Industrial control protocol vulnerability mining system based on fuzzy test
A technology of fuzz testing and vulnerability mining, applied in transmission systems, digital transmission systems, electrical components, etc., can solve problems such as real-time performance and high reliability requirements, and achieve the effect of improving adaptability and improving hit rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The present invention will be further described below in combination with specific embodiments.
[0035] For example, exploit the vulnerabilities of the ModbusTCP protocol in the industrial control system.
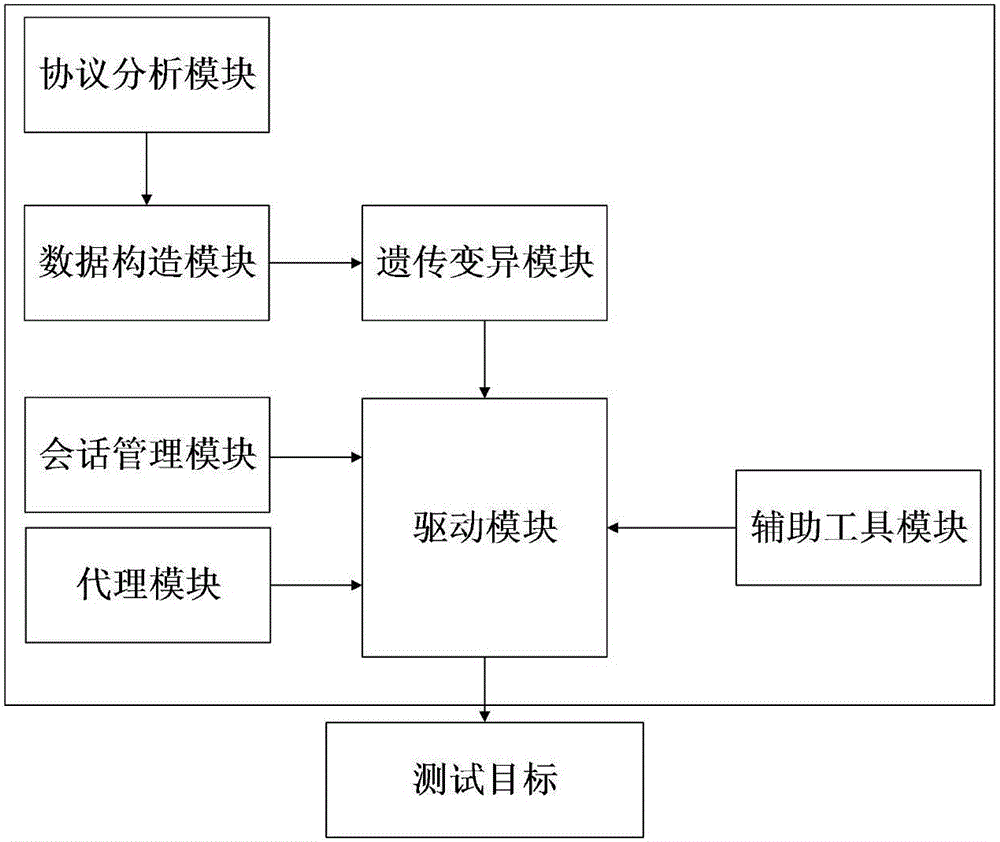
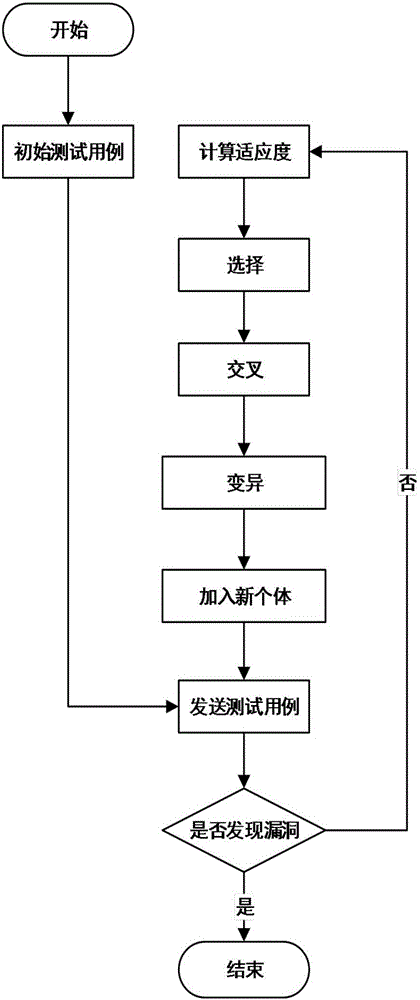
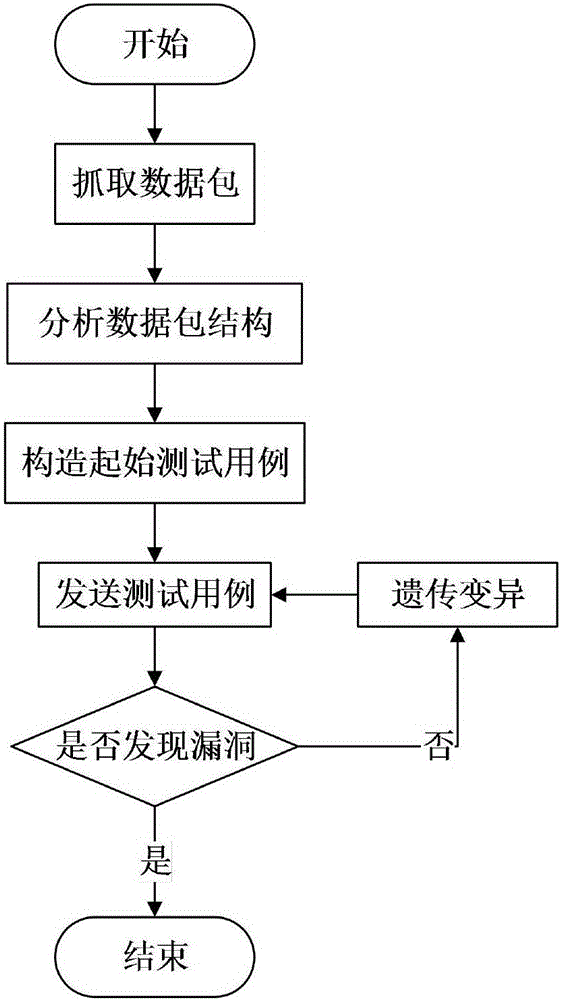
[0036] 1) Grab the data packets in the network through the protocol analysis module, store and analyze the valid data, and then send the obtained protocol format and other information to the data construction module. By capturing and analyzing the data packets, the ModbusTCP data frame format can be known, including the MBPA message header and the PDU data unit. Among them: the MBAP message header includes 4 parts of the transmission flag, protocol identifier, length and unit flag, a total of 7 bytes; the PDU data unit is in the same format as the Modbus protocol, including two parts, the function code and the data field. At the same time, the population size of this test is set to 100 according to the characteristics of the industrial control system.
[0037] 2) ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com