Patents
Literature
320 results about "Software license" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A software license is a legal instrument (usually by way of contract law, with or without printed material) governing the use or redistribution of software. Under United States copyright law, all software is copyright protected, in both source code and object code forms, unless that software was developed by the United States Government, in which case it cannot be copyrighted. Authors of copyrighted software can donate their software to the public domain, in which case it is also not covered by copyright and, as a result, cannot be licensed.
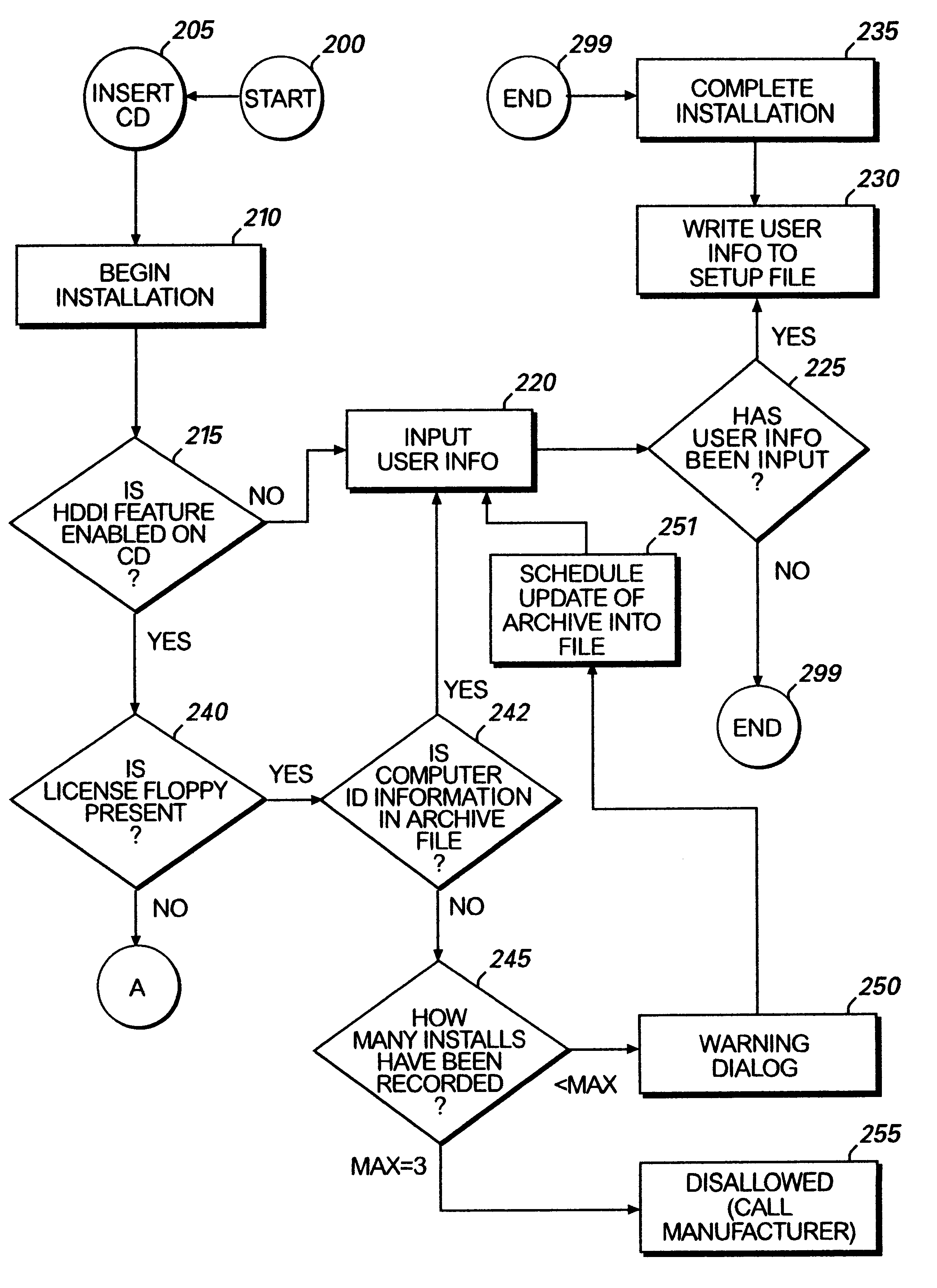
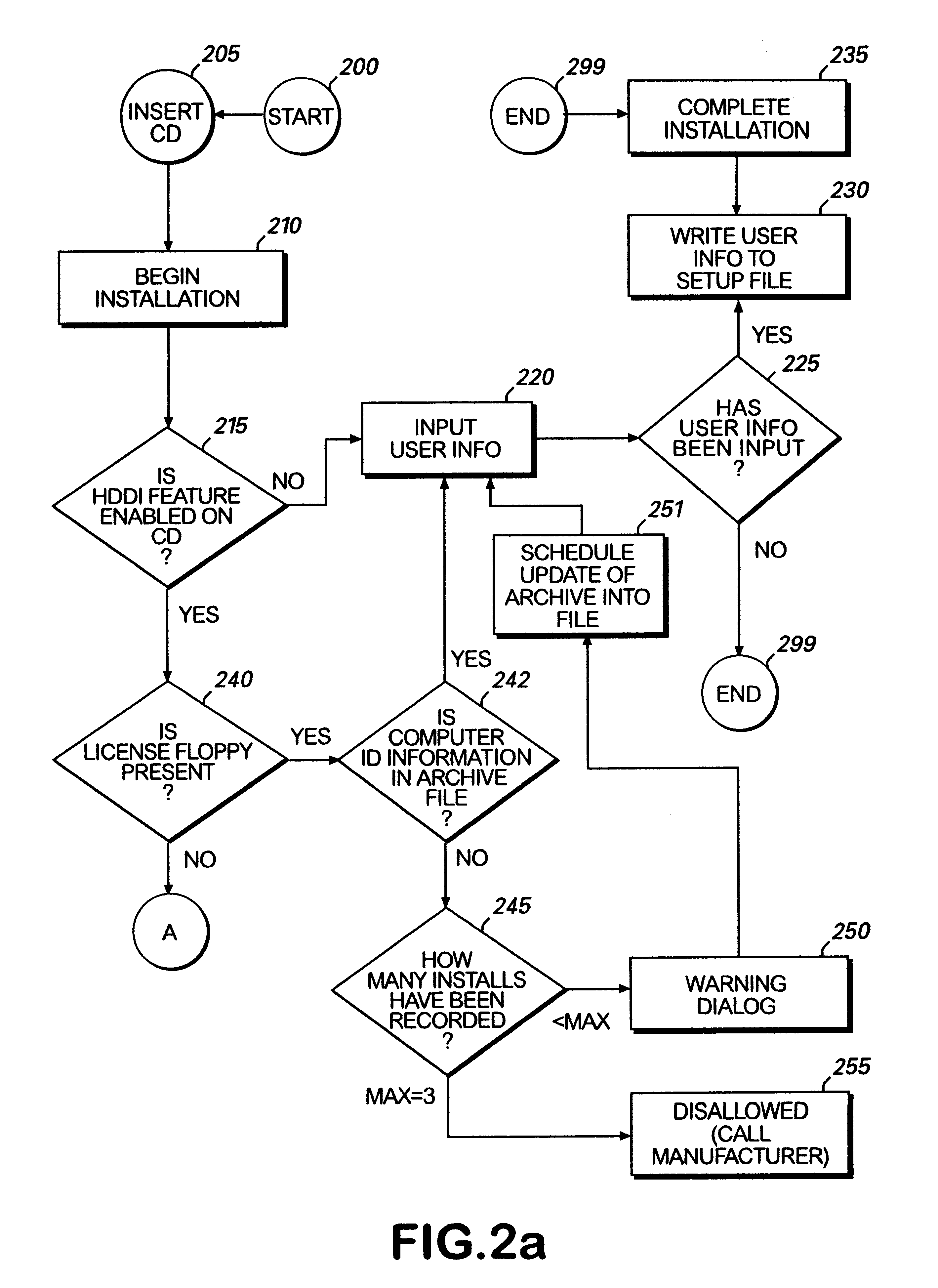
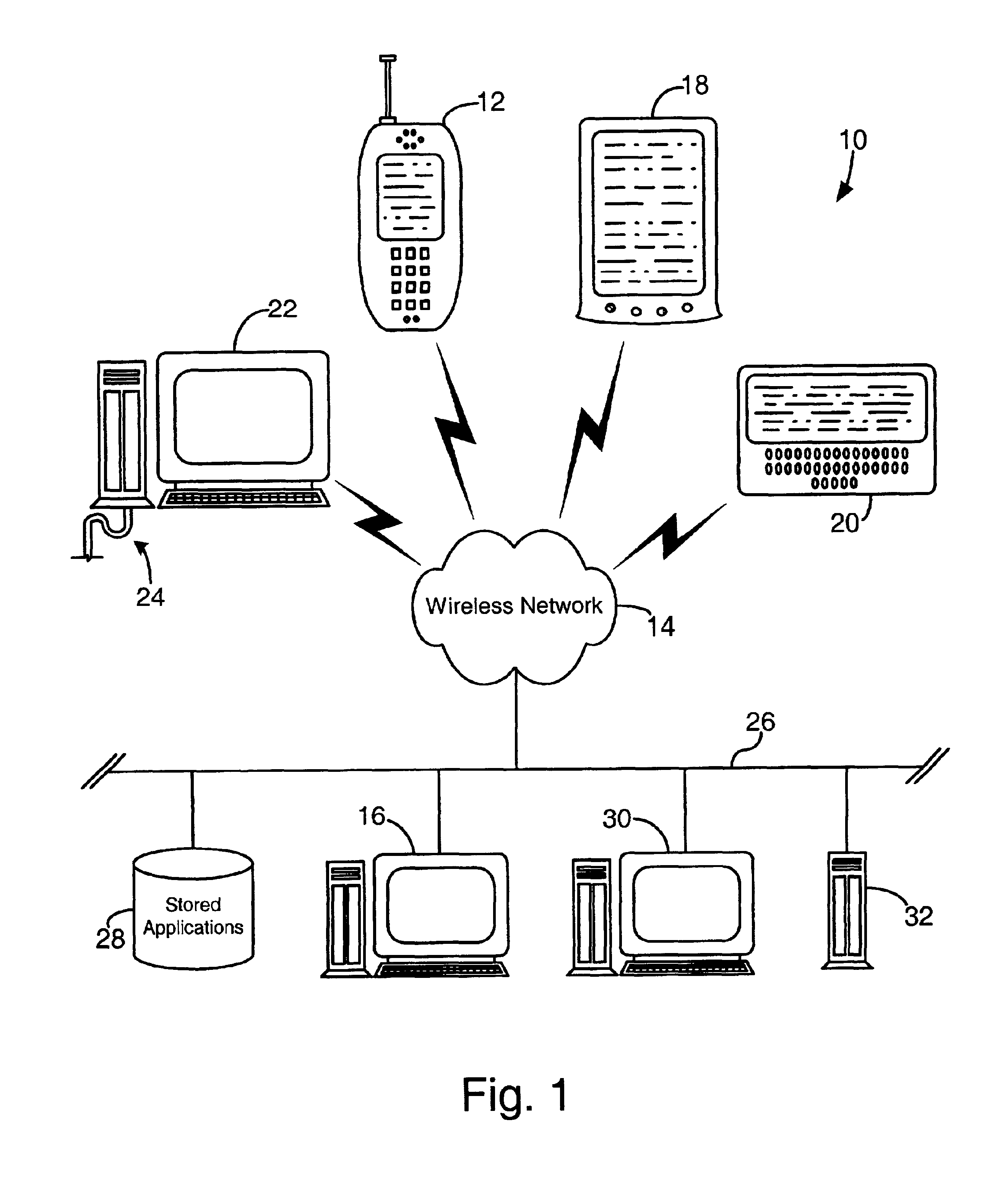
Method for preventing software piracy during installation from a read only storage medium
InactiveUS6226747B1Easy to installDigital data processing detailsRecord information storageSoftware licenseComputer software
The method and system for limiting the number of installations of a computer software program located on a read only disk from the read only disk to a computer. The read only disk is linked to a removable read / write memory by data on the removable read / write memory corresponding to data on the read only disk. Prior to installation of the computer software program from the read only disk to the computer, software residing on the removable read / write memory determines whether the installation is authorized. Such determination is made by comparing identification information corresponding to computers on to which the computer software program has previously been installed to installation limitations dictated by a software license agreement.
Owner:MICROSOFT TECH LICENSING LLC
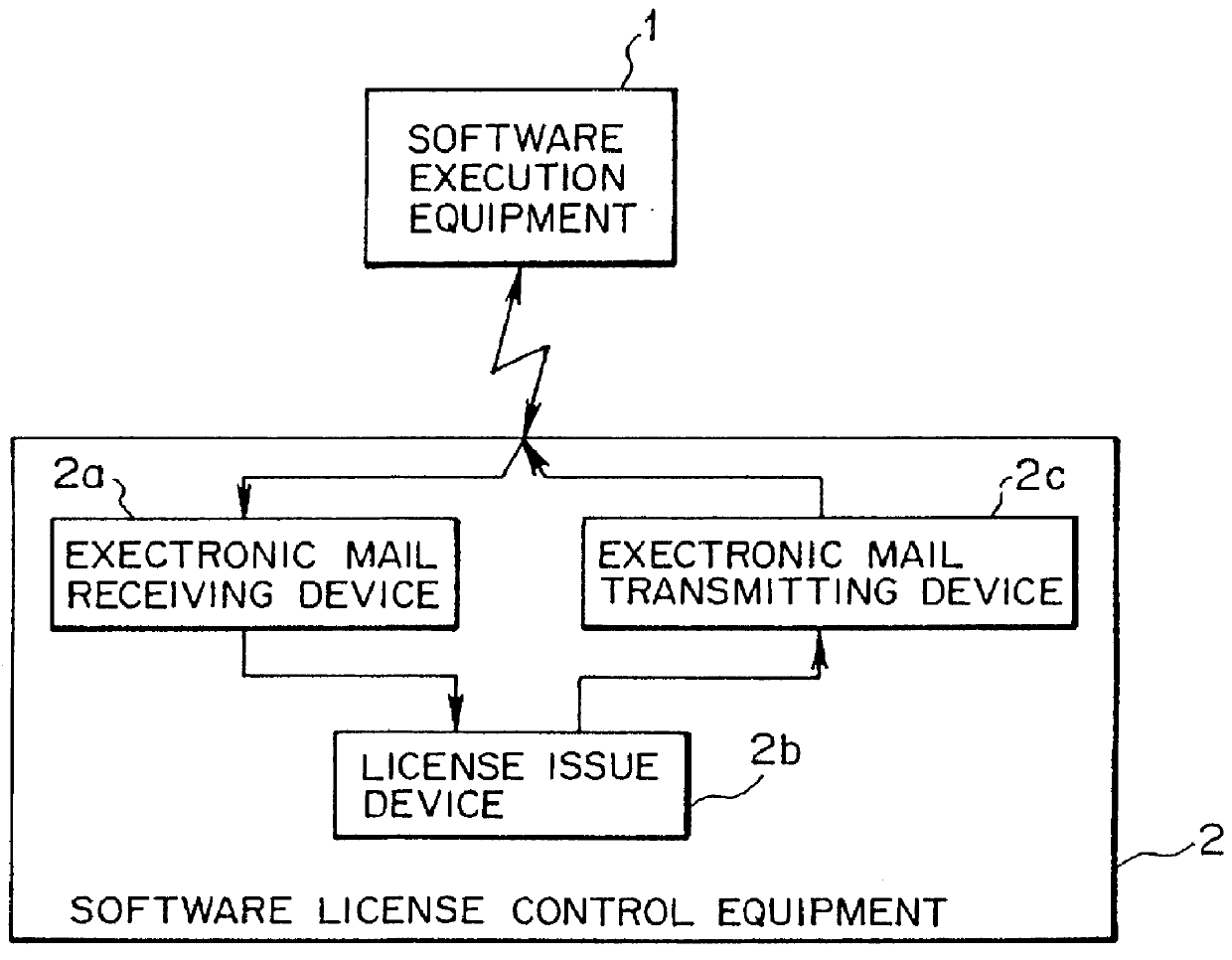
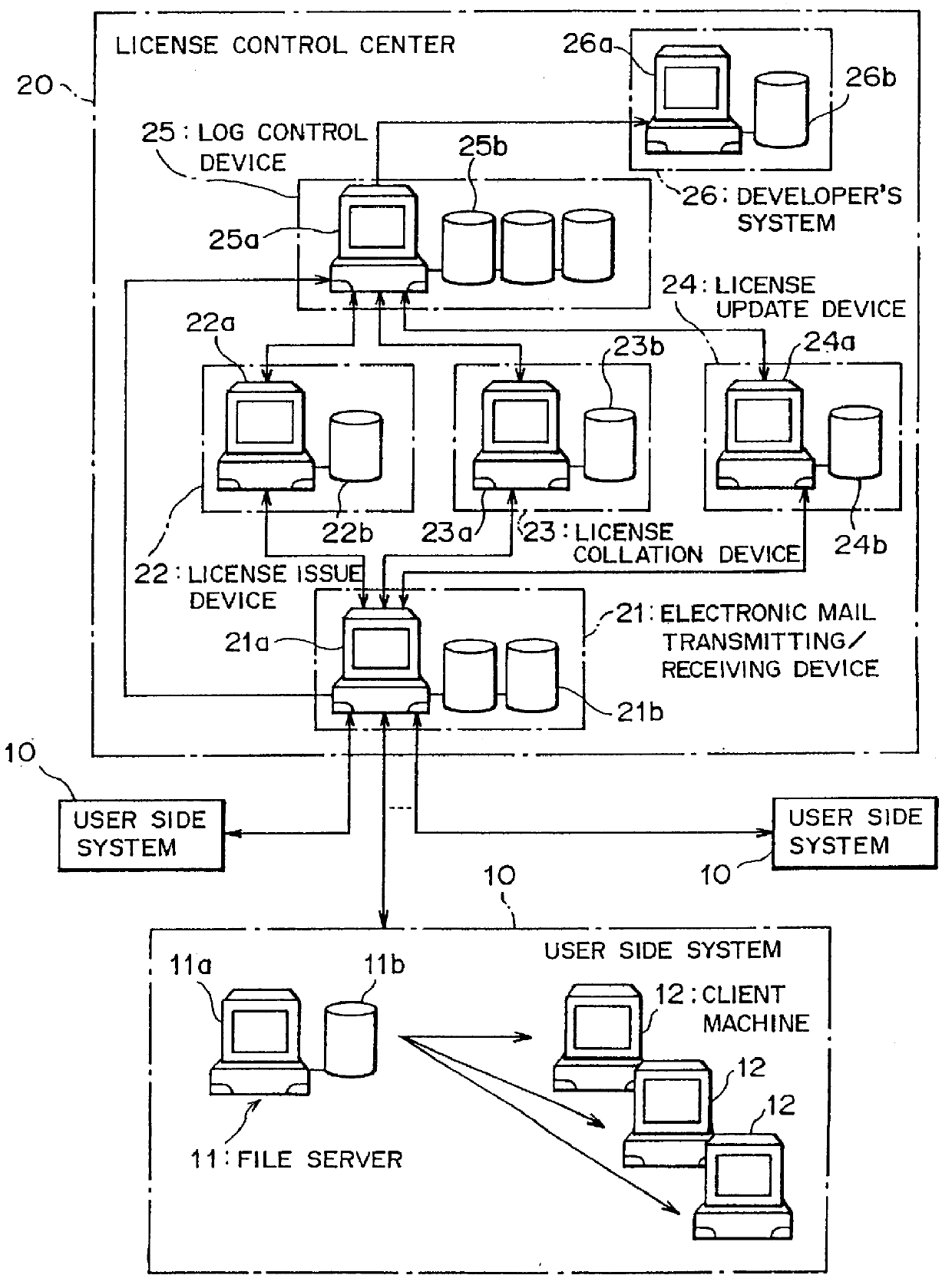
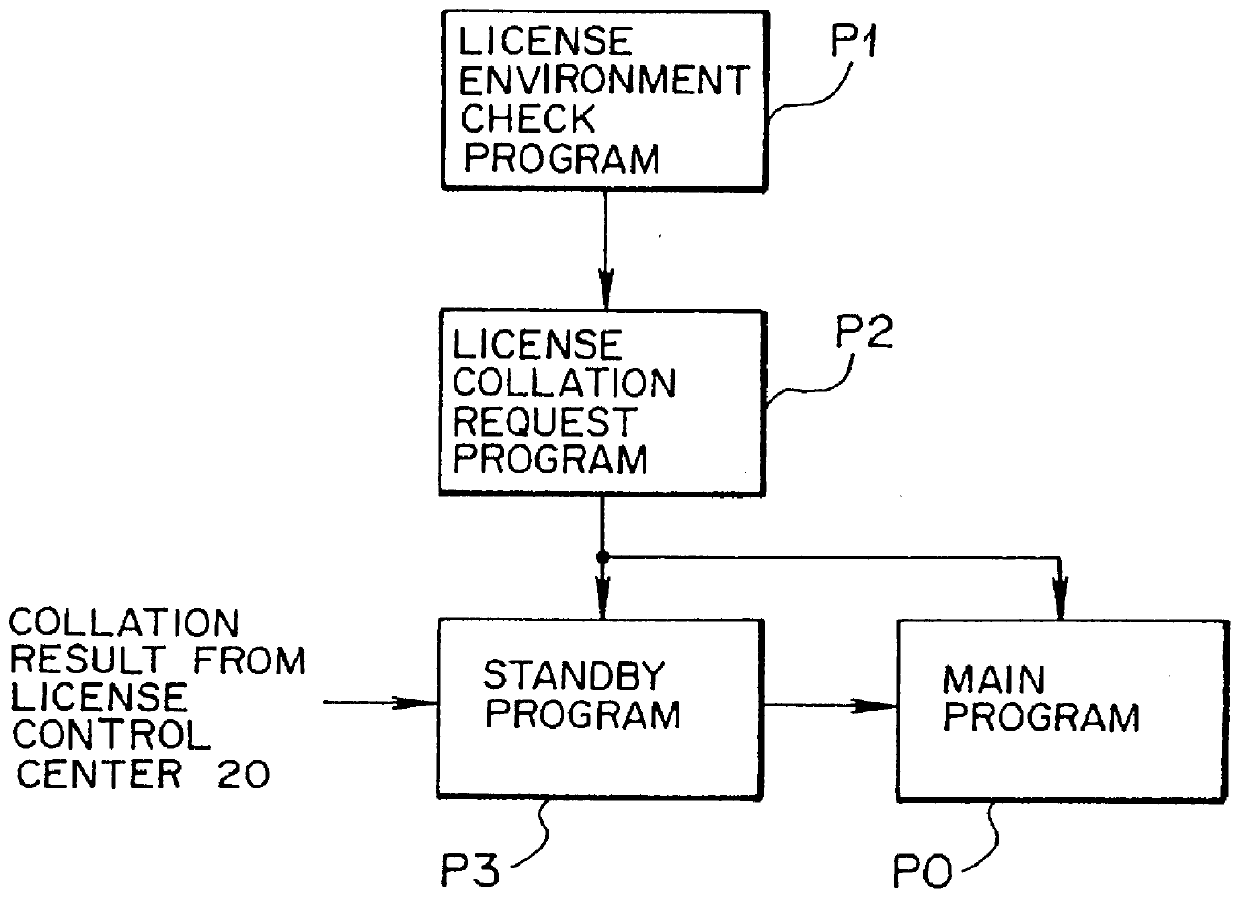
Software license control system and software license control equipment
InactiveUS6023766AImprove reliabilityEasy to operate and controlDigital data processing detailsUnauthorized memory use protectionSoftware licenseLicense control
The invention provides a software license control system and a software license control equipment that control a license for a software (application program) used in a computer, that realizes to make the license control of the software efficient, to enhance reliability of the license, and to simplify control operations by users. In order to achieve the object, the system according to the invention is provided with a software execution equipment that executes the software on which a license control software is added and a software license control equipment that controls the license for the software. The system is so designed as to interchange information relating to the license for the software between the software execution equipment and the software license control equipment by means of an electronic mail.
Owner:SOCIONEXT INC
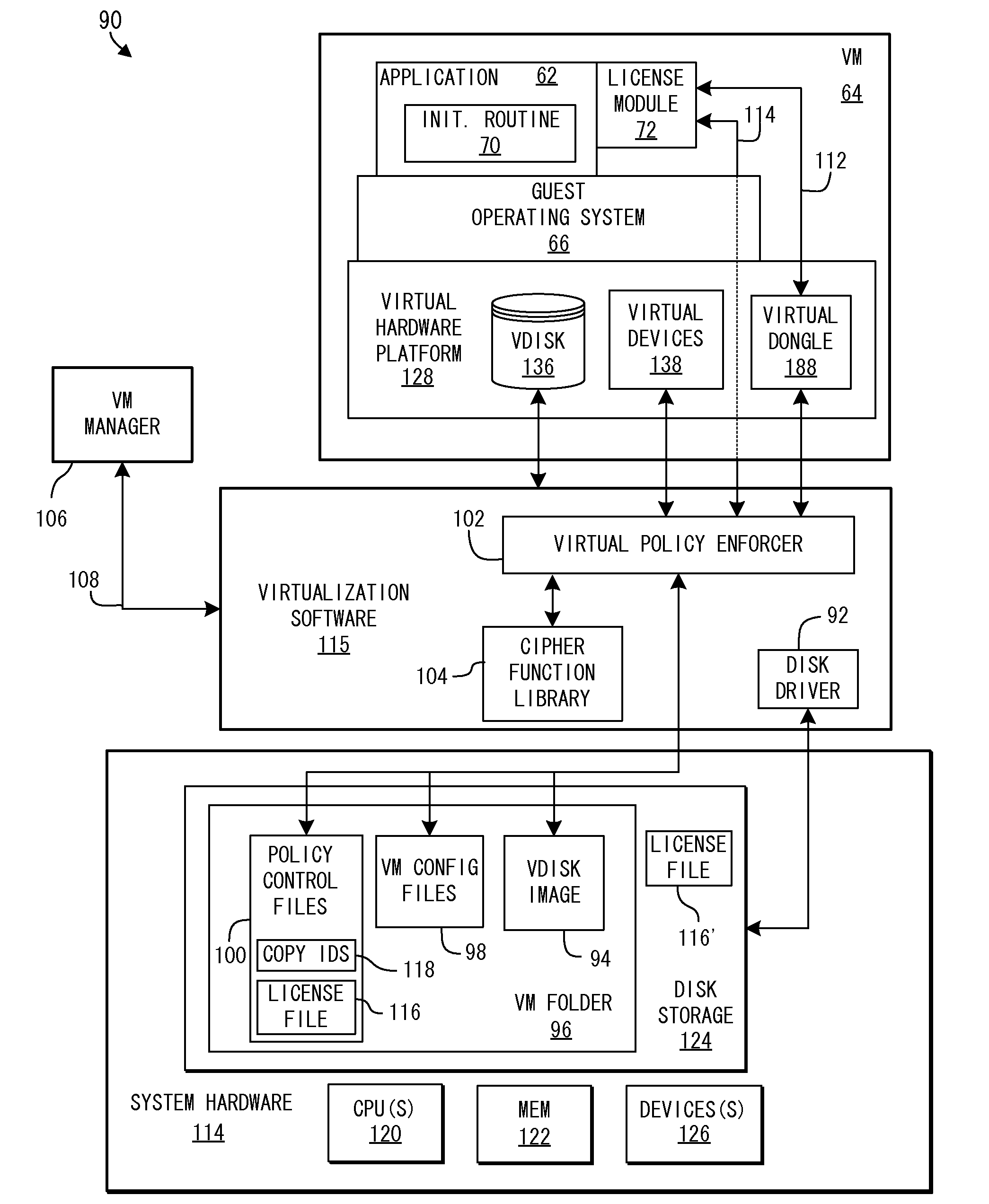
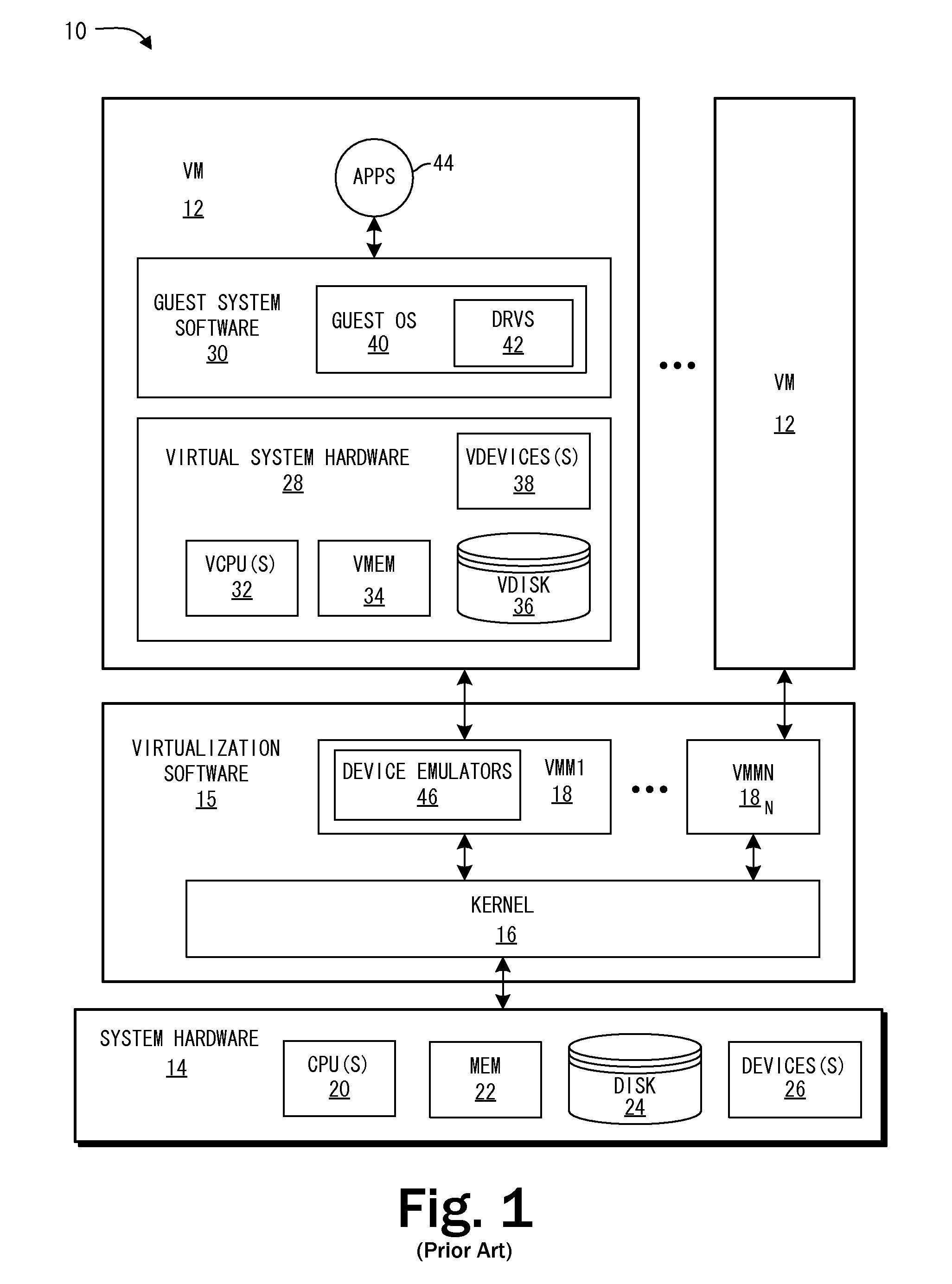
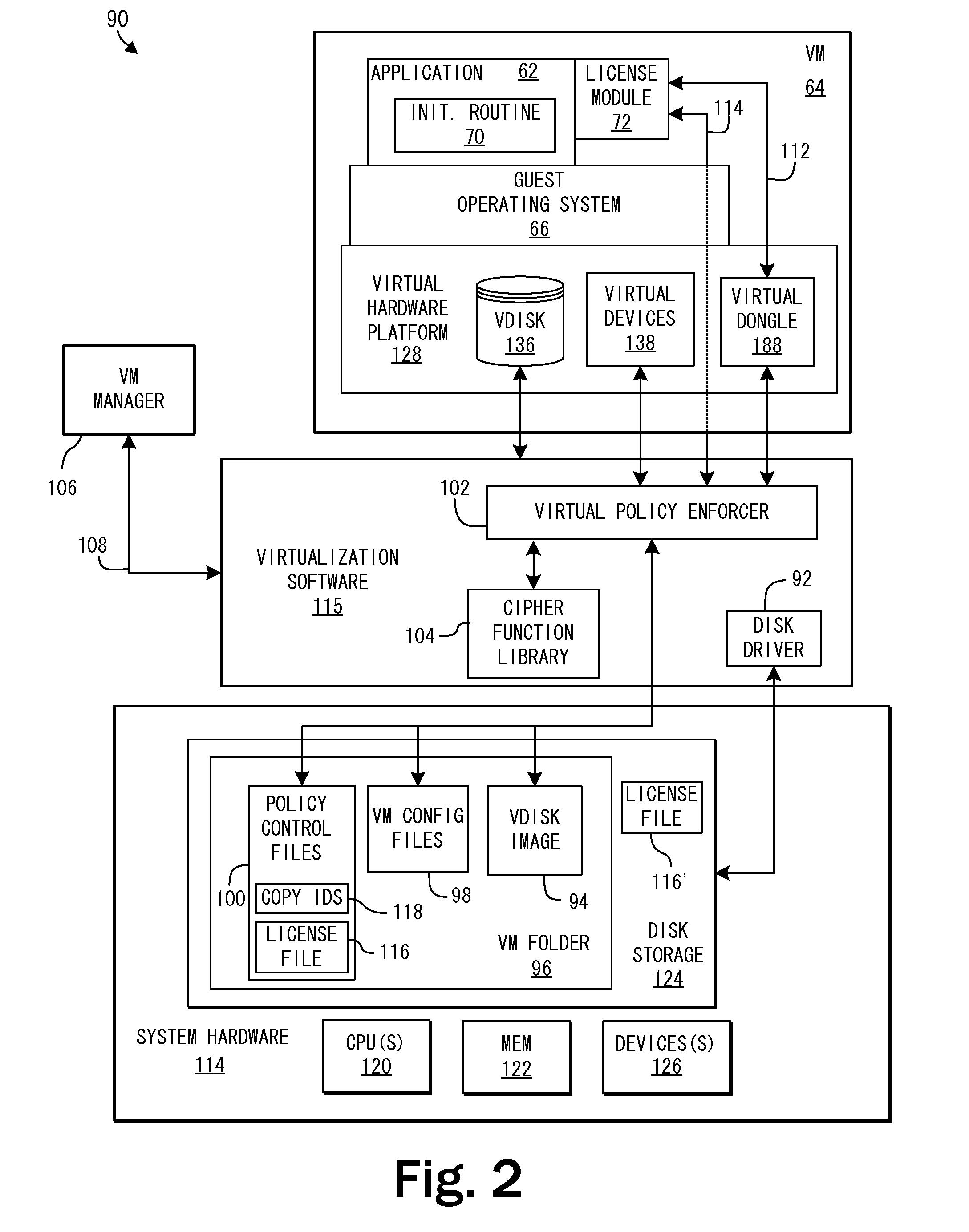
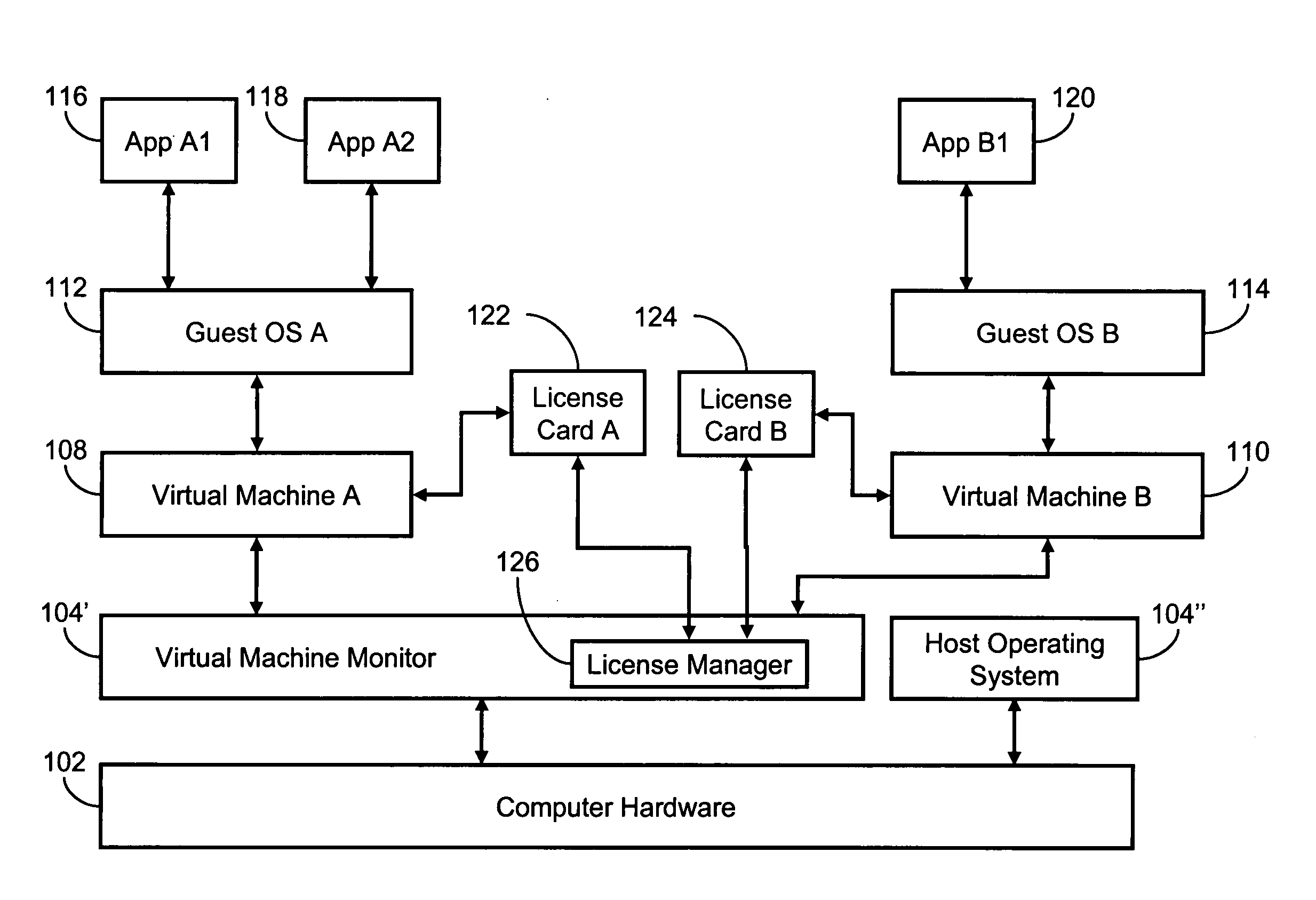
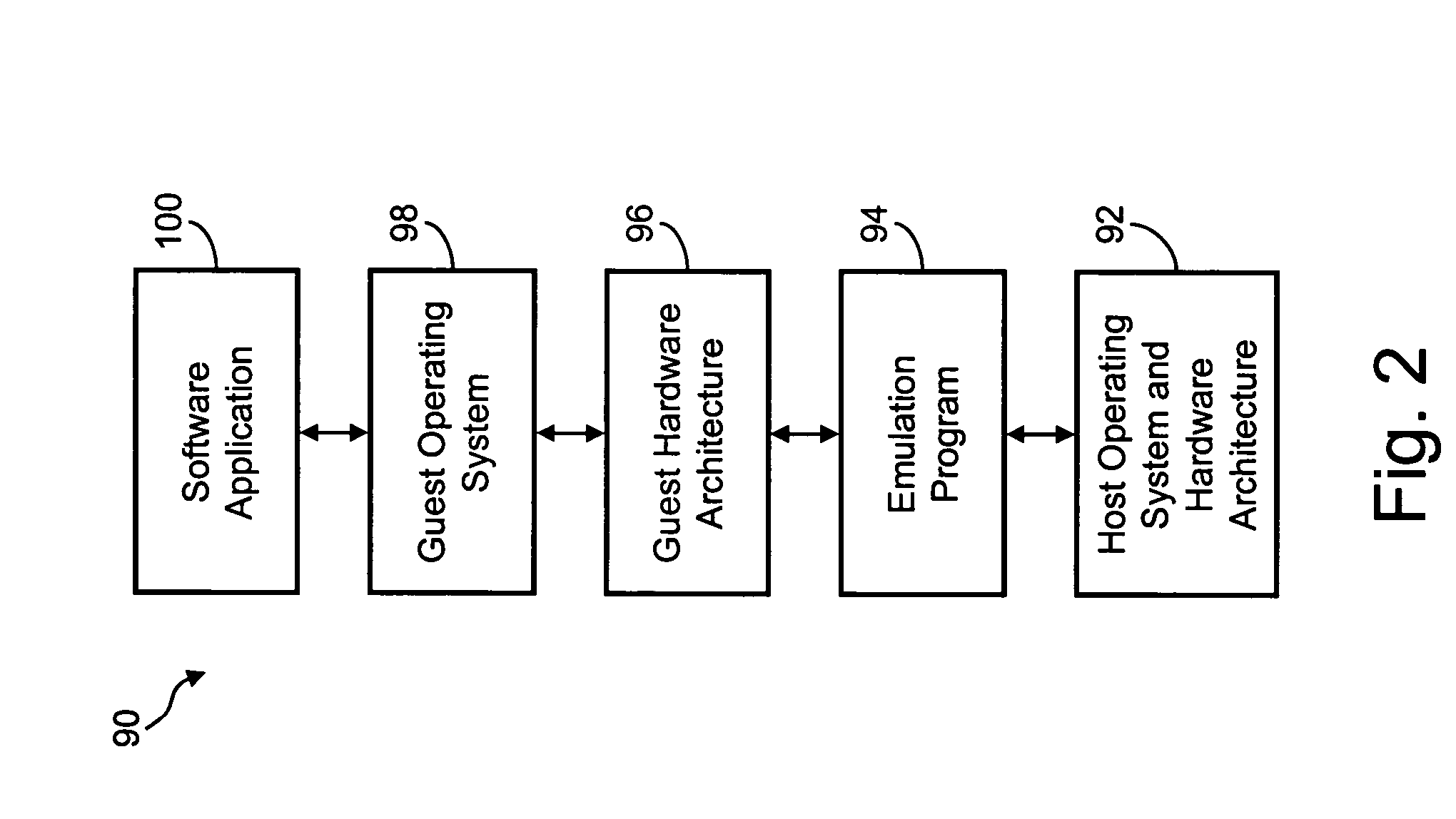
System and Methods for Enforcing Software License Compliance with Virtual Machines
ActiveUS20090328225A1Digital data processing detailsAnalogue secracy/subscription systemsVirtualizationOperational system
A virtualization system supports secure, controlled execution of application programs within virtual machines. The virtual machine encapsulates a virtual hardware platform and guest operating system executable with respect to the virtual hardware platform to provide a program execution space within the virtual machine. An application program, requiring license control data to enable execution of the application program, is provided within the program execution space for execution within the virtual machine. A data store providing storage of encrypted policy control information and the license control data is provided external to the virtual machine. The data store is accessed through a virtualization system including a policy controller that is selectively responsive to a request received from the virtual machine to retrieve the license control data dependent on an evaluation of the encrypted policy control information.
