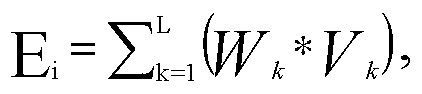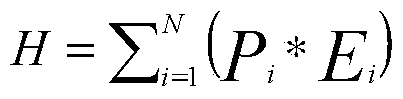Patents
Literature
34 results about "Security metric" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
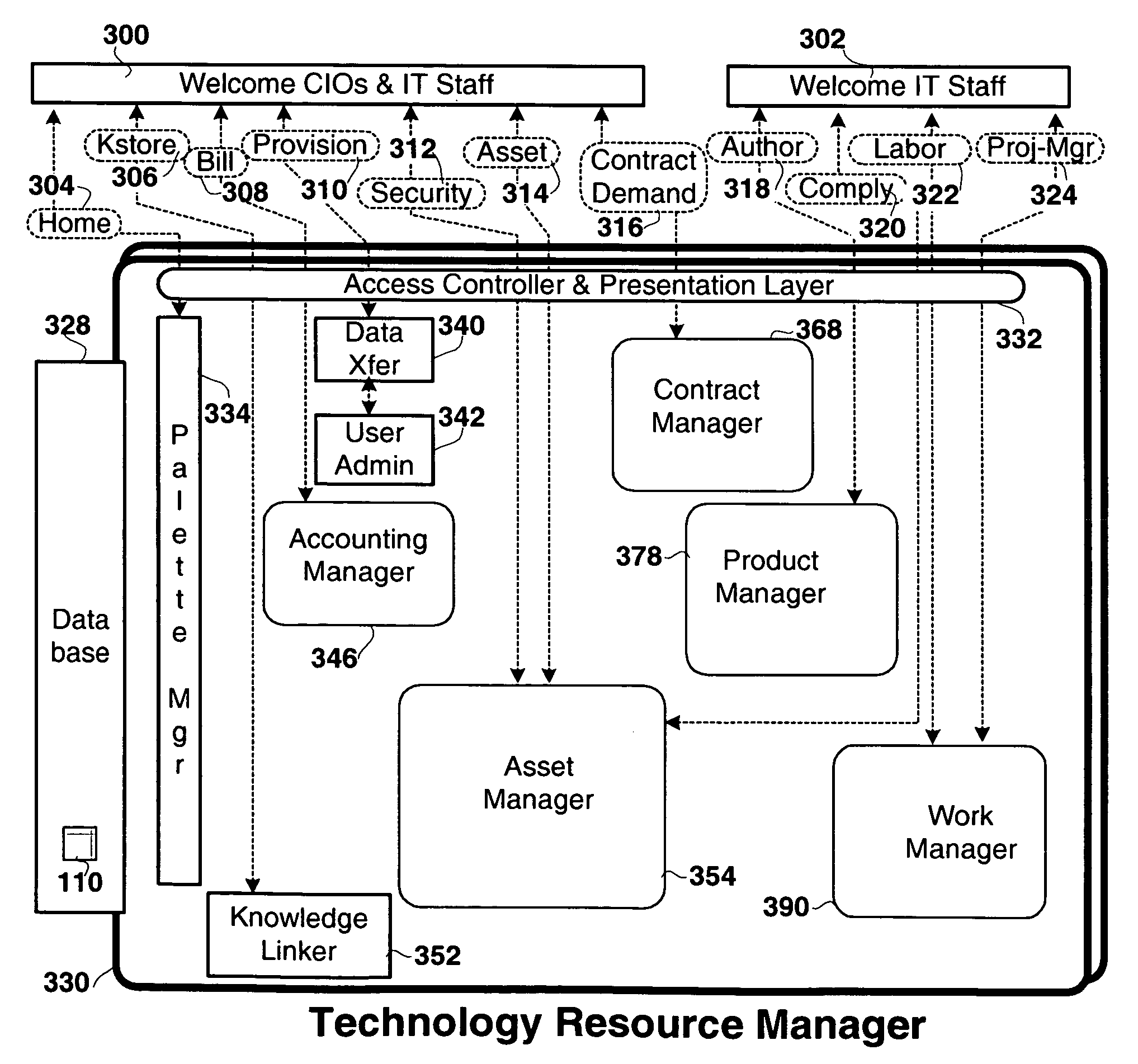
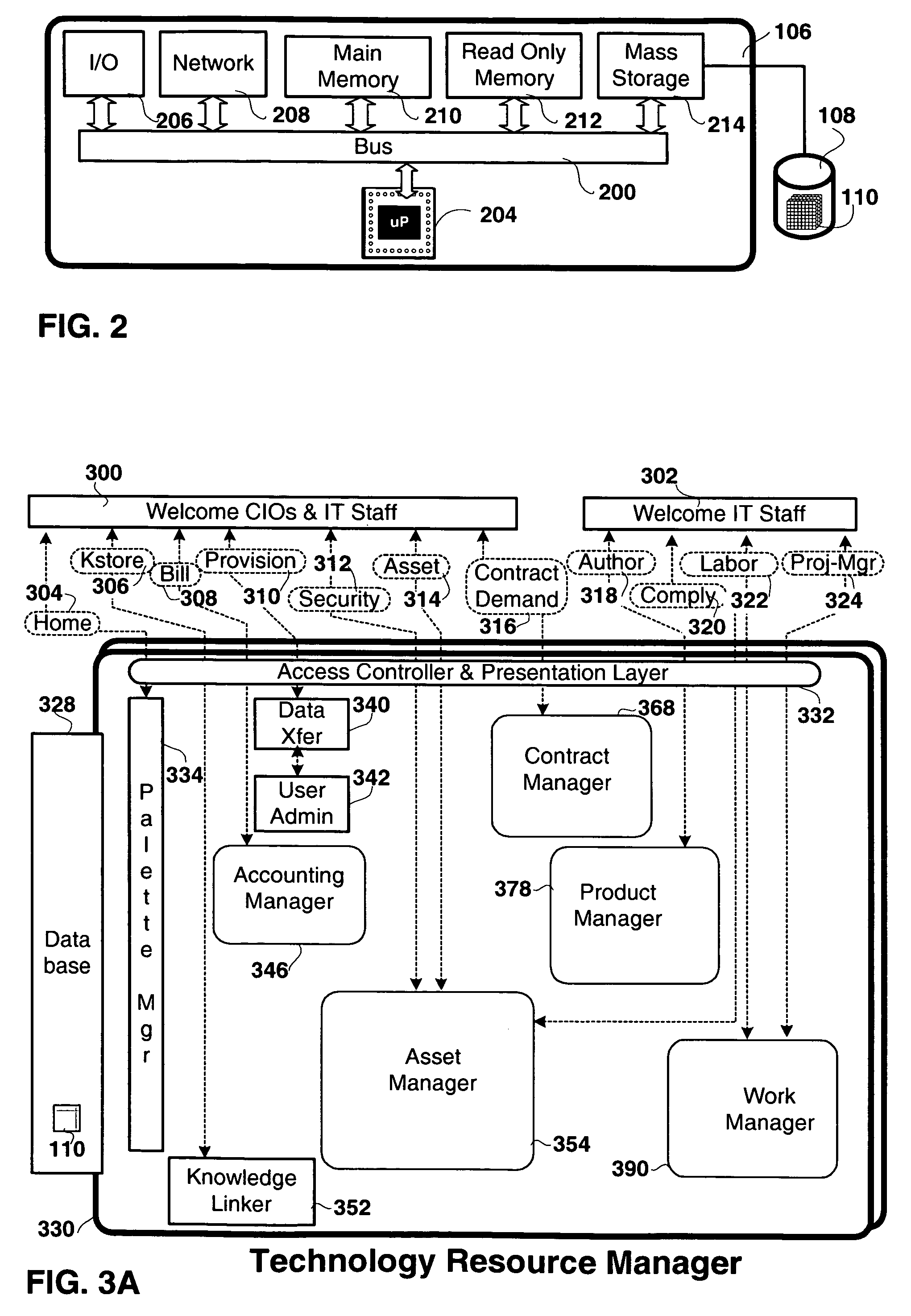
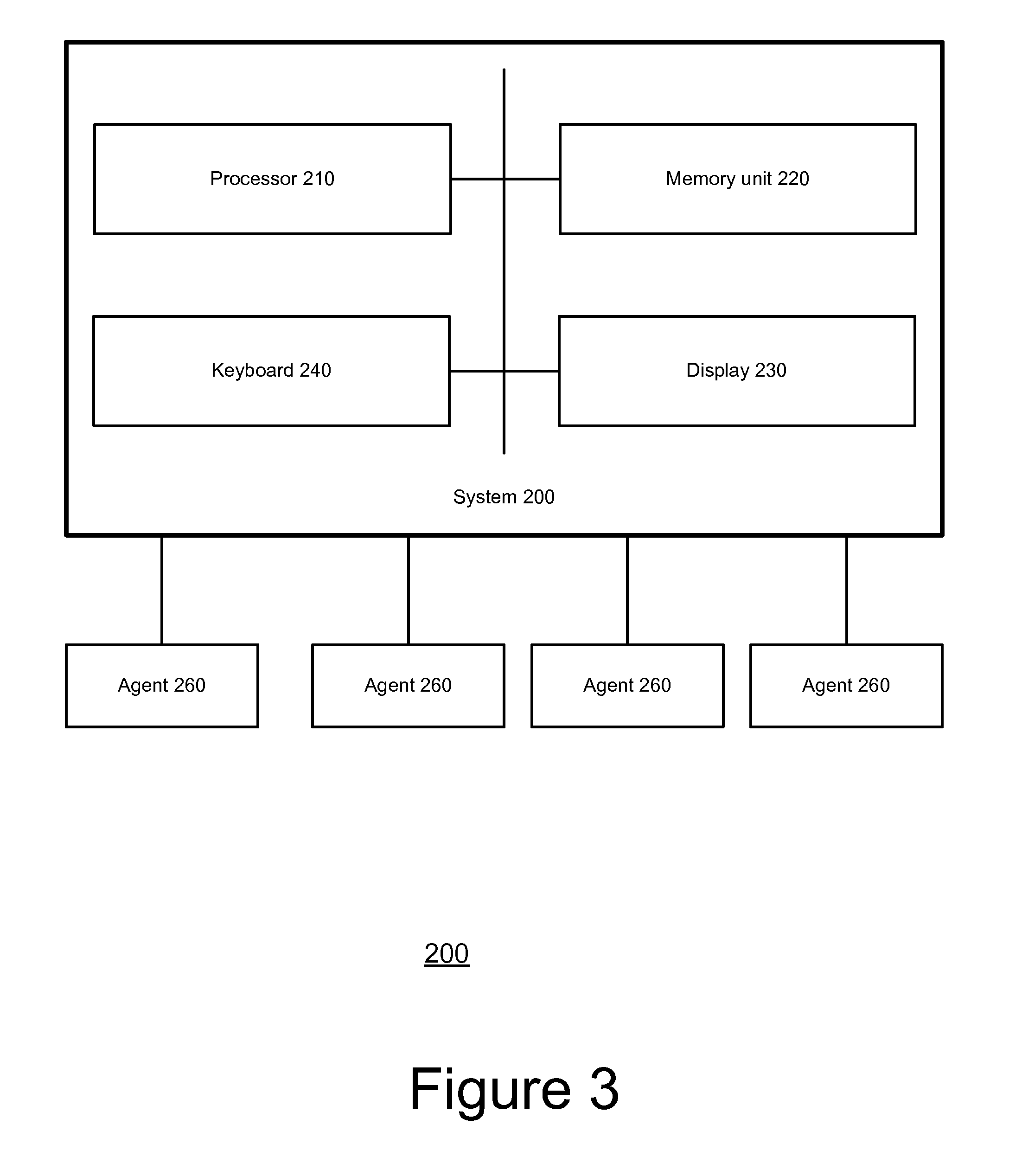
Method and apparatus for technology resource management
Apparatus, and associated methods, manage technology resources in hosted applications including: demand, service level agreements, assets both hardware and software, projects, labor, knowledge and provisioning. The apparatus includes an asset manager configured to couple to host servers and a network, to manage the host servers and software deployed thereon. In embodiments of the invention the asset manager: determines demand for new assets and allocates available assets to meet the demand; determines assets not in compliance with existing software licenses; determines which host servers have actual service level metrics which are not compliant with the target service level metrics; and determines availability of a patch or upgrade for selected software and instances of the selected software among the assets. In an embodiment of the invention the asset manager couples to a contract manager with the asset manager determining the assets for which actual monitored service level metrics violate contract service level metrics. In an embodiment of the invention the asset manager couples to a product manager and scans the host severs to determine which have actual security metrics which are not compliant with the target security metrics managed by the product manager. In an embodiment of the invention the asset manager couples with a product manager, a work manager and an accounting manager to compare the actual costs of the new assets from the accounting manager and the work manager with the price of the assets from the product record.
