Patents
Literature
85 results about "Unified threat management" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Unified threat management (UTM) is an approach to information security where a single hardware or software installation provides multiple security functions. This contrasts with the traditional method of having point solutions for each security function. UTM simplifies information-security management by providing a single management and reporting point for the security administrator rather than managing multiple products from different vendors. UTM appliances have been gaining popularity since 2009, partly because the all-in-one approach simplifies installation, configuration and maintenance. Such a setup saves time, money and people when compared to the management of multiple security systems. Instead of having several single-function appliances, all needing individual familiarity, attention and support, network administrators can centrally administer their security defenses from one computer. Some of the prominent UTM brands are Sophos, SonicWall and Check Point.
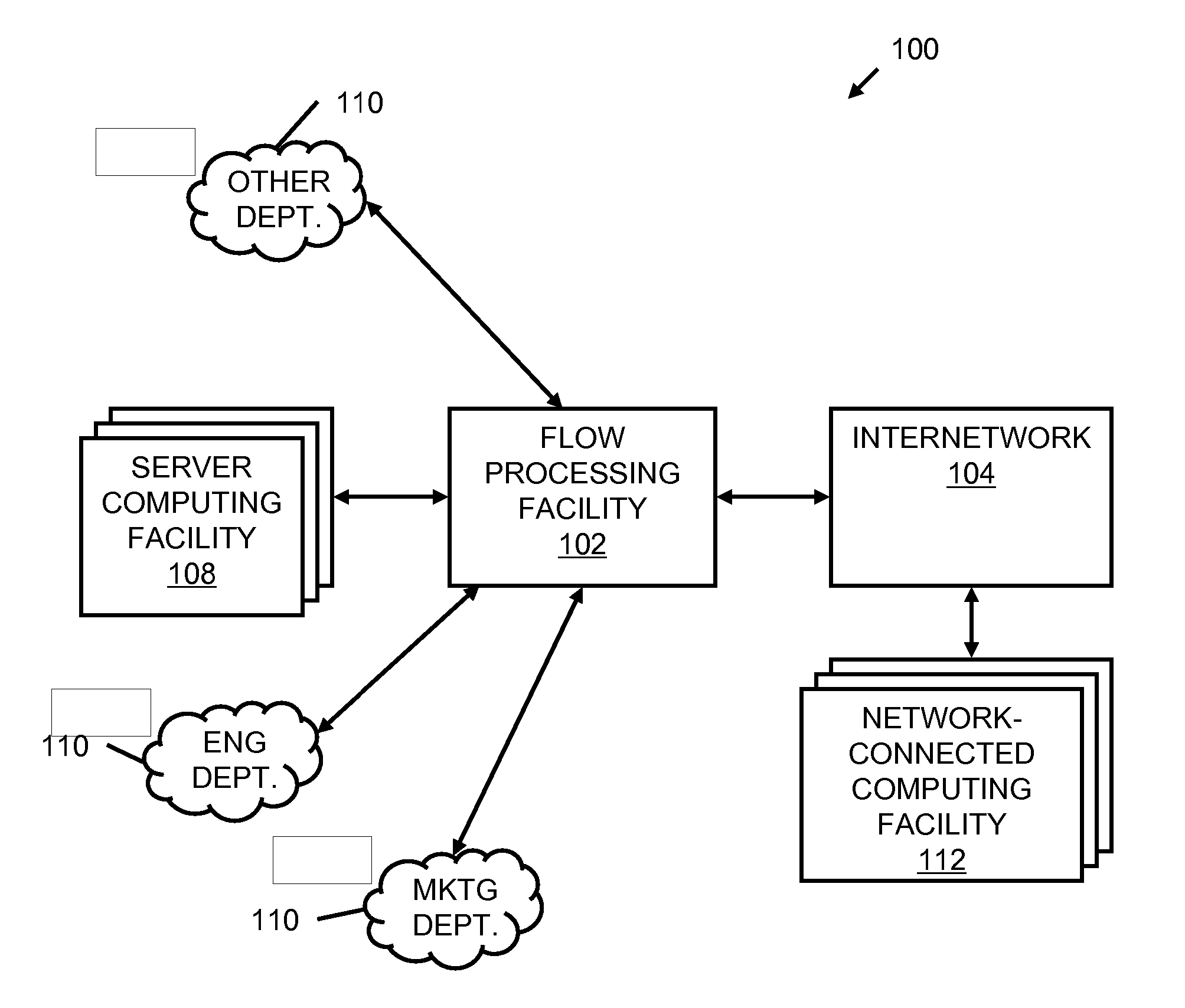
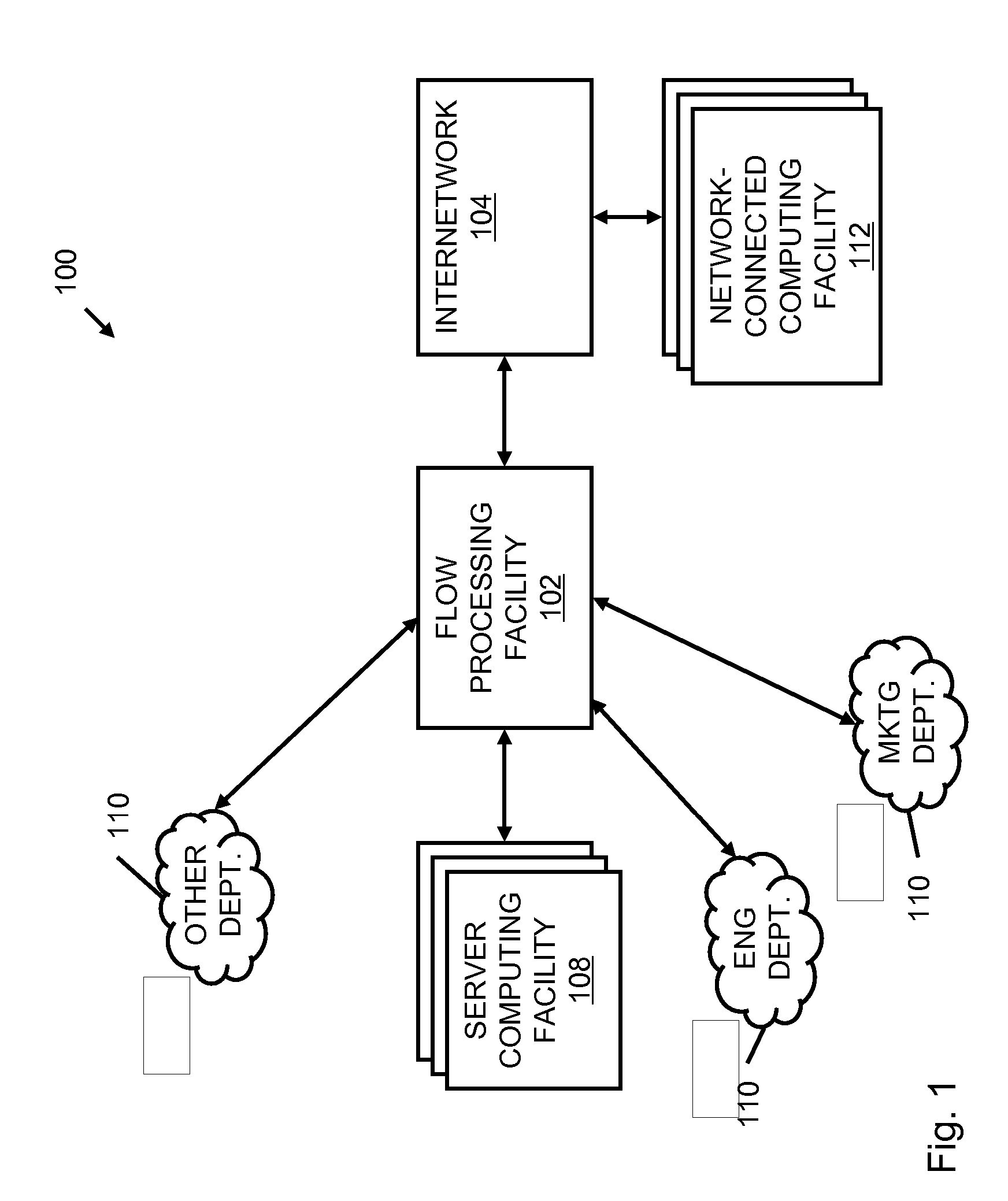
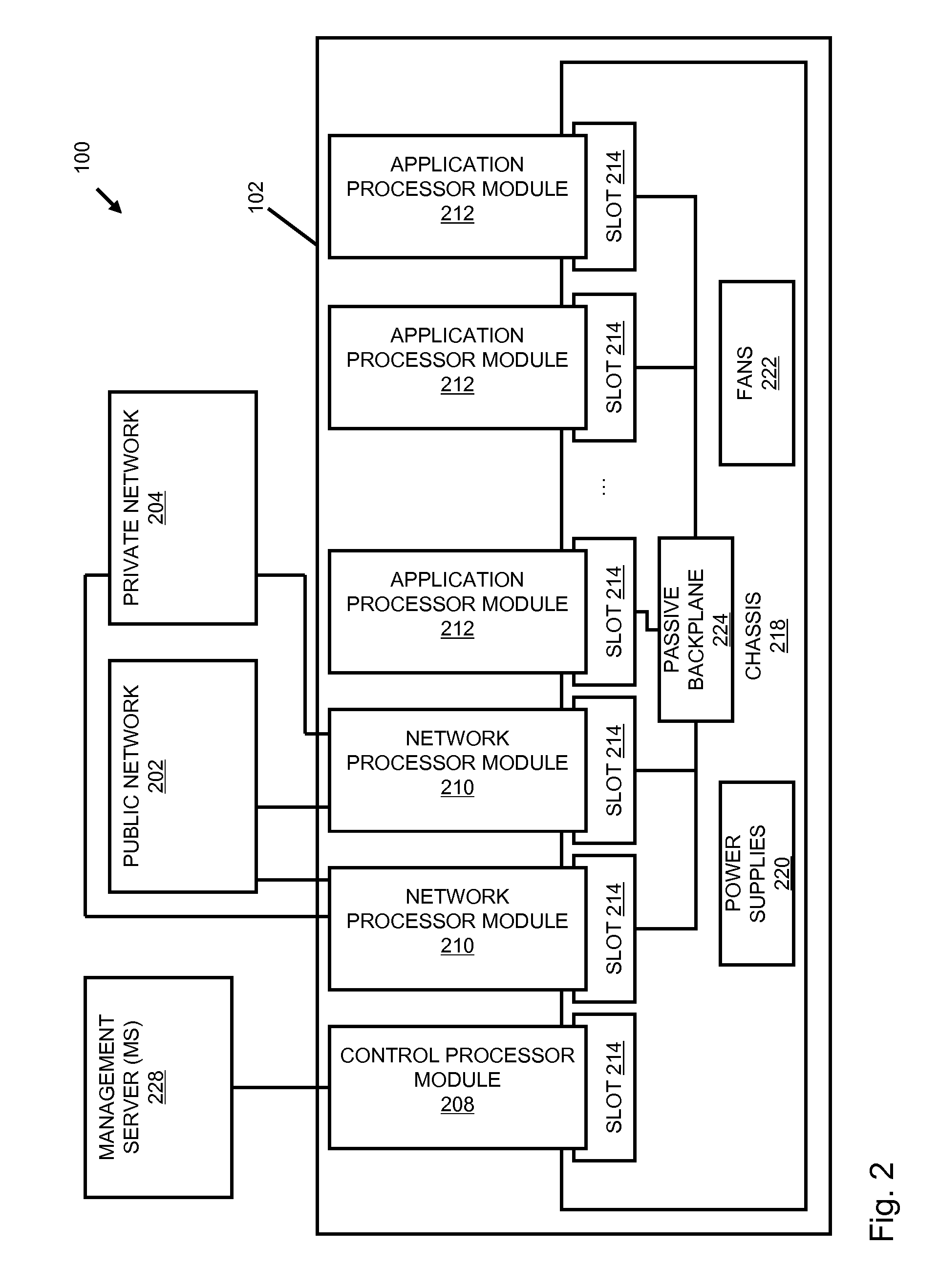
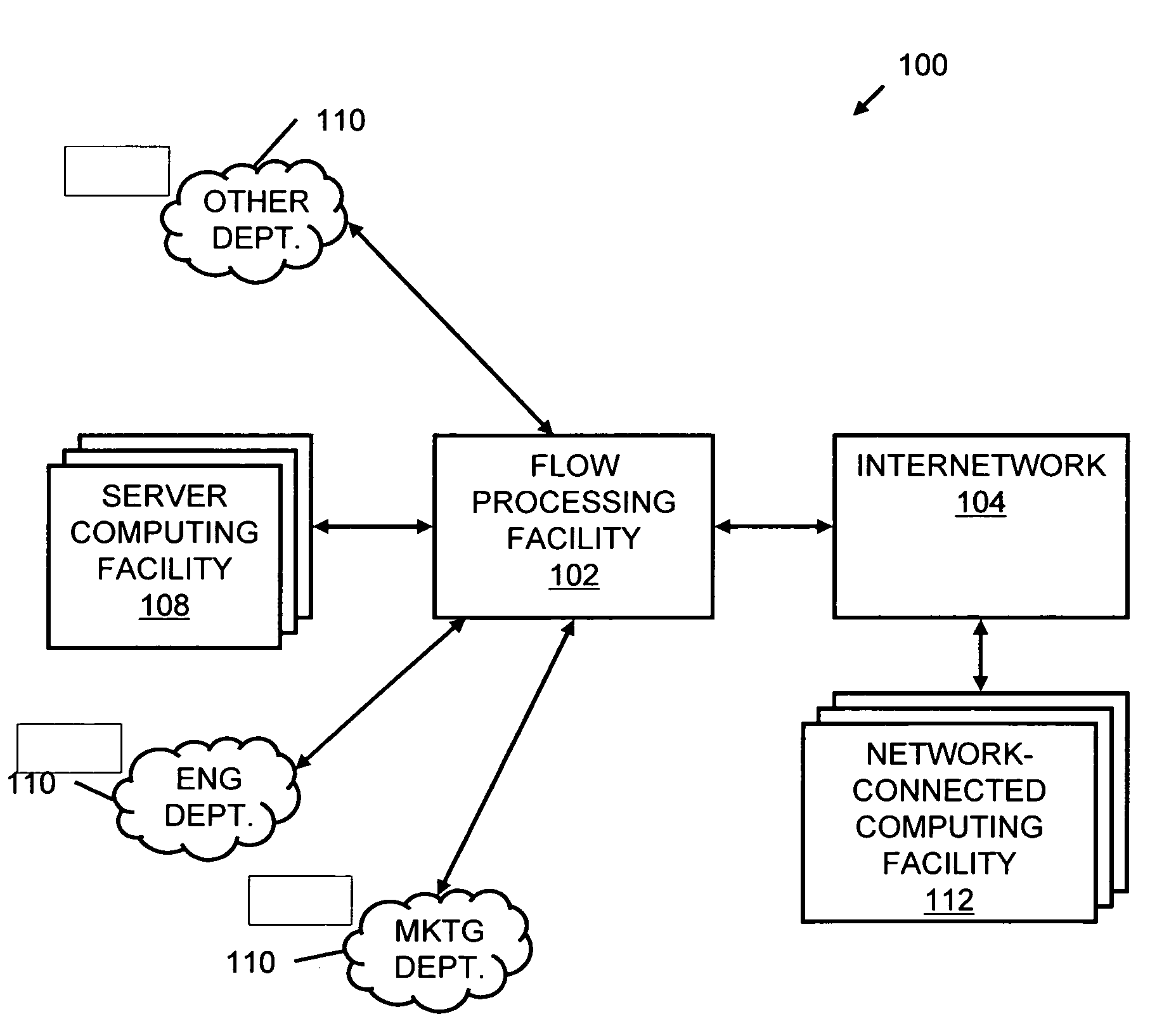
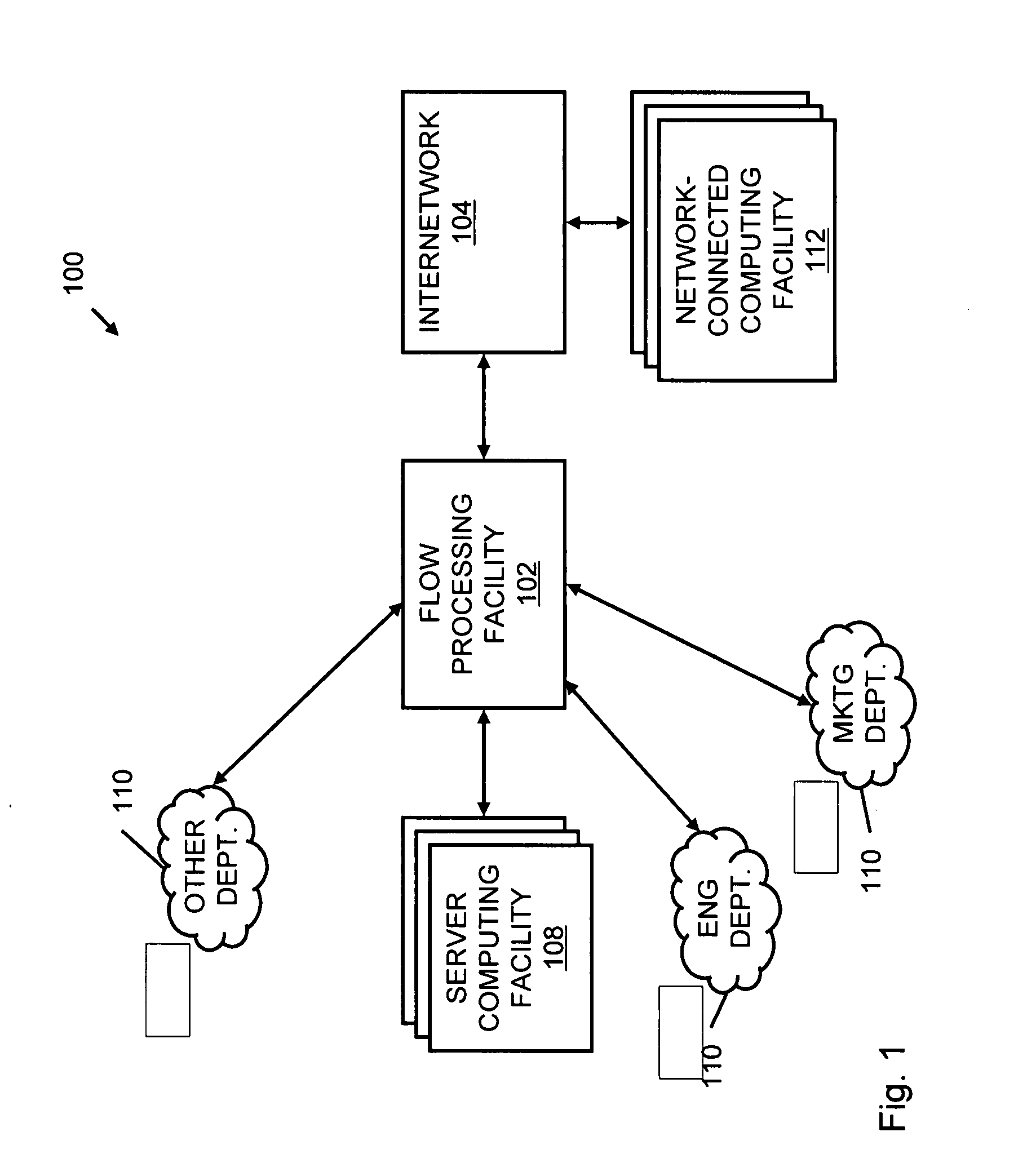
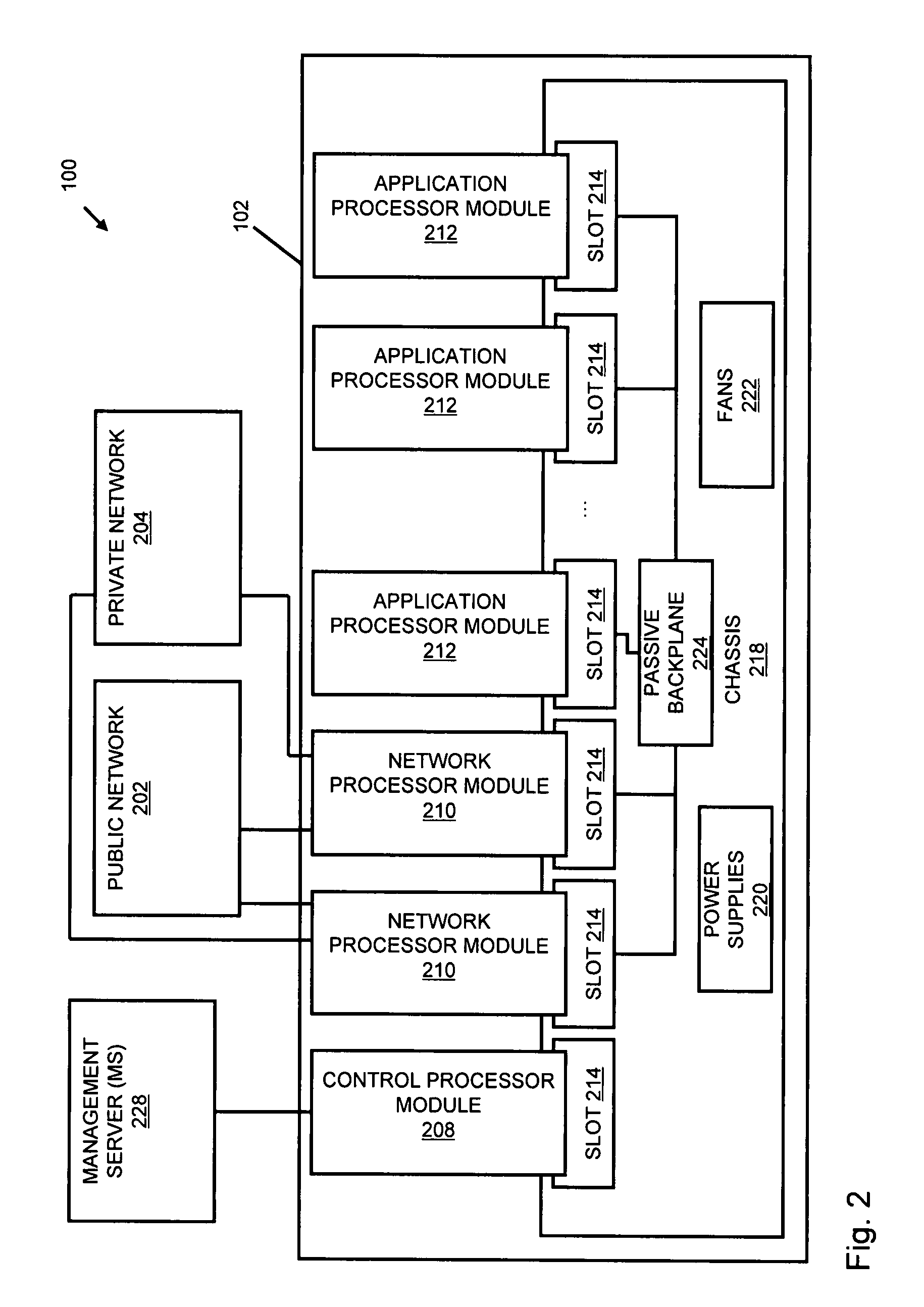
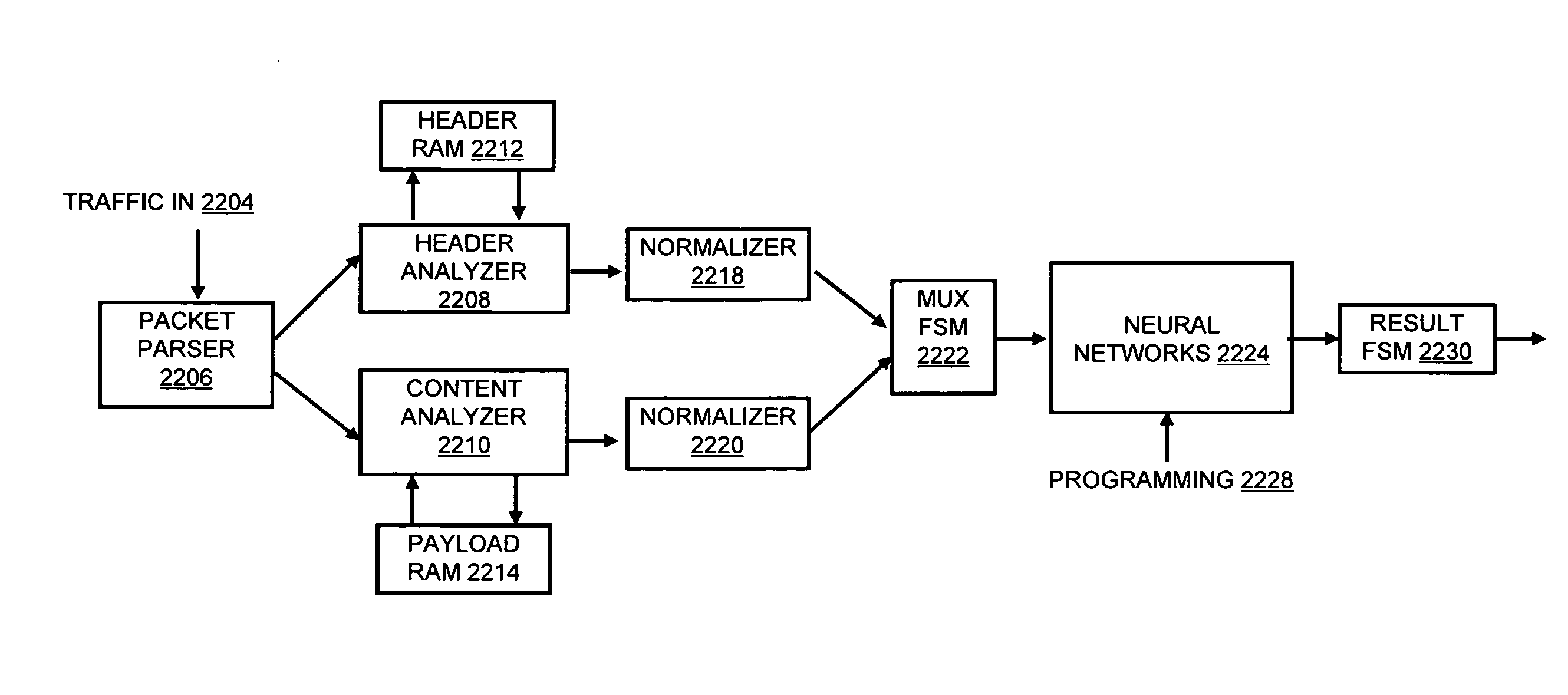
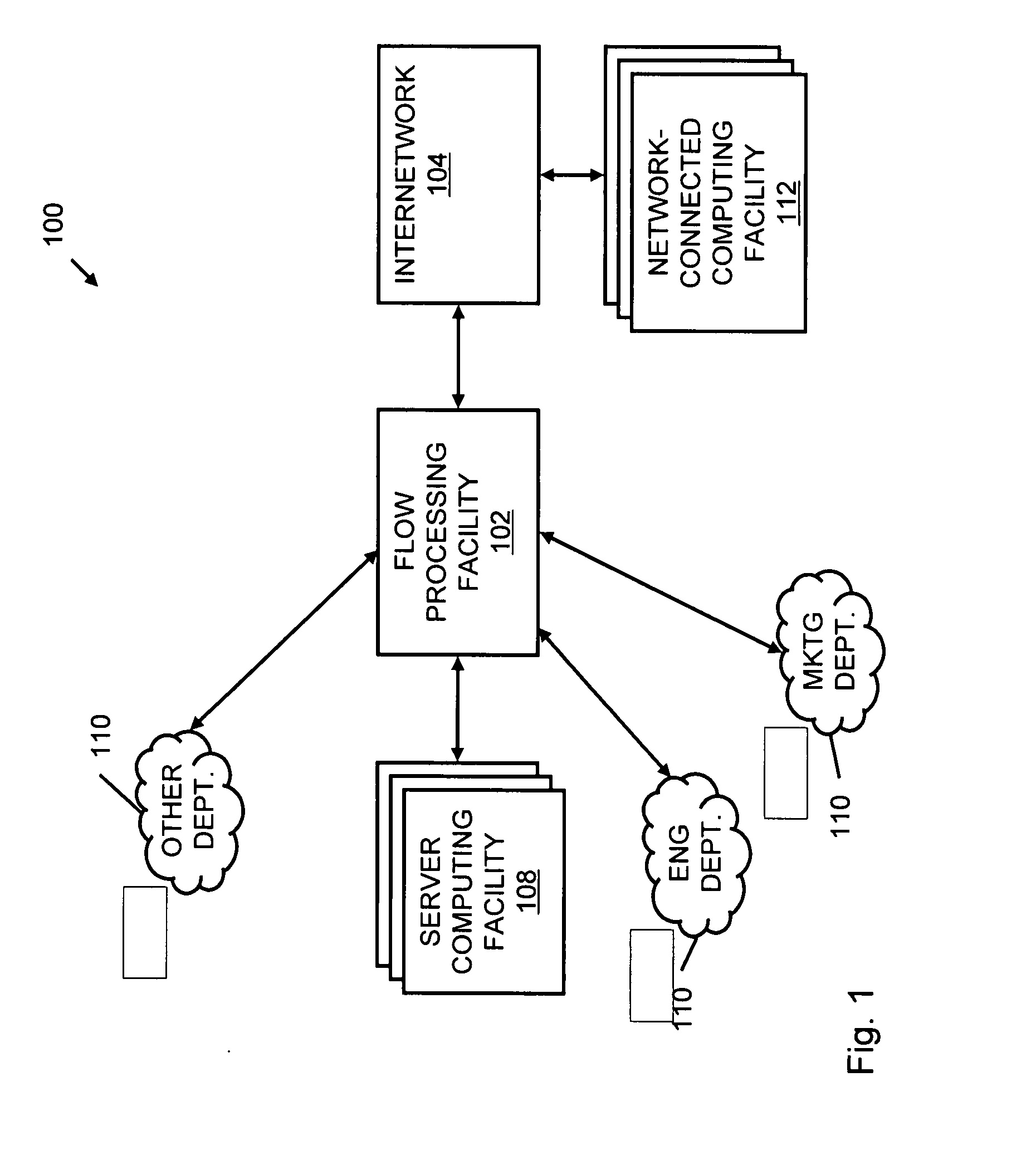
