Patents
Literature
219results about How to "Efficient networking" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
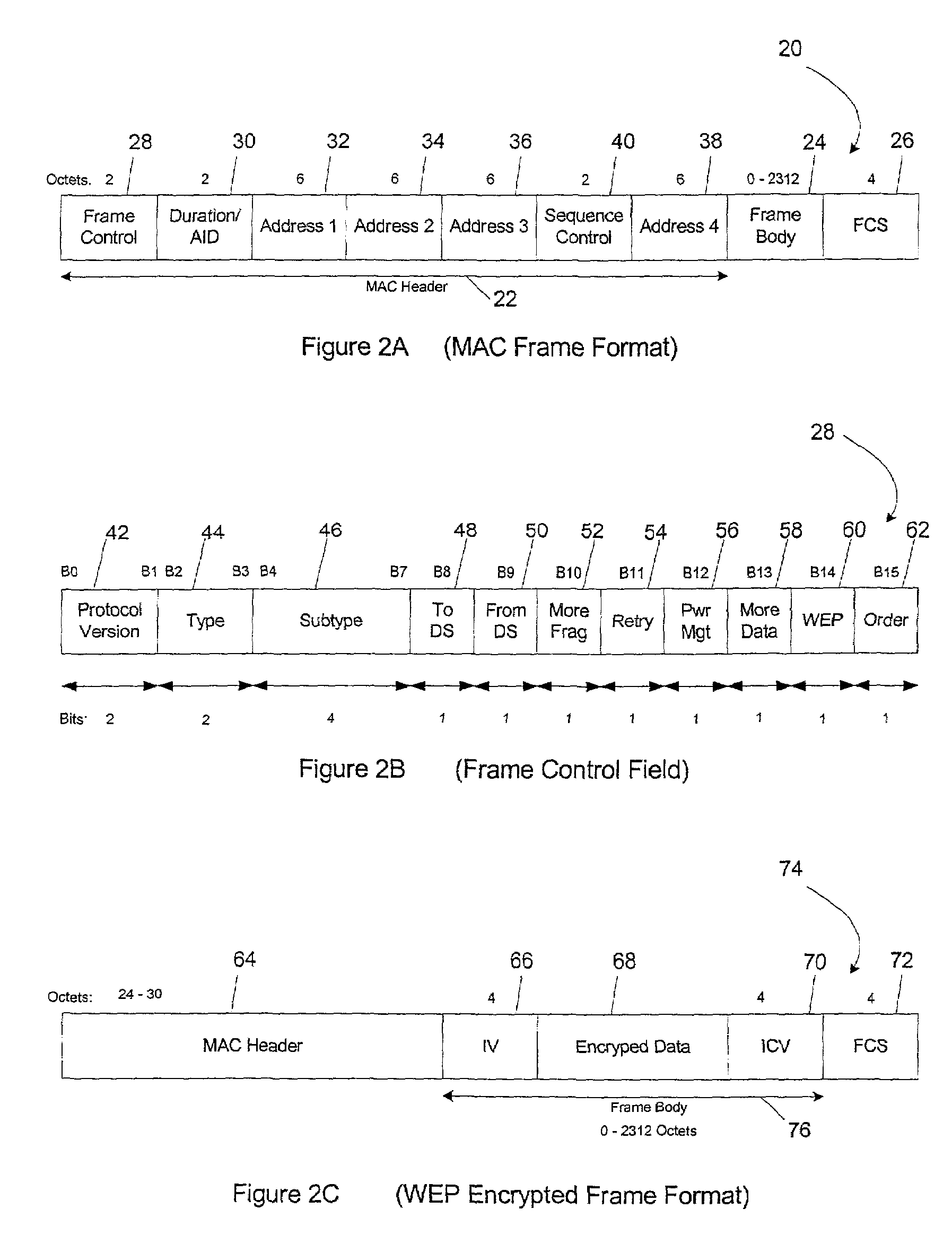
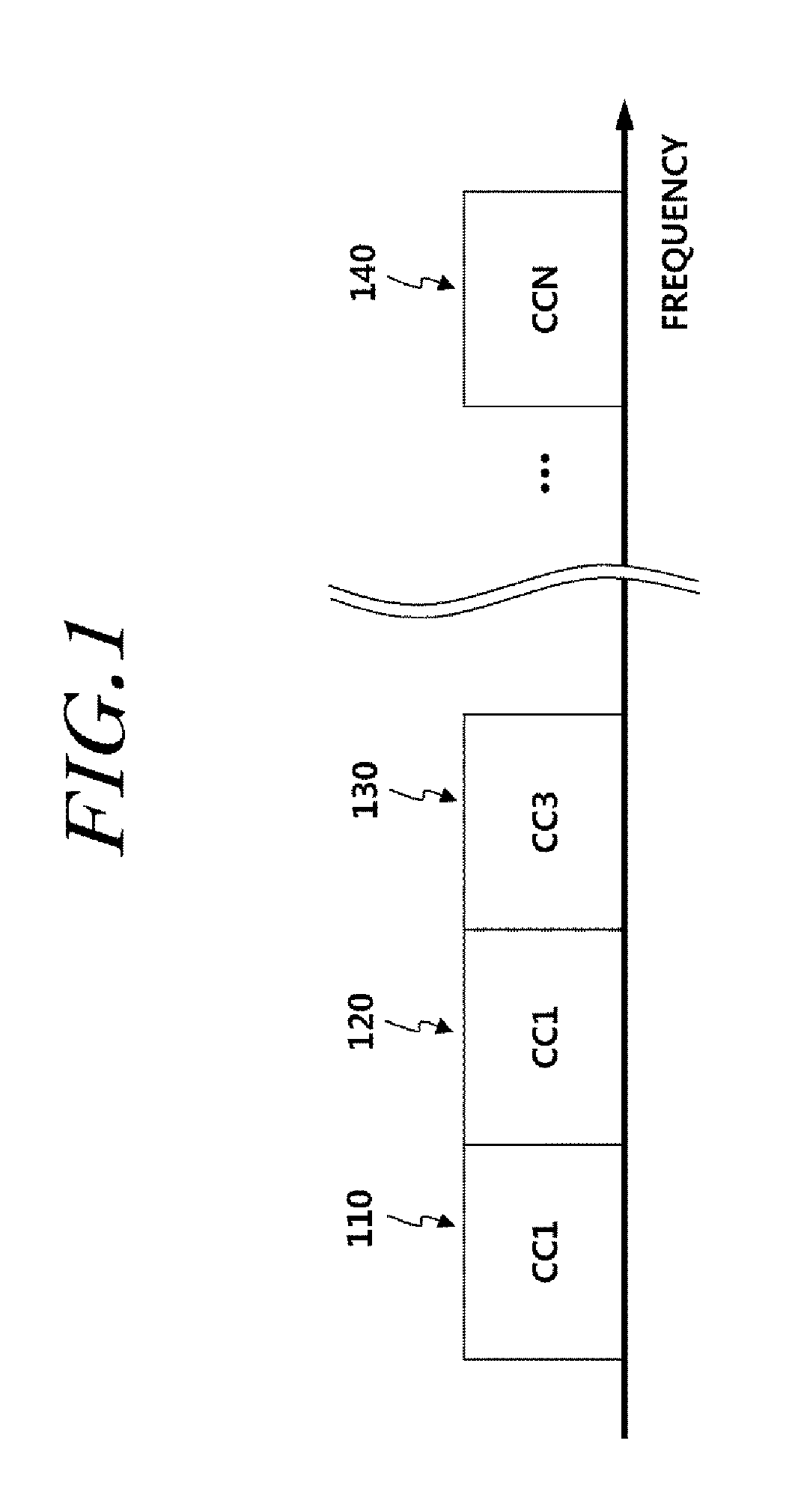
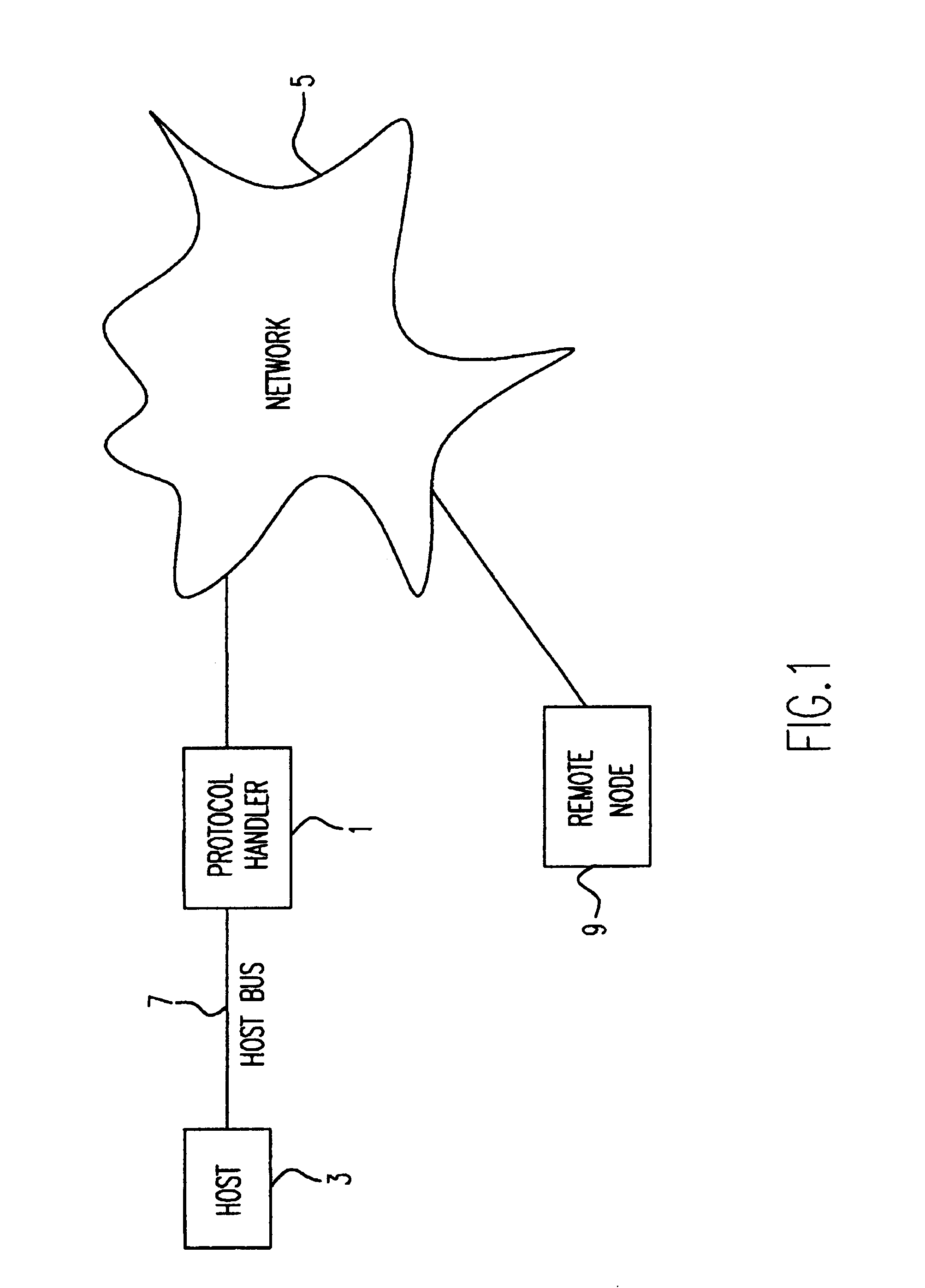
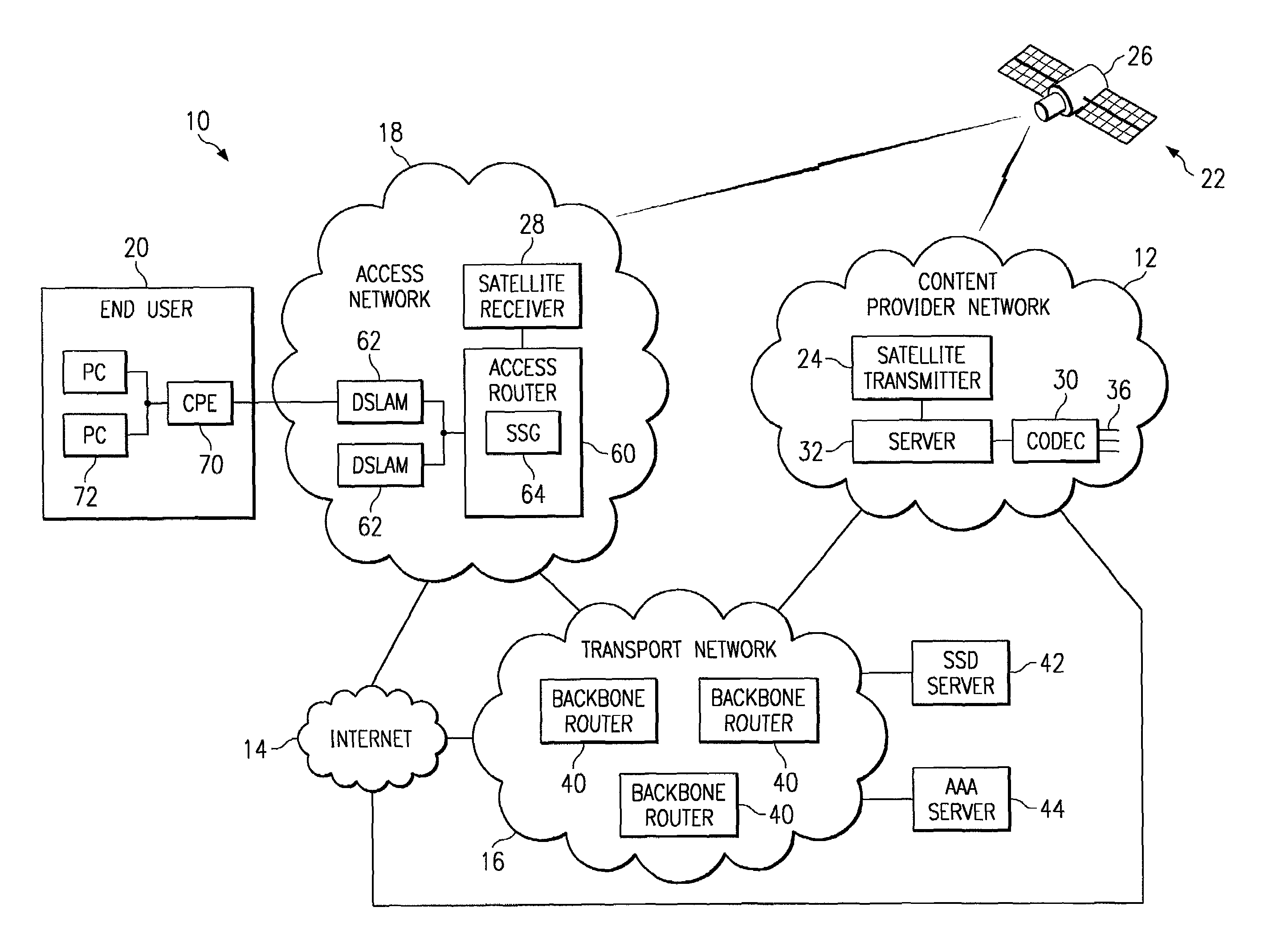
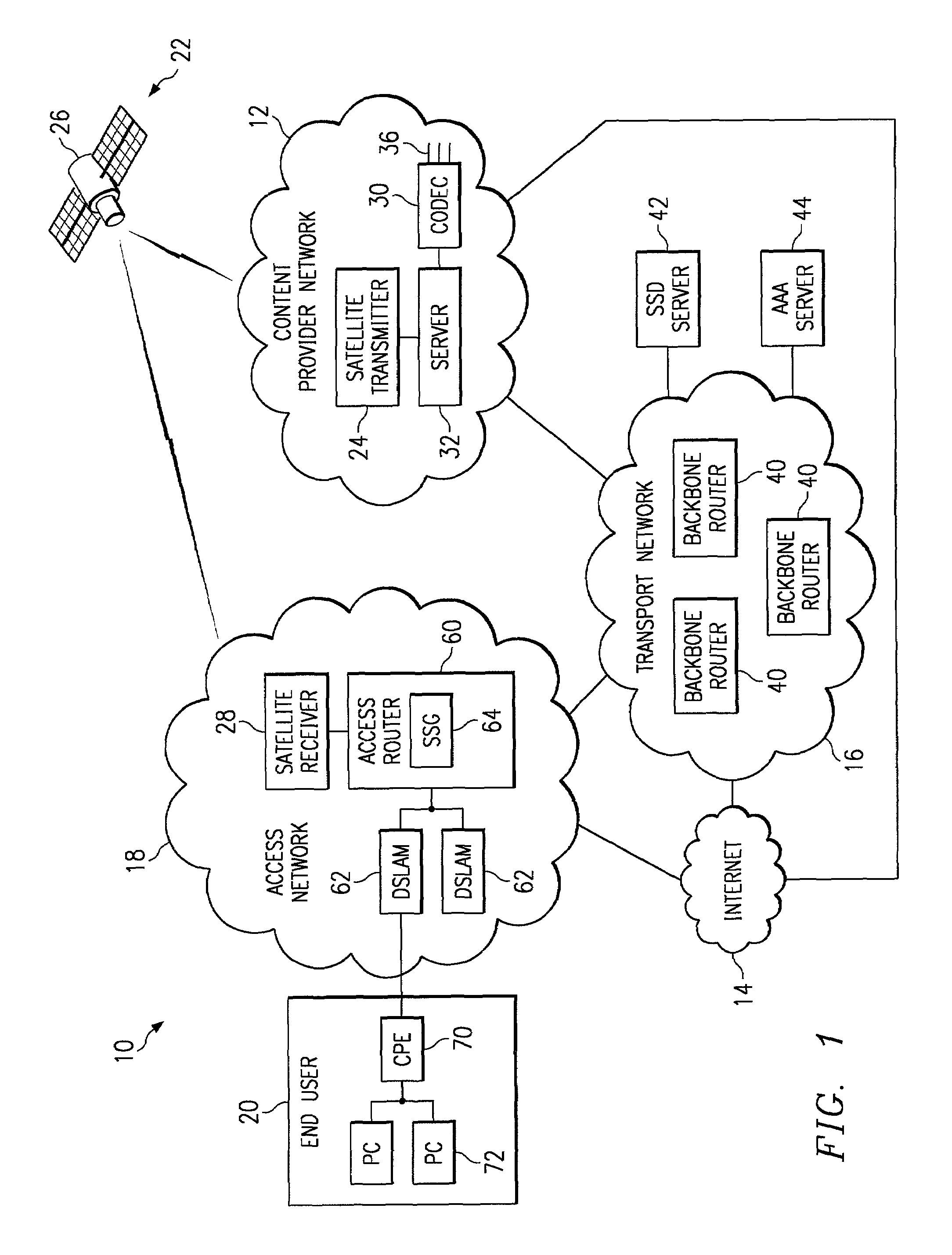
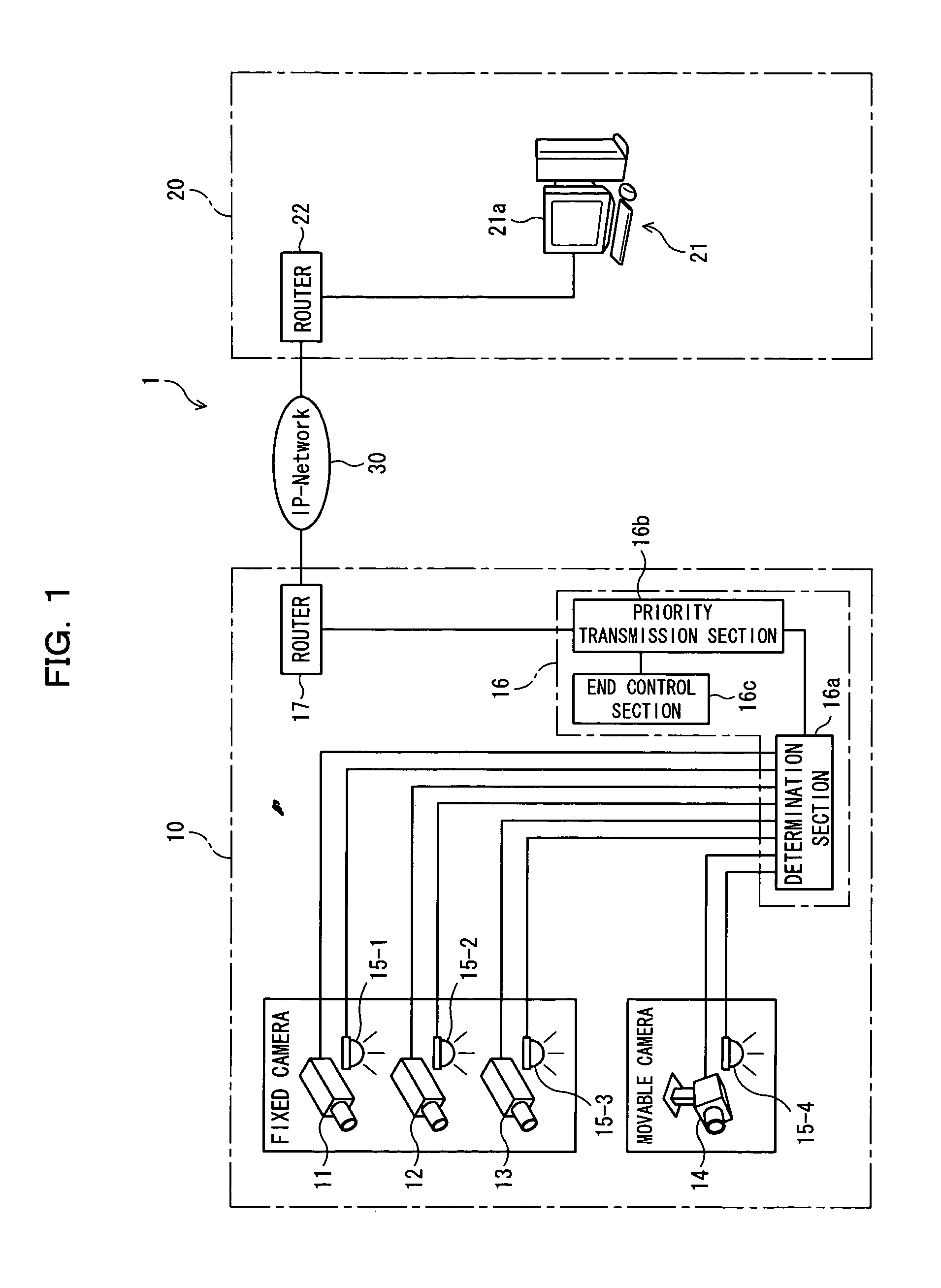
MAC extensions for smart antenna support
ActiveUS20030169769A1Reduce reception errorsLess bitError prevention/detection by using return channelSpatial transmit diversityTelecommunicationsStation
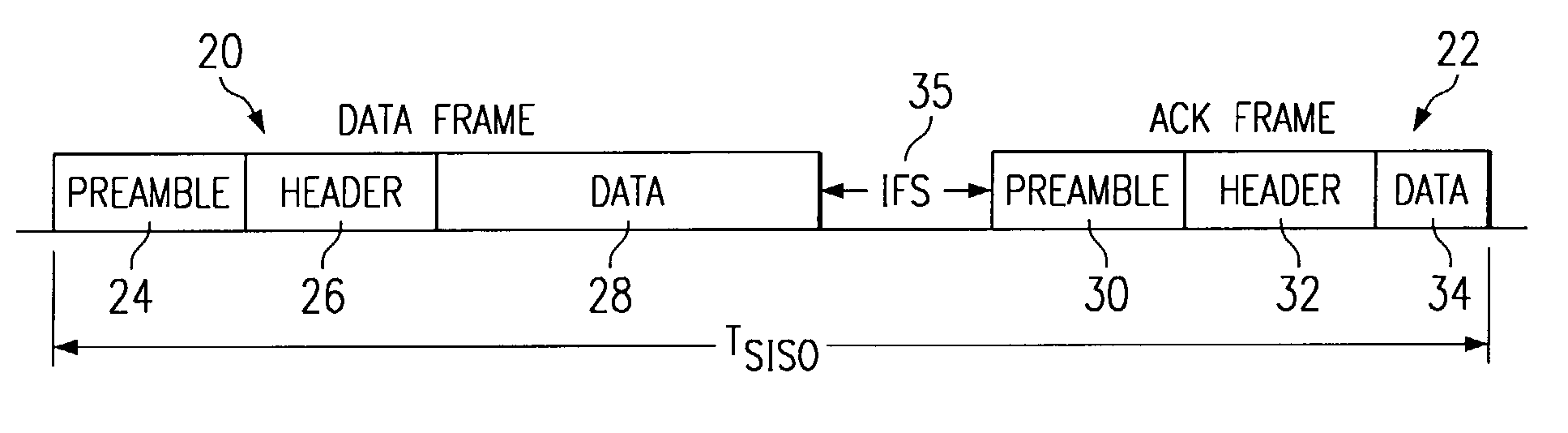
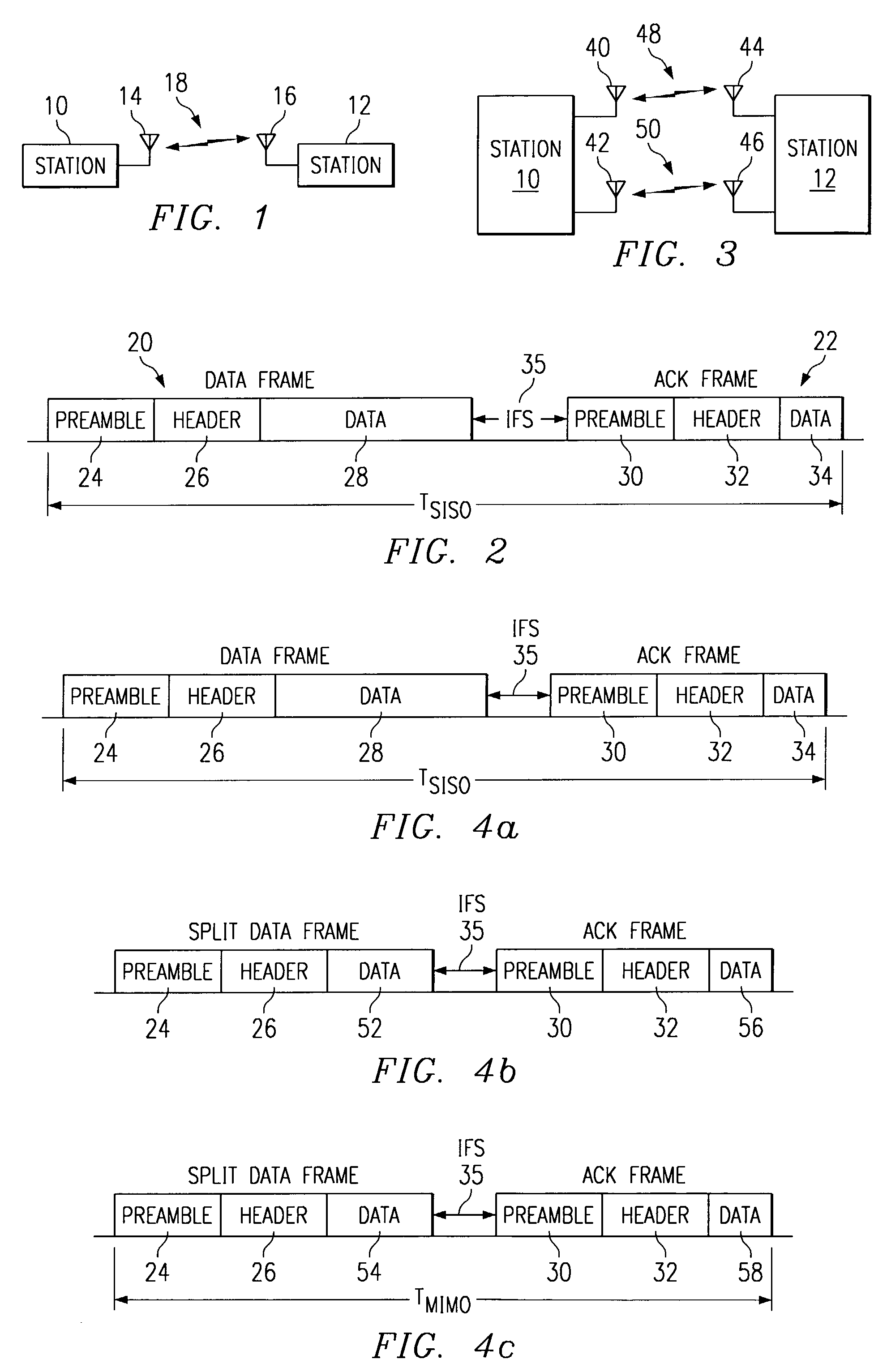
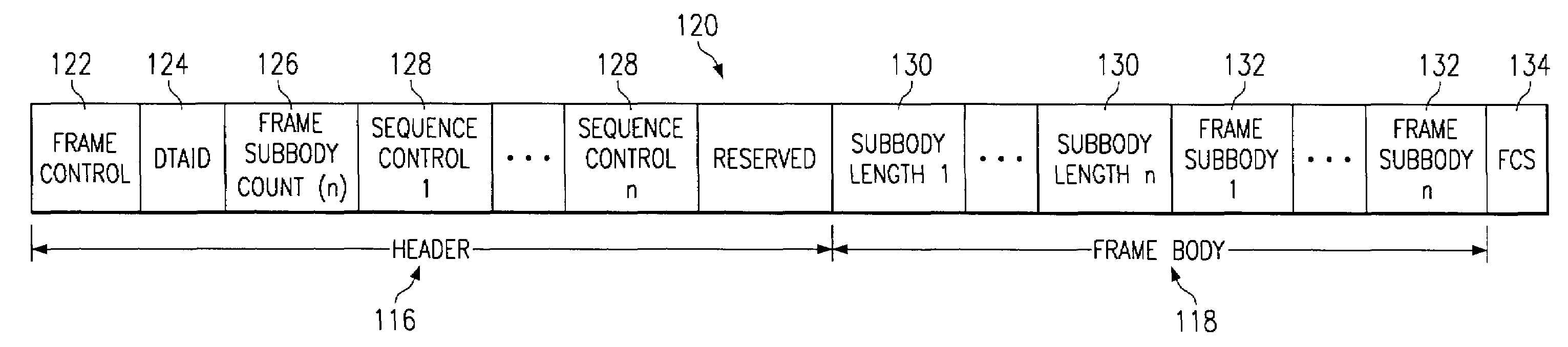
Apparatus and methods implement aggregation frames and allocation frames. The aggregation frames include a plurality of MSDUs or fragments thereof aggregated or otherwise combined together. An aggregation frame makes more efficient use of the wireless communication resources. The allocation frame defines a plurality of time intervals. The allocation frame specifies a pair of stations that are permitted to communicate with each other during each time interval as well as the antenna configuration to be used for the communication. This permits stations to know ahead of time when they are to communicate, with which other stations and the antenna configuration that should be used. A buffered traffic field can also be added to the frames to specify how much data remains to be transmitted following the current frame. This enables network traffic to be scheduled more effectively.
