Patents
Literature
652 results about "Computer file" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A computer file is a computer resource for recording data discretely in a computer storage device. Just as words can be written to paper, so can information be written to a computer file. Files can be edited and transferred through the internet on that particular computer system.
Method, system and computer program product for detecting at least one of security threats and undesirable computer files
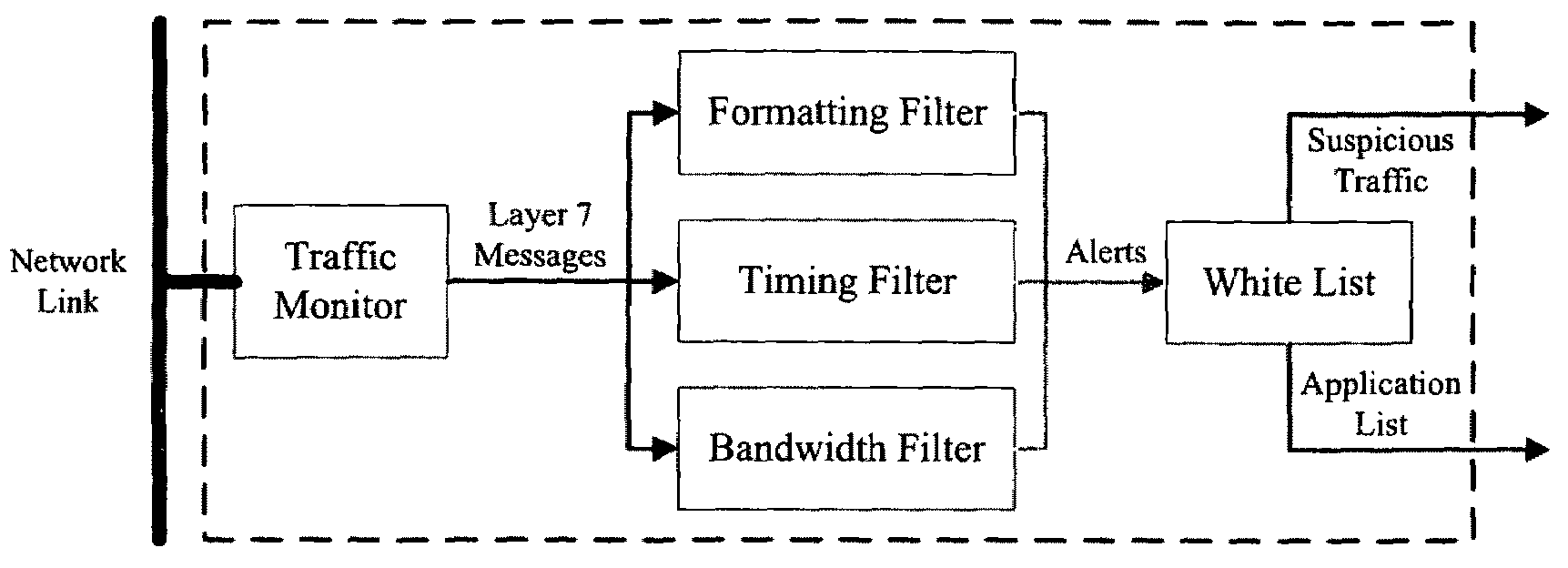
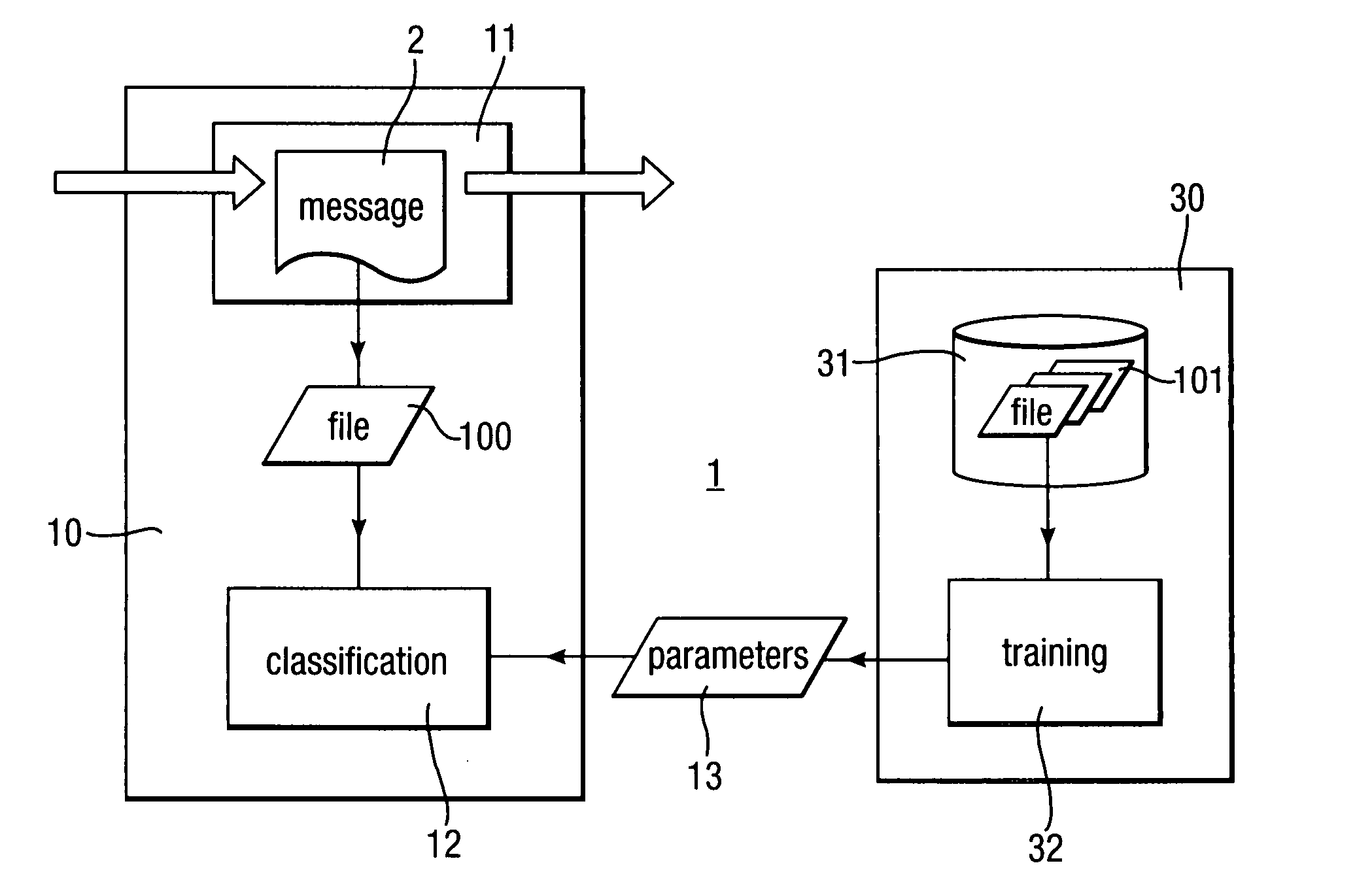
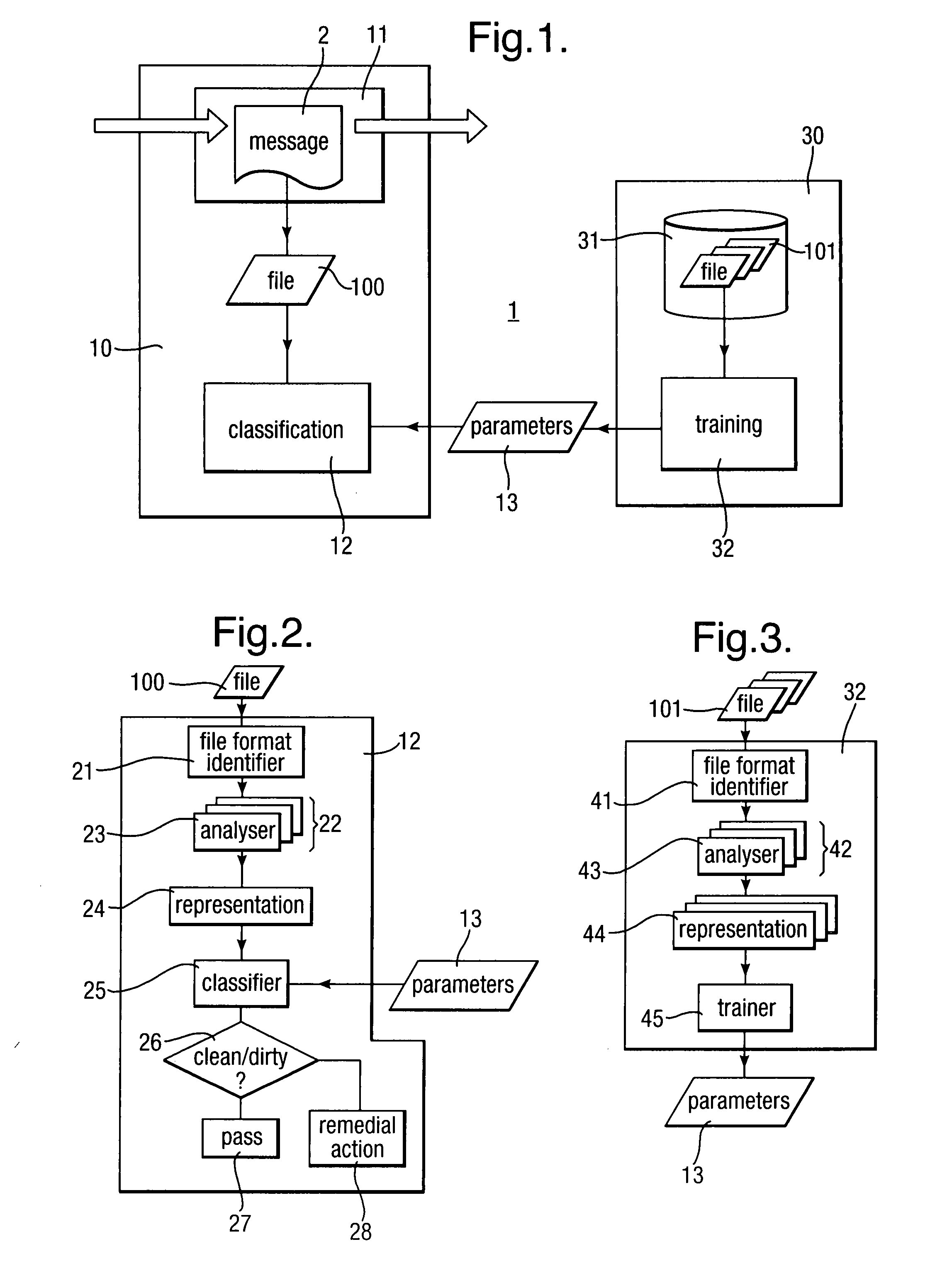
Method, system and computer program product for detecting at least one of security threats and undesirable computer files are provided. A first method includes receiving a data stream which represents outbound, application layer messages from a first computer process to at least one second computer process. The computer processes are implemented on one or more computers. The method further includes monitoring the data stream to detect a security threat based on a whitelist having entries which contain metadata. The whitelist describes legitimate application layer messages based on a set of heuristics. The method still further includes generating a signal if a security threat is detected. A second method includes comparing a set of computer files with a whitelist which characterizes all legitimate computer files. The whitelist contains one or more entries. Each of the entries describe a plurality of legitimate computer files.
Owner:SYROWIK DAVID R
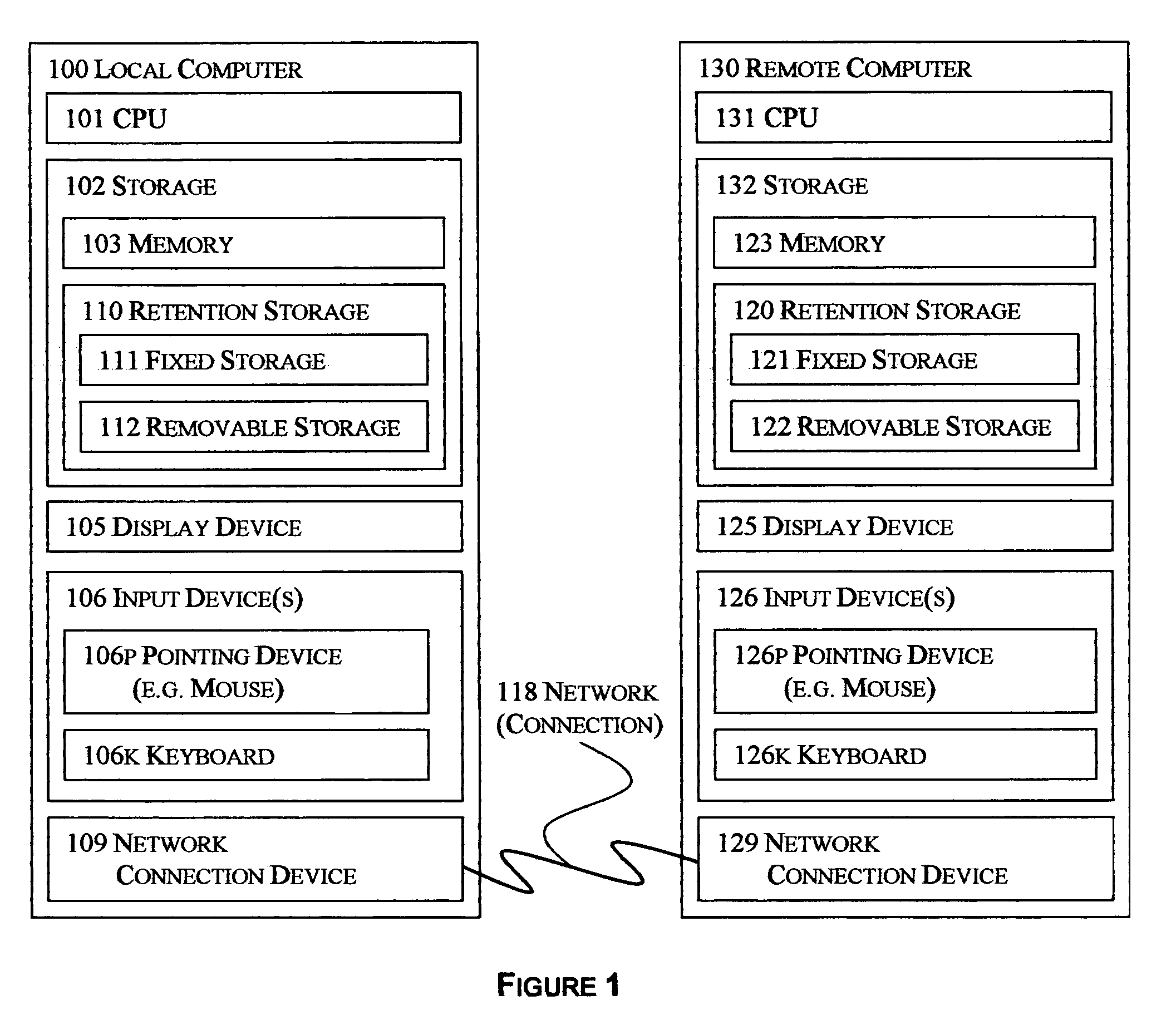
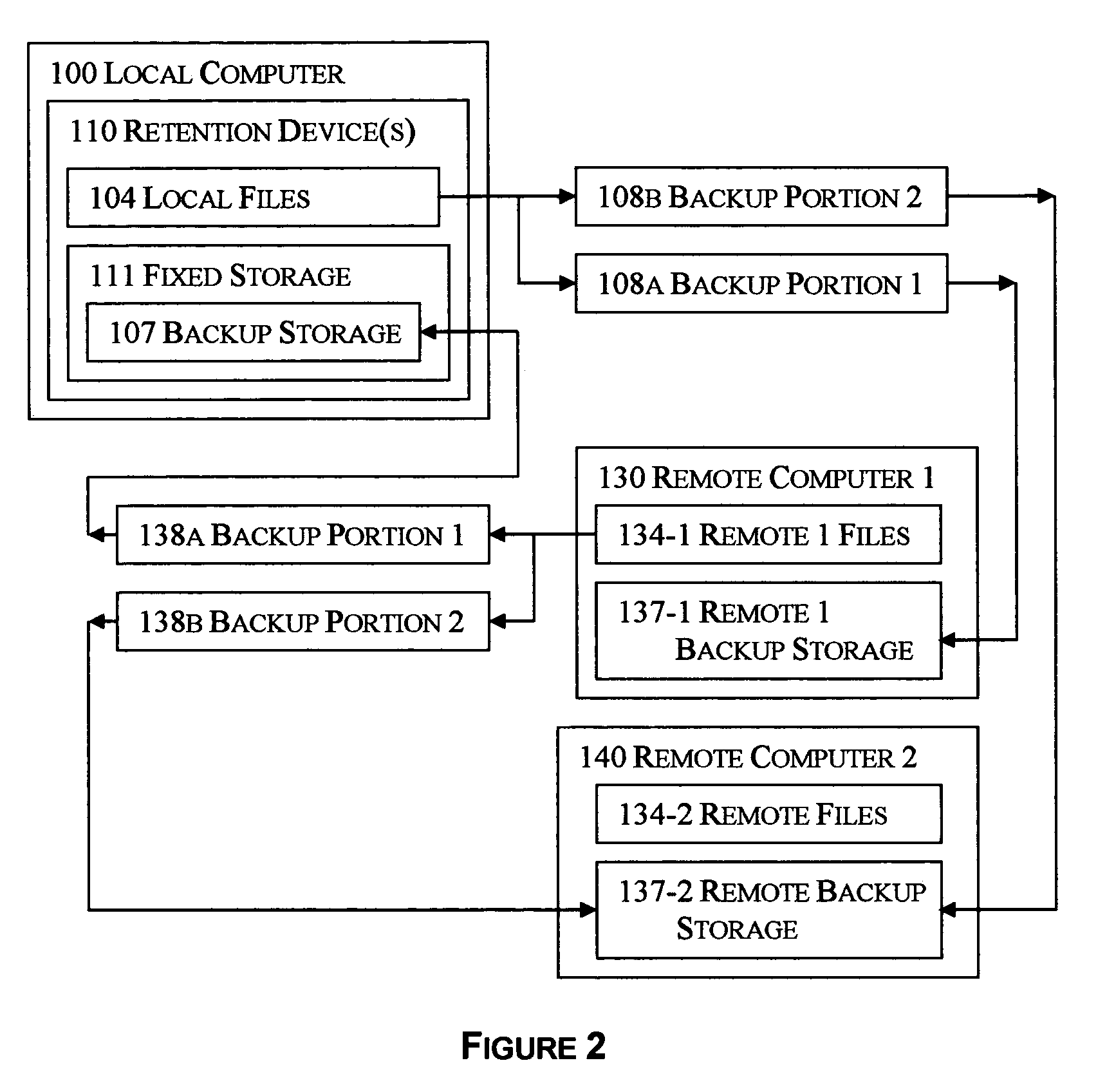
Selective reciprocal backup
InactiveUS7330997B1Risk minimizationIncrease probabilityError detection/correctionMemory systemsNetwork connectionApplication software
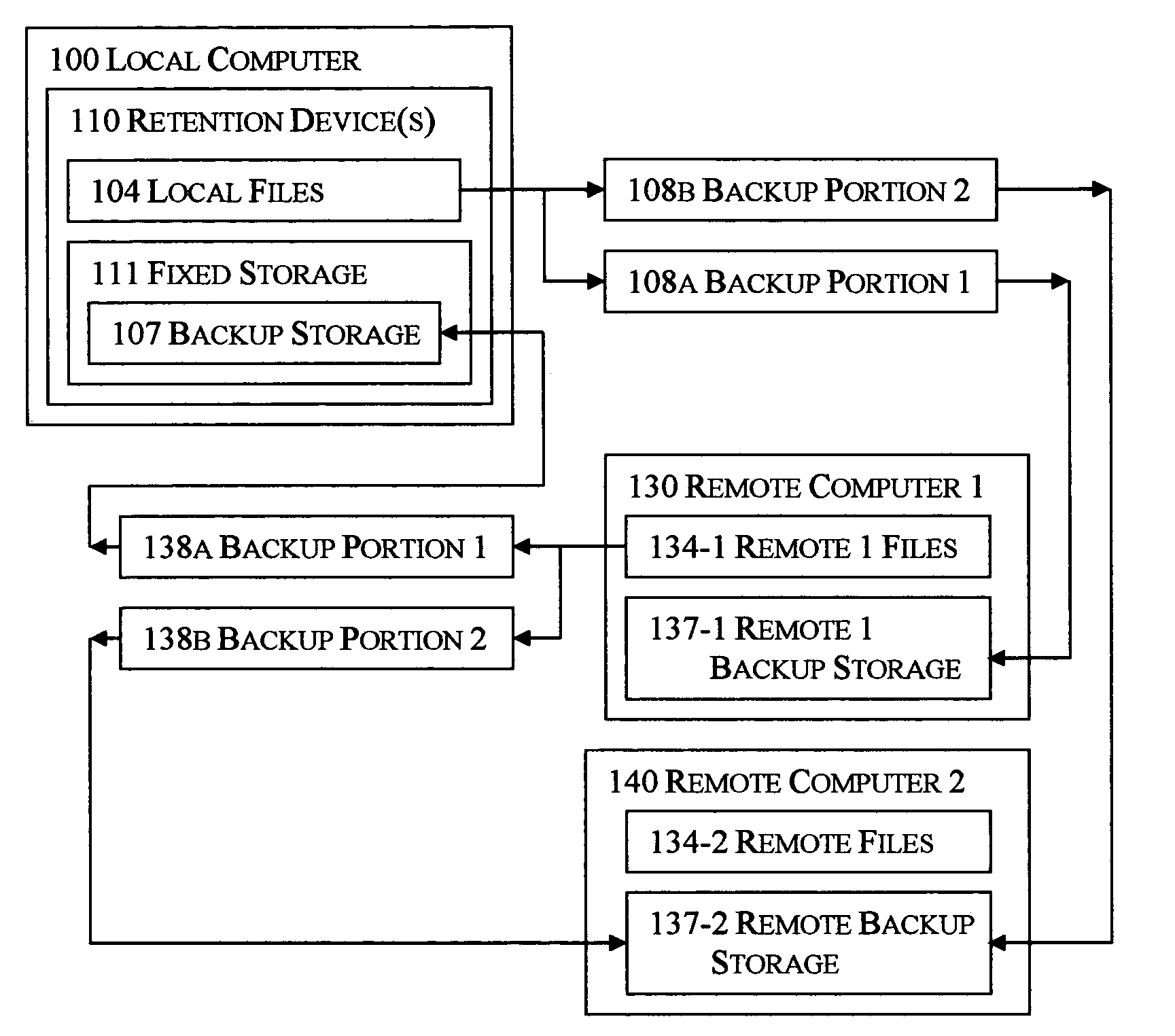
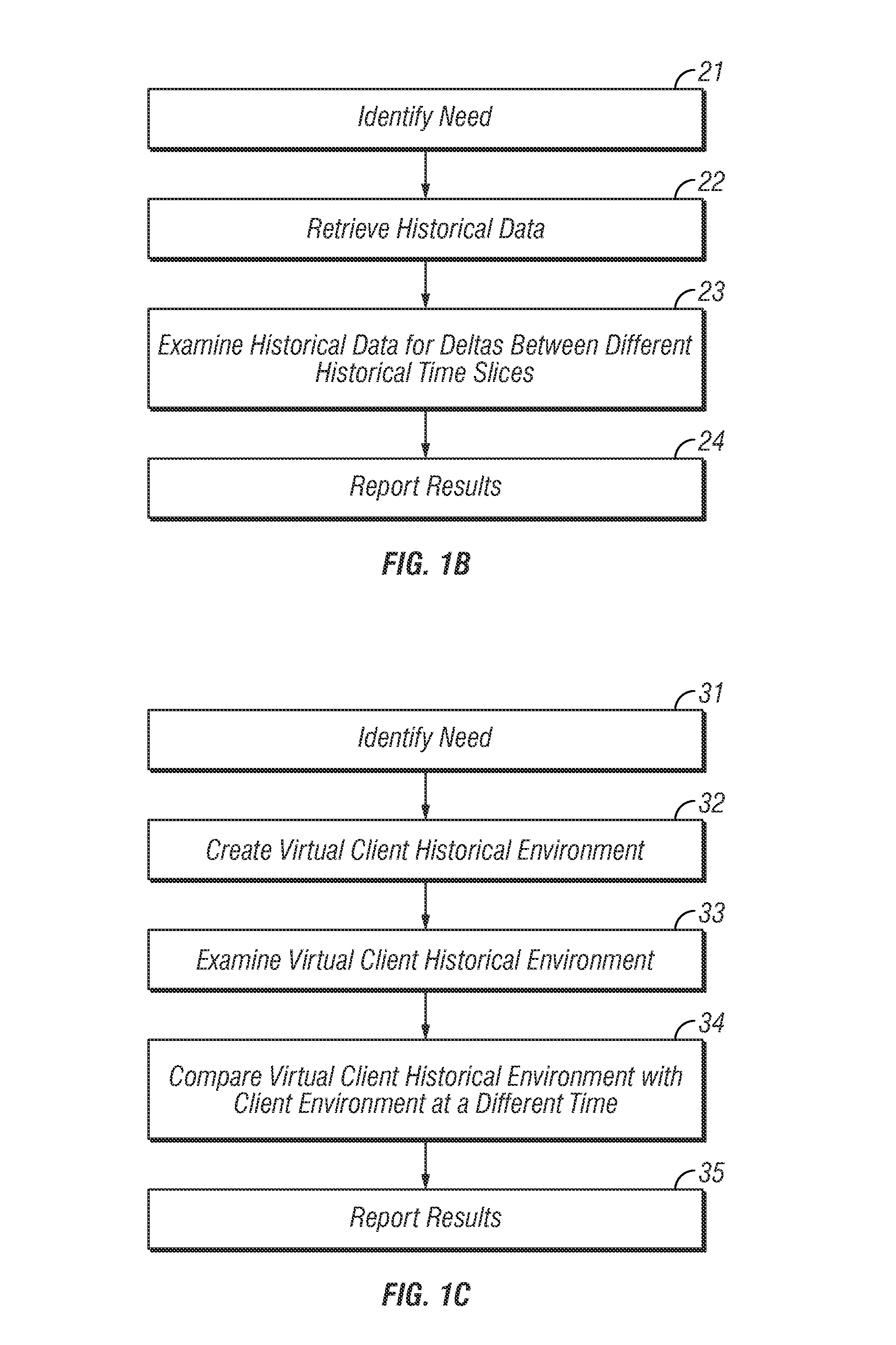
The disclosed technology applies the principle of anonymous reciprocity to facilitate remote backups. A local computer stores other computer's backup files, while storing backup copies of local files on other computers connected through a network. Each computer may securely maintain and manage storage for other computers' files. Application may be constrained to a local area network, or work on the Internet. The disclosed technology works in a peer-to-peer environment; no central server is required. The same disclosed technology may also apply to file sharing.