Owner:VMWARE INC
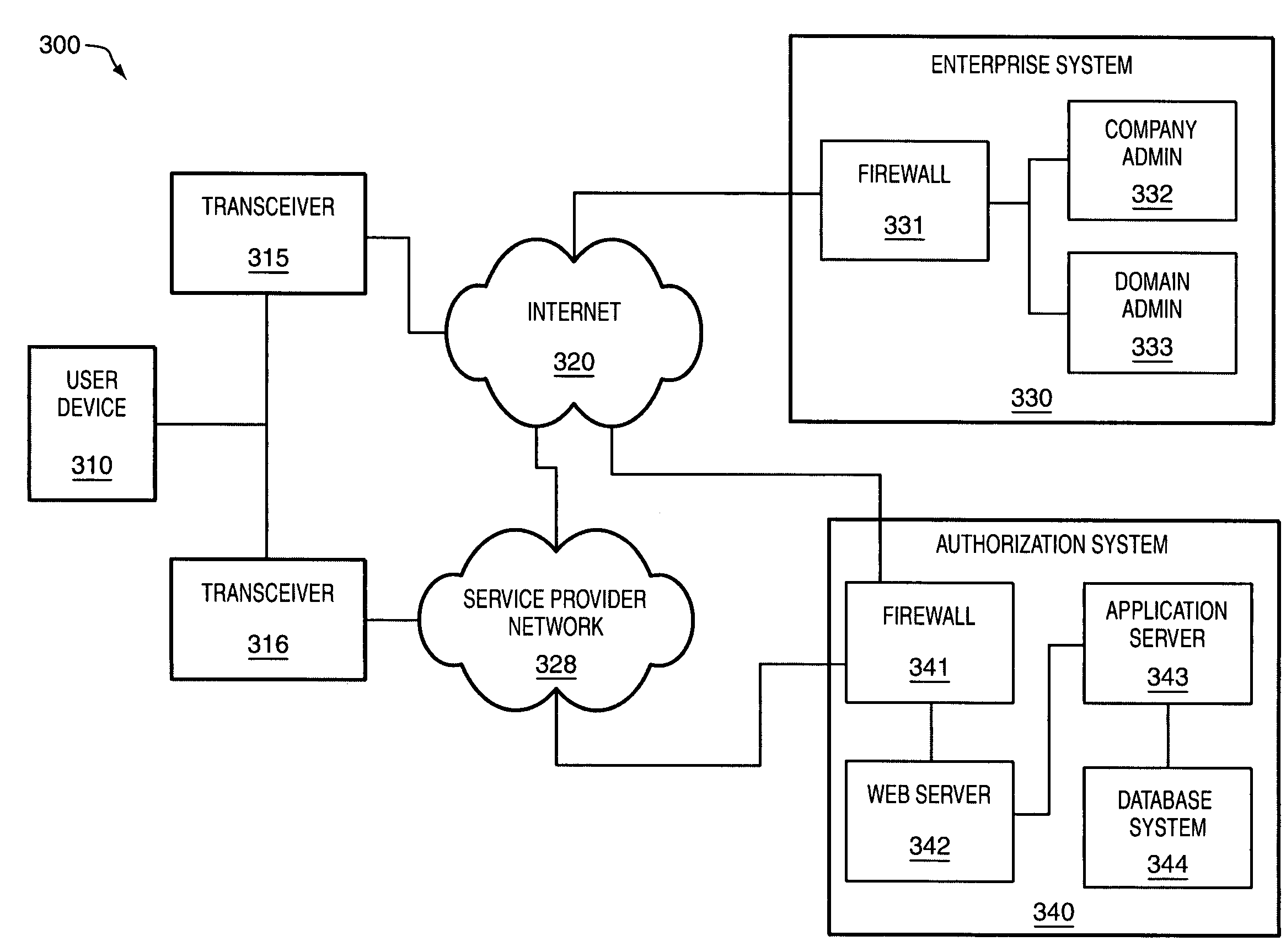
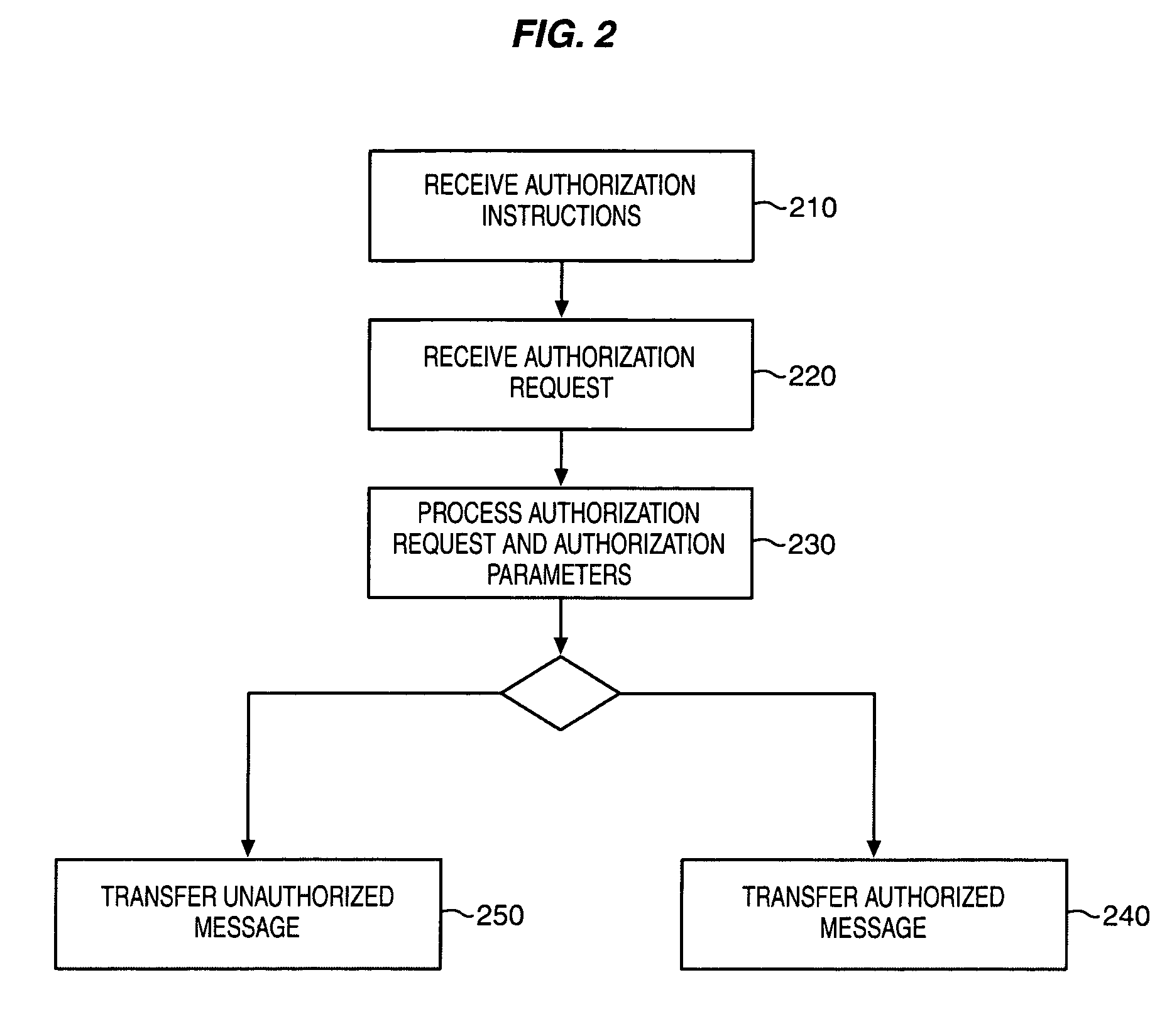
Software license authorization system
ActiveUS7703142B1Digital data processing detailsUser identity/authority verificationUser deviceSoftware license
An authorization system is described that includes a first interface, a processing system, and a second interface. The first interface is configured to receive an authorization instruction from an enterprise and receive an authorization request from a user device. The authorization instructions indicate authorization parameters. The user device transfers the authorization request each time the application is selected for execution. The authorization instructions are based on a license obtained by the enterprise for an application and wherein a user device operated by a user has the application. The processing system is configured to process the authorization request and authorization parameters to determine if the execution of the application is authorized. The second interface is configured to transfer an authorized message to the user device if the execution of the application is authorized and transfer an unauthorized message to the user device if the execution of the application is not authorized.
Owner:T MOBILE INNOVATIONS LLC
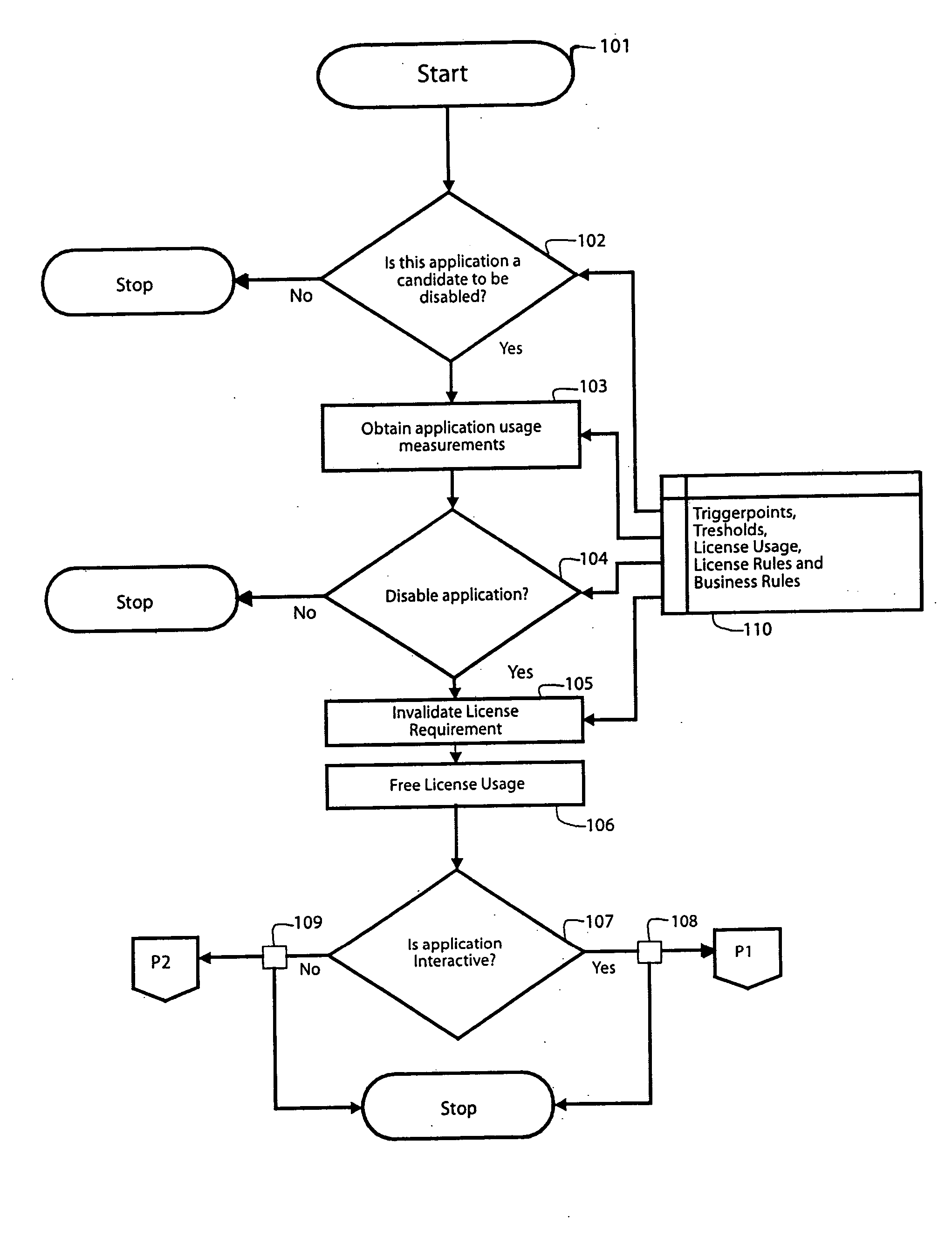
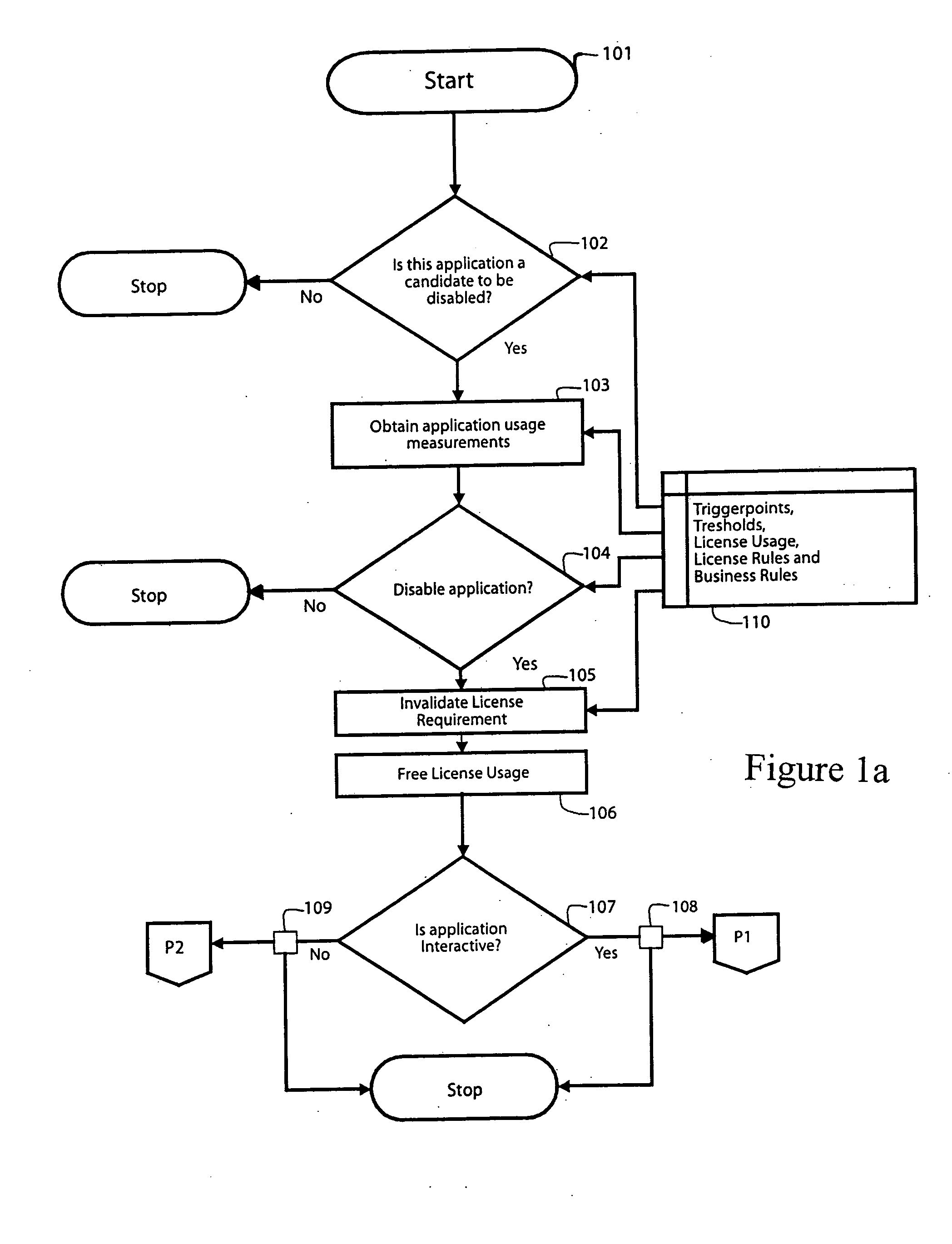
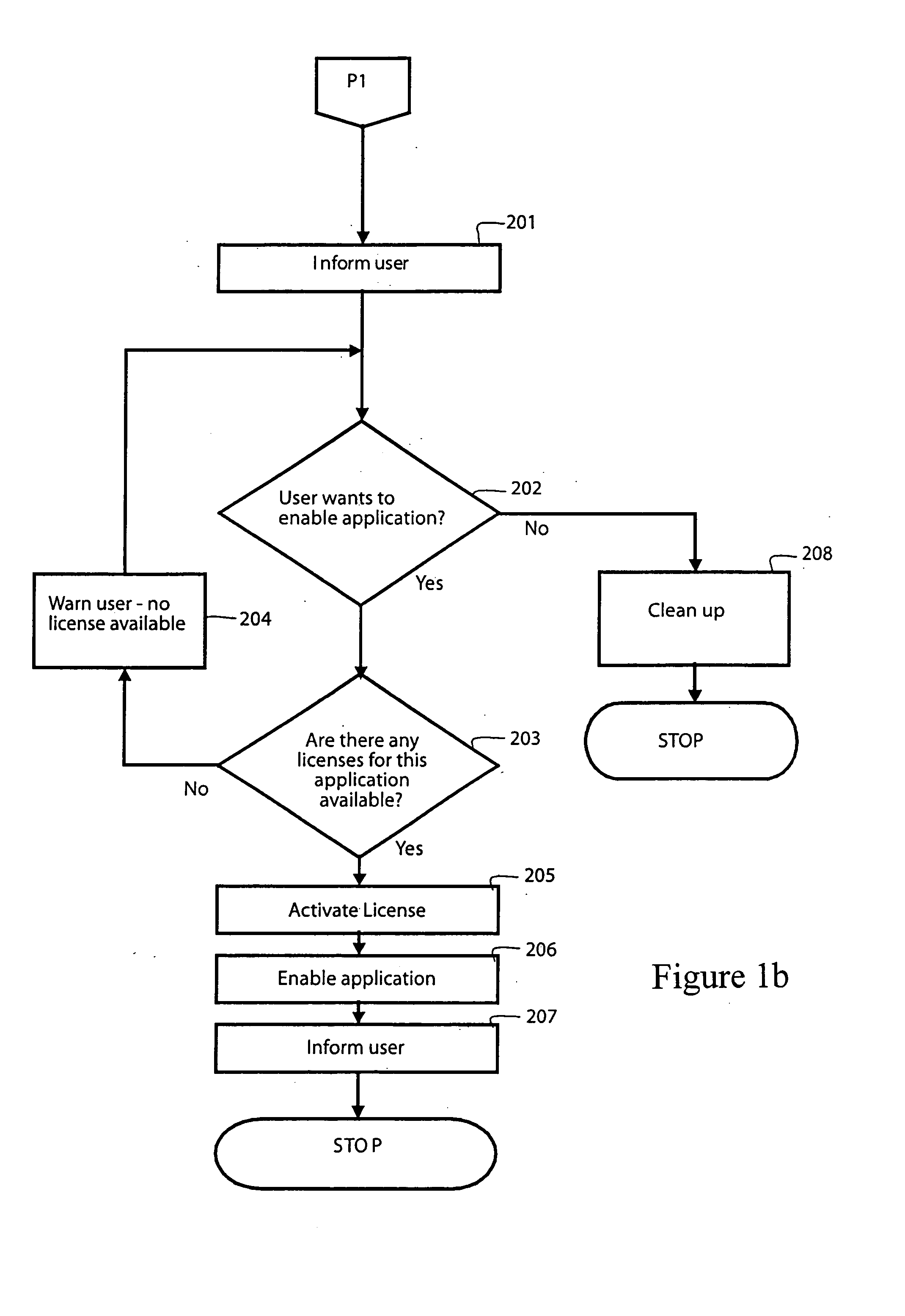
Method and program for automated management of software license usage by monitoring and disabling inactive software products
InactiveUS20050049973A1Optimal and efficientLow costResourcesProgram/content distribution protectionSoftware licenseApplication software
Method and automatic software application for monitoring and controlling usage of application-type and operating system software programs under bulk software licenses to organizations to cost-effectively utilize software license usage rights. The program automatically monitors and identifies fallow program usages based on criteria that are configurable selectable, disables the fallow program(s) to free-up one or more licenses, and then withdraws the license rights thereto and notifies the user of the disabled program of the action taken. The disabling of a program or application is on the basis of the least disruptive to the user, and the user may have the program re-enable the program. Enterprise-selected priorities can be assigned to related programs to permit completion of tasks in process, in preference to other users. The program may itself, or via a license manager redistribute, or make available freed-up license rights as needed in the organization.