Owner:TEXAS INSTR INC
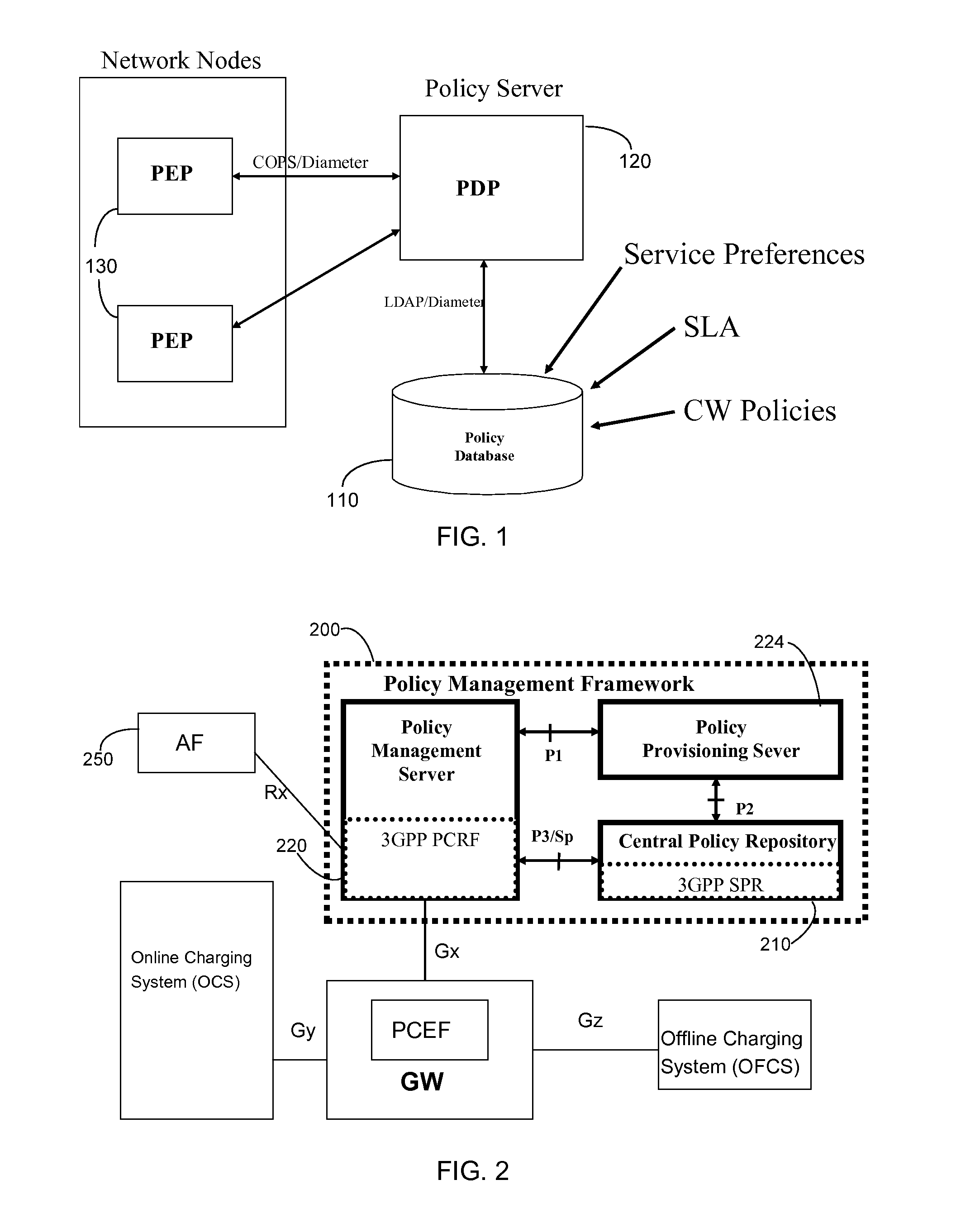
Cascading Policy Management Deployment Architecture
InactiveUS20090113514A1Improve performanceLimitation is enforcedError preventionTransmission systemsPolicy decisionWireless mesh network
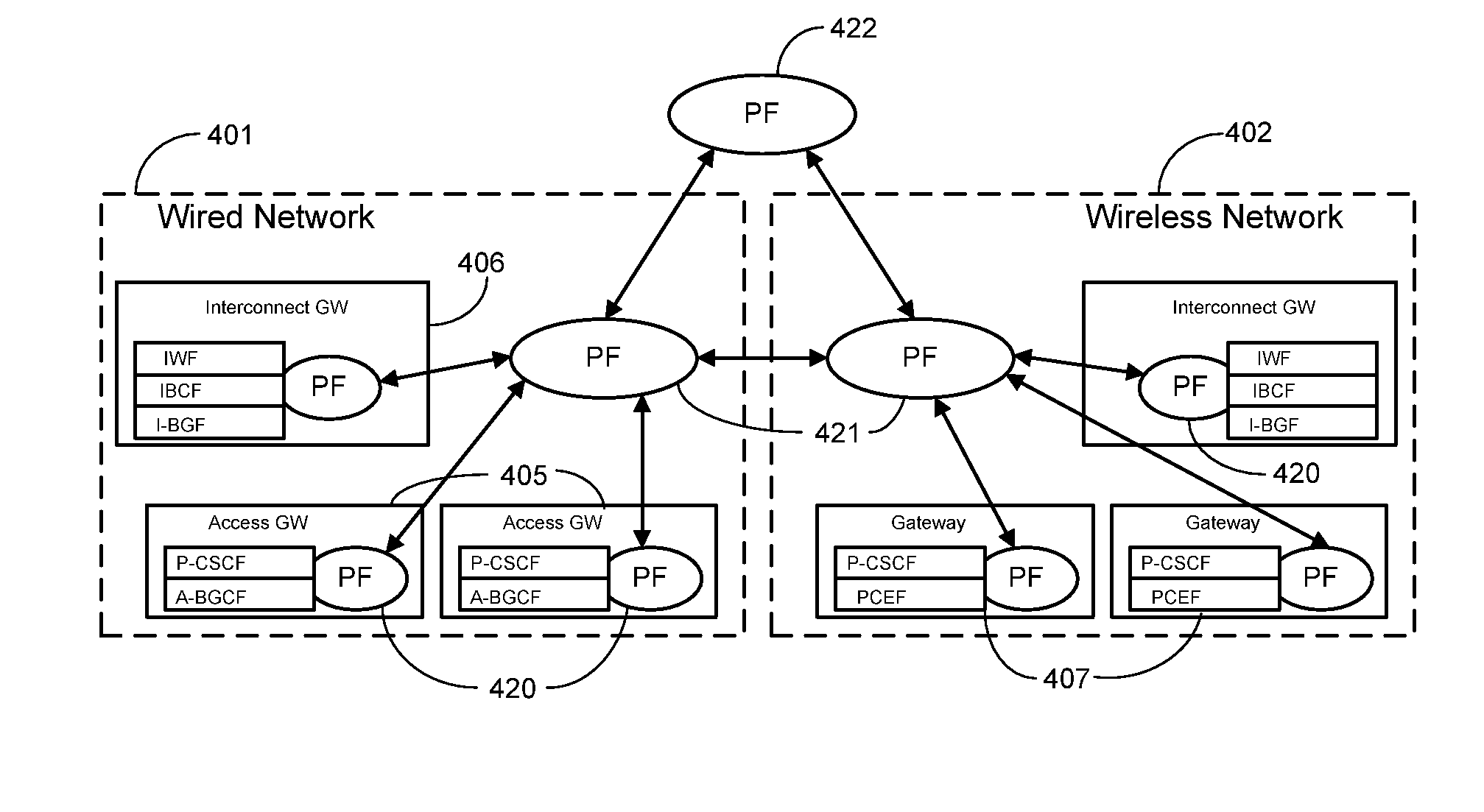
Systems and methods are provided to implement a dynamic and efficient cascading policy management framework architecture for both wired and wireless networks. A plurality of Policy Functions (PFs) are assigned to a plurality of Policy Enforcement Points (PEP). The PFs make decisions regarding local policy control at the specific PEP. The PFs then delegate the policy requests or IP flows to a separate PEP that is more conducive to enforcing that policy request. Thus, policy decisions are made at the point where the most information is available, leading to fewer policy requests traversing back and forth across a network. Additionally, this cascading Policy Management Framework Architecture allows for unified policy management across multiple types of networks, including wired (Internet) and wireless (UMTS).
Owner:AT&T MOBILITY II LLC
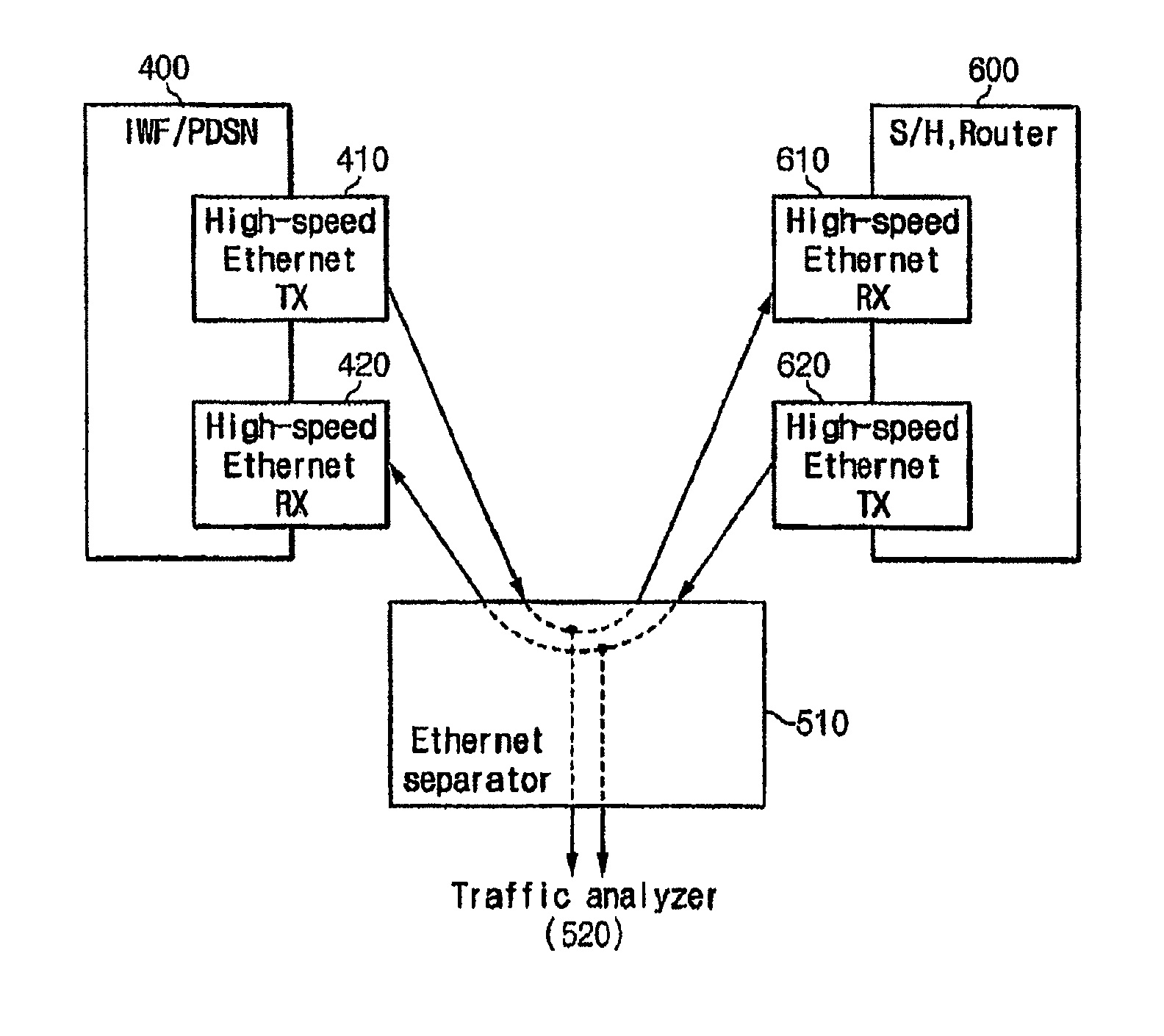
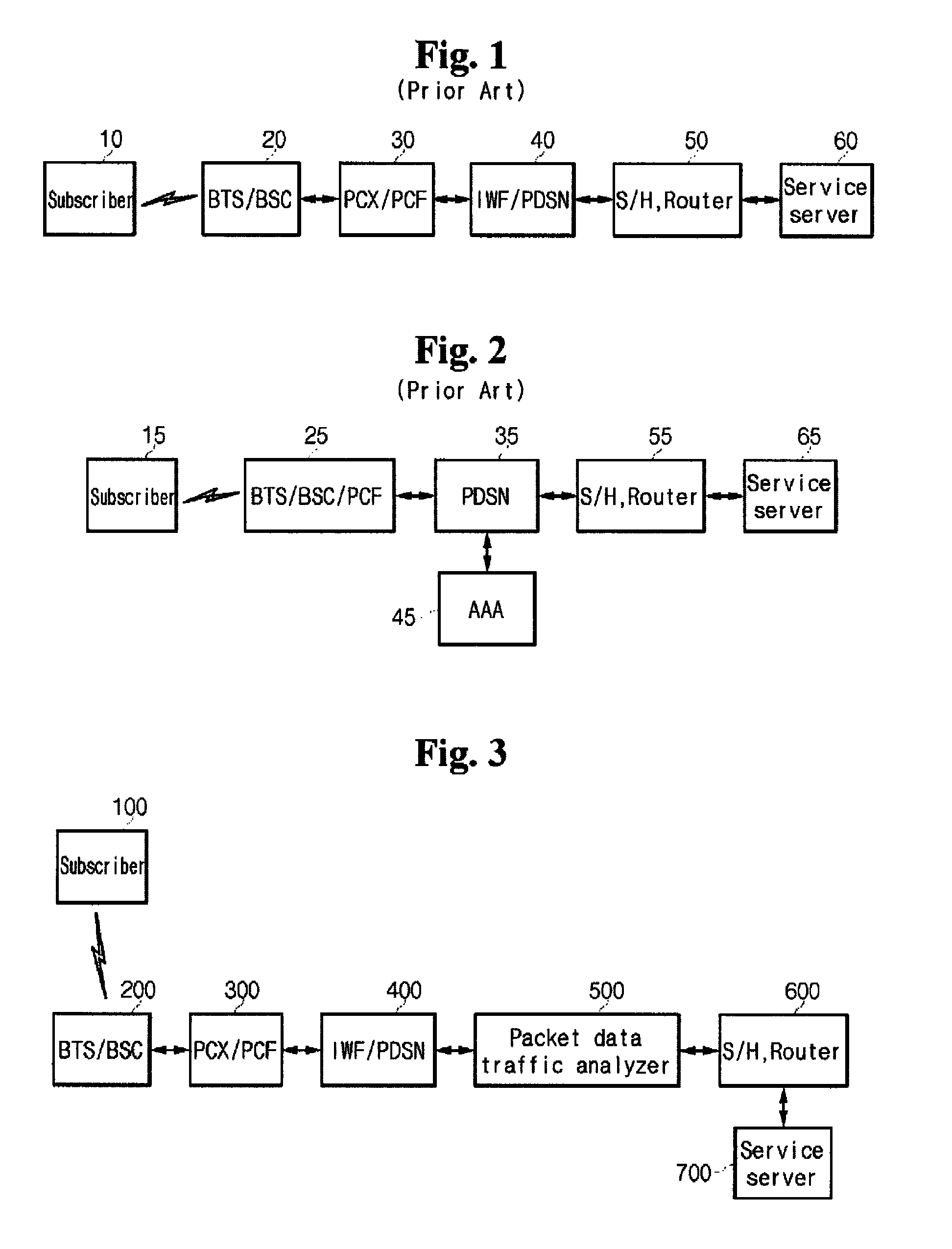
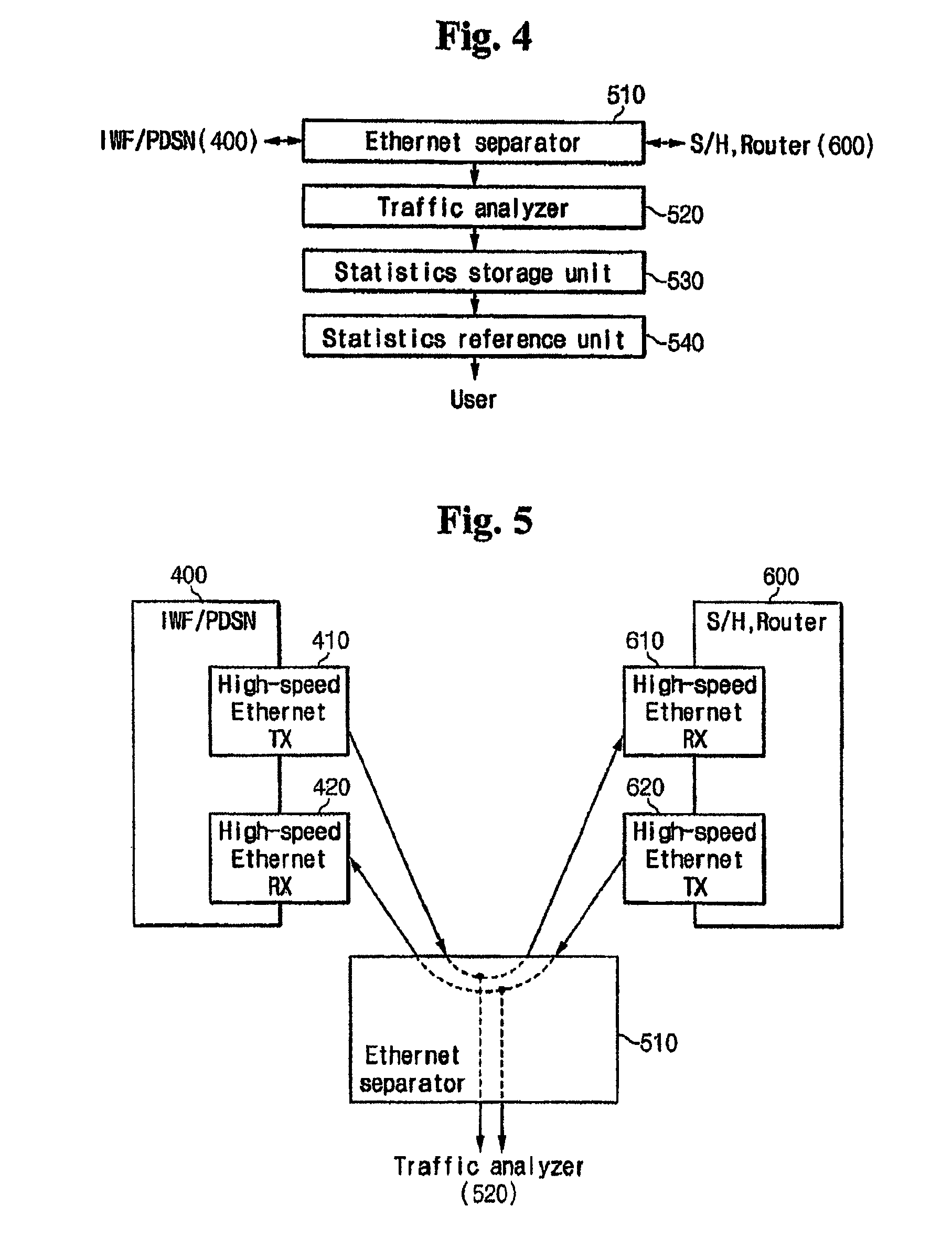
Apparatus for analyzing the packet data on mobile communication network and method thereof
InactiveUS8180881B2Easy to analyzeEfficient networkingMetering/charging/biilling arrangementsMultiple digital computer combinationsTraffic capacityWireless data services
A packet data analyzer on a mobile communication network for analyzing packet data traffic, monitoring services, generating billing information per data service, and monitoring the network based on a protocol analysis, comprises a packet data separator provided between one of a mobile communication exchange and a packet controller that provide a wireless data service to the subscriber, and the service server, for separating user packet data transmitted between one of the mobile communication exchange and the packet controller and the service server, and receiving the user packet data; a traffic analyzer for separating the user packet data received through the packet data separator according to transmission directions, and analyzing the user packet data; a statistics storage unit for storing and managing result data analyzed by the traffic analyzer; and a statistics reference unit for retrieving data stored in the statistics storage unit, and providing statistical information desired by the user.
Owner:KT CORP
Method and apparatus for detailed protocol analysis of frames captured in an IEEE 802.11 (b) wireless LAN
ActiveUS7016948B1Efficient networkingAssisting maintenanceDigital computer detailsTransmissionTroubleshootingReal-time computing
A wireless network troubleshooting tool for monitoring an IEEE 802.11 wireless LAN is connected via an access point to the latter, and programmed for capturing a plurality of frames data packets traveling to and from the LAN, for performing a detailed protocol analysis on the contents of the headers associated with the captured frames, to detect and diagnose failures or defects in the monitored wireless networks, to permit repair.
