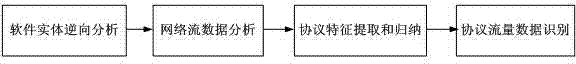
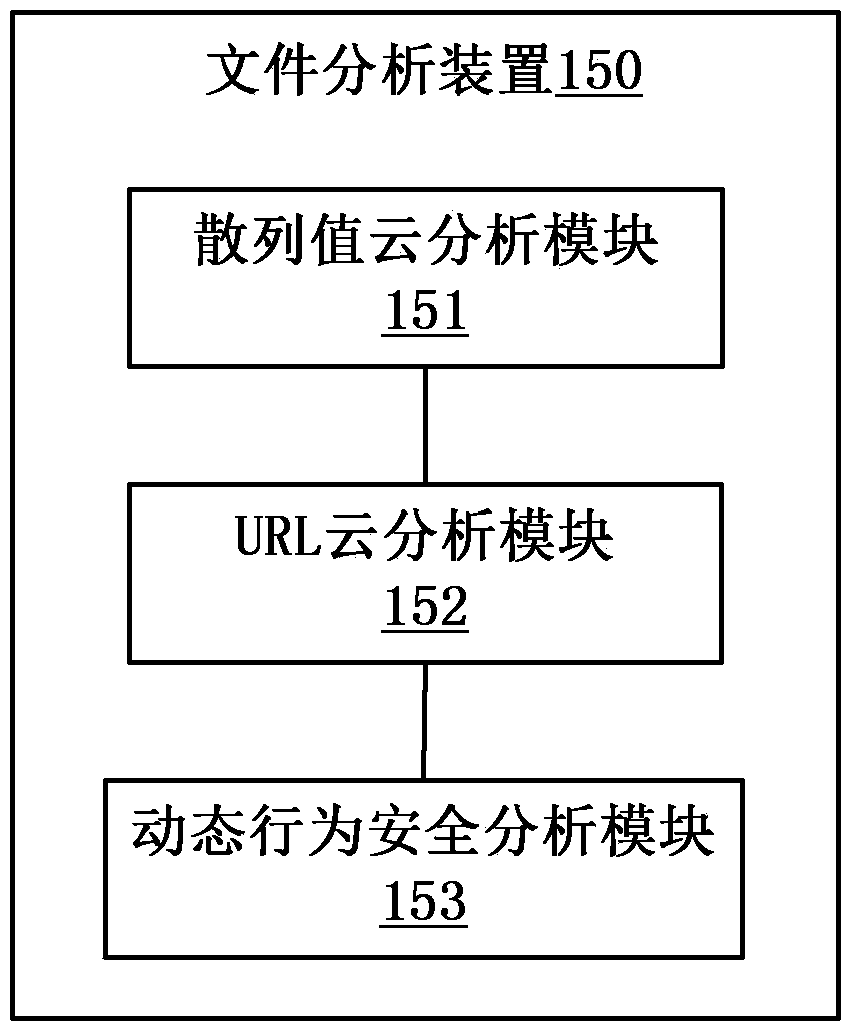
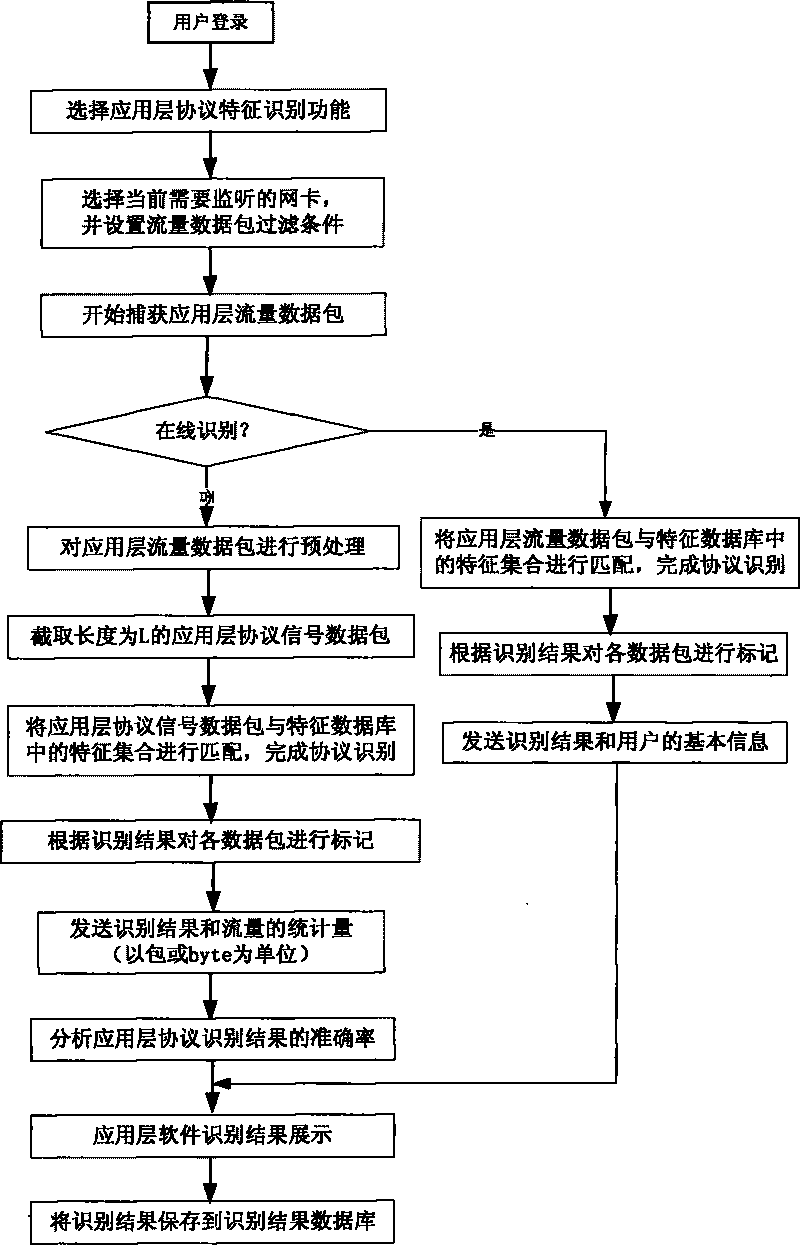
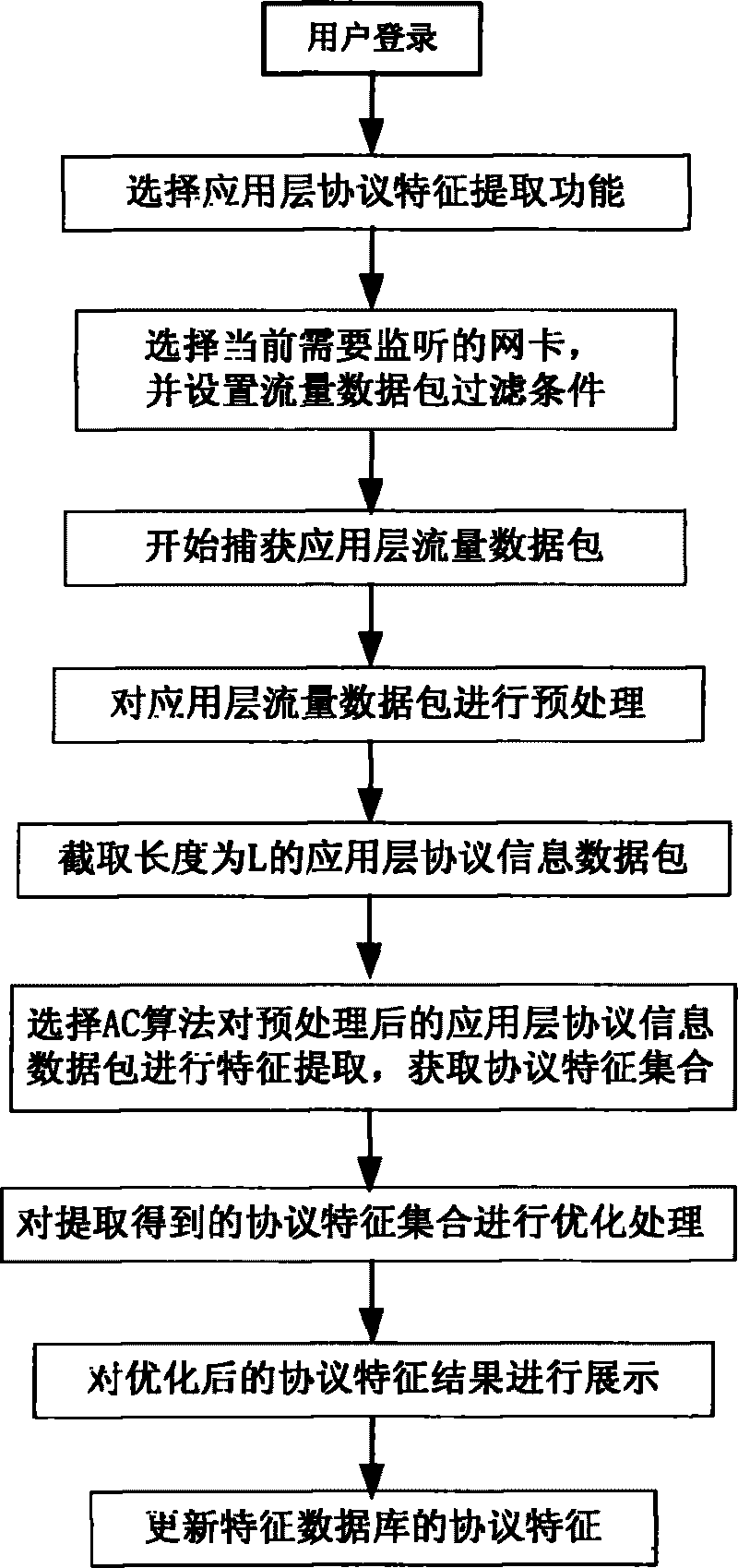
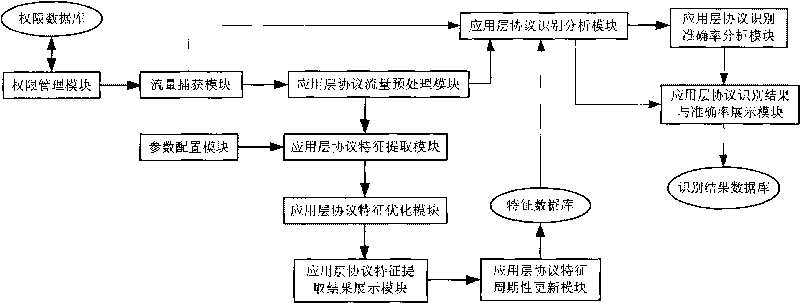
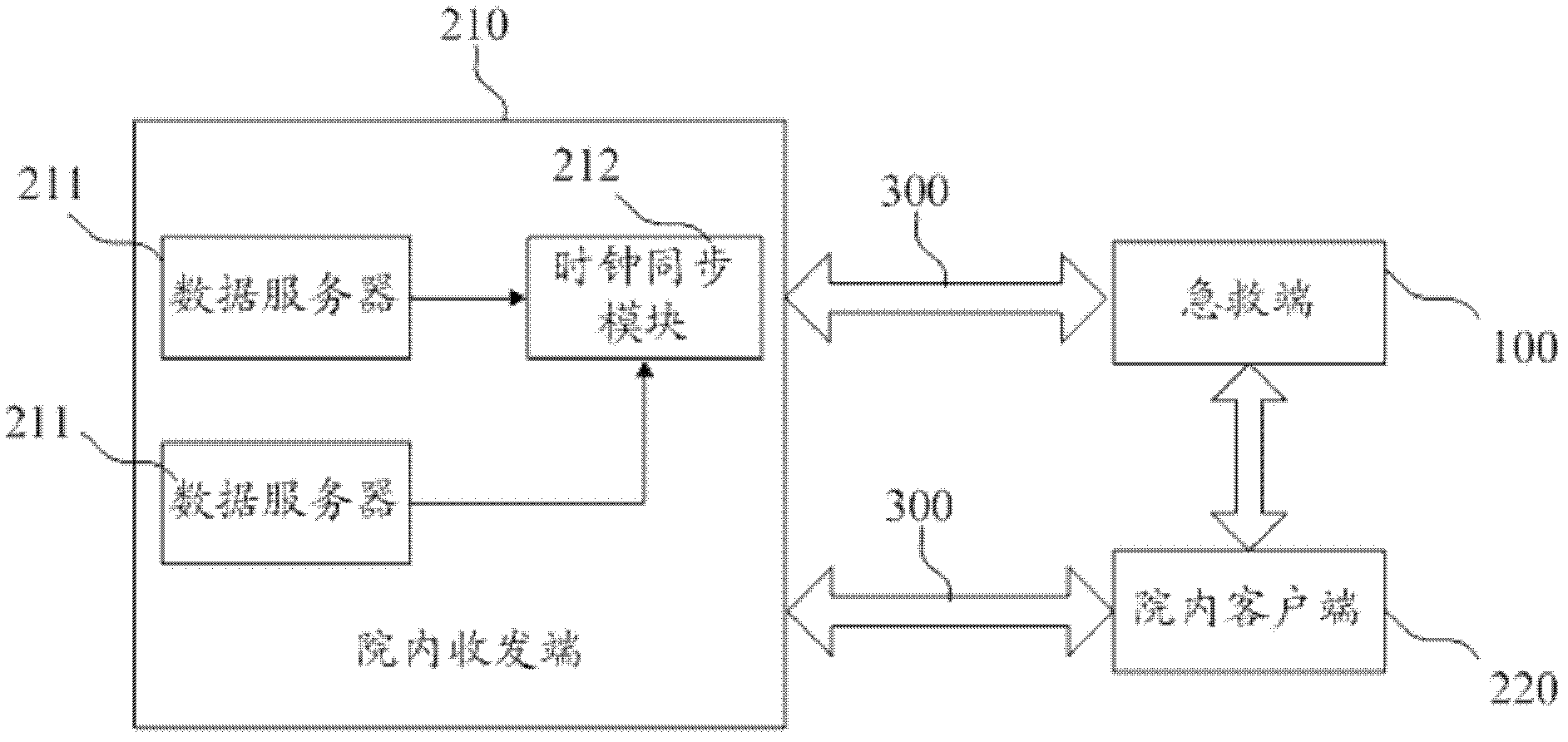Patents
Literature
189 results about "Agreement analysis" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
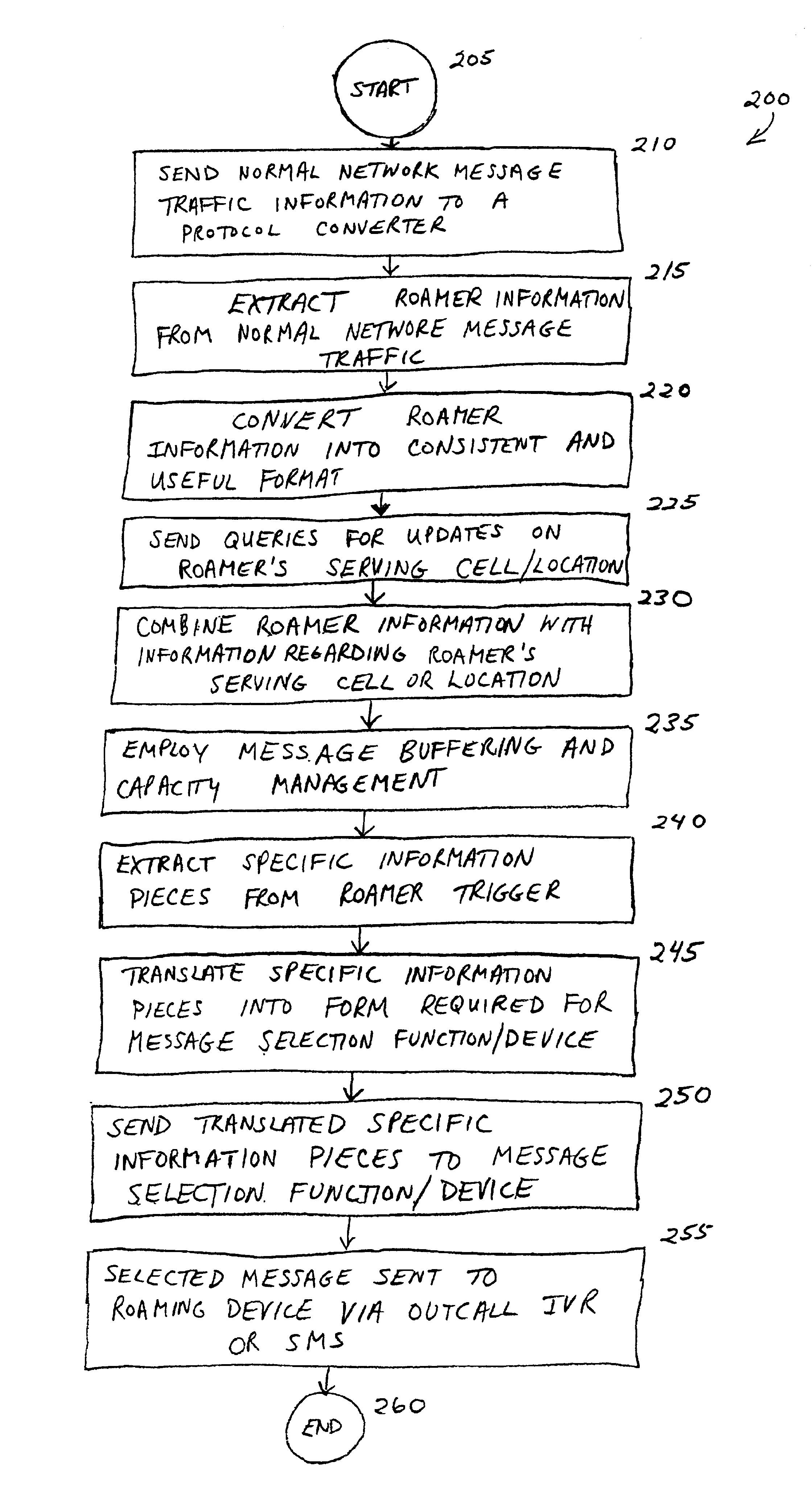
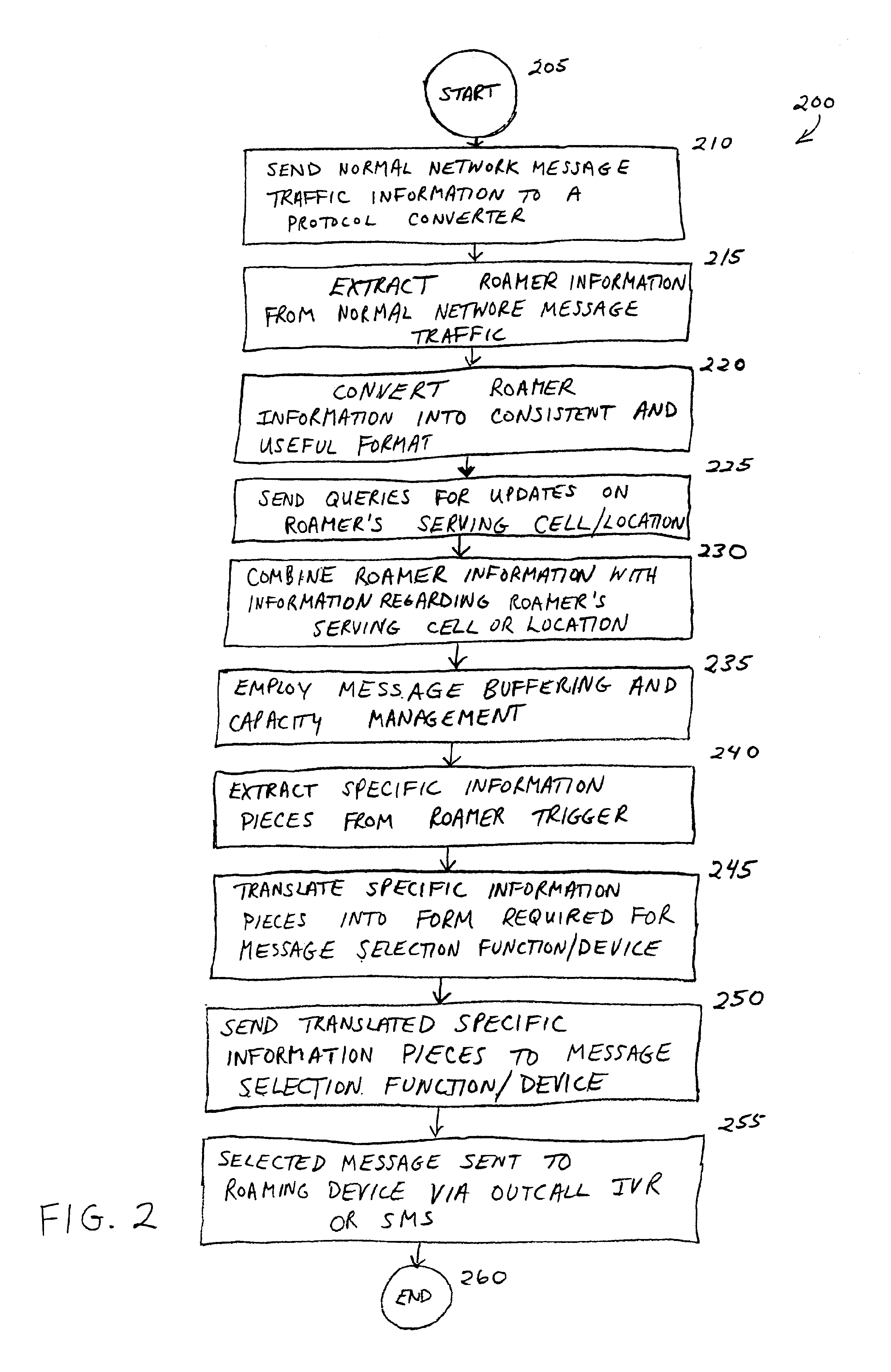
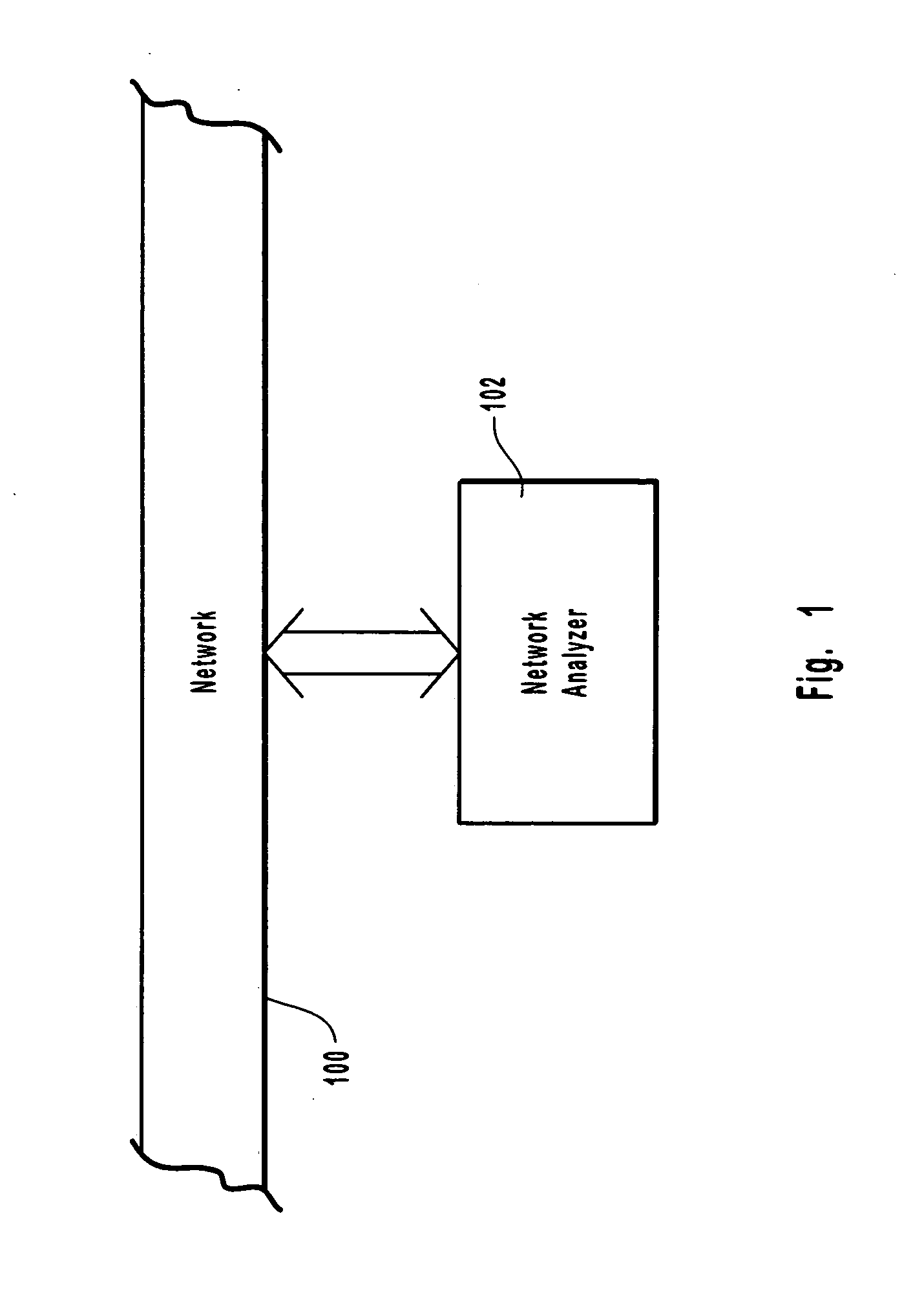
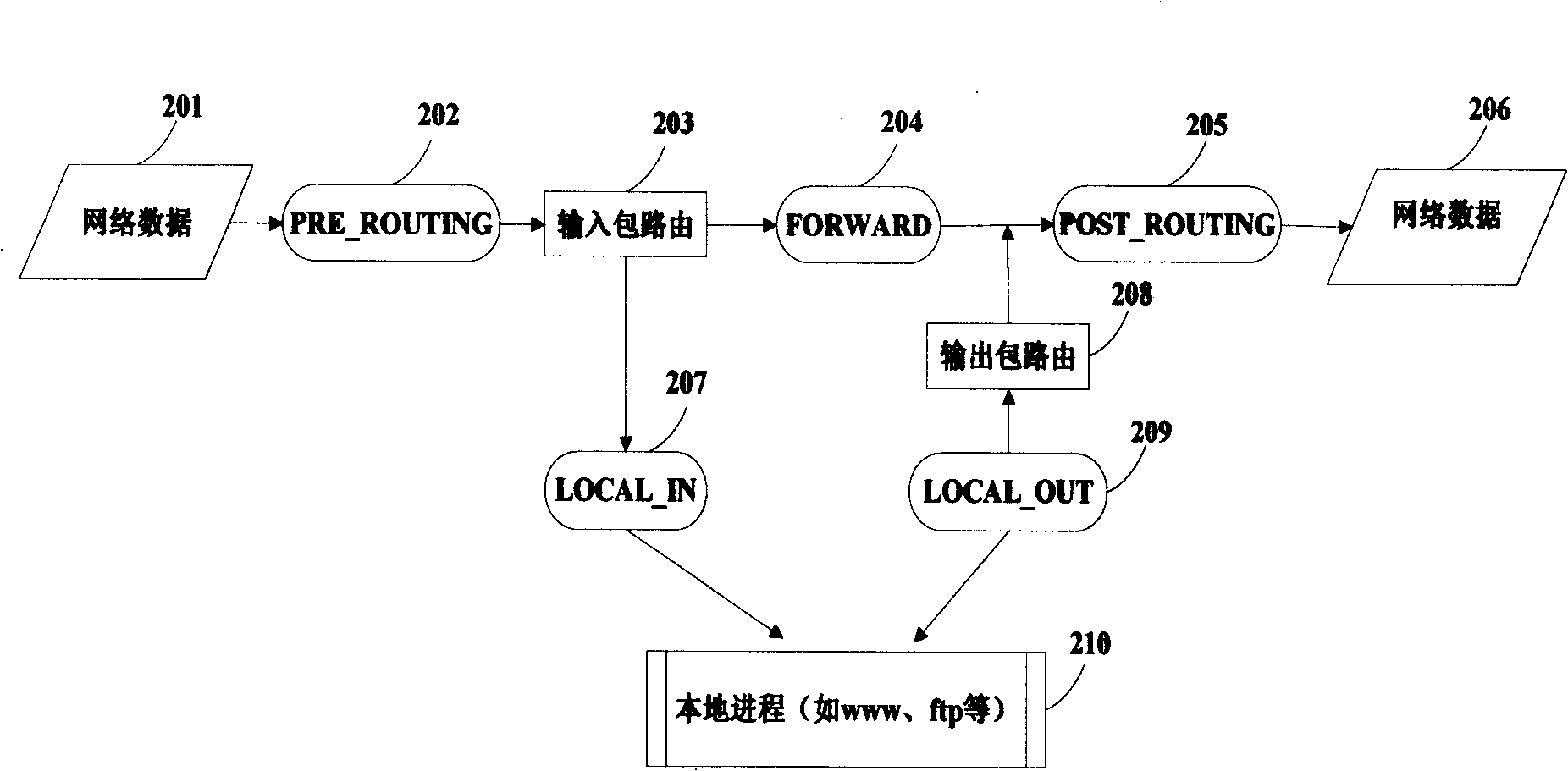
System and method for providing information services to cellular roamers
InactiveUS6922562B2Special service for subscribersTime-division multiplexTelecommunicationsProtocol converter
A method for providing information services to a wireless device roaming in a wireless system is disclosed. Normal network message traffic information is obtained from a wireless system. The normal network message traffic information is transmitted to a protocol converter. In the protocol converter, roamer information is extracted from the normal network message traffic information and converted into a protocol analyzer format. A query is transmitted to a Mobile Switching Center requesting information regarding the wireless device's serving cell or location. Information regarding the wireless device's serving cell or location is received and combined with the converted roamer information to form a roamer trigger. The roamer trigger is transmitted to protocol analyzer. In the protocol analyzer, specific information pieces regarding the wireless device are extracted. The extracted specific information pieces are transmitted to a data interpreter for translation and delivery to a wireless device.