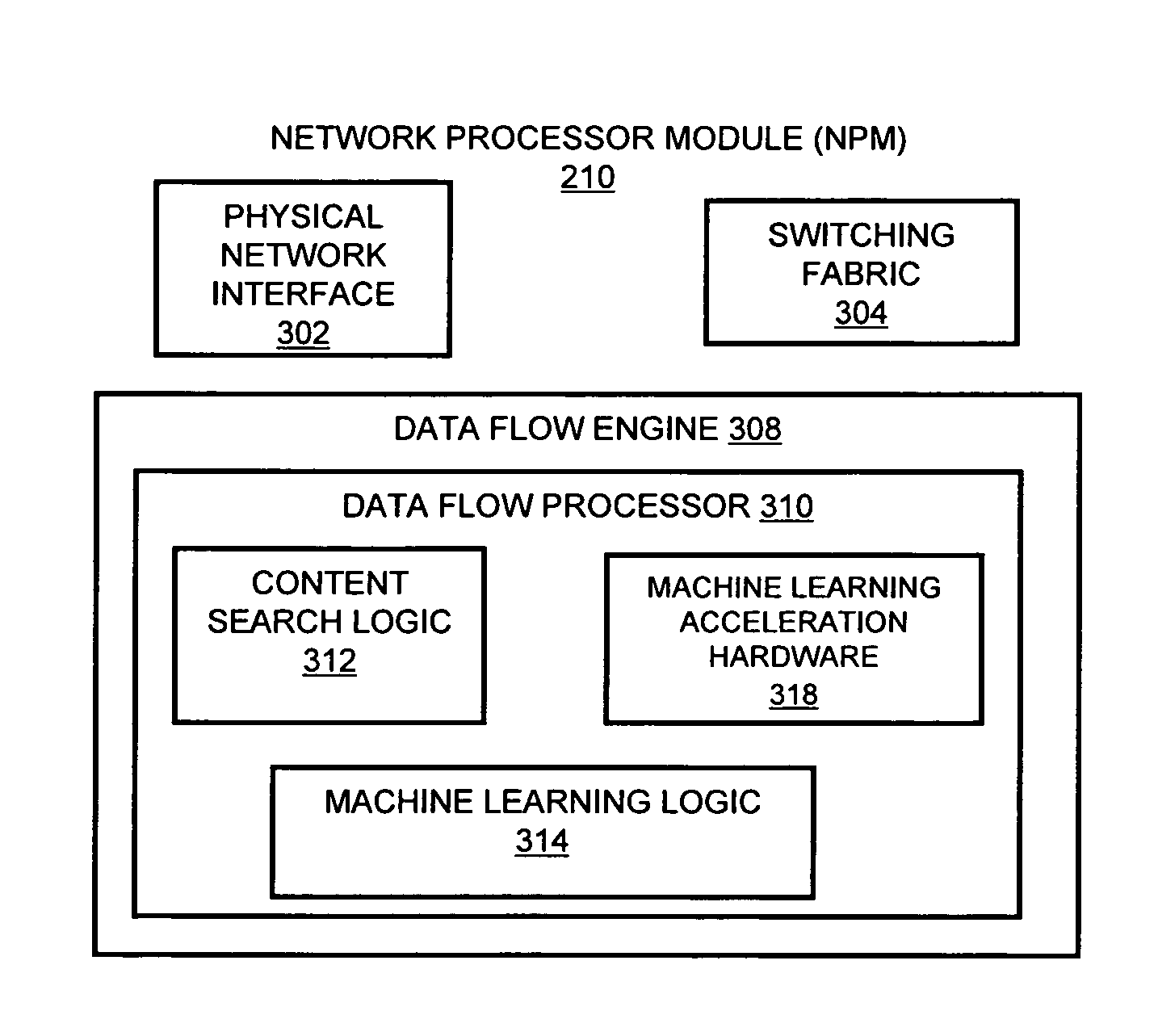
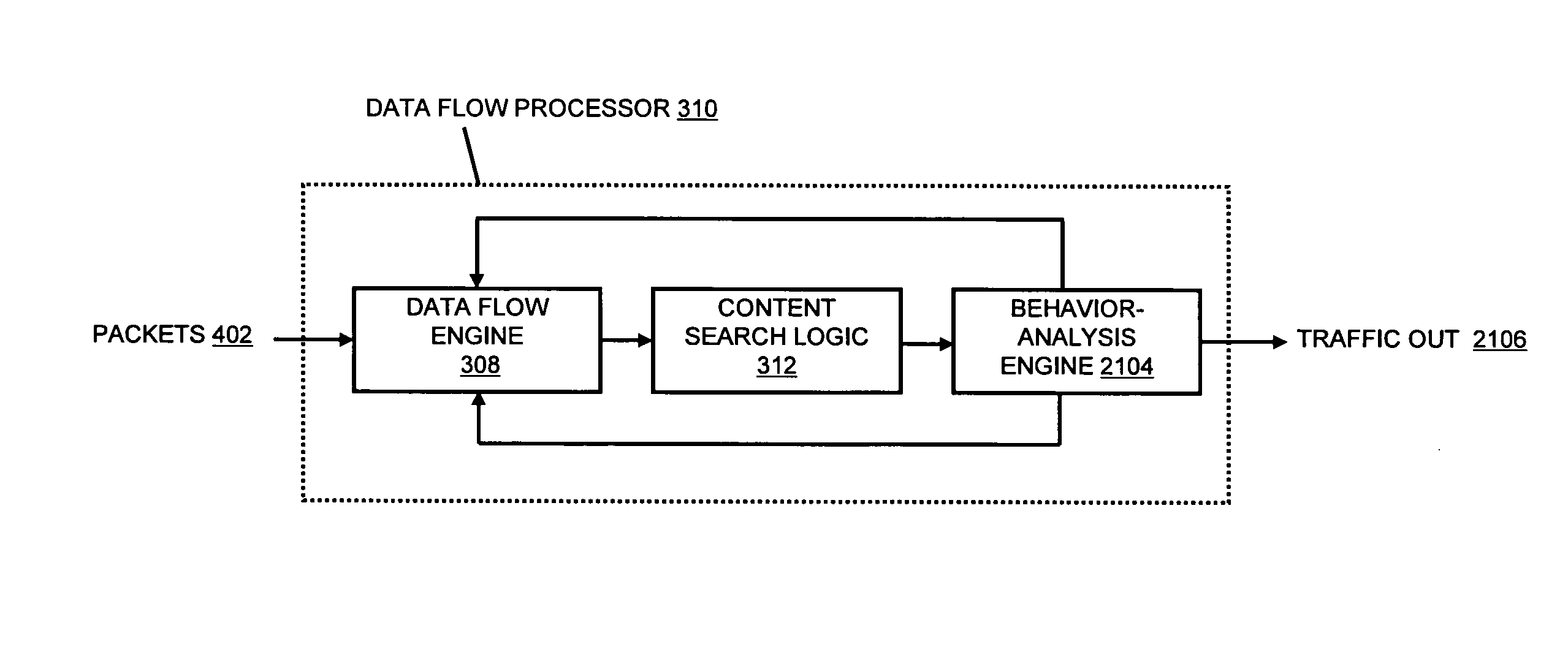
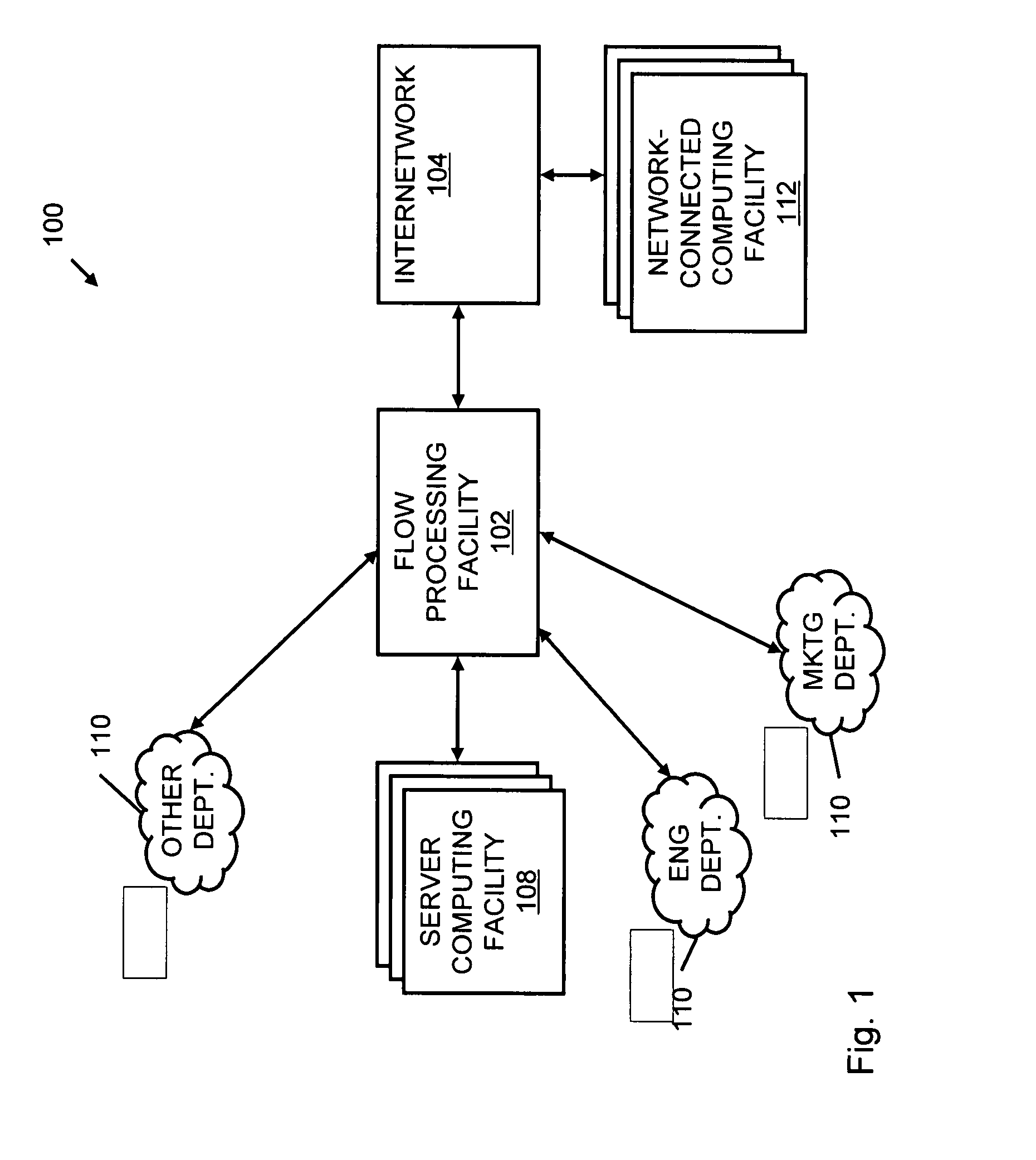
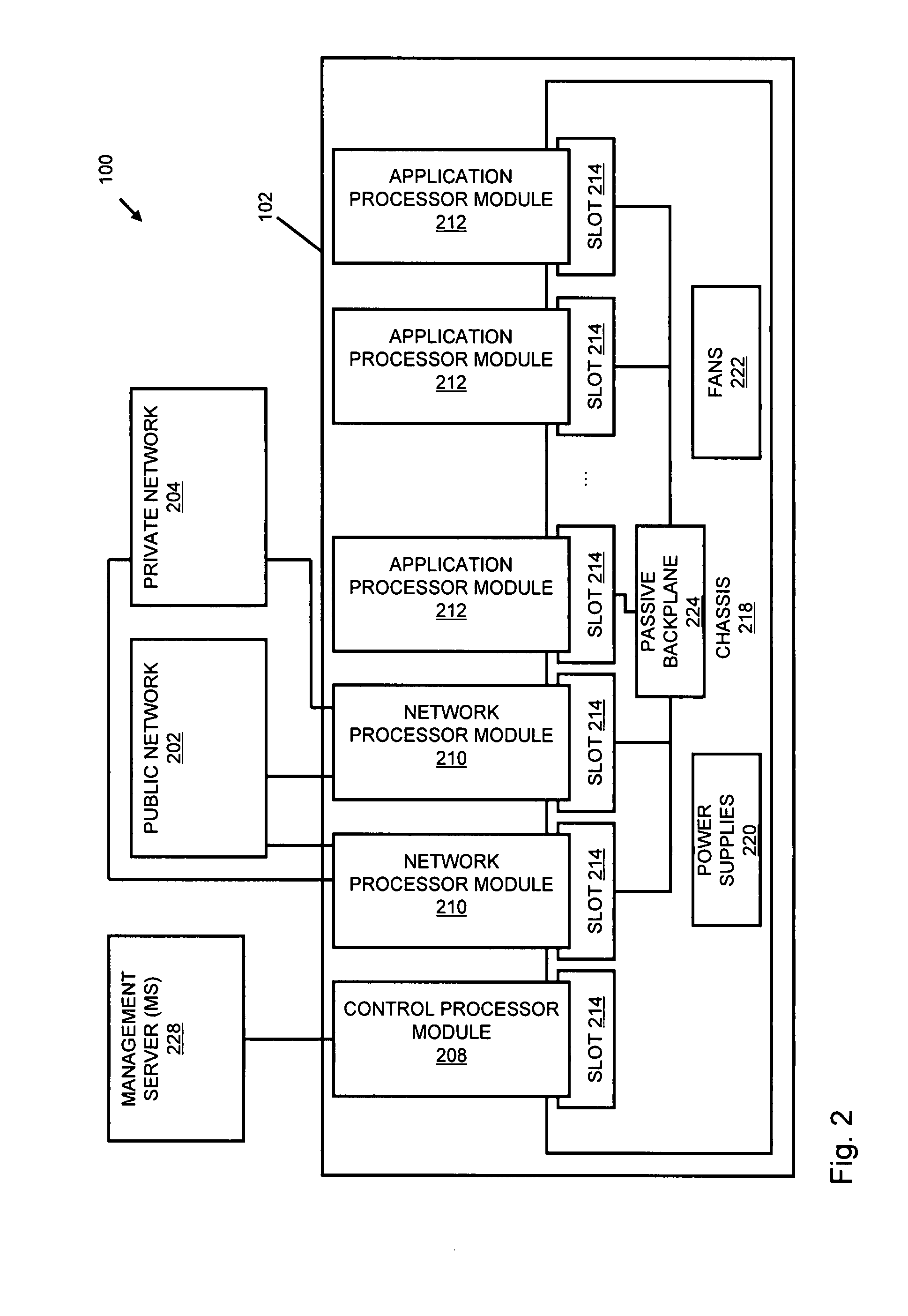
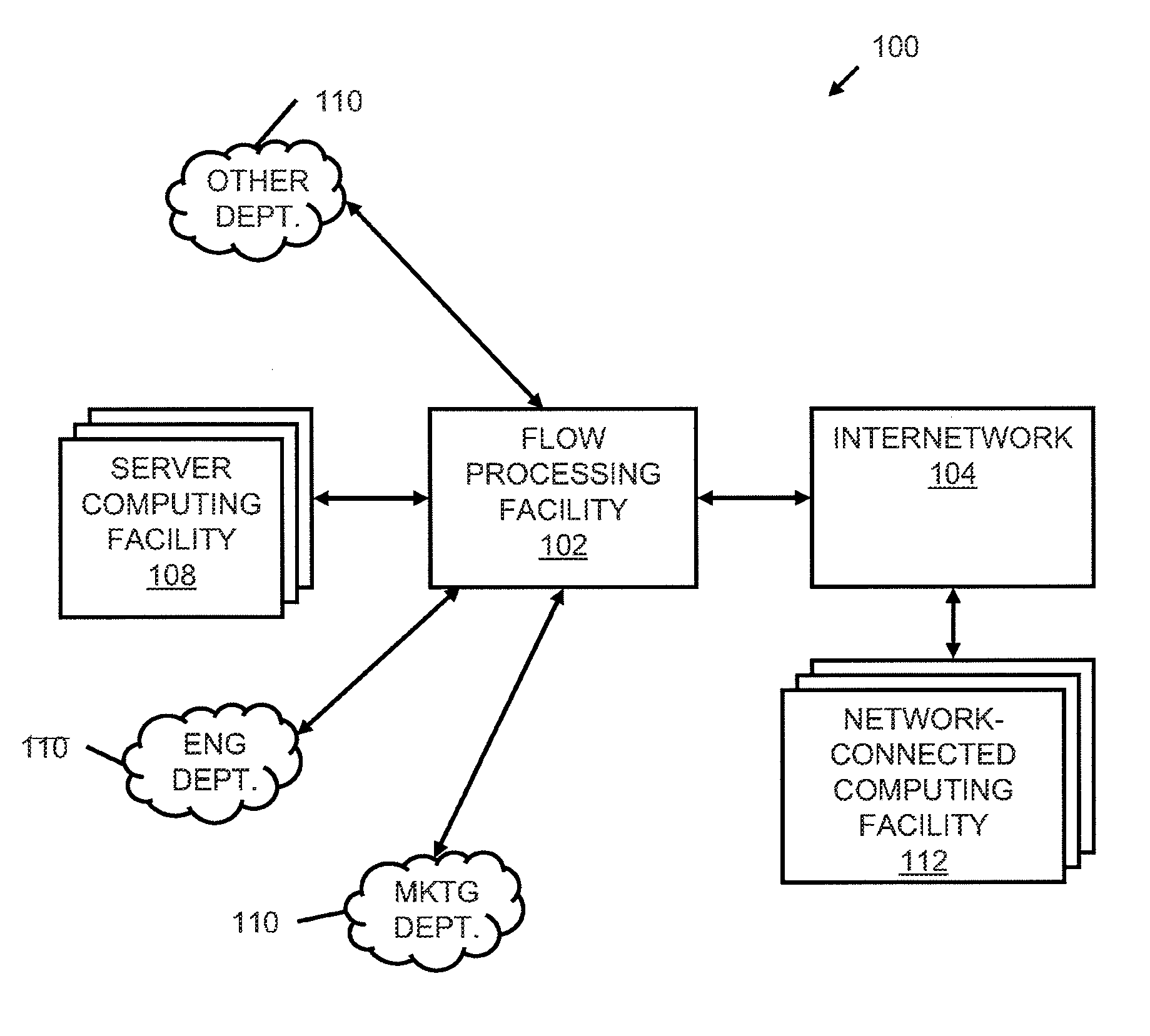
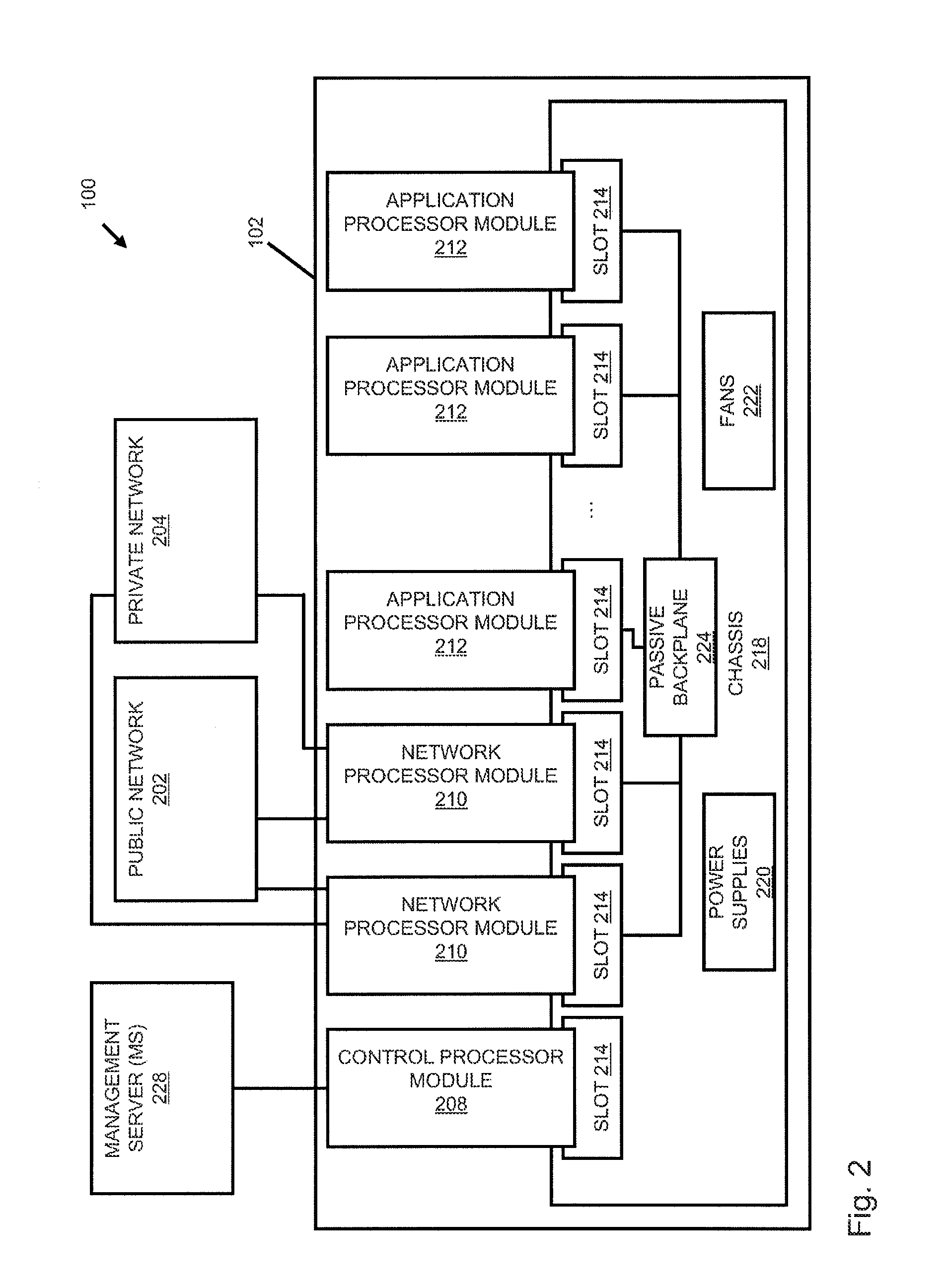
Systems and methods for processing data flows
InactiveUS20070192863A1Increased complexitySignificant expenseMemory loss protectionError detection/correctionData packData stream
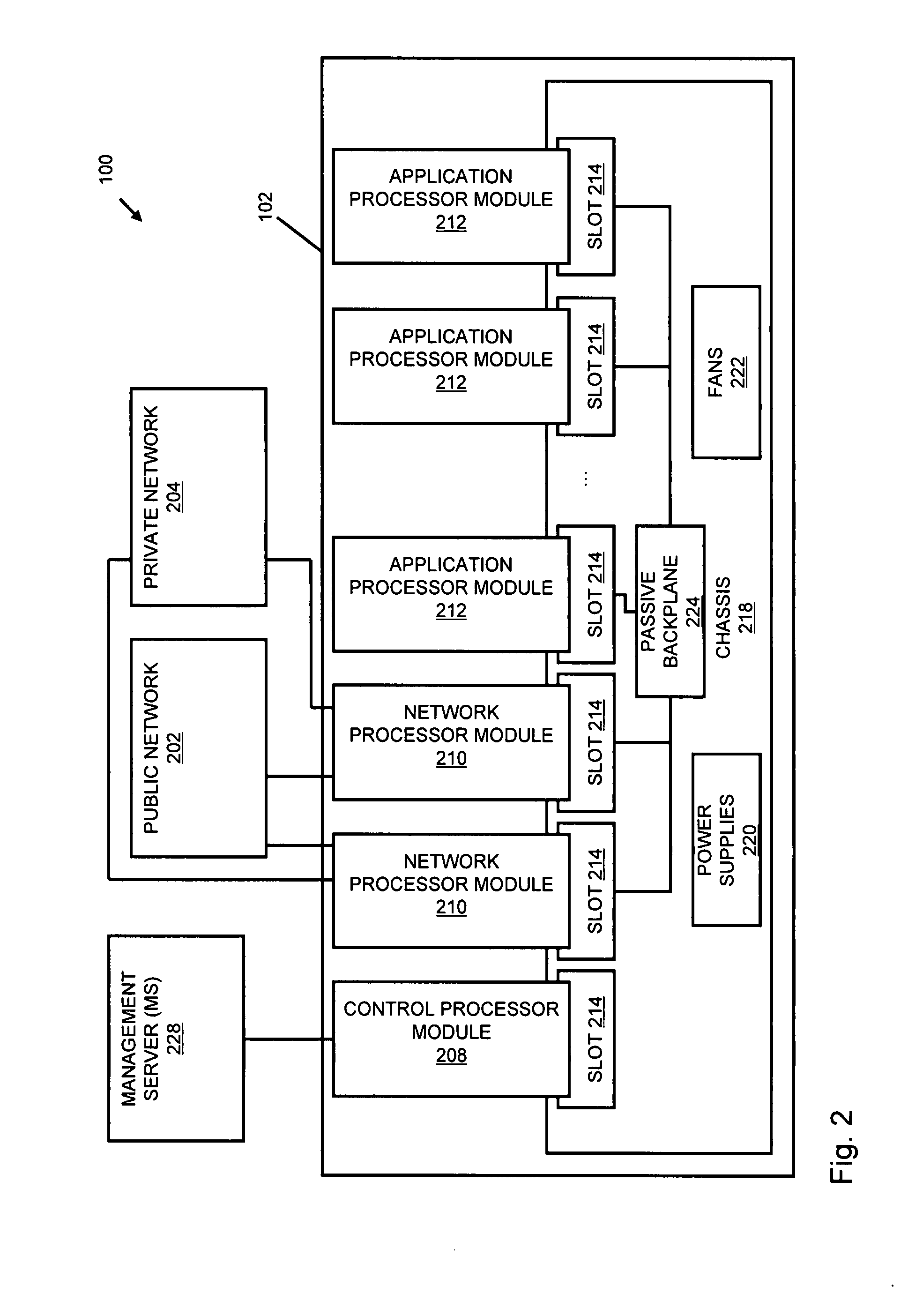
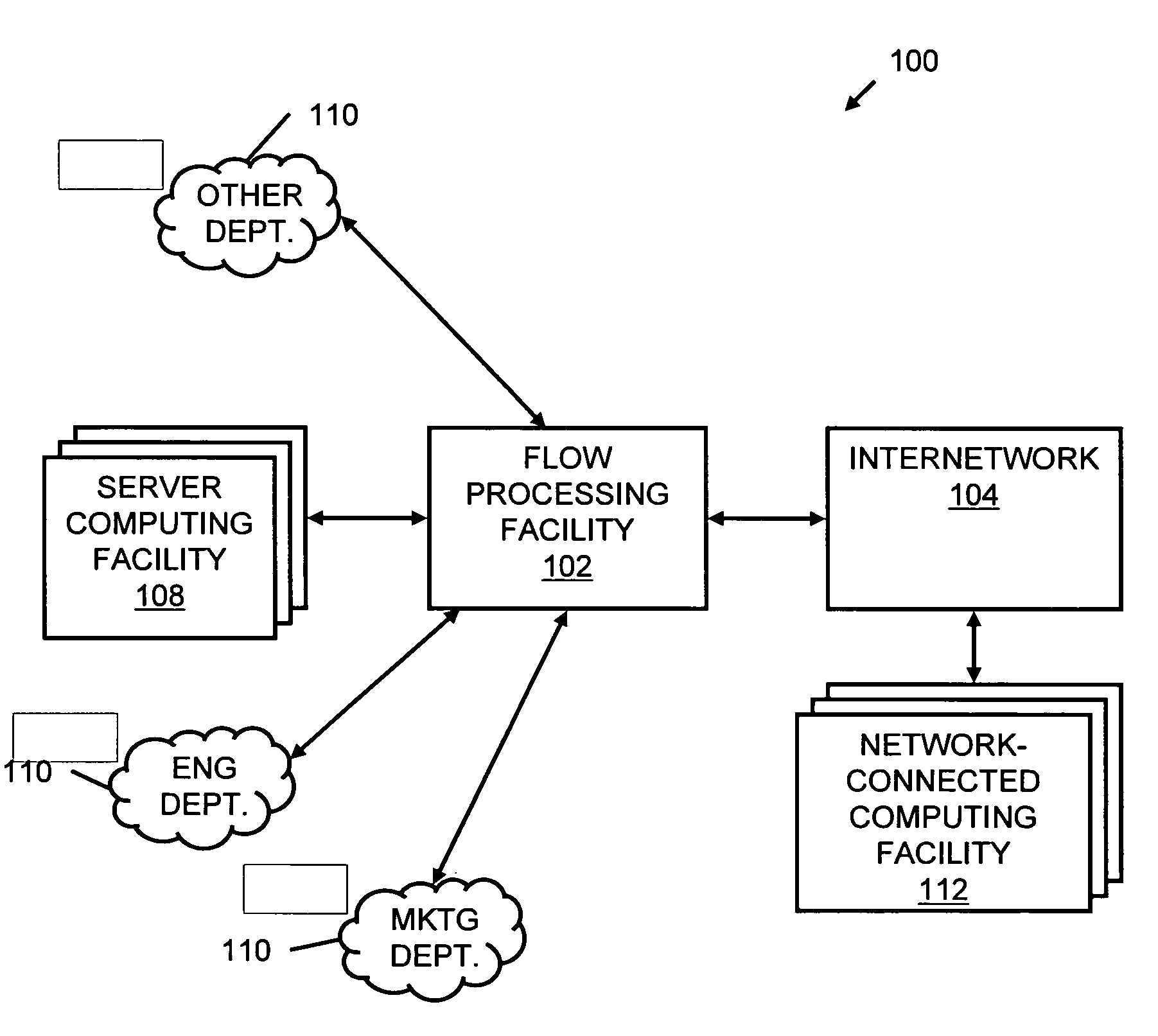
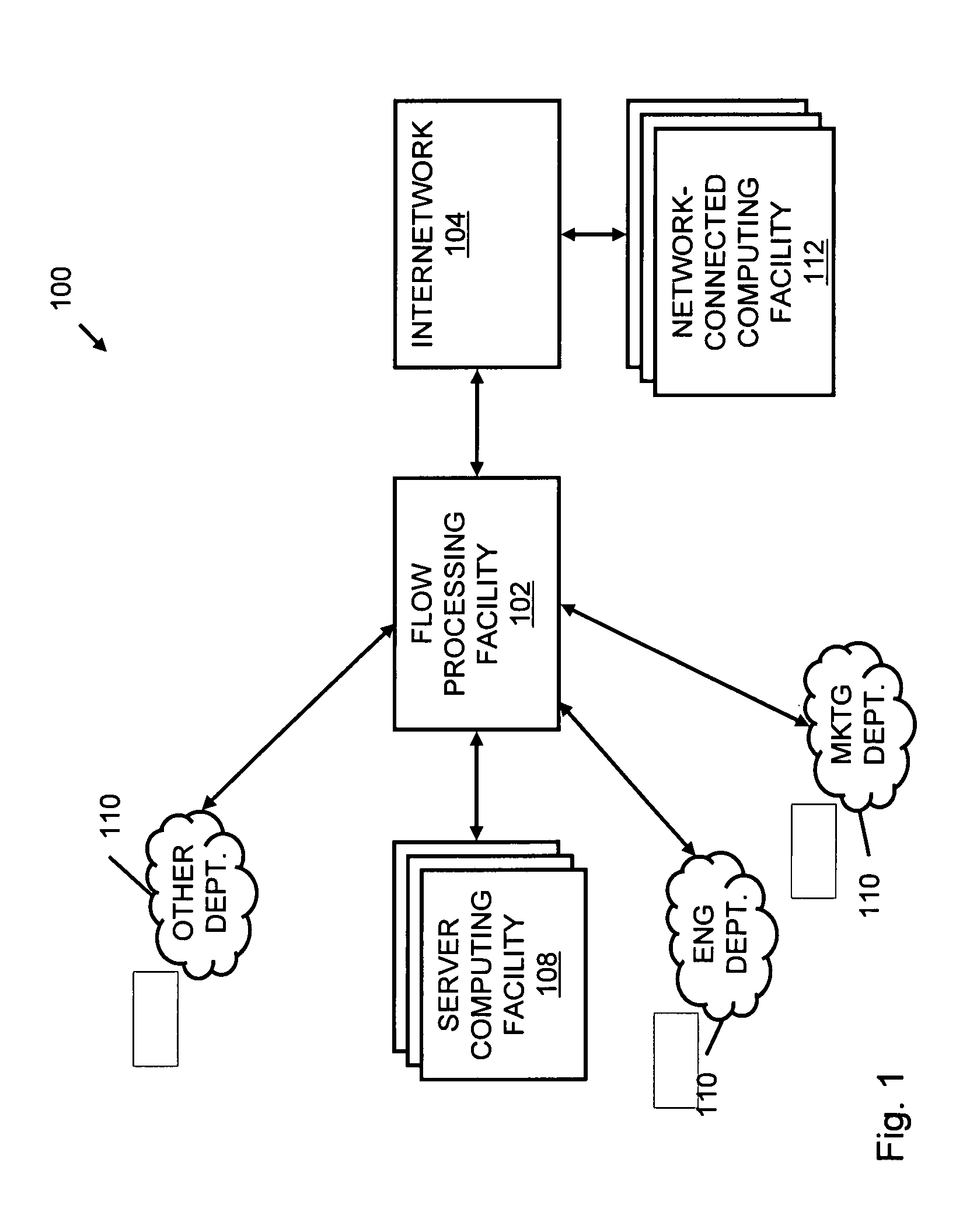
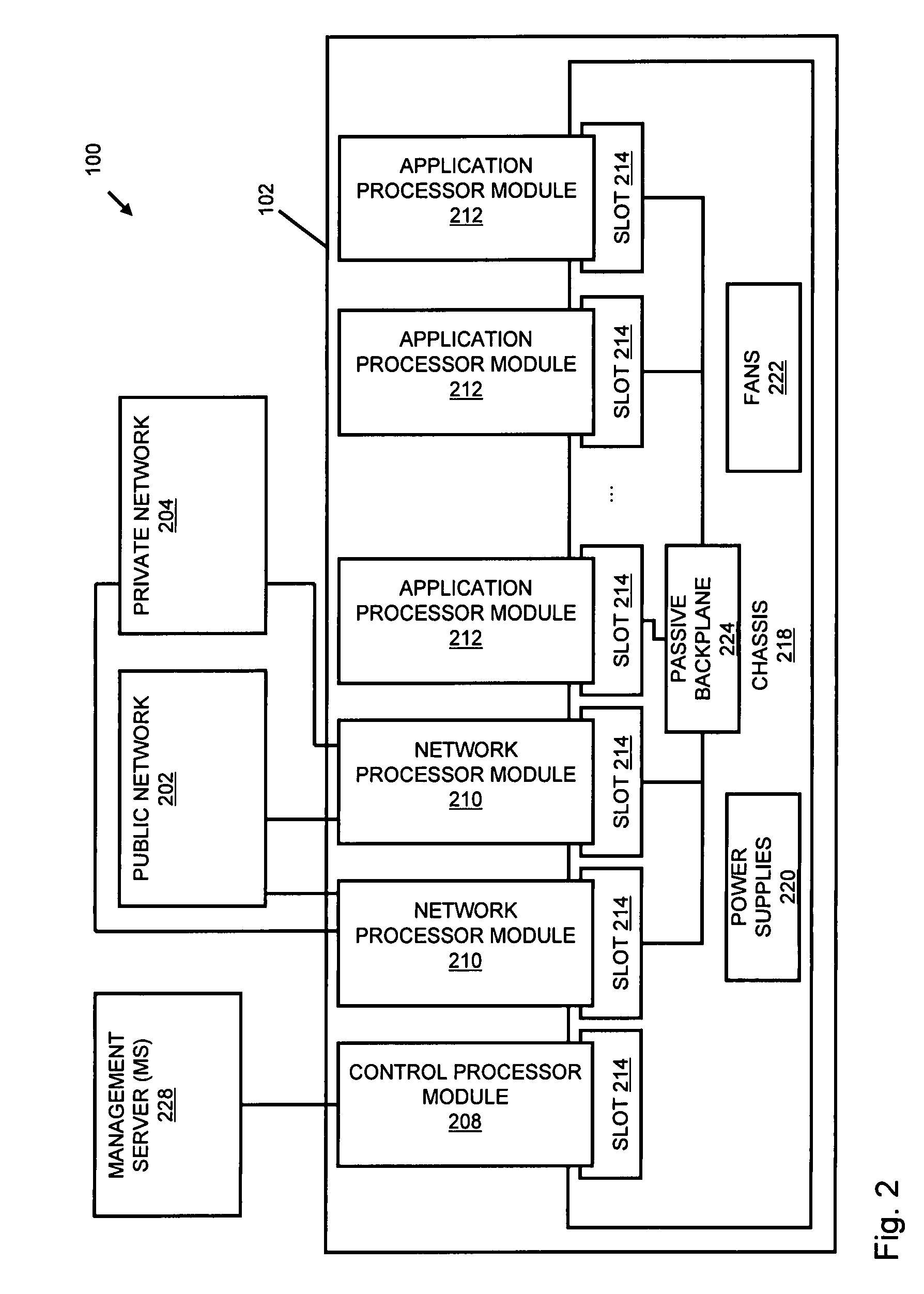
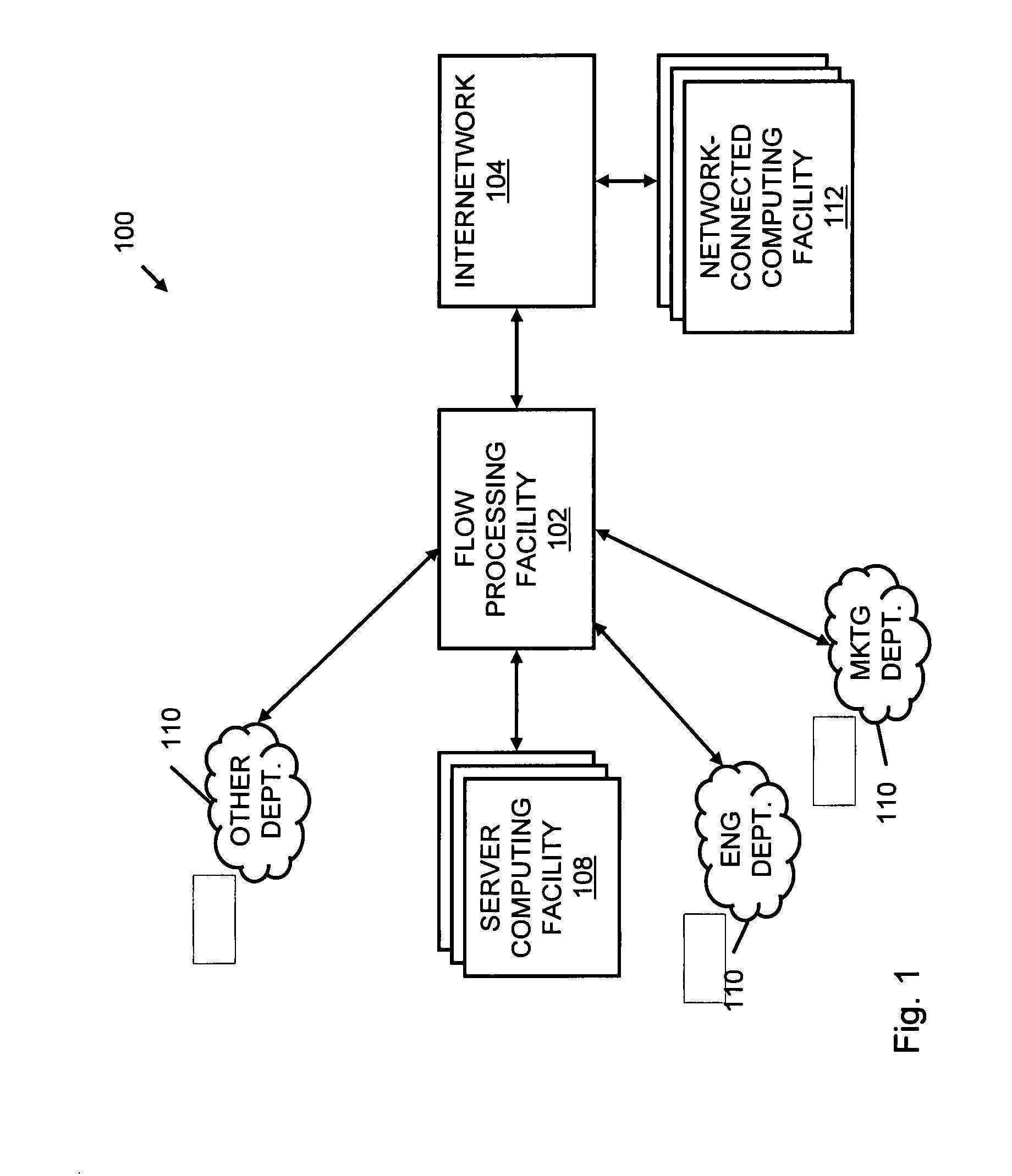
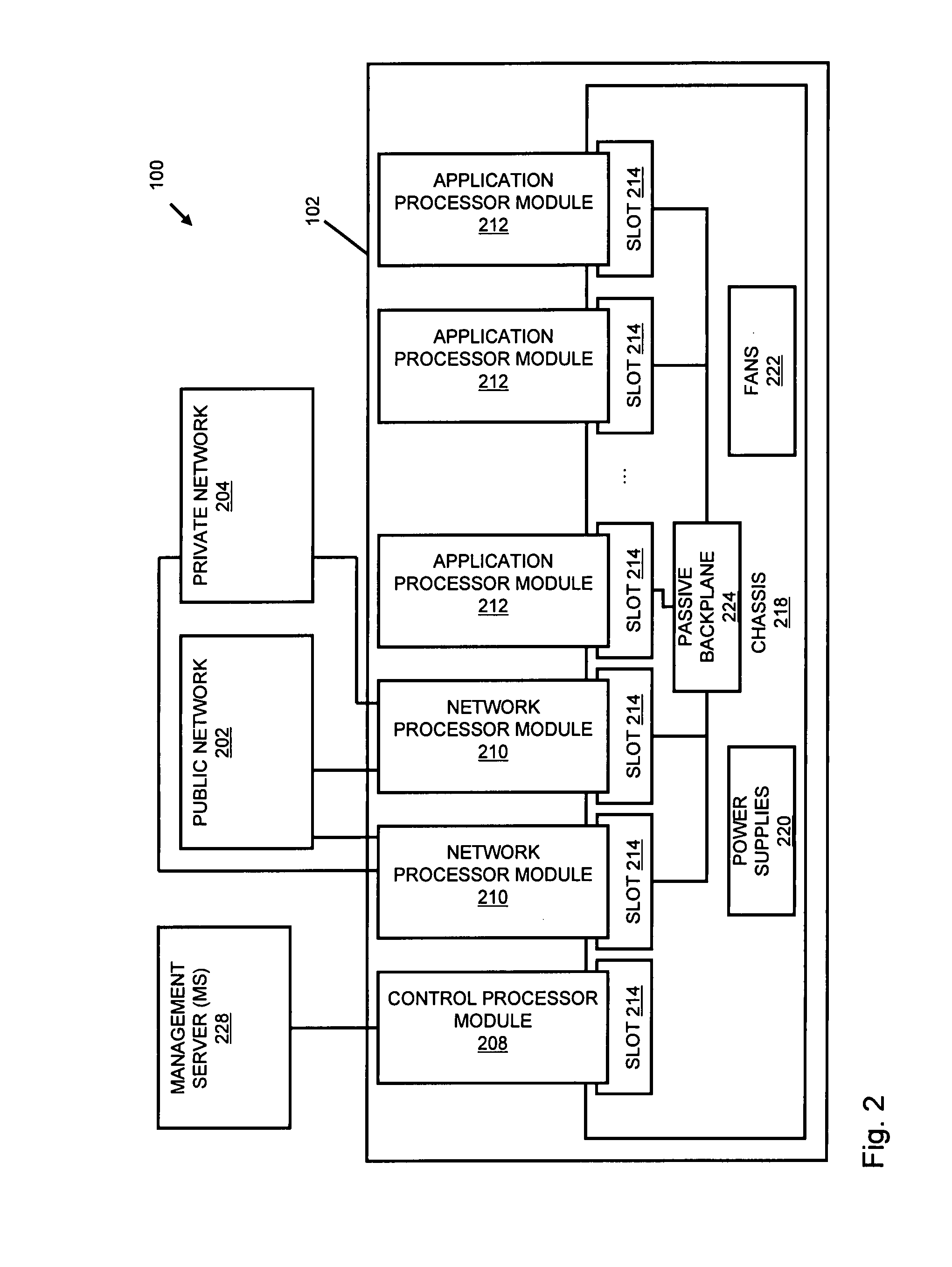
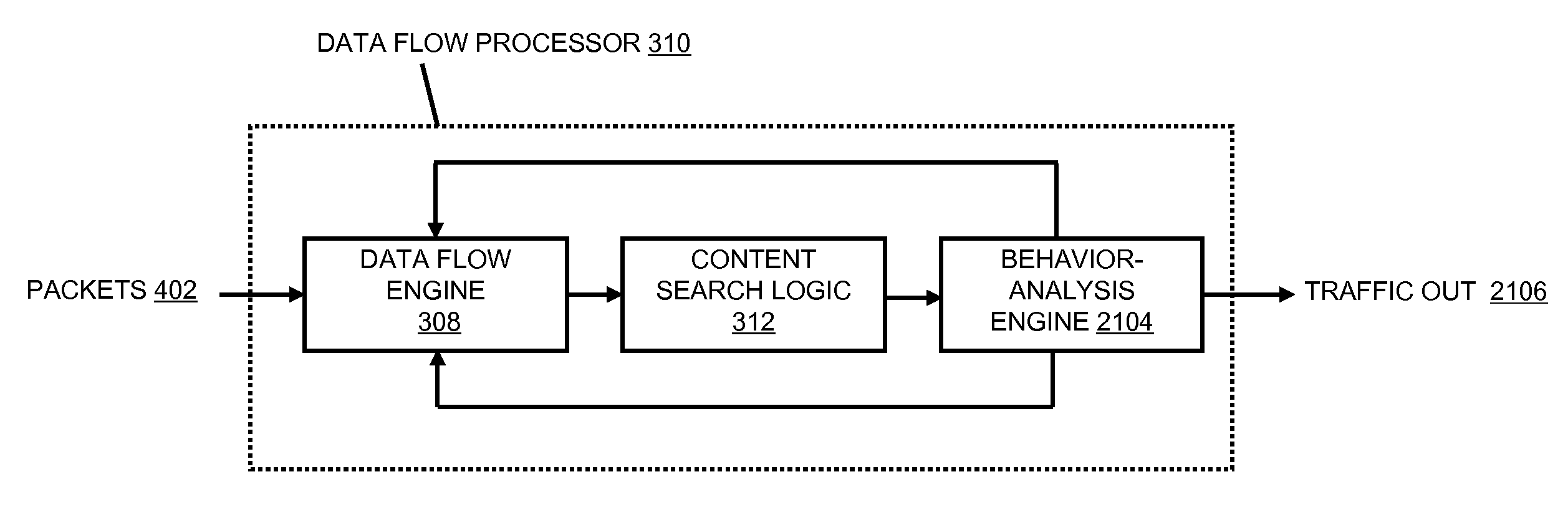
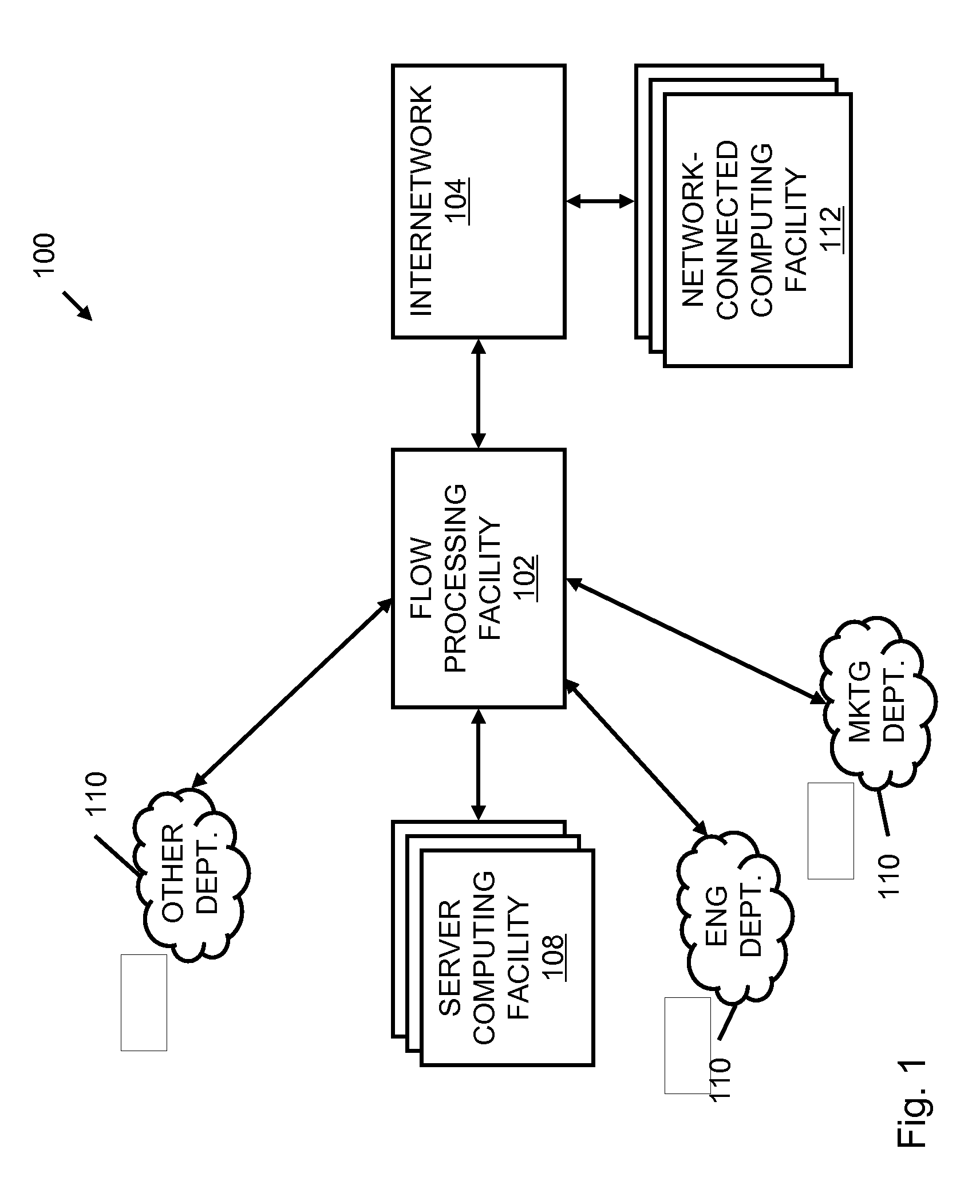
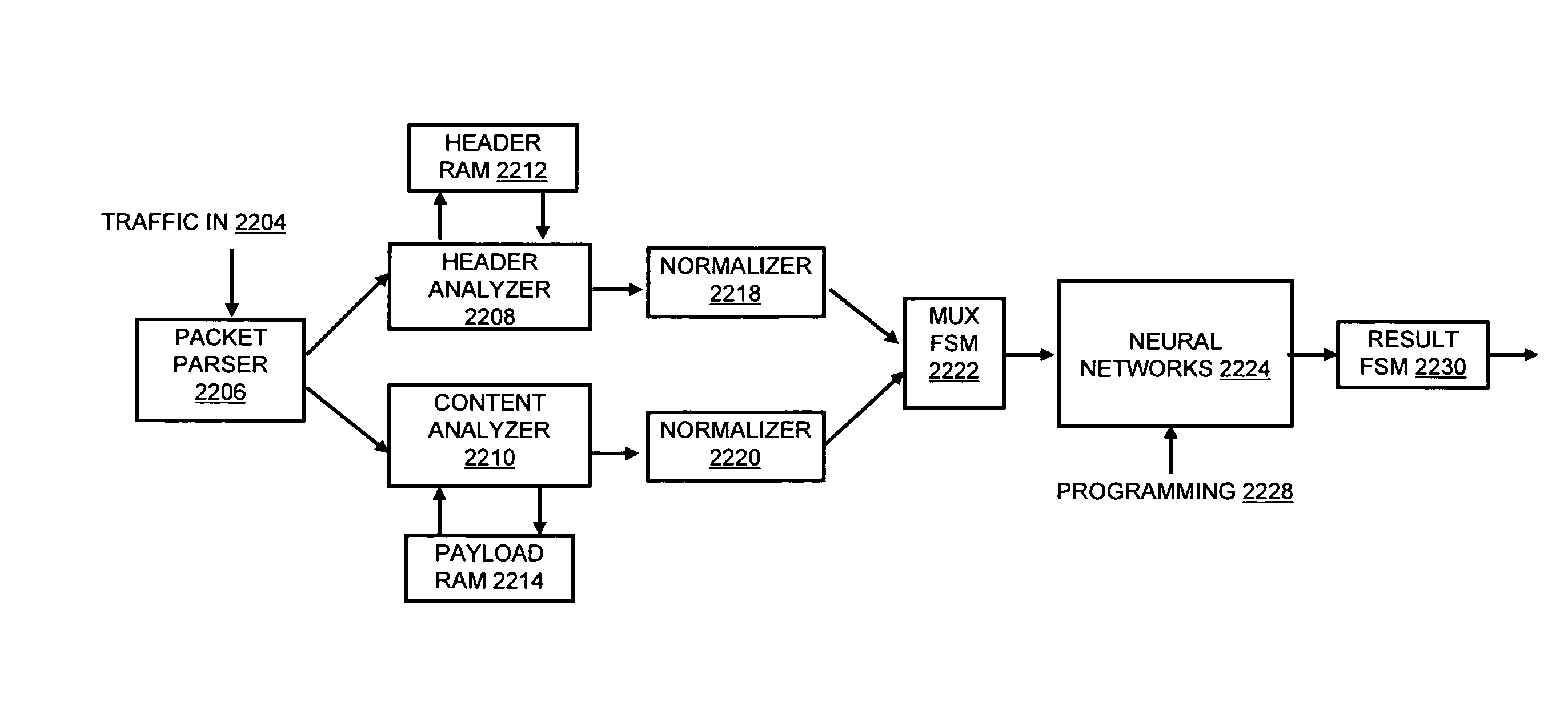
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080229415A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262991A1Easy to detectPreventing data flowDigital computer detailsBiological neural network modelsData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080134330A1Increased complexityAvoid problemsMemory loss protectionError detection/correctionData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
Systems and methods for processing data flows
InactiveUS20080262990A1Easy to detectPreventing data flowMemory loss protectionError detection/correctionData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS20080133518A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYST INC
