Patents
Literature
169 results about "Packet payload" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
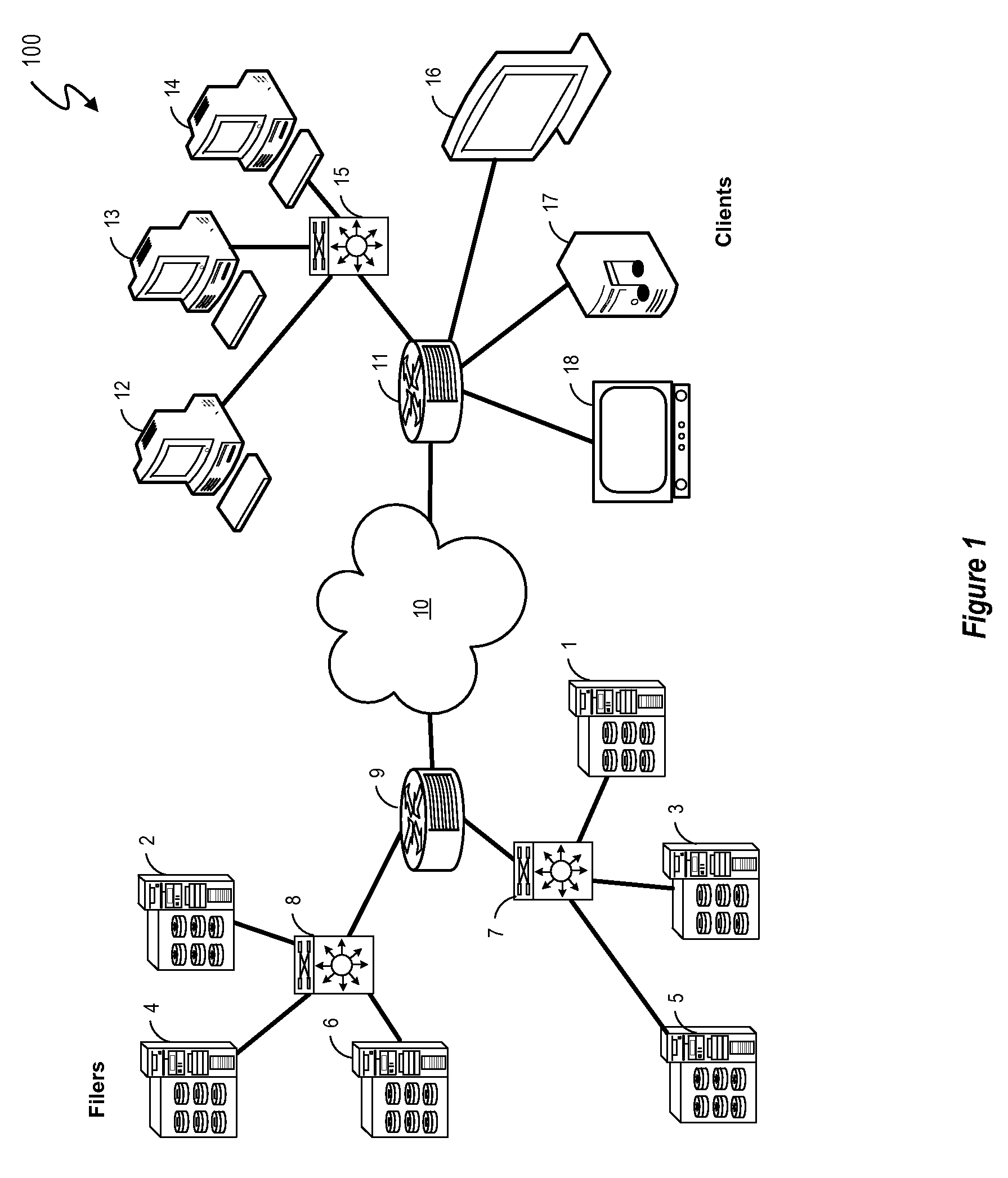
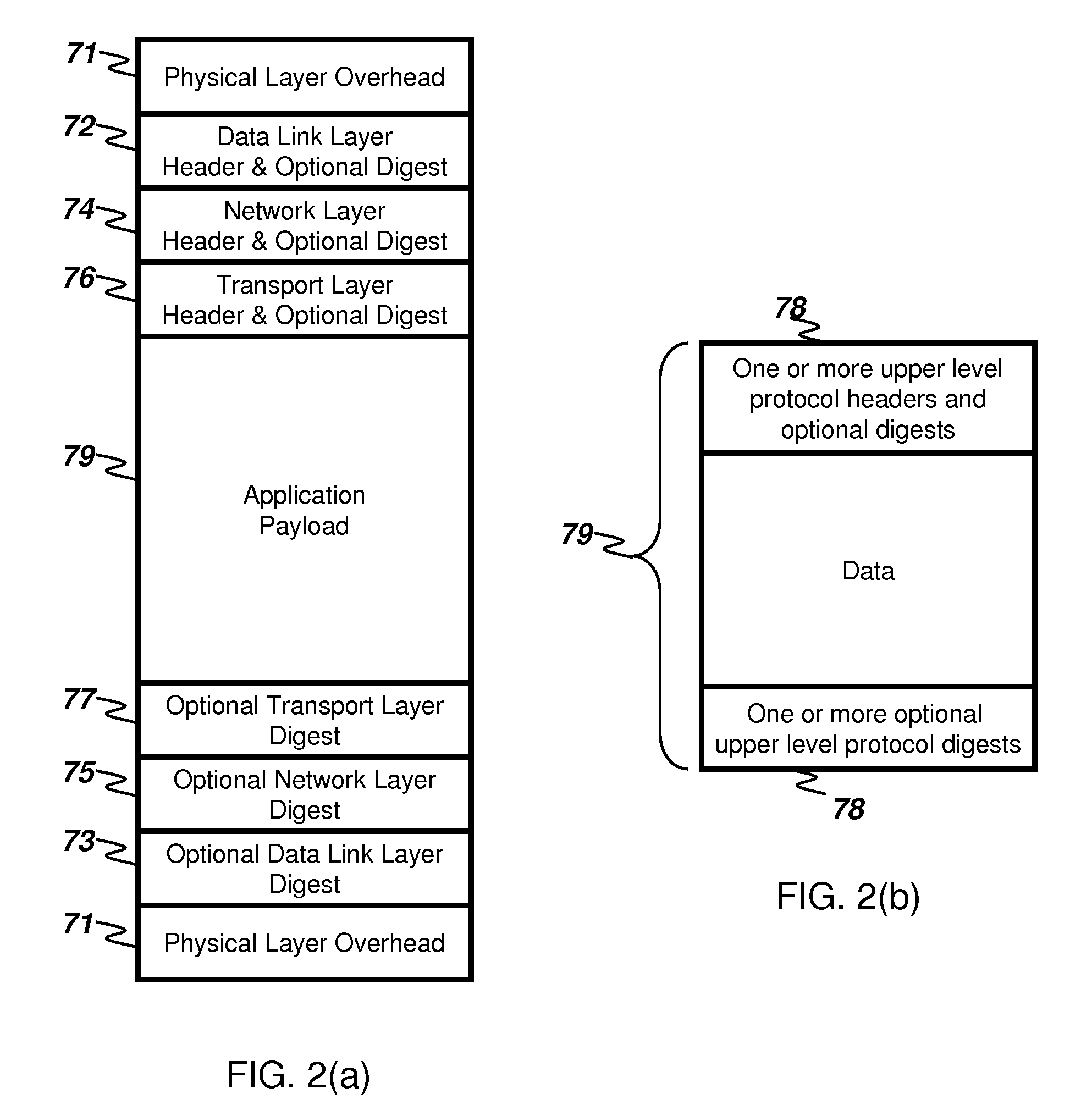
In computing, a payload is the carrying capacity of a packet or other transmission data unit.
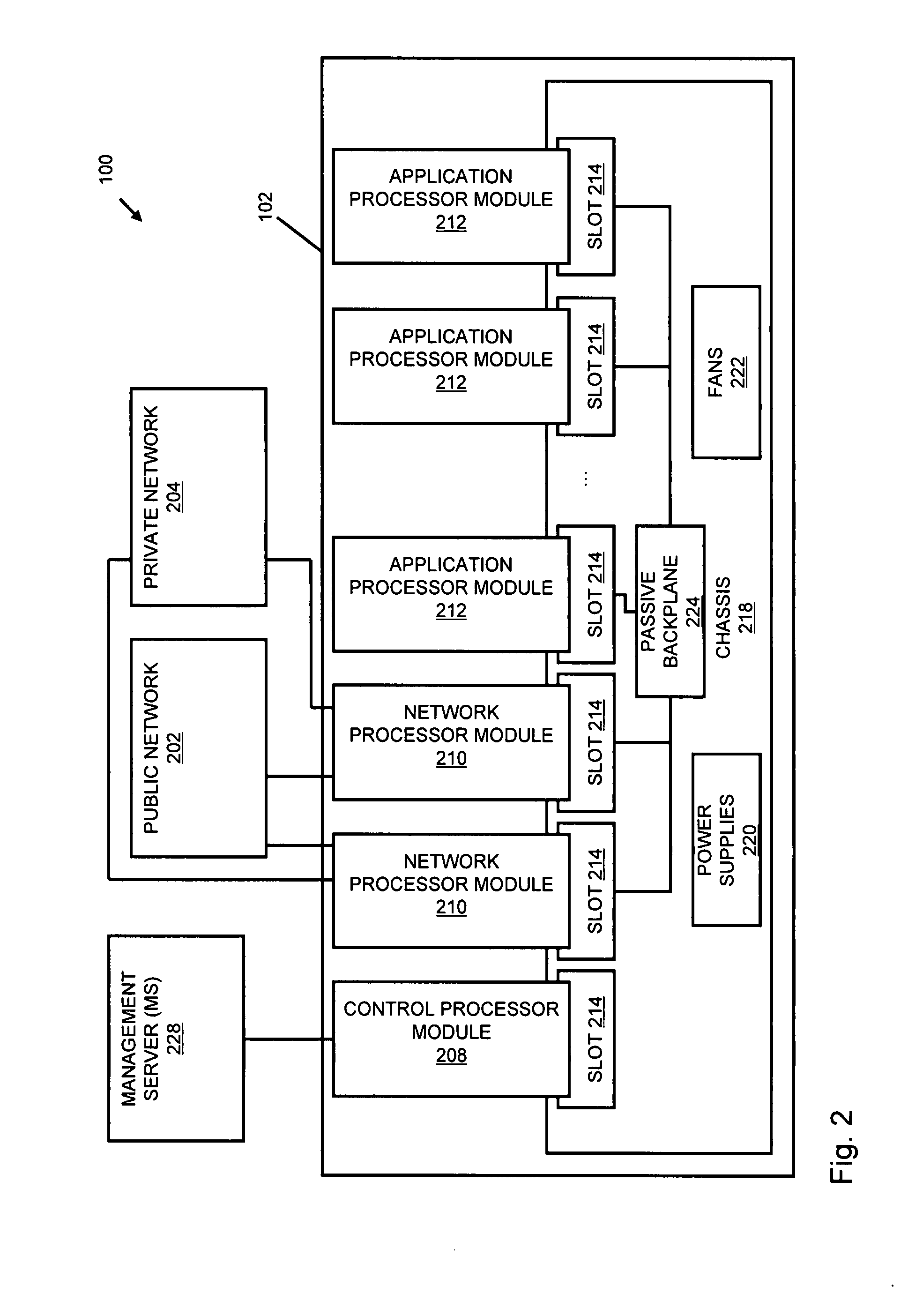
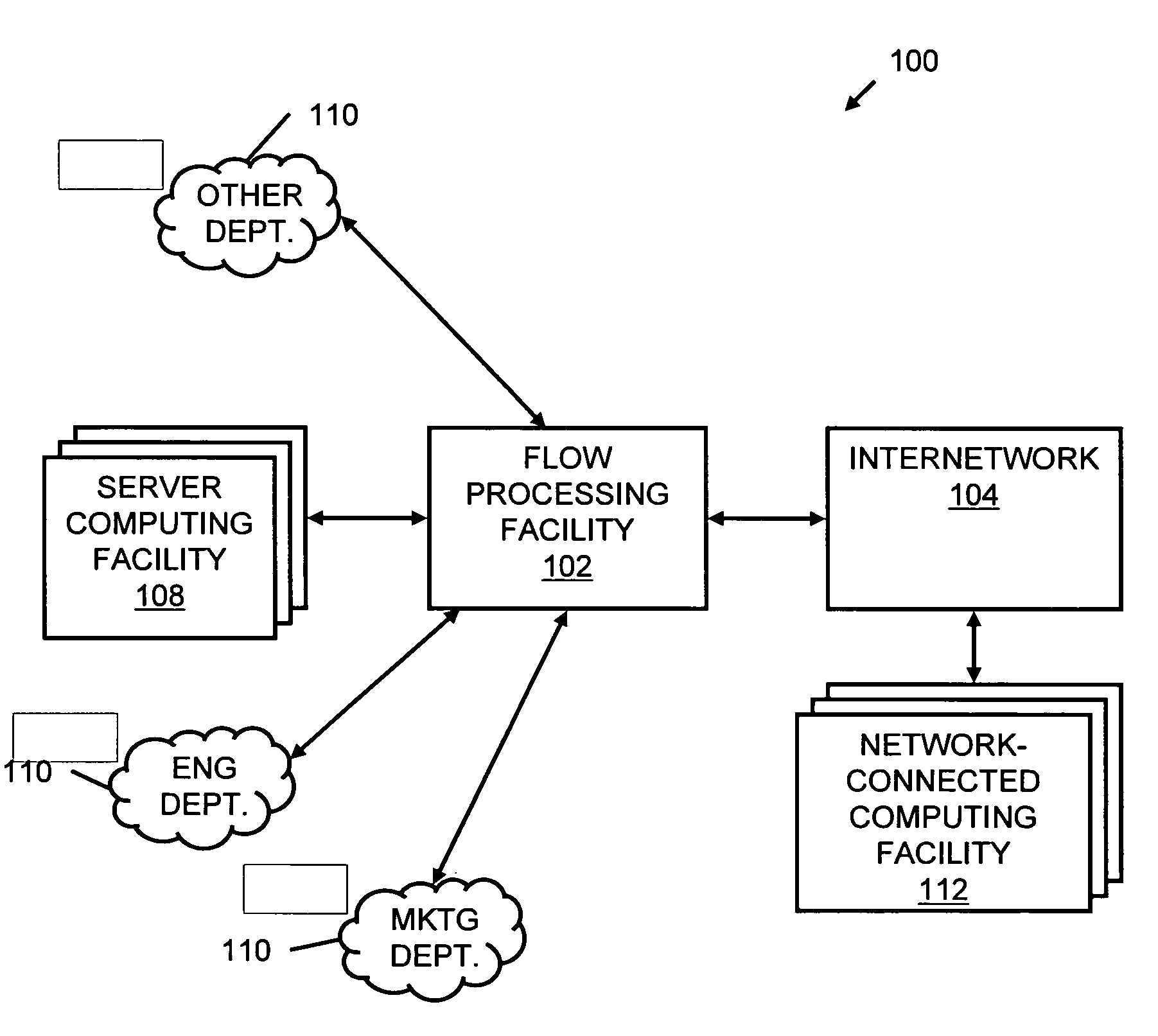
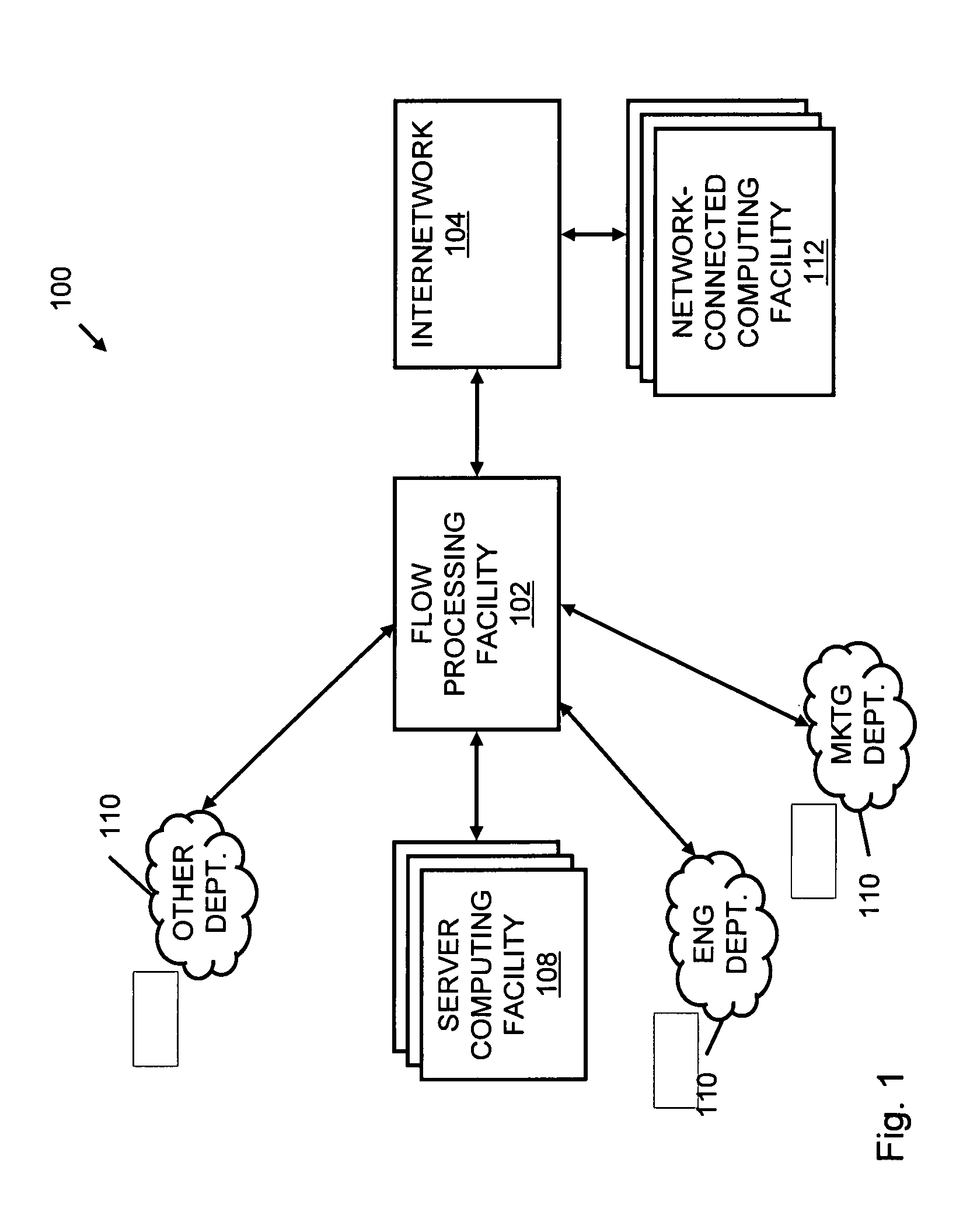
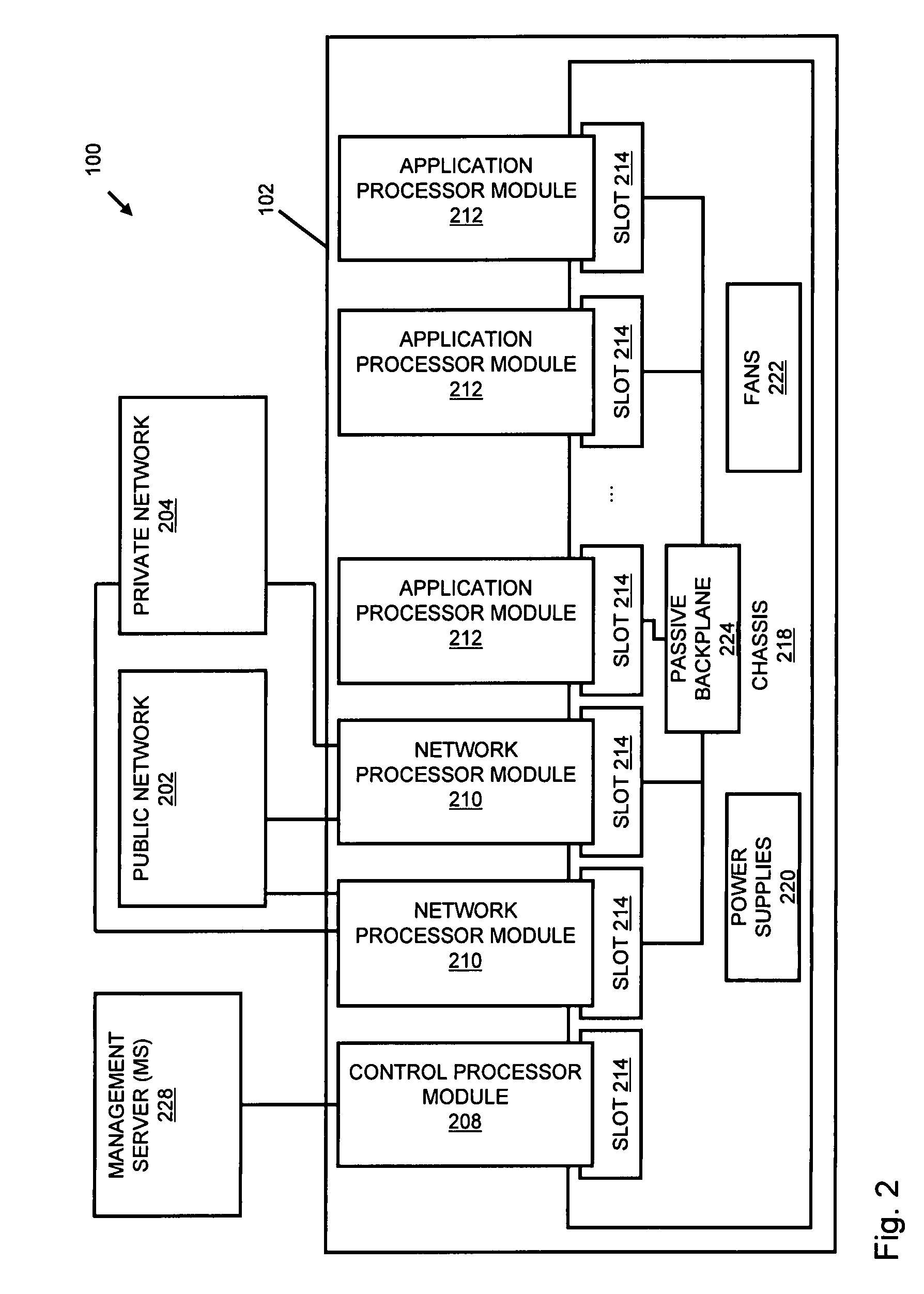
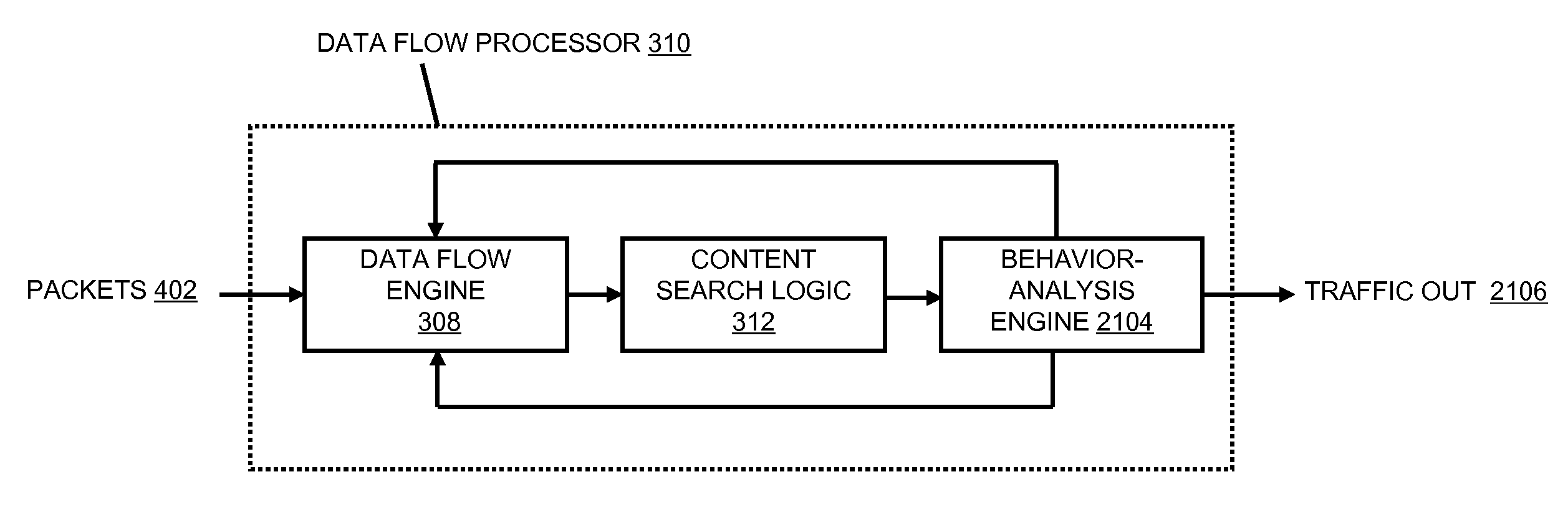
Systems and methods for processing data flows
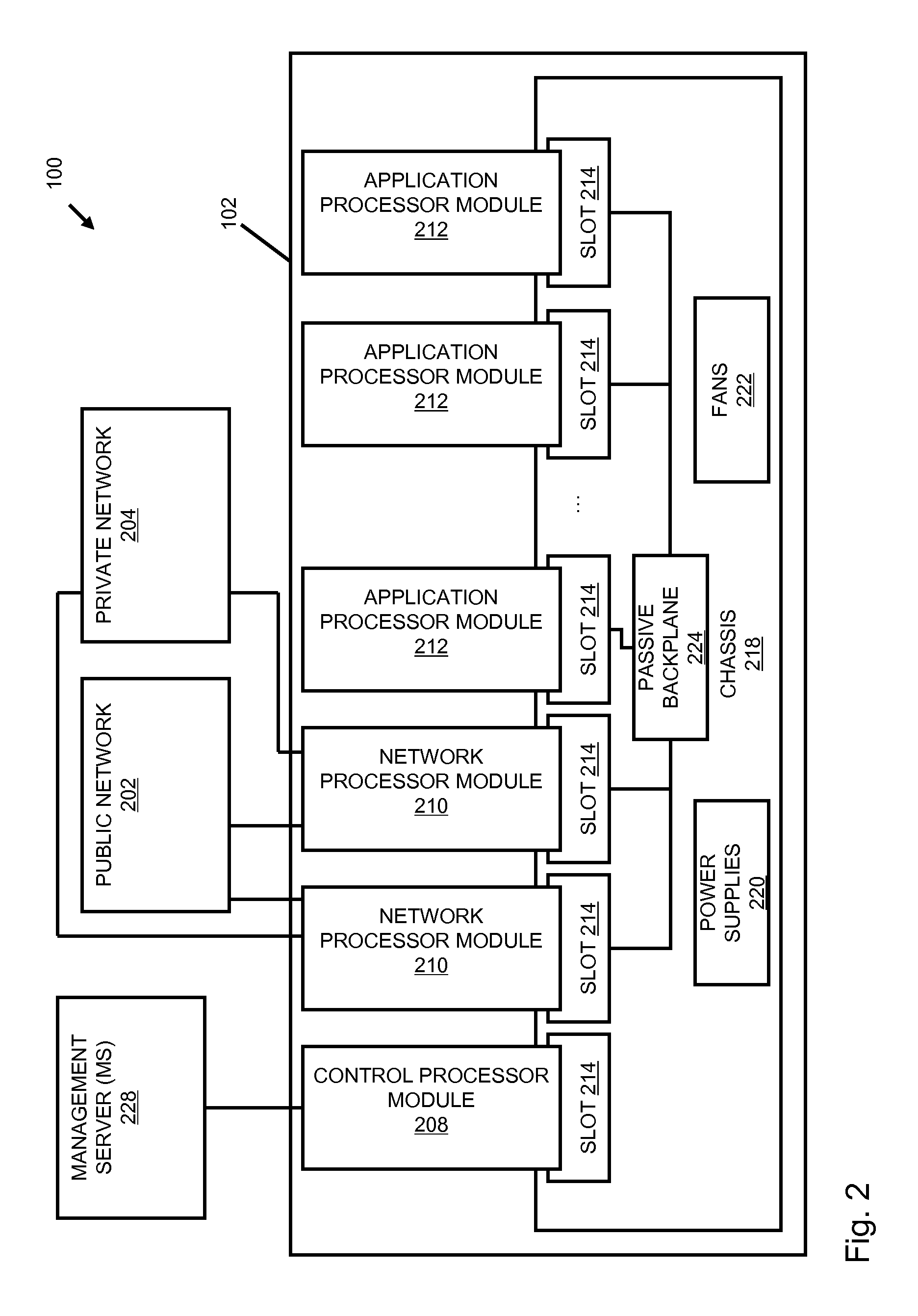
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
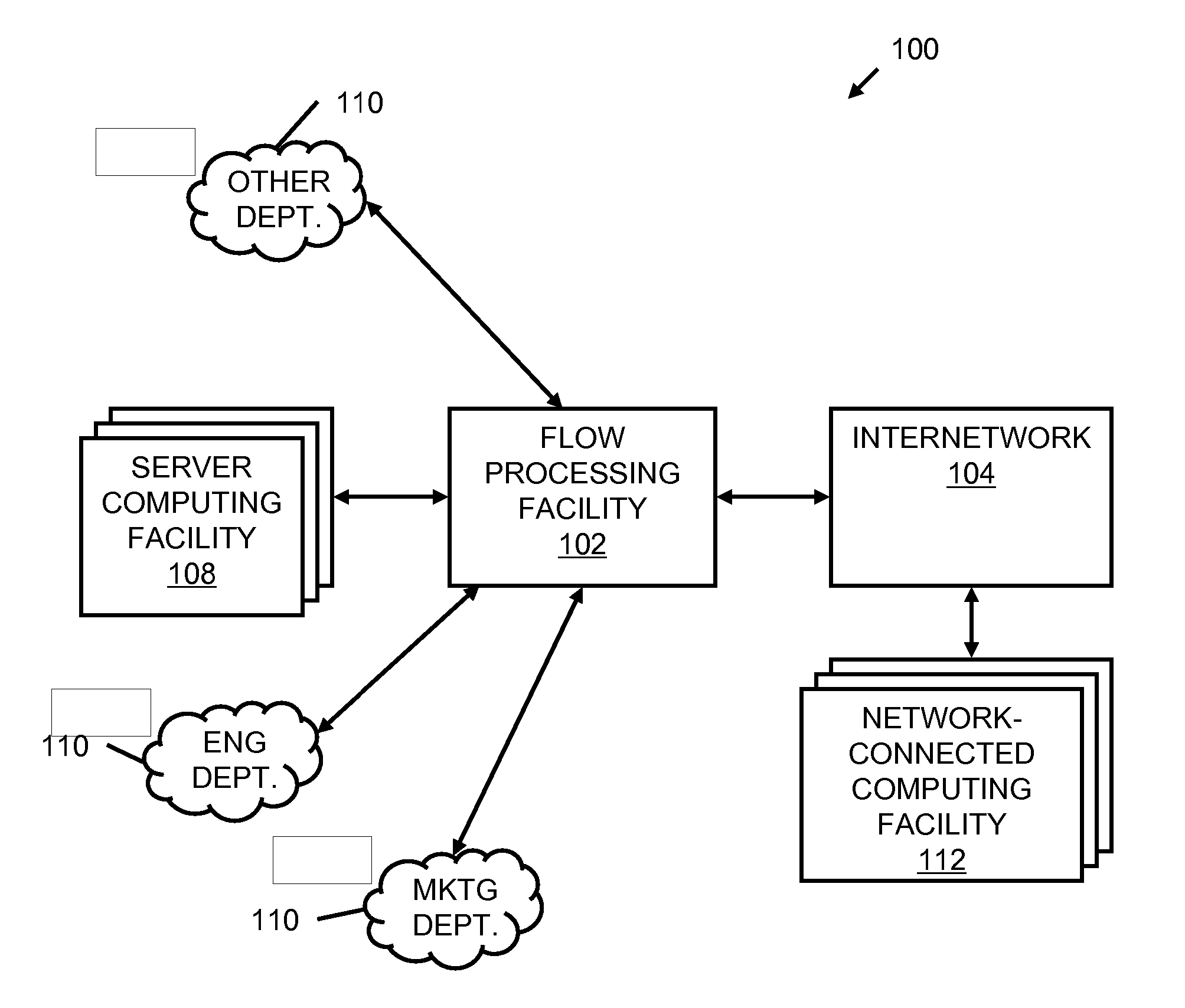
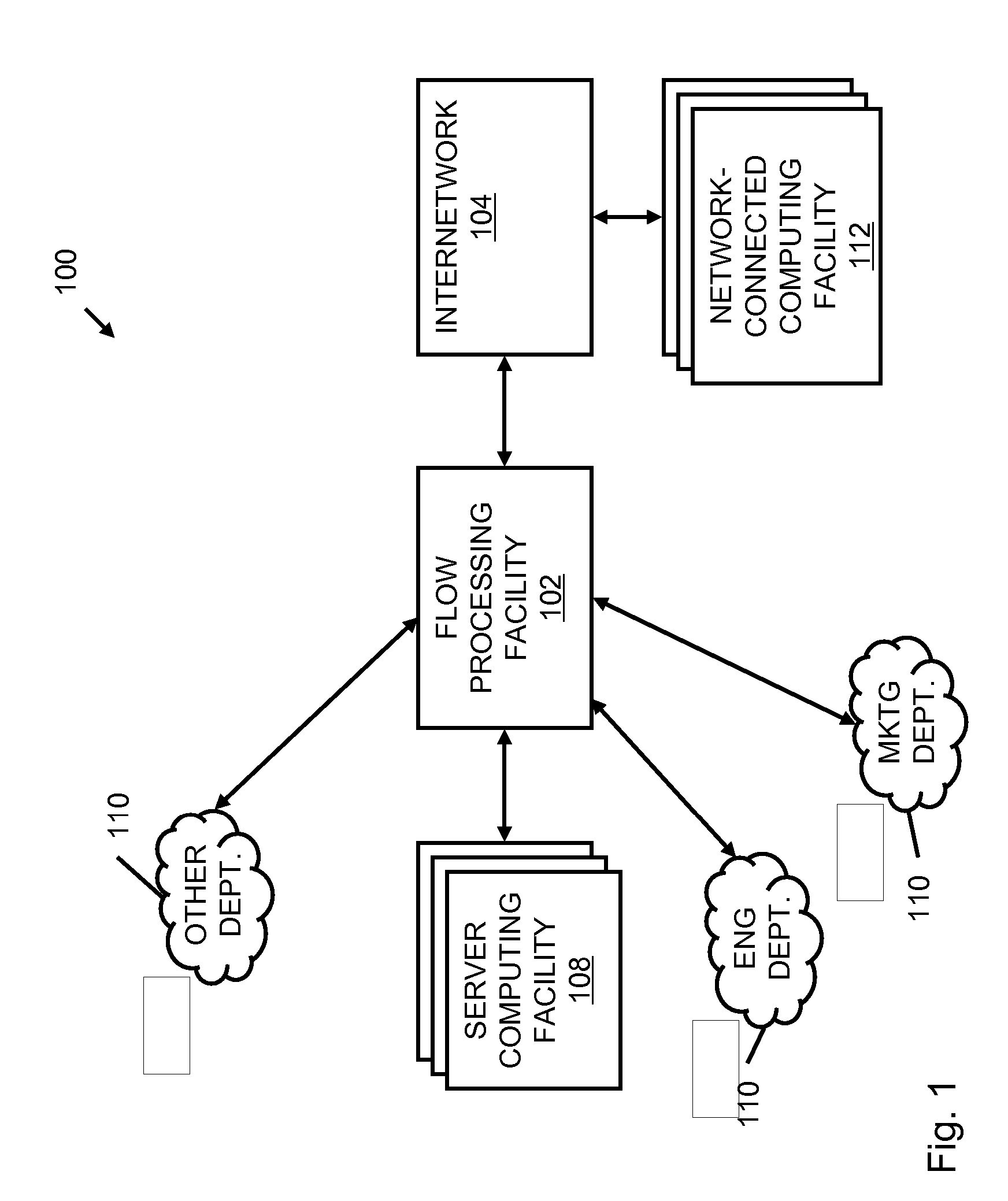
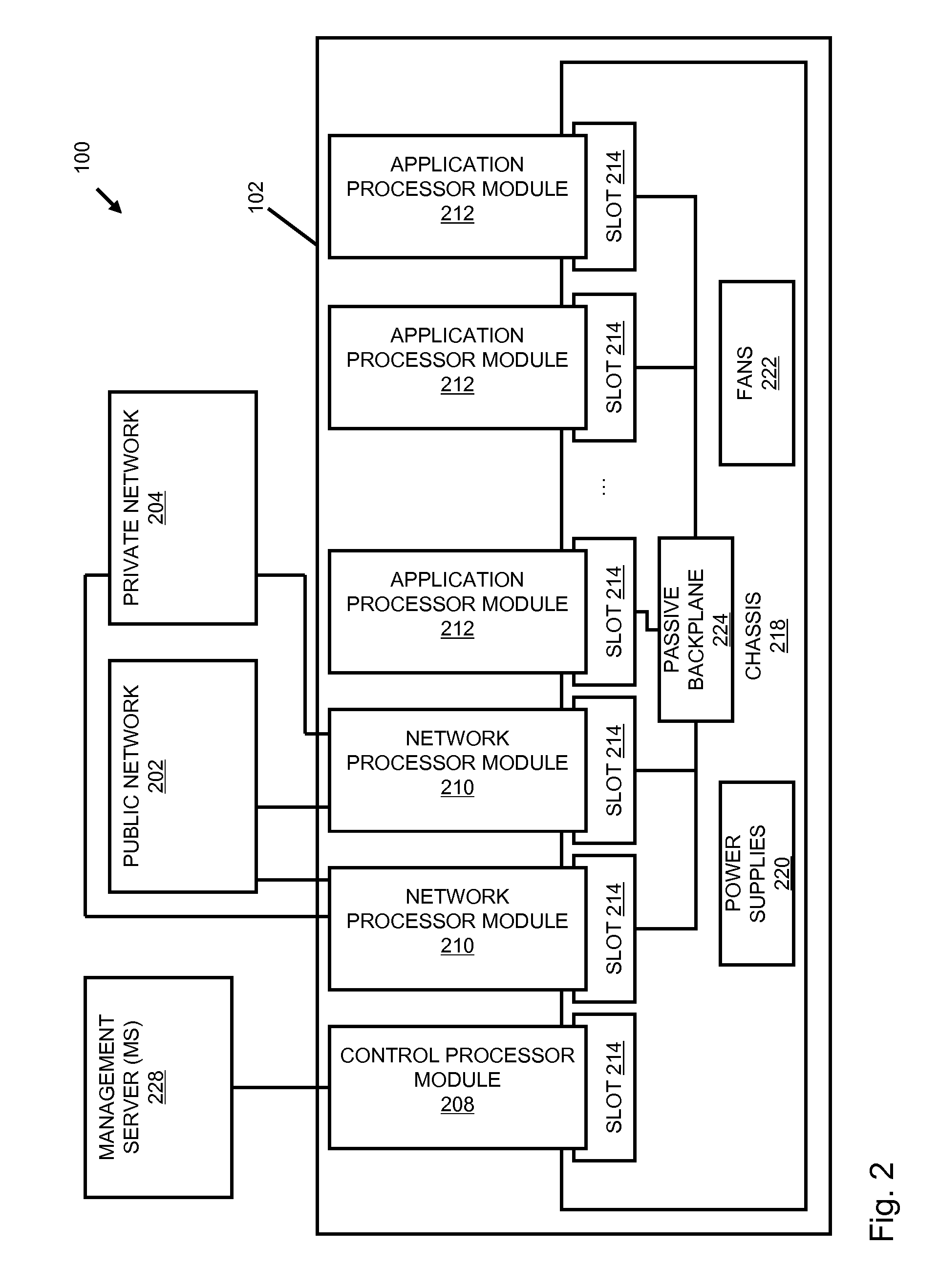
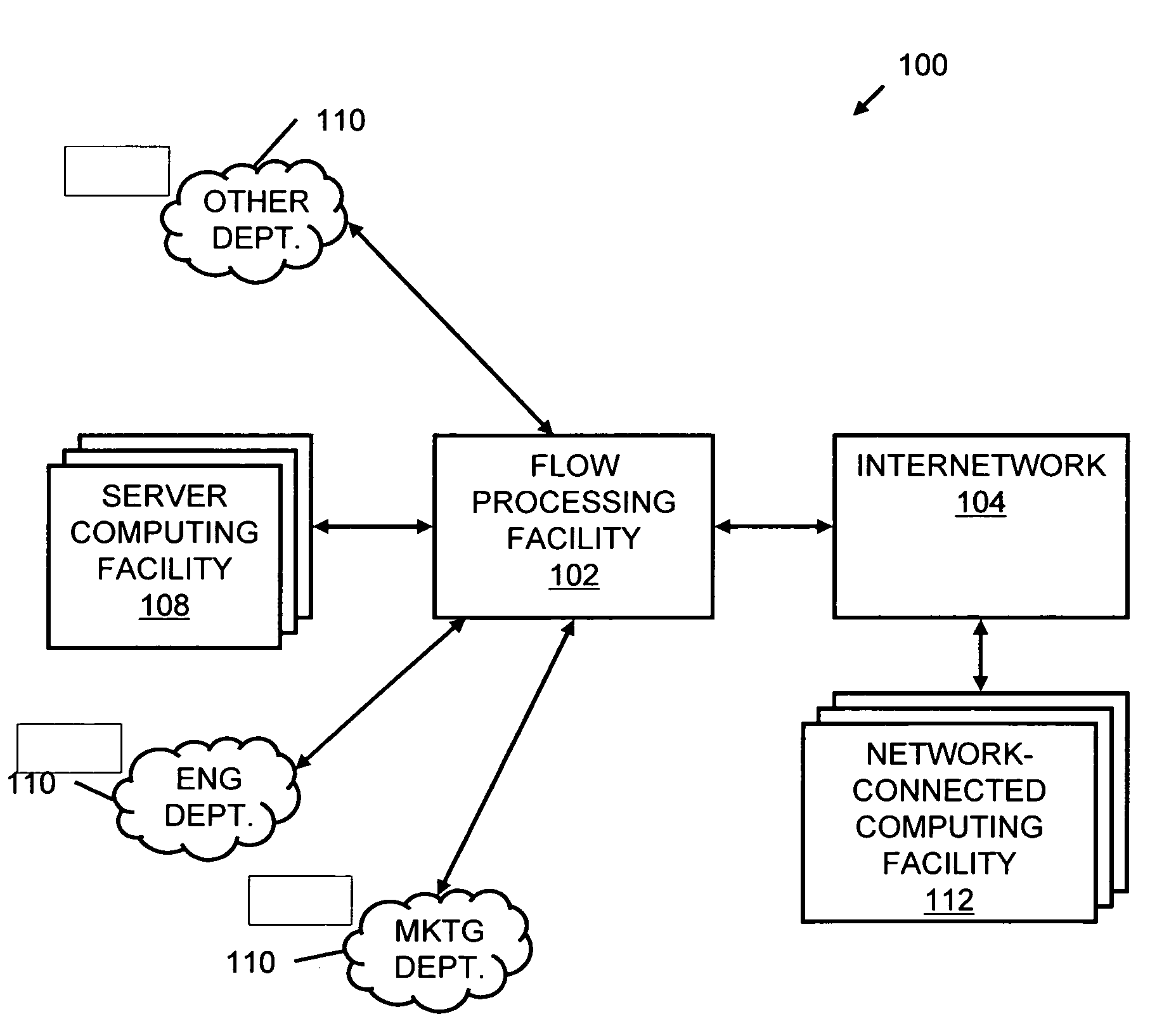
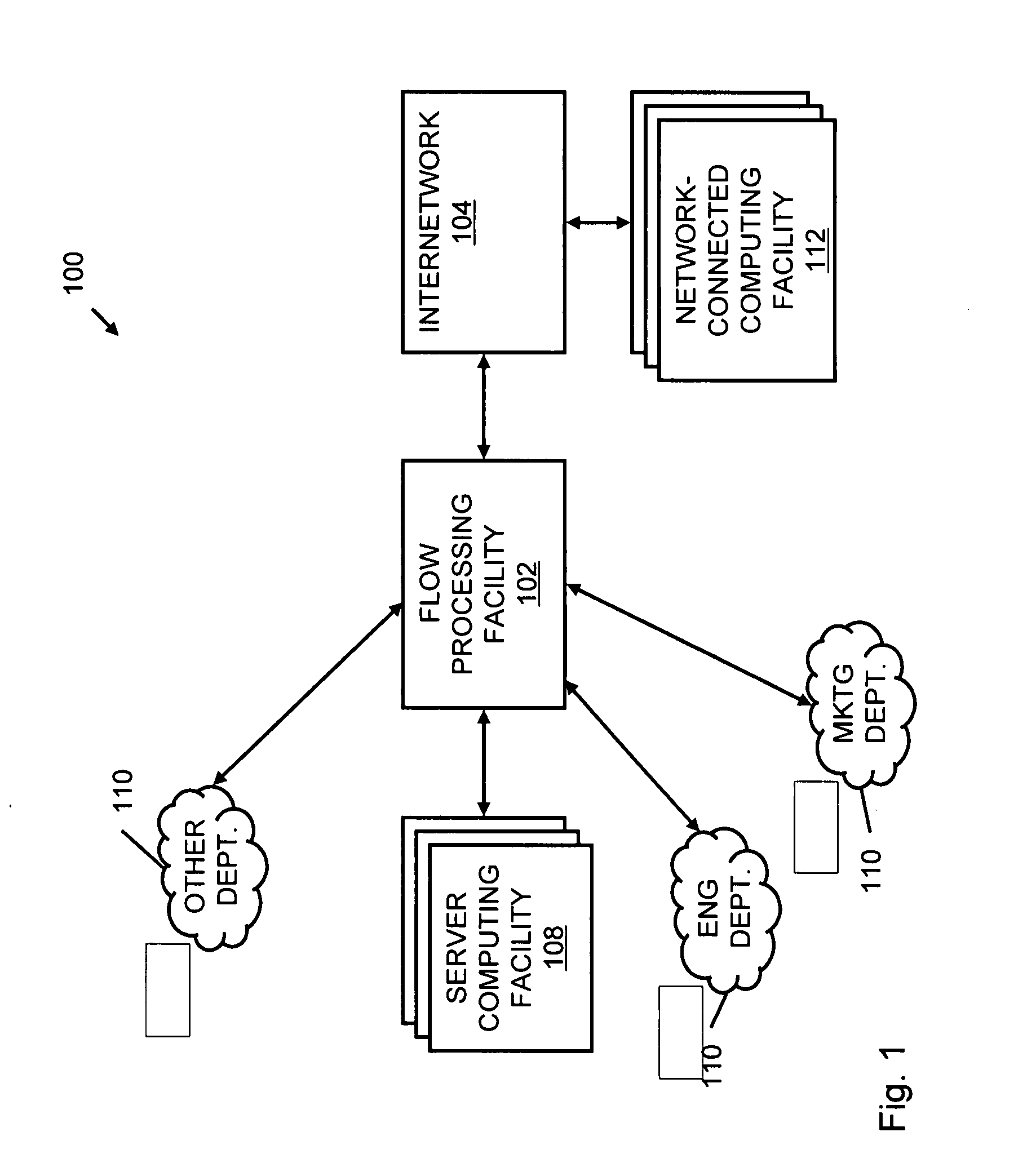
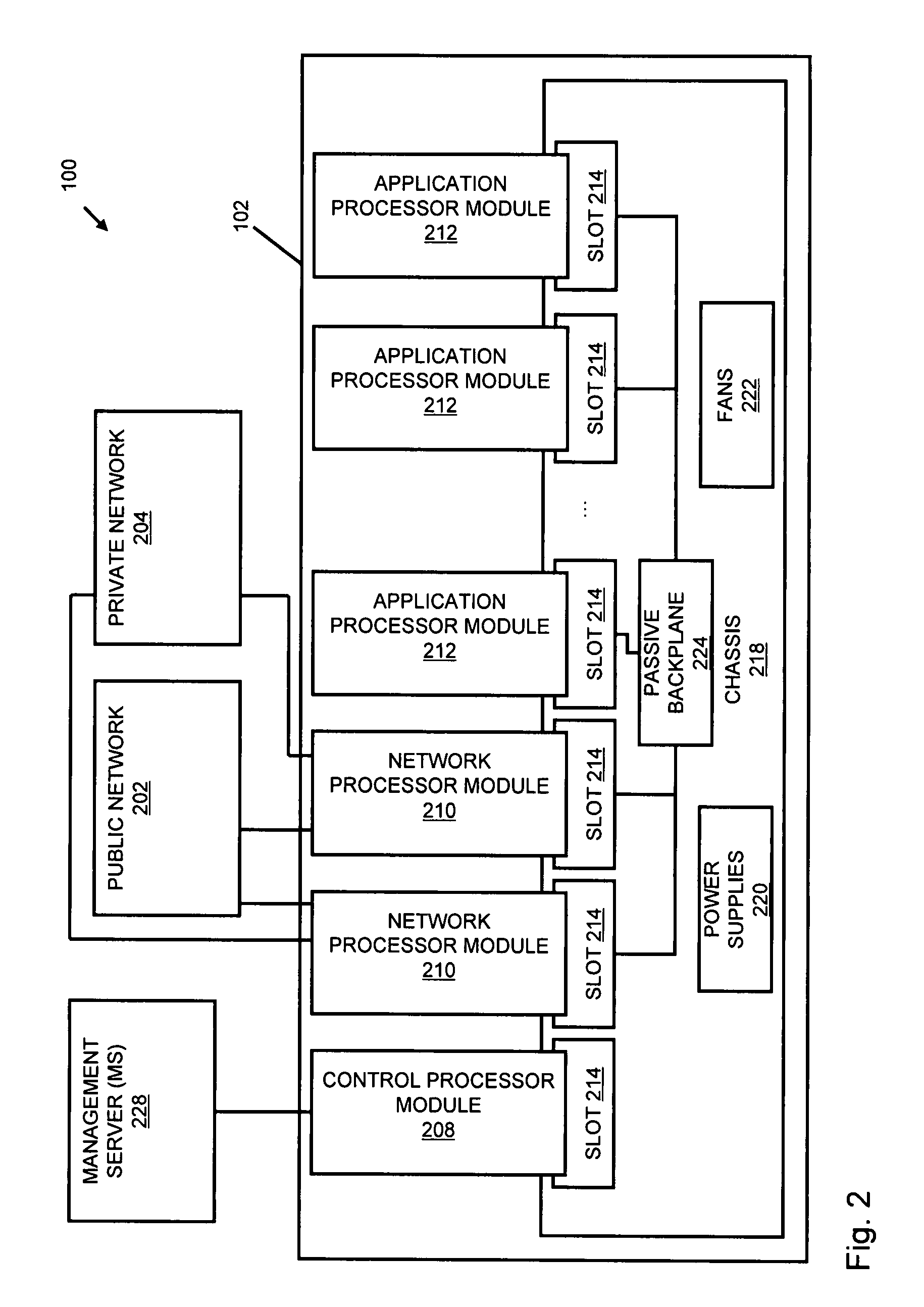
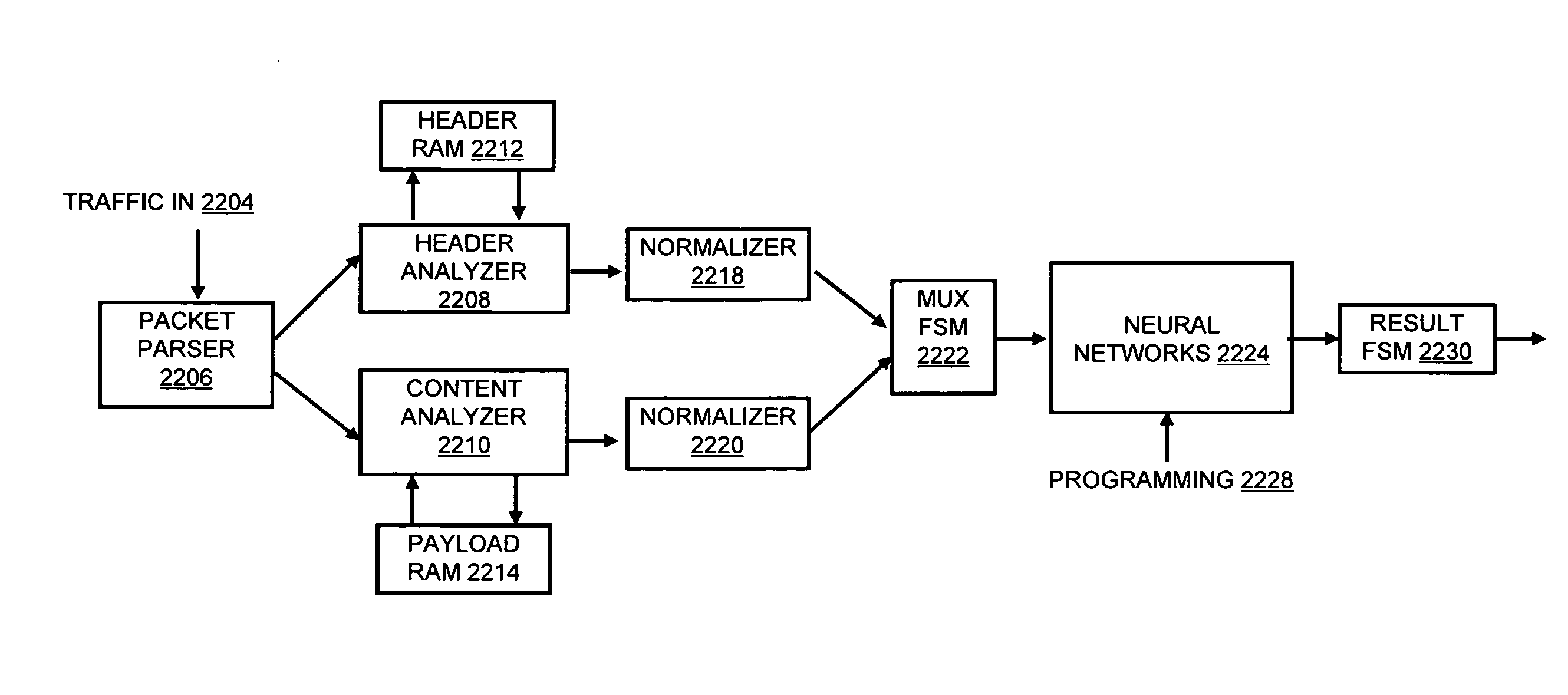