Owner:IBM CORP
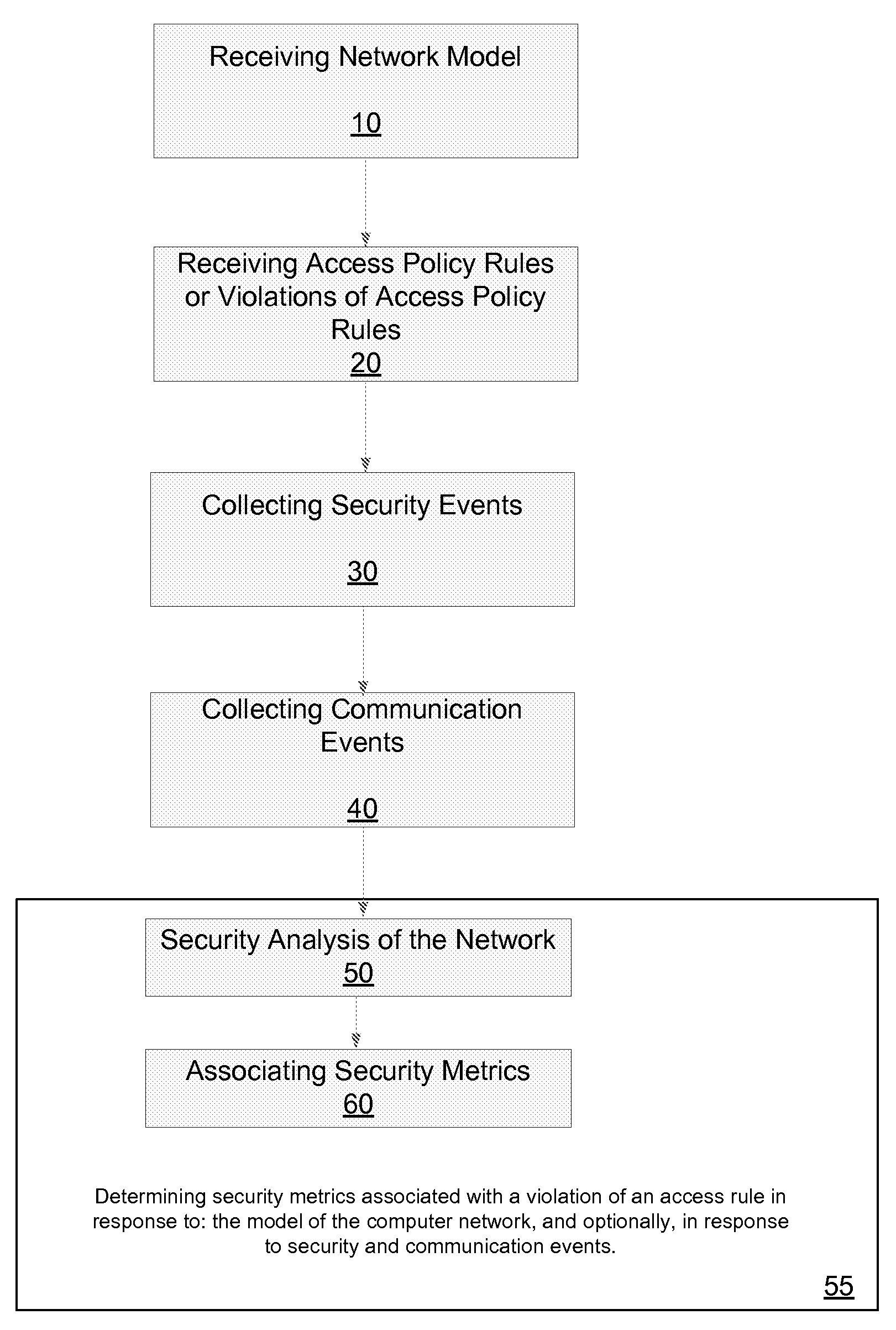