Owner:ODOM GARY
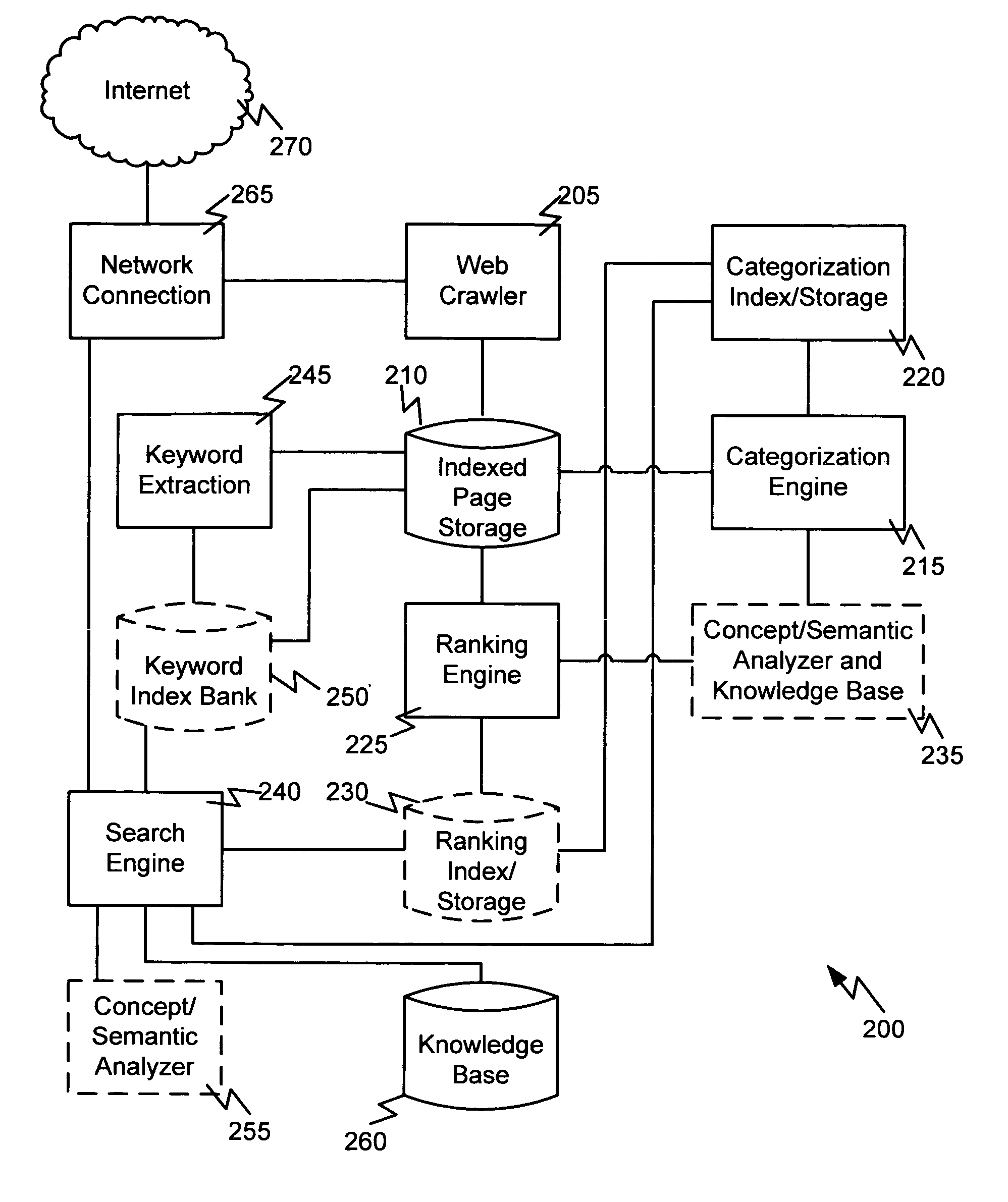
Advanced search, file system, and intelligent assistant agent
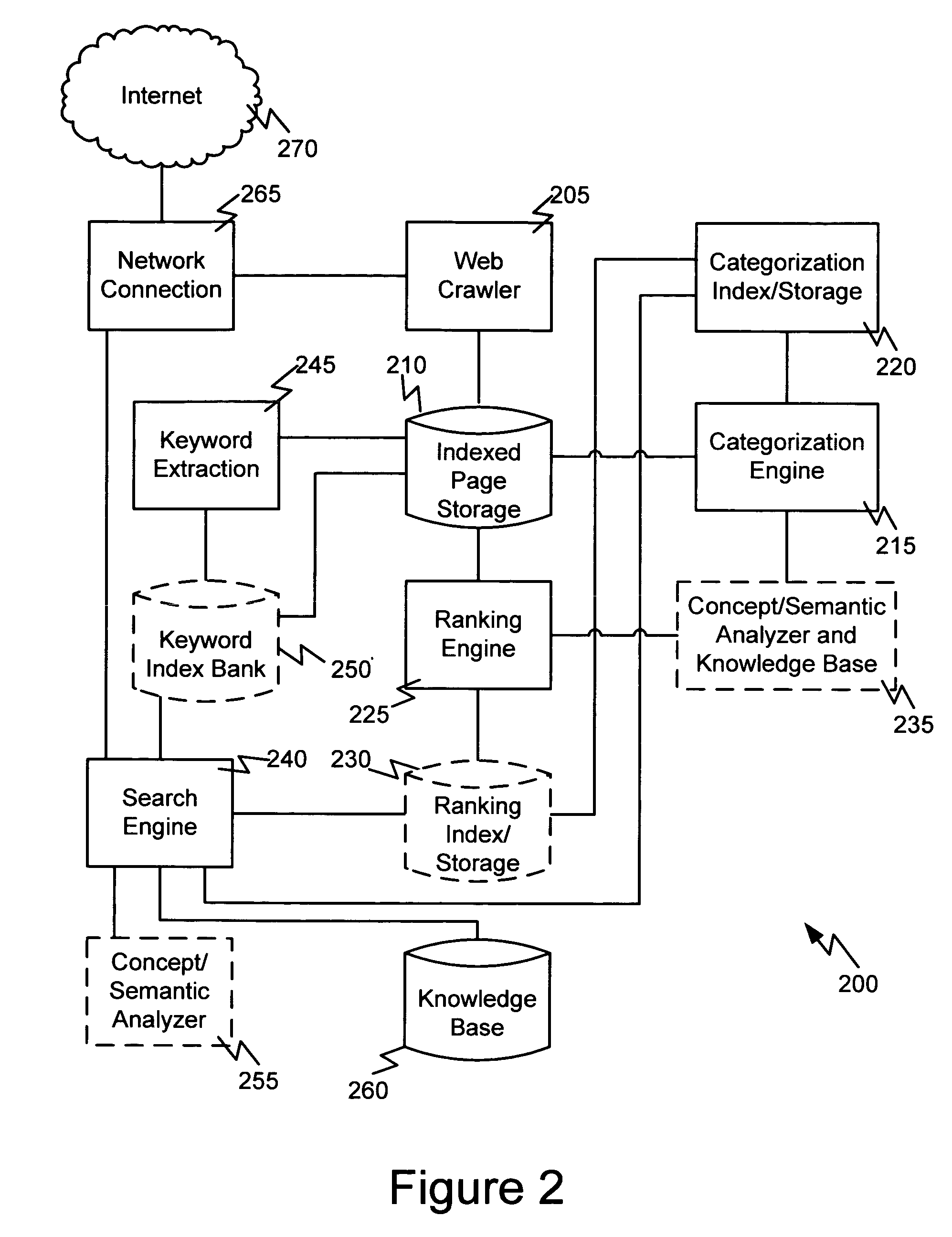
The present invention presents embodiments of methods, systems, and computer-readable media for advanced computer file organization, computer file and web search and information retrieval, and intelligent assistant agent to assist a user's creative activities. The embodiments presented herein categorize search results based on the keywords used in the search, provide user selectable ranking, use user's search objectives and advices to refine search, conduct search within an application program and using a file based, provide always-on search that monitors changes over a period of time, provide a high level file system that organizes files into categories, according to relations among files, and in ranking orders along multiple categorization and ranking dimensions and multiple levels of conceptual relationships, conduct searches for associations between keywords, concepts, and propositions, and provide validations of such associations to assist a user's creative activity.
Owner:LIANG PING
Device, System and Method for Storage and Access of Computer Files
InactiveUS20070226320A1Digital data information retrievalMultiple digital computer combinationsFile systemClient server systems
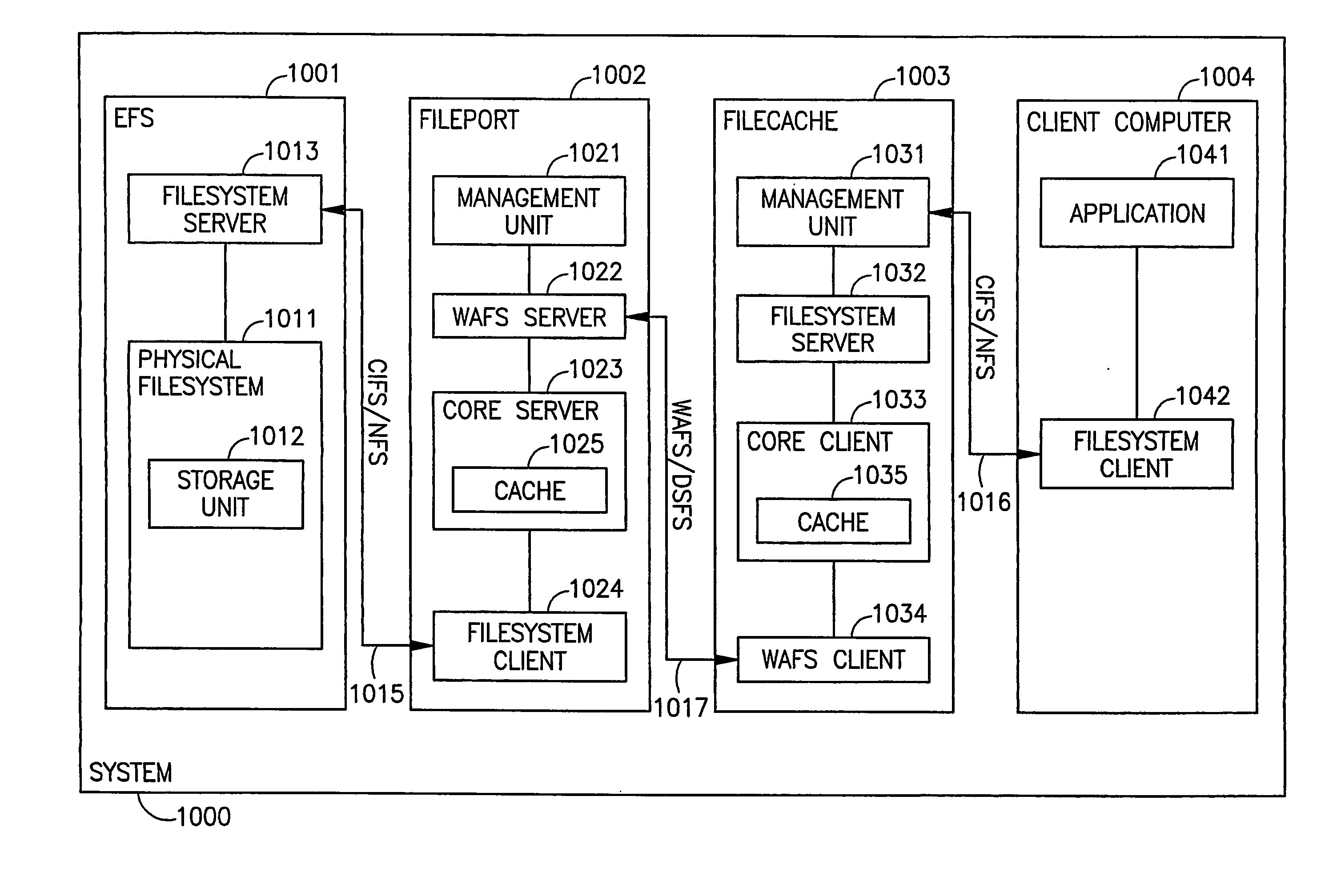
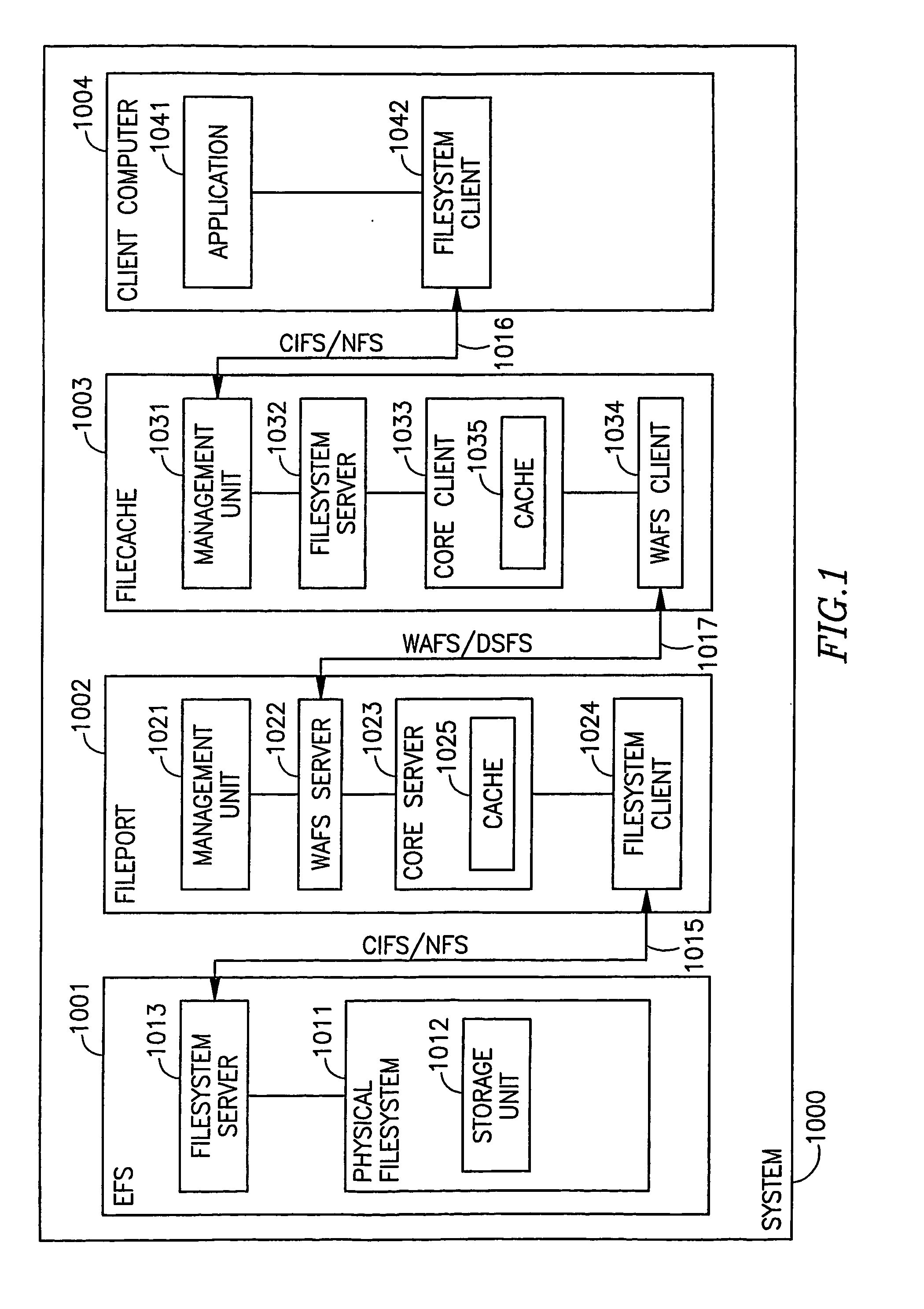
Briefly, some embodiments of the invention provide, for example, devices, systems and methods for storage and access of computer files. A method in accordance with an embodiment of the invention may include, for example, receiving from a remote site a request to access a first file having a plurality of blocks, said request having a pre-defined format encapsulating an original request of a client of a synchronous client-server system and in accordance with a pre-defined file system; determining, for each of at least some of said plurality of blocks, a differential portion representing a difference between each said block and a corresponding block of a second file; and sending said differential portion to said remote site.
Owner:DISKSITES RES & DEV
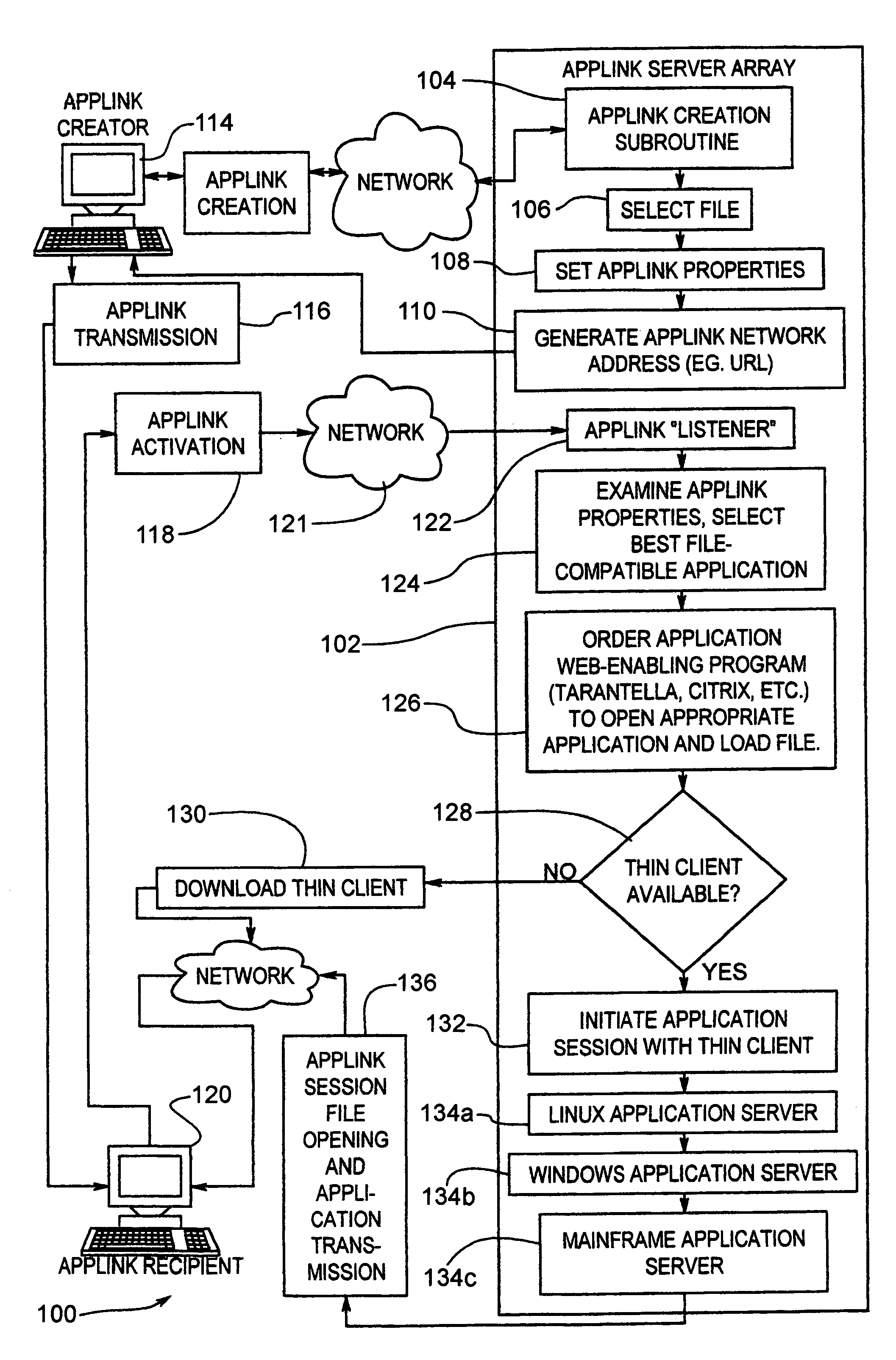
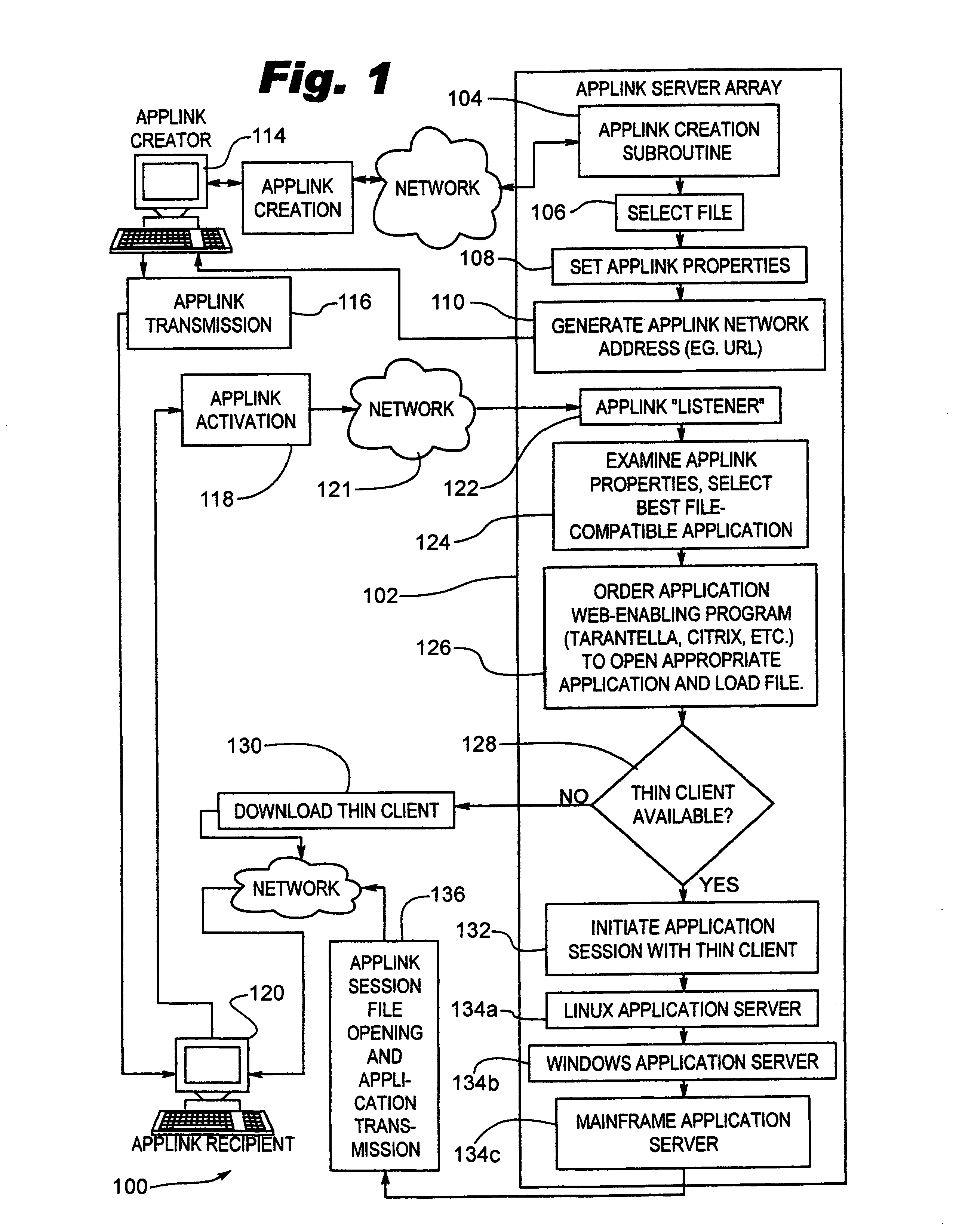
System and method of permissive data flow and application transfer
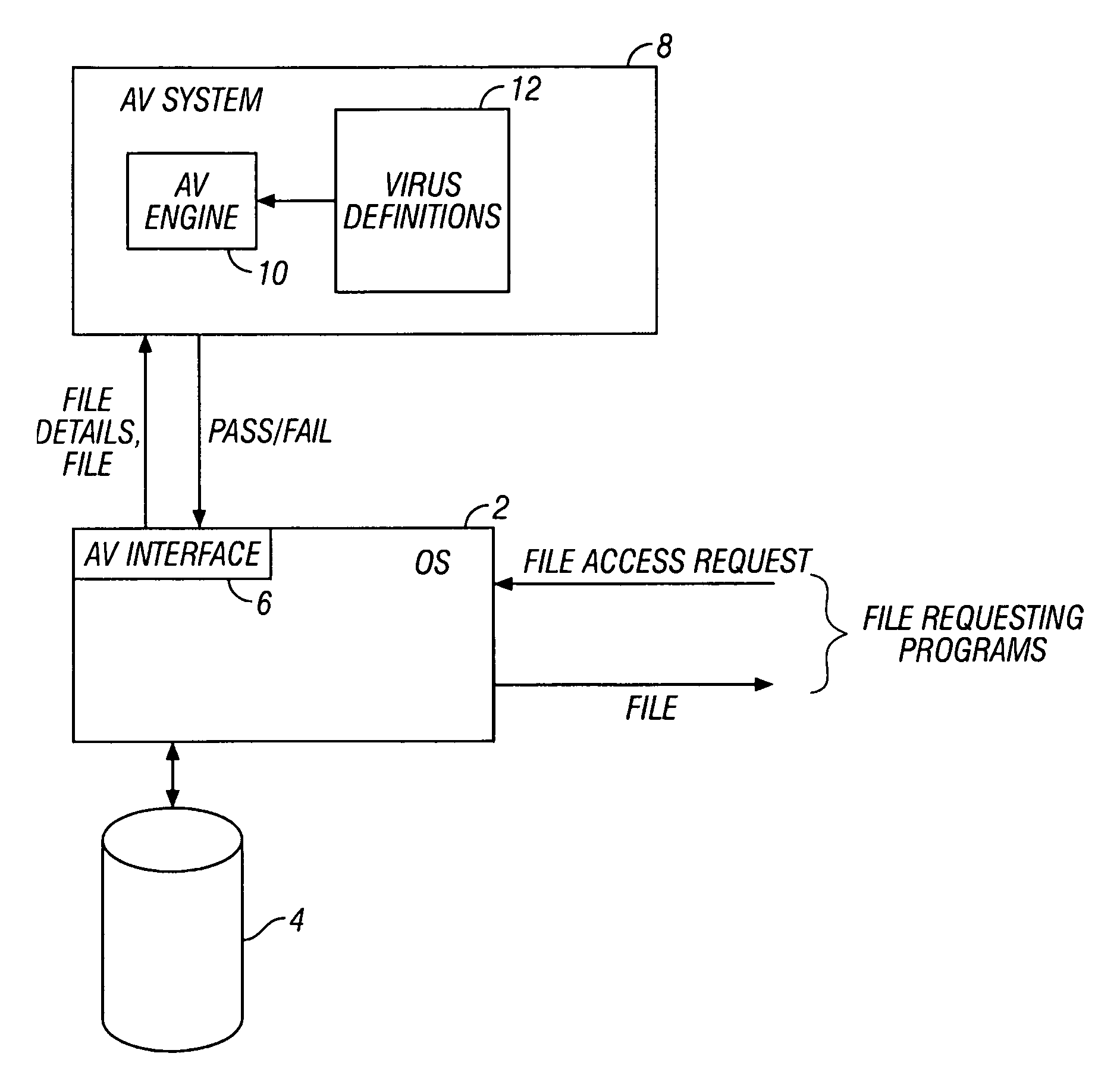
ActiveUS7424543B2Television system detailsDigital data information retrievalData streamApplication software
A computer system and computer control software is provided which allows for secure document delivery between remote parties, and control by the sender of the further distribution and handling by the recipient of an electronic document or other computer file. A file in an application may be stored on a server and manipulated by the file's native application. The recipient of the file information is given preferably automatic operation to view the user output of the server application, via a thin-client system. The recipient of the file is thus limited, as dictated by the sender, as to the operations it can perform on the document via the server application. Files attached to electronic messages may also be removed and stored on a server, thus eliminating any possible effect on the recipient machine by the computer file. Also provided for is an adaptable thin-client system which adapts to local environmental and use conditions to provide the correct degree of thin-client or local application reliance.