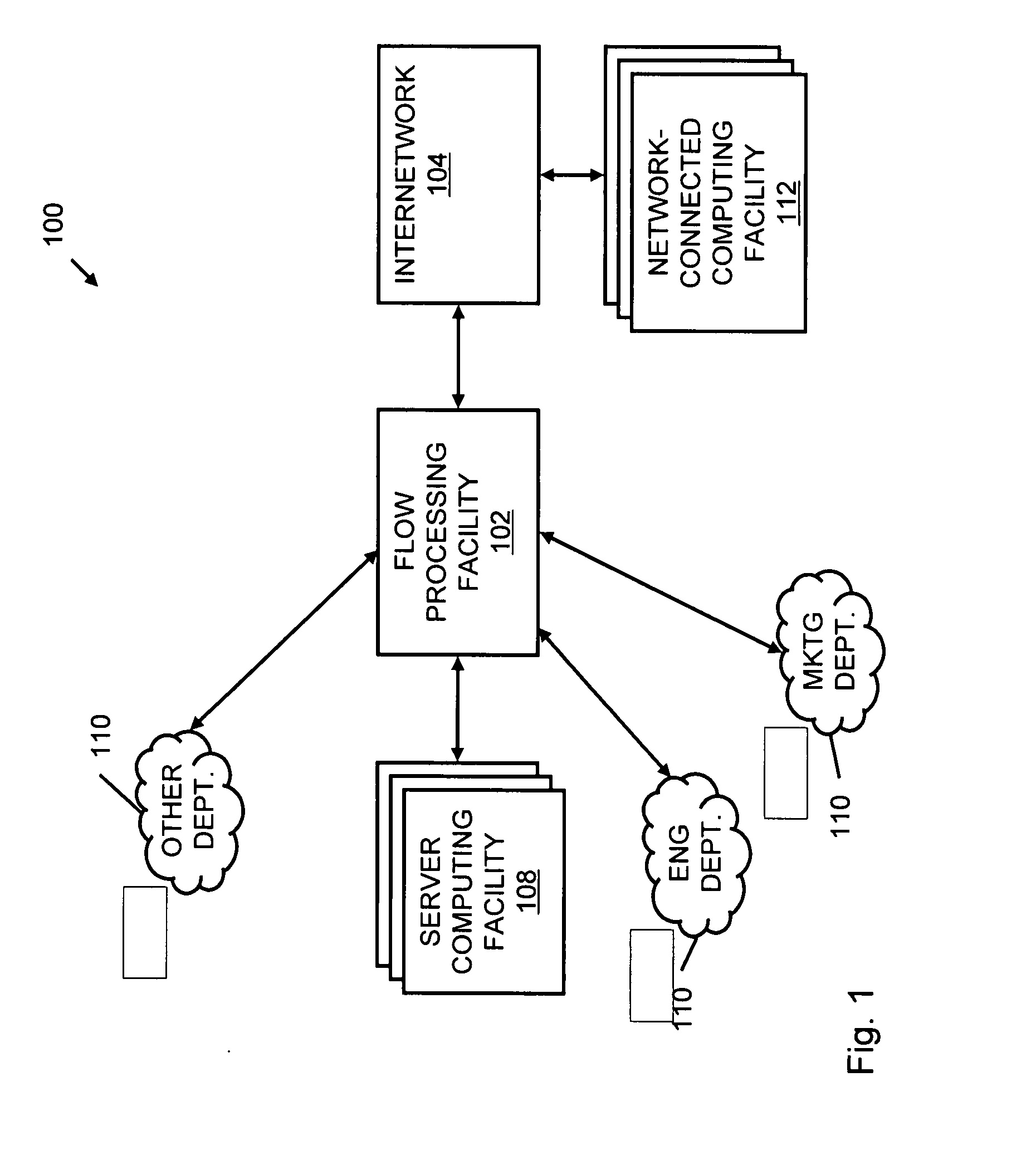
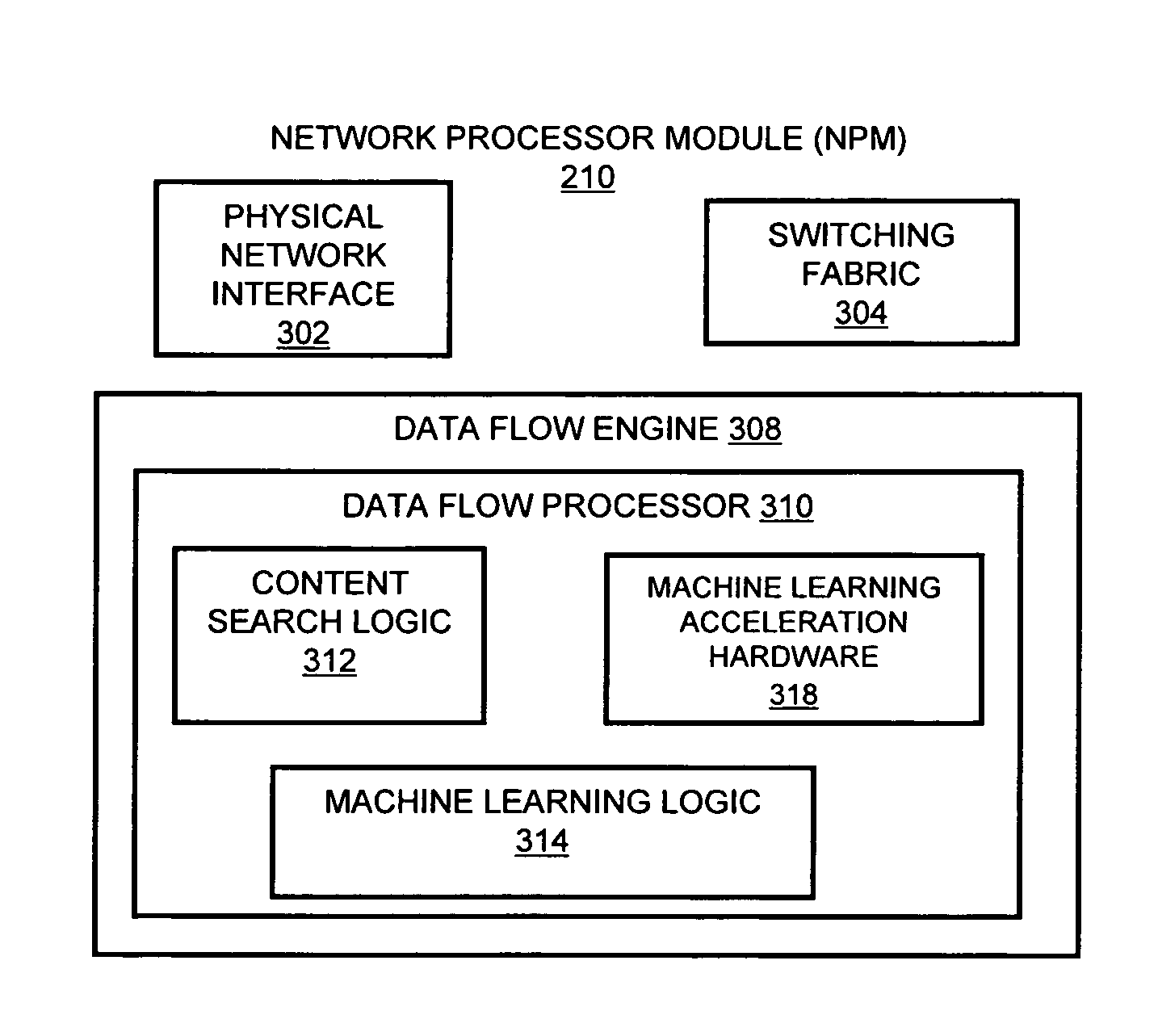
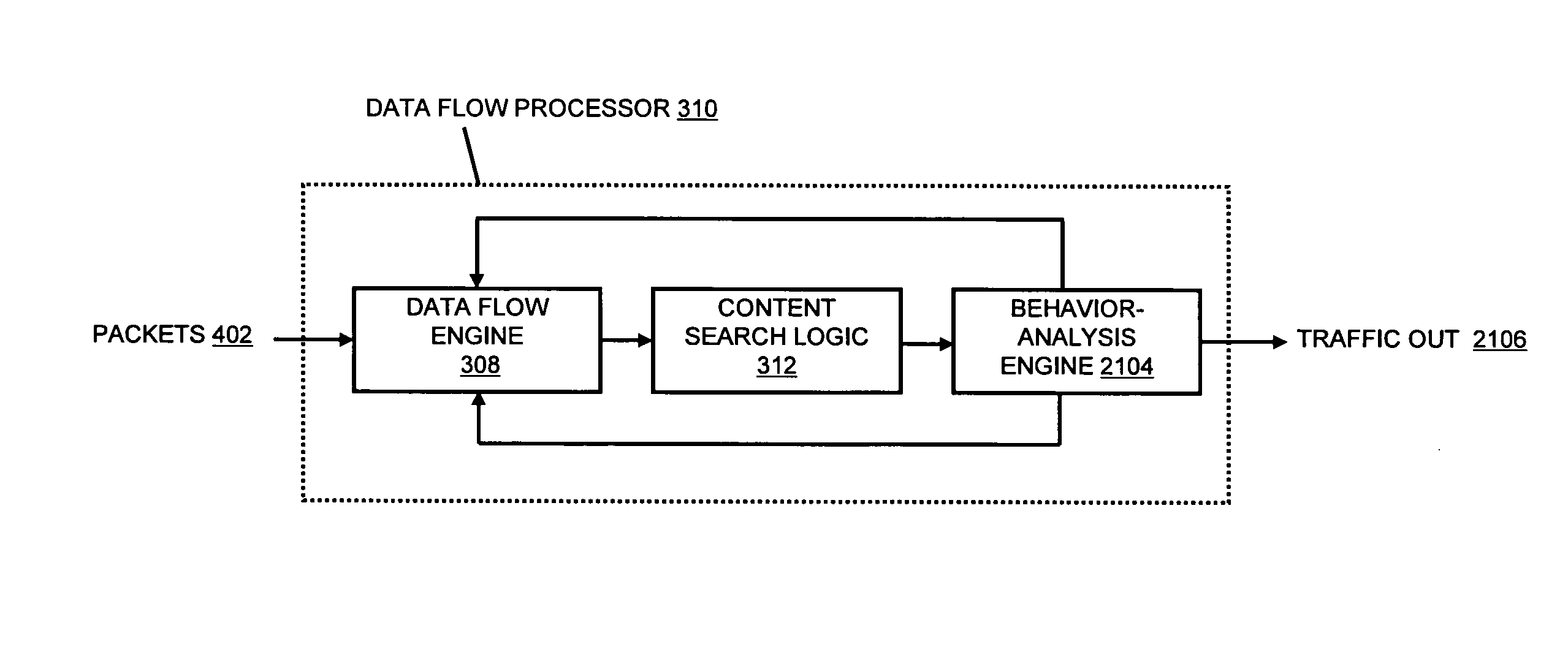
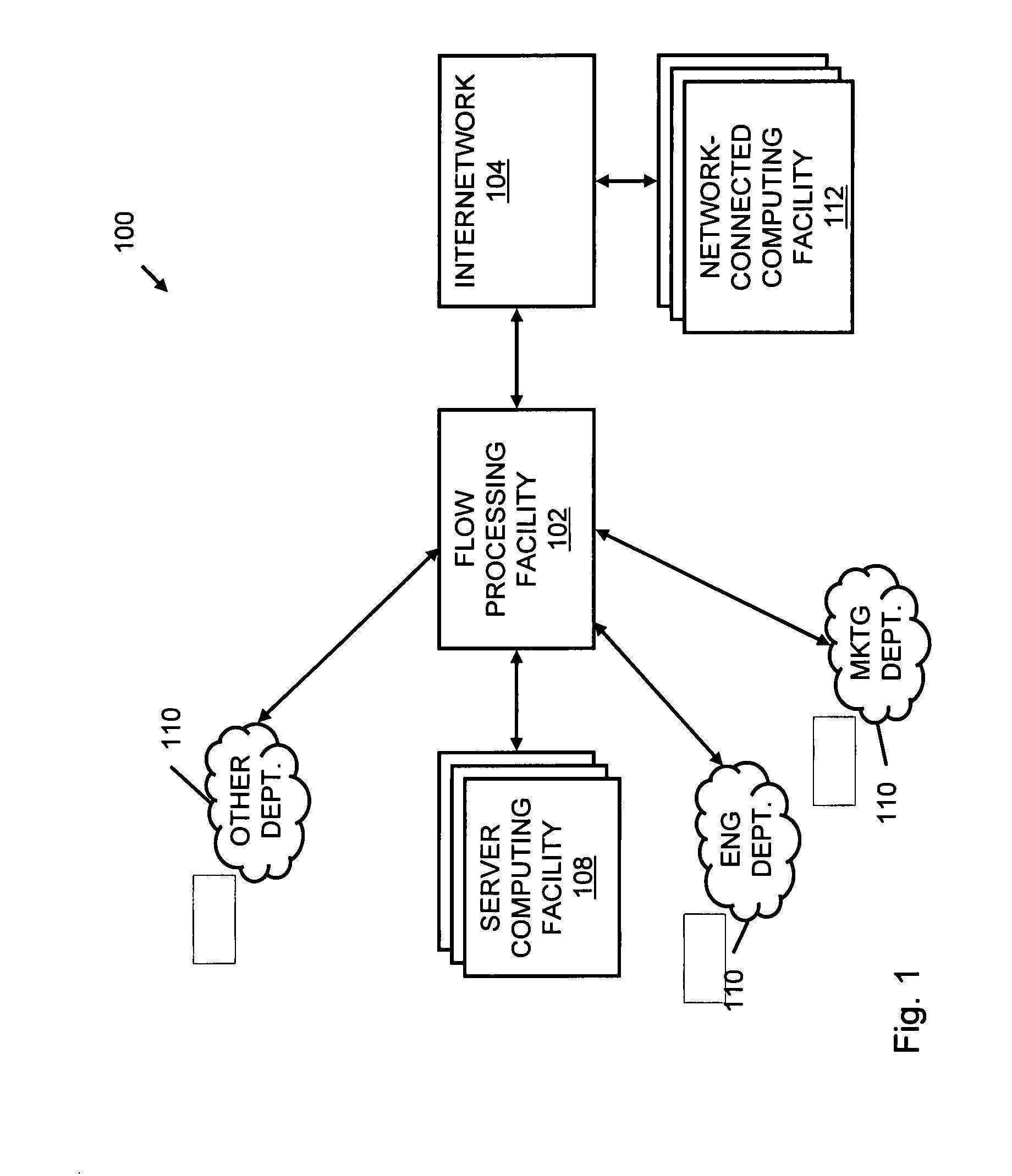
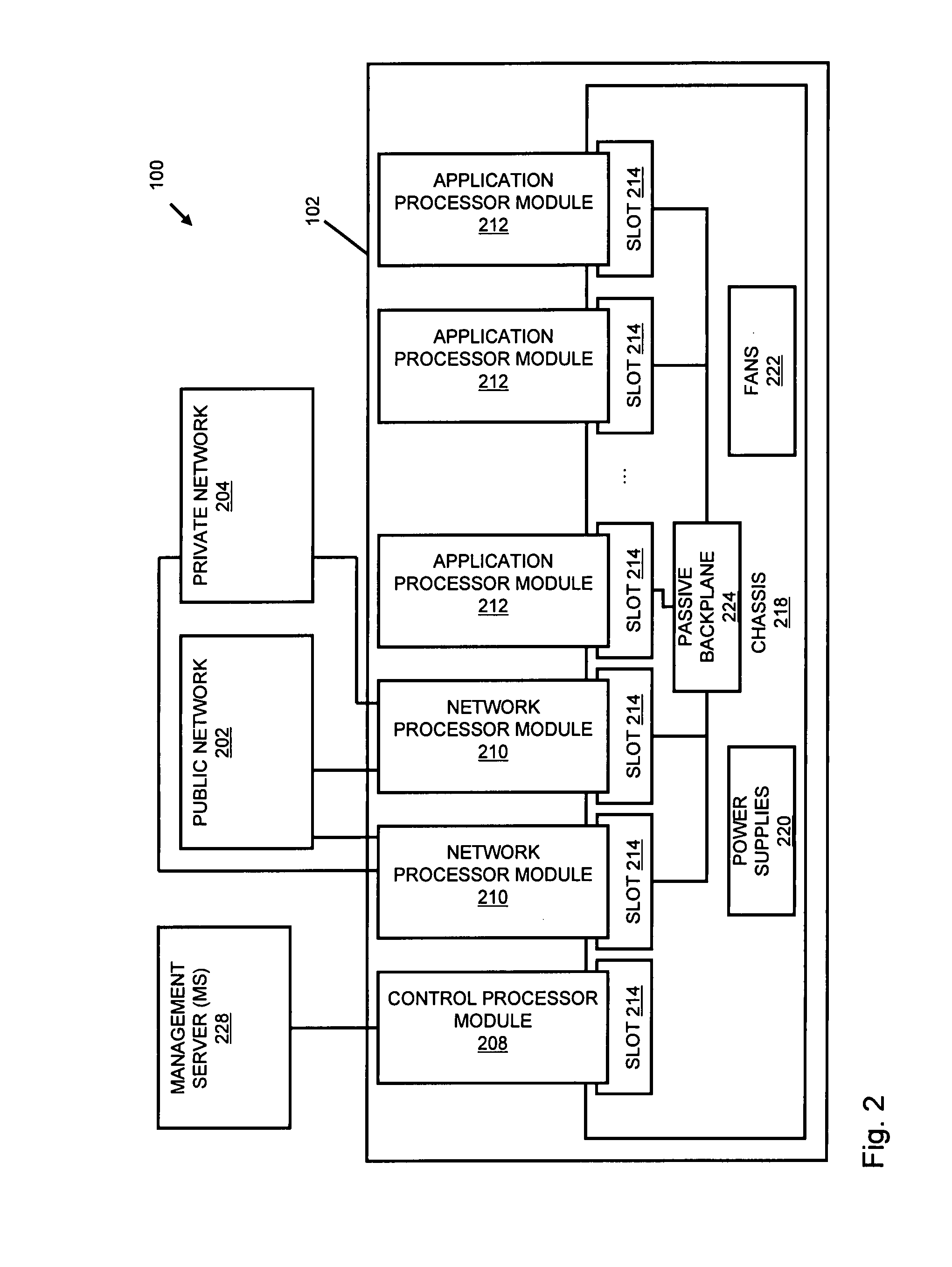
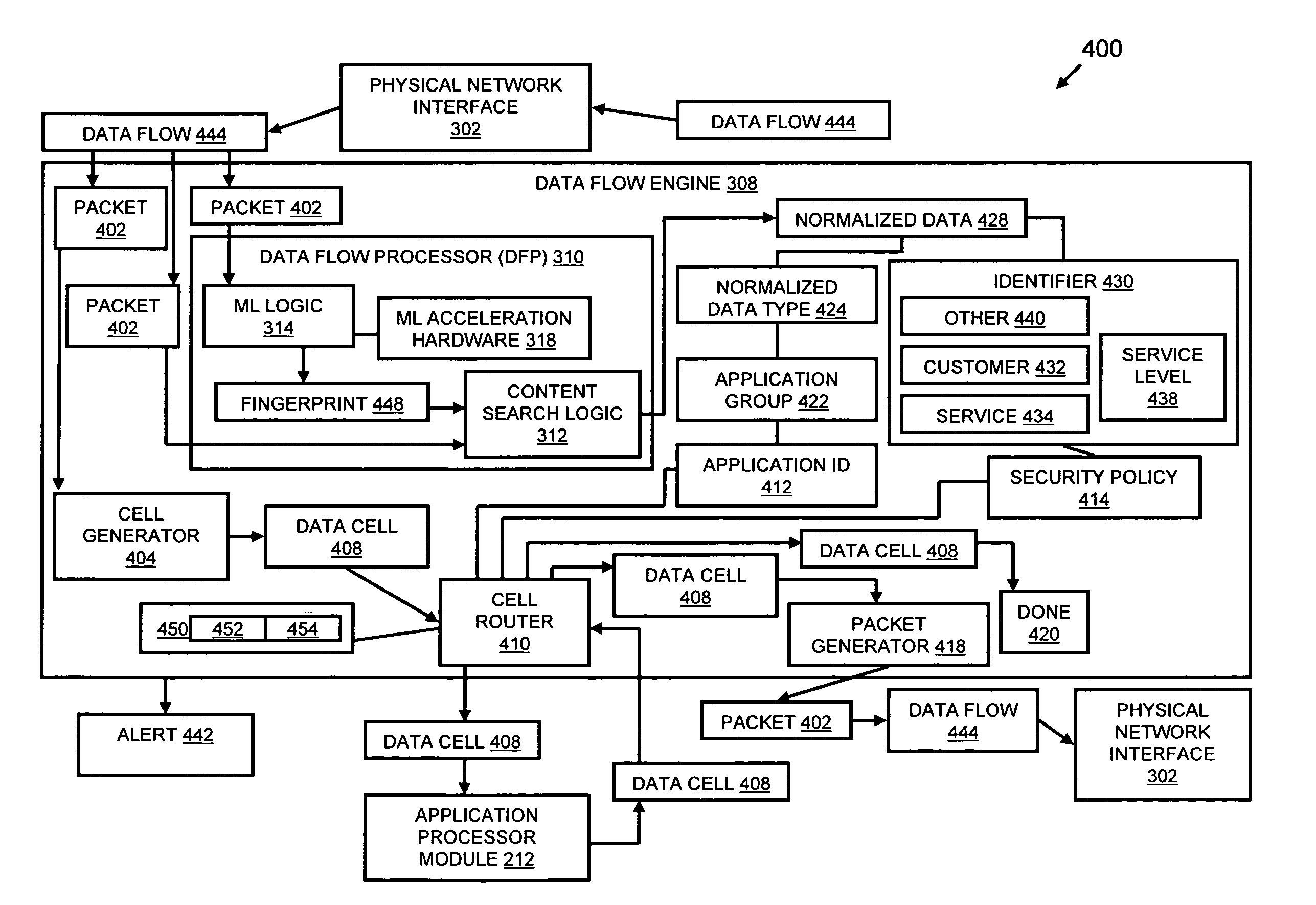
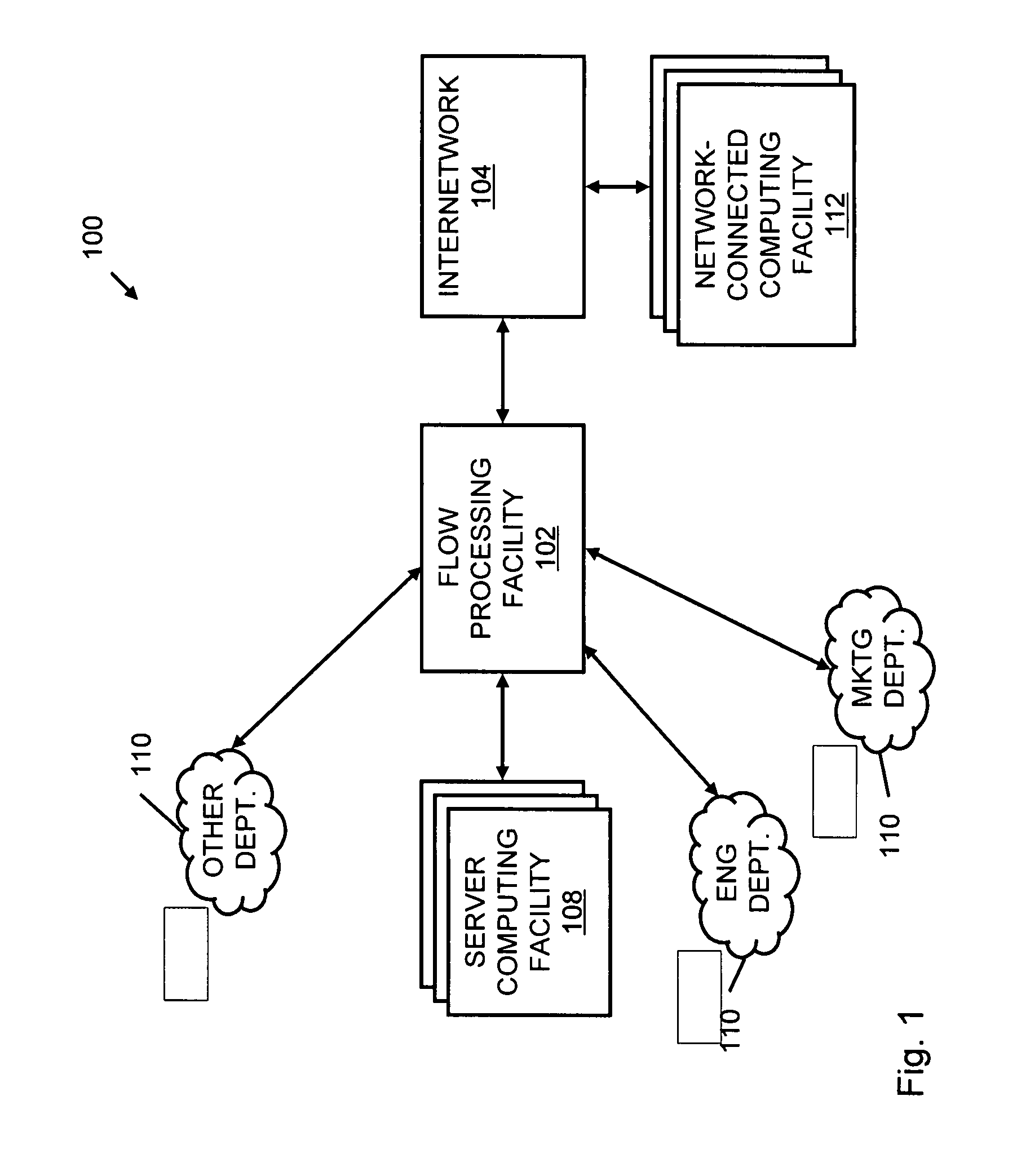
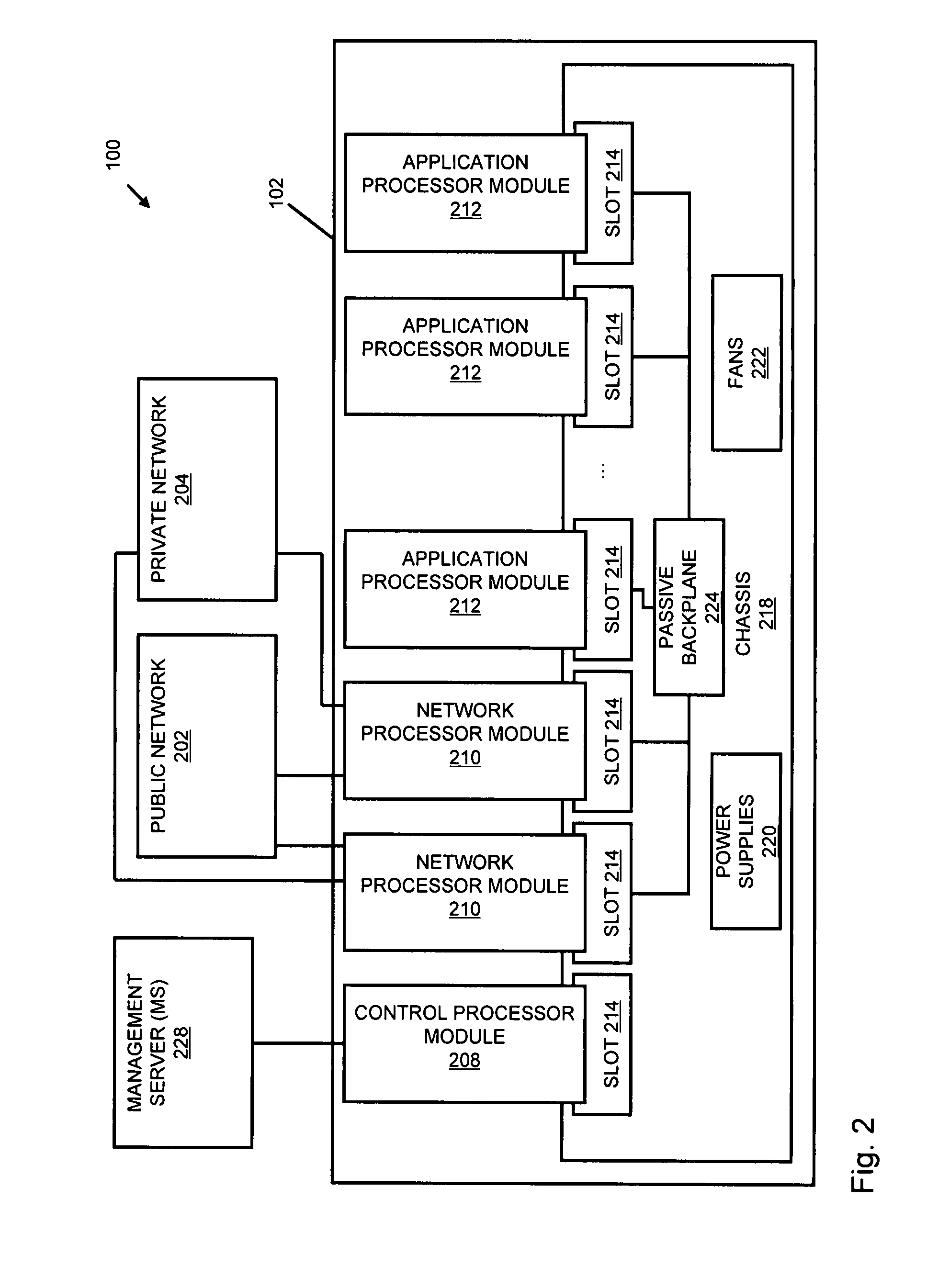
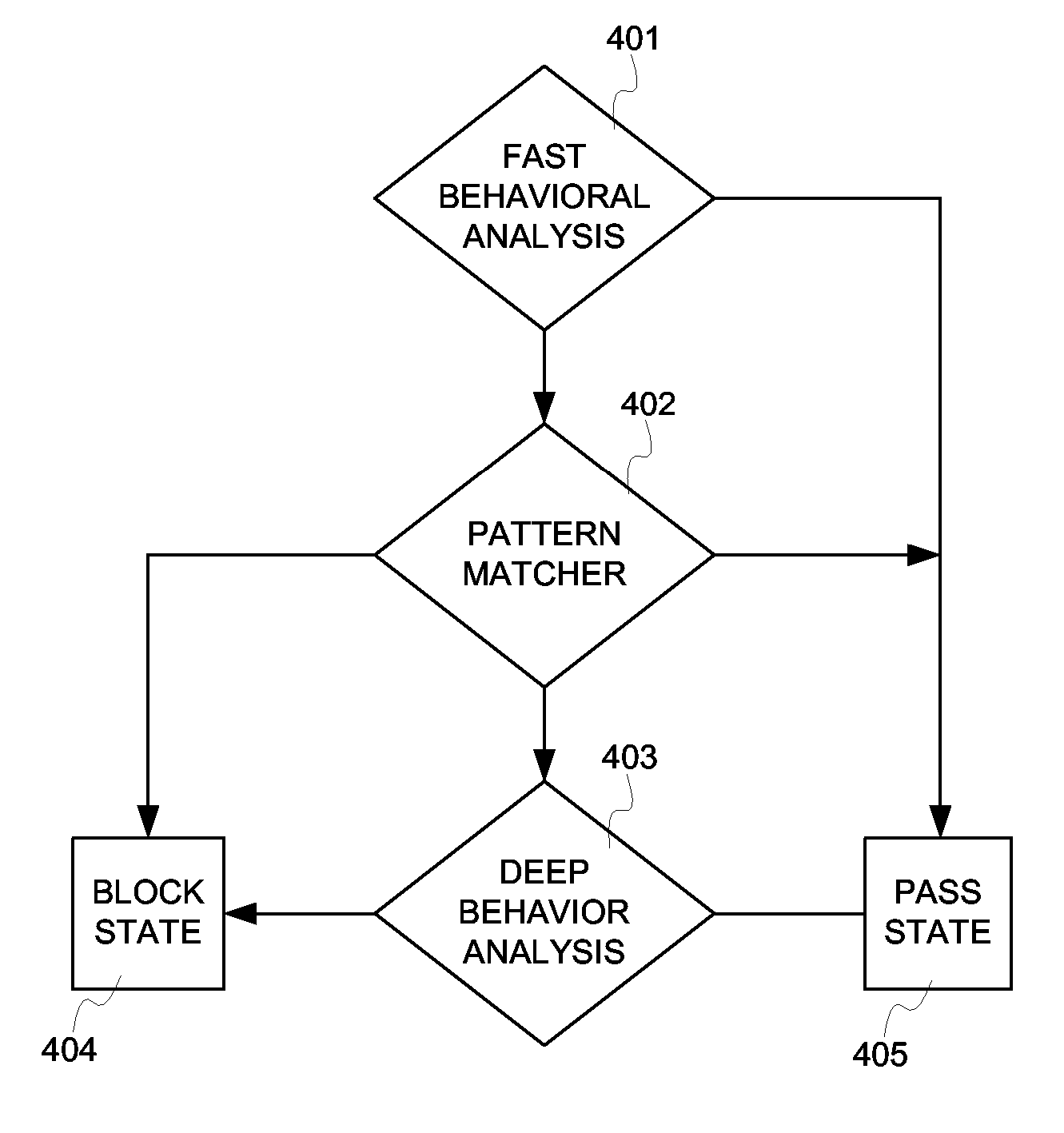
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
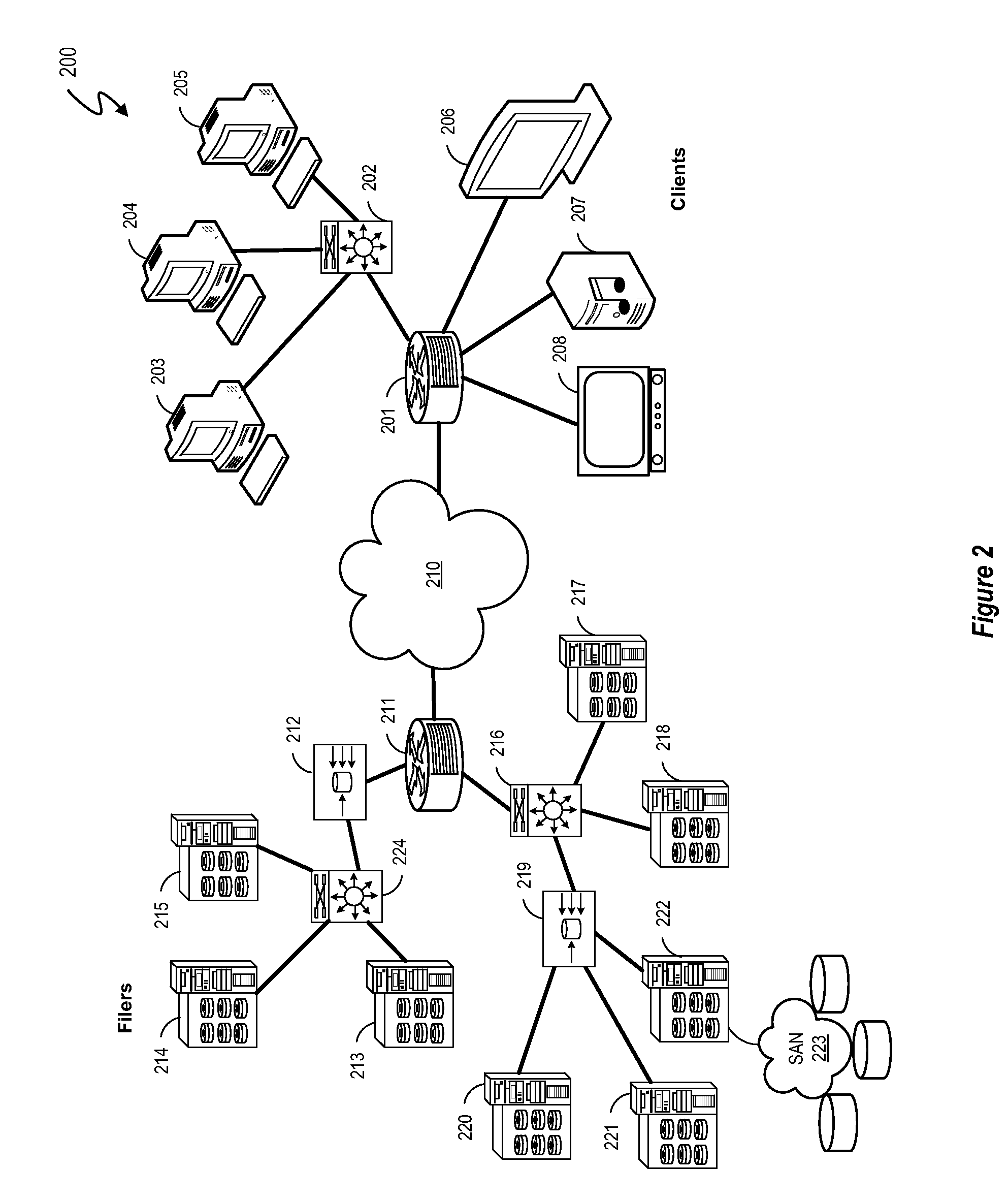
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
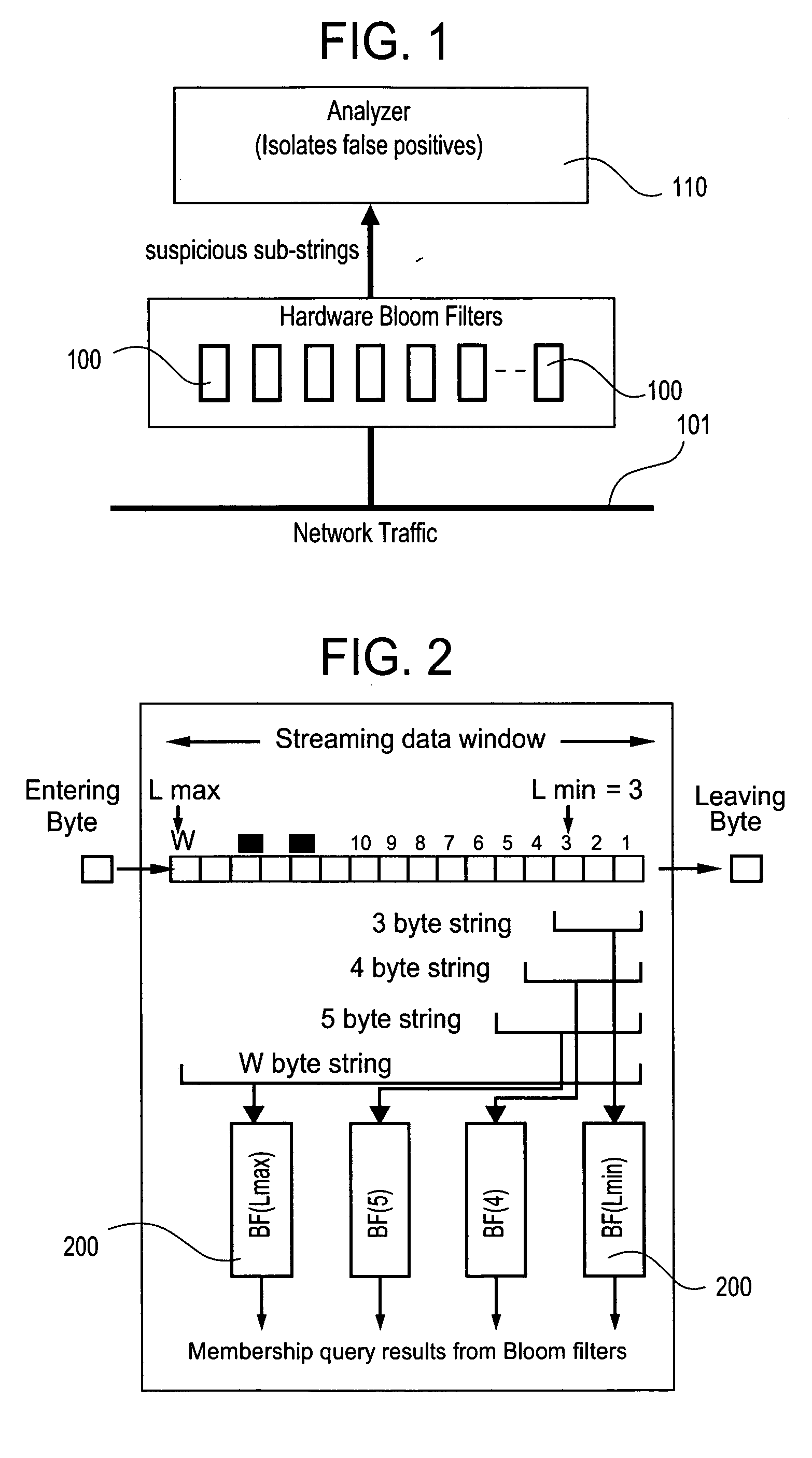
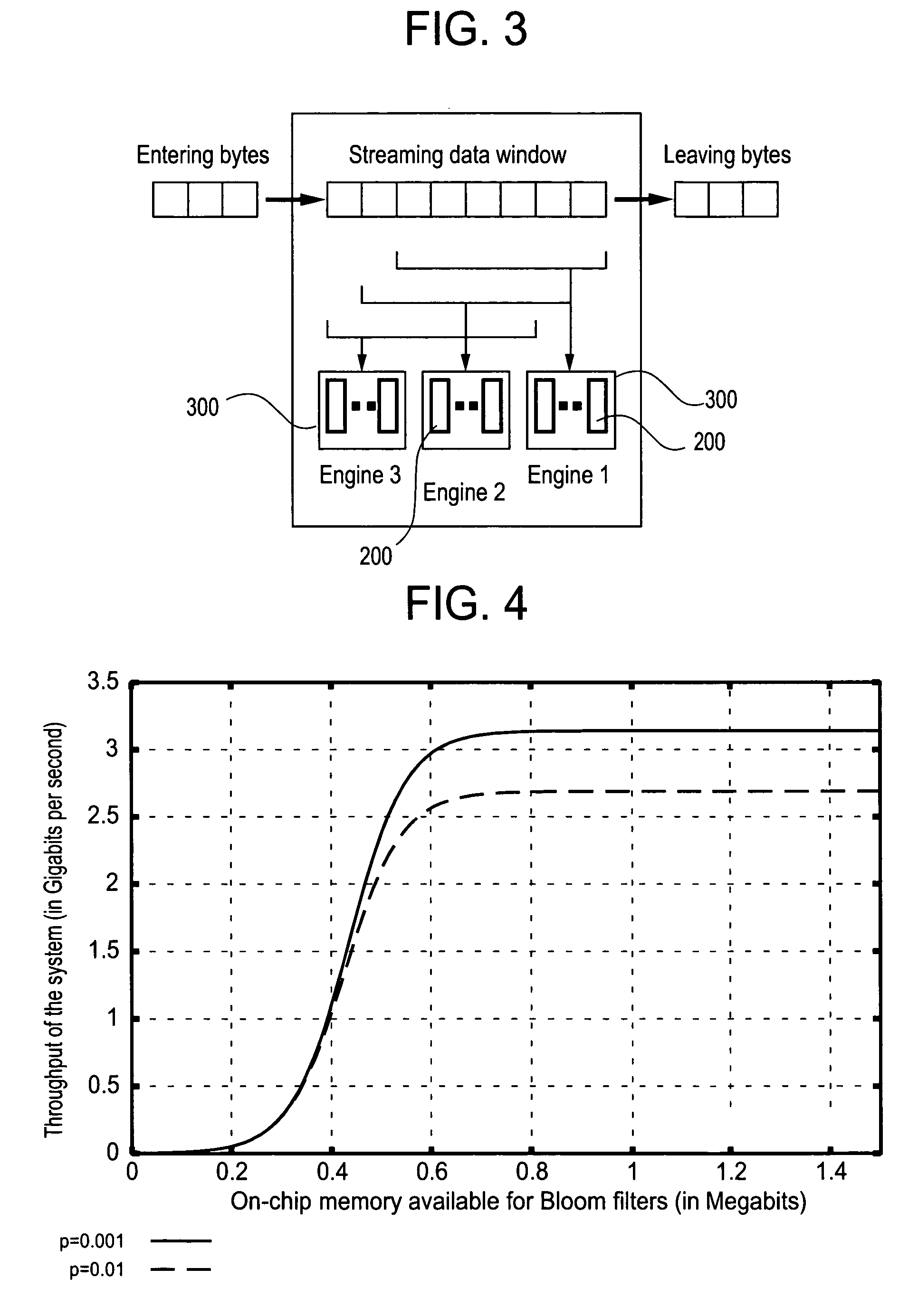
Method and apparatus for detecting predefined signatures in packet payload using bloom filters
ActiveUS20050086520A1Digital data processing detailsUser identity/authority verificationBloom filterNetwork data
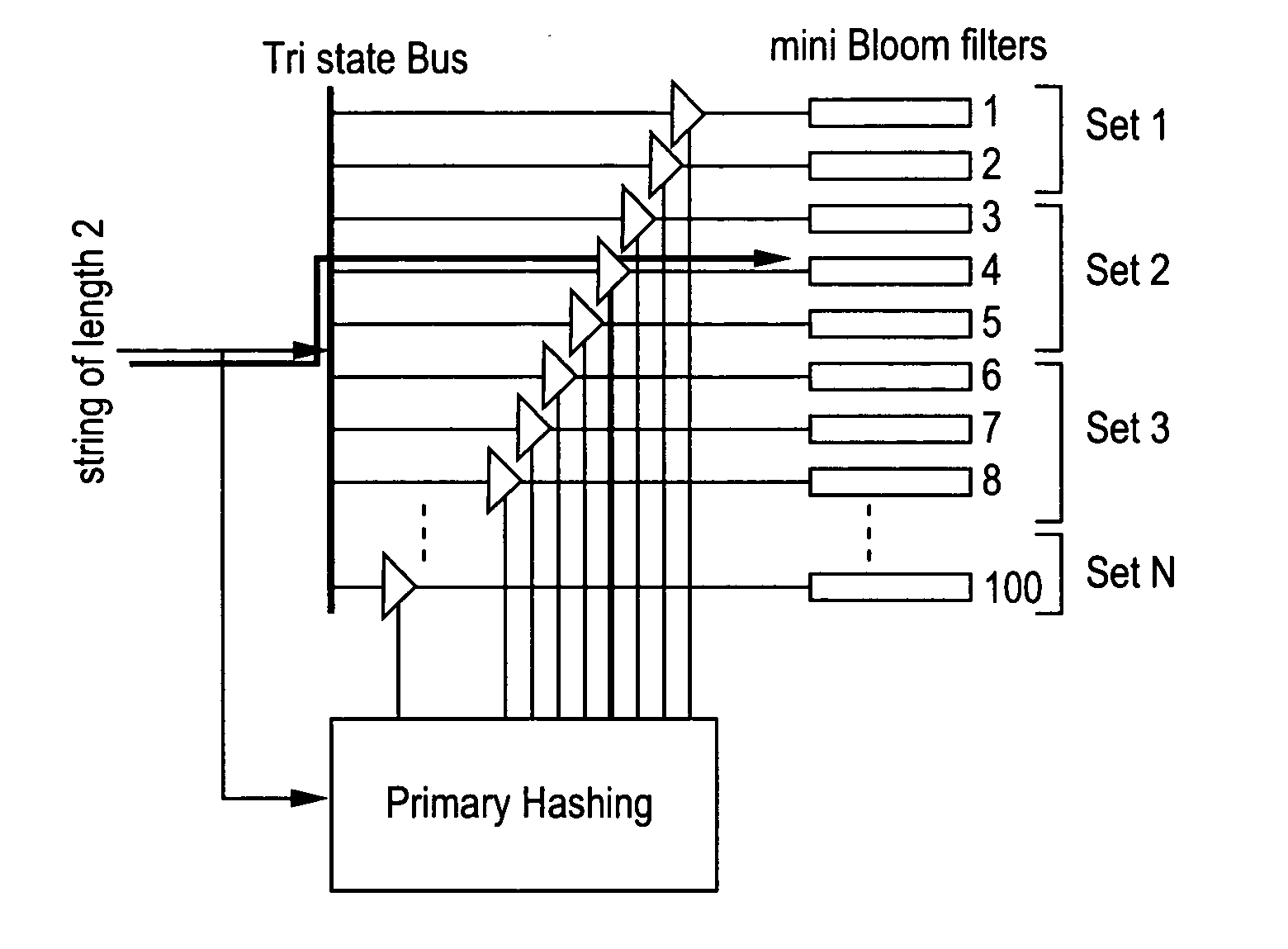
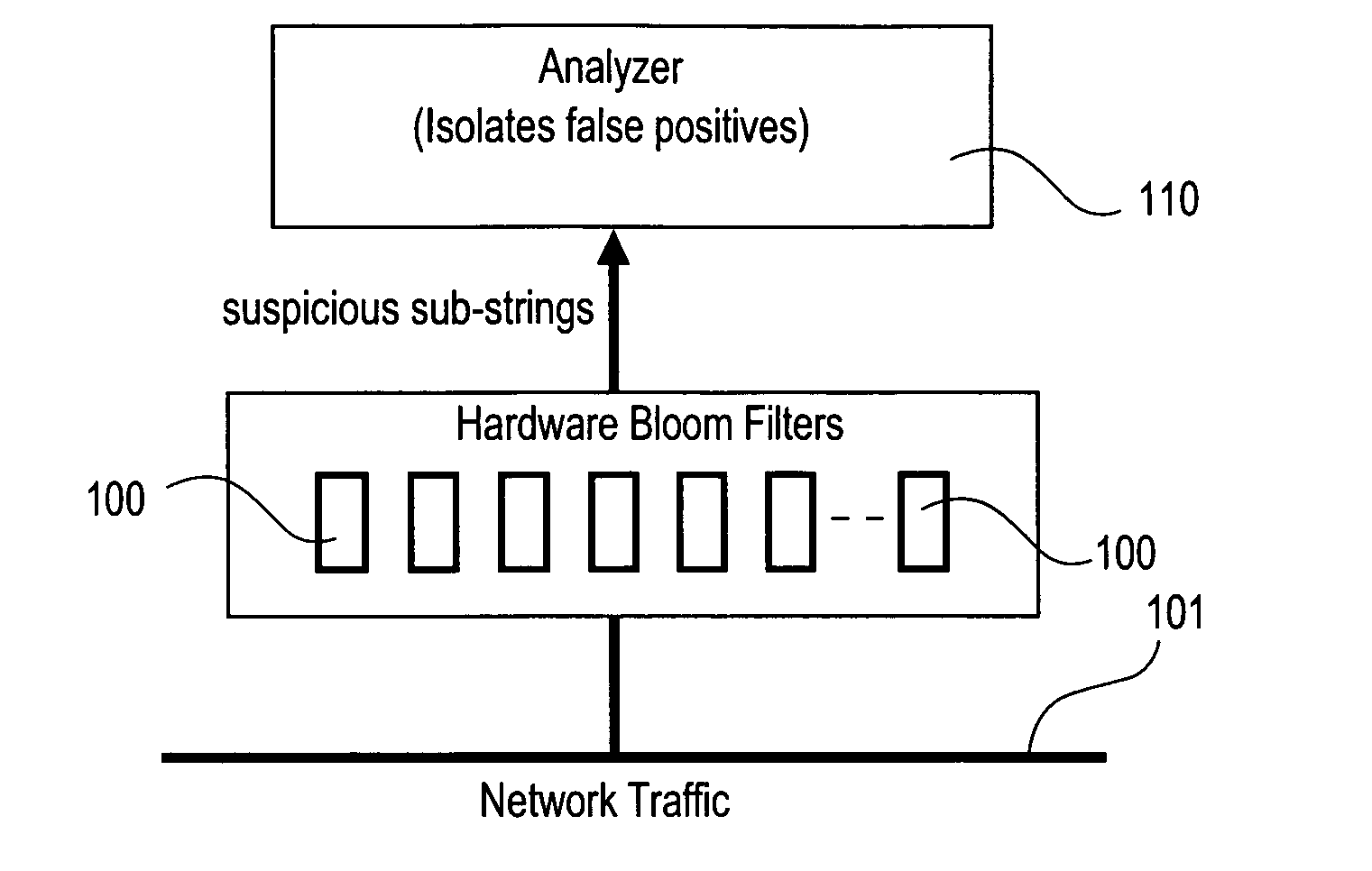
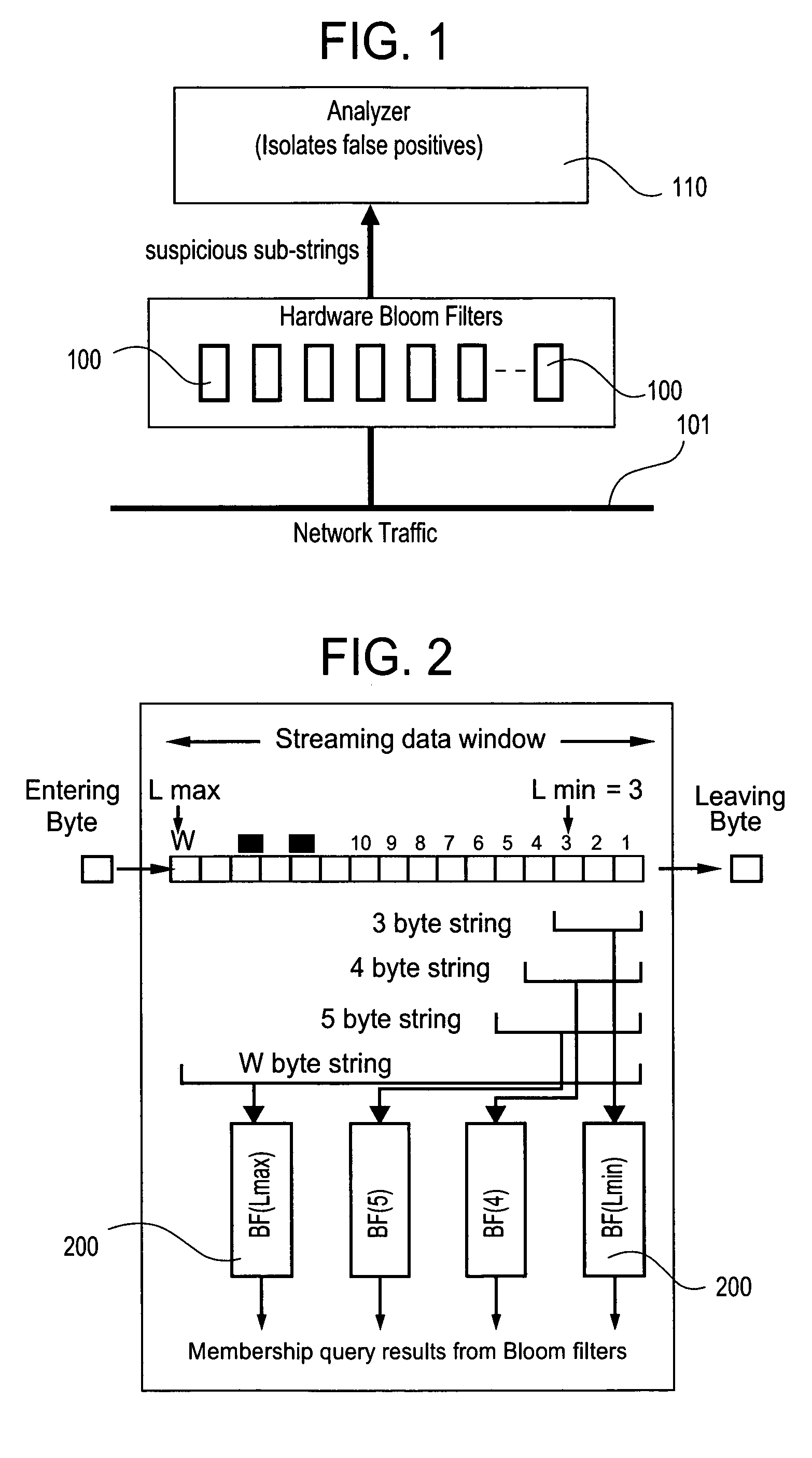