Owner:READ MARK A +3
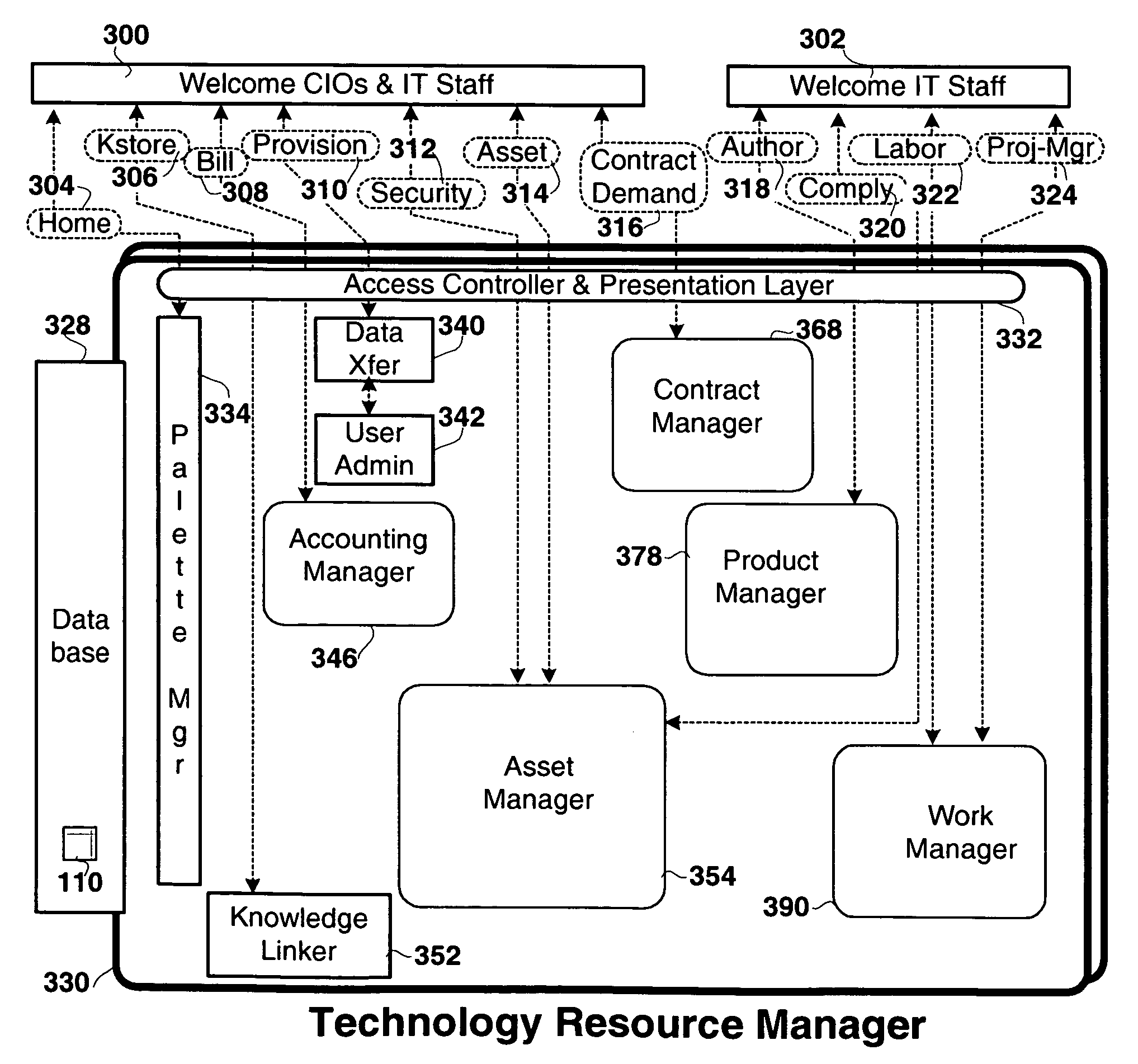
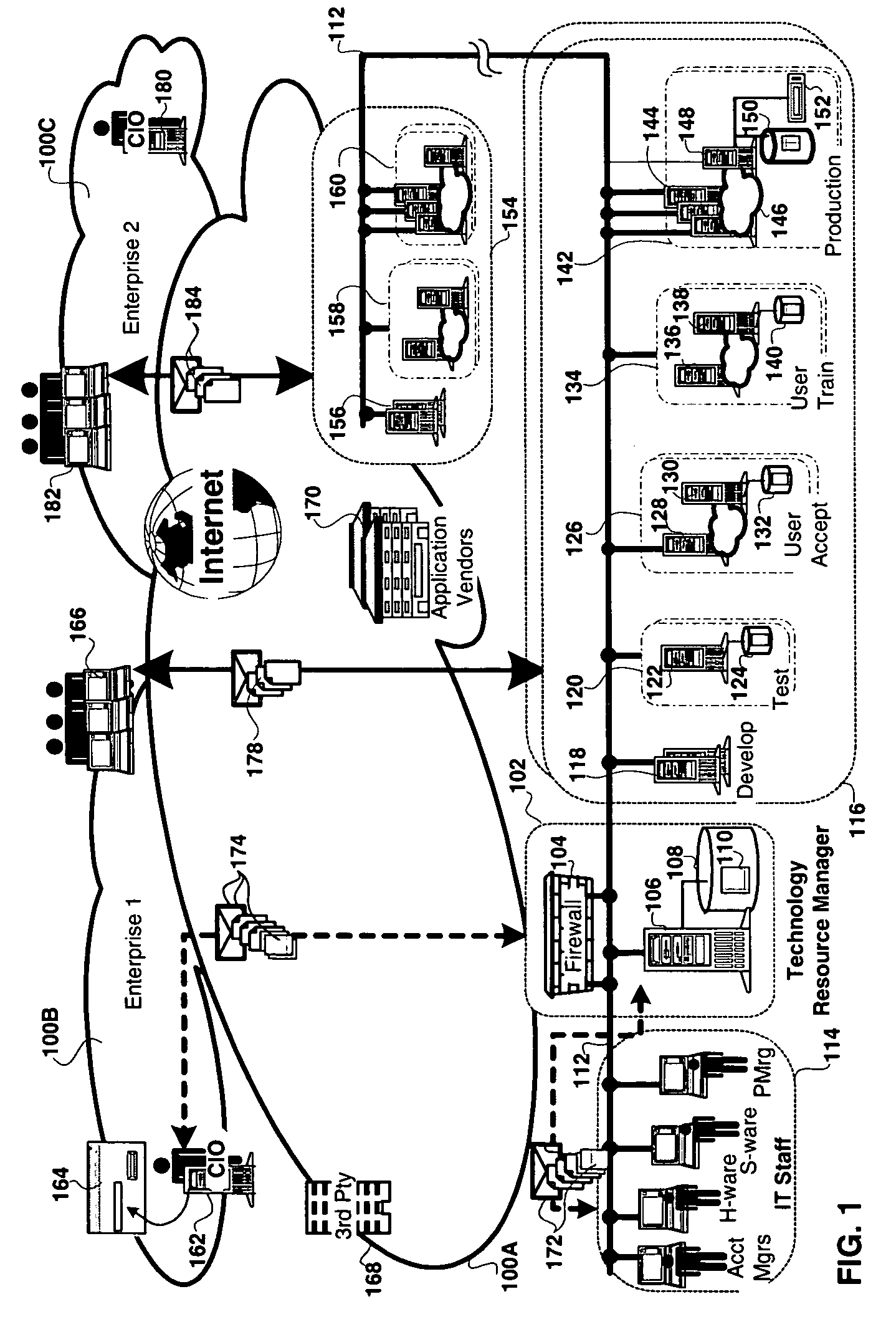
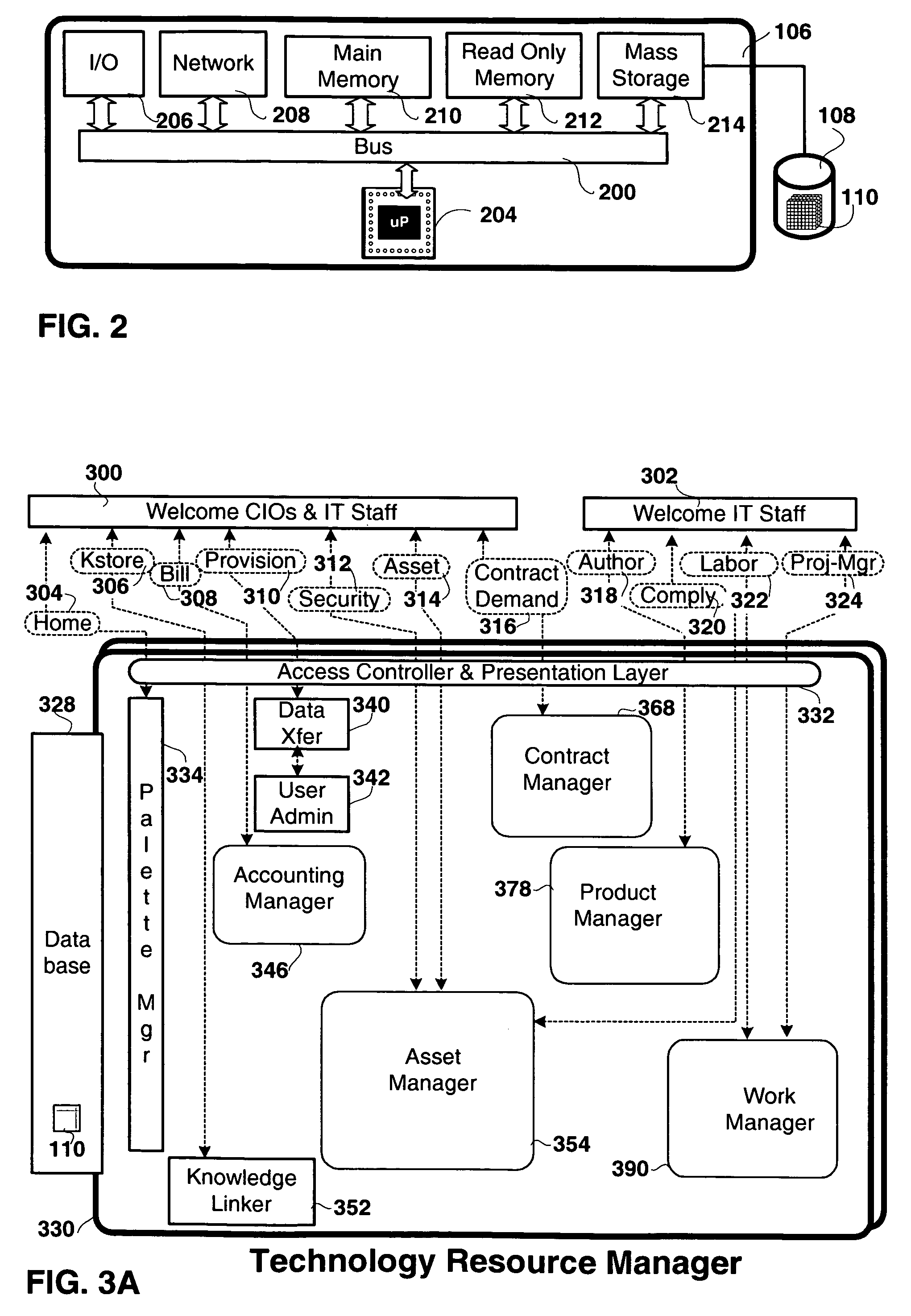
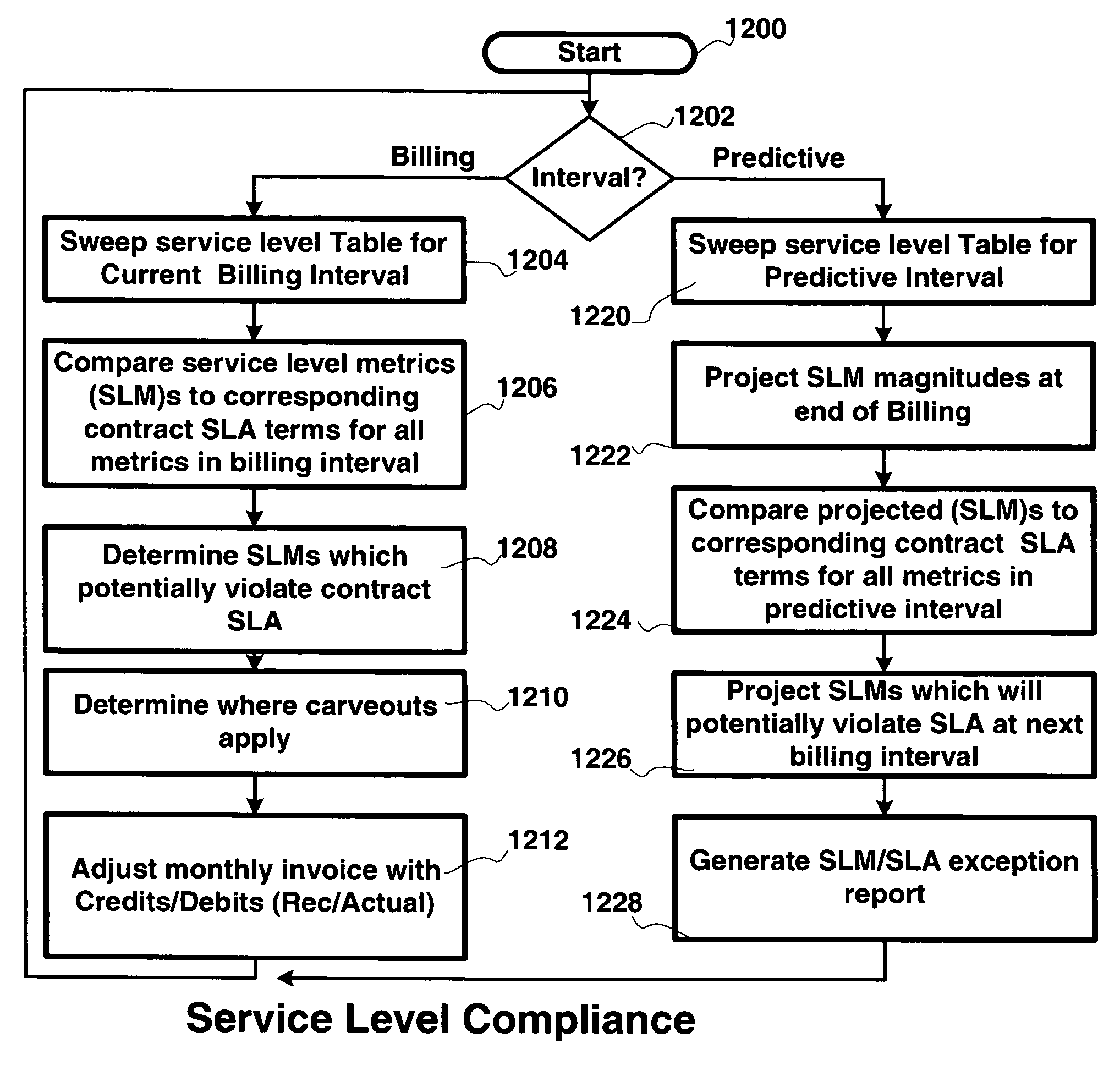
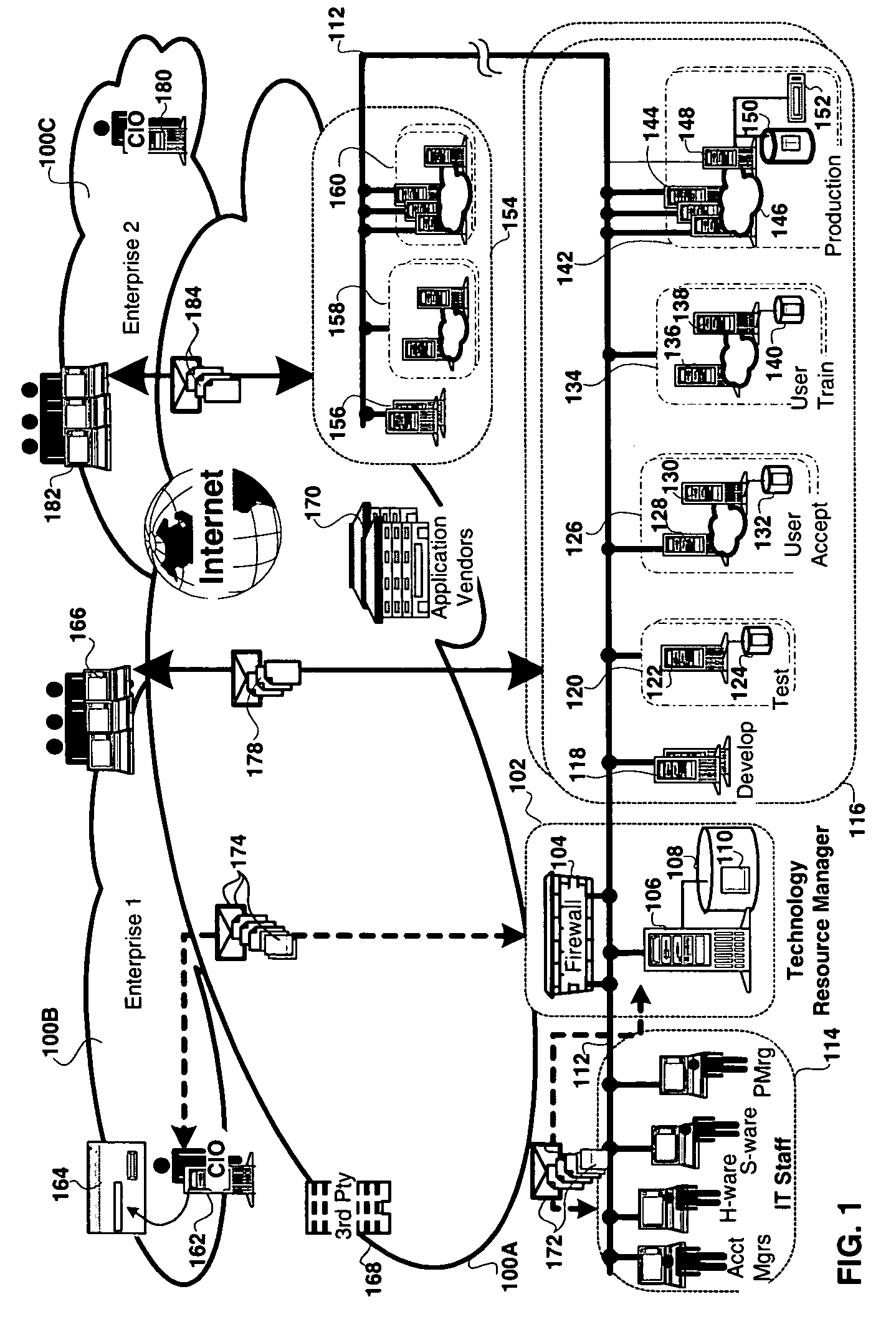
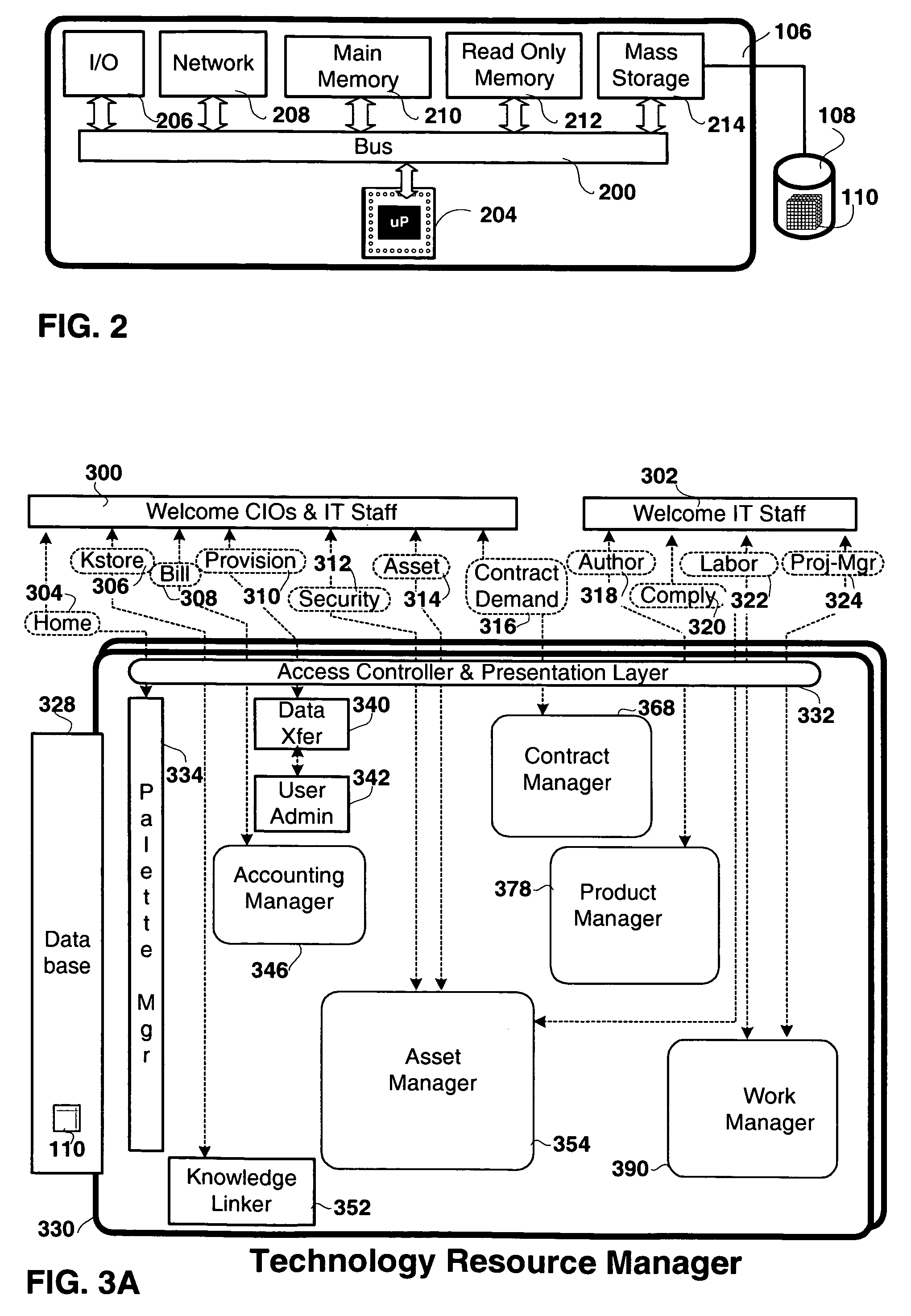
Method and apparatus for technology resource management
Apparatus, and associated methods, manage technology resources in hosted applications including: demand, service level agreements, assets both hardware and software, projects, labor, knowledge and provisioning. The apparatus includes an asset manager configured to couple to host servers and a network, to manage the host servers and software deployed thereon. In embodiments of the invention the asset manager: determines demand for new assets and allocates available assets to meet the demand; determines assets not in compliance with existing software licenses; determines which host servers have actual service level metrics which are not compliant with the target service level metrics; and determines availability of a patch or upgrade for selected software and instances of the selected software among the assets. In an embodiment of the invention the asset manager couples to a contract manager with the asset manager determining the assets for which actual monitored service level metrics violate contract service level metrics. In an embodiment of the invention the asset manager couples to a product manager and scans the host severs to determine which have actual security metrics which are not compliant with the target security metrics managed by the product manager. In an embodiment of the invention the asset manager couples with a product manager, a work manager and an accounting manager to compare the actual costs of the new assets from the accounting manager and the work manager with the price of the assets from the product record.
Owner:IBM CORP
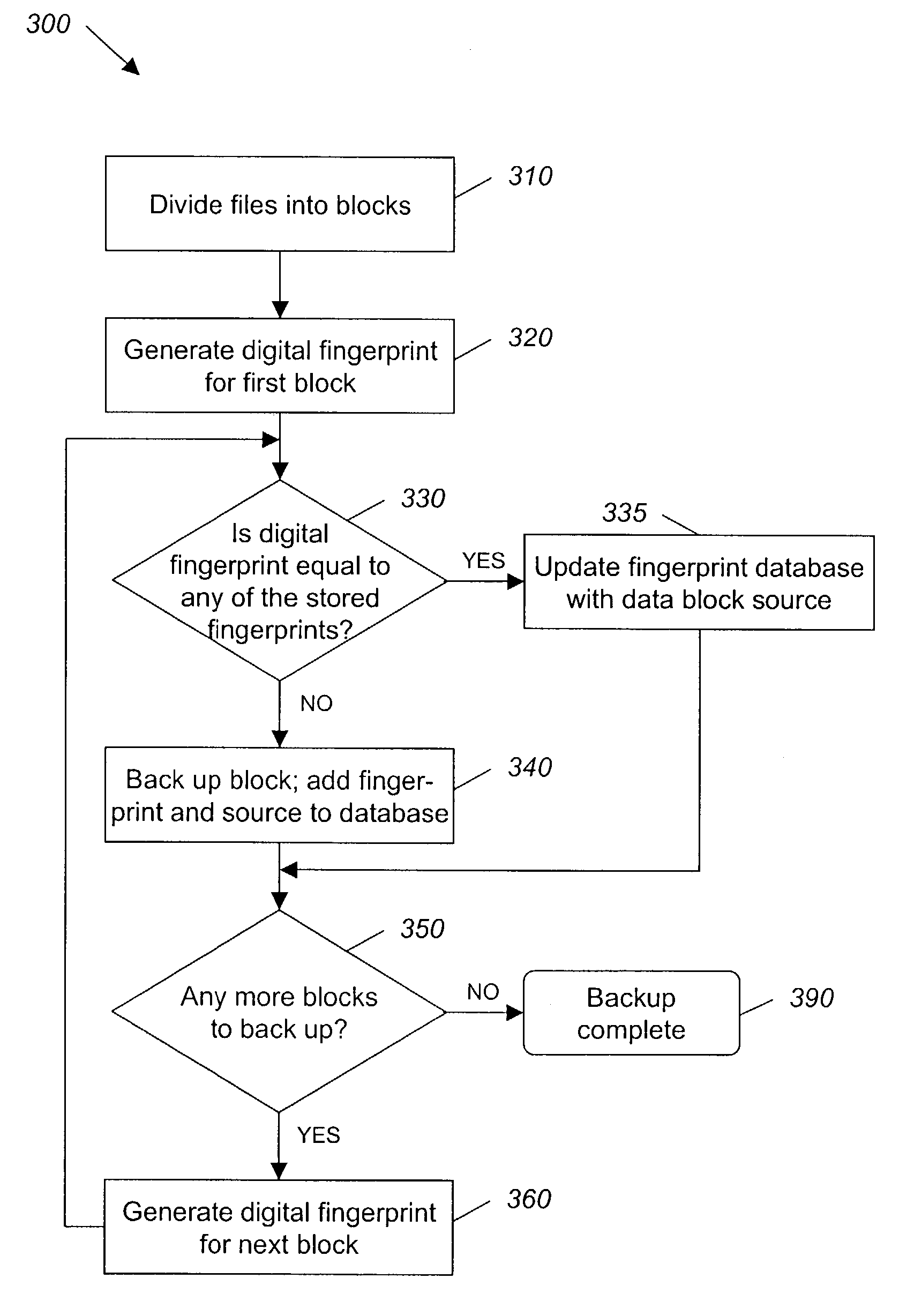
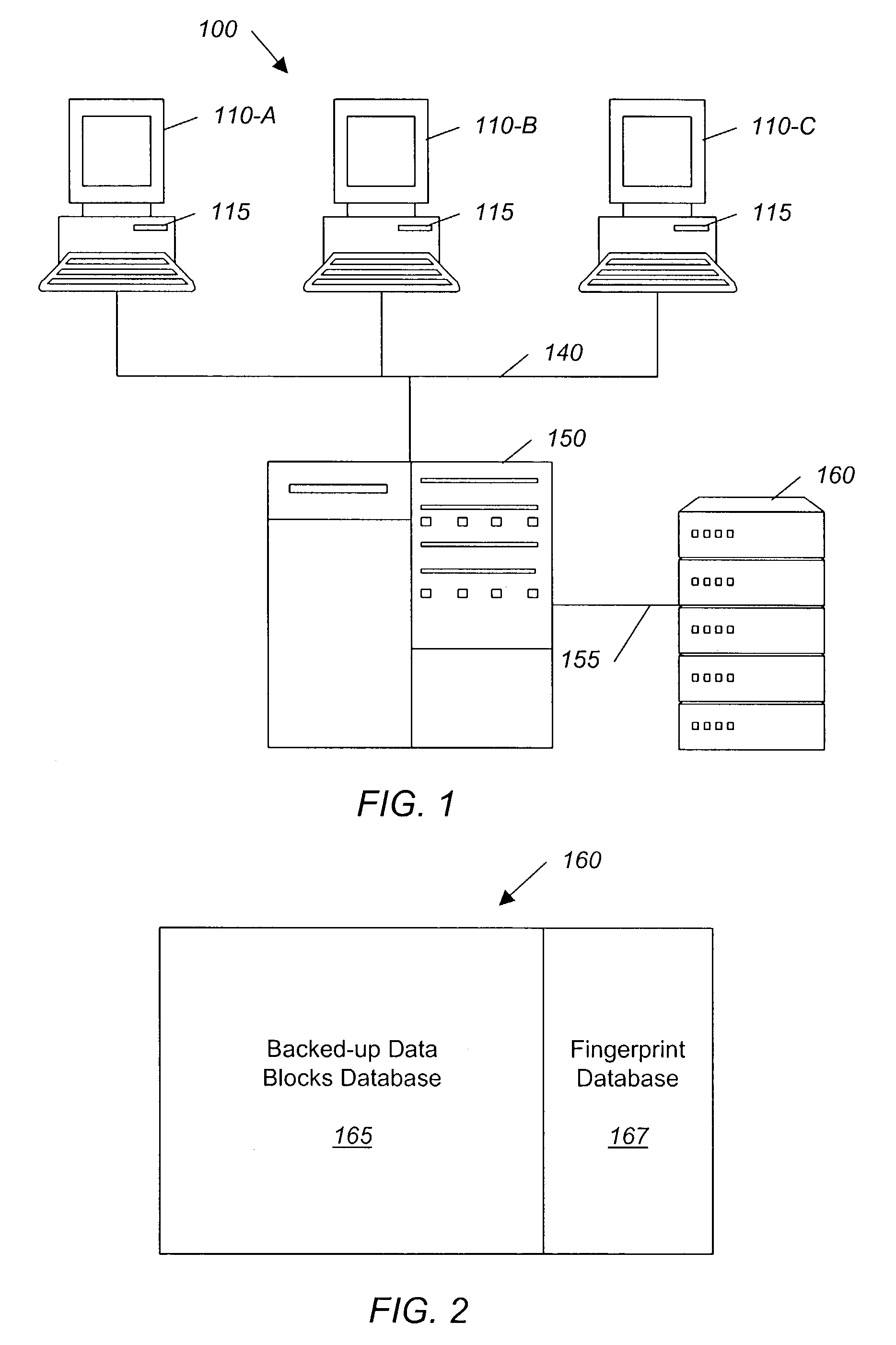
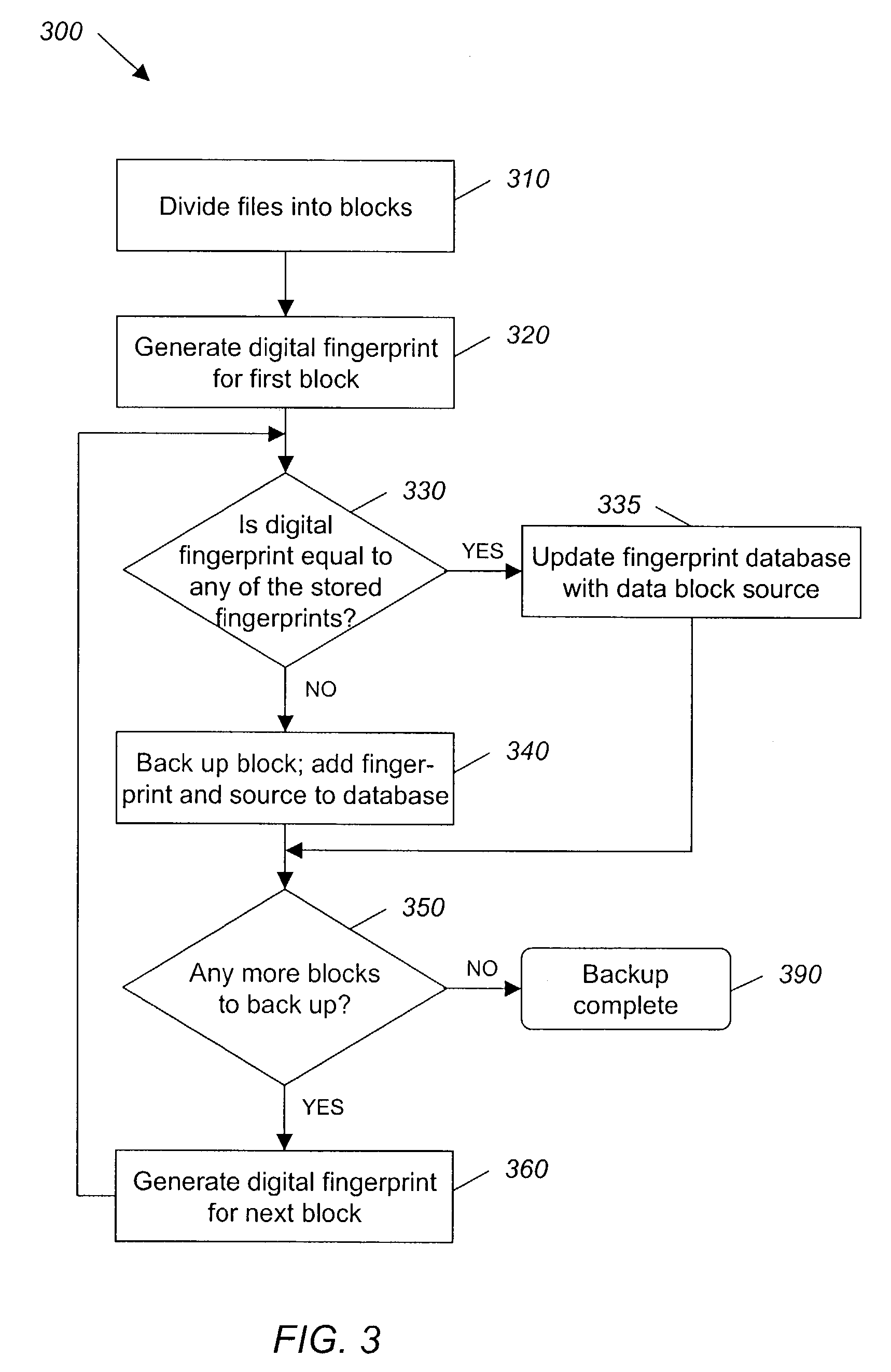
System and method for backing up data
ActiveUS7055008B2Avoid inefficiencyInefficiency of the Shnelvar patent can be avoidedCamera focusing arrangementPayment architectureSoftware licenseData content
A hash-optimized backup system and method takes data blocks and generates a probabilistically unique digital fingerprint of the content of each data block using a substantially collision-free algorithm. The process compares the generated fingerprint to a database of stored fingerprints and, if the generated fingerprint matches a stored fingerprint, the data block is determined to already have been backed up, and therefore does not need to be backed up again. Only if the generated fingerprint does not match a stored fingerprint is the data block backed up, at which point the generated fingerprint is added to the database of stored fingerprints. Because the algorithm is substantially collision-free, there is no need to compare actual data content if there is a hash-value match. The process can also be used to audit software license compliance, inventory software, and detect computer-file tampering such as viruses and malware.
Owner:FALCONSTOR
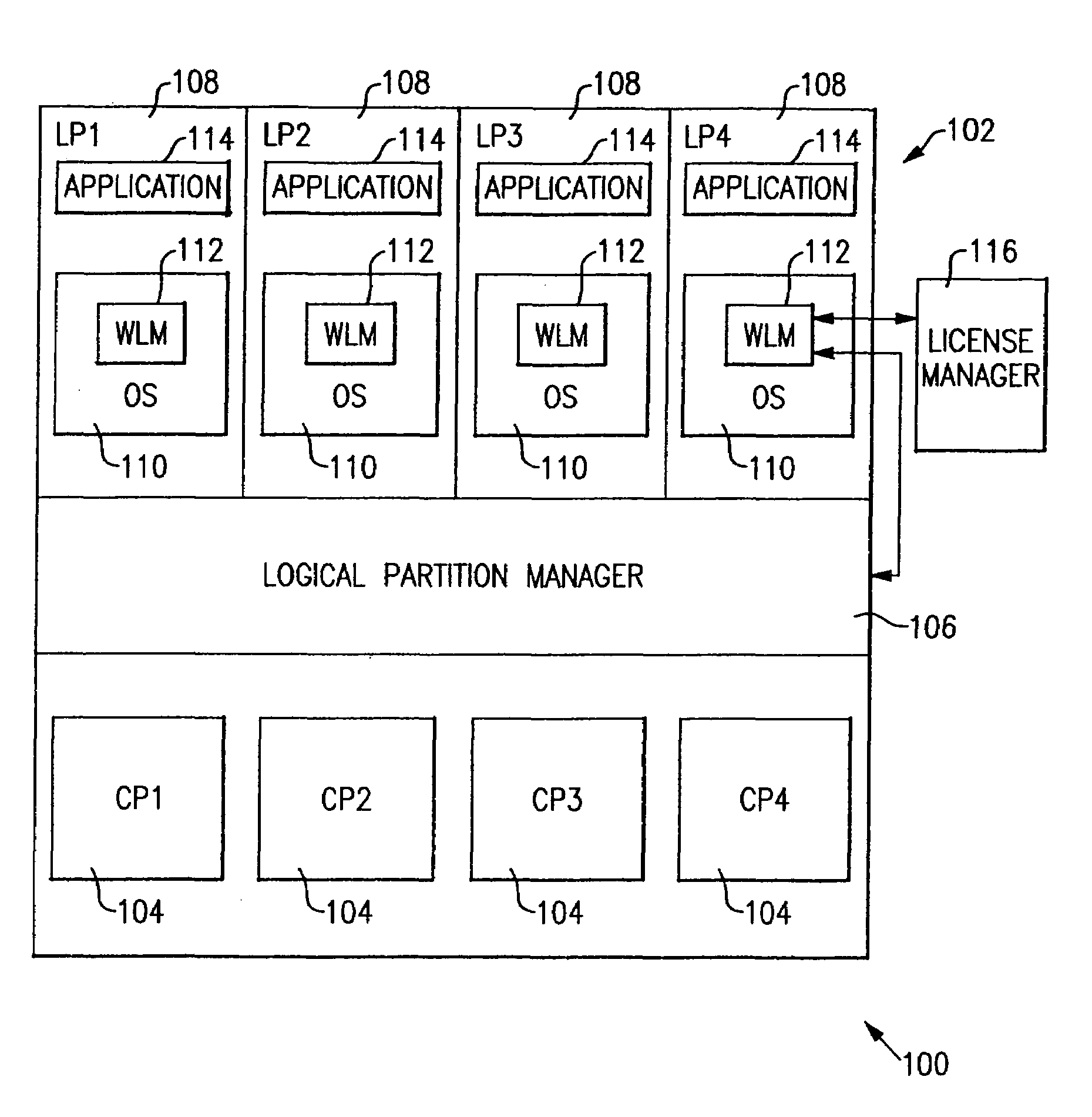
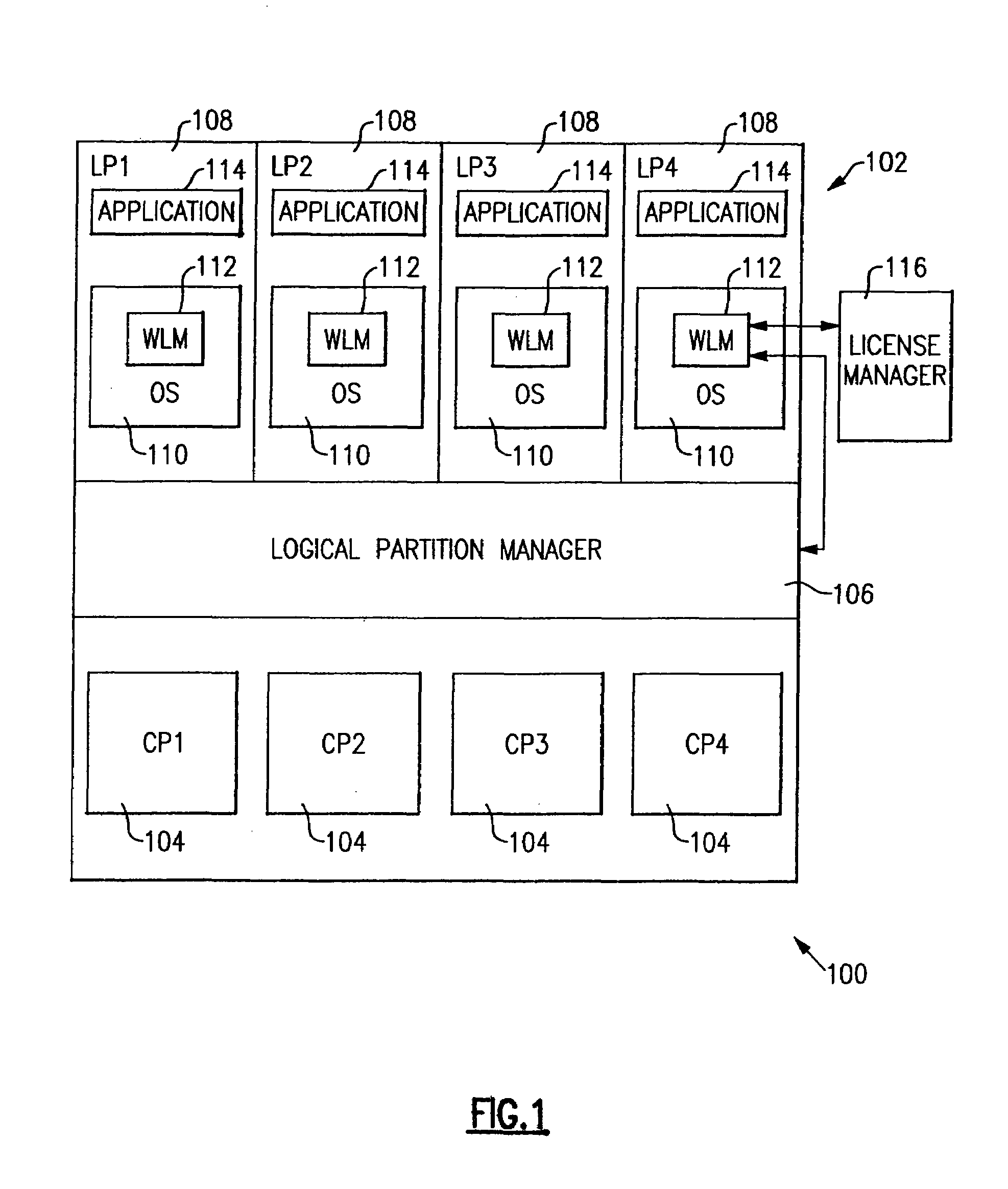
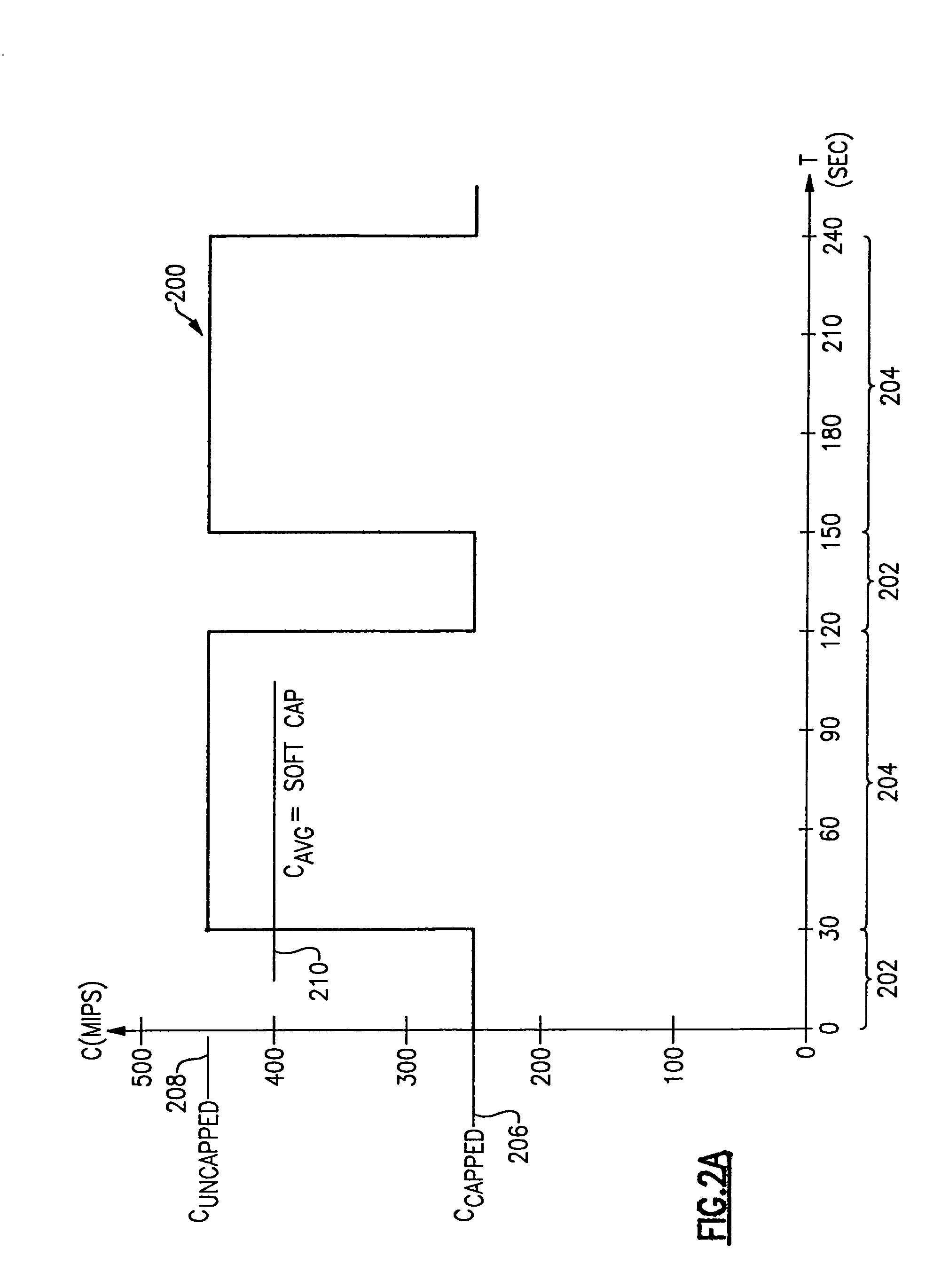
Method and apparatus for enforcing capacity limitations in a logically partitioned system
InactiveUS7096469B1Minimal costIncrease workloadResource allocationDigital computer detailsSoftware licenseHandling system
A method and apparatus for enforcing capacity limitations such as those imposed by software license agreements in an information handling system in which a physical machine is divided into a plurality of logical partitions, each of which is allocated a defined portion of processor resources by a logical partition manager. A software license manager specifies a maximum allowed consumption of processor resources by a program executing in one of the logical partitions. A workload manager also executing in the partition measures the actual consumption of processor resources by the logical partition over a specified averaging interval and compares it with the maximum allowed consumption. If the actual consumption exceeds the maximum allowed consumption, the workload manager calculates a capping pattern and interacts with the logical partition manager to cap the actual consumption of processor resources by the partition in accordance with the calculated capping pattern. To provide additional capping flexibility, partitions are assigned phantom weights that the logical partition manager adds to the total partition weight to determine whether the partition has exceeded its allowed share of processor resources for capping purposes. The logical partition thus becomes a “container” for the licensed program with an enforced processing capacity less than that of the entire machine.