Owner:WARD STEPHEN L +1
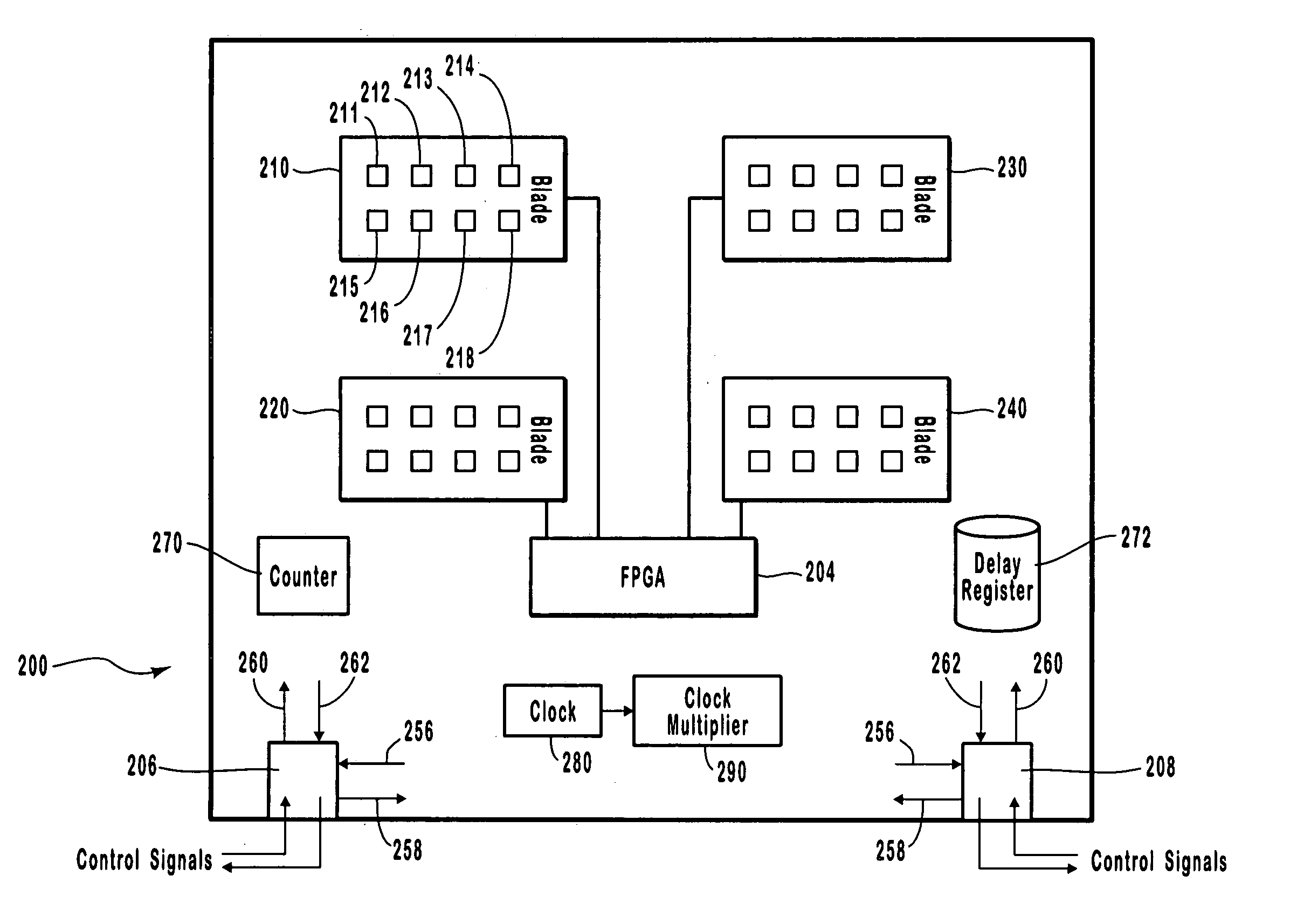
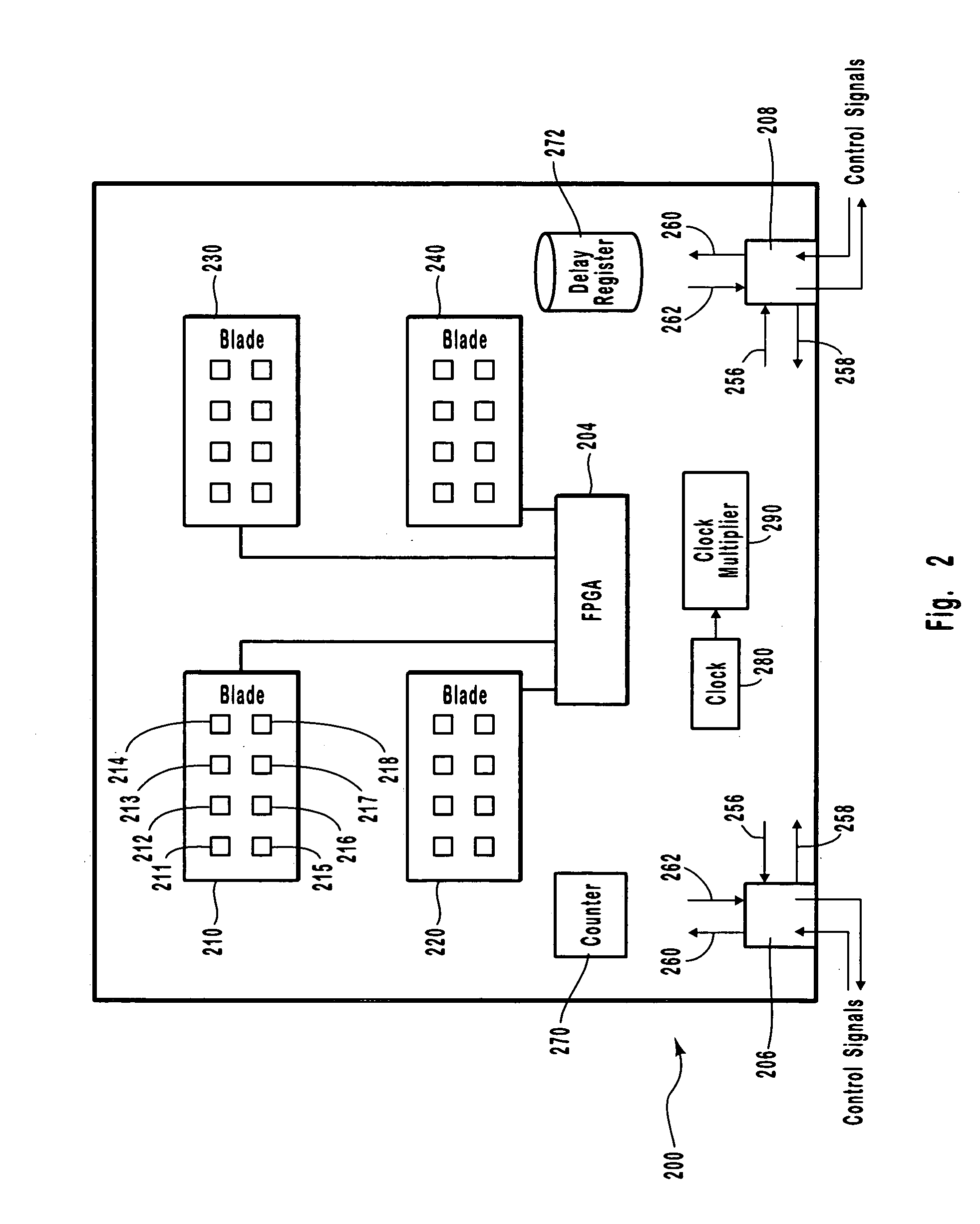
Synchronization of timestamps to compensate for communication latency between devices
InactiveUS20050010691A1To overcome the large delayTime-division multiplexMultiple digital computer combinationsTimestampControl signal
Protocol analyzer systems enable synchronization of timestamps and the capture of data across serially chained boxes that are used together to monitor and capture network data. Through experiment, it can be determined how long it takes to propagate a signal to each box in the chain. These values are then recorded in each box in a delay register so that each box has a recorded delay value corresponding to the time required to propagate a signal to or receive a signal from every other box. Each box applies a control signal, such as a run signal or a trigger signal, to the ports in the box only after the expiration of the delay value indicated in the delay register. The box initiating the signal has the largest delay since the other boxes need to get the signal before the boxes can begin to operate with a common counter, with successive boxes having smaller delays.
Owner:VIAVI SOLUTIONS INC
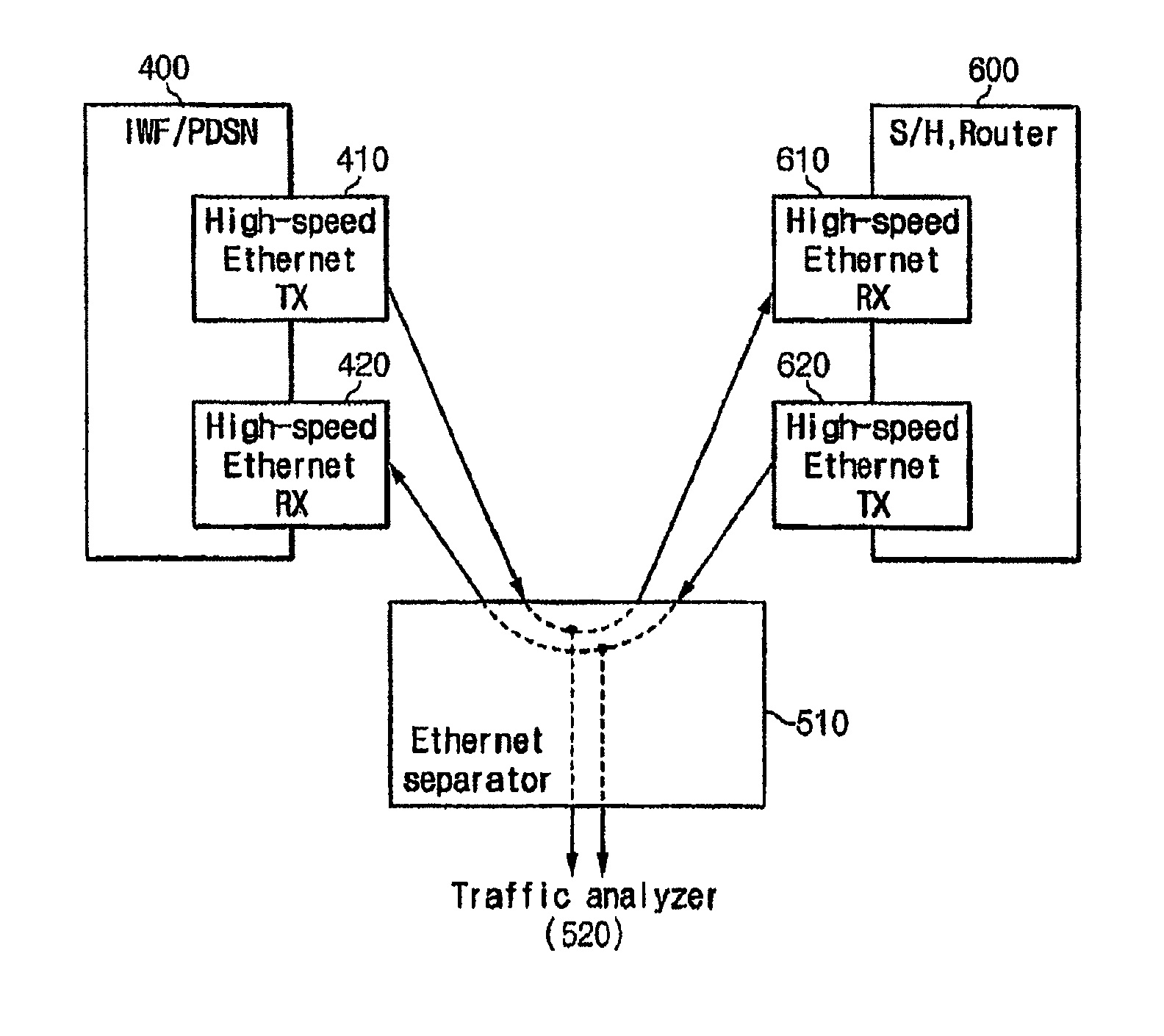
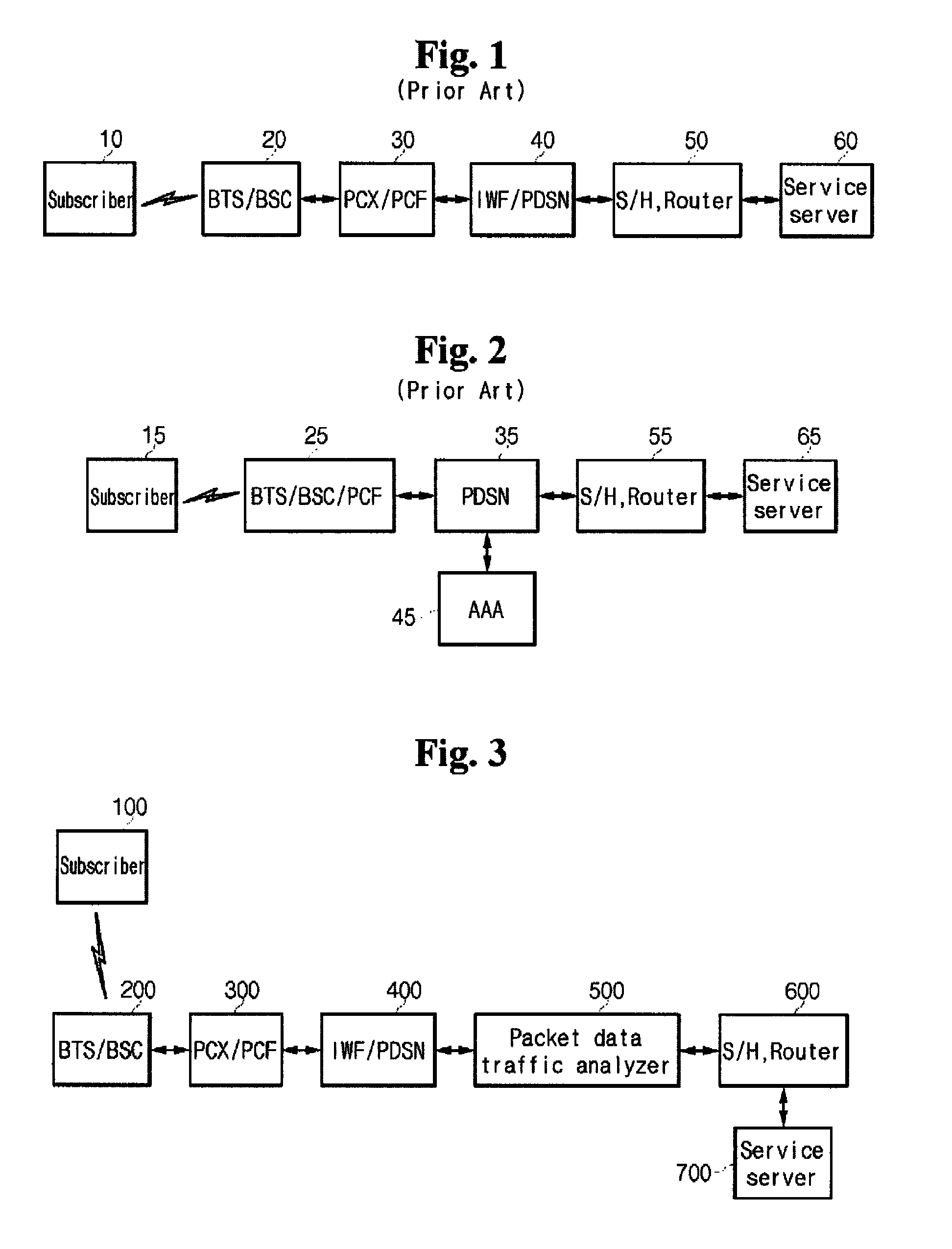
Apparatus for analyzing the packet data on mobile communication network and method thereof
InactiveUS8180881B2Easy to analyzeEfficient networkingMetering/charging/biilling arrangementsMultiple digital computer combinationsTraffic capacityWireless data services
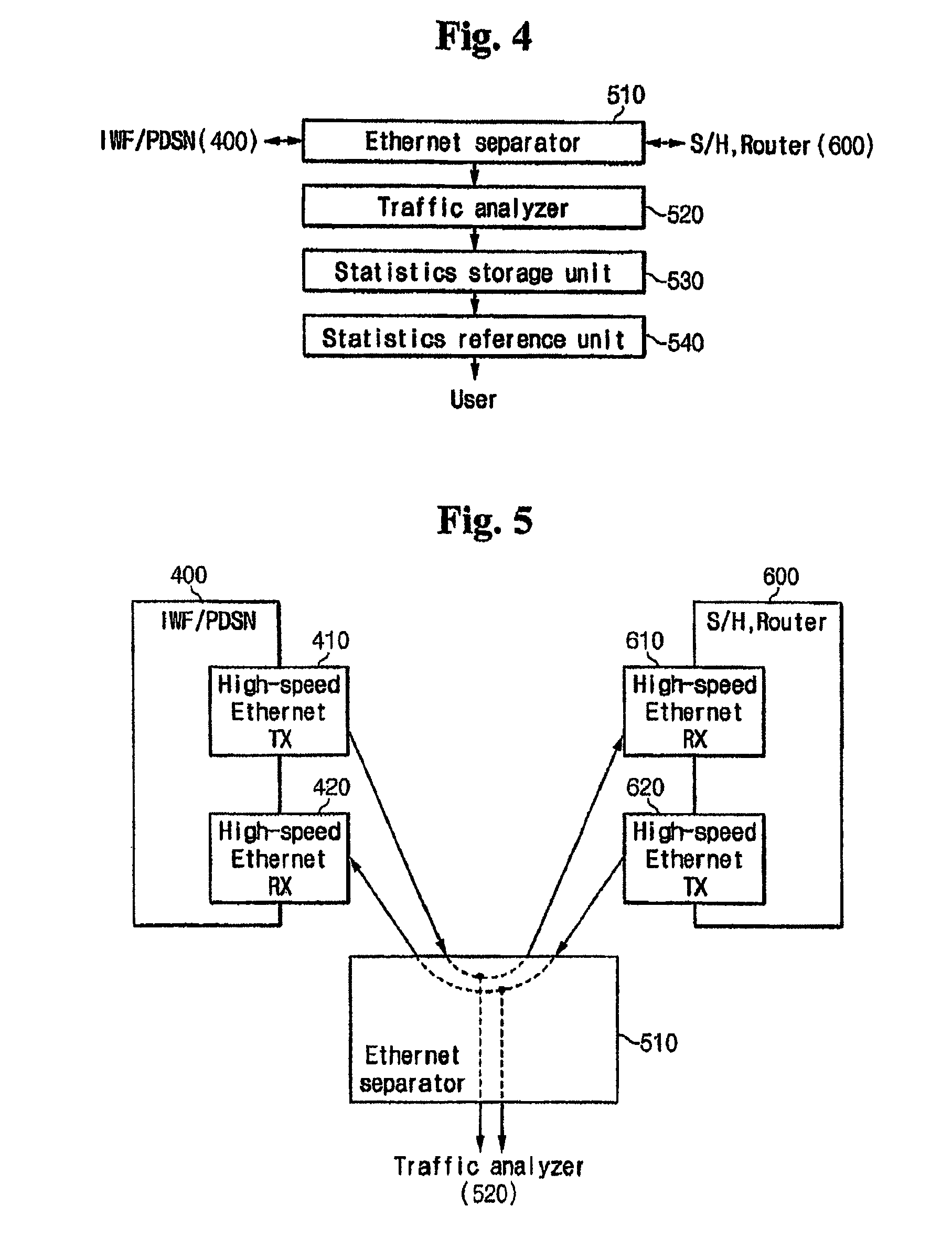
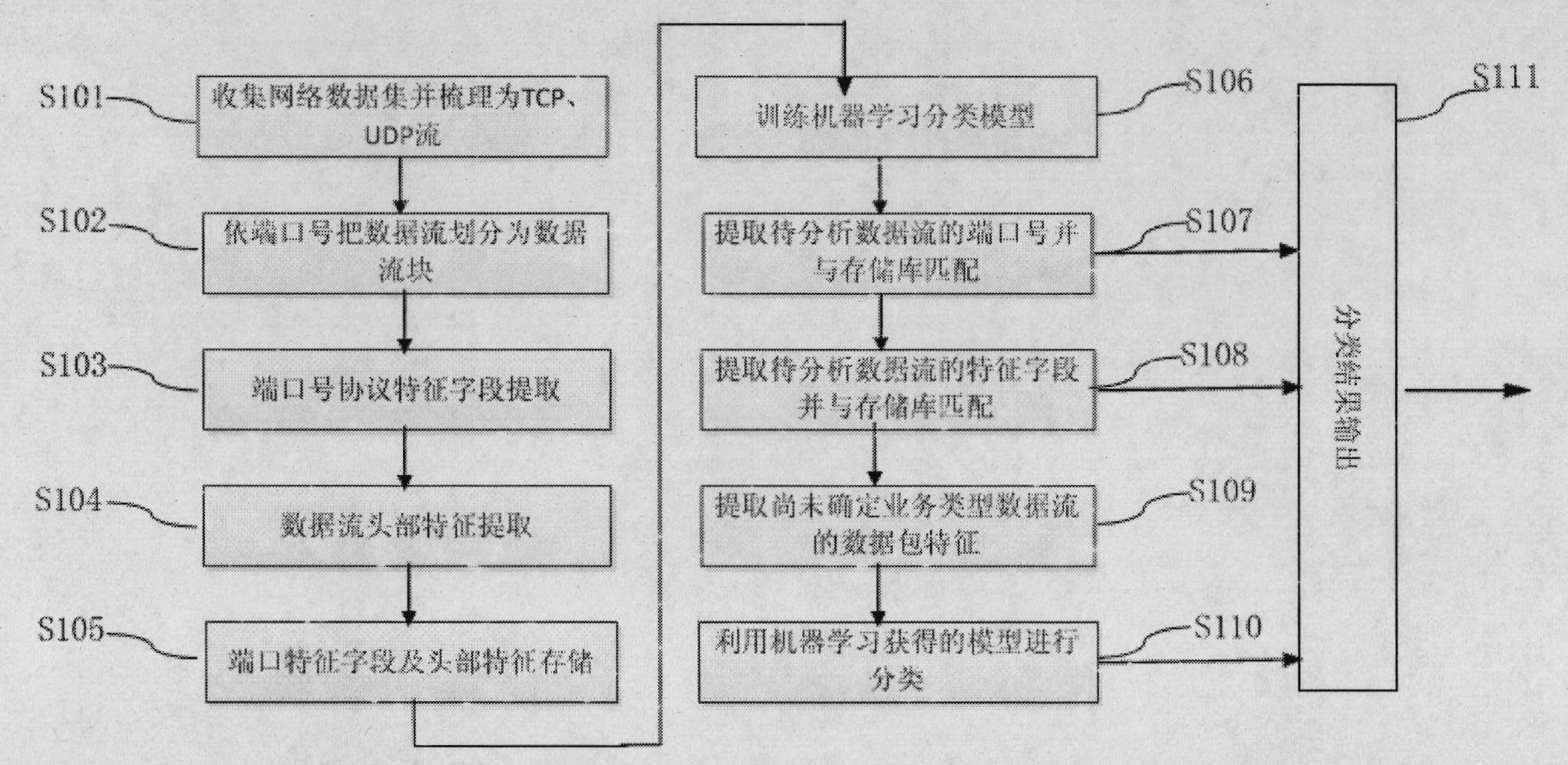
A packet data analyzer on a mobile communication network for analyzing packet data traffic, monitoring services, generating billing information per data service, and monitoring the network based on a protocol analysis, comprises a packet data separator provided between one of a mobile communication exchange and a packet controller that provide a wireless data service to the subscriber, and the service server, for separating user packet data transmitted between one of the mobile communication exchange and the packet controller and the service server, and receiving the user packet data; a traffic analyzer for separating the user packet data received through the packet data separator according to transmission directions, and analyzing the user packet data; a statistics storage unit for storing and managing result data analyzed by the traffic analyzer; and a statistics reference unit for retrieving data stored in the statistics storage unit, and providing statistical information desired by the user.