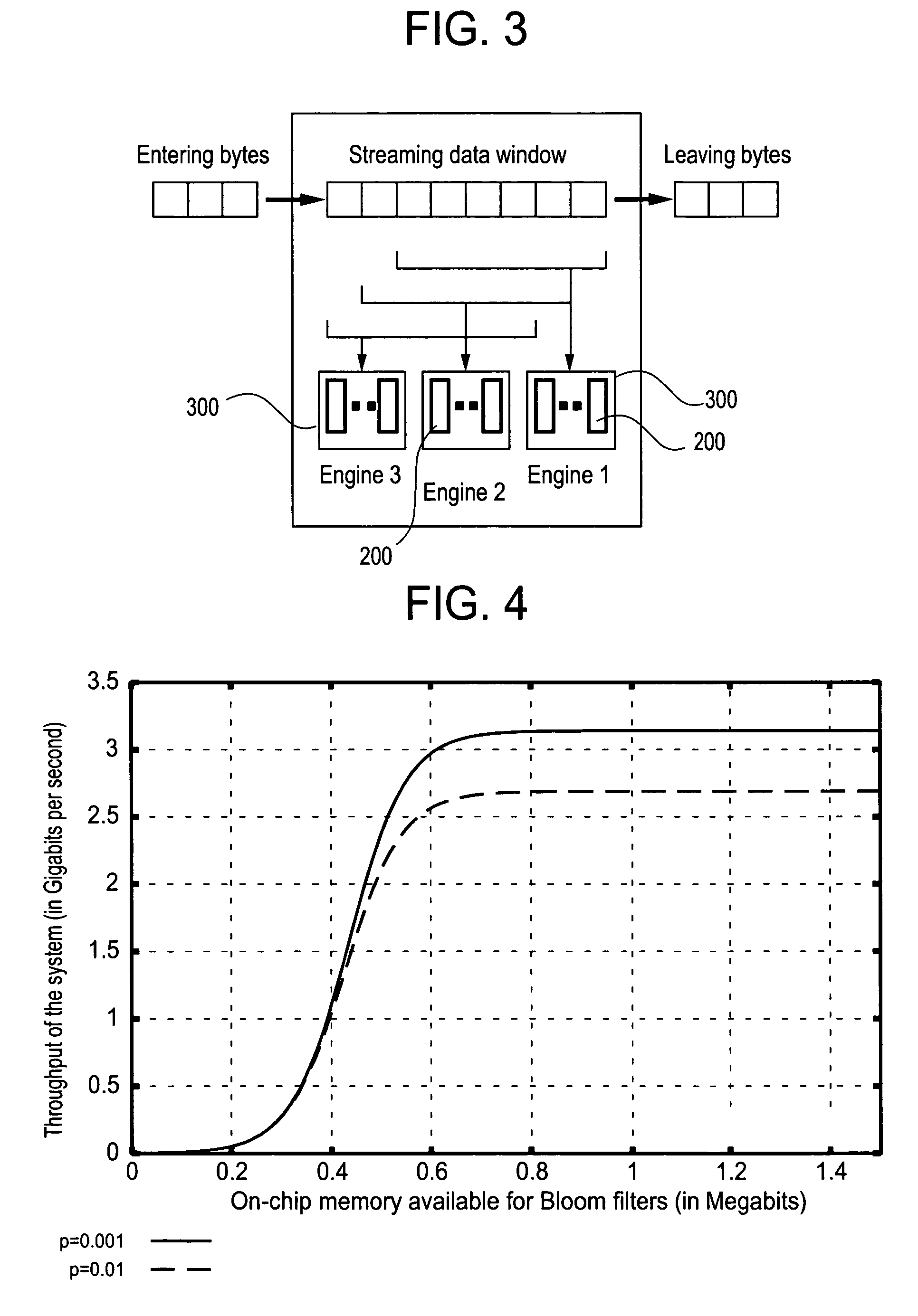
The present invention relates to a method and apparatus based on Bloom filters for detecting predefined signatures (a string of bytes) in a network packet payload. A Bloom filter is a data structure for representing a set of strings in order to support membership queries. Hardware Bloom filters isolate all packets that potentially contain predefined signatures. Another independent process eliminates false positives produced by the Bloom filters. The system is implemented on a FPGA platform, resulting in a set of 10,000 strings being scanned in the network data at the line speed of 2.4 Gbps.
Owner:WASHINGTON UNIV IN SAINT LOUIS
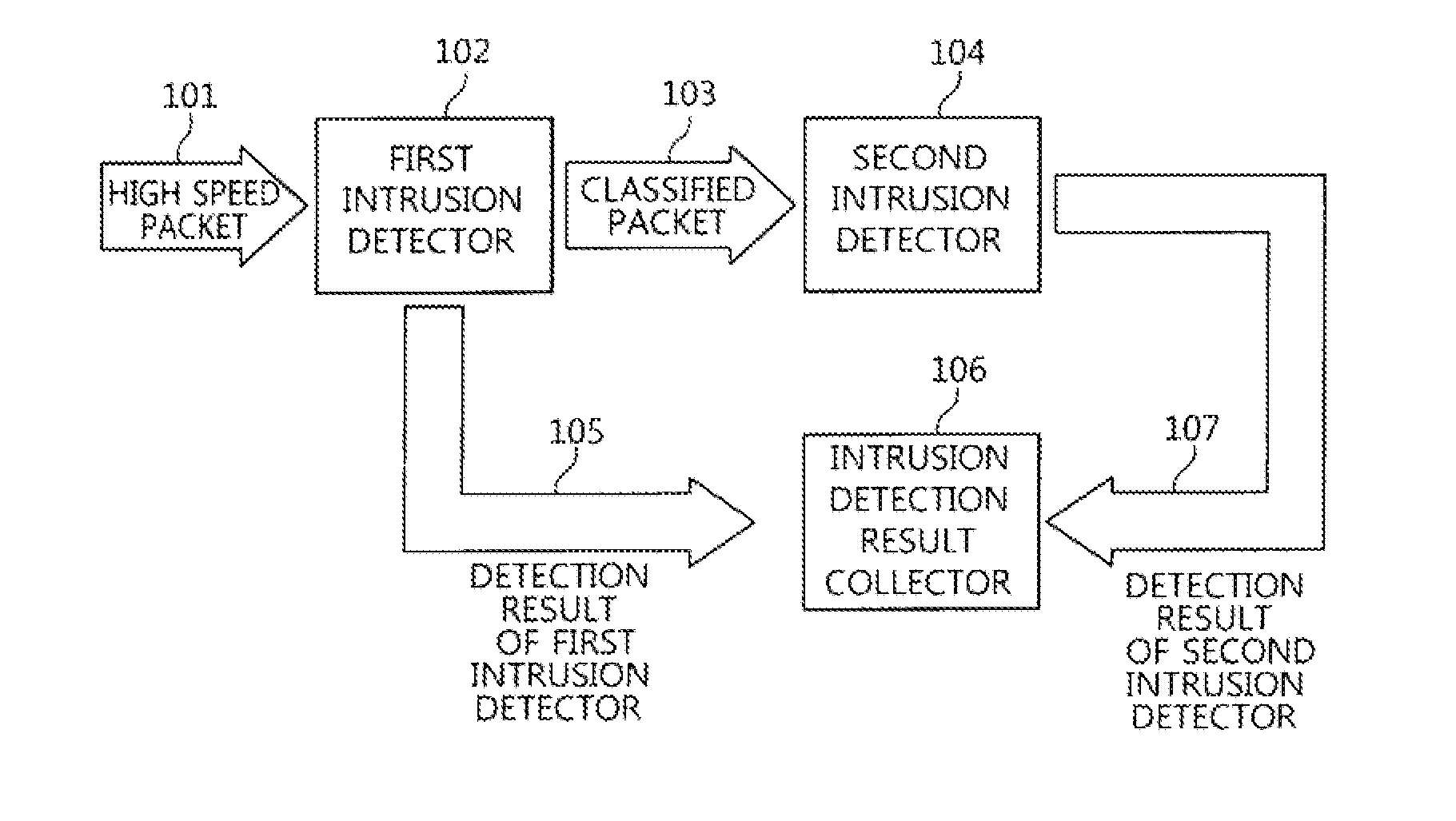
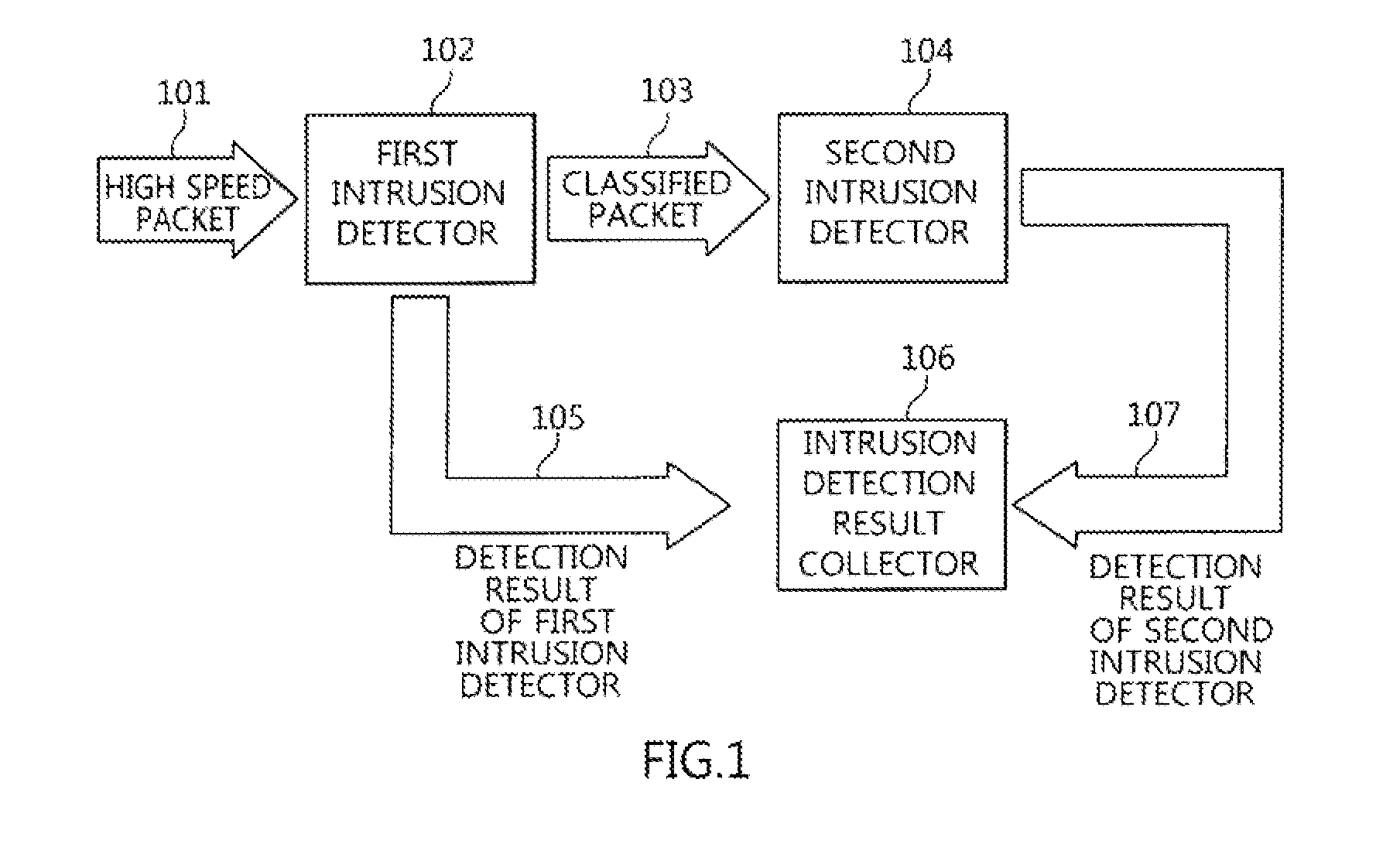
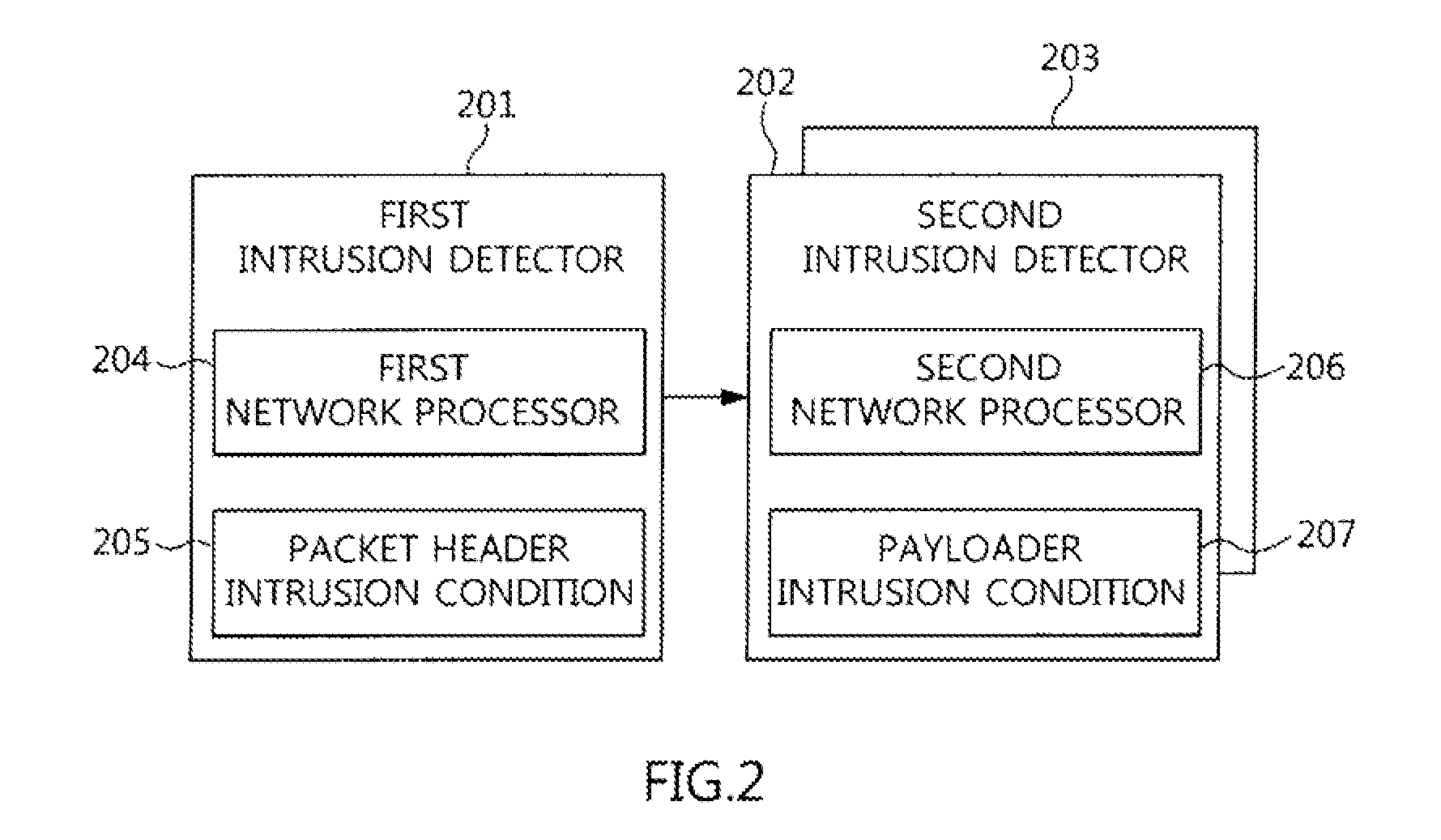
Two-stage intrusion detection system for high-speed packet processing using network processor and method thereof
ActiveUS20130160122A1Memory loss protectionData taking preventionNetwork processorDistributed computing
A system and method for detecting network intrusion by using a network processor are provided. The intrusion detection system includes: a first intrusion detector, configured to use a first network processor to perform intrusion detection on layer 3 and layer 4 of a protocol field among information included in a packet header of a packet transmitted to the intrusion detection system, and when no intrusion is detected, classify the packets according to stream and transmit the classified packets to a second intrusion detector; and a second intrusion detector, configured to use a second network processor to perform intrusion detection through deep packet inspection (DPI) for the packet payload of the packets transmitted from the first intrusion detector. Thereby, intrusion detection for high-speed packets can be performed in a network environment.
