Test device used for testing intrusion detection system and test method thereof
An intrusion detection system and testing device technology, applied in the field of information security, can solve problems such as incompleteness, security defects, inability to test IDS or IDS modules, etc., to achieve the effect of improving efficiency and accuracy, improving ability and flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
test Embodiment ID
[0027] Test Case ID: IF-020
[0028] Test case name: buffer overflow attack - Printer Overflow of IIS
[0029] Test case description: Perform a Printer Overflow attack
[0030] Function Type: 1
[0031] File name: IF-020-Overflow-Printer.cap
[0032] Vulnerability ID: V02-1020
[0033] Vulnerability: 3
[0034] Policy Type: 1
[0035] Source IP: 192.168.1.100
[0036] Destination IP: 192.168.1.20
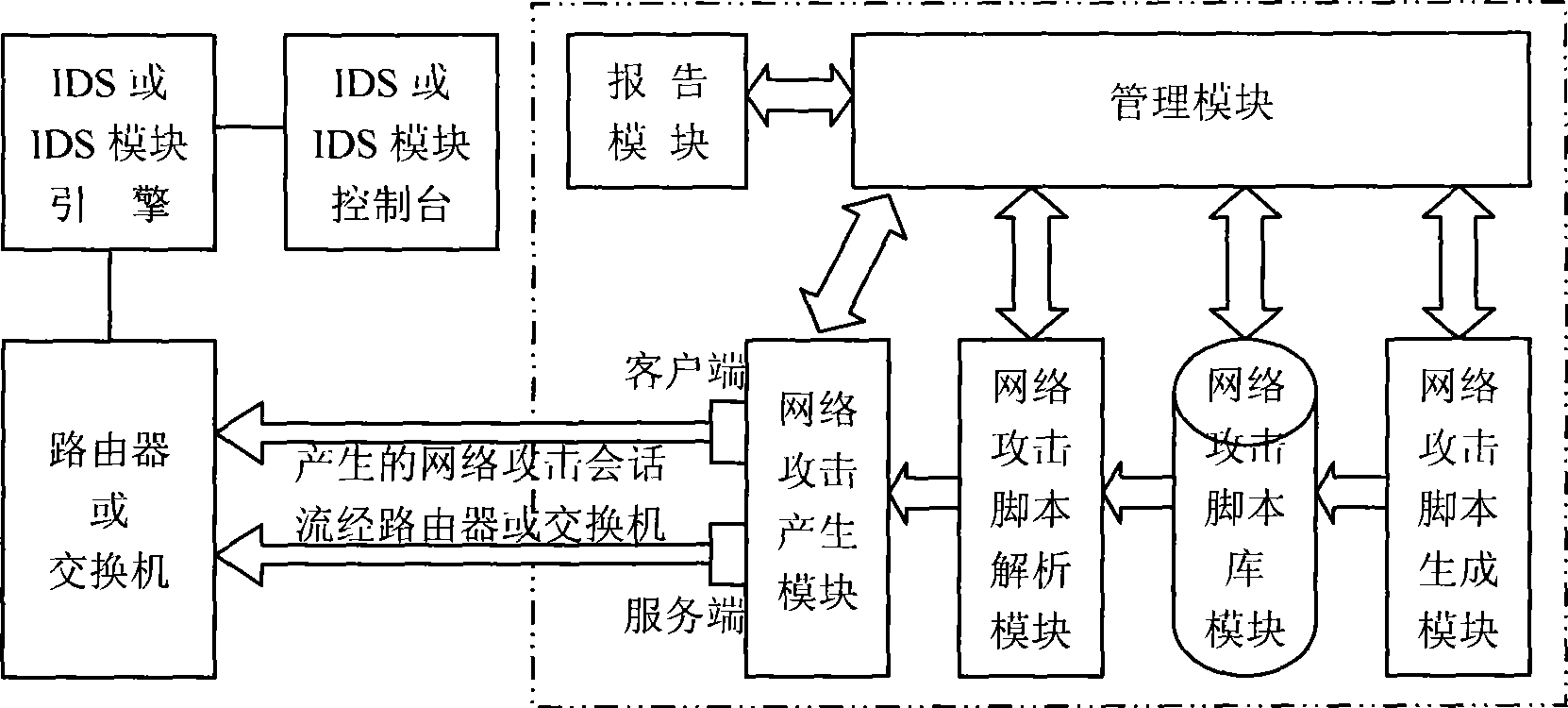
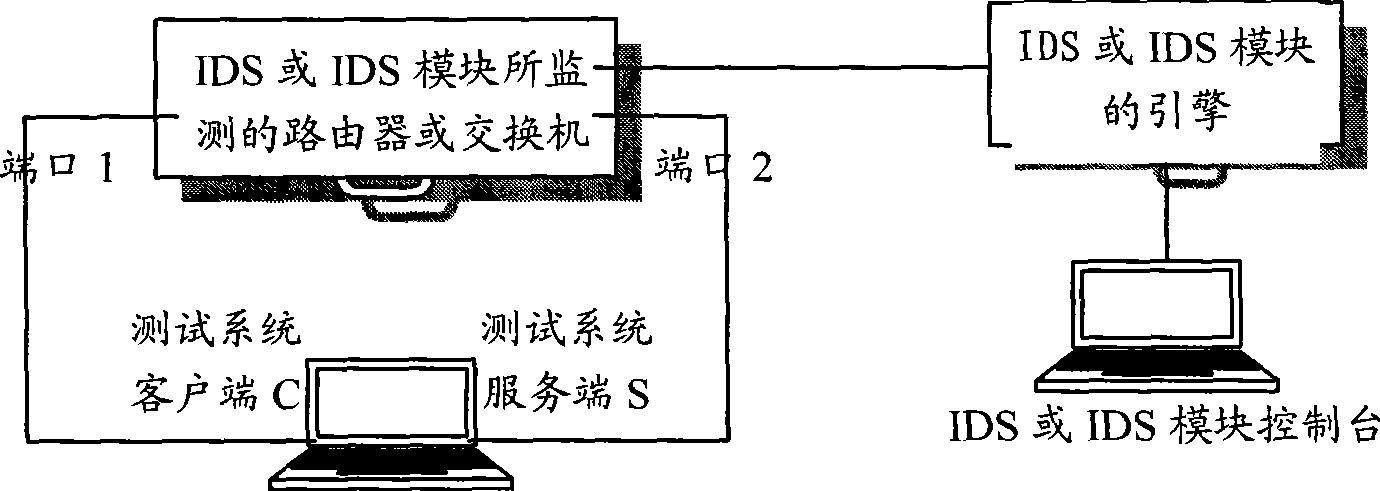
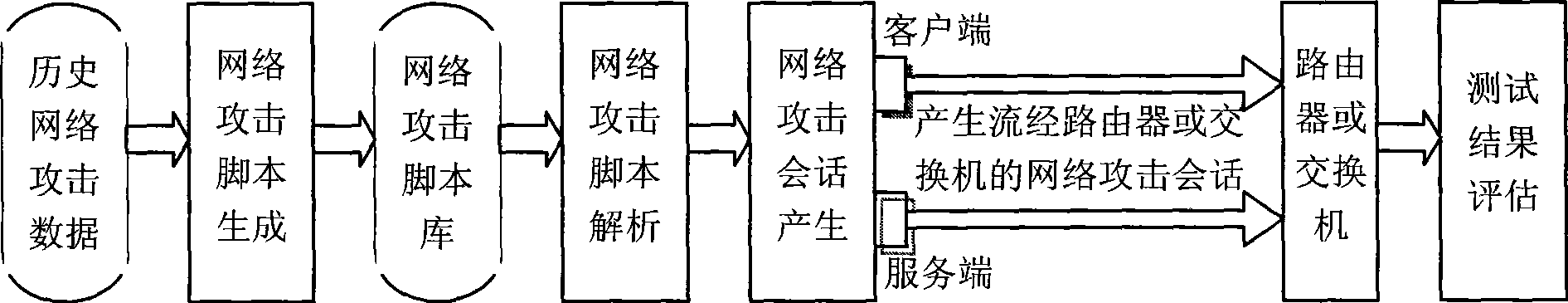
[0037] The other file is a data file of a network attack session, including all network session data required by the attack, and the session data is stored in the order of time when the network attack occurs. The data file is a network packet file in CAP format, which comes from historical network attack data. The historical attack data may be real-time and real network attack data captured by a protocol analyzer or a sniffer program, or attack data stored in a historical attack database.
[0038] For example, the buffer overflow attack—the CAP file of the IIS Printer Overf...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com