Owner:JOLLY SEVEN SERIES 70 OF ALLIED SECURITY TRUST I
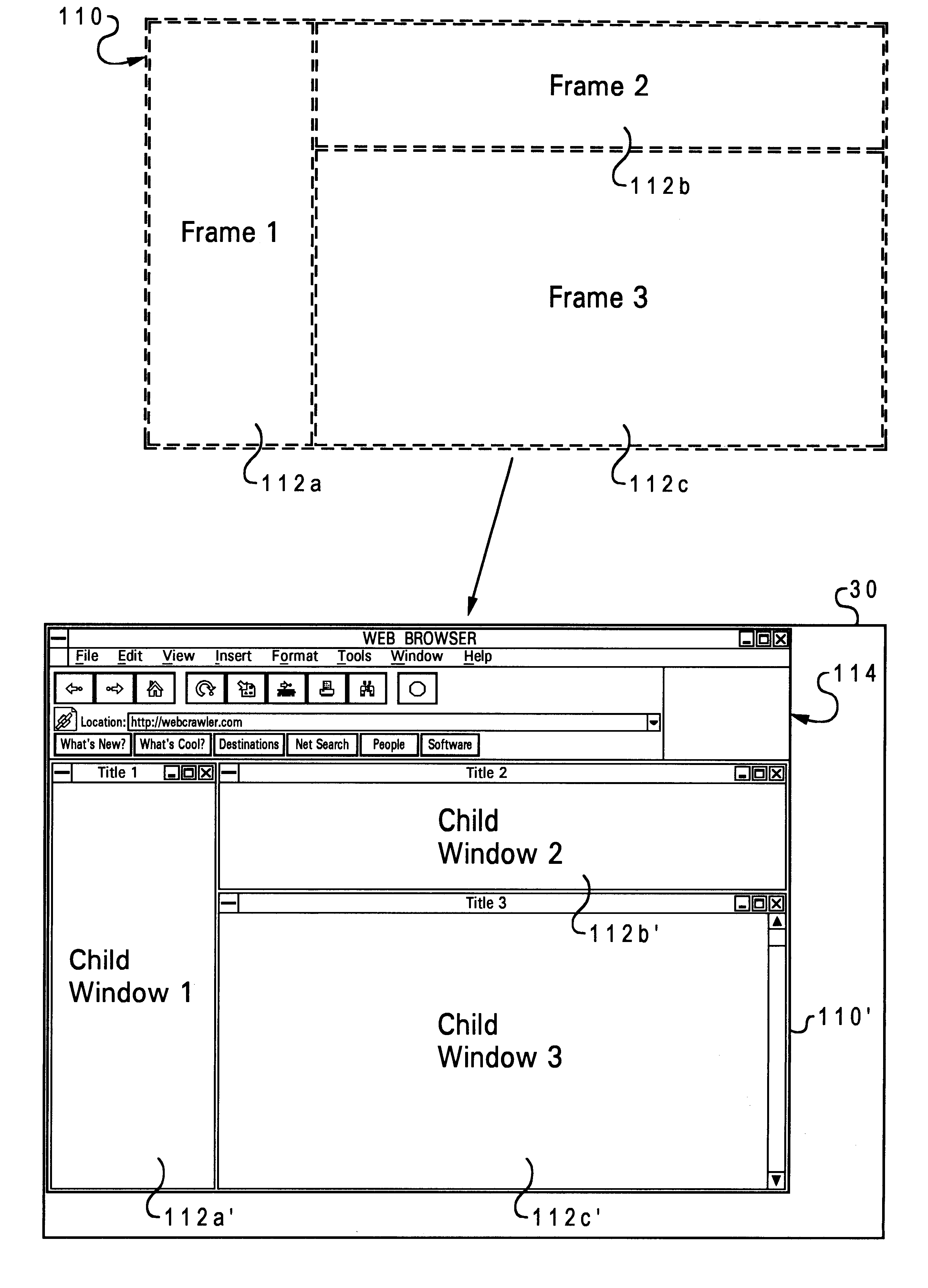
Display mechanism for HTML frames
InactiveUS6313854B1Cathode-ray tube indicatorsExecution for user interfacesComputer graphics (images)Computerized system
A method of accessing an electronic page on a computer system, by ascertaining that the electronic page is adapted to be displayed as a single window containing a plurality of frames (having fixed attributes), but then displaying separate windows for respective frames, and enabling one or more window operations for each of the windows, such as resizing, minimizing, maximizing, and closing each of the windows. The windowed frames can be displayed as child windows within a parent window on the display device, or in separate parent windows. The frame windowing mode can be toggled between active and inactive states. Initial attributes of the windows can be based on the frame attributes of the respective frames. These attributes can be ascertained by interpreting tags in a main computer file associated with the electronic page, e.g., an HTML file which is downloaded over the World Wide Web.
Owner:IBM CORP
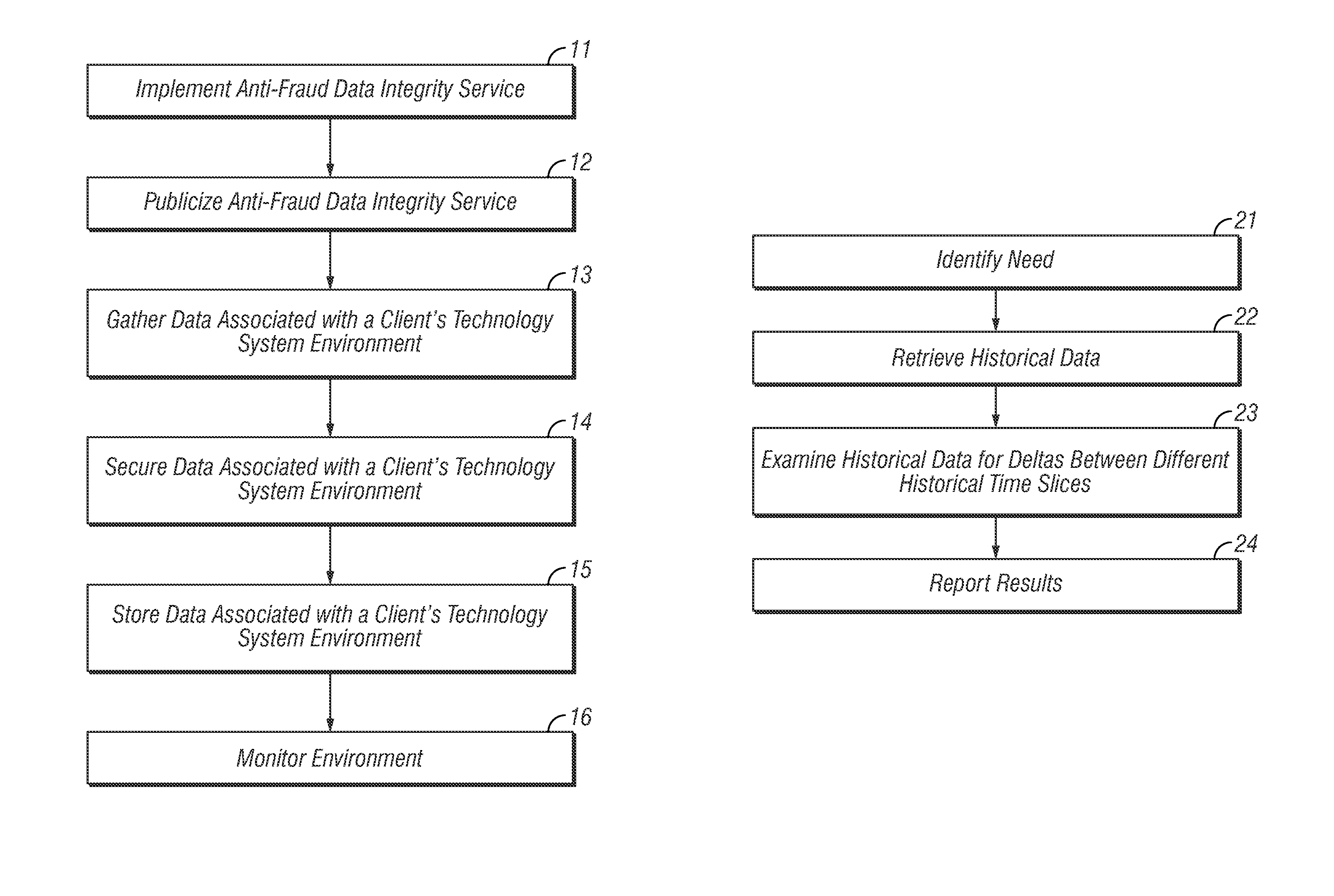
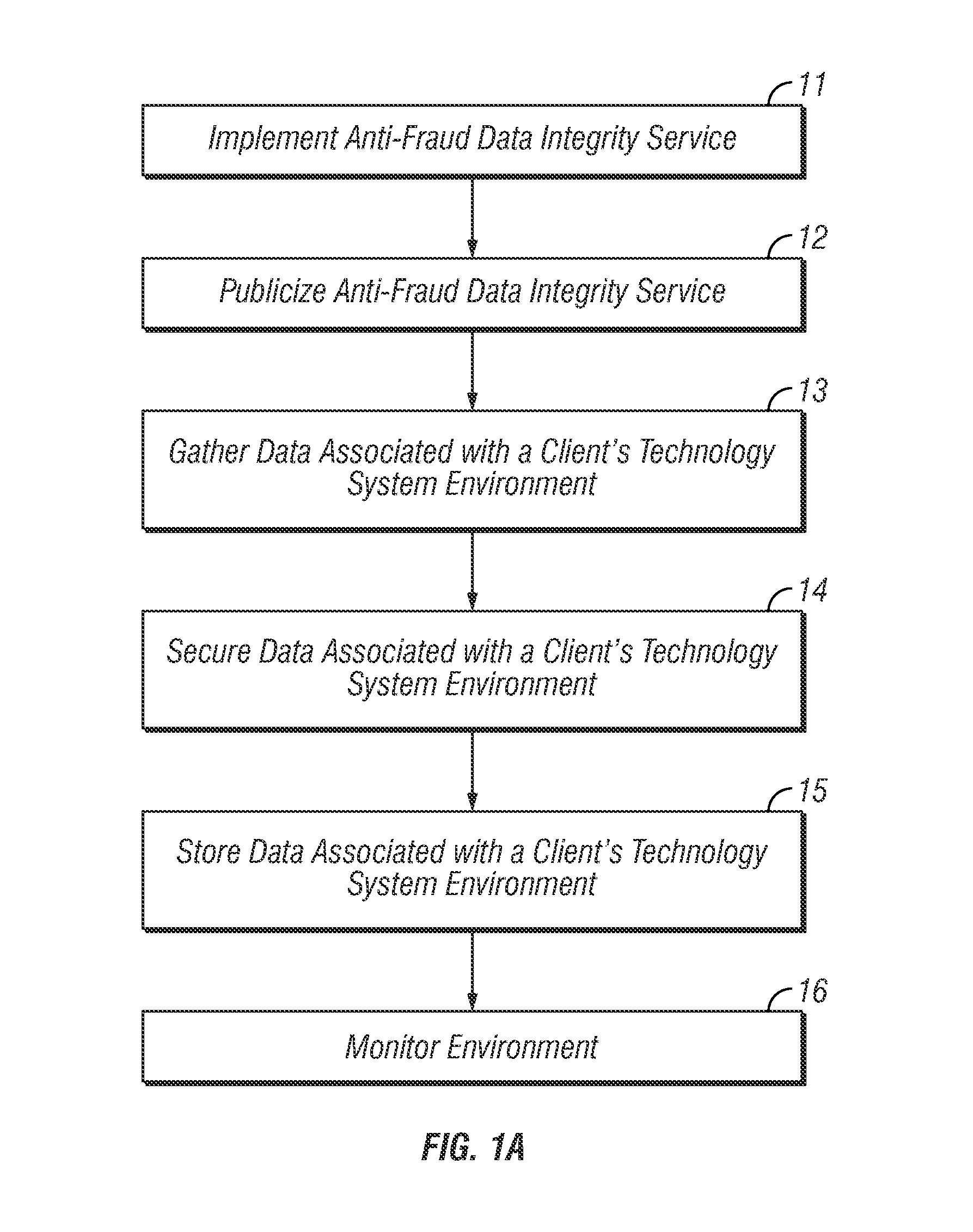
Method and apparatus for maintaining high data integrity and for providing a secure audit for fraud prevention and detection
ActiveUS8805925B2Easy to findReduce the burden onComplete banking machinesFinanceData integrityInvoice
Owner:NBRELLA
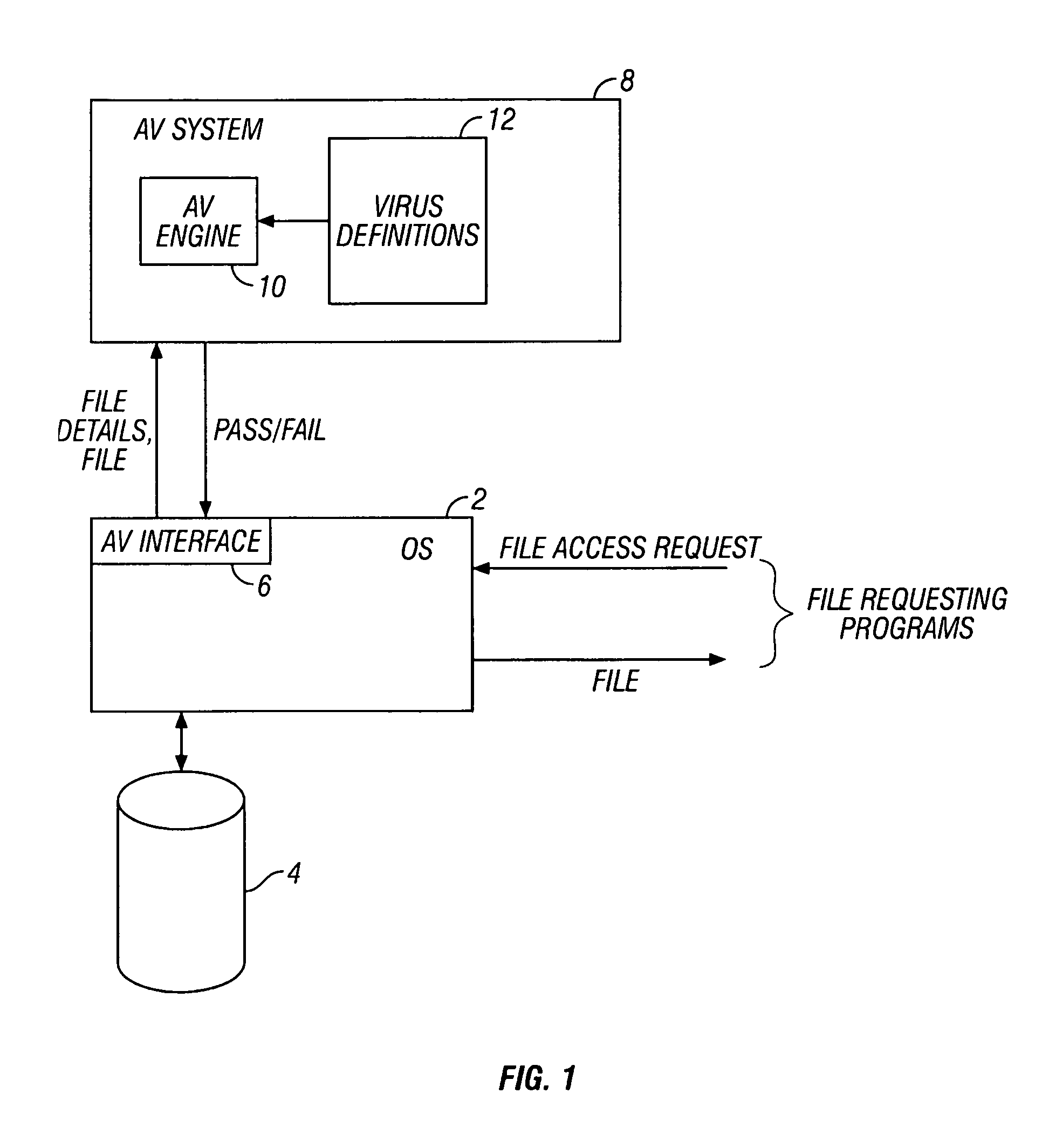
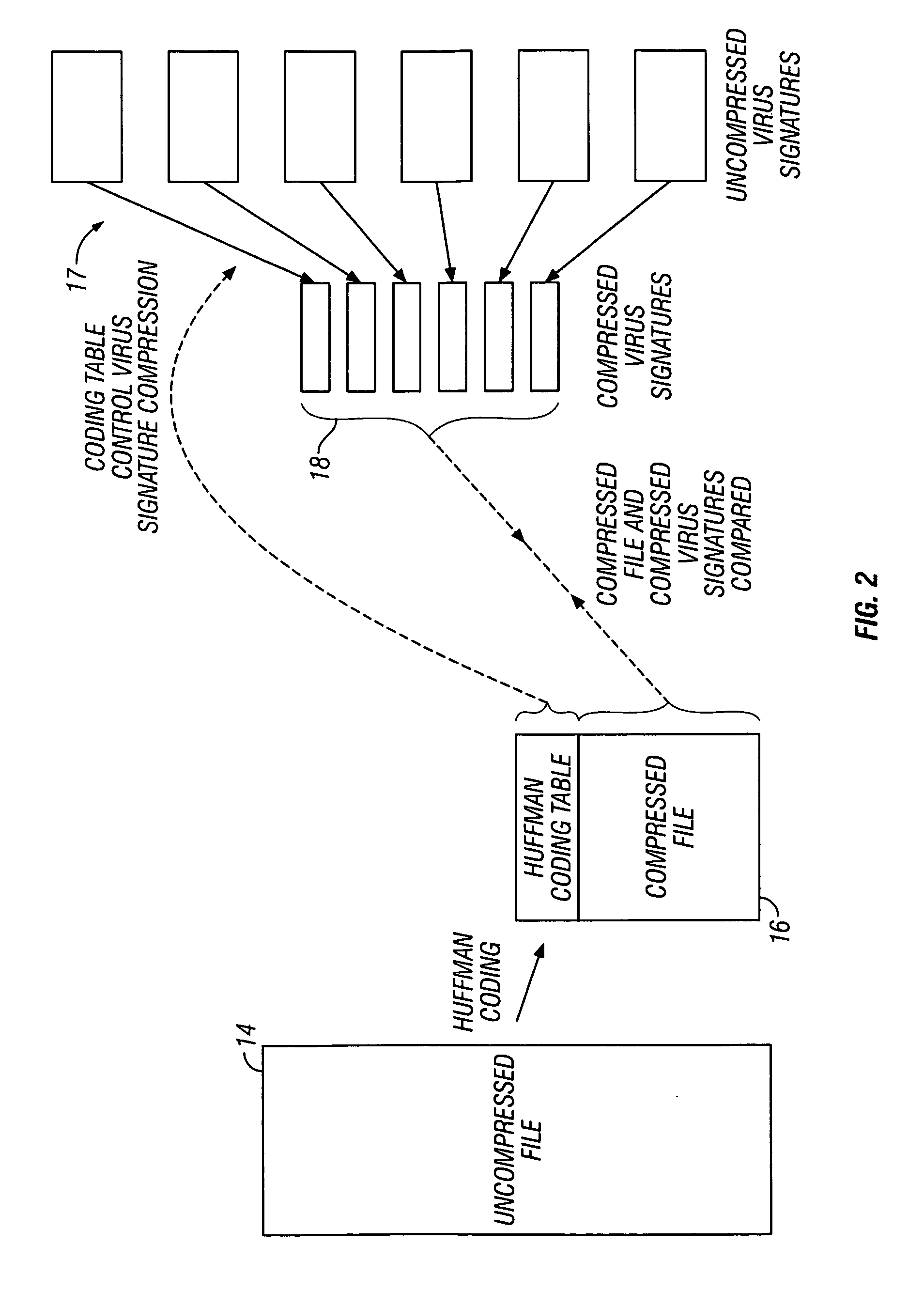
Malware scanning of compressed computer files
ActiveUS7107617B2Improve efficiencyMemory loss protectionError detection/correctionMalwareComputer file
A malware scanner (8) operates to scan compressed computer files (16) by compressing the malware signatures (17) using the same compression algorithm as used for the compressed computer file and then comparing the compressed malware signatures (18) with the compressed computer file directly.