Owner:KT CORP
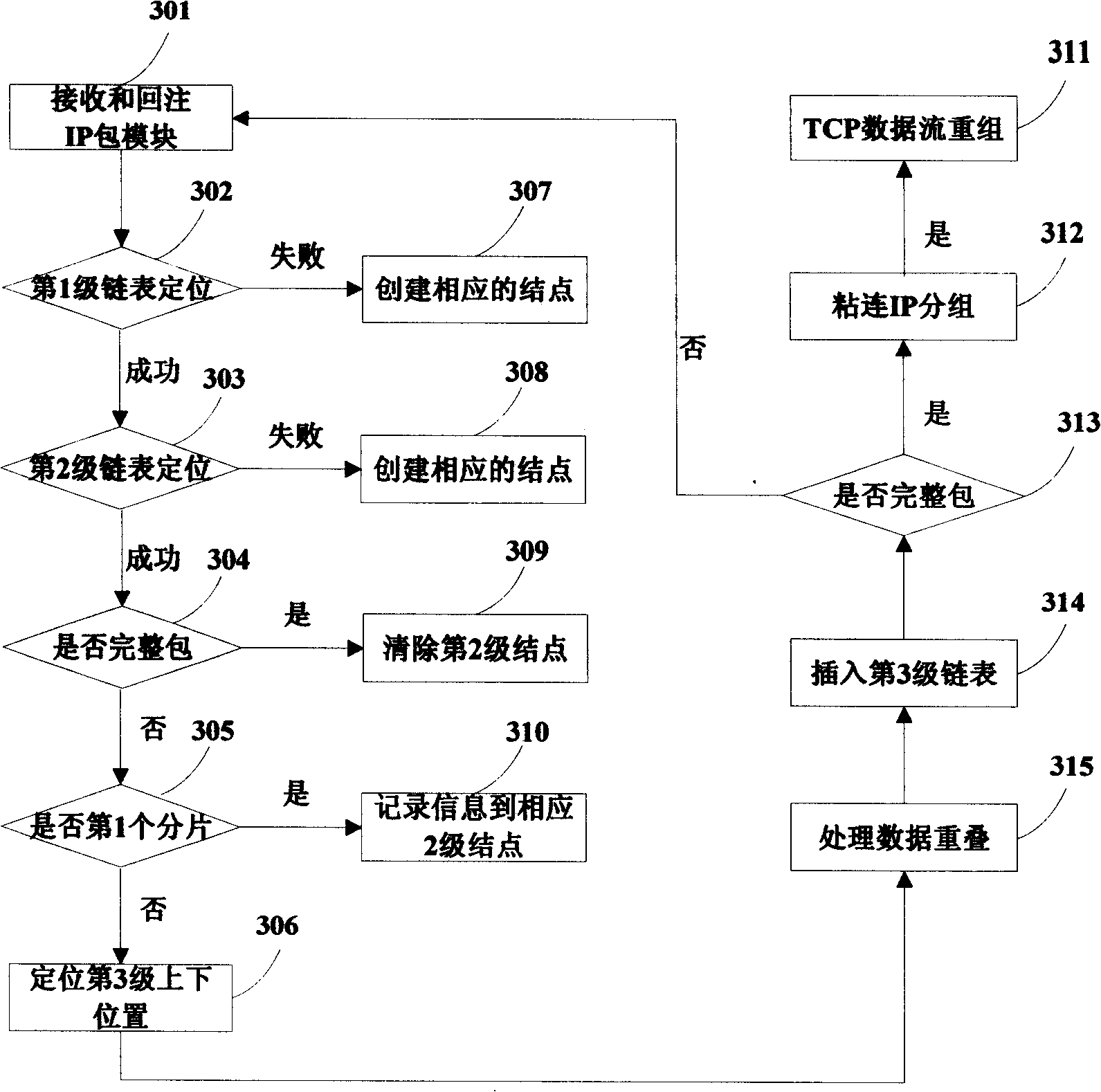
Stratification characteristic analysis-based method and apparatus thereof for on-line identification for TCP, UDP flows
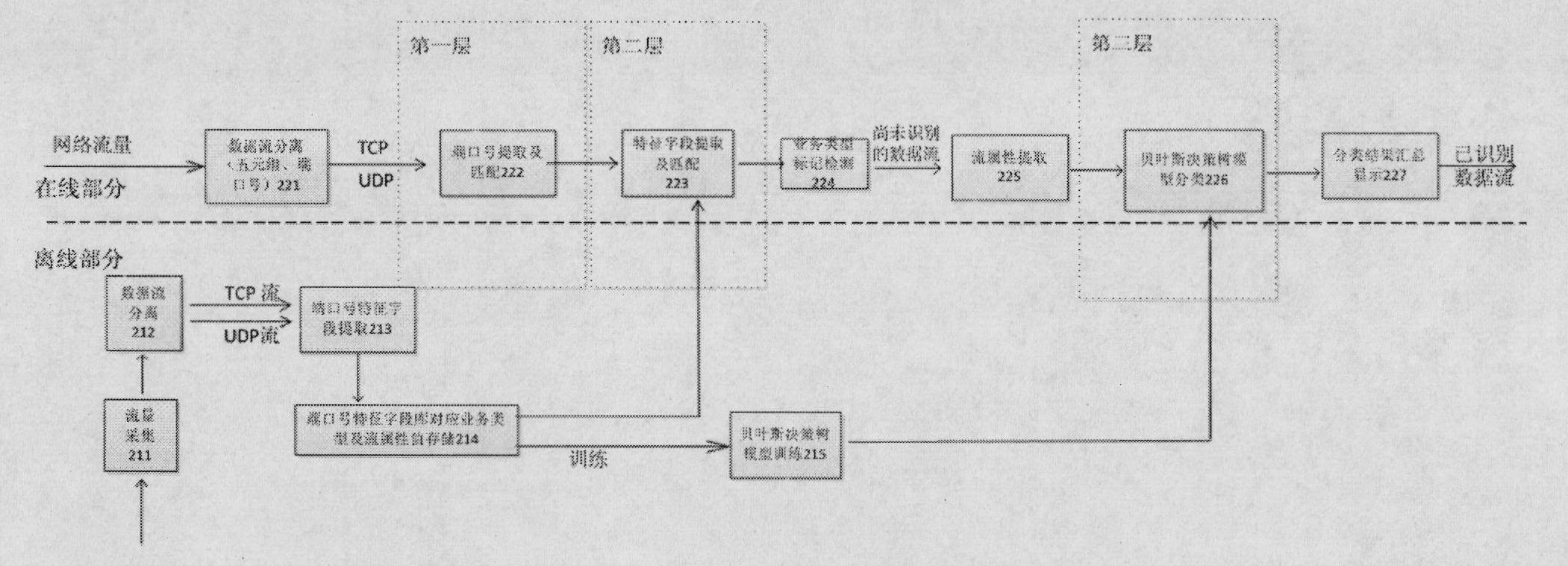
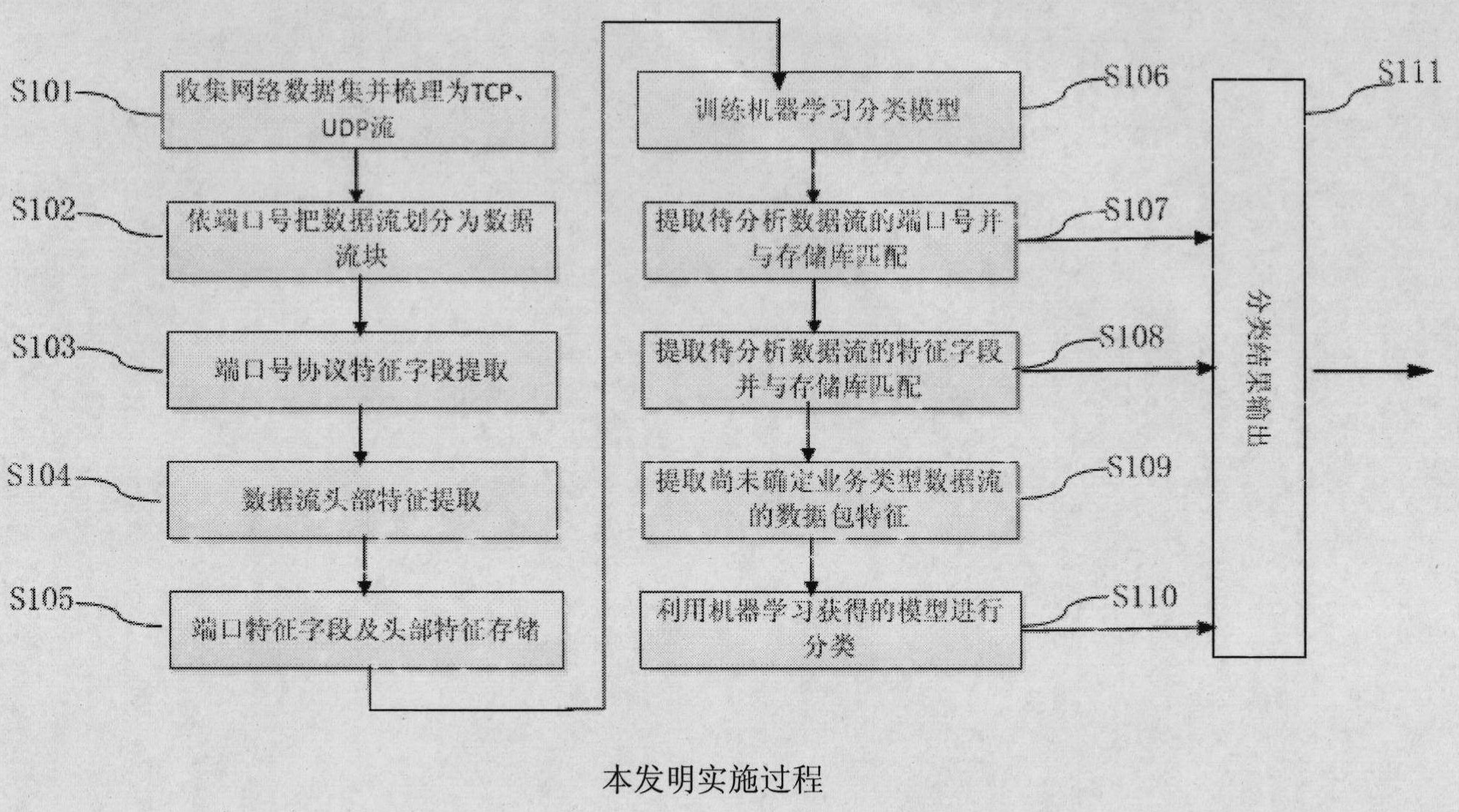
The invention relates to a stratification characteristic analysis-based method and an apparatus thereof for on-line identification for TCP, UDP flows. The method comprises the following steps that: an off-line phase determines a common port number of a first layer to-be-identified service type and a characteristic field of a second layer to-be-identified service data flow through a protocol analysis; a port number and characteristic field database is constructed; meanwhile, a third layer Bayesian decision tree model is obtained by training by employing a machine study method; and service type identification on a flow is completed by utilizing the characteristic database and a study model at an on-line classification phase. In addition, the apparatus provided in the invention comprises a data flow separating module, a characteristic extraction module, a characteristic storage module, a characteristic matching module, an attribute extraction module, a model construction and classification module and a classification result display module. According to the embodiment of the invention, various application layer services based on TCP and UDP are accurately identified; moreover, the identification process is simple and highly efficient; therefore, the method and the apparatus are suitable for realization of a hardware apparatus and can be applied for equipment and systems that require on-line flow identification in a high speed backbone network and an access network.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Proprietary protocol analysis and identification method
ActiveCN104506484AEfficient analysisEasy to implementTransmissionStructure of Management InformationClient-side
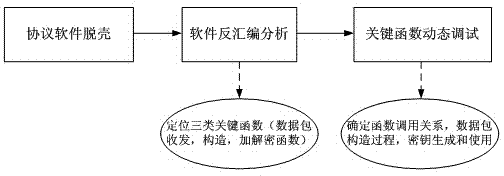
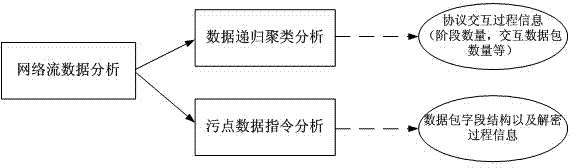
The invention relates to the technical field of protocol communication, and discloses a proprietary protocol analysis and identification method. The method comprises the following specific steps: I, performing shelling processing on communication client software by adopting a proprietary protocol; disassembling an original program; and dynamically debugging a key function in an assembly code; II, fetching the network flow data of the proprietary protocol, performing message data packet classification according to different stages of protocol interaction, and resolving the field structure of each type of message data packet respectively; III, extracting and inducing protocol characteristics in an interaction process, wherein the protocol characteristics comprise interaction process information and the field structure characteristics of the message data packets; and IV, setting a matching expression of protocol identification by using the protocol characteristics obtained in the step III, and identifying flow acquired in a network. Through the method, the analysis and identification of the proprietary protocol are realized.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
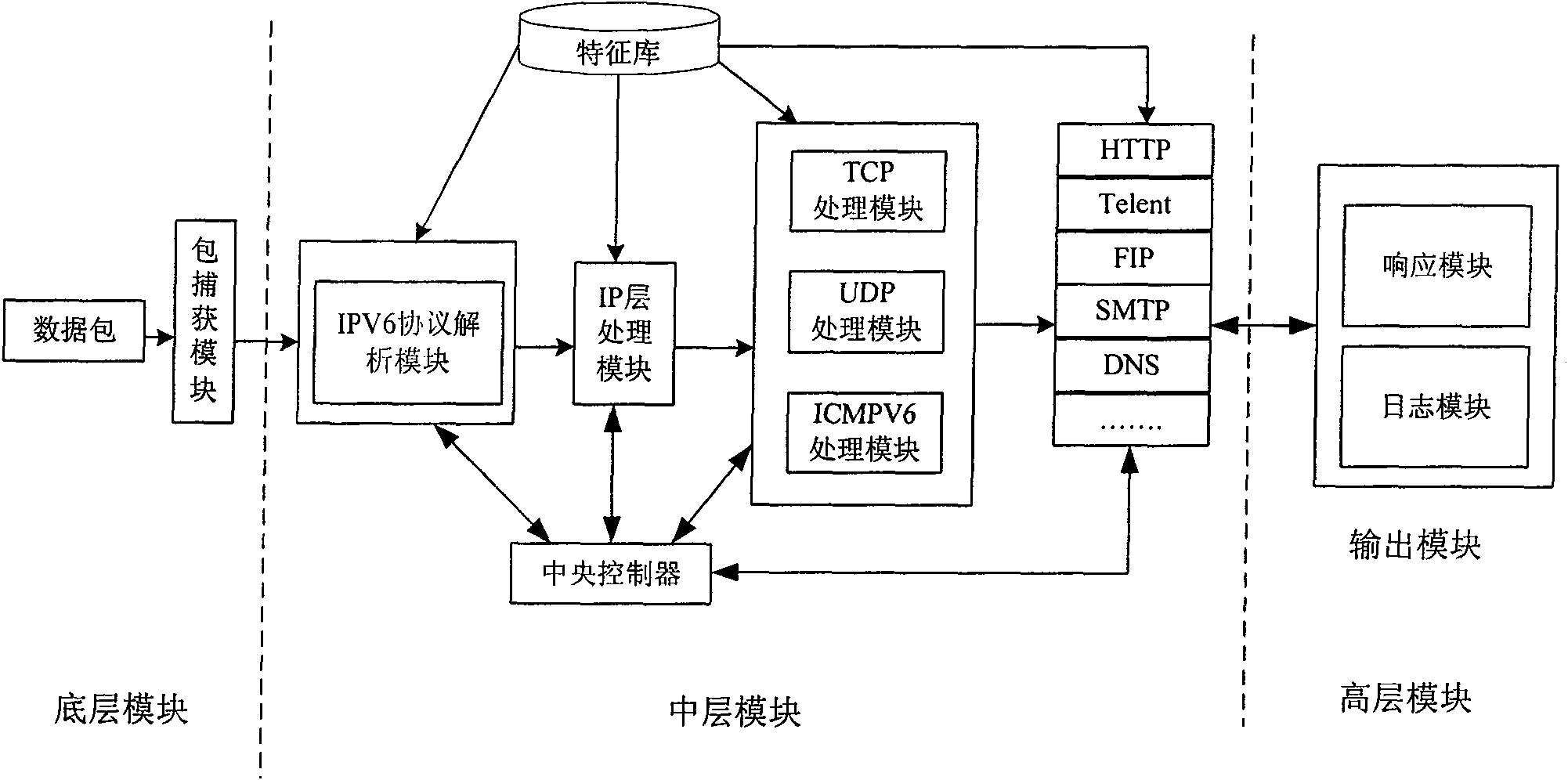
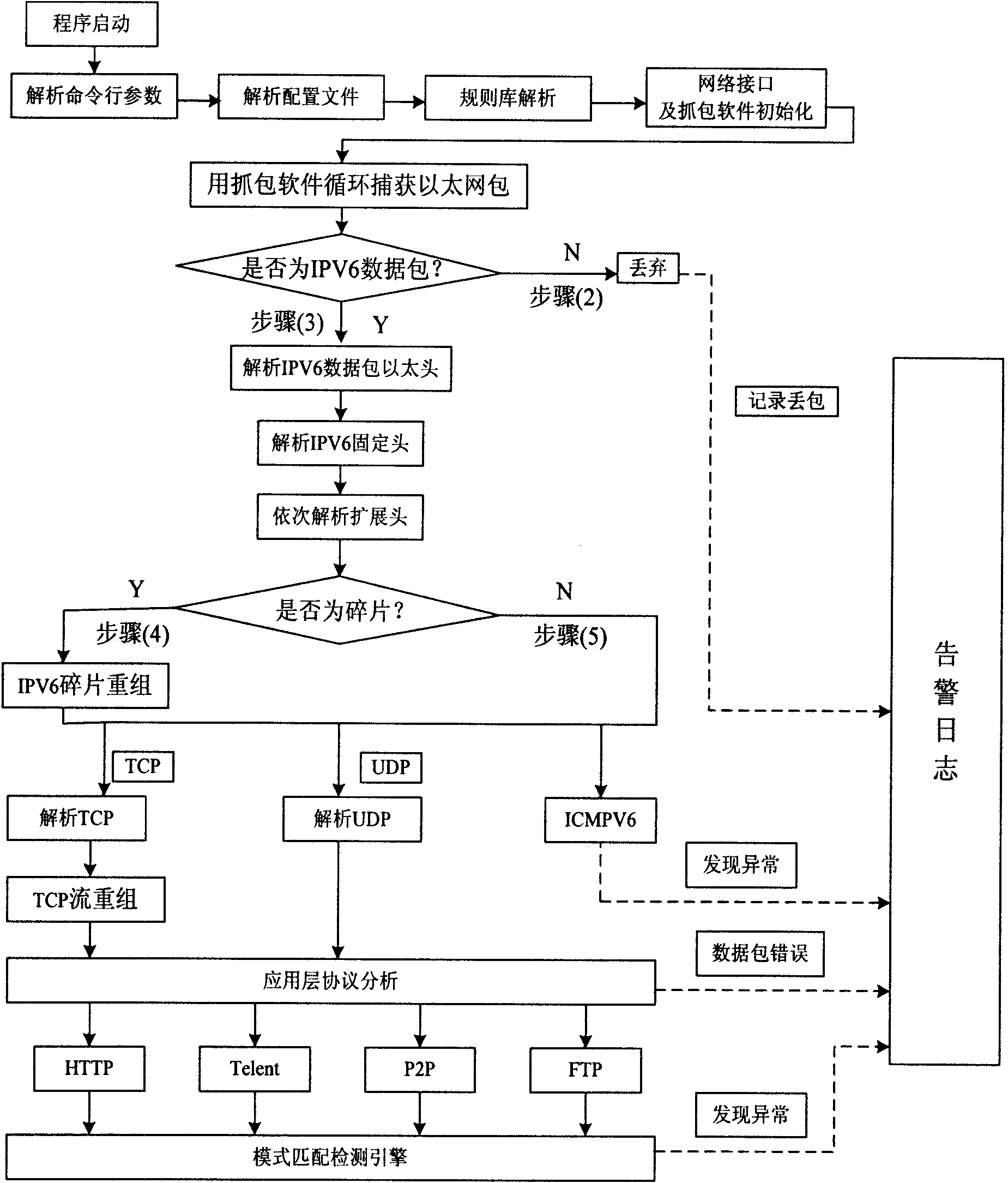
Intrusion detection system and method based on IPv6 network environment
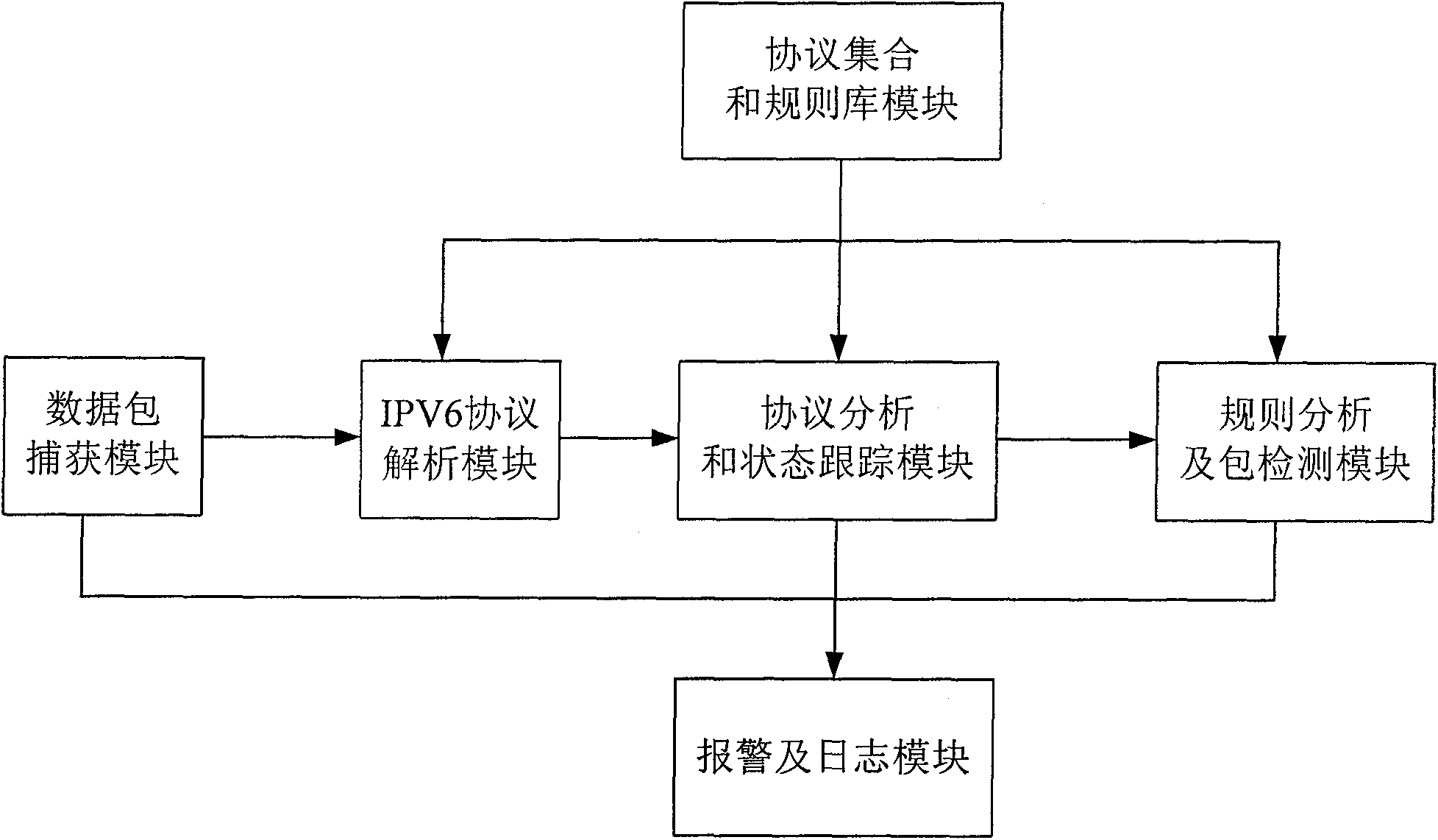
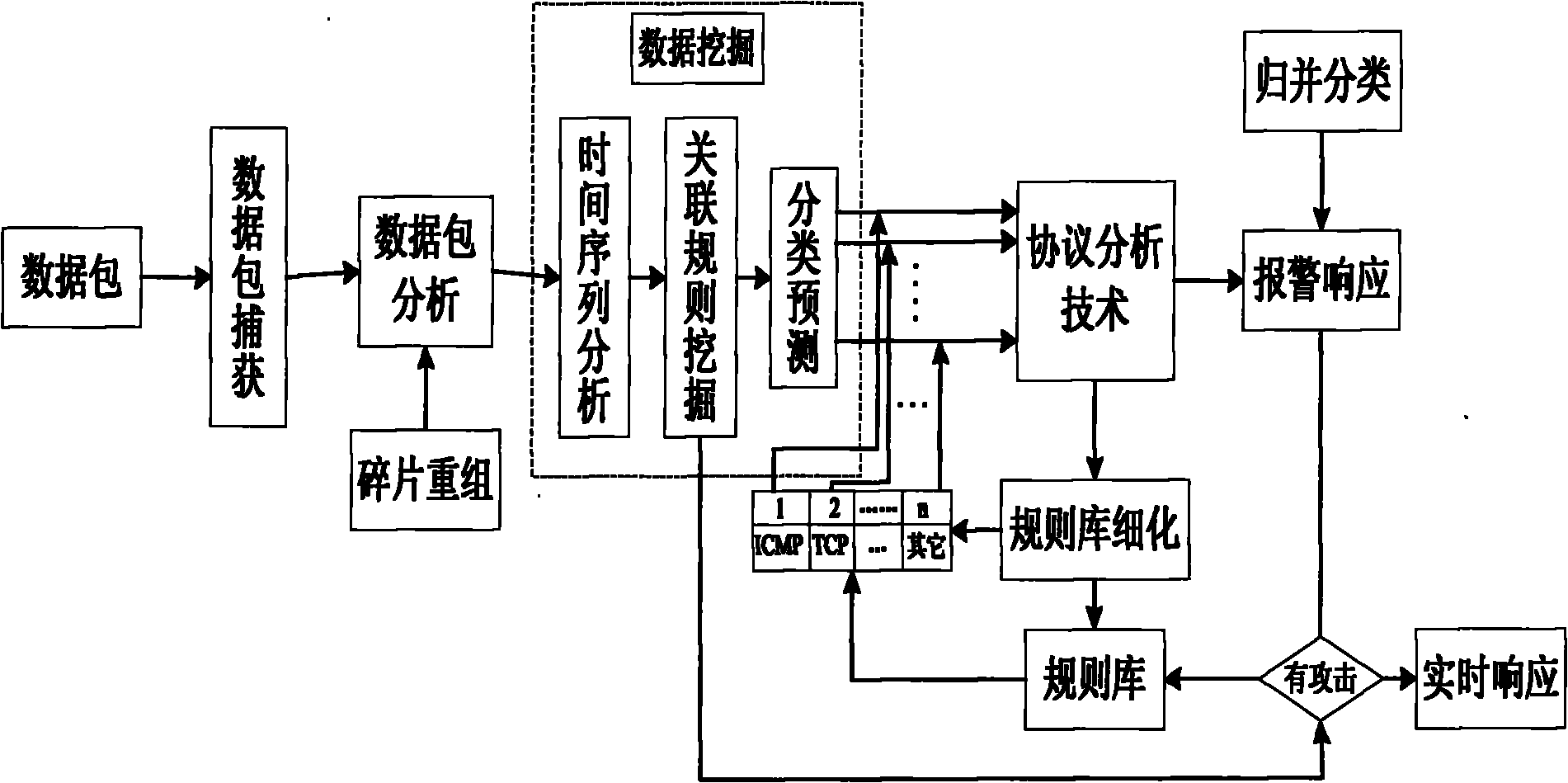
The invention provides an intrusion detection system (IDS) and a method based on IPv6 network environment. The system comprises a protocol set and rule base module, a data packet capture module, an IPV6 protocol analysis module, a protocol analysis and state tracking module, a rule analysis and packet detection module and a warning and logging module. The invention well solves the new problem of transplant of the IDS, brought about by the new IPv6 standards and characteristics, and improves the capture ability of the data packet, the detection means of the IDS and the safety detection abilityof the IDS.
Owner:JINAN UNIVERSITY
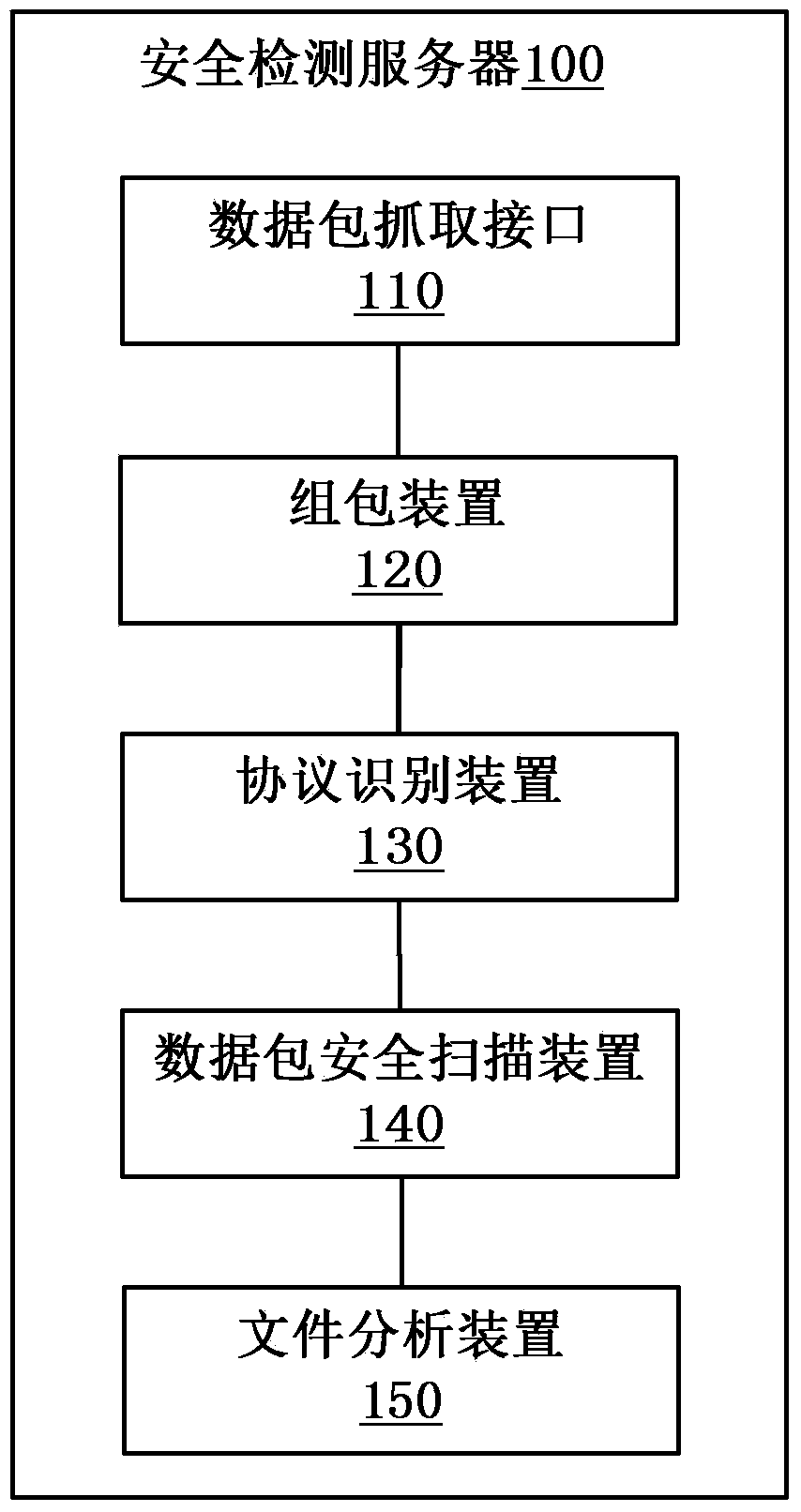
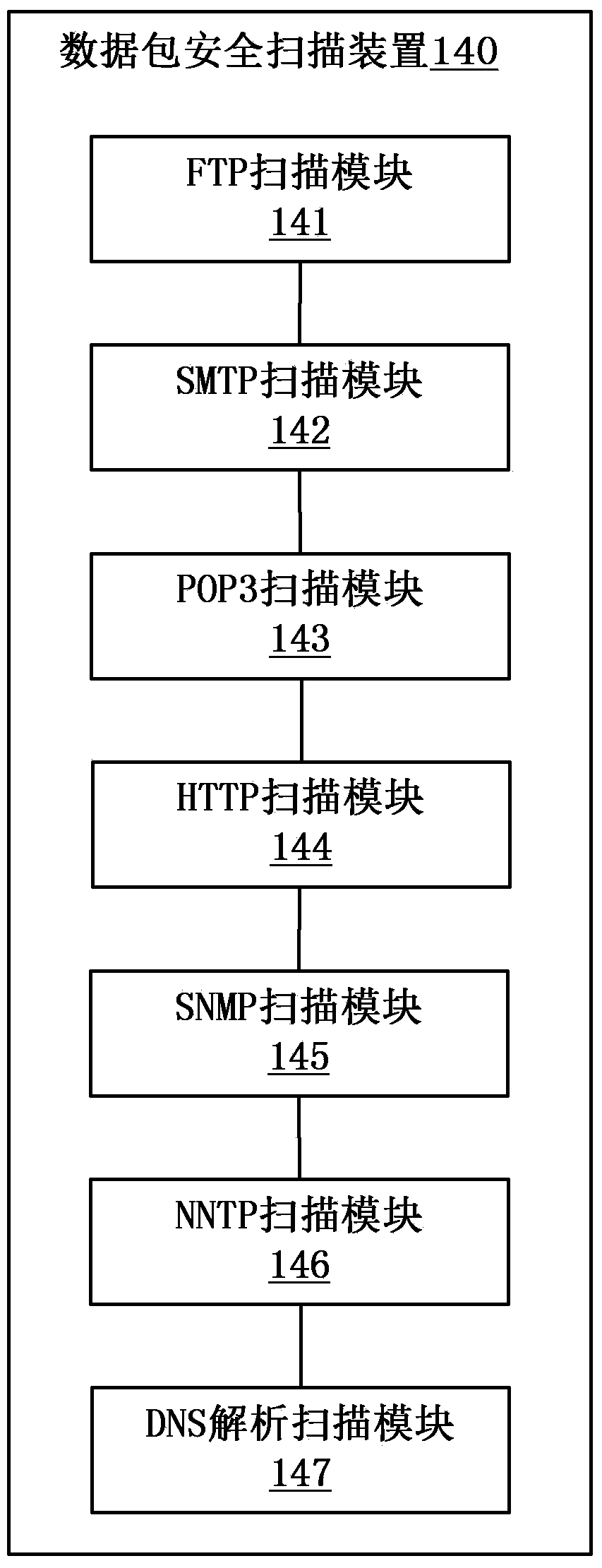
Security detection method and security detection server for network data
ActiveCN103634306AIdentify attackImprove securityData switching networksNetwork attackNetwork security policy
The invention provides a security detection method and a security detection server for network data. The security detection method for network data comprises the steps: capturing data packets transmitted in a network; performing packet composing on the data packets so as to restore TCP (Transmission Control Protocol) connection data; recognising an application layer protocol used by the TCP connection data; performing security scanning on the TCP connection data by a security scanning module corresponding to the application layer protocol. According to the technical scheme, after the data packets are captured and subjected to packet composing, security monitoring is performed on the data according to the application layer protocol corresponding to the data packets; protocol analysis is carried out based on the repacked data of the application layer protocol; the pertinence is strong, network attack can be fast and effectively recognised, and the network security is improved.
Owner:三六零数字安全科技集团有限公司
Identification method for application layer protocol characteristic
InactiveCN101741908AImprove accuracyPromote informatizationData switching networksInformatizationNetwork packet
The invention discloses an identification method for application layer protocol characteristics, comprising the following processes: capturing a flow packet, selecting an identification mode, pretreating the flow packet, combining a characteristic set in a characteristic database to identify current network flow and displaying an identification result. The characteristic set in the characteristic database is updated timely by adopting a set of data mining AC algorithm based on an Apriori algorithm, thereby improving the accuracy of identifying the application layer protocol, overcoming various disadvantages of identifying network protocols by the traditional manual analysis method, promoting the informatization and intellectualization of application layer protocol analysis work for enterprises and companies, reducing labor source load for enterprises and companies and improving work efficiency and rate of progress.
