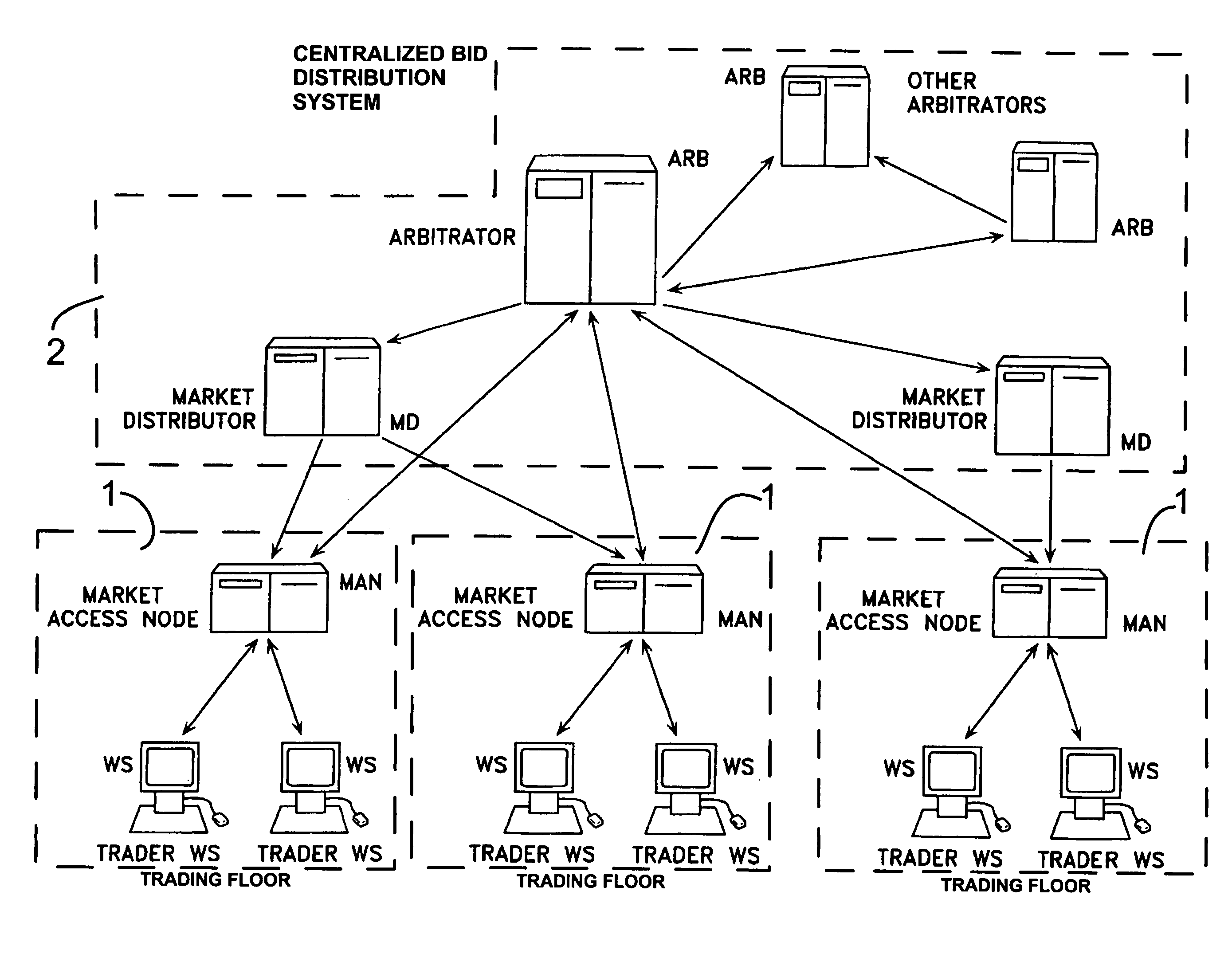
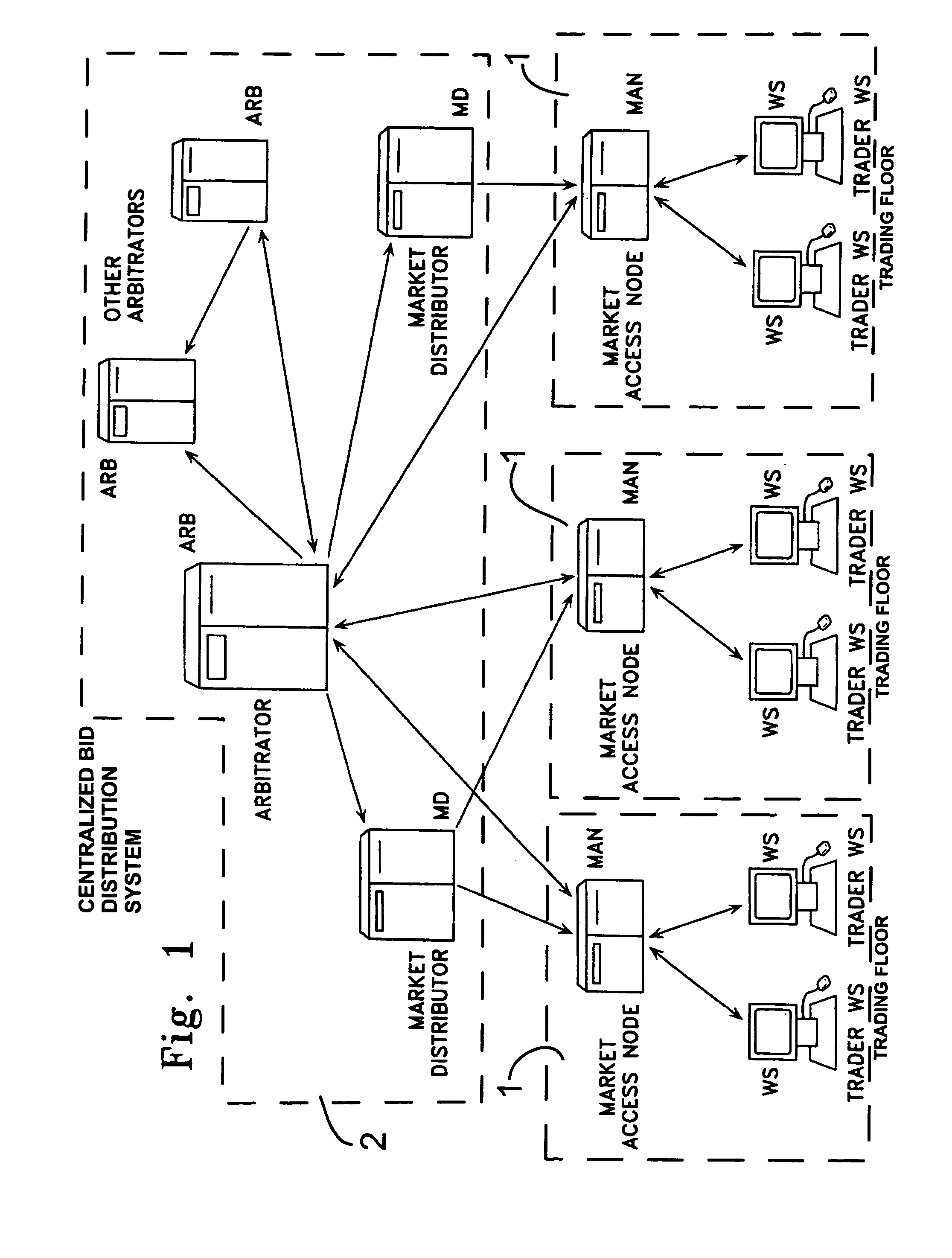
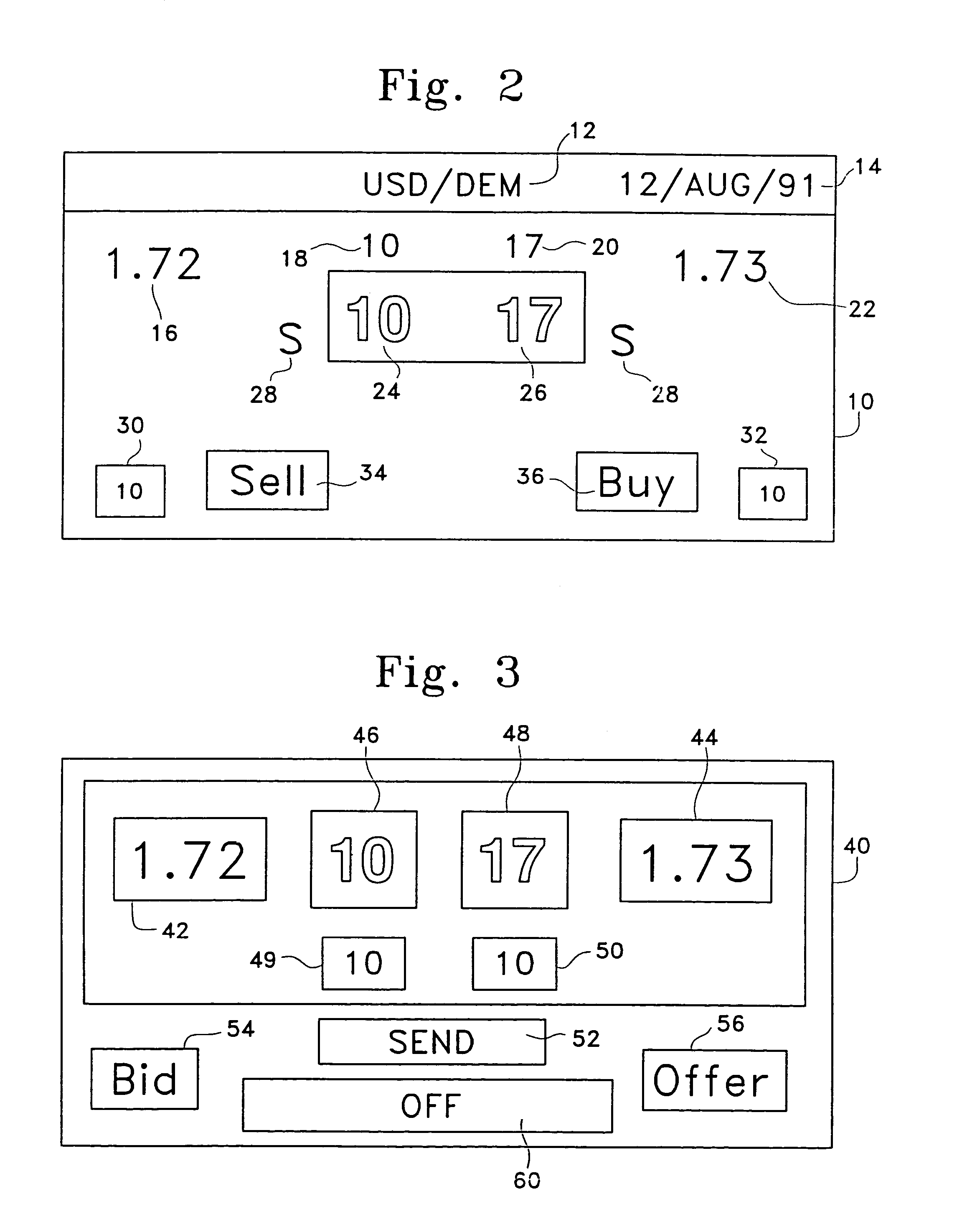
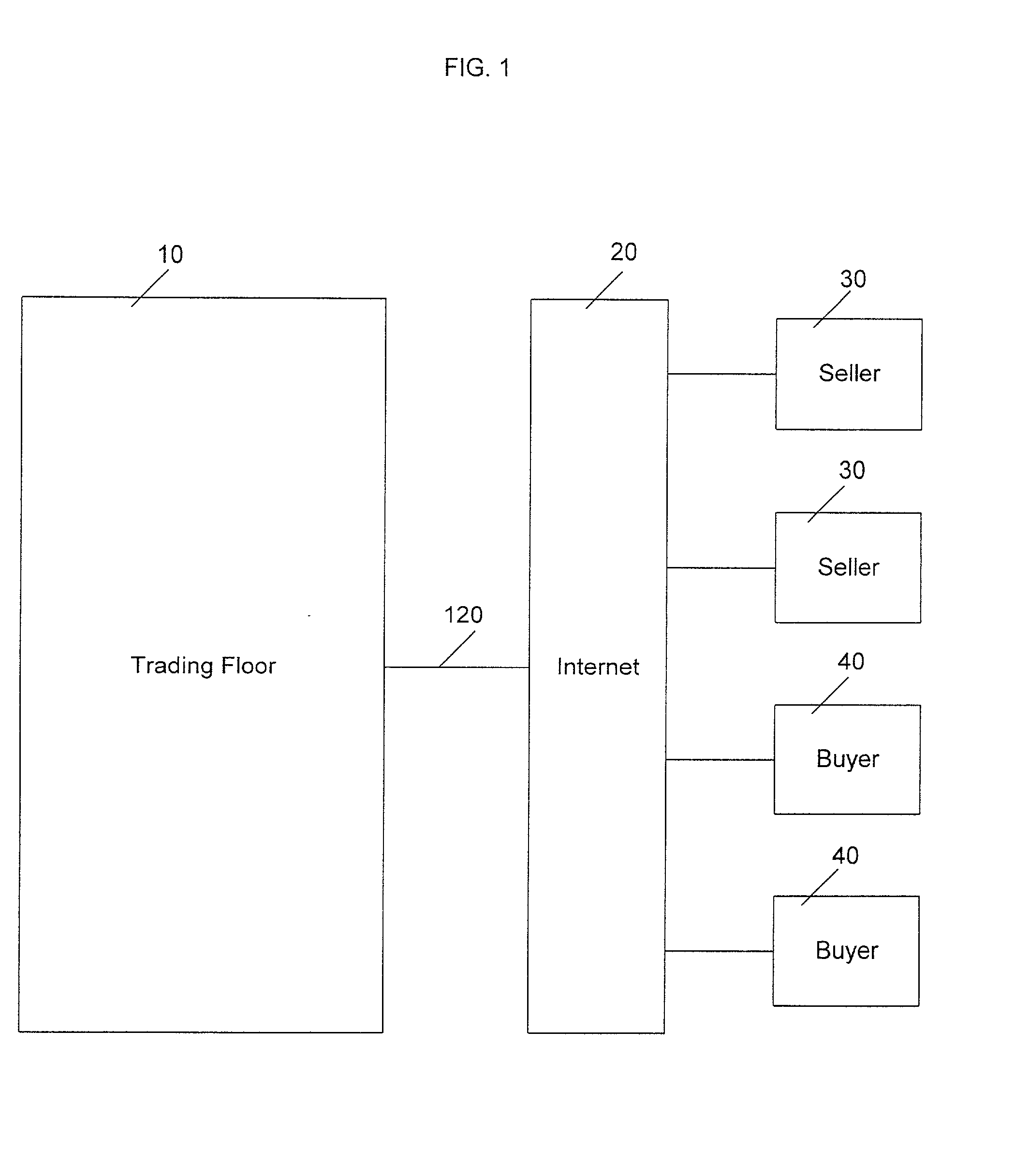
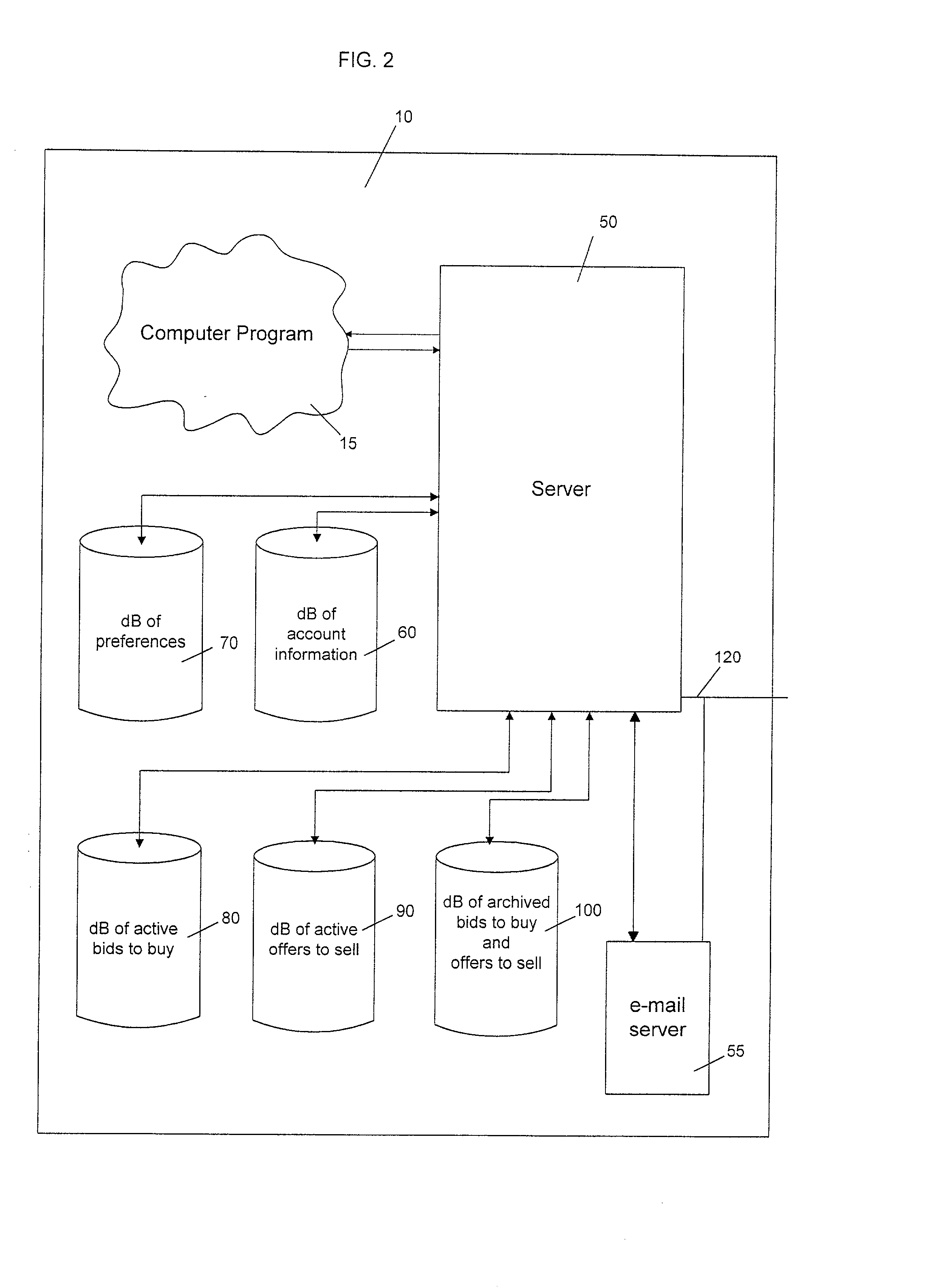
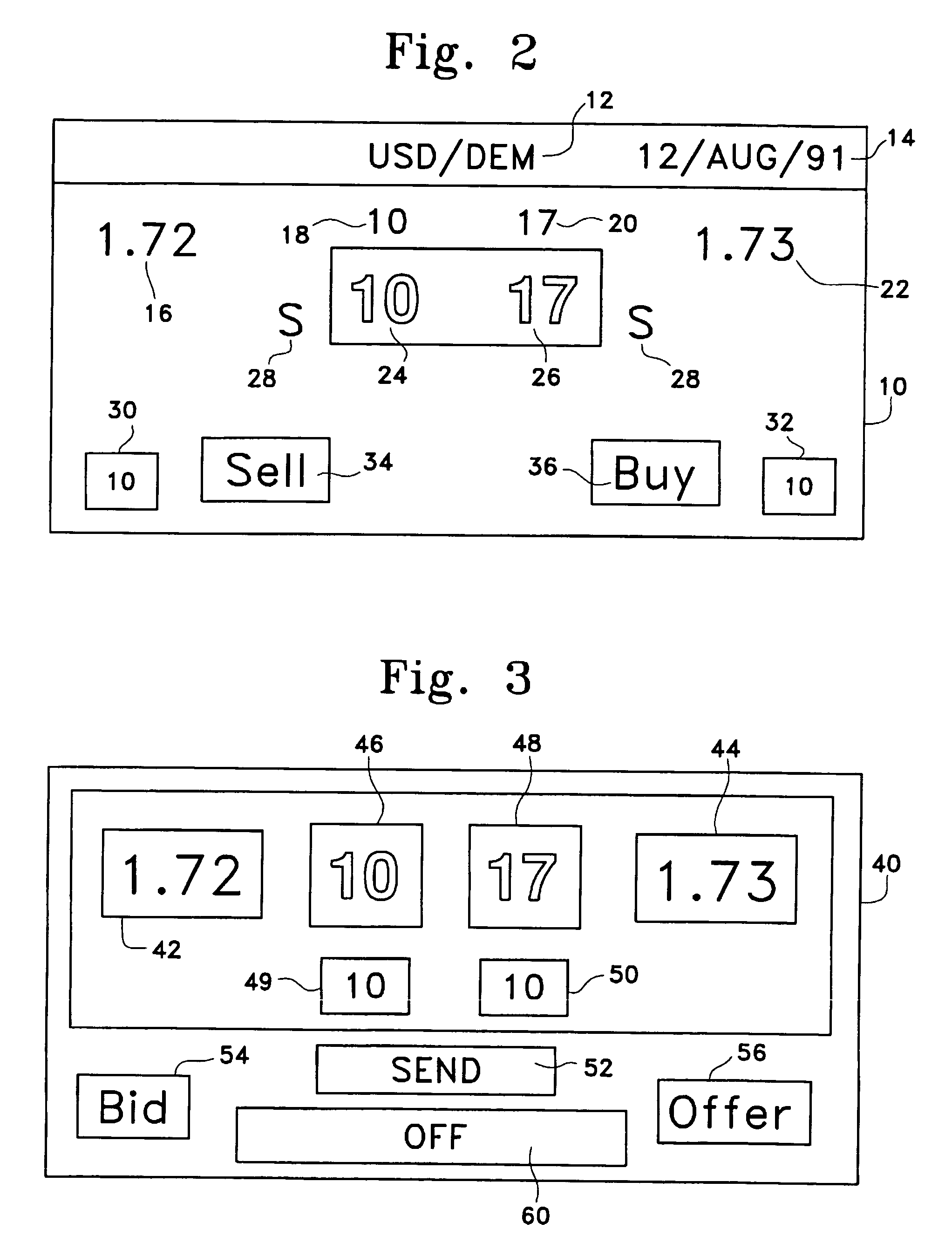
An anonymous trading system (FIG. 1) identifies the best bids and offers (QuoteSubmit, FIG. 3) from those counterparties (WS A1a1) with which each party (WS A1fb1, WS A1b2, ... WS A2a2) is currently eligible to deal, while maintaining the anonymity of the potential counterparty and the confidentiality of any specific credit limitations imposed by the anonymous potential counterparty. To that end, each bid or offer (QuoteSubmit, FIG. 3) for a particular type of financial instrument is prescreened by the system for compatibility with limited credit information (for example, a one bit flag indicating whether a predetermined limit has already been exceeded) and an anonymous “Dealable” price (24,26) is calculated for each of the traders (WS A1b, . . . WS A2a) dealing with that particular financial instrument.