Owner:IBM CORP
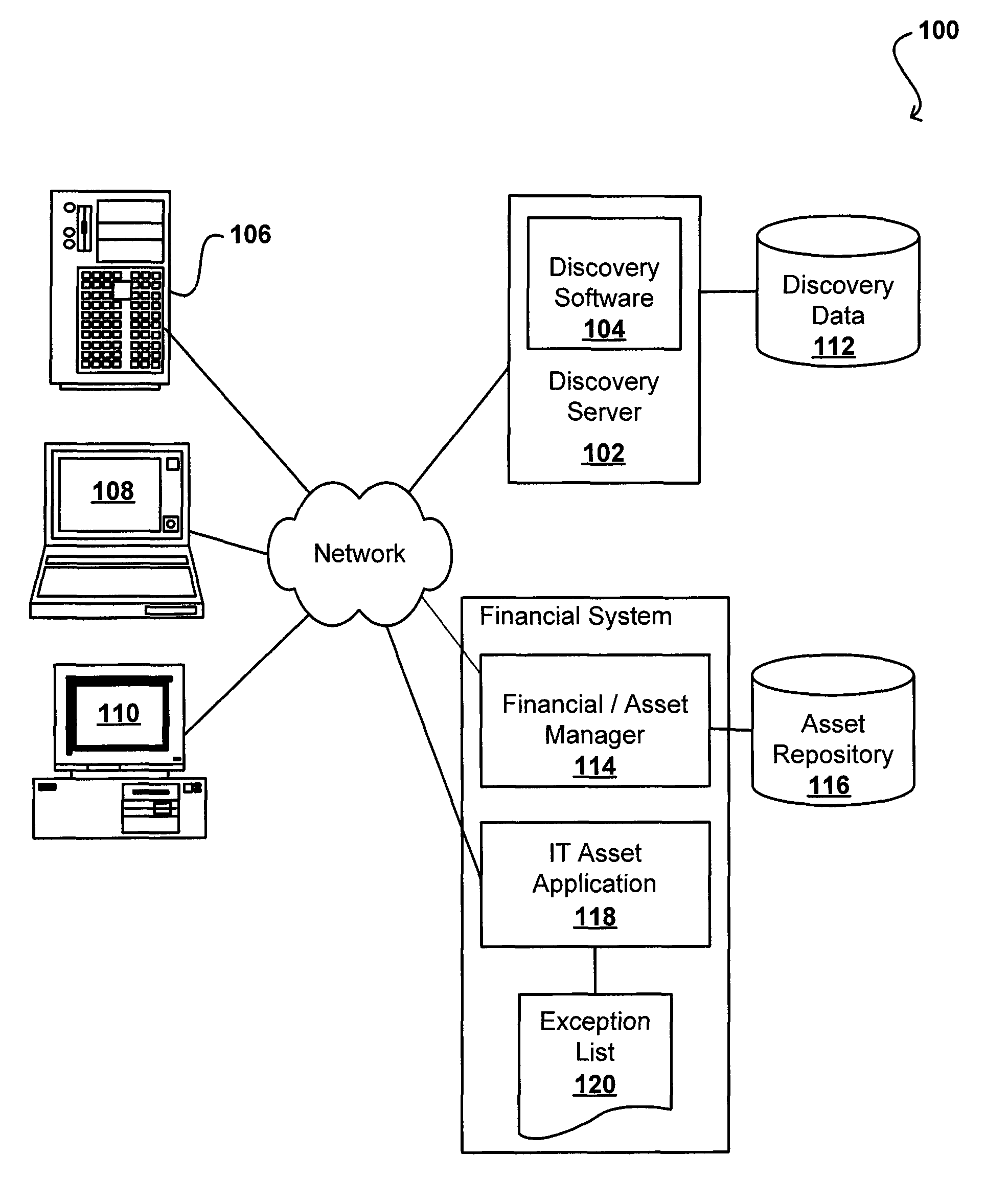
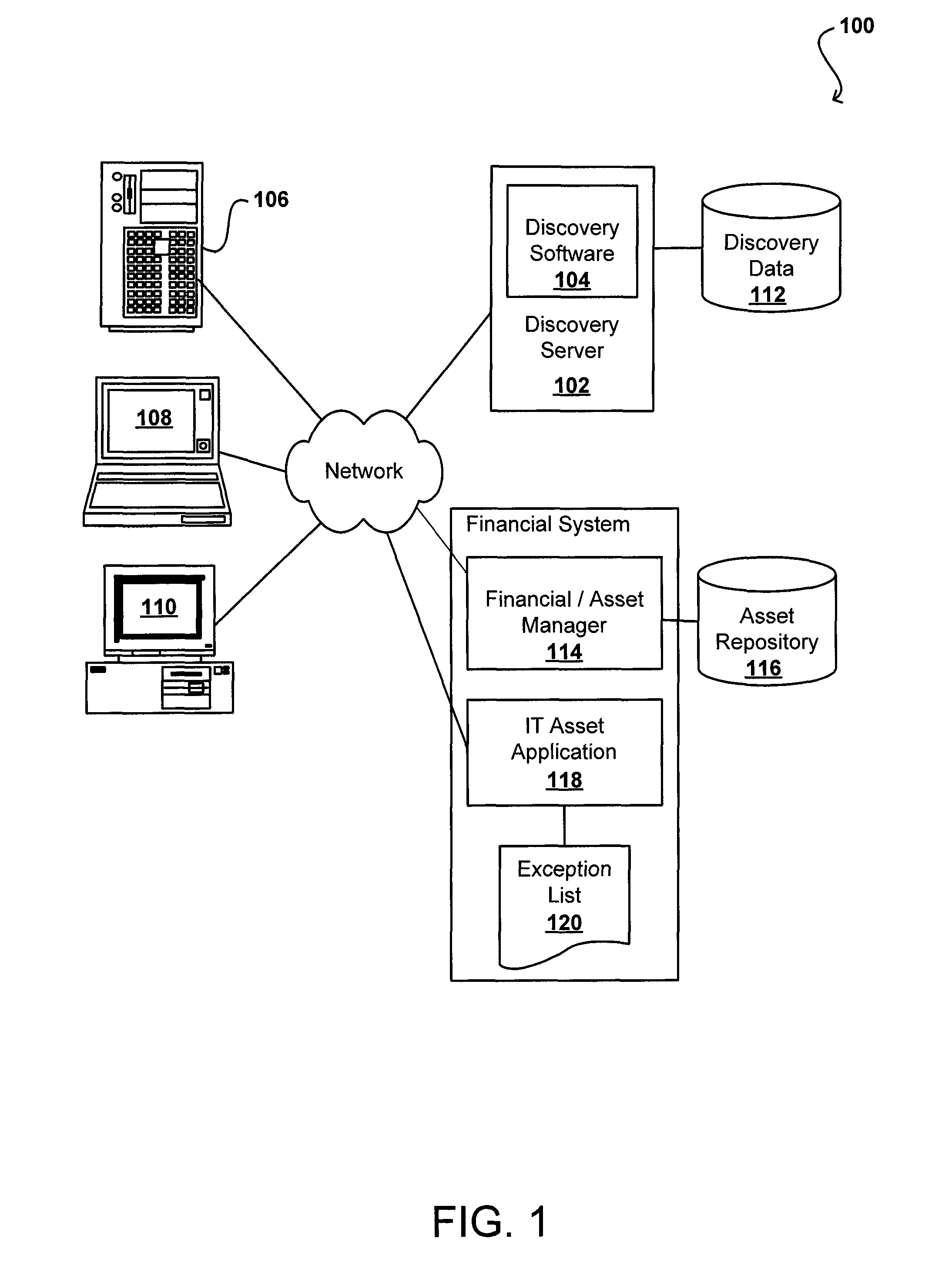
Web-based system for managing software assets
InactiveUS7197466B1Avoid litigationAvoid fineData processing applicationsComputer security arrangementsSoftware development processManagement process
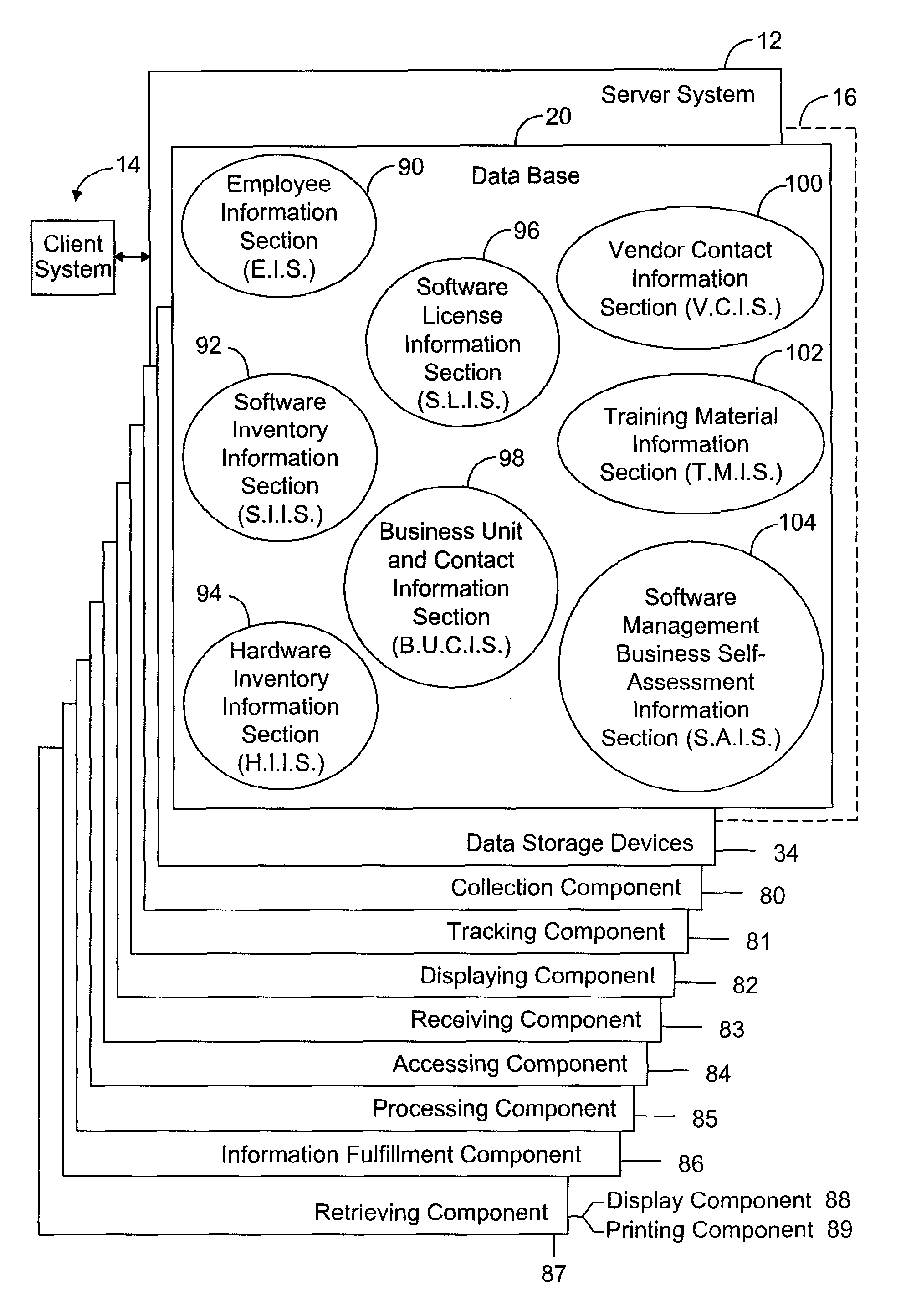
The disclosed invention is a software license management system (SLMS) utilizing a web-based interactive database to automate a software management process (SWMP) for managing software assets, measuring compliance requirements, and tracking / reporting status as necessary to assure proficiency and adherence to implementation requirements of the software management process. The SWMP is a process consisting of five different phases. The five steps of the SWMP involve identification of various solution alternatives, acquisition, deployment, maintenance and software retirement. The SWMP establishes high-level software management process to avoid litigation and penalties, maximize software asset utilization through tighter inventory control, and capitalize on the software procurement process.
Owner:GE CAPITAL US HLDG INC +1
On-demand active role-based software provisioning
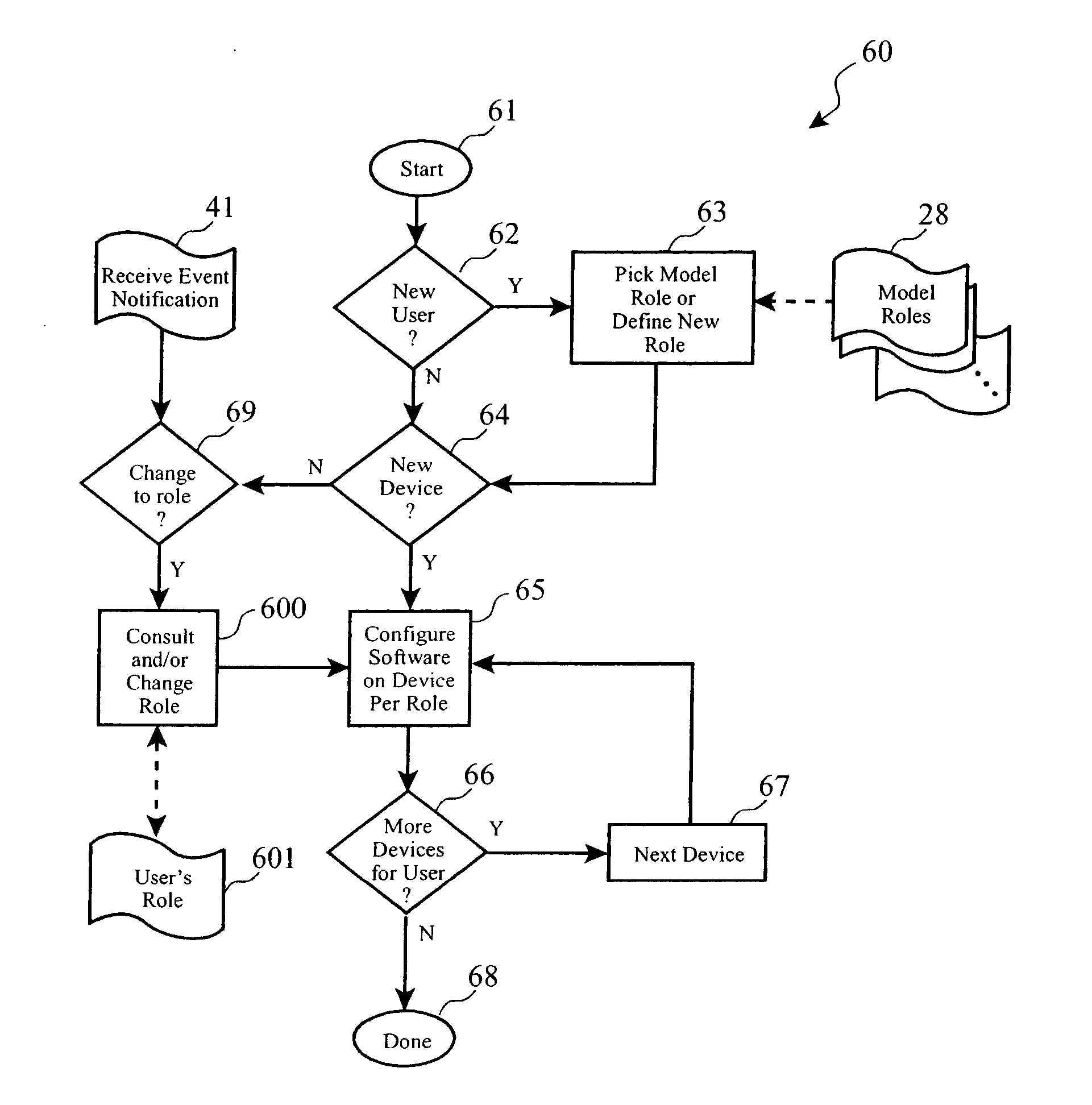
ActiveUS20050125509A1Avoid the needMultiple digital computer combinationsProgram loading/initiatingSoftware distributionSoftware license
Automated software provisioning based upon a set of role definitions for a user of a configurable device such as a computer or personal digital assistant. The present invention may be realized as an enhancement or extension to currently available software distribution tools which are used to distribute software to remote and local machines, and to permit unattended software installation and maintenance. The invention provides role-based software provisioning which automatically distributes the appropriate software programs and updates to computers that are owned by users based on the role of each user, thereby avoiding the need for intensive manual efforts to determine which computers need what software. The invention may also be interfaced to a License Management system in order to accomplish automatic recovery of unused software licenses, and to obtain permission for installing new licenses, based on user role changes.
Owner:DROPBOX
Method and apparatus for enforcement of software licence protection
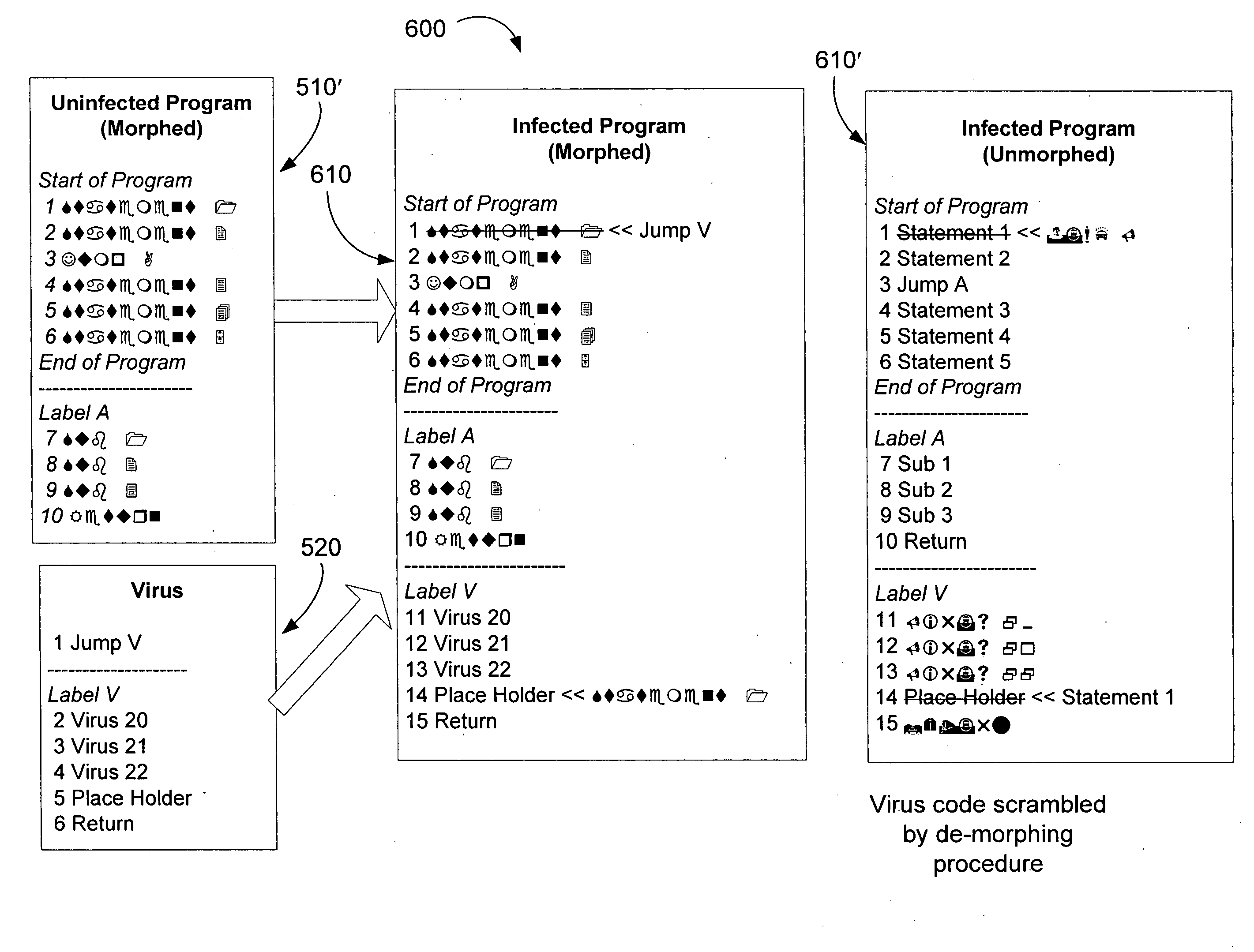
A method of enforcing software license protection in a computer system comprising; morphing the data prior to distribution, resulting in morphed data; wherein morphing of data is accomplished by applying a reversible morphing algorithm to modify data, wherein said reversible morphing algorithm is uniquely seeded and / or controlled with control information.
Owner:VALTRUS INNOVATIONS LTD +1
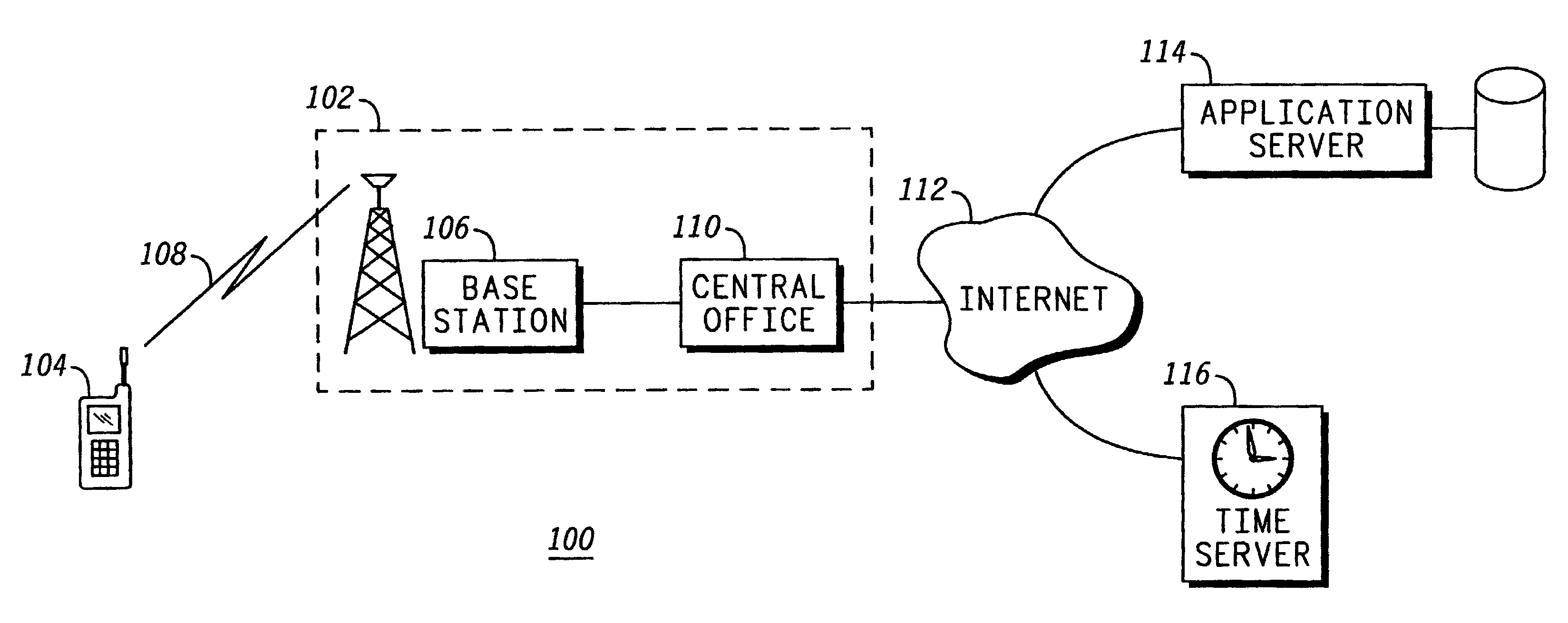
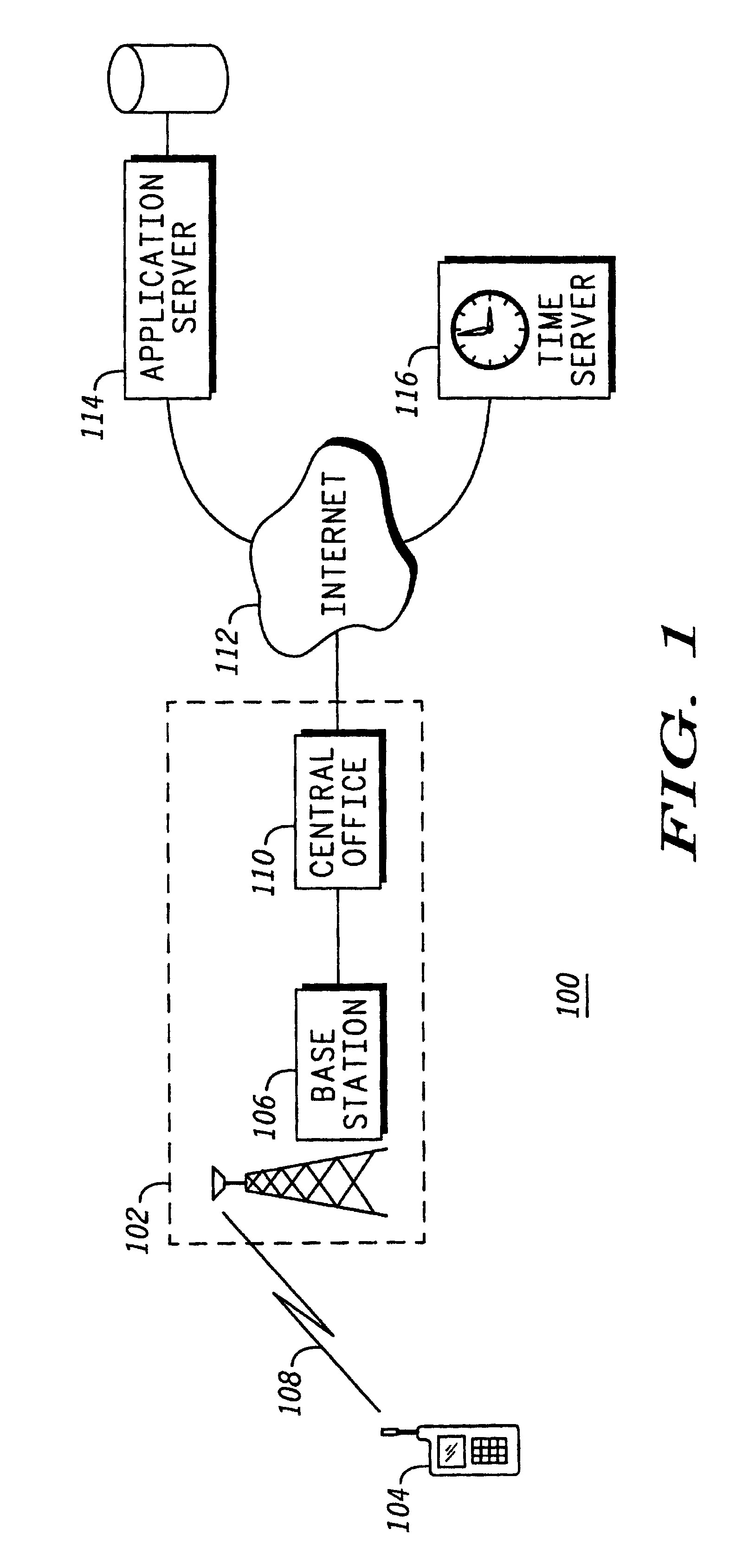
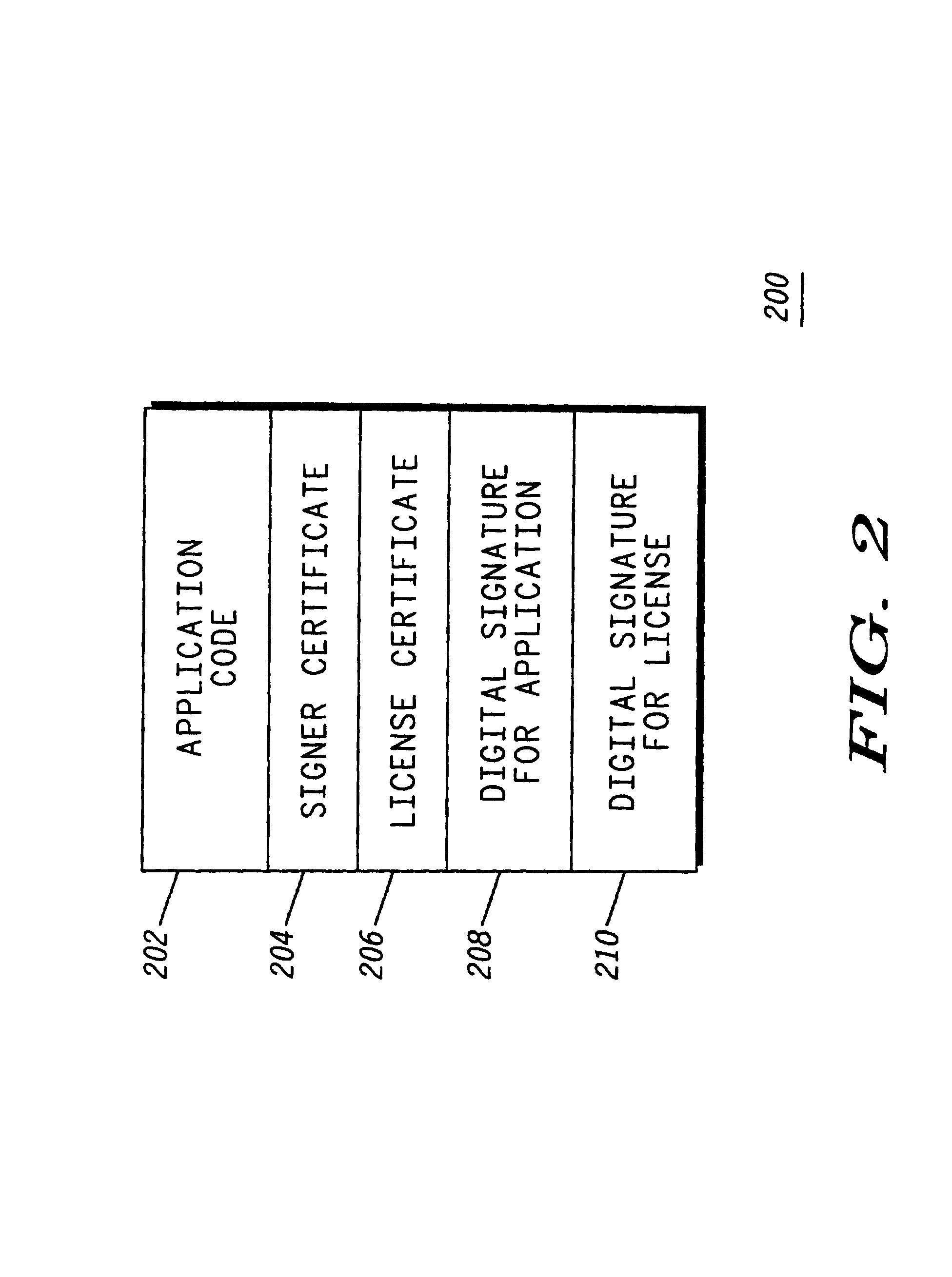
Method for enforcing a time limited software license in a mobile communication device
InactiveUS6889212B1Multiplex system selection arrangementsSpecial service provision for substationSoftware licenseApplication software
A mobile communication device (104) loads an application bundle (200), which includes a software application (202) and an indication of a time limited license (206). To enforce the time limited license, the mobile communication device, upon attempting to invoke the application code (310), obtains a secure time reading (312). It is contemplated that a secure time server (116) may be used to facilitate license enforcement. Once the secure time reading is obtained, the mobile communication device compares the time with the license period, and executes the code only if the time reading is within the license period.