Owner:青岛朗讯科技通讯设备有限公司
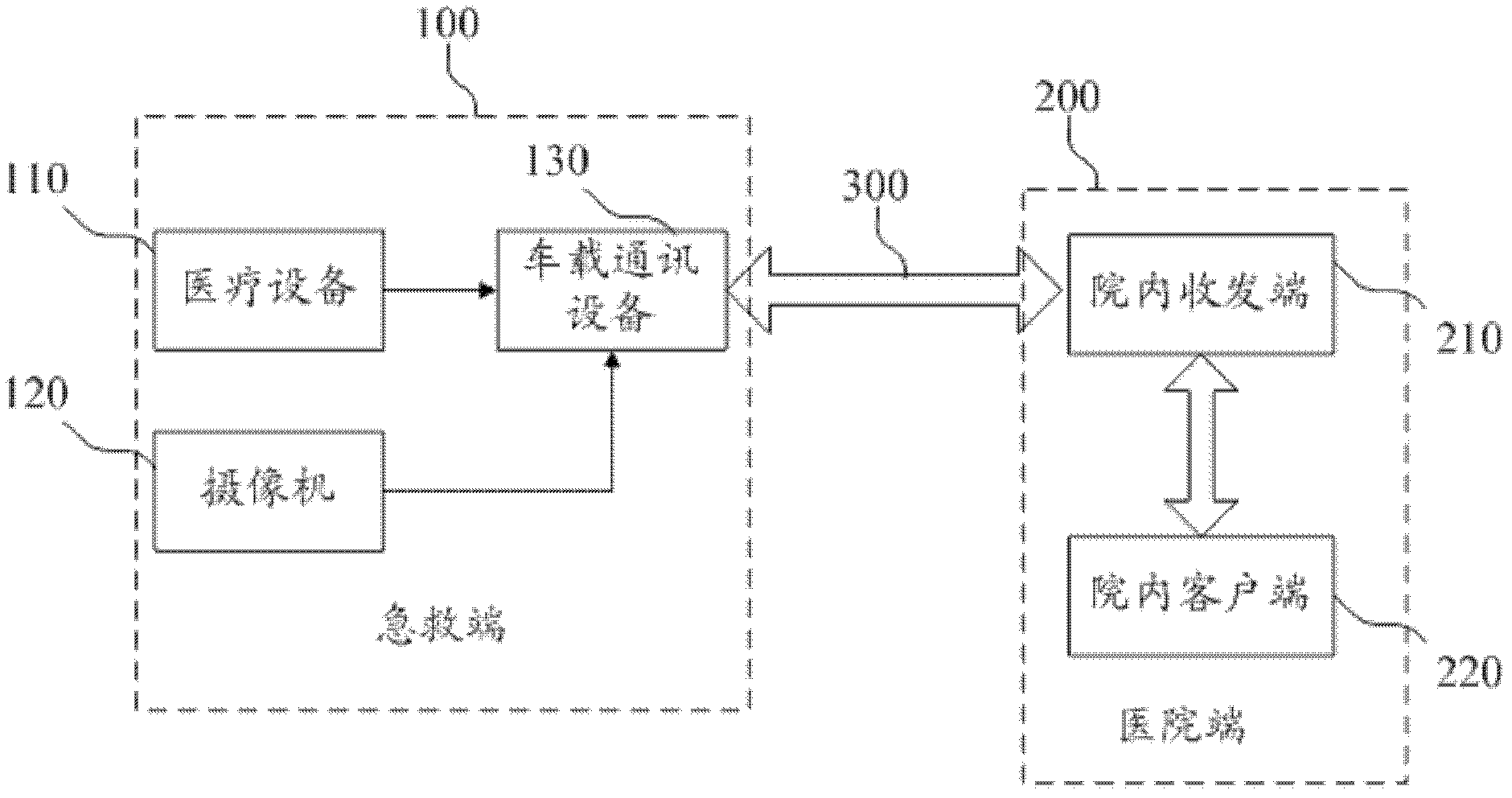
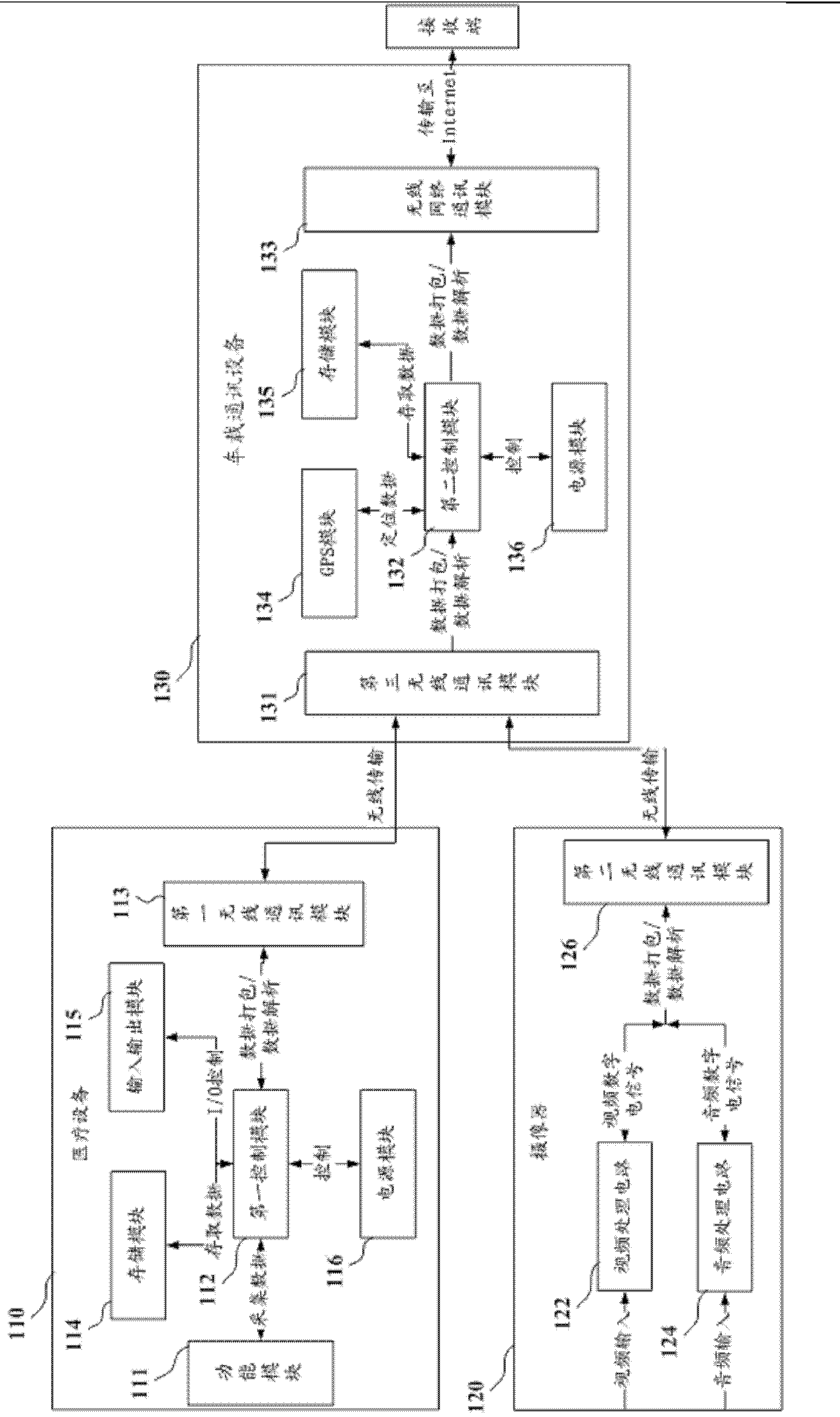
Prehospital first-aid system, first-aid end and hospital end
ActiveCN103136438ARealize two-way communicationAchieve interactionSpecial data processing applicationsData informationData transmission
The invention discloses a prehospital first-aid system, an ambulance and a hospital end. The first-aid end comprises medical equipment, a camera and vehicle-mounted communication equipment. The vehicle-mounted communication equipment receives data sent by the medical equipment and the camera and transmits the received data to the hospital end. The hospital end comprises a within-hospital receive and dispatch end which comprises one or a plurality of networking data servers. Each data server is configurated to receive data from the first-aid end, to conduct agreement analysis, processing and storage on the received data, to send data to the first-aid end and to receive at least response information or data information or a control instruction. The prehospital first-aid system, the first-aid end and the hospital end achieve two-way communication between the prehospital and the first-aid end, not only achieve interaction of prehospital monitoring data, curing information and treatment spot audio and video information between a hospital and the first-aid end, but also enable the outside hospital first-aid process to be guided by hospital in time.
Owner:SHENZHEN MINDRAY BIO MEDICAL ELECTRONICS CO LTD
Network intrusion detector with combined protocol analyses, normalization and matching
ActiveUS20080047012A1Unnecessary inspectionReduce in quantityMemory loss protectionUnauthorized memory use protectionNetwork dataRegular expression
A network intrusion detection system combines the normally sequential steps of protocol analysis, normalization, and signature matching through the use of a regular expression to speed the monitoring of network data. The regular expression also allows the creation of a superset matcher, permitting multiple stages of matching of increased accuracy to produce additional throughput gains.
Owner:WISCONSIN ALUMNI RES FOUND
Method and device for producing test case
InactiveCN101902367AImprove effectivenessSave time and costData switching networksComputer hardwareComputer science
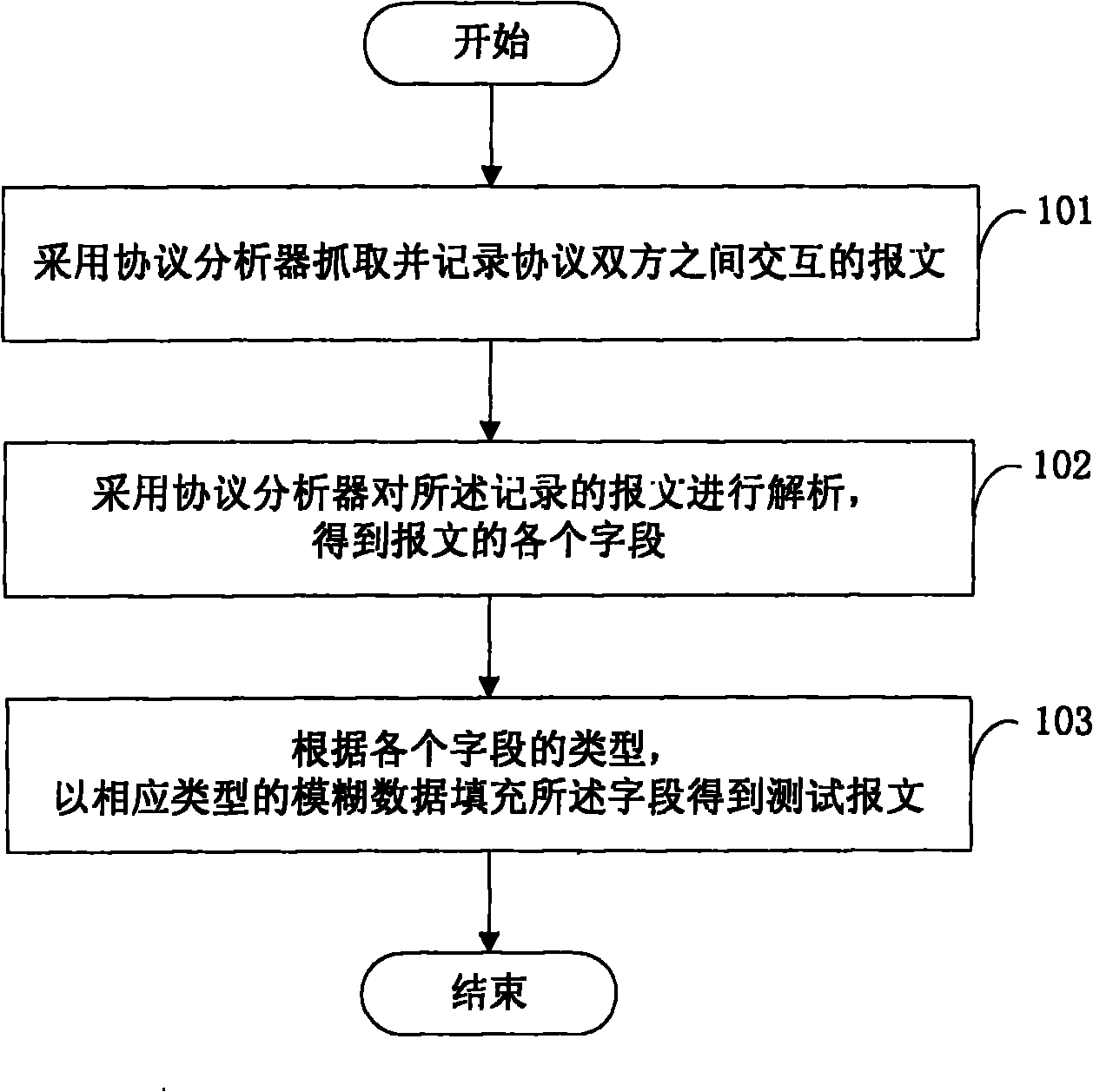
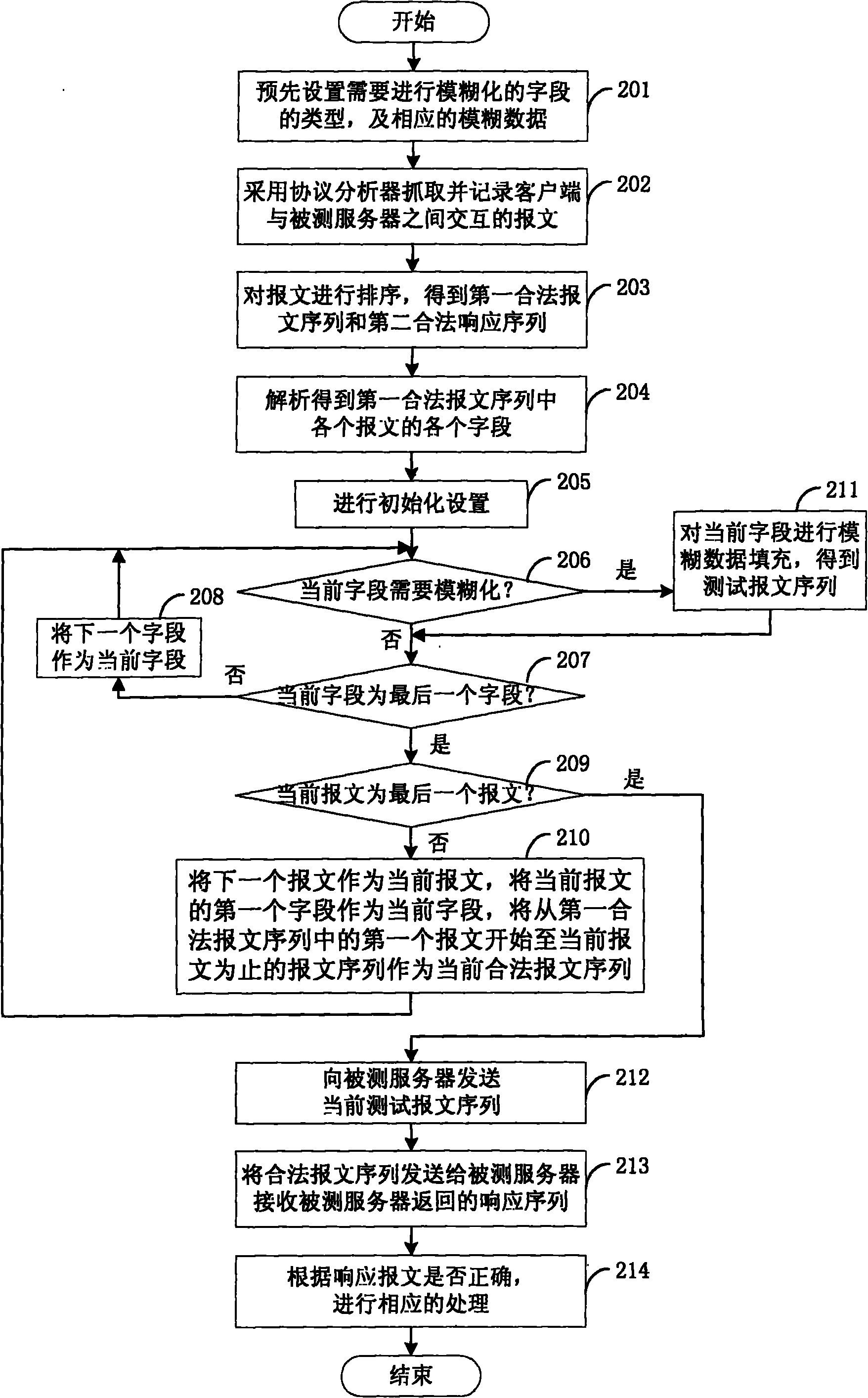
The invention discloses a method for producing a test case, which is used for performing fuzz testing on protocols and comprises the following steps: grabbing and recording interactive messages between both sides of a protocol by a protocol analyzer; analyzing the recorded messages by the protocol analyzer to obtain each field of the messages; and filling each field by fuzzy data with corresponding types to obtain test messages according to the type of each field. The invention also discloses a system for producing a test case. By the invention, a complete and effective test case can be produced in no need of understanding the relative knowledge of protocol specifications so as to completely and effectively evaluate the safety of a protocol product.
Owner:SIEMENS CHINA
Industrial control protocol vulnerability mining system based on fuzzy test
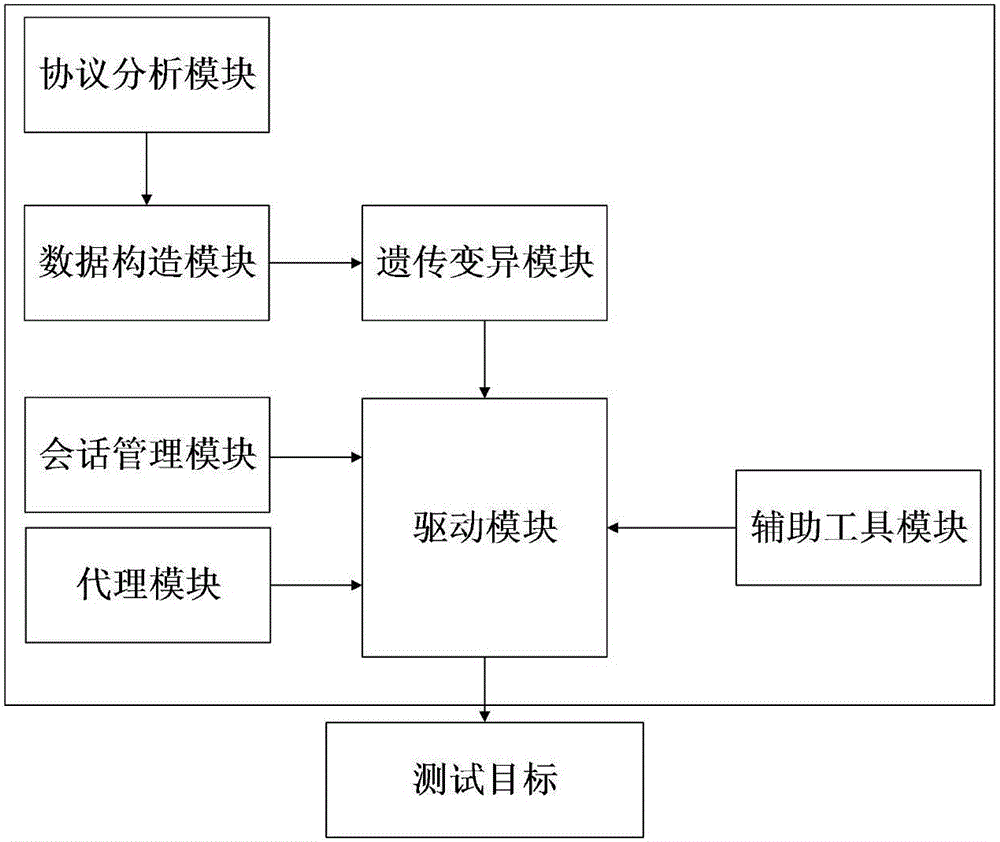
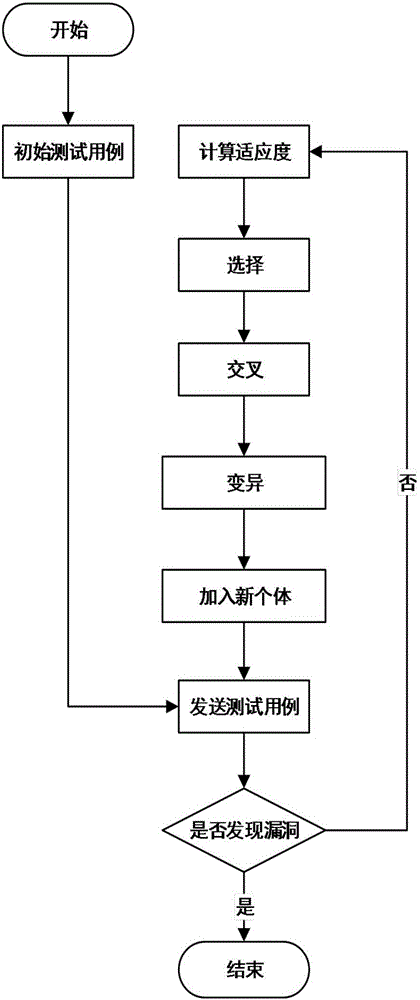
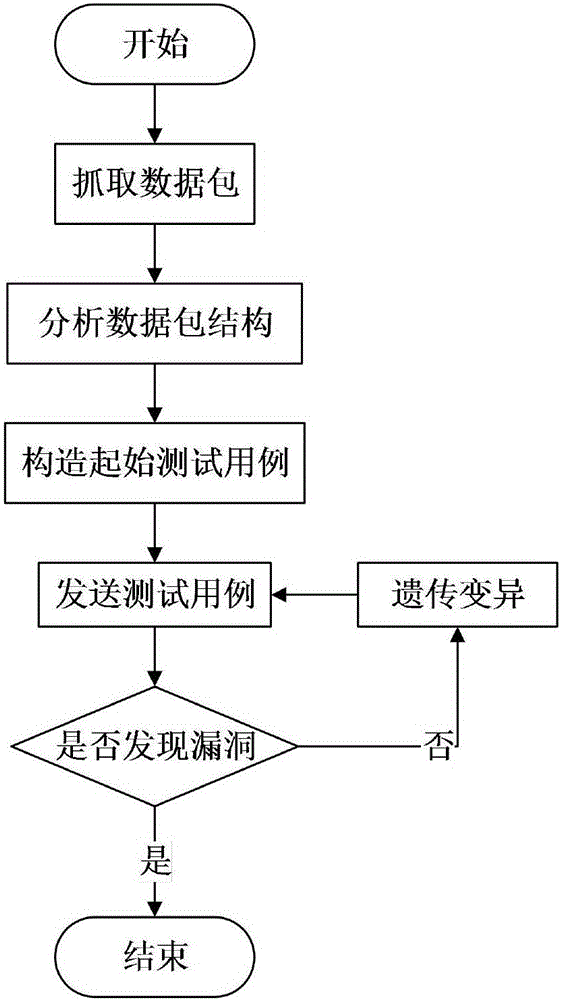
InactiveCN105721255AImprove hit rateImprove digging efficiencyData switching networksSession managementTest script
The invention discloses an industrial control protocol vulnerability mining system based on a fuzzy test. The system comprises a protocol analyzing module, a data construction module, a genetic variation module, a session management module, an agent module, a drive module and an auxiliary tool module; the genetic variation module, the session management module and the agent module are connected with the drive module; the protocol analyzing module is connected with the data construction module and then is connected with the genetic variation module; and the drive module is used for connecting a test target. According to the system, the conditions of the tested target can be learned and analyzed; related data such as test scripts and a test case are specifically constructed according to the analyzed information; the hit rate of the test case is increased through analyzing the tested target; in a test process, the generation method or variation direction of the test case is adjusted specifically according to the information such as the current state of the tested target and the feedback of the test case; the vulnerability mining efficiency is improved through an efficient adjusting algorithm; and moreover, the system adaptation is increased.
Owner:BEIJING UNIV OF TECH
Test device used for testing intrusion detection system and test method thereof
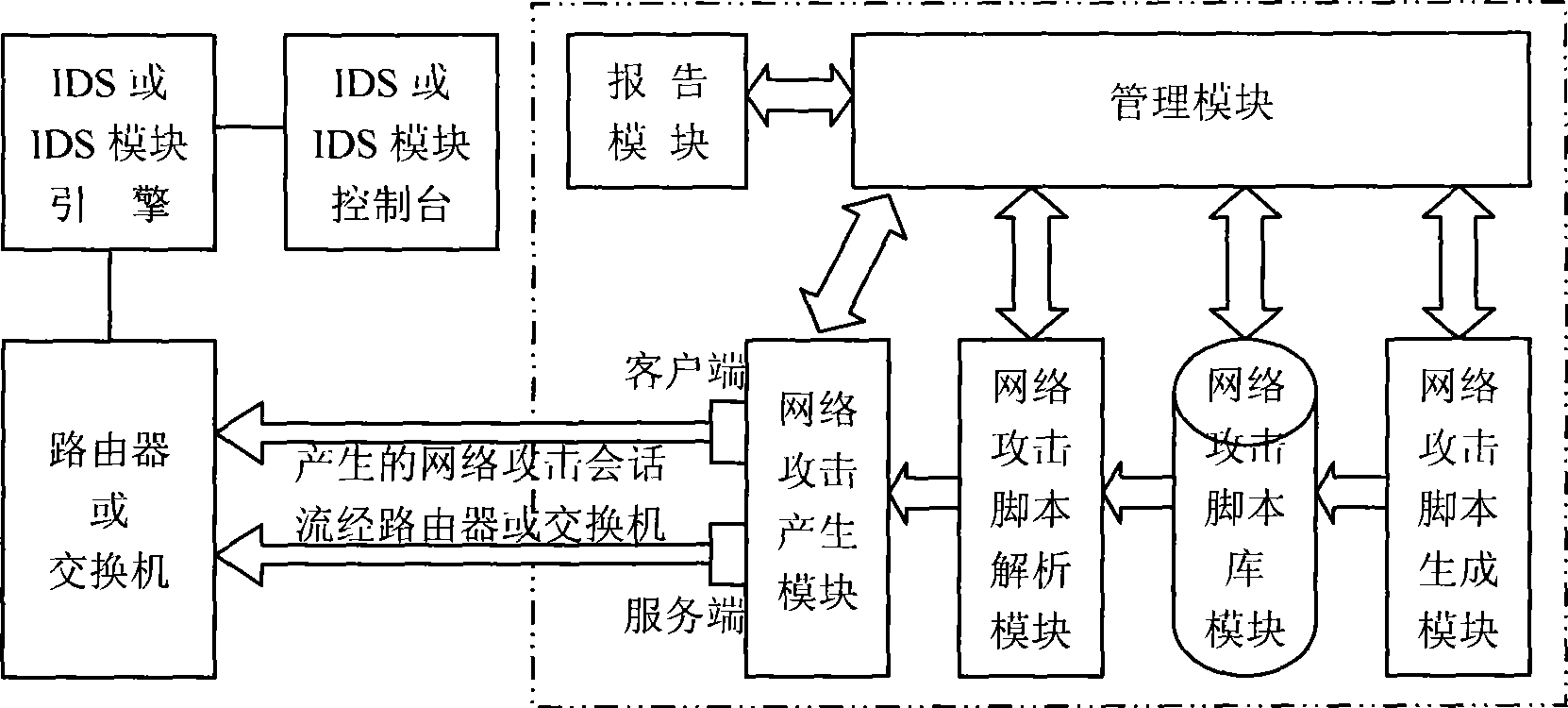
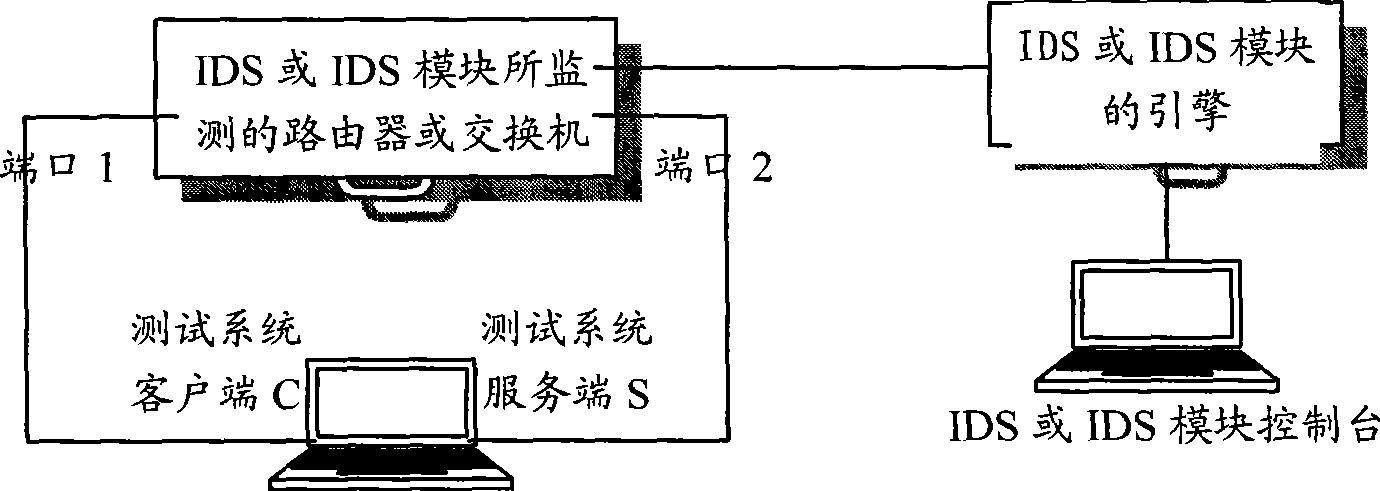
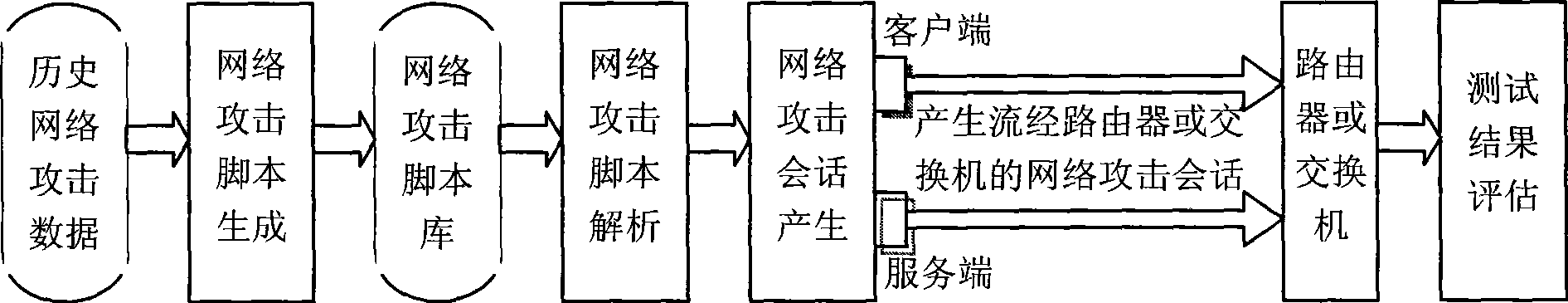
InactiveCN101447991AResolution statusAddressed issues with the IDS module testing correctlyData switching networksNetwork attackTest fixture
The invention discloses a test device used for testing an intrusion detection system and a test method thereof. The test device comprises a network attack script generating module, a network attack script library module, a network attack script analyzing module, a network attack generating module and a reporting module. The test method comprises the steps as follows: (a) a network attack script is generated and is stored in a network attack script library; (b) an appointed script is selected from the network attack script library and is analyzed for getting a key parameter field of the network attack to prepare for regenerating an attack session; (c) related parameter obtained from step (b) is reconfigured, and a network attach session is established; and (d) a test report is generated according to the warning condition of an IDS or IDS module towards the network attack. The invention can realize the test towards the IDS or IDS module and in particular the test towards the IDS or IDS module which adopts a state protocol analyzing technology and can improve the efficiency and the accuracy of the test.