Owner:EBS DEALING RESOURCES
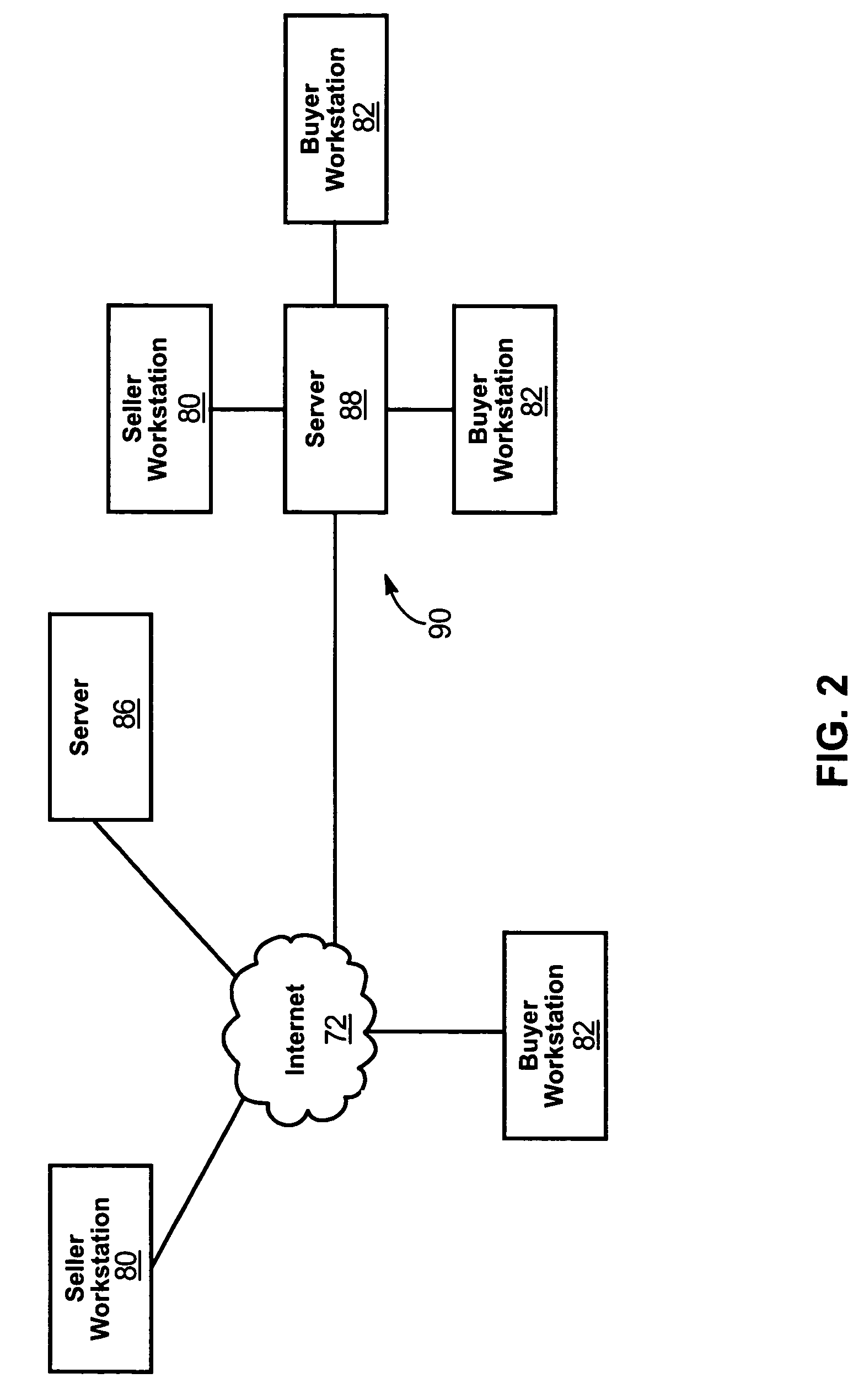
Online transaction hosting apparatus and system
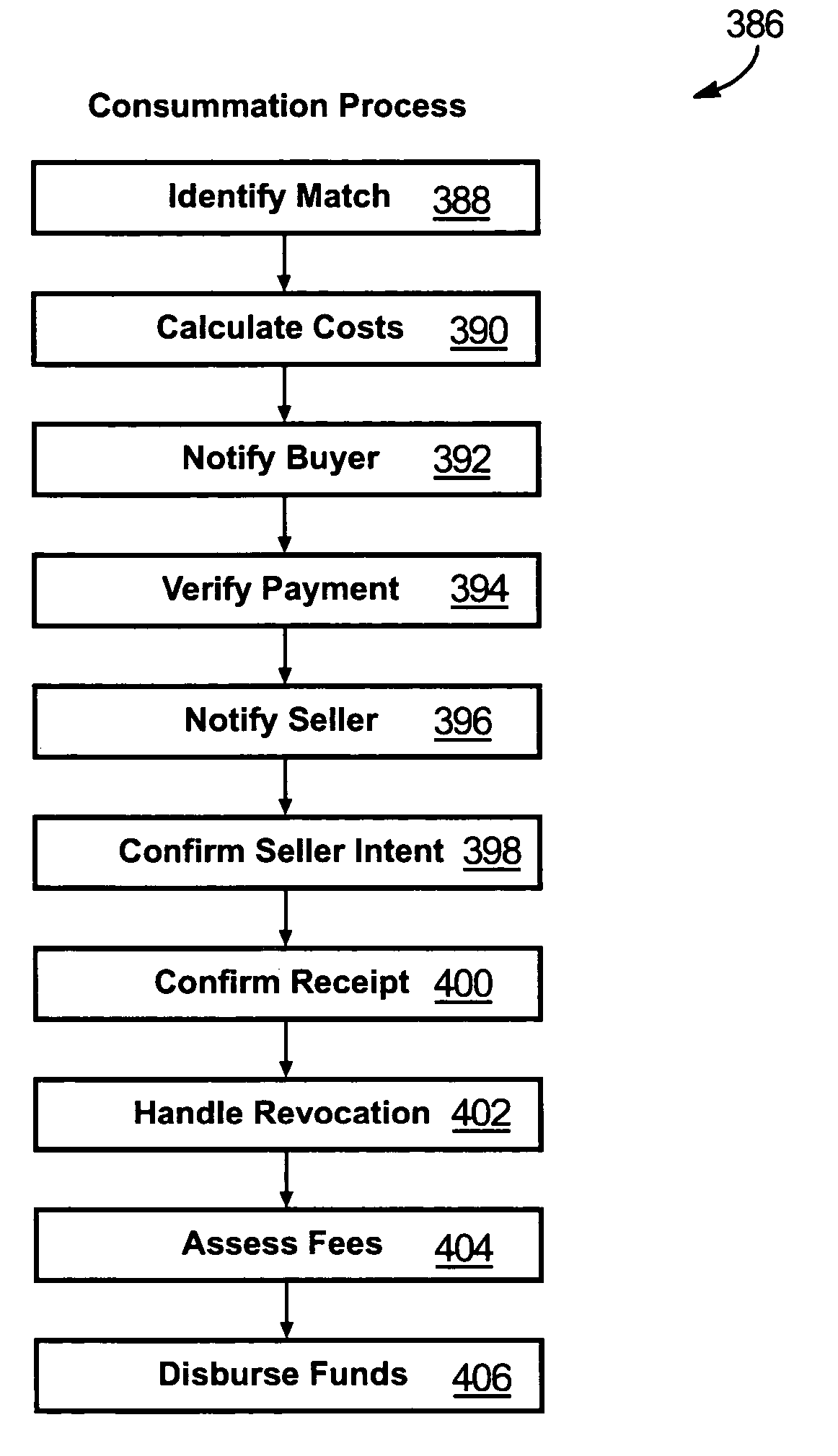
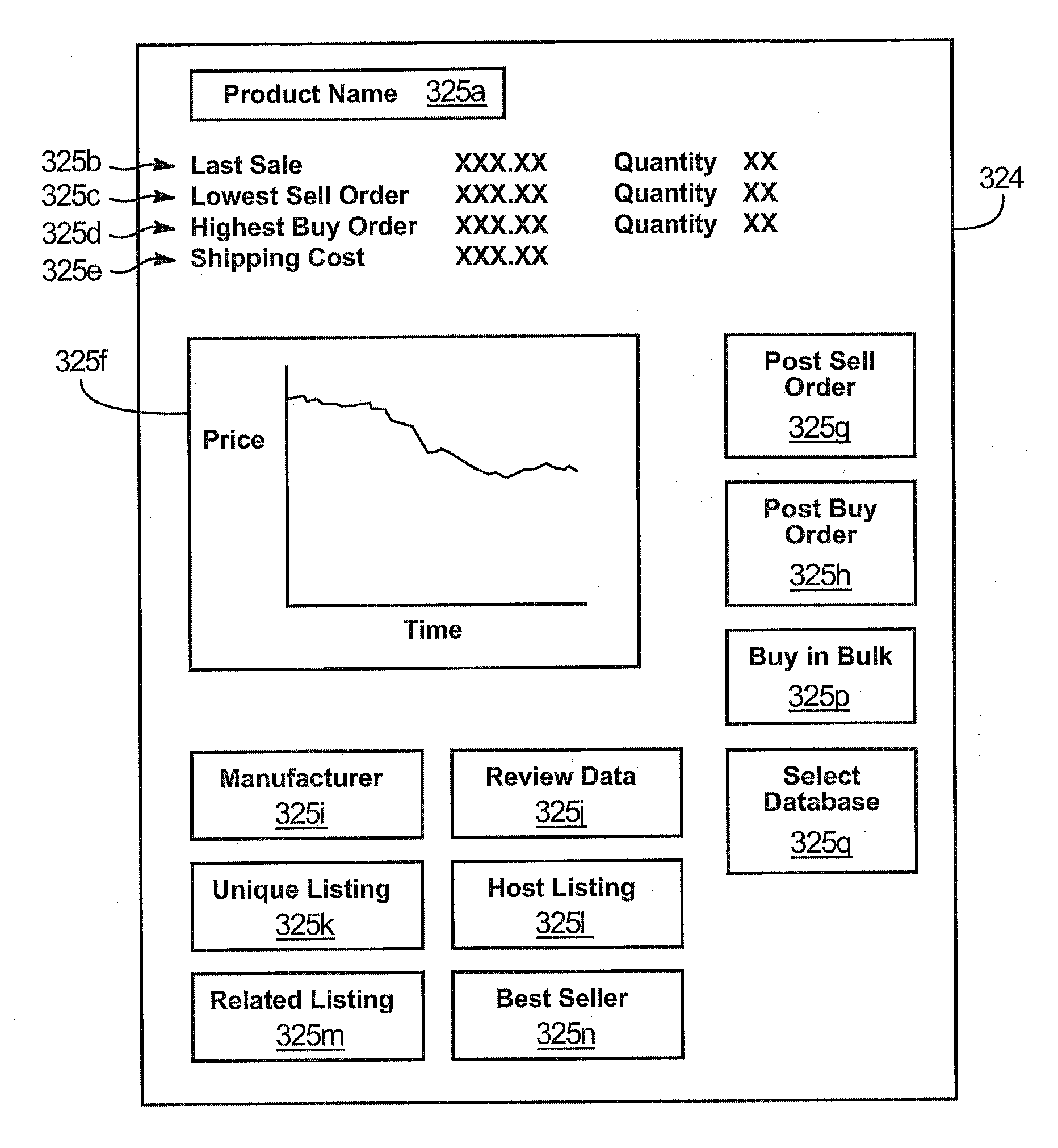
An invention is disclosed relating to an apparatus and method for hosting transactions over a network such as the Internet. Sellers post offers to sell under a listing belonging to an organized database of listings. Likewise, buyers post offers to buy. A matching module selects offers to sell and matches them to offers to buy based on a predefined criteria. Before posting offers to sell or buy, buyers and sellers may be presented with data concerning the market for the product that is the subject of the offer. A sale is consummated between the buyer and seller of the matched offer to buy and offer to sell. Consummation may include assessing the risk of fraud posed by the matched buyer and matched seller. Fees may be charged to the matched buyer, the matched seller, or both as insurance against fraud. Payment may be made by the buyer directly to the seller or to a host hosting the apparatus and method for conducting the transaction. Payment is forwarded to the seller by the host upon confirmation by the buyer that a product has been received in good order. An automated, or partially automated, dispute resolution process may resolve disputed transactions.
Owner:REVOLUTIONARY E COMMERCE SYST
Anonymous mailing and shipping transactions
InactiveUS7213748B2Improve identityGood serviceCredit registering devices actuationDetergent solventsCredit cardInternet privacy
The anonymity of a consumer is protected in mailing and shipping transactions by utilizing an alias. A secure database is utilized to retrieve the true name and address for making mail delivery or shipment. The true name and address may be retrieved by the shipper during transit, by a disguised mailing center, or by a mail distributor. The anonymous mailing and shipping transactions may include anonymous payment transactions, such as payments made from an anonymous credit card account.
Owner:FIRST DATA
Opt-in delivery of advertisements on mobile devices
InactiveUS20060149630A1Maintaining anonymityWithout significantly detracting from the user's mobile device experienceMarketingAnonymityMobile app
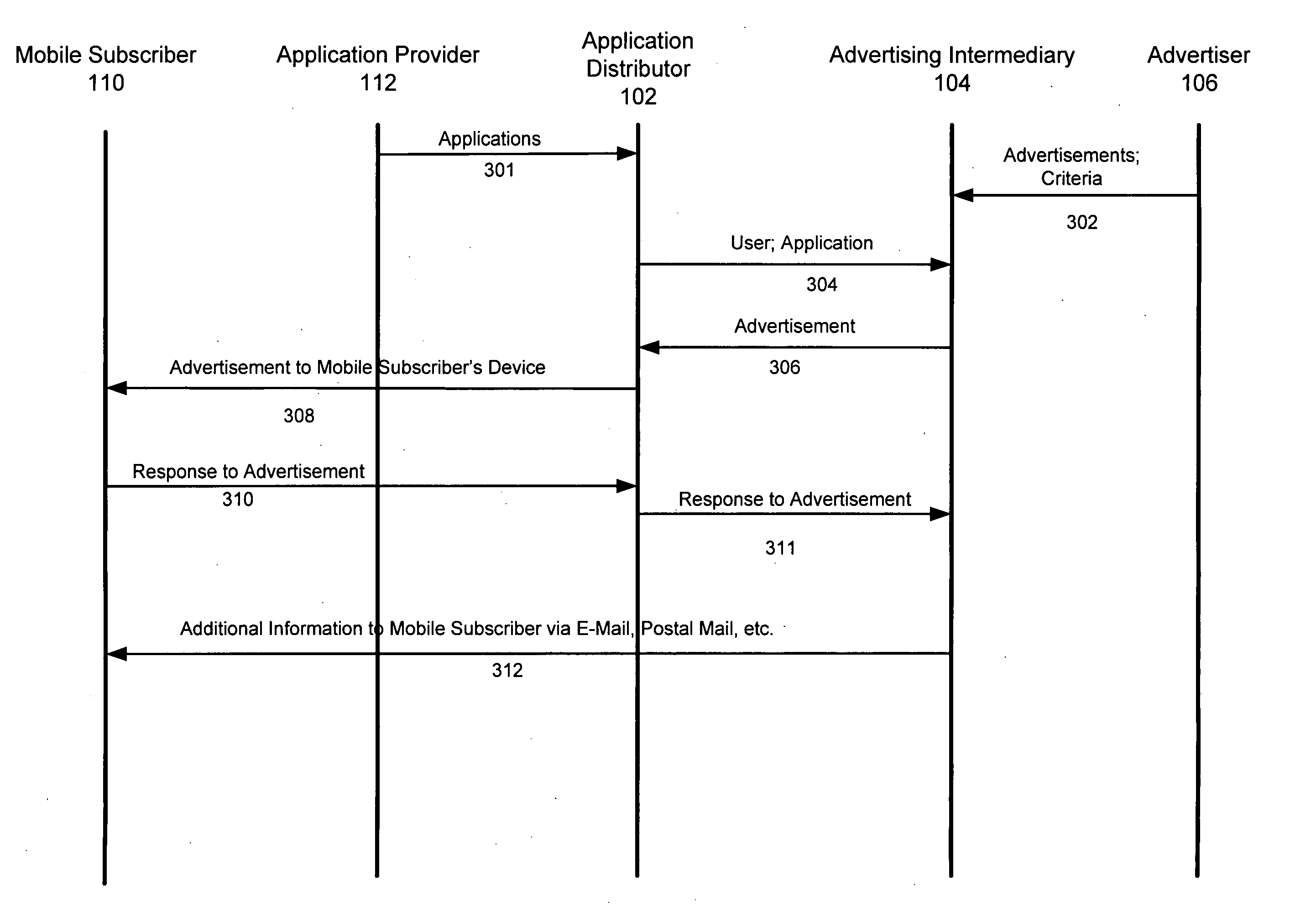
Advertisements provided to a mobile device user allow the user to obtain information from advertisers without revealing the user's identity. Advertisers supply advertisements to an advertising intermediary, which maintains the advertisements in a database, and also maintains a database of mobile device users who are subscribers to its service. Separately, application providers provide mobile applications to an application distributor. The application distributor in turn provides the applications to the mobile subscriber. The application distributor integrates advertisements supplied by the advertising intermediary into the applications and application content it distributes to the subscriber. If the subscriber requests additional information, an indication of this interest is sent to the advertising intermediary, which forwards additional information provided by the advertiser, such as a URL, product brochure, or the like to the mobile subscriber via his indicated preferred medium, e.g., e-mail or post, maintaining anonymity for the subscriber with respect to the advertisers.
Owner:VEEKER CORP
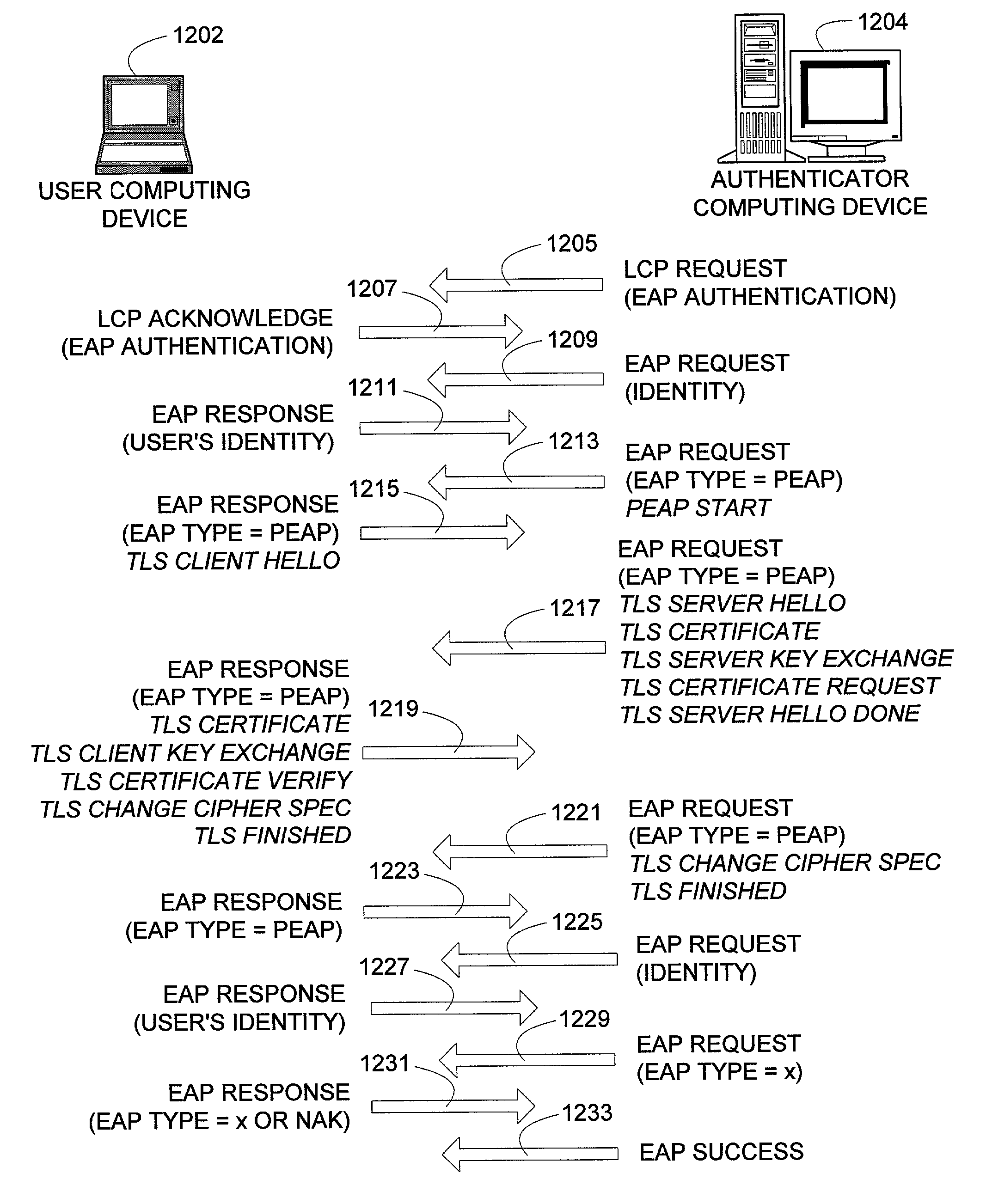
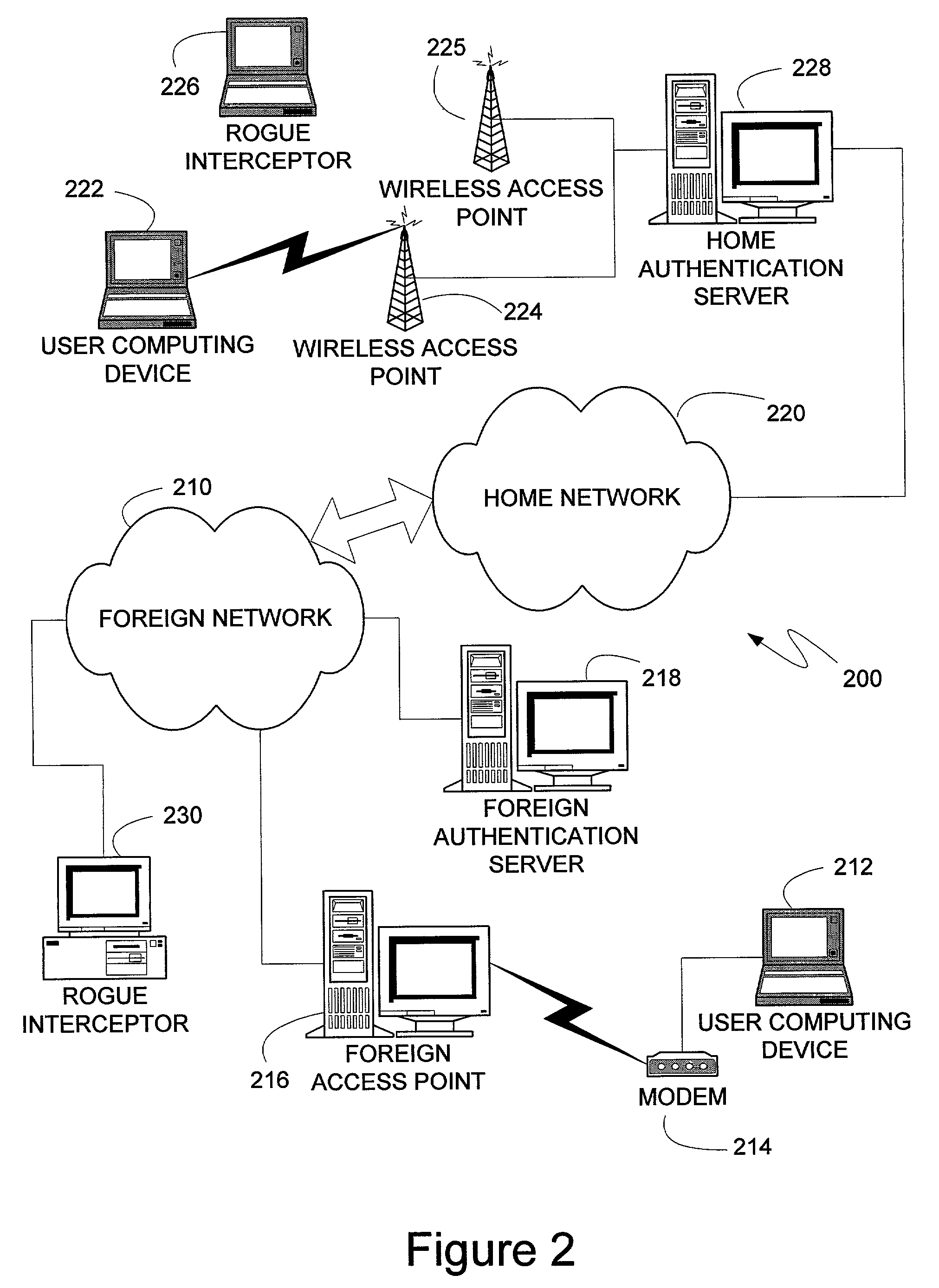
TLS tunneling
InactiveUS7529933B2Reduce interceptionProtect normal transmissionUser identity/authority verificationSecret communicationSecure communicationWireless mesh network
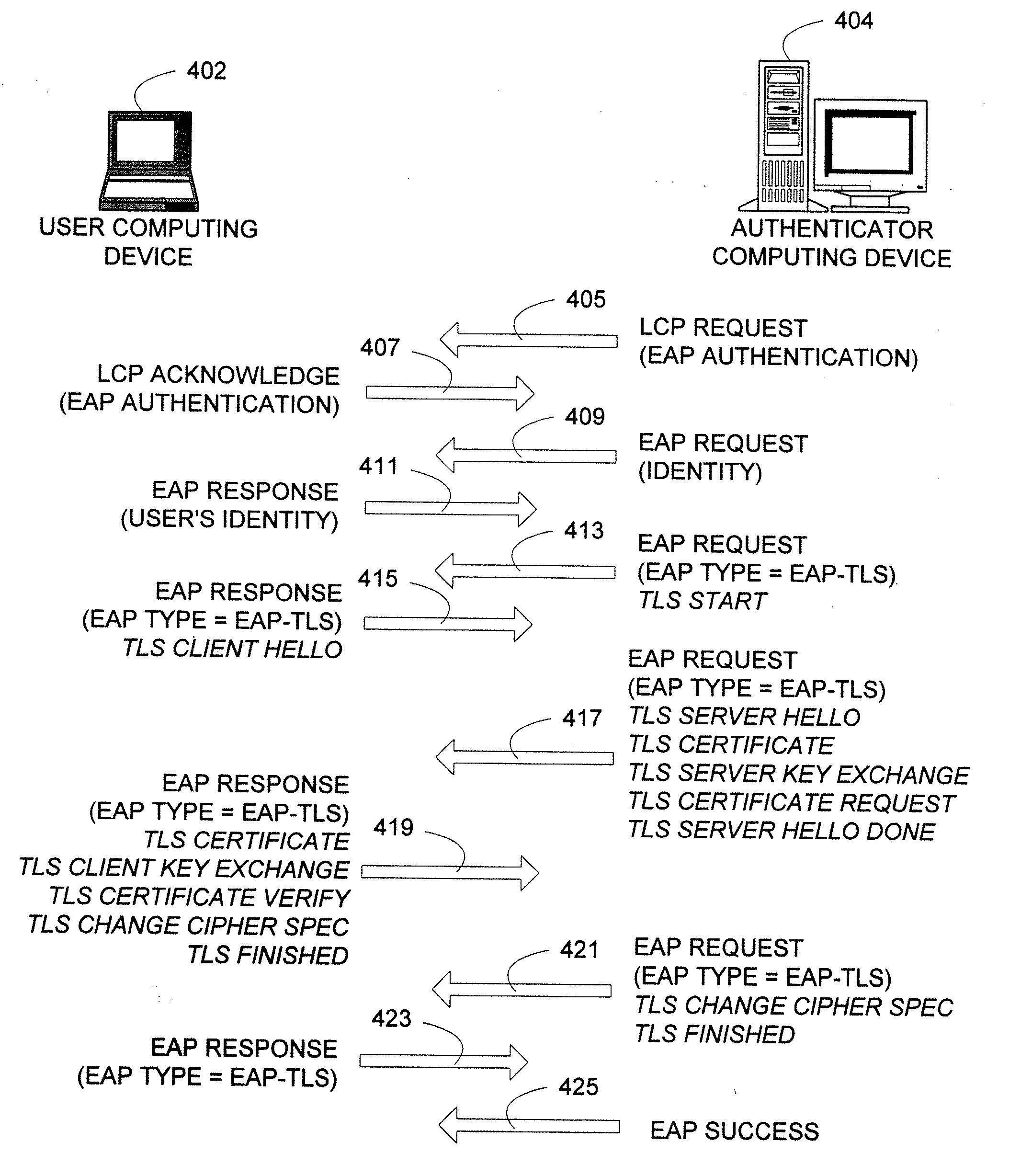
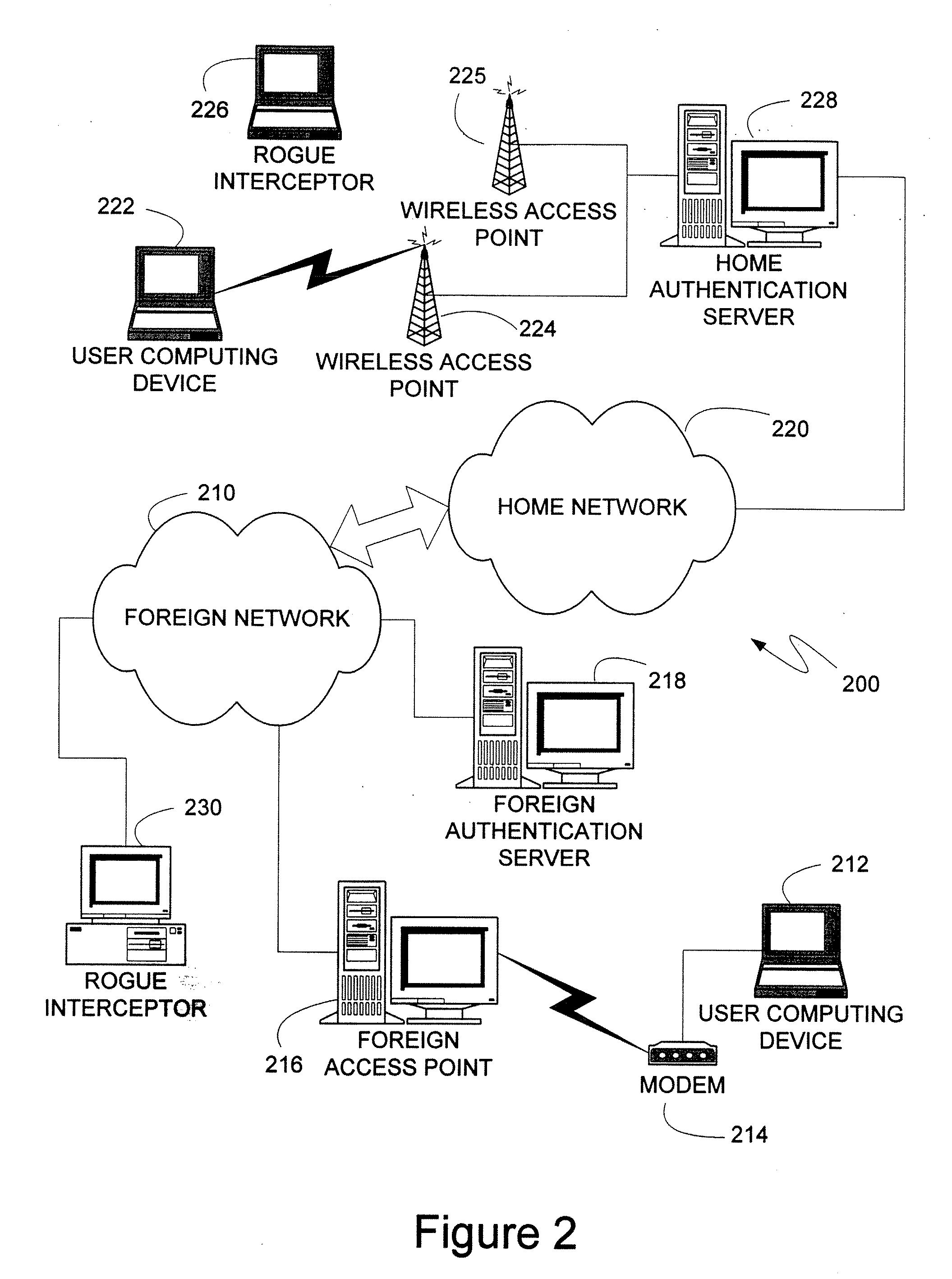