Owner:GOOGLE TECH HLDG LLC
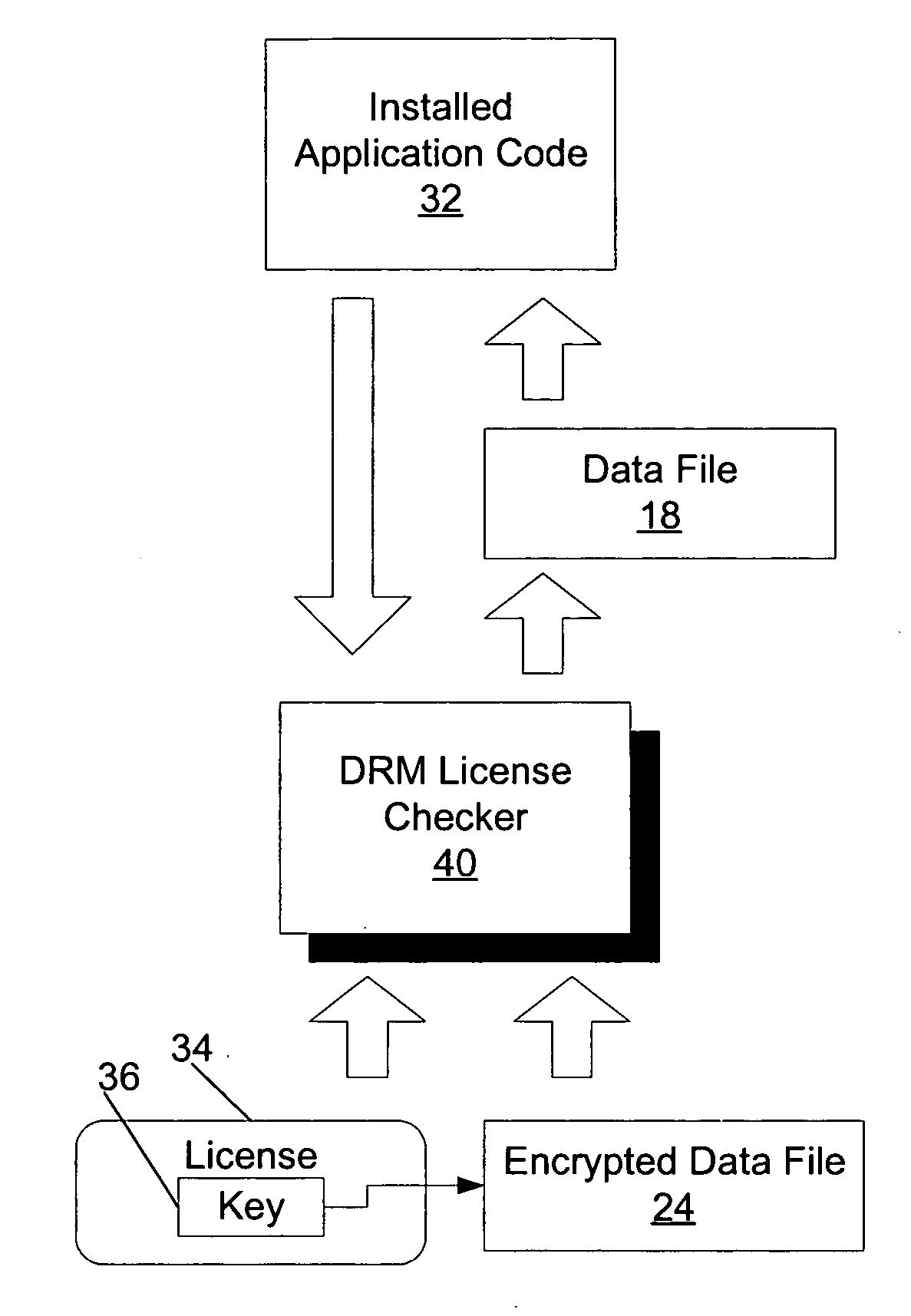
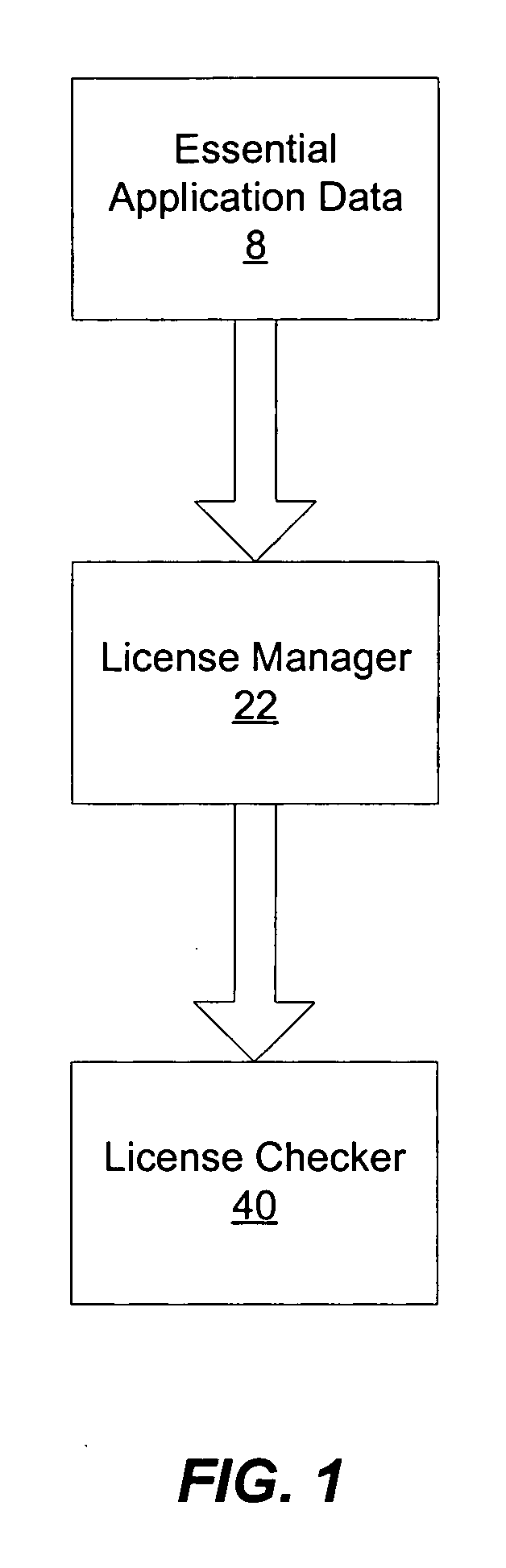
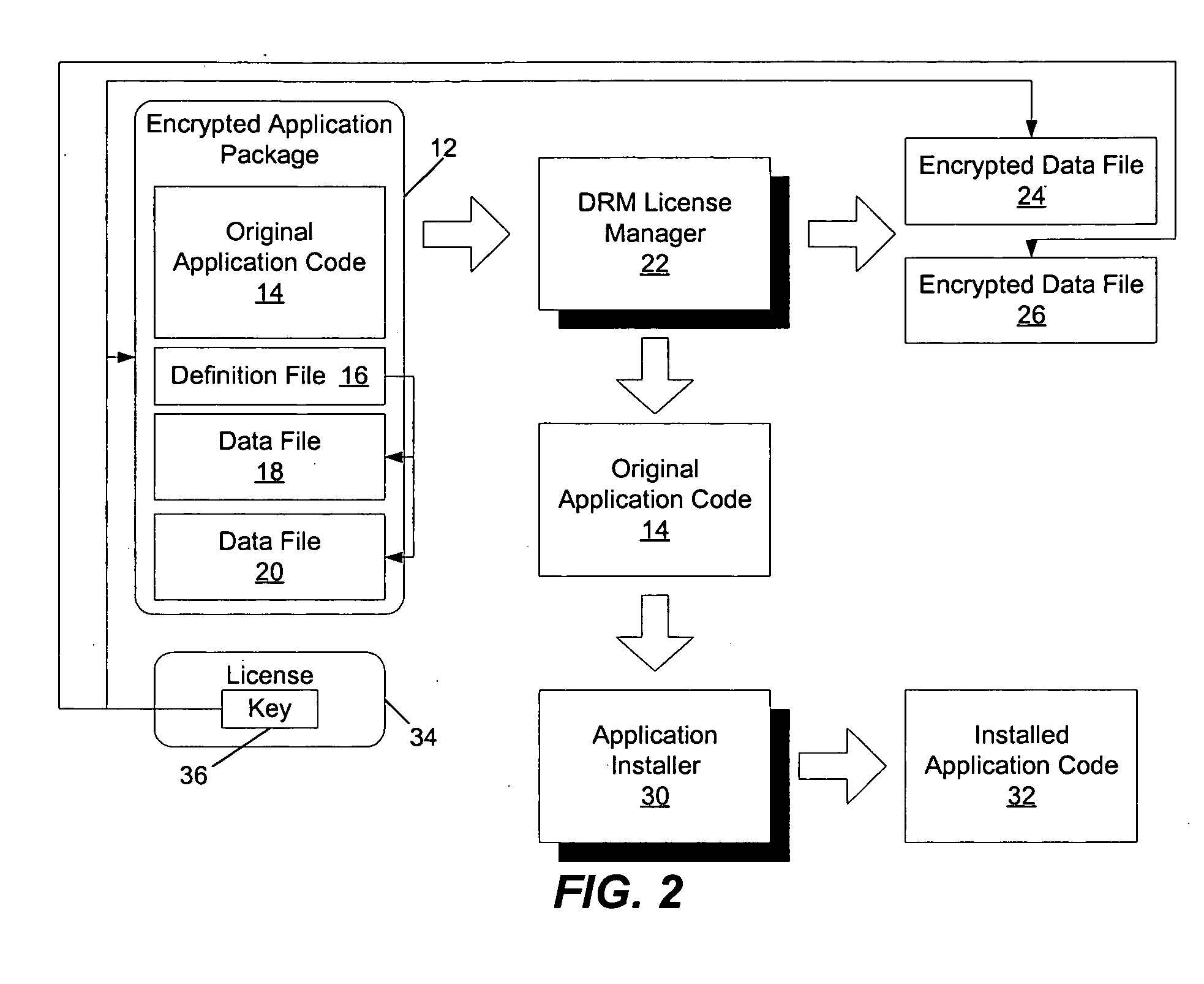
Digital rights management (DRM) license manager
ActiveUS20050278716A1Key distribution for secure communicationUnauthorized memory use protectionComputer hardwareSoftware license
A method, device, and system including a digital rights management (DRM) license manager to protect software applications from unauthorized use. The DRM license manager system binds essential application data to a software license. This binding is achieved by adding an encryption key to a software license and encrypting the application data with that key. The essential application data is any kind of data which is required for proper operation of the program, such as media files, game levels or state tables. The DRM license manager system performs a check and decrypt operation of the essential application data during program run time. It requires that the license is available on the system. It also ensures that the decryption operation can only take place if the conditions defined in the license are met.
Owner:NOKIA TECHNOLOGLES OY
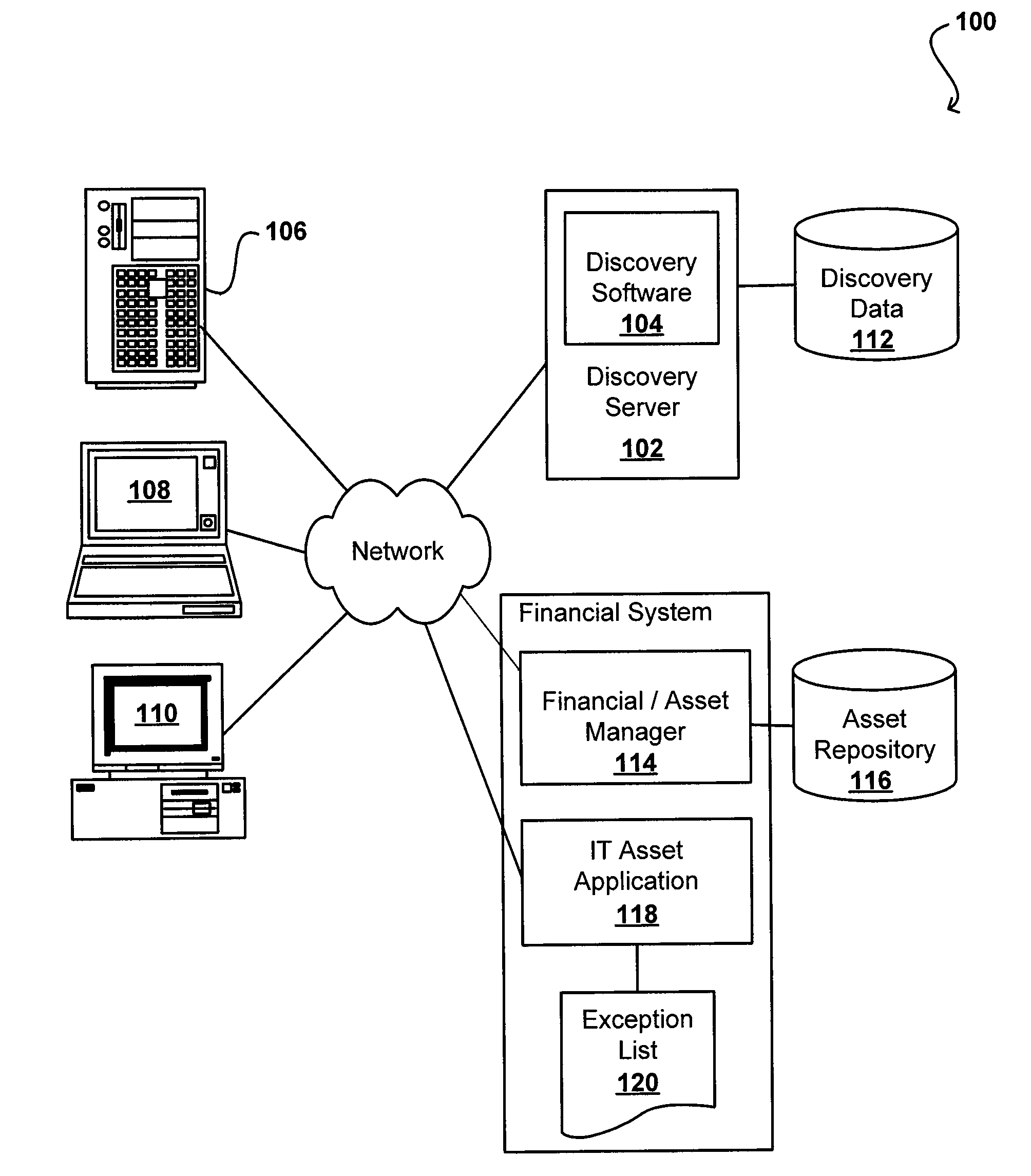
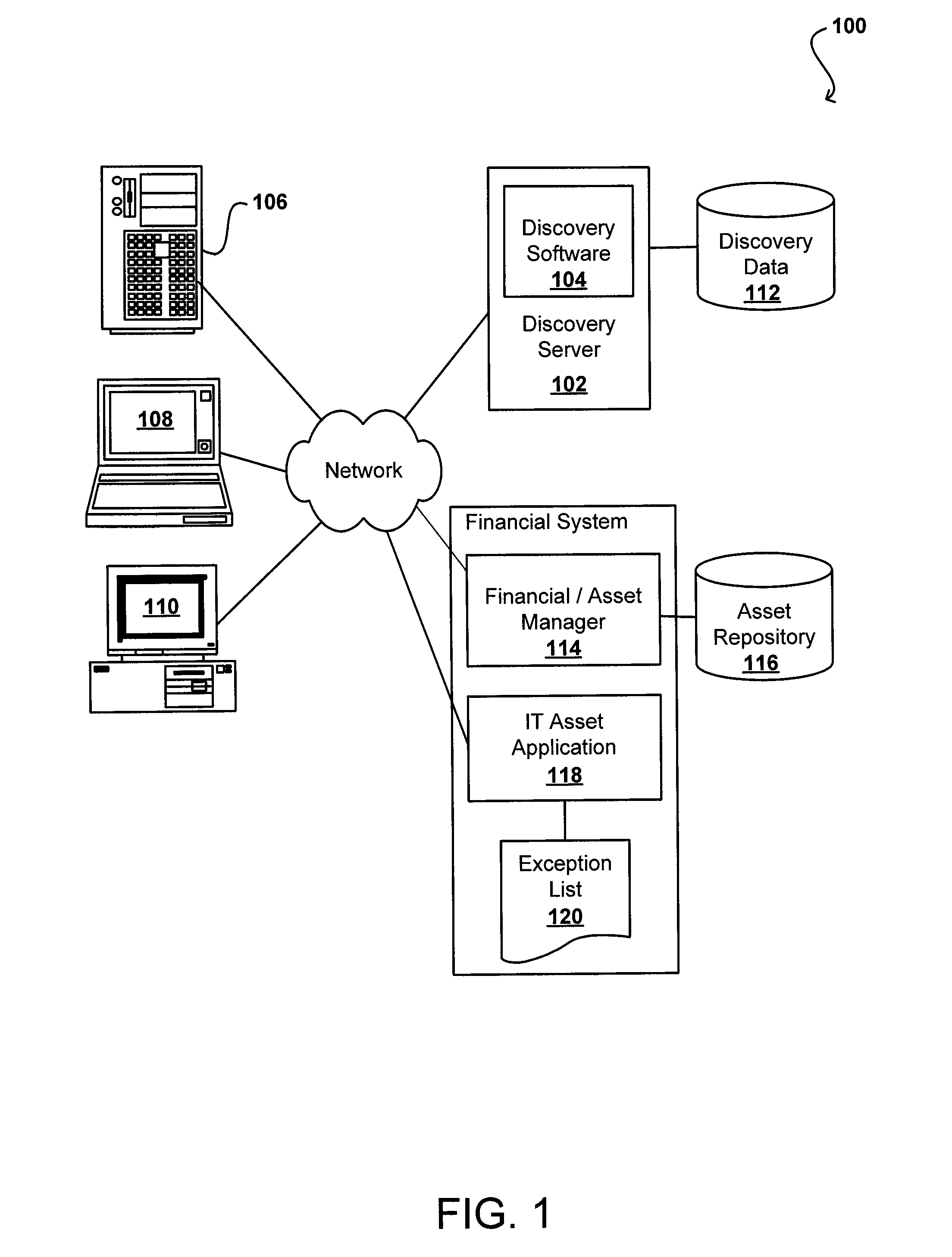
Device based software authorizations for software asset management
ActiveUS8407669B2Easy and automatic determinationOffice automationResourcesSoftware asset managementSoftware license
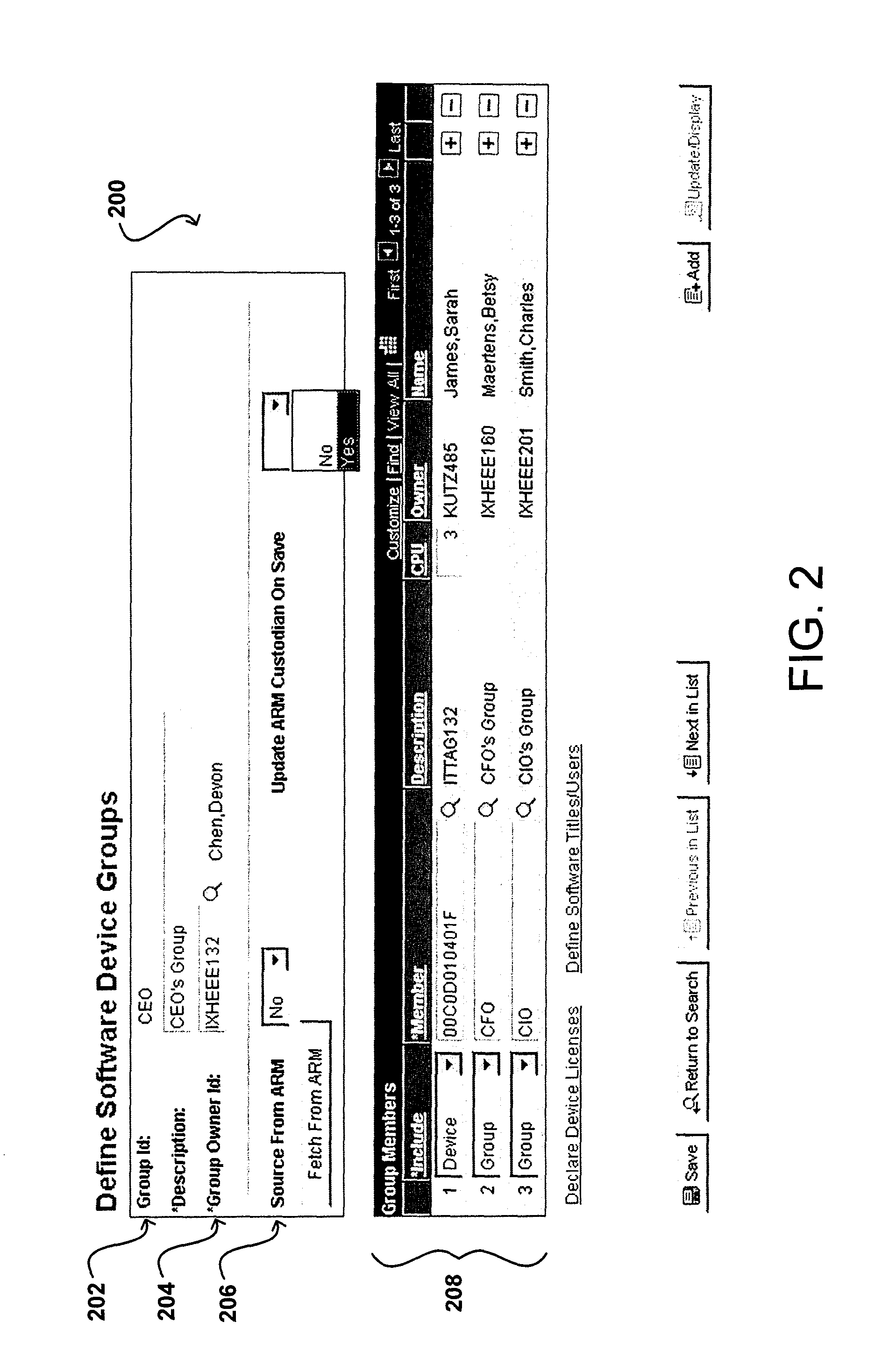
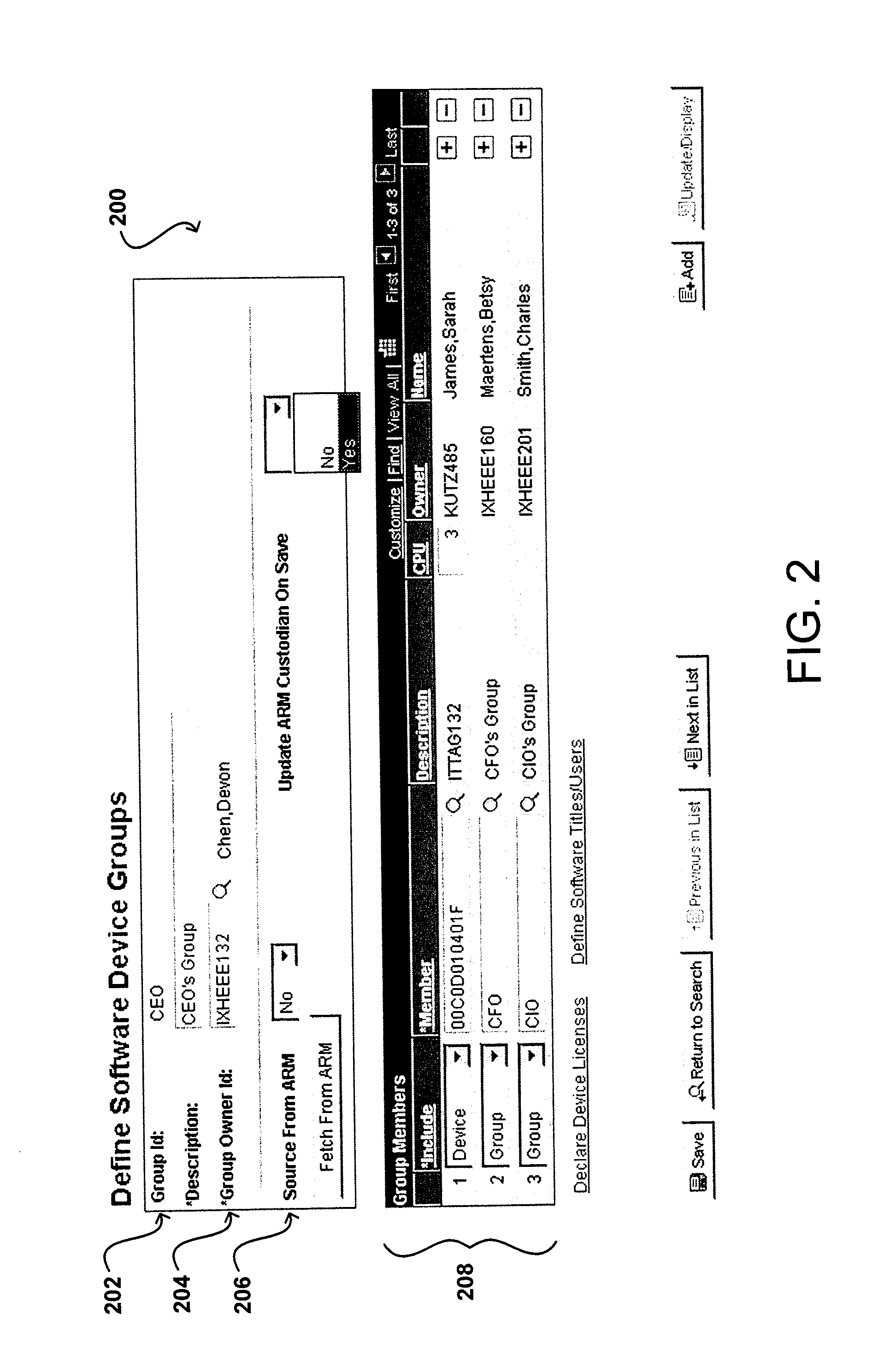
Software device groups allow owners and administrators to be defined for various intelligent devices, instead of tracking by primary user. A software license compliance management system obtains discovery information for these devices to determine software installed or active on these devices. The management system also obtains the number of licenses for each software package and determines whether the software is in compliance, or if the number of instances exceeds the number of licenses. This determination is flexible and can handle various license types, such as per user, per device, and per processor. For any exception, the group owner is informed and then can re-allocate licenses, purchase additional licenses, or request the uninstalling of a software instance(s). Device groups also can include sub-groups with sub-group owners responsible for handling any exception in that sub-group.
Owner:ORACLE INT CORP
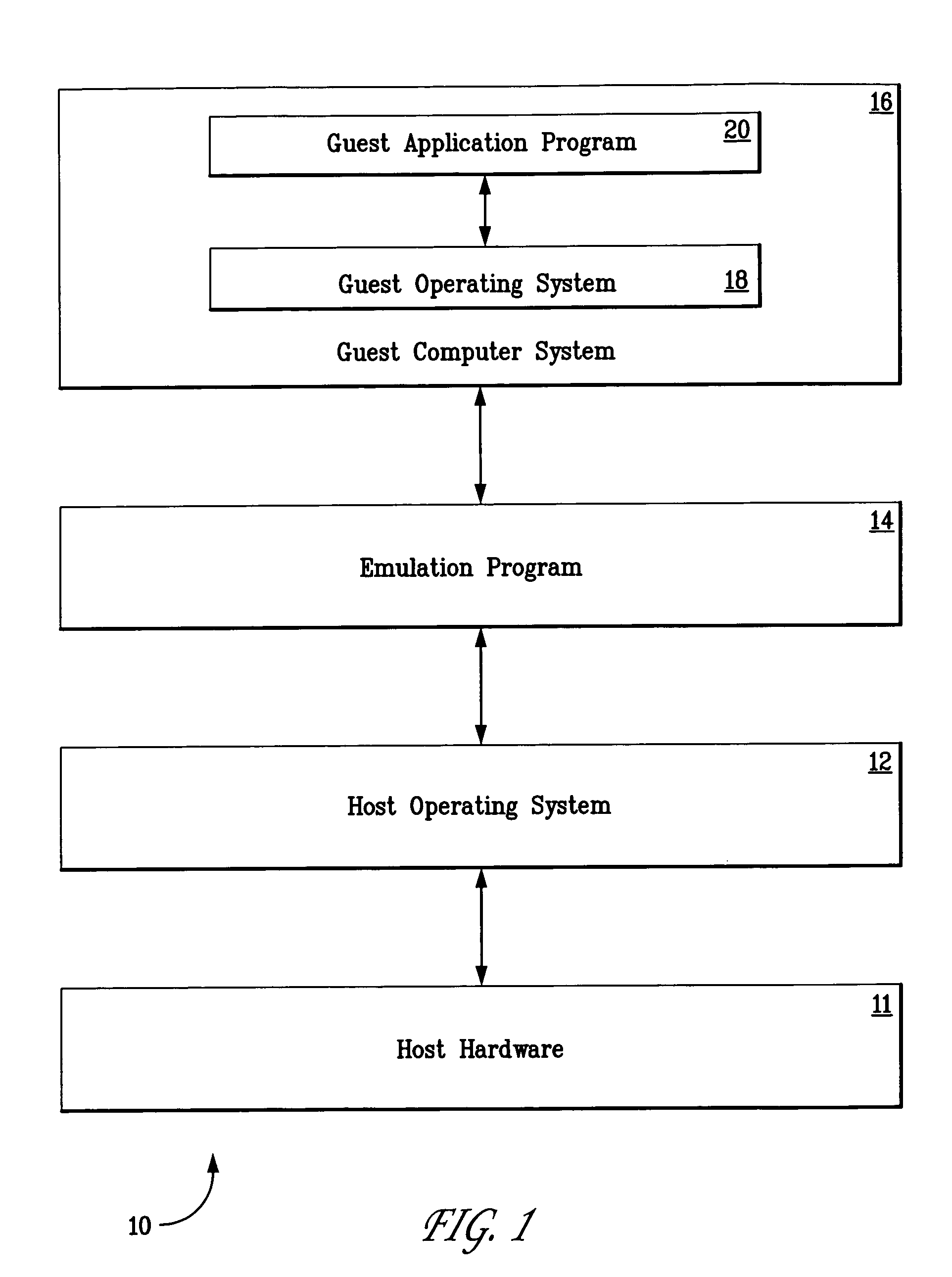
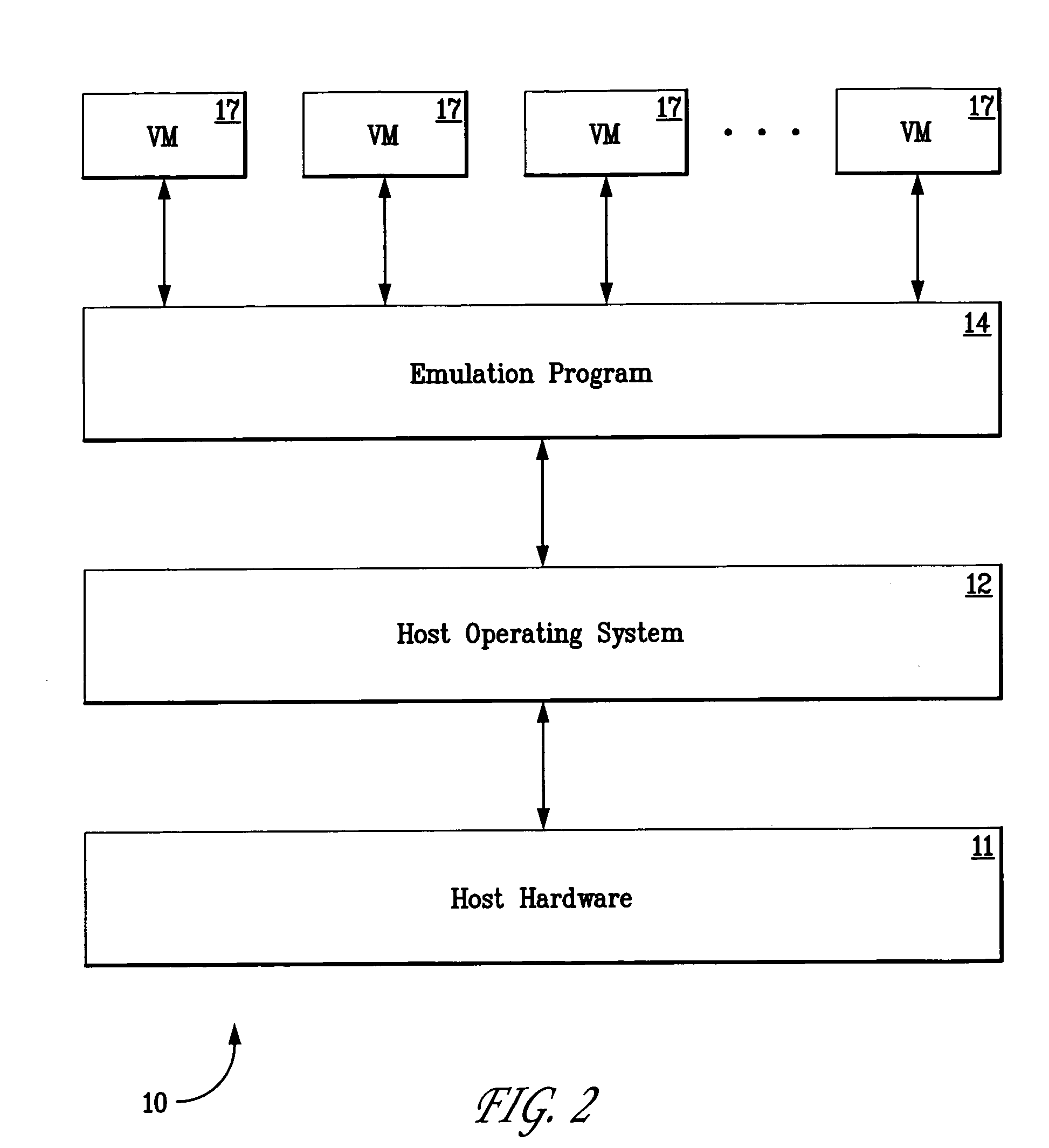
Systems and methods for collecting operating system license revenue using an emulated computing environment
InactiveUS20060004667A1Simple methodProvide supportData processing applicationsProgram/content distribution protectionVirtualizationOperational system
Several embodiments of the present invention provide means for collecting license revenue for operating systems or applications software that resides in a virtualized computer system. Certain of these embodiments are specifically directed to providing a means for collecting license revenue for modern or legacy operating systems or applications in a virtual machine environment and further provide an ongoing revenue stream, rather than a one-time transaction, for a software manufacturer. More specifically, certain embodiments are directed to a system for and method of providing software license enforcement by using a license manager in a virtual machine environment and thereby provide improved methods of collecting license revenue in a computer system that supports legacy operating systems and applications. Finally, several embodiments of the present invention are directed to providing incremental software support and upgrades for operating systems and applications that run in a virtual machine environment.