Systems and methods for processing data flows
InactiveUS20080133517A1Increased complexityAvoid problemsPlatform integrity maintainanceProgram controlData integrityData stream
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:BLUE COAT SYSTEMS
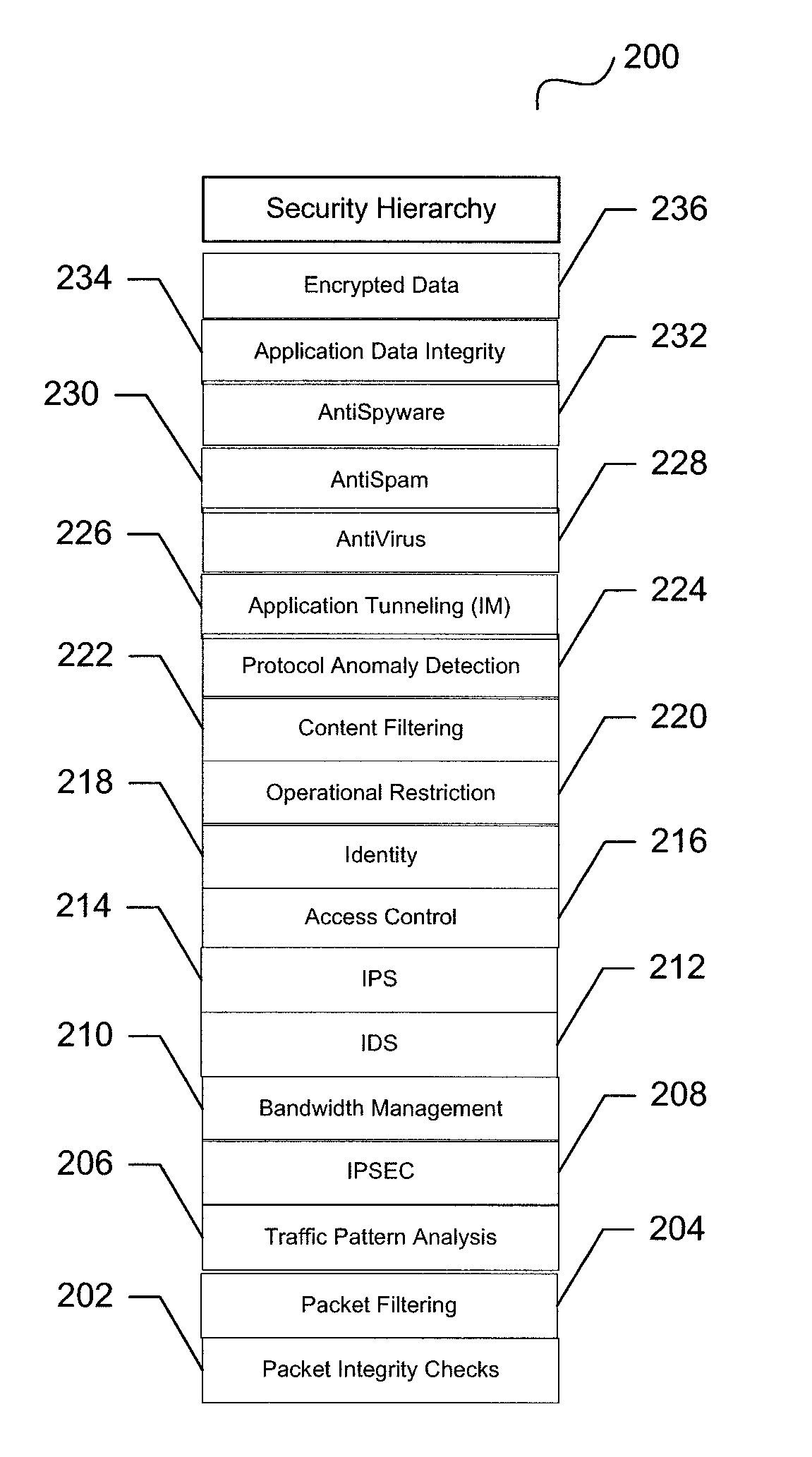
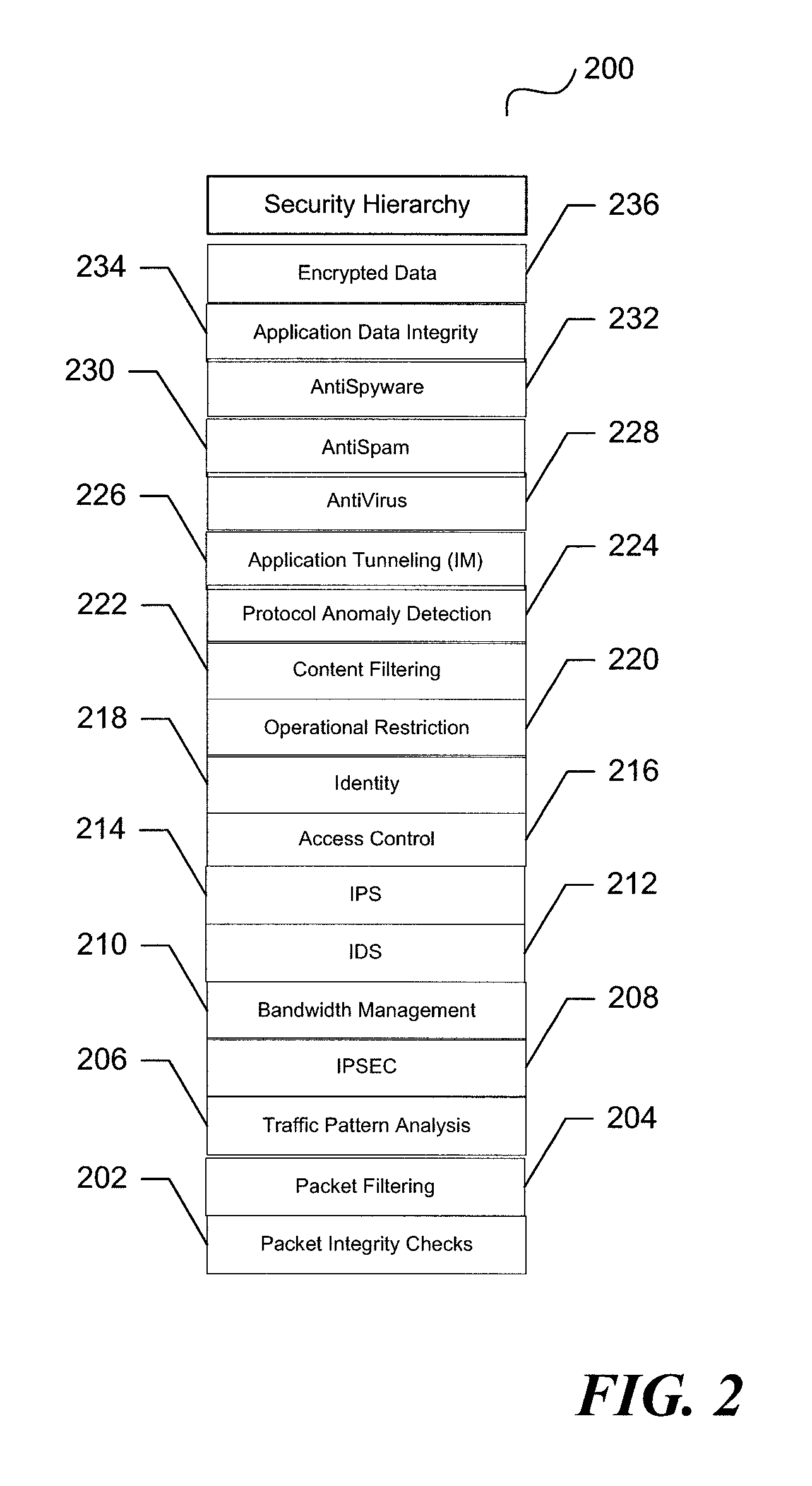
System and method for unified threat management with a relational rules methodology
ActiveUS7735116B1Improve performanceImprove securityDigital data processing detailsUser identity/authority verificationSecurity measurementSecurity Measure
A unified threat management system is provided with a uniform relational rules model. The unified relational rules model provides for the sub-setting of rules and the ability to derive a result based partially from previous security measurements. The sharing of a security check from one security implementation to another using an object-oriented methodology is facilitated. Security policy is divided into specific security features that result in a security hierarchy. The security features may be considered to be listed sequentially, from bottom to top, and form a relationship with one another. These relationships are used to build a current security measure upon a previous security measure and may be used as a pre-cursor when marshalling data content to be validated.