Owner:MCAFEE LLC
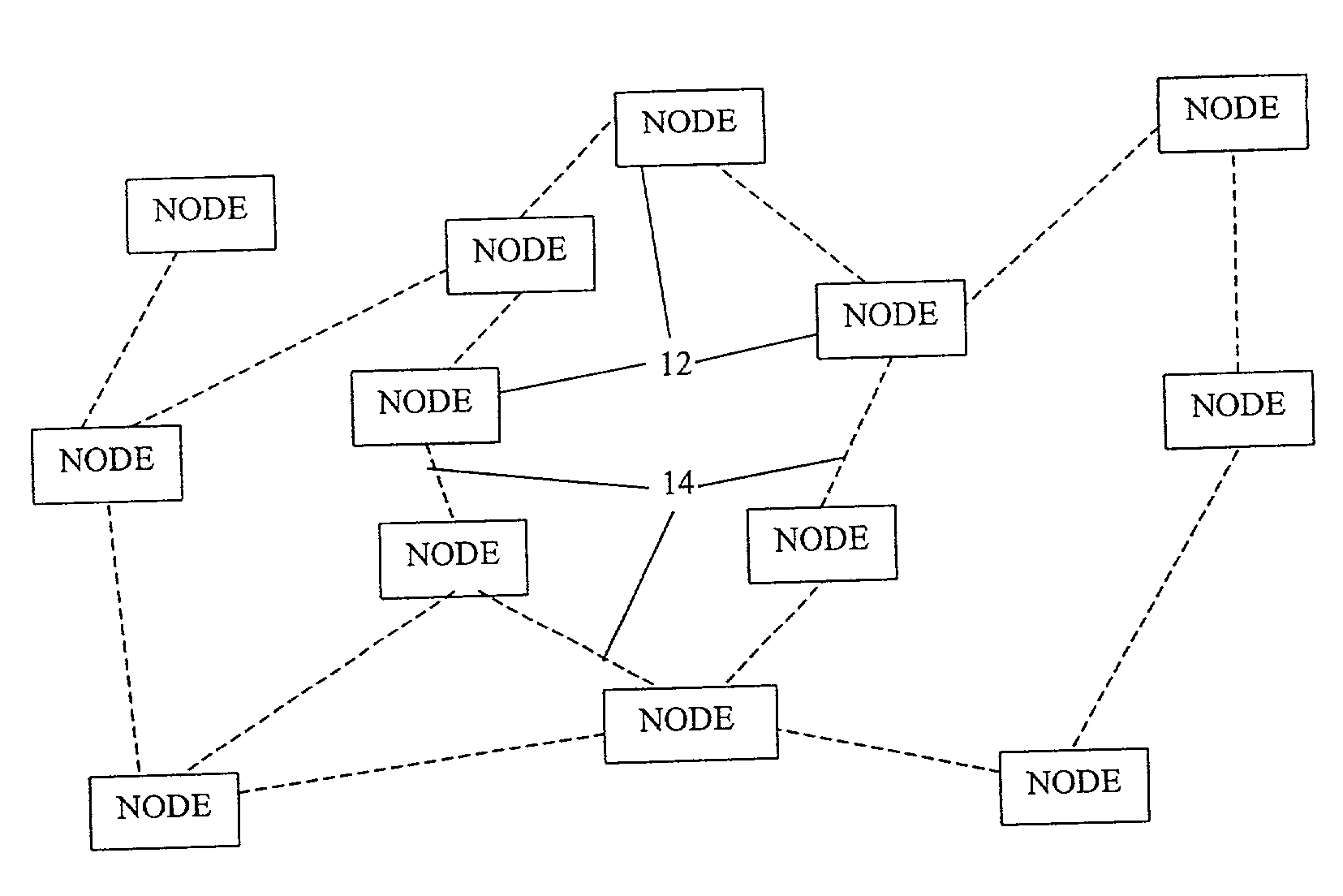
Adaptive topology discovery in communication networks
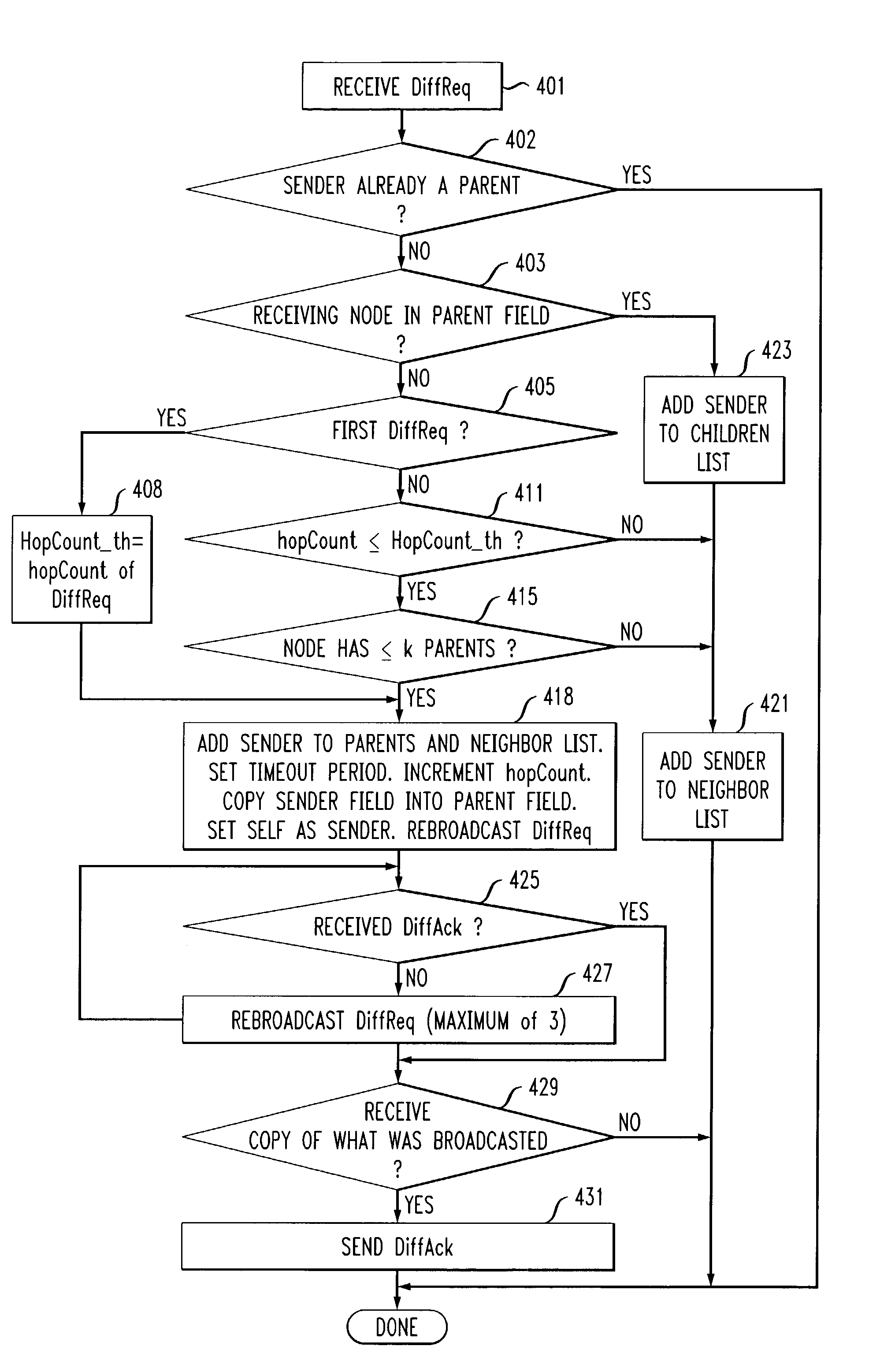
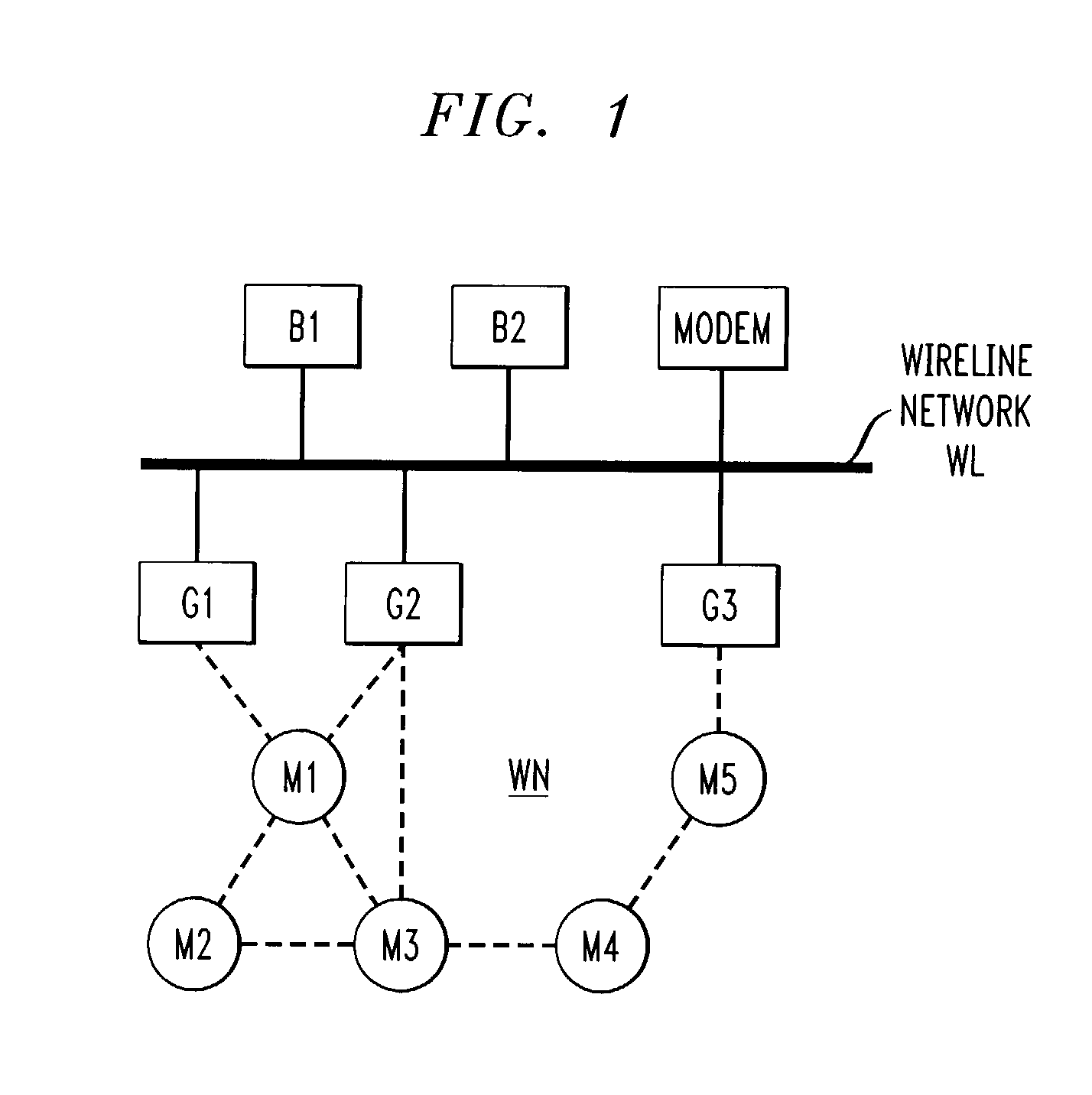
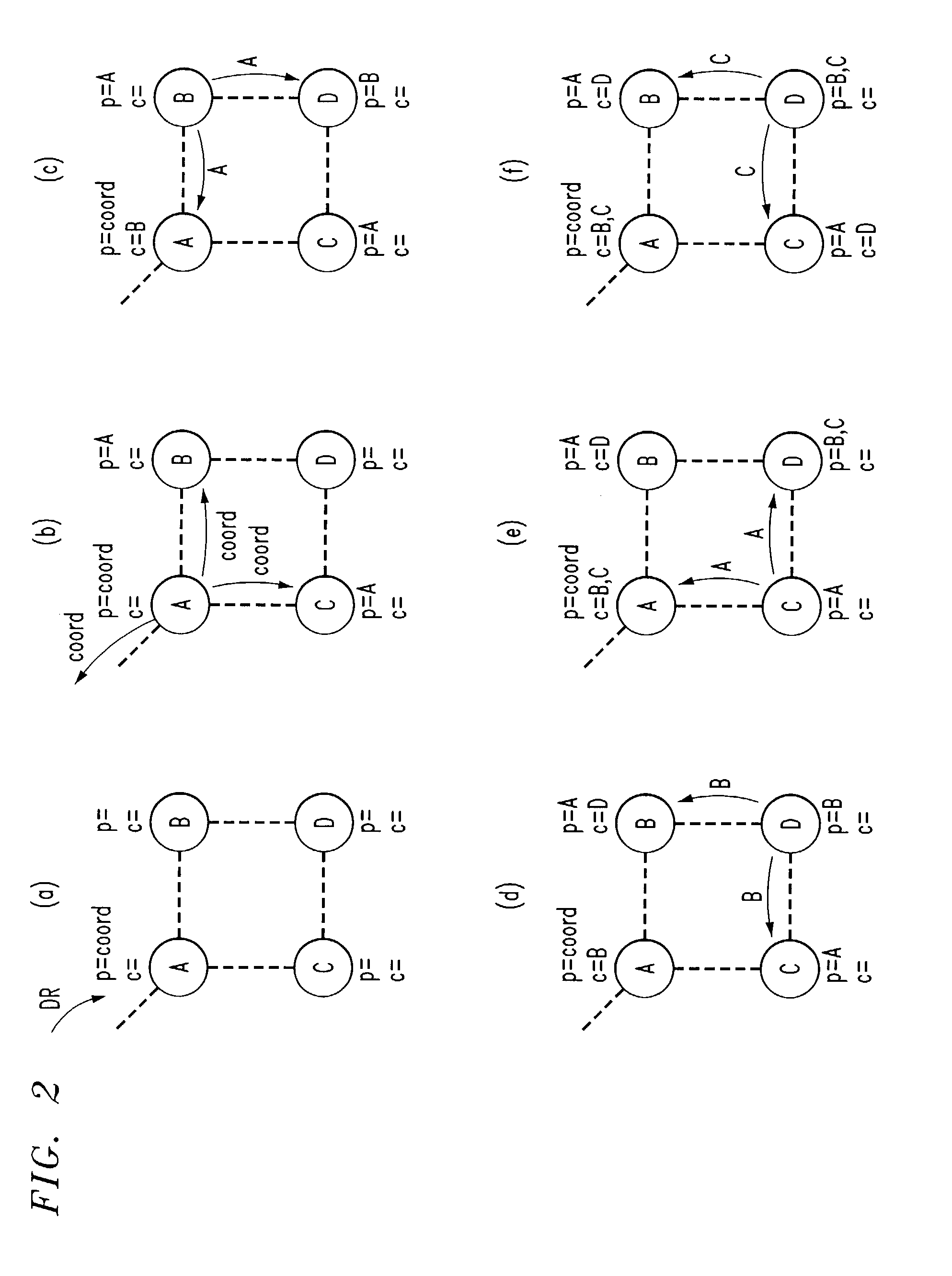
InactiveUS7366113B1Increase elasticityImprove robustnessData switching by path configurationWireless communicationRouting tableTopology information
A topology discovery process is used to discover all of the links in an ad hoc network and thereby ascertain the topology of the entire network. One of the nodes of the network, referred to as the coordinator, receives the topology information which can then be used to, for example, distribute a routing table to each other node of the network. The process has a Diffusion phase in which a k-resilient mesh, k>1, is created by propagating a topology request message through the network. Through this process, the nodes obtain information from which they are able to discern their local neighbor information. In a subsequent, Gathering phase, the local neighbor information is reported upstream from a node to its parents in the mesh and thence to the parents' parents and so forth back to the coordinator. The robustness of the Diffusion phase is enhanced by allowing a node to have more than one parent as well as by a number of techniques, including use of a so-called diffusion acknowledgement message. The robustness of the Gathering phase is enhanced by a number of techniques including the use of timeouts that ensure that a node will report its neighbor information upstream even if it never receives neighbor information from one or more downstream neighbors and the use of a panic mode that enhances the probability that a node will get its neighbor information, and its descendents' neighbor information, reported upstream even if that node has lost connectivity with all of its parents.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Mesh network and piconet work system and method
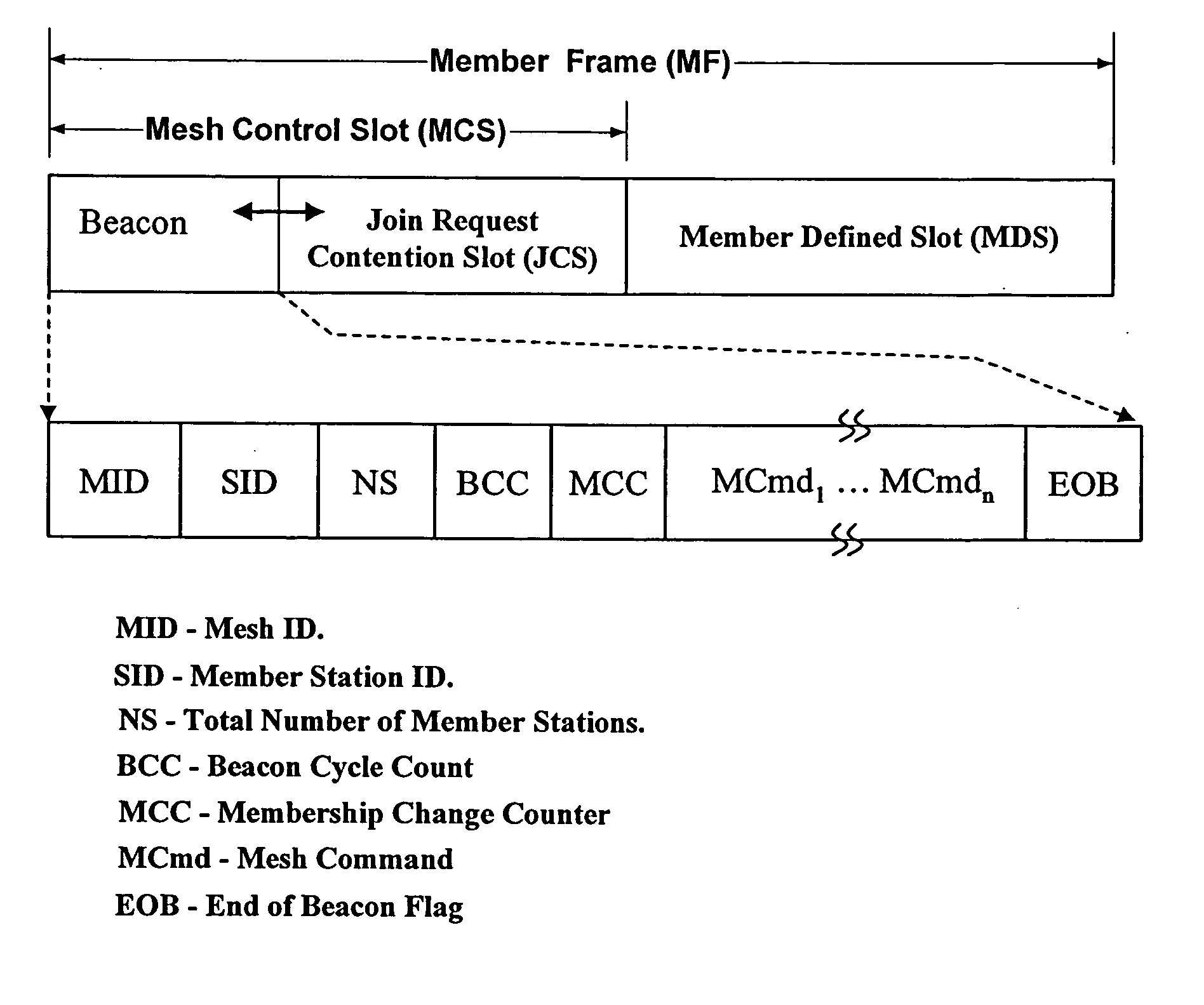
InactiveUS20050243765A1Removed positioningEfficient networkingNetwork traffic/resource managementAssess restrictionGlobal topologyWireless mesh network
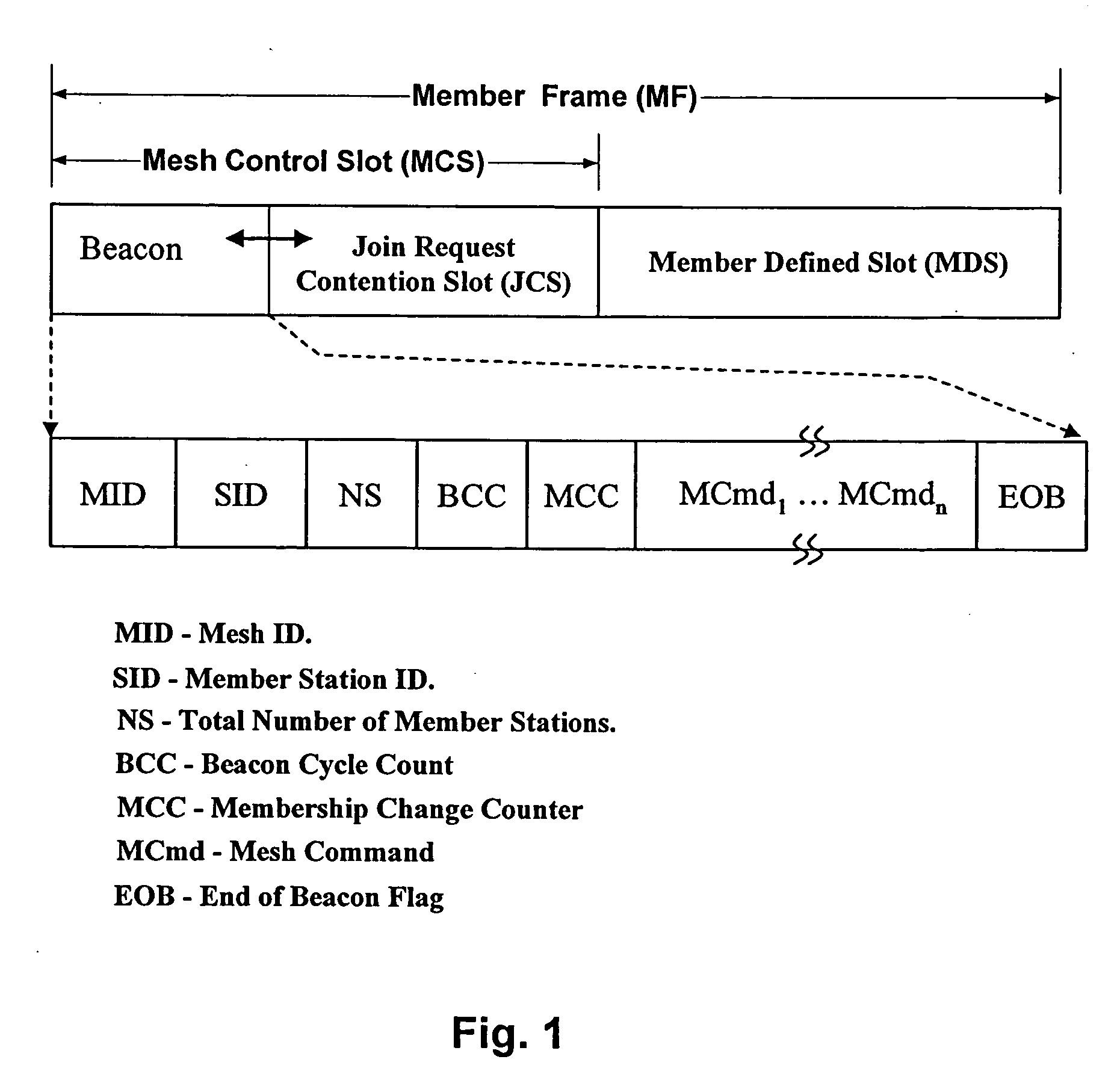
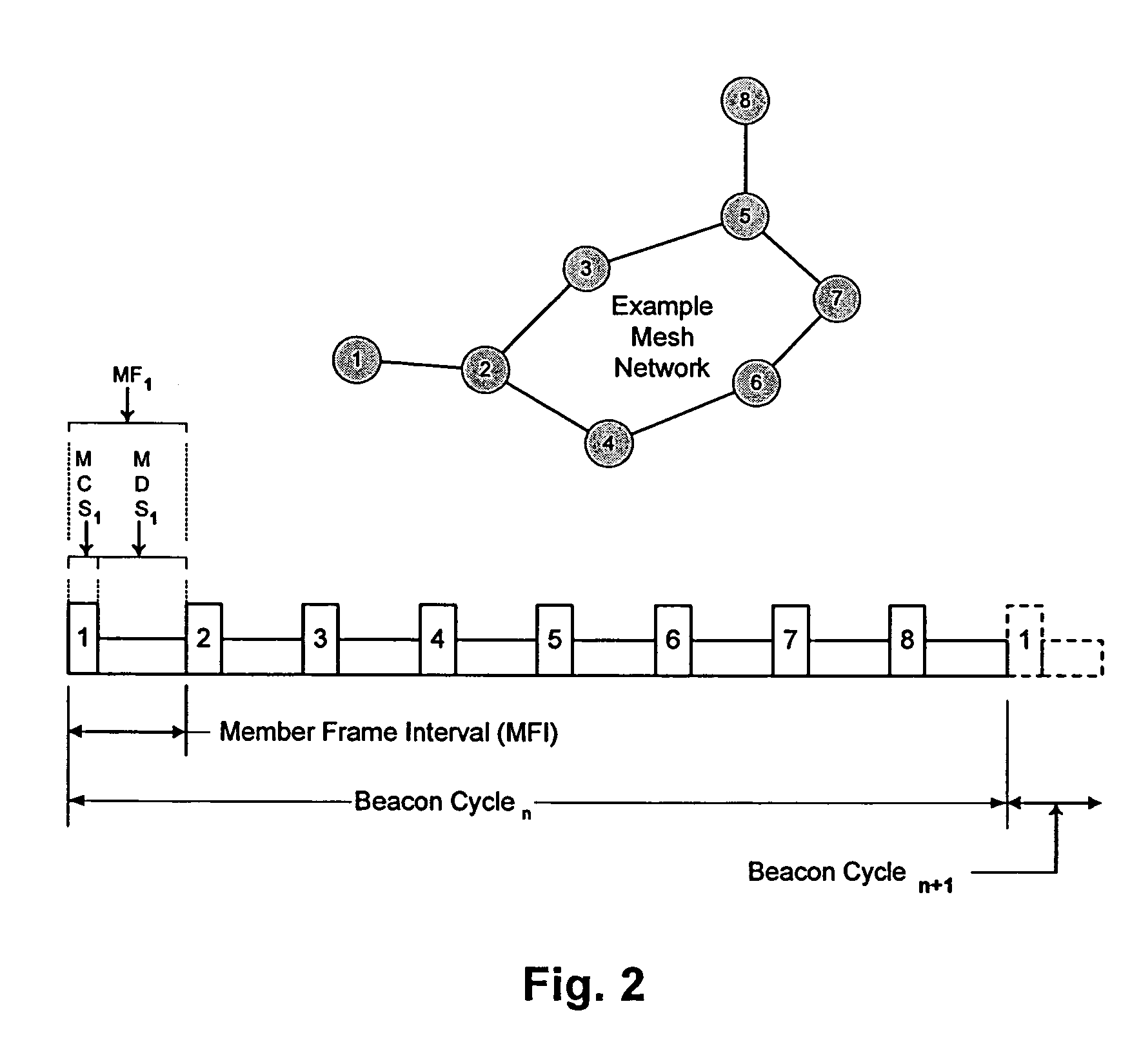
A method of distributed control of a wireless mesh network without knowledge of global topology. The method includes: a station joining the network with any current member by propagating the join-request, or two meshes merging using the steps of: one mesh joining the other as a whole and then re-synchronizing its timing. The method further includes: first, each station periodically transmits a beacon; second, in response to a beacon being no longer detected, a station transmitting a bitmap of stations that it can still receive; third, each station responds by adding stations that it can receive with all of the bitmaps received from other members, and retransmitting the updated bitmap; fourth, after time for all stations to respond, all stations base current membership on the bitmap. The method further includes: determining sharable time slots that will not interfere with neighbors or other slot sharers, using and then releasing those slots.