Owner:中国人民解放军信息安全测评认证中心
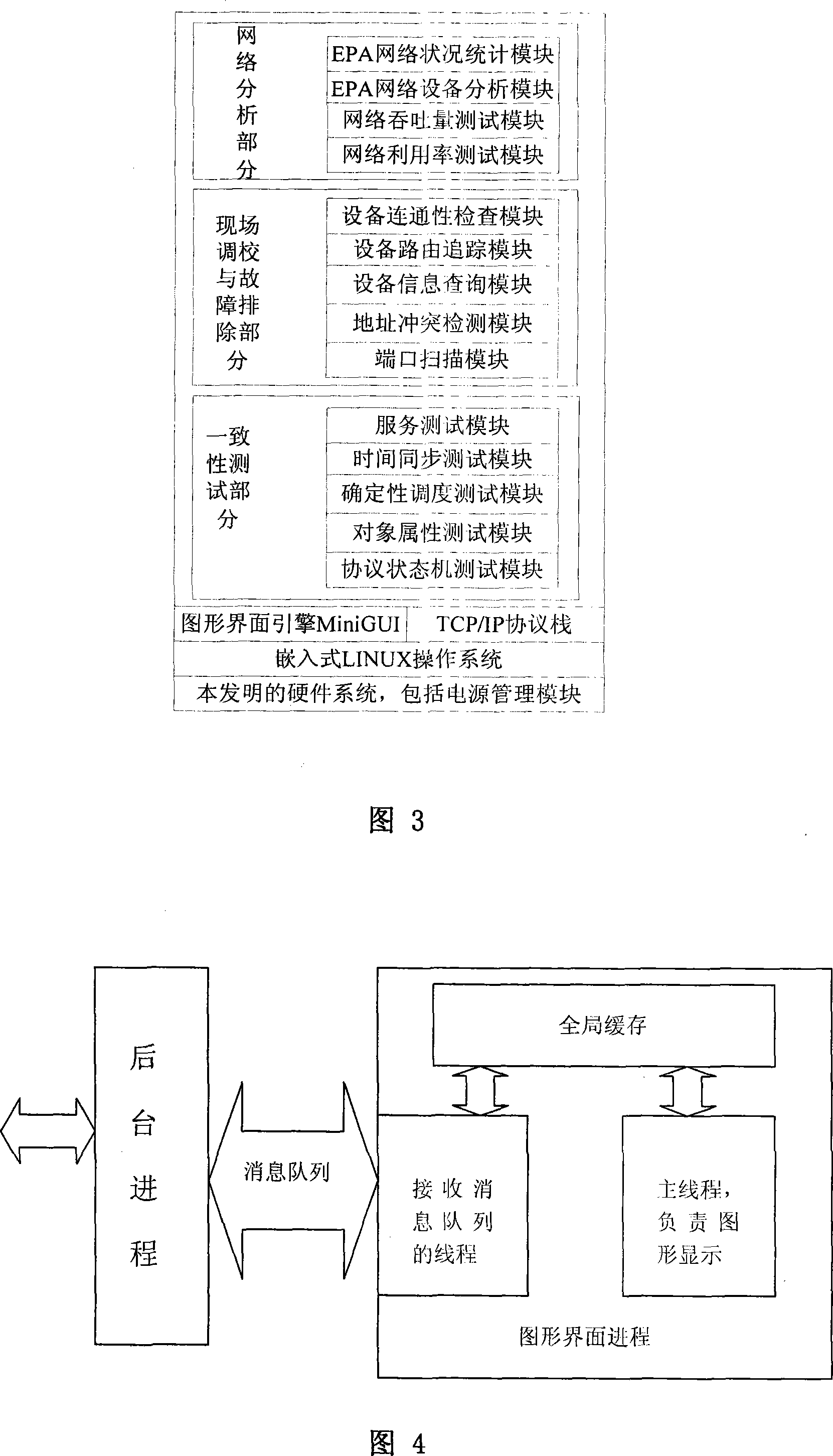
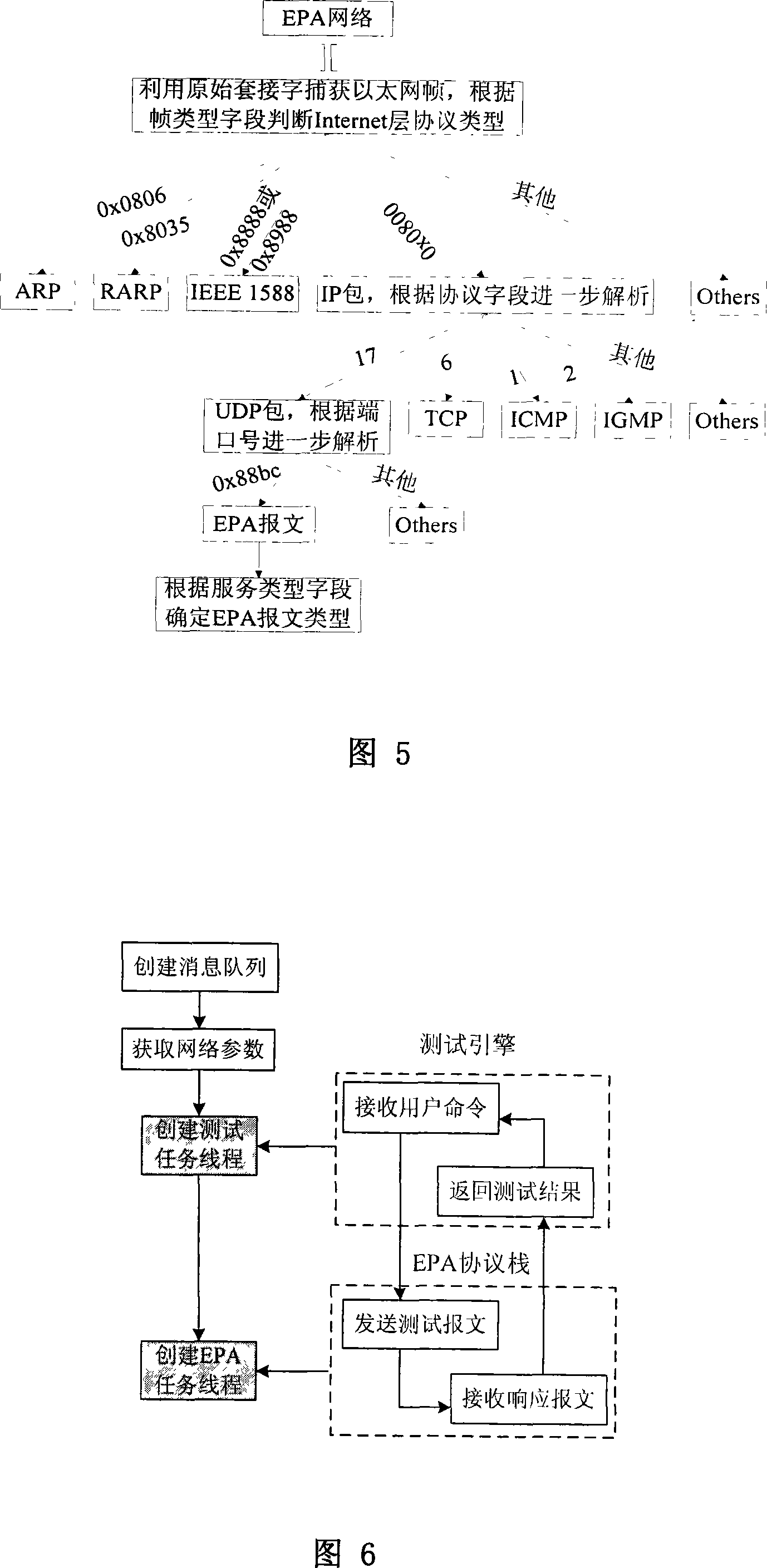
Industrial Ethernet protocol analysisand field tester
InactiveCN101072147AImprove continuous working abilityData switching by path configurationIndustrial EthernetManagement information base
Aiming at disadvantages of current on site testing instrument for industrial control network, the invention designs portable instrument of analyzing and on site testing industrial Ethernet protocol (IEP). The designed instrument possesses features: monitoring state of EPA network in real time; carrying out performance analysis based on message of equipment declaration on network; detecting whether network connection and equipment are connected to network correctly; determining route of target equipment (TE), querying information of TE, detecting port state of TE; testing whether the tested object realizes service declared by the object according to EPA standard; testing time Synch precision between tested equipment and main clock; based on EPA standard to carry out deterministic scheduling analysis for message captured from network; carrying out attribute test for objects in management information database etc. The invention can widely be applicable to analyze and on site testing IEP.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
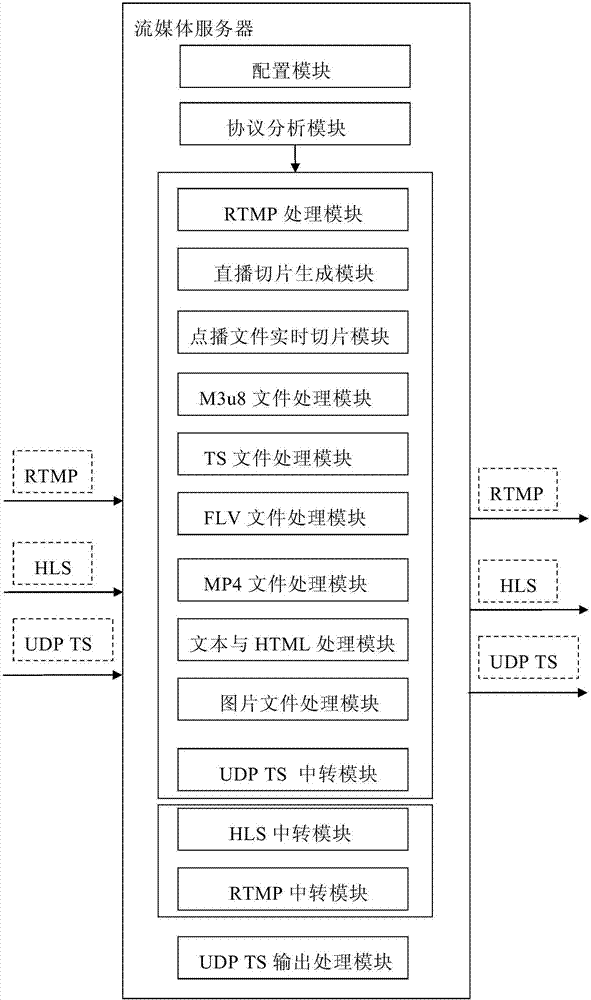
Streaming media server system supporting multi-protocol input and output
ActiveCN107222484AImprove experienceImplement adaptive playbackTransmissionMulti protocolMedia server
The invention discloses a streaming media server system supporting multi-protocol input and output. The streaming media server system comprises a protocol analysis module and a data stream analysis processing module; an access rule of a request message sent by a client is defined, the request message comprises the protocol type, the application type, the publishing point and the file name of a request, the application types comprise live broadcast and on-demand broadcast, and for a on-demand broadcast application, the request message further comprises a physical path corresponding to a request file; the data stream analysis processing module comprises an RTMP processing module, a live broadcast fragment generation module, a on-demand broadcast file real-time fragmentation module, an M3u8 file processing module, a TS file processing module, an FLV file processing module and an MP4 file processing module; the protocol analysis module is used for conducting analysis processing on the received request message according to the access rule and sending the request message to the corresponding data stream analysis processing module to be subjected to corresponding process according to an analysis result. The streaming media server system supports streaming media data broadcast of multiple terminals.
Owner:北京经纬中天信息技术有限公司
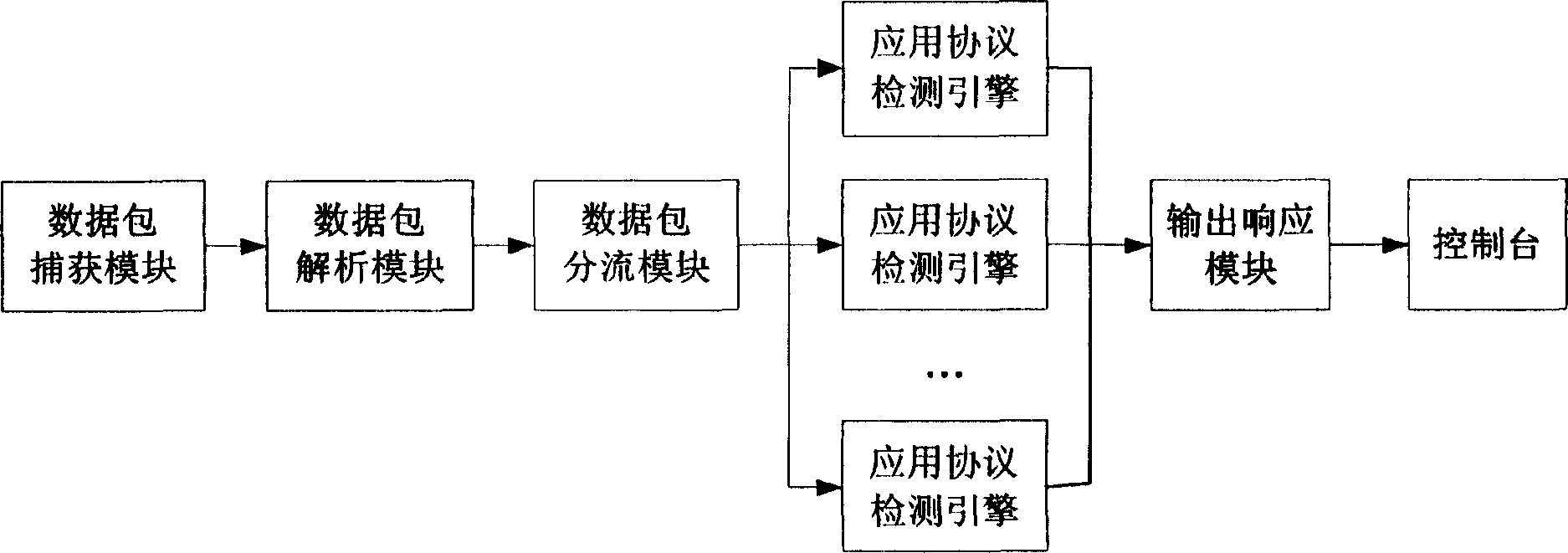
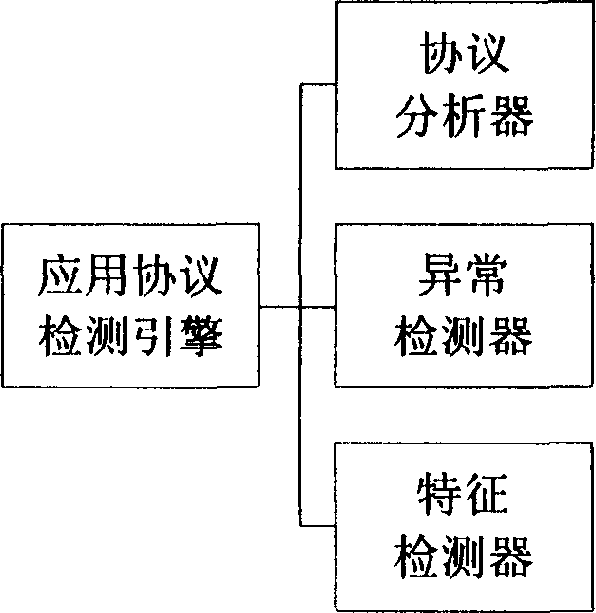
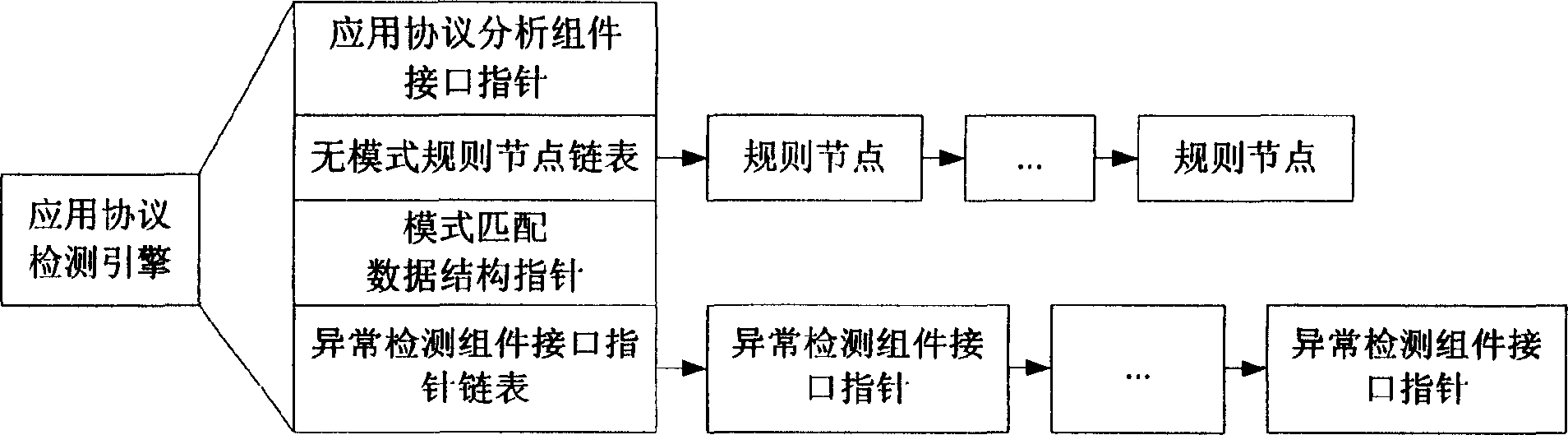
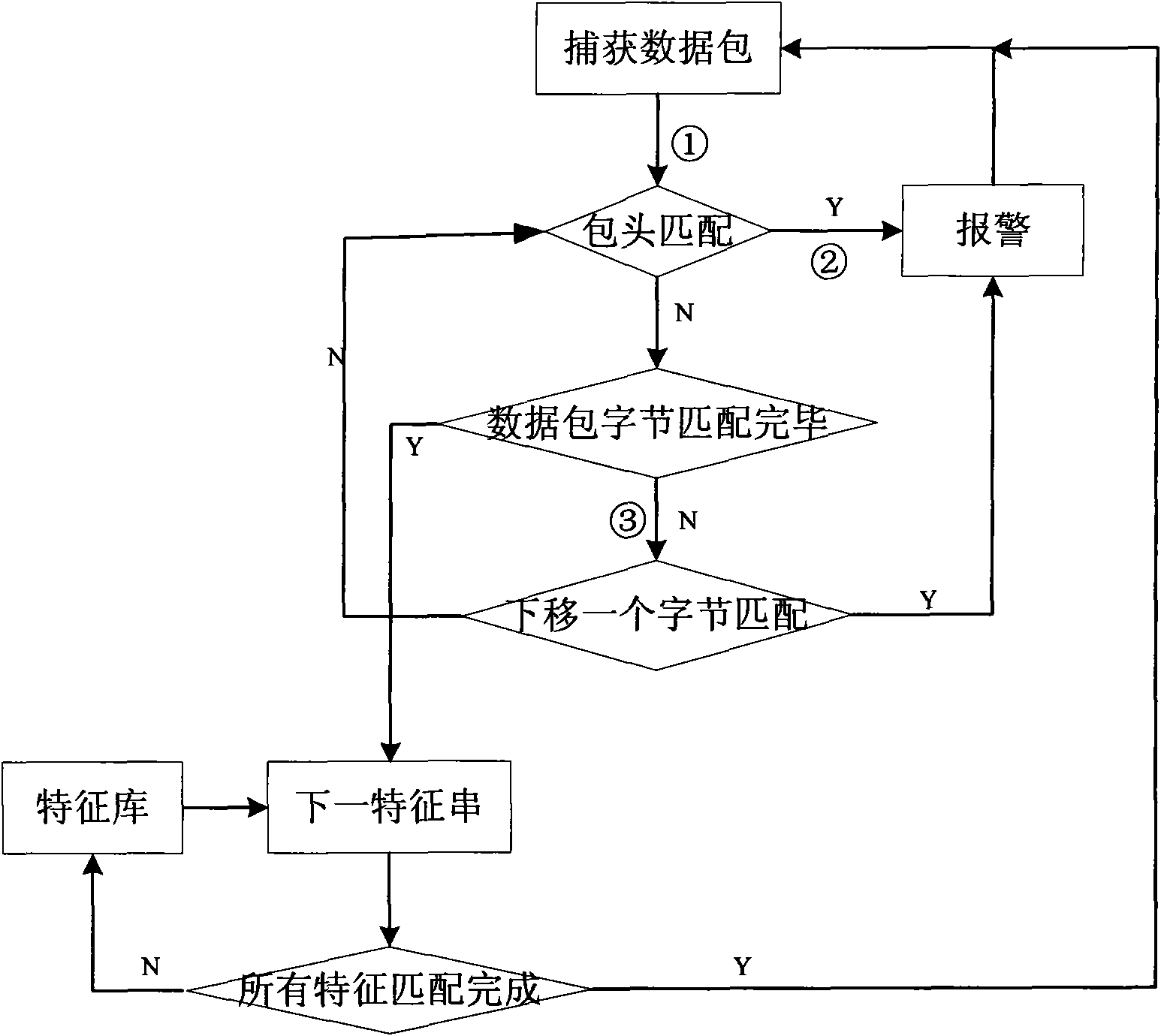
Network intrusion detection system and method based on application protocol detection engine
InactiveCN1738257AMake up for the defect of not being able to detect new attack methodsGuaranteed scalabilityData switching networksComponent Object ModelAnomaly detection
The invention provides a network invasion detecting system based on the application protocol detecting engine and its method. The application protocol detecting engine comprises three detector units as a application protocol analyzer, a abnormal detector and a feature detector while these detectors can all or partly use simply components object models and supply uniform calling interface. The character of said network invasion detecting method is that the invention comprises three steps as protocol analysis, abnormal detecting and feature detecting. The invention can solve the defect of present network invasion detecting system that the inability for detecting new invasion type; and the invention realizes components of the application protocol analyzer, the abnormal detector and the feature detector by the components technique, which allows the detecting component after decoding can connect the detecting system directly without decoding again, so the spreading and the maintenance of network invasion detecting system are improved.
Owner:PEKING UNIV
Network intrusion detection system and method based on data mining
InactiveCN101789931AEasy to spot coordinated attacksProtect against distributed attacksData switching networksTime responseNetwork packet
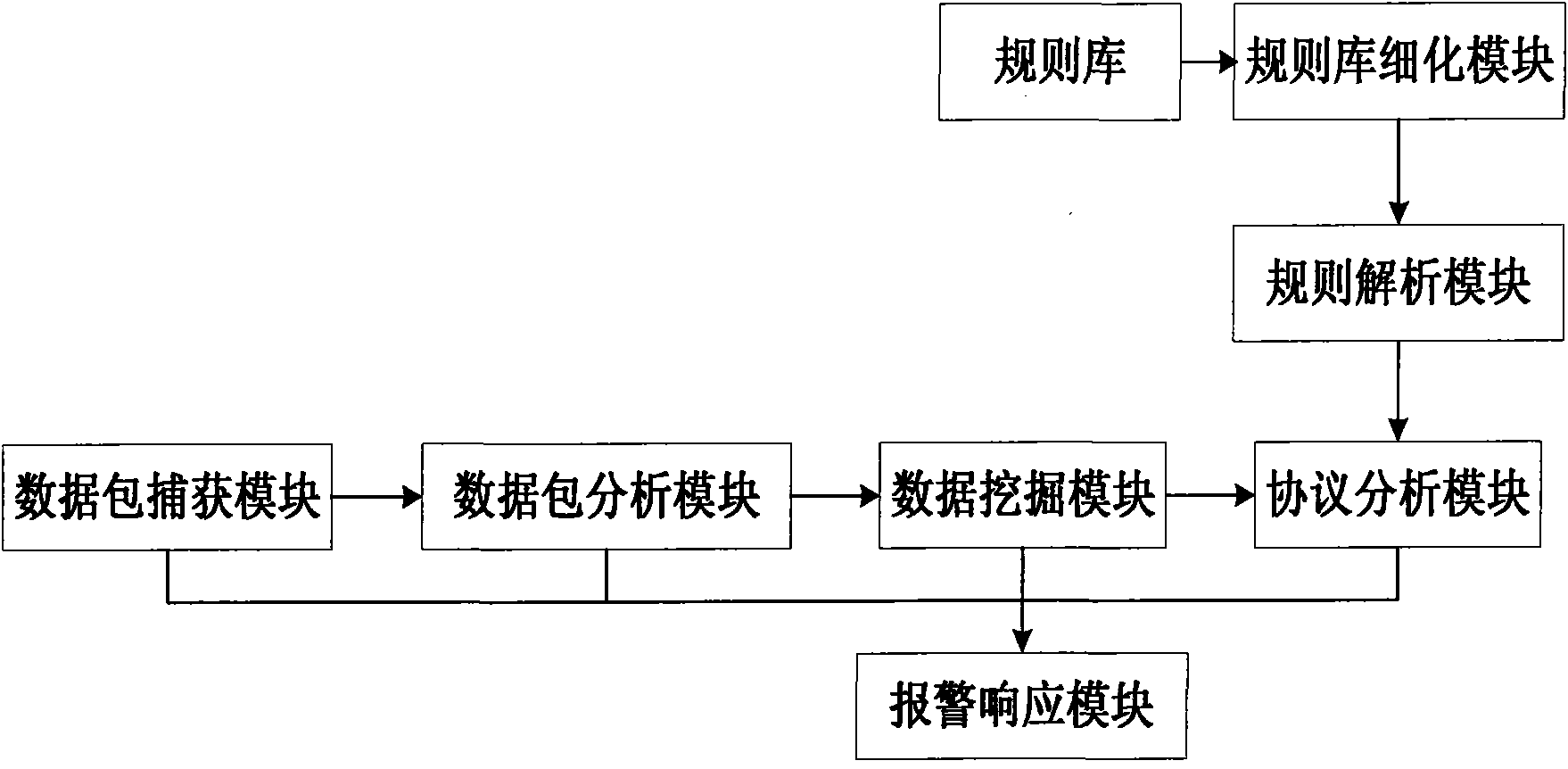
The invention relates to a network intrusion detection system and a method based on data mining. The system comprises a data packet capturing module, a data packet analyzing module, a fragment recombination module, a data mining module, a protocol analyzing module, an alarm responding module and a rule analyzing module. The invention effectively combines data mining technology and protocol analyzing technology, thereby improving the accuracy and the reliability of detection; and simultaneously, the data mining technology is used for processing mass data, thereby realizing real-time response.
