Network intrusion detection system and method based on application protocol detection engine
A network intrusion detection and application protocol technology, applied in the field of network information security, can solve the problems of lack of automatic upgrade method, easy system scalability and easy maintenance, etc., to achieve convenient development and maintenance, ensure easy scalability, and ensure easy maintenance. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
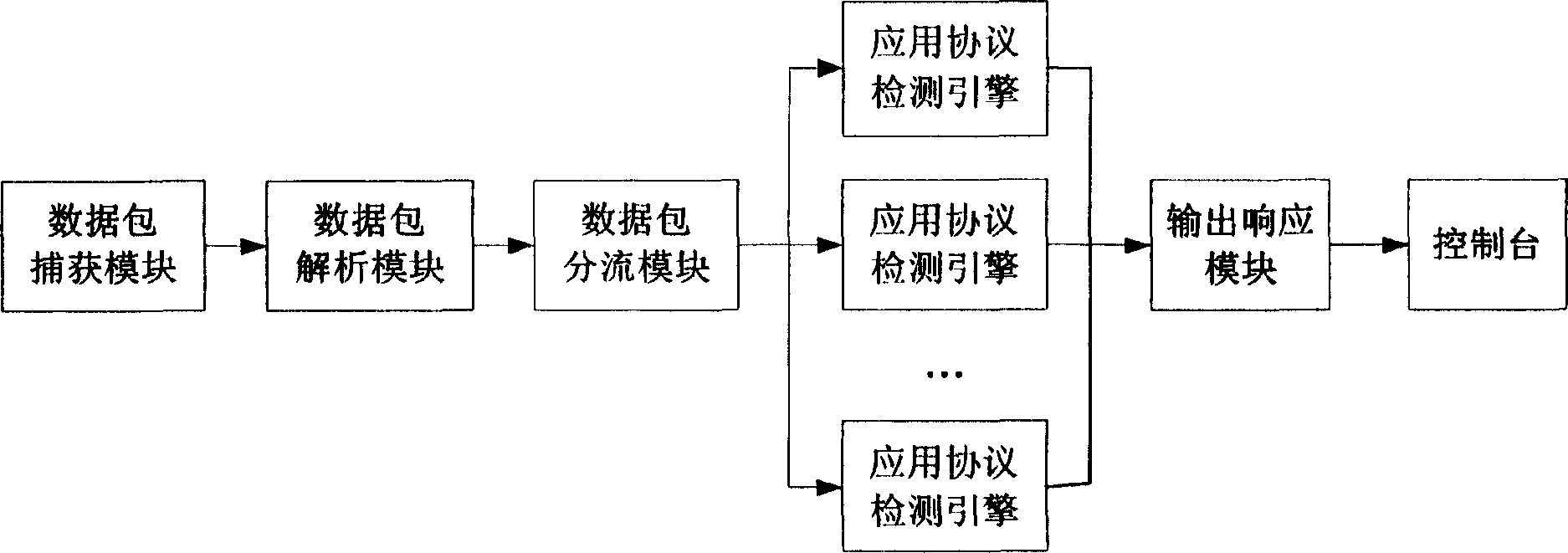
[0039] Refer to the attached Figures 1 to 5 Describe in detail the network intrusion detection system based on the application protocol detection engine provided by the present invention:
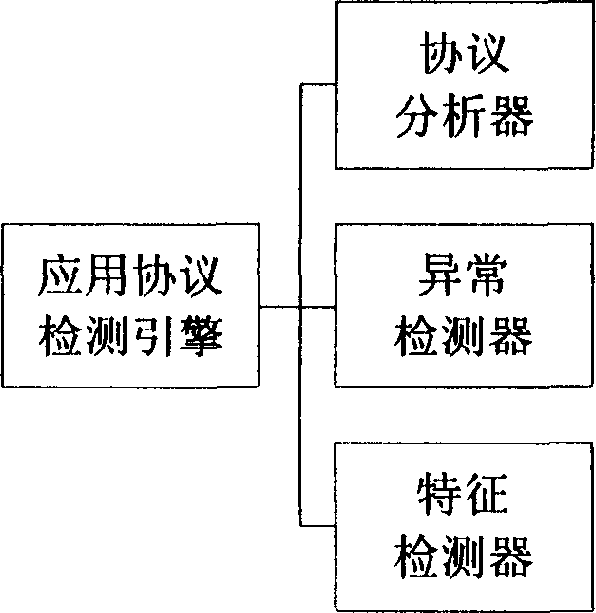
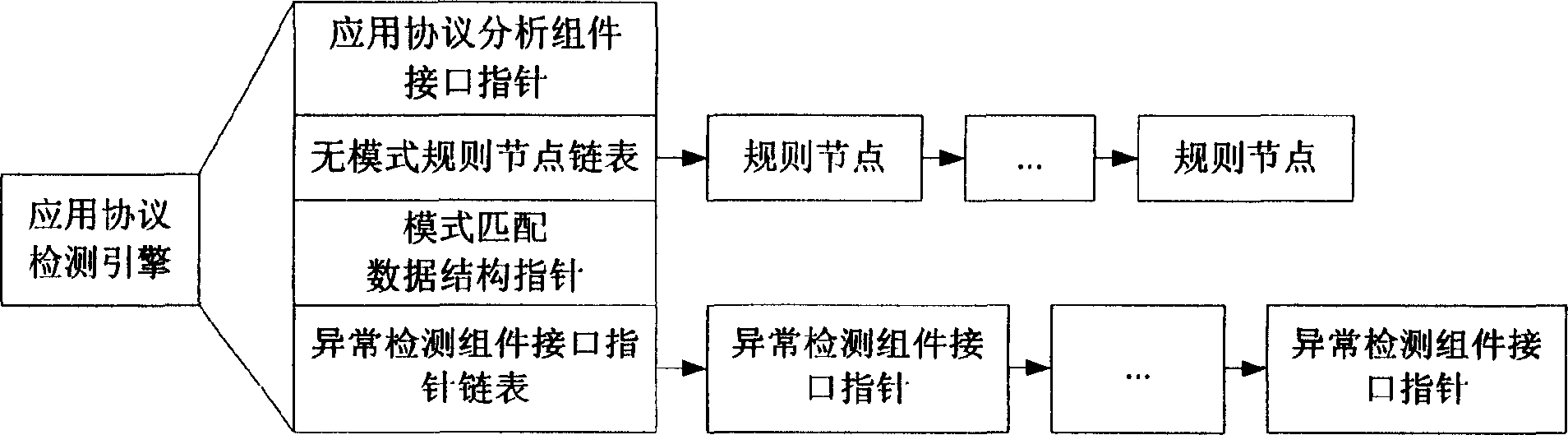
[0040] Such as figure 1 As shown, the network intrusion detection system based on the application protocol detection engine provided by the present invention, wherein the data packet capture module, data packet analysis module, data packet shunt module, output response module and the structural composition, connection relationship and function of the console All are the same as the existing network intrusion detection system. It is characterized in that, as figure 2 As shown, the application protocol detection engine also includes three detection function modules: a protocol analyzer, an anomaly detector and a feature detector. The three modules respectively use a simple component object model to implement the application protocol analysis component, anomaly detection component and The f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com