Method and apparatus for filtrating network rubbish information supported by multiple protocols
A spam and spam technology, applied in data exchange network, user identity/authority verification, digital transmission system, etc., can solve problems such as poor intelligence, inability to process large flow of information, and inability to block spam in real time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0174] The implementation of the technical solution will be further described in detail below in conjunction with the accompanying drawings.
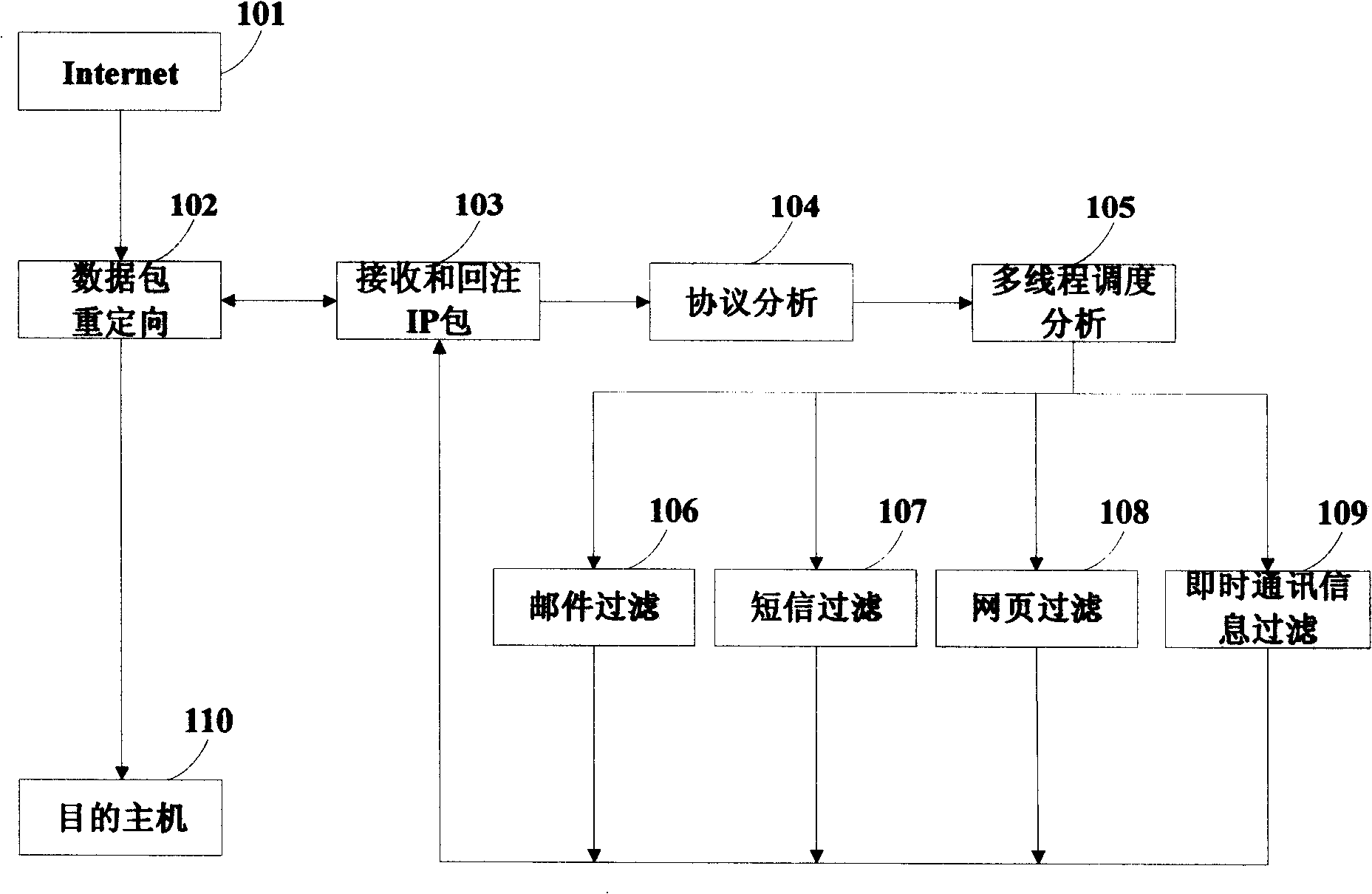
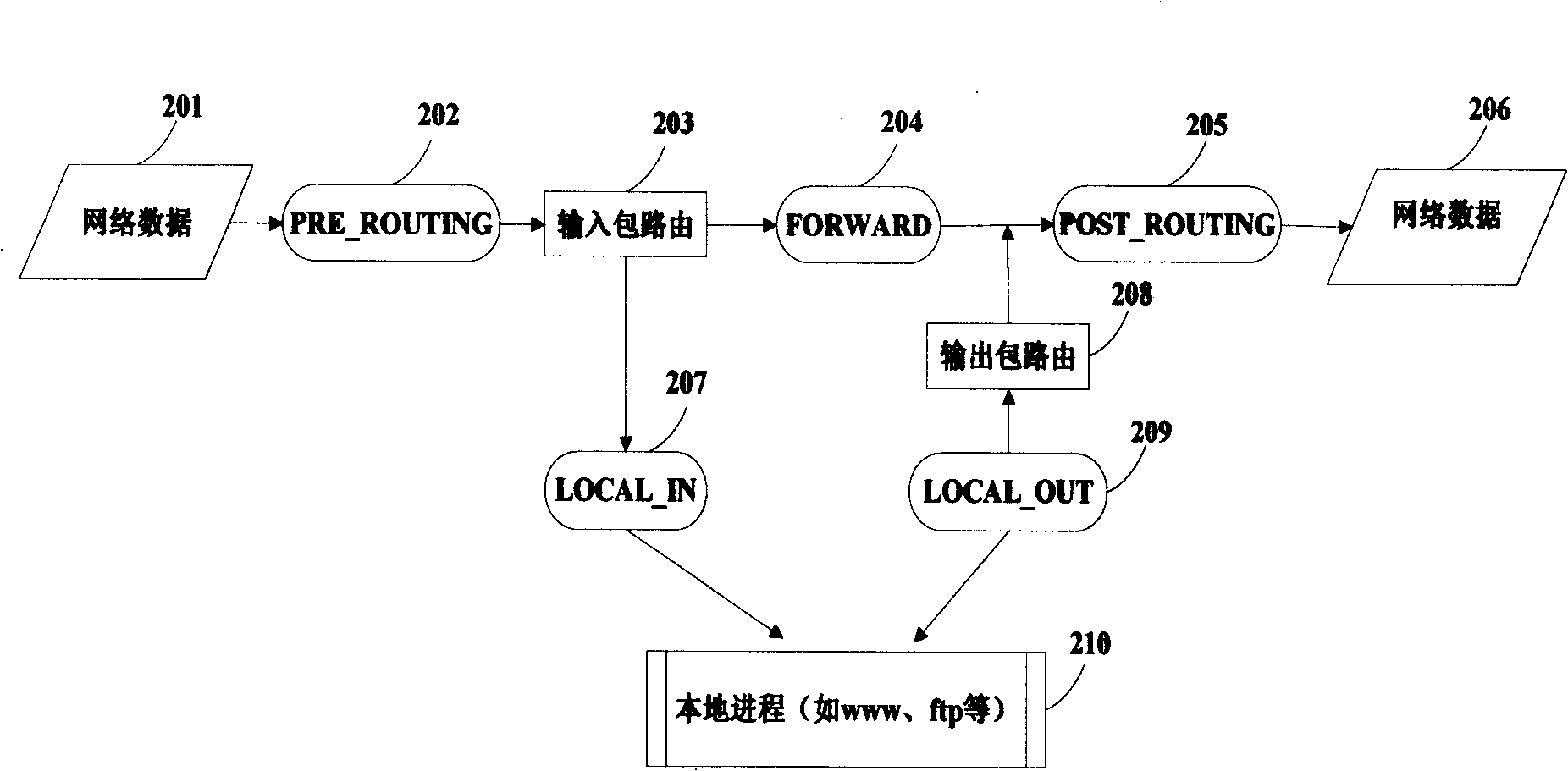
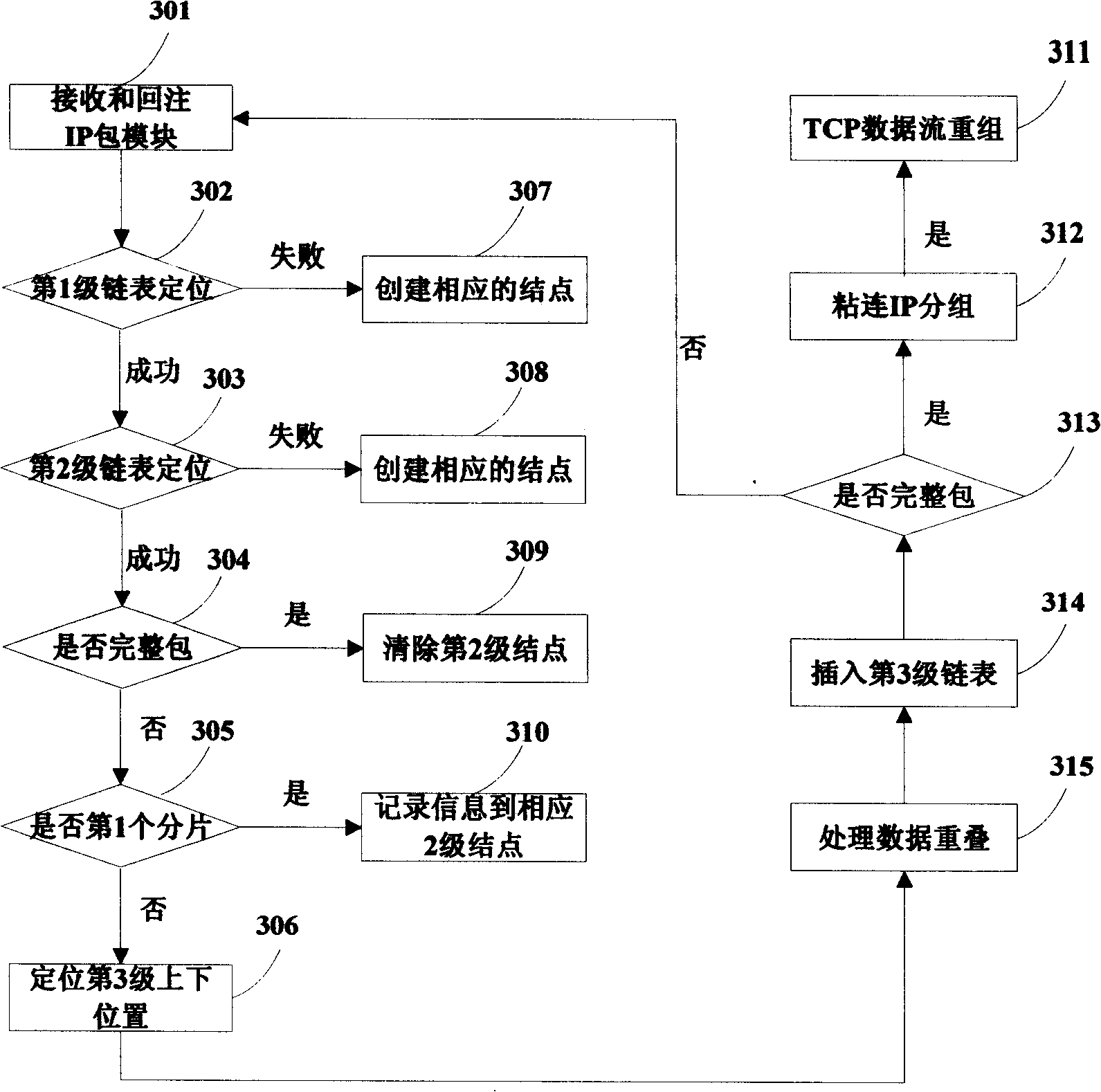
[0175] see figure 1 , which is a general flowchart of the whole device. When the network information is transmitted from the source host to the destination host (110) through the internet (101), the data packet redirection module uses netfilter / iptables (102) to detain the relevant protocol information and store it in the IP packet queue. The receiving and re-injecting IP packet module (103) directs the data packet from the kernel state to the user state, and then performs protocol analysis (104) on the data packet, mainly completing IP fragmentation reassembly and TCP data flow reassembly. When the TCP data stream recombination is completed, the completed information, such as the completed mail, can be obtained, and the restored information is stored in the double buffer queue. The multi-thread scheduling analysis module (105) utili...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com