Owner:FENCE WORKS INC +1
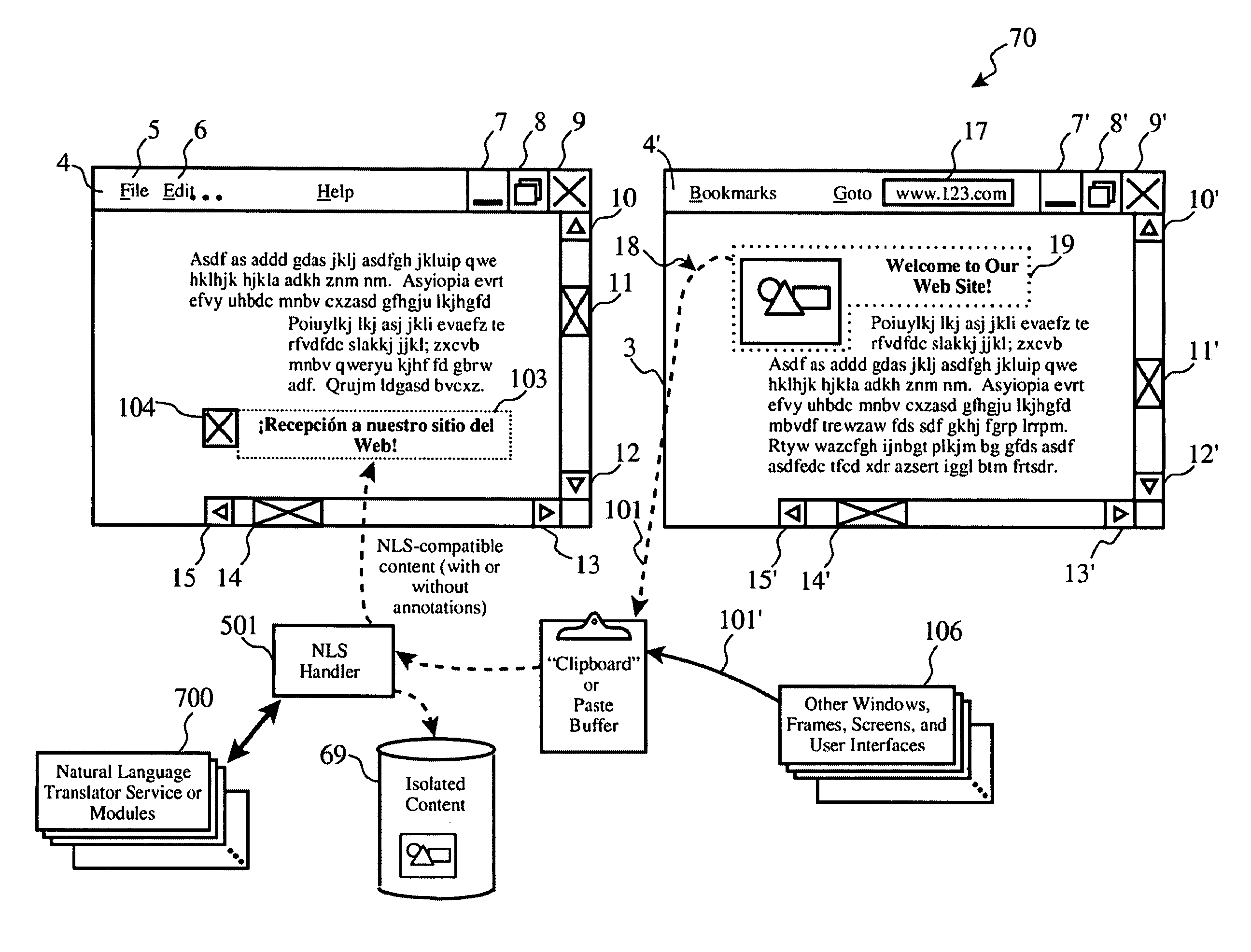
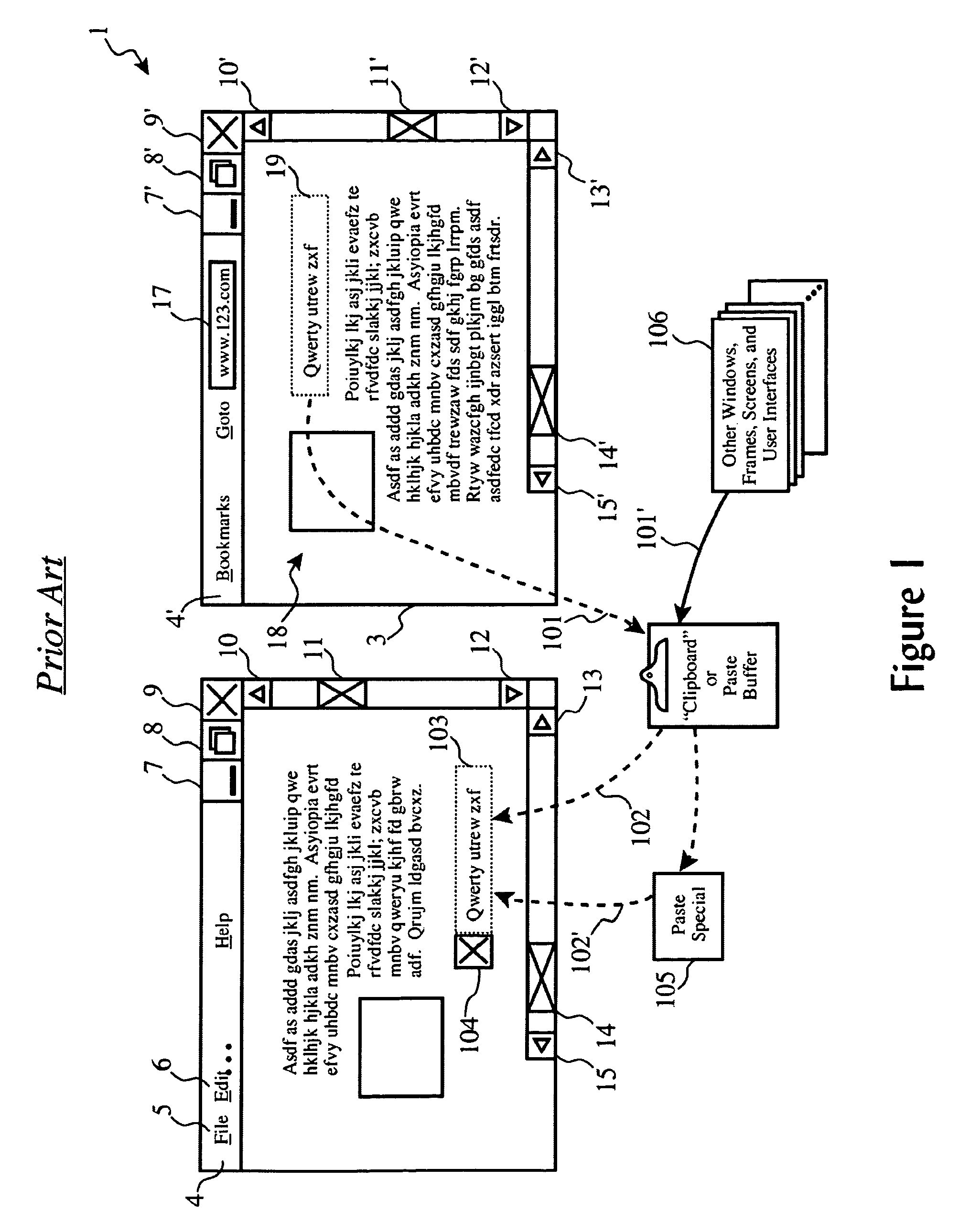
Automatic natural language translation of embedded text regions in images during information transfer
ActiveUS8031943B2Character and pattern recognitionNatural language data processingImaging dataInformation transfer
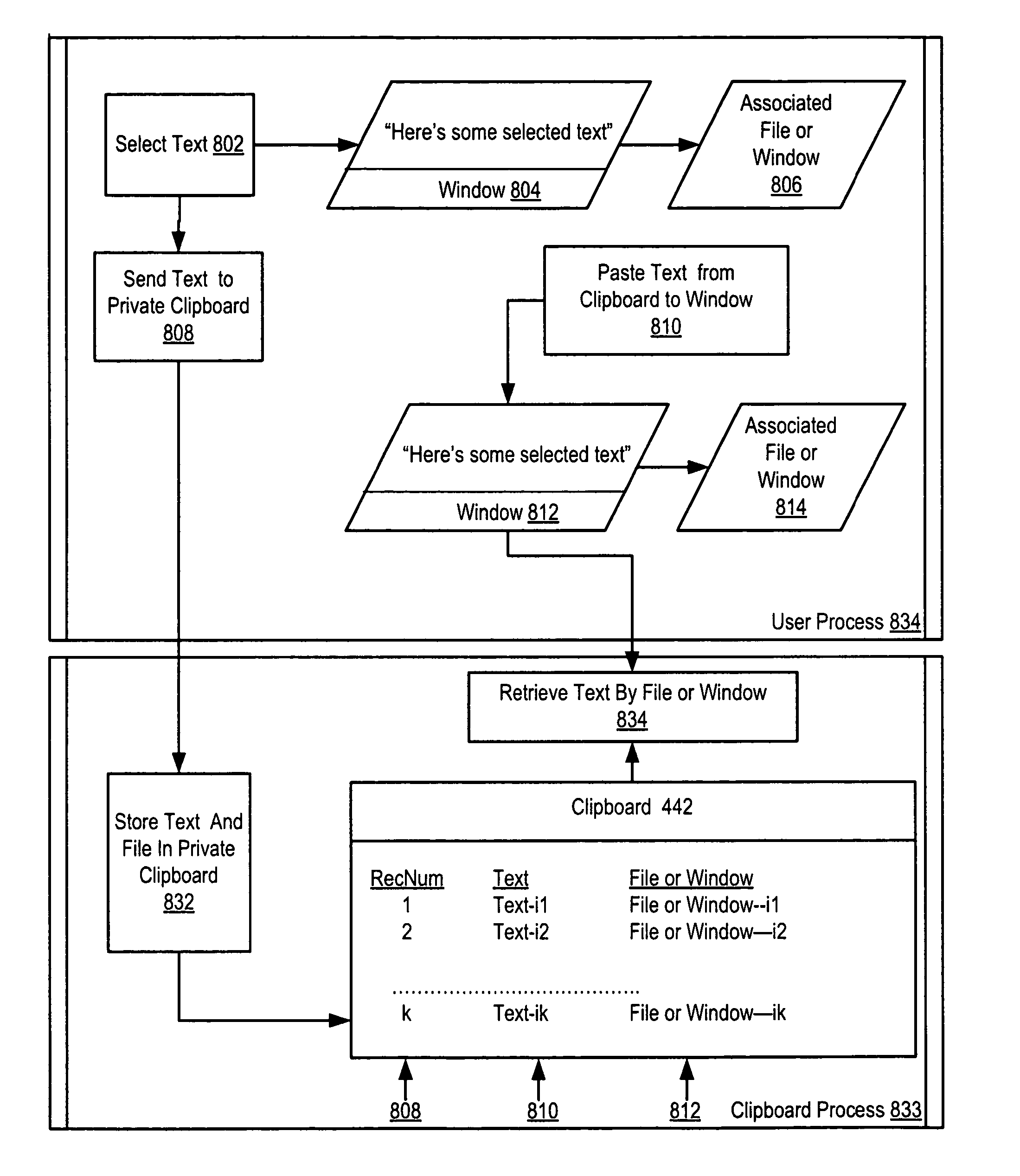
Text regions of natural language embedded in images are automatically translated via a clipboard buffer during a cut-and-paste command according to an isolation rule defining one or more types of image elements to be isolated, by examining the image elements, responsive to meeting the isolation rule, transferring the image element from the clipboard to an isolation store, disabling pasting of the image element; recognizing text within the isolated image; determining a natural language in which the recognized text is expressed; performing natural language translation of the recognized text into a user-specified destination natural language; producing image data for the translated text; overlaying the image data onto the embedded text in the isolated image element; and pasting the modified image element from the isolation store to a user-designated destination points within a destination computer file.
Owner:GOOGLE LLC
Advanced search, file system, and intelligent assistant agent
Owner:LIANG PING
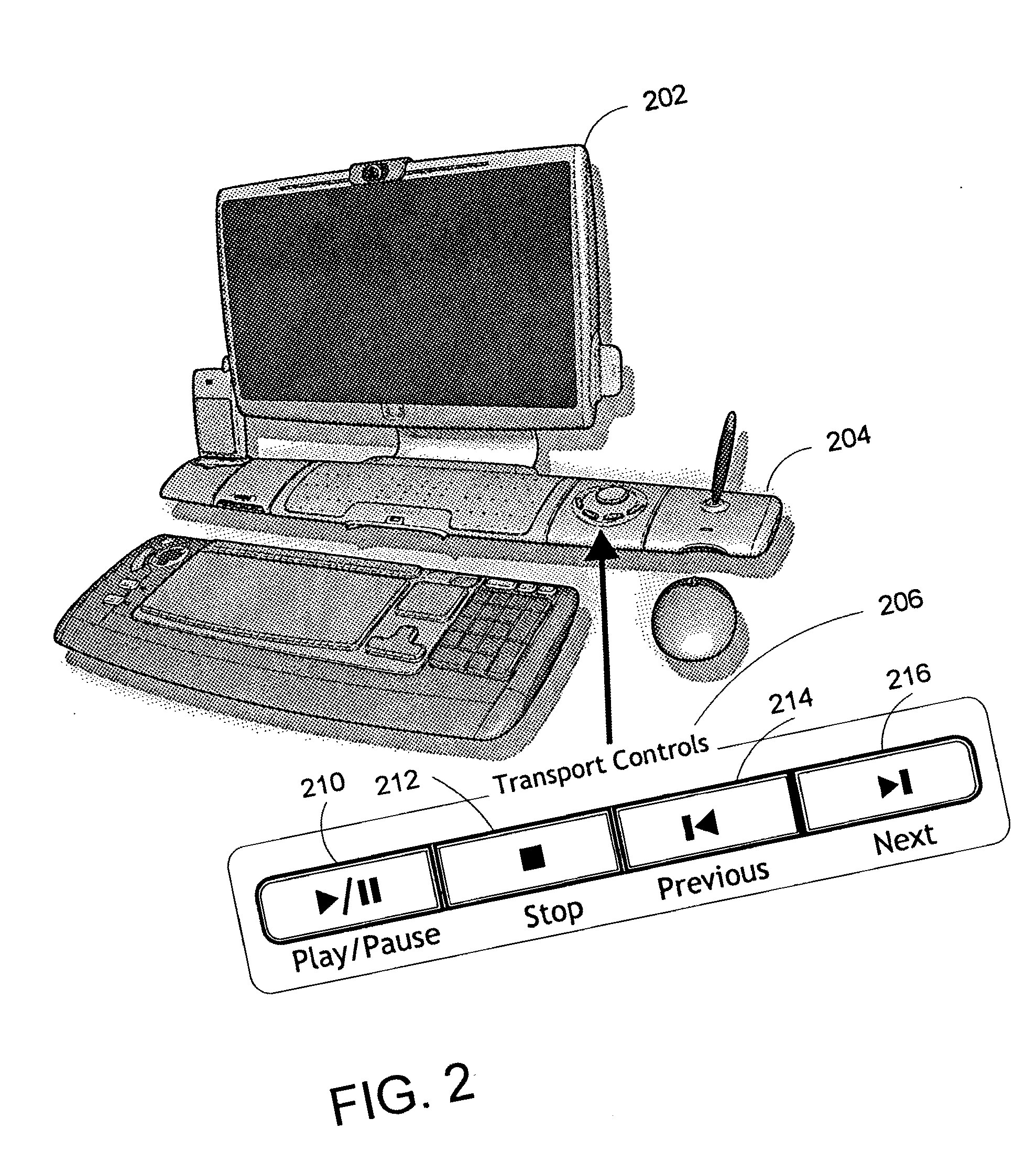
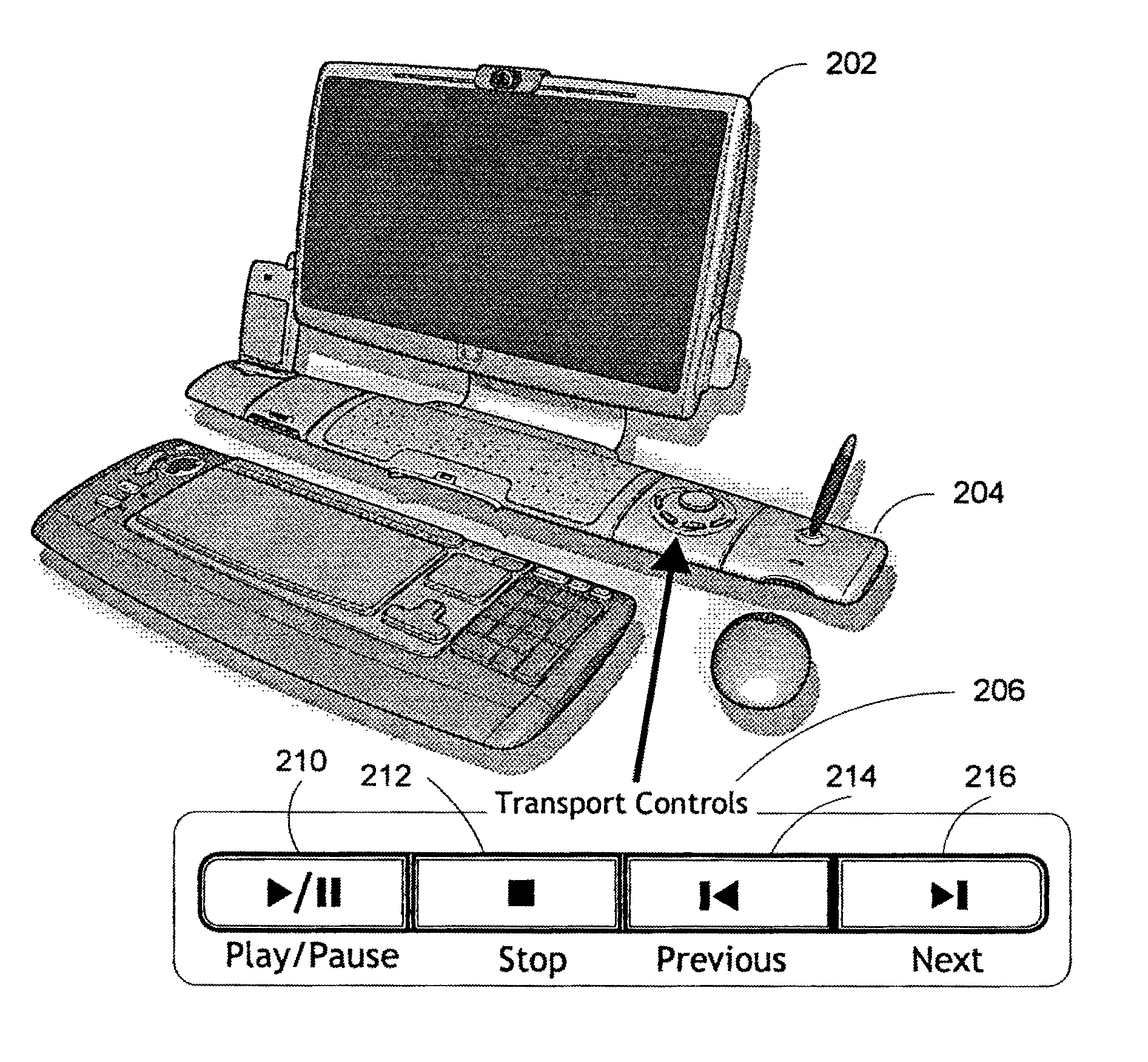
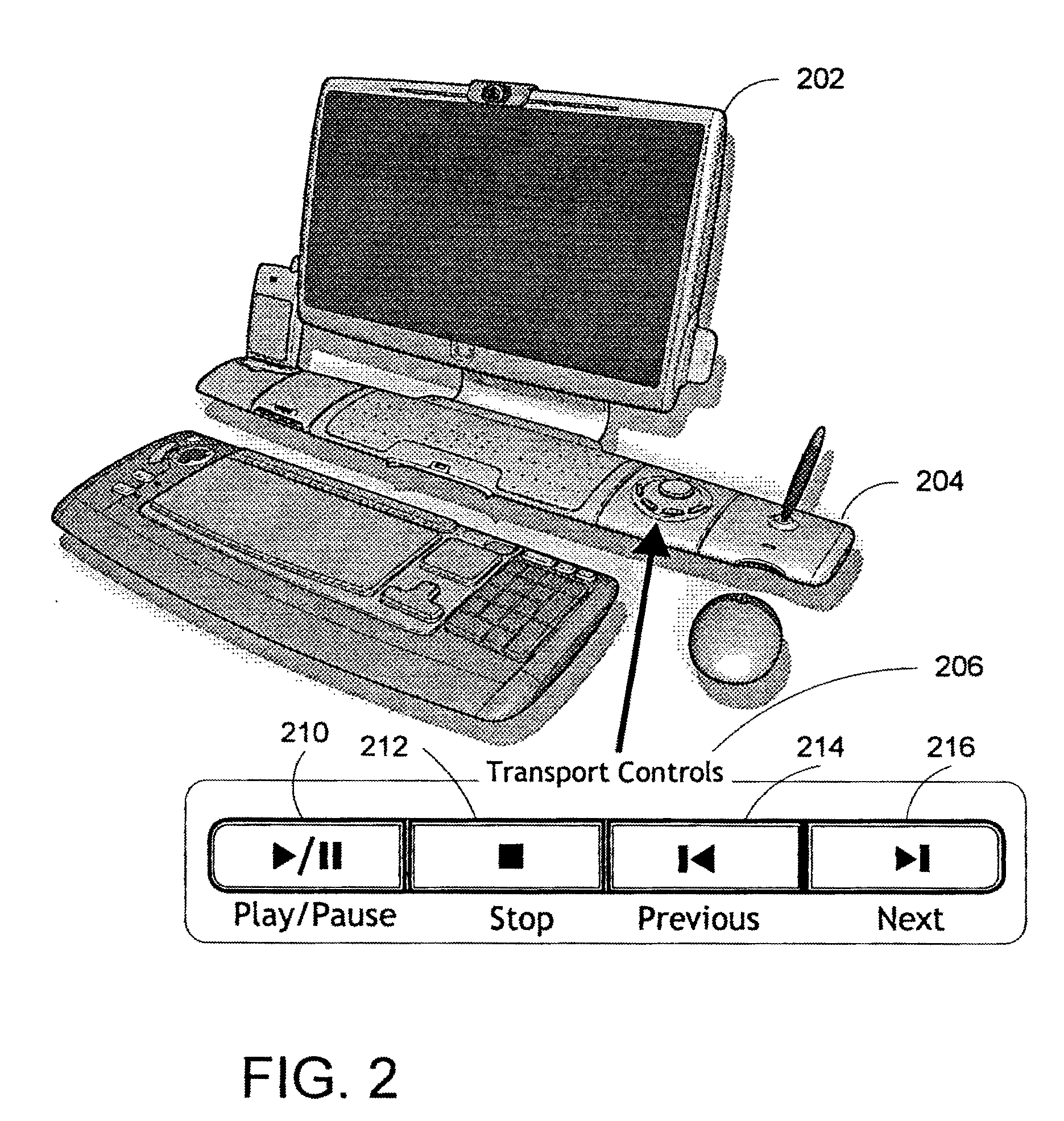
Method and system for navigation using media transport controls
ActiveUS20050071437A1Improve playbackSimple systemInput/output for user-computer interactionDigital computer detailsRemote controlElectronic form
A system and method for improved navigation and access of computer media content using media transport controls is provided. These transport controls may be placed in various locations such as on the computer housing, on a keyboard, on a monitor or a remote control. With these controls, a user may easily play multimedia content and navigate to individual tracks or segments of an audio and / or video stream. The transport controls include a play / pause button, a stop button, a previous button, and a next button. A user may intuitively activate and interact with media content in a variety of applications using these transport controls. For example, users may play recordings such as voice mail and review their recorded replies using the transport controls. Users may similarly play and / or review multimedia annotations made to any application files, including traditional computer files such as spreadsheets, documents and presentations.
Owner:MICROSOFT TECH LICENSING LLC
Advanced search, file system, and intelligent assistant agent
The present invention presents embodiments of methods, systems, and computer-readable media for advanced computer file organization, computer file and web search and information retrieval, and intelligent assistant agent to assist a user's creative activities. The embodiments presented herein categorize search results based on the keywords used in the search, provide user selectable ranking, use user's search objectives and advices to refine search, conduct search within an application program and using a file based, provide always-on search that monitors changes over a period of time, provide a high level file system that organizes files into categories, according to relations among files, and in ranking orders along multiple categorization and ranking dimensions and multiple levels of conceptual relationships, conduct searches for associations between keywords, concepts, and propositions, and provide validations of such associations to assist a user's creative activity.