Owner:CA TECH INC
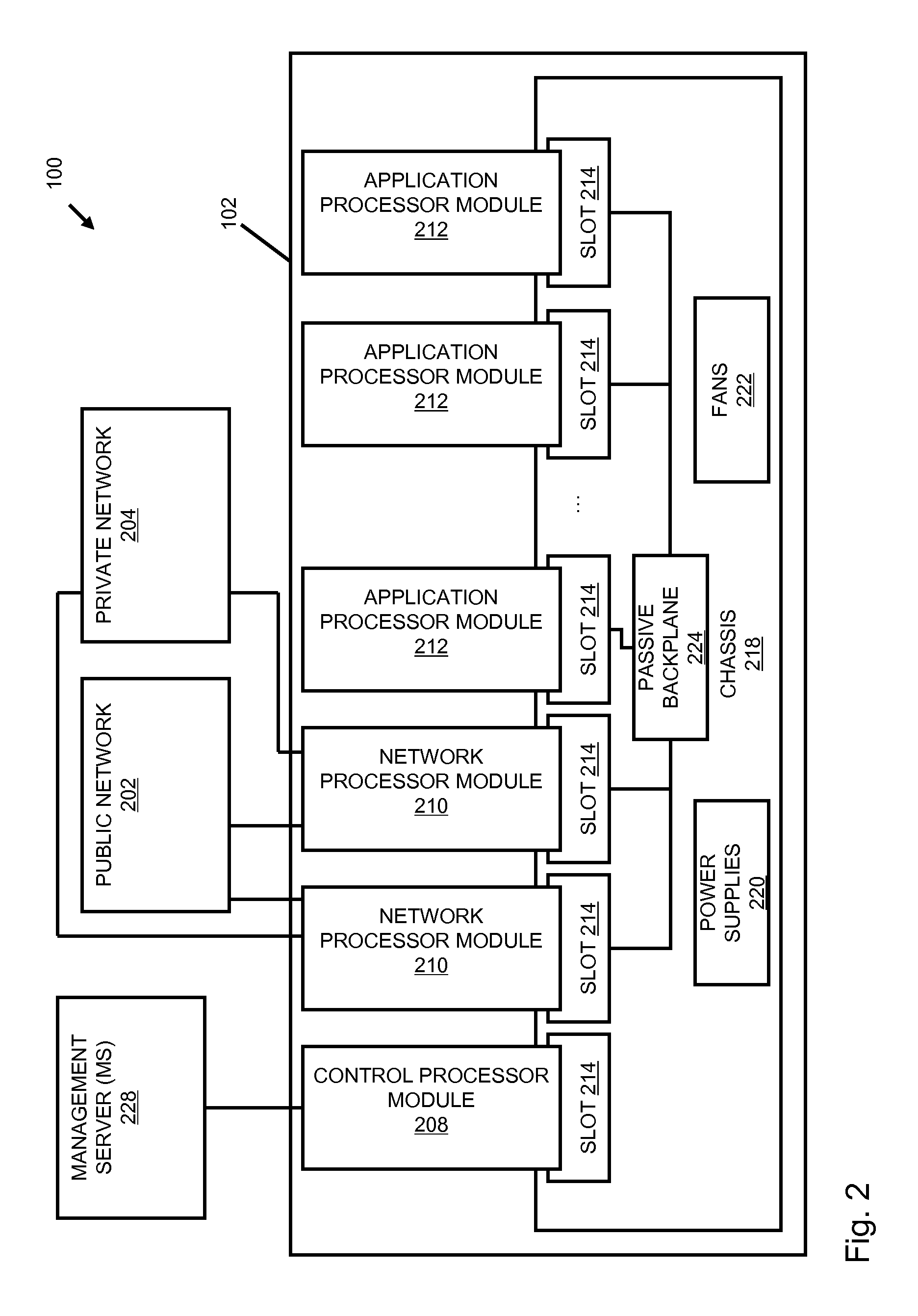
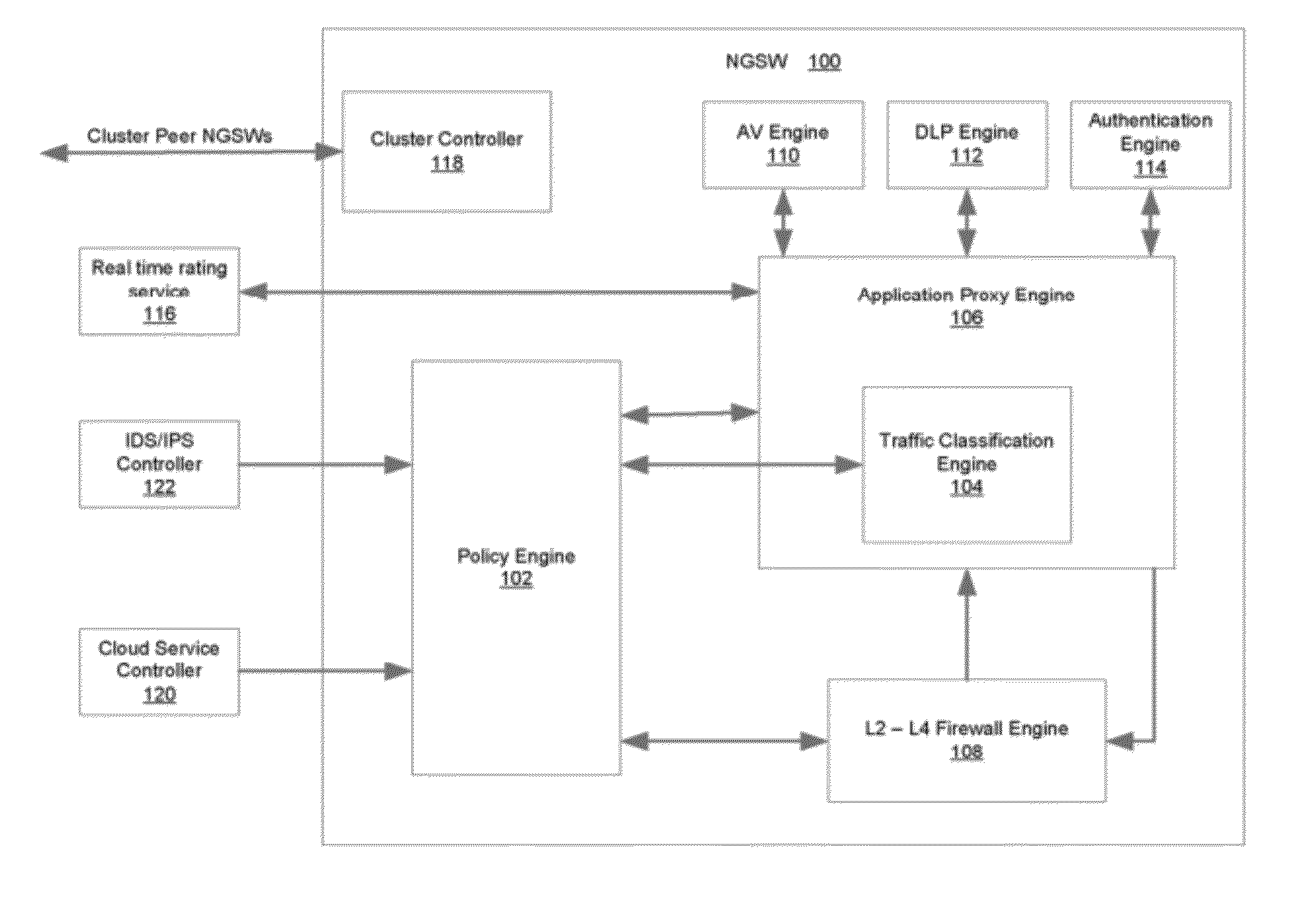
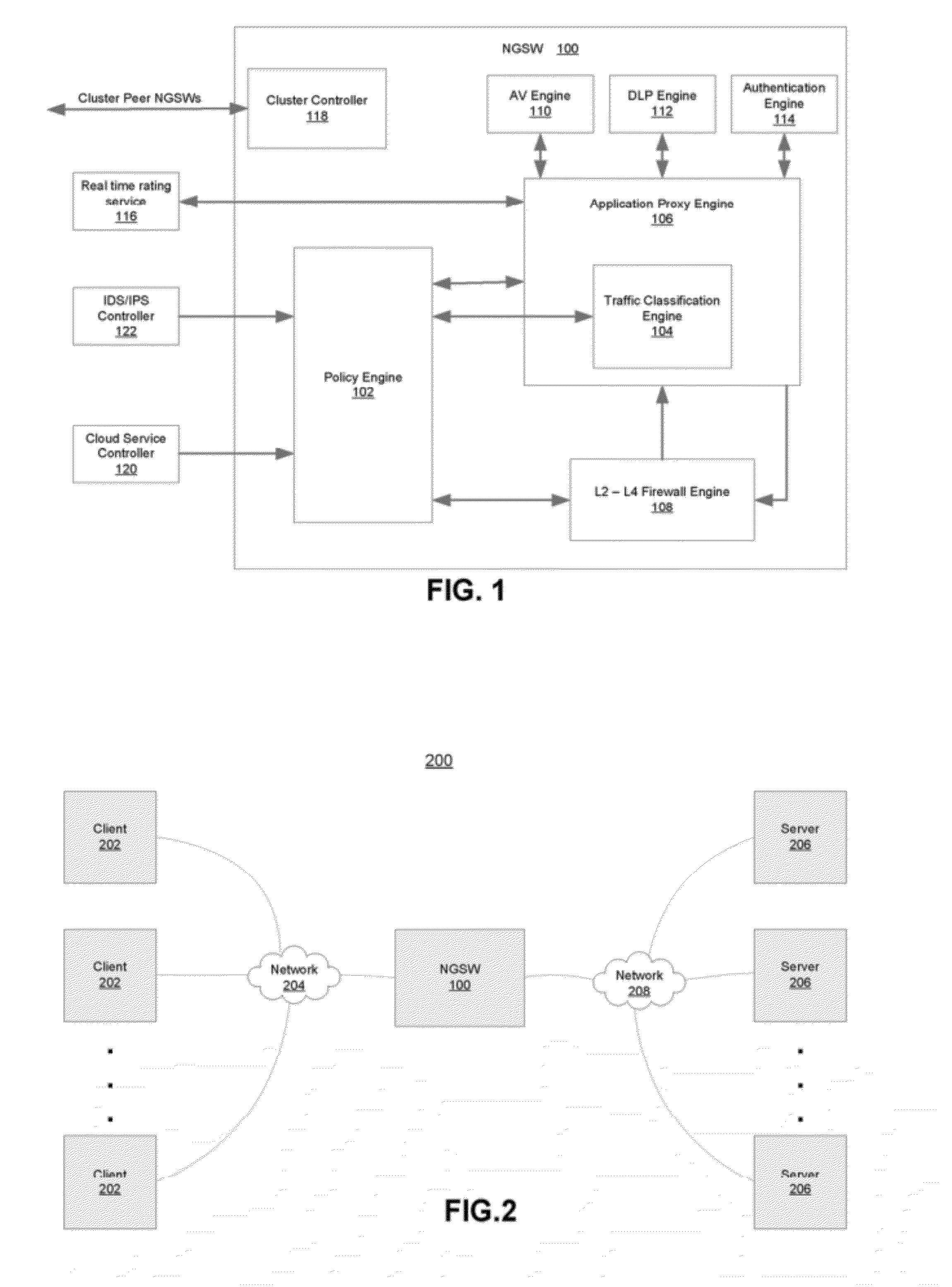
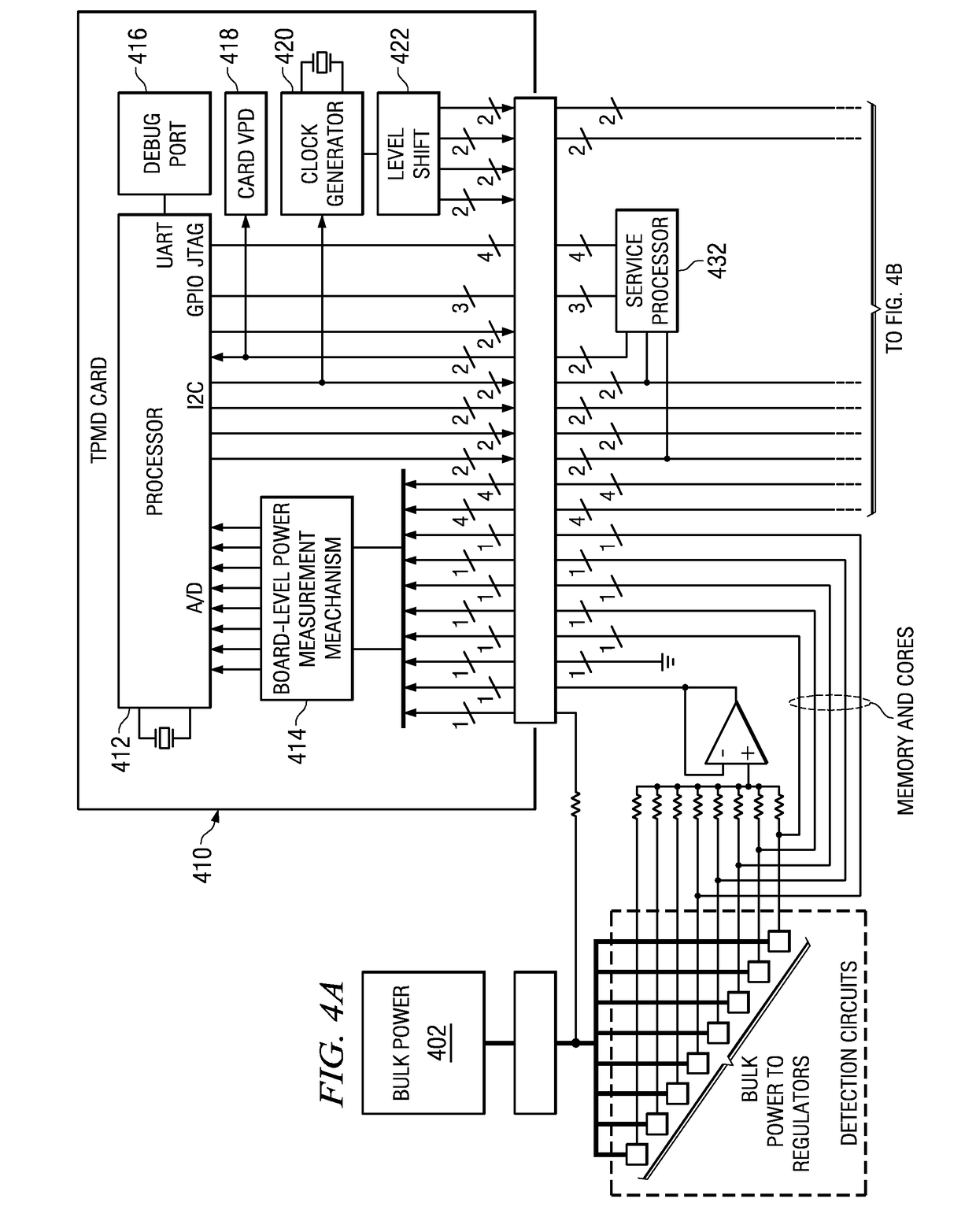
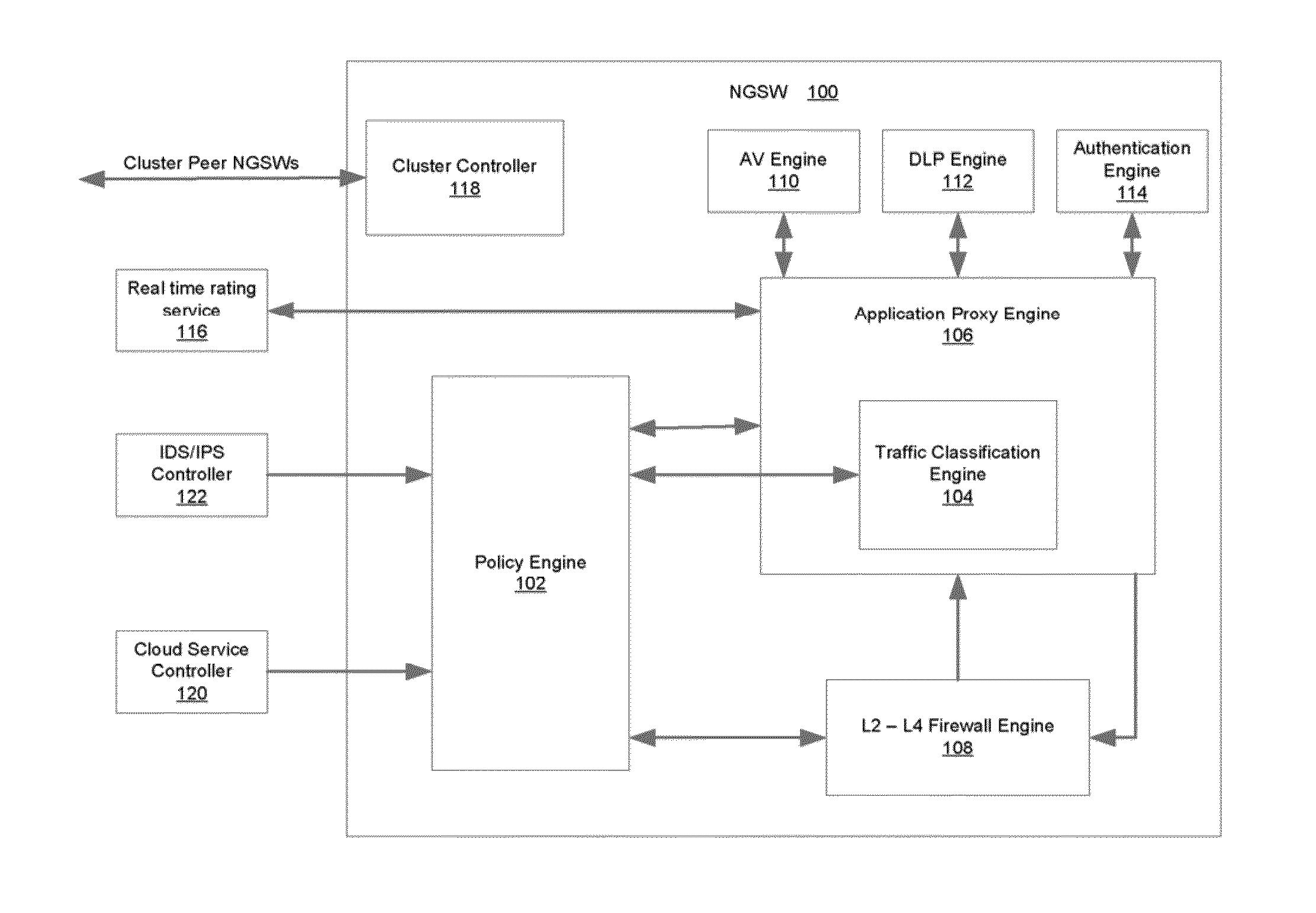
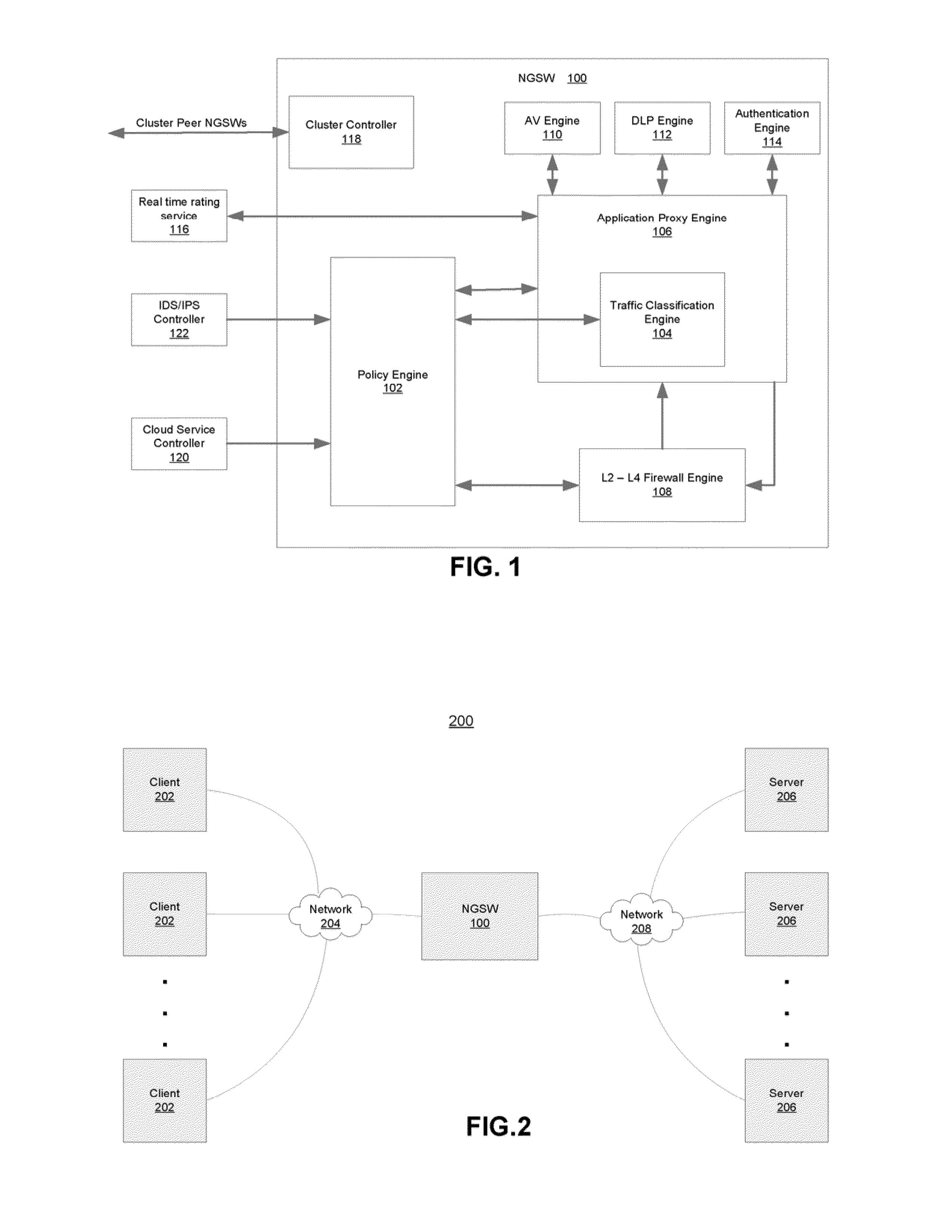
System and Method for Building Intelligent and Distributed L2 - L7 Unified Threat Management Infrastructure for IPv4 and IPv6 Environments
ActiveUS20120304277A1Easy to handleQuality of serviceComputer security arrangementsMultiple digital computer combinationsAnti virusApplication software
A security gateway appliance is configured to evaluate network traffic according to security rules that classify traffic flows according to specifically identified application programs responsible for producing and / or consuming the network traffic and to enforce policies in accordance with network traffic classifications. The appliance includes an on-box anti-virus / anti-malware engine, on-box data loss prevention engine and on-box authentication engine. One or more of these engines is informed by an on-box dynamic real tie rating system that allows for determined levels of scrutiny to be paid to the network traffic. Security gateways of this type can be clustered together to provide a set of resources for one or more networks, and in some instances as the backbone of a cloud-based service.