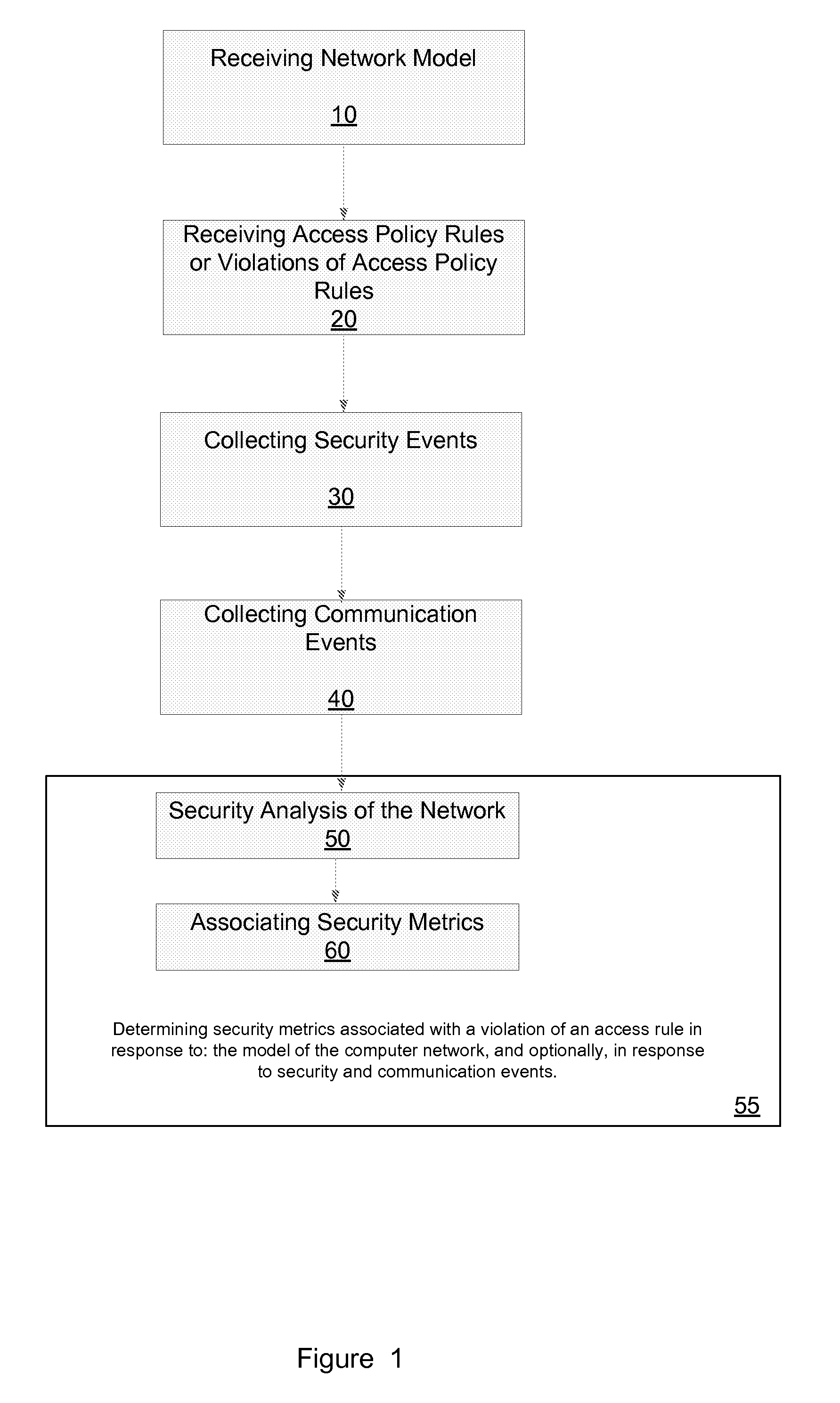