An authentication protocol can be used to establish a secure method of communication between two devices on a network. Once established, the secure communication can be used to authenticate a client through various authentication methods, providing security in environments where intermediate devices cannot be trusted, such as wireless networks, or foreign network access points. Additionally, the caching of session keys and other relevant information can enable the two securely communicating endpoints to quickly resume their communication despite interruptions, such as when one endpoint changes the access point through which it is connected to the network. Also, the secure communication between the two devices can enable users to roam off of their home network, providing a mechanism by which access through foreign networks can be granted, while allowing the foreign network to monitor and control the use of its bandwidth.
Owner:MICROSOFT TECH LICENSING LLC
Methods and apparatus for providing user anonymity in online transactions
InactiveUS20060274896A1Avoid the needEliminate the problemDigital data processing detailsMultiple digital computer combinationsPaymentWeb site
End-to-end user anonymity is provided in electronic commerce or other types of online transactions through the use of an intermediary. An intermediary machine, which may be implemented in the form of a set of servers or other type of computer system, receives communications from a consumer or other user, and generates and maintains an alias for that user. Connections between the user machine and any online vendor or other web site are implemented through the intermediary using the alias. When the user desires to make a purchase from a given online vendor, the intermediary may present the user with a number of options. For example, the user may be permitted to select a particular payment card number and real destination address as previously provided to the intermediary. The intermediary then communicates with the online vendor and supplies intermediary payment information, e.g., a payment card number associated with the intermediary rather than the user, along with appropriate authorizing information and an alias destination address, e.g., a third party physical shipping address for deliverable goods, an alias electronic address for downloadable material, etc. The online vendor charges the purchase to the intermediary, and redirects the delivery of the goods or services to the destination address provided by the intermediary. The intermediary charges the payment card number of the user, and arranges for the redirection of the delivery to the real user address. In this manner, the invention provides complete end-to-end anonymity for the user, even when the user desires to enter transactions involving purchase and receipt of deliverable goods and services.
Owner:LIVESAY PAUL OWEN
Tls tunneling
ActiveUS20070157027A1Reduce interceptionProtect normal transmissionUser identity/authority verificationMultiple digital computer combinationsSecure communicationRelevant information
An authentication protocol can be used to establish a secure method of communication between two devices on a network. Once established, the secure communication can be used to authenticate a client through various authentication methods, providing security in environments where intermediate devices cannot be trusted, such as wireless networks, or foreign network access points. Additionally, the caching of session keys and other relevant information can enable the two securely communicating endpoints to quickly resume their communication despite interruptions, such as when one endpoint changes the access point through which it is connected to the network. Also, the secure communication between the two devices can enable users to roam off of their home network, providing a mechanism by which access through foreign networks can be granted, while allowing the foreign network to monitor and control the use of its bandwidth.
Owner:MICROSOFT TECH LICENSING LLC