Owner:CA TECH INC
Systems and methods for processing data flows
InactiveUS7979368B2Increased complexityAvoid problemsDigital computer detailsDigital dataData packData stream
Owner:CA TECH INC
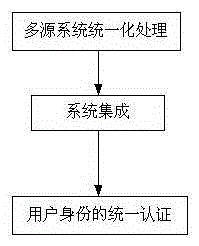
Unified authentication method for simulation identity
InactiveCN106612246AImprove the guarantee service abilityImprove service capabilitiesTransmissionSystem integrationPassword
The invention discloses a unified authentication method for a simulation identity, and belongs to the technical field of computer application. The unified authentication method is characterized by comprising the steps of 1, multi-source system unified processing, 2, system integration and 3, unified authentication for the user identity. The advantages are that the method in the embodiment of the invention adopts a corresponding means of identity authentication and a means of performing unified processing on systems with different architectures so as to enable a user to log in a plurality of related systems to perform business processing by only a single user name and a single password when the user logs in the associated systems. Unified management, authority setting and the like are performed on the user. The unified authentication method lays a foundation for construction of an information service system through standardized administration of an information-based means, the safeguard service ability is improved in continuous promotion for the information-based infrastructure construction, a platform support is provided for comprehensively promoting the information construction, and a foundation is laid for the timeliness and the integrity of information resources.
Owner:星际空间(天津)科技发展有限公司
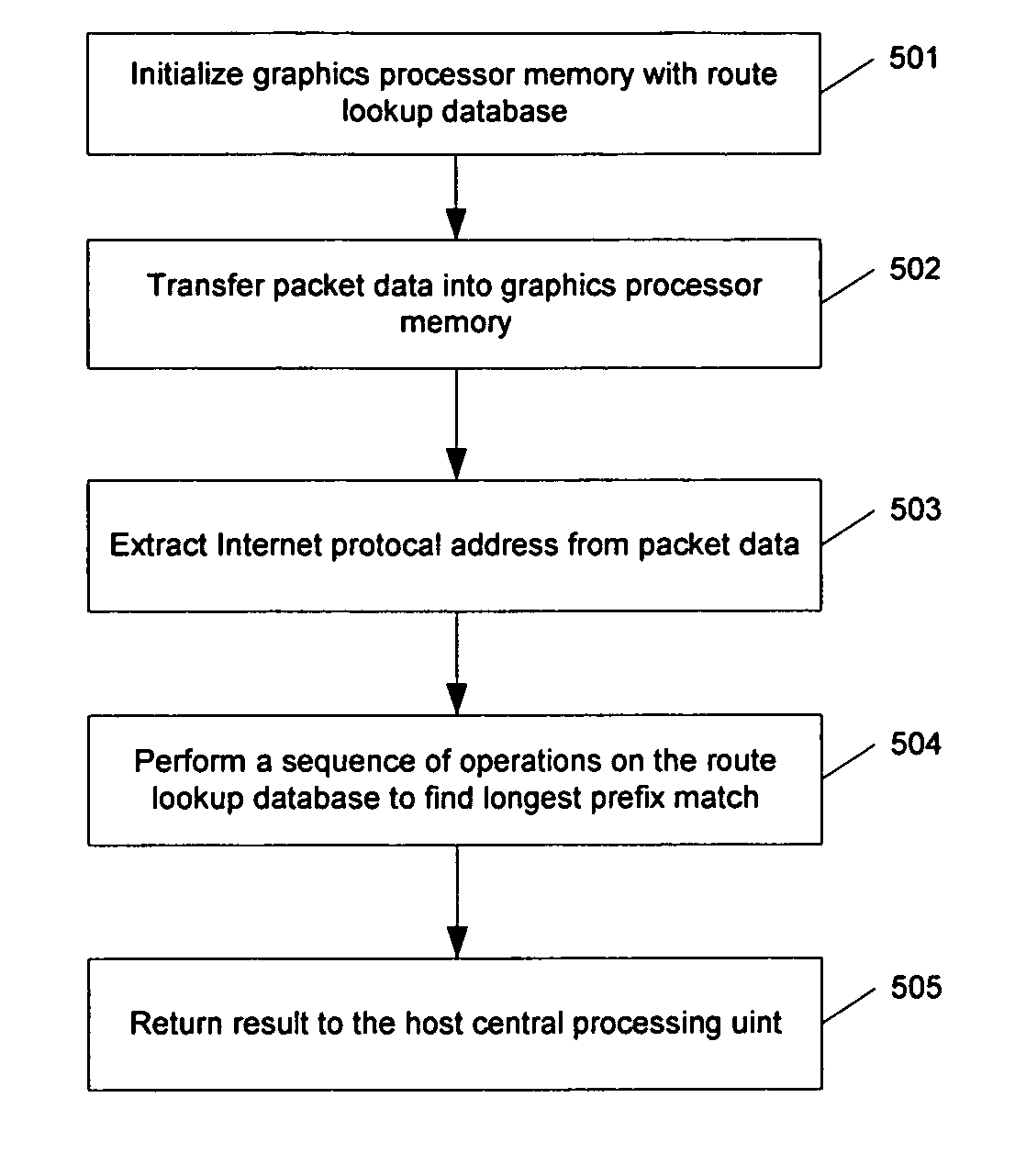
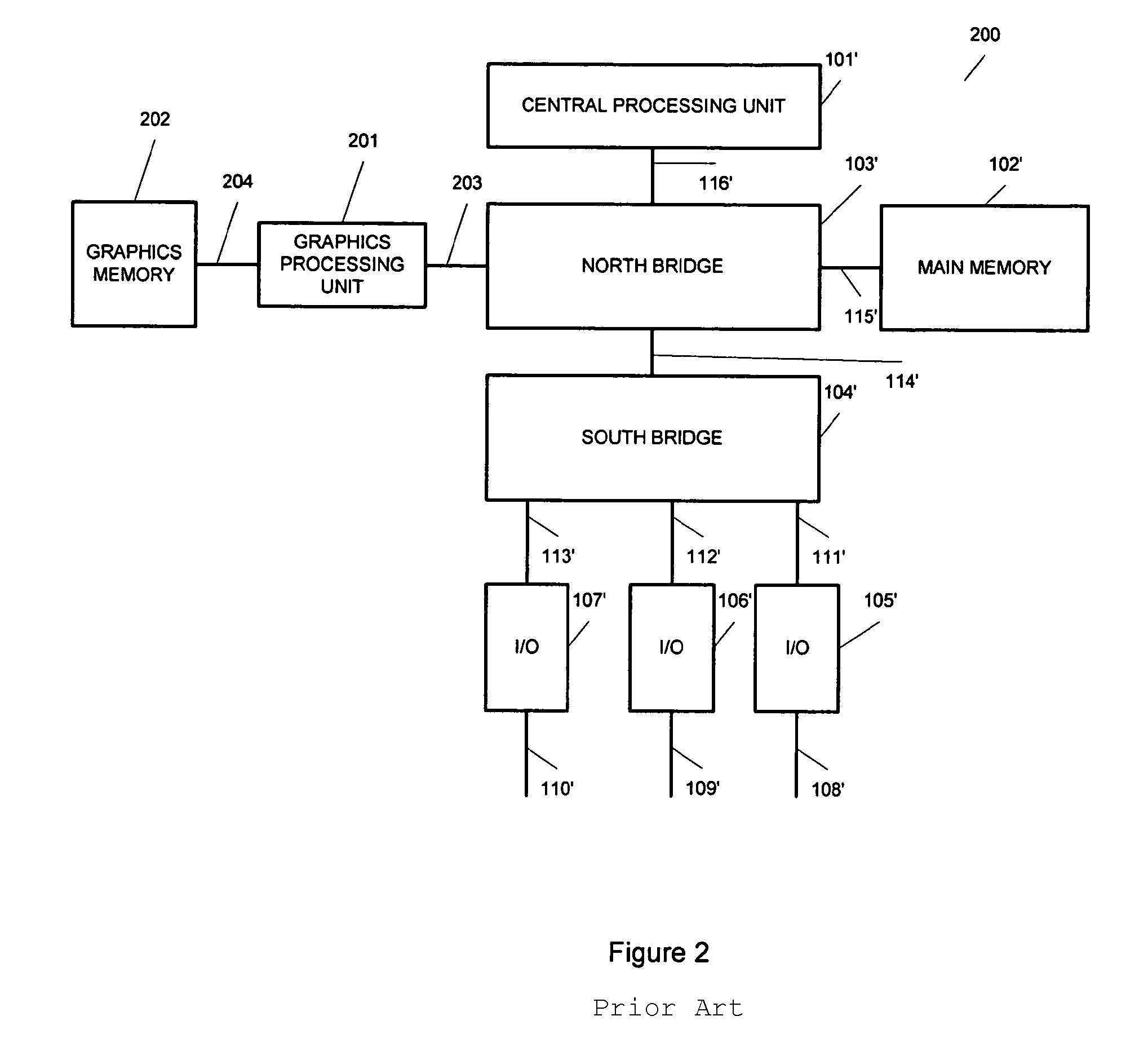
System and method for a fast, programmable packet processing system
InactiveUS20060242710A1Improve performanceEnhanced network operationMemory loss protectionError detection/correctionData packHandling system
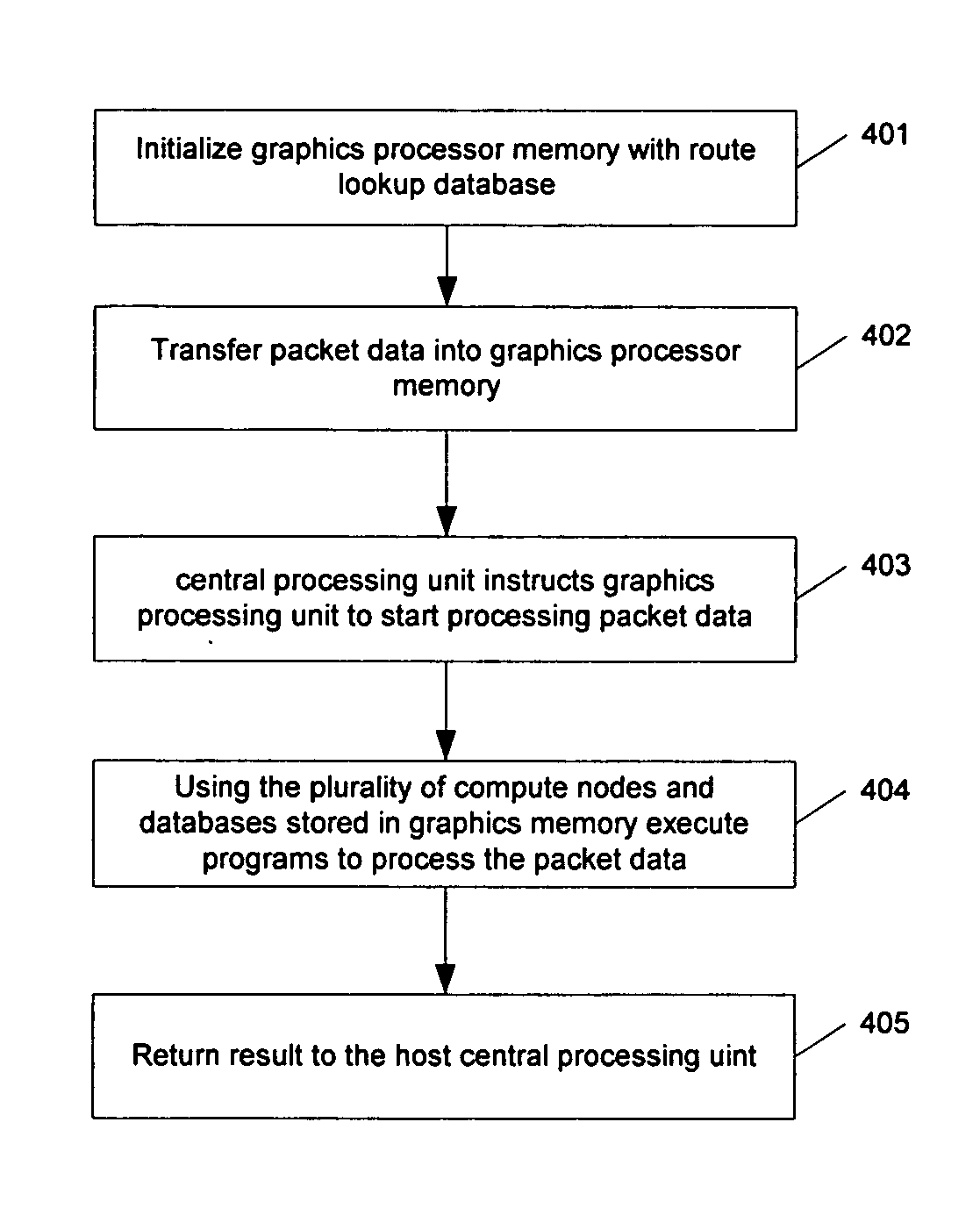
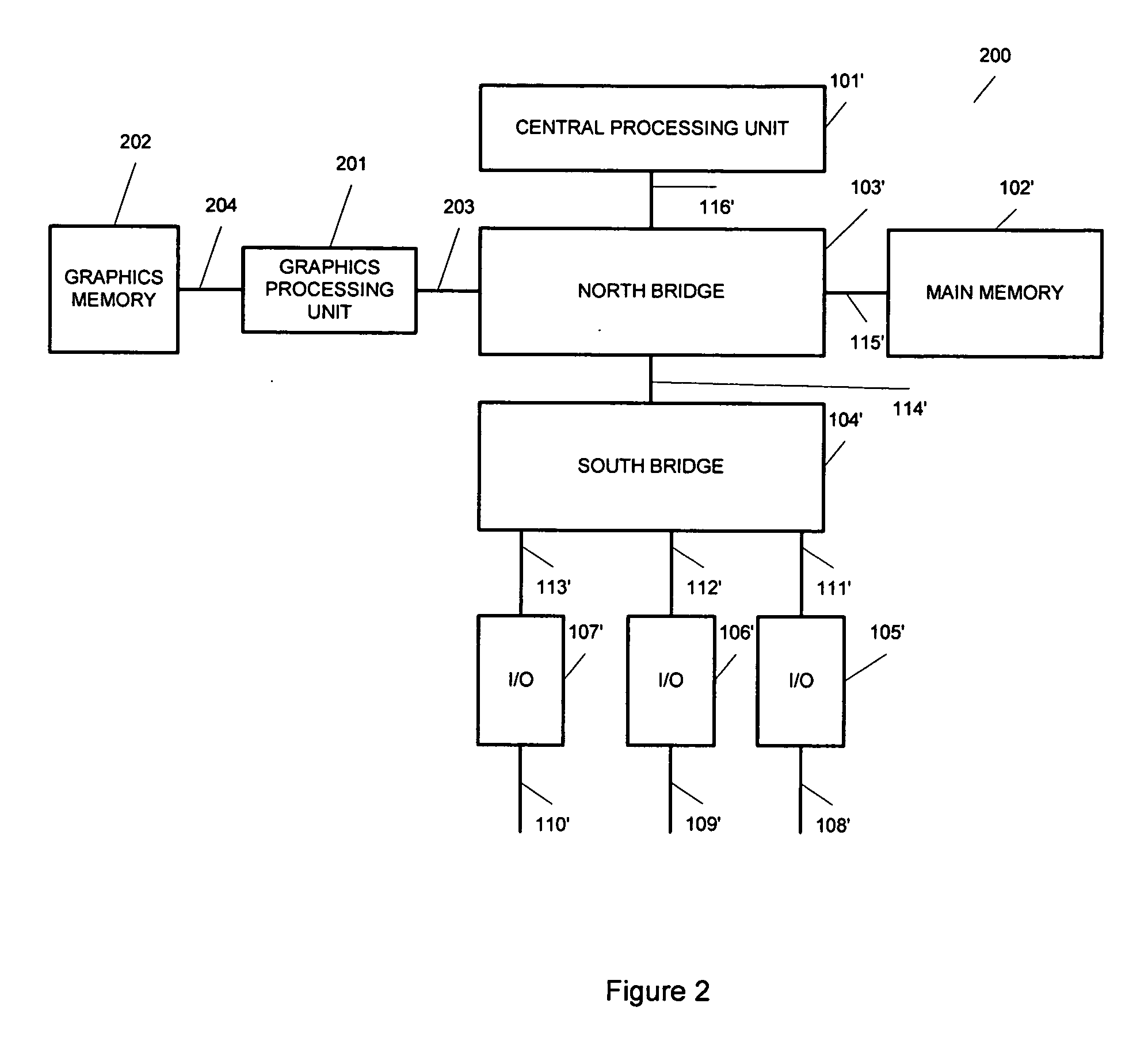
The present invention provides a cost effective method to improve the performance of communication appliances by retargeting the graphics processing unit as a coprocessor to accelerate networking operations. A system and method is disclosed for using a coprocessor on a standard personal computer to accelerate packet processing operations common to network appliances. The appliances include but are not limited to routers, switches, load balancers and Unified Threat Management appliances. More specifically, the method uses common advanced graphics processor engines to accelerate the packet processing tasks.
Owner:ALEXANDER THOMAS
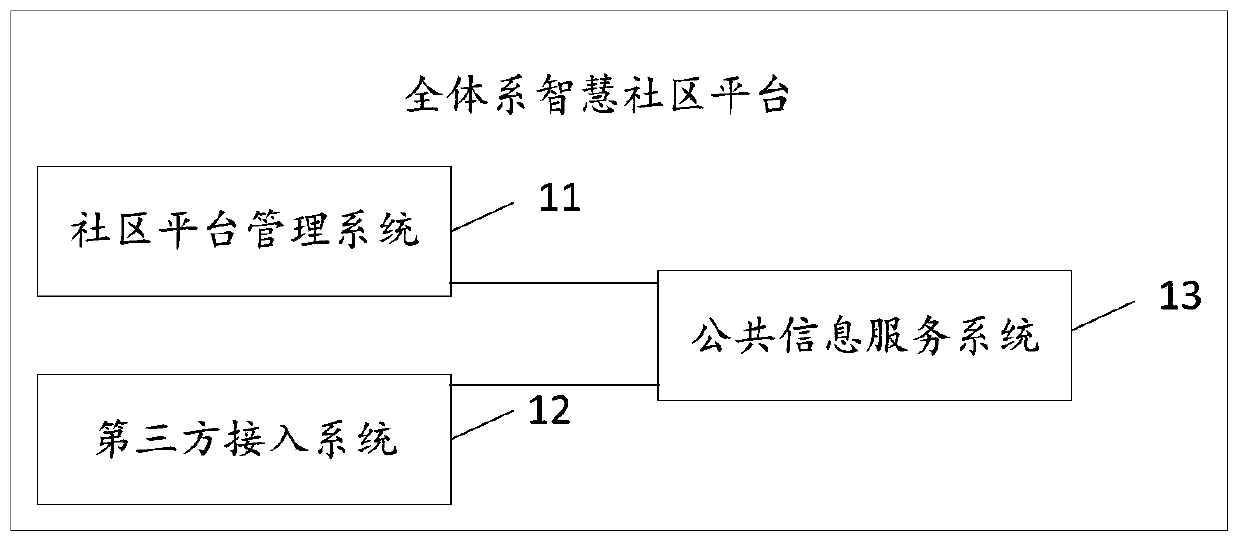
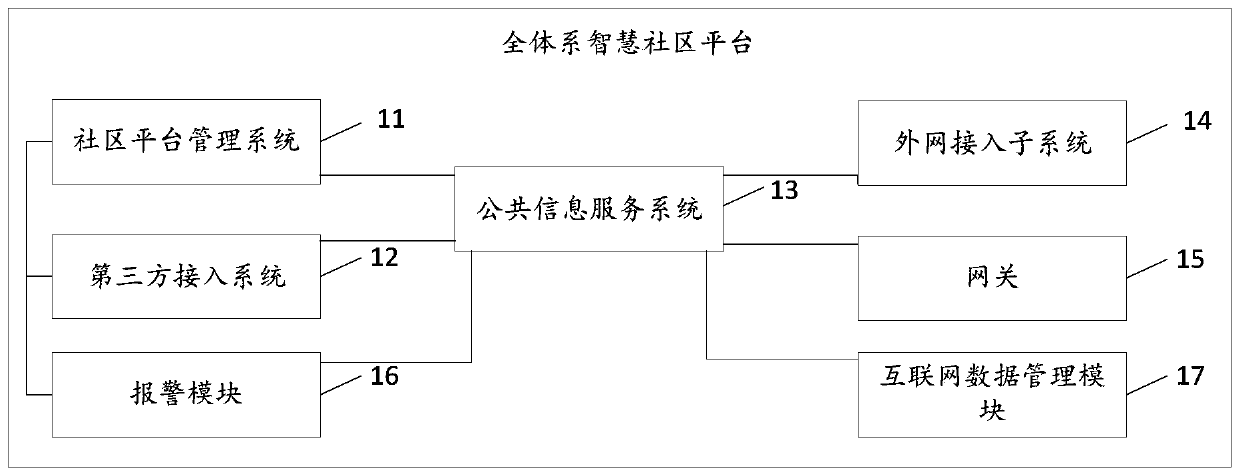
Whole-system intelligent community platform
ActiveCN109729180AConvenient and high-quality lifeData processing applicationsTransmissionThe InternetIntelligent equipment
The invention discloses a whole-system intelligent community platform, and relates to the technical field of Internet, and mainly aims to solve the problems that system equipment of an existing community cannot realize unified management, intelligent linkage and data fusion, the community does not have a unified sustainable business and service operation platform channel, and more convenience cannot be brought to residents, managers, service parties, business and the like. The whole-system intelligent community platform comprises a community platform management system, a third-party access system and a public information service system. The whole-system intelligent community platform in the embodiment of the invention provides an open interface for users needing to be accessed to a third-party intelligent equipment system, as object management, residents, merchants and the like, supports seamless access of various manufacturer platforms, systems and hardware, realize dual backup through unified management, deployment and data management of the community platform management system, are safe and reliable, can provide various business and service operations, and create more convenientand faster high-quality life.
Owner:SHENZHEN ANENDA TECH
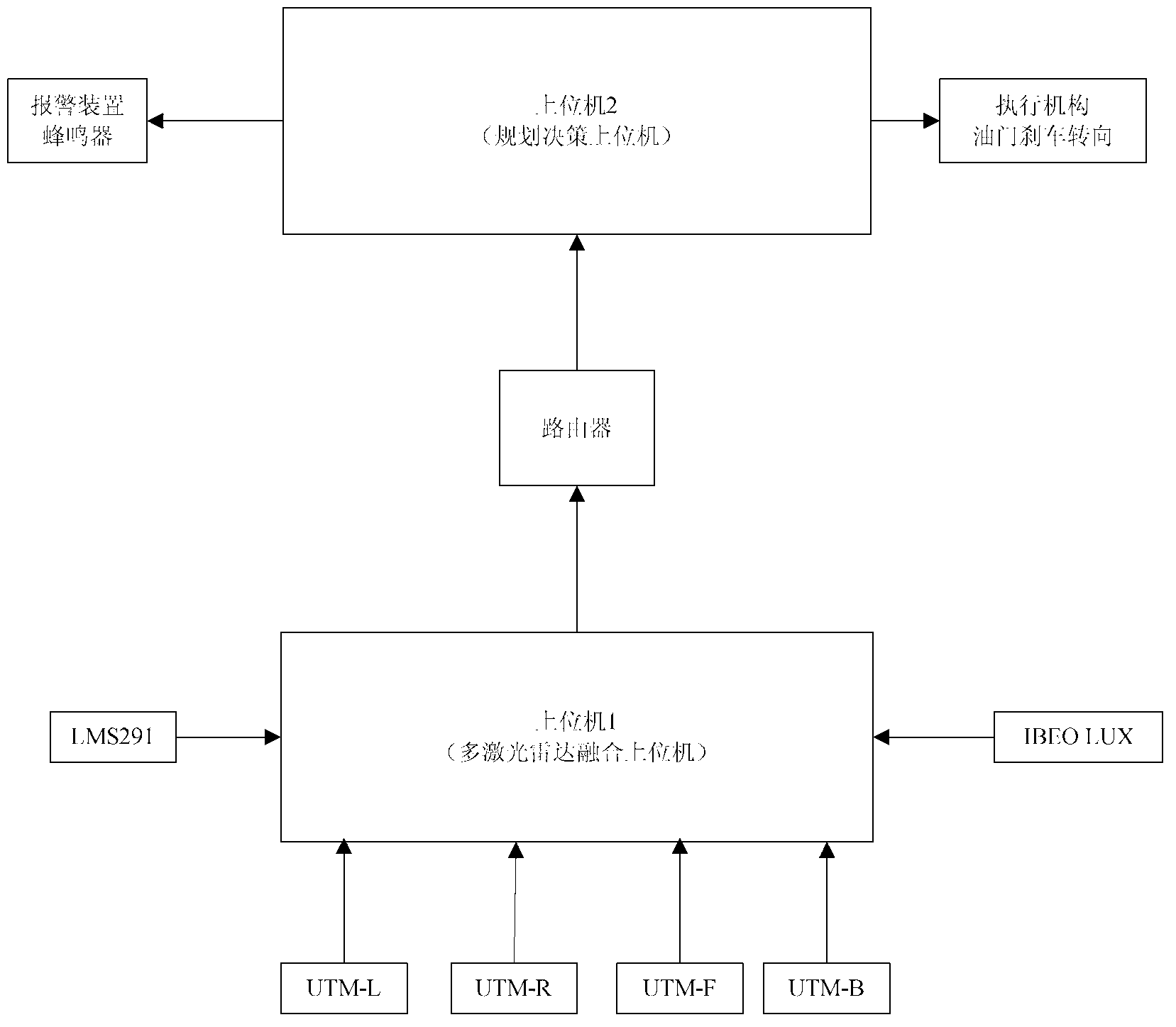
Intelligent vehicle multi-laser-radar data integration system and method thereof
InactiveCN102837658AImprove securityPedestrian/occupant safety arrangementElectromagnetic wave reradiationRadarEngineering
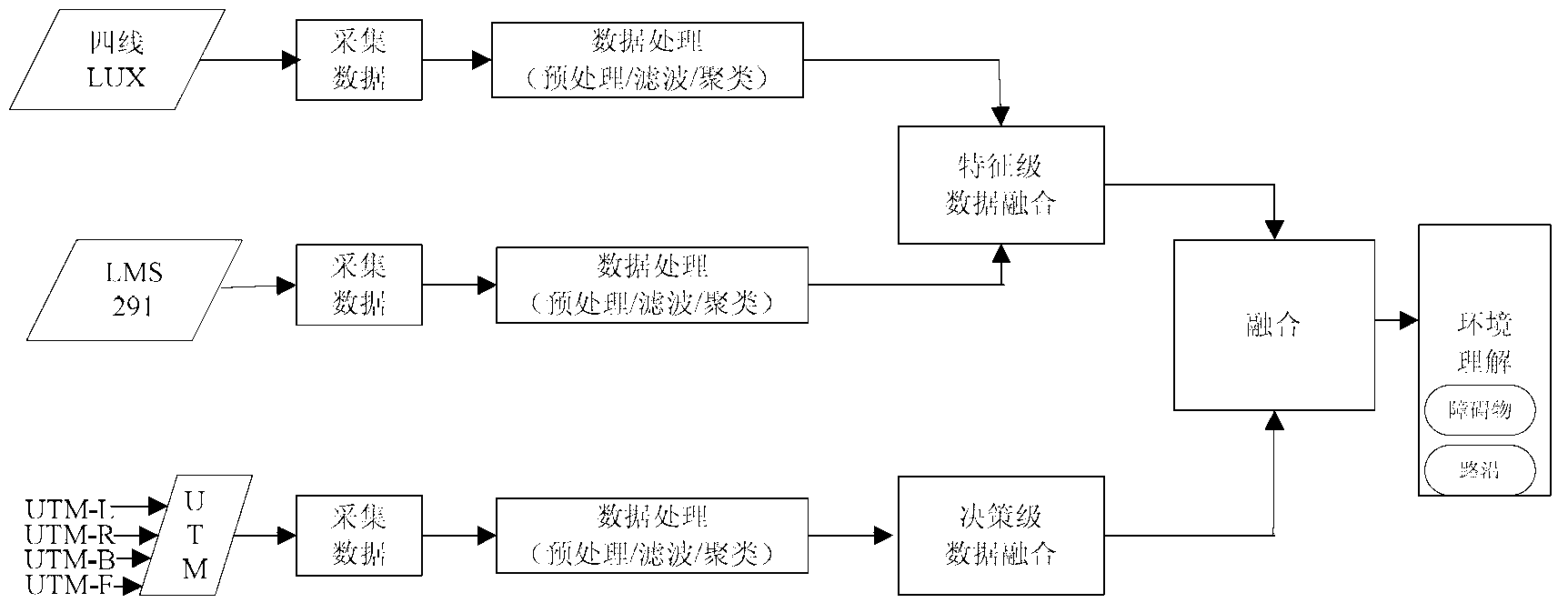
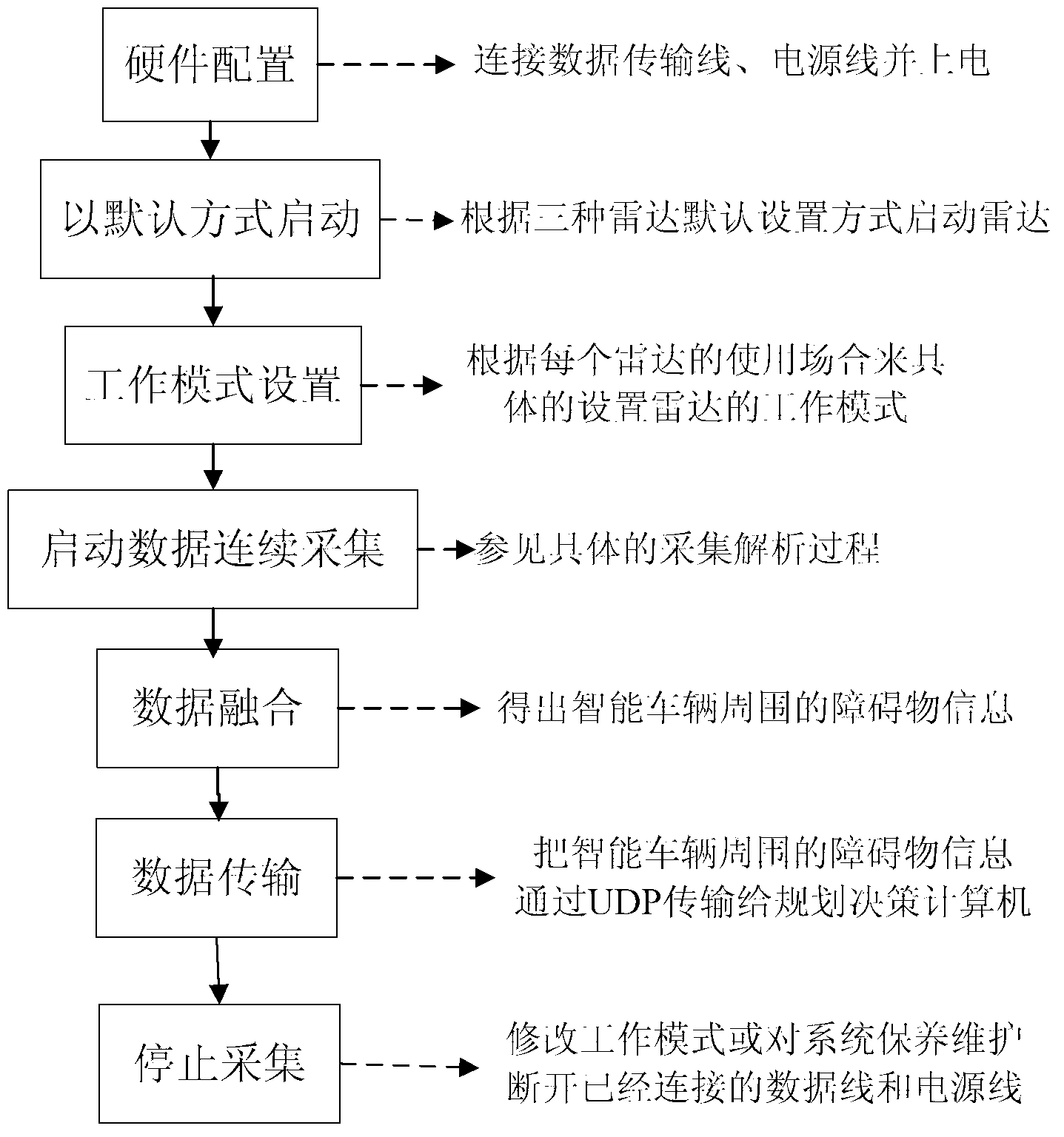
An intelligent vehicle multi-laser-radar data integration system and a method of the intelligent vehicle multi-laser-radar data integration system utilize unified threat management (UTM) - 30 LX laser radars installed at the front side, the rear side, the left side and the right side of an intelligent vehicle body to acquire surrounding information and transmit the information to an upper computer in charge of data integration to obtain surrounding obstacle information, and utilize data acquired by a (learning managed system) LMS 291 and IBEO LUX installed at the front of an intelligent vehicle and transmit the data to the upper computer in charge of the data integration to obtain the obstacle information in front range of 80 meters. Accurate and final obstacle information map is obtained after the upper computer integrates the data according to a certain algorithm. The obstacle information grid map is packed and is transmitted to a programmed decision-making upper computer through a local area network built by routers, and the programmed decision-making upper computer analyzes the information, judges, makes decisions, and makes corresponding execution instructions. Through the intelligent vehicle multi-laser-radar data integration system and the method of the intelligent vehicle multi-laser-radar data integration system, obstacle-shielding capacity and safe driving performance of an unpiloted intelligent vehicle are effectively improved.