Owner:ELECTRONICS & TELECOMM RES INST
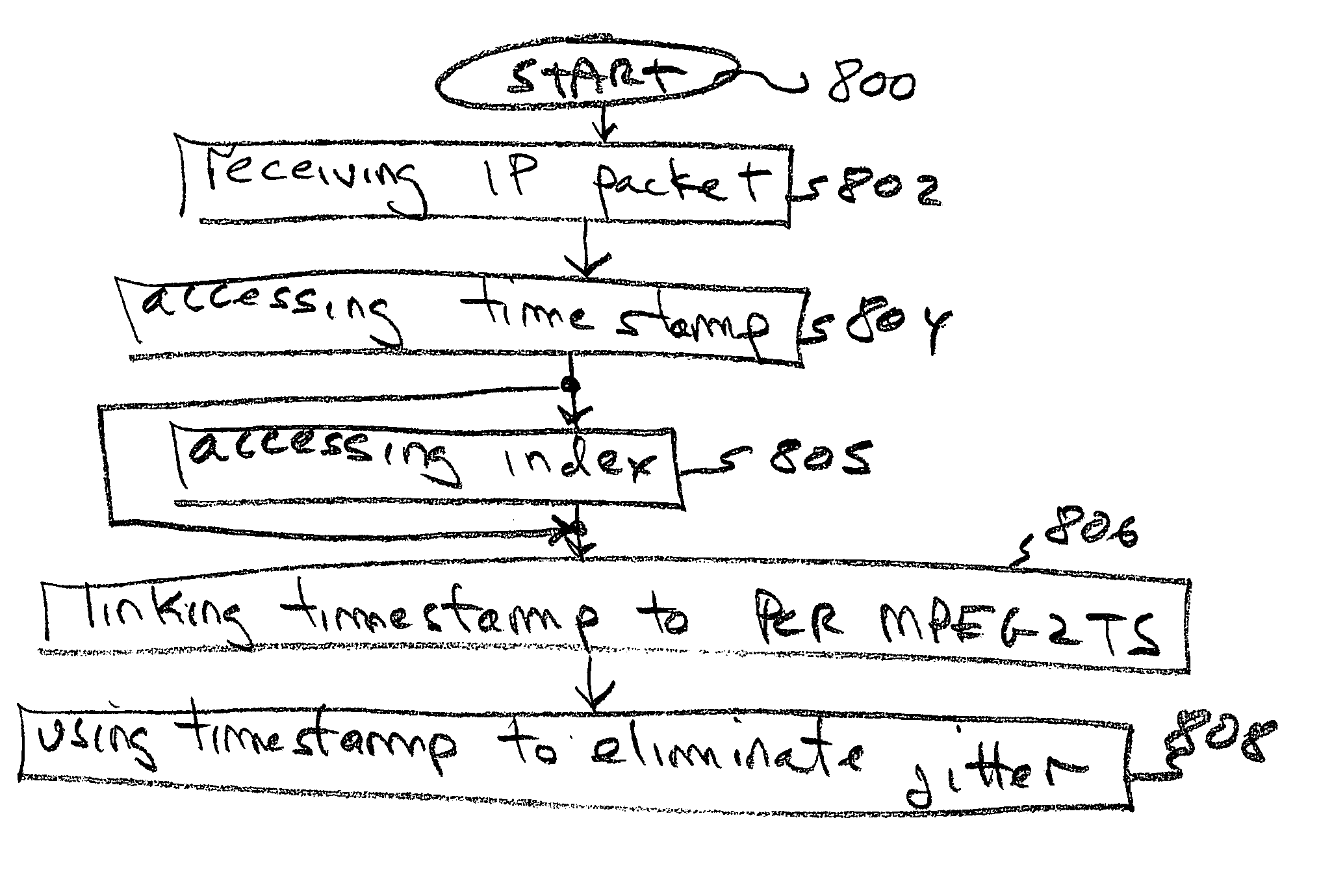
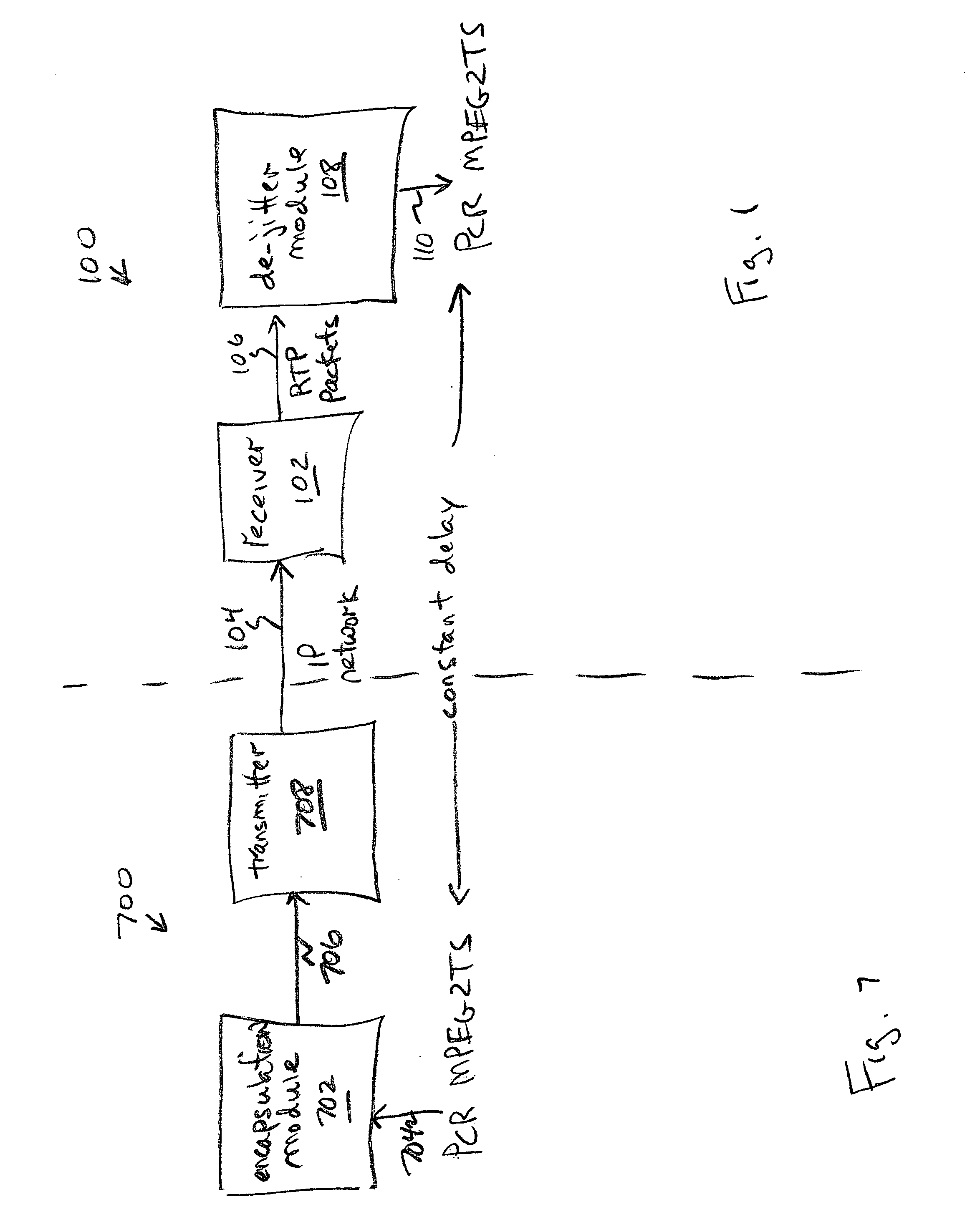
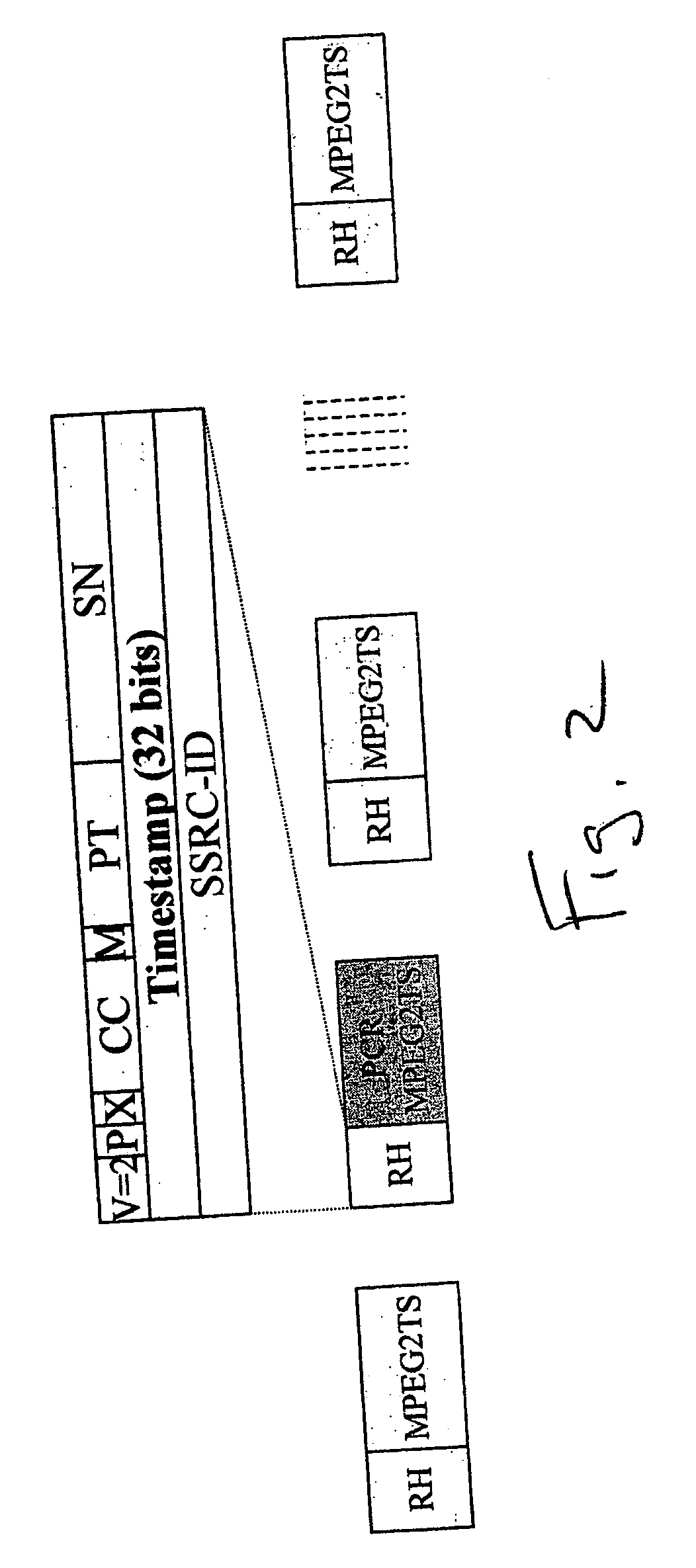
System and method for transporting MPEG2TS in RTP/UDP/IP
InactiveUS20050177643A1Eliminate variable transmission delay jitterError preventionFrequency-division multiplex detailsProgram clock referenceNanosecond
Systems and methods are provided for receiving and transmitting an MPEG2 transport stream (TS) in a real-time protocol (RTP) / user datagram protocol (UDP) / Internet protocol (IP) packet. The receiving method comprises: receiving an IP packet via an IP network, having a variable transmission delay; accessing a timestamp carried in a RTP packet; linking the timestamp with a program clock reference (PCR) MPEG2TS carried in the RTP packet payload; and, using the timestamp to eliminate variable transmission delay jitter, associated with the PCR MPEG2TS. In one aspect of the method, the timestamp has a resolution of greater than 500 nanoseconds (ns), so that the variable transmission delay jitter, associated with the PCR MPEG2TS can be reduced to a jitter of less than 500 ns.
Owner:SHARP KK
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
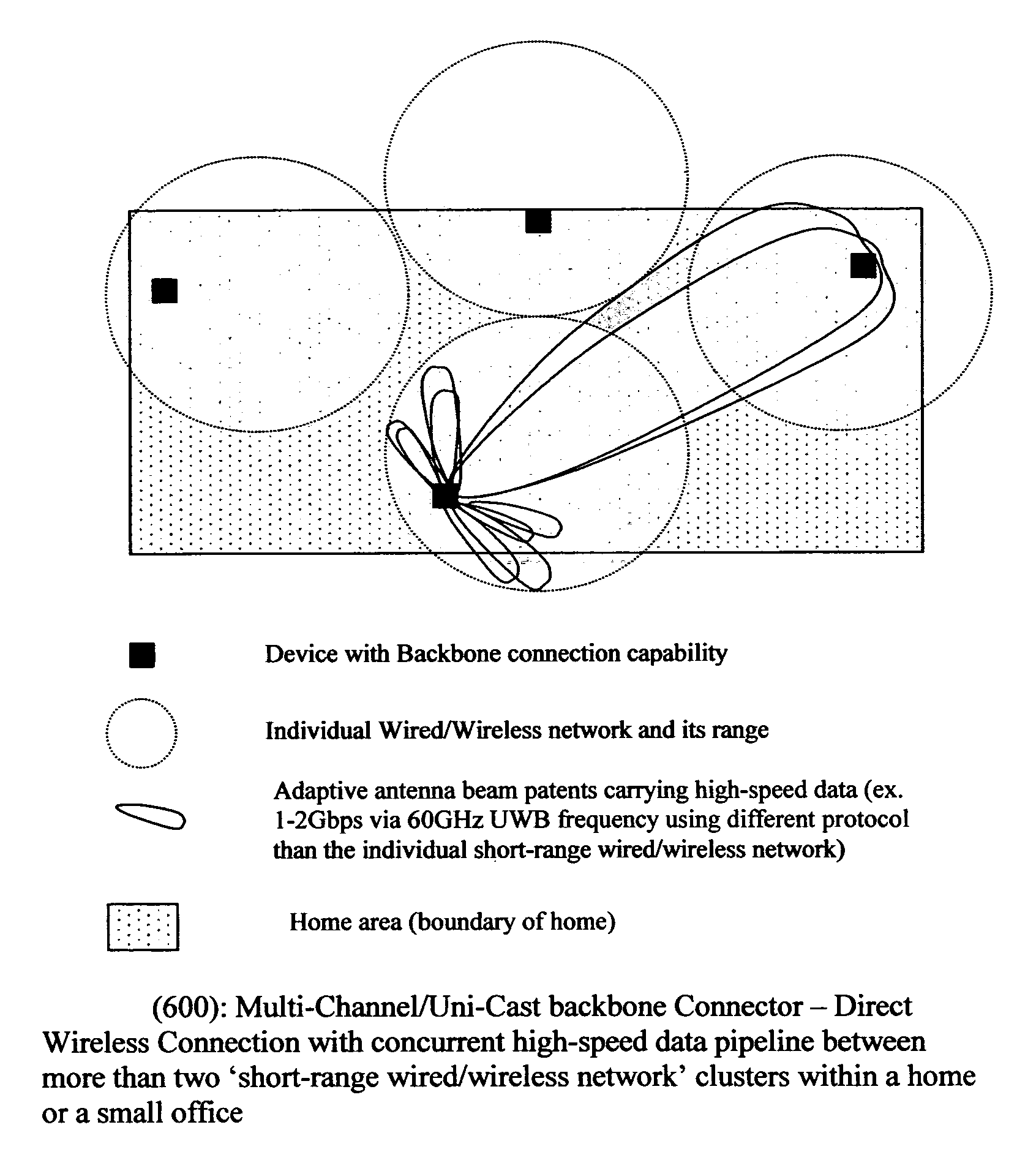
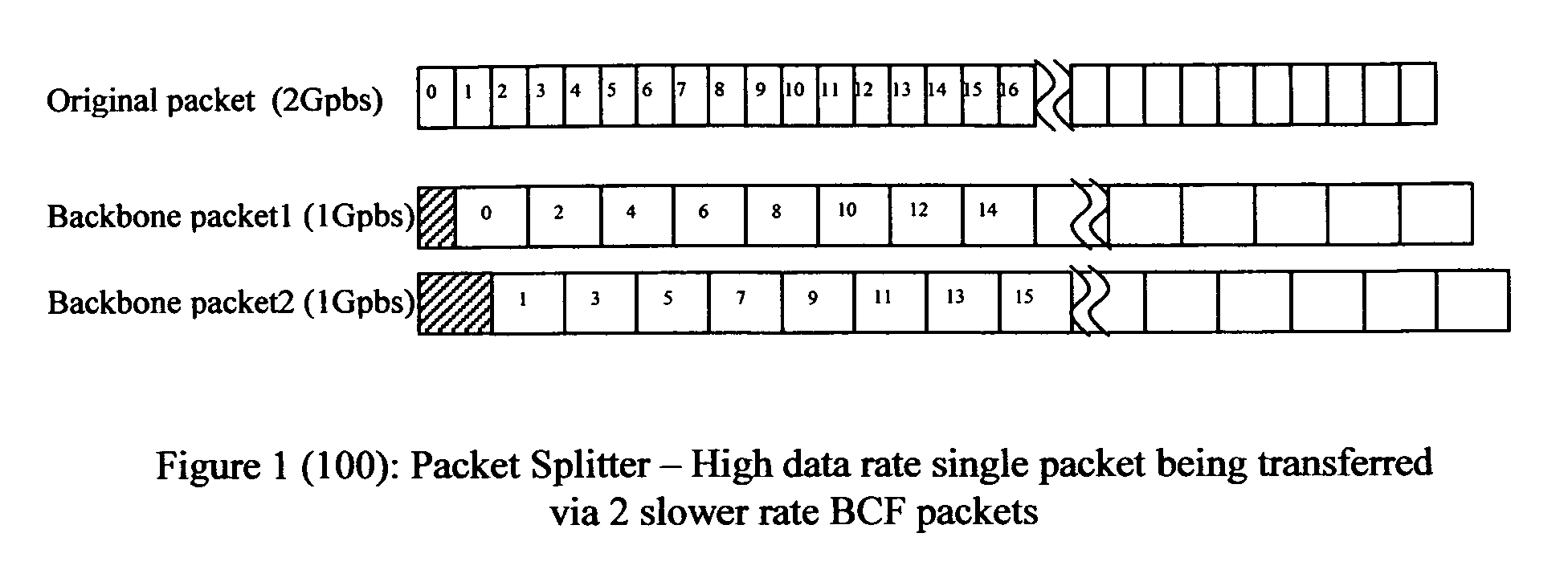
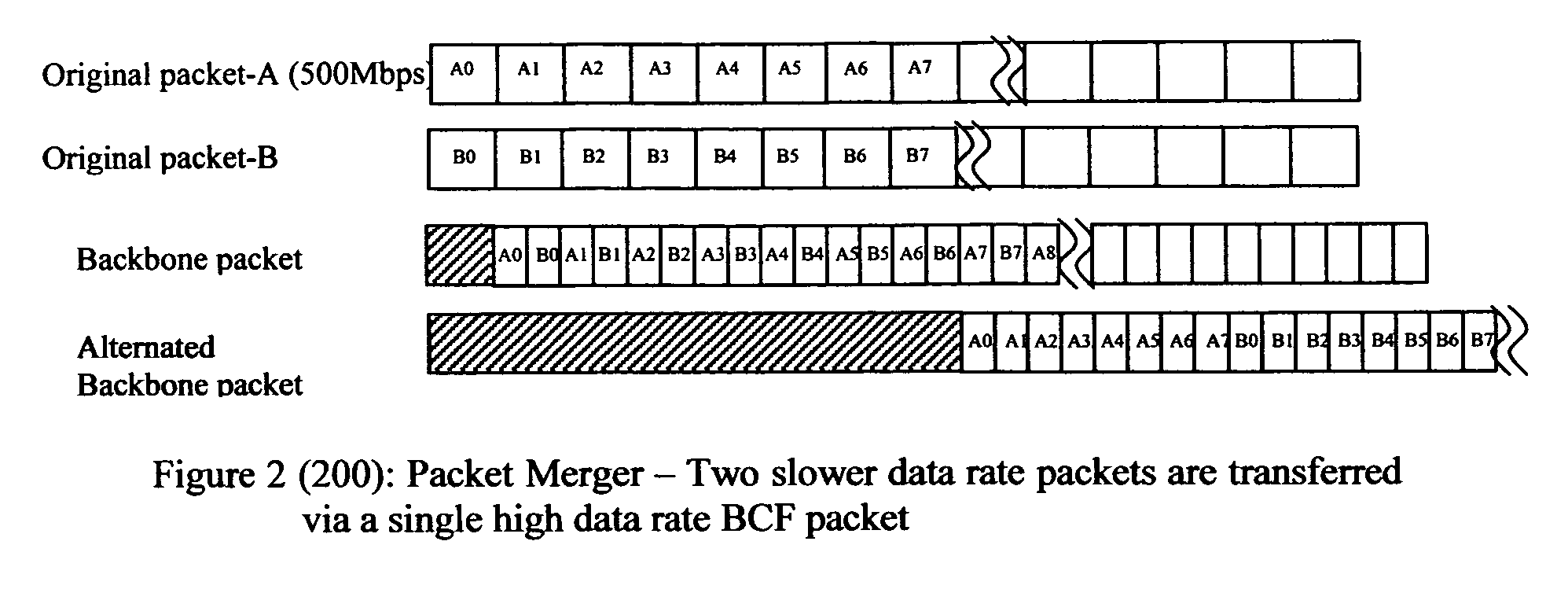
Method of constructing wireless high speed backbone connection that unifies various wired/wireless network clusters by means of employing the smart/adaptive antenna technique and dynamically creating concurrent data pipelines
InactiveUS7672271B2Reduce distractionsMinimize powerMultiplex system selection arrangementsEnergy efficient ICTTransmitted powerData link layer
In accordance with the present invention, there is provided a high-speed wireless backbone connection, Backbone Connection Facilitator (BCF), to create a wireless home network, which may consist of many short-range wired / wireless networks. BCF dynamically creates concurrent data pipelines to meet the data bandwidth demand to transfer packets from one short-range wired / wireless network to another. BCF employs the newly developed antenna technologies (ex. MIMO, SDMA) to minimize the transmit power, to reduce the interferences, and to support the real time communication.BCF contains the BCF-PHY layer, the BCF-Data-Link-Layer, and the BCF-Network-Layer. The BCF-PHY layer consists of antenna array, a PHY Base Band controller, and a digital beam former. The BCF-Data-Link-Layer provides the MAC functionality. The BCF-Network-Layer assembles the packet, provides the source and destination address, and provides the BCF-PHY beam forming information. The BCF-Network-Layer is also responsible for parsing and assembling the packet payloads for the high-speed backbone connection.
Owner:LEE HYUN
Systems and methods for processing data flows
InactiveUS20080133517A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Method for thwarting application layer hypertext transport protocol flood attacks focused on consecutively similar application-specific data packets
ActiveUS20140289854A1Effective thwartingDifferent level of accuracyMemory loss protectionError detection/correctionThe InternetComputerized system
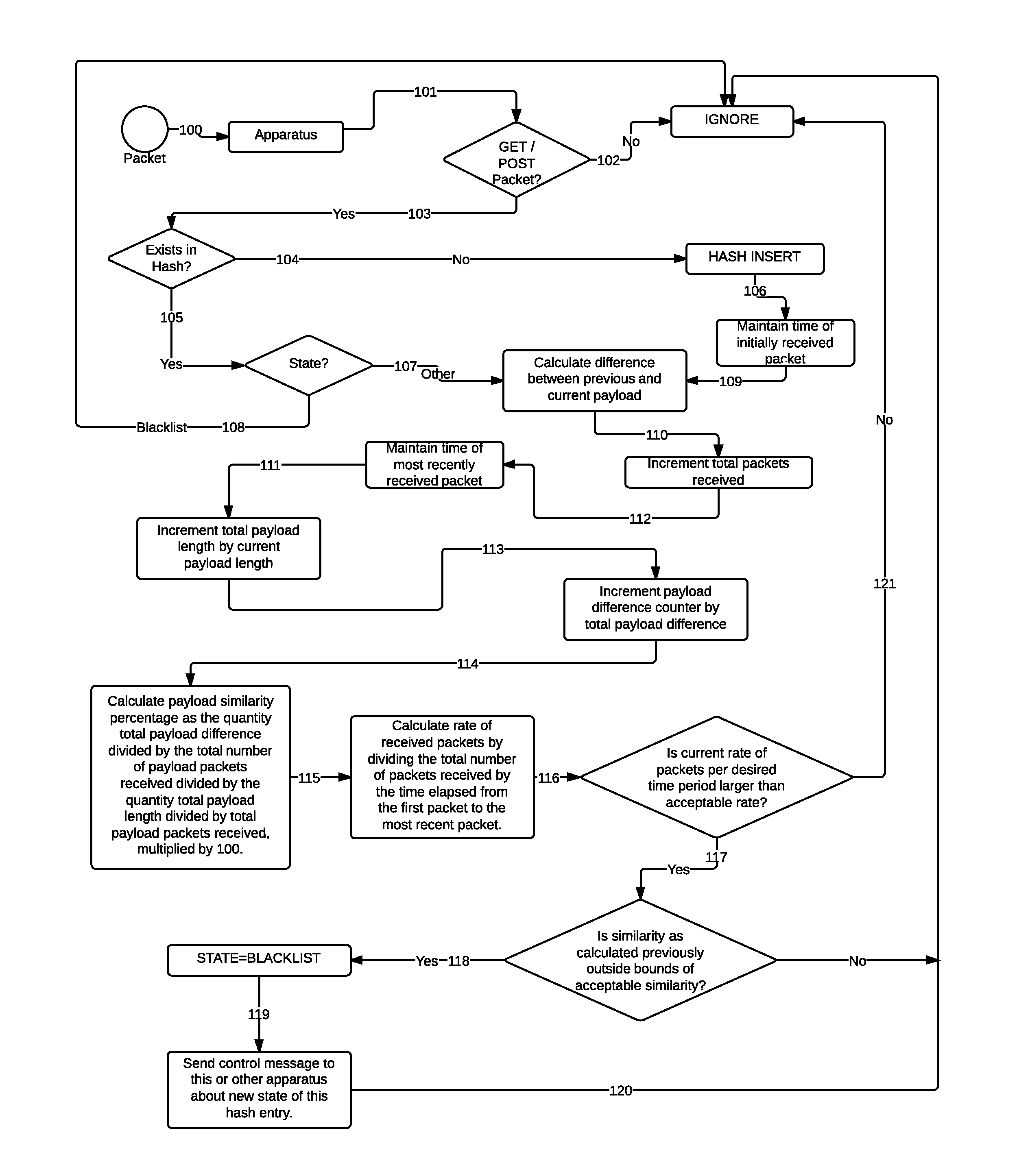
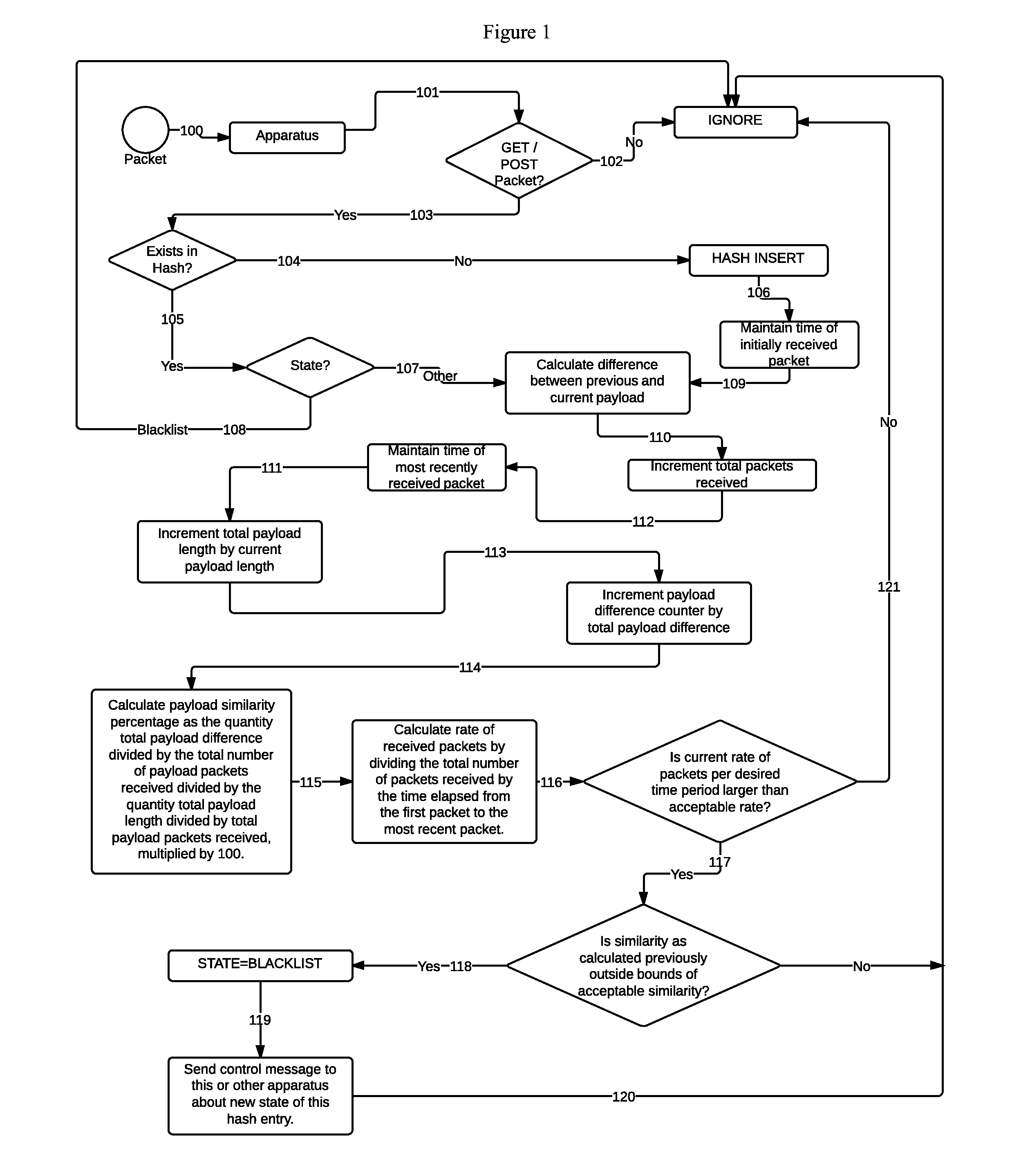
The present invention provides a methodology to thwart attacks that utilize consecutive hypertext transport protocol packets with similar structures, arriving from a plurality of computer systems on a network, such as the Internet, destined for a single or more computer systems on a secondary network, at such a rate with sufficient complexity to produce an effect on the target computer system or systems such that legitimate clients are denied access to requested services, thus creating a “denial of service” situation. The methodology focuses on the dynamic and proactive reassessment of data packet payload content to maintain a running value of similarity or dissimilarity, thus permitting intermediary apparatuses that are performing this computation to create distinction between legitimate clients and illegitimate clients.
Owner:MAHVI MEHDI
Systems and methods for processing data flows
InactiveUS8010469B2Increased complexityAvoid problemsMemory loss protectionError detection/correctionData streamSelf-organizing map
Methods and systems for flow processing and switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security are described. Such flow processing facilities may be used for inspecting network traffic packet payloads to detect security threats and intrusions across accessible layers of the network IP stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources.
Owner:CA TECH INC
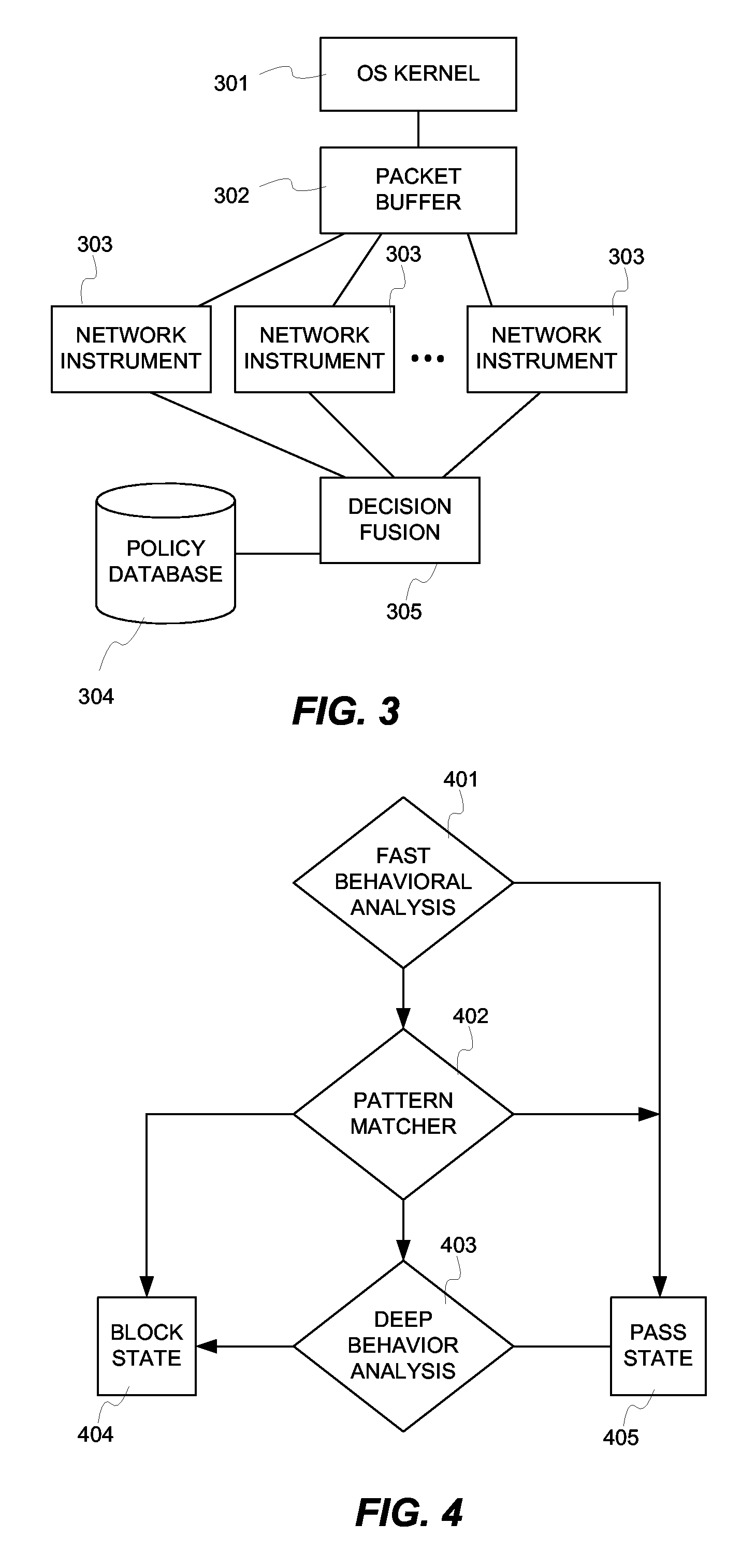
Fusion instrusion protection system
InactiveUS20070056038A1Solve the high false positive rateEfficient Anomaly DetectionMemory loss protectionError detection/correctionAnomaly detectionSensor fusion
An intrusion protection system that fuses a network instrumentation classification with a packet payload signature matching system. Each of these kinds of systems is independently capable of being effectively deployed as an anomaly detection system. By employing sensor fusion techniques to combine the instrumentation classification approach with the signature matching approach, the present invention provides an intrusion protection system that is uniquely capable of detecting both well known and newly developed threats while having an extremely low false positive rate.