Owner:LIANG PING
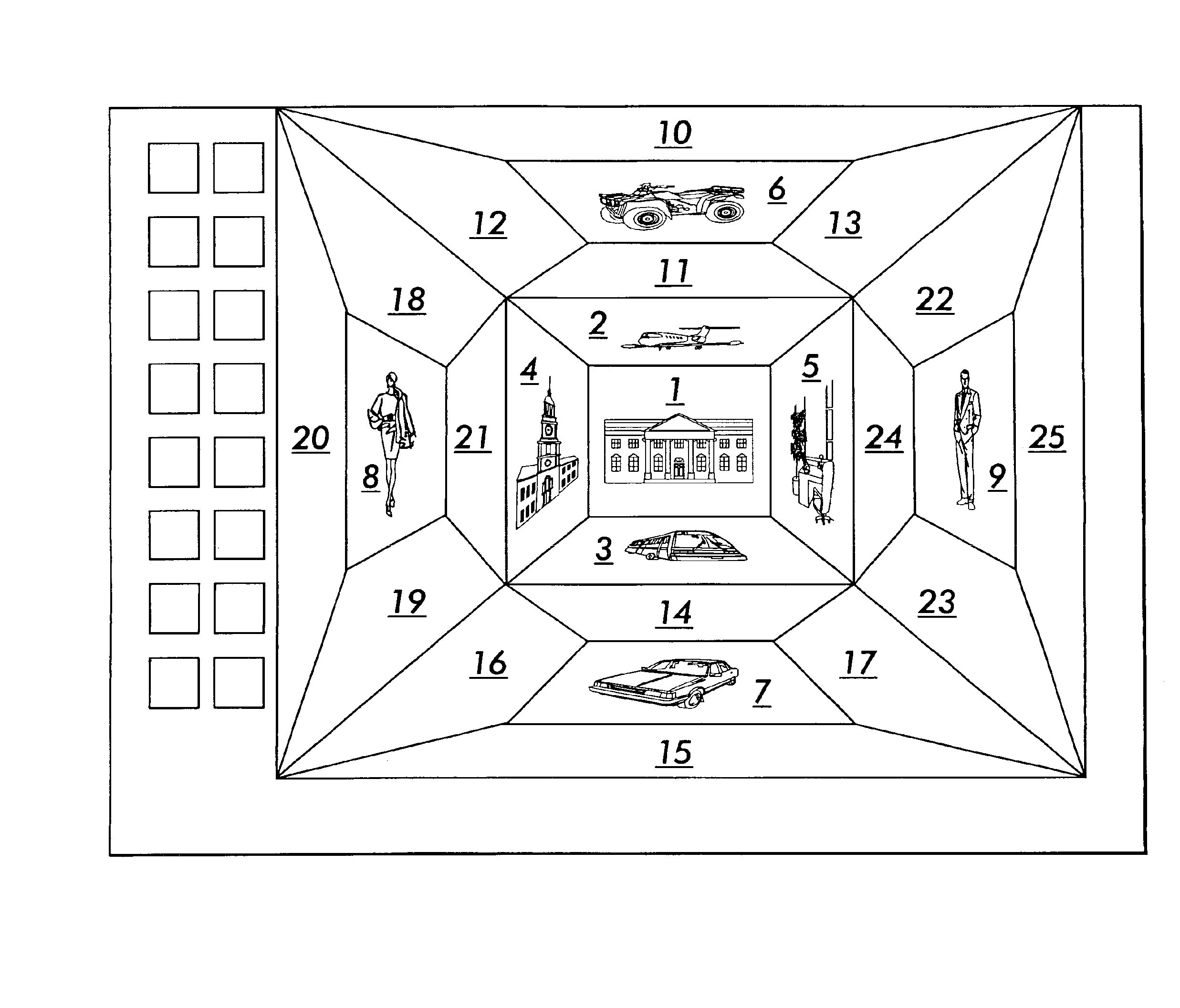
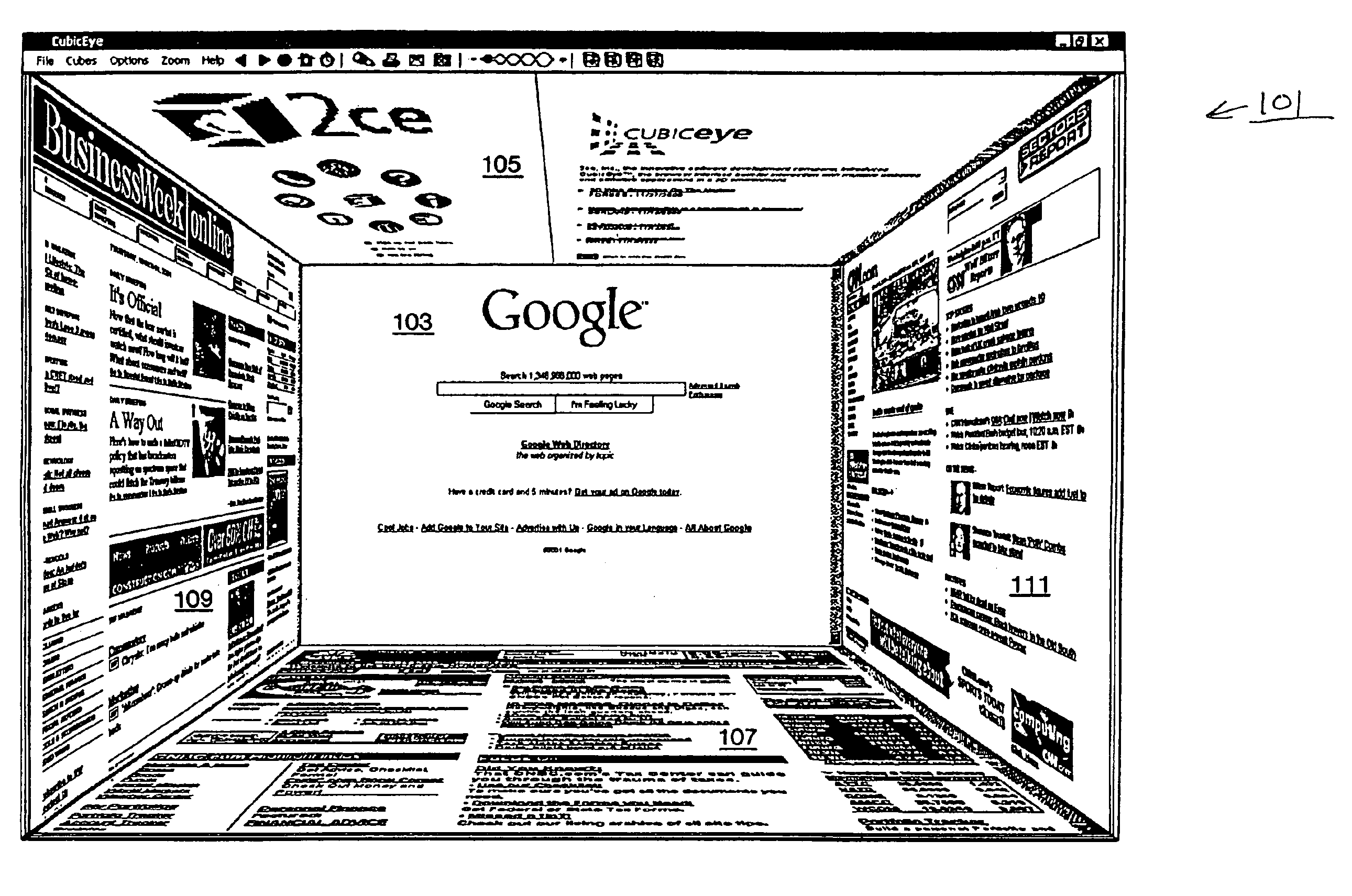
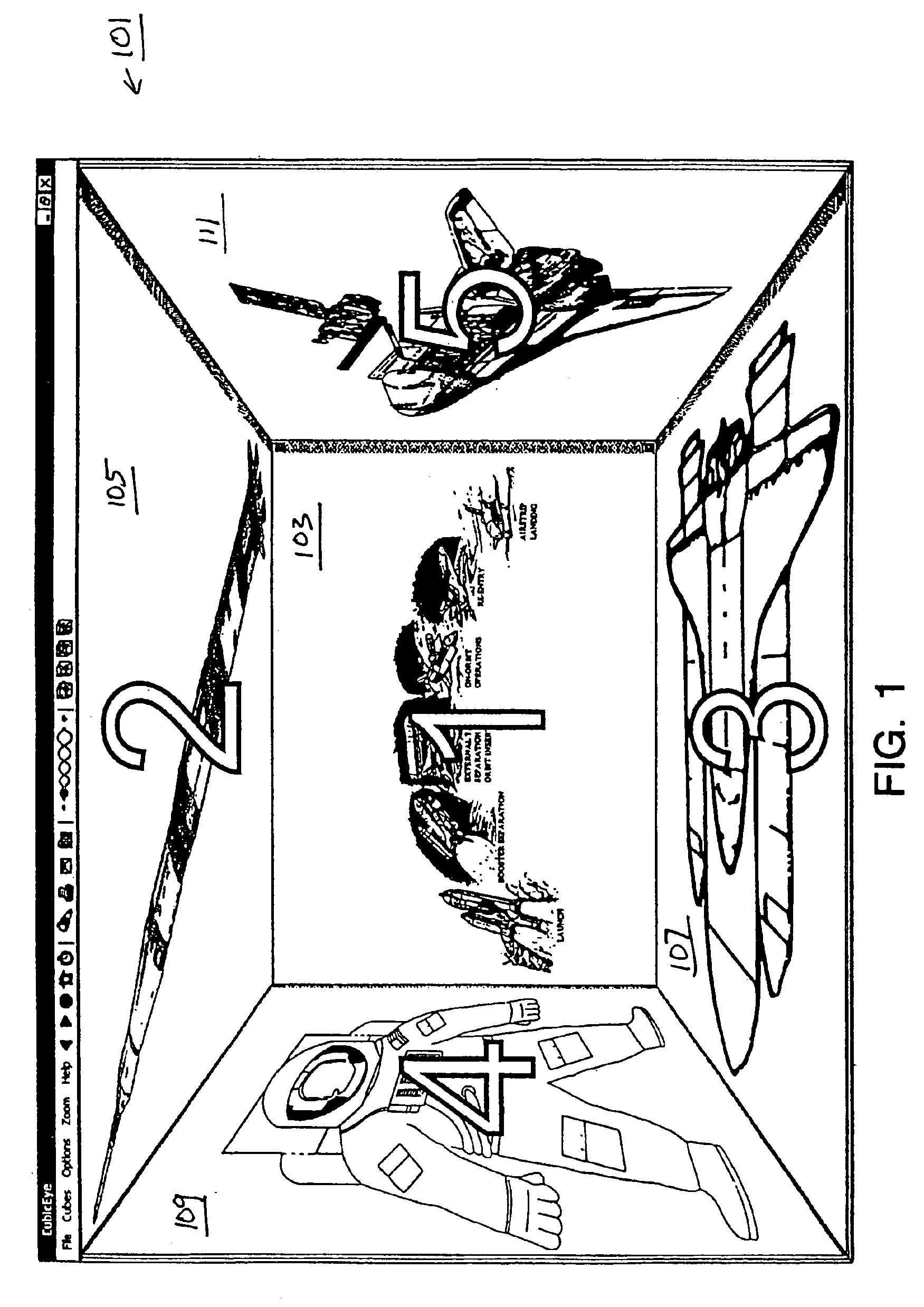
Method and apparatus for three dimensional internet and computer file interface
InactiveUS6938218B1Input/output processes for data processing3D-image renderingOperator interfaceDisplay device
A method and apparatus for geometrically organizing, interfacing to, surfing, authoring, converting and viewing computer files such as pages on the World Wide Web or operator interface windows of application software. A plurality of related Web pages or windows are organized and presented for view on a computer display in an apparent three or four dimensional relationship to each other with a front, right, left, top, and bottom face (page). A back face may be accessed by a button. Each face and its corresponding page / file can be further spatially related to five other faces and their corresponding pages / files in the same manner ad infinitum. The related pages are organized as a matrix of three dimensional cubes or four dimensional hypercubes.
Owner:NOLEN JAMES A III
Method and system for navigation using media transport controls
ActiveUS7194611B2Improve playbackSimple systemInput/output for user-computer interactionDigital computer detailsRemote controlElectronic form
Owner:MICROSOFT TECH LICENSING LLC
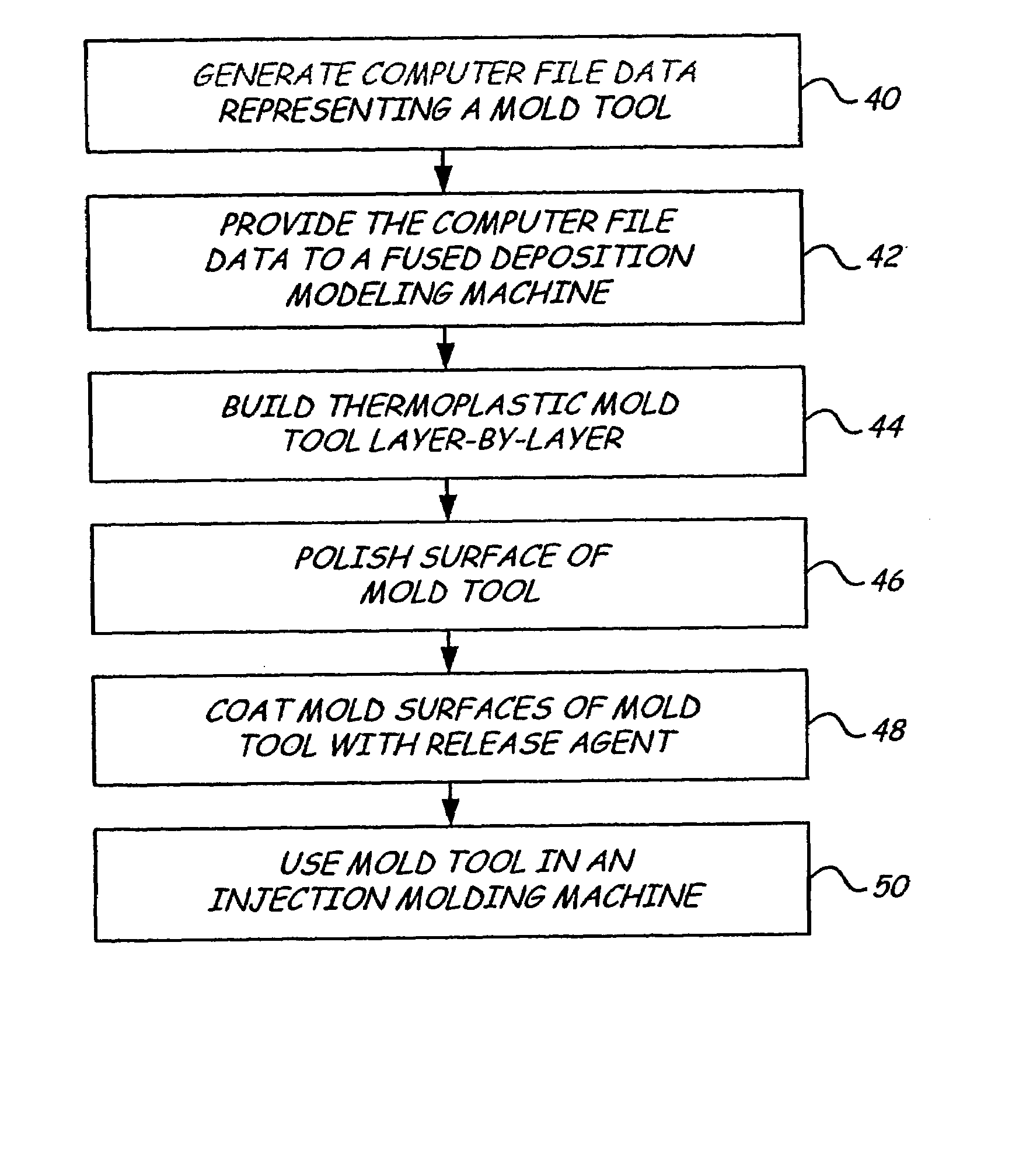
Layered deposition bridge tooling
InactiveUS7255821B2Additive manufacturing apparatusAdditive manufacturing with liquidsFilling materialsInjection molding machine
Disclosed is a method for making a prototype plastic injection molded part from a mold tool (10) built by fused deposition modeling. The mold tool (10) is built by depositing roads of a molten thermoplastic resin in layers in a predetermined pattern defined by computer file data representing the inverse of the desired prototype molded part, and is used in an injection molding machine without the addition of any reinforcement fill material or layers to create the prototype part. The disclosed method provides prototype plastic injection molded parts within a twenty-four hour time period.
Owner:STRATSYS INC
High-availability file archiving
ActiveUS8326805B1Digital data information retrievalError detection/correctionWide areaHigh availability
Computer file archiving systems and techniques are described. Various aspects include wide area high-availability file archiving, volume-level management capabilities of archiving systems, and methods and systems for storing file archiving metadata. The methods and systems described can be used individually or in combination.
Owner:EMC IP HLDG CO LLC
Downloadable and controllable music-on-hold
InactiveUS20060072716A1Easy to updateEasy to downloadAutomatic call-answering/message-recording/conversation-recordingAutomatic exchangesData processing systemData treatment
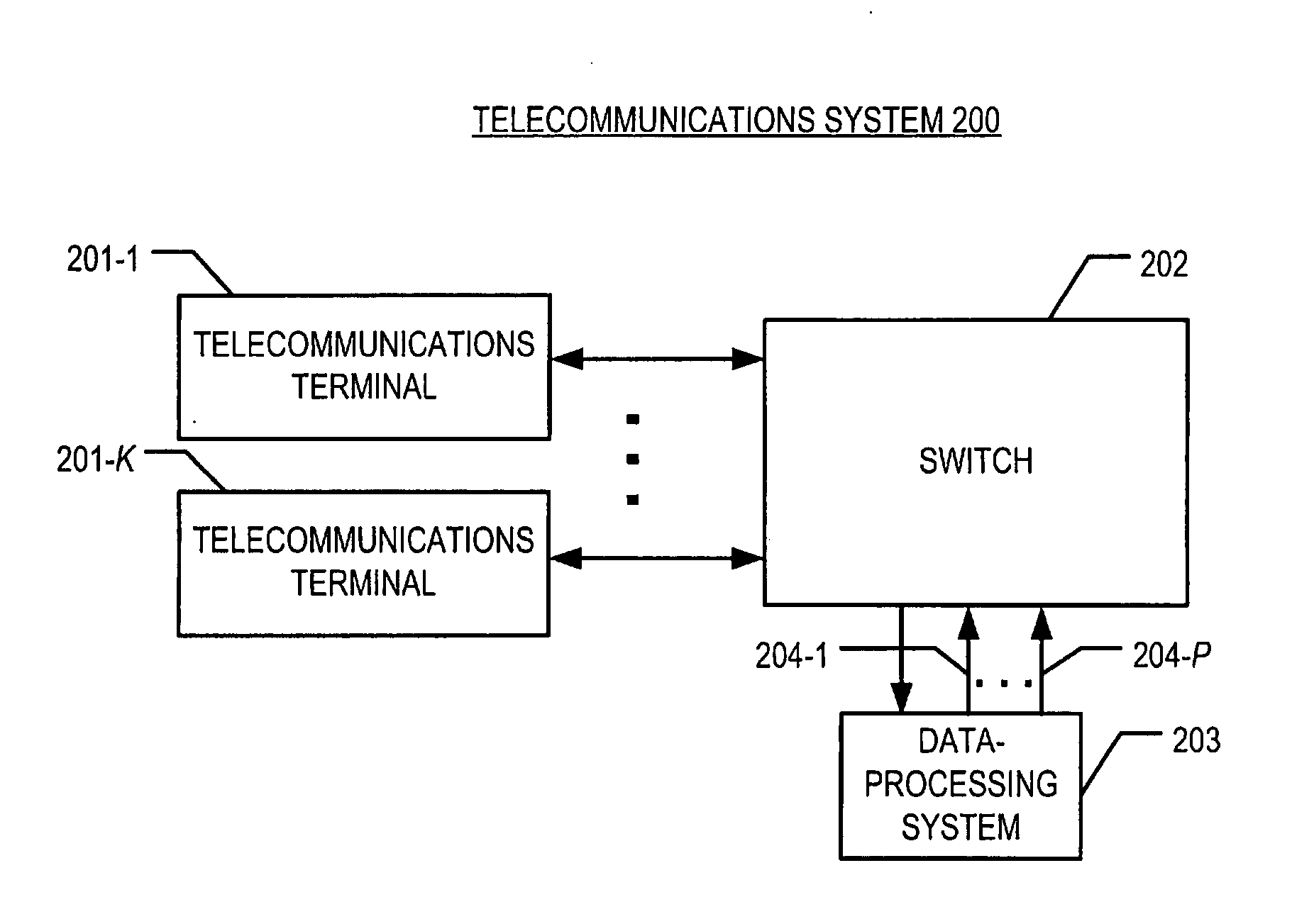
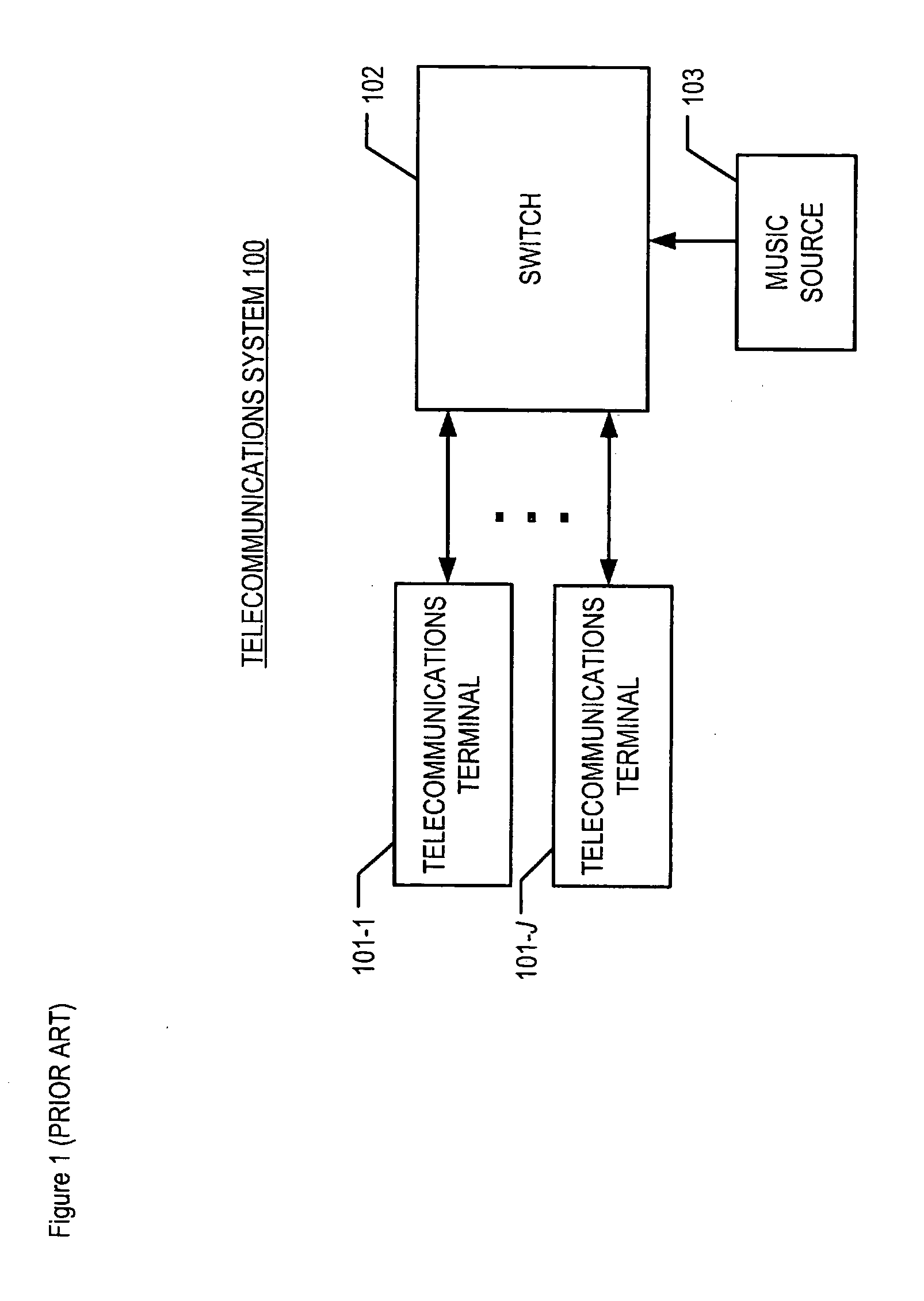
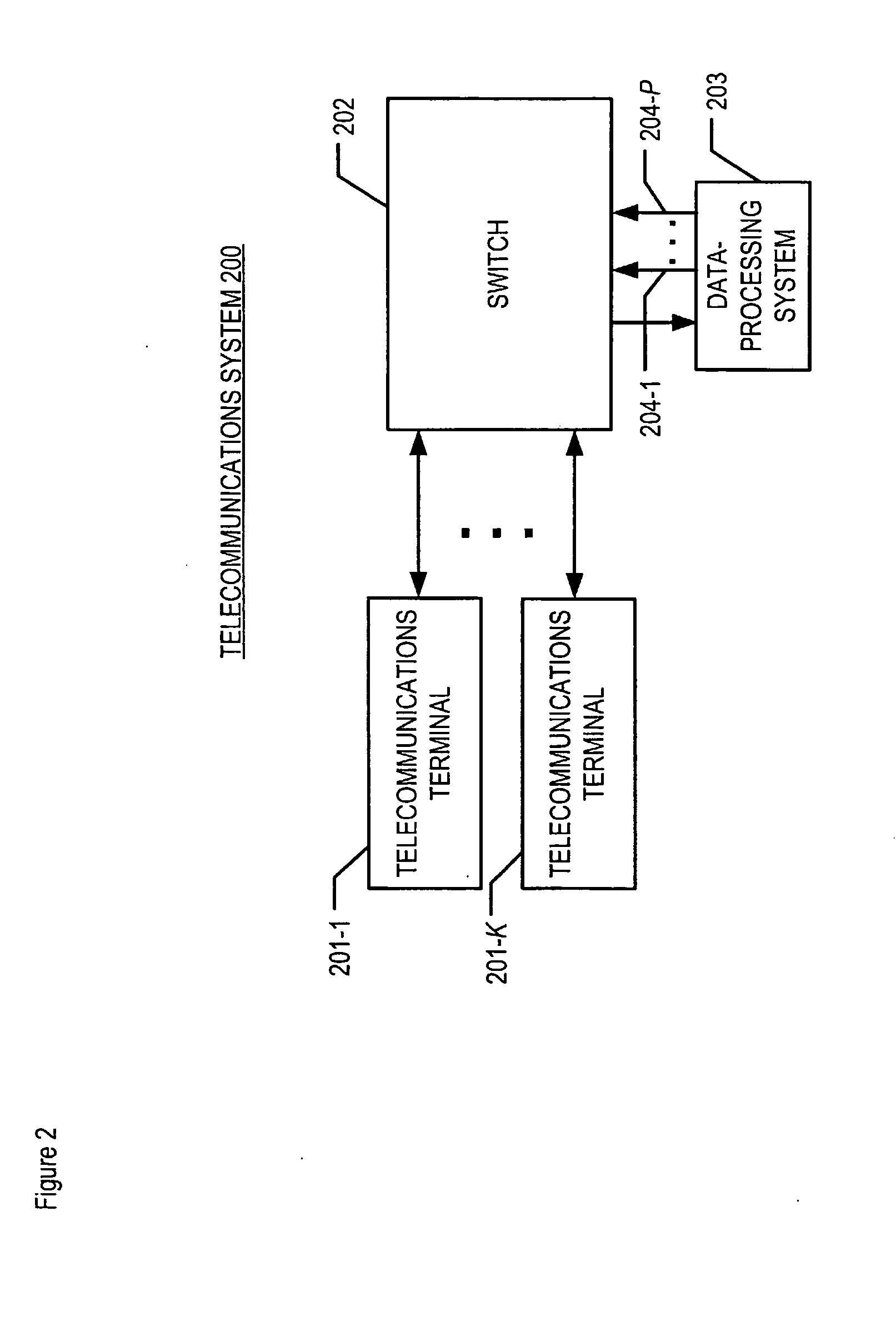
A method is disclosed that enables a telecommunications terminal user who is on hold during a call to determine which audio segments, such as musical compositions, are to be played, without some of the costs, disadvantages, and limitations of techniques in the prior art. The illustrative embodiment of the present invention provides a controllable music-on-hold capability that allows the user to enter commands via the user's telecommunications terminal keypad. In accordance with the illustrative embodiment of the present invention, a structure for storing computer files, referred to as an “audio segment box,” is established in a data-processing system. The audio segment box is similar to a “voice mail box” used in voice mail systems, except that the audio segment box is designated for audio segments that include musical compositions.