Owner:ASTER WIRELESS
Wavelocker for Improving Laser Wavelength Accuracy in WDM Networks
InactiveUS20110135301A1Easy mappingMaintaining full visibilityMultiplex system selection arrangementsWavelength-division multiplex systemsLasing wavelengthOptoelectronics
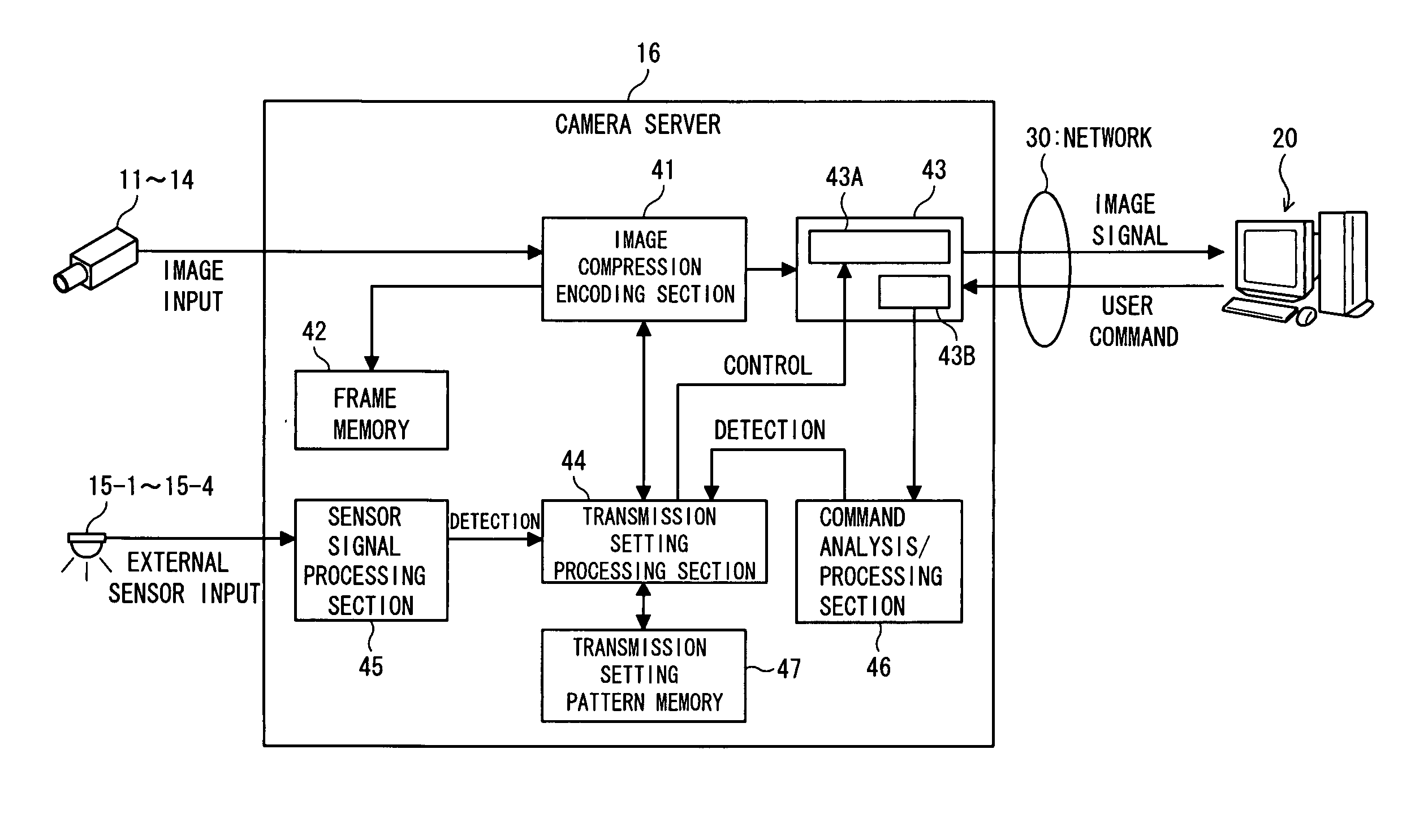
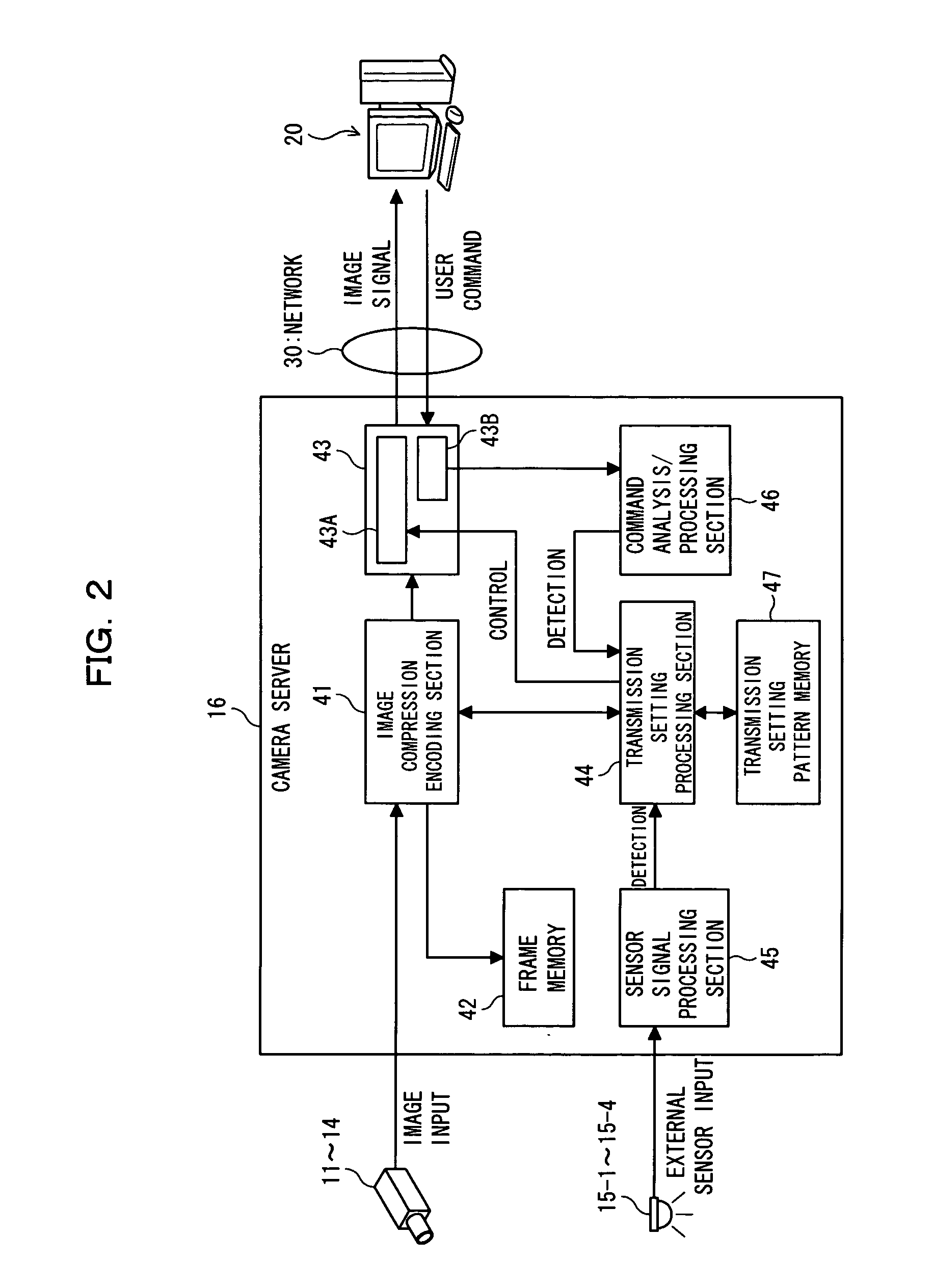
The present invention includes novel techniques, apparatus, and systems for optical WDM communications. Various wavelocker apparatus and methods are disclosed that measure the frequency offsets between signal lasers and reference lasers. The measured offsets are used to adjust the signal laser frequencies to meet their target frequencies. The absolute accuracy of the reference laser frequency is improved by measuring the absorption of the reference laser by a gas cell with known fixed absorption lines versus the reference laser frequency. Apparatus and methods are disclosed to cover scenarios in which the reference laser polarization is aligned with the signal lasers, as well as those in which the reference laser polarization is not aligned with the signal lasers. The wavelocker apparatus may or may not be located at the same network site as the signal lasers.
Owner:VELLO SYST +1
Method and apparatus for computing a path through specified elements in a network
InactiveUS7031253B1Effective blockingAmount of timeError preventionFrequency-division multiplex detailsAutomatic routingDistributed computing
Methods and apparatus for automatically creating a circuit path that includes specified elements are disclosed. According to one aspect of the present embodiment, a method for computing a circuit path between a source node and a destination node of a network includes identifying at least a first element that is to be traversed by the circuit path such that the path passes from the source node, traverses the first element, then passes to the destination node. The method also includes routing a first segment of the circuit path automatically such that the source node and the first element are components of the first segment. In one embodiment, routing the first segment automatically includes routing the first segment automatically using a shortest path first algorithm.
Owner:CISCO TECH INC
Method and system for efficient distribution of network event data
ActiveUS7043727B2Reduce amountImproved and efficient techniqueSpecial service provision for substationDigital computer detailsClient-sideData memory
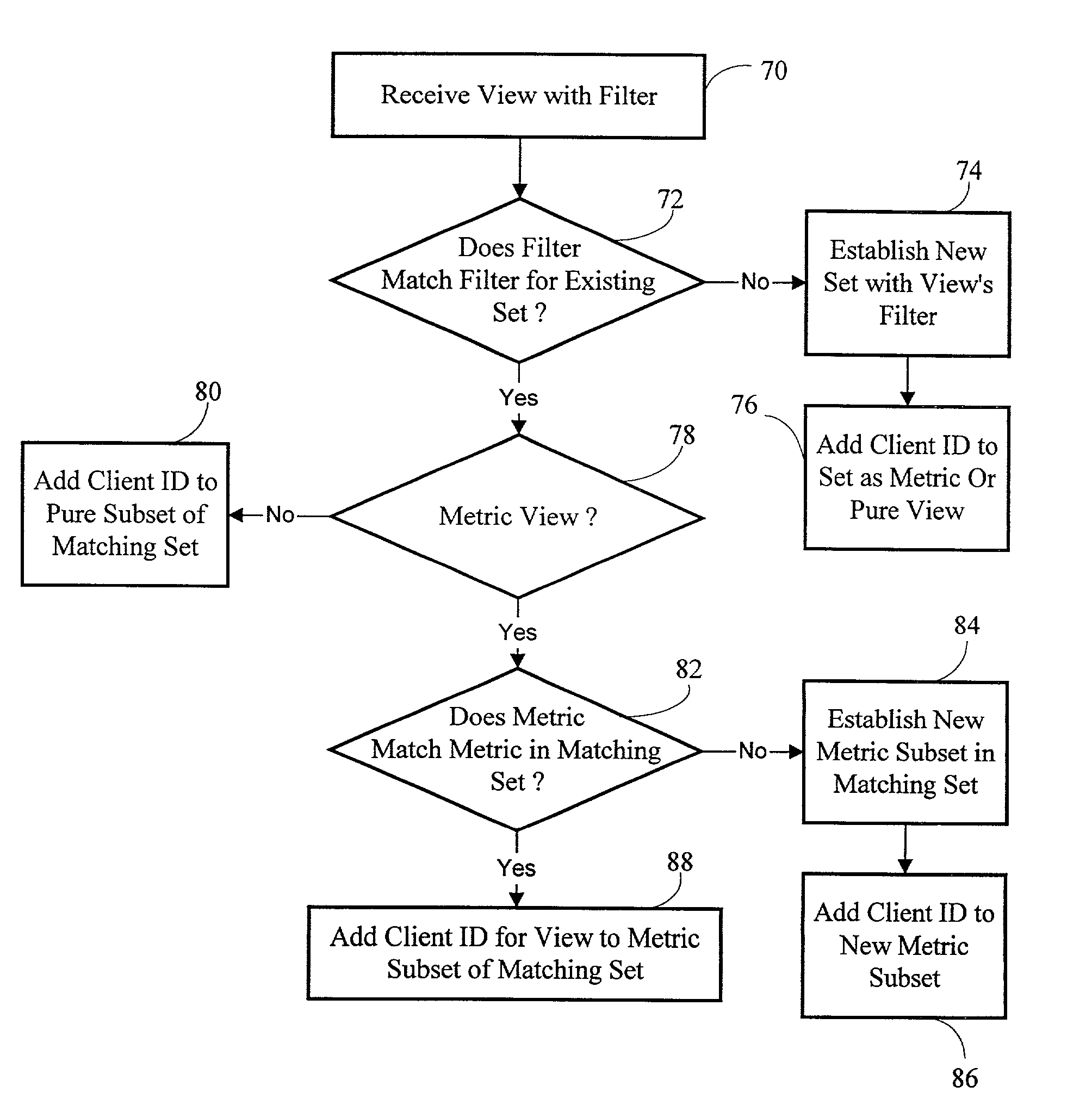
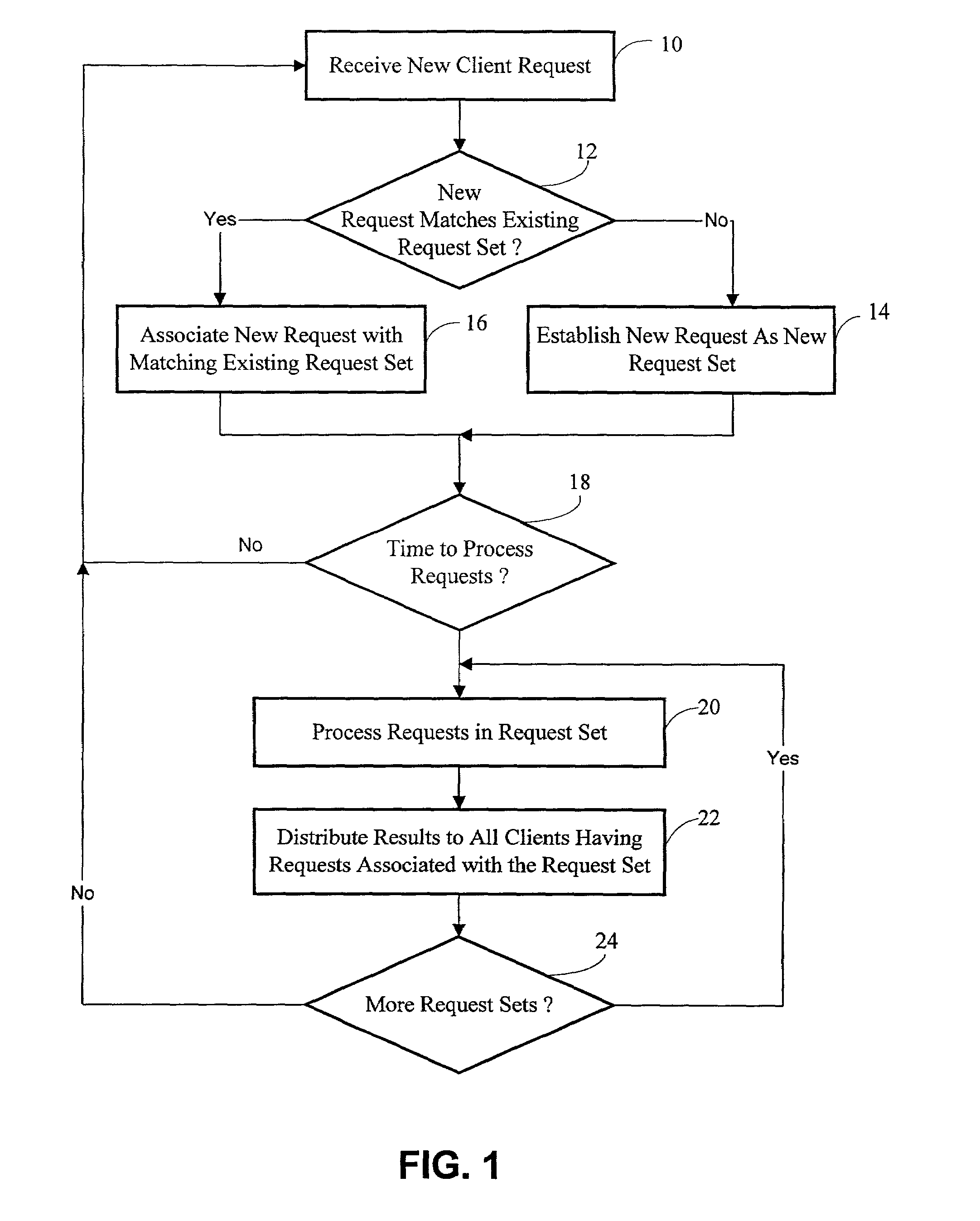
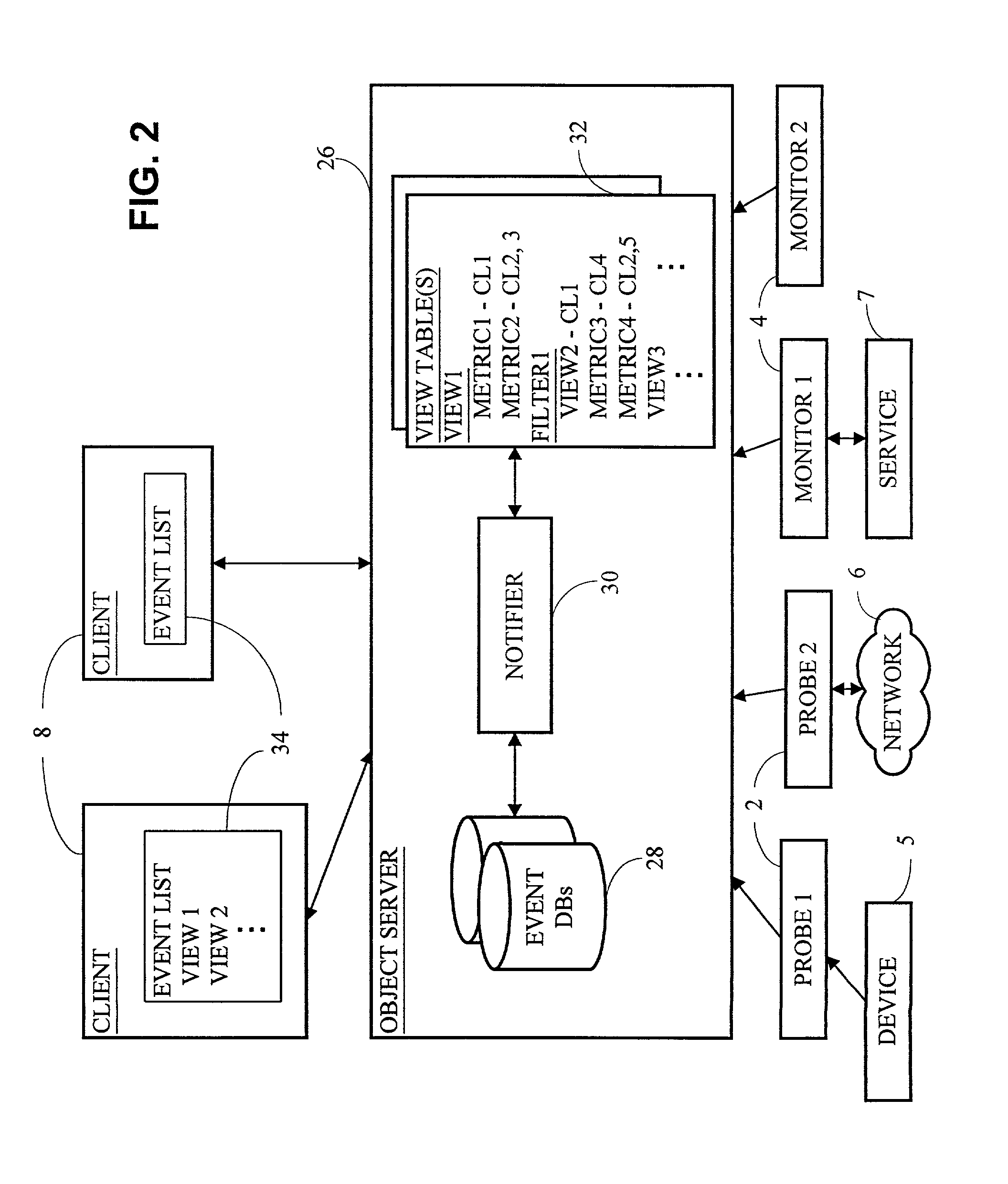
Described herein are methods and systems for preparing to efficiently distribute data to be extracted from a data store to clients and for distributing such prepared data to the clients. The methods and system have particular utility in the context of a network monitoring system which captures and stores network event data and makes the event data available to clients according to any desired view or summary. One method for preparing the data involves storing as primary requests one or more client requests for data to be extracted from the event database. Additional client requests for event are each compared to the stored primary requests to determine whether each additional request matches a stored primary request in accordance with a given criterion, such as a filter or summary formula. If the additional request matches a stored primary request, the additional client request is associated with the matching primary request. If the additional request does not match a stored primary request, the additional request is stored as a new primary request. As a result of this method, client requests which match one another can be processed at once and distributed to all clients registering the request.
Owner:IBM CORP
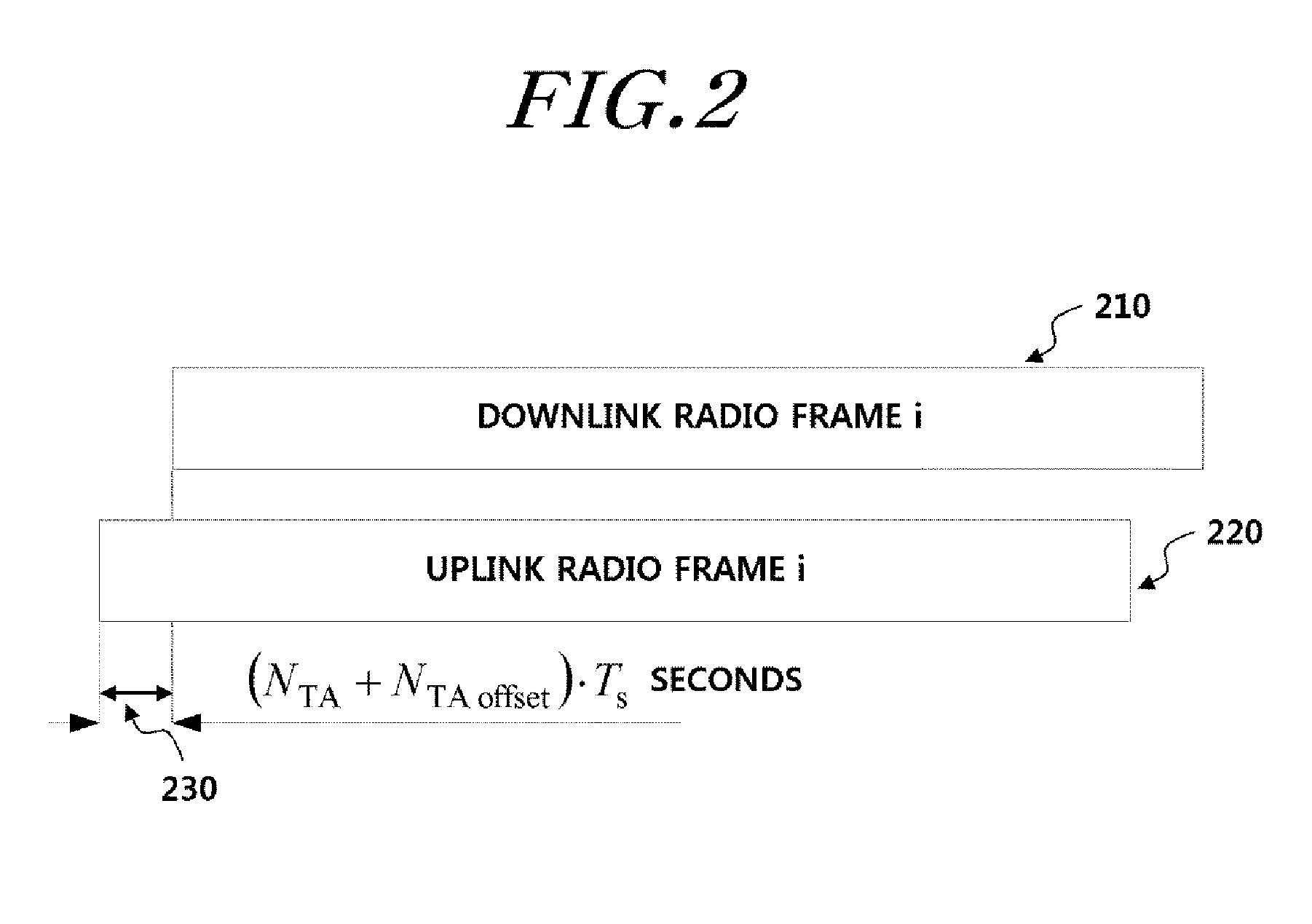
Apparatus and method for establishing uplink synchronization in a wireless communication system
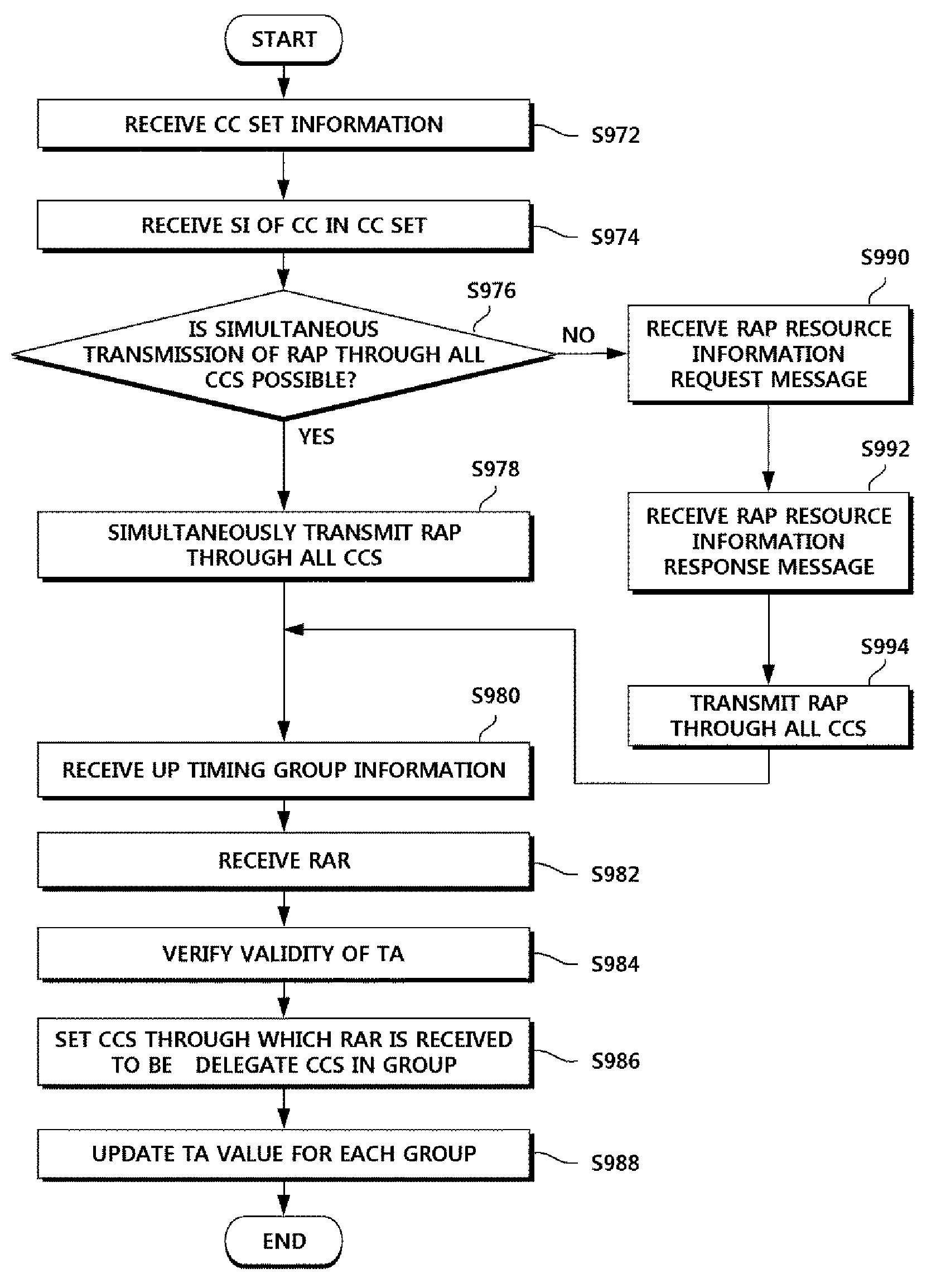
ActiveUS9054835B2Easy to operateProcess safety and stabilitySynchronisation arrangementTransmission path divisionCommunications systemCarrier signal
Uplink synchronization establishment in a base station which operates a plurality of component carriers according to one embodiment of the present description, is performed in that the base station is connected to a user equipment, sets component carrier aggregation information, generates an uplink timing groups in the set component carrier aggregation, and transmits information on the thus-generated uplink timing groups to the user equipment.