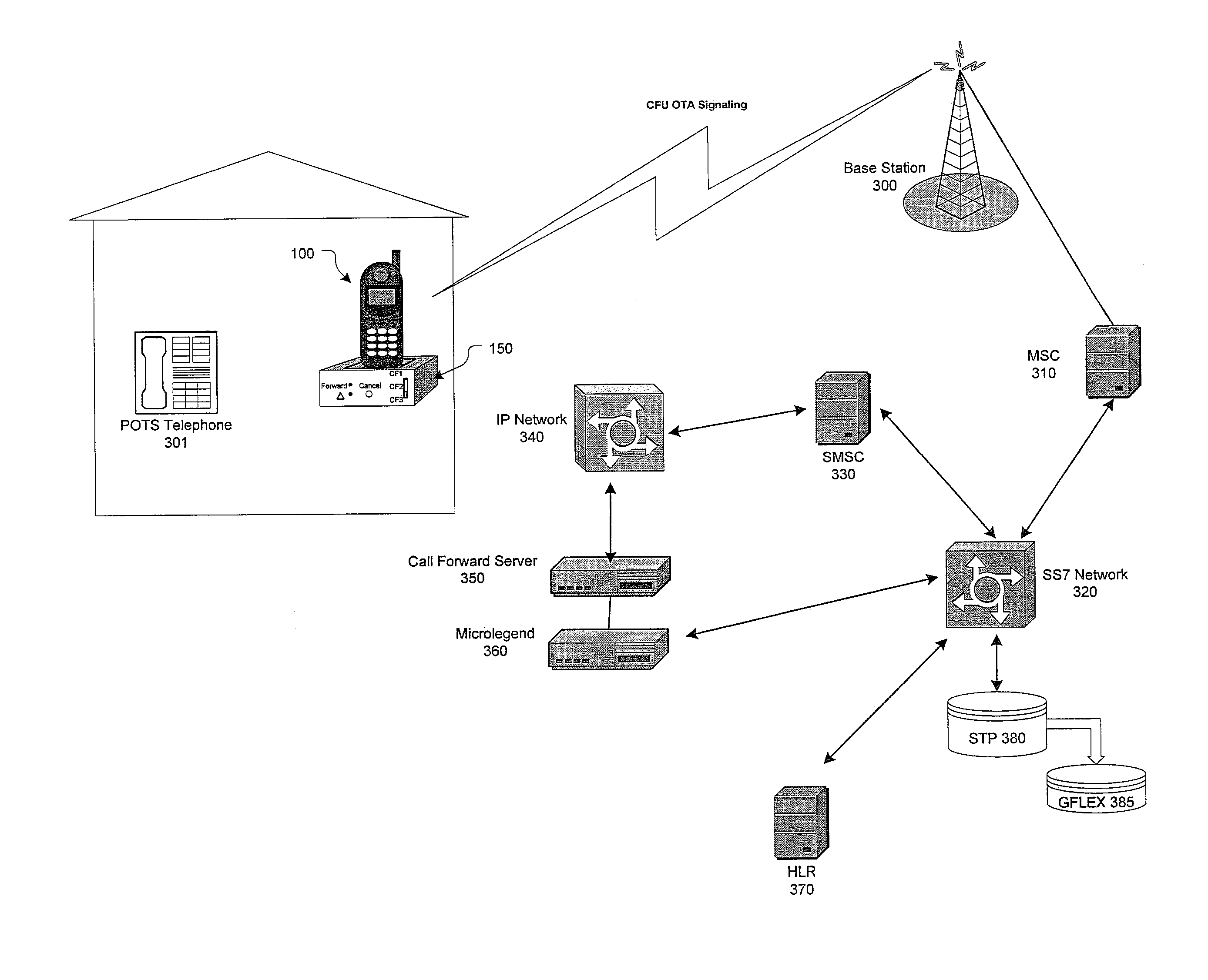
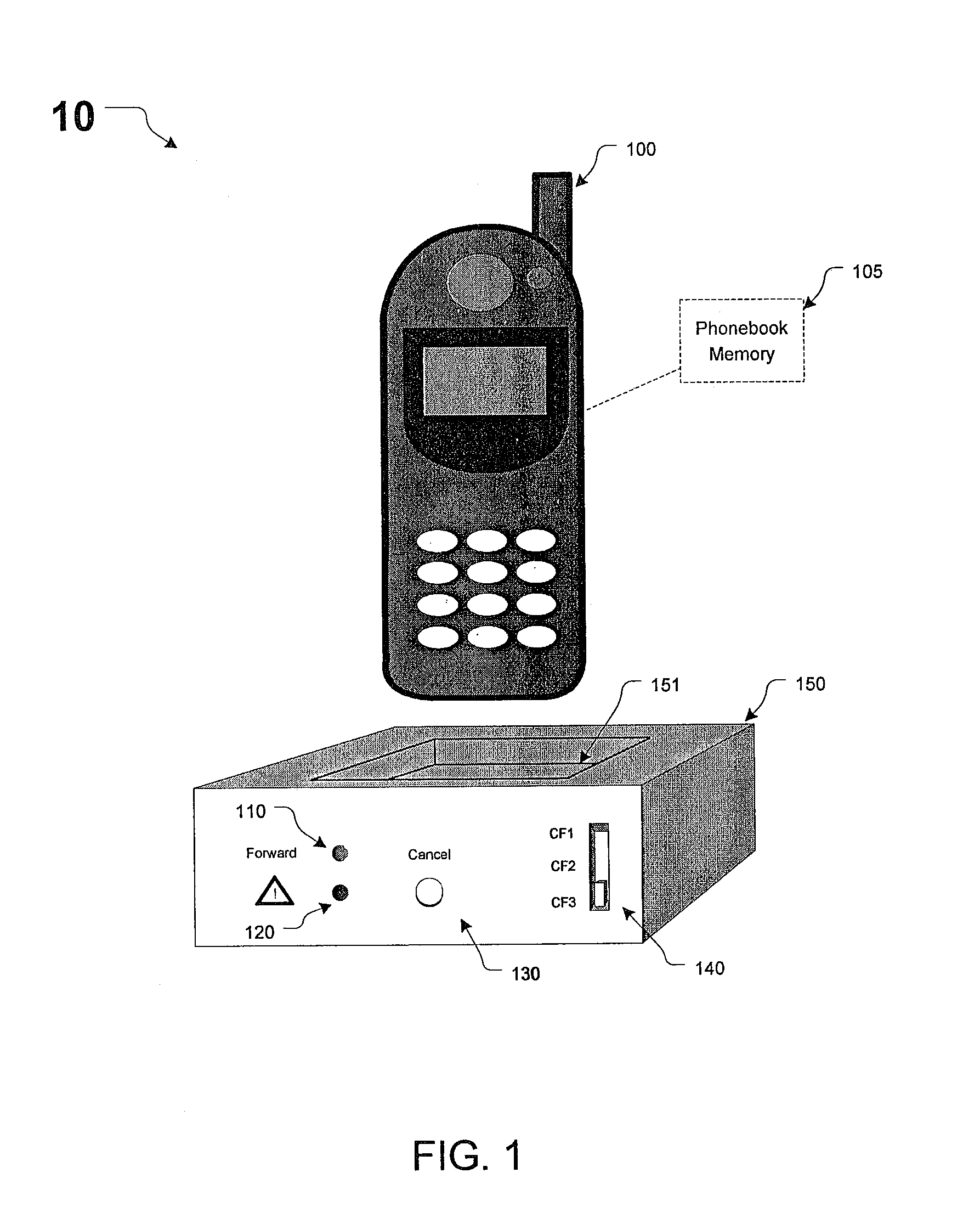
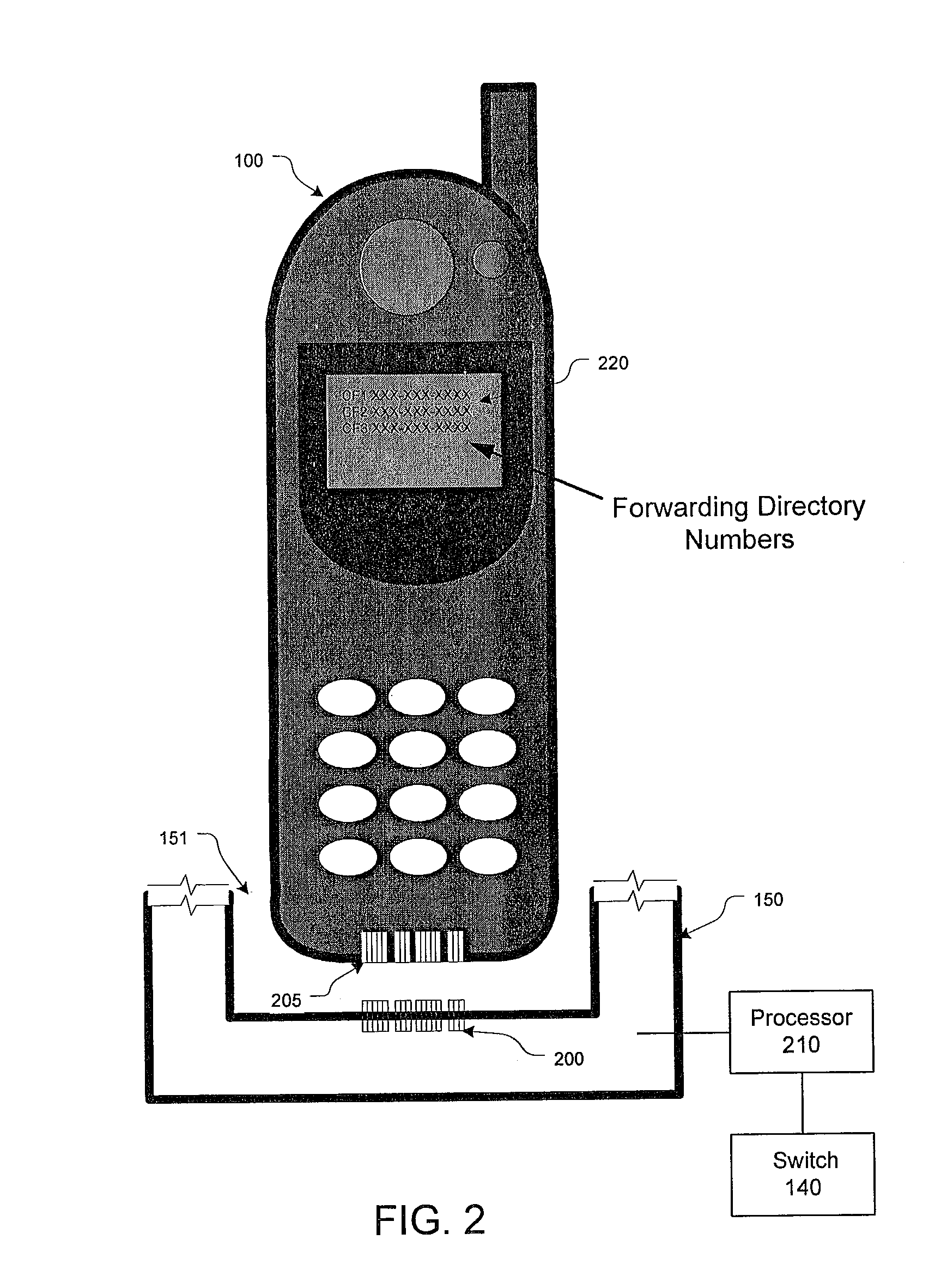
Systems and methods for automatic call forwarding in a wireless mobile station
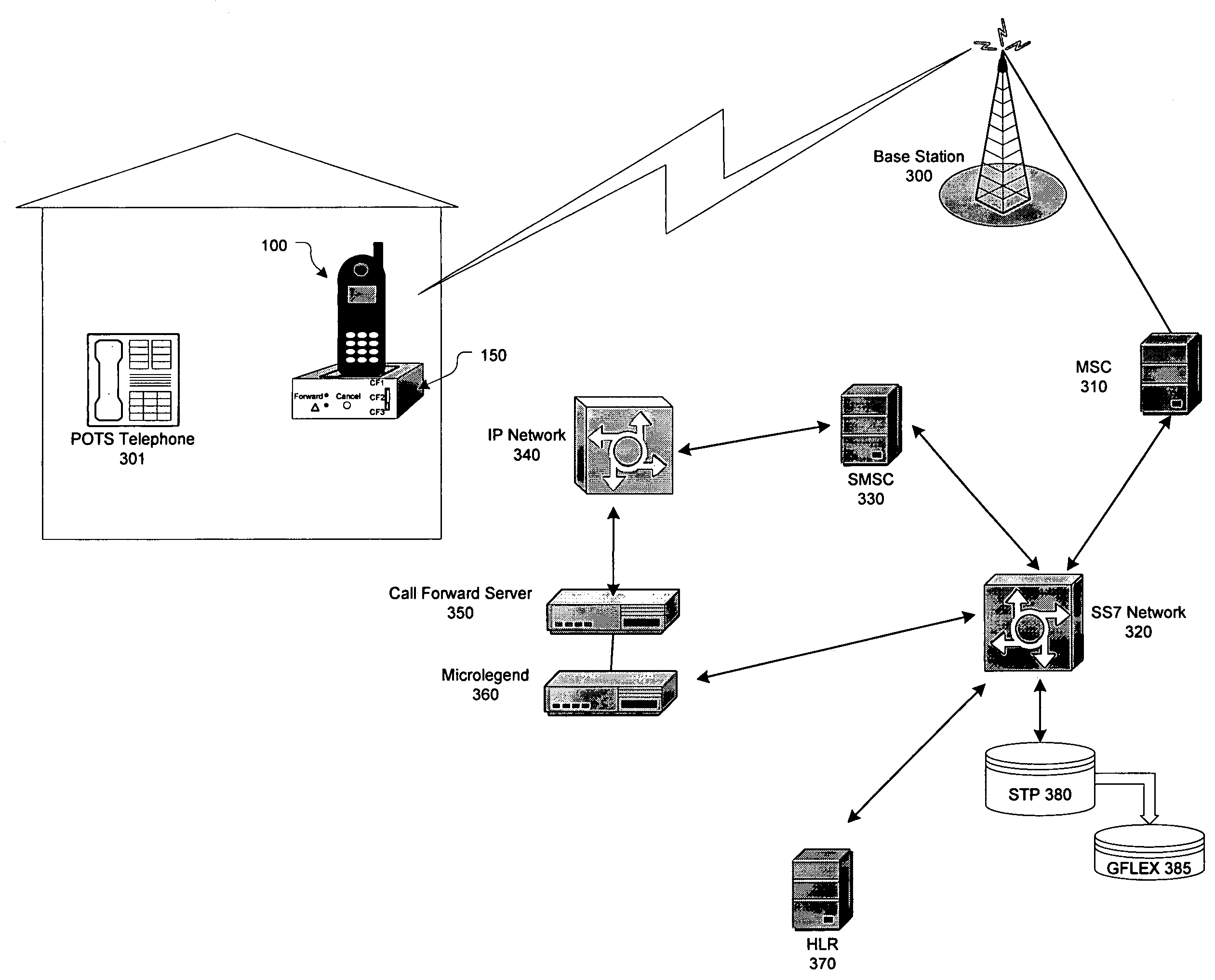
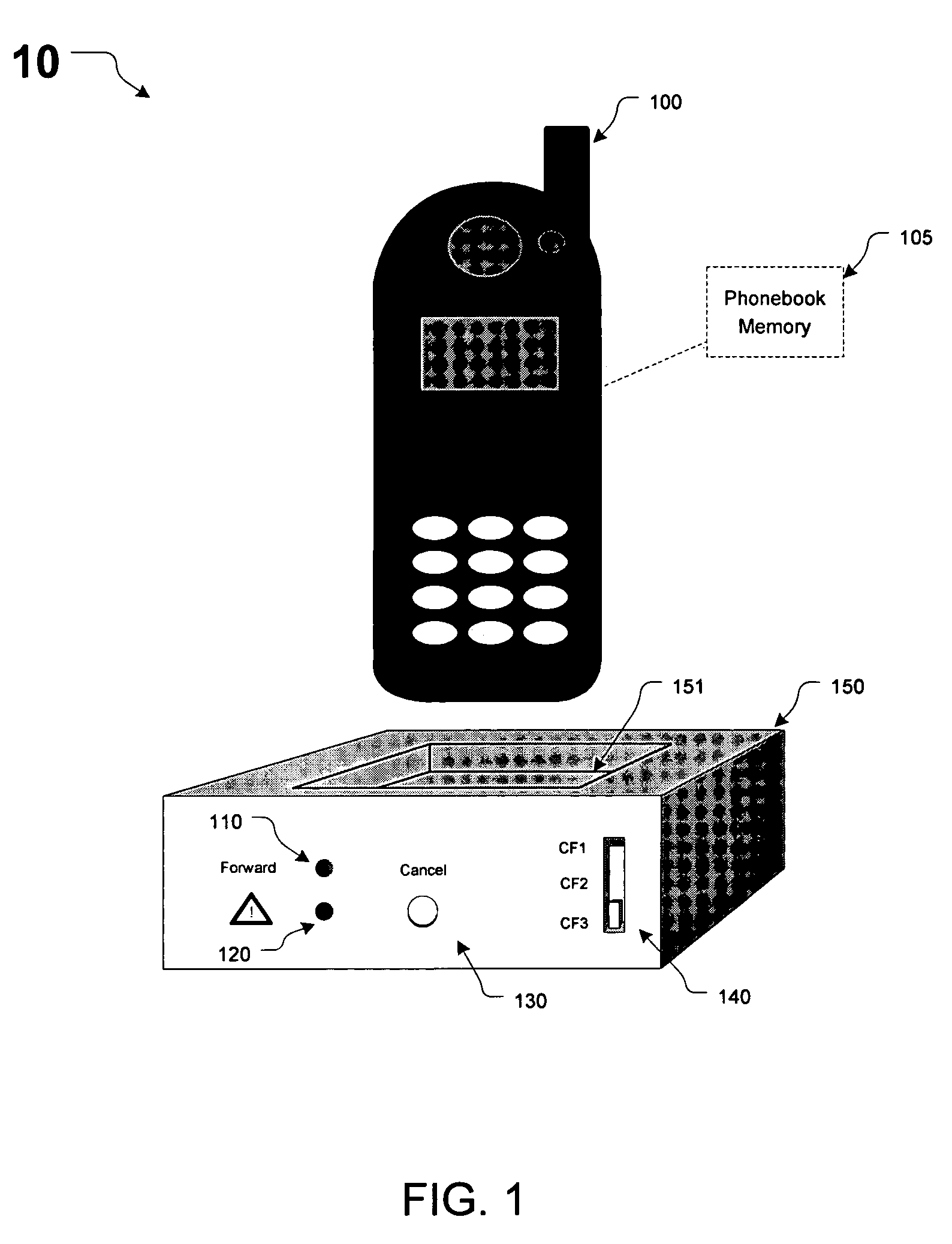
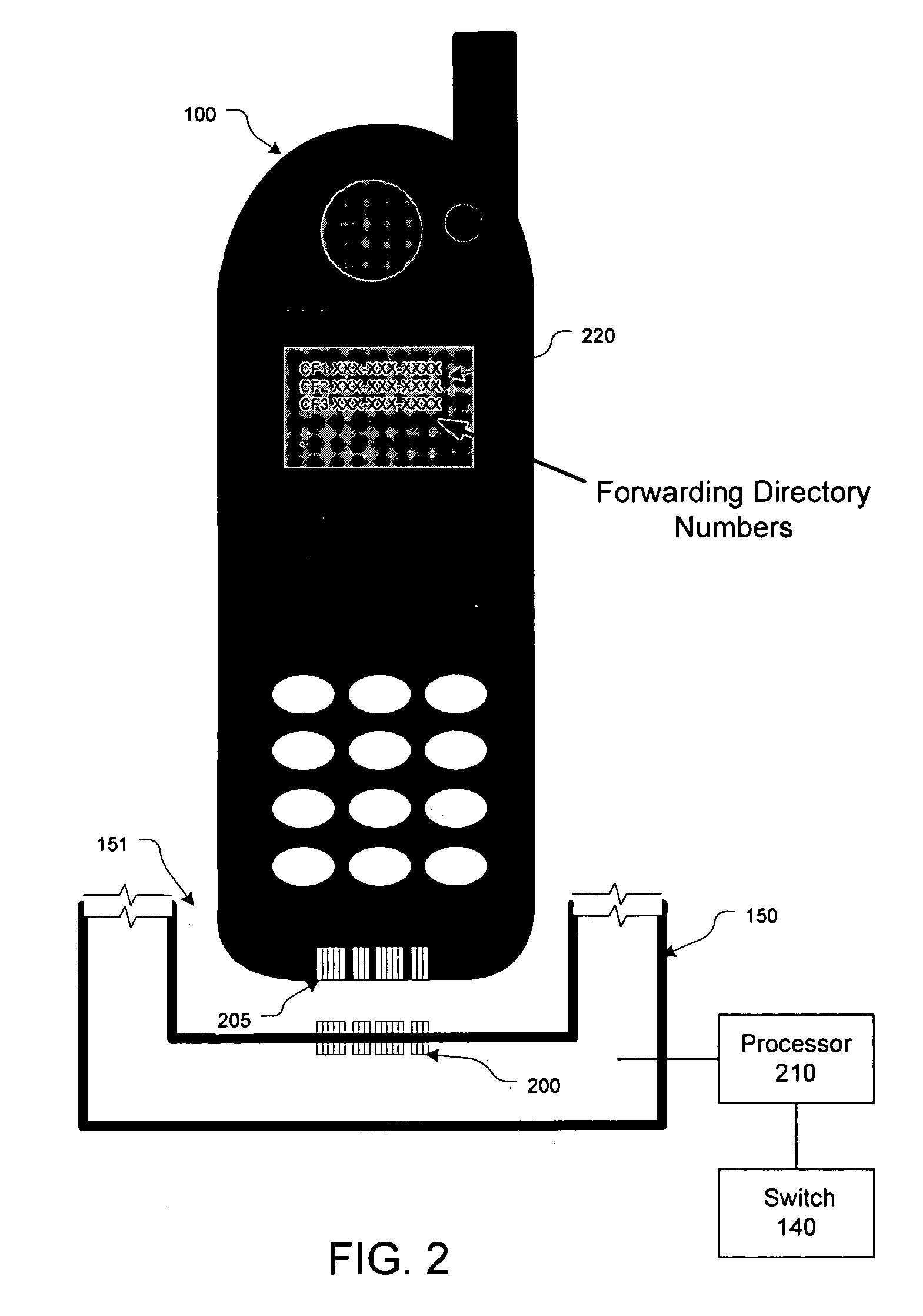
ActiveUS7116975B1Easy to mergeService conveniently and inexpensivelySpecial service for subscribersCommmunication supplementary servicesCall forwardingMobile station
Apparatus, method and system for notifying a communications-switching center that subsequent communications directed to a wireless number associated with the wireless unit are to be routed to a destination number associated with the wireless unit. In response to a triggering event by the wireless unit through the base unit, the base unit causes the wireless unit to transmit an SMS message to the communications-switching center. The SMS message includes a notification that subsequent communications directed to the wireless number associated with the wireless unit are to be routed to the destination number associated with the wireless unit.
Owner:CINGULAR WIRELESS II LLC
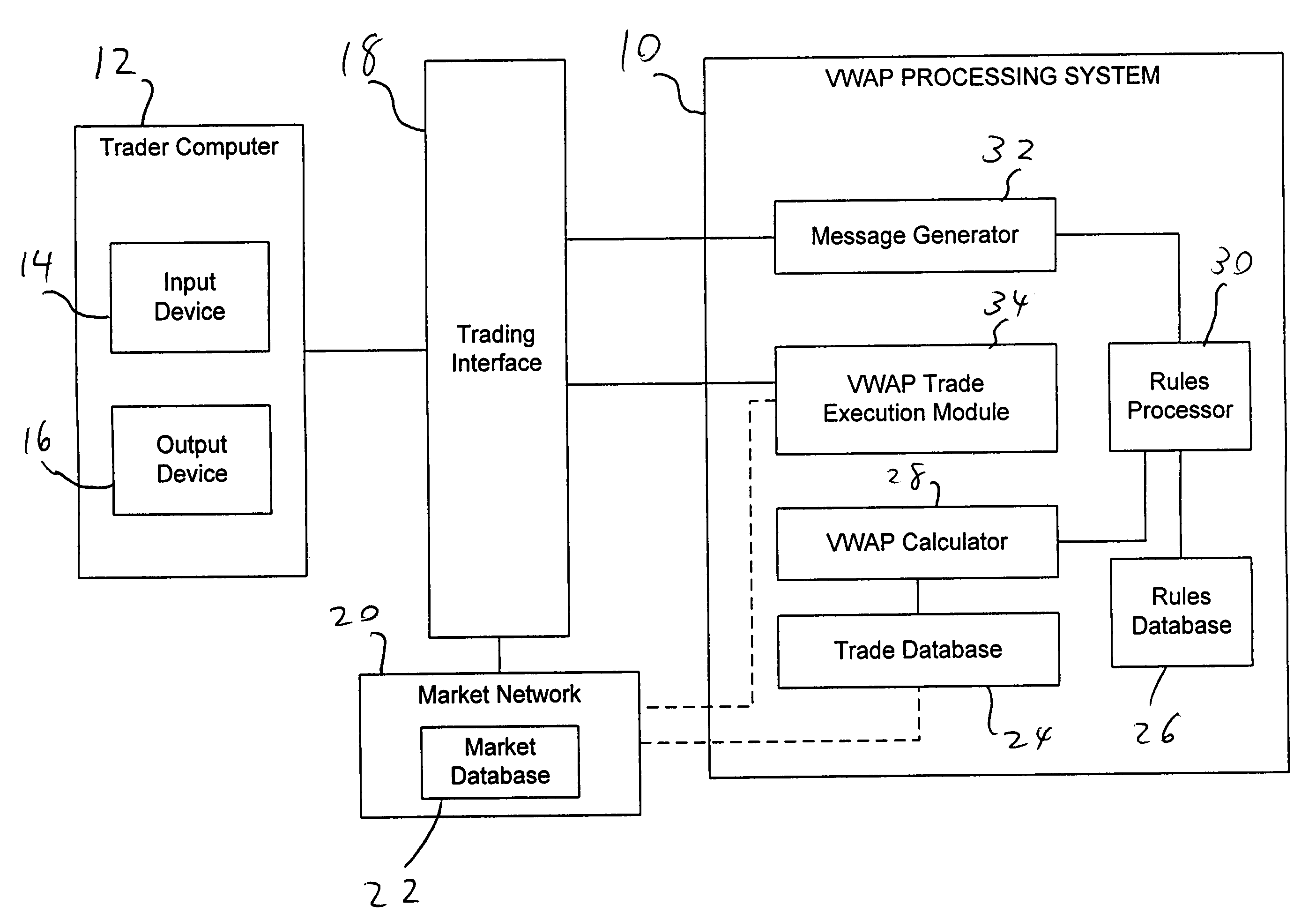
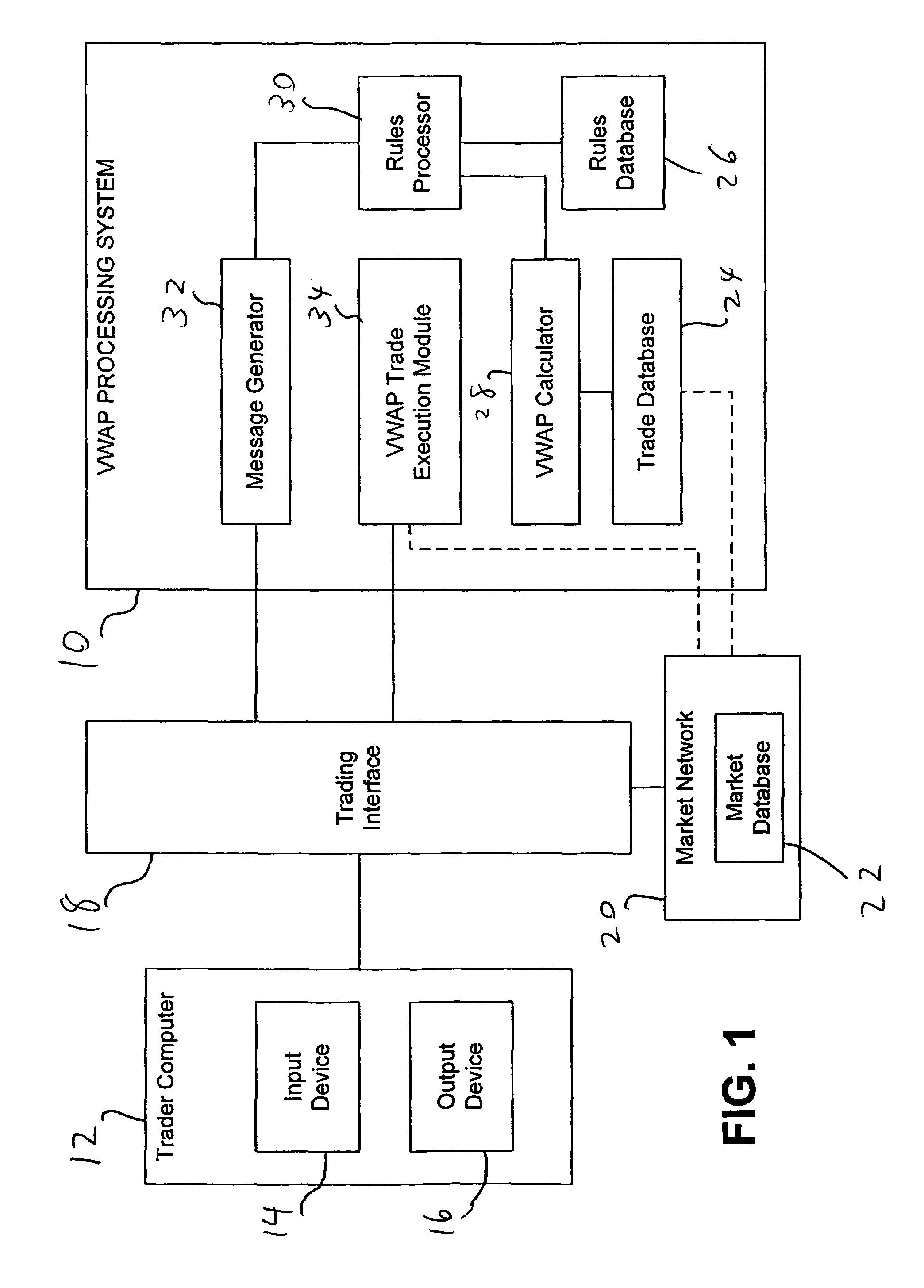
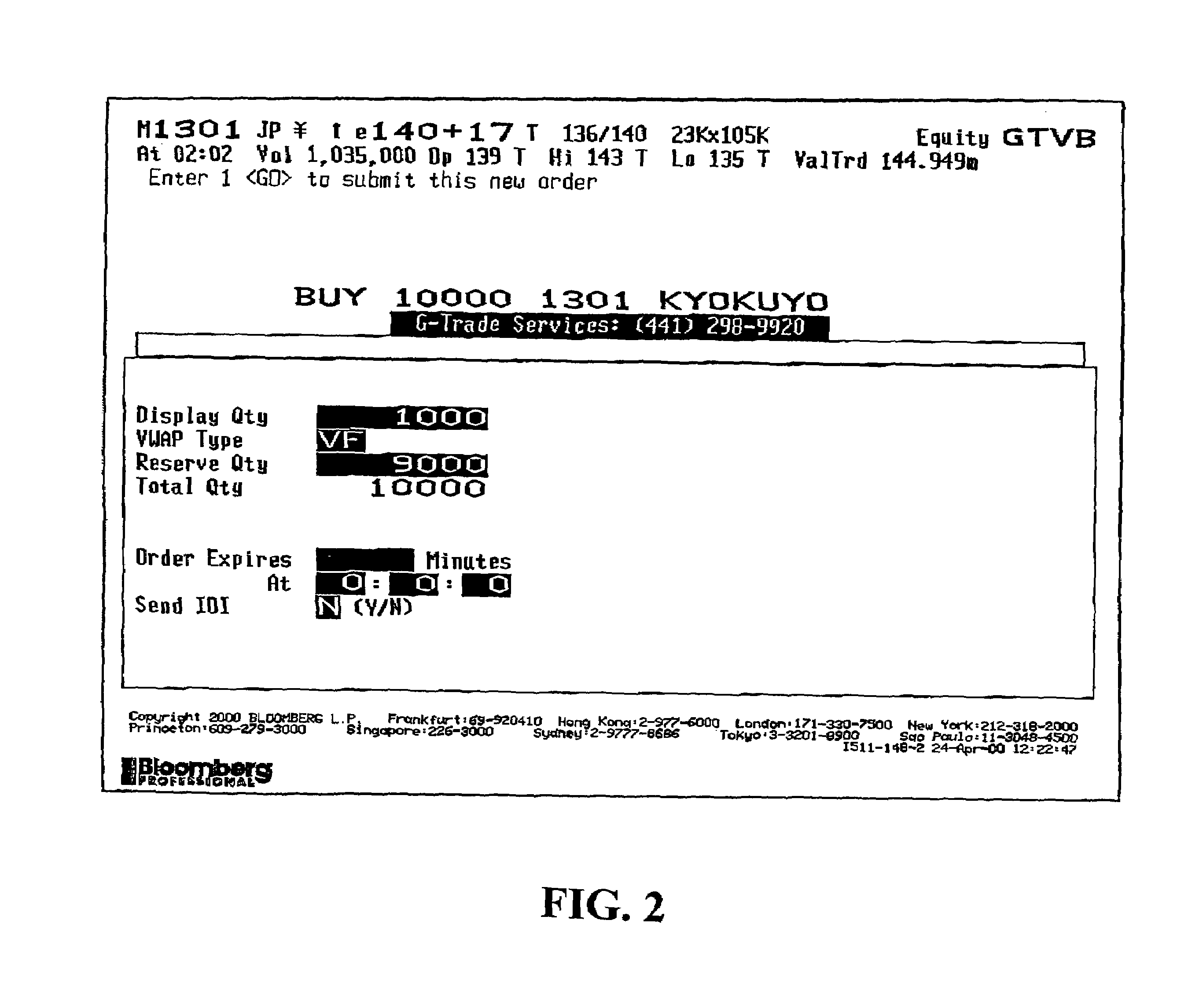
System and method for processing trades using volume-weighted-average pricing techniques
A computerized system and method electronically conduct trades in securities, display information corresponding to orders, match the orders, and price the matched orders on the basis of volume-weighted-average price (VWAP). Orders are matched of buyers and sellers who wish to trade designated quantities of securities at a price based on the VWAP for the security in question determined with reference to a defined time period, which is set in advance of order matching, and may consist of an entire trading day on the market on which the security is traded or a portion thereof as determined by the trading parties and / or the disclosed system. VWAP trading is facilitated by displaying, over an output device, orders entered on the “buy” side and “sell” side. Trades of matched orders are continuously and / or non-continuously executed and the trades priced after the close of the relevant defined time period at the calculated VWAP.
Owner:BLOOMBERG +1
Trading system with anonymous rating of participants
InactiveUS20020087453A1Maintaining anonymityPreserve integrityFinanceBuying/selling/leasing transactionsThe InternetDissemination
A method and apparatus for the analysis and dissemination of data in an on-line trading environment is disclosed. The trading environment is implemented on a server such that users have easy access to an electronic trading exchange via the Internet. A user may set account preferences such that a table is generated and displayed for easy recognition of preferred, acceptable and unacceptable trading partners. In addition, the identity of all sellers may remain unknown to protect the integrity of the trading environment.
Owner:AGEX COM
Credit management for electronic brokerage system
InactiveUS6996541B2Maintaining anonymitySpecial service provision for substationFinanceConfidentialityAnonymity
An anonymous trading system identifies the best bids and offers from those counterparties with which each party is currently eligible to deal, while maintaining the anonymity of the potential counterparty and the confidentiality of any specific credit limitations imposed by the anonymous potential counterparty. To that end, each bid or offer for a particular type of financial instrument is prescreened by the system for compatibility with limited credit information (for example, a one bit flag indicating whether a predetermined limit has already been exceeded) and an anonymous “Dealable” price is calculated for each of the traders dealing with that particular financial instrument.