Owner:LOK TECH
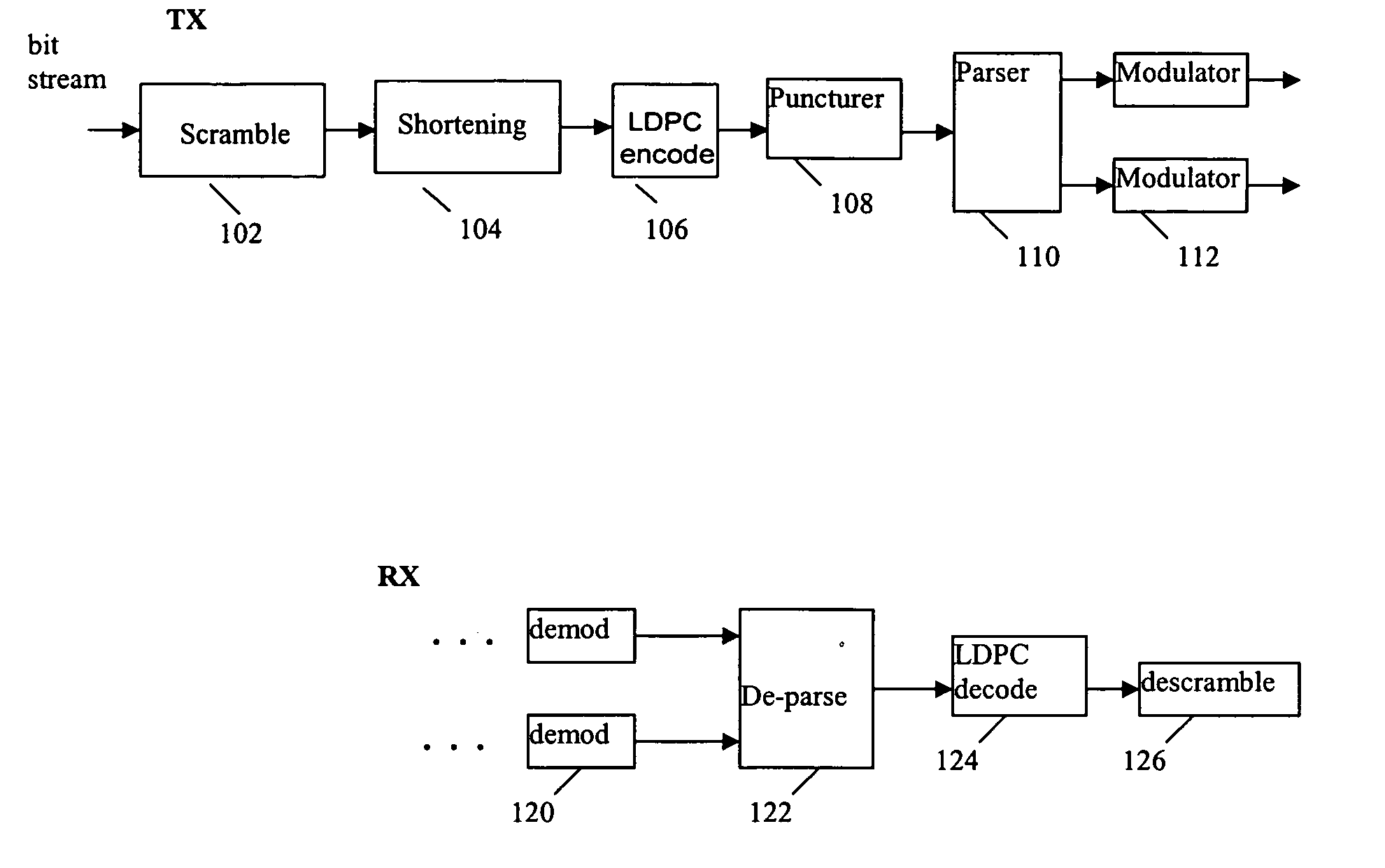
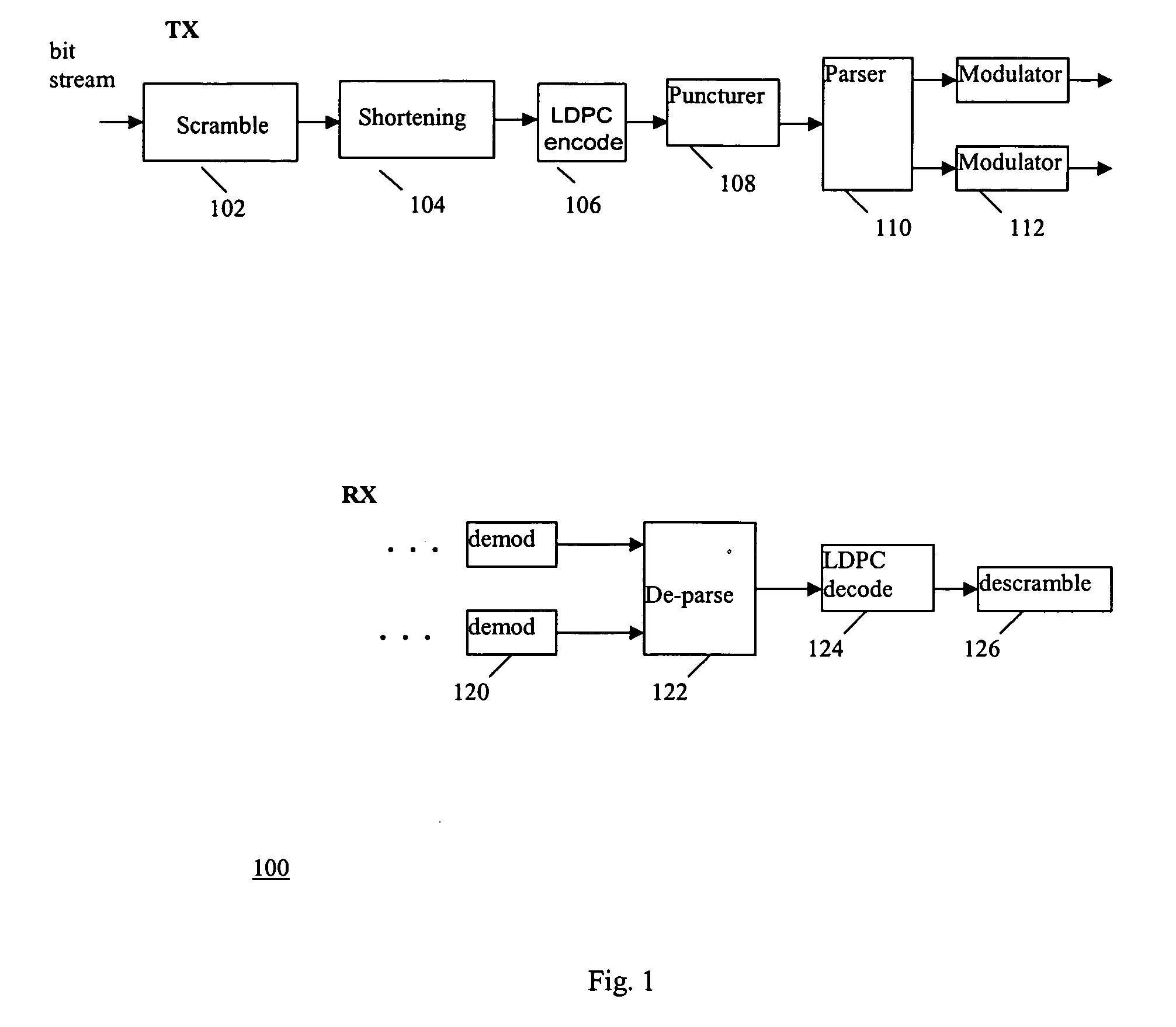
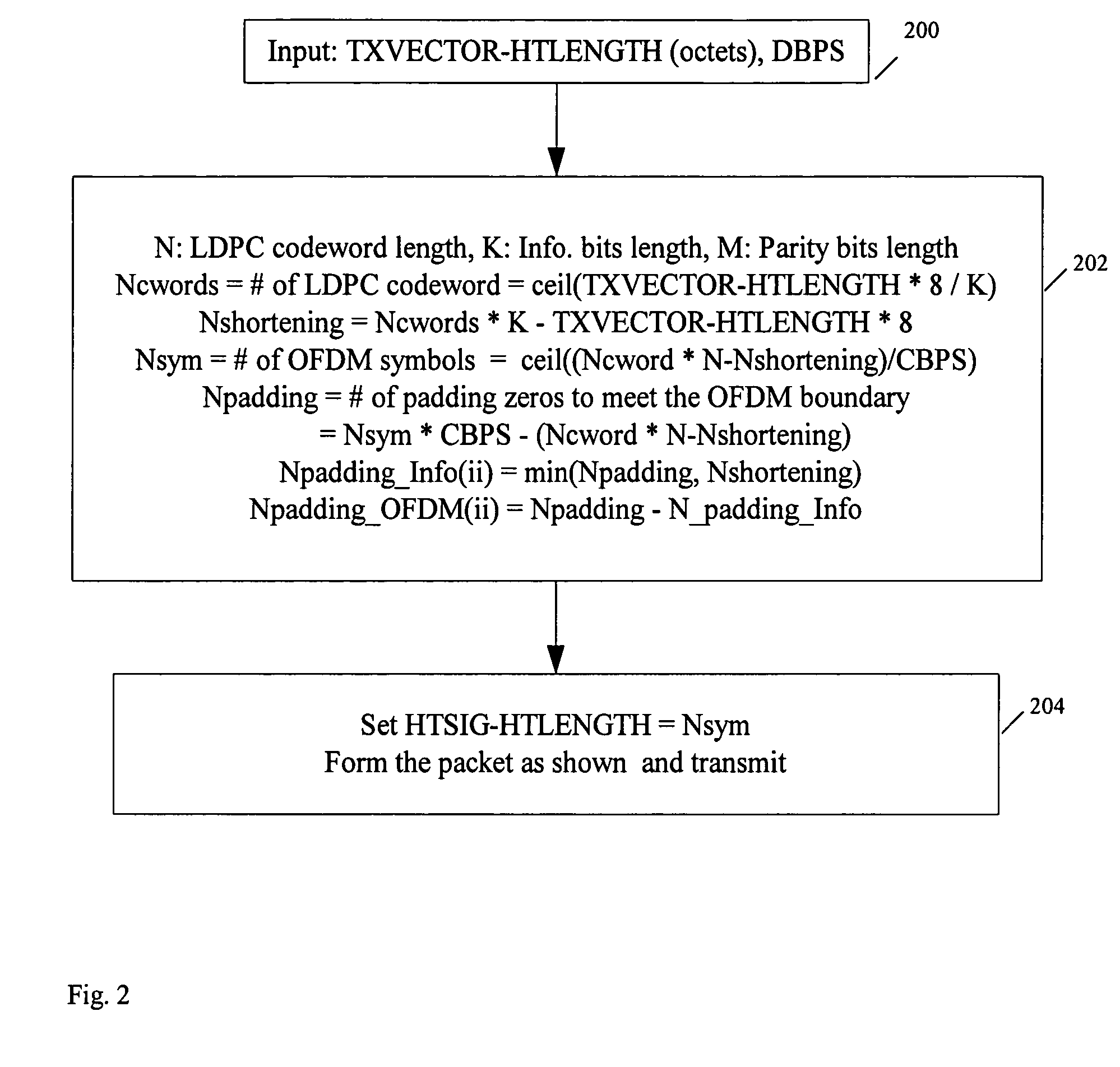
LDPC concatenation rules for IEEE 802.11n system with packets length specified in OFDM symbols
InactiveUS20070143655A1Data representation error detection/correctionError preventionByteConcatenation
A method of concatenation for LDPC encoding in an OFDM wireless system selects codewords based on the data packet payload size, wherein the payload size is the number of transmitted information bits in octets. For low transmission rates, shortening and puncturing across all codewords within the packet is applied to minimize OFDM symbol padding. For high transmission rates, only shortening across all codewords within the packet is applied to minimize OFDM symbol padding.
Owner:SAMSUNG ELECTRONICS CO LTD
Method and apparatus for detecting predefined signatures in packet payload using Bloom filters
ActiveUS7444515B2Digital data processing detailsUser identity/authority verificationBloom filterNetwork data
The present invention relates to a method and apparatus based on Bloom filters for detecting predefined signatures (a string of bytes) in a network packet payload. A Bloom filter is a data structure for representing a set of strings in order to support membership queries. Hardware Bloom filters isolate all packets that potentially contain predefined signatures. Another independent process eliminates false positives produced by the Bloom filters. The system is implemented on a FPGA platform, resulting in a set of 10,000 strings being scanned in the network data at the line speed of 2.4 Gbps.
Owner:WASHINGTON UNIV IN SAINT LOUIS
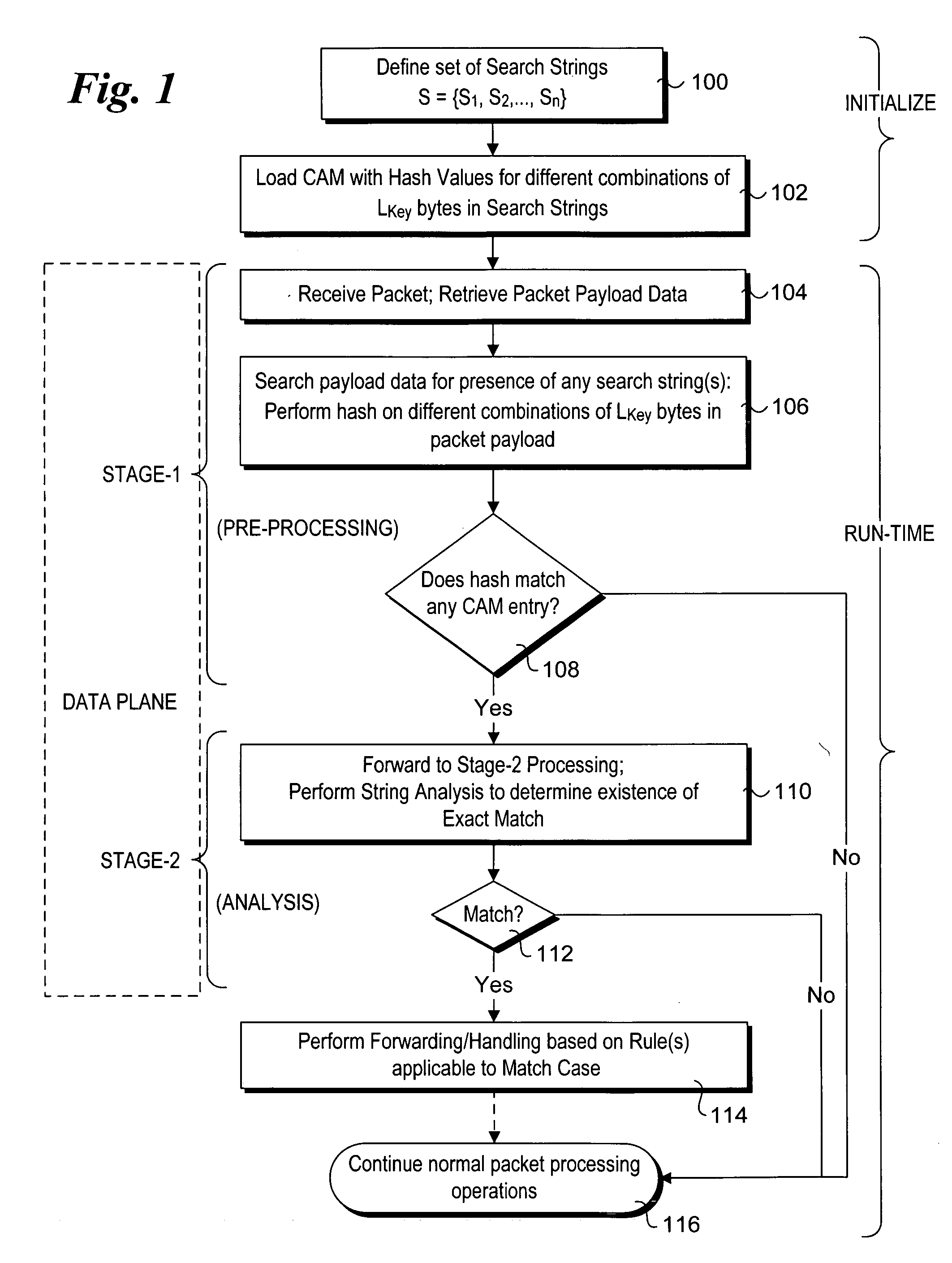
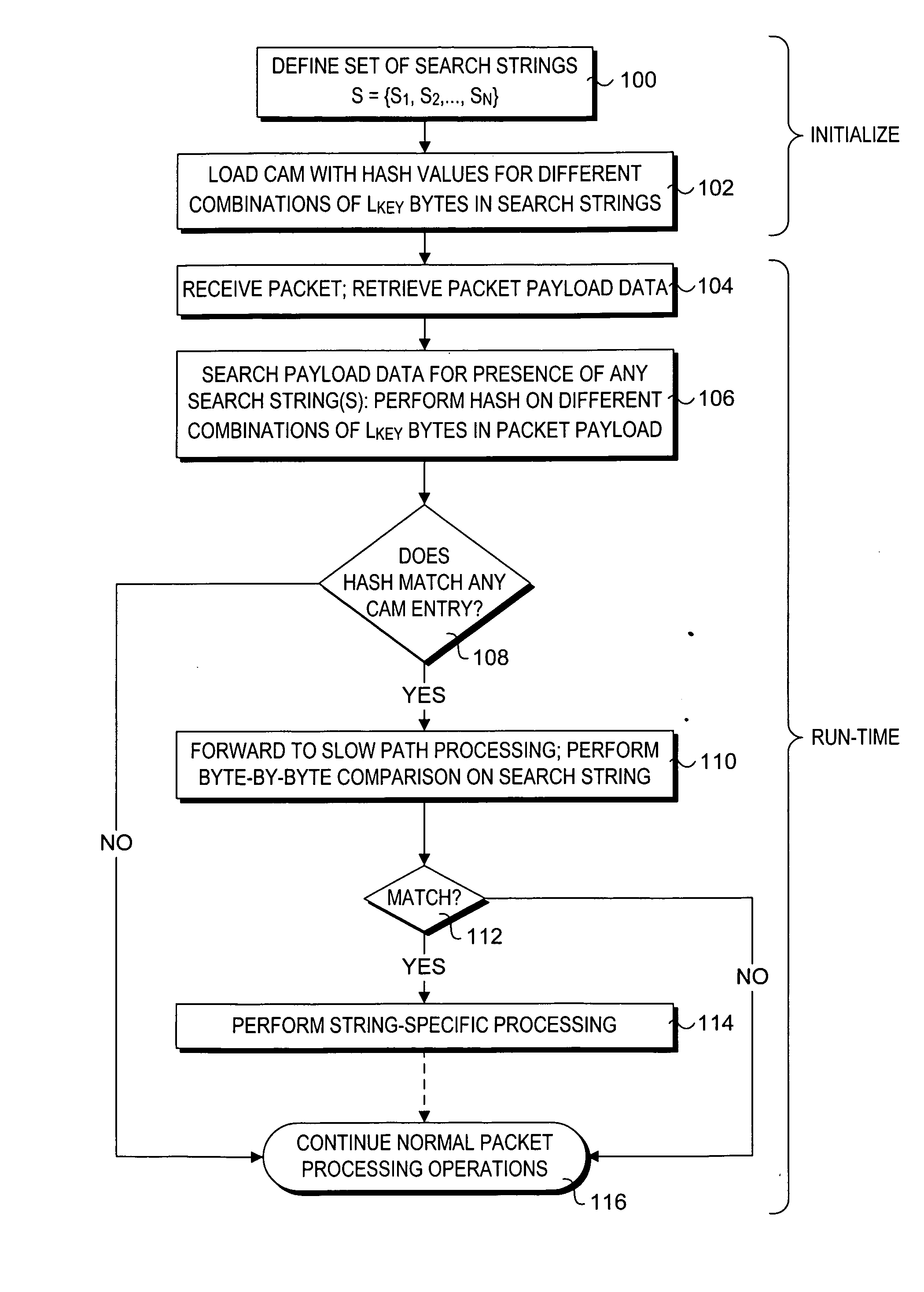
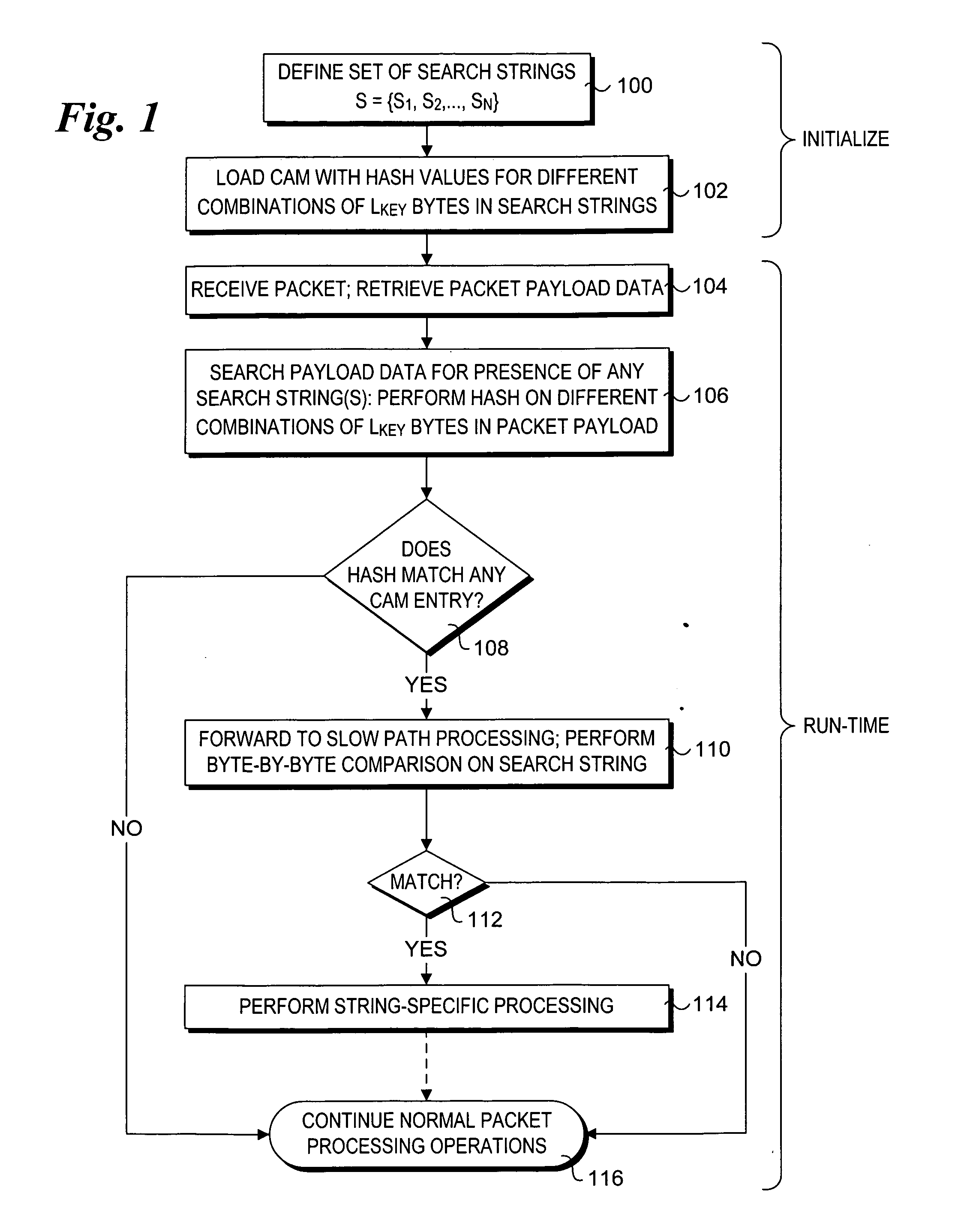
Method to perform exact string match in the data plane of a network processor
InactiveUS20070115986A1Digital computer detailsData switching by path configurationData packLine rate
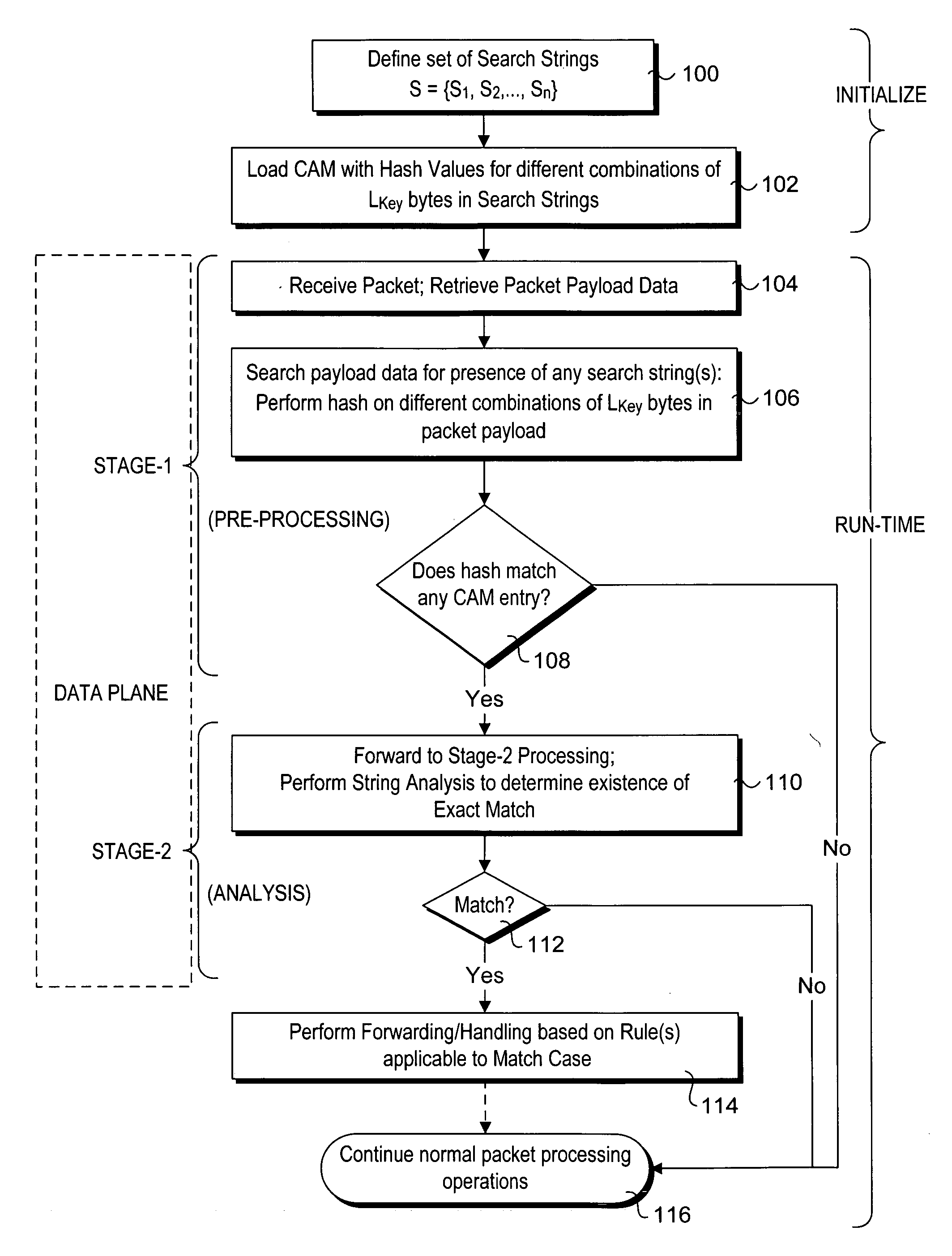
Methods for performing exact search string matches in the data plane of a network processor. The methods employ a two-stage string search mechanism to identify the existence of a search string from a set S in a packet payload. A first pre-processing stage identifies a potential search string match and a second analysis stage determines whether the first stage match corresponds to an exact string match. The first stage is implemented using hash values derived from at least one of search strings in set S or sub-strings of those search strings. In one embodiment, a plurality of Bloom filters are used to perform the first pre-processing stage, while in other embodiments various CAM-based technique are used. Various TCAM-based schemes are disclosed for performing the second analysis stage. The methods enable packet payloads to be searched for search strings at line-rate speeds.
Owner:INTEL CORP
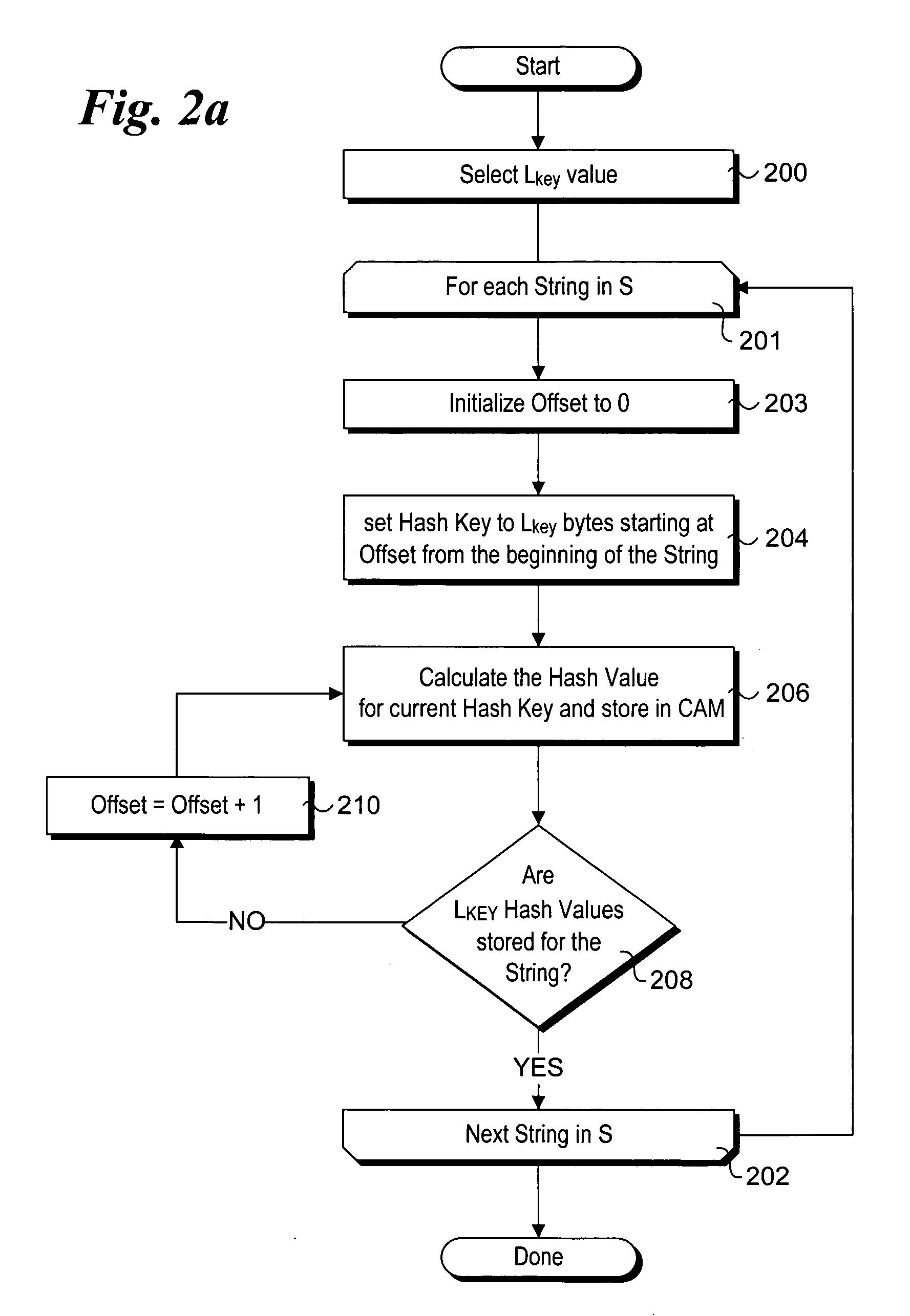
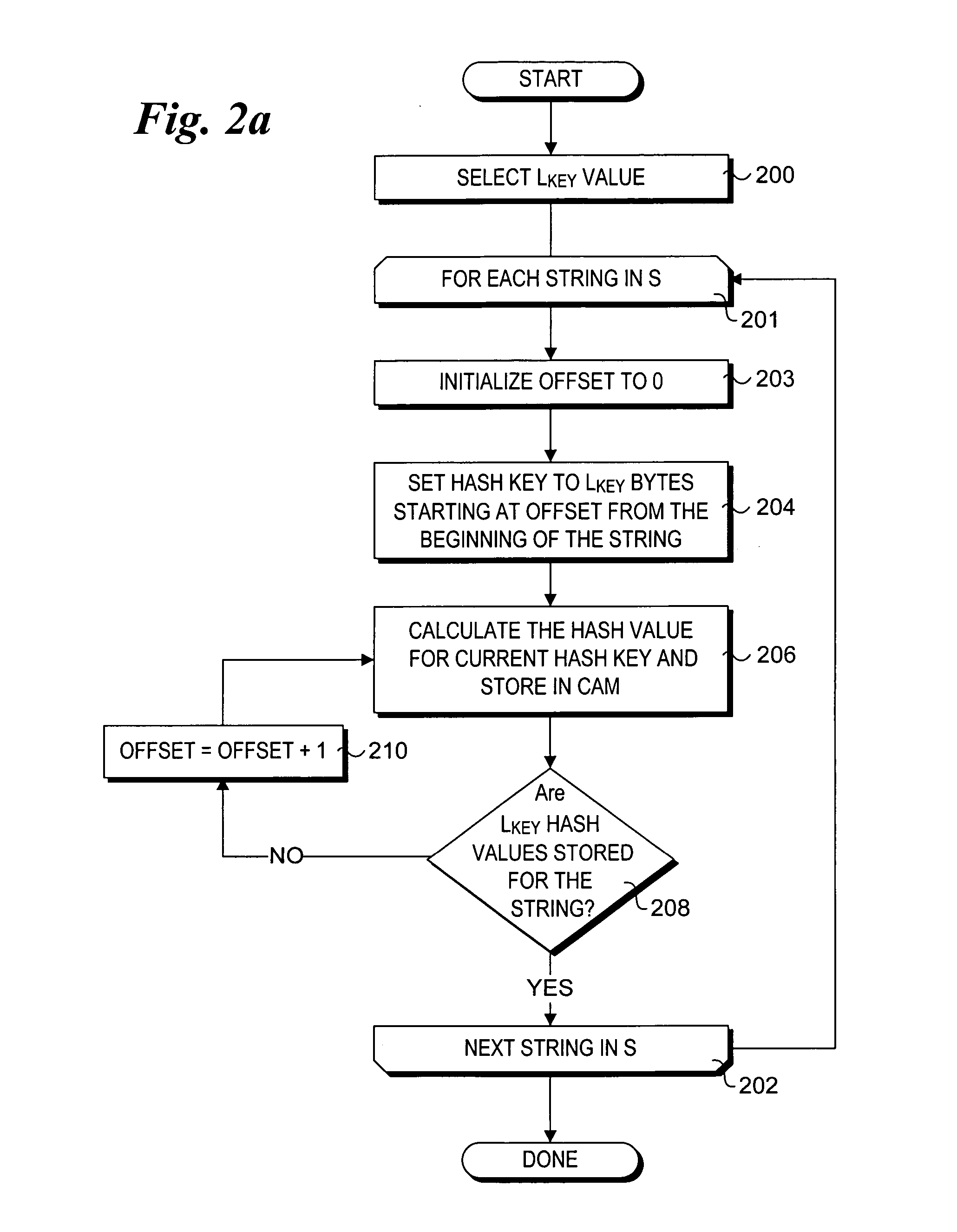
Efficient CAM-based techniques to perform string searches in packet payloads
InactiveUS20060212426A1TransmissionSpecial data processing applicationsData packTheoretical computer science
Efficient Content Addressable Memory (CAM)-based techniques for performing string searches in packet payloads. Hashes are performed on hash keys comprising overlapping sub-strings in one or more search strings. The resulting hash values are stored in a CAM. During packet processing operations, a search of the packet payload data is made to determine if any of the search strings are present. Hashes are performed on non-overlapping sub-strings in the payload data, and the hash results are submitted to the CAM for comparison with the previously-generated search string hash values. If no CAM hits result, the payload data does not contain any of the search strings, while a CAM hit indicates that at least one of the search strings might be present in the payload data. In this instance, a full string comparison is made between the search strings (or an identified search string) and strings in the payload data to verify whether a search string is actually present.