Owner:BEIJING UNIV OF TECH
Systems and Methods for Processing Data Flows
InactiveUS20160366160A1Increased complexitySignificant expenseData switching networksNeural learning methodsData streamData integrity
A flow processing facility, which uses a set of artificial neurons for pattern recognition, such as a self-organizing map, in order to provide security and protection to a computer or computer system supports unified threat management based at least in part on patterns relevant to a variety of types of threats that relate to computer systems, including computer networks. Flow processing for switching, security, and other network applications, including a facility that processes a data flow to address patterns relevant to a variety of conditions are directed at internal network security, virtualization, and web connection security. A flow processing facility for inspecting payloads of network traffic packets detects security threats and intrusions across accessible layers of the IP-stack by applying content matching and behavioral anomaly detection techniques based on regular expression matching and self-organizing maps. Exposing threats and intrusions within packet payload at or near real-time rates enhances network security from both external and internal sources while ensuring security policy is rigorously applied to data and system resources. Intrusion Detection and Protection (IDP) is provided by a flow processing facility that processes a data flow to address patterns relevant to a variety of types of network and data integrity threats that relate to computer systems, including computer networks.
Owner:CA TECH INC
Pattern management method and system of NoSQL database
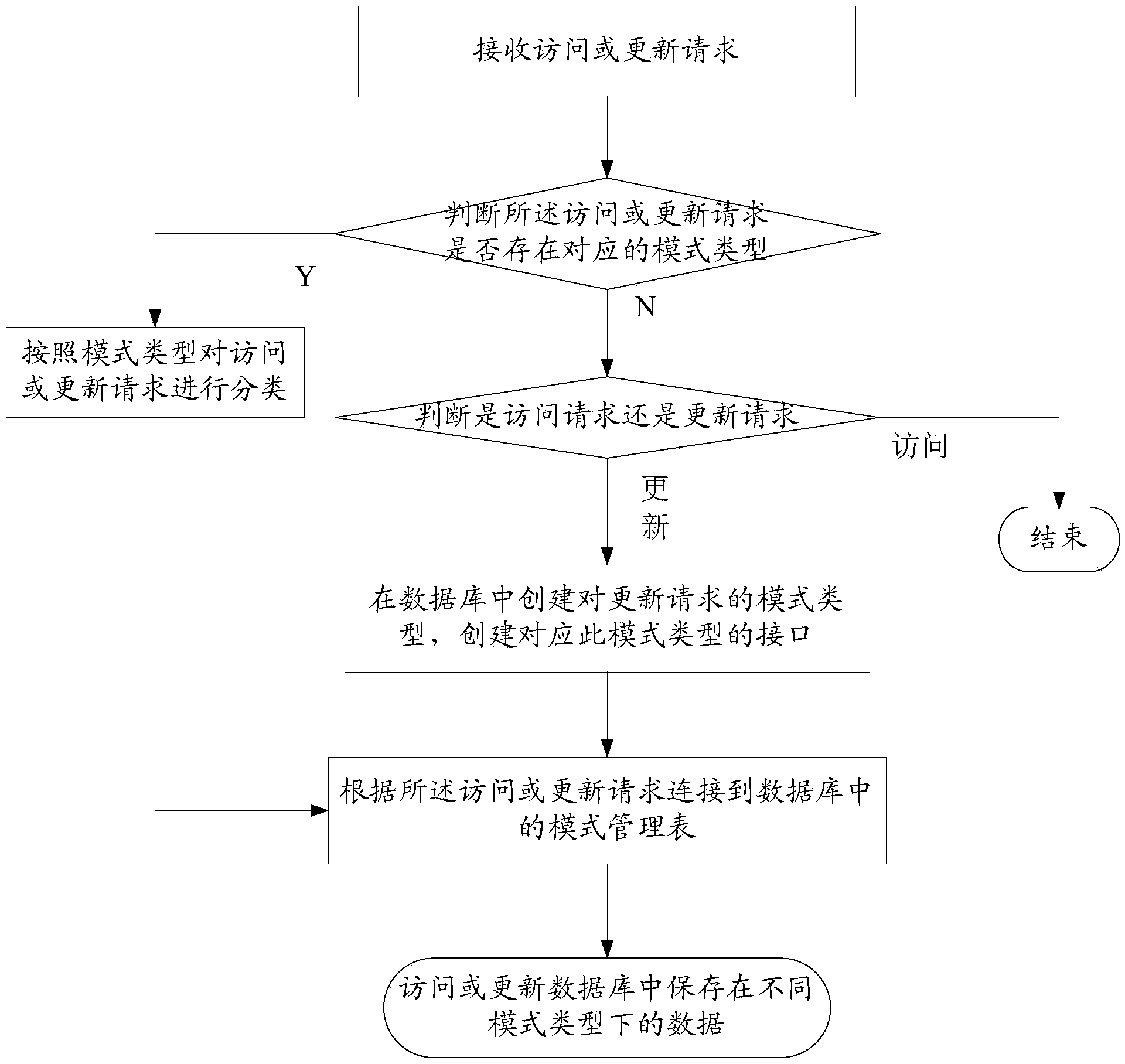
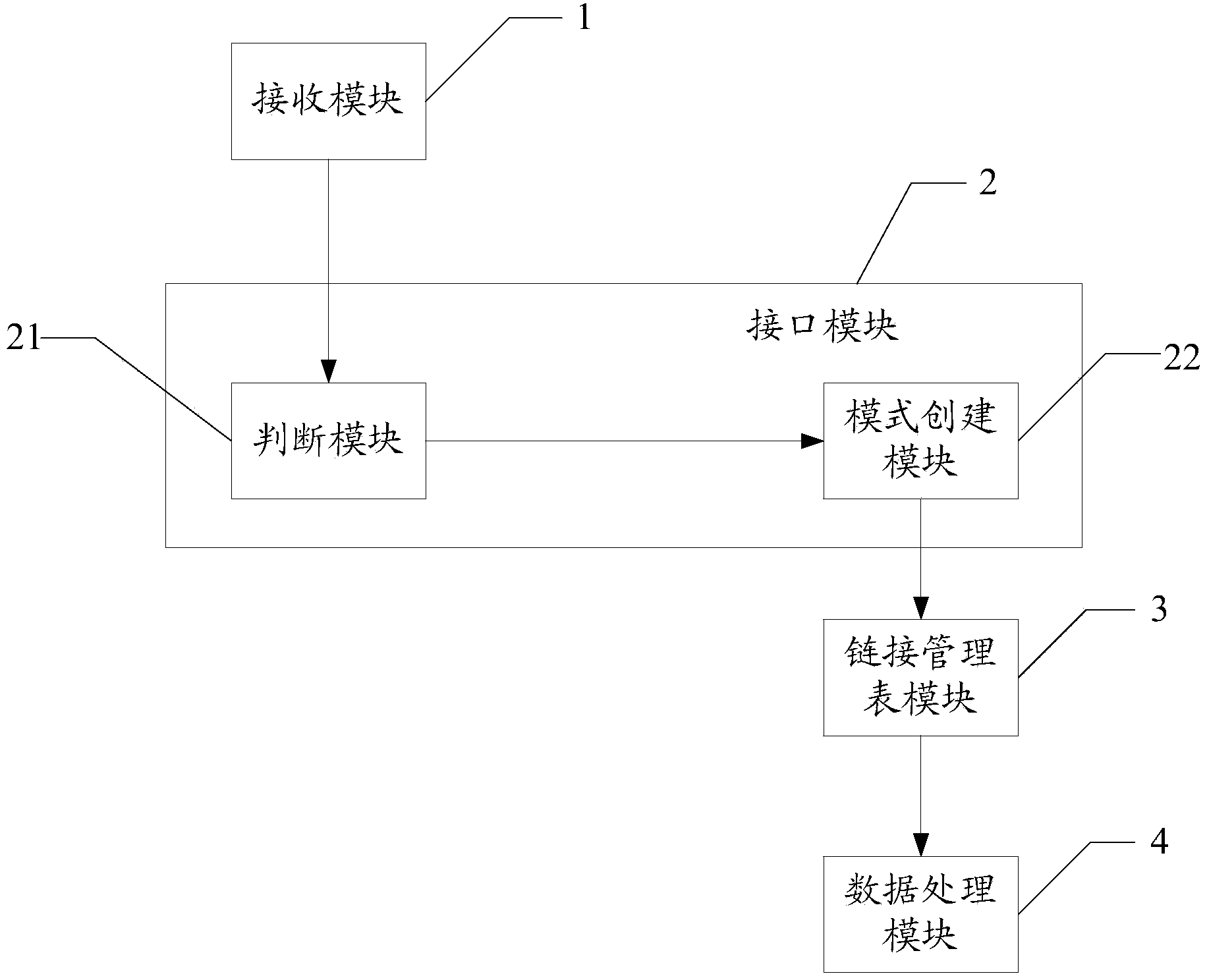
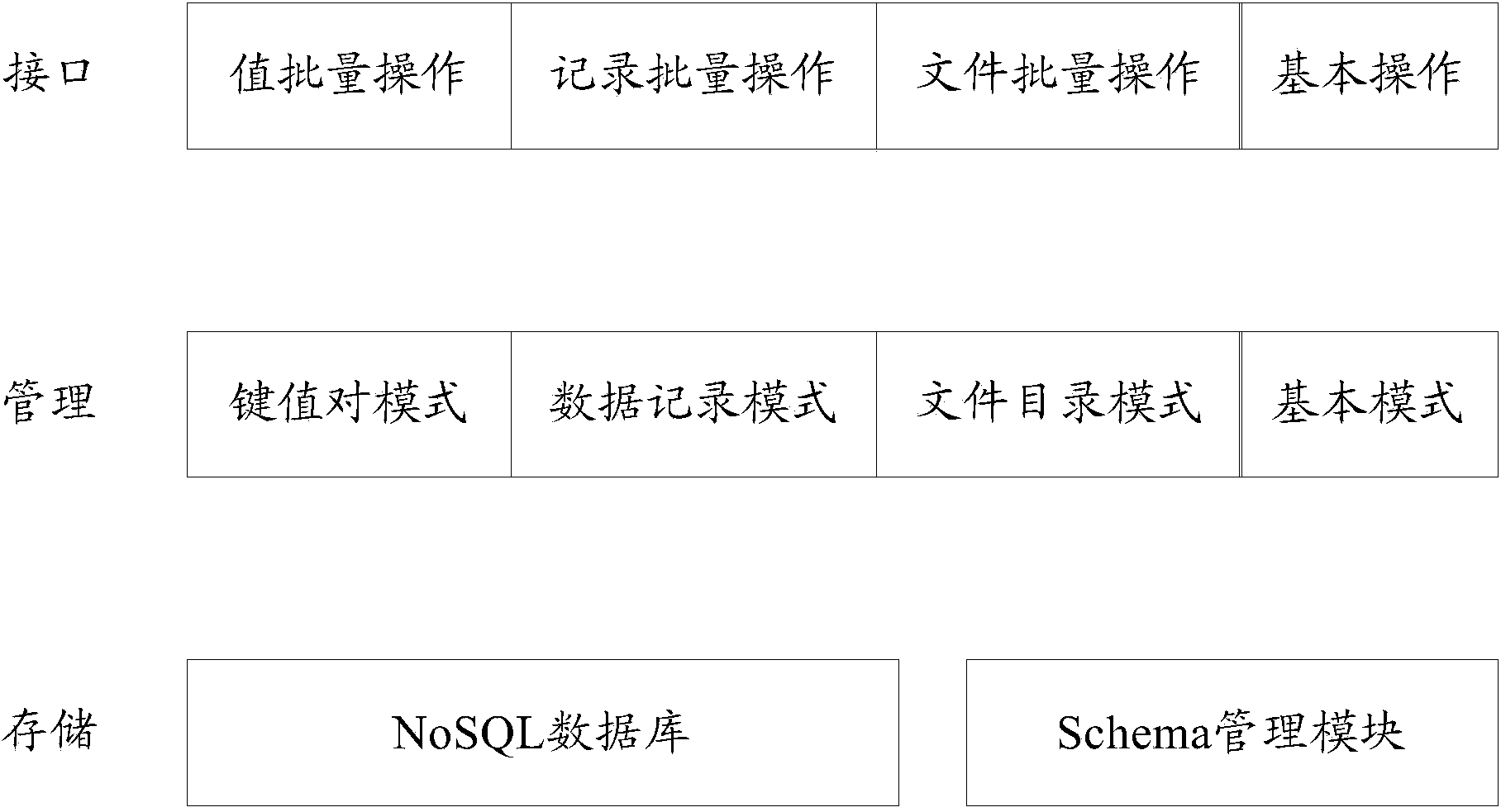
ActiveCN103714163APerfectly compatibleRealize unified managementSpecial data processing applicationsInterface designHigh Readings
The invention relates to a pattern management method of a NoSQL database. The pattern management method specifically includes the following steps that firstly, accessing or updating requests are received; secondly, classification is performed on the accessing or updating requests according to pattern types, or new pattern types and interfaces corresponding to the new pattern types are constructed according to the accessing or updating requests; thirdly, according to a pattern management table connected into the database by the accessing or updating requests through the interfaces corresponding to the pattern types, pattern information in the pattern management table is obtained; fourthly, according to a route provided by the pattern management table, data stored under different pattern types in the database are accessed or updated according to the accessing or updating requests. According to the pattern management method of the NoSQL database, unified management of various heterogeneous data in the NoSQL database is performed; according to different types and features of the data, differential pattern and interface design is achieved, and the high reading and writing performance is ensured. Meanwhile, the universal schema management strategy and a universal read-write interface are provided, and convenience is provided for expansion of data patterns.
Owner:INST OF INFORMATION ENG CAS
System and method for a fast, programmable packet processing system
InactiveUS7839854B2Improve performanceAccelerate packet processing operationMemory loss protectionError detection/correctionGraphicsCoprocessor
The present invention provides a cost effective method to improve the performance of communication appliances by retargeting the graphics processing unit as a coprocessor to accelerate networking operations. A system and method is disclosed for using a coprocessor on a standard personal computer to accelerate packet processing operations common to network appliances. The appliances include but are not limited to routers, switches, load balancers and Unified Threat Management appliances. More specifically, the method uses common advanced graphics processor engines to accelerate the packet processing tasks.
Owner:ALEXANDER THOMAS
Method, device and system for implementing unified authentication management
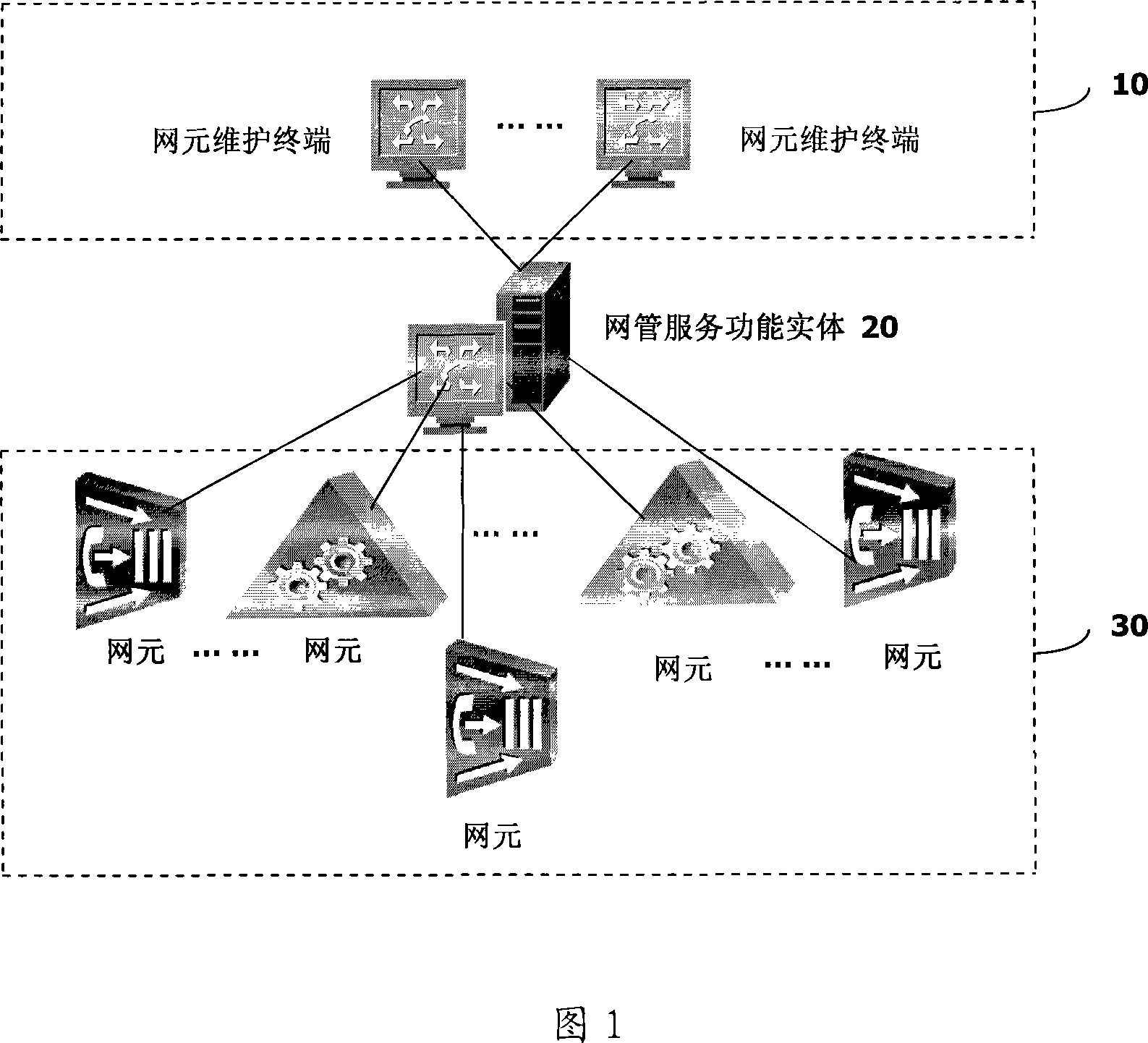
InactiveCN101197711AEasy to operateEnsure safetyData switching networksNetwork managementUser authentication
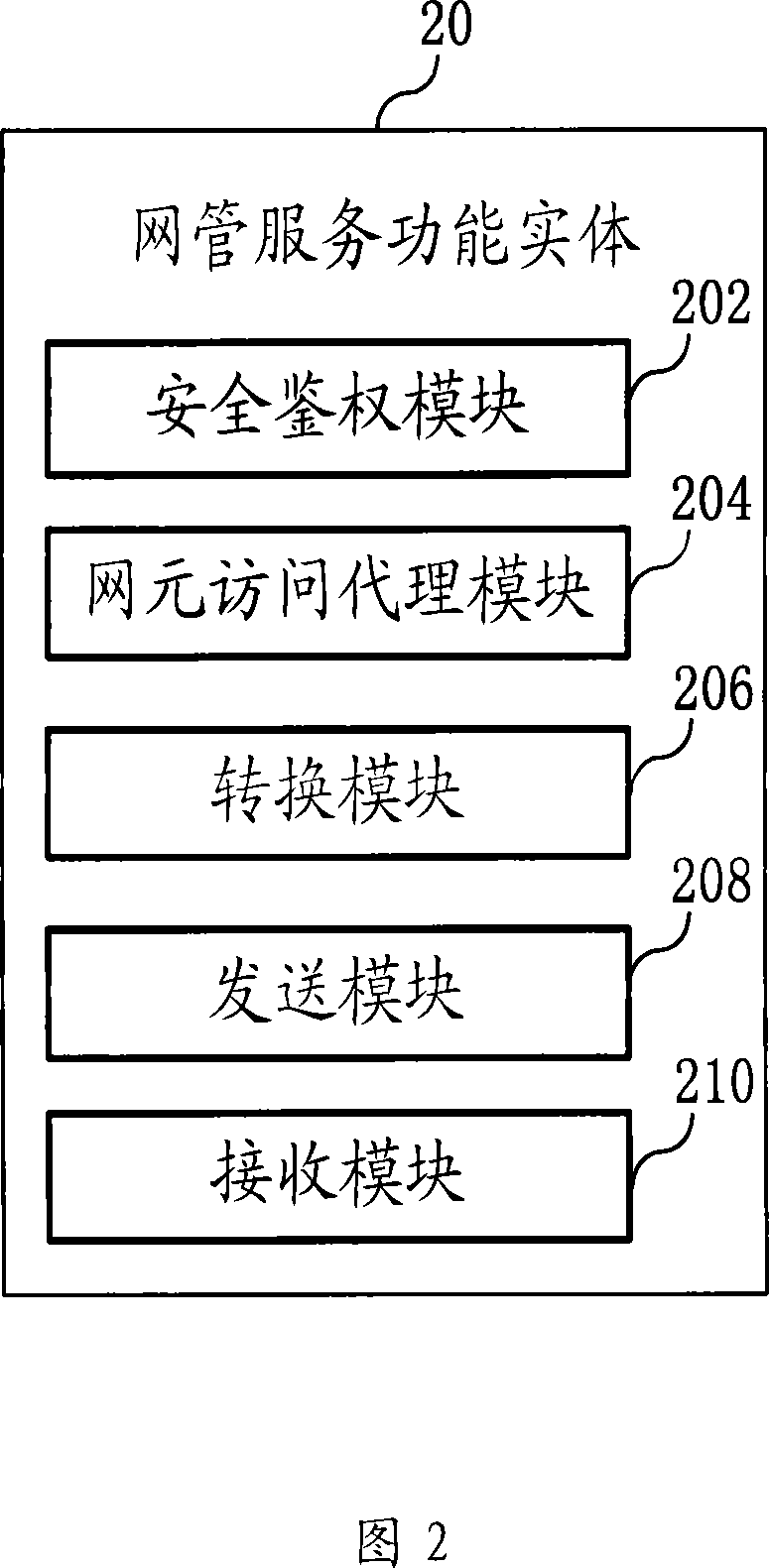
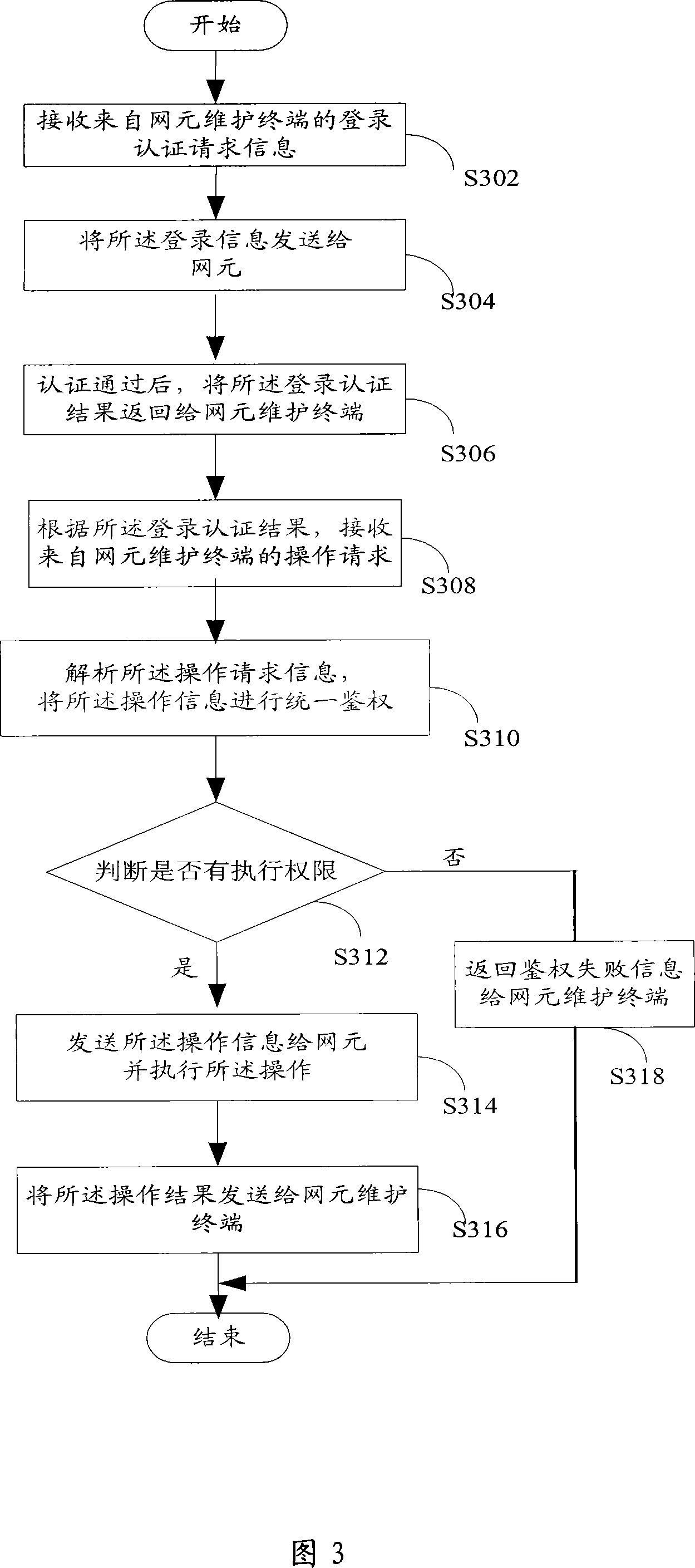
The invention provides a method, device and system of realizing unified authentication management. The method provided by the invention comprises the following steps: a network management service functional entity receives an operation request message from a network element maintenance terminal; according to the operation request message, the network management service functional entity carries out unified right authentication on the request message; according to authentication results, the network element maintenance terminal executes the operation concerning the network element. The network management service functional entity provided by the invention is characterized in that: the entity comprises a security authentication module, a network element access agent module, a transmission module and a reception module. The invention also provides a system of realizing unified authentication management. The invention solves the problems of conflicting user authentication and right authentication between a network management server and the network element, complicated management right and repeated logon and authentication. With the unified right authentication management, the invention facilitates user operation, improves use satisfaction degree of user and ensures network safety.