Owner:EBS DEALING RESOURCES
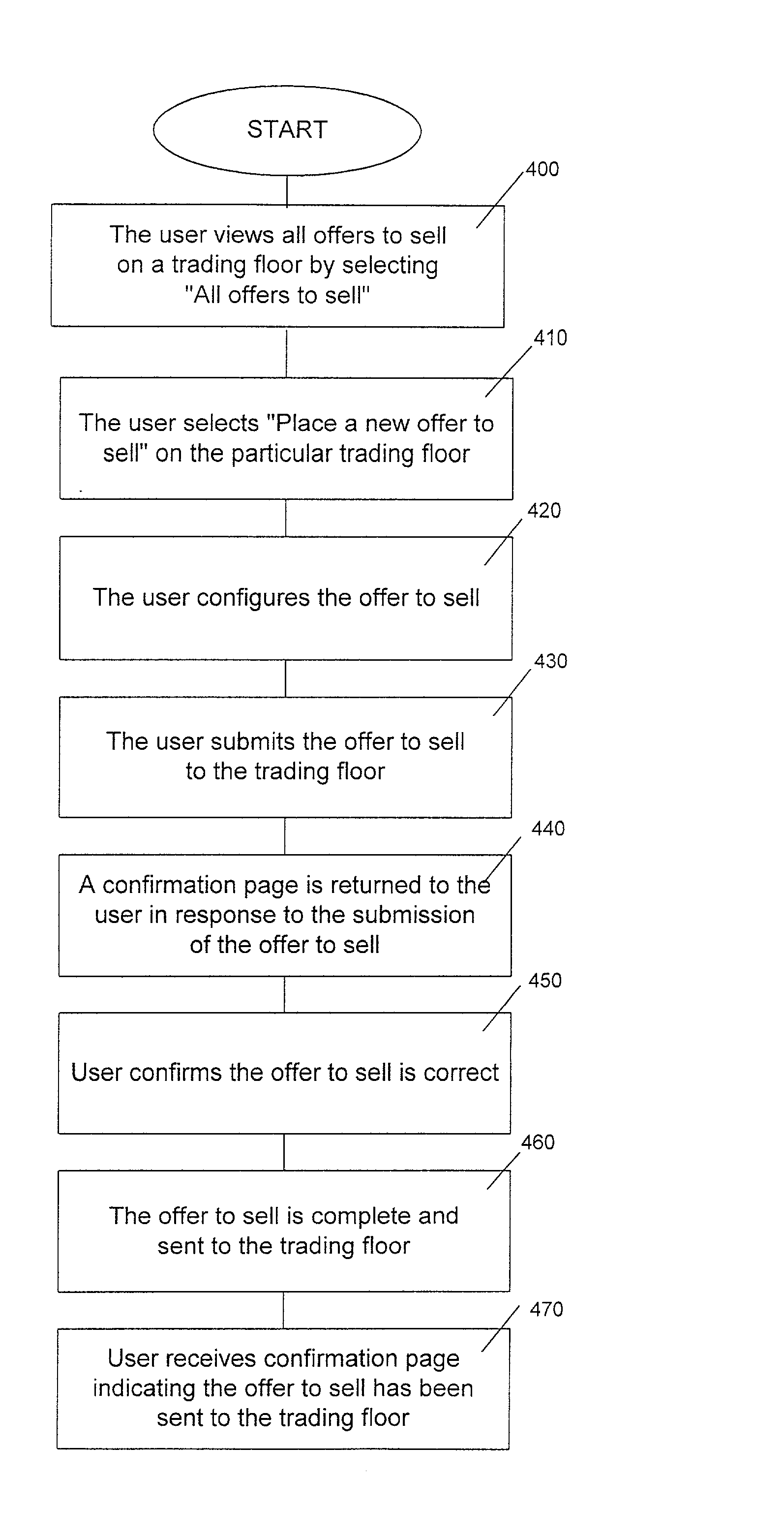
Online transaction hosting apparatus and method
InactiveUS20110112869A1Improve matchLow costFinanceMultiple digital computer combinationsPaymentThe Internet
An invention is disclosed relating to an apparatus and method for hosting transactions over a network such as the Internet. Sellers post offers to sell under a listing belonging to an organized database of listings. Likewise, buyers post offers to buy. A matching module selects offers to sell and matches them to offers to buy based on a predefined criteria. Before posting offers to sell or buy, buyers and sellers may be presented with data concerning the market for the product that is the subject of the offer. A sale is consummated between the buyer and seller of the matched offer to buy and offer to sell. Consummation may include assessing the risk of fraud posed by the matched buyer and matched seller. Fees may be charged to the matched buyer, the matched seller, or both as insurance against fraud. Payment may be made by the buyer directly to the seller or to a host hosting the apparatus and method for conducting the transaction. Payment is forwarded to the seller by the host upon confirmation by the buyer that a product has been received in good order. An automated, or partially automated, dispute resolution process may resolve disputed transactions.
Owner:REVOLUTIONARY E COMMERCE SYST
Method and system for enabling anonymous communications between two or more interested parties
ActiveUS20130218983A1Maintaining anonymityData processing applicationsUnauthorised/fraudulent call preventionCommunications serverTelephony
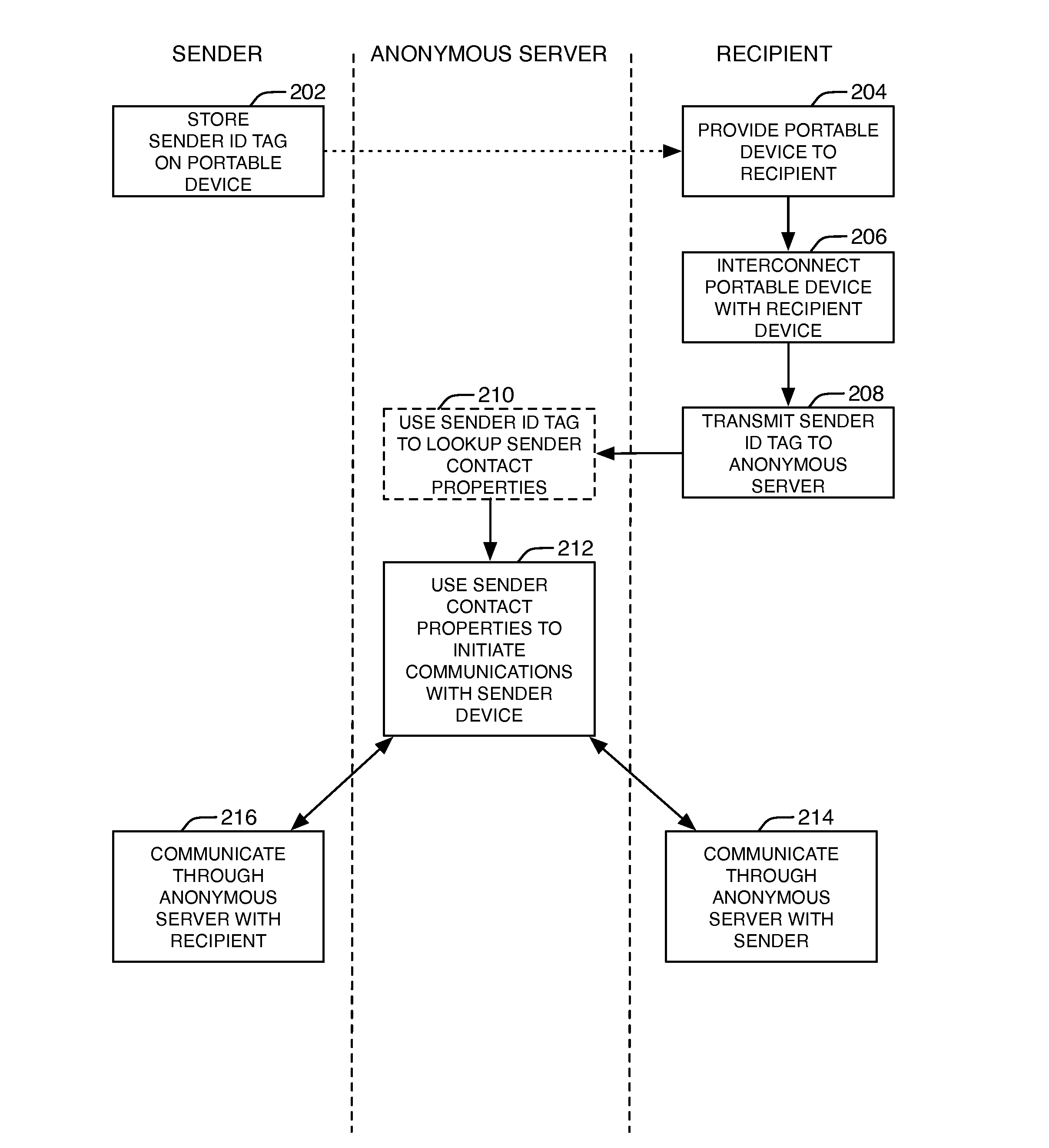
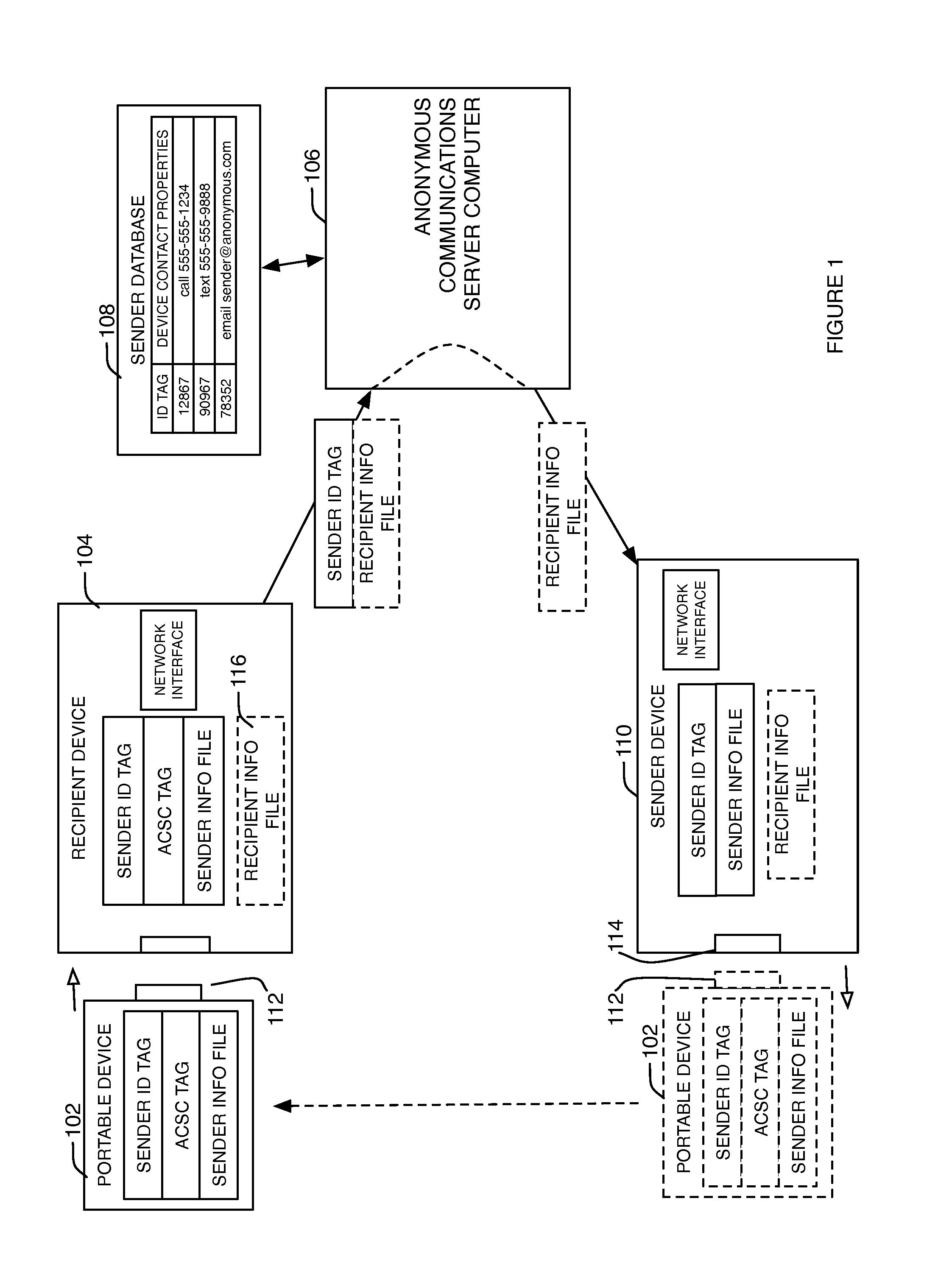
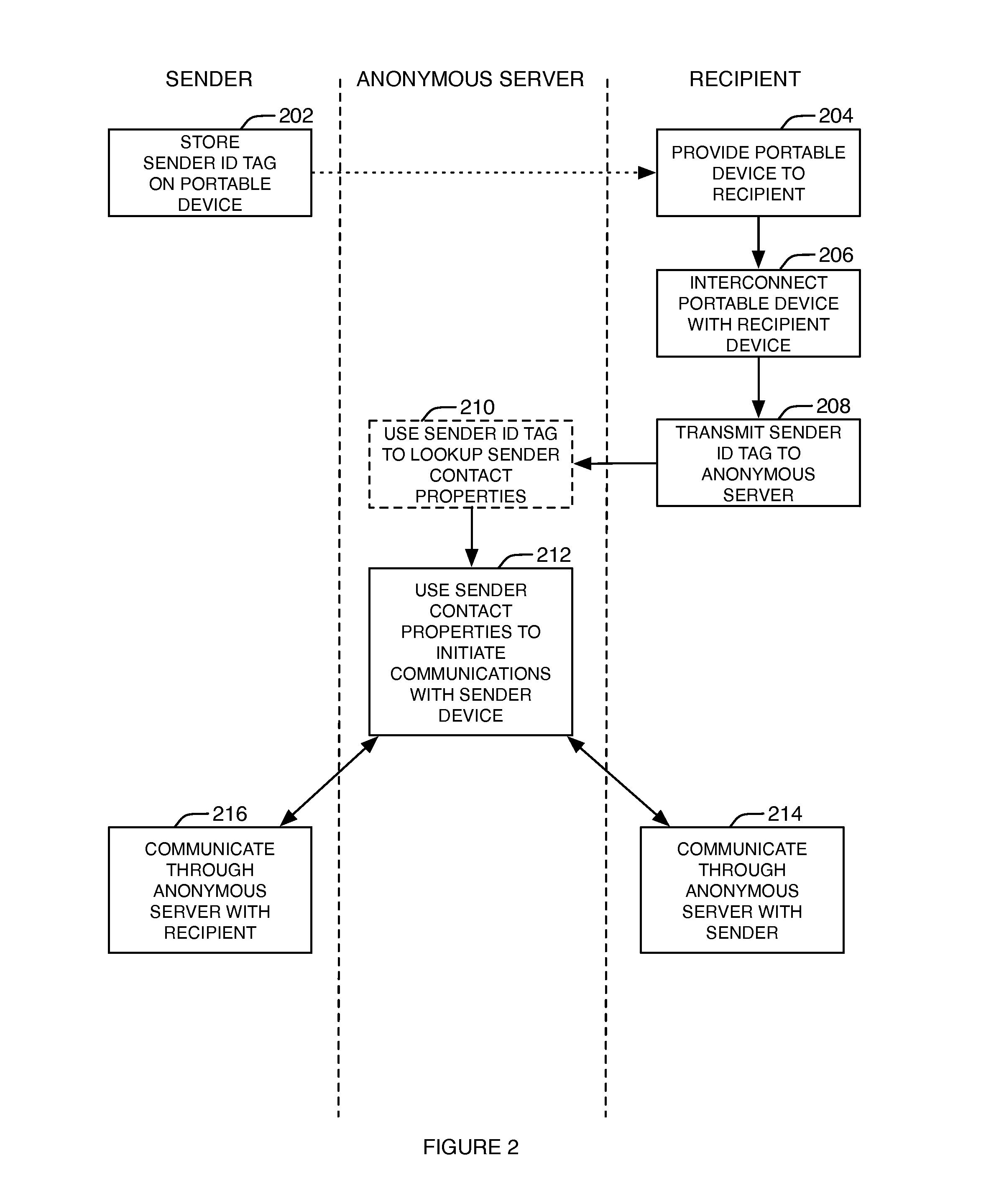
A method and system for communicating anonymously between two parties until such time that the parties may wish to reveal their identities to each other. This is accomplished by using a portable device that enables anonymous communications between a sender (operating a sender device such as a smartphone) and a recipient (operating a recipient device such as a smartphone) via an anonymous communications server computer.
Owner:RICHARD POSTREL
Method and system for dynamically obscuring addresses in IPv6
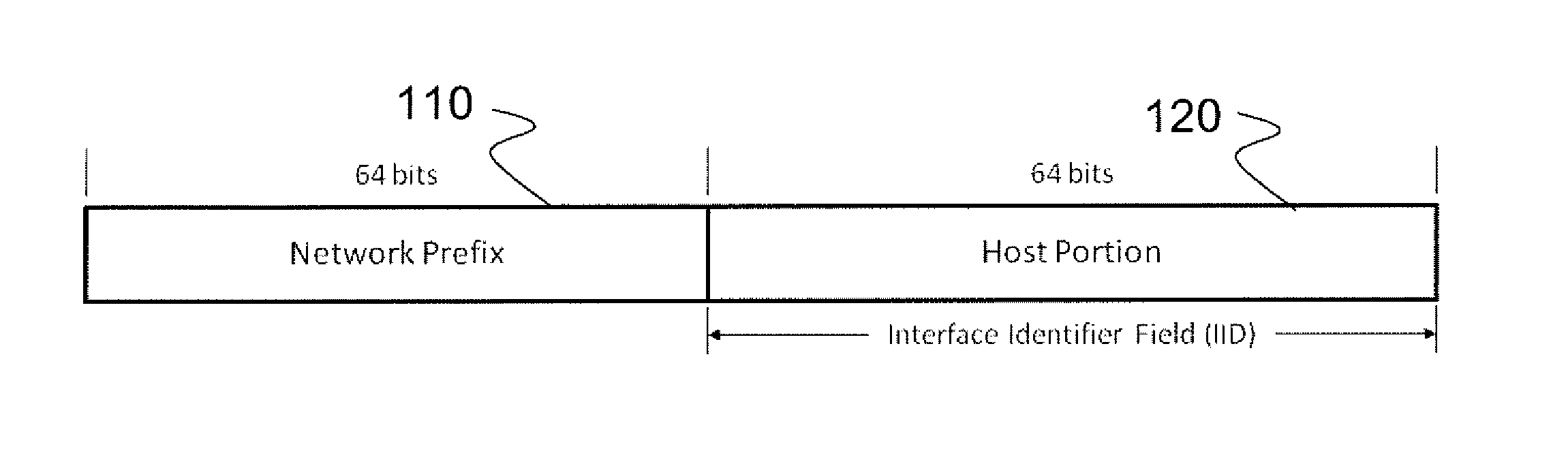
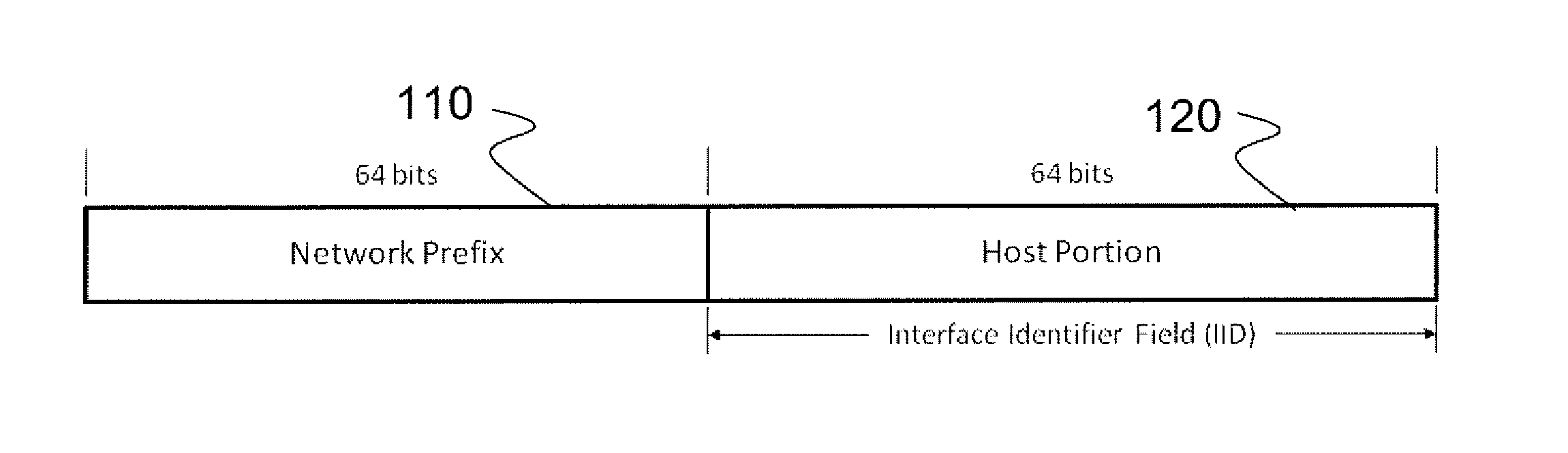
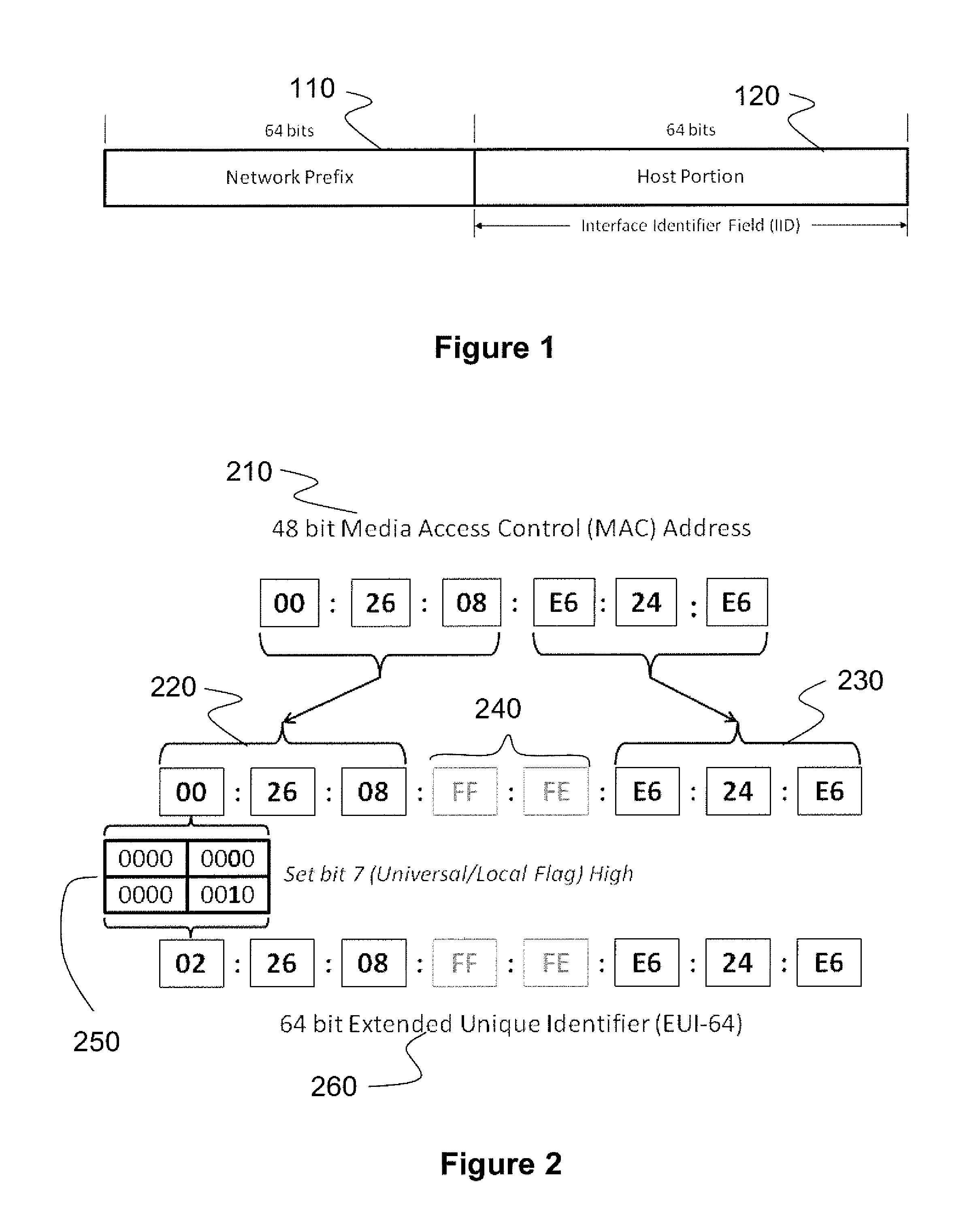
ActiveUS9461875B2Reduce usageMaintaining anonymityMultiple keys/algorithms usageData switching networksAuto-configurationManagement unit
The invention dynamically obscures network and transport layer addresses of packets to achieve anonymity, including authentication privacy, as well as protection against tracking and traffic correlation and certain classes of network attacks by combining both intrusion protection with anonymity, avoiding the use of a separate management unit outside the host for distribution of obscured addresses. The invention enables a host to automatically configure obscured addresses and determine the obscured address of the intended recipient without outside involvement, computing addresses based on a set of parameters, and to operate without re-authentication whenever an address changes. The invention enables encryption of the packet payload to prevent traffic correlation. The technology of the invention can be implemented embedded on a host device or as a connected gateway device and requires negligible configuration and is therefore transparent to hosts.