Owner:PANTECH CORP
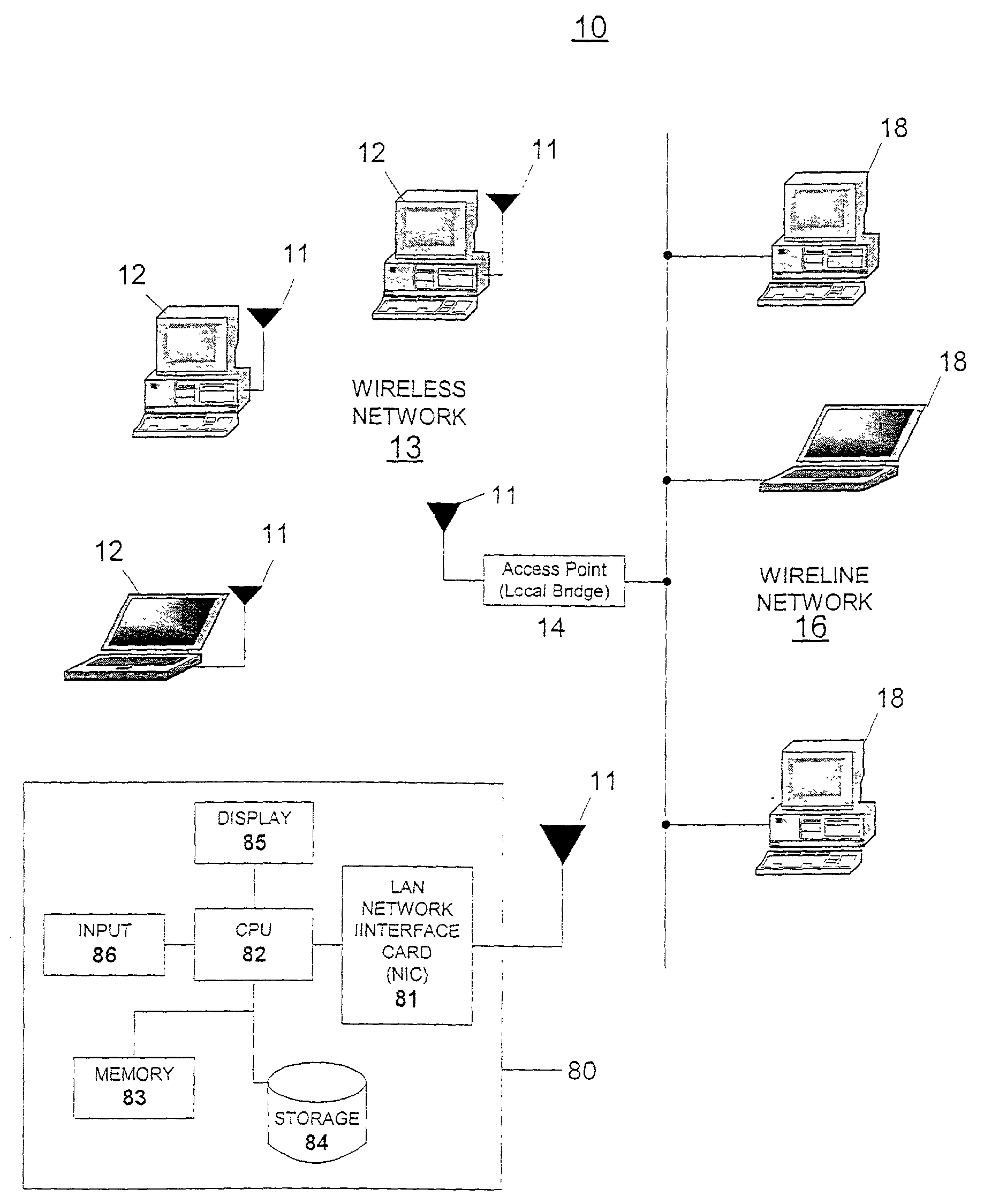
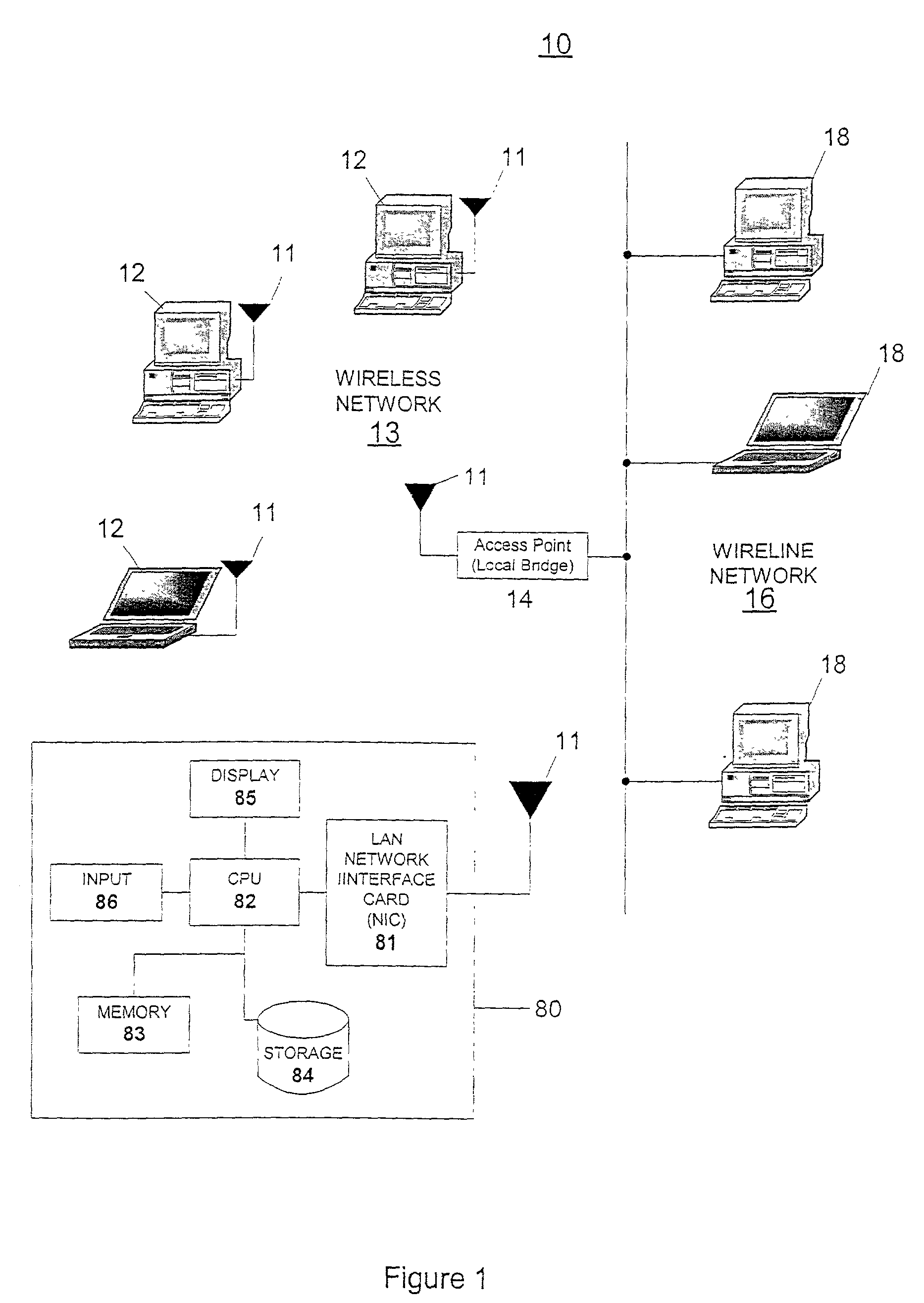
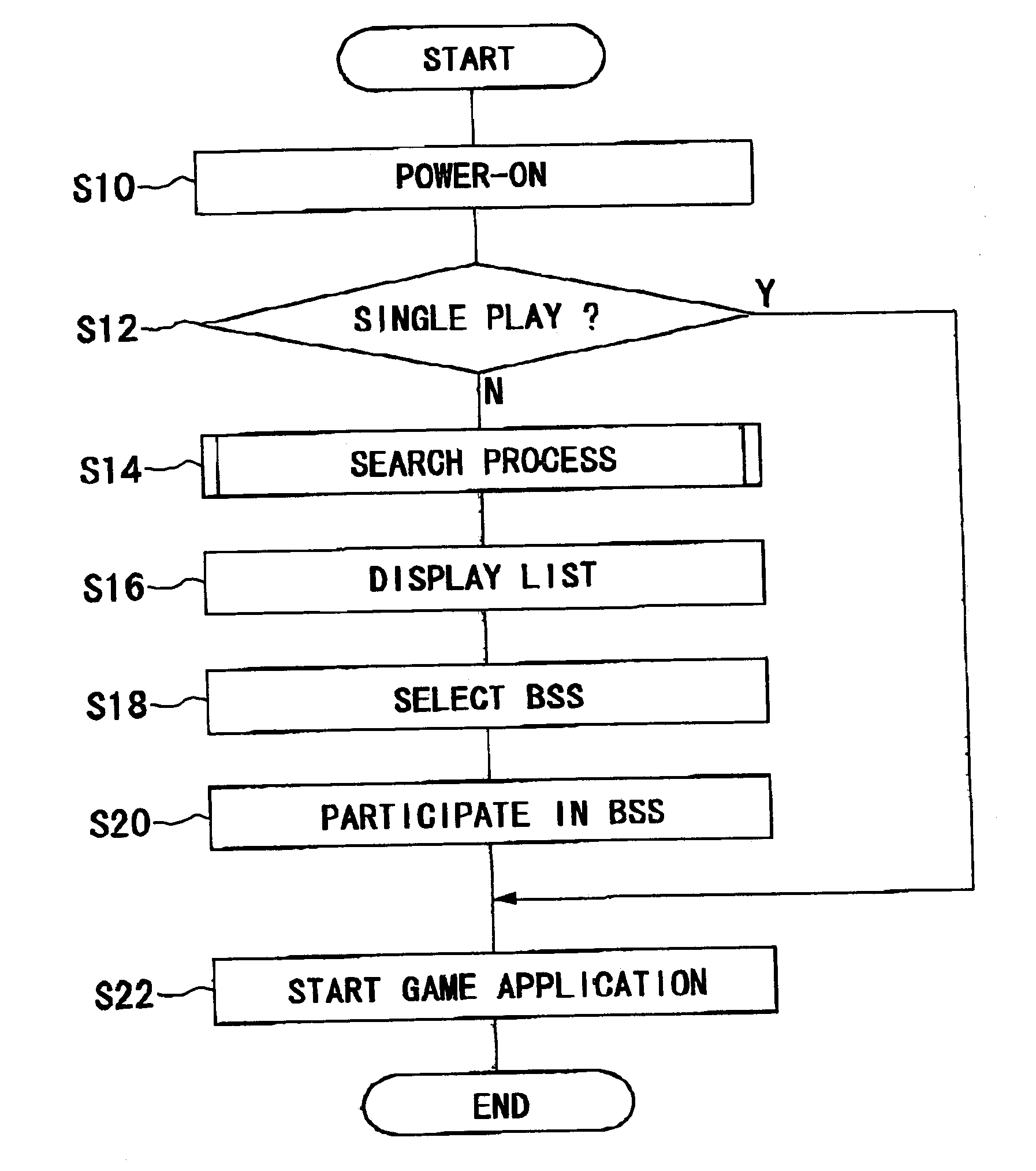
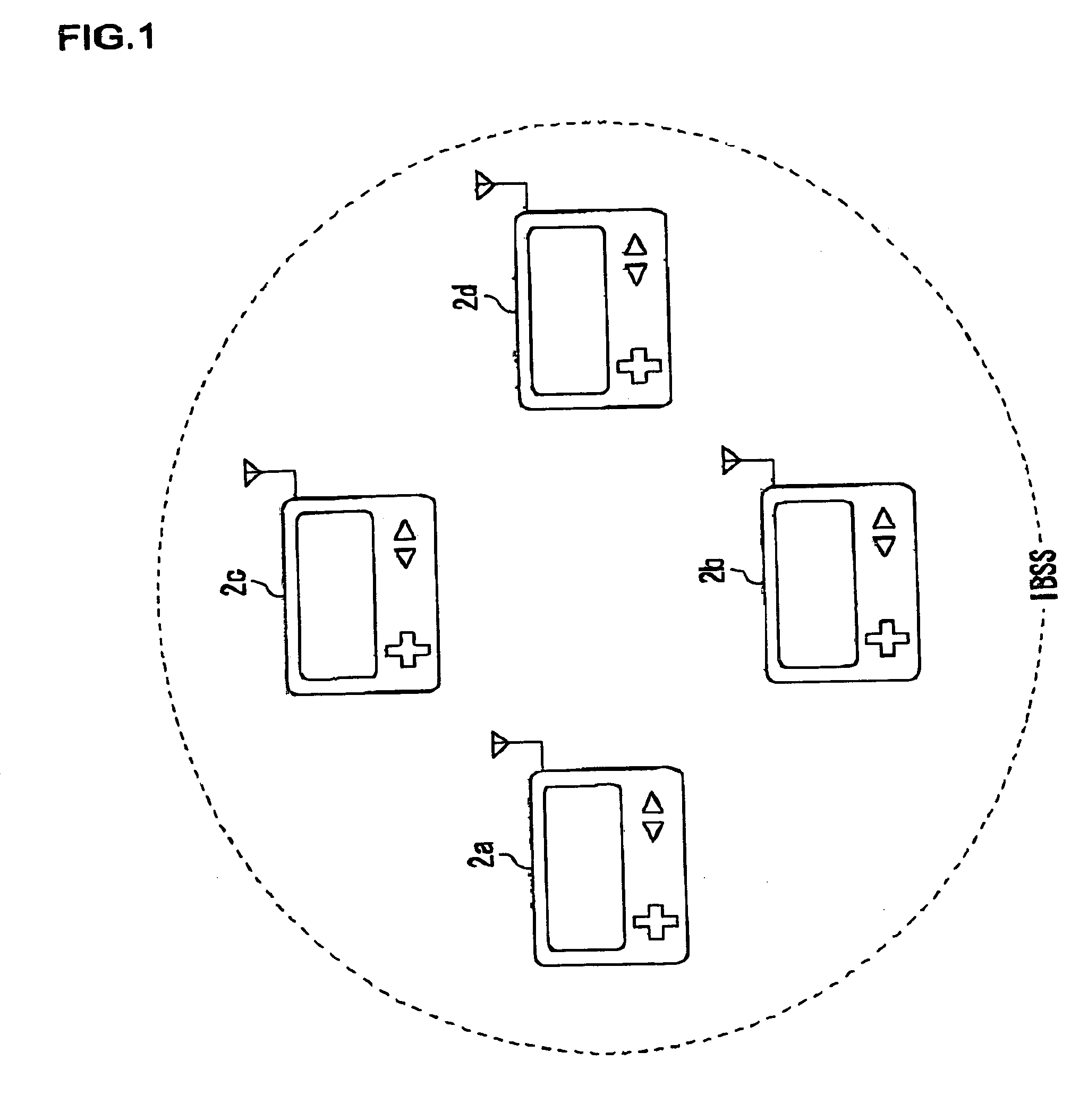
Wireless communication terminal, air interface apparatus and method for participating in wireless network
ActiveUS20050250487A1Effectively participateEfficient networkingDigital data processing detailsUser identity/authority verificationTelecommunicationsAir interface
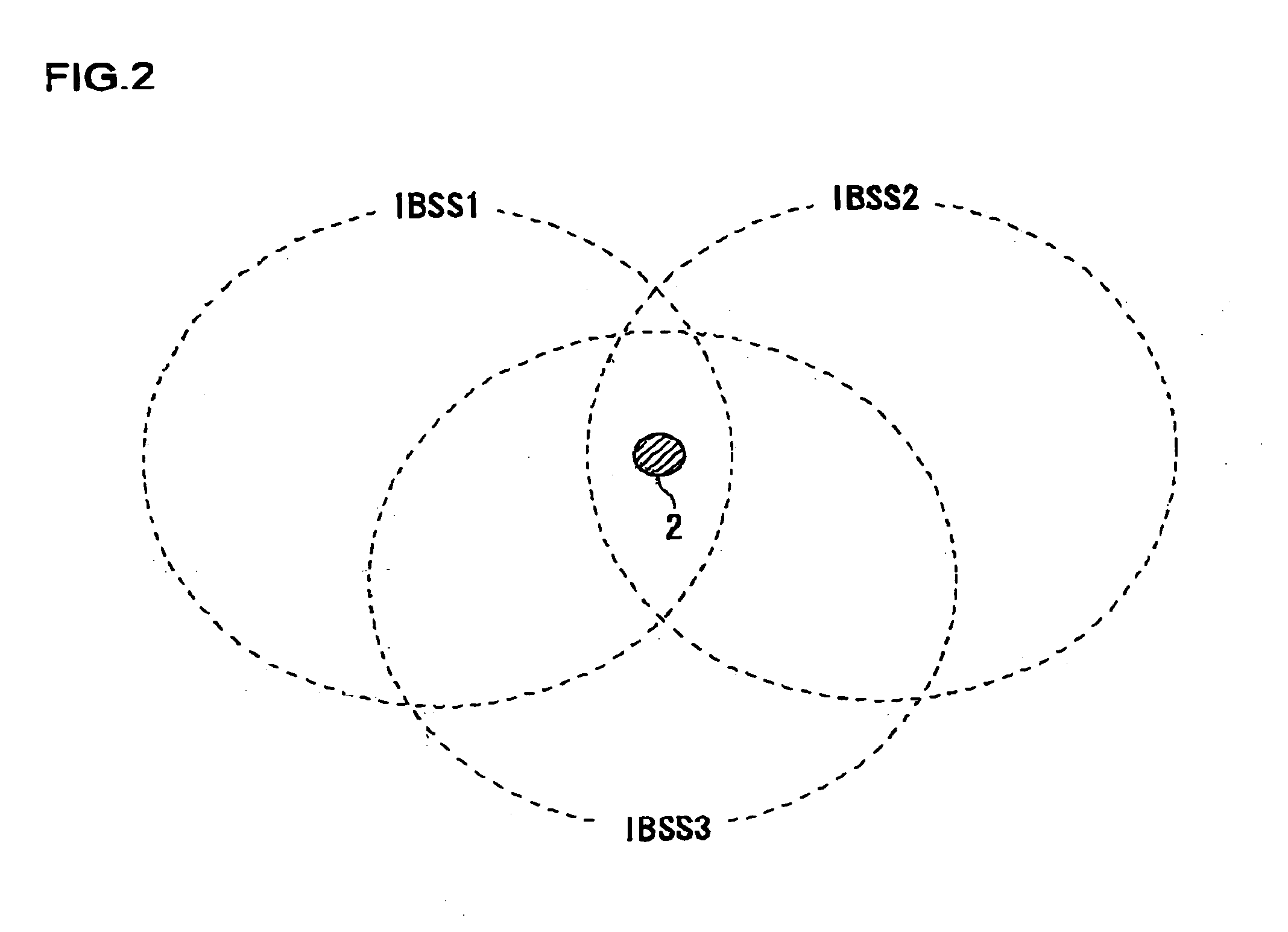
A game device is provided with a processor and an air interface apparatus. In a wireless communication environment such as that of IEEE802.11, a CPU of the air interface apparatus selects, in a search process, an SSID that includes at least in a portion thereof a predetermined pattern. Network information including the selected SSID is retained in a memory unit as a BSS list registering wireless networks that are targets, for connection. The processor refers to the BSS list and determines a wireless network to participate in.
Owner:SONY COMPUTER ENTERTAINMENT INC
Radiofrequency identification (RFID) based intelligent logistics managing system
InactiveCN103593751AEfficient informatizationFlexible managementLogisticsEmbedded systemStorage garage
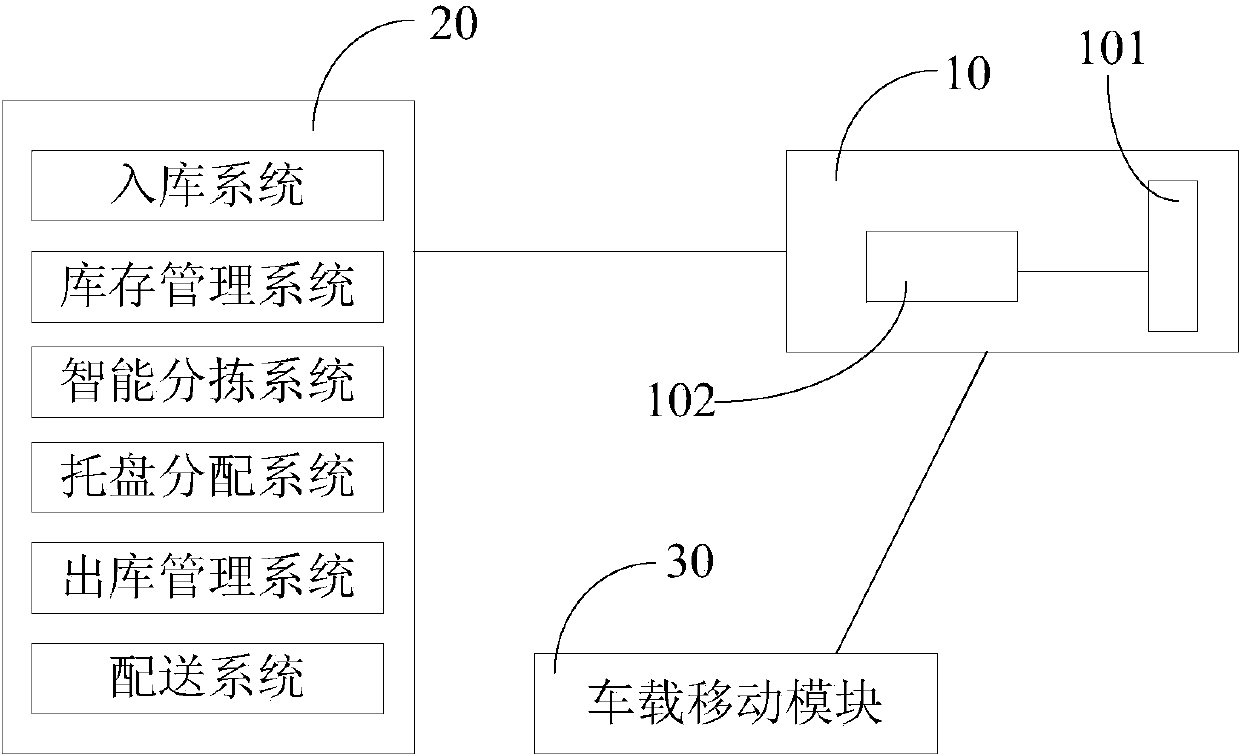
The invention relates to an RFID based intelligent logistics managing system, which belongs to the field of logistics management, and used for managing logistics information of cargoes with RFID tags. The logistics managing system comprises a logistics control system, a storage system arranged in a warehouse and a vehicle-mounted mobile module, wherein the logistics control system is connected with the storage system and the vehicle-mounted mobile module via a communication network to realize commutation between the logistics control system and the storage system or the vehicle-mounted mobile module, each of the storage system and the vehicle-mounted storage system is equipped with an RFID reader, the RFID readers read information of the RFID tags, and the RFID information is transmitted to the logistics control system. According to the RFID based intelligent logistics managing system, logistics information can be managed in a highly-efficient, automatic, informationized, networked, intelligent and flexible manner.
Owner:CHINA CONSTR EIGHT ENG DIV CORP LTD
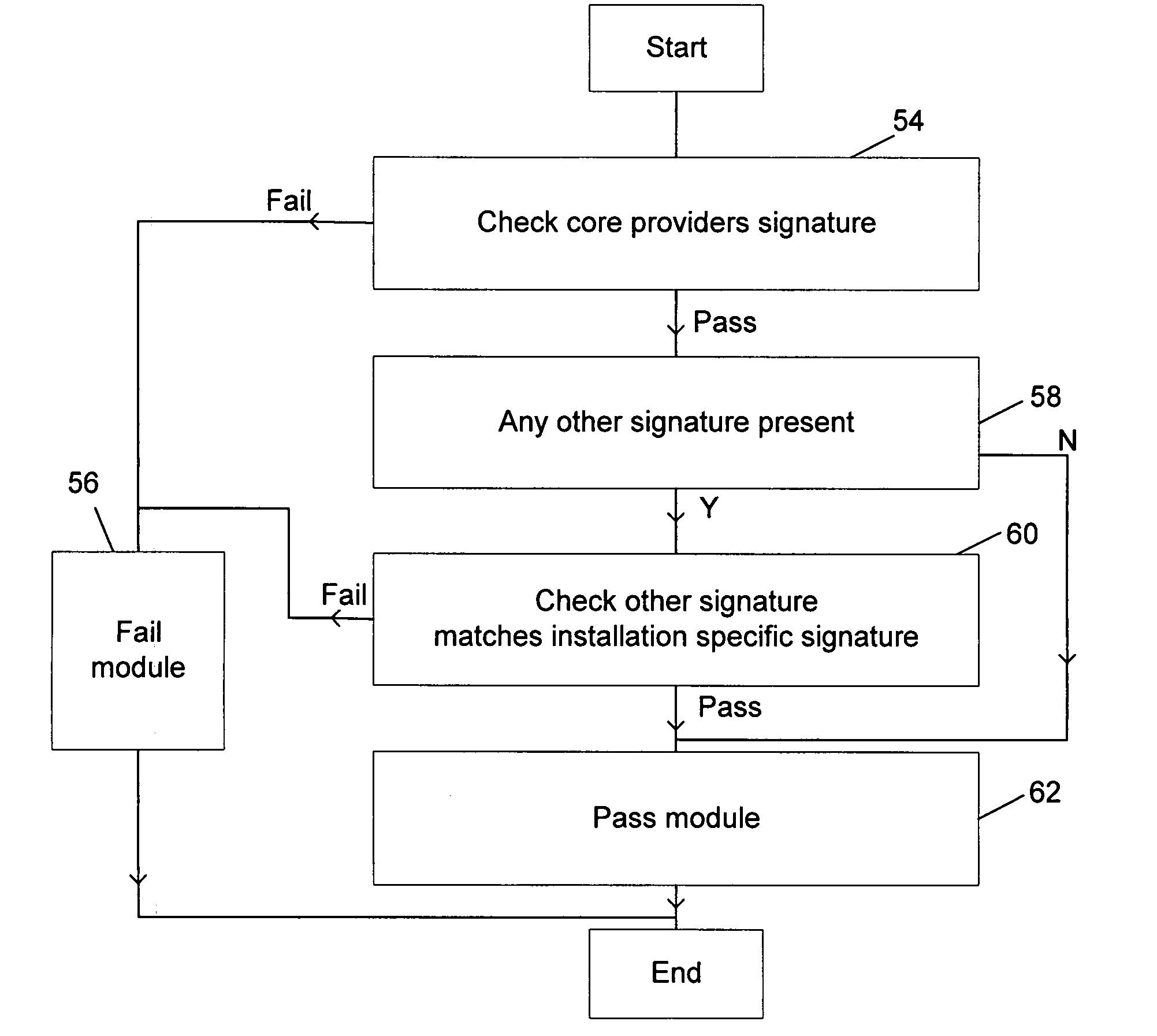
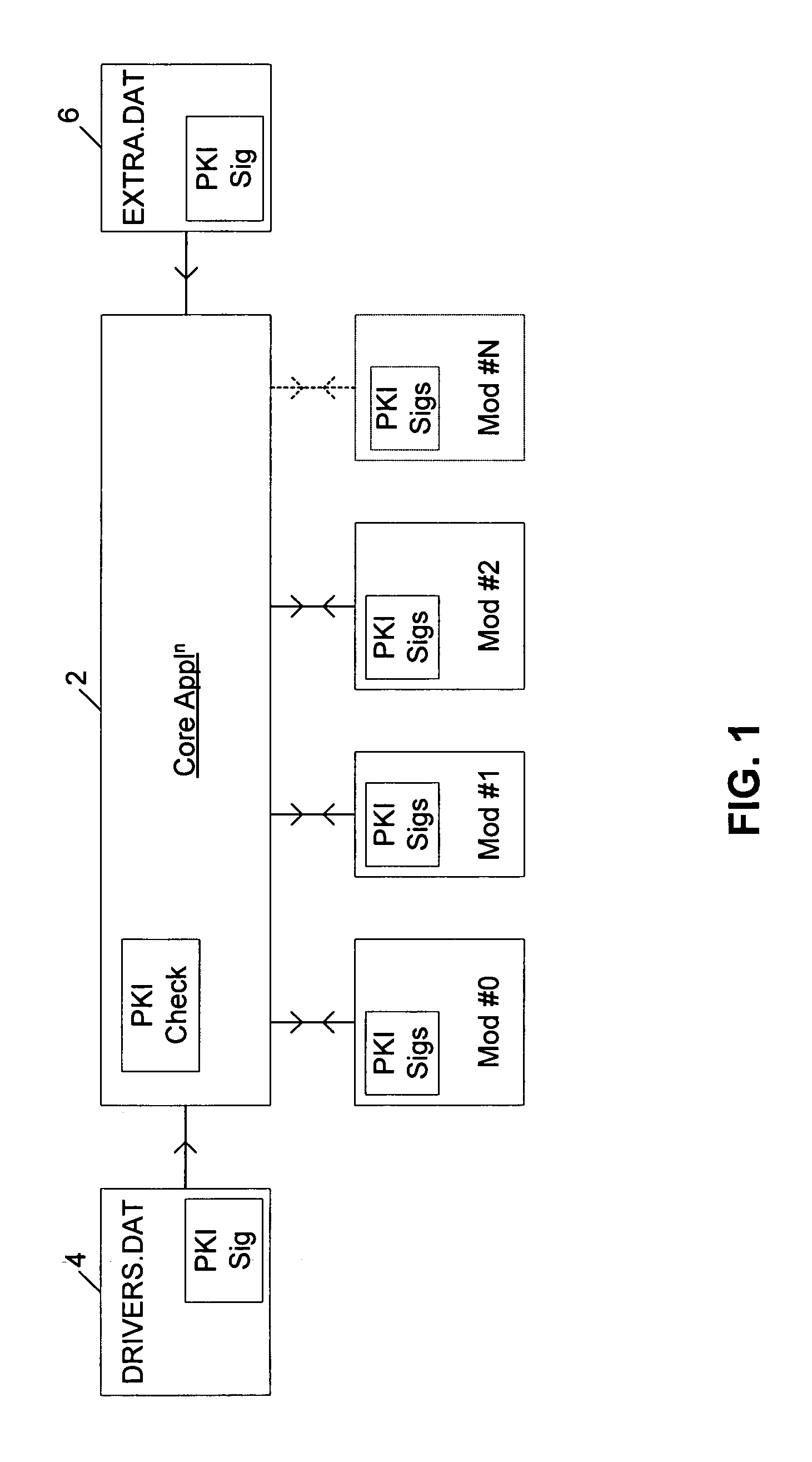
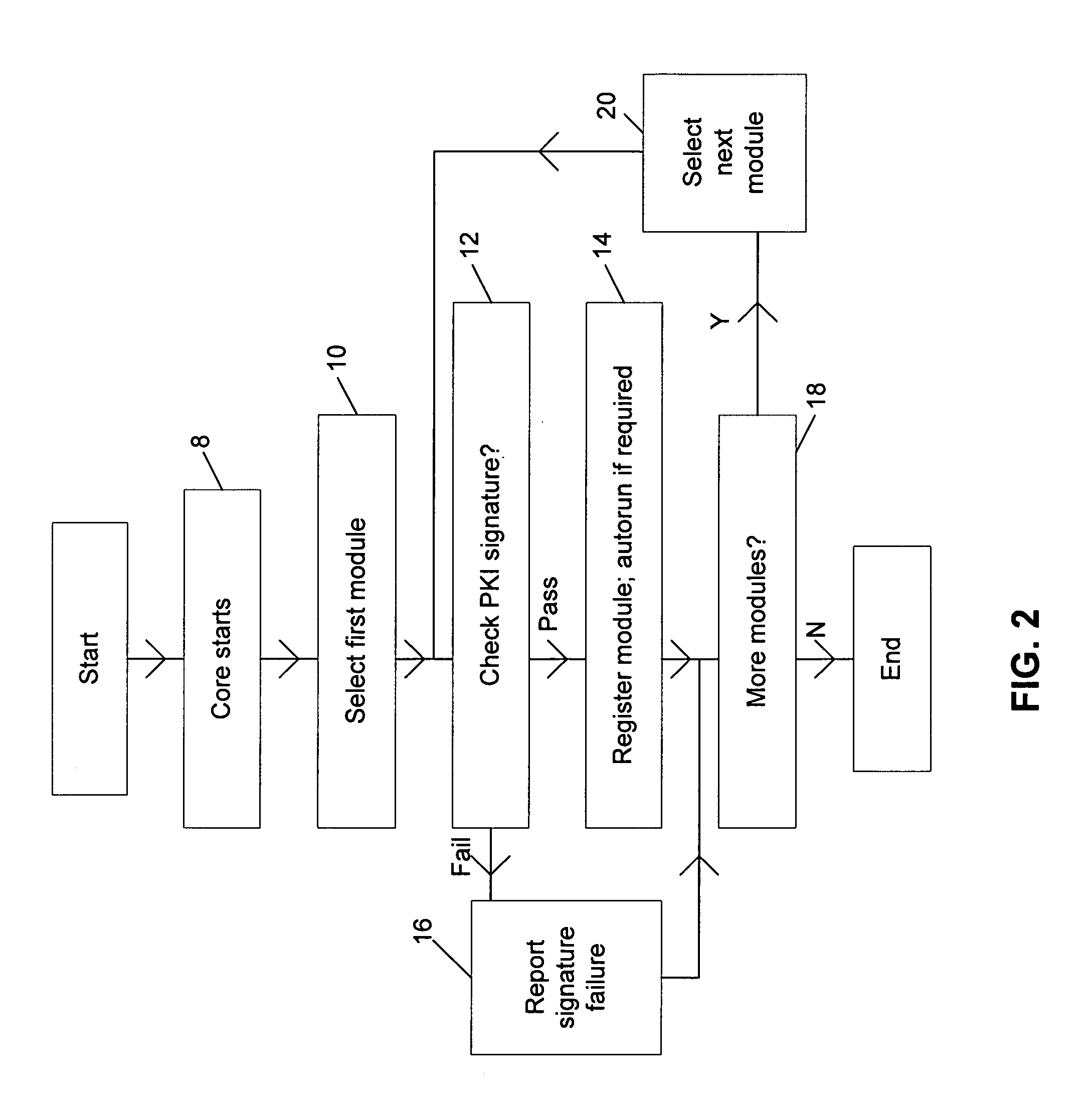
Authorizing an additional computer program module for use with a core computer program
InactiveUS6971023B1Improve performanceEfficiency advantageUser identity/authority verificationUnauthorized memory use protectionComputer usersComputer module
A system for scanning computer files for unwanted properties, such as containing computer viruses or being spam e-mail, allocates a priority to pending scan requests based upon the identity of a computer user associated with the scan request. In the case of a normal file access request, the computer user associated with the scan request may be the file access request or in the case of an on-demand scan, then the computer user associated with a particular scan request for a computer file may be the owner or creator of that computer file. In the case of scan requests associated with e-mails, the sender or recipient computer user may be used in the allocation of a priority level for the scan request.