Owner:MICROSOFT TECH LICENSING LLC
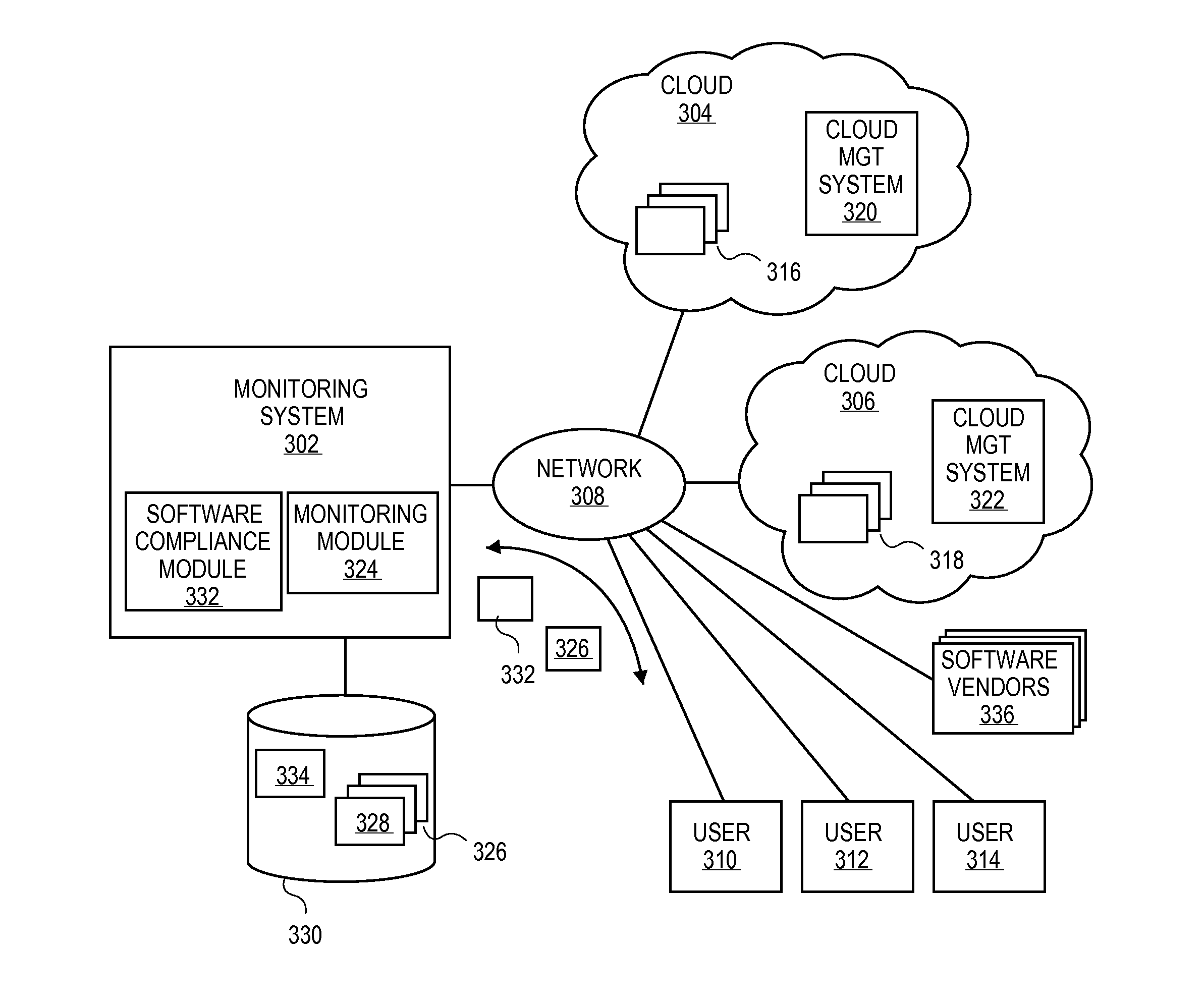
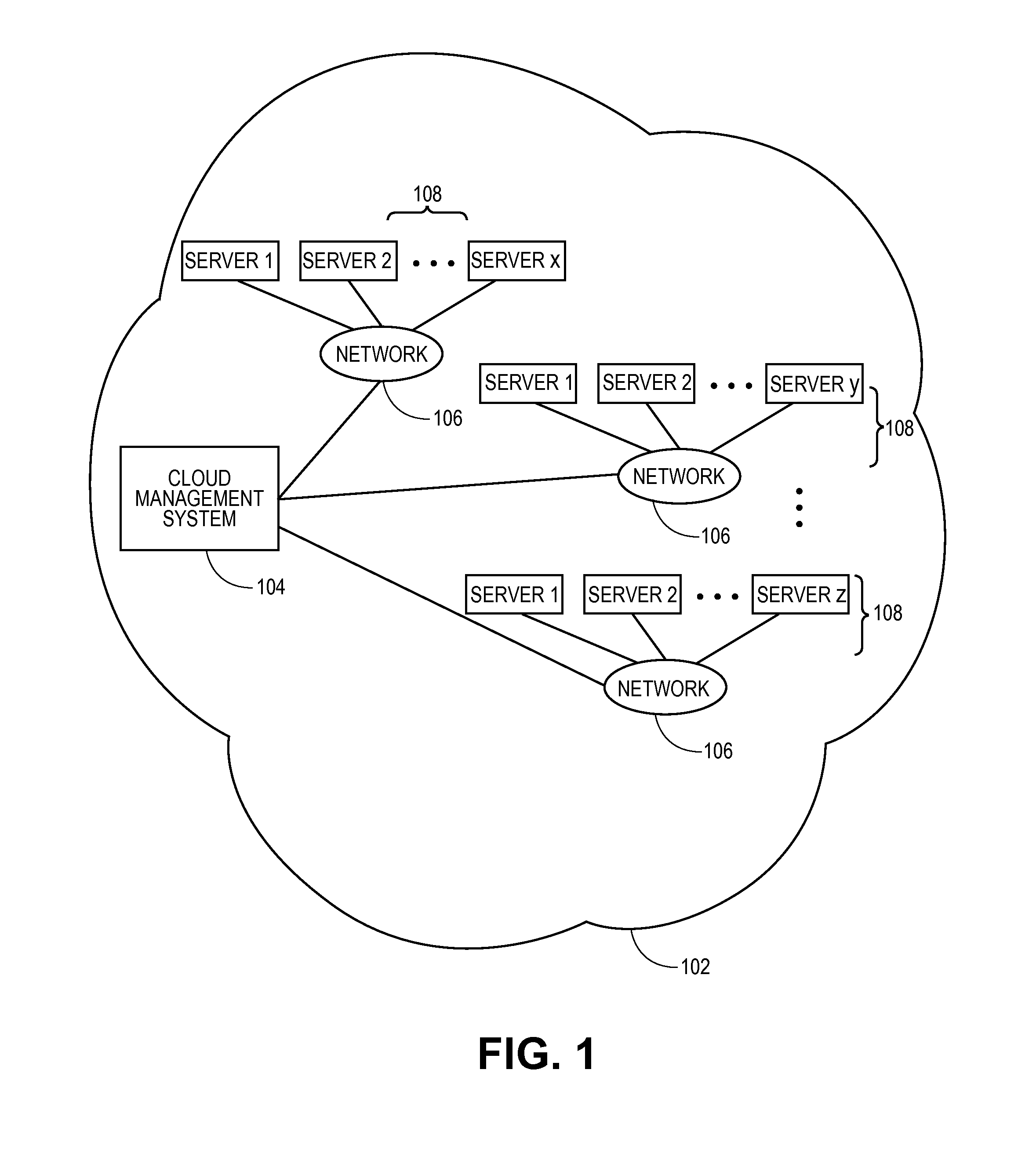
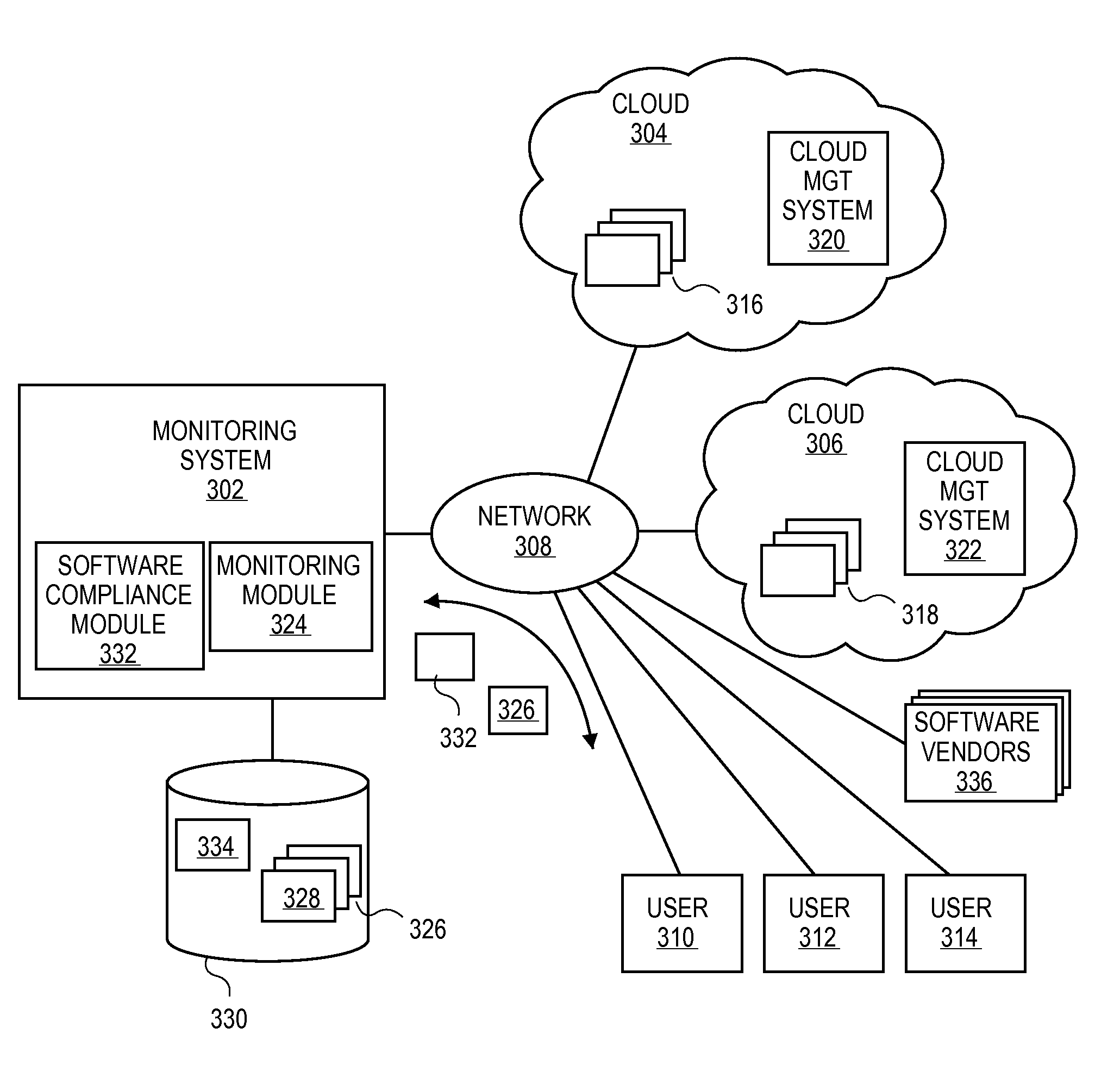
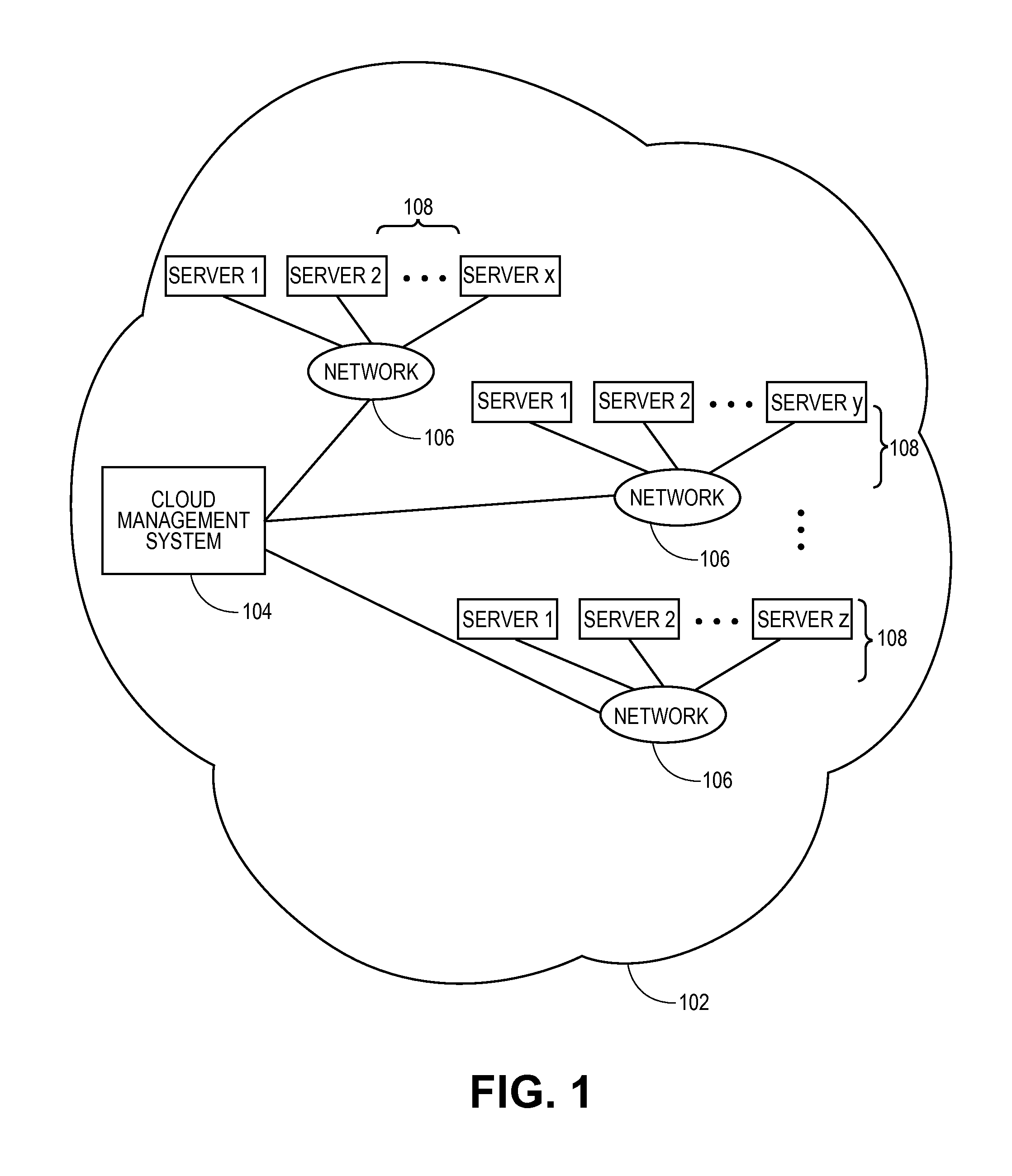
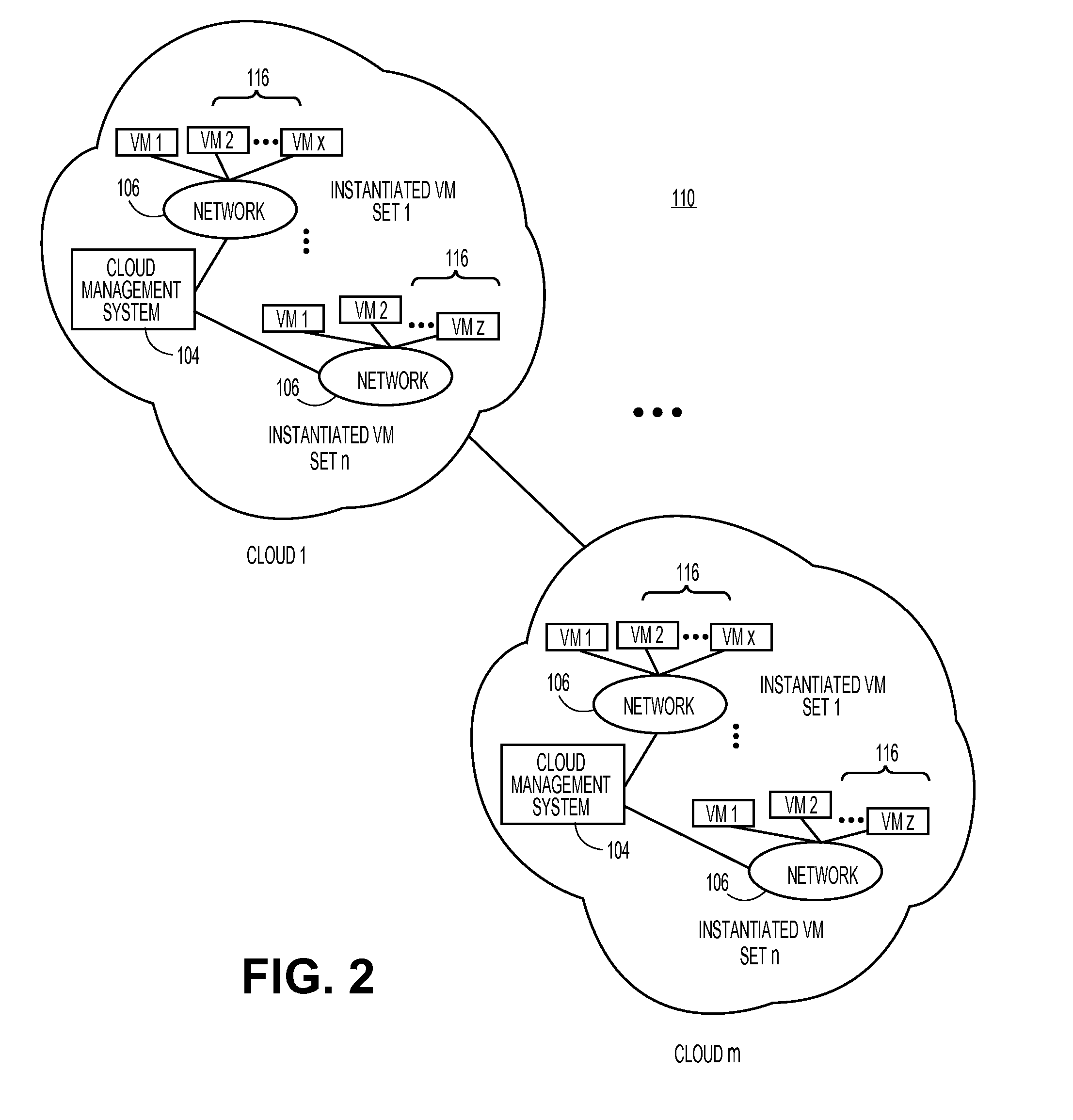
Methods and systems for verifying software license compliance in cloud computing environments
ActiveUS20110131315A1Digital computer detailsComputer security arrangementsSoftware licenseMonitoring system
A monitoring system can monitor computing processes in clouds. The monitoring system can verify software license compliance in the computing processes instantiated in the clouds. The monitoring system can generate and maintain a software license knowledge base. The software license knowledge base can include the software license requirements for various software programs. To verify software license compliance, the monitoring system can determine the software programs utilized by the computing processes instantiated in the clouds. The monitoring system can compare the software programs utilized by the computing processes to the software license knowledge base to determine the number of software licenses required by the computing processes. The monitoring system can compare the number of software licenses required to the number of software licenses currently held by the user to determine if the user is in compliance.
Owner:RED HAT
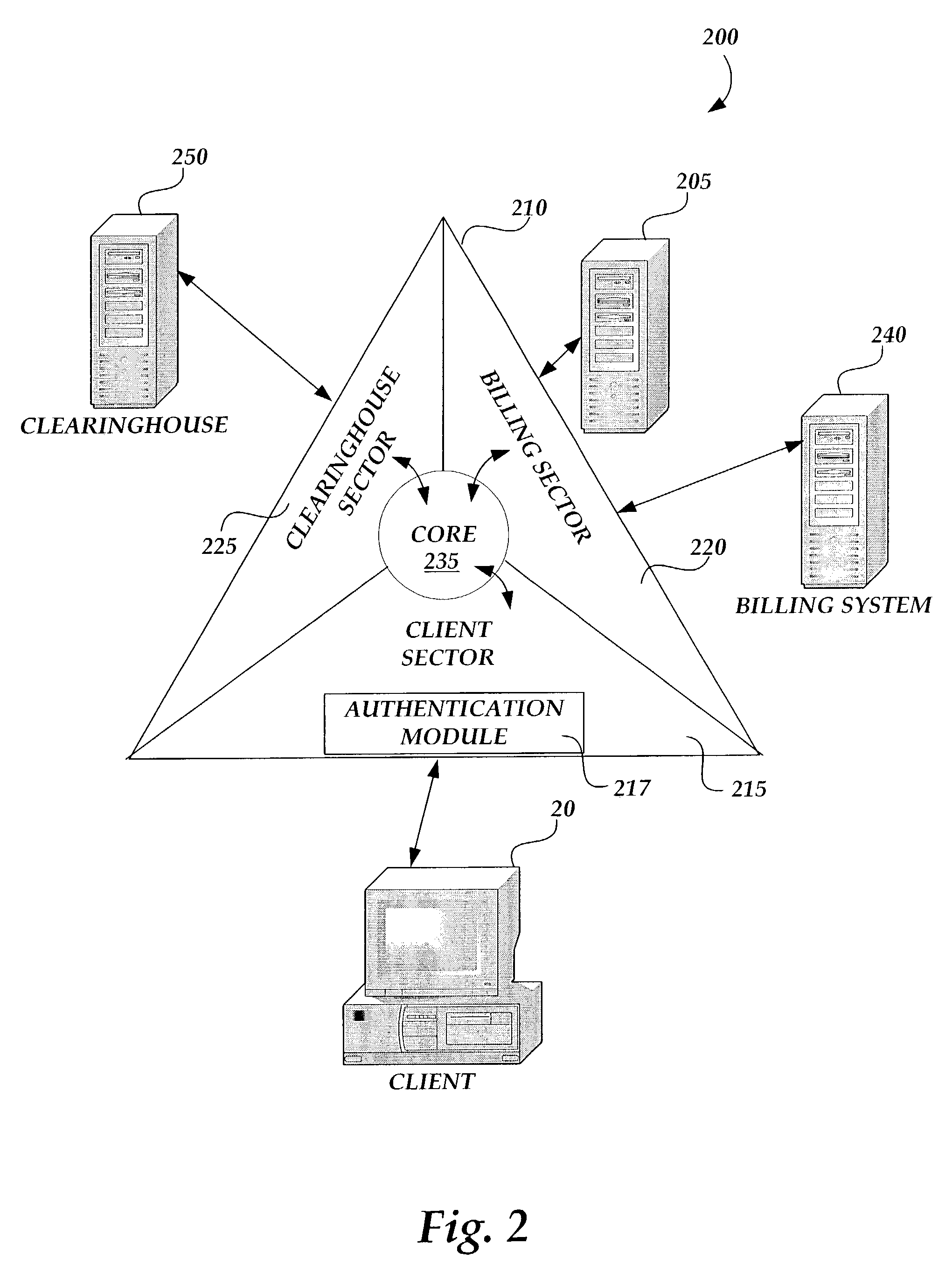
Computer software and services license processing method and system
InactiveUS7346585B1Improve and streamline abilityDigital data processing detailsAnalogue secracy/subscription systemsSoftware licenseSoftware engineering
Integrated computer services and software licensing processing methods and systems are provided. A license processing service (LPS) receives a services or software license request from a user via a client computer. The LPS communicates the request to a billing system for the services or software provider to obtain an expiration date for use of a desired service or software product. The LPS receives and forwards the expiration date from the billing system to a licensing clearinghouse operated by the provider of the desired service or software product. The clearinghouse, in turn, provides a use license for the desired service or software application to the client computer via the LPS.
Owner:MICROSOFT TECH LICENSING LLC
Method and apparatus for technology resource management
InactiveUS7660731B2Multiprogramming arrangementsResourcesService-level agreementHuman resource management
Apparatus and methods to manage demand, service level agreements, hardware and software assets, projects, labor, knowledge and provisioning resources in hosted applications. An asset manager coupled to host servers and a network, manages the host servers and software to determine the demand for new assets and allocate available assets to meet the demand; determine assets not in compliance with existing software licenses; determine and compare actual service level metrics with the target service level metrics; and determine availability of a patch or upgrade for selected software and instances of the selected software among the assets. The asset manager may be coupled to other managers, e.g., contract, product, work and / or accounting managers, to monitor service level metrics and / or costs.
Owner:IBM CORP
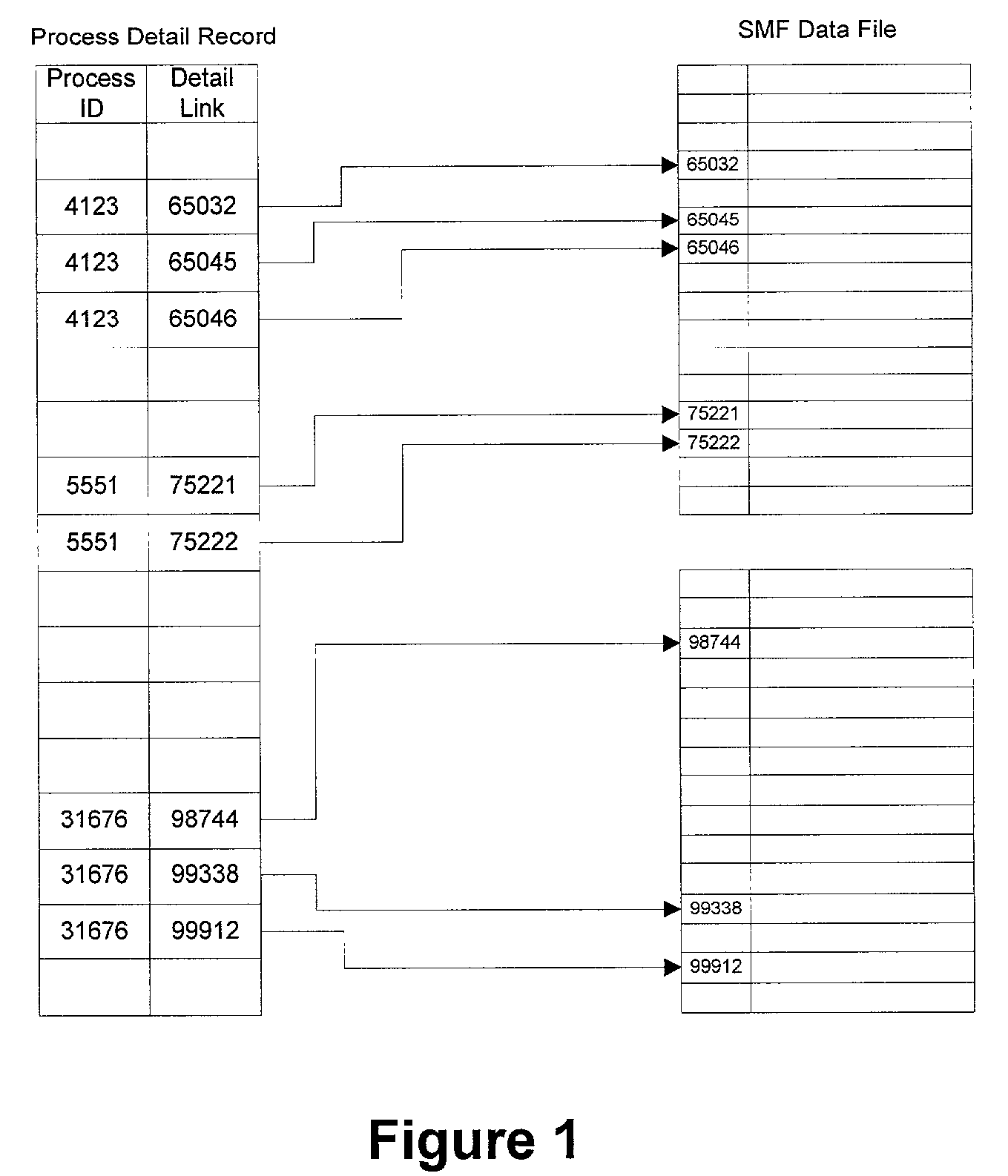
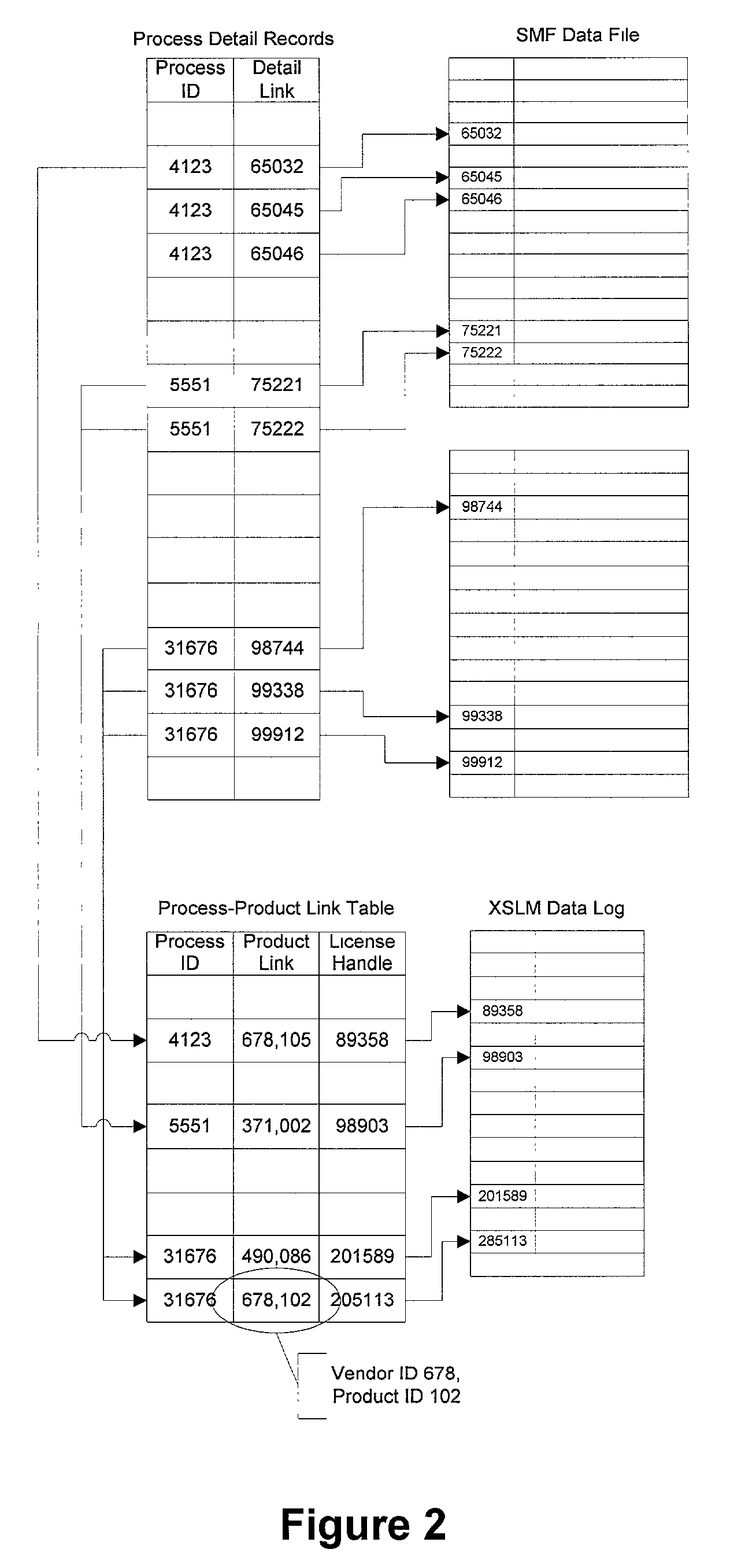
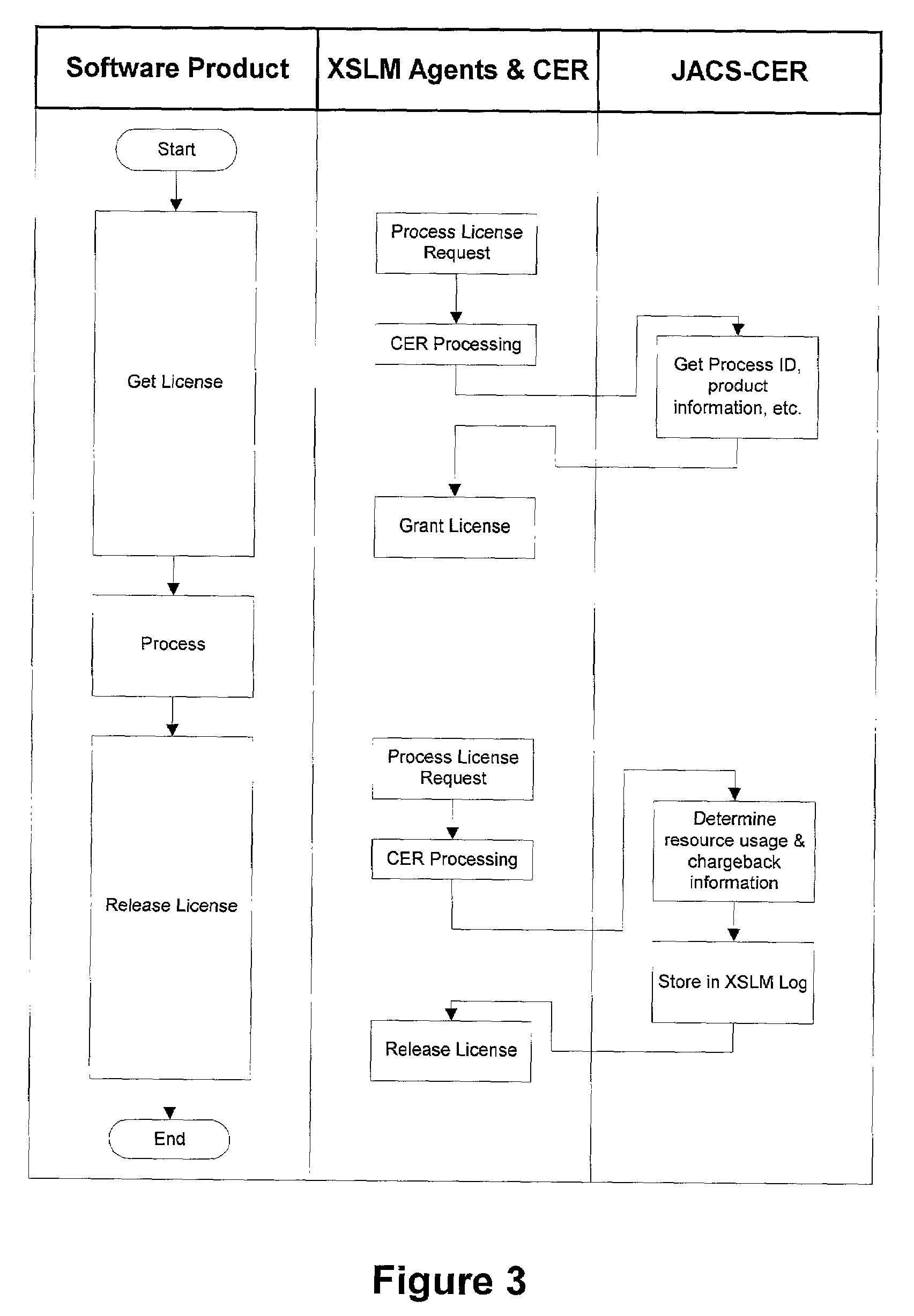
Method and system for correlating job accounting information with software license information
A job accounting and chargeback system for software products is comprised of a software license manager in the form of a software product use monitoring subsystem that handles requests for and grants rights to use software products, in such a manner that chargeback data is developed, which is then referenced to entities that are charged for the use of the software products. To better correlate the chargeback data with the use of software products, the chargeback data is referenced to the actual amount and type of use of software products being used, rather than on the use of computer facilities.
Owner:IBM CORP
Methods and systems for generating a software license knowledge base for verifying software license compliance in cloud computing environments
A monitoring system can monitor computing processes in clouds. The monitoring system can verify software license compliance in the computing processes instantiated in the clouds. The monitoring system can generate and maintain a software license knowledge base. The software license knowledge base can include the software license requirements for various software programs. To generate the software license knowledge base, the monitoring system can communicate with various sources (software vendors, clouds, publicly available sources, etc.) to determine license requirements for the various software programs.