Owner:VIRGINIA TECH INTPROP INC
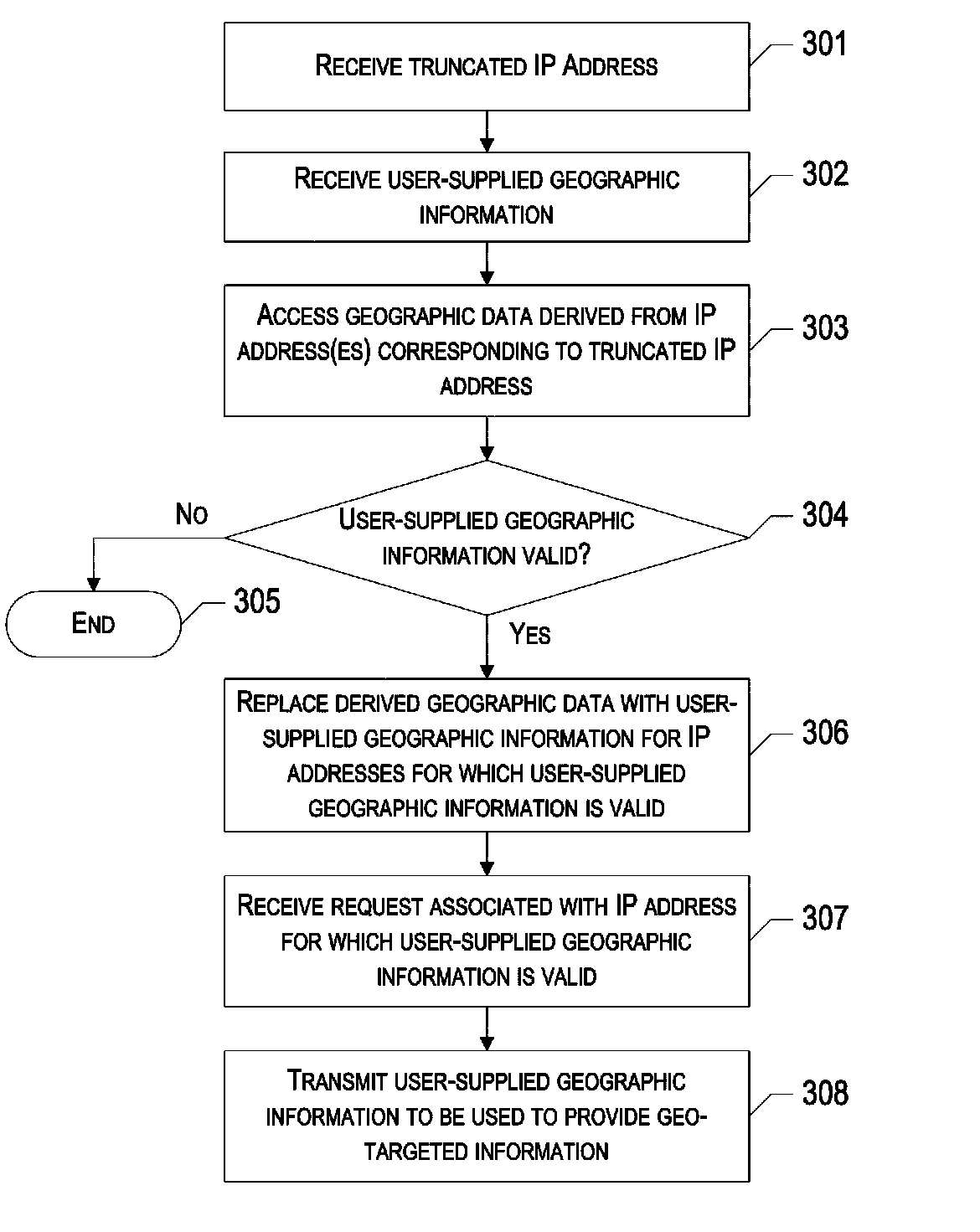
Method, computer program product and electronic device for hyper-local geo-targeting
ActiveUS20110113116A1Maintaining anonymityMaintain privacyDigital data processing detailsMultiple digital computer combinationsGeotargetingIp address
A method, computer program product and electronic device are provided for providing hyper-local geo-targeting based on validated, user-supplied geographic information, wherein the user's anonymity may be maintained. In particular, user-supplied geographic information may be collected in association with a truncated IP address. Once collected, the user-supplied information may be validated using geographic data previously derived from one or more complete IP addresses corresponding to the received truncated IP address. The derived geographic data may have been derived using a system that maps the routing infrastructure of the Internet in order to determine where endpoints on the Internet are located. The validated, user-supplied geographic information, which may be more specific than the derived geographic data, may then be used to provide more granular and accurate geo-targeting, all the while maintaining the privacy of the individual users.
Owner:DIGITAL ENVOY
Data management method and registration method for an anonymous data sharing system, as well as data manager and anonymous data sharing system
ActiveUS20190213356A1Maintaining anonymityKey distribution for secure communicationMultiple keys/algorithms usageEntity identifierData source
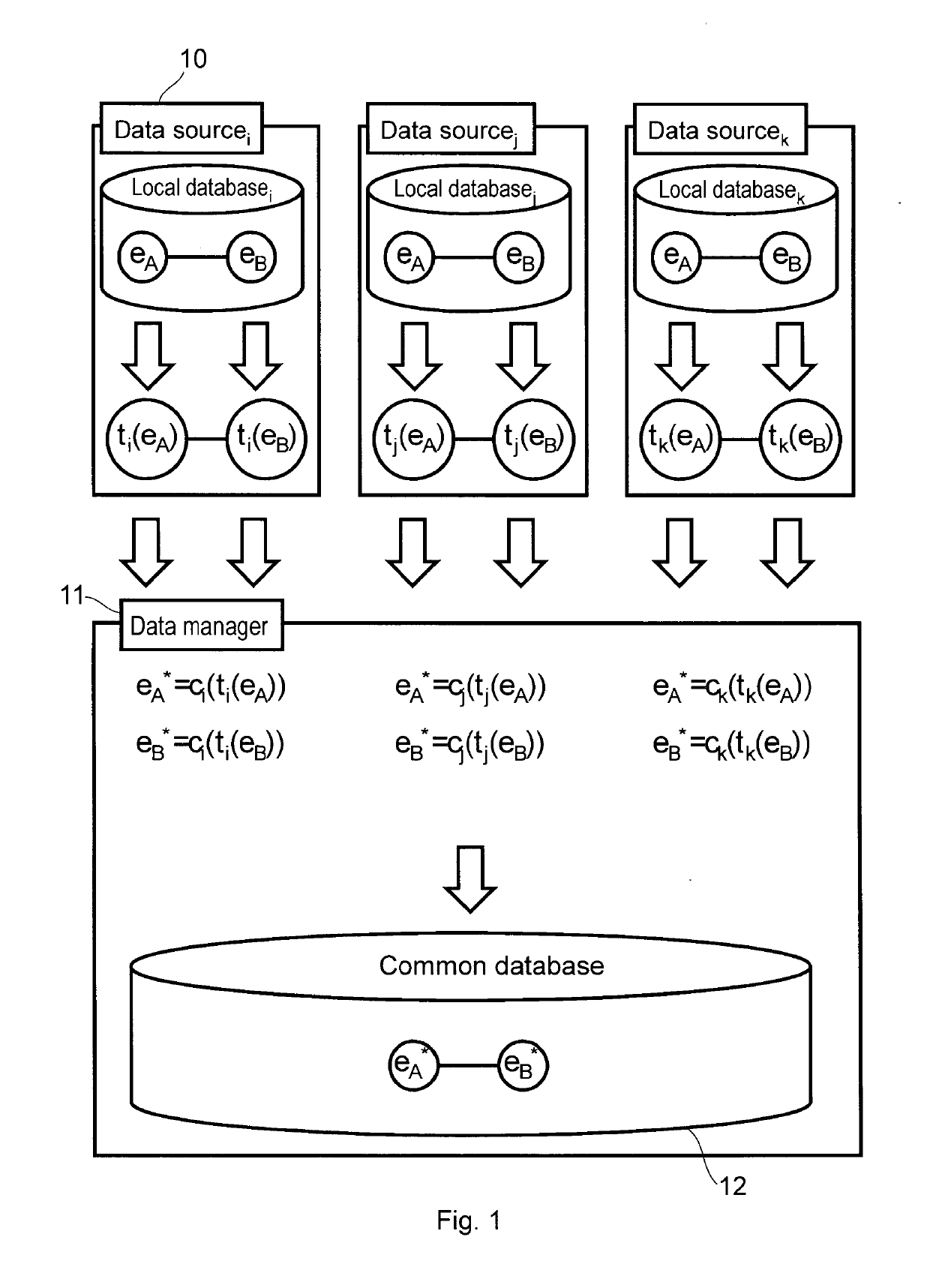
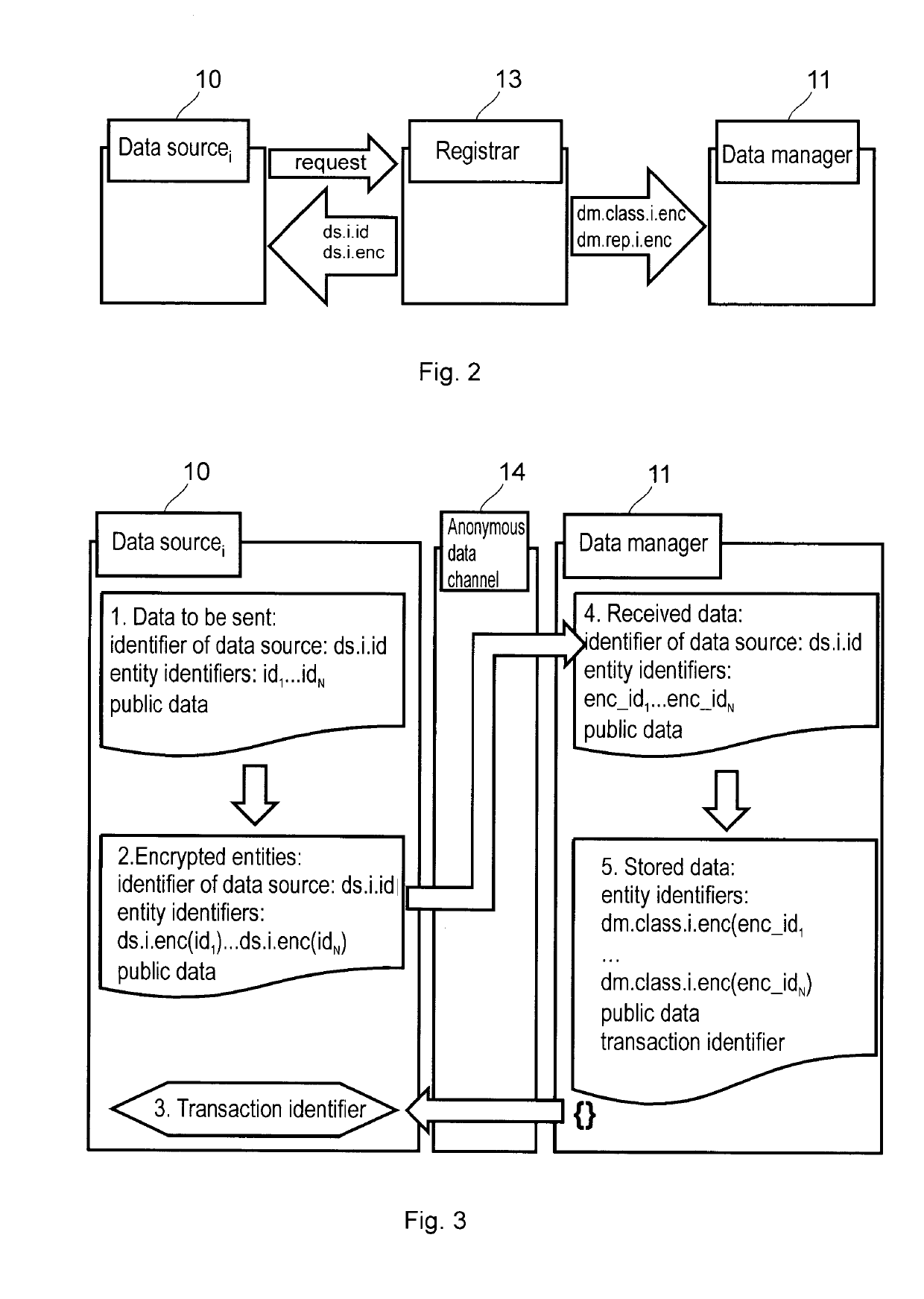
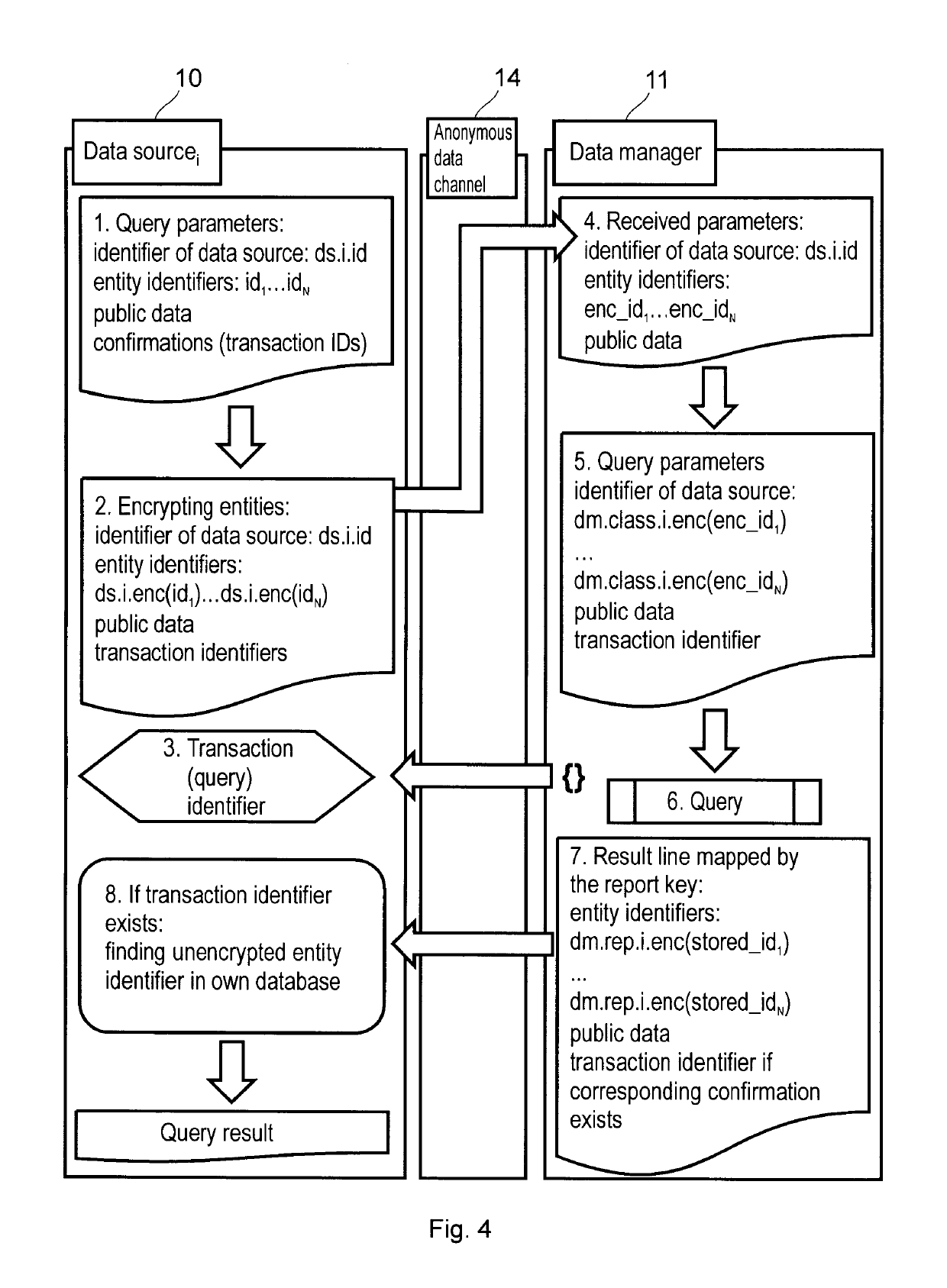
The invention is a data management method for an anonymous data sharing system, comprising the steps of receiving a data supply from a data source (10), the data supply comprising an anonymous data source identifier, an entity identifier encrypted with the private encryption key of the data source (10), and data associated with the entity. The method further comprises mapping the encrypted entity identifier to a common anonymous entity identifier by applying a classifier key associated with the data source identifier in such a manner that for every entity identifier the following applies: by encrypting said entity identifier with the private encryption key of any data source (10) and by mapping it using the classifier key associated with the identifier of the data source, the same common anonymous entity identifier is obtained, wherein the data associated with the entity are stored in a database (12) in a manner that said data are assigned to the common anonymous identifier. The invention also relates to a registration method, to a data manager, and to an anonymous data sharing system comprising same.
Owner:XTENDR ZRT
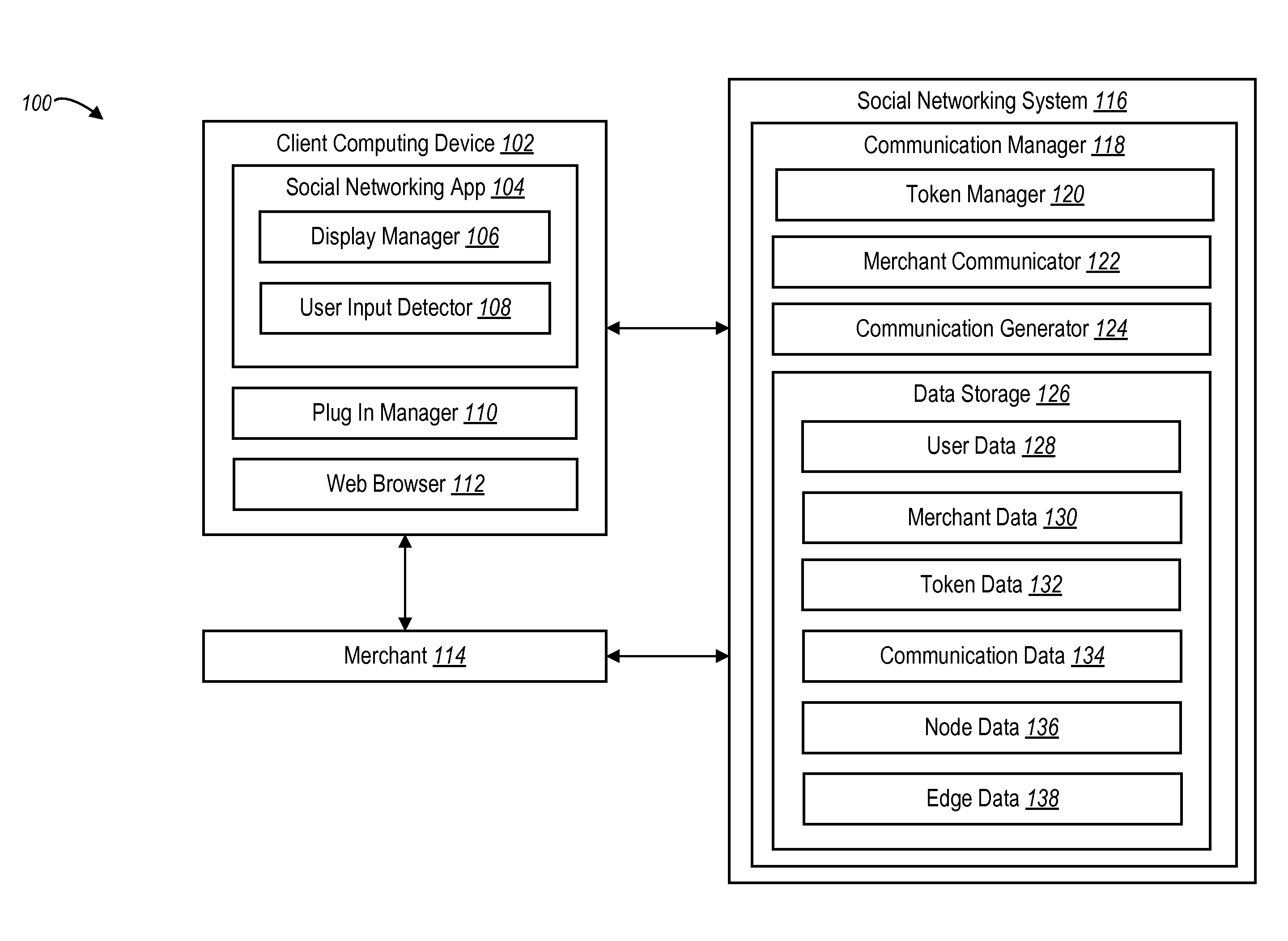
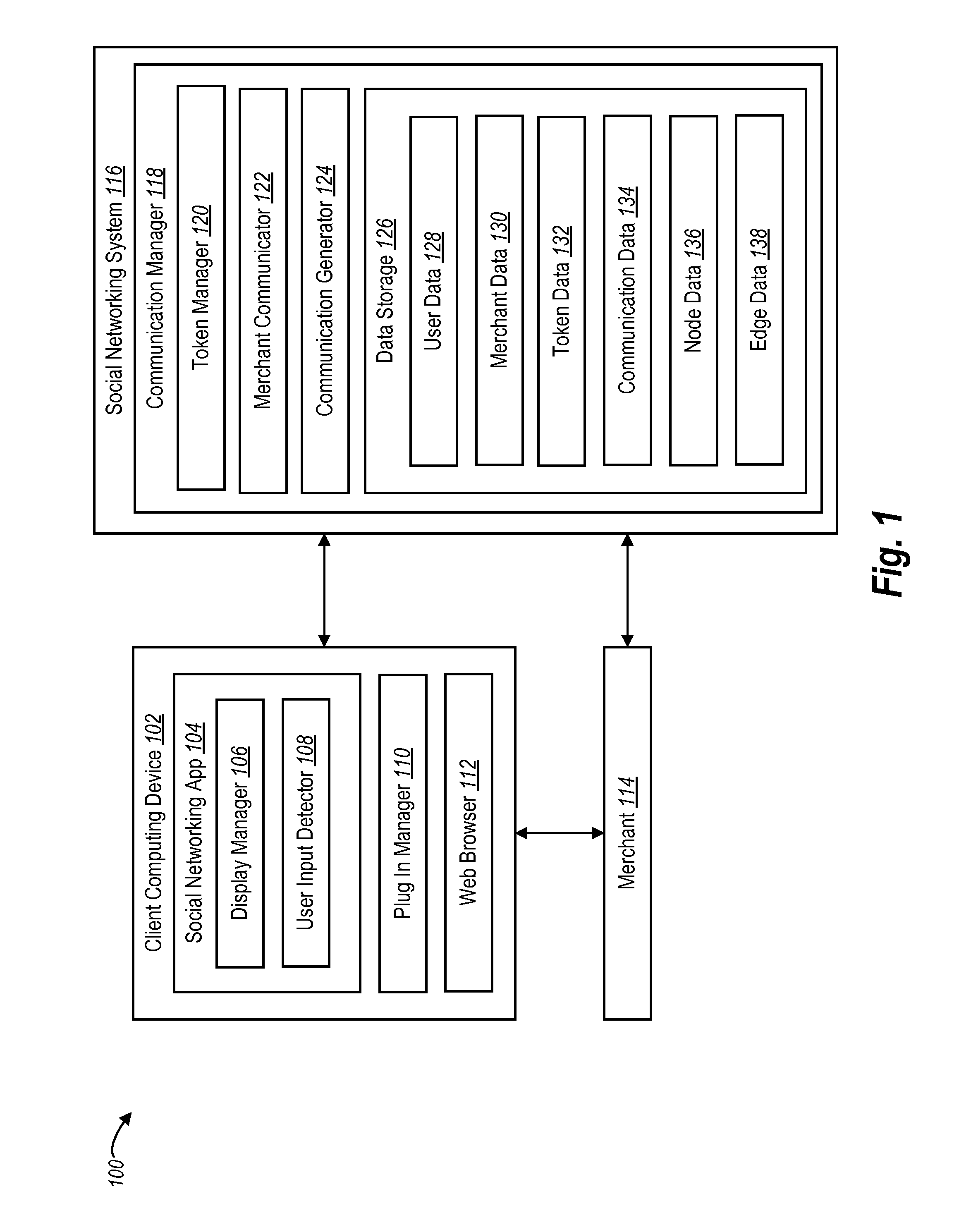
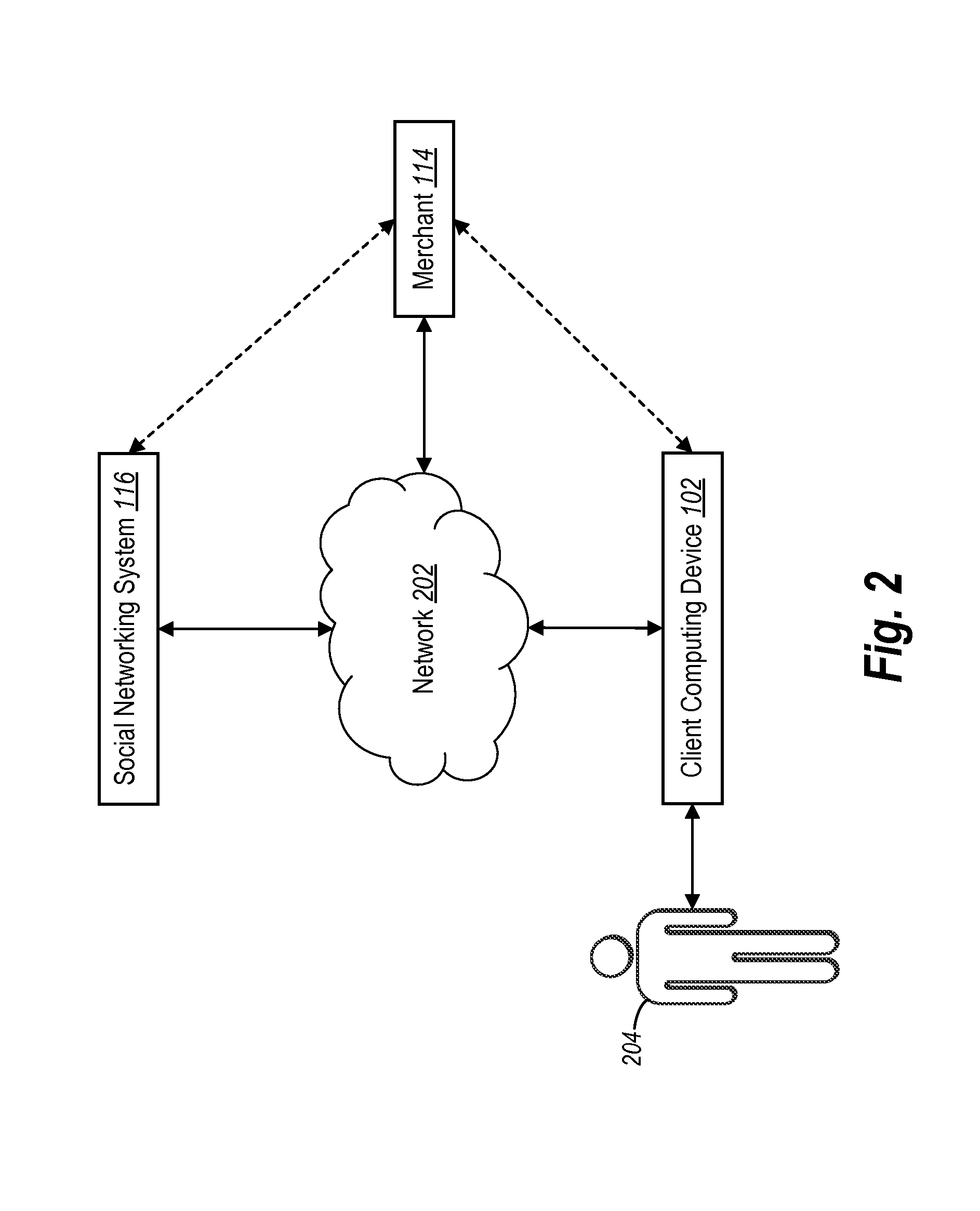
User communications with a merchant through a social networking system
ActiveUS20160283936A1Improve identityMaintaining anonymityCryptography processingBuying/selling/leasing transactionsSocial webMultimedia
The present disclosure is directed toward systems and methods for facilitating anonymous communications between a user and a merchant via a social networking system, wherein the user's identifying information is obfuscated from the merchant.