Owner:INTEL CORP
Data transfer efficiency in a cryptography accelerator system
InactiveUS20030226018A1User identity/authority verificationInternal/peripheral component protectionCryptographic acceleratorChecksum
Methods and apparatus are provided for performing authentication and decryption operations in a cryptography accelerator system. Input data passed to a cryptography accelerator from a host such a CPU includes information for a cryptography accelerator to determine where to write the processed data. In one example, processed data is formatted as packet payloads in a network buffer. Checksum information is precalculated and an offset for a header is maintained.
Owner:AVAGO TECH INT SALES PTE LTD
Multi-output packet server with independent streams
InactiveUS20070233891A1Data representation error detection/correctionCode conversionData setClient-side
A method of serving content to multiple clients via a network is provided. Independent sessions with each of a plurality of clients are maintained, wherein the number of clients in the plurality of clients can vary over time, and wherein the start of each session and the end of each session can be independent of the start and end of other sessions. A stream of packet payloads is received, each packet payload of the stream of packet payloads including data generated from the content, wherein each packet payload in at least a subset of the stream of packet payloads includes a different set of data. Each packet payload in the stream of packet payloads is transmitted to each client of the plurality of clients in corresponding packets, wherein the packet payload transmitted to a client at any particular time is independent of the state of the corresponding session.
Owner:QUALCOMM INC
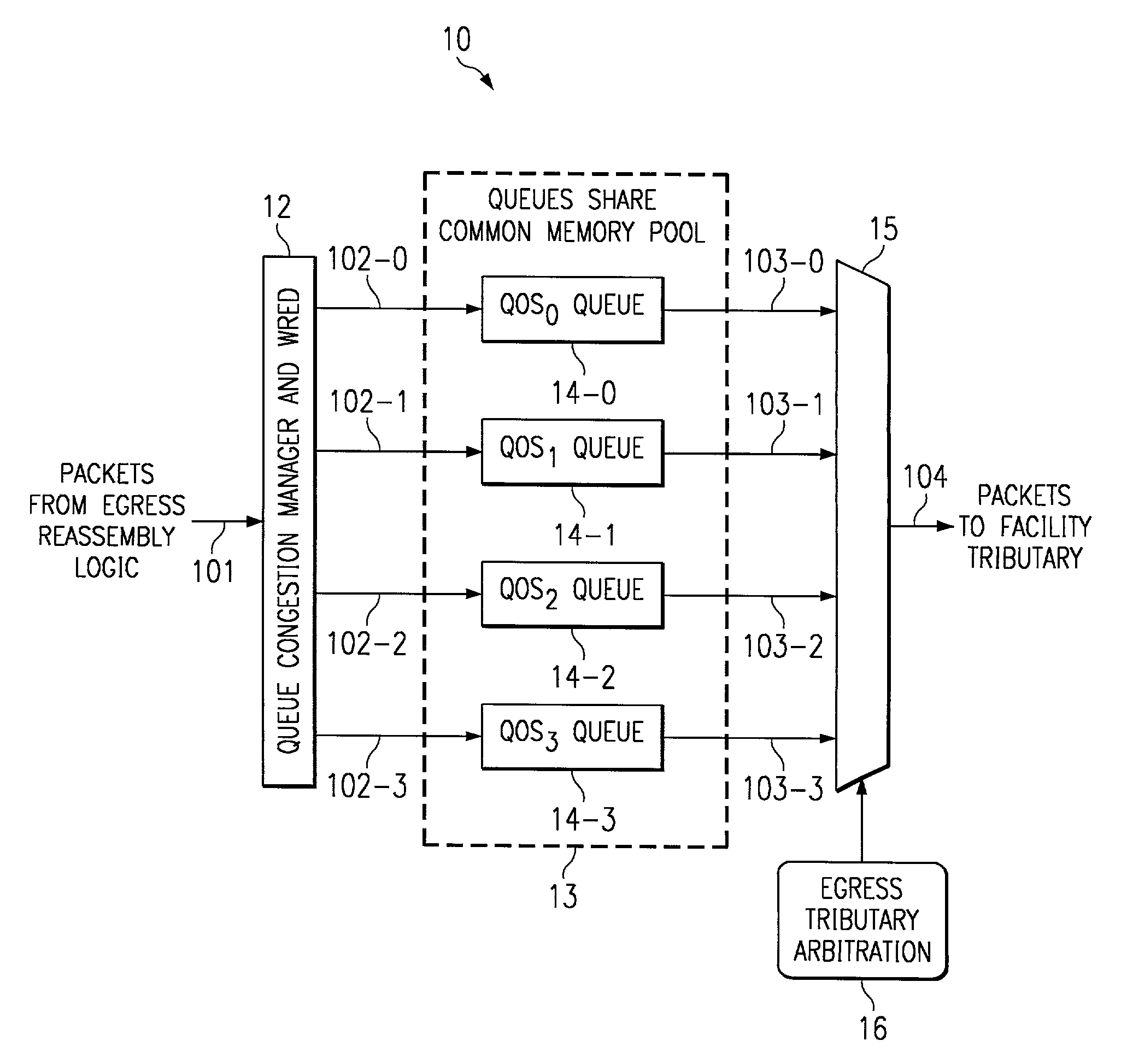
System and method for router queue and congestion management
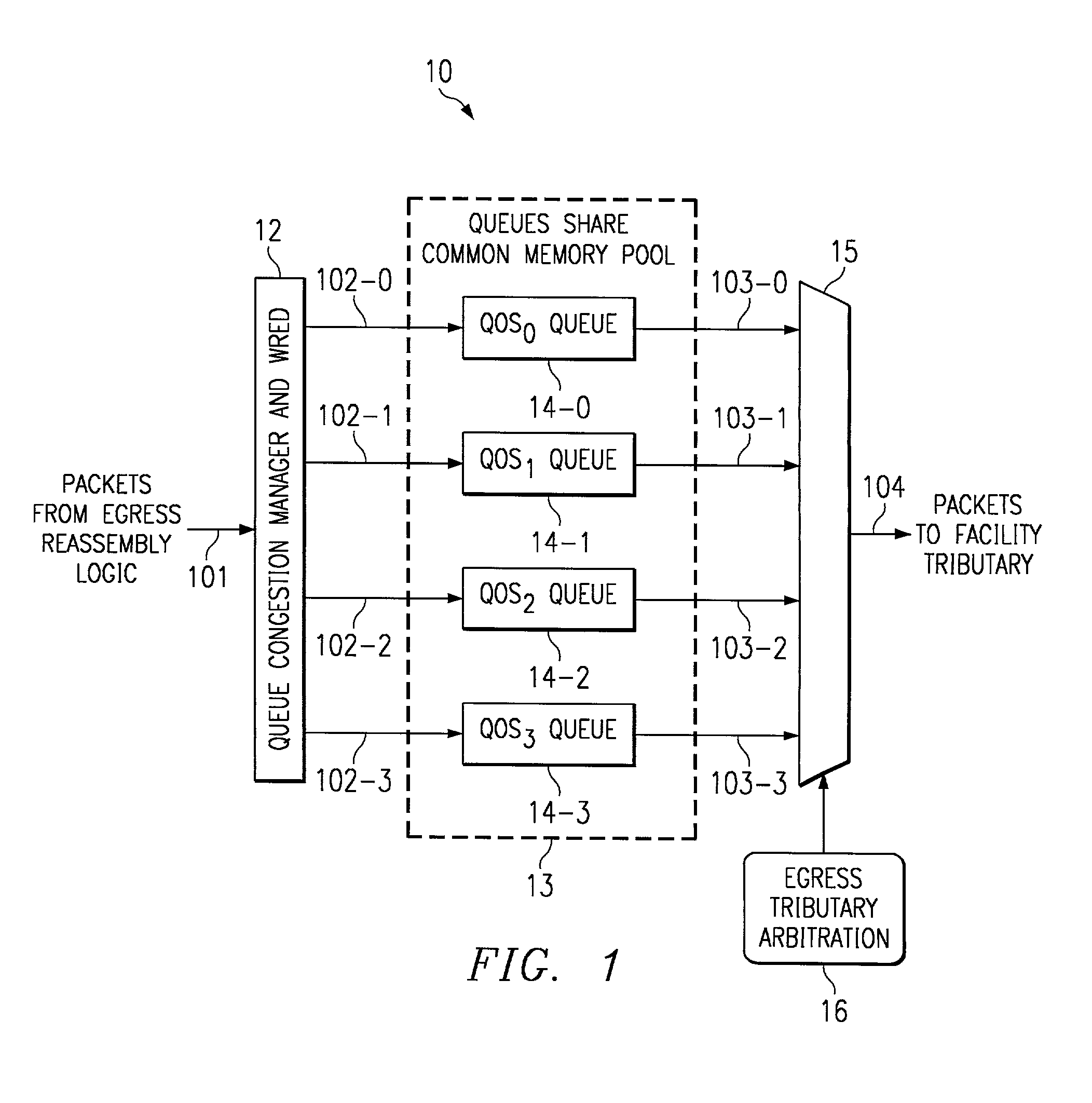
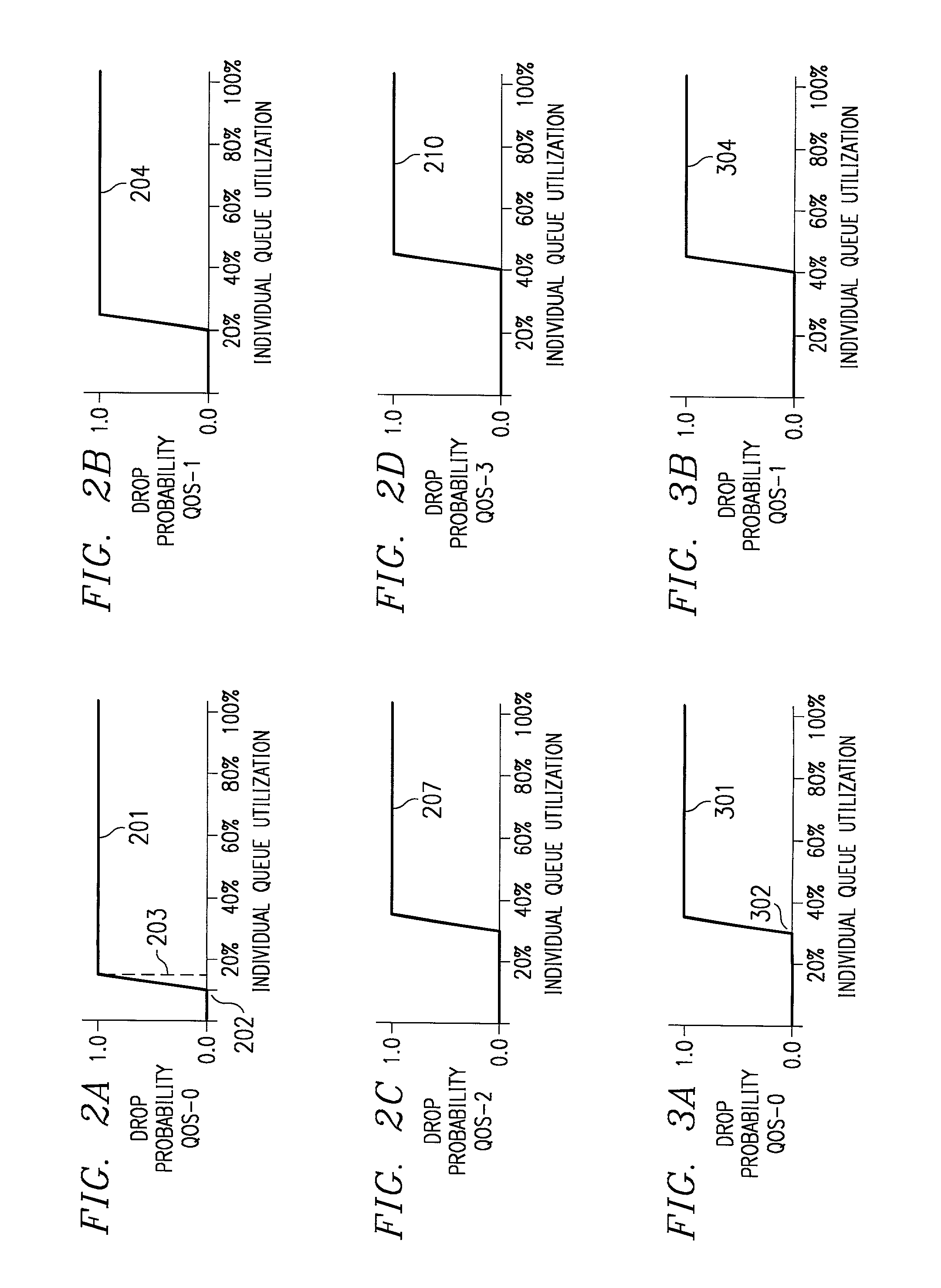
In a multi-QOS level queuing structure, packet payload pointers are stored in multiple queues and packet payloads in a common memory pool. Algorithms control the drop probability of packets entering the queuing structure. Instantaneous drop probabilities are obtained by comparing measured instantaneous queue size with calculated minimum and maximum queue sizes. Non-utilized common memory space is allocated simultaneously to all queues. Time averaged drop probabilities follow a traditional Weighted Random Early Discard mechanism. Algorithms are adapted to a multi-level QOS structure, floating point format, and hardware implementation. Packet flow from a router egress queuing structure into a single egress port tributary is controlled by an arbitration algorithm using a rate metering mechanism. The queuing structure is replicated for each egress tributary in the router system.
Owner:AVAGO TECH INT SALES PTE LTD
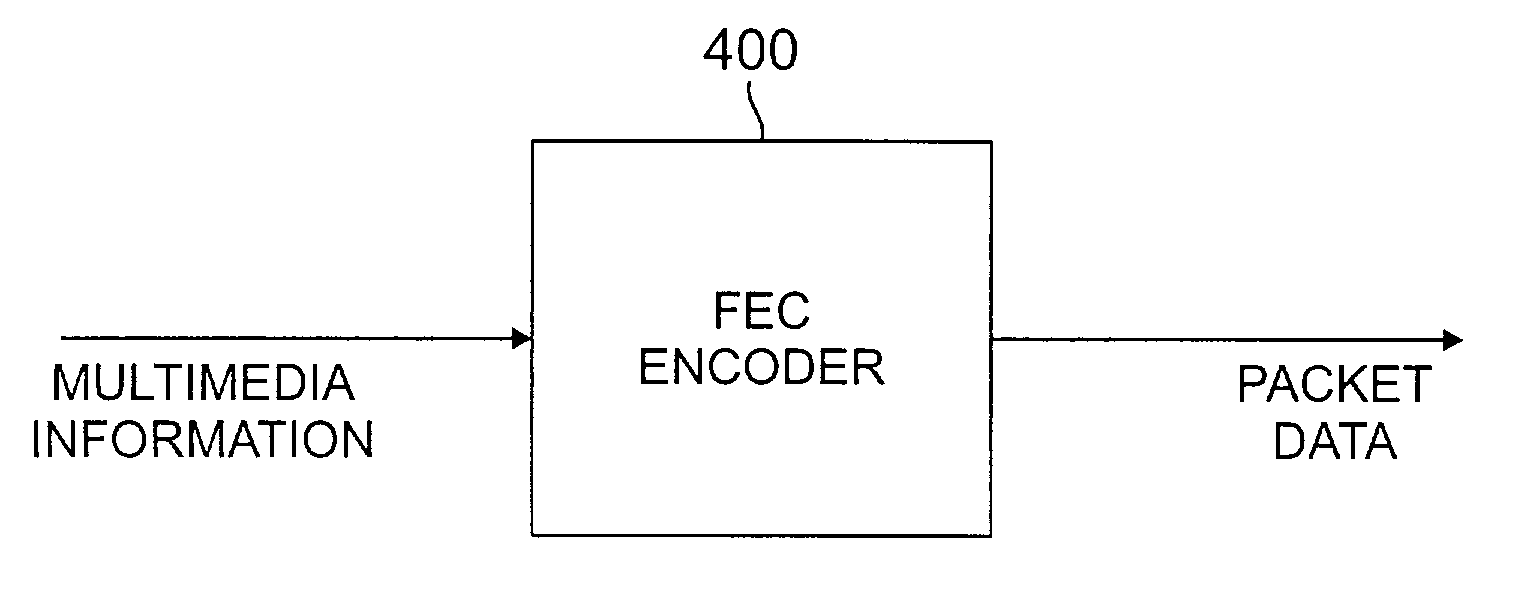
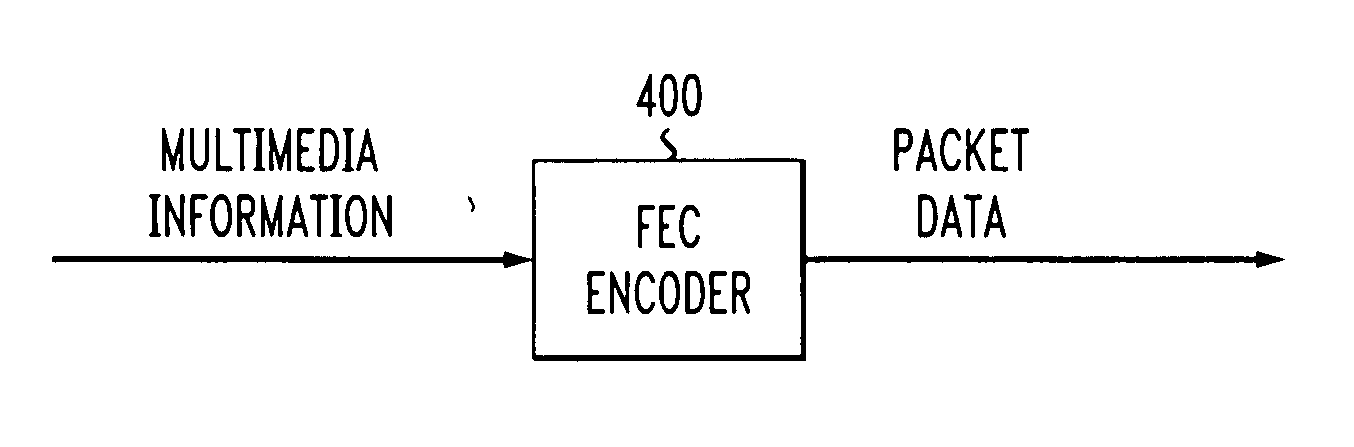
Complete user datagram protocol (CUDP) for wireless multimedia packet networks using improved packet level forward error correction (FEC) coding
InactiveUS7151754B1Reduces unnecessary packet discardingReduce information lossTransmission systemsCode conversionPacket lossForward error correction
A complete User Datagram Protocol (CUDP) is disclosed that reduces packet loss. Channel frame error information is used with a packet level forward error correction (FEC) coding technique to accommodate wireless multimedia traffic. Each packet, as well as the channel frame error information, is forwarded to a given application. The CUDP protocol further assists the FEC decoding process by forwarding the locations of corrupted frames to the FEC decoder. Maximal Distance Separable (MDS) codes can be applied to a group of packets, to achieve additional robustness. An MDS decoder utilizes the frame error information to recognize the erasures within each packet. The error information can be represented as a set of LTU error indicators associated with each packet (for FEC decoders requiring an erasure indicator). The error indicators point to the starting and ending location of the erroneous data. The error information can also be represented as a reformatted packet (for FEC decoders Recognizing Erasures). The frame (LTU) error information from the lower layers is incorporated in the packet payload. An FEC encoder is also disclosed that encodes multimedia packets utilizing a packet-coding scheme, such as a Vertical Packet Coding (VPC) scheme or a Long Vertical Packet Coding (LVPC) scheme.
Owner:ALCATEL-LUCENT USA INC
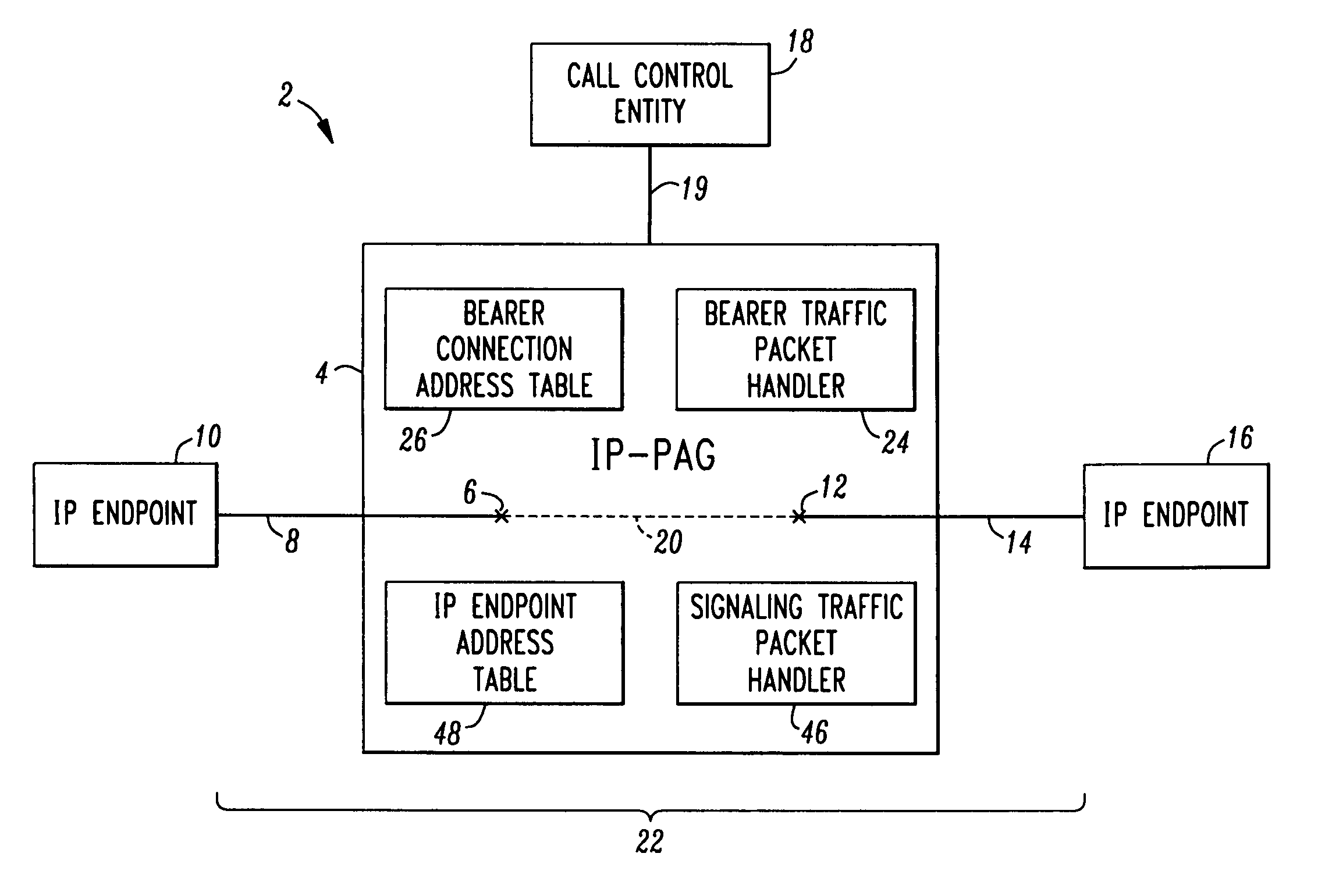
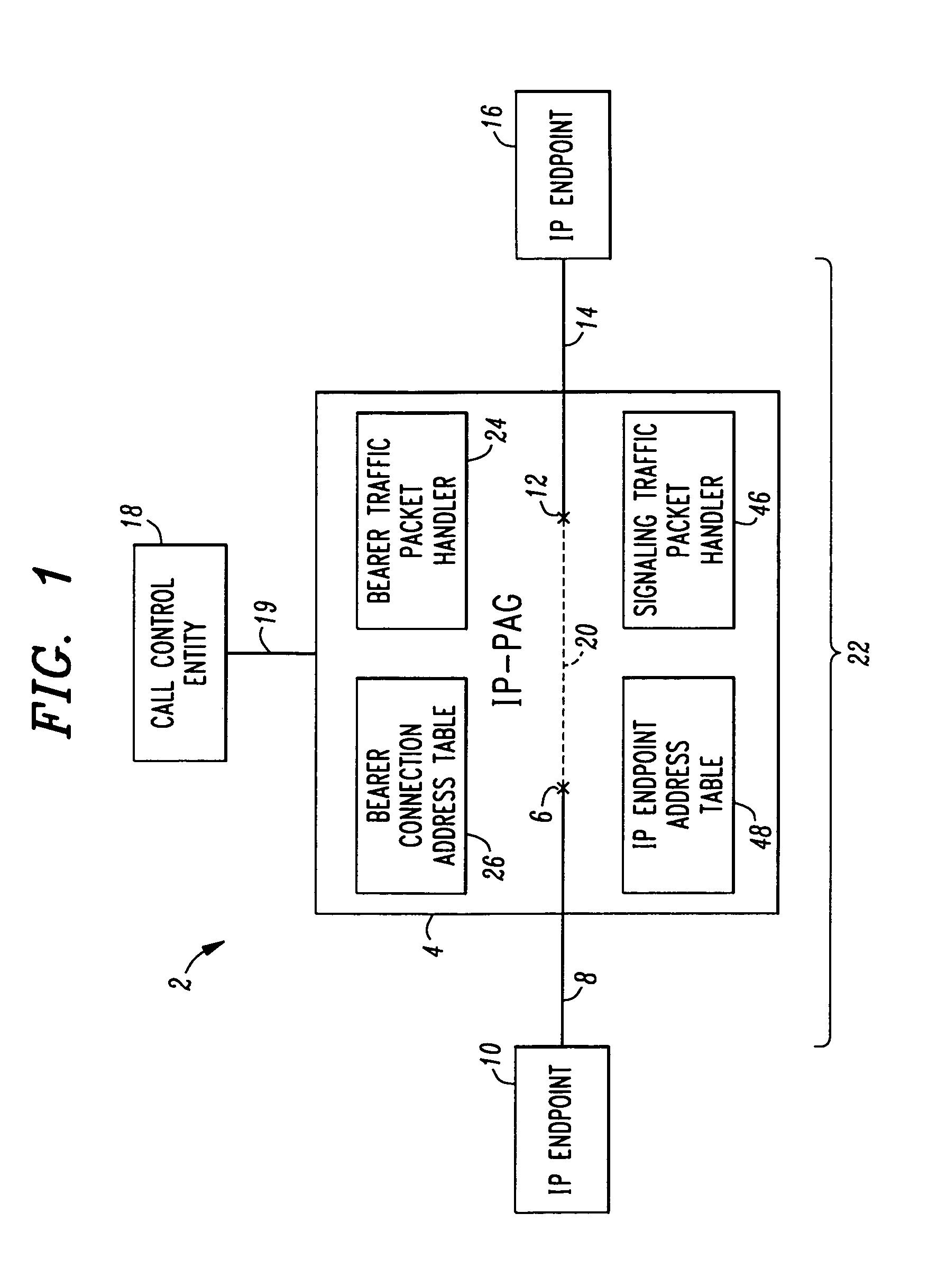
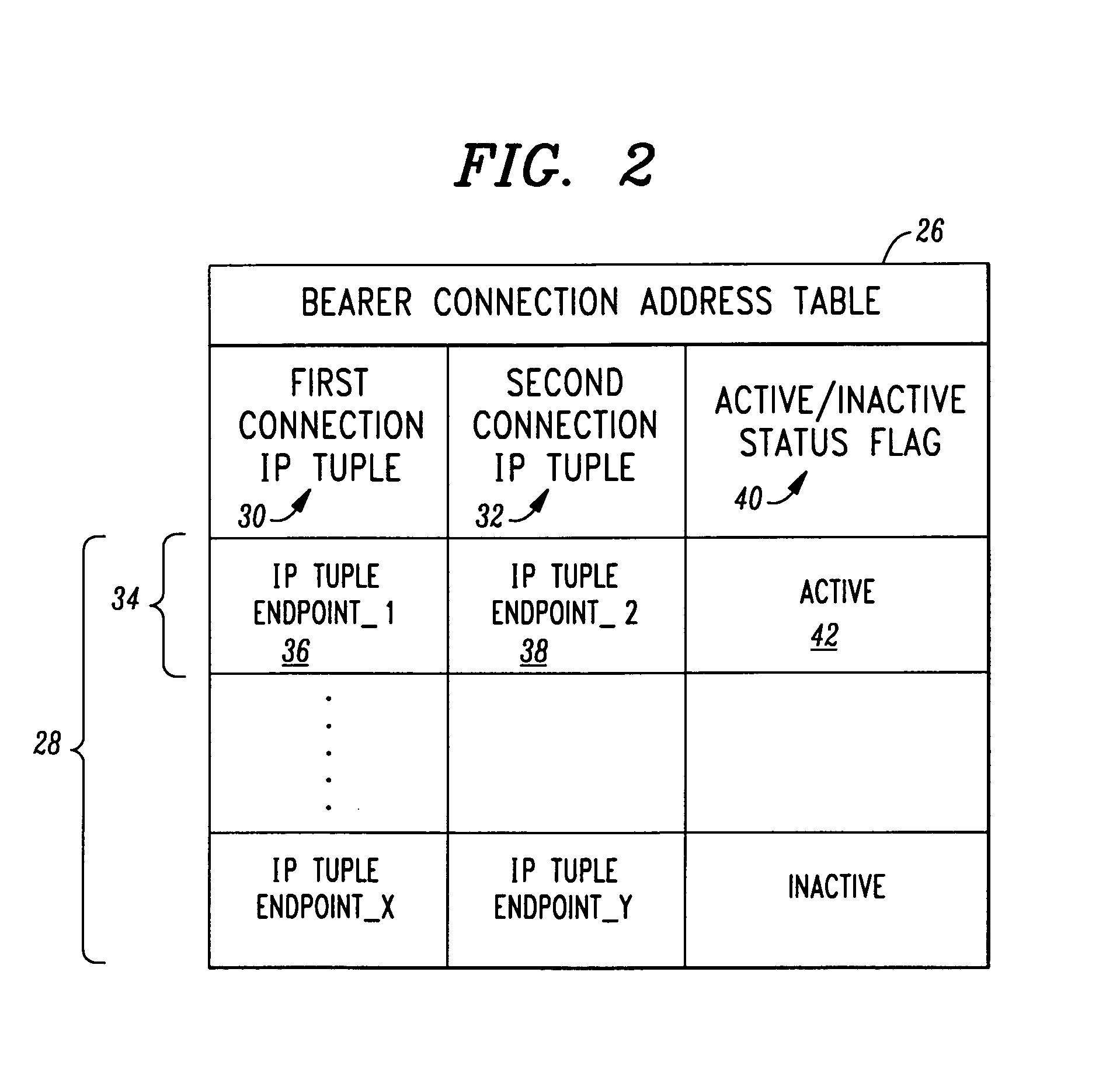
IP packet access gateway
An IP Packet Access Gateway (IP PAG) system manages an IP bearer path between communicating IP endpoints. The system includes an IP PAG having a first IP bearer connection termination for terminating a first bearer connection with a first IP endpoint, and a second IP connection termination or terminating a second bearer connection with a second IP endpoint. A call control entity is associated with the IP PAG and communicates call control instructions thereto. The call control instructions include instructions for logically concatenating the connections into an active IP bearer path extending between the first IP endpoint and the second IP endpoint. A bearer traffic IP packet handler in the IP PAG moves bearer traffic IP packet payloads over the active IP bearer path.