Owner:RED HAT
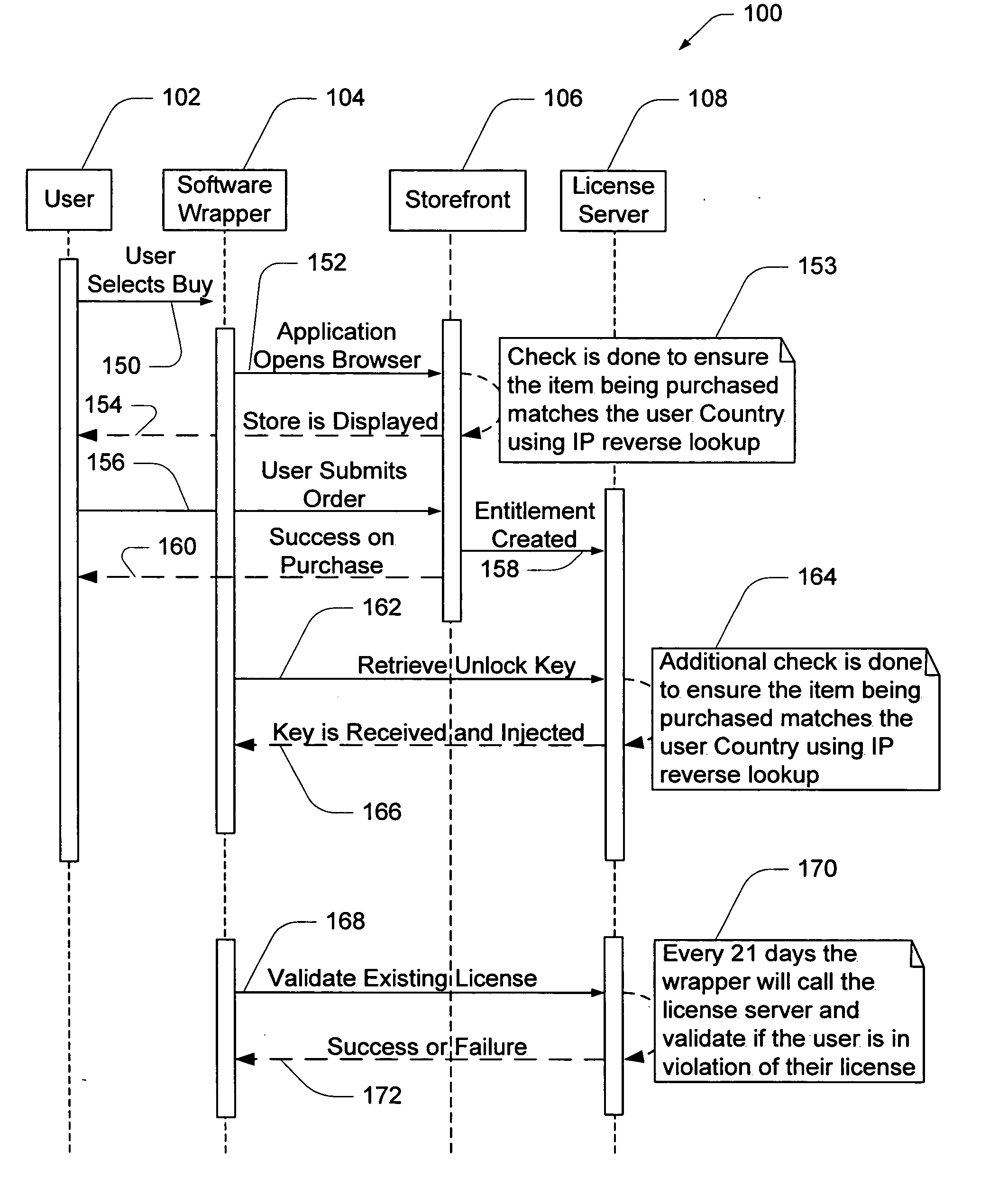
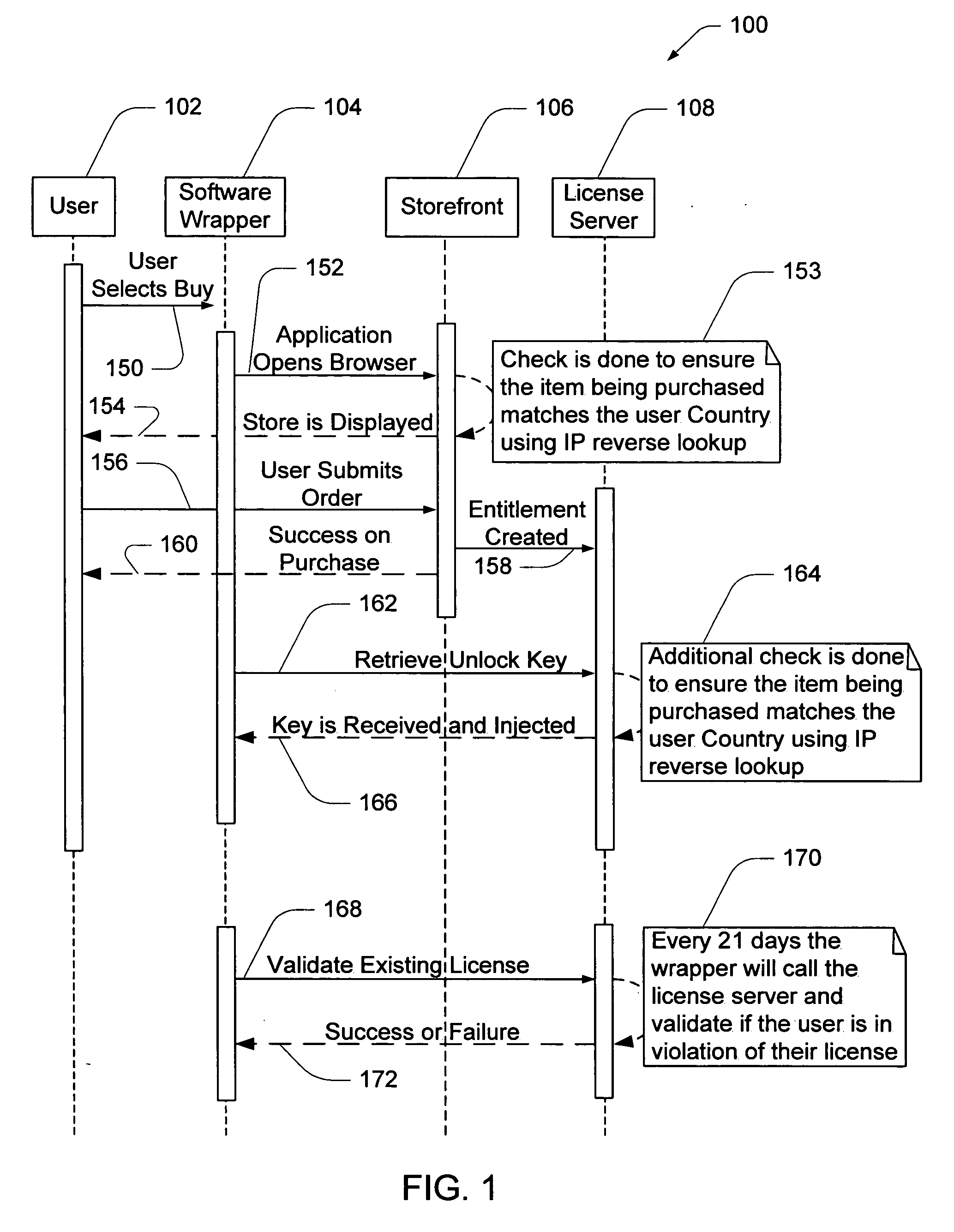
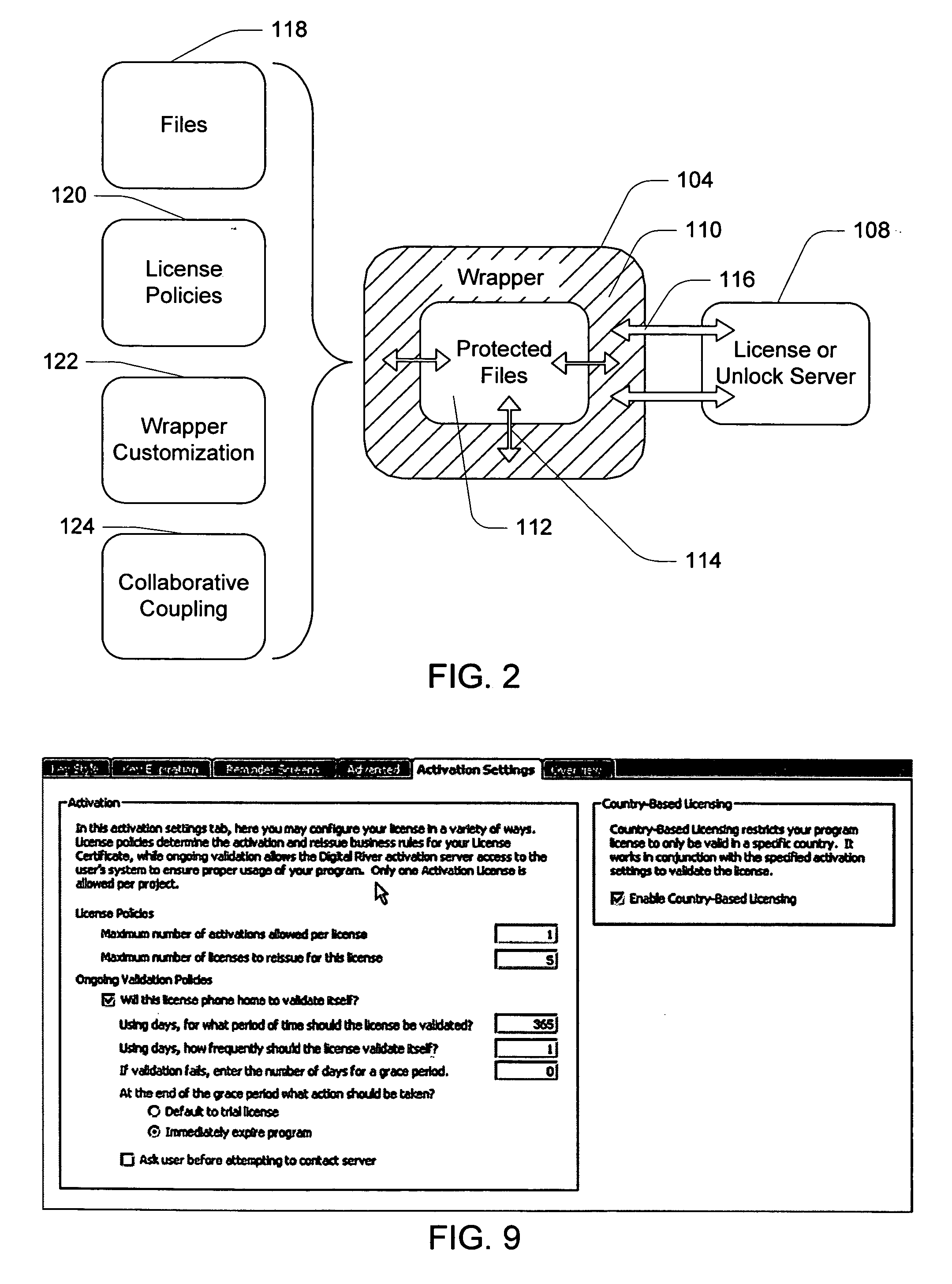
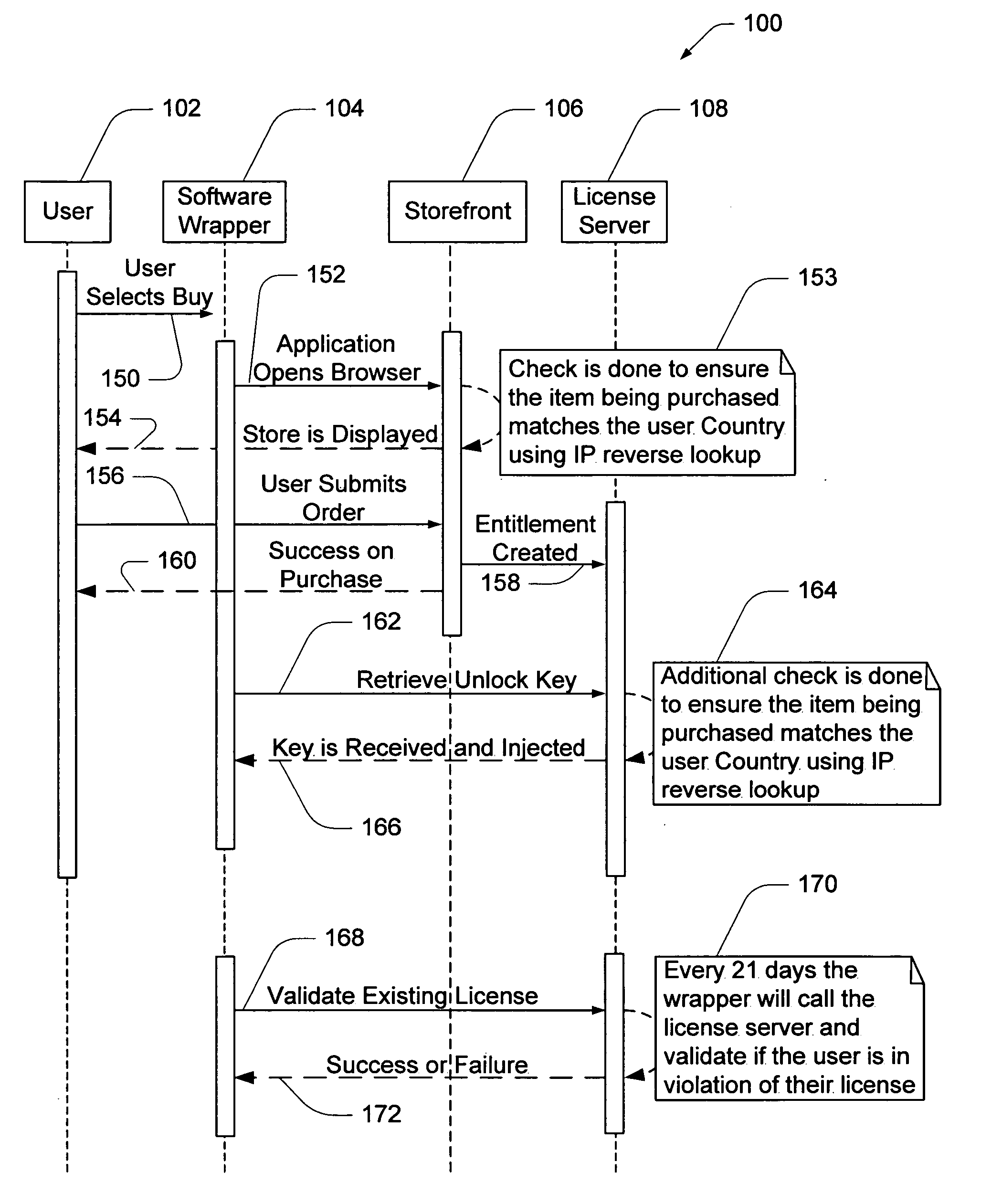
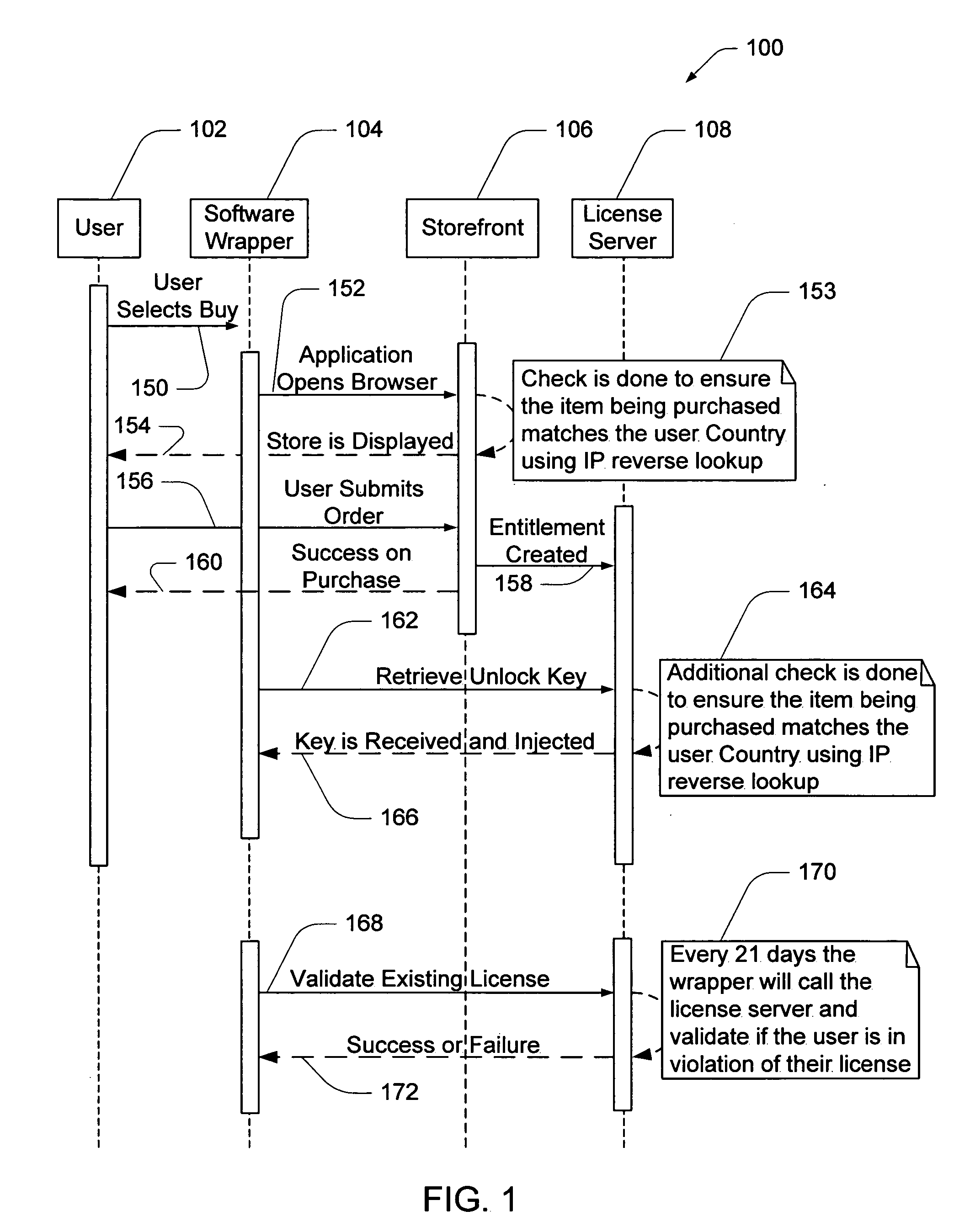
Electronic storefront that limits download of software wrappers based on geographic location
InactiveUS20060059561A1Digital data processing detailsAnalogue secracy/subscription systemsSoftware licenseSecurity software
A computer software license management system wrapper for use in a local computer is described. The software wrapper includes a wrapper interface that provides controlled access to a computer software application file. The software application file is encapsulated by security software code to protect it from unauthorized access. The software wrapper also includes a software license key identifying a license policy specifying a use limitation within a geographic boundary. In addition, the software wrapper includes a license validation mechanism that periodically determines compliance with the license policy. The license validation mechanism permits access by another process operating on the local computer through the wrapper interface in response to a valid license confirmation signal received from the license server. A license server that utilizes and an electronic storefront that sells software license wrappers having software use limitations within a geographic boundary also are described.
Owner:DIGITAL RIVER INC
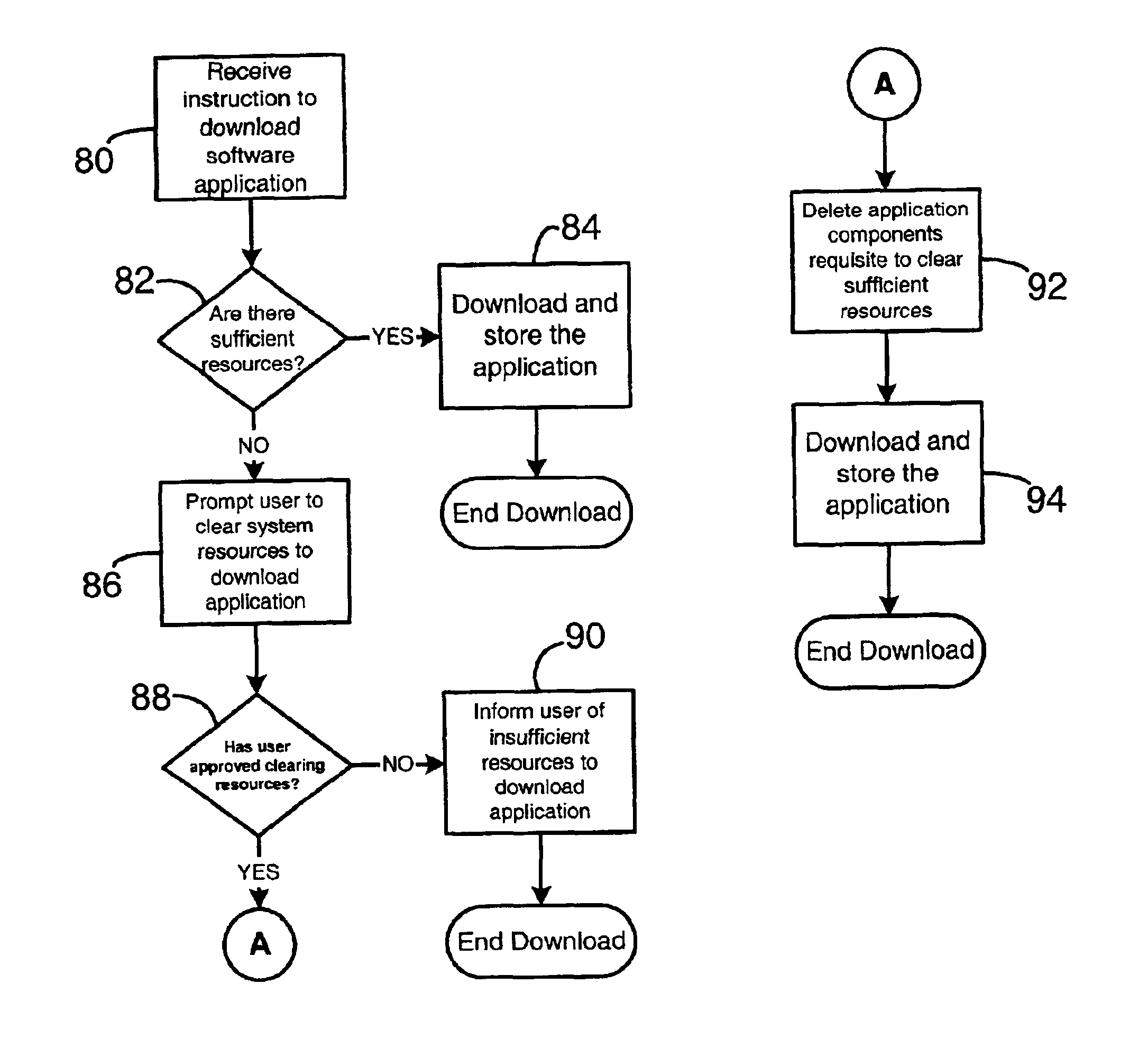
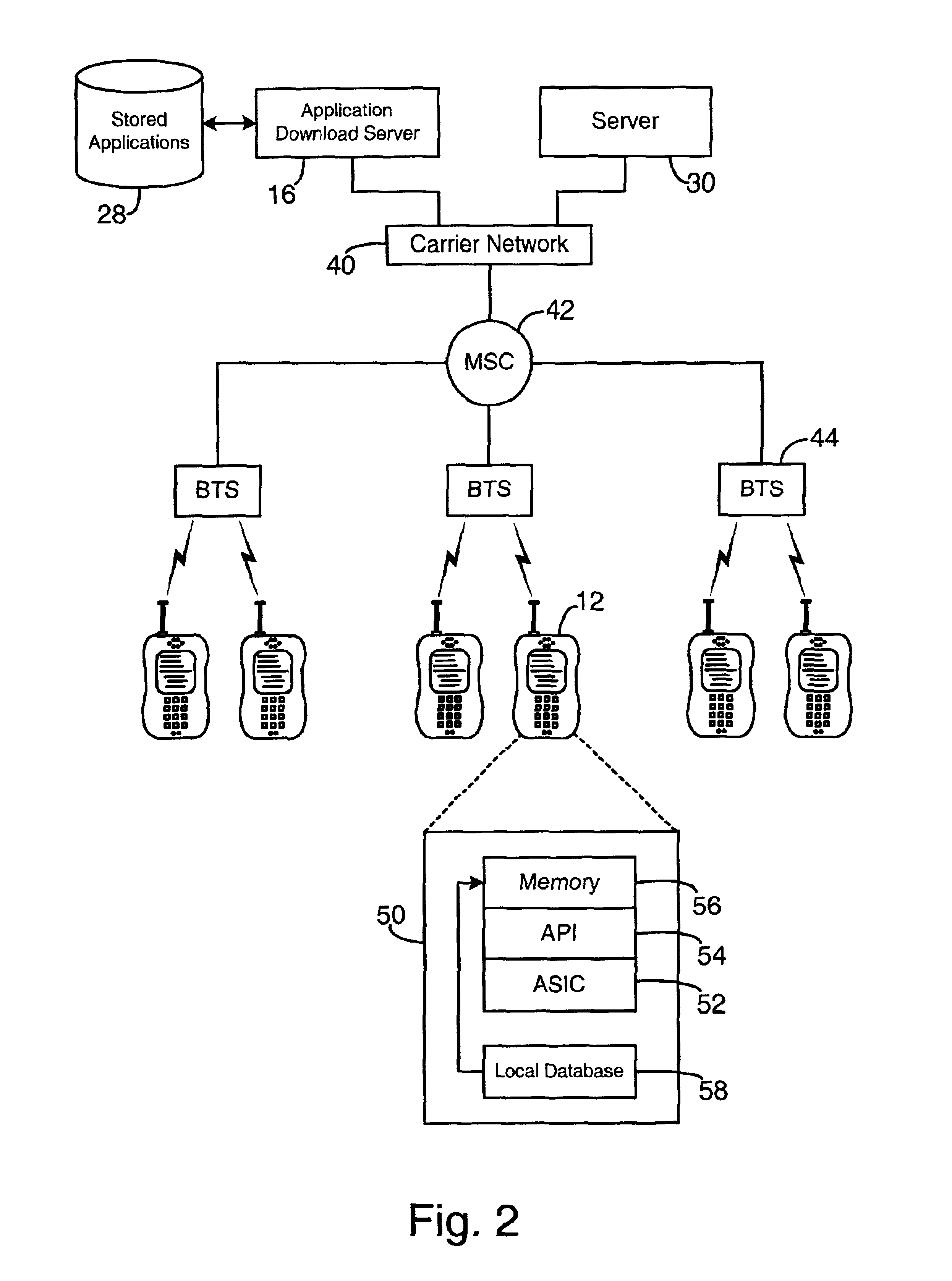
System and method for temporary application component deletion and reload on a wireless device
InactiveUS6941135B2Maximize utilizationEasy to useSpecial service for subscribersDigital computer detailsSoftware licensePager
A system and method for managing the deleting and reloading of software application components on a wireless device, such as a cellular telephone, personal digital assistant, pager, or other computer platform. The wireless device has one or more resident executable software applications wherein each application has one or more application components and application-associated data, such as software licenses and user-specific data. The wireless device selectively deletes one or more application components of the resident software applications without loss of the application-associated data to clear resources on the wireless device, and selectively prompts an application download server across a wireless network to transmit deleted application components needed to be reinstalled on the wireless device to execute the application.
Owner:QUALCOMM INC
Device-based software authorizations for software asset management
ActiveUS20090031286A1Easy and automatic determinationOffice automationResourcesSoftware asset managementSoftware license
Software device groups allow owners and administrators to be defined for various intelligent devices, instead of tracking by primary user. A software license compliance management system obtains discovery information for these devices to determine software installed or active on these devices. The management system also obtains the number of licenses for each software package and determines whether the software is in compliance, or if the number of instances exceeds the number of licenses. This determination is flexible and can handle various license types, such as per user, per device, and per processor. For any exception, the group owner is informed and then can re-allocate licenses, purchase additional licenses, or request the uninstalling of a software instance(s). Device groups also can include sub-groups with sub-group owners responsible for handling any exception in that sub-group.
Owner:ORACLE INT CORP
Distributed run-time licensing
InactiveUS20050086174A1Little additional processing overheadDigital data processing detailsAnalogue secracy/subscription systemsSoftware licenseRunning time
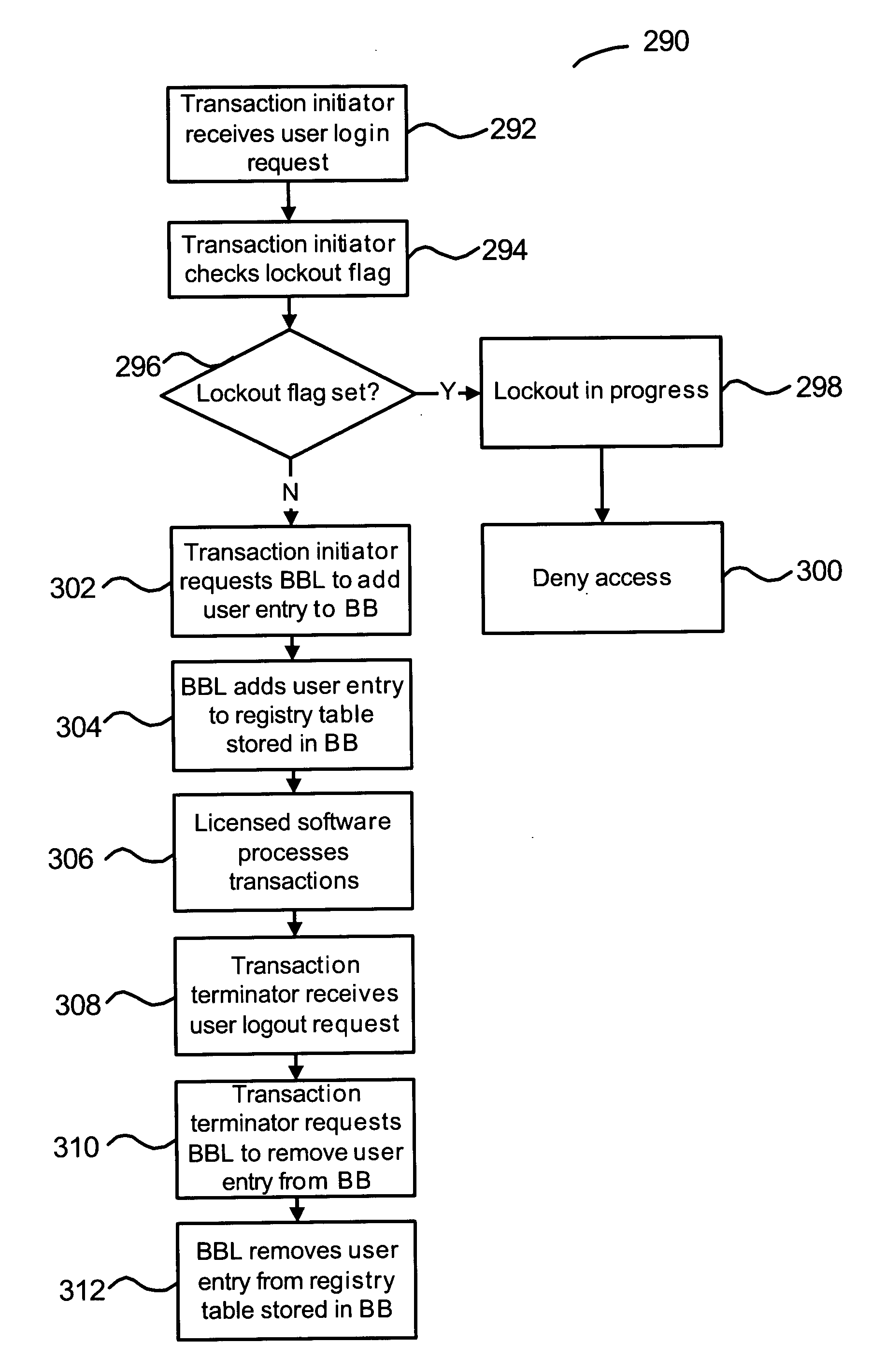
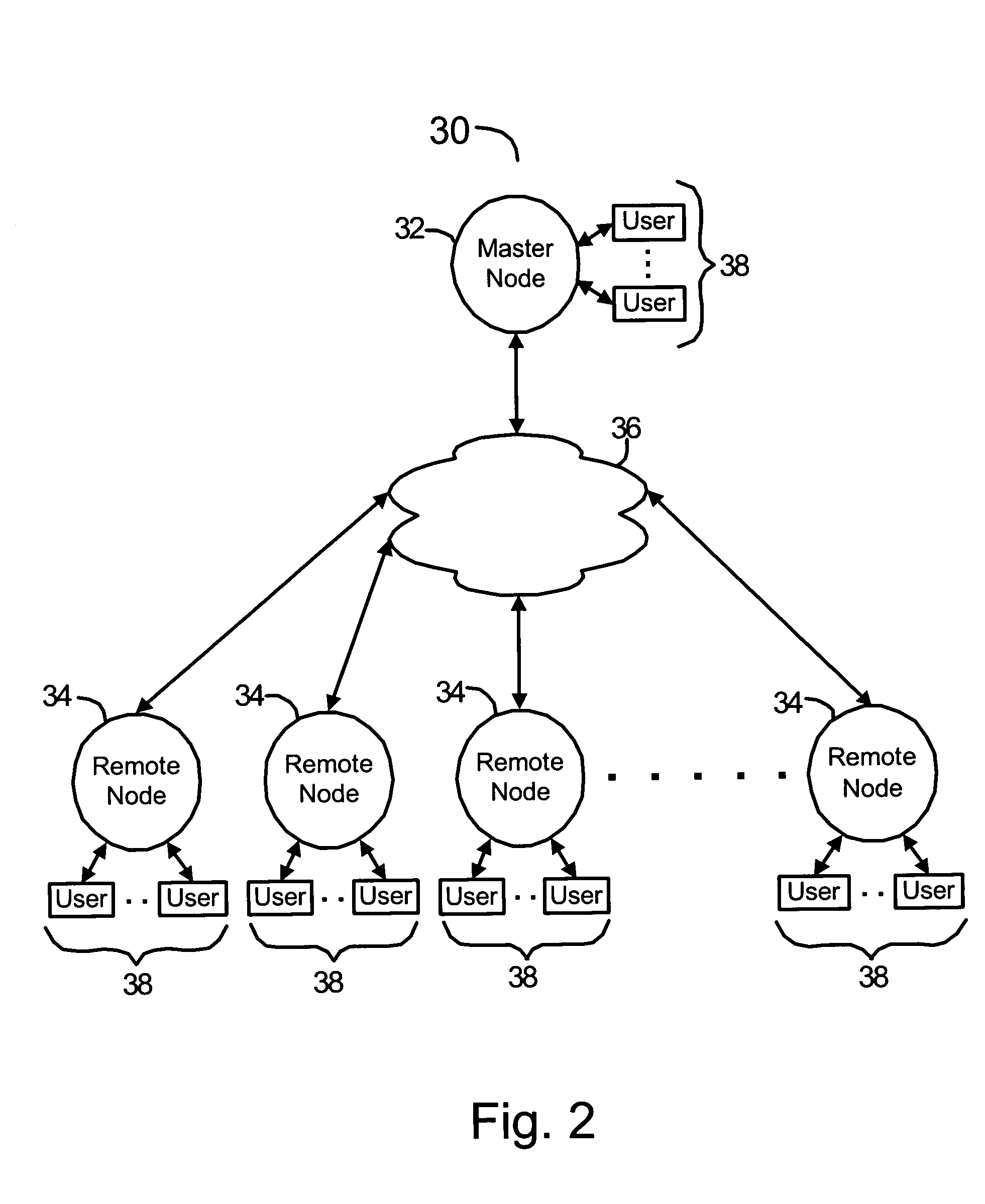
Methods and systems are disclosed for managing software licenses in a distributed computer network. The number of software licenses allocated to software users can be determined on a node-by-node basis in realtime with little or no additional processing overhead incurred by the network. Upon of the occurrence of a node failure, software licenses are efficiently reallocated to new users. In one implementation, users are periodically counted at each network node and transmitted to a master node with a sanity scan result message. A license allocation condition is periodically evaluated using the sum of the counts. If the condition is met, a license lockout can be performed upon the expiration of a grace period.
Owner:ORACLE INT CORP
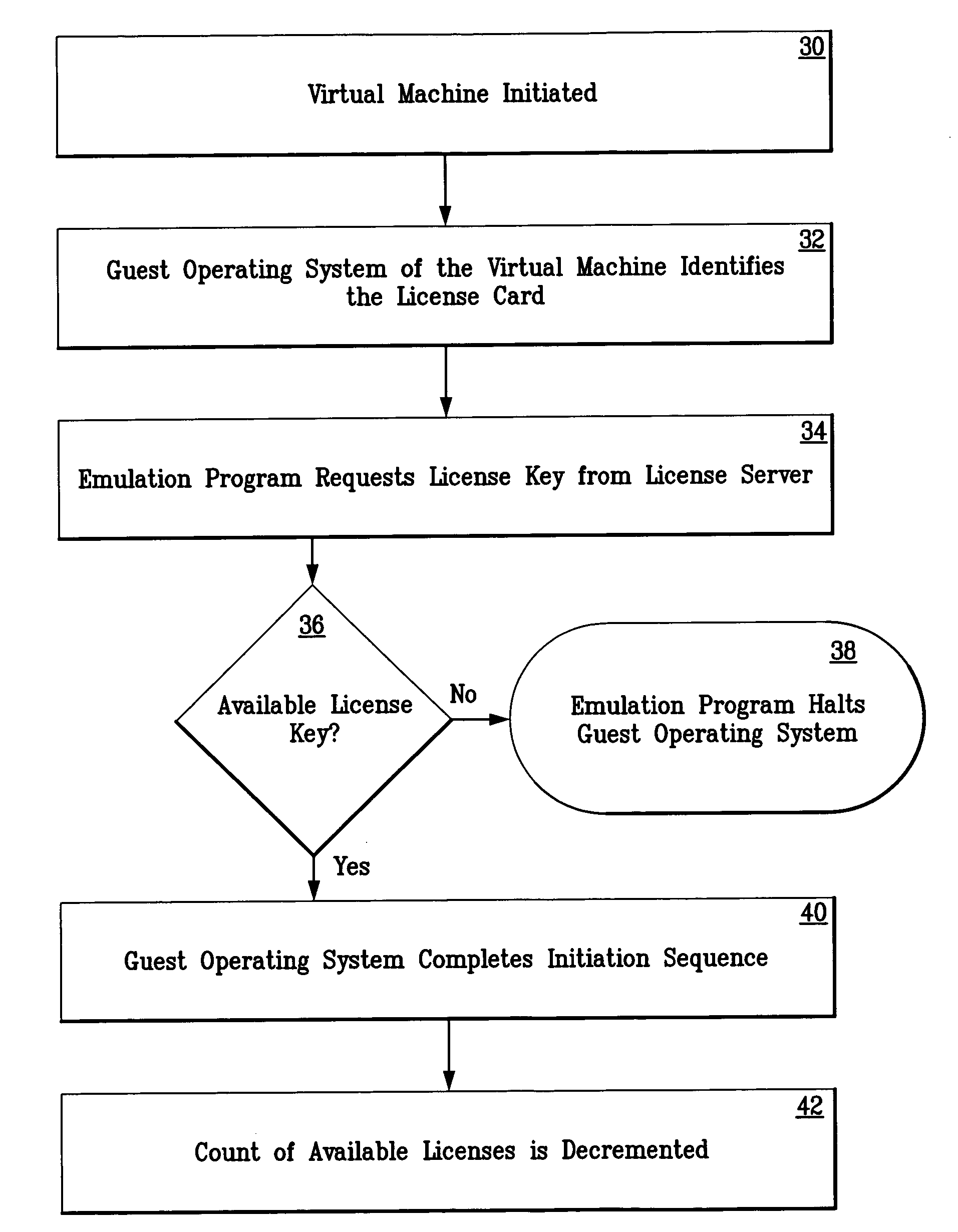
Software license enforcement mechanism for an emulated computing environment
ActiveUS7313512B1Count can be incrementedPrevent theftDigital data processing detailsAnalogue secracy/subscription systemsOperational systemSoftware license
In an emulated computing environment, a method is provided for licensing software of one or more guest computer systems. A license key server is provided in the host computer system for monitoring the initiation of unlicensed software, including operating system software, in the guest computer system. A determination is made by the license key server as to whether additional a license is available for each unlicensed software application. If a license is available, a license is granted and the count of available licenses is decremented. If a license is not available, a license is not granted and the unlicensed software application in the guest computer system is disabled.
