Intrusion detection system and method based on IPv6 network environment
An intrusion detection system and intrusion detection technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as network security control capability limitations, illegal access to LAN network resources, and immature network management technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
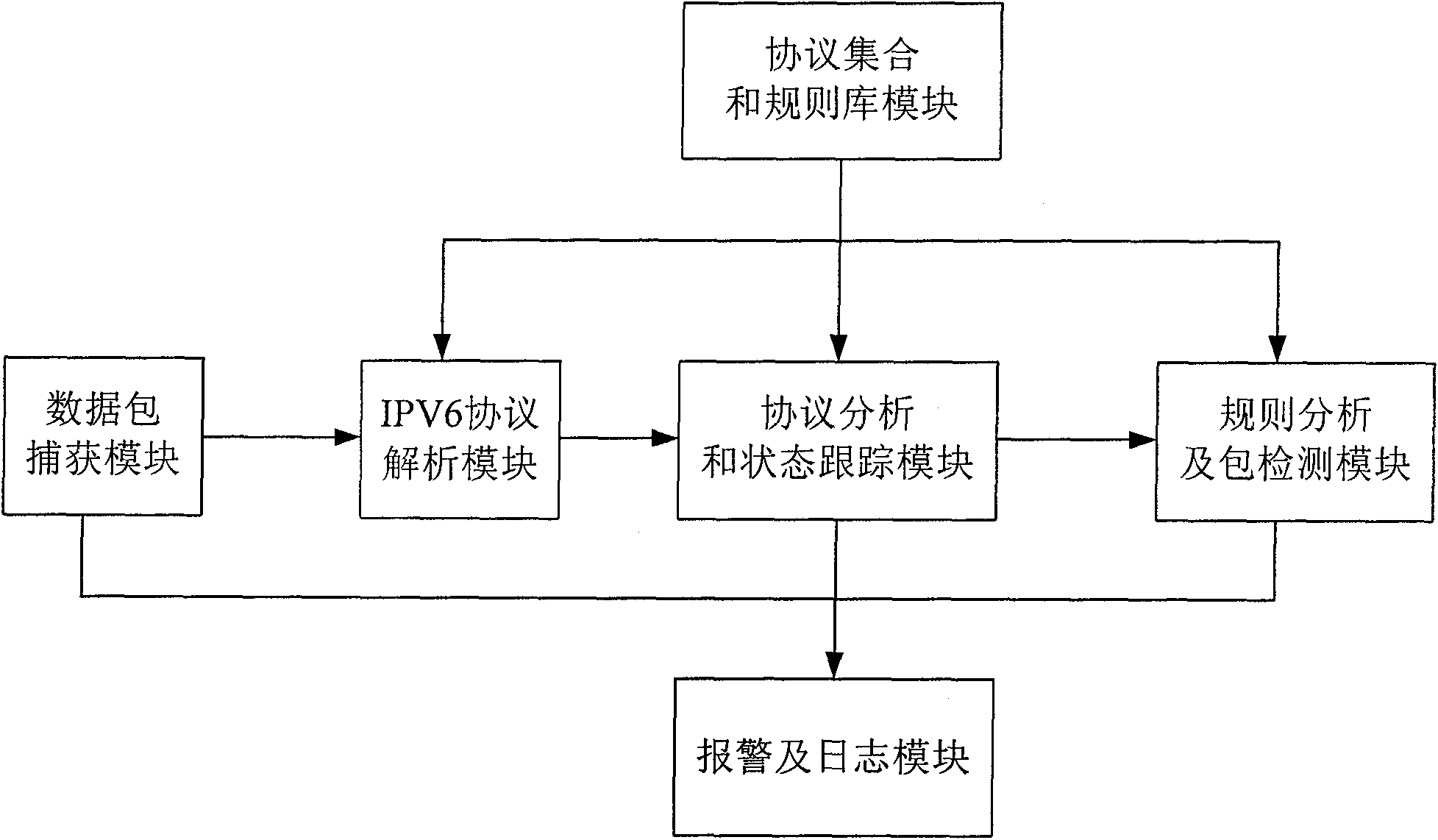
[0064] Such as figure 1As shown, the intrusion detection system based on the IPv6 network environment includes:
[0065] Protocol collection and rule library modules that can be set in detail;
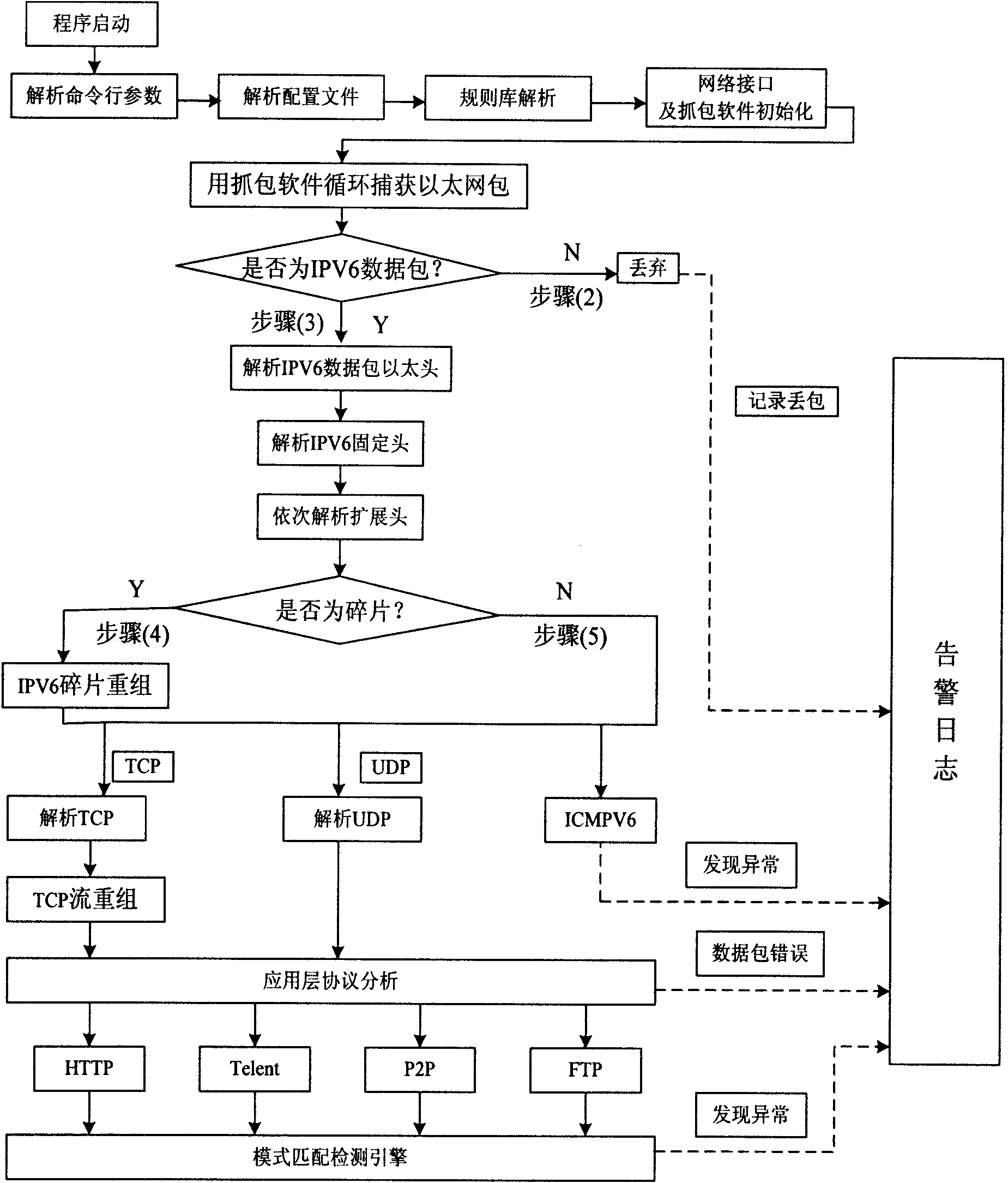
[0066] The data packet capture module is used to capture the data packets and process them, discard the non-IPv6 data packets in the captured data packets, and generate corresponding records according to the discarded packets to send and store them in the alarm and log module, and then process the obtained The complete IPv6 packet is sent to the IPV6 protocol analysis module;