Owner:深圳市智通天下科技服务有限公司
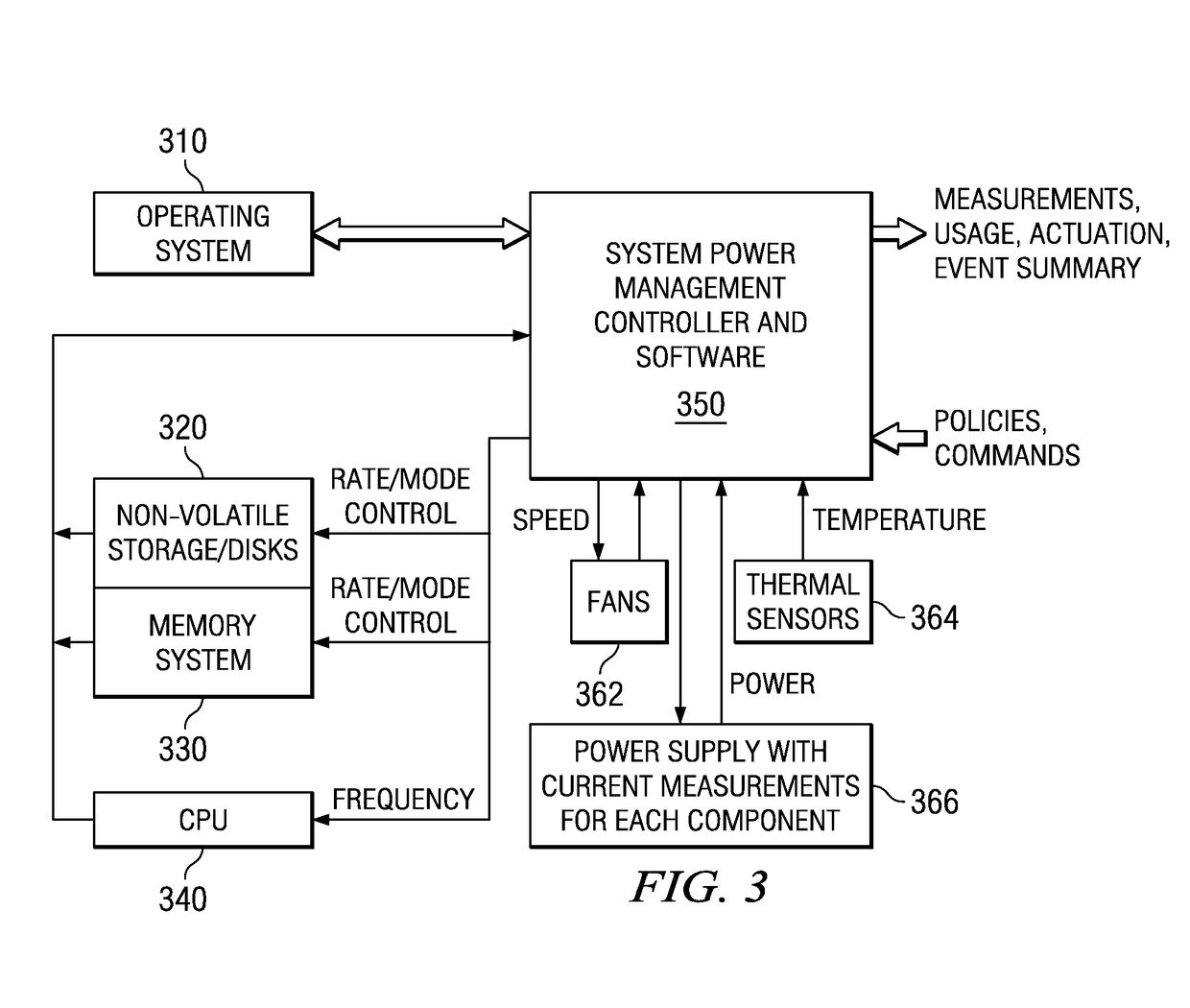
Unified management of power, performance, and thermals in computer systems
InactiveUS7908493B2Improve efficiencyEfficient solutionPiezoelectric/electrostriction/magnetostriction machinesPower supply for data processingStructure of Management InformationComputerized system
A mechanism is provided for unified management of power, performance, and thermals in computer systems. This mechanism incorporates elements to effectively address all aspects of managing computing systems in an integrated manner, instead of independently. The mechanism employs an infrastructure for real-time measurements feedback, an infrastructure for regulating system activity, component operating levels, and environmental control, a dedicated control structure for guaranteed response / preemptive action, and interaction and integration components. The mechanism provides interfaces for user-level interaction. The mechanism also employs methods to address power / thermal concerns at multiple timescales. In addition, the mechanism improves efficiency by adopting an integrated approach, rather than treating different aspects of the power / thermal problem as individual issues to be addressed in a piecemeal fashion.
Owner:INT BUSINESS MASCH CORP
System and method for building intelligent and distributed L2-L7 unified threat management infrastructure for IPv4 and IPv6 environments
ActiveUS8839404B2Easy to handleQuality of serviceDigital data processing detailsMultiple digital computer combinationsAnti virusApplication software
Owner:CA TECH INC
Method and system for realizing unified threat management in heterogeneous network
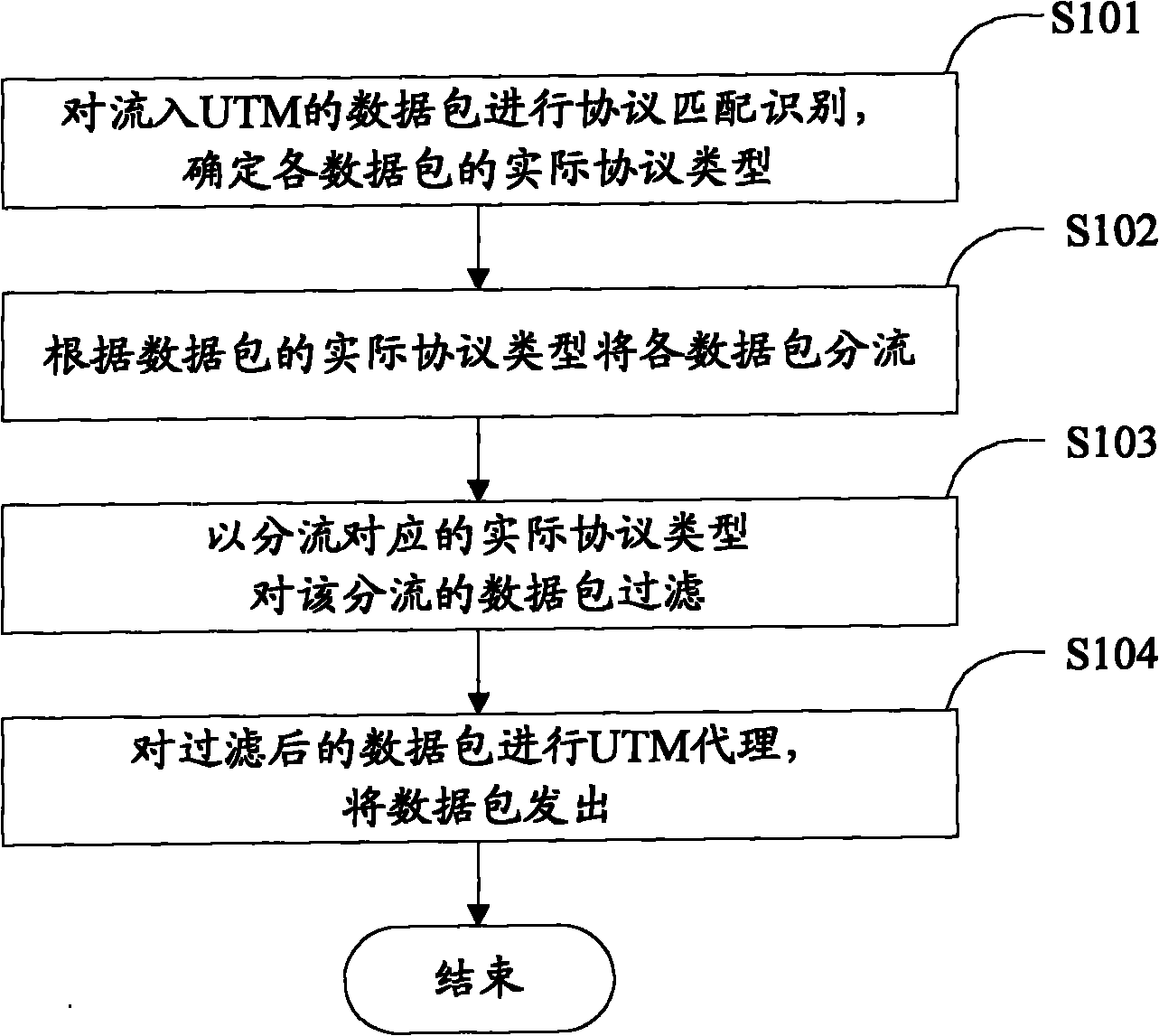
ActiveCN101827083ARealize single-device UTM prevention modeData switching networksNetwork packetHeterogeneous network
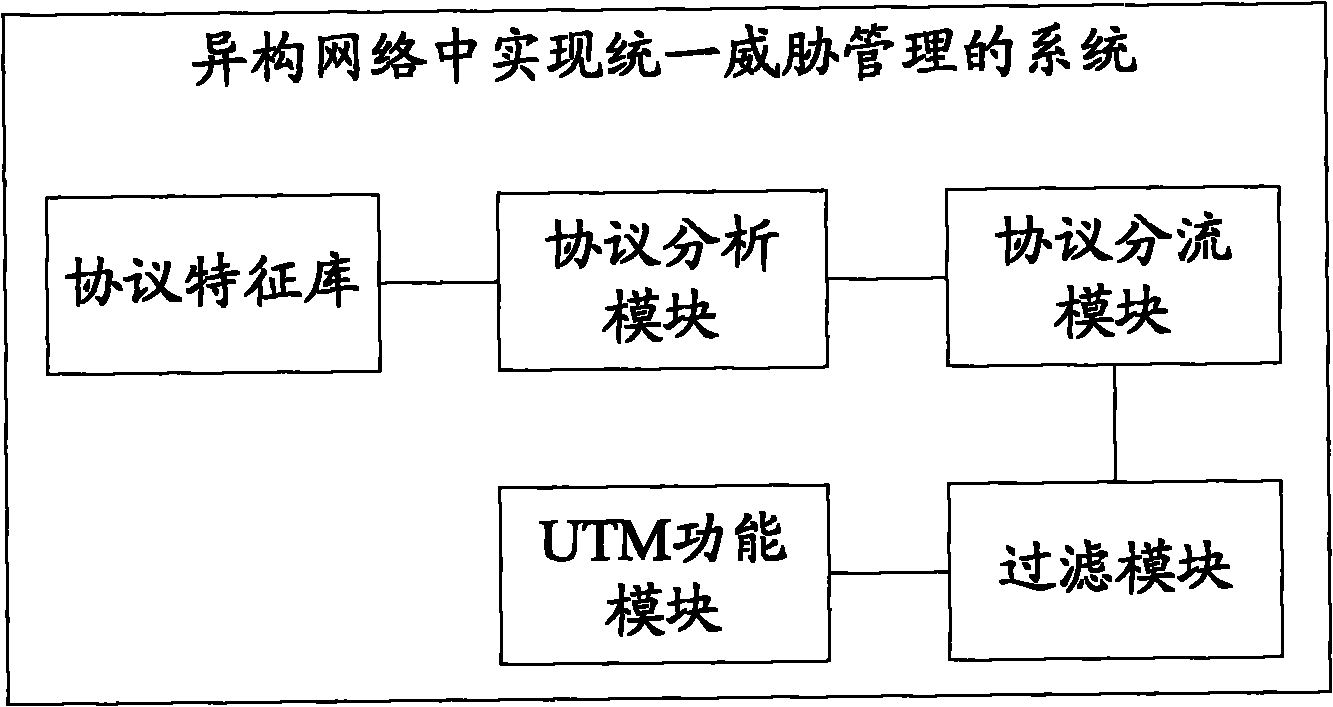
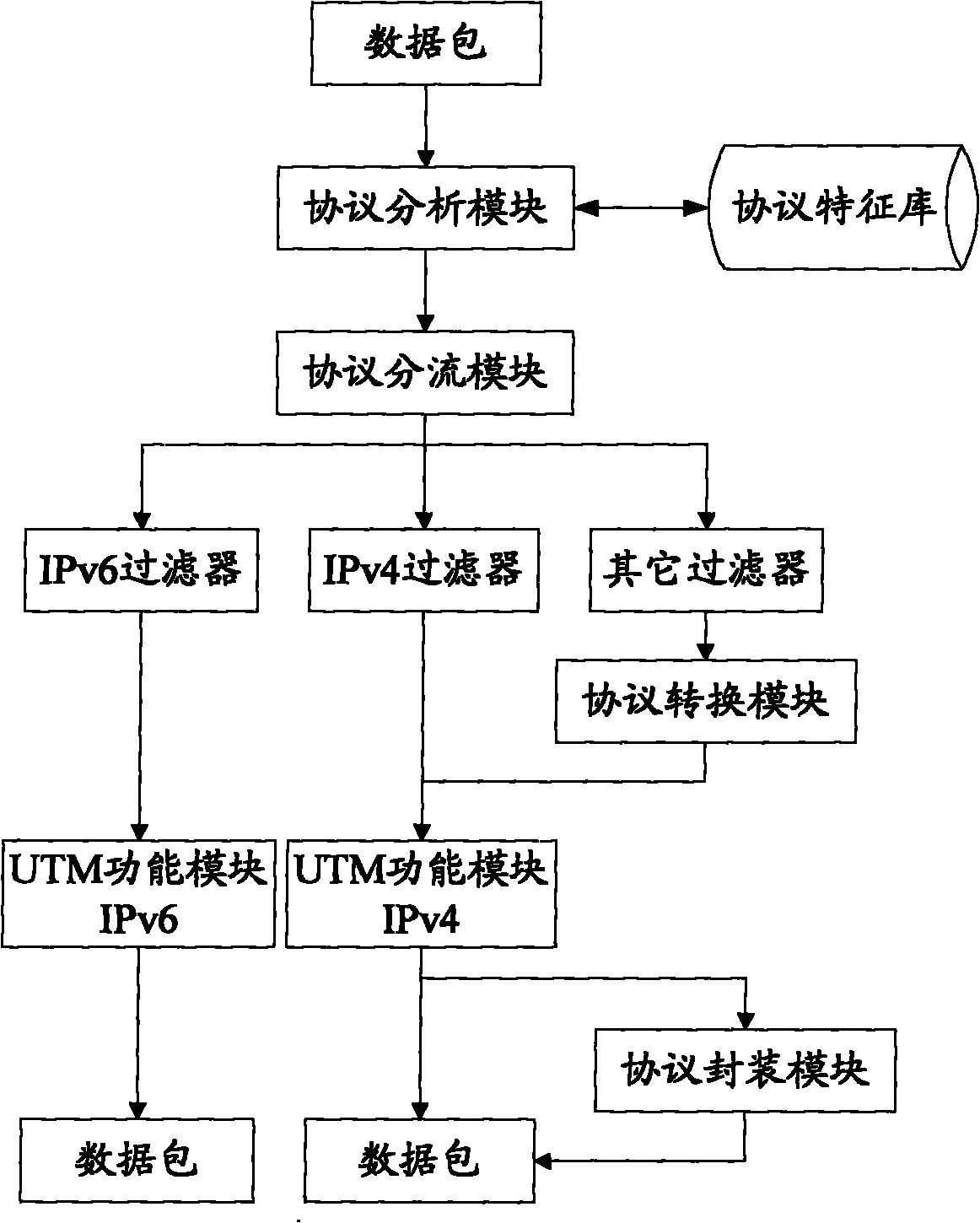
The invention discloses a method and a system for realizing unified threat management in a heterogeneous network, relating to the field of network security and aiming at solving the problem that the preventive mode of single equipment UTM of the current heterogeneous network can not be realized. The method comprises the following steps: carrying out protocol matching recognition on data flowing into the UTM, and determining actual protocol types of all data packets; distributing all the data packets according to the actual protocol types of all data packets; filtering the distributed data packet by the actual protocol type corresponding to distribution; and carrying out UTM agency on filtered data packets, and sending out the data packets. The system comprises a protocol analysis module, a protocol distribution module, a filtering module and a UTM function module. As the method and the system provides a set of complete mechanism including analysis, distribution, filtering, protocol conversion, UTM agency and protocol reduction mechanism, the preventive mode of single equipment UTM of the heterogeneous network can be realized.
Owner:BLUEDON INFORMATION SECURITY TECH CO LTD
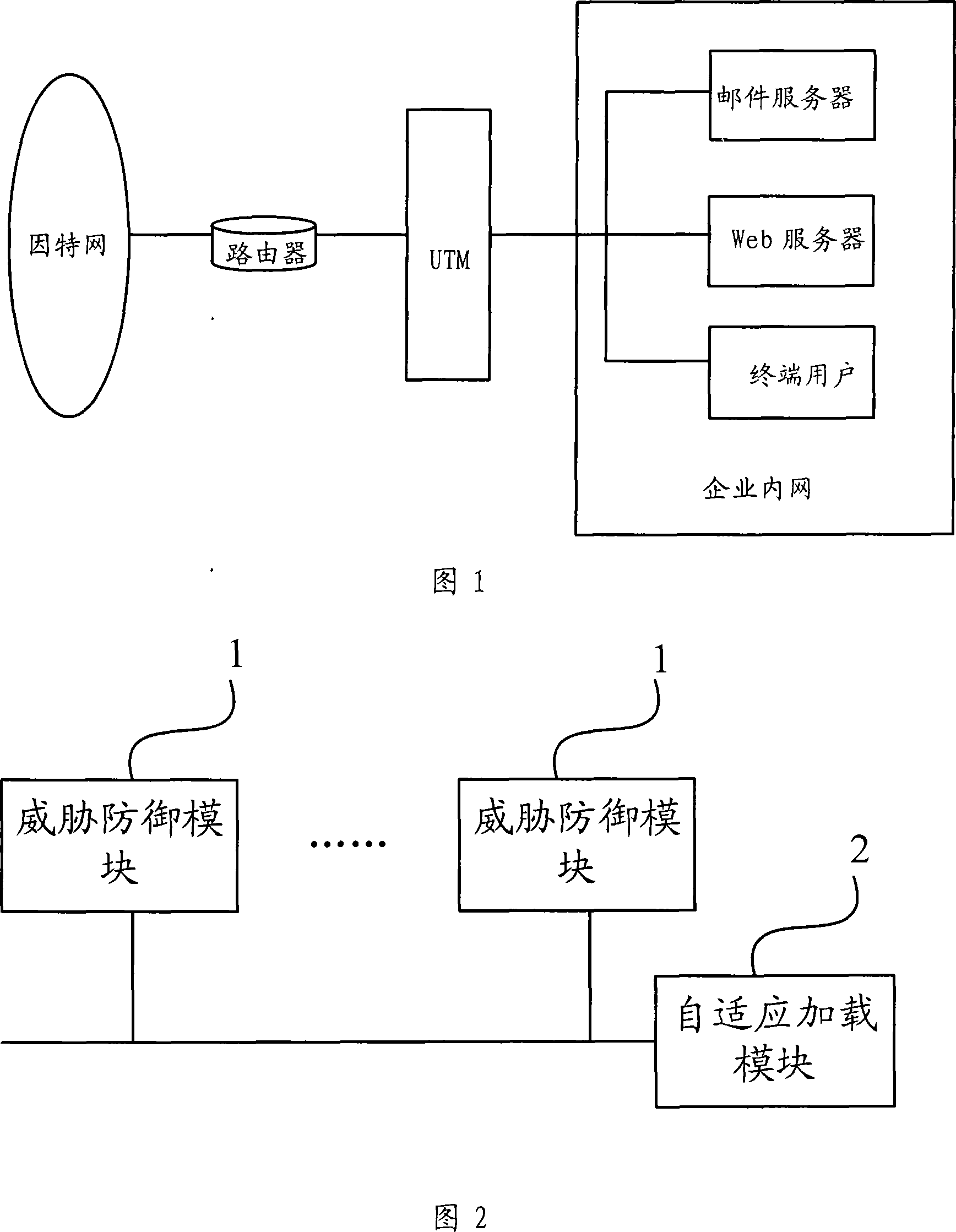
Uniform intimidation managing device and loading method of intimidation defense module
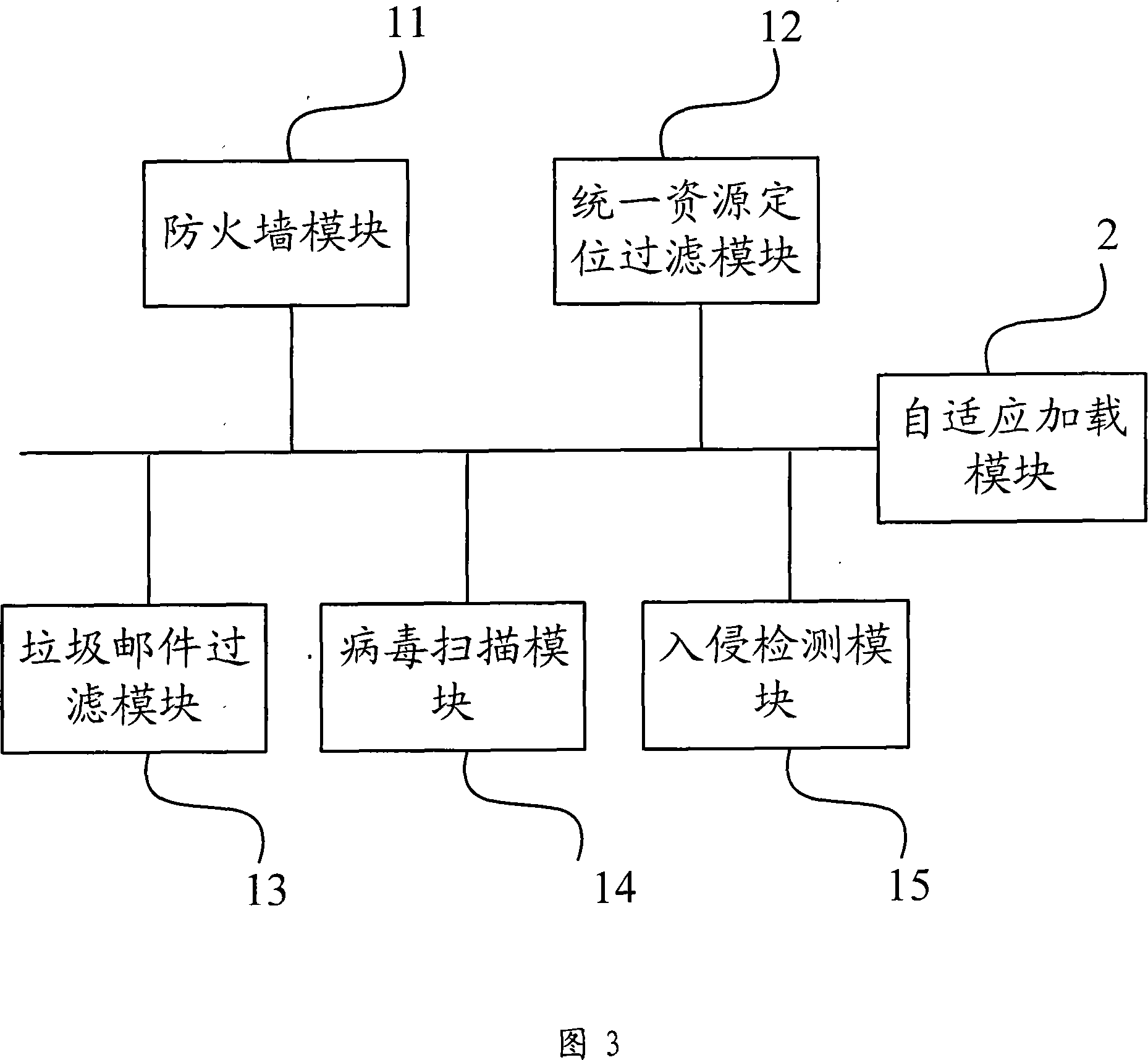
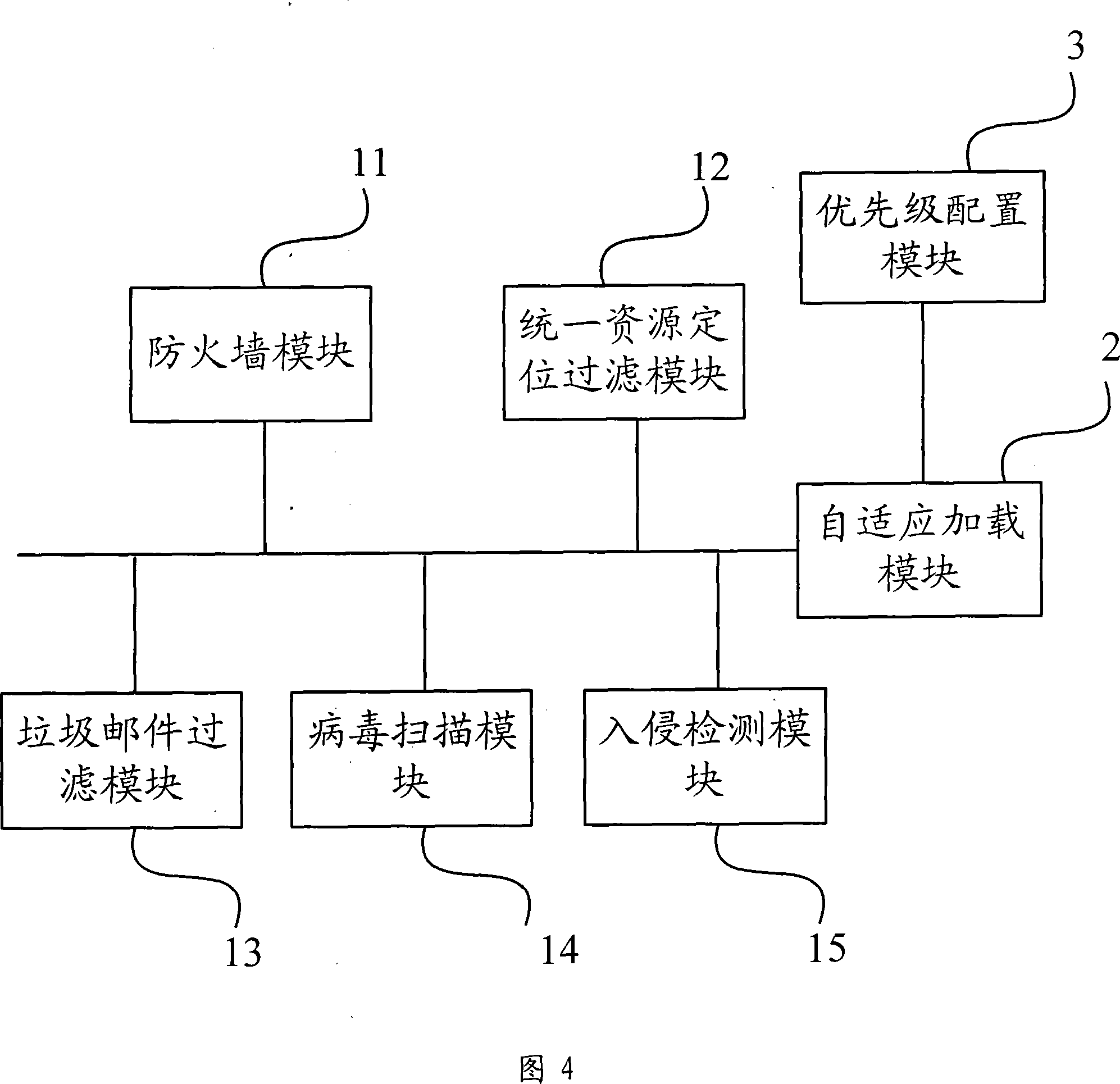
The example of the invention discloses a method for loading unified threat management equipment and a threat defending module, the equipment comprises at least a threat defending module and a self-adaptive loading module which is used to dynamically load the threat defending module according to processing performance information of the unified threat management equipment, the method comprises: obtaining the processing performance information of the unified threat management equipment after the unified threat management equipment receives message and loading the threat defending module according to the processing performance information. From the above technical scheme, the example of the invention dynamically loads the threat defending module through a self-adaptive dynamic adjustment mode namely the processing performance of the equipment, which considers to various security defending functions and normal service processing abilities of the equipment and guarantees the throughput of the equipment to the maximum.