Owner:MICROSOFT TECH LICENSING LLC
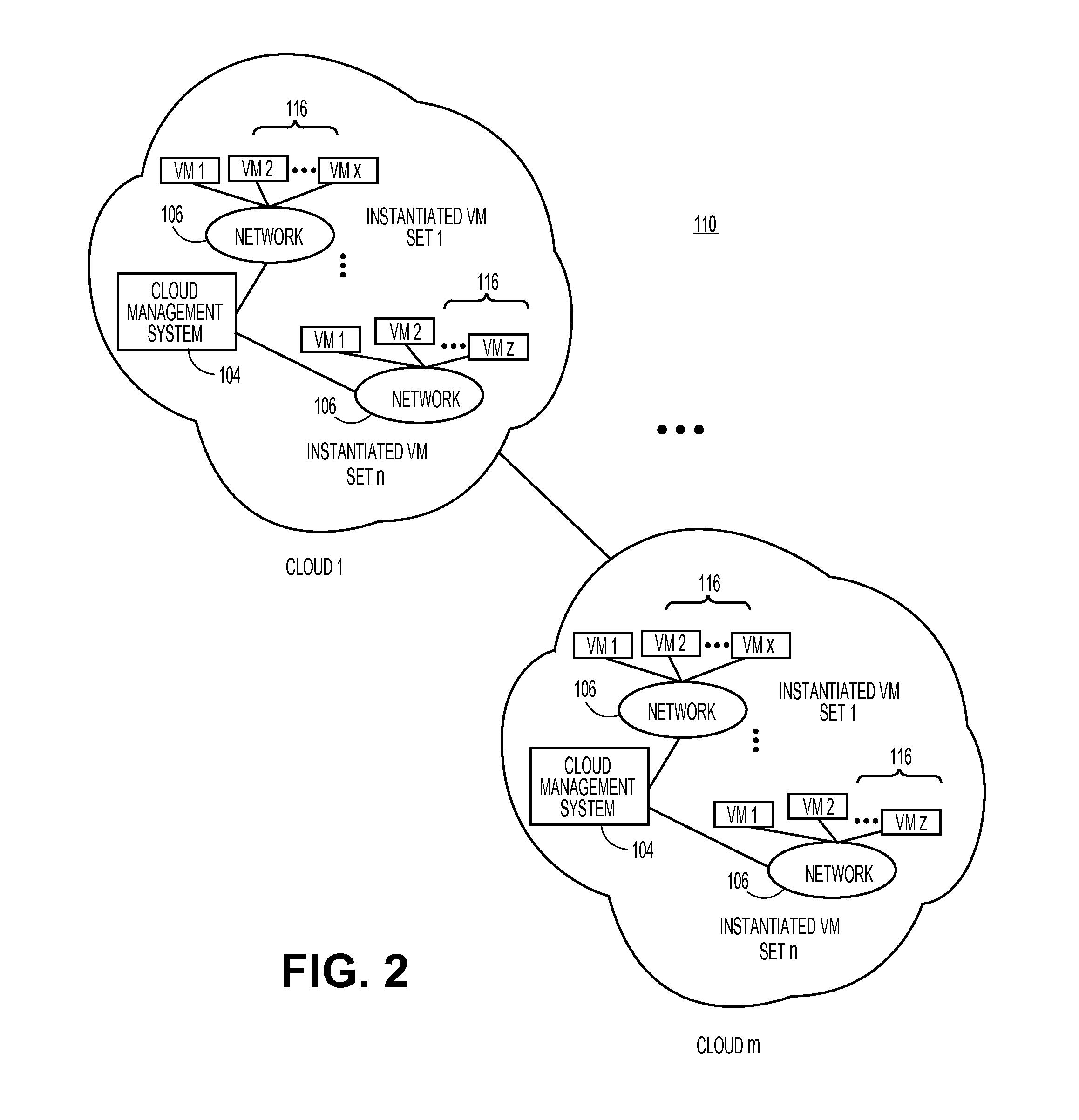
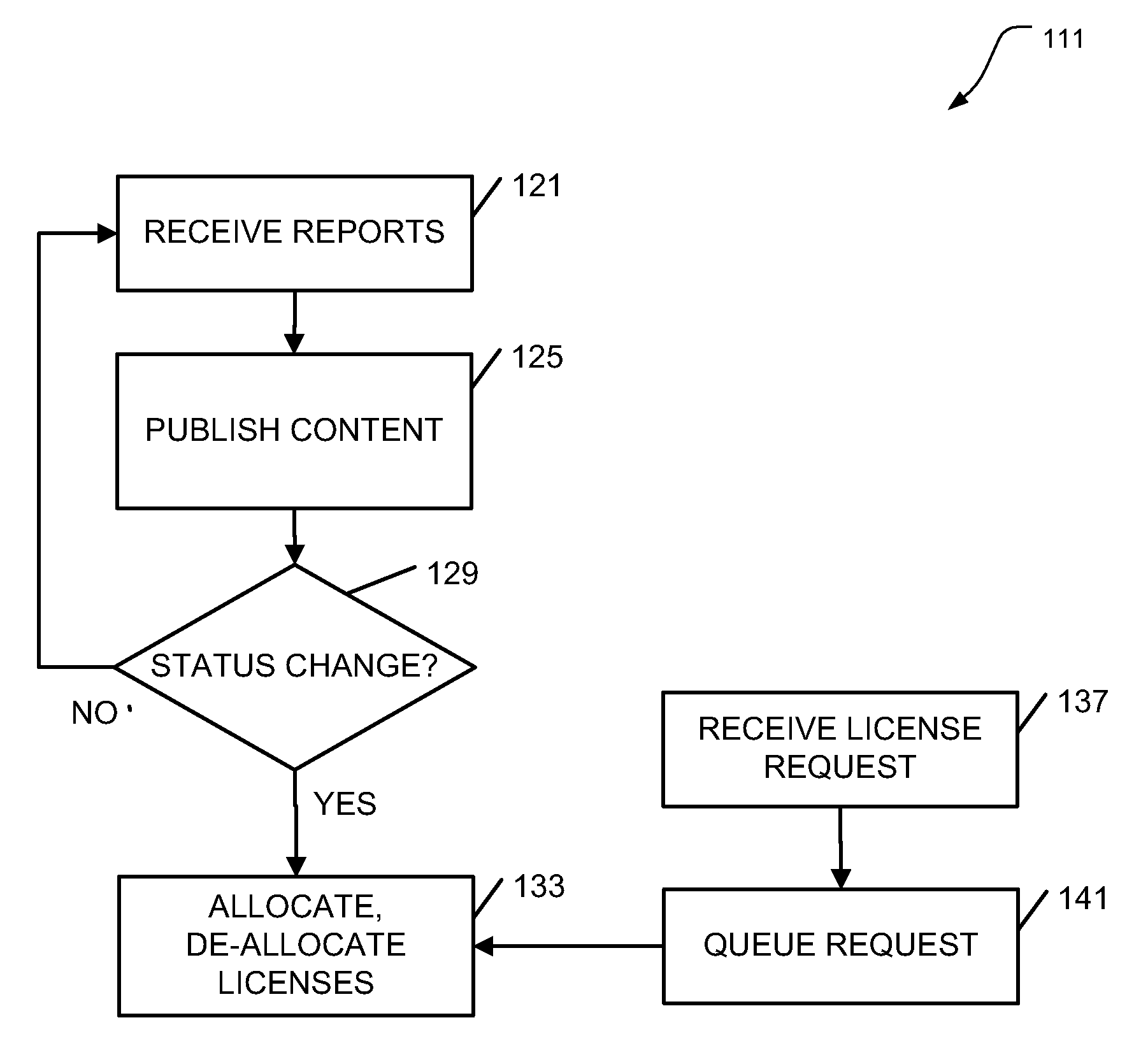
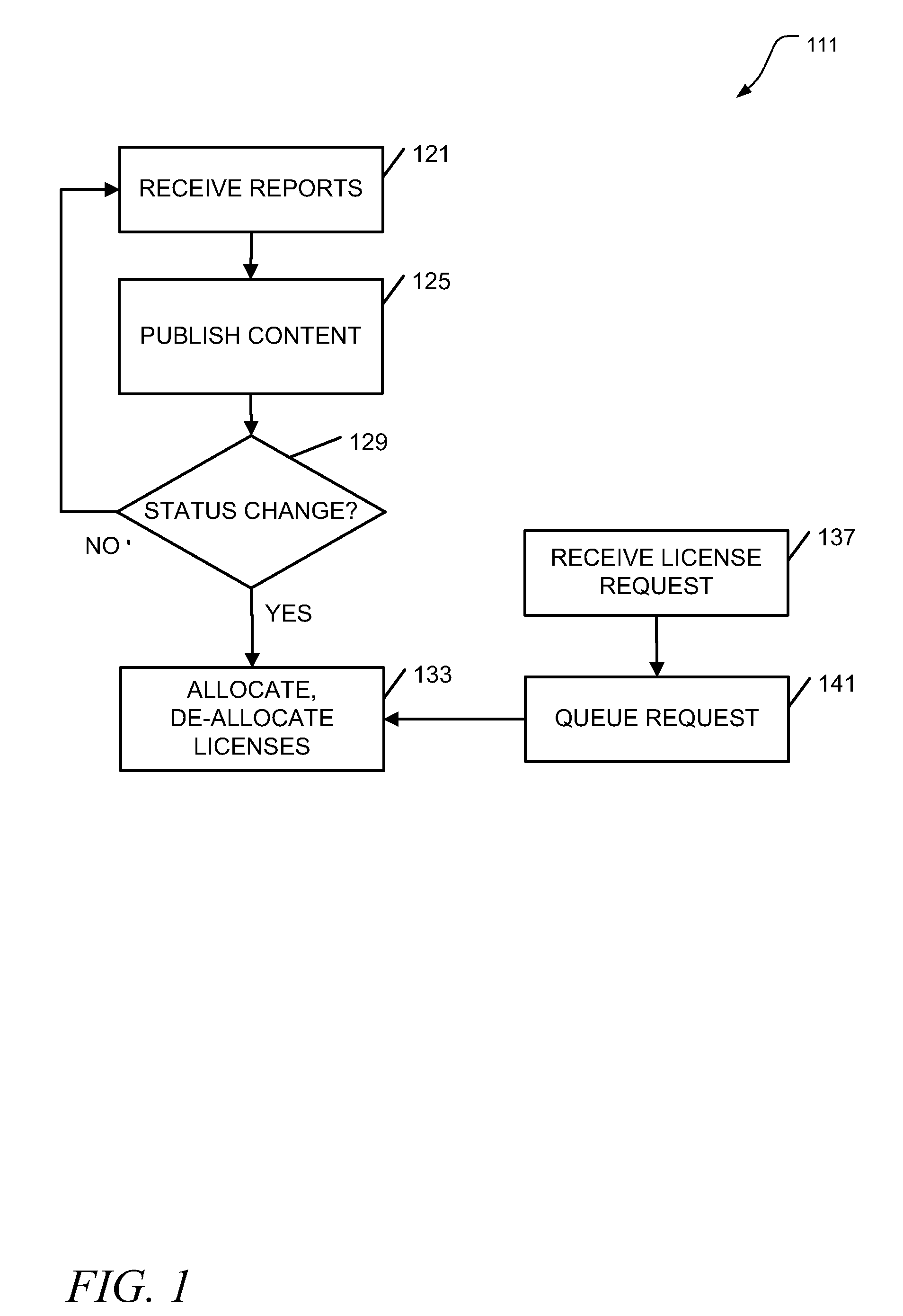
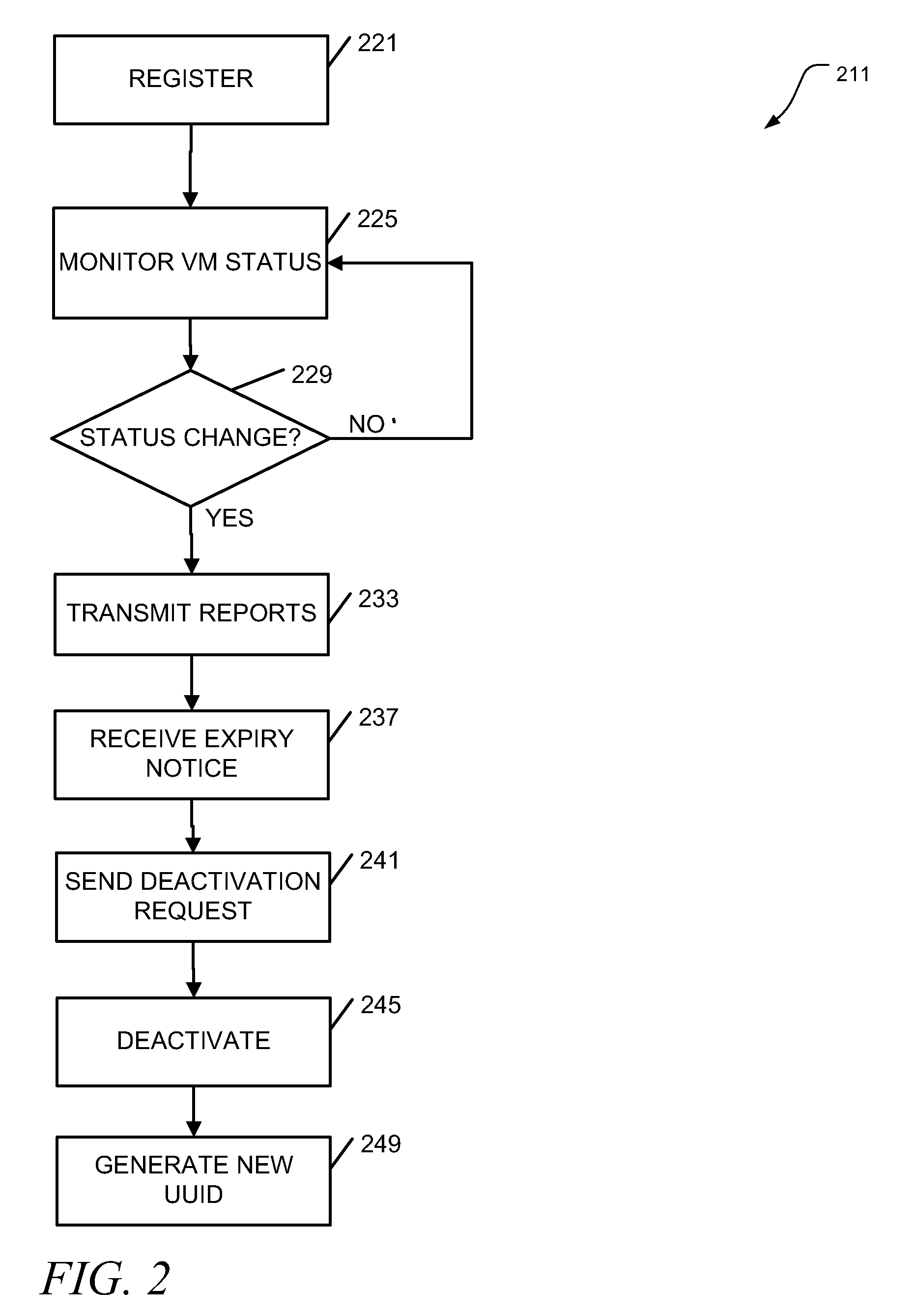
Virtual machine software license management
ActiveUS20100205303A1Digital computer detailsProgram/content distribution protectionSoftware licenseVirtual machine
Apparatus, systems, and methods may operate to receive reports at a server node, the reports indicating a change in virtual machine status for virtual machines hosted on a virtual machine host node; and to allocate / de-allocate software licenses to the virtual machines based on the change in virtual machine status. In some embodiments, operations may include detecting, at a virtual machine host node, a change in virtual machine status for virtual machines hosted on the host node; and transmitting reports to a server node from the host node. The reports can be used to indicate the change in virtual machine status, enabling the server node to allocate / de-allocate software licenses to the virtual machines based on the change in virtual machine status. Additional apparatus, systems, and methods are disclosed.
Owner:MICRO FOCUS SOFTWARE INC
Software license brokering within a cloud computing environment
InactiveUS20110251937A1Complete banking machinesDigital data processing detailsPaymentSoftware license
Under embodiments of the present invention, a set (at least one) of Clouds, a set of software providers, and a set of Cloud consumers (hereinafter “consumers”) are registered with a Cloud software license broker (hereinafter “broker”). Consumer information will be matched with the set of software providers to determine applicable licenses as well as pricing and usage rates. Use of software within the set of Clouds by the set of Cloud consumers will be tracked, aggregated, and reported. Based on the use, a licensing arrangement (including a price) will be determined. Applicable amounts will then be billed, and payments will be collected and disbursed (e.g., to the set of software providers) in accordance with the licensing arrangements. Under the present invention, prices / amounts can be determined based on a per use / on-demand of software and / or based on use of the software over an interval of time (e.g., interval-based pricing).
Owner:IBM CORP
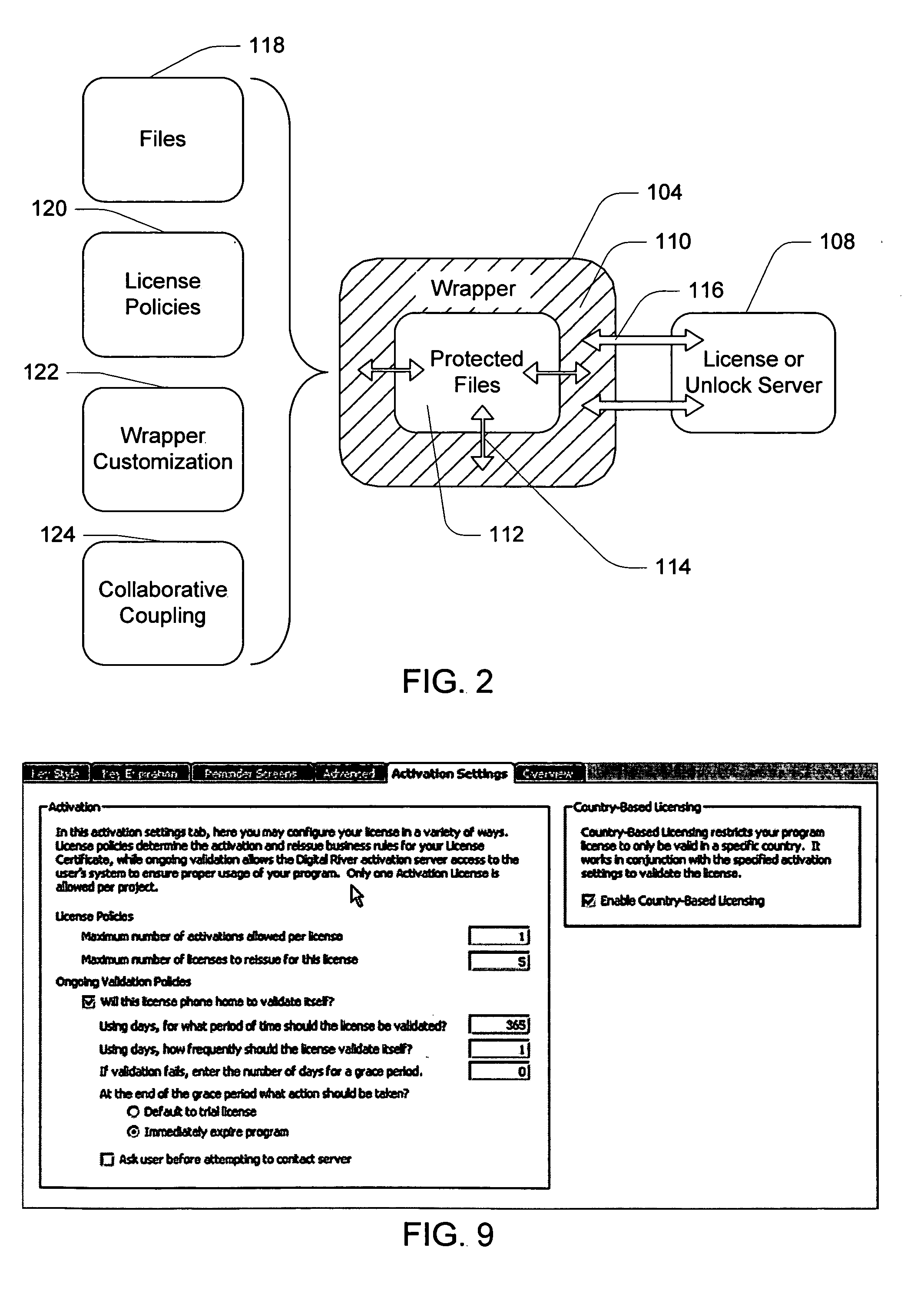
Software wrapper having use limitation within a geographic boundary
ActiveUS20060059099A1Payment architectureProgram/content distribution protectionSecurity softwareSoftware license
A computer software license management system wrapper for use in a local computer is described. The software wrapper includes a wrapper interface that provides controlled access to a computer software application file. The software application file is encapsulated by security software code to protect it from unauthorized access. The software wrapper also includes a software license key identifying a license policy specifying a use limitation within a geographic boundary. In addition, the software wrapper includes a license validation mechanism that periodically determines compliance with the license policy. The license validation mechanism permits access by another process operating on the local computer through the wrapper interface in response to a valid license confirmation signal received from the license server. A license server that utilizes and an electronic storefront that sells software license wrappers having software use limitations within a geographic boundary also are described.
Owner:DIGITAL RIVER INC
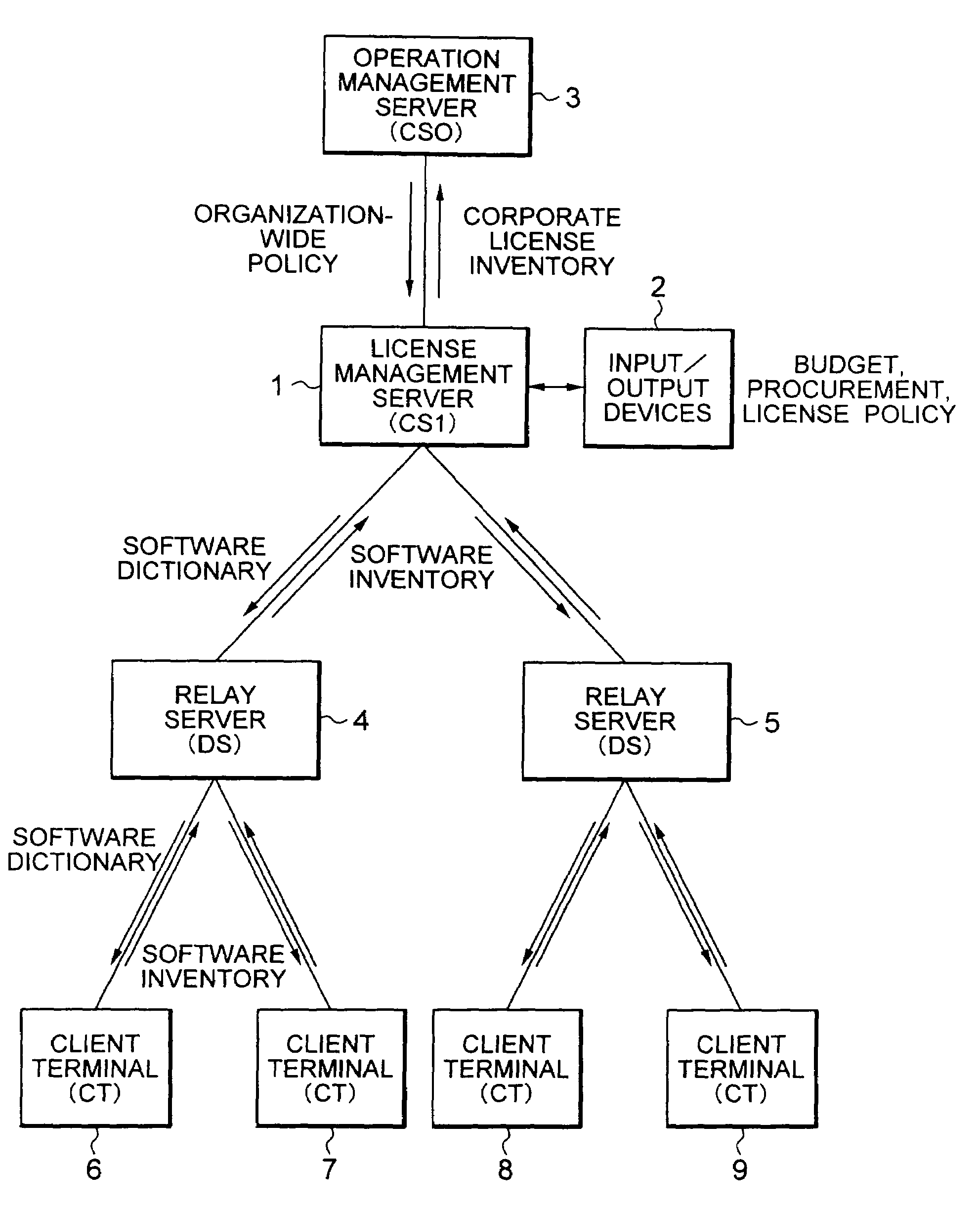
Apparatus and method for managing software licenses and storage medium storing a program for managing software licenses
InactiveUS7139737B2Easy to correctReduce negotiated unit priceData processing applicationsDigital data processing detailsSoftware licenseSoftware engineering
An inventory information collecting unit automatically collects inventory information including inventory information regarding software installed in each of a plurality of computers within an organization. A usage-state information collecting unit updates a software license usage number which represents the number of software licenses used in each section of the organization. When the sum of the software license usage numbers of the respective sections of the organization exceeds a software license holding number which represents the number of software licenses owned by the organization, a license purchasing unit generates a purchase transaction for purchasing software licenses, the number of which is equal to the difference between the sum and the software license holding number and transfers a purchase expense to relevant sections.
Owner:FUJITSU LTD
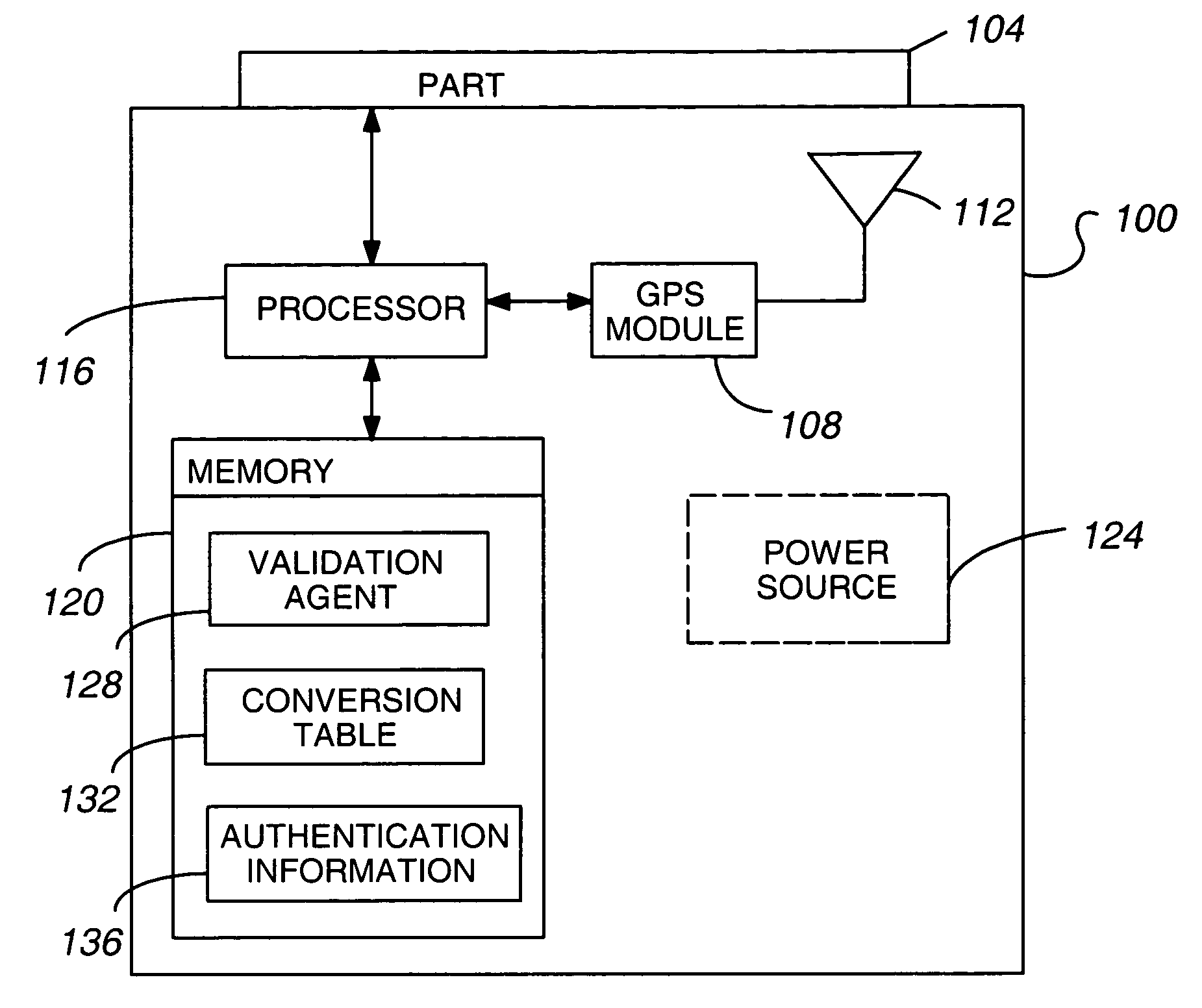
Global positioning system hardware key for software licenses
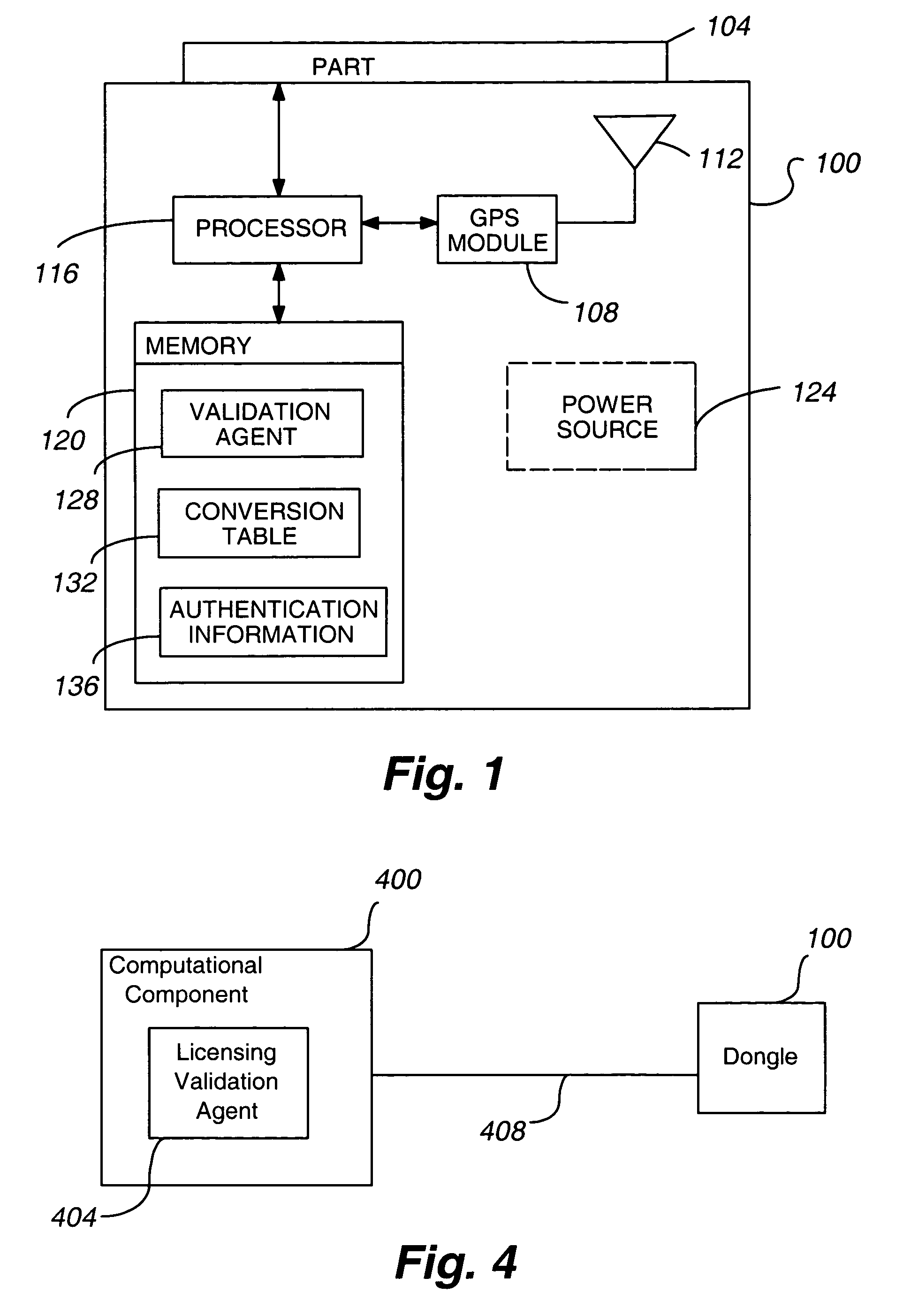
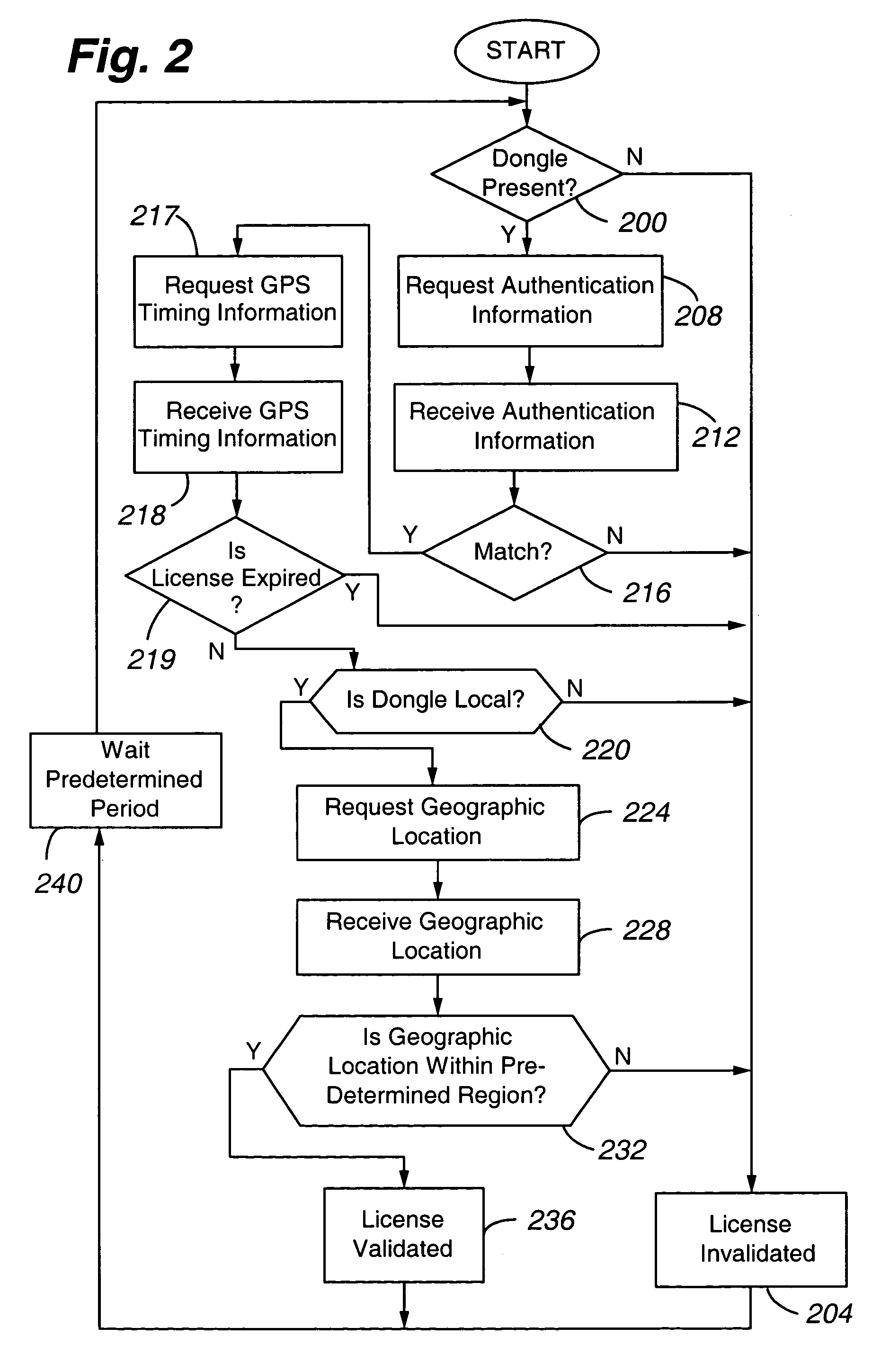
ActiveUS7272500B1Efficient processingLow costElectric signal transmission systemsDigital data processing detailsSoftware licenseGeolocation
A system for validating a license to use a computational component, comprising (a) a GPS module 108 to determine one or more of GPS timing information and a geographic location of at least one of the computational component 400 and a key device 100 in communication with the computational component 400 and (b) a validation agent 128 and / or 404 operable to (a) compare the GPS timing information against the license expiration date and / or compare the geographic location with at least one predetermined geographic location permitted by the license and (b), when the GPS timing information is outside of the permissible license term and / or when the geographic location is not a permitted geographic location under the license, determine that the computational component 400 is not validly licensed.
Owner:AVAYA INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com