Owner:AVAYA INC
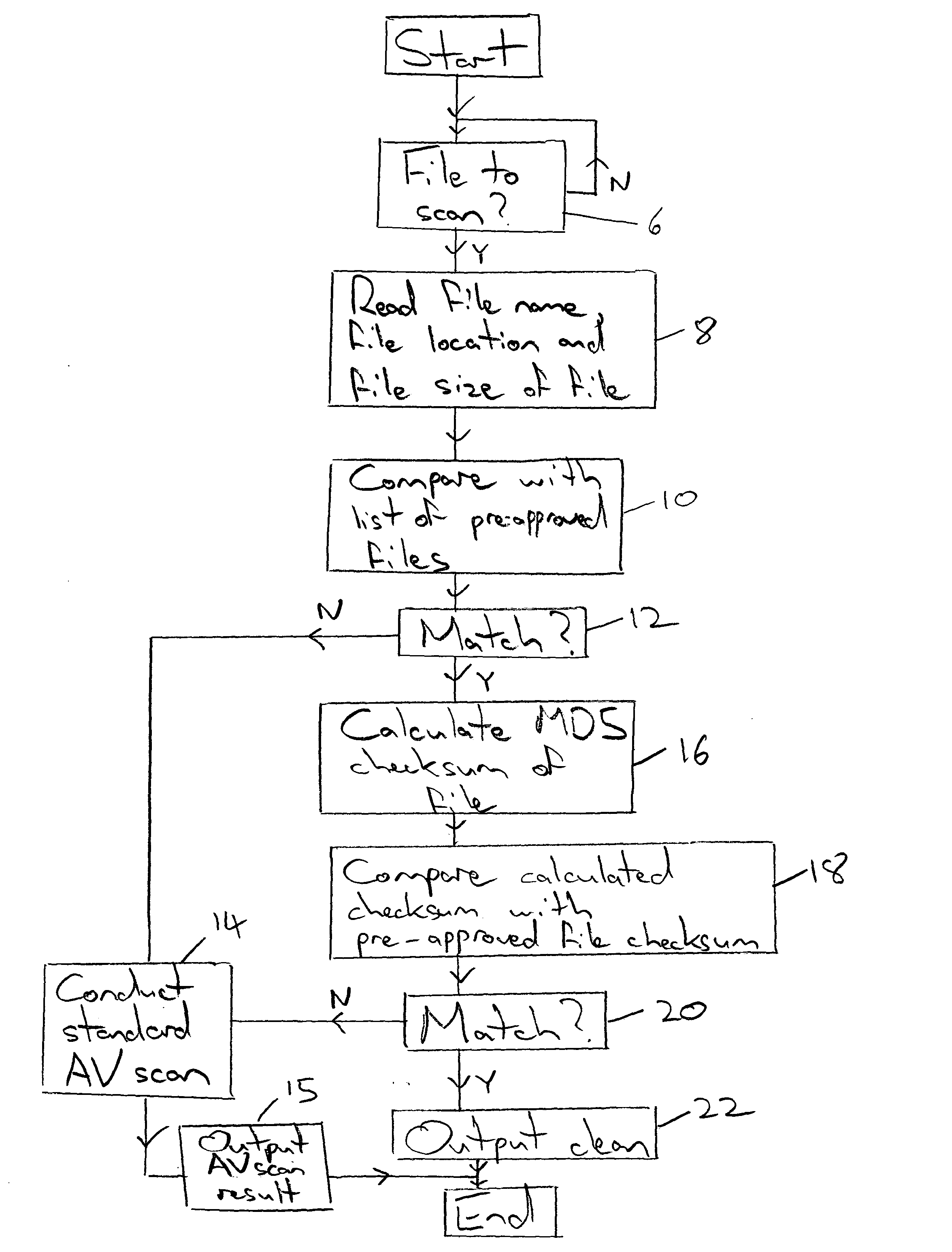
Pre-approval of computer files during a malware detection
InactiveUS20050021994A1Addressing slow performanceEffectively ensureMemory loss protectionDigital data processing detailsChecksumFile size
A malware detection system seeking to identify computer viruses, worms, Trojans, banned files and the like acts to determine from the file name, file size and storage location of a computer file being tested, whether that computer file potentially matches a specific known malware free computer file stored within a list of such specific known malware free computer files. If a match occurs indicating that the candidate computer file is potentially the specific known malware free computer file, then this is confirmed by calculating a checksum of the candidate computer file and comparing this against a stored corresponding checksum of the specific known malware free computer file. If these checksums match, then the candidate computer file can be passed as clean without requiring further time consuming malware detection scanning.
Owner:MCAFEE INC
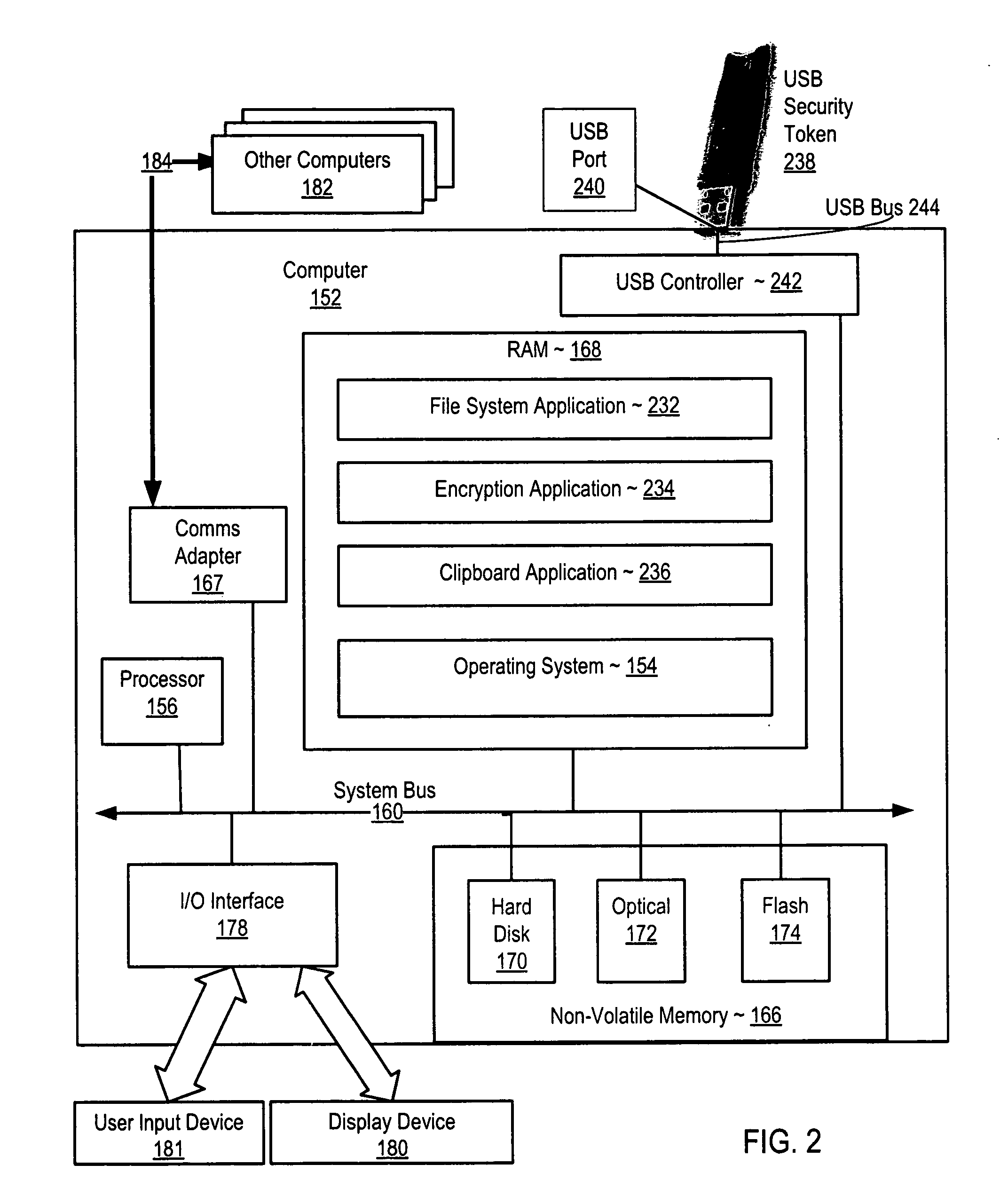
Maintaining security for file copy operations
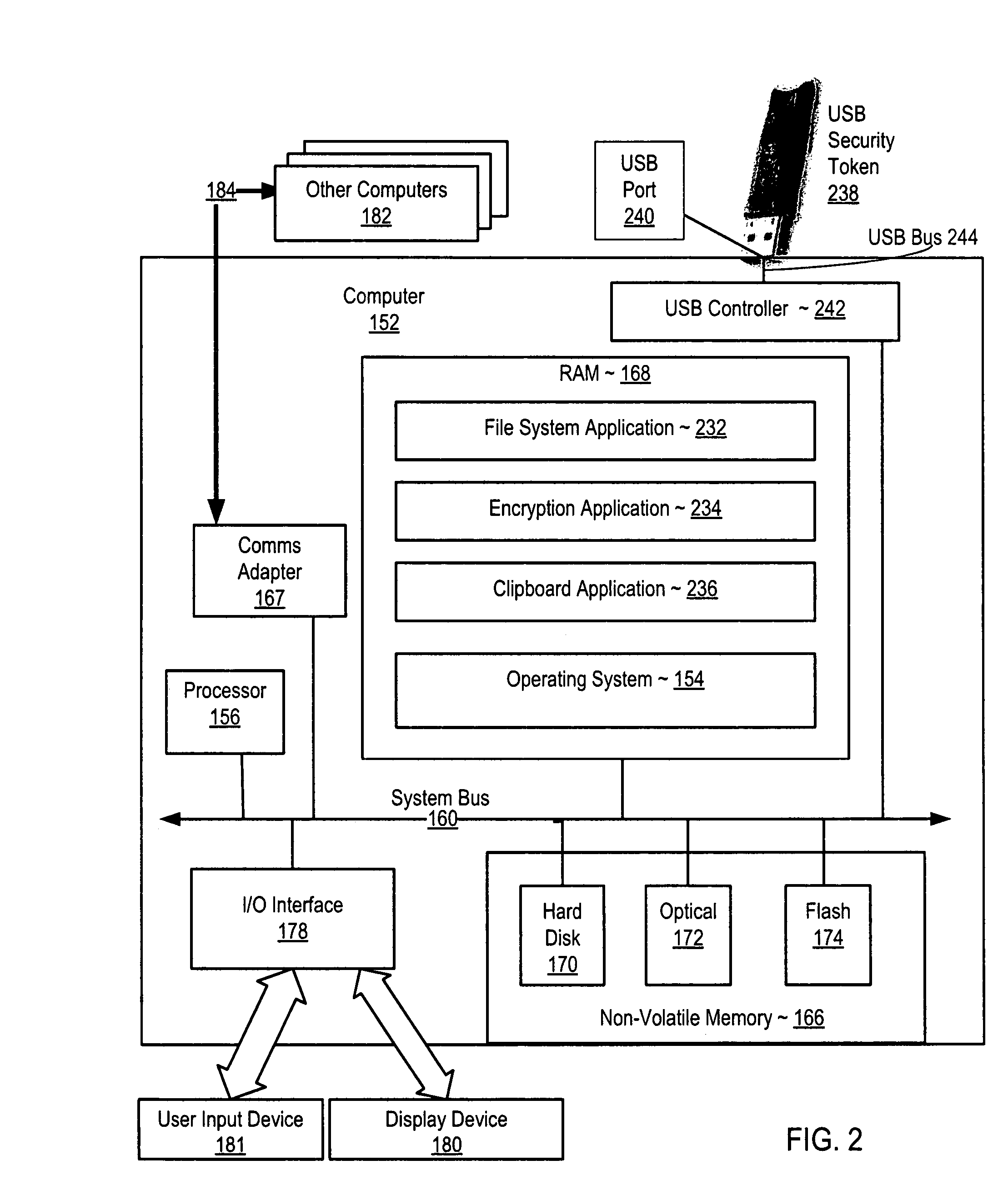
Securing computer files in which a publish permission is present in a file system. Upon receiving a request to write data from one file to another, the file system determines whether publish permission is needed. If so and the user lacks the publish permission, the request is rejected. Disclosed is securing computer files which include encrypting metadata about an encrypted file and storing both the encrypted file and the encrypted metadata. The metadata includes a key for decrypting the encrypted file. The key for decrypting the metadata is stored in a USB security token. Disclosed is securing computer files which include copying material from a window displaying the contents of a file to a clipboard application. The file or window is associated with the material. The clipboard application can deny a request to paste material associated with one file to a window displaying the contents of a different file.
Owner:SIMDESK TECH INC
Storing and retrieving computer data files using an encrypted network drive file system
ActiveUS20060206547A1Easy to storeEasy retrievalData processing applicationsError detection/correctionHard disc driveData file
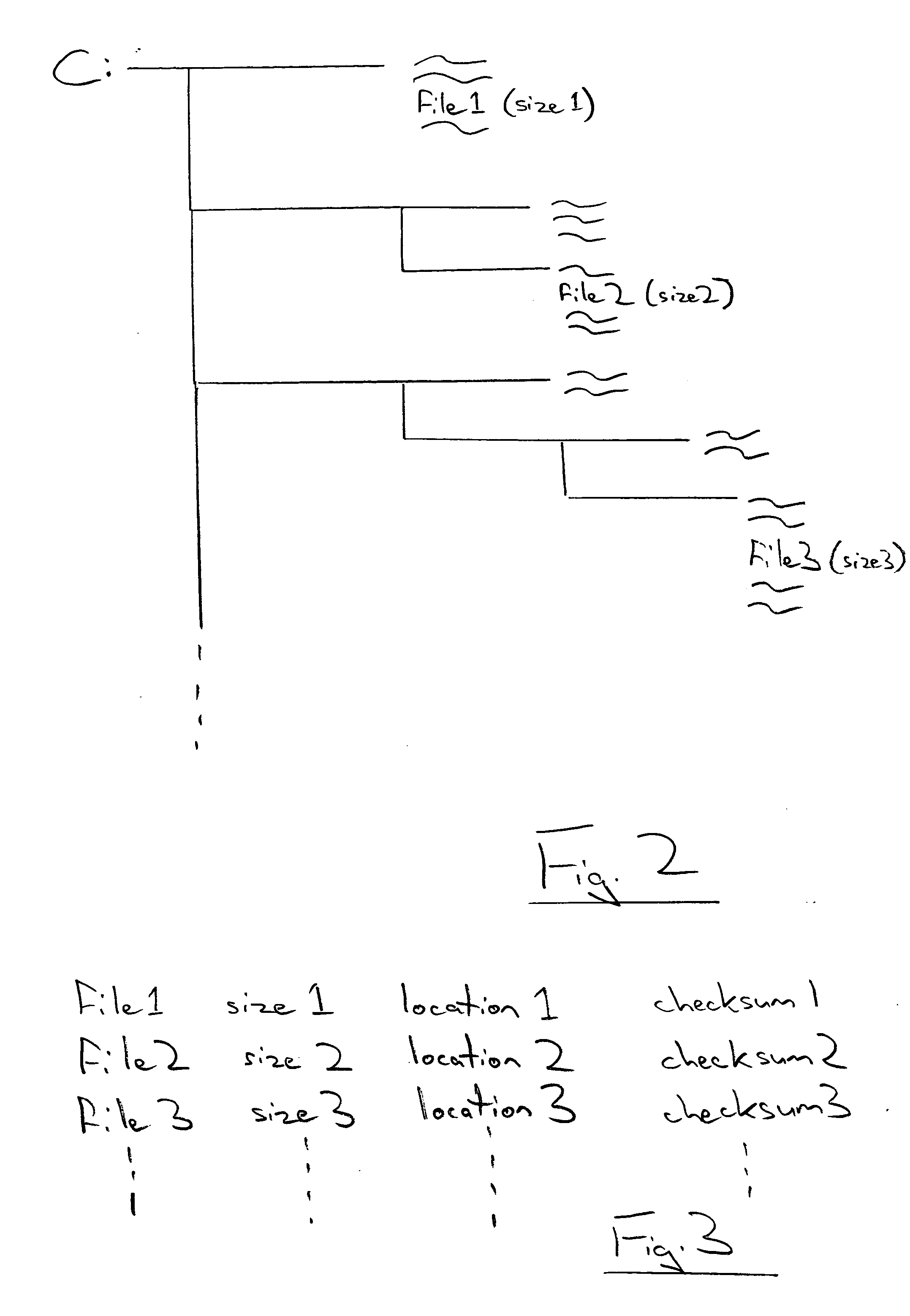
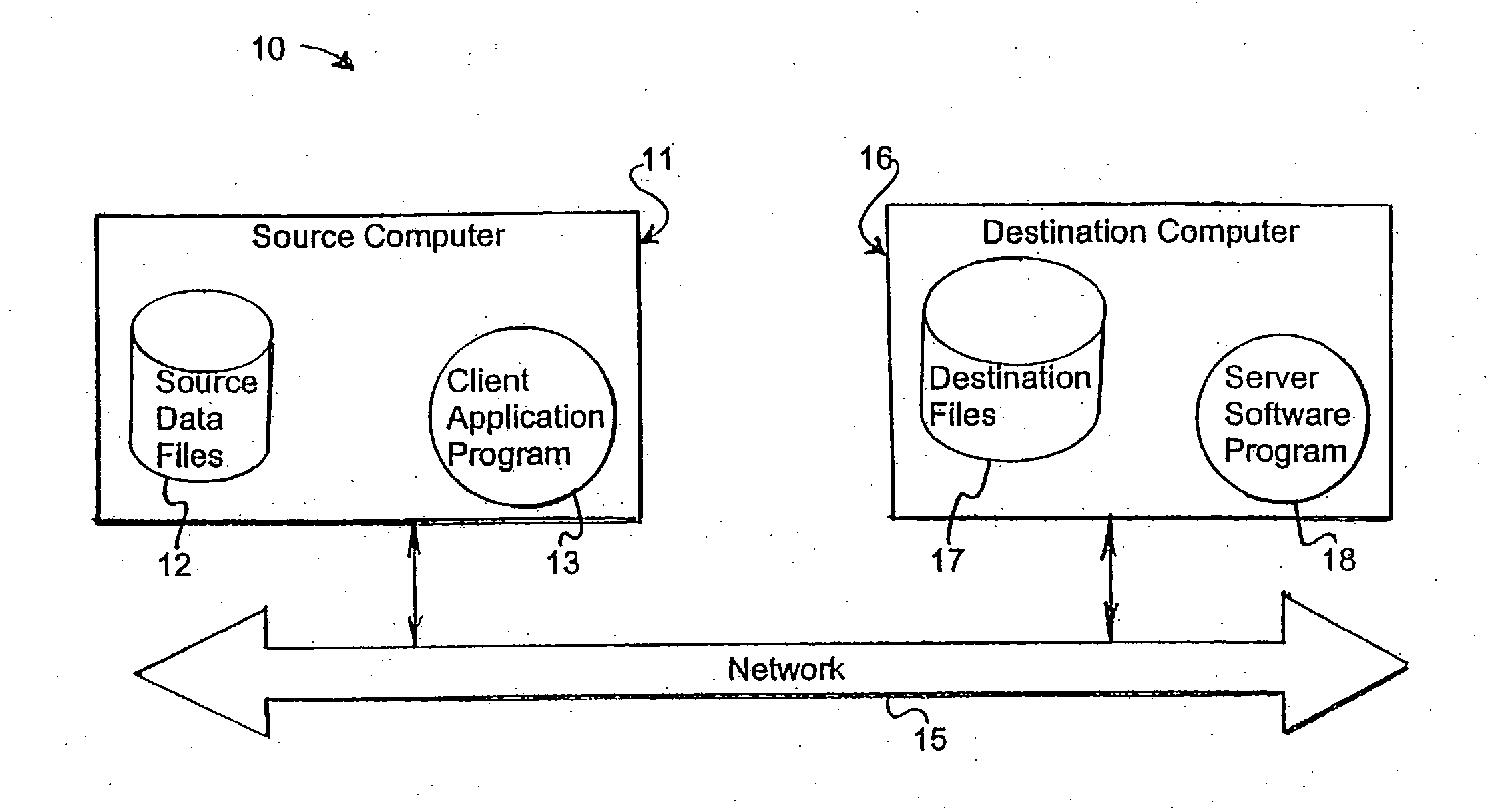
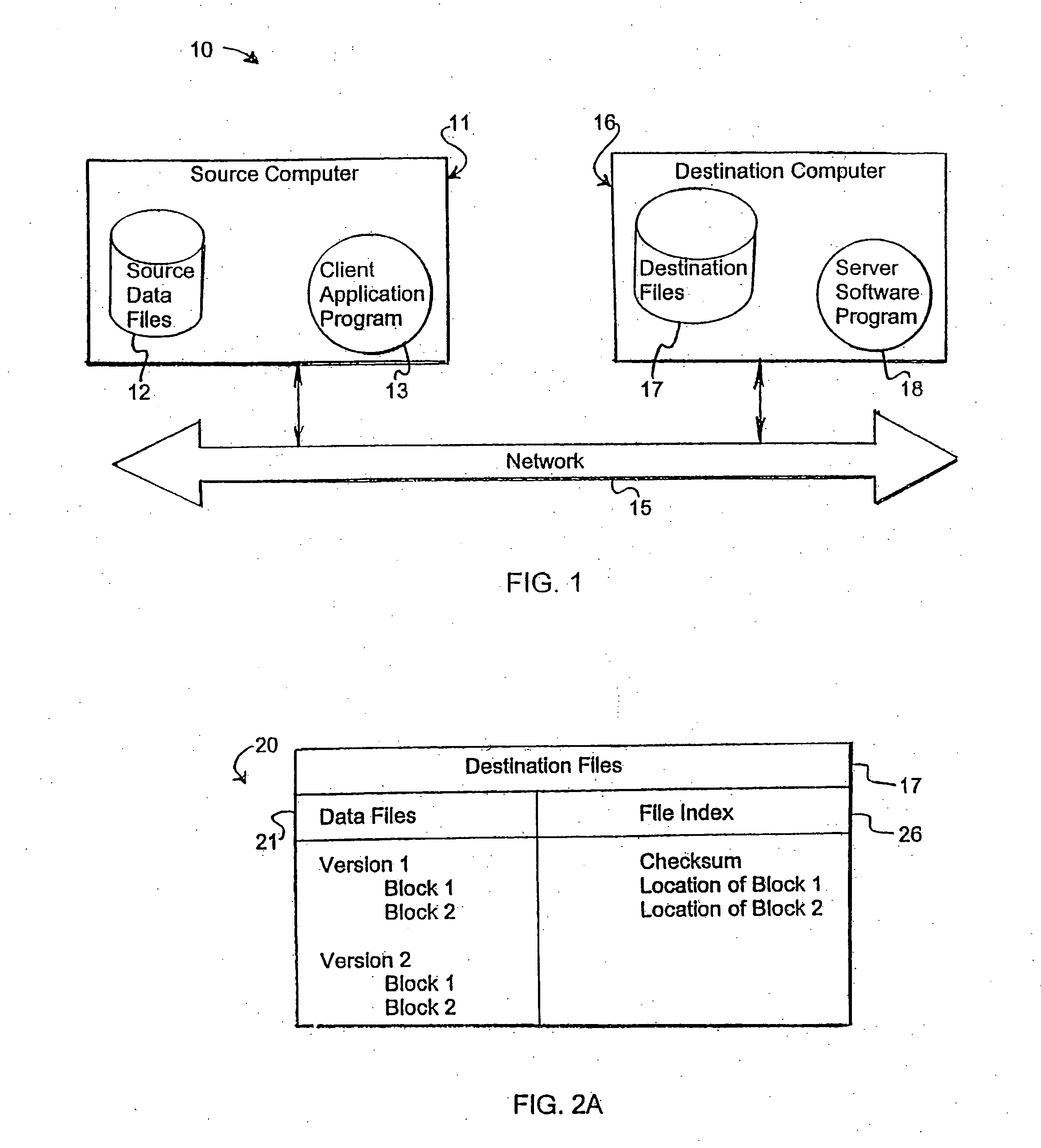
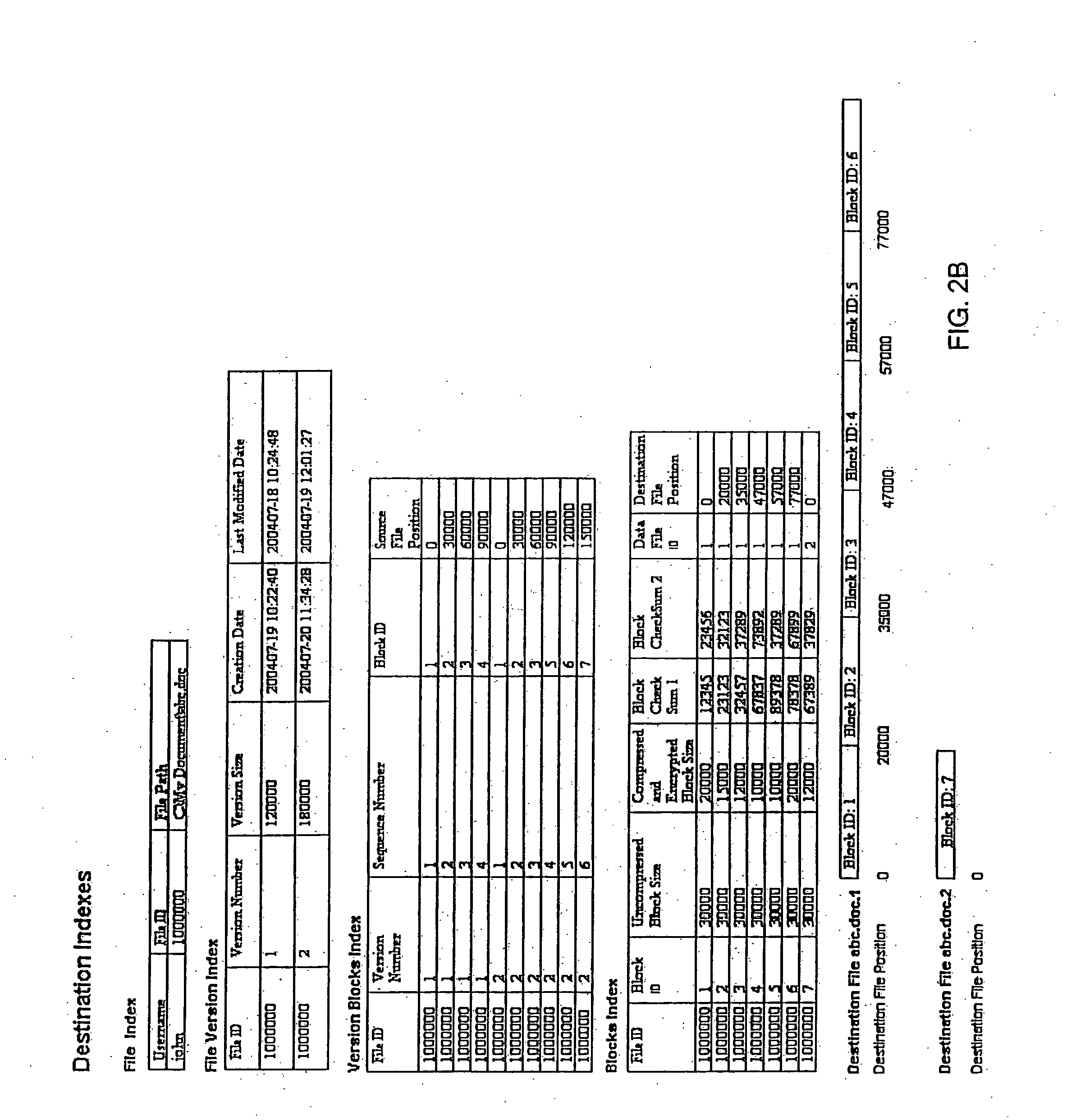
A system and method for storing computer files in a destination file is described, which may be an incremental backup system. File headers related to the files may be stored in a file index separate from a data file, or subsequent versions may be stored in the same data file while maintaining earlier versions. File headers may include locations of files, checksums, metadata about individual blocks corresponding to the data files. A system may include a client application program stored on a client computer, a network, and a server software program on a destination computer. Embodiments may include compression, encryption, or both, performed by the client application program. Files may be divided into blocks, and metadata may include locations of blocks. Files may be restored from the destination computer to the source computer. Files storage locations on the destination computer may be mapped to the client computer to appear as a virtual hard drive for convenient access by a user.