Owner:META PLATFORMS INC
Method, computer program product and electronic device for hyper-local geo-targeting
ActiveUS8443107B2Maintaining anonymityMaintain privacyDigital data processing detailsMultiple digital computer combinationsGeotargetingIp address
A method, computer program product and electronic device are provided for providing hyper-local geo-targeting based on validated, user-supplied geographic information, wherein the user's anonymity may be maintained. In particular, user-supplied geographic information may be collected in association with a truncated IP address. Once collected, the user-supplied information may be validated using geographic data previously derived from one or more complete IP addresses corresponding to the received truncated IP address. The derived geographic data may have been derived using a system that maps the routing infrastructure of the Internet in order to determine where endpoints on the Internet are located. The validated, user-supplied geographic information, which may be more specific than the derived geographic data, may then be used to provide more granular and accurate geo-targeting, all the while maintaining the privacy of the individual users.
Owner:DIGITAL ENVOY
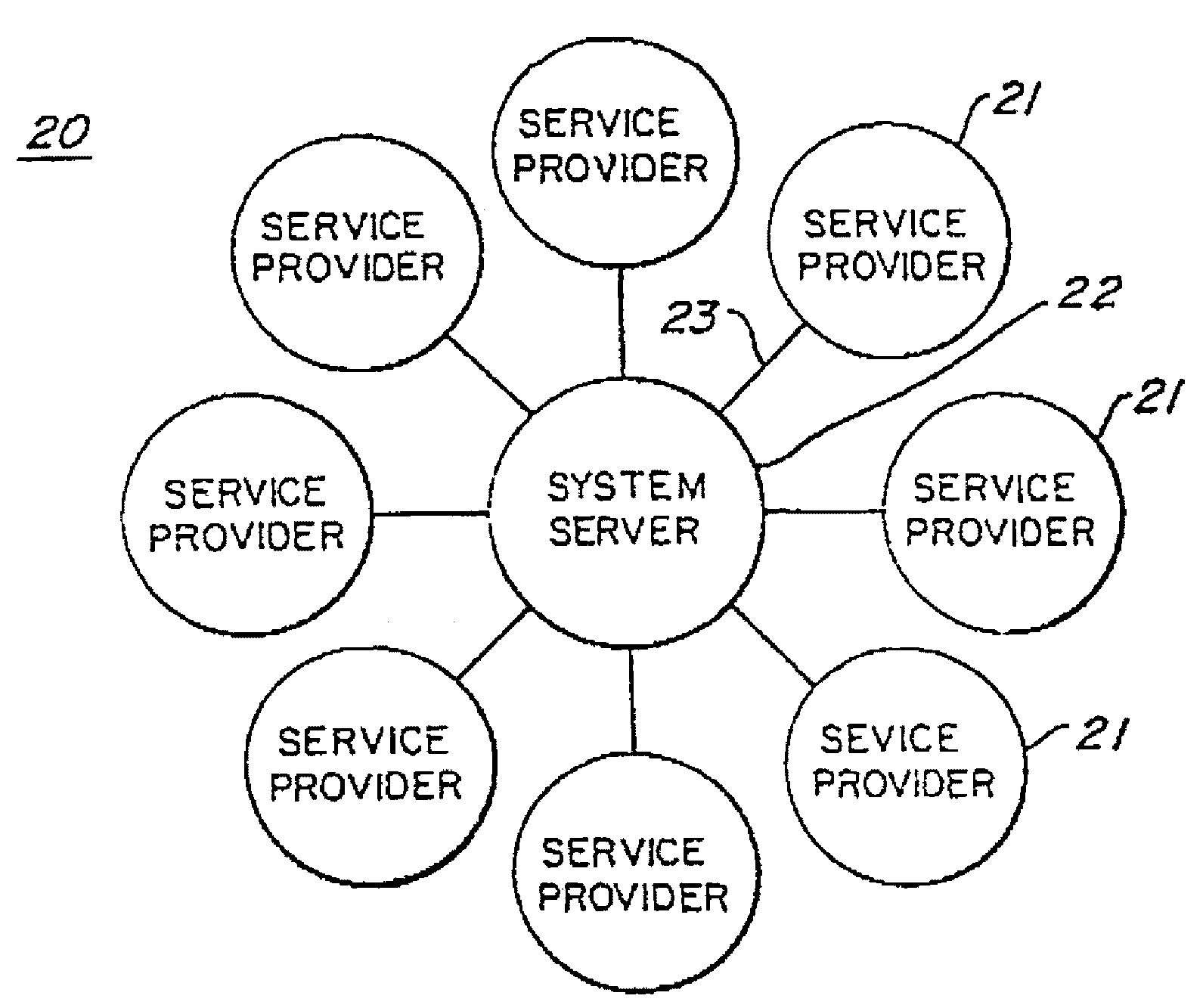
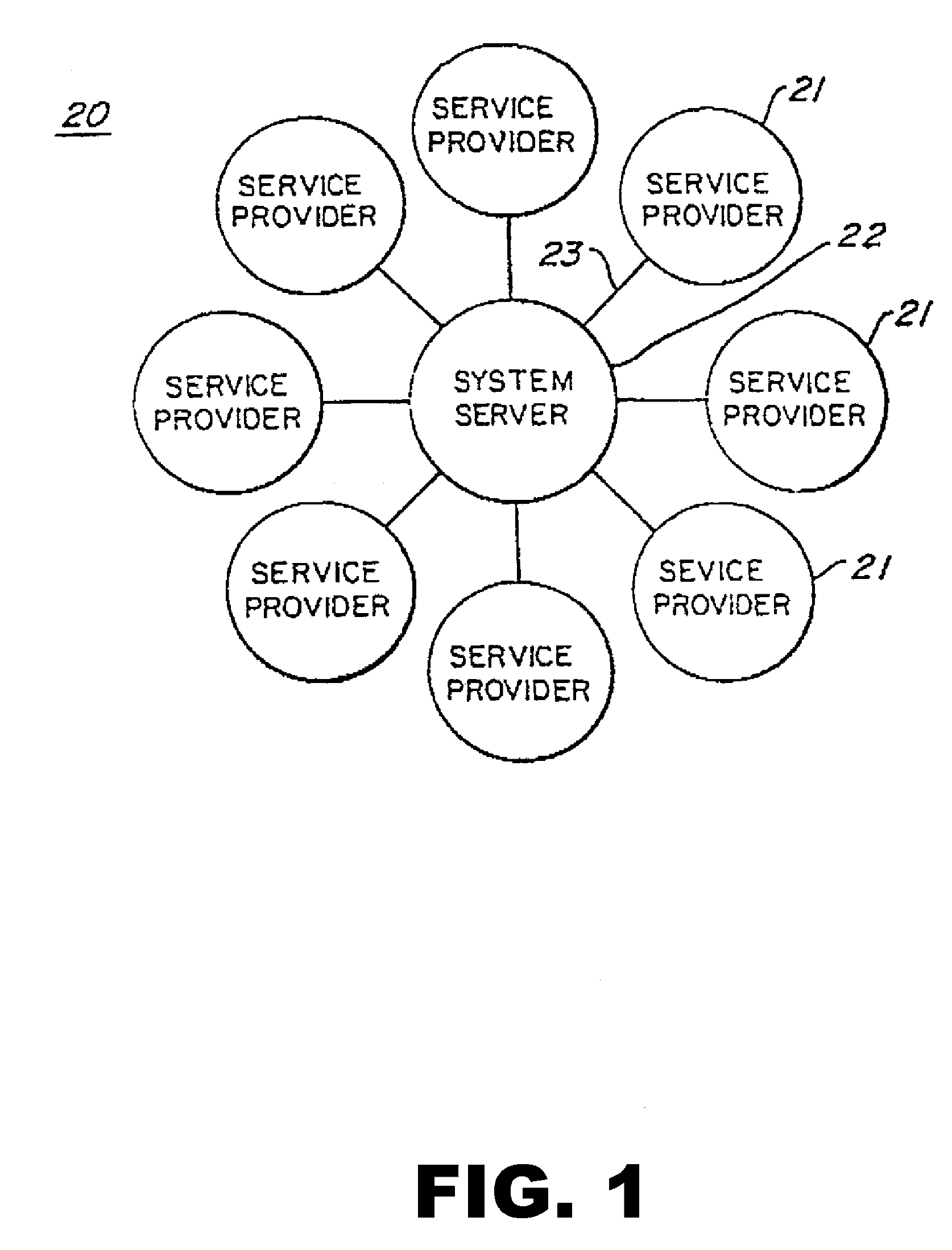
Apparatus and method for simulating artificial intelligence over computer networks
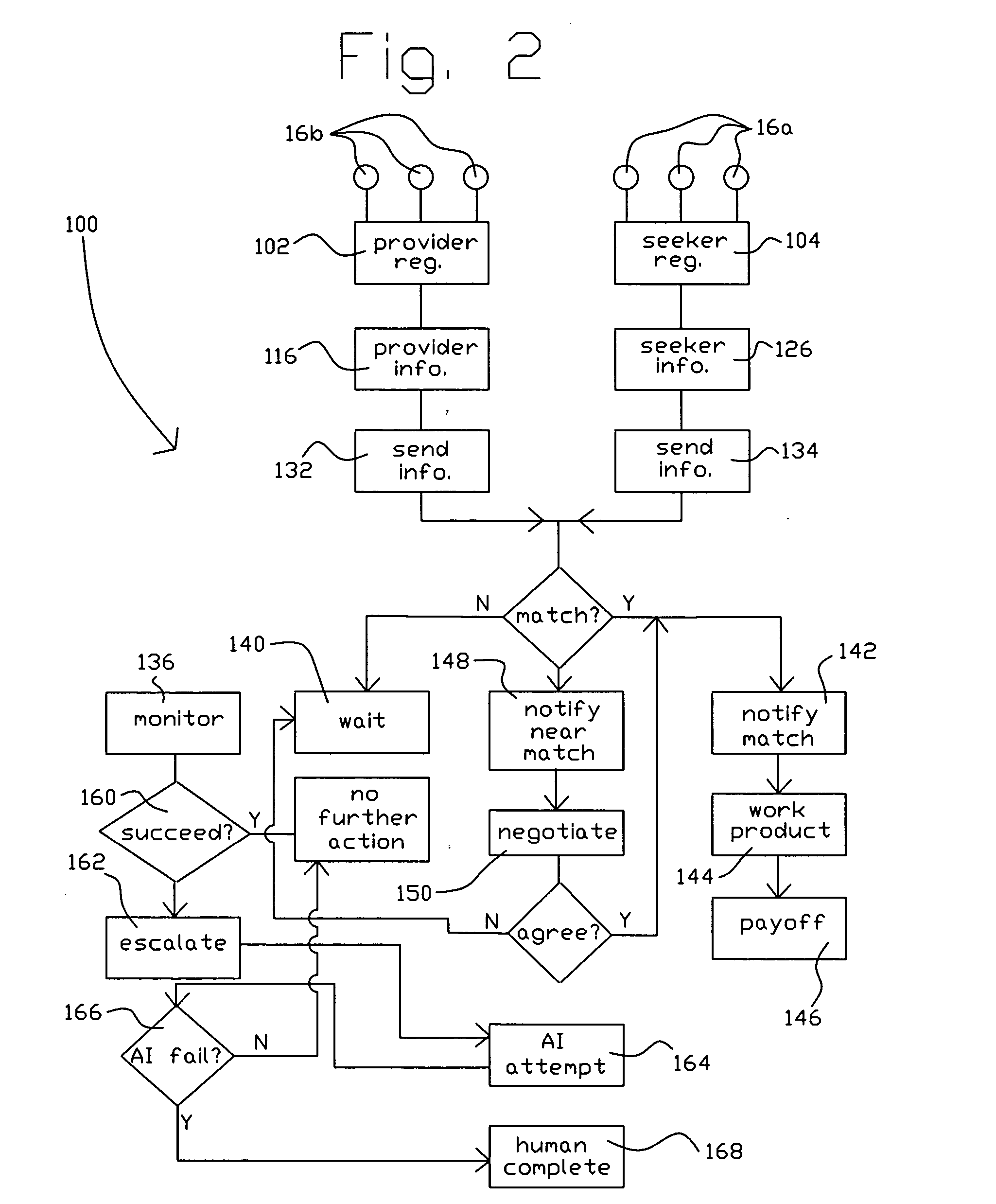
An Internet based simulated artificial intelligence system (10) and associated method (100) for brokering expertise, services, information, and the like by remote communication such as over the Internet (12). Seekers (16a) and providers (16b) register personal information and information about services sought and available, respectively. A brokering computer (18) matches information obtained in registration operations (106, 118, 126). A matching operation (138) results in either no match, an exact match or a near match. In the case of a near match, a negotiation operation (50) is initiated. It either the successful culmination of the negotiation operation (50) or in the case of an exact match, the negotiated service is rendered in a provider sends work product operation (144) and monetary considerations are accomplished in a payoff operation (146).
Owner:BLUE OAK MOUNTAIN TECH
Computer Method and Apparatus Providing Brokered Privacy of User Data During Searches
InactiveUS20100132044A1Maintaining anonymityDigital data processing detailsAnalogue secracy/subscription systemsInternet privacyAnonymity
Computer method and apparatus brokers and provides user data in a computer network of users. The invention system stores user data of the users. A search engine enables a searching user to query the stored user data and maintain anonymity of the users. The invention system brokers the query / search results. Each user whose stored user data matches the query maintains stewardship or control over the exposure of her / his user data. An output unit displays to the searching user the matching user data as brokered through (approved and optionally edited by) the respective user.
Owner:IBM CORP
Method and system for dynamically obscuring addresses in ipv6
ActiveUS20130212249A1Reduce usageMaintaining anonymityMultiple keys/algorithms usageDigital computer detailsManagement unitTransport layer
The invention dynamically obscures network and transport layer addresses of packets to achieve anonymity, including authentication privacy, as well as protection against tracking and traffic correlation and certain classes of network attacks by combining both intrusion protection with anonymity, avoiding the use of a separate management unit outside the host for distribution of obscured addresses. The invention enables a host to automatically configure obscured addresses and determine the obscured address of the intended recipient without outside involvement, computing addresses based on a set of parameters, and to operate without re-authentication whenever an address changes. The invention enables encryption of the packet payload to prevent traffic correlation. The technology of the invention can be implemented embedded on a host device or as a connected gateway device and requires negligible configuration and is therefore transparent to hosts.