Owner:MCAFEE LLC
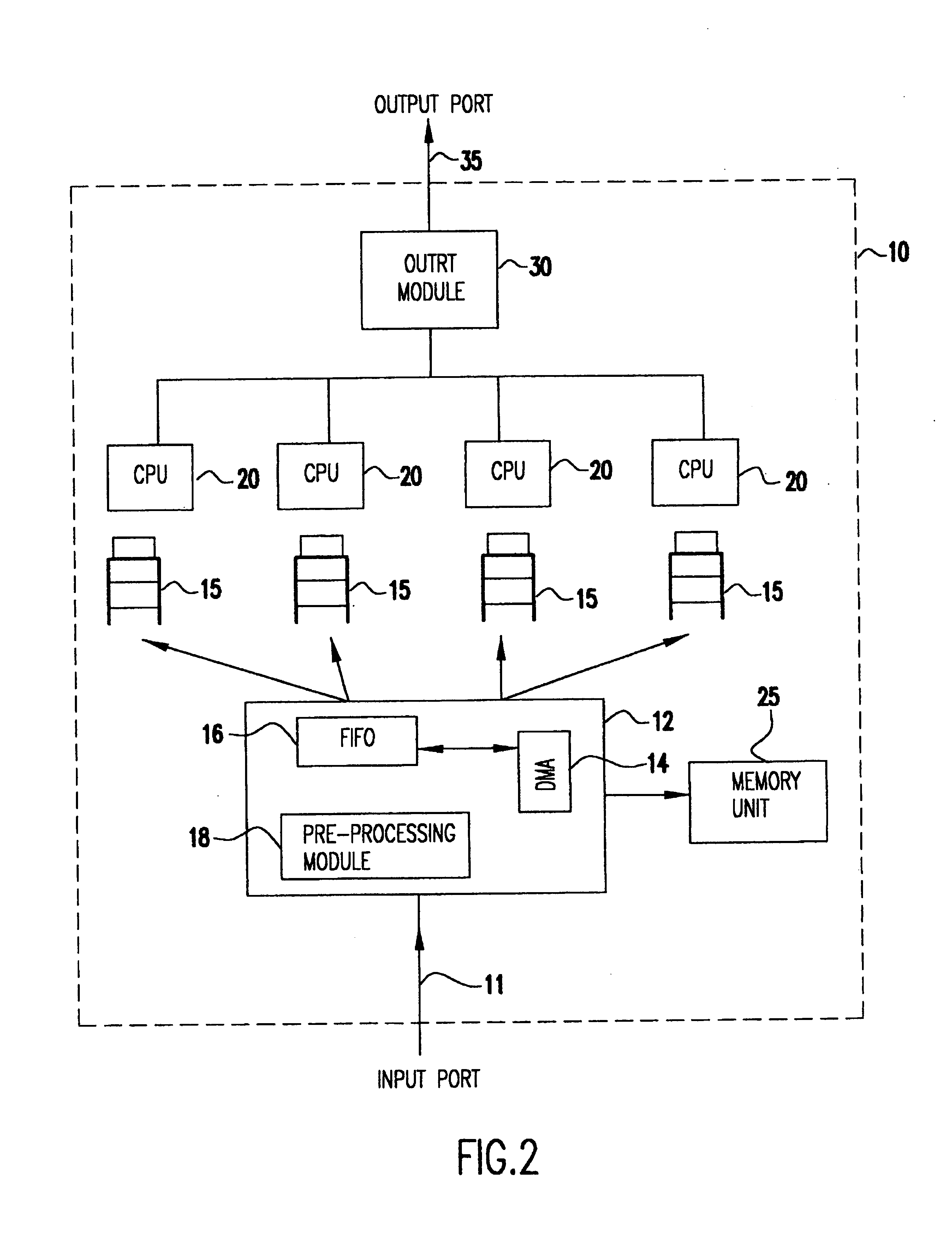
Packet preprocessing interface for multiprocessor network handler
InactiveUS6904040B2Efficient networkingEfficient processingData switching by path configurationMultiple digital computer combinationsTraffic capacityHash function
A network handler uses a DMA device to assign packets to network processors in accordance with a mapping function which classifies packets based on its content, e.g., bits in one or more header fields. Preferably, the mapping function is implemented as a hash function, which uses a predetermined number of bits from packet as inputs. The result of this function specifies the processor to which the packet is assigned. To make implementation manageable in a high-traffic environment, each processor may be equipped with a queue, which holds pointer information. Such a pointer provides an indication of the area in memory where incoming packet resides. The network handler is particularly useful in a Fiber Channel environment, where the hash function may be implemented to assign all packets from the same sequence to the same processor, thereby resulting in improved processing efficiency.
Owner:IBM CORP
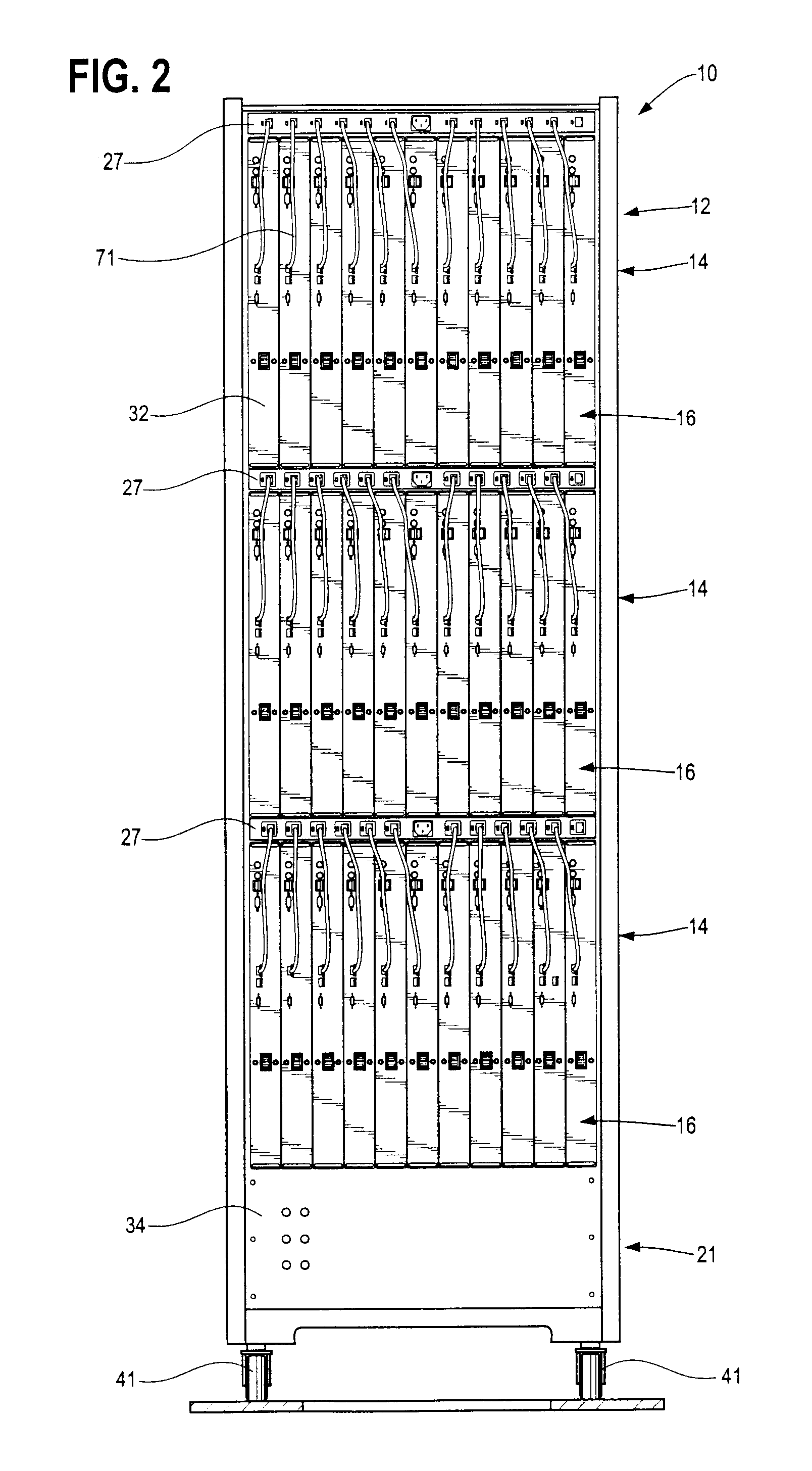
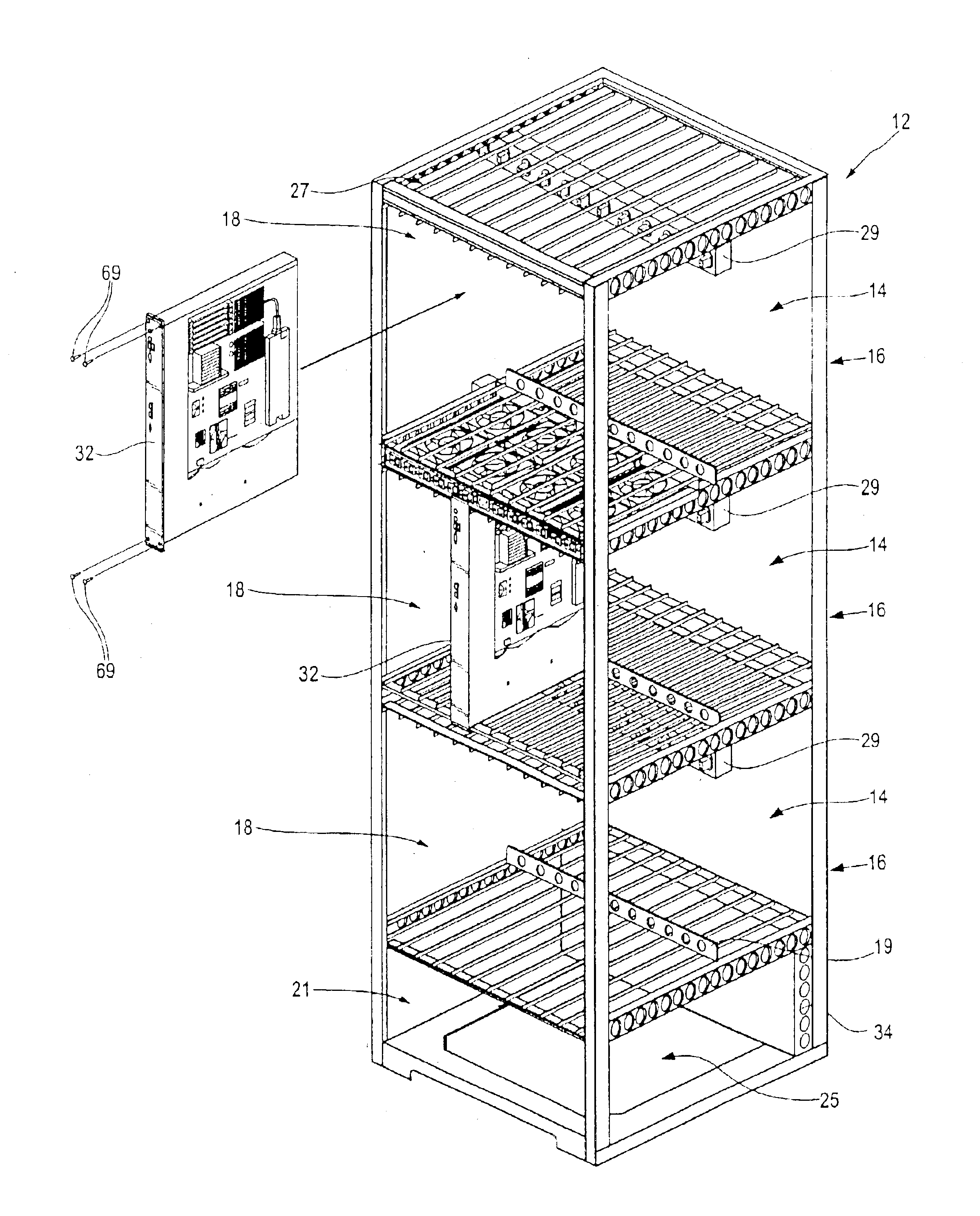
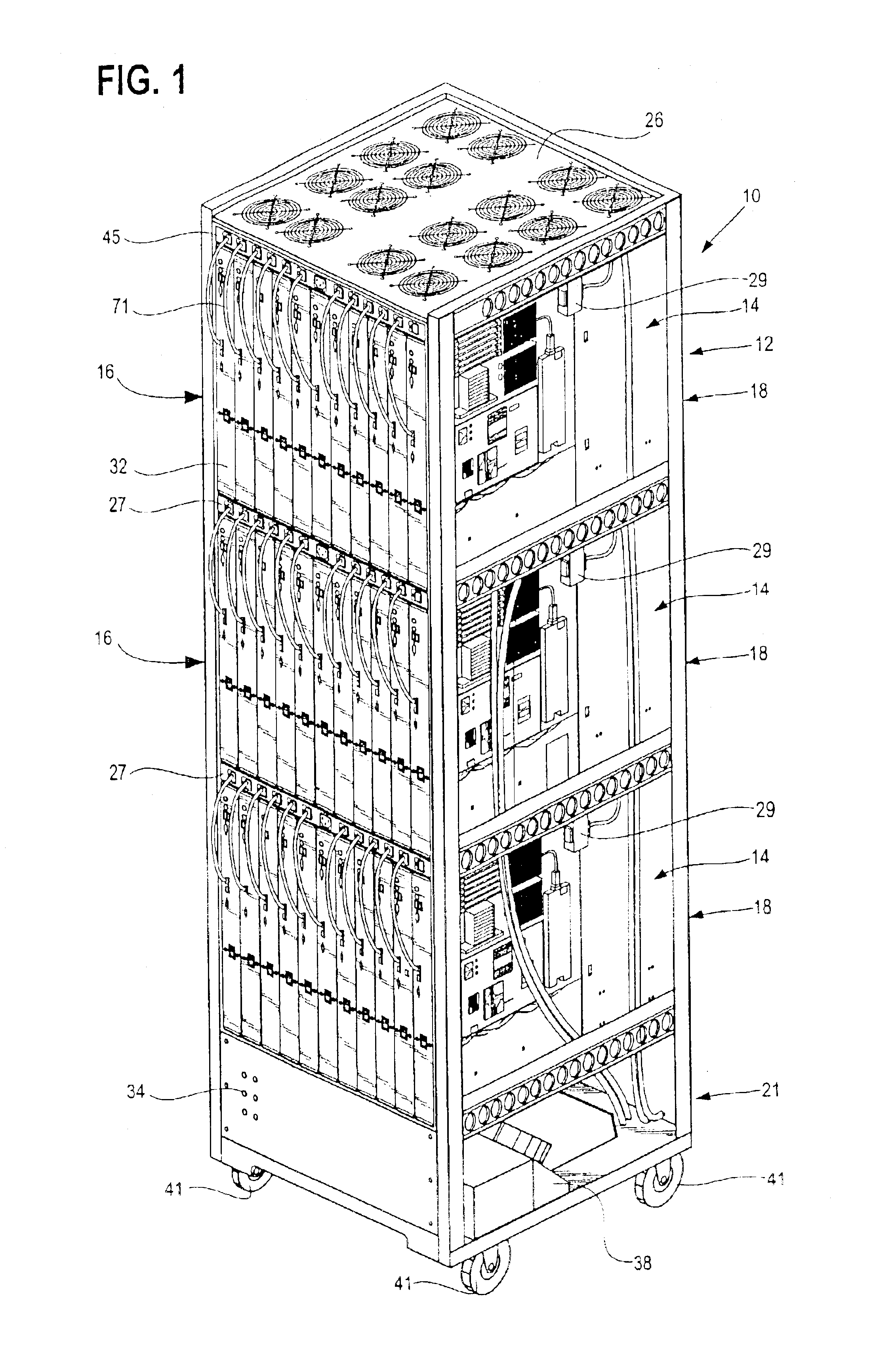
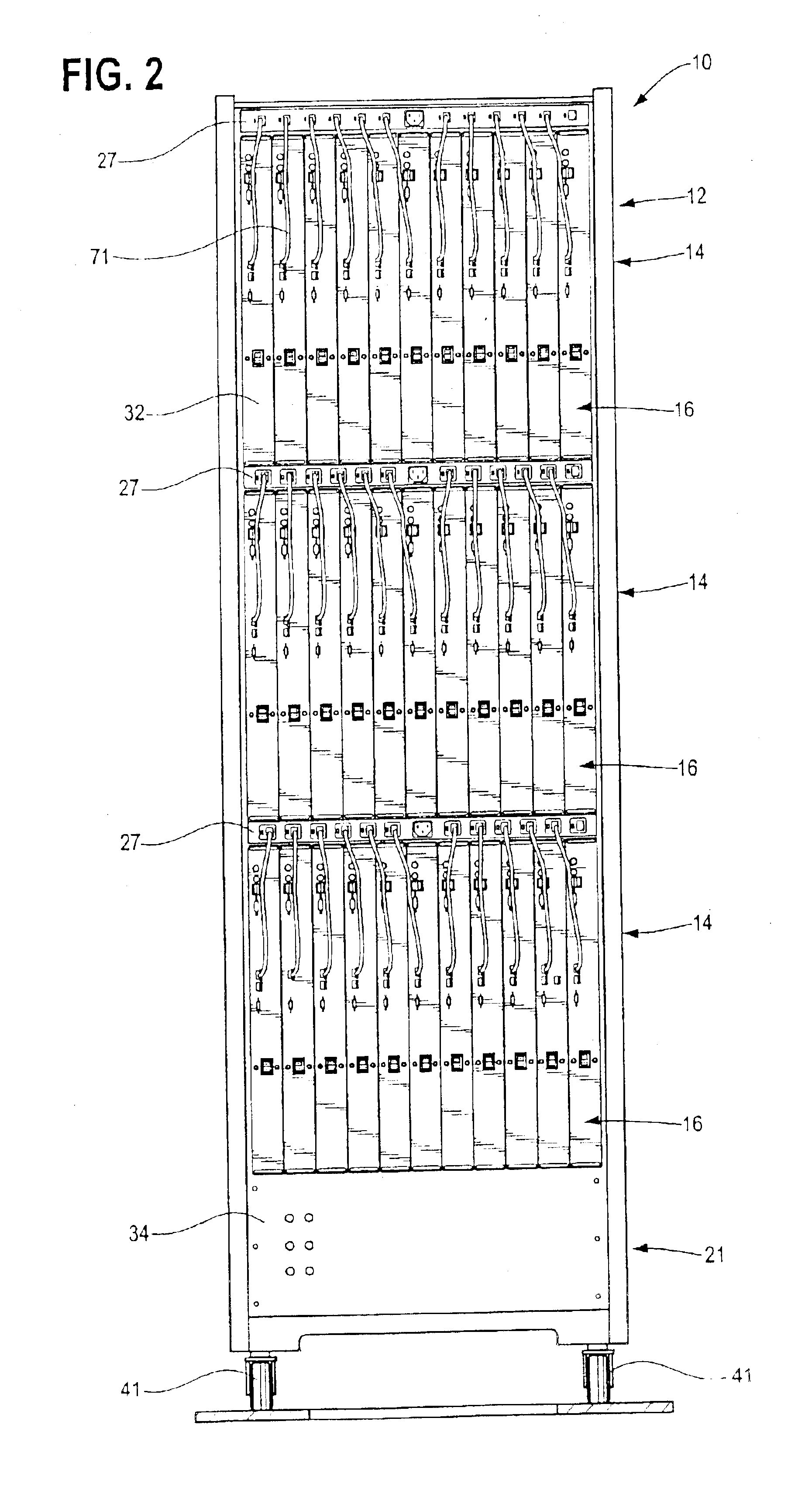
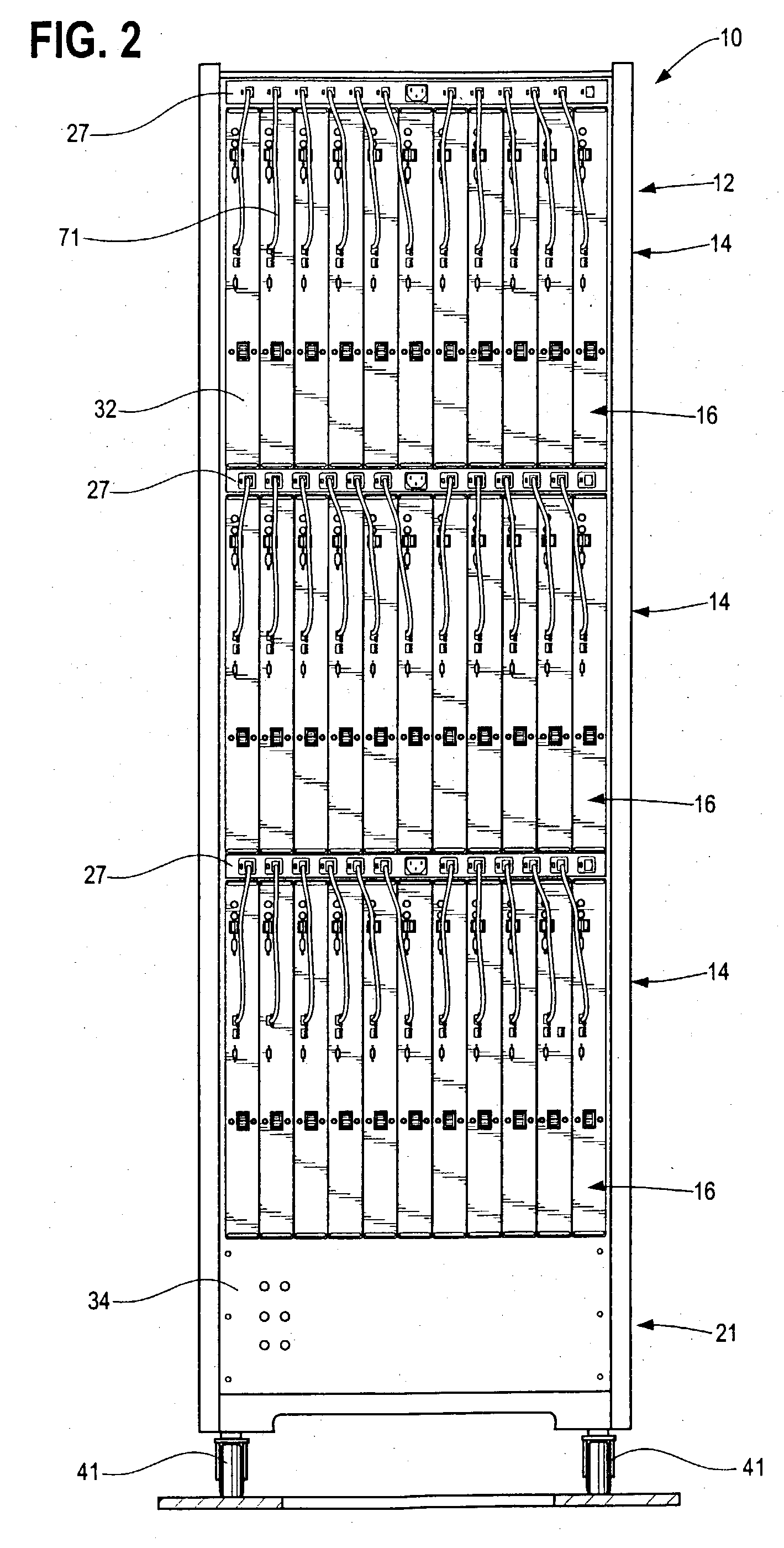
Rack mountable computer component fan cooling arrangement and method
InactiveUS6801428B2Easy to carryEasy to operateBatteries circuit arrangementsDigital data processing detailsElectricity
Owner:BOXX TECH LLC
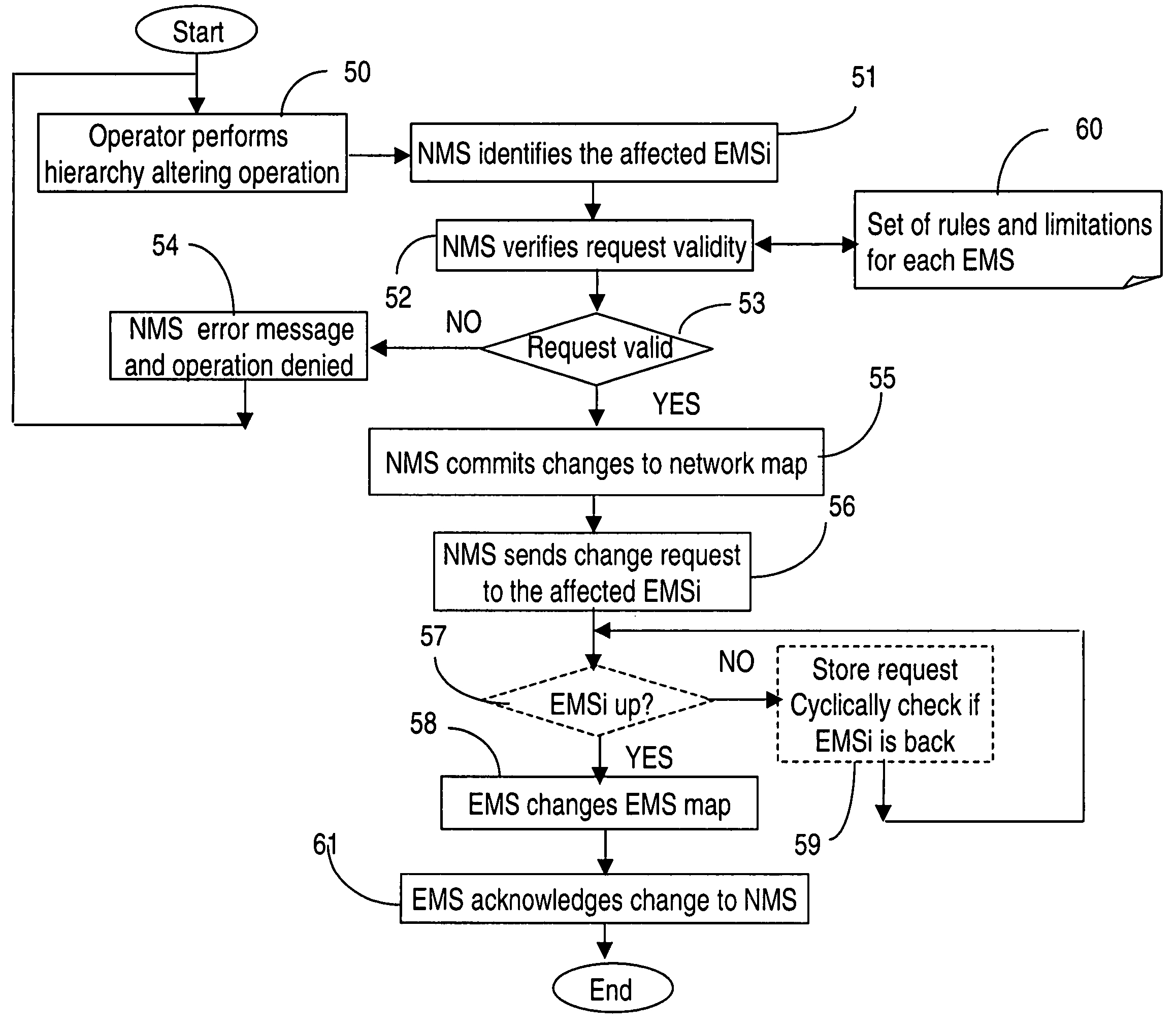
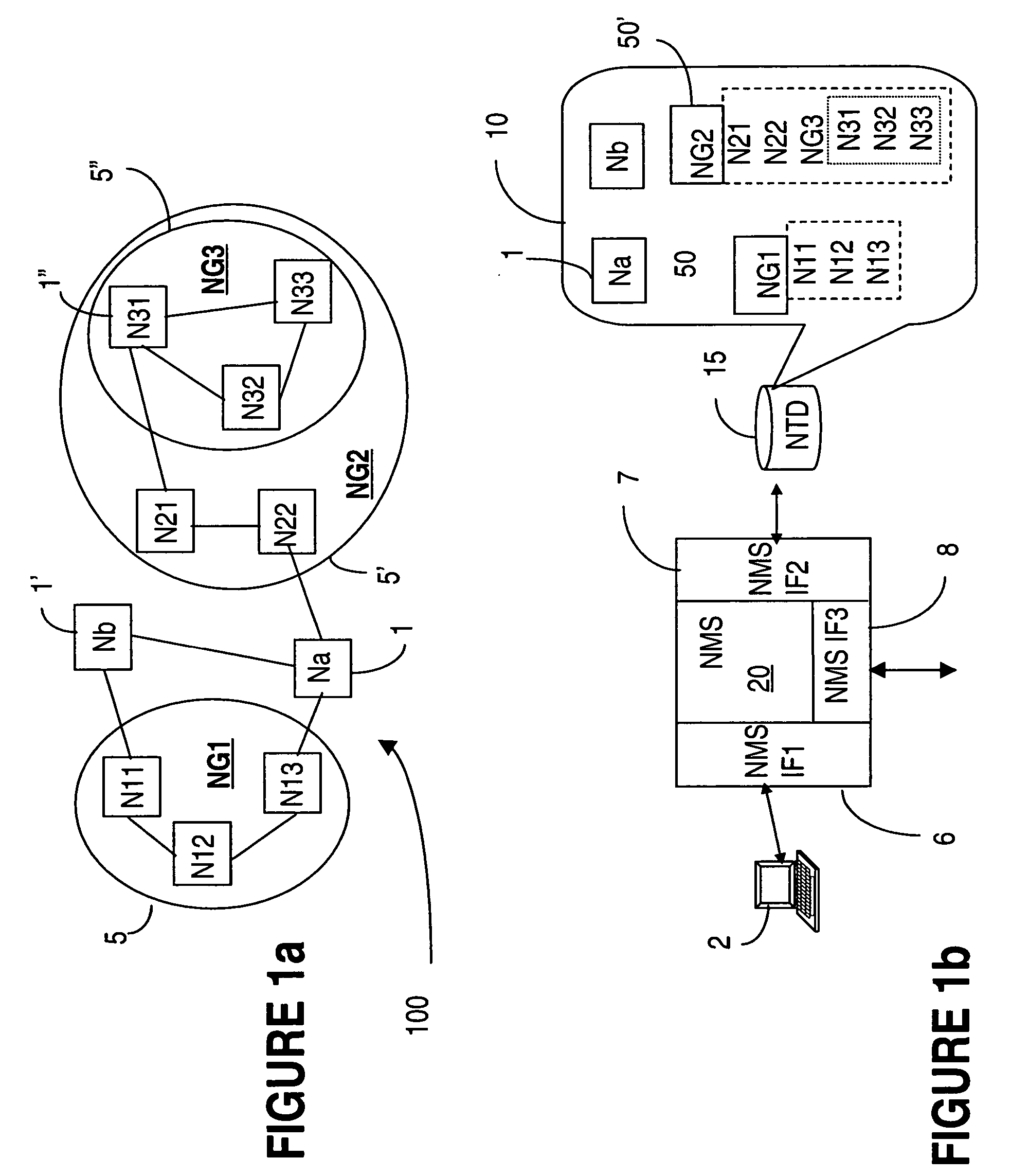
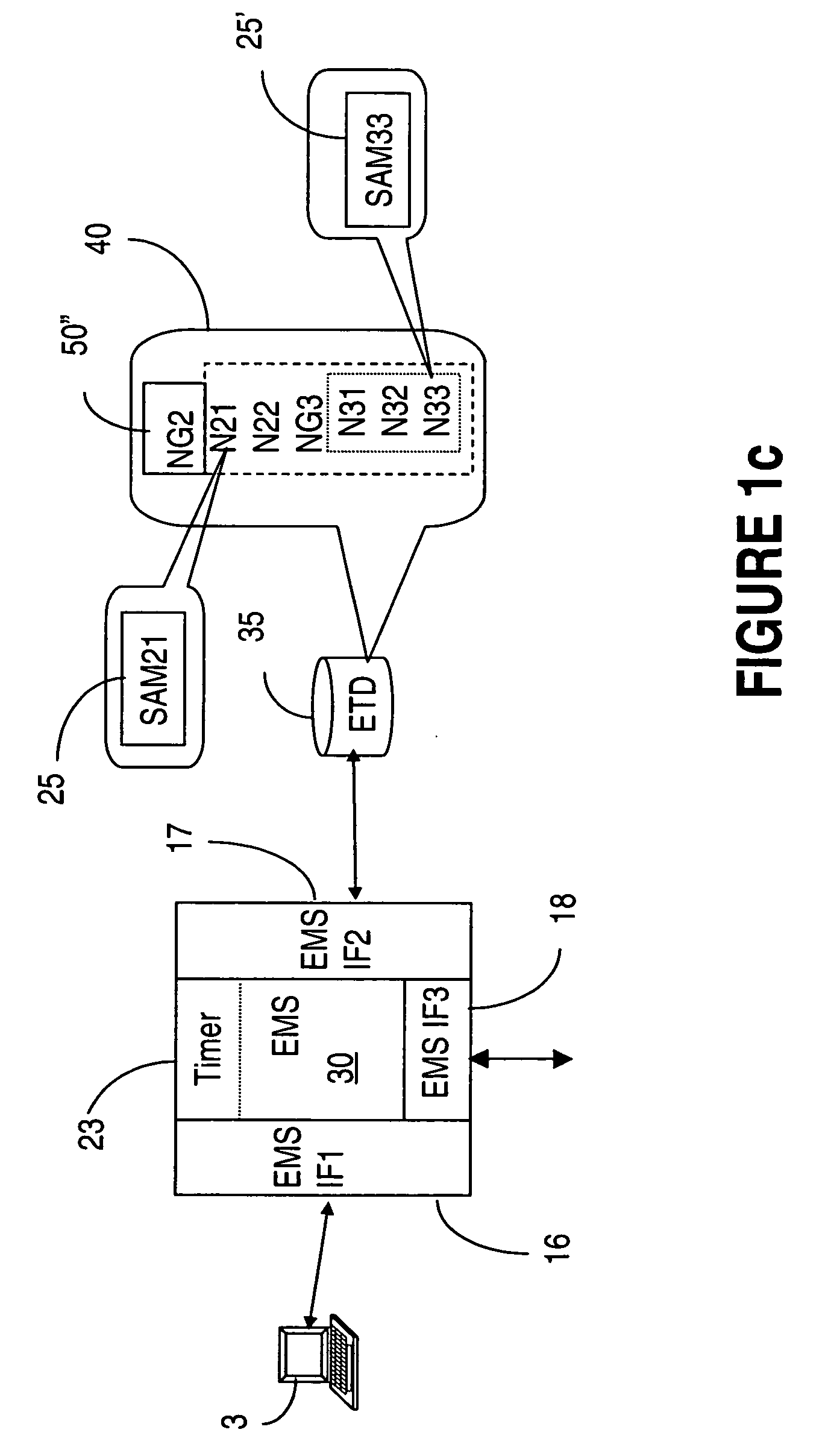
Interworking network maps of network management and element management systems
InactiveUS20050201299A1Improve efficiencyEfficient networkingDigital computer detailsData switching by path configurationElement management systemNetwork management
In a communication network, the network management system NMS keeps one or more element management system EMS in synchronization of network topology changes using requests that are automatically generated or manually requested and then sent from the NMS to the affected EMS(s) whenever a node topology change is made at the NMS. Examples of changes are node creation, node move, node group move, node group renaming, etc. As the changes are completed in the EMS topology database, the EMS sends acknowledgments of the request to the NMS. This functionality requires verification of the validity of the request for that specific EMS, before the change is implemented at the NMS.
Owner:WSOU INVESTMENTS LLC
Network system, method and protocols for hierarchical service and content distribution via directory enabled network
InactiveUS20050198250A1Improve performanceBetter and scalable service provisioning and managementDigital computer detailsData switching networksContent distributionData center
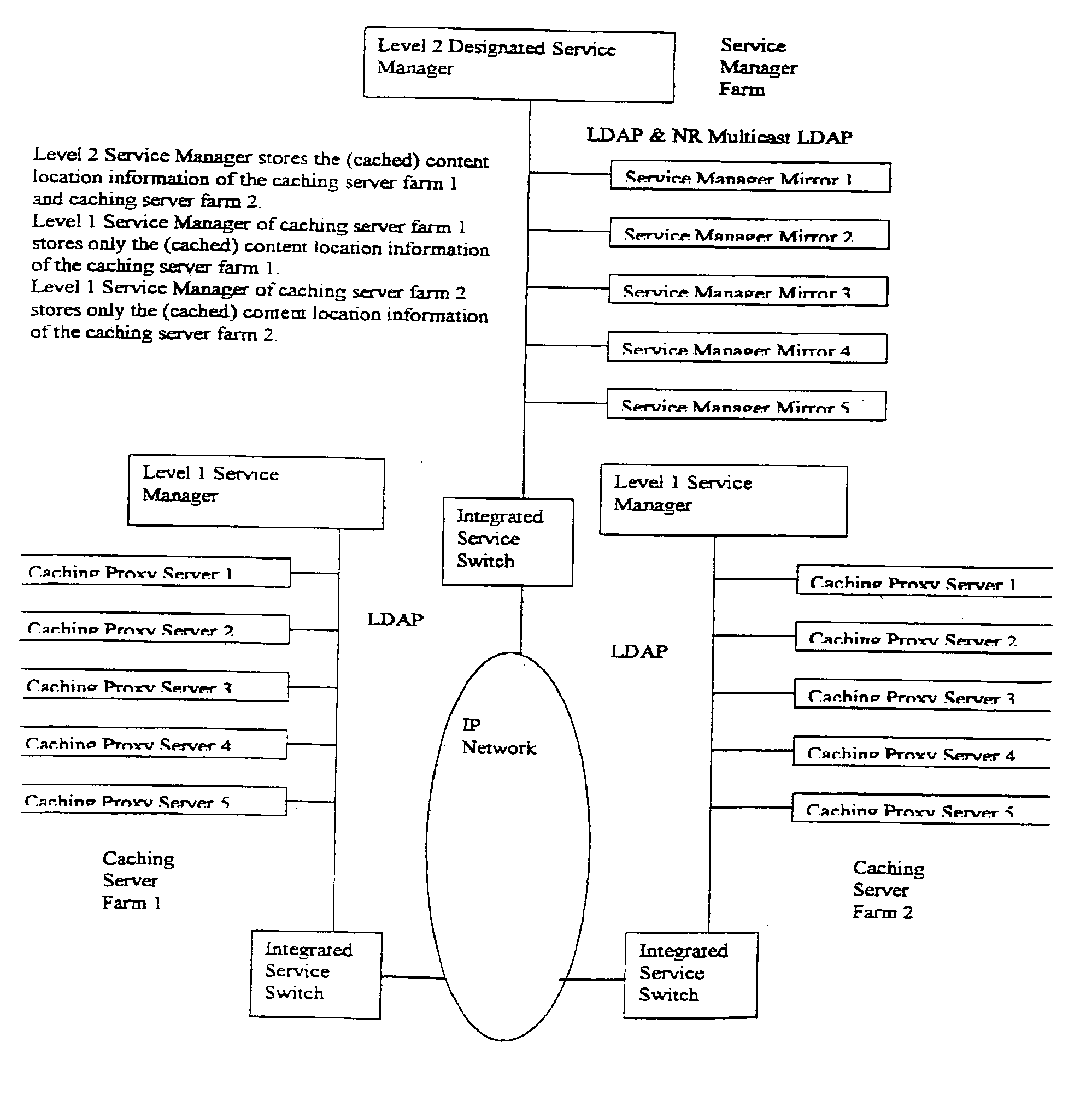
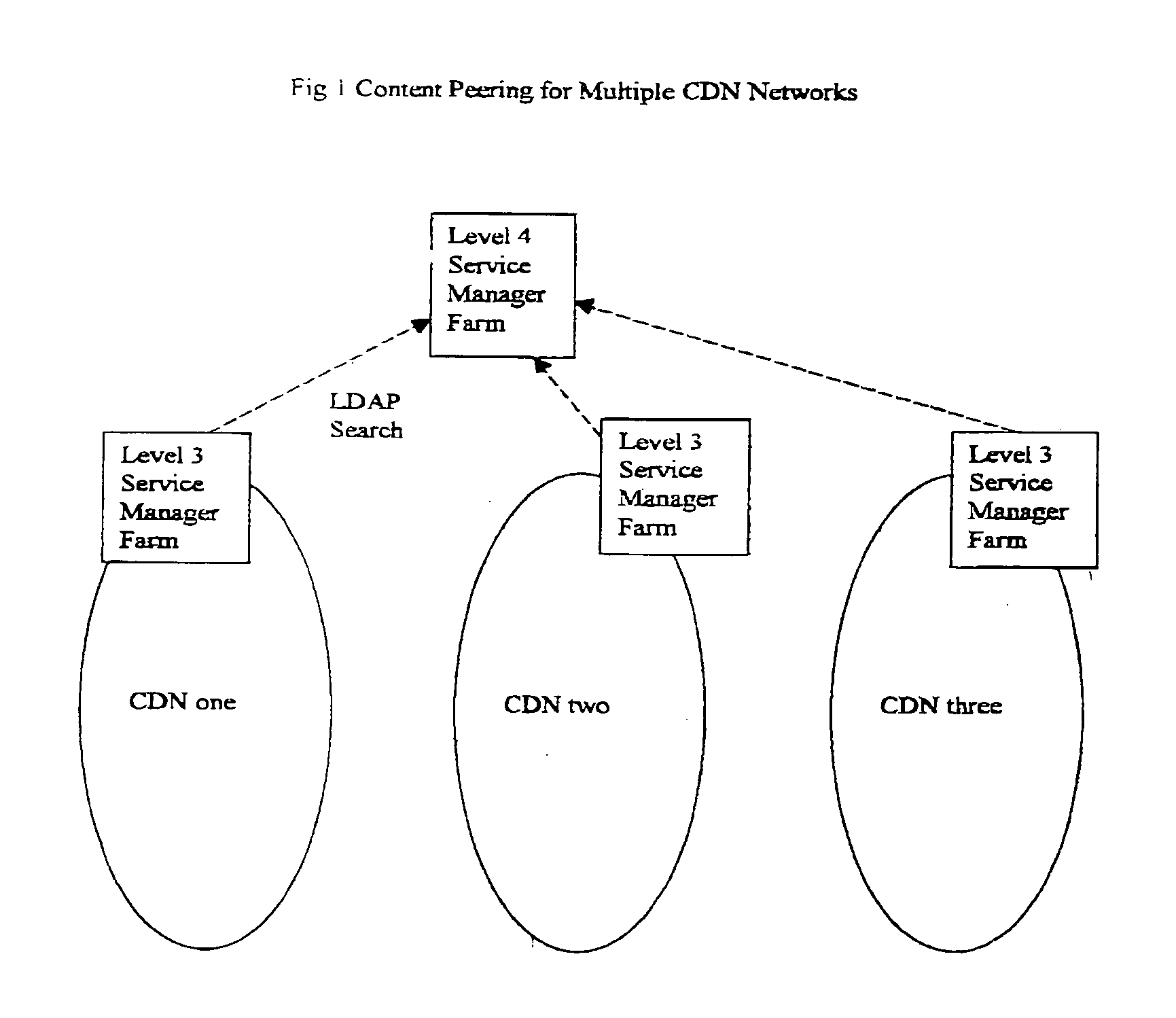
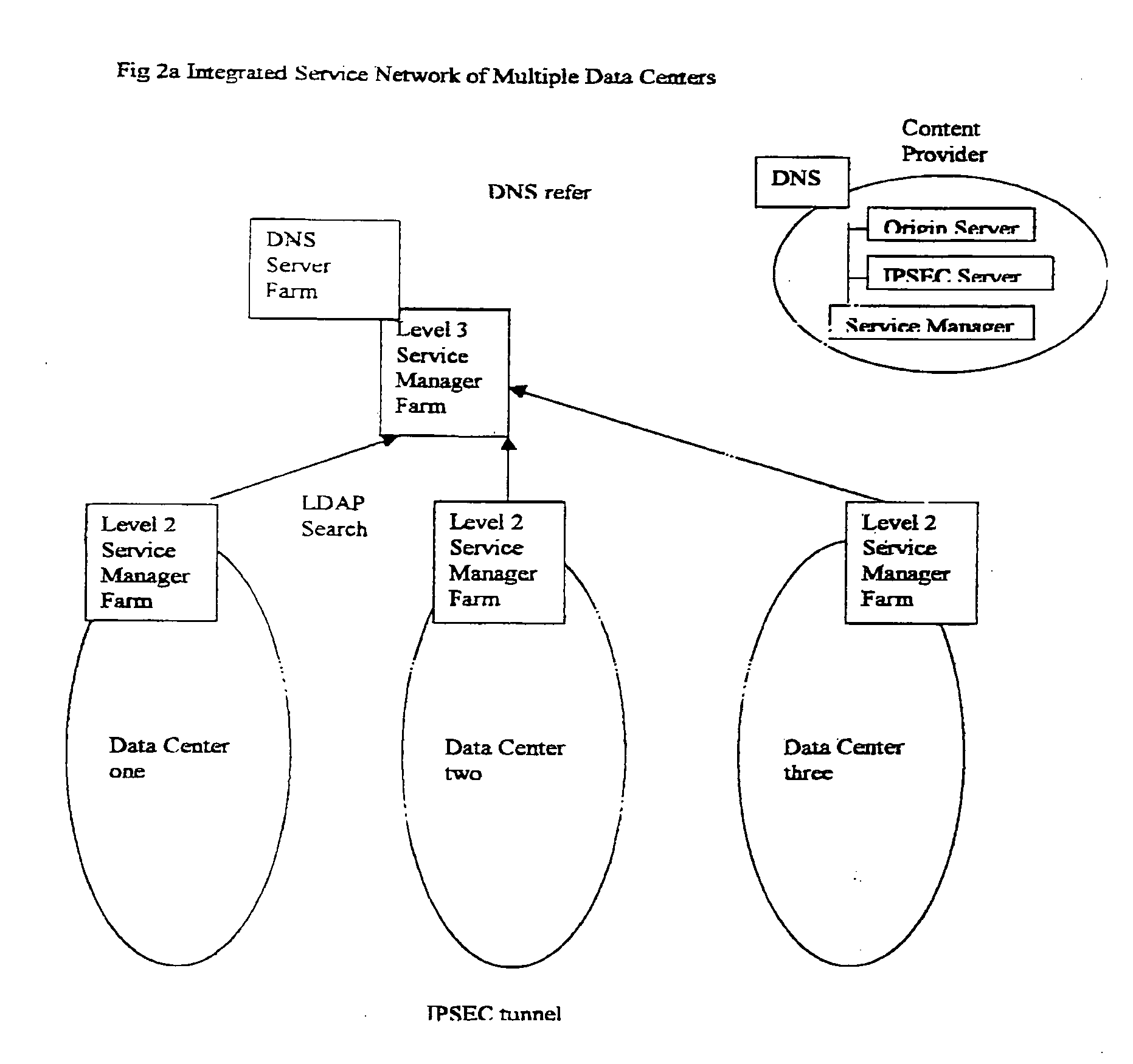