Owner:LUCENT TECH INC
Method and apparatus for packet segmentation and concatenation signaling in a communication system
ActiveUS20090116490A1Error preventionNetwork traffic/resource managementCommunications systemStructure of Management Information
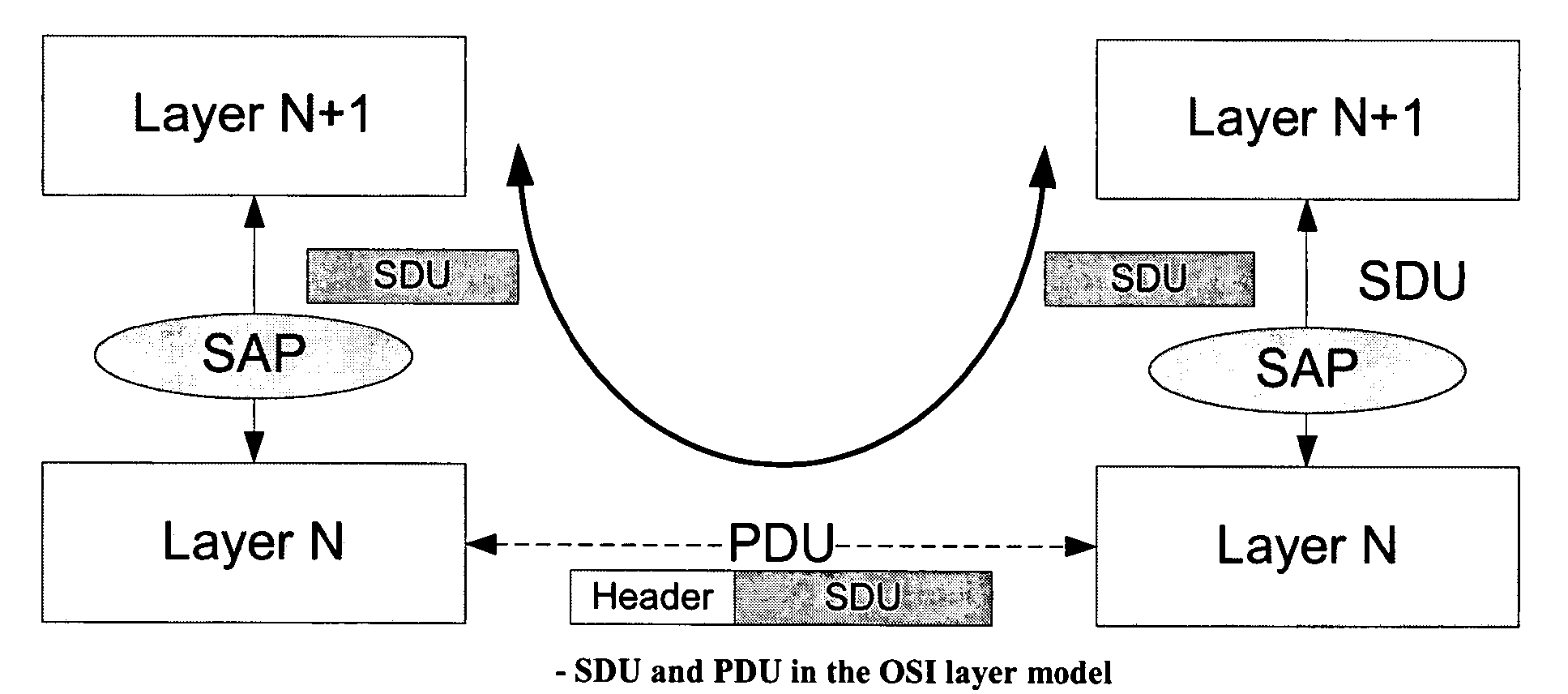
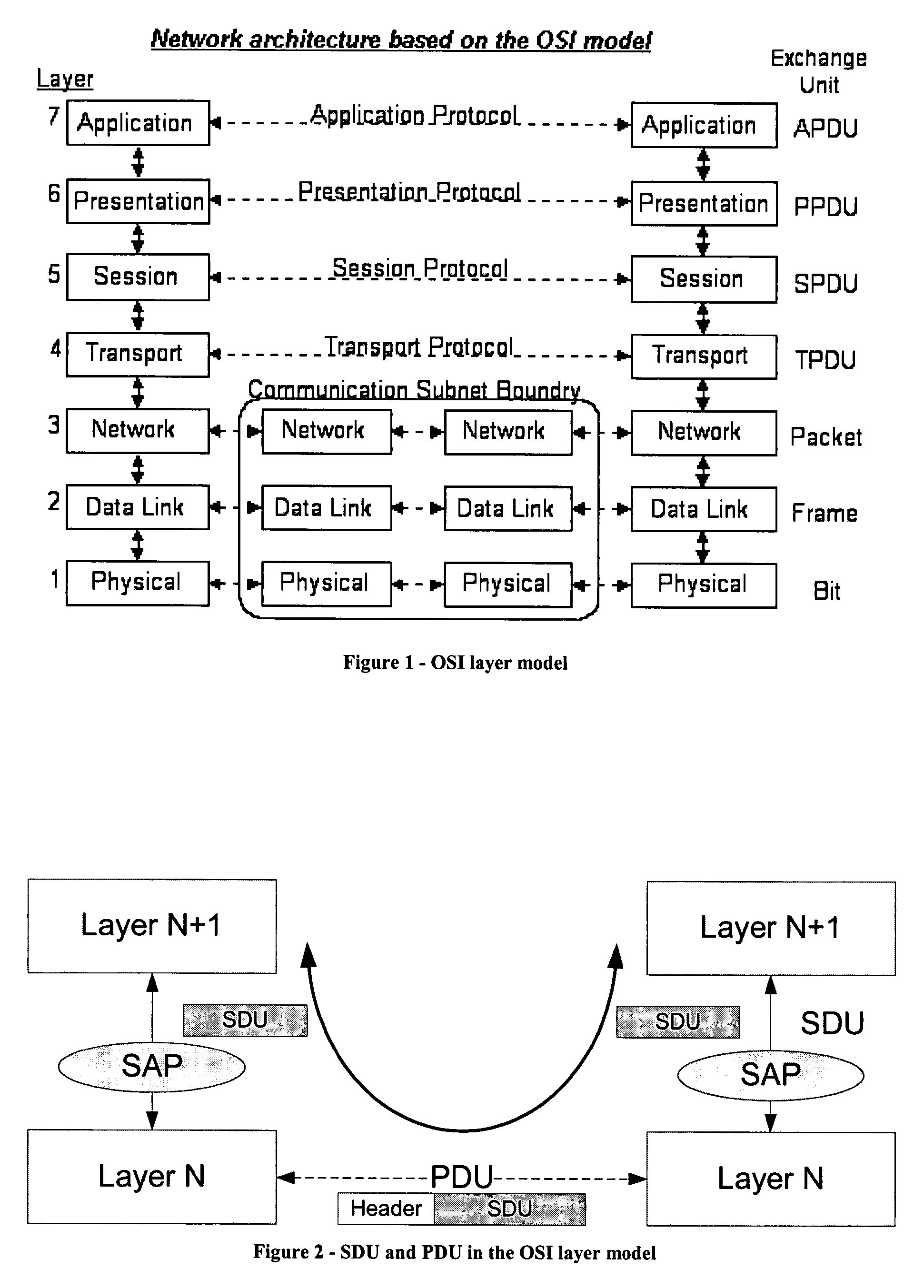
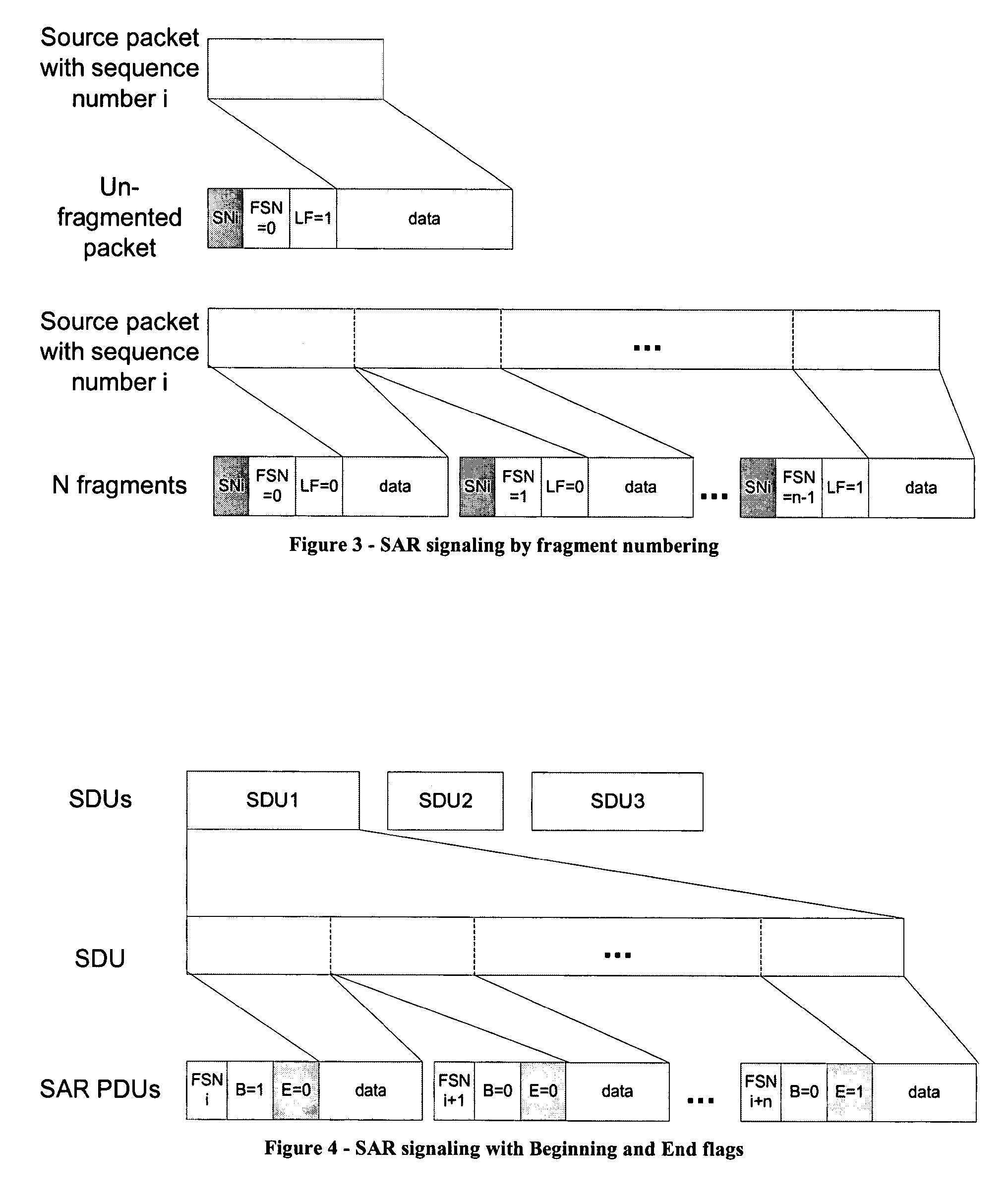
The invention relates to a data packet structure for conveying data of service data units (SDU) using protocol data units (PDU). The data packet comprise a data packet payload comprising at least one protocol data unit (PDU), wherein a protocol data unit (PDU) comprises a service data unit (SDU) or a fragment of a service data unit; and a data packet header comprising an indicator (FFF, SFF) indicating whether or not the data packet payload begins with a protocol data unit (PDU) being a fragment of a service data unit and whether or not the data packet payload ends with a protocol data unit (PDU) being a fragment of a service data unit.
Owner:OPTIS WIRELESS TECH LLC
Pattern Matching Technique
ActiveUS20100095064A1Fast executionMemory loss protectionError detection/correctionPattern matchingParallel computing
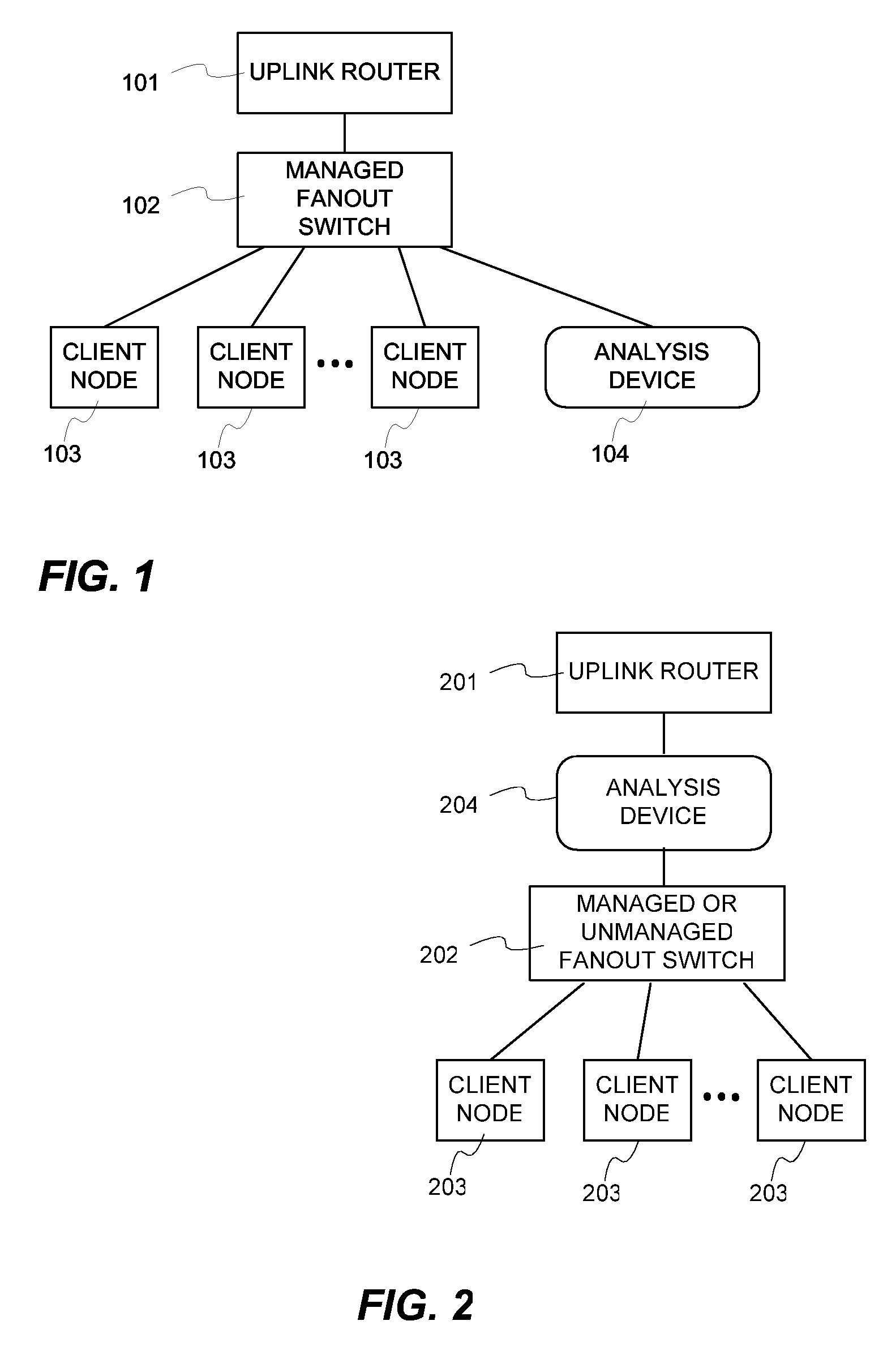
A method, system and program are disclosed for accelerating data storage in a cache appliance that transparently monitors NFS and CIFS traffic between clients and NAS subsystems and caches files in a cache memory by using a perfect hashing memory index technique to rapidly detect predetermined patterns in received packet payloads and retrieve matching patterns from memory by generating a data structure pointer and index offset to directly address the pattern in the datagram memory, thereby accelerating evaluation of the packet with the matching pattern by the host processor.
Owner:NETWORK APPLIANCE INC
Network packet payload compression
ActiveUS8001278B2Energy efficient ICTMultiple digital computer combinationsPayload (computing)Term memory
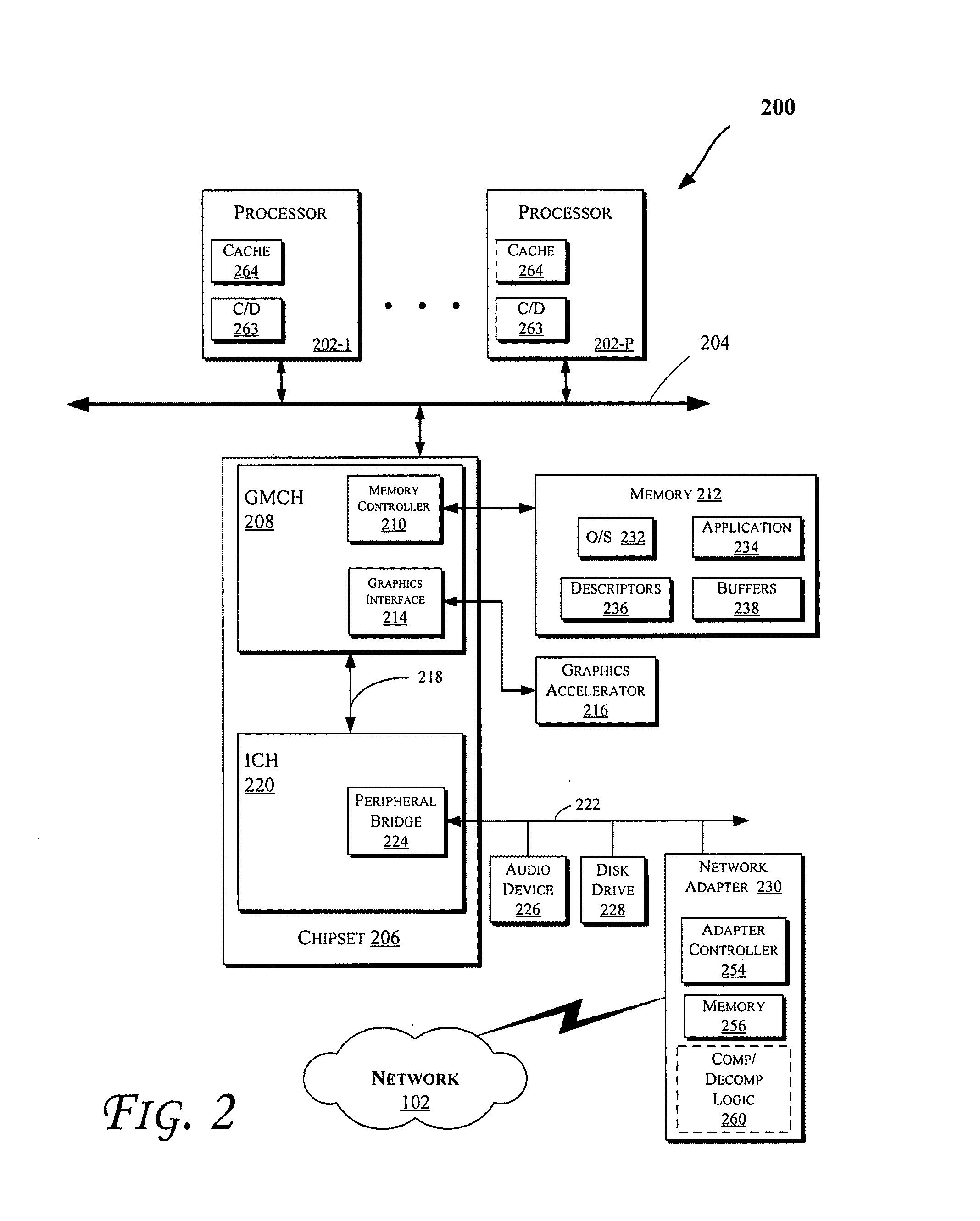
Methods and apparatus relating to network packet payload compression / decompression are described. In an embodiment, an uncompressed packet payload may be compressed before being transferred between various components of a computing system. For example, a packet payload may be compressed prior to transfer between network interface cards or controllers (NICs) and storage devices (e.g., including a main system memory and / or cache(s)), as well as between processors (or processor cores) and storage devices (e.g., including main system memory and / or caches). Other embodiments are also disclosed.
Owner:INTEL CORP
Systems and methods for reducing denial of service attacks against dynamically generated next secure records
ActiveUS20140344925A1Lower capability requirementsService degradationMemory loss protectionError detection/correctionData packIp address
In one aspect, the present disclosure is directed to a method for reducing denial of service (DoS) attacks against dynamically generated next secure (NSEC) records. A domain name system (DNS) proxy may prevent spoofed IP addresses by forcing clients to transmit DNS queries via transmission control protocol (TCP), by replying to a user datagram protocol (UDP) DNS request with a blank or predetermined resource record with a truncation bit set to indicate that the record is too large to fit within a single UDP packet payload. Under the DNS specification, the client must re-transmit the DNS request via TCP. Upon receipt of the retransmitted request via TCP, the DNS proxy may generate fictitious neighbor addresses and a signed NSEC record and transmit the record to the client. Accordingly, the DNS Proxy need not waste time and processor cycles generating and signing records for requests from spoofed IP addresses via UDP.
Owner:CITRIX SYST INC
Complete user datagram protocol (CUDP) for wireless multimedia packet networks using improved packet level forward error correction (FEC) coding
InactiveUS20060156198A1Reduces unnecessary packet discardingReduce information lossCode conversionWireless network protocolsData packPacket loss
A complete User Datagram Protocol (CUDP) is disclosed that reduces packet loss. Channel frame error information is used with a packet level forward error correction (FEC) coding technique to accommodate wireless multimedia traffic. Each packet, as well as the channel frame error information, is forwarded to a given application. The CUDP protocol further assists the FEC decoding process by forwarding the locations of corrupted frames to the FEC decoder. Maximal Distance Separable (MDS) codes can be applied to a group of packets, to achieve additional robustness. An MDS decoder utilizes the frame error information to recognize the erasures within each packet. The error information can be represented as a set of LTU error indicators associated with each packet (for FEC decoders requiring an erasure indicator). The error indicators point to the starting and ending location of the erroneous data. The error information can also be represented as a reformatted packet (for FEC decoders Recognizing Erasures). The frame (LTU) error information from the lower layers is incorporated in the packet payload. An FEC encoder is also disclosed that encodes multimedia packets utilizing a packet-coding scheme, such as a Vertical Packet Coding (VPC) scheme or a Long Vertical Packet Coding (LVPC) scheme.
Owner:LUCENT TECH INC
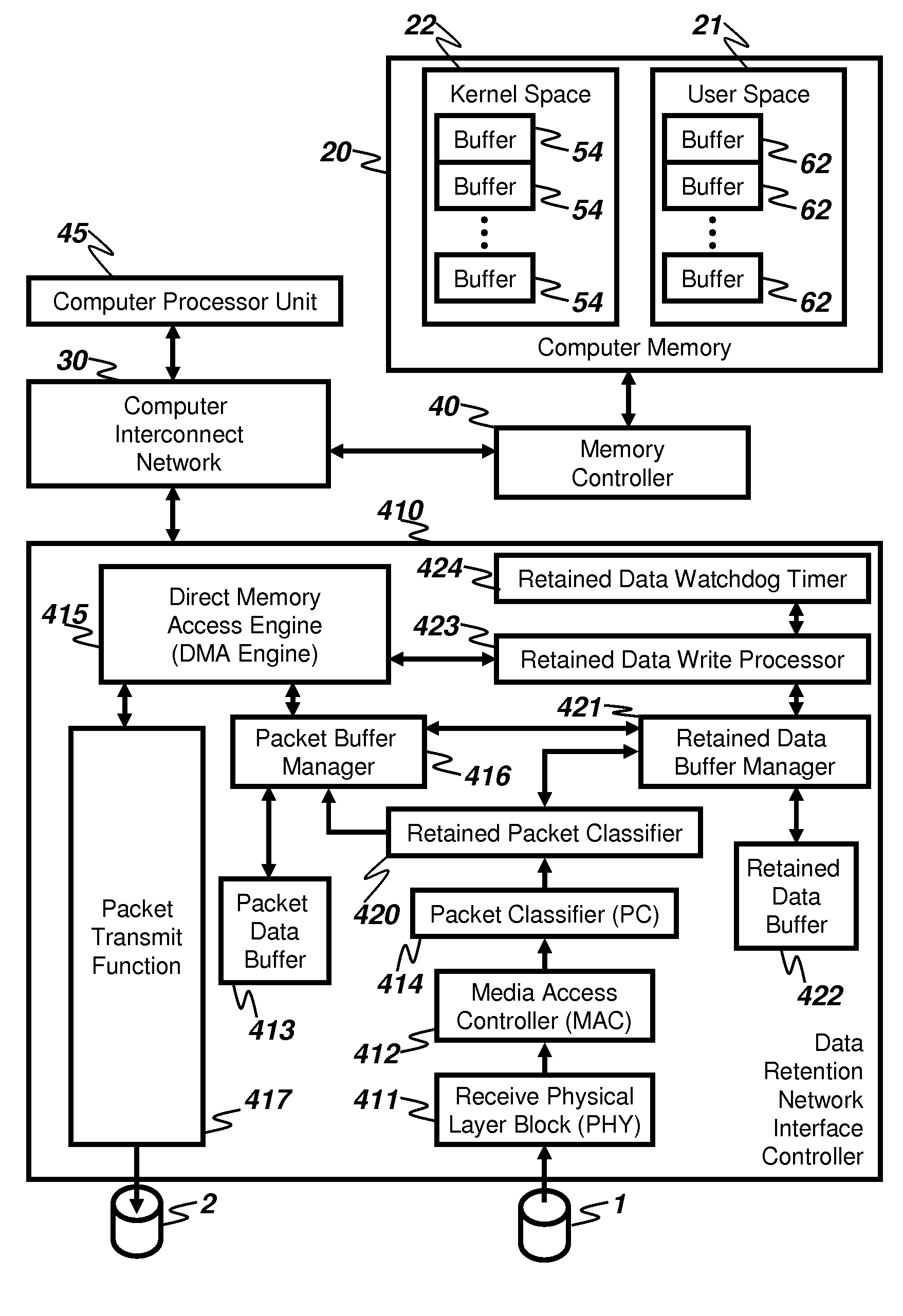
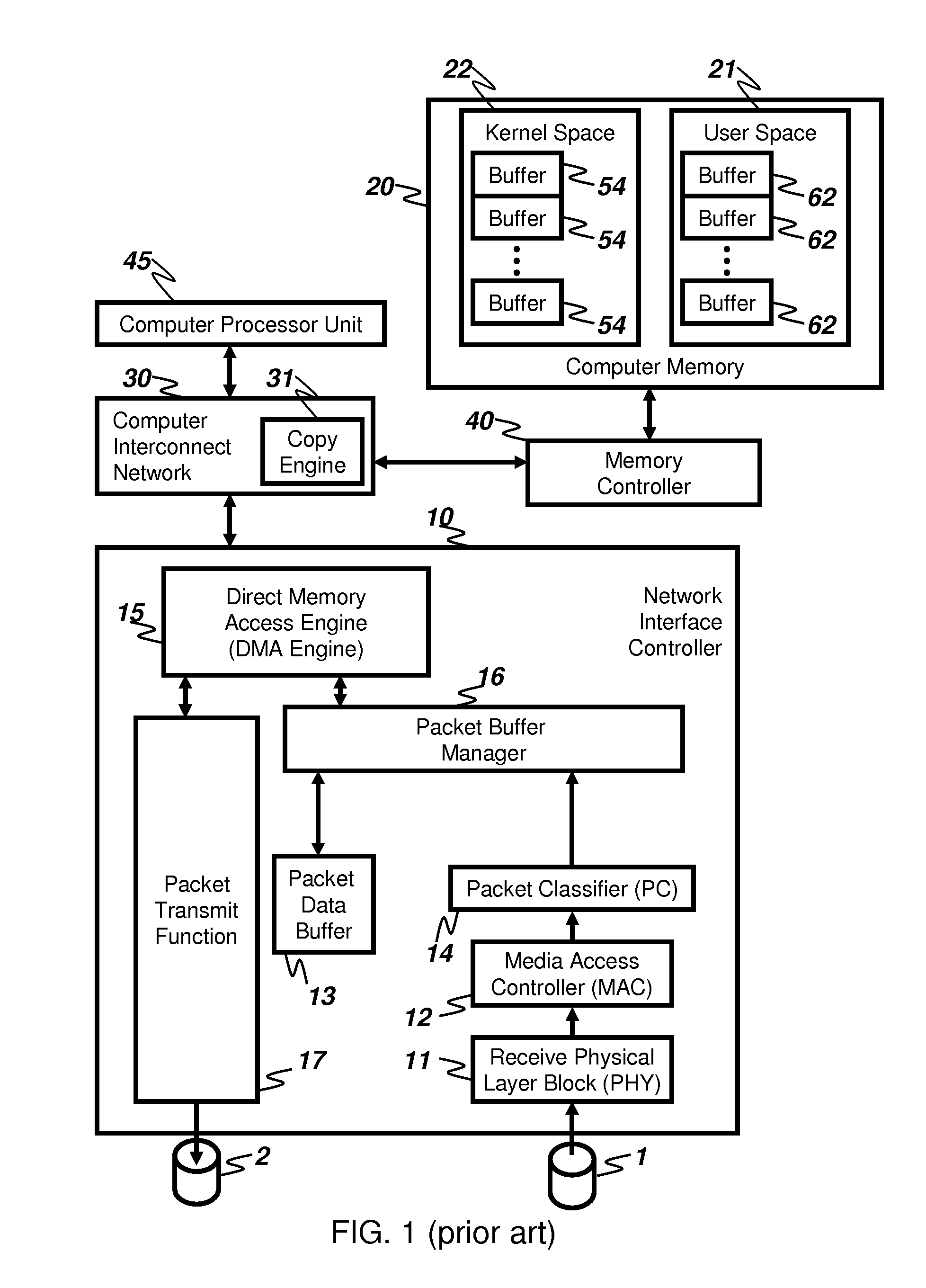
Method and apparatus for writing network packets into computer memory
An apparatus receives packets from a network and inserts the packet data into the memory of a computer system. The invention reduces the amount of computer system memory bandwidth required to receive packets through the use of a retained data buffer. Packet headers and a summary of packet validation results are processed by network stacks within the computer system to identify the intended memory buffer in which the packet payload is to be placed. Packet payload data is directly placed from the retained data buffer to the intended memory buffer without the use of intermediate buffers. A preferred embodiment includes a data retention network interface card (DRNIC) which includes the required data retention buffer for use in direct placement of received data.
Owner:GADELRAB SERAG
Network edge device configured for adding protocol service header identifying service encoding of IP packet payload
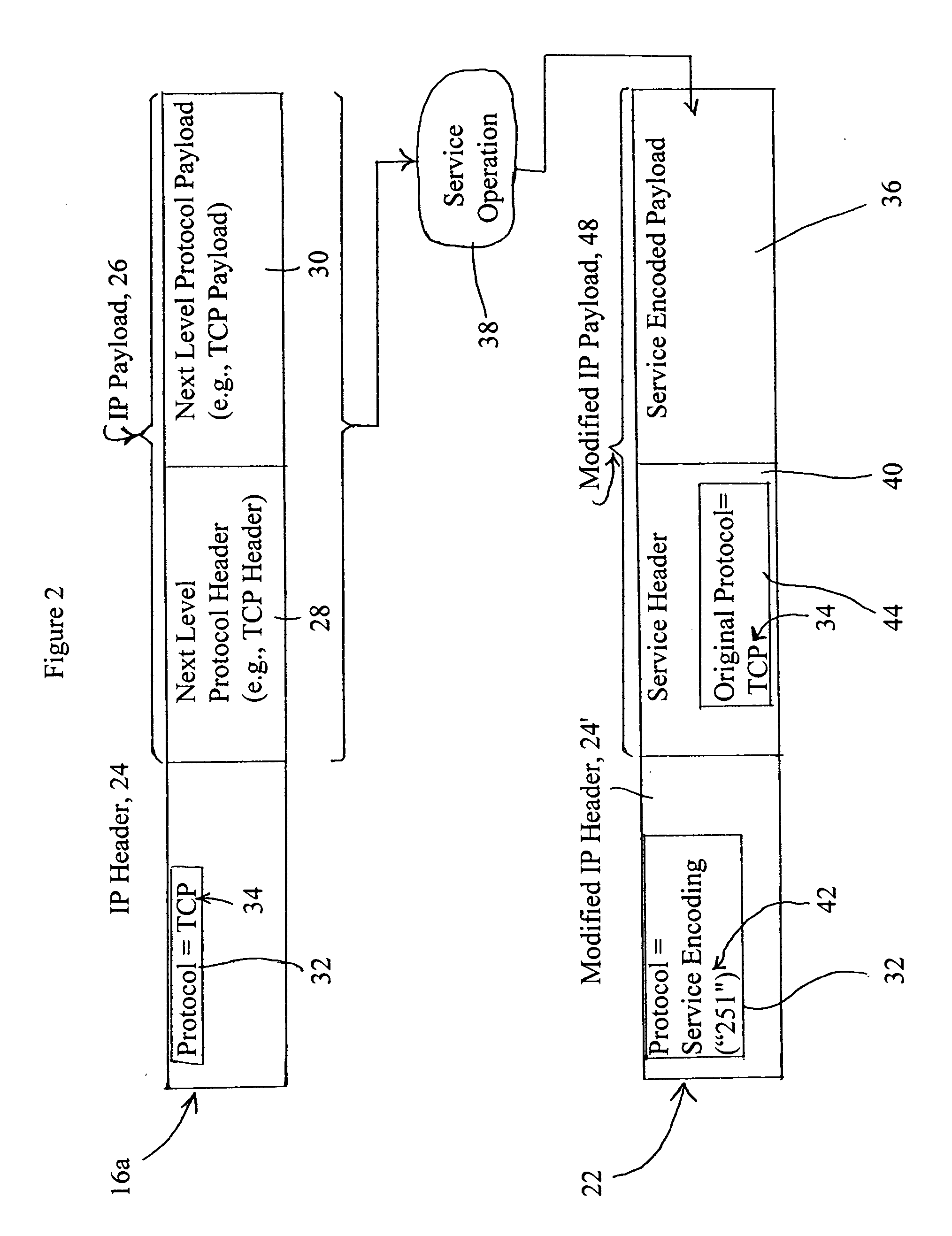
InactiveUS20070147363A1Quality of service operationEasy to addData switching by path configurationNetwork servicePage header
A service header is generated by an edge device (e.g., a gateway or a router) configured for providing a prescribed service operation for a prescribed network service for a received IP packet. The received IP packet includes an IP payload and an IP header having a protocol field specifying an original protocol of the IP payload. The edge device generates an encapsulated payload from the IP payload according to the prescribed network service, and generates a service header that identifies the prescribed network service and the original protocol of the IP payload. The edge device creates a modified IP header from the IP header and that identifies the service header in the corresponding protocol field, and outputs a modified IP packet including the modified IP header, the service header, and the encapsulated payload.
Owner:CISCO TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com