Owner:VIRGINIA TECH INTPROP INC
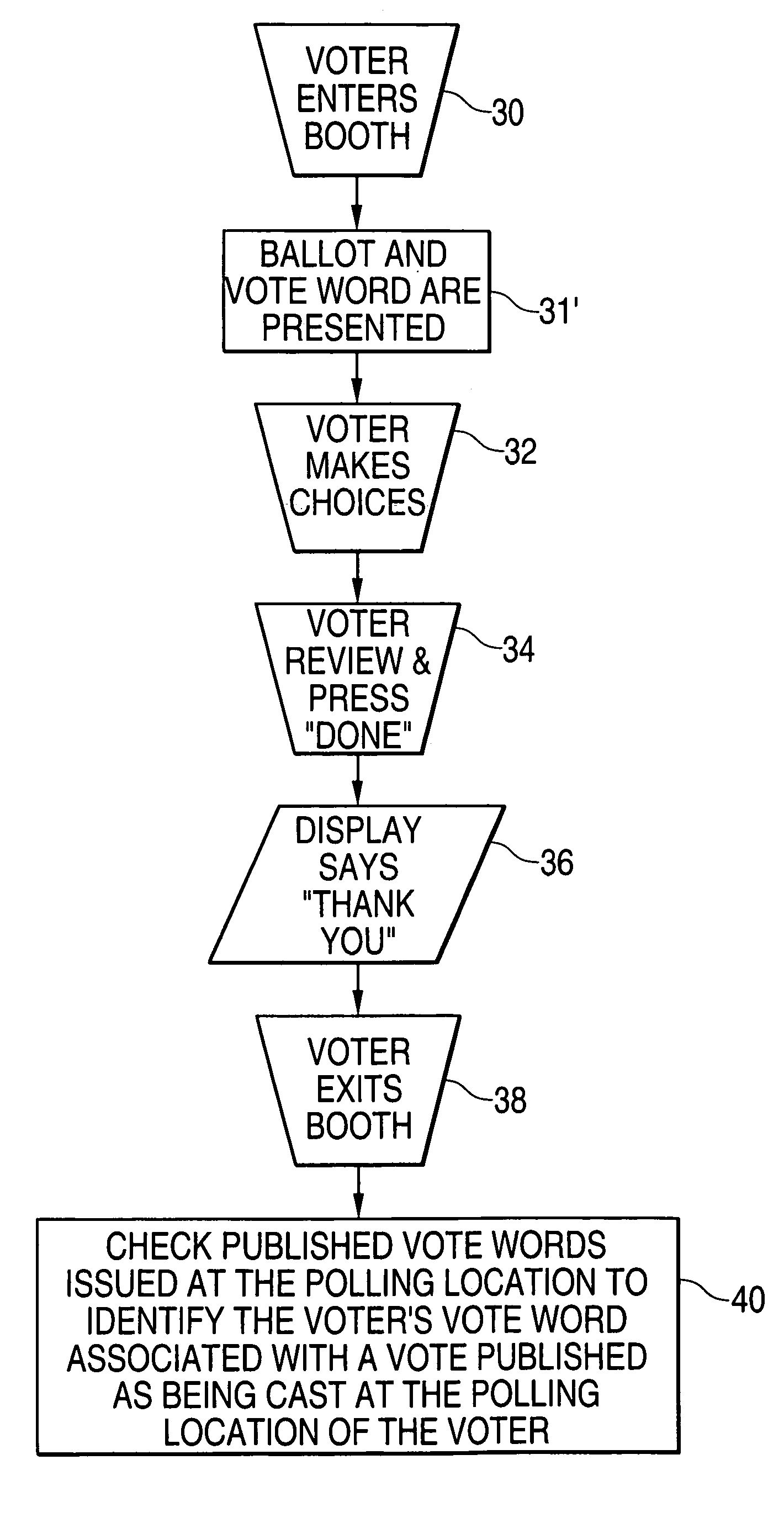
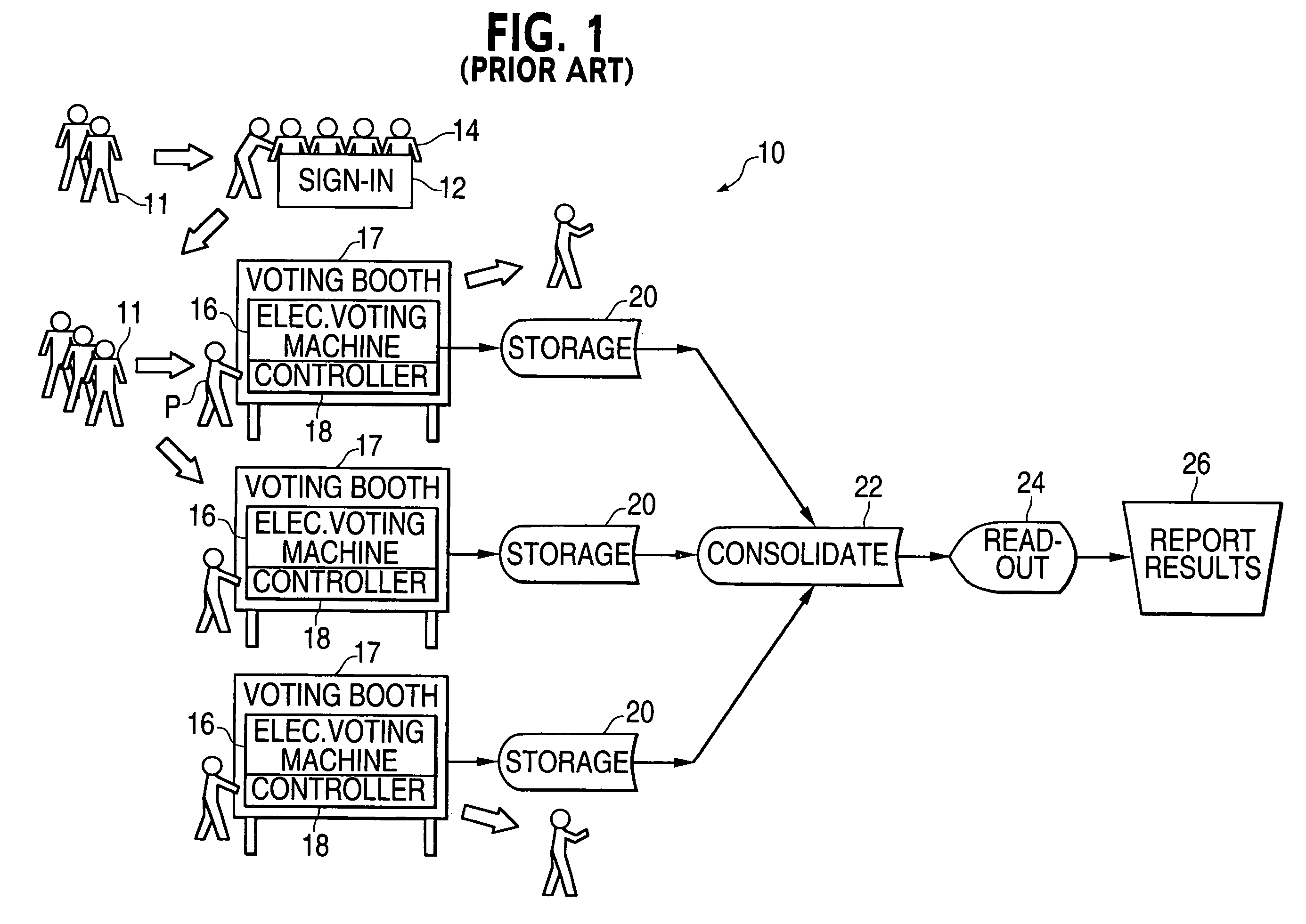
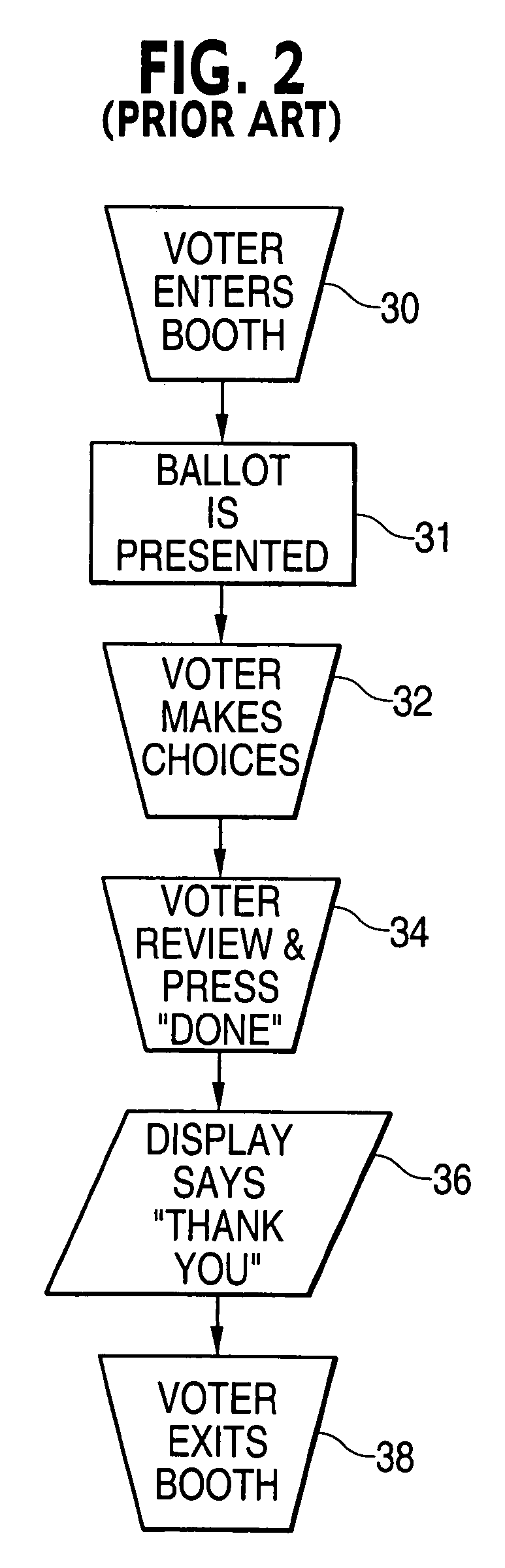
Electronic voting apparatus, system and method
ActiveUS6991161B2Maintaining anonymityLow-cost and simple approachVoting apparatusError detection/correctionComputer scienceHuman language
The invention is a method, system, programmed processor and a program stored on a storage medium used for providing voter confirmation that electronically cast ballots have been properly registered. A method for providing voter confirmation that electronically cast ballots have been properly registered in accordance with the invention includes generating a group of unique vote words which each comprise at least one word within at least one language understood by voters at at least one polling location; assigning individual voters at the at least one polling location at least one of the vote words chosen from the group of vote words which is unique to each of the voters, each of the assigned at least one vote word upon casting of voter's ballot being associated and recorded with the voter's ballot electronically cast by the voter at the at least one polling location; and publishing the vote words associated with the ballots which were cast at the at least one polling location whereby a voter who cast a ballot at the at least one polling location may check the published at least one vote word associated with the voter's votes at the at least one polling location as published to permit the voter to verify that the voter's votes were properly recorded.
Owner:PAZNIOKAS PAUL
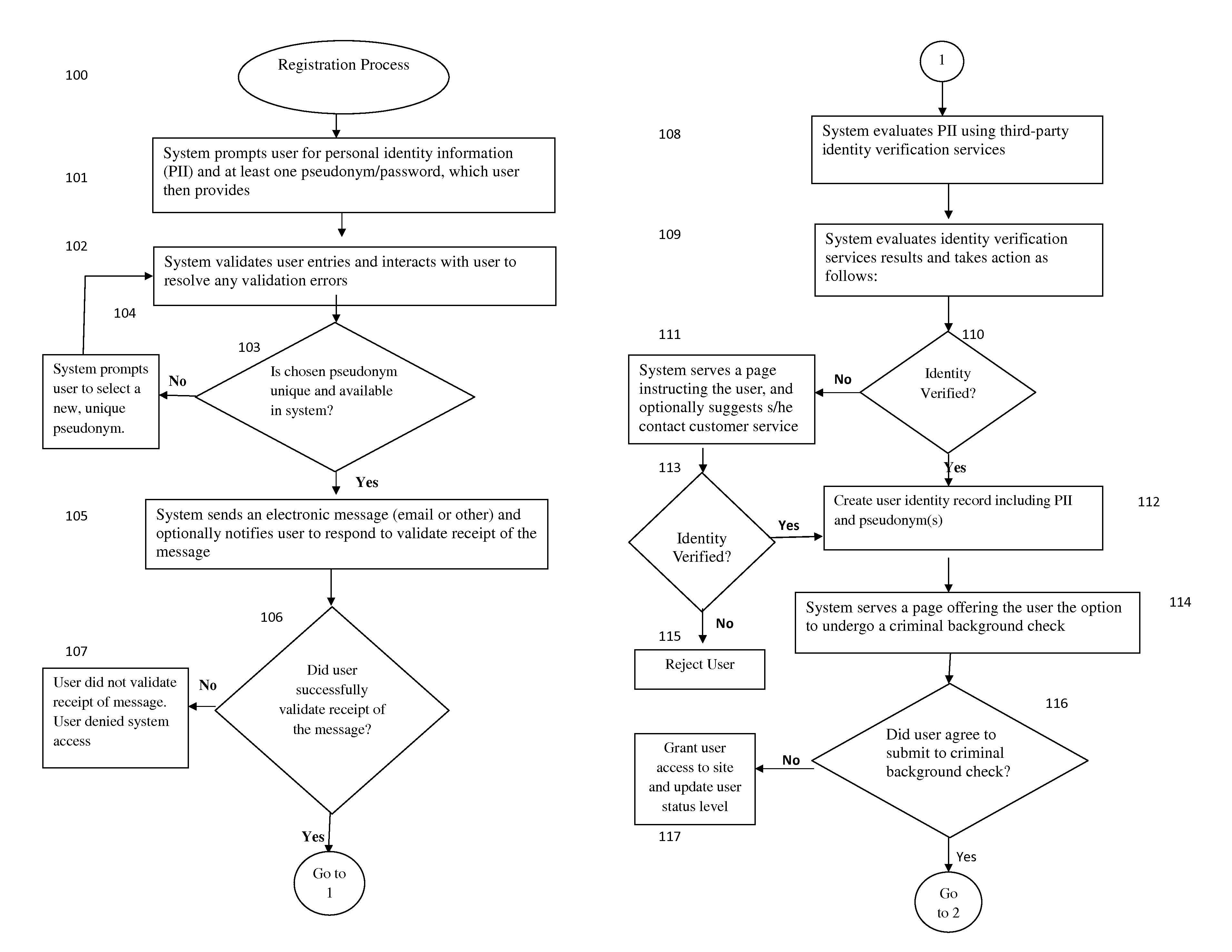
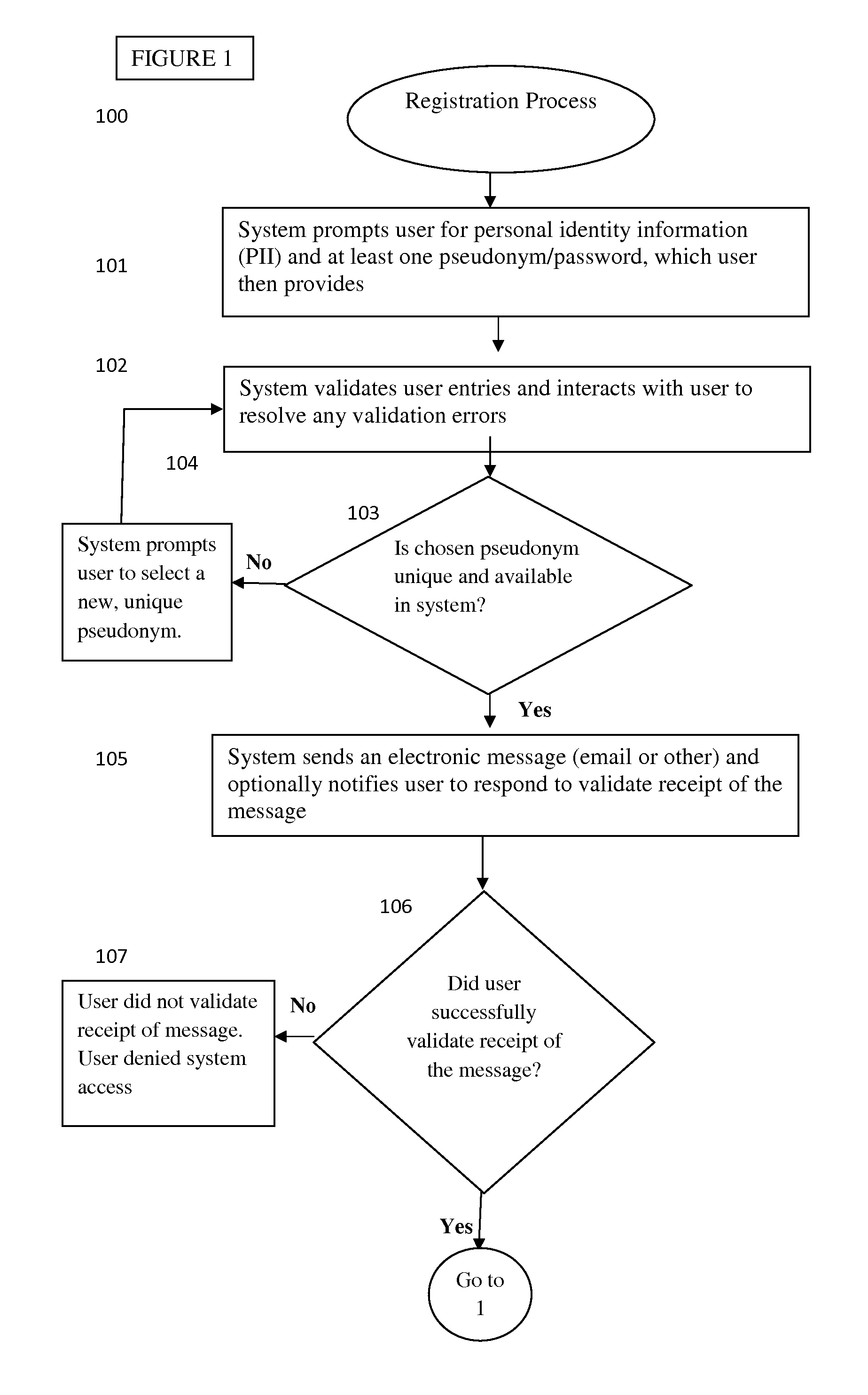
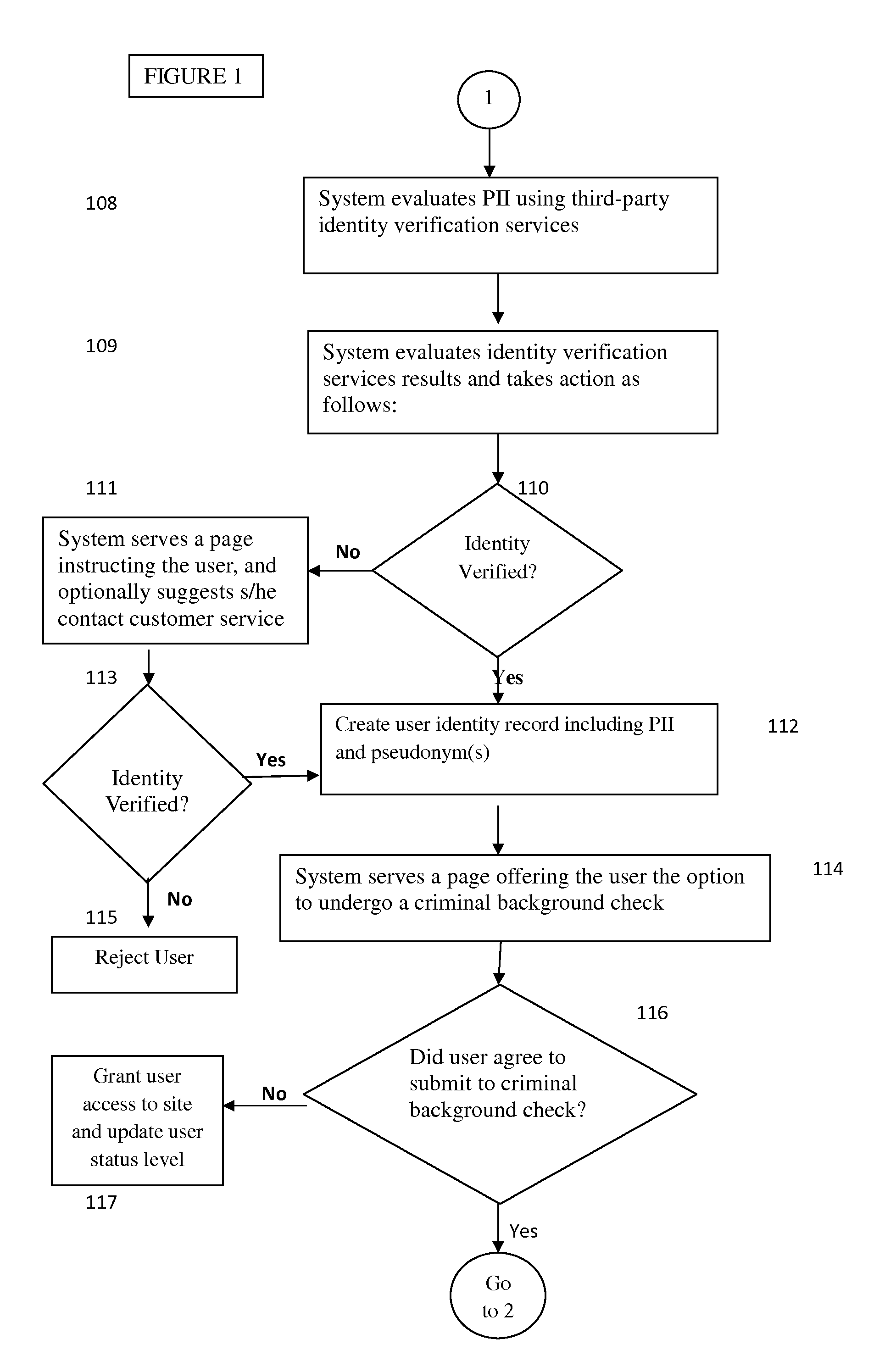
Methods and Systems for Establishing and Maintaining Verified Anonymity in Online Environments
InactiveUS20130091581A1Maintaining anonymityDigital data processing detailsAnalogue secracy/subscription systemsE-commerceAnonymity
In online communities and e-commerce sites that desire identity verification of individuals, a verified user is restricted to a single user identity, typically the user's real name. The use of one's real name in the context of online transactions and communication, however, is often not ideal, and in some instances, may present a safety risk for the individual. Further, specific transactions may require privacy. This invention provides methods and systems that allow an online user to establish and maintain verified anonymity. To accomplish this, a user's real identity is first verified, after which s / he establishes one or more pseudonyms each associated with the user's account, which the user may select to for use in the online environment, for example, an online social network.
Owner:PIRANI KARIM
Systems and methods for facilitating interactions between data subscribers and users sharing a health condition
InactiveUS20110093404A1Maintaining anonymityEnhanced interactionMedical communicationMedical data miningMedication regimenDrug delivery
A system is disclosed that enables peer-to-peer interactions between individual users sharing an interest in a health condition. The system provides the service in return for the user providing the system with data relating to lifestyle and health of the user, including those relating to diet, exercise, use of diagnostic and drug delivery devices, medication frequency and compliance with the medication regimen. The health profile data is used to generate parameters including a level of expertise of a user and a quality indicator for the data provided by the user. The database containing health profile data is accessible to a subscriber who queries the data anonymously to retrieve information.
Owner:LAWLESS GREGORY B +2
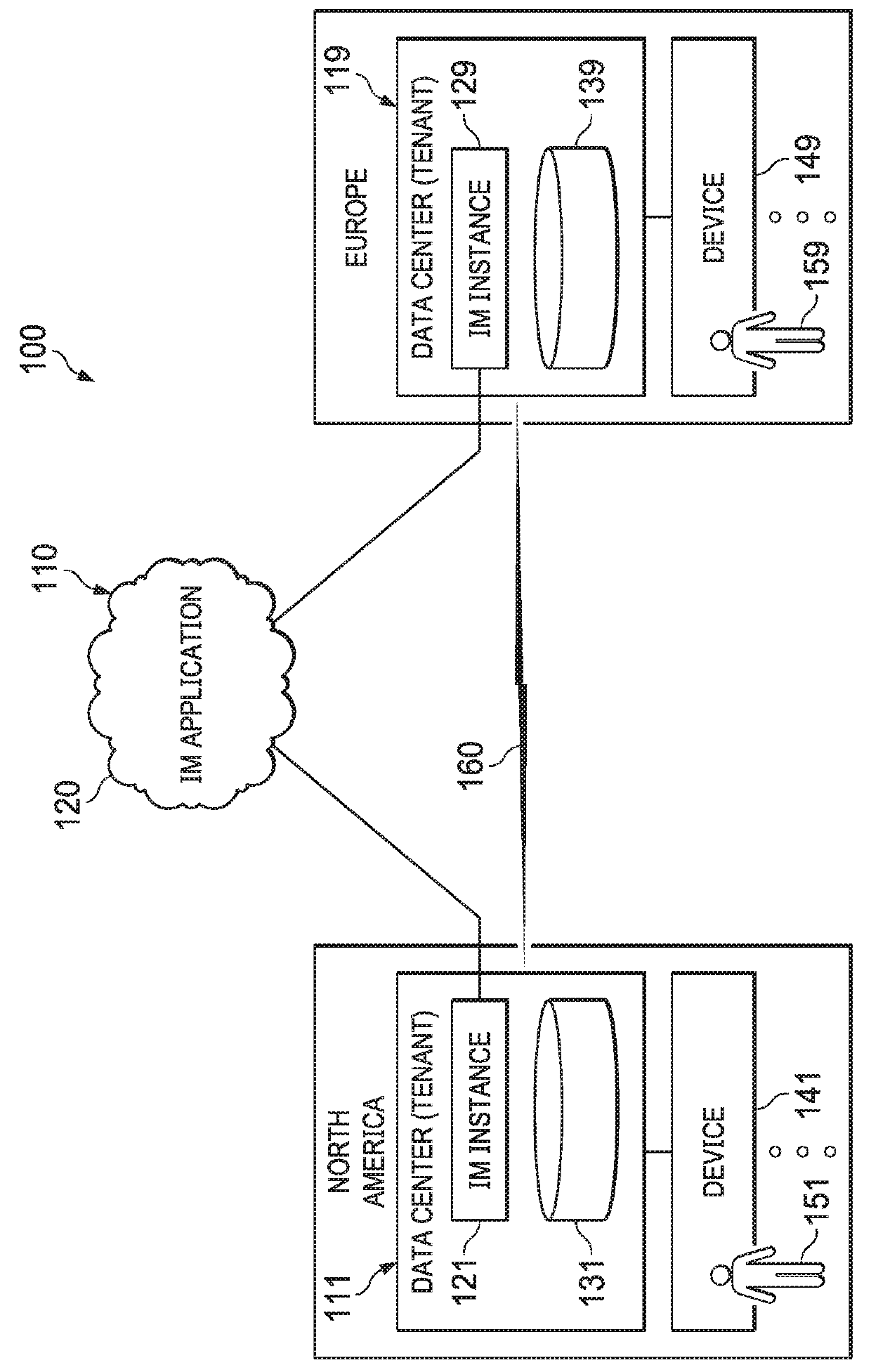
Systems and methods for multi-region data center connectivity
ActiveUS20180276414A1Maintain anonymityNot conduciveKey distribution for secure communicationDigital data information retrievalUser privacyData sharing
Disclosed is a multi-region data center connectivity solution for seamless integration between multi-region data center users and content. The solution supports user pinning (e.g., users and their personal content can be pinned to a particular geographical location / data center); protects personal content (e.g., personal content uploaded by a user is stored in that user's pinned geographical location / data center); and enables data sharing between multi-region data center users in a manner that is seamless and transparent to end users, while respecting user privacy, complying with data sovereignty requirements, and maintaining system anonymity.
Owner:OPEN TEXT SA ULC
Systems and methods for automatic call forwarding in a wireless mobile station
InactiveUS7450935B1Service conveniently and inexpensivelyReliable and more cost-efficientSpecial service for subscribersCommmunication supplementary servicesCall forwardingMobile station
Owner:AT&T MOBILITY II LLC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com