Owner:JINAN UNIVERSITY
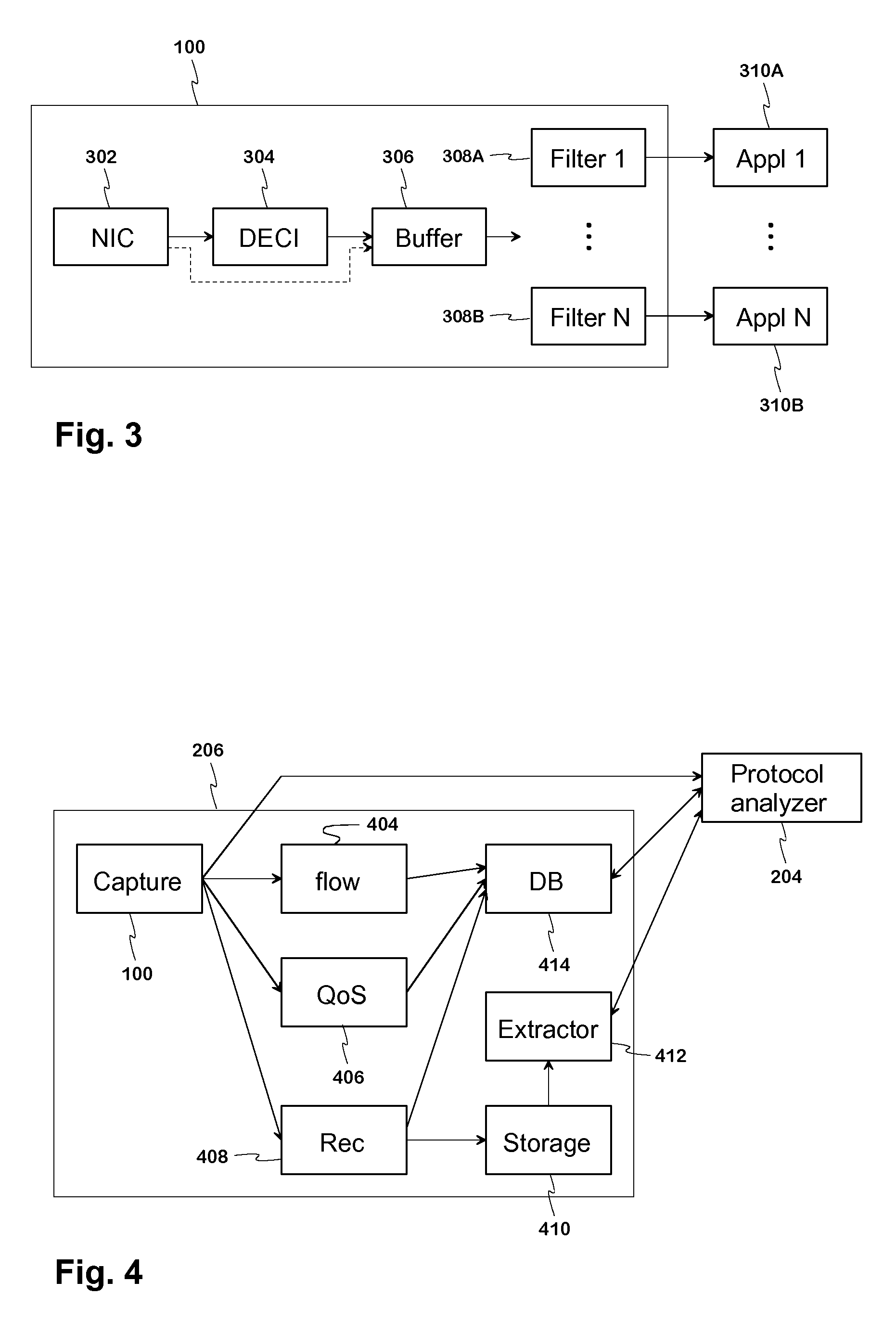
Real-time network data analysing system
InactiveUS20100211675A1High trafficDigital data processing detailsMultiple digital computer combinationsTraffic capacityReal-time web
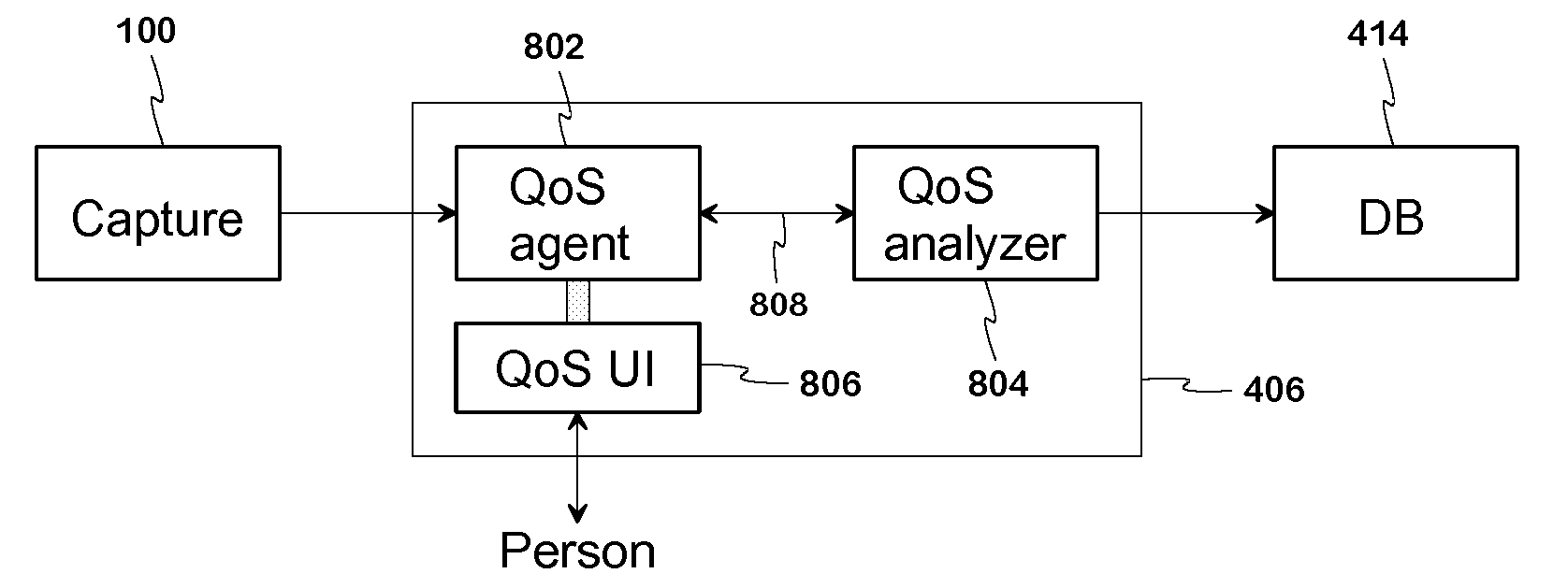
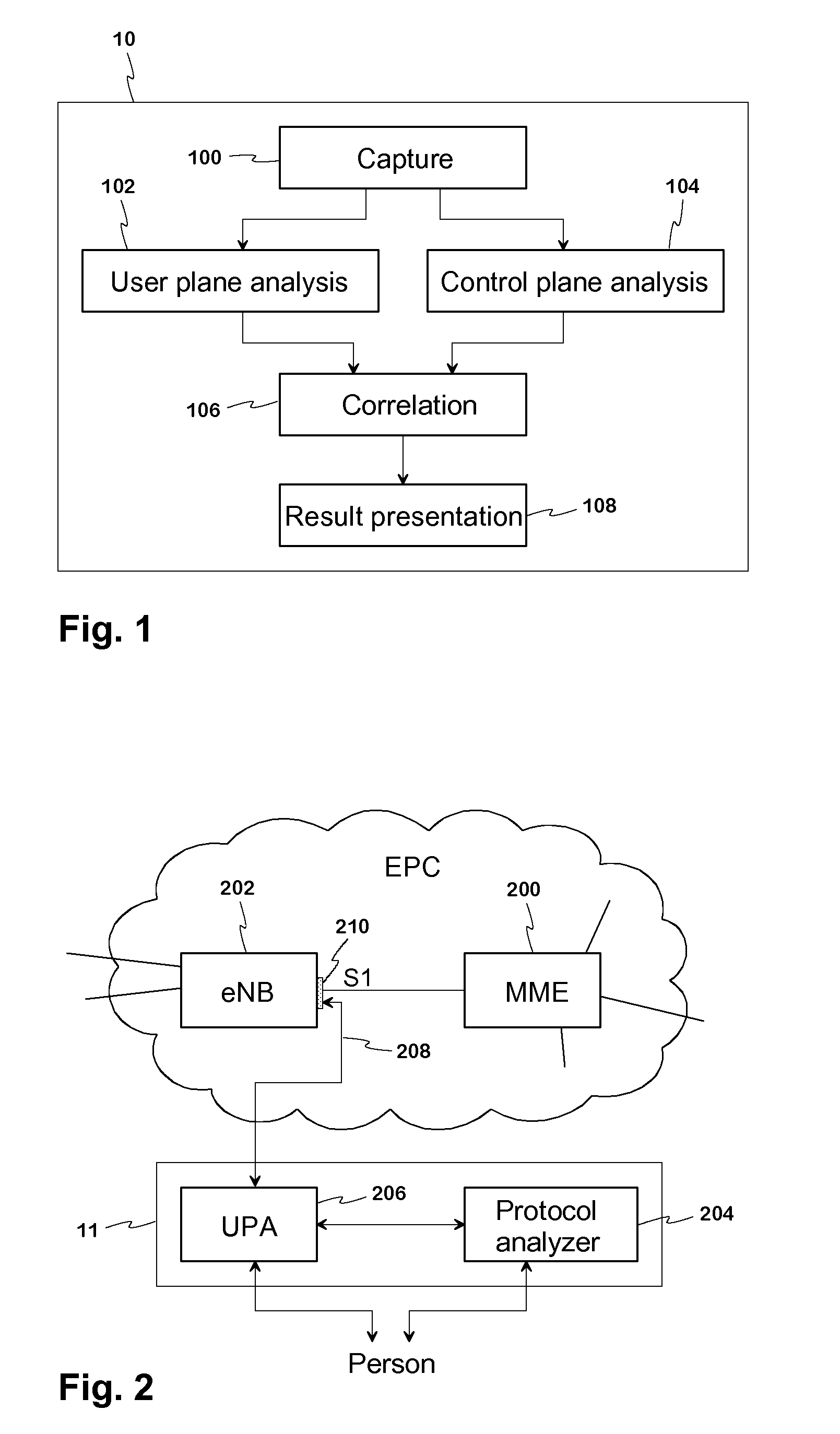
An arrangement and method for analysing the data transferred in communications networks. The fact that though the amount of user plane traffic and data is increasing fast, the amount of signalling traffic is hardly increasing at all, is utilised. In the present system the analysis of the user plane and the control plane is done separately in user plane analysis appliance (206) and protocol analyser (204). The separate analysis results are then combined by certain criteria and the combined data is shown. An at least nearly real-time network data analysis is possible also in the networks with high speed traffic.
Owner:NETHAWK
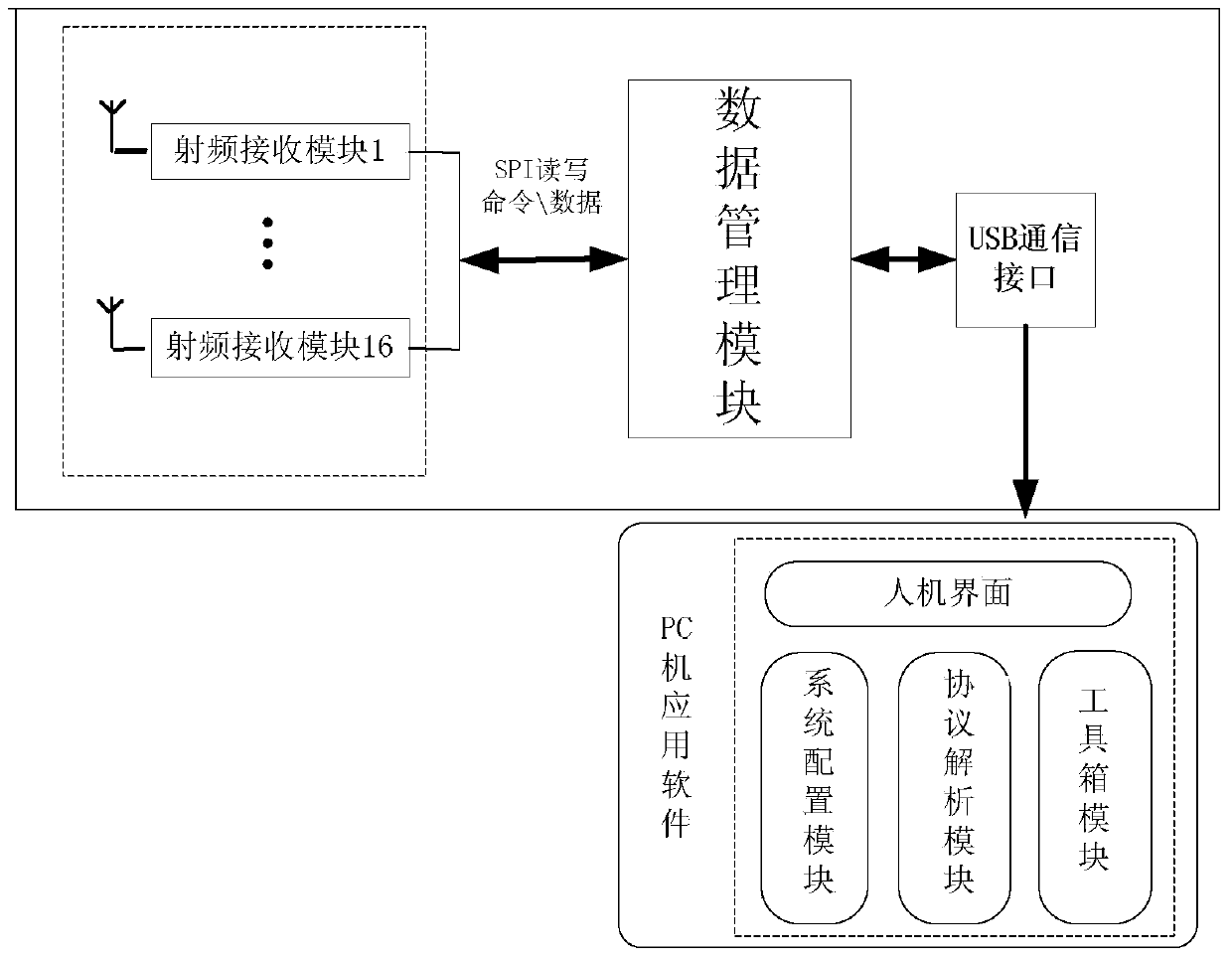
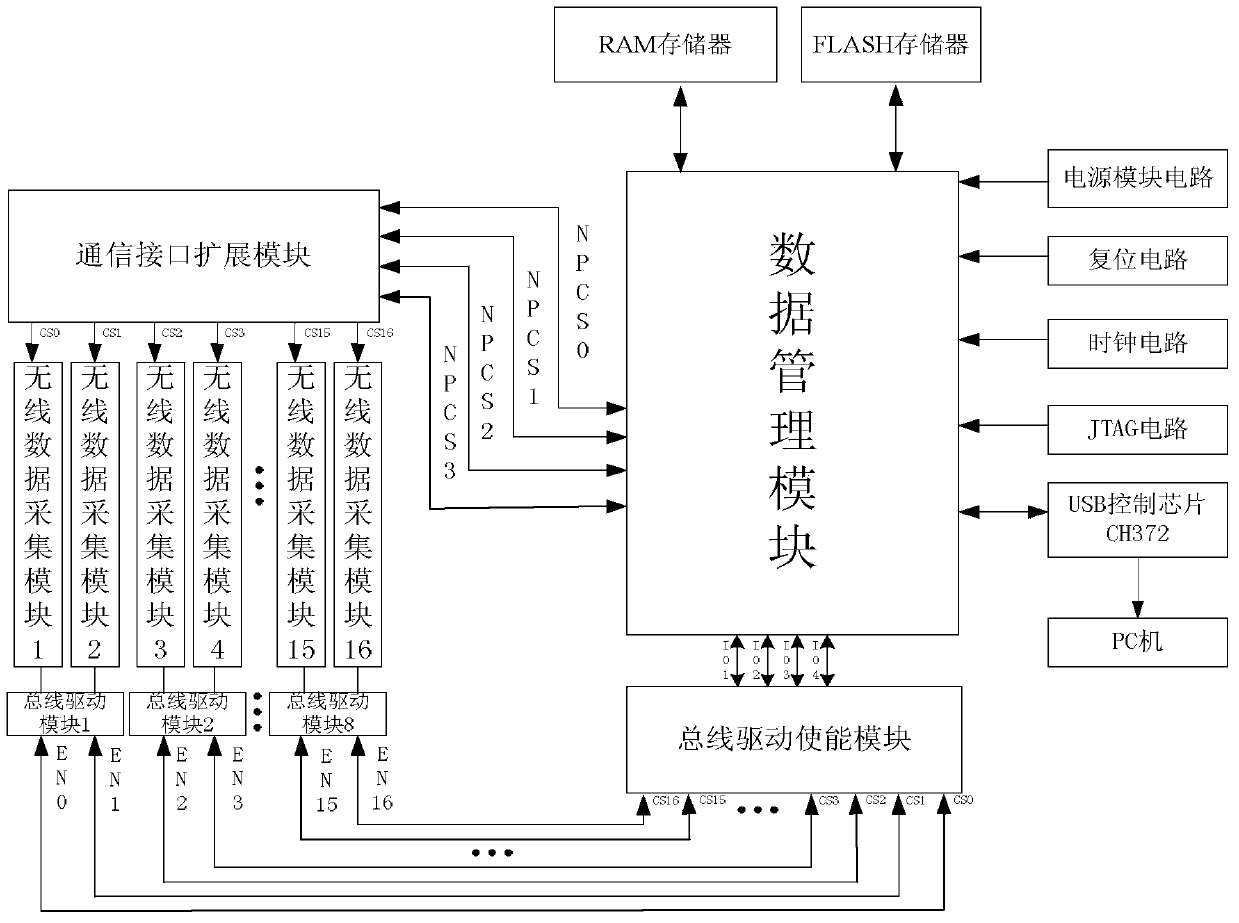
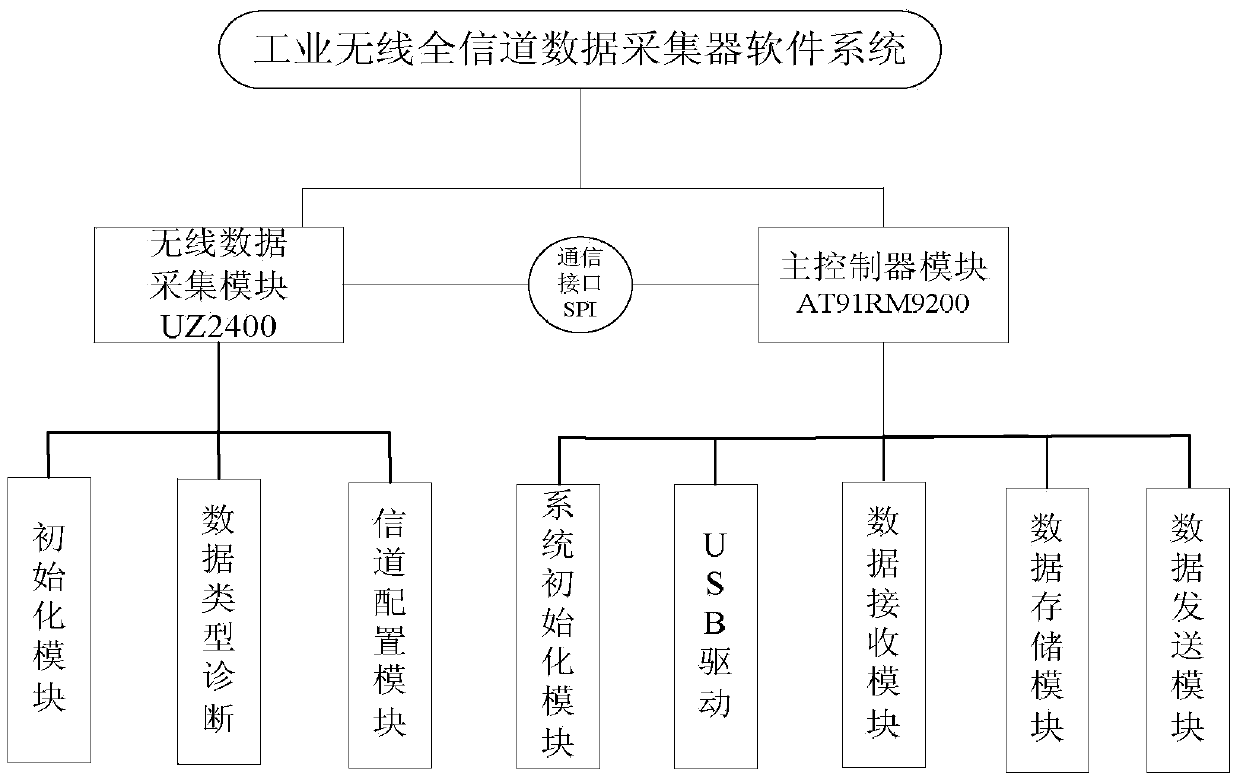
Two point four gigahertz full-channel data collection and protocol analysis instrument based on IEEE802.15.4
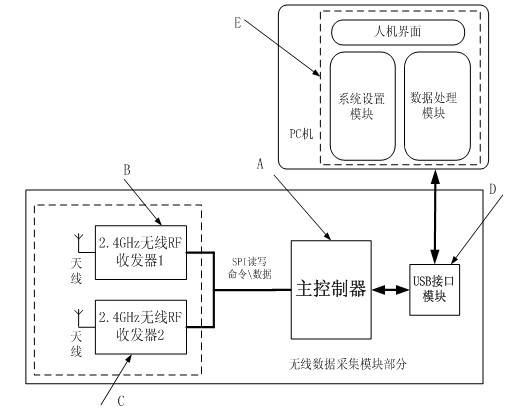
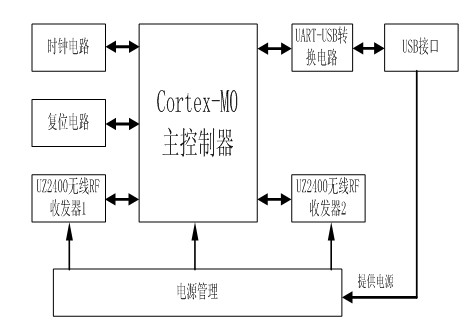
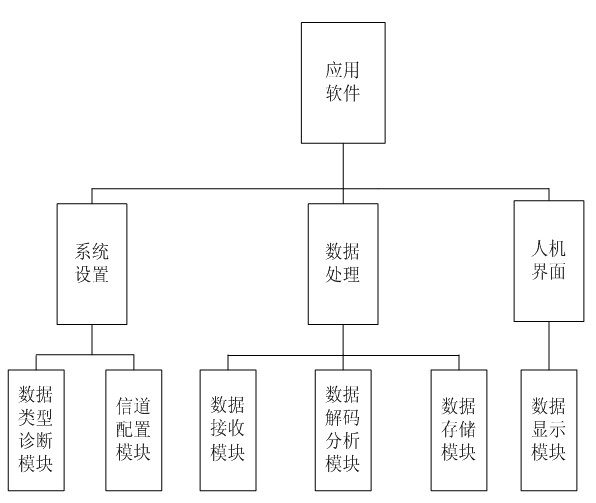
ActiveCN103781088AImprove anti-interference abilityRealize detailed analysisNetwork topologiesWireless network protocolsLine sensorWireless data
The invention provides a two point four gigahertz full-channel data collection and protocol analysis instrument based on the IEEE802.15.4, and relates to the technical field of wireless sensor networks. The system comprises 16 radio frequency receiving modules. Each radio frequency receiving module is in charge of unceasingly monitoring whether a wireless data message exists in a channel of the network in the 2.4 GHz ISM band or not. A data management module reads an interrupt mark in a wireless module through polling, reads the data message from the FIFO of the corresponding radio frequency receiving module, detects whether the data message confirms to the standard format of the wireless data message or not and processes the data message. The data message enters a corresponding analysis module according to a selected protocol, data packet information is analyzed field by field, the analyzed information is stored in a database to form a new data message, and the new data message is uploaded to an upper computer by calling an application program. The system further has the channel scanning function, and quality index numbers of all current channels can be obtained in real time.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Method and device for inspecting deep packets among heterogeneous platforms
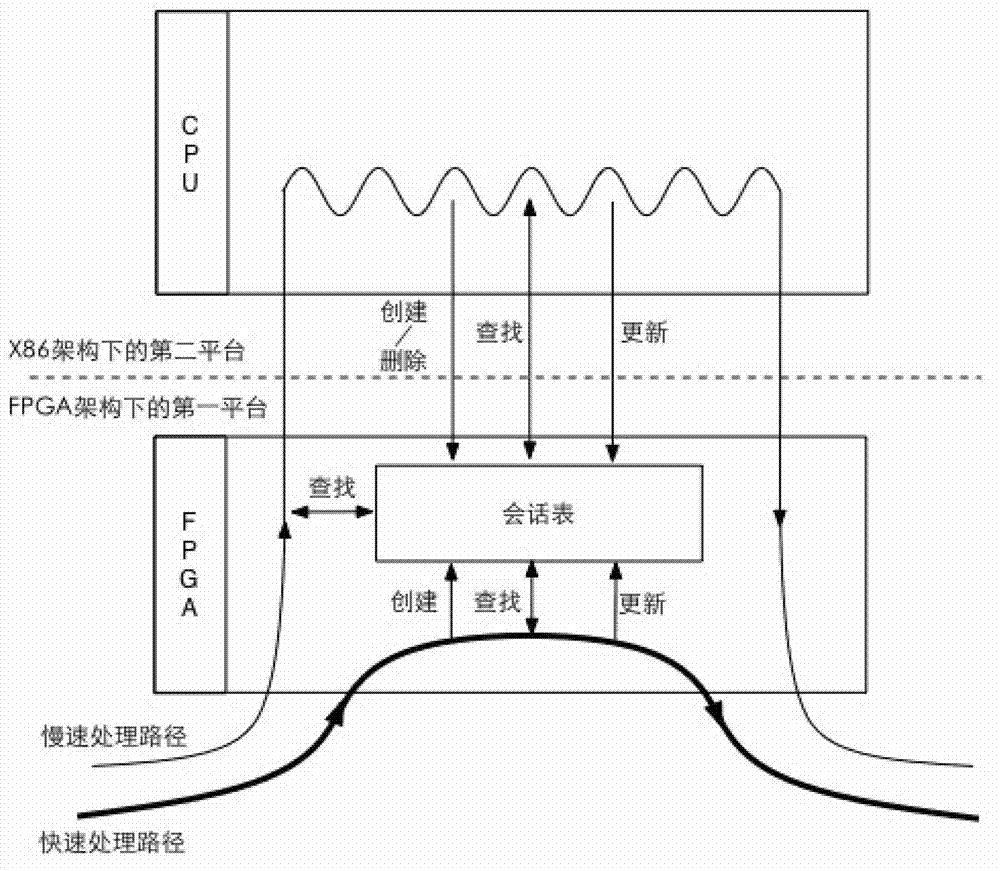
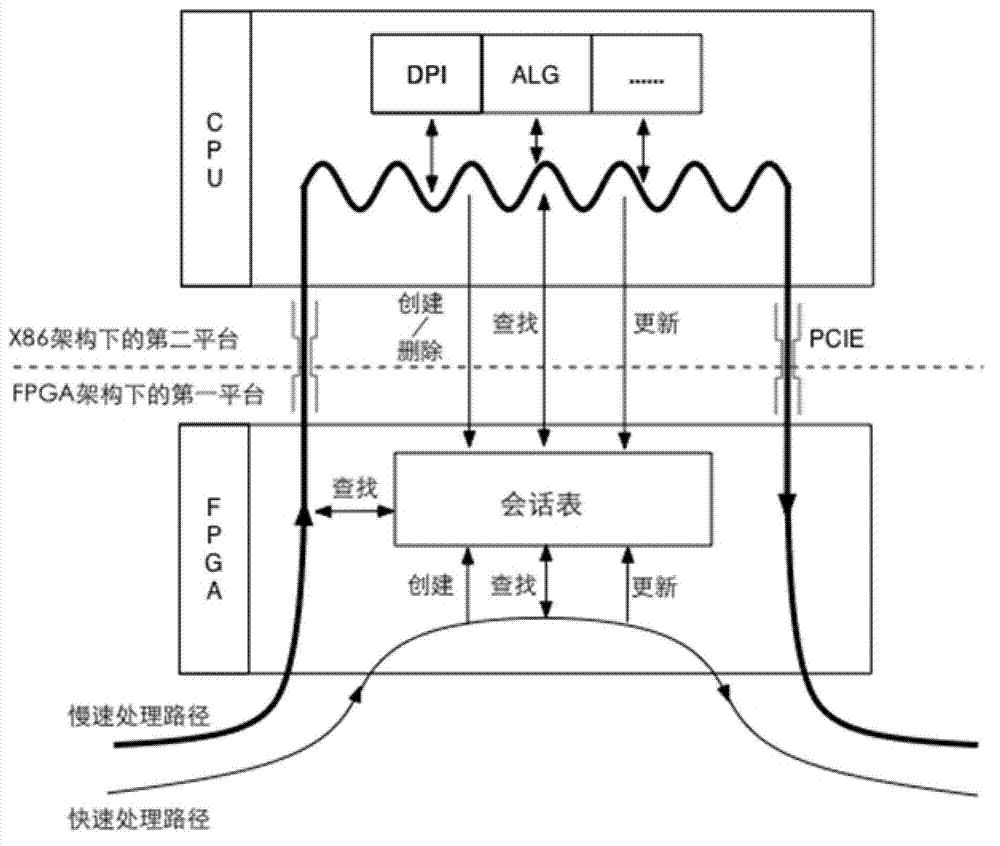
ActiveCN102932203ALighten the computational burdenReduce packet trafficData switching networksField-programmable gate arrayDeep packet inspection
The invention provides a method for inspecting deep packets among heterogeneous platforms. The method comprises the following steps of: when the condition that corresponding session entries of a received packet contain instruction information required for being subjected to deep packet inspection is judged on a first platform in an FPGA (Field Programmable Gate Array) architecture, carrying out protocol analysis on the packet on the first platform so as to determine a bearer protocol; determining whether the multimode matching is required for being carried out or not based on a predefined bearer protocol-multimode match mapping table; when the multimode matching is required for being carried out, carrying out multimode matching on a payload part of the packet on the first platform based on a predefined application-related multimode characteristic set; and after multimode matching hit, transmitting the packet and a multimode matching result to a second platform, and carrying out deep packet inspection on the packet on the second platform based on the multimode matching result. With the adoption of the method, the packet traffic uploaded to the second platform for processing and the calculating burden of the second platform can be reduced.
