Method and system for realizing unified threat management in heterogeneous network
A heterogeneous network and management system technology, applied in the field of network security, can solve the problems that single-device UTM prevention methods cannot be realized
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
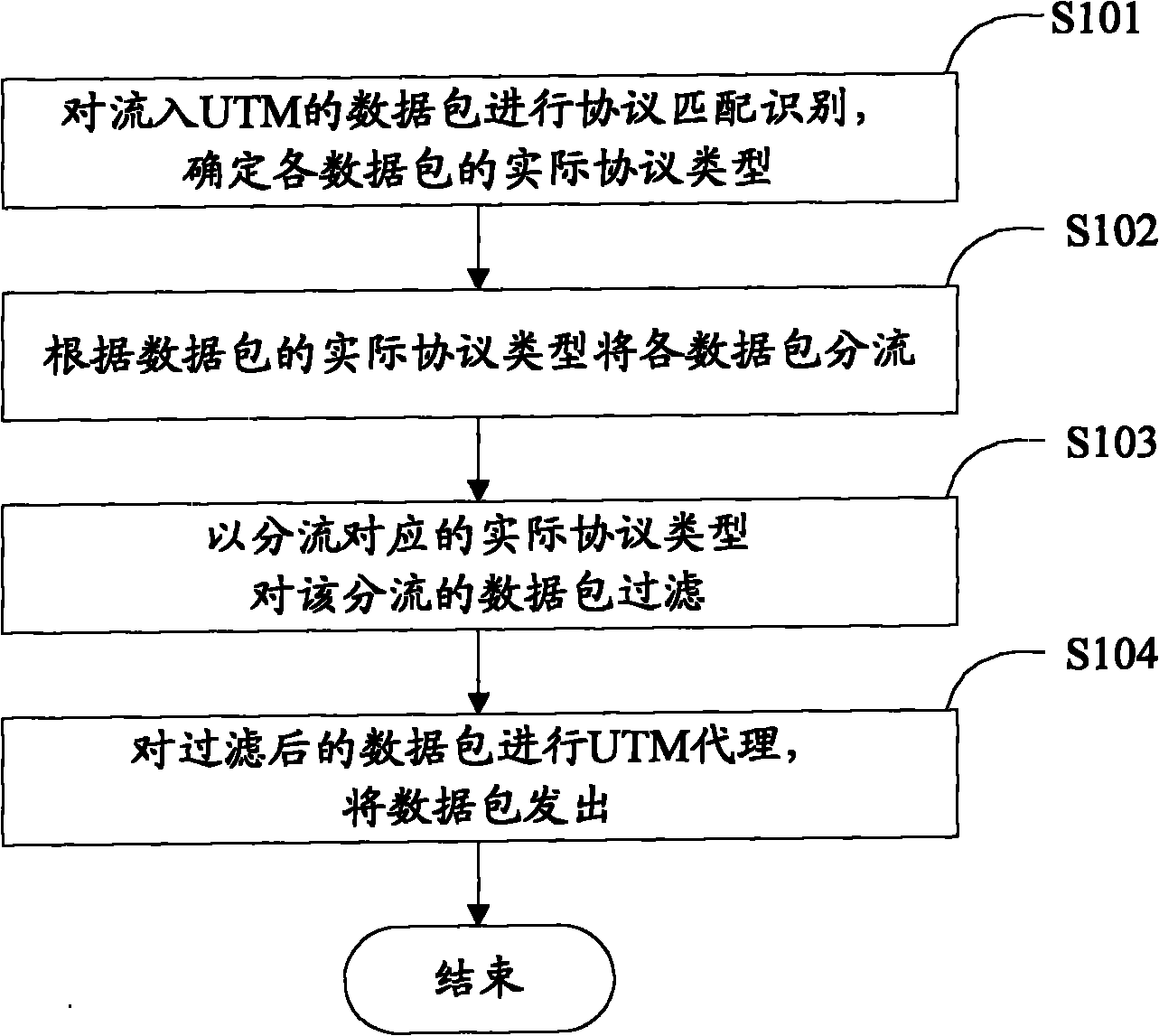
[0021] Embodiment 1, see figure 1 As shown, the method for realizing unified threat management in the heterogeneous network in the embodiment of the present invention includes the following main steps:
[0022] S101. Perform protocol matching and identification on the data packets flowing into the UTM, and determine the actual protocol type of each data packet.
[0023] S102. Distribute each data packet according to the actual protocol type of the data packet.