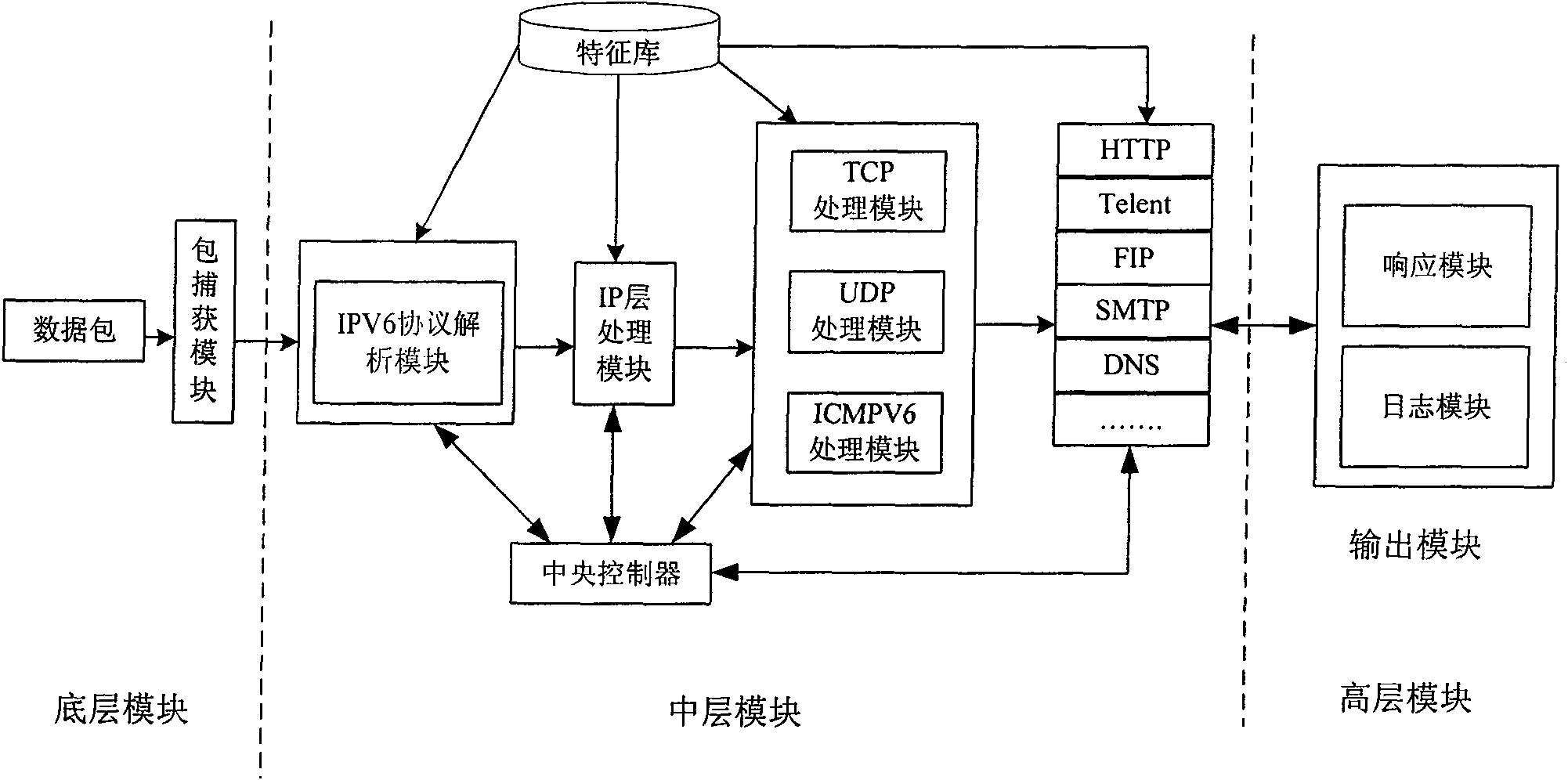
[0067] The IPV6 protocol parsing module is used to perform protocol decoding on the complete IPv6 data packet sent by the data packet capture module according to the protocol set set by the system and according to the data structure of the protocols of each layer of the network, to obtain the application data actually carried by the data packet and Sent to the protocol analysis and state tracking module;
[0...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com