Owner:HUAWEI DIGITAL TECH (CHENGDU) CO LTD
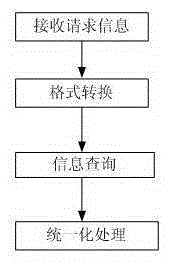
A unified management system for debugging information
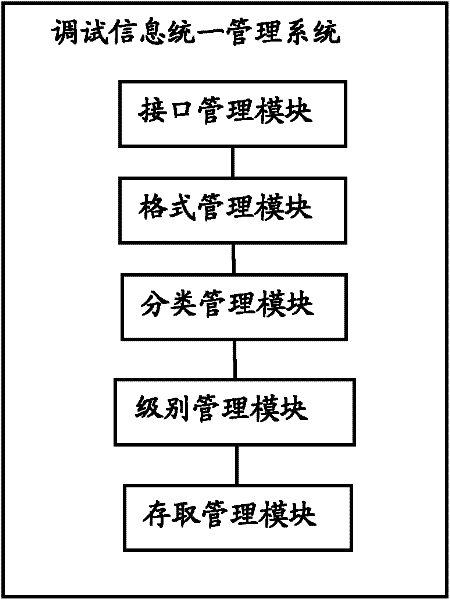
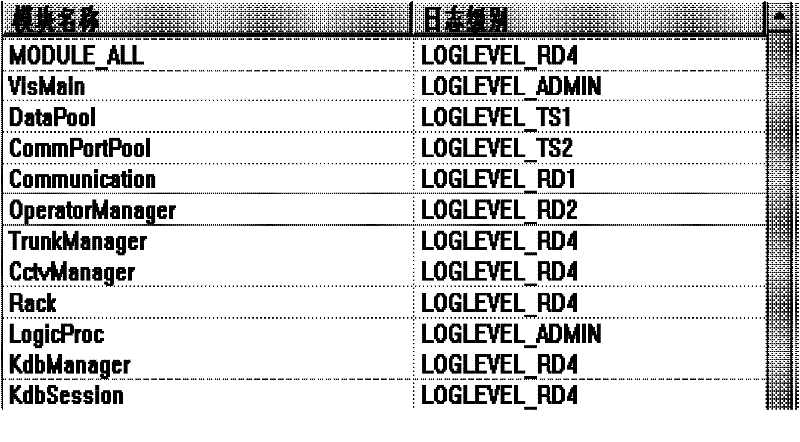
InactiveCN102270131AConvenient research and development referenceEasy to useSpecific program execution arrangementsSpecial data processing applicationsSoftware systemSoftware engineering
The invention discloses a unified management system for debugging information, which is used in the field of software engineering. The system includes: an interface management module, which is used to provide a management and operation interface for debugging information; a format management module, which is used for debugging information. The format and contained information are standardized, and the contained information includes output time, module name, level and / or user-defined description information, and the grid includes the display color and layout of the information; the classification management module is used to According to the module, the debugging information is classified and managed to filter unnecessary module information or to filter out effective module information; the level management module is used for level management of the debugging information; the access management module is used for all The above debugging information is used to manage the access mode. The invention enables the software system to uniformly manage the debugging information in the process of modular development and subsequent use, so as to facilitate and effectively use the debugging information.
Owner:深圳市博康智能信息技术有限公司
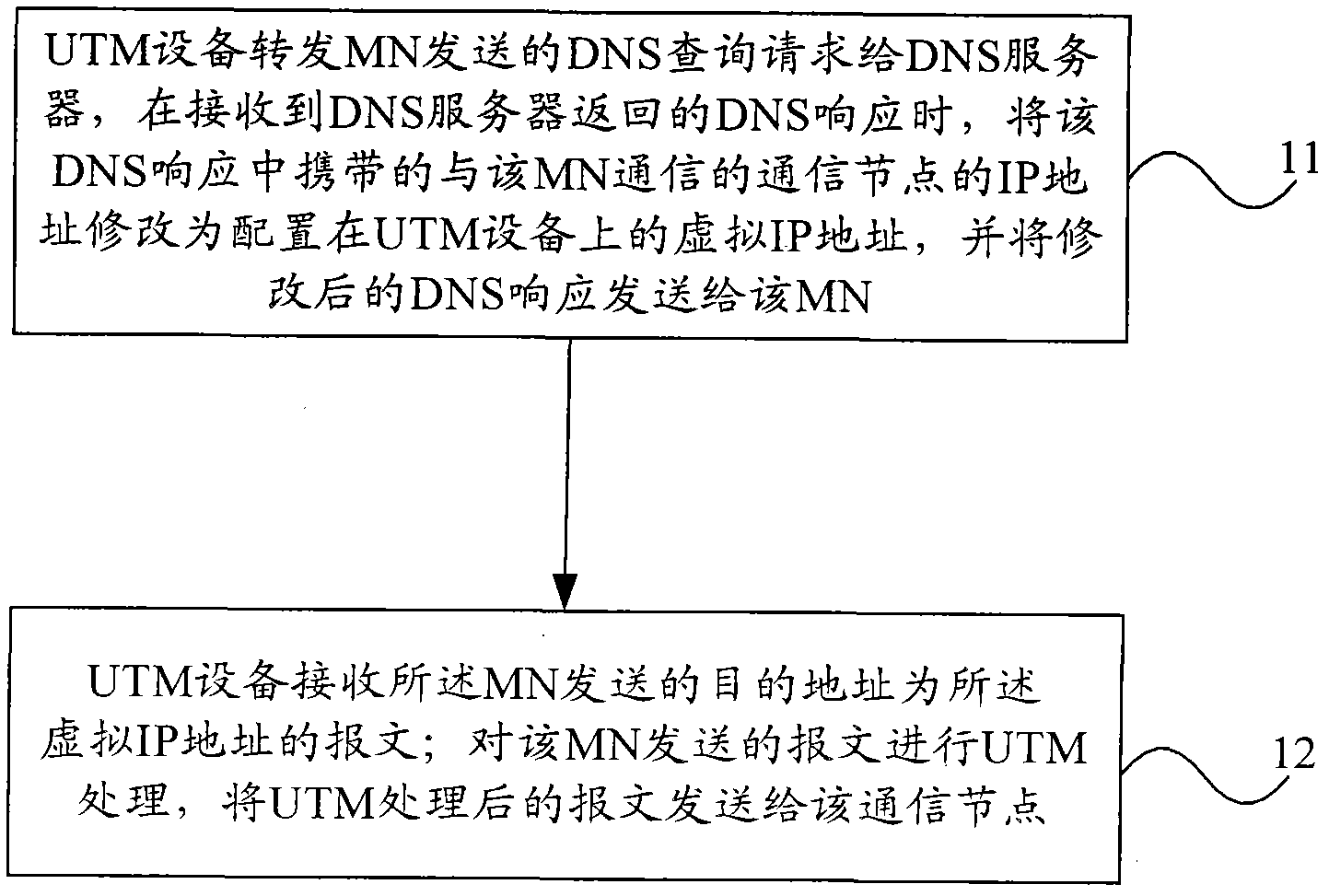
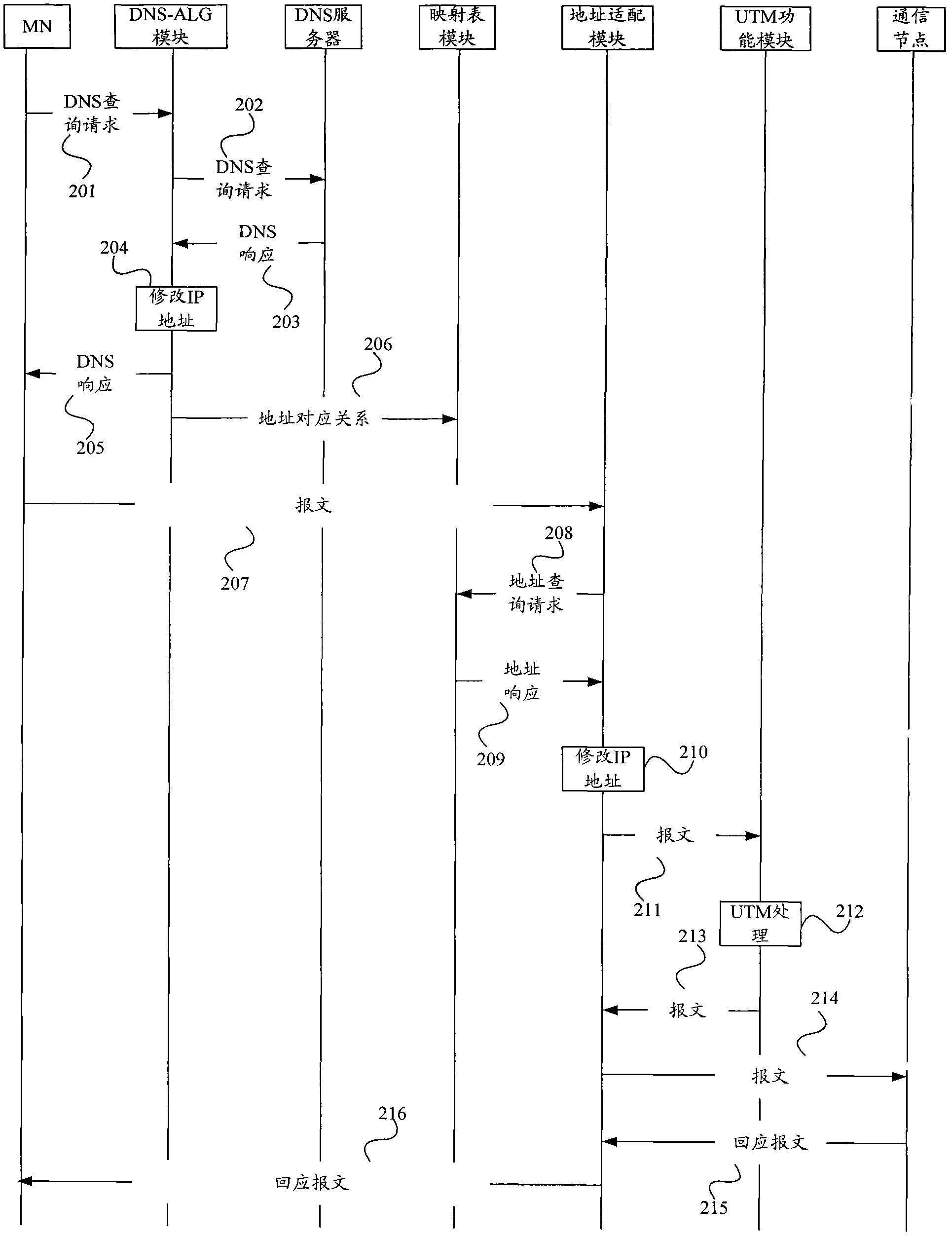
Message transmission method in mobile IPv6 and UTM (unified threat management) equipment
ActiveCN102045260AGuarantee unimpededOperational securityWireless network protocolsData switching networksDomain nameOperation safety
The embodiment of the invention provides a message transmission method in mobile IPv6 and UTM (unified threat management) equipment. The method comprises: forwarding a DNS (domain name server) search request transmitted by an MN (mobile node) to a DNS server; after a DNS response returned by the DNS server is received, revising the IP address of the communication node communicated with the MN and carried in the DNS response to a virtual IP address configured on the UTM equipment, and transmitting the revised DNS response to the MN; receiving a message transmitted by the MN, wherein the target address of the message is the virtual IP address; carrying out UTM processing on the message transmitted by the MN; and transmitting the message processed by the UTM to the communication node. After the MN leaves a home network, the embodiment of the invention ensures that the transmitted message still passes through the UTM equipment to guarantee operation safety and service smoothness.
Owner:CHENGDU HUAWEI TECH
Unified identity authentication method supporting data integration of heterogeneous application module
ActiveCN101951319AImprove versatilityImprove shareabilityUser identity/authority verificationCouplingComputer module
The invention discloses a unified identity authentication method supporting data integration of heterogeneous application module Through unified management of user information of an enterprise and the account information of an application system in which the user information is stored, unified and integrated providing of a user information access interface, one-step unified generation of user authentication certificates, unified and integrated registering of the characteristic attributes of each heterogeneous application module (4) and unified method call of the an application system authentication interface according to the characteristic attributes of each application system, unified identity authentication of a data integration process of heterogeneous application modules (4) is realized, the reusability and the extendibility in the whole data integration process are improved; the consistency of identity authentication on the whole technical route is guaranteed; and the problems of high system coupling degree, low universality, poor sharing and high management and maintenance cost of the heterogeneous application modules (4) in the data integration process are effectively solved.
Owner:北京航天方石科技有限公司
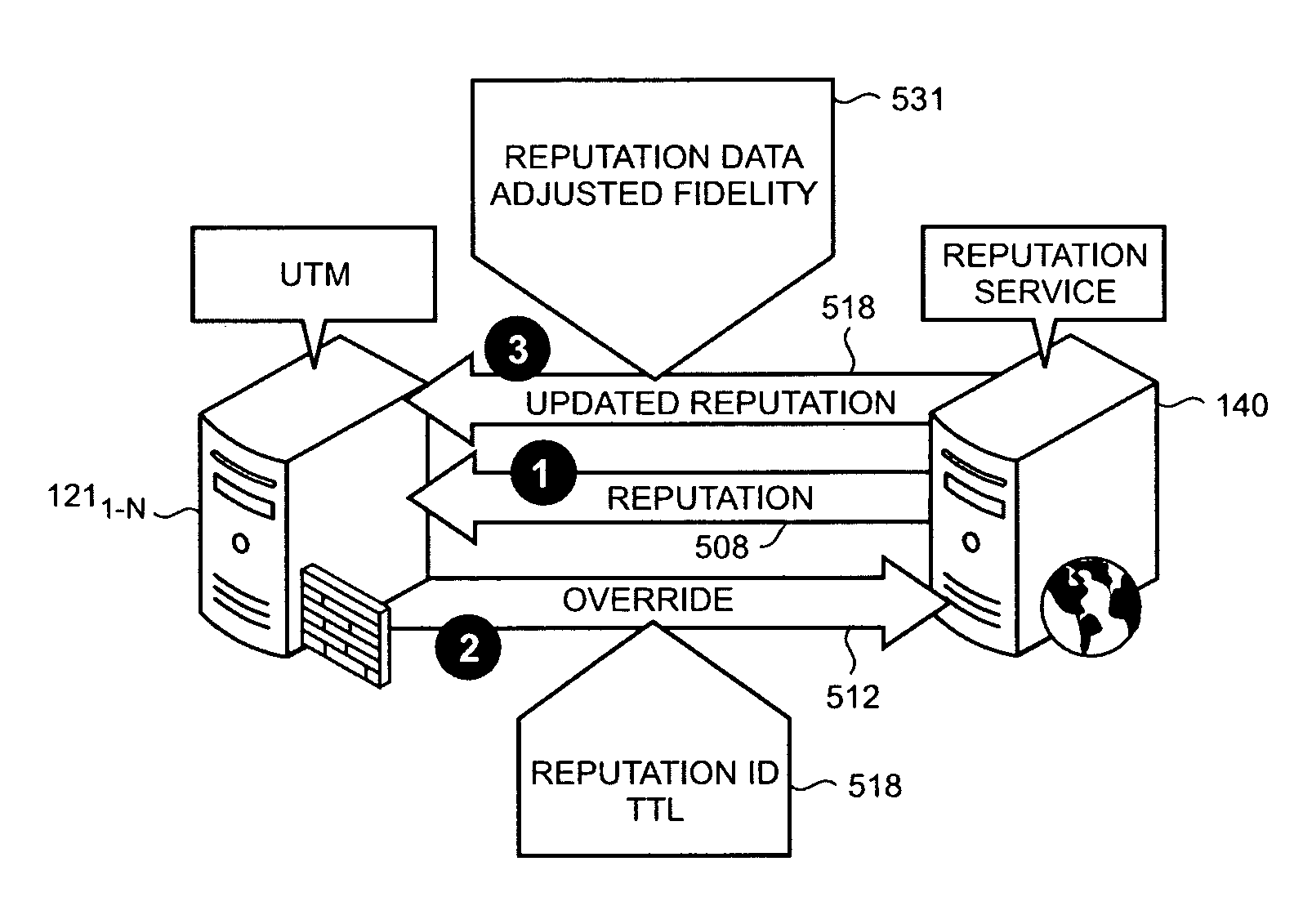
Reduction of false positive reputations through collection of overrides from customer deployments
ActiveUS7953969B2Great confidenceReduce generationUser identity/authority verificationMultiple digital computer combinationsTraffic capacityIp address
An automated arrangement for reducing the occurrence and / or minimizing the impact of false positives by a reputation service is provided in which overrides for a reputation of an adversary are reported to a reputation service from security devices, such as unified threat management systems, deployed in enterprise or consumer networks. An override is typically performed by an administrator at a customer network to allow the security device to accept traffic from, or send traffic to a given IP address or URL. Such connectivity is allowed—even if such objects have a blacklisted reputation provided by a reputation service—in cases where the administrator recognizes that the blacklisted reputation is a false positive. The reputation service uses the reported overrides to adjust the fidelity (i.e., a confidence level) of that object's reputation, and then provides an updated reputation, which reflects the fidelity adjustment, to all the security devices that use the reputation service.
Owner:MICROSOFT TECH LICENSING LLC
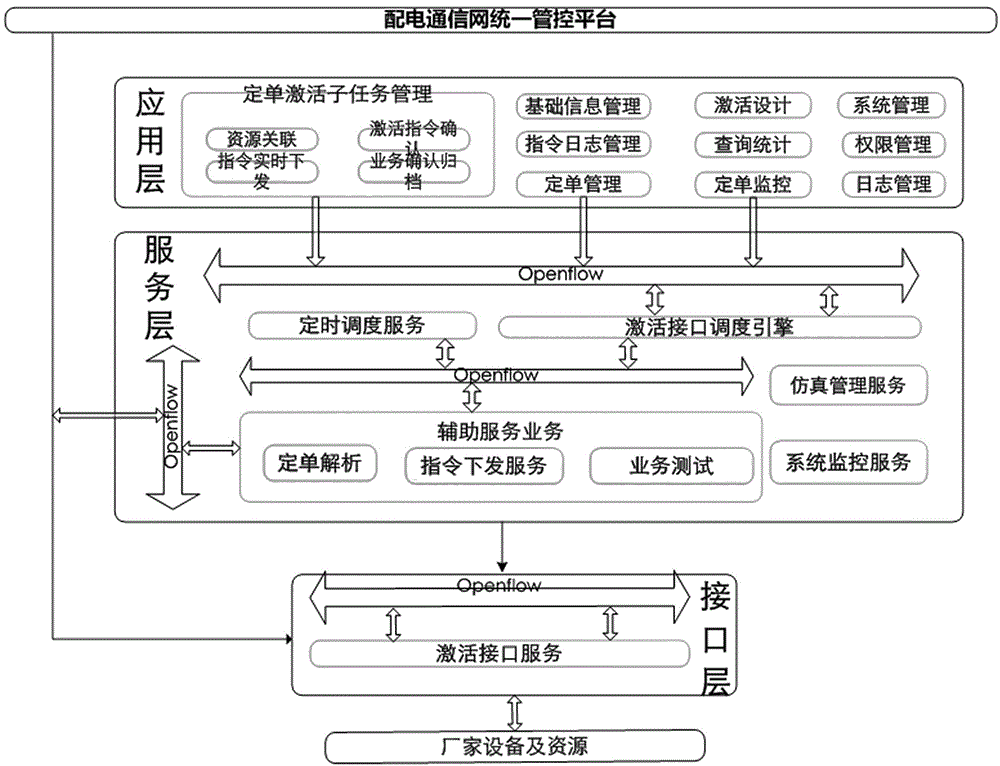
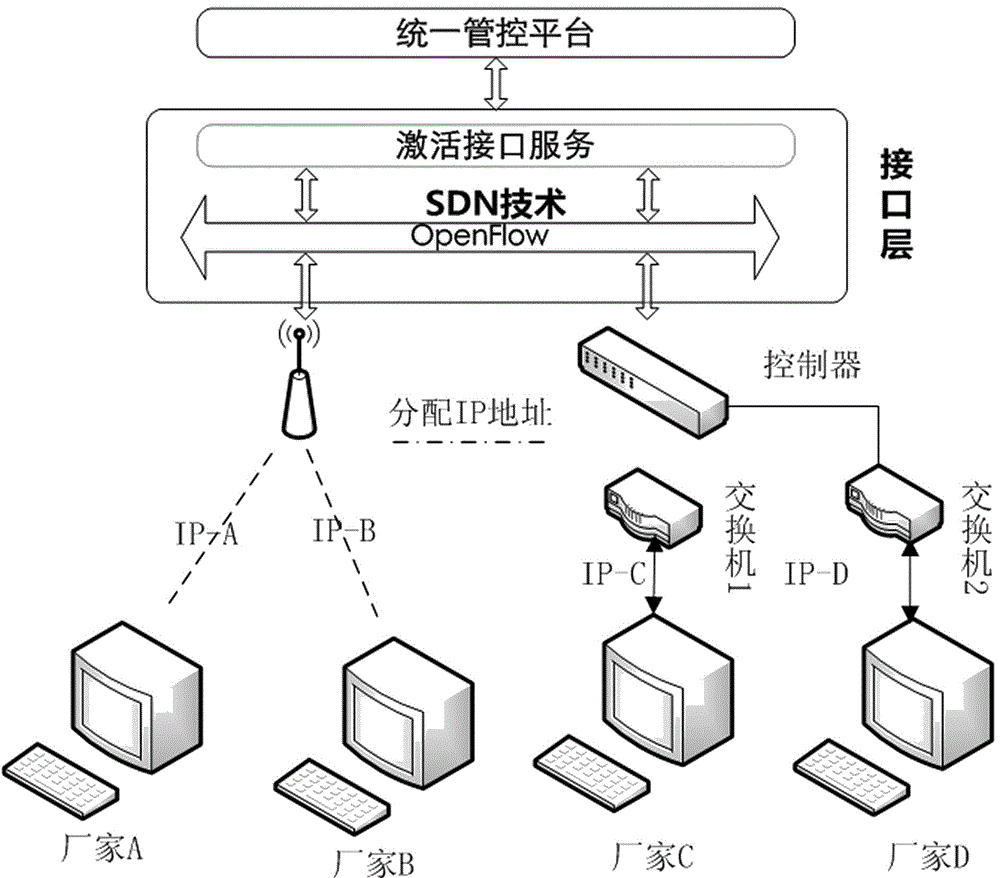
Unified management and control platform for power distribution communication networks
ActiveCN106027287AEfficient use ofComprehensive utilizationData switching networksStructure of Management InformationNetwork management
The invention relates to a unified management and control platform for power distribution communication networks, belonging to the technical field of power communication. The unified management and control platform for the power distribution communication networks provided by the invention can solve the incompatible condition of network management systems of various manufactures. The unified management and control platform disclosed by the invention comprises an interface layer, an application layer and a service layer, and is structurally characterized in that data interaction among various layers is carried out through an Openflow protocol and a message queue manner; the interface layer is used for being docked with an external system; the interface layer manages a management protocol and an equipment interface, and is docked with element management systems EMS of various manufactures through a northbound interface; the interface layer comprises activation application and reply of an interface and activation of a data standardization data module of the interface, and activates a related task of the interface and performs interface log management; the application layer comprises an application functional module; and the application functional module controls logical processing of a process flow service by obtaining configuration information in a related link when the flow is activated.
Owner:STATE GRID LIAONING ELECTRIC POWER CO LTD SHENYANG POWER +2
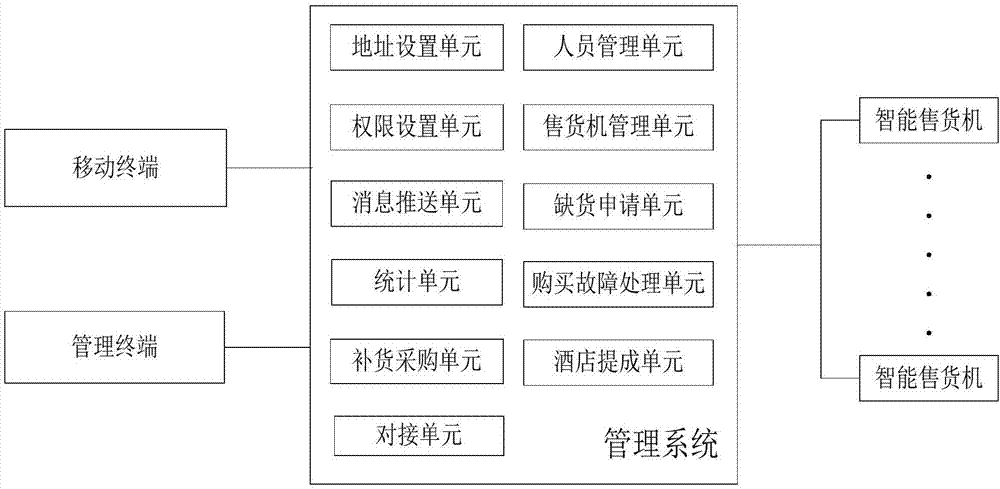
Intelligent terminal information management cloud platform
ActiveCN107341914AMeet immediate needsSave human effortCoin-freed apparatus detailsPayment architectureComputer terminalComputer science
The invention belongs to the technical field of intelligent vending machines, and provides an intelligent terminal information management cloud platform. The cloud platform comprises an intelligent vending terminal, a management terminal and a mobile terminal which are installed in a hotel, and a management system for being communicated with the intelligent vending terminal, the management terminal and the mobile terminal; the management system includes an address setting unit for setting the address of storage cells, an authority setting unit for setting the authority of staff, a message push unit for pushing information, a statistical unit for counting commodity vending information, a replenishment and procurement unit for reminding replenishment and procurement, and a connecting unit for being connected with a supplier's delivery system. The intelligent terminal information management cloud platform can conduct unified management on the vending and procurement conditions of goods on the platform, and saves manpower and time, and the intelligent vending machines on the platform meet the immediate needs of hotel users, and can be assembled freely into various sizes according to the requirements of a site, which shortens the manufacturing period and saves the customization cost.
Owner:无锡动力立方科技有限公司
A data management platform based on cloud computing
InactiveCN109086301AGuarantee effective service utilizationUnified storage implementationDigital data protectionOffice automationService modelInformation resource
The invention provides a data management platform based on cloud computing, comprising a data management collection module, a data management storage module and a data support service module. The invention forms the unified collection of information resources, unified storage management, unified utilization management and application system management based on platform and shared information resources, forms the corresponding technology and management standard of the platform, and guarantees the effective service utilization of government information resources. At the same time, through the standard cloud platform technology under the exchange of shared services model, the data management platform can achieve unified storage of government data on the public cloud platform, unified maintenance and flexible service, improve the security of existing government data storage and efficient use of capacity, complete more in-depth data mining and other work, to create more value.
Owner:江苏网域科技有限公司
Collaborative management system based on workflow engine
InactiveCN110097255AGuaranteed normalizationEnsure transparencyFinanceOffice automationFull life cycleClosed loop
The invention relates to a collaborative management system based on a workflow engine. The system comprises a workflow engine, a project management subsystem, a research and development management subsystem, a budget management subsystem, a performance management subsystem, a financial management subsystem and a background setting subsystem, and the workflow engine is used for defining and creating business processes of a plurality of business systems and driving execution of the business processes and process connection among the business systems. On the basis of the workflow engine, full-process closed-loop management of all business systems such as projects, contracts, finance and performance is achieved, comprehensive budget management penetrating through the full life cycle of the projects and unified management of internal operation performance are achieved, and the problems that data is complex, multi-system crossing occurs, manual report statistics is depended, efficiency is low, and errors are likely to happen are solved.
Owner:中通服创发科技有限责任公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com