Owner:IDRIVE INC
Using sequencing and timing information of behavior events in machine learning to detect malware
ActiveUS8401982B1Memory loss protectionError detection/correctionFeature vectorTheoretical computer science
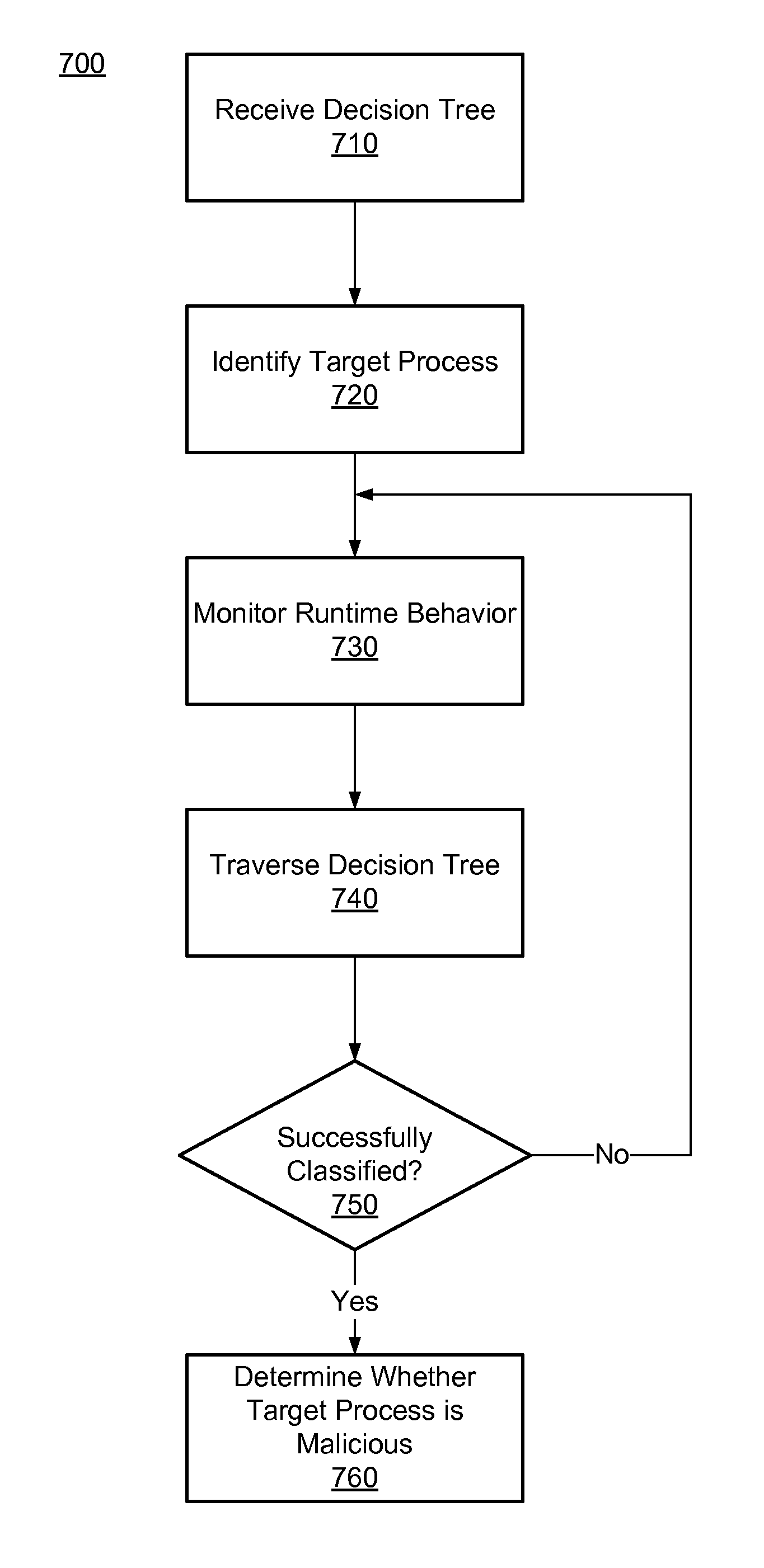
A decision tree for classifying computer files is constructed. A set of training files known to be legitimate or malicious are executed and their runtime behaviors are monitored. When a behavior event is detected for one of the training file at a point in time, a feature vector is generated for that training file. Behavior sequencing and timing information for the training file at that point in time is identified and encoded in the feature vector. Feature vectors for each of the training files at various points in time are fed into a decision tree induction algorithm to construct a decision tree that takes into account of the sequencing and timing information.
Owner:NORTONLIFELOCK INC
System and method for backing up data
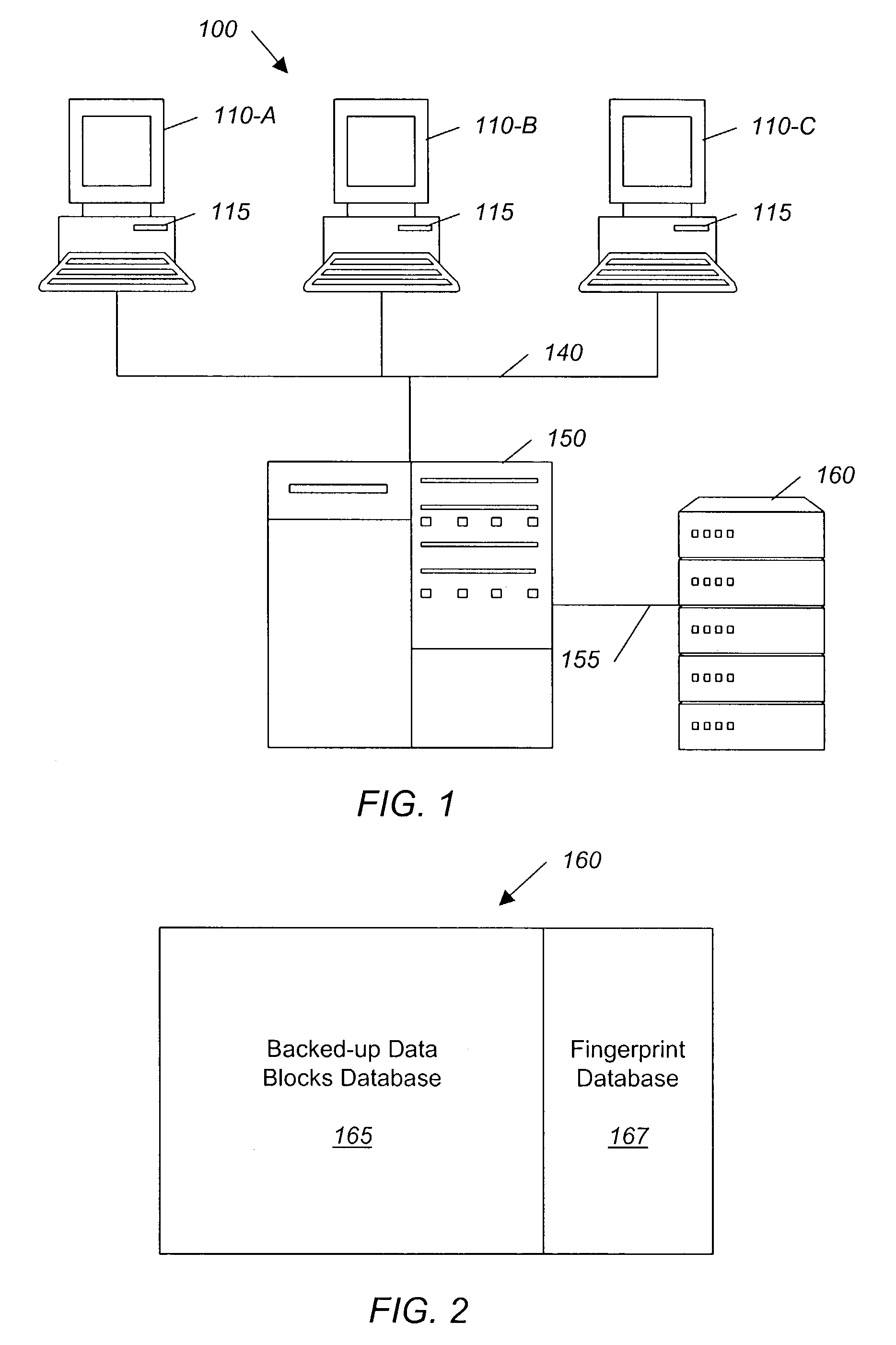
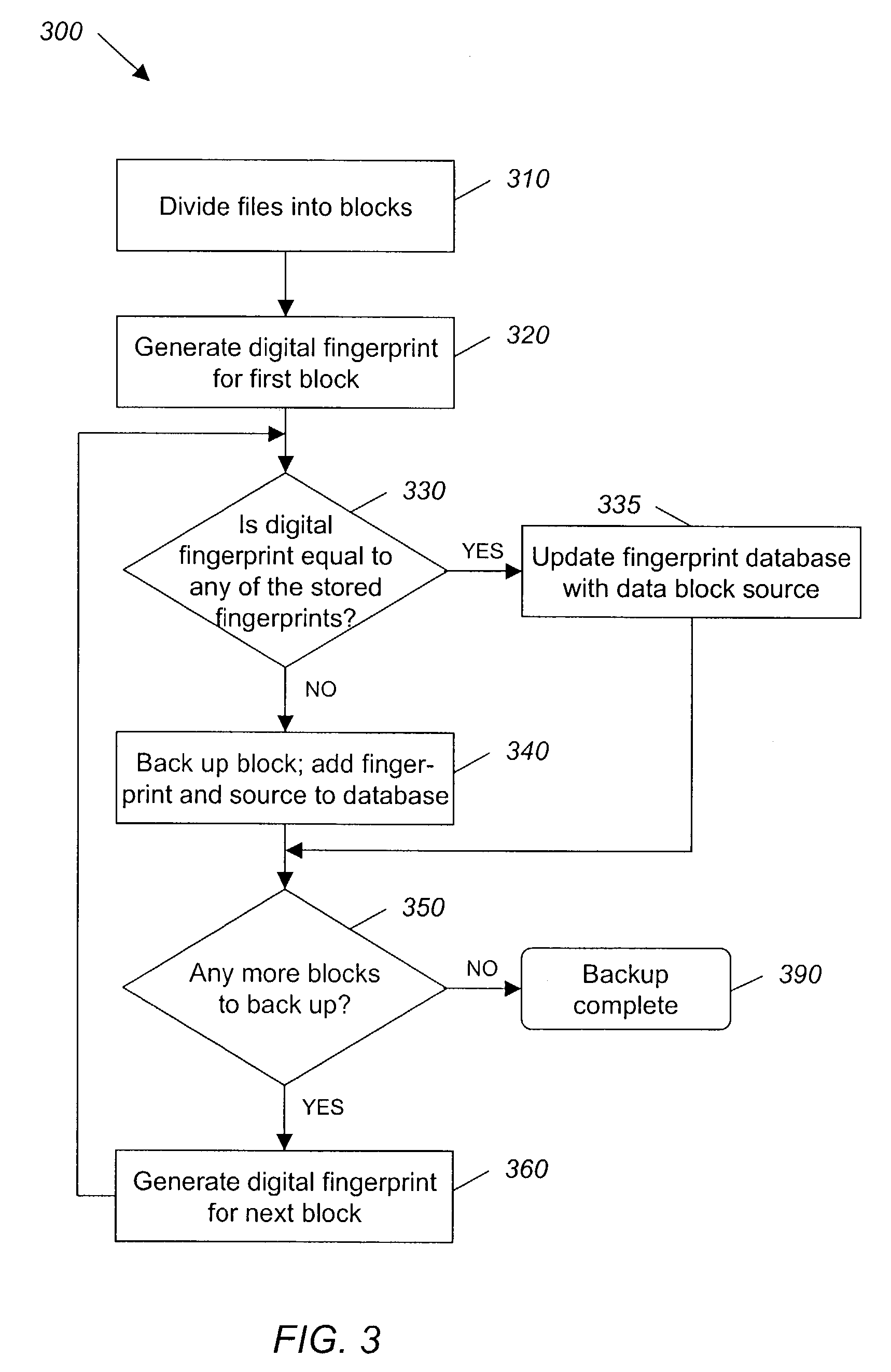
ActiveUS7055008B2Avoid inefficiencyInefficiency of the Shnelvar patent can be avoidedCamera focusing arrangementPayment architectureSoftware licenseData content
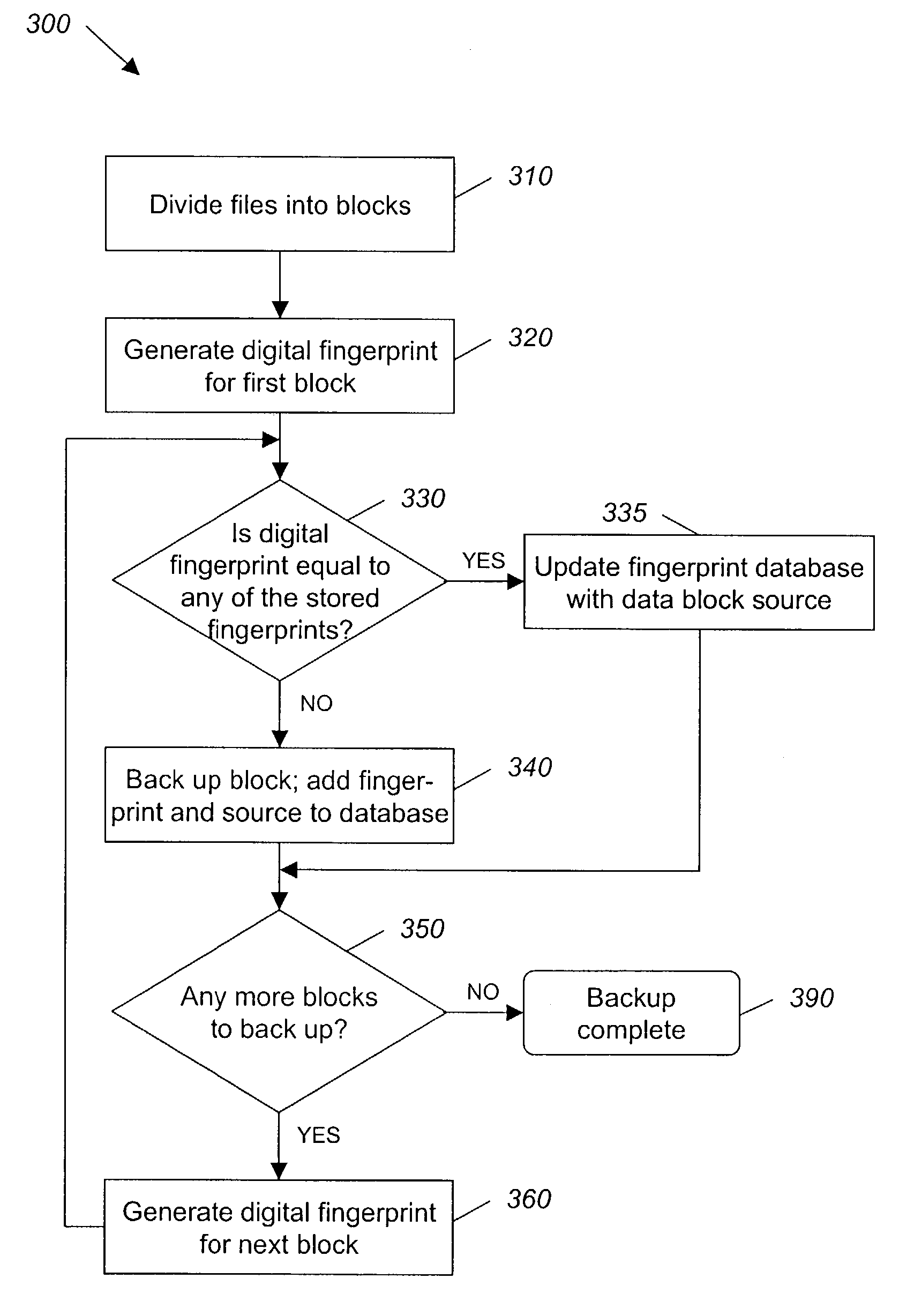
A hash-optimized backup system and method takes data blocks and generates a probabilistically unique digital fingerprint of the content of each data block using a substantially collision-free algorithm. The process compares the generated fingerprint to a database of stored fingerprints and, if the generated fingerprint matches a stored fingerprint, the data block is determined to already have been backed up, and therefore does not need to be backed up again. Only if the generated fingerprint does not match a stored fingerprint is the data block backed up, at which point the generated fingerprint is added to the database of stored fingerprints. Because the algorithm is substantially collision-free, there is no need to compare actual data content if there is a hash-value match. The process can also be used to audit software license compliance, inventory software, and detect computer-file tampering such as viruses and malware.
Owner:FALCONSTOR
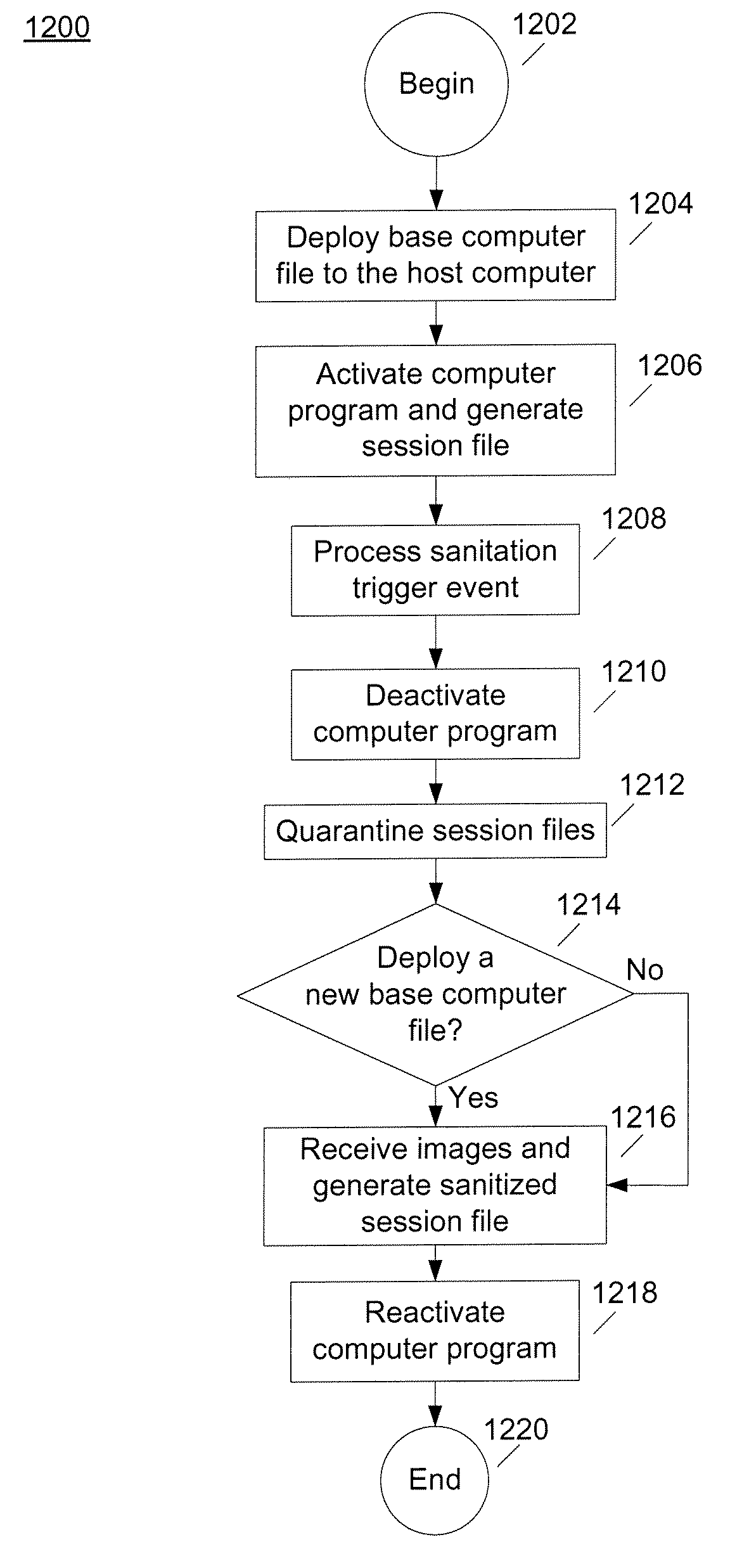
System and method for sanitizing a computer program
InactiveUS20070234337A1Specific program execution arrangementsMemory systemsEvent triggerComputer file
A system and method that may include deploying a base computer file on a computer, activating a computer program by processing the base computer file, and generating a file for storing data associated with operation of the computer program. The system and method may further include processing an event trigger triggering sanitation of the file and replacing the file with a sanitized file.