A network system manages hierarchical service and content distribution via a directory enabled network to improve performance of the content delivery network with a hierarchical service network infrastructure design. The network system allows a user to obtain various Internet services, especially the content delivery service, in a scalable and fault tolerant way. In particular the network system is divided into 4 layers, each layer being represented and managed by a service manager with back up mirrored managers. The layer 4 service manager is responsible for management of multiple content delivery networks (CDNs). The layer 3 service manager is responsible for management of one CDN network that has multiple data centers. The layer 2 service manager is responsible for management of one data center that has multiple server farms or service engine farms. The layer 1 service manager is responsible for all servers in a server farm. Each server of the server farm can be connected by a LAN Ethernet Switch Network that supports the layer 2 multicast operations or by an Infiniband switch.
Owner:TERITED INT
Rack mountable computer component power distribution unit and method
InactiveUS6836030B2Easy to carryEasy to operateBus-bar/wiring layoutsDc network circuit arrangementsElectricityEngineering
According to the disclosed embodiments of the invention, there is provided a method of supplying electrical power to a series of upright computer blades mounted side-by-side in a closely spaced configuration, including extending an elongated power distribution unit transversely to the upright blades, and electrically interconnecting the upright blades with a series of electrical connectors arranged side-by-side on one side of the distribution unit. In one embodiment of the invention, a second series of electrical connectors are arranged side-by-side on the opposite side of the body of the power distribution unit.
Owner:BOXX TECH LLC
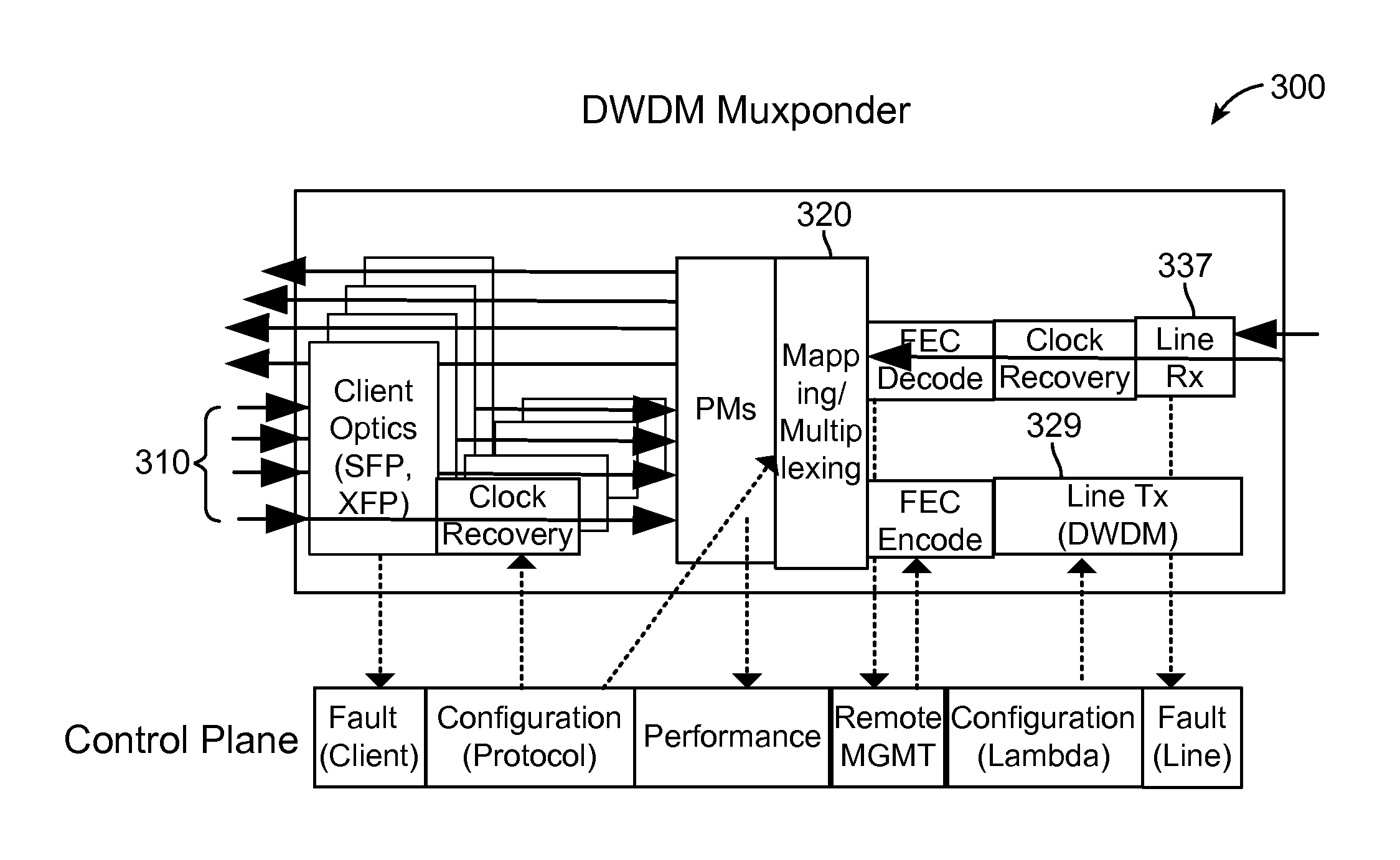
Optical Subchannel Routing, Protection Switching and Security
ActiveUS20110135305A1Easy mappingMaintaining full visibilityMultiplex system selection arrangementsWavelength-division multiplex systemsNetwork architectureEngineering
The present invention includes novel techniques, apparatus, and systems for optical WDM communications. Tunable lasers are employed to generate subcarrier frequencies representing subchannels of an ITU channel to which client signals can be mapped. Client circuits can be divided and combined before being mapped, independent of one another, to individual subchannels within and across ITU channels. Subchannels may be independently routed to a single subchannel receiver filter, such that each subchannel detected at the receiver may come from a different source location. Network architectures and subchannel transponders, muxponders and crossponders are disclosed, and techniques are employed (at the subchannel level / layer), to facilitate the desired optical routing, switching, concatenation and protection of client circuits mapped to these subchannels across the nodes of a WDM network. Subchannel hopping may also be used to increase the optical network security.