[0024] S103. Filter the offloaded data packets according to the actual protocol type corresponding to the offload.
[0025] S104. Perform UTM proxy on the filtered data packet, and send the data packet.
Embodiment 2
[0026] Embodiment 2. The method for implementing unified threat management in a heterogeneous network in the embodiment of the present invention includes the following main steps:
[0027] S201. Perform protocol matching and identification on the data packets flowing into the UTM, and determine the actual protocol type of each data packet.
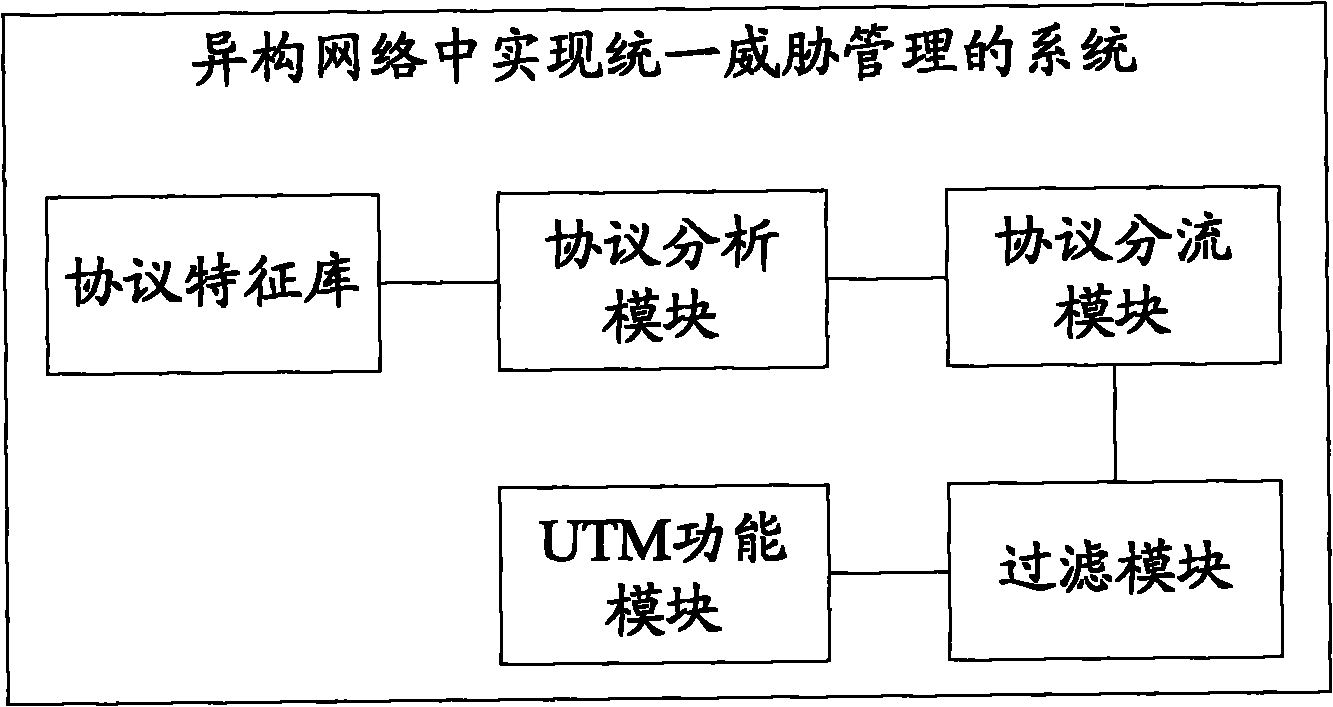
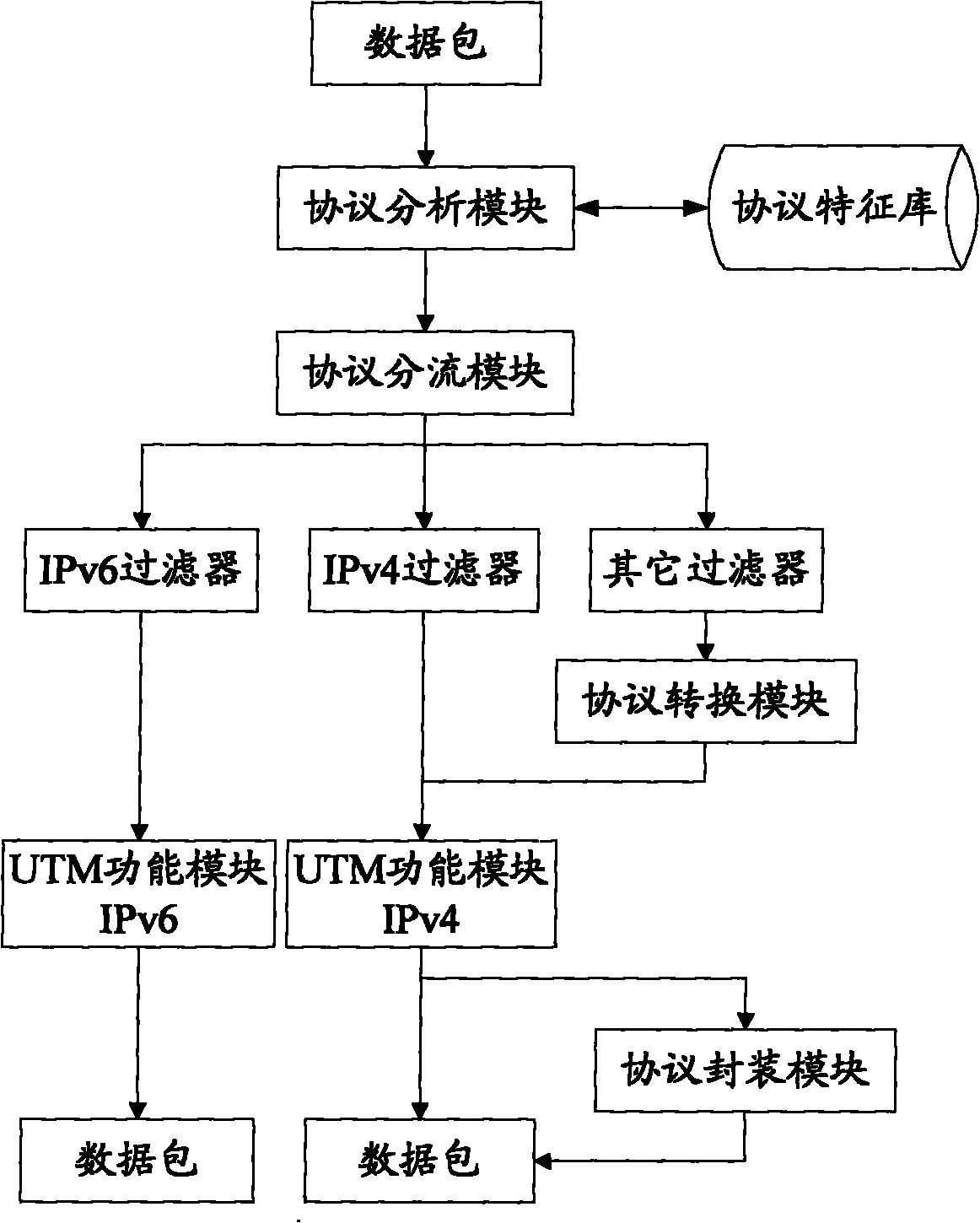
[0028] Since in a composite network (heterogeneous network), the network protocol used is not a single protocol, but uses multiple protocols at the same time, therefore, the data packets transmitted in the composite network usually carry multiple protocols, such as TCP / IP protocol (IPv4, IPv6), non-TCP / IP protocol (IPX / SPX, NETBEUI, GRE and other protocols). The process of the actual protocol type determined in this step is for example: the data packet sent by the composite network is an IPv4 data packet encapsulated in IPv6 mode, after matching and identifying with the protocol feature information in the protocol signature database, it i...
Embodiment 3
[0035] Embodiment 3. The method for implementing unified threat management in a heterogeneous network in the embodiment of the present invention includes the following main steps:
[0036] S301. Perform protocol matching and identification on the data packets flowing into the UTM, and determine the actual protocol type of each data packet.
[0037] Since in a composite network (heterogeneous network), the network protocol used is not a single protocol, but uses multiple protocols at the same time, therefore, the data packets transmitted in the composite network usually carry multiple protocols, such as TCP / IP protocol (IPv4, IPv6), non-TCP / IP protocol (IPX / SPX, NETBEUI, GRE and other protocols). The process of the actual protocol type determined in this step is for example: the data packet F1 sent by the composite network at T1 time is an IPv4 data packet encapsulated in IPv6 mode. After matching and identifying the protocol feature information in the protocol signature datab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com