Owner:PROWESS CONSULTING LLC
Collaborative document development and review system
ActiveUS7818678B2Easy to spotCathode-ray tube indicatorsNatural language data processingData fileDocument preparation
A computer software product for allowing simultaneous multi-level collaboration, including in real time between an author and a group of reviewers invited by the author to comment on a document stored in a computer file. The computer software enables each reviewer to view the document and make changes thereto which are stored in a secondary data file without modifying the contents of the original document. The author receives and views the secondary data files from the reviewers and selectively incorporates the changes into the document. Each reviewer may invite an unlimited number of sub-reviewers to review the document, the comments of each sub-reviewer similarly being stored in a secondary data file wherein only the author may edit the document directly.
Owner:LITERA CORP
Histogram-based virus detection
InactiveUS6971019B1Easy to detectDigital data processing detailsUser identity/authority verificationCode moduleComputer science
A virus detection system (VDS) (400) uses a histogram to detect the presence of a computer virus in a computer file. The VDS (400) has a P-code data (410) for holding P-code, a virus definition file (VDF) (412) for holding signature of known viruses, and an engine (414) for controlling the VDS. The engine (414) contains a P-code interpreter (418) for interpreting the P-code, a scanning module (424) for scanning regions of the file (100) for the virus signatures in the VDF (412), and an emulating module (426) for emulating instructions in the file. The emulating module (426) contains a histogram generation module (HGM) (436) for generating a histogram of characteristics of instructions emulated by the emulating module (426) and a histogram definition module (HDF) (438) for specifying the characteristics to be included in the generated histogram. The emulating module (426) uses the generated histogram (500) to determine how many of the instructions of the computer file (100) to emulate. The emulating module (426) emulates (712) instructions and the HGM (436) generates a histogram of the instructions until active instructions are note detected. When active instructions are not detected (714), a P-code module is executed (722) to analyze the histogram (500) and determine whether a the file (100) contains a virus. The P-code can also decide to extend (728) emulation. The HGM (436) is also used to detect (822) the presence of dummy loops during virus decryption.
Owner:CA TECH INC
Display method and apparatus for facilitating interaction with Web sites
The invention is a computer-implemented method and apparatus for organizing Web pages and other computer files relative to each other in a manner analogous to a three or four dimensional spatial relationship and displaying multiple Web pages simultaneously in multiple panels of a computer monitor in accordance with said spatial organization, whereby despite the organization, at least one of the Web pages or files can be made to stay in the same panel of the display while the user navigates through the virtual multidimensional space.
Owner:NOLEN JAMES A III
Managed distribution of digital assets
ActiveUS20050060537A1High acceptanceEasy to produceHardware monitoringComputer security arrangementsOperational systemNetwork connection
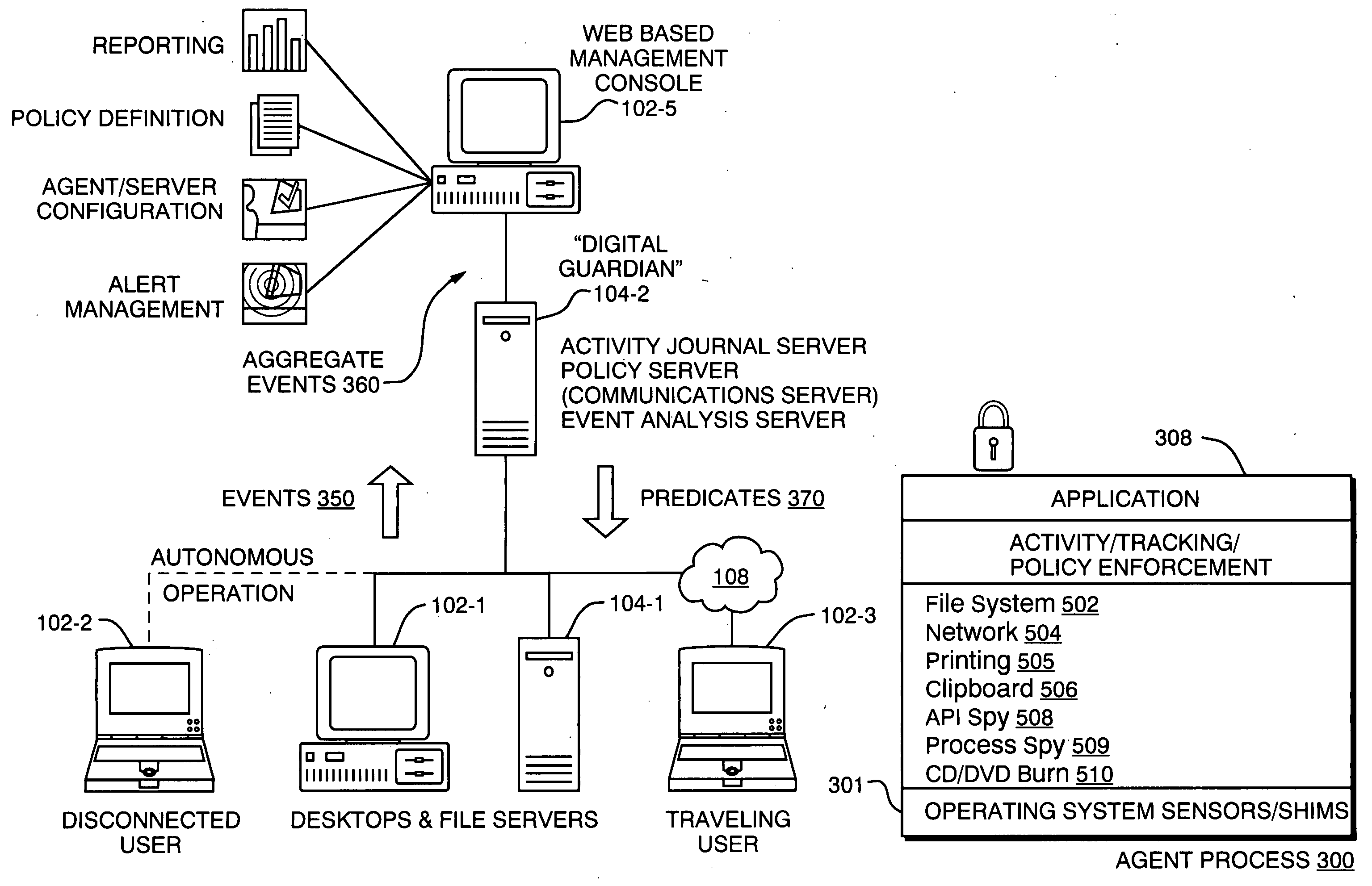
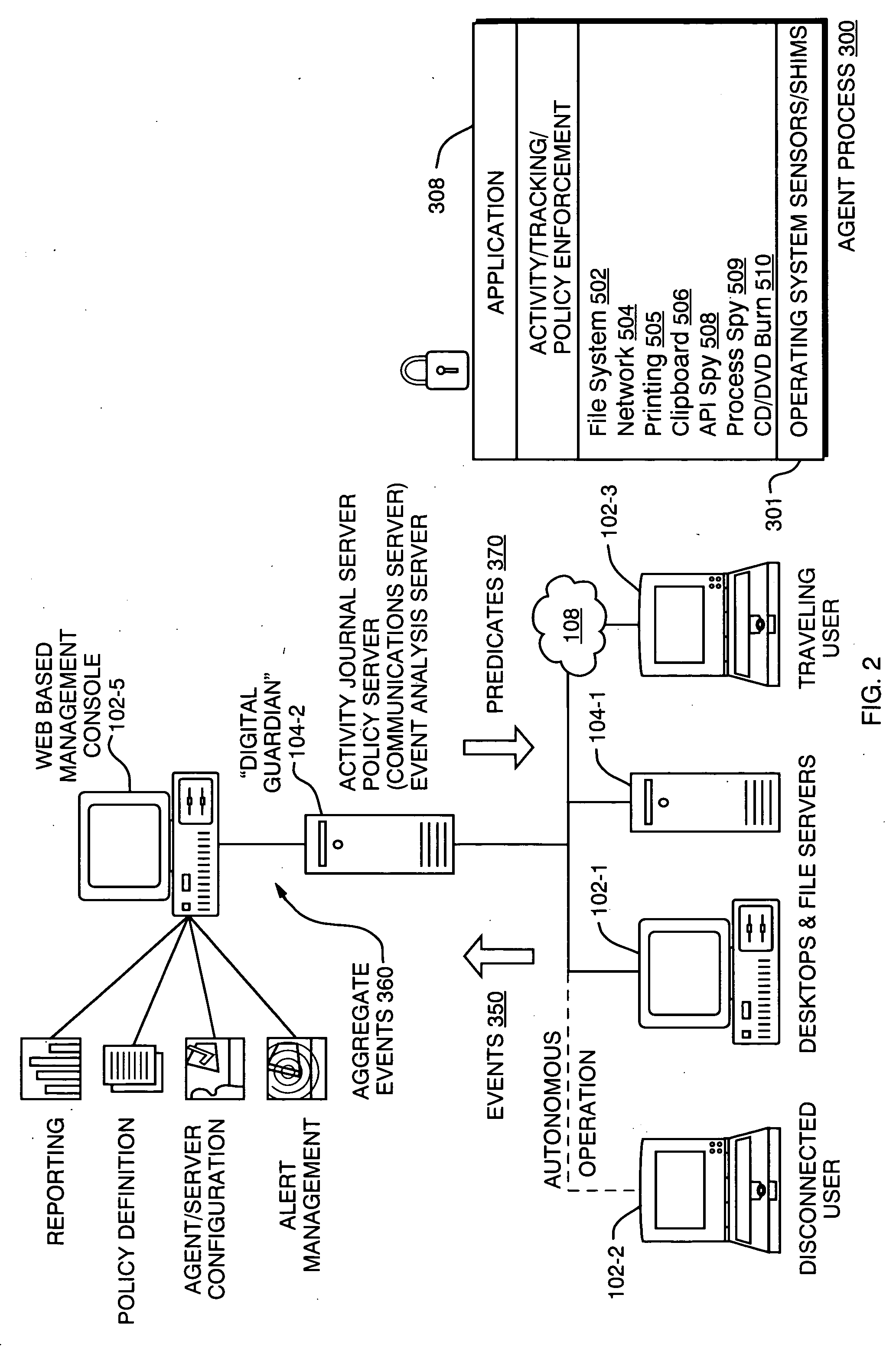
A technique for establishing usage control over digital assets such as computer files. The system model not only tracks authorized users' access to files, but monitors passage of such files to uncontrollable removable storage media or through network connections and the like which may indicate possible abuse of access rights. In accordance with a preferred embodiment, an autonomous independent agent process running at a point of use, such a background process in a client operating system kernel, interrupts requests for access to resources. The agent process senses low level system events, filters, and aggregates them. A policy engine analyzes sequences of aggregate events to determine when policy violations occur.
Owner:DIGITAL GUARDIAN LLC
Heuristic detection of malicious code
InactiveUS20090013405A1Avoid the needImprove the detection rateMemory loss protectionUnauthorized memory use protectionData fieldMalware
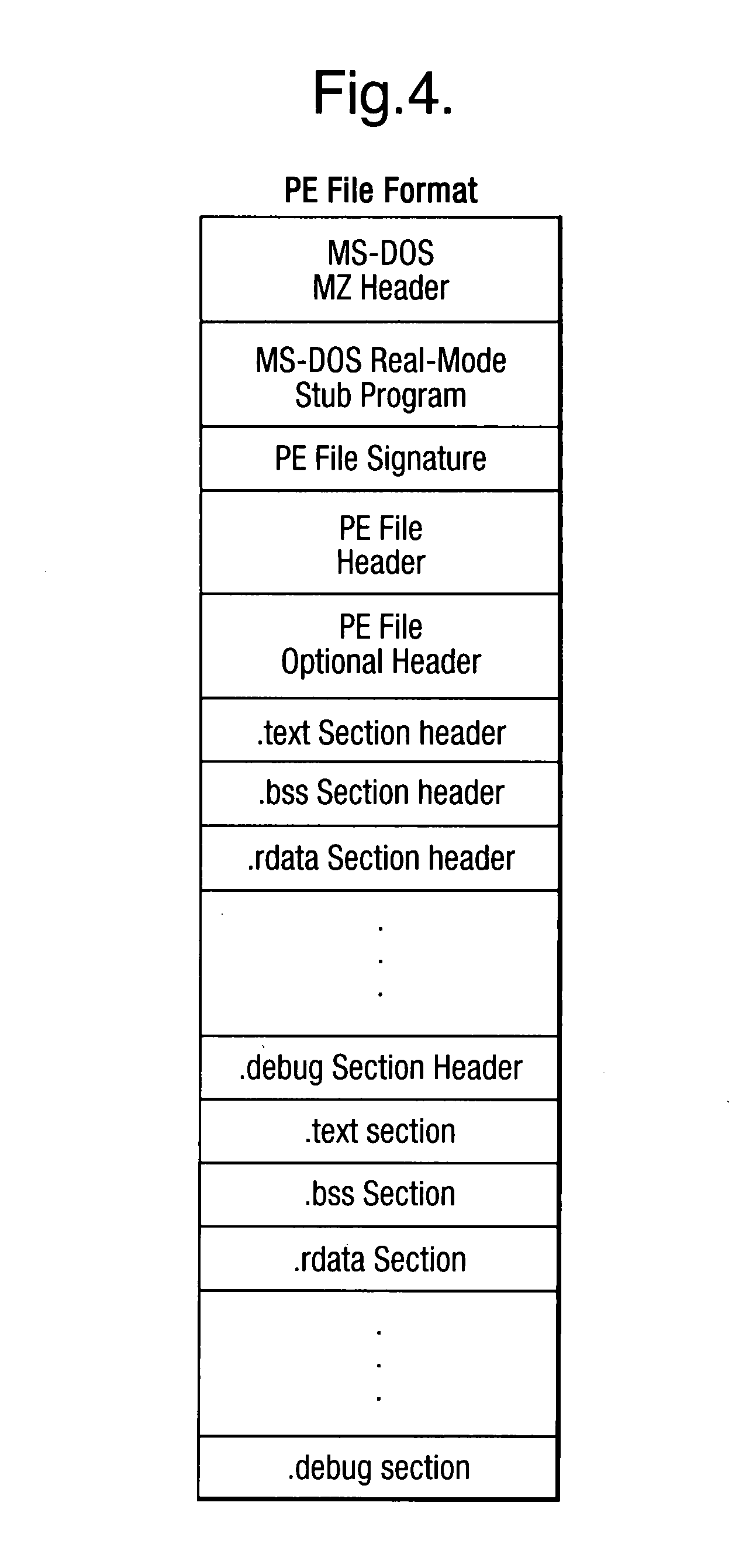
Scanning of computer files for malware uses a classifying technique to classify an input file as a clean file or a dirty file. The parameters of the classifying technique are derived to train the classification on a corpus of reference files including clean files known to be free of malware and dirty files known to contain malware. The classification is performed using a representation of the files in a feature space defined by a set of predetermined features for respective file formats, the features being a predetermined value or range of values for one or more data fields of given meanings. The representation of a file is derived by determining the file format, parsing the file on the basis of the structure of data fields in the determined file format to identify the data fields and their meaning, and determining, on the basis of the identified data fields, which of the set of predetermined features are present.
Owner:SYMANTEC CORP
Secure clipboard function
InactiveUS20070011749A1Digital data processing detailsUser identity/authority verificationFile systemUSB
Securing computer files in which a publish permission is present in a file system. Upon receiving a request to write data from one file to another, the file system determines whether publish permission is needed. If so and the user lacks the publish permission, the request is rejected. Disclosed is securing computer files which include encrypting metadata about an encrypted file and storing both the encrypted file and the encrypted metadata. The metadata includes a key for decrypting the encrypted file. The key for decrypting the metadata is stored in a USB security token. Disclosed is securing computer files which include copying material from a window displaying the contents of a file to a clipboard application. The file or window is associated with the material. The clipboard application can deny a request to paste material associated with one file to a window displaying the contents of a different file.
Owner:SIMDESK TECH INC
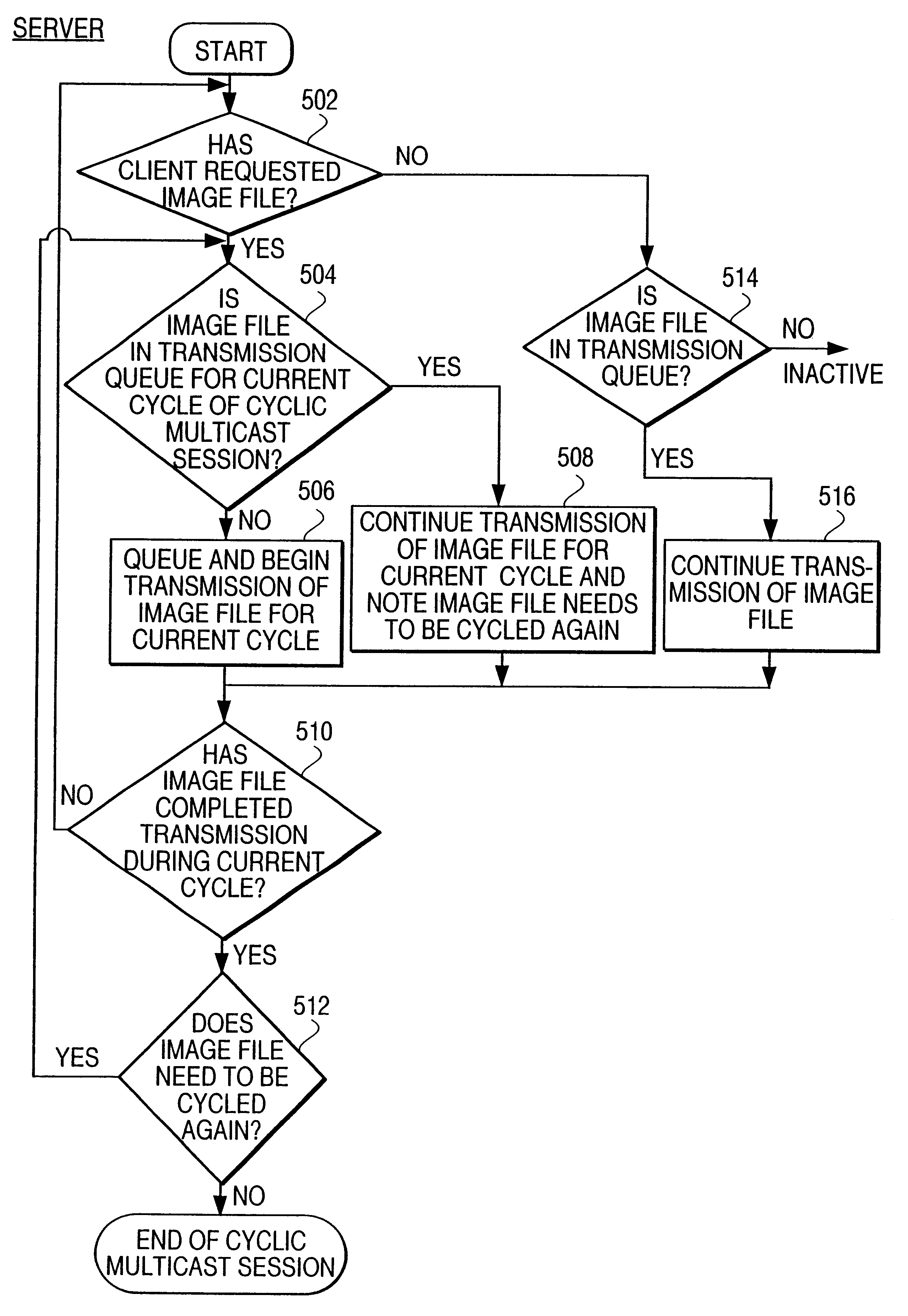
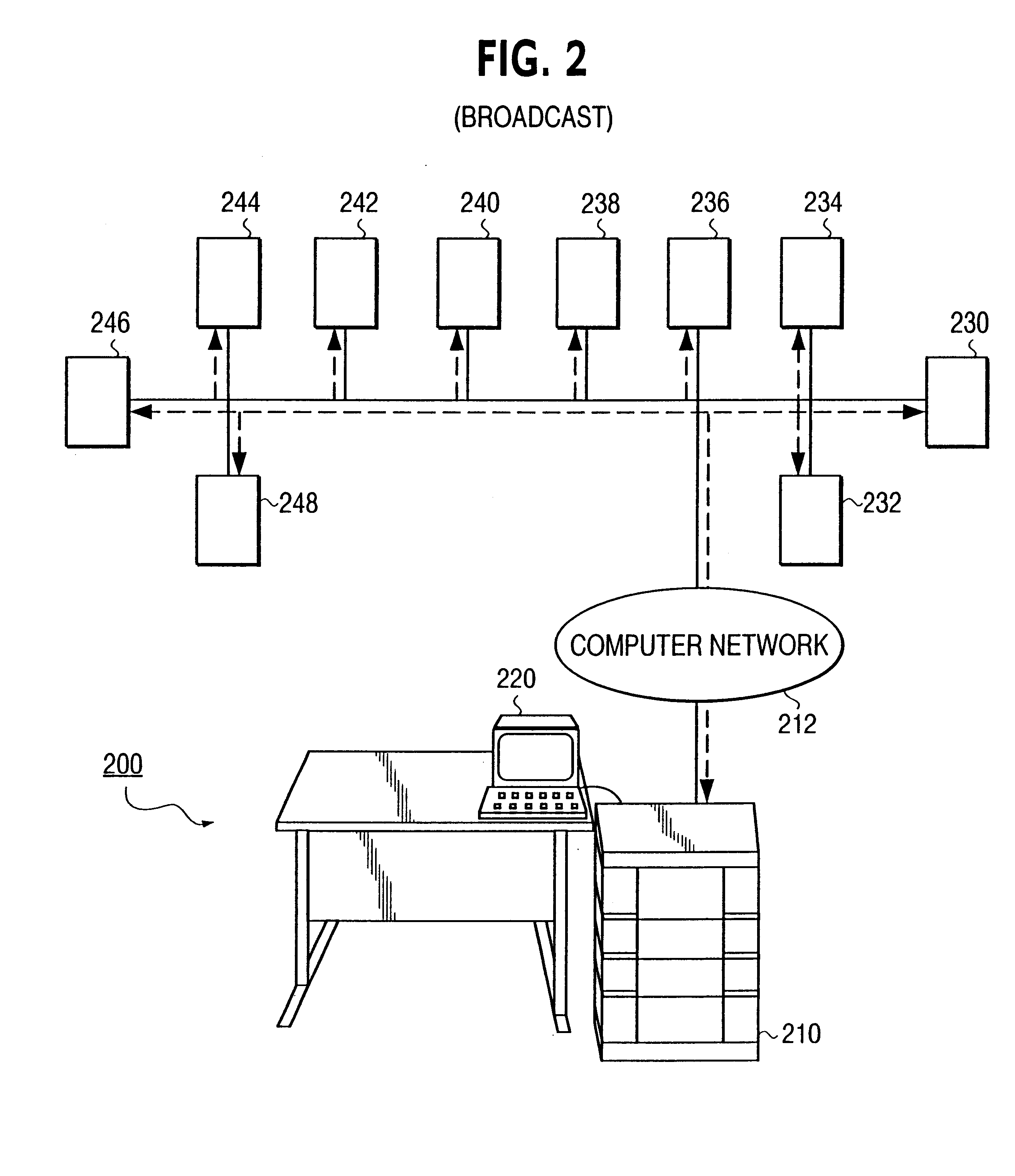
Cyclic multicasting or asynchronous broadcasting of computer files
InactiveUS6256673B1Special service provision for substationMultiple digital computer combinationsData providerNetworked system
A client / server network system is disclosed for cyclic multicasting of an image file from a central data provider (server) to one or more remote client machines (workstations) over a computer network with minimum network transmission while allowing any number of client machines (workstations) to download the image file at any moment in time without the need to synchronize with the central server's transmission. The network system includes a computer network; a plurality of remote client machines on the computer network; and a central server for providing a cyclic multicasting of an image file to one or more client machines over the computer network concurrently through the use of different transmission cycles of a single cyclic multicast session. An image file is asynchronously transferred from the central server to one or more remote client machines concurrently over a computer network through the use of different transmission cycles during a single cyclic multicast session so as to keep the network transmission and network bandwidth to a minimum.
Owner:MICRON TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com