Owner:NEUSOFT CORP
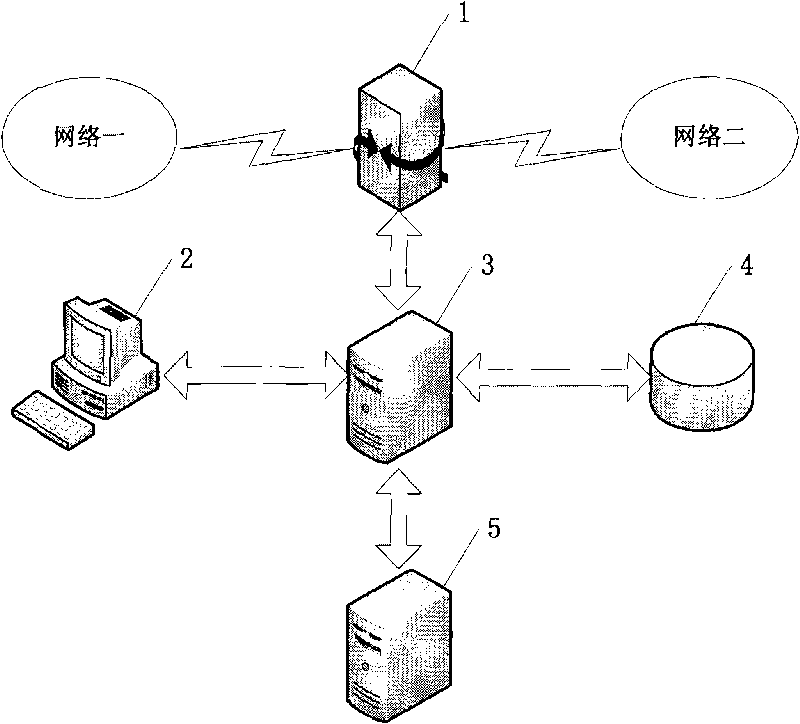
Multi-protocol information resolving system based on network packet
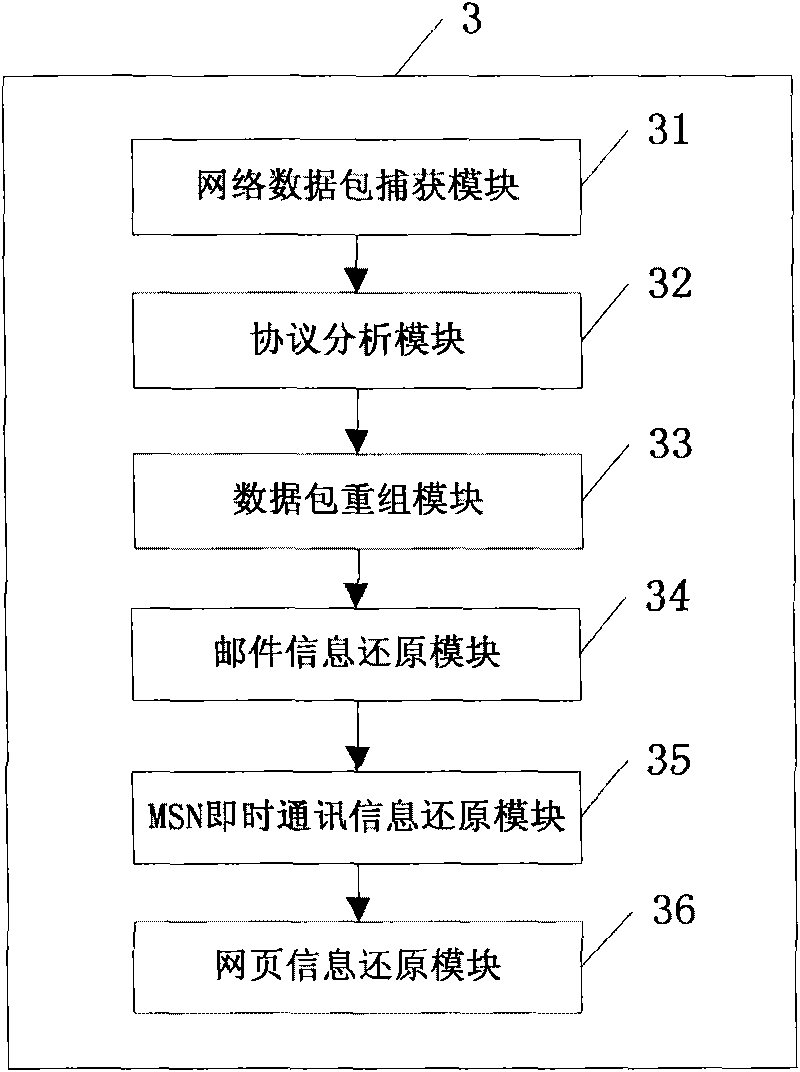
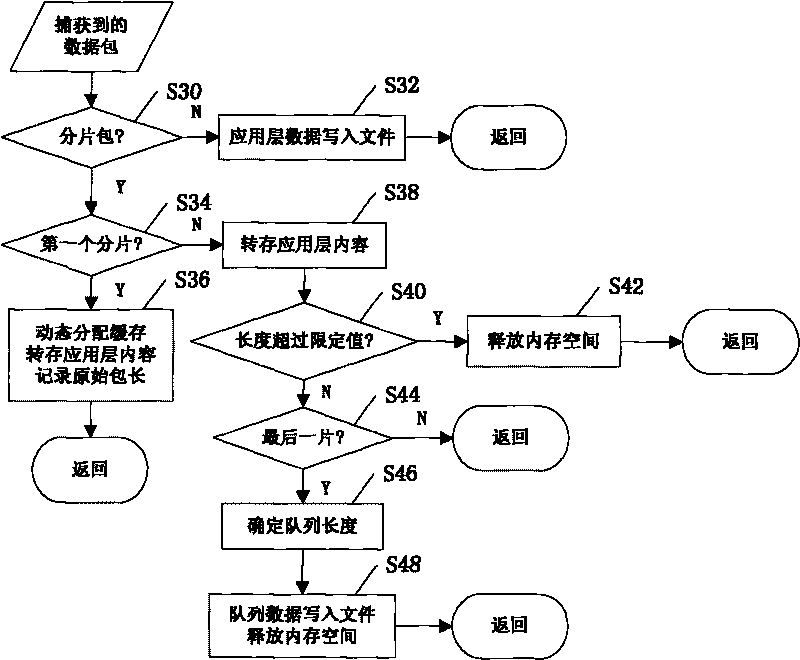
The invention discloses a multi-protocol information resolving system based on a network packet, comprising gateway equipment 1, a client computer 2, a server 3, a database 4 and an information security server 5, wherein the server 3 is respectively connected with the gateway equipment 1, the client computer 2, the database 4 and the information security server 5; the difference is that the server 3 is provided with a network packet capturing module 31, a protocol analysis module 32, a packet recombination module 33, a mail information reduction module 34, an MSN instant messaging information reduction module 35 and a webpage information reduction module 36. The method reduces to obtain all content of the E-mail, MSN instant communication and HTTP requested key information by the protocol analysis, packet recombination and application layer resolution to the original packet, and two filtering modes of pre-filtering and back filtering are adopted to accurately judge and analyze content filtering.
Owner:SHANGHAI UNIV
Method for realizing peer-to-peer network caching system based on Ares protocol
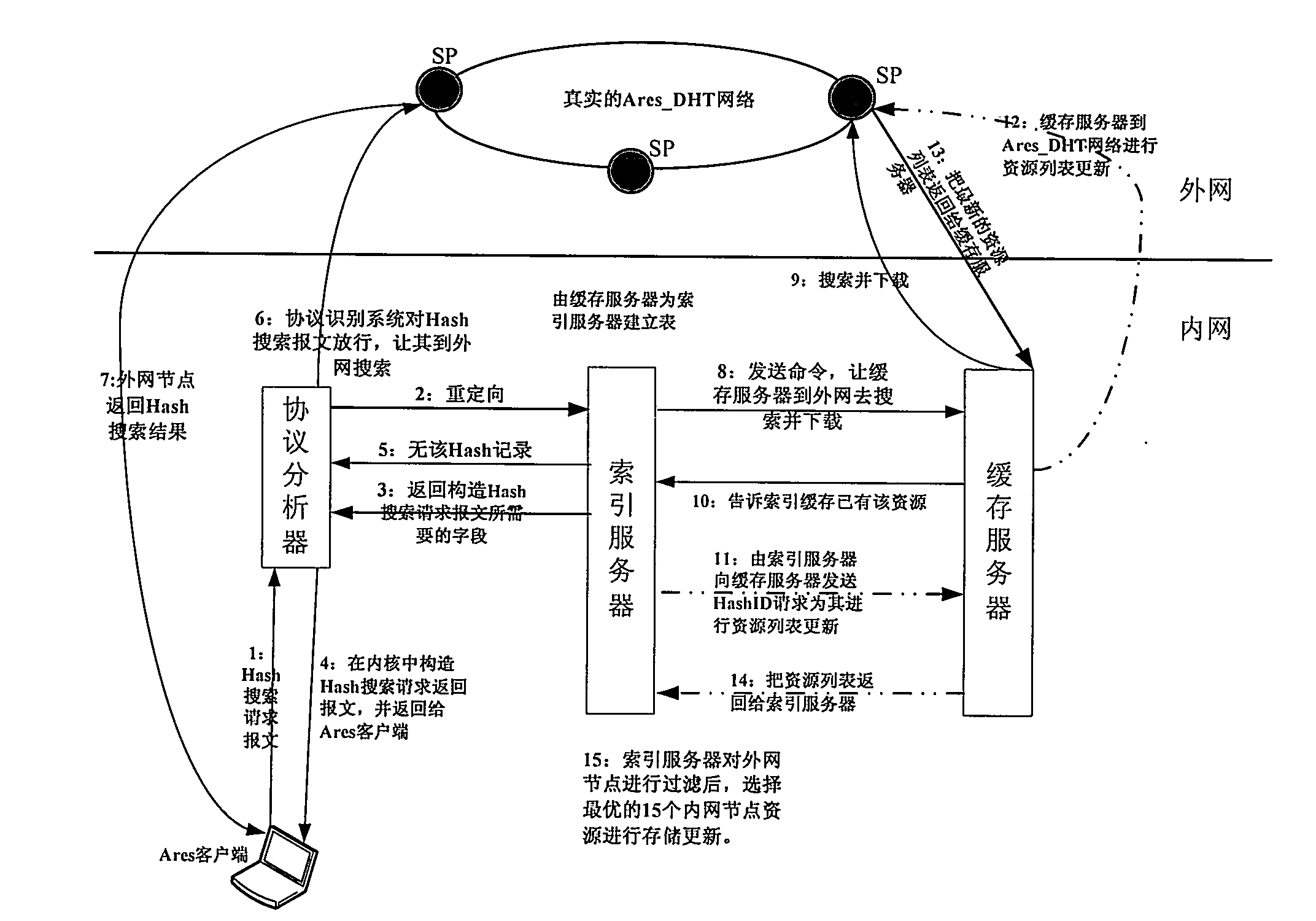
InactiveCN102130838AImprove performanceReduce load pressureData switching networksCache serverIndexing Service
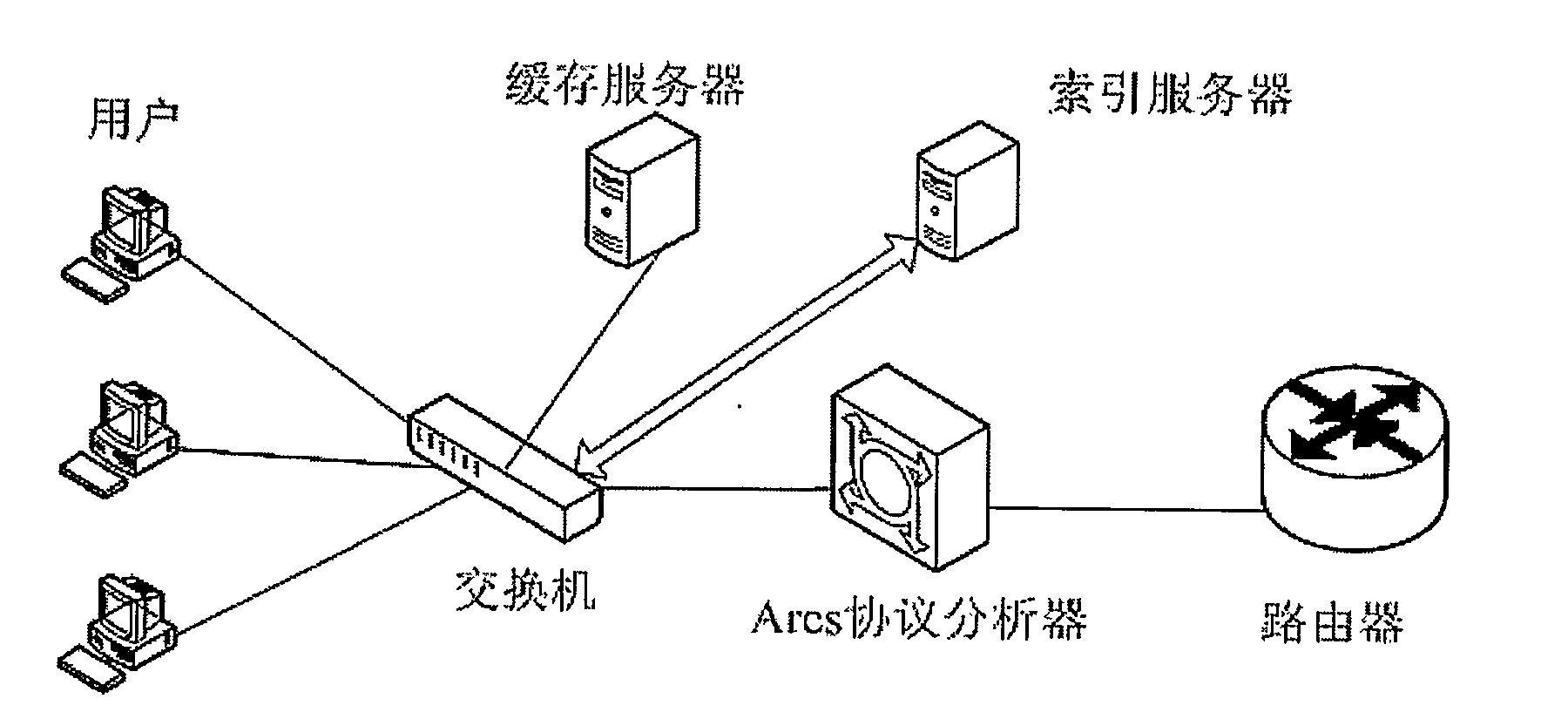
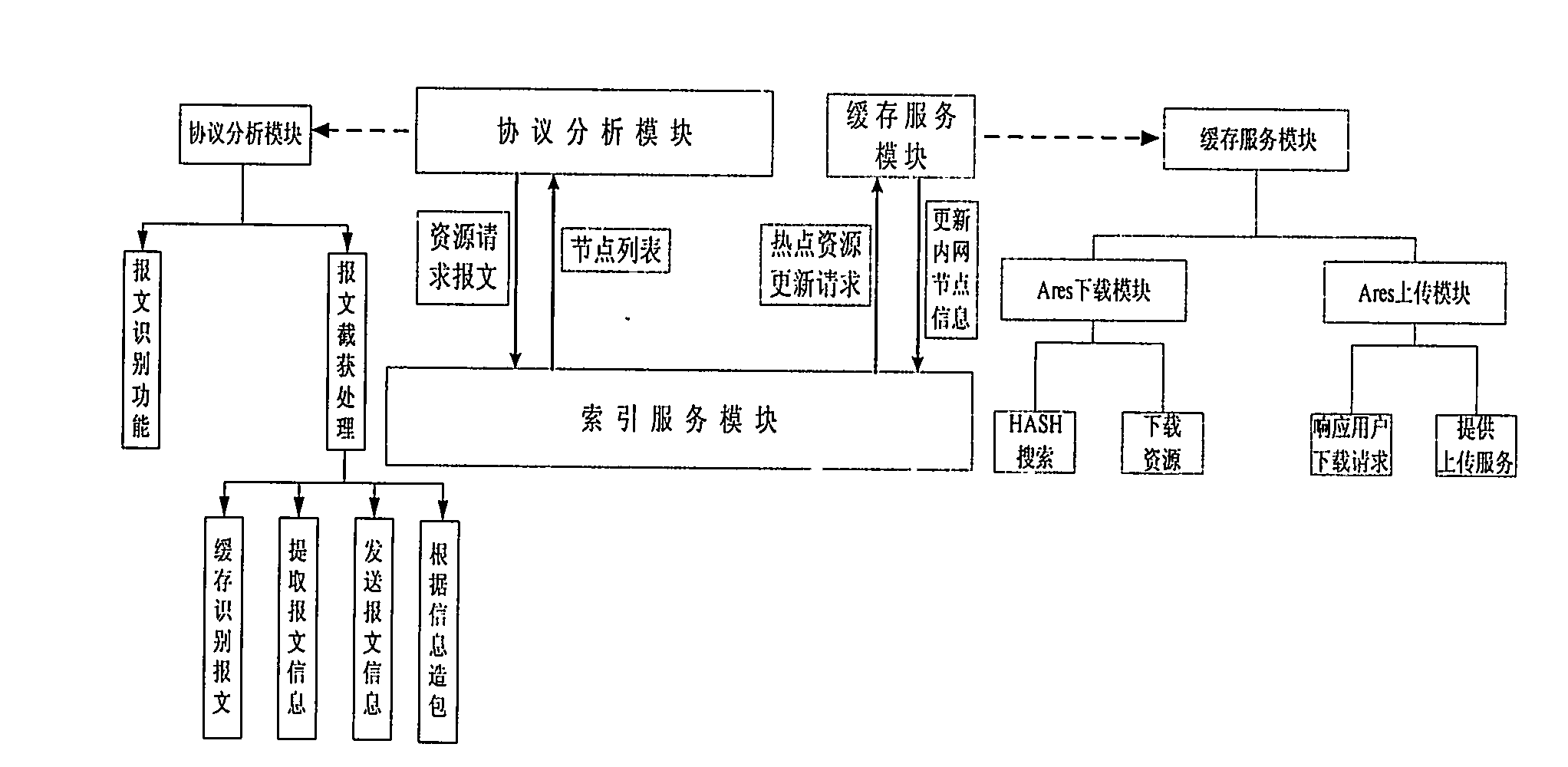
The invention discloses a peer-to-peer network caching system based on an Ares protocol and a method for realizing the system. The system comprises a protocol analyzer, an index server and a caching server, wherein the protocol analyzer is used for recognizing a Hash search request message according to a deep data packet detection technology, analyzing the message, extracting a source address, downloading resource identification information and transmitting the information to the index server; the index server is used for returning information such as a searched Intranet node list owning a resource, the list address of the cache server and the like; the protocol analyzer is used for configuring a Hash search return result message according to the returned information and transmitting the result to an Ares client, so that a peer-to-peer network user can download resources from an Intranet node and the caching server; and if needed file information is not inquired in the index server, the protocol analyzer is informed of not processing the Hash search request message of the user, the caching server is informed of downloading a file to be shared by an Intranet user, and an index service module is informed of updating the information after the file is downloaded.
Owner:NANJING UNIV OF POSTS & TELECOMM
Networking protocol analysis-based business analysis monitoring method and system
ActiveCN102932195AEasy to defineExcellent replicableData switching networksData streamNetworking protocol
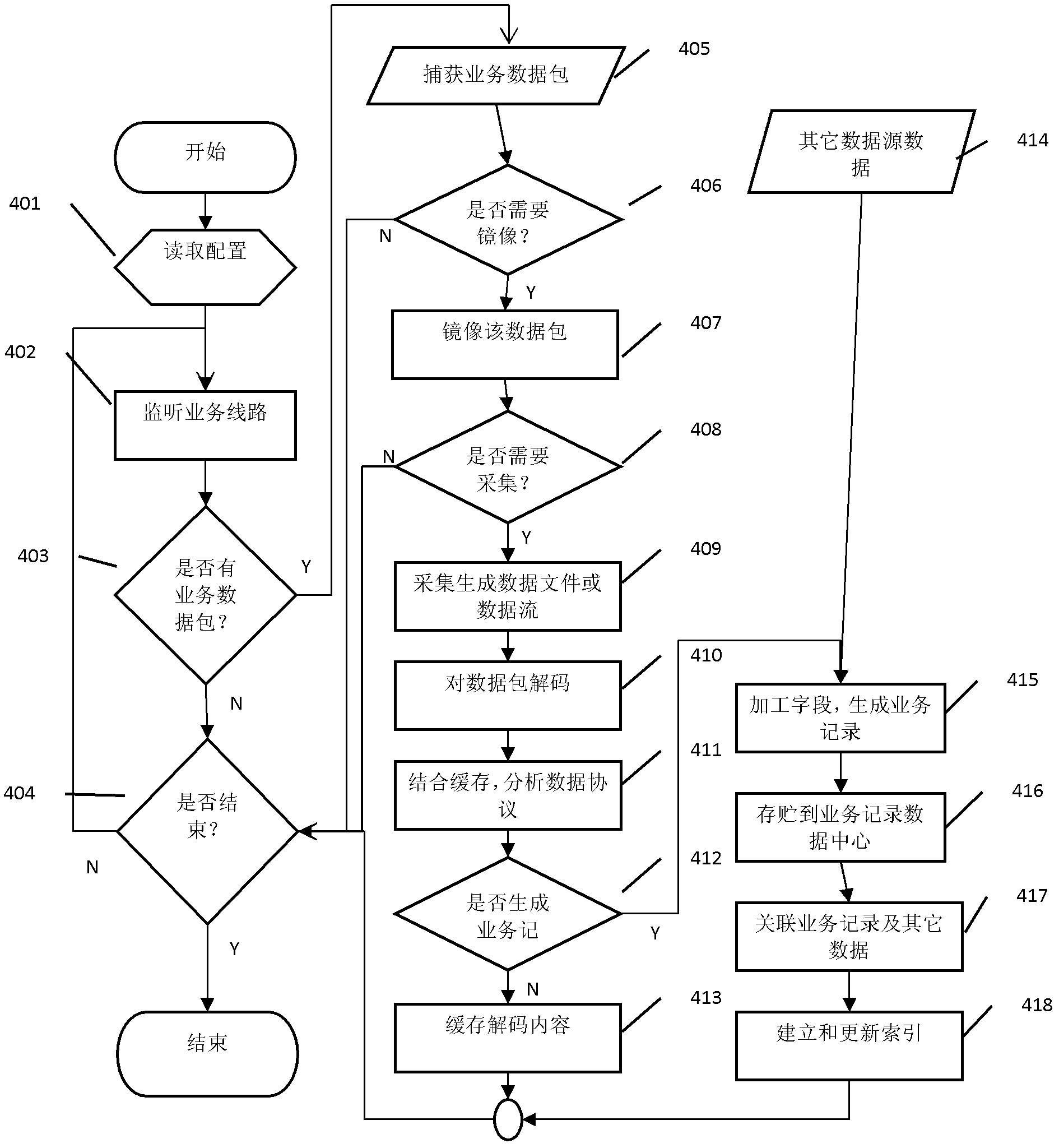
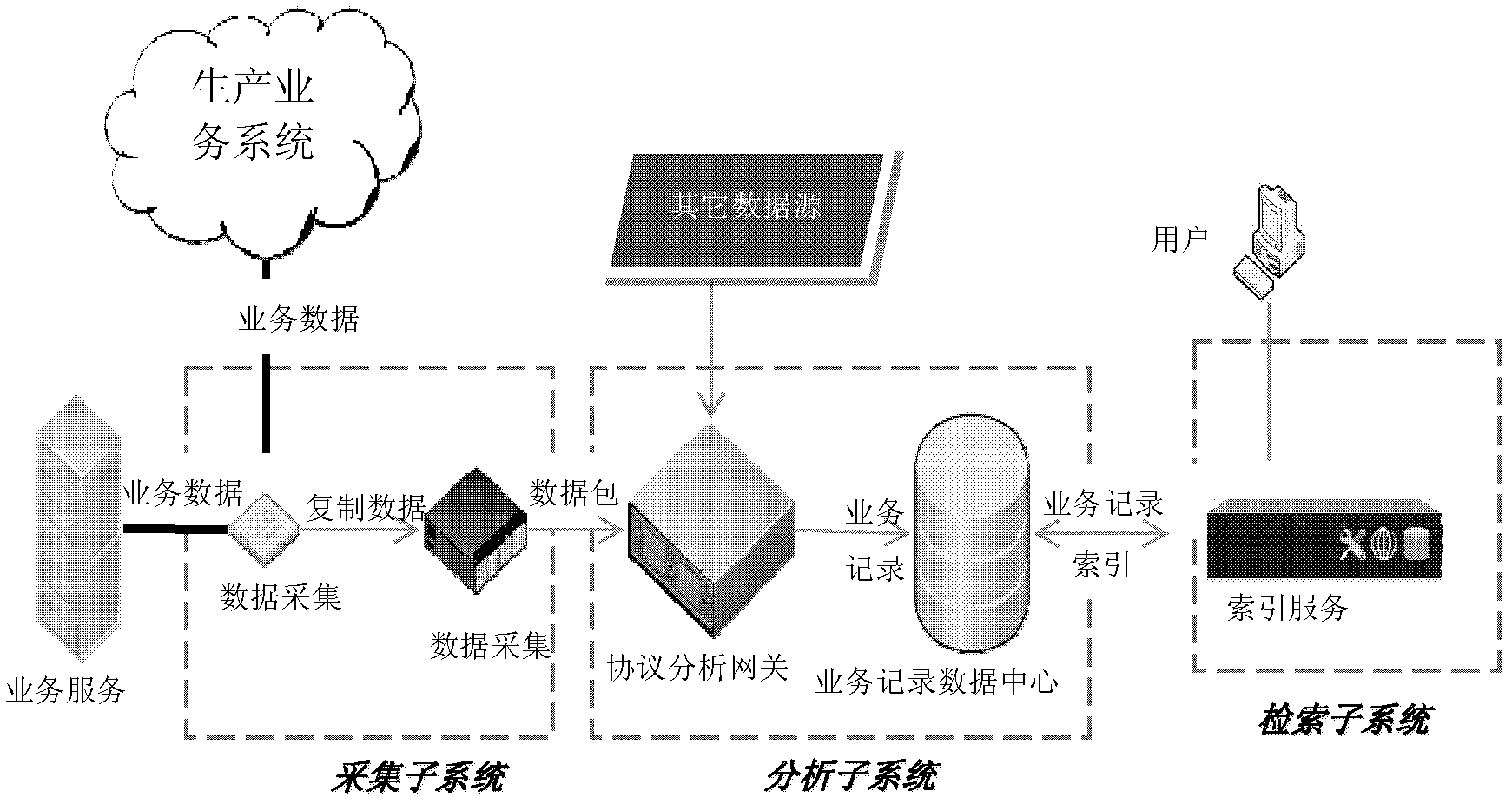
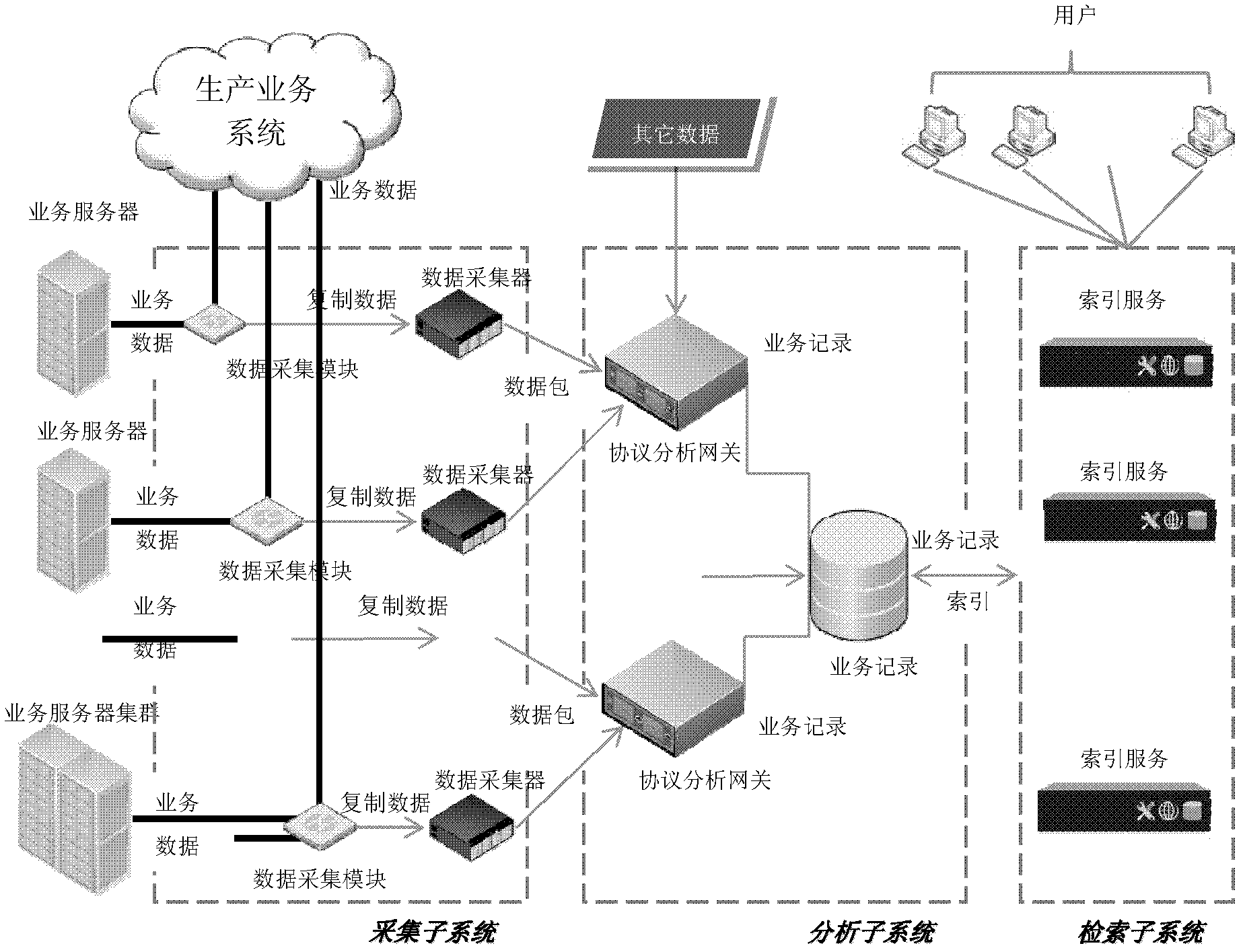
The invention relates to a networking protocol analysis-based business analysis monitoring method and system. The networking protocol analysis-based business analysis monitoring method comprises the steps that: a data acquisition module acquires a new business data packet generated by a production business system, copies the business data packet to a data acquirer; the data acquirer stores a data file or sends the data file to an appointed position in a data stream mode; a protocol analysis gateway extracts the business data packet and decodes the business data packet; the protocol analysis gateway further processes a field of the data packet, decomposes, translates, merges or shields a decoding field, finally generates a business record, and outputs the business record to a business record data center; and the business record data center stores the received business record, associates various kinds of business records, and establishes and updates a record data index. Compared with the prior art, the networking protocol analysis-based business analysis monitoring system has the advantages of dependence of a business system, no increase of business system complexity, excellent replication and extension capacities and the like.
Owner:SHANGHAI NETIS TECH
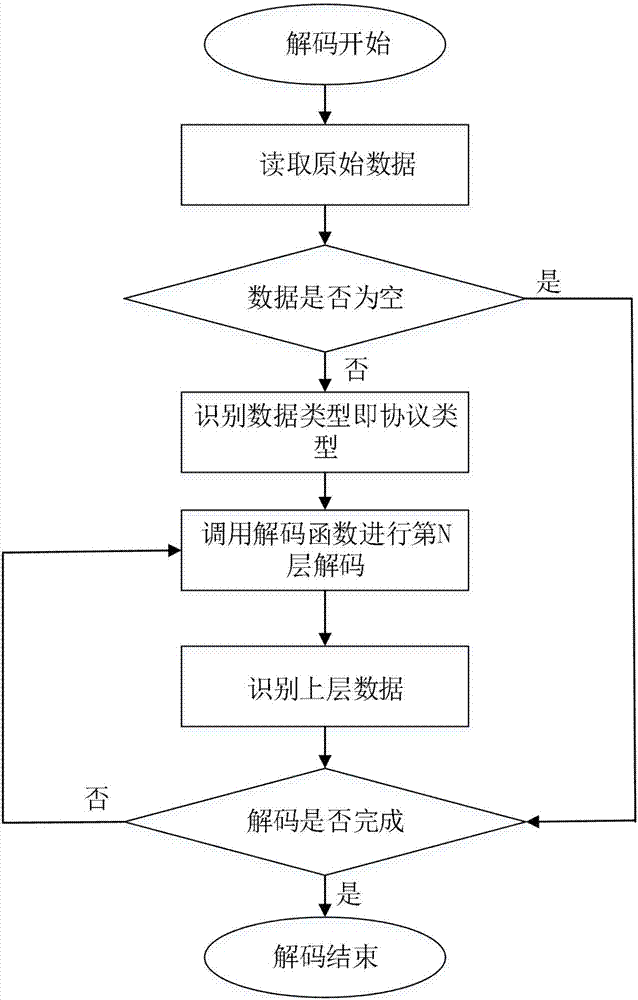
Network behaviour active analyzing and diagnosing method
ActiveCN101605067AAdapt to the requirements of application developmentAvoid hysteresisData switching networksSpecial data processing applicationsNetwork behaviorComputer science
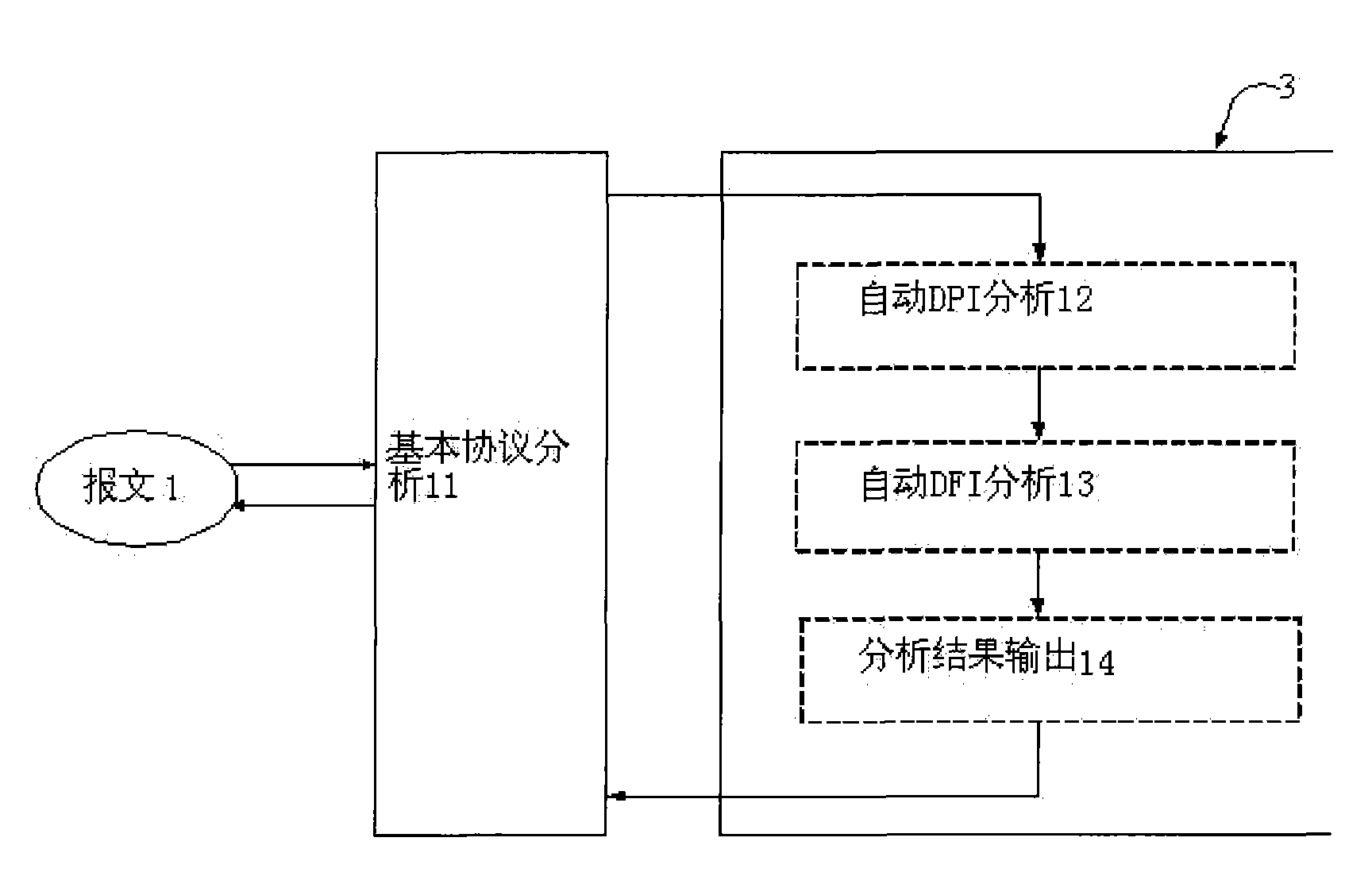
The invention provides a network behaviour active analyzing and diagnosing method; firstly, messages are initially tested, the messages and a known protocol library are matched to remove the known protocol messages; sequentially, unknown messages are subjected to protocol analysis, the unknown messages are designated with port, IP and time interval information, and the messages are extracted to protocol automatic analysis flow to be analyzed; and finally, the analysis result is output, the protocol automatic analysis flow establishes DPI and DFI models for the designated messages and outputs the analysis result. The method of the invention can analyze and diagnose unknown messages, is a beneficial supplement by combining a prior protocol analysis model, can carry out active analysis and diagnosis on sudden network situation and newly appeared network application as well as network behaviours in which users are interested, and avoids hystereticnature of passive tracing.
Owner:网经科技(苏州)有限公司
Two-channel data detection and protocol analysis meter based on 6LowPAN and method
ActiveCN102158882AReduce the probability of packet lossNetwork topologiesWireless network protocolsLine sensorTransceiver
The invention provides a two-channel data detection and protocol analysis meter based on 6LowPAN and a method and relates to the technical field of wireless sensor network. The analysis meter comprises a wireless data acquisition module, an upper computer decoding analysis part, a wireless RF (radio frequency) transceiver 1 and a wireless RF (radio frequency) transceiver 2. The method comprises the following steps: continuously monitoring if wireless data message exists in the channel; to the data message, packaging the message header and the channel signal by a main controller and sending to the upper computer; using an upper computer data processing module to confirm the frame type according to a frame type subsection in a frame control field of MAC (media access control) layer message header of the received data message; if being 6LowPAN packet, analyzing the protocol message header of the 6LowPAN packet layer by layer according to a protocol rule of a 6LowPAN protocol model; and performing analytic statistics and displaying on a man-machine interface.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Network analysis software real-time
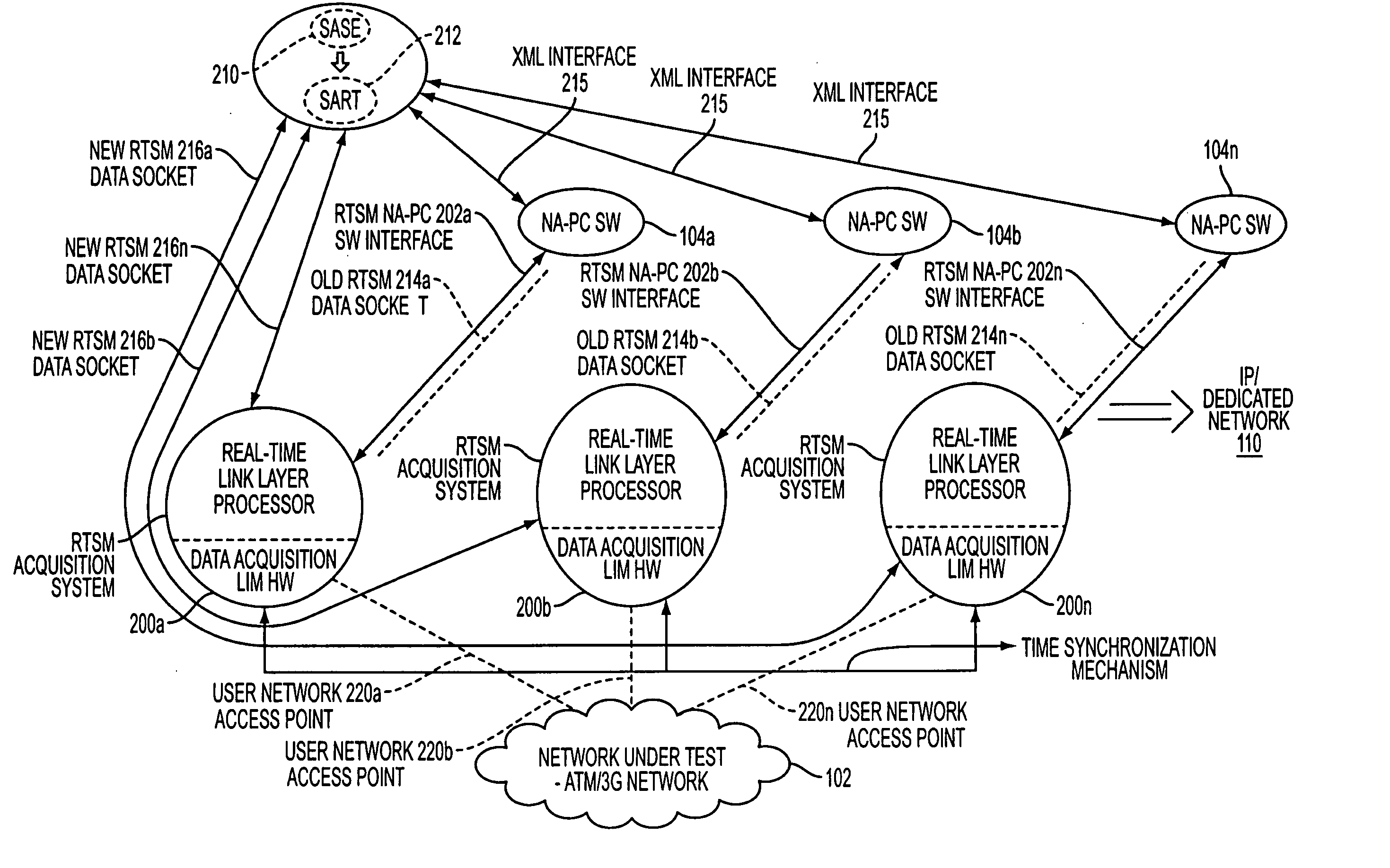
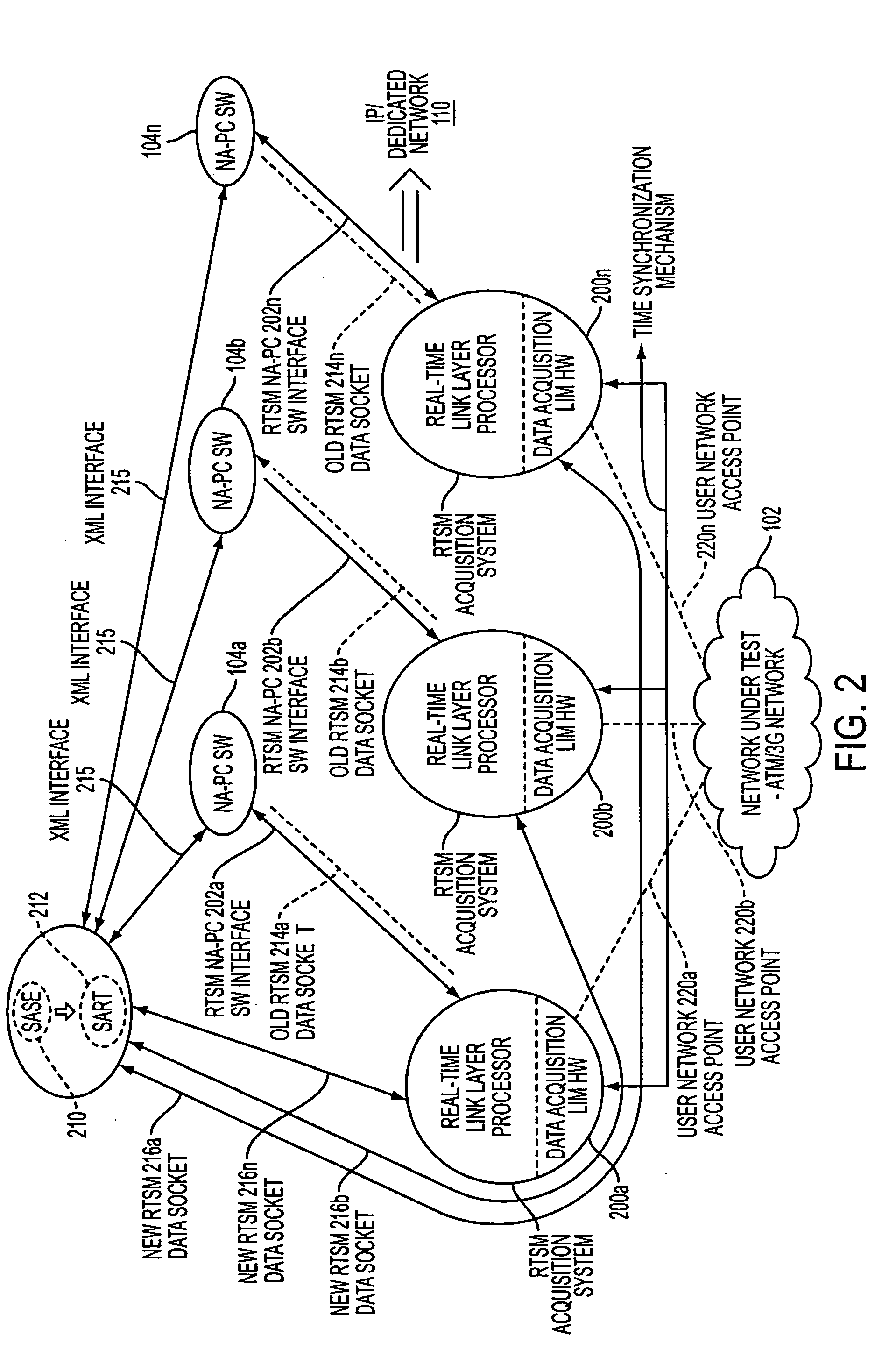
InactiveUS20050278437A1Digital computer detailsData switching networksTime ProtocolNetworking protocol
A method and system of enabling real-time network protocol analysis of network data by a post-time network protocol analyzing software that is incompatible with a real-time protocol analyzing software real-time capturing network data, by controlling the real-time protocol analyzing software and taking over a communication socket opened by the real-time protocol analyzing software, thereby transparently porting the post-time network protocol analyzing software to the real-time protocol analyzing software. Further, a method and system of enabling the post-time network data analyzer software to analyze network data captured concurrently in real-time from two or more of the real-time protocol analyzing software based upon time stamping by the real-time protocol analyzing software of every data frame received over the taken-over sockets.
Owner:AGILENT TECH INC
Method and apparatus for filtrating network rubbish information supported by multiple protocols
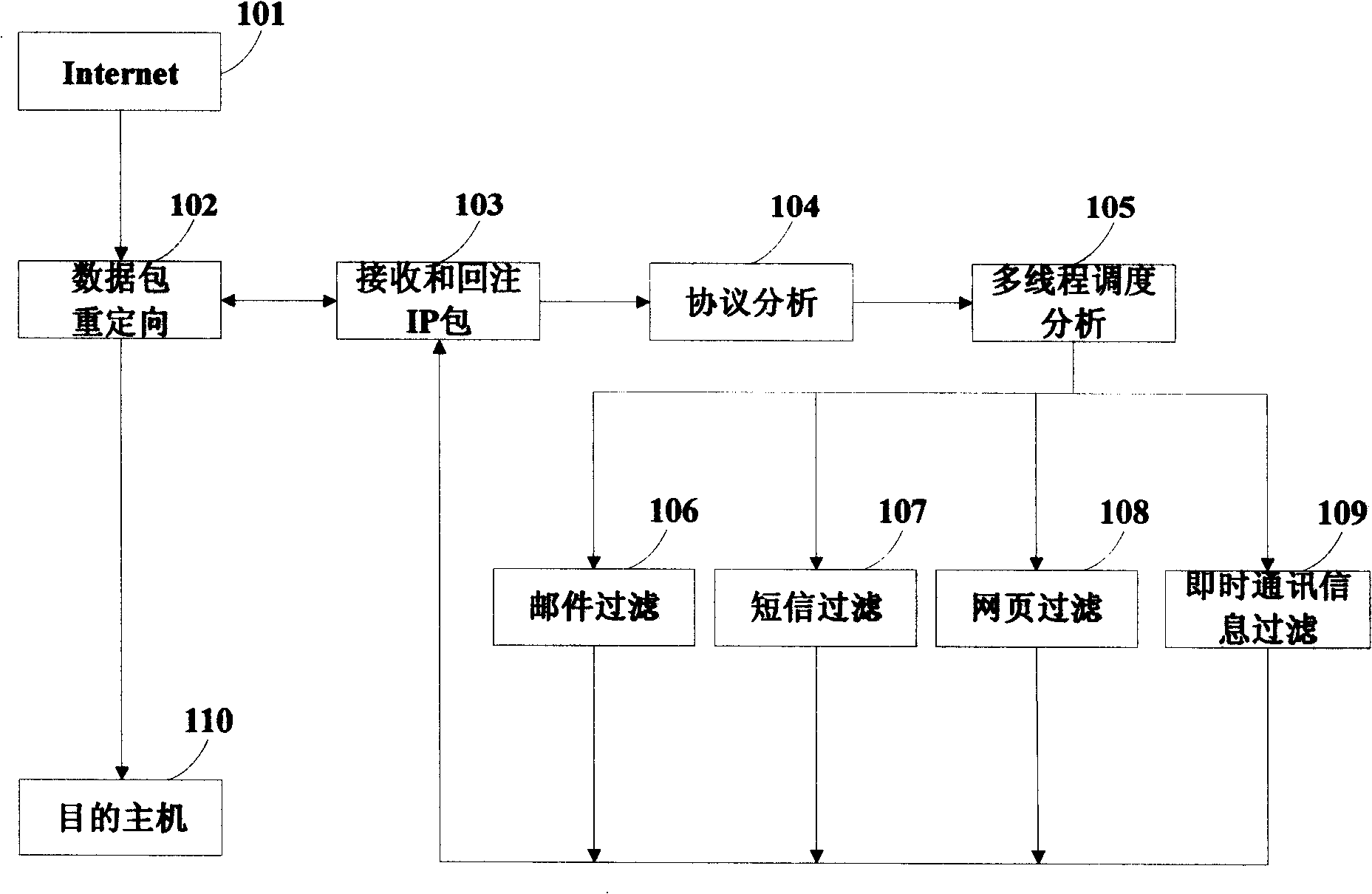
InactiveCN101330473AUser identity/authority verificationData switching networksData streamRelevant information
The invention discloses a network garbage information filtering method supported by multiprotocols and based on the transparent bridge, and a device, which belongs to the information security domain. The method and the device comprise a transparent bridge, data packet redirection, IP packet receiving and reinjecting, protocol analysis, a multi-thread scheduling analysis module and filtering modules (such as a mail filtering module and a short message filtering module, etc.) of various protocols. The method and the device adopt the technical proposal that the related information in the network is detained on the well-built linux transparent bridge by using iptables / netfilter, then ip lamination processing is completed, tcp data stream is restored, and complete network information is obtained and stored in a double-buffering queue; then the worker thread in a thread-scheduling awakened thread pool retrieves information form the double-buffering queue, and different filtering modules are invoked for filtering; the information is discarded when being judged as the garbage information, otherwise, the information is released. The device can be positioned at the front end of the gateway of a large and medium-sized enterprise or deployed at the front end of a border router for filtering the network information.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
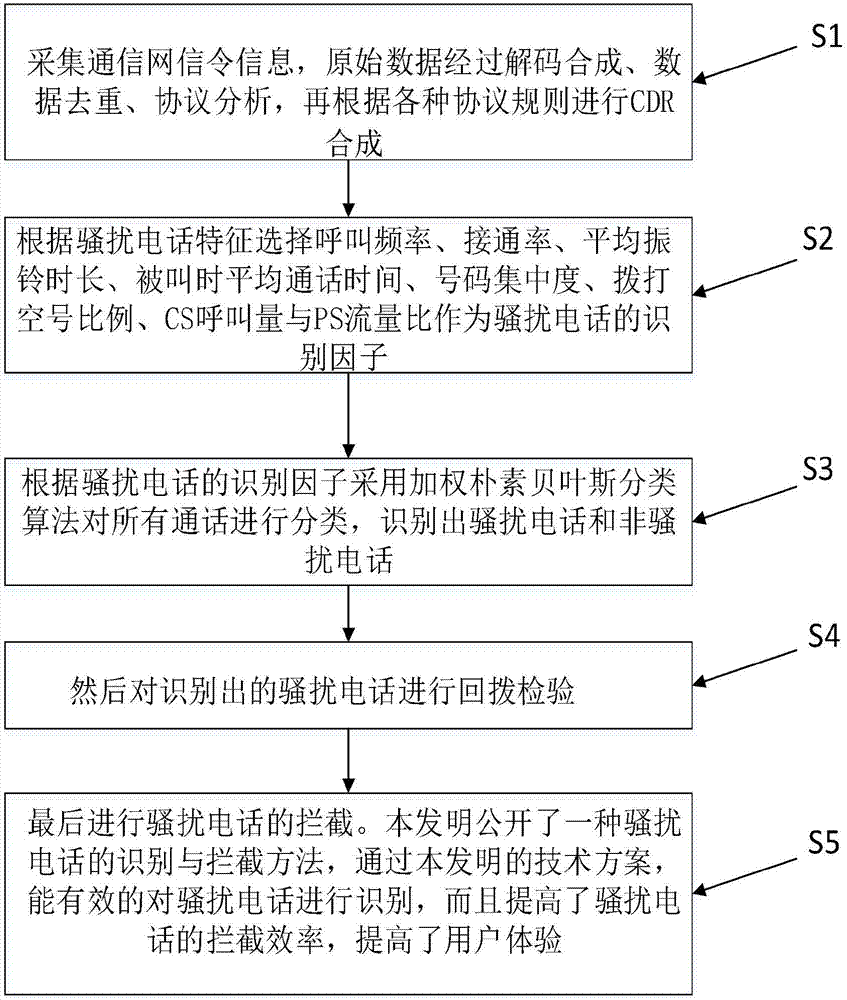
Harass call identification and interception method
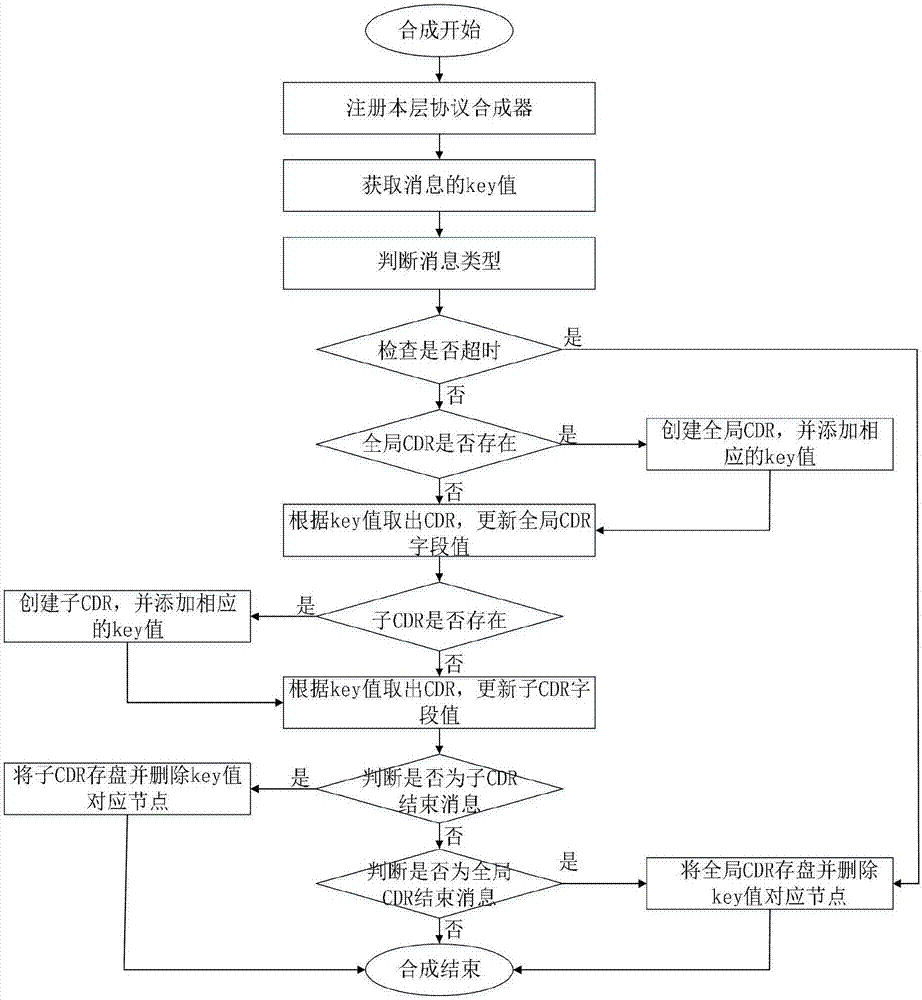
InactiveCN107331385AImprove recognition accuracyReduce workloadUnauthorised/fraudulent call preventionSpecial service for subscribersOriginal dataData mining
The invention relates to a harass call identification and interception method, and discloses the harass call identification and interception method. The method comprises the steps that S1: communication network signaling information is acquired, decoding synthesis, data deduplication and protocol analysis are performed on original data and then CDR synthesis is performed according to various protocol rules; S2: identification factors are selected according to the harass call characteristics; S3: all the calls are classified by using a weighted naive Bayesian classification algorithm according to the identification factors of the harass calls and the harass calls and the non-harass calls are identified; S4: then the callback inspection is performed on the identified harass calls; and S5: finally the harass calls are intercepted. The harass calls can be effectively identified, and the interception efficiency of the harass calls can be enhanced and the user experience can be enhanced.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Application protocol analysis method based on DPI (Distributed Protocol Interface)
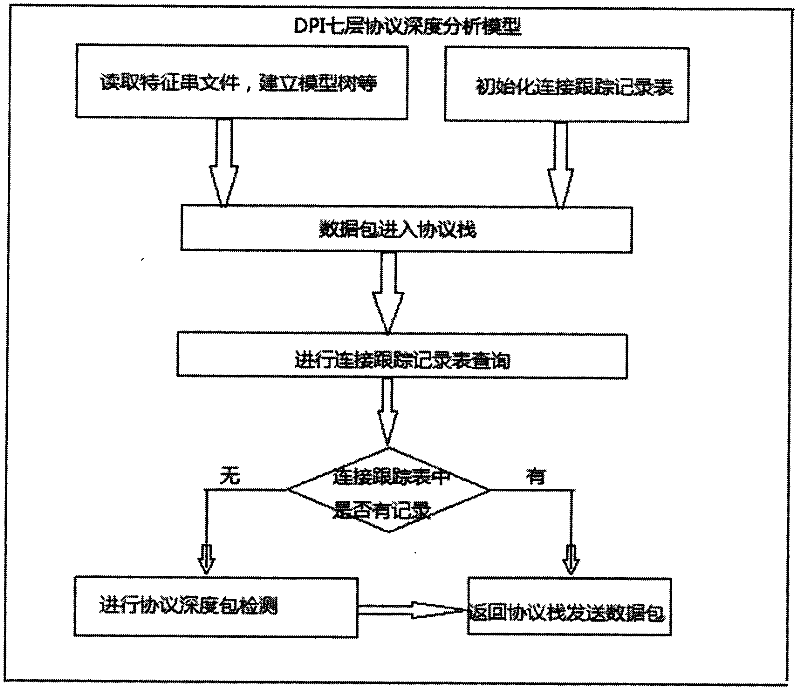
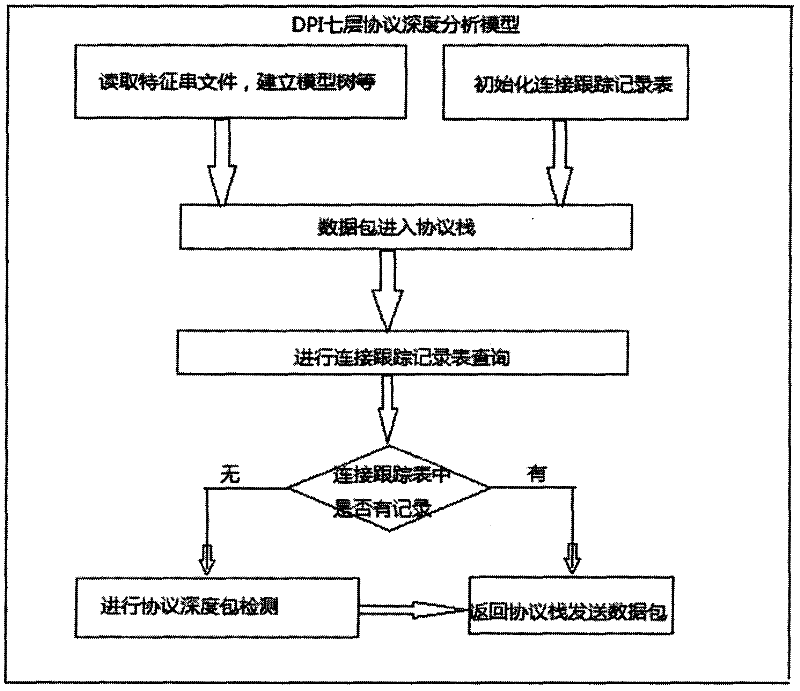
InactiveCN102347949AQuick analysisImprove analysis efficiencyTransmissionAnalysis dataPattern matching
The invention relates to a network application protocol analysis method, in particular to a seven-layer application protocol depth analysis method based on a DPI. The method comprises the following steps of: obtaining various application software data packets by using a packet capturing tool; determining which kind or which one obtained application software belongs to through the following steps: (1) adding an application protocol analysis layer into a tcp / ip protocol stack, (2) establishing an application protocol matching model by using a depth packet analysis arithmetic, and (3) obtaining a network data packet and analyzing characteristic application of the data packet to obtain application protocol information of the network data packet; carrying out protocol matching through the application protocol matching model with a multi-mode matching arithmetic; and determining which kind or which one the protocol type belongs to. According to the application protocol analysis method based on the DPI disclosed by the invention, various application software data packets are obtained by using the packet capturing tool; the protocol matching is carried out by using a high-efficient DPI depth packet detection technology with the multi-mode matching arithmetic; the rapid application protocol analysis is carried out on the data packets; and the analysis efficiency and accuracy are increased.
Owner:深圳西默万网科技技术有限公司
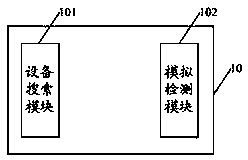
ONVIF simulating testing device and method
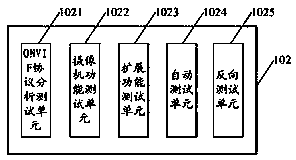
The invention discloses an ONVIF simulating testing device and method. The device includes: a device searching module used for searching for an online camera device in the same network segment and obtaining related information of the camera device; and a simulating testing module used for performing an ONVIF simulating test based on the related information. The ONVIF simulating test includes: protocol analysis testing, camera function testing, extended-function testing, automatic testing and reversed testing so that technical problems of test-method singularity, complex testing, high test cost and lower test efficiency, existing in the prior ONVIF testing, are solved and a technical effect that the ONVIF test is completed in a simple, efficient and diversified manner at a low cost is realized.
Owner:STATE GRID CORP OF CHINA +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com