Owner:SNELL HLDG LLC +1
Method and apparatus for detailed protocol analysis of frames captured in an IEEE 802.11(b) wireless LAN
InactiveUS7251685B1Efficient networkingAssisting maintenanceDigital computer detailsTransmissionRogue access pointWireless lan
A system, method and computer program product are provided for identifying MAC addresses of known access points operating in an IEEE 802.11(b) wireless communication channel, checking addresses of detected access points against the addresses of the known access points, and identifying for display as a rogue access point any access point detected that is not included as a known access point.
Owner:MCAFEE LLC
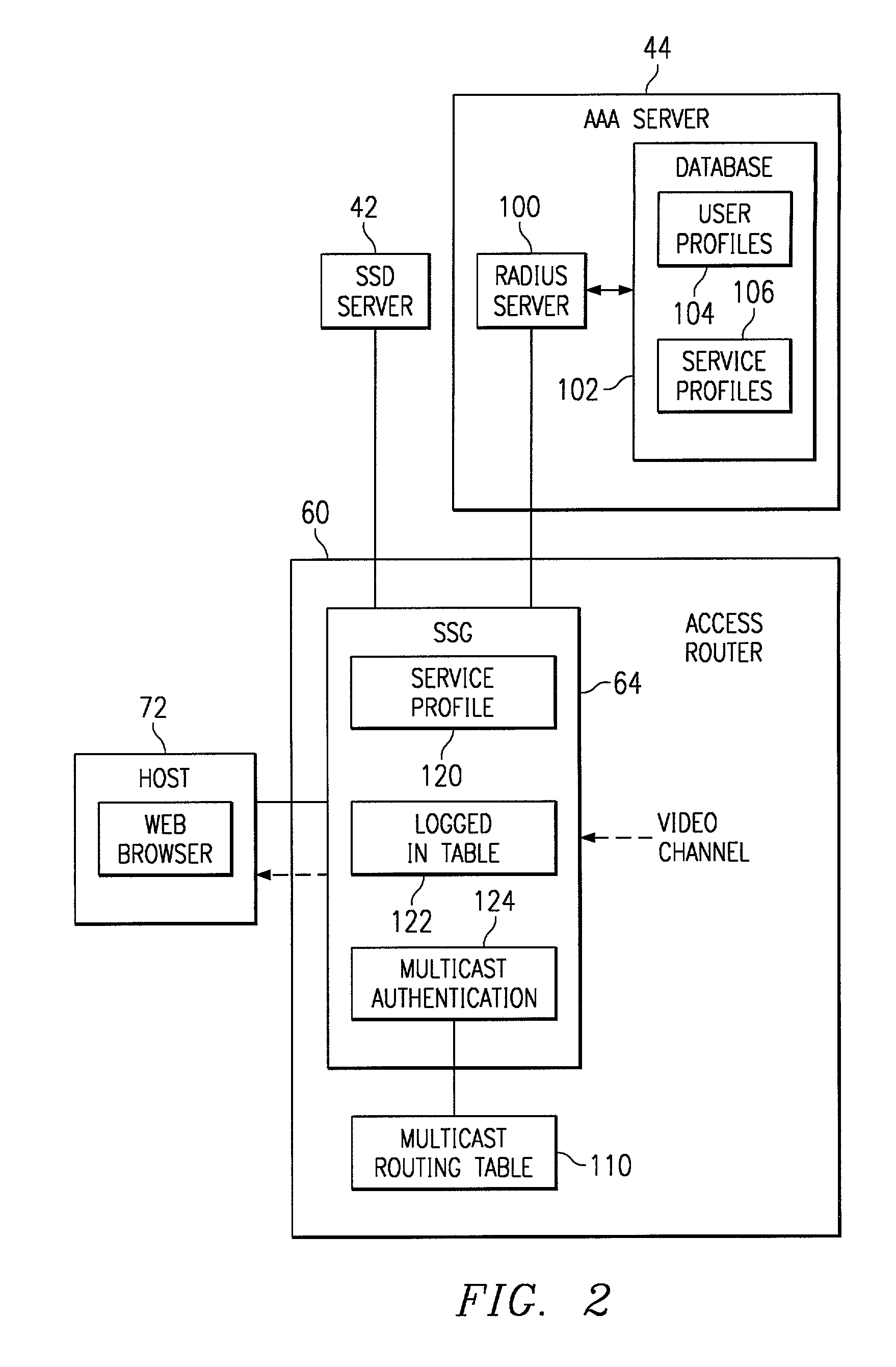
Method and system for authenticated access to internet protocol (IP) multicast traffic
InactiveUS7549160B1Reduce and eliminate and disadvantageReduce and eliminate problemDigital data processing detailsUser identity/authority verificationInternet protocol suiteTraffic capacity
A method and system for authenticated access to multicast traffic receives a request for a user to join a multicast channel. Access privileges of the user to the multicast channel are authenticated. The request is disallowed in response to at least an unsuccessful authentication.
Owner:CISCO TECH INC
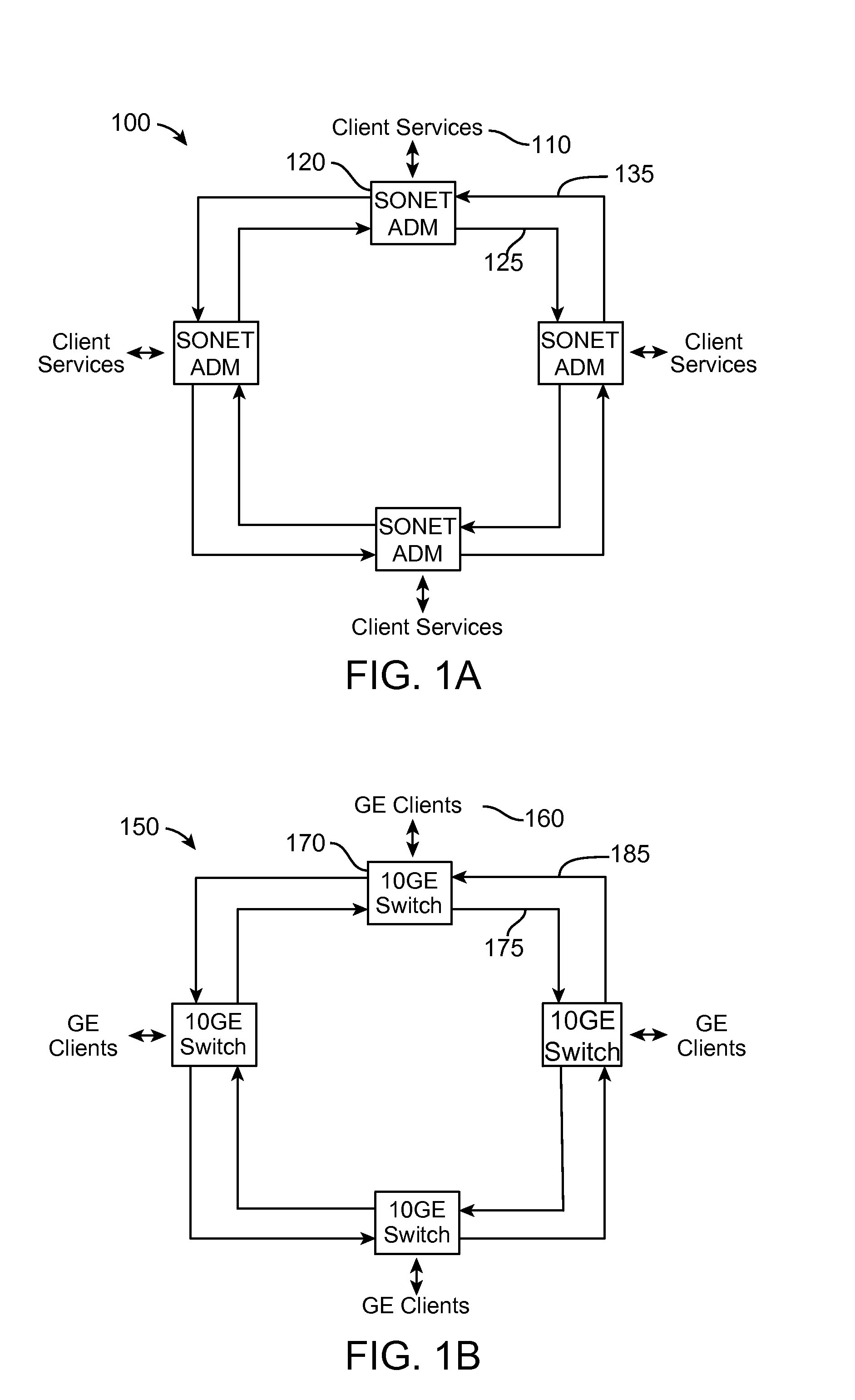
Method for designing rings in telecommunications network
InactiveUS20020036988A1Avoid less flexibilityQuicker and flexibleMultiplex system selection arrangementsInterconnection arrangementsTelecommunications networkTelecommunications link
A network design method proceeds by generating cycles, evaluating the economics of building rings on those cycle, and building any economic rings. Generating a cycle involves picking two endpoints between which two disjoint link and node paths are desired-the two nodes selected are thus nodes on the candidate rings. Once a cycle is generated, various combinations of OADM / ADM nodes on the cycle are tried, from rings using three nodes to rings using all of the nodes on the cycle. The network design method considers a sequence of SONET / SDH and DWDM rings on each cycle generated, and compares the cost of carrying demand by SONET / SDH rings, DWDM rings, and an alternative dual-hub benchmark architecture. The ring constraints such as maximum circumference are applied before ring costs are calculated, and rings violating those constraints are eliminated from consideration. The demand carried by the most economic ring is removed from the input list of demands, and the entire process is repeated until no demand remains or it is not economical to carry the remaining demands by using rings. After all economic rings are considered, any remaining demands are carried on point-to-point systems.
Owner:RSOFT DESIGN GRP
Rack mountable computer component fan cooling arrangement and method
InactiveUS20030223196A1Facilitates rearward re-direction of air flowEasy to carryBatteries circuit arrangementsDigital data processing detailsElectricityEngineering
According to certain embodiments of the invention, there is provided an arrangement for cooling a series of closely spaced upright computer components mounted to a support, the arrangement including a tray having a plurality of air moving devices such as fans. Members are used for helping mount removably the tray to the support in a generally horizontal disposition, and the air moving devices move air in a generally upright path of travel to help cool the upright computer components. The tray also has a series of connector ports for connecting electrically to outputs from individual ones of the computer components.
Owner:BOXX TECH LLC
Controller and Method for Controlling Communication Services for Applications on a Physical Network
ActiveUS20140372617A1Easy to controlEfficient networkingProgramme controlDigital computer detailsNetwork modelCalculator
A method, computer program product and controller for controlling communication services for a plurality of applications on a physical network having a plurality M of network nodes providing certain network resources, wherein each of the applications is described by a set of requirements and is configured to run on at least two of the network nodes. The controller includes a generator and a calculator. The generator generates a network model of the physical network including a topology of the physical network and a node model for each of the network nodes, where the node model describes node capabilities and node resources of the network node. The calculator calculates virtual networks for the applications by mapping each respective set of requirements of the applications to the generated network model, where each of the calculated virtual networks includes at least two network nodes and a slice of the certain network resources.
Owner:SIEMENS AG
Imaging data server and imaging data transmission system
InactiveUS20050226463A1Efficient networkingRaise priorityTelemetry/telecontrol selection arrangementsCharacter and pattern recognitionComputer scienceImaging data
The present invention relates to an imaging data server. The imaging data server acquires a plurality of types of imaging data pertaining to a plurality of objects of surveillance and transmits the acquired imaging data to a monitoring station over a network. The imaging data server comprises determination section for determining whether or not a change has arisen in the status of each of the objects of surveillance pertaining to a plurality of types of the imaging data; and a priority transmission section for transmitting, to the monitoring station, imaging data pertaining to an object of surveillance in which the status change is determined to have arisen by the determination section, with a higher priority than that utilized in the case of imaging data pertaining to an object of surveillance in which no status change is determined to have arisen.
Owner:FUJITSU LTD
Re-configurable communication device and managing method thereof
InactiveUS20080261537A1Spectrum efficiencyEfficient networkingPower managementNetwork traffic/resource managementControl signalCommunication device
A communication apparatus including a physical information recognizing module, an MAC information recognizing module, a coordinating module, and a re-configurable transmitting / receiving module is provided. The physical information recognizing module recognizes a set of physical information relative to at least one communication network. The MAC information recognizing module recognizes a set of MAC information relative to the at least one communication network. The coordinating module generates a set of control signals selectively based on the set of physical information and the set of MAC information. The re-configurable transmitting / receiving module is configured according to the set of control signals and is used for transmitting / receiving data via the at least one communication network.
Owner:MSTAR SEMICON INC
Method and system for pre-pending layer 2 (L2) frame descriptors
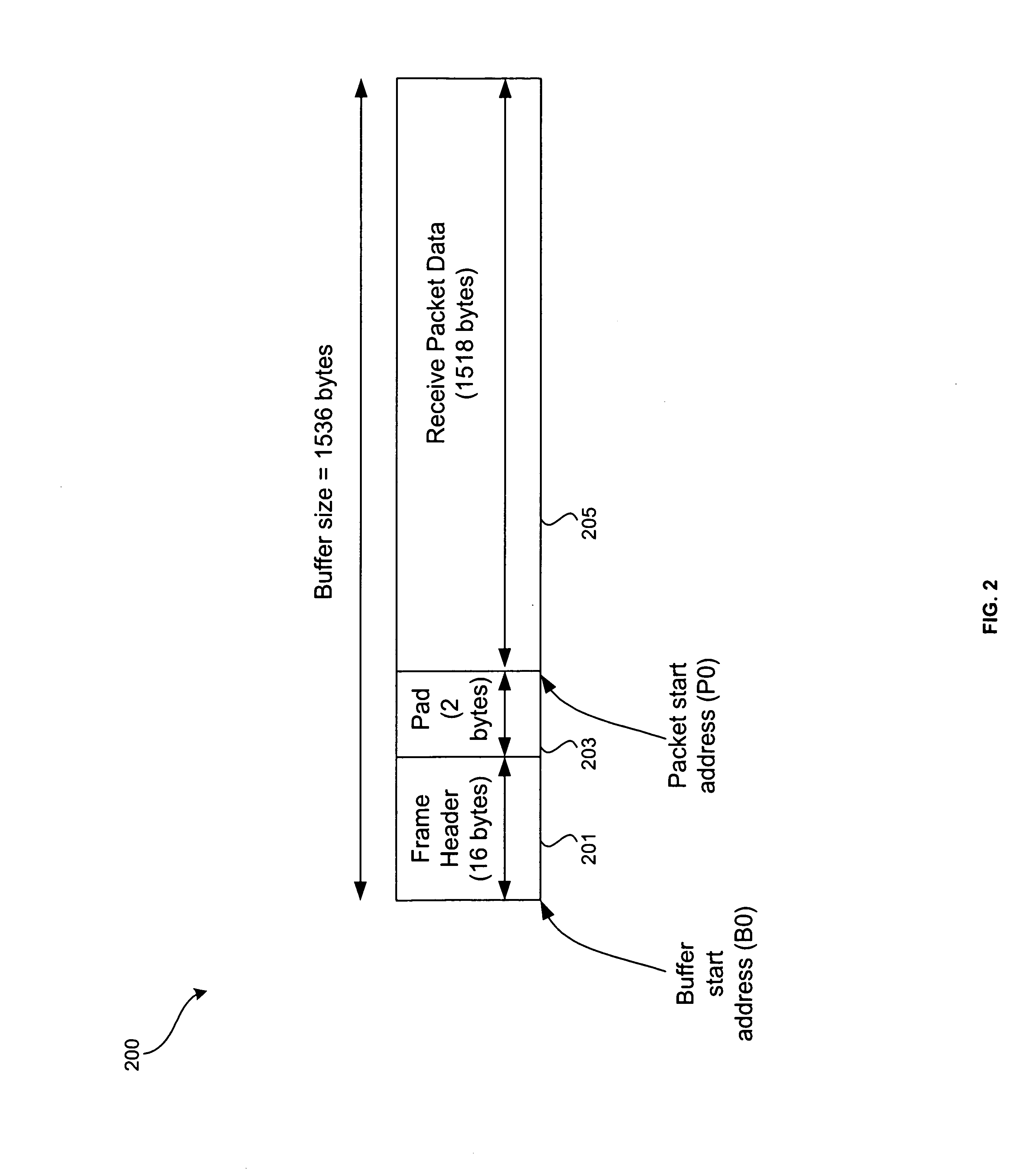
InactiveUS20050135395A1Efficiently utilize networkEfficiently processing bandwidthData switching by path configurationControl dataChecksum
Method and system for arranging and processing packetized network information are provided herein. A single receive buffer may be allocated in a host memory for storing packet data and control data associated with a packet and a single DMA operation may be generated for transferring the packet data and the control data into the single allocated receive buffer. A plurality of the single receive buffers may be arranged so that they are located contiguously in the host memory. The packet data and the control data for the packet may be written in the single receive buffer via the single DMA operation. At least one pad byte may be inserted in the single receive buffer for byte alignment. The pad may separate the control data from the packet data in the single receive buffer. The control data may comprise packet length data, status data, and / or checksum data.
Owner:AVAGO TECH WIRELESS IP SINGAPORE PTE
Dynamic multiple access for distributed device communication networks with scheduled and unscheduled transmissions
ActiveUS20190132196A1Preventing network saturationMinimizing data collisionData switching networksWireless communicationComputer networkPacket switch
Disclosed herein are systems and networks comprising a network operations server application for improving a packet-switched communications network, the application configured to: receive data from data source nodes; provide a management console allowing a user to configure a network multi-access protocol for: i) a node, ii) a type of node, iii) a group of nodes, iv) a type of data packet from a node, v) a type of data packet from a type of node, vi) a type of data packet from a group of nodes, or vii) a specific instance of a data packet from a node, the network multi-access protocol a scheduled or random access protocol; and dynamically create channel assignments to allocate bandwidth of the network among channels based on the configured network multi-access protocols to prevent network saturation and minimize data collisions in the packet-switched network.
Owner:SKYLO TECH INC
MAC aggregation frame with MSDU and fragment of MSDU
ActiveUS7630403B2Reduce errorsEasy to useError prevention/detection by using return channelSpatial transmit diversityTraffic capacityReal-time computing
Owner:TEXAS INSTR INC
Technique for establishing a virtual backbone in an ad hoc wireless network
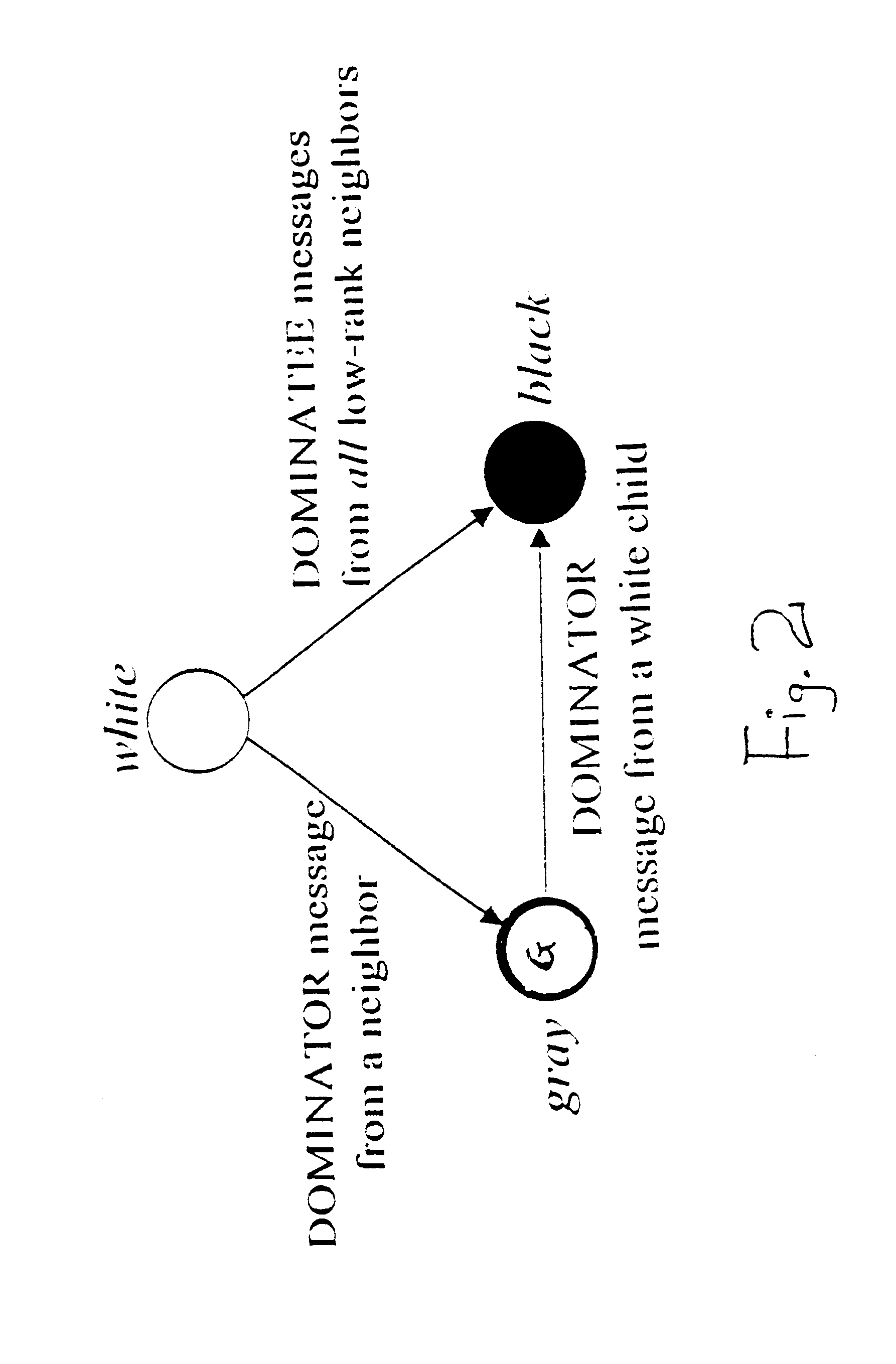
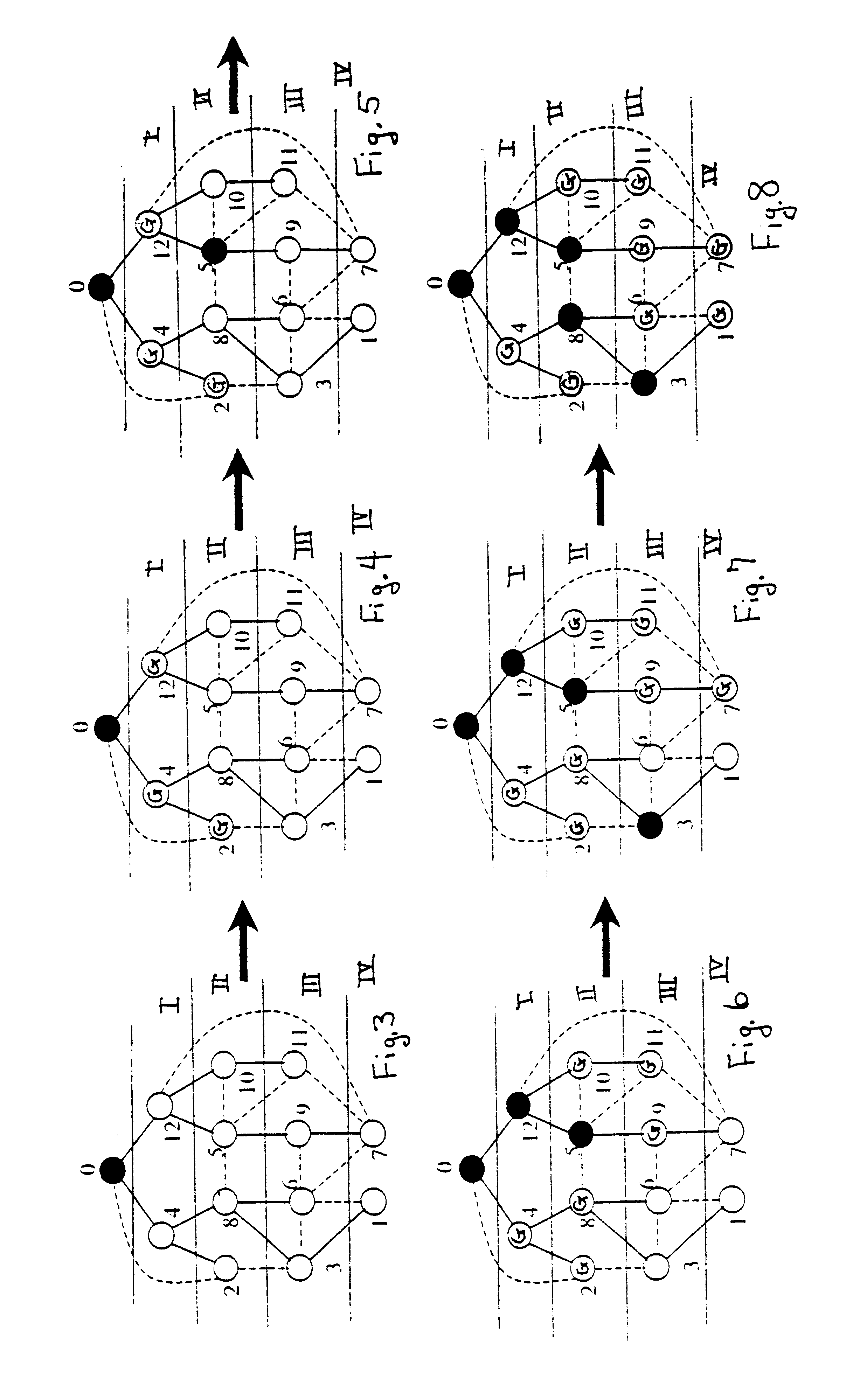
InactiveUS6839541B2Efficient processReduce the burden onNear-field transmissionNetwork topologiesLeader electionWireless mesh network
An algorithm on a computer readable medium for efficiently creating a message efficient virtual backbone in a wireless ad hoc network utilizes three phases to establish an efficient network among the independent transceivers of a wireless ad hoc network. Independent transceivers within the transmission range of each other are neighbors. A leader election and tree construction phase constructs a tree of neighboring transceivers with one transceiver being designated the root and with each transceiver establishing and recording its location in the tree structure and the identifiers of its neighbors; and reporting when the tree is established. A level calculation phase determines the level of each transceiver away from the root transceiver, with each transceiver recording the level of its neighbors. Precedence for each transceiver is established with consideration of each transceiver's tree level and identifier, with tree level being paramount in deciding precedence; and reporting when the levels of the tree are established. A backbone construction phase establishes all transceivers as a dominator or a dominatee, with the dominators forming the network backbone and the dominatees all being neighbors to a dominator. Within the network each transceiver only needs to know the information of its neighboring transceivers.
Owner:ILLINOIS INSTITUTE OF TECHNOLOGY
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com