Proprietary protocol analysis and identification method
A proprietary protocol and identification method technology, applied in the direction of electrical components, transmission systems, etc., can solve the problems of not being able to identify encryption protocols, and achieve high accuracy and simple effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The specific implementation manners of the present invention will be described in detail below in conjunction with the accompanying drawings.
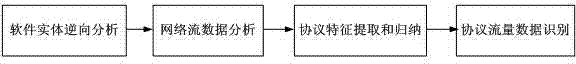
[0028] The invention discloses a private protocol analysis and identification method, which specifically includes the following steps:
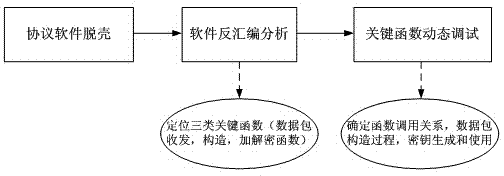
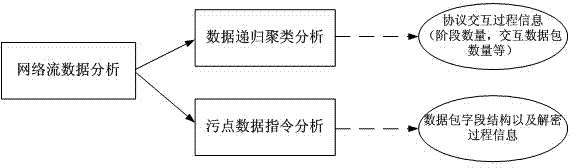
[0029]Step 1: Unpack the client software that uses a private protocol for communication to obtain the unpacked original program; then disassemble the original program to obtain the assembly code of the original program; and then disassemble the original program in the assembly code The key functions are dynamically debugged to obtain the field length and structural characteristics of the message type of the private protocol; the key functions include: 1. The constructor of the message data packet; 2. The function of sending and receiving the message data packet; 3. . Encryption and decryption functions. For the analysis of the encryption protocol, this step is a method to obtain the division a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com