Network intrusion detection system and method based on data mining
A network intrusion detection and data mining technology, applied in the field of network security, can solve the problems that the protocol analysis technology does not have the audit function, cannot process massive data in time, and limits the application of the protocol analysis technology, so as to improve the detection speed and detection accuracy , Reduce system false positives and false positives, and prevent distributed attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
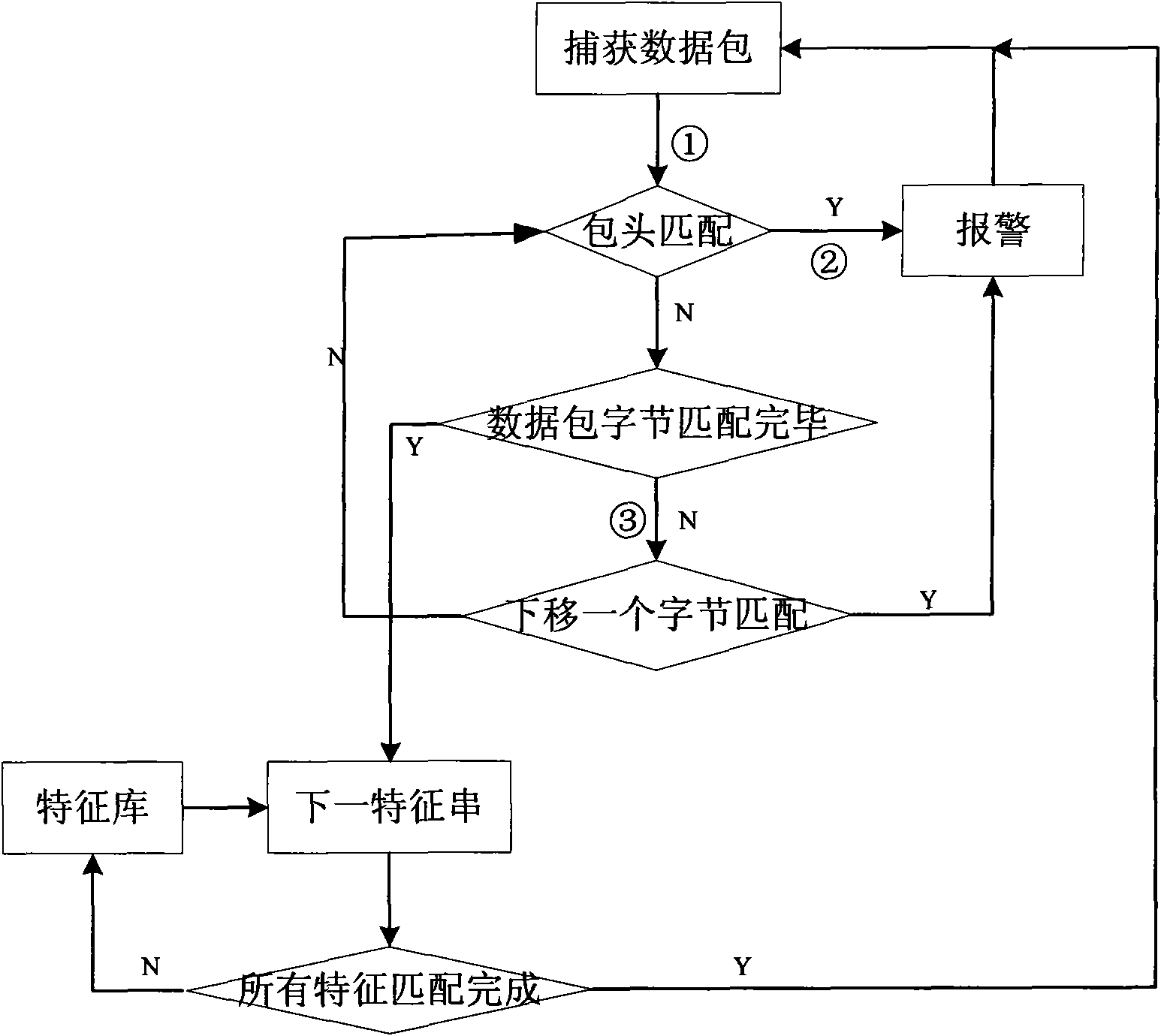
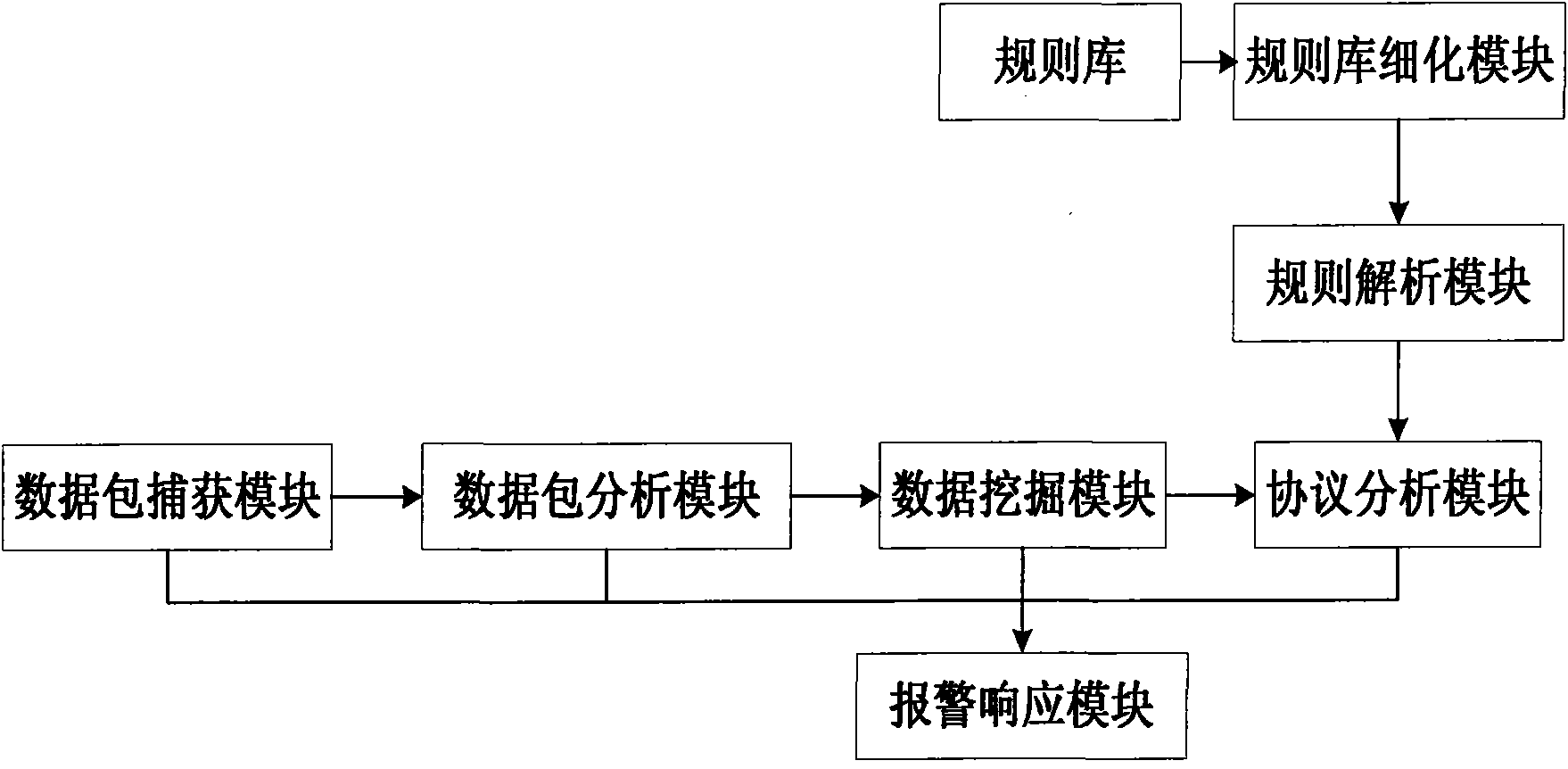
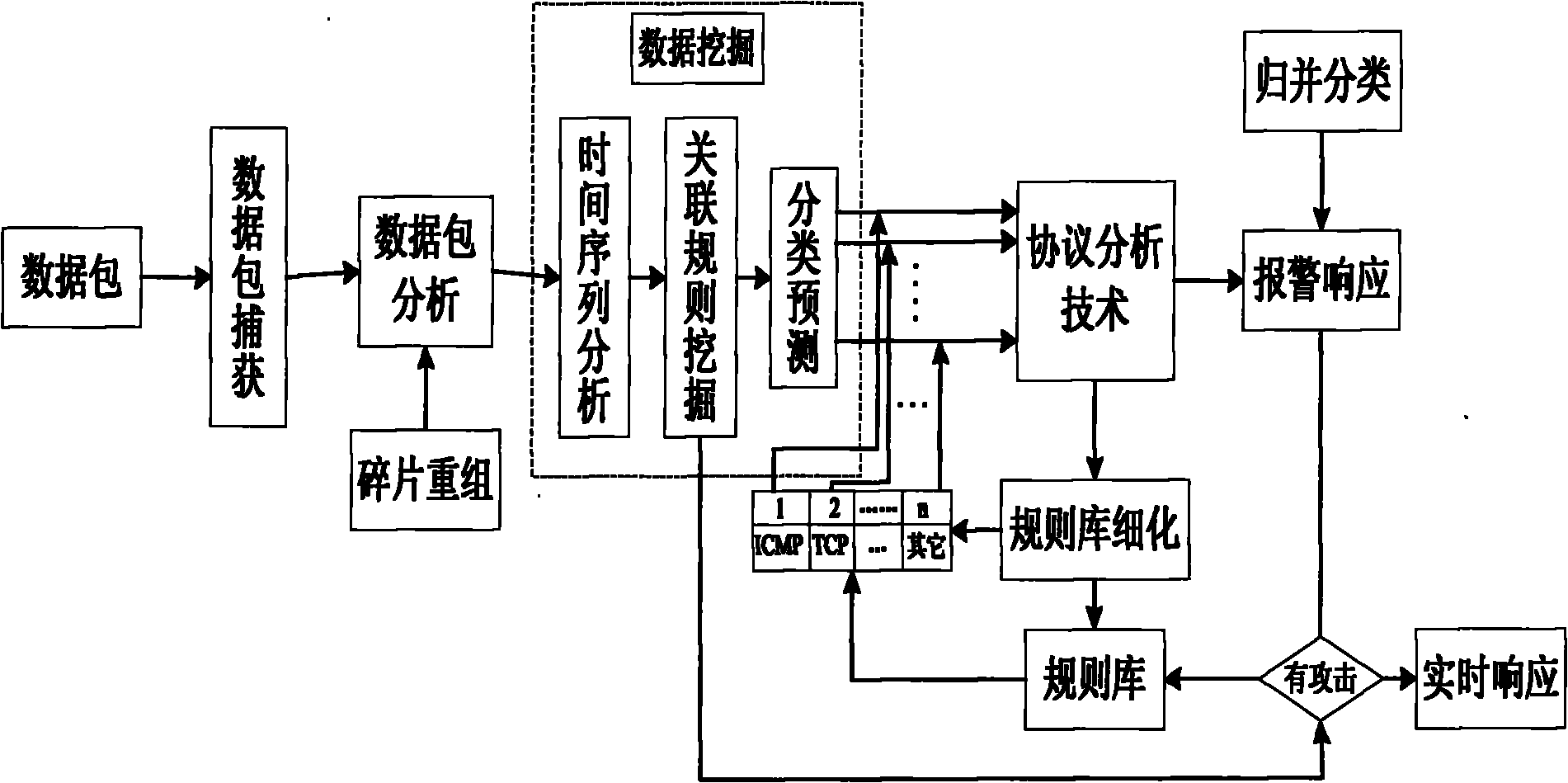
[0055] Such as figure 2 As shown, a network intrusion detection system based on data mining includes:
[0056] The data packet capture module is used to capture data packets in the network, classify the captured data packets by type, discard non-compliant data packets and generate discarded data packet report information to send to the alarm response module, and then classify and discard processing The final data packet is sent to the data packet analysis module;
[0057] The data packet analysis module is used to analyze the datagram format of the data packet sent by the data packet capture module, and judge whether the current data packet is a complete data packet, and if so, directly send the complete data packet to the data mining module, otherwise call the fragment The reassembly module reassembles the fragmented data packets;
[0058] The fragment reassembly module is used to reassemble the fragmented data packets, send the reassembled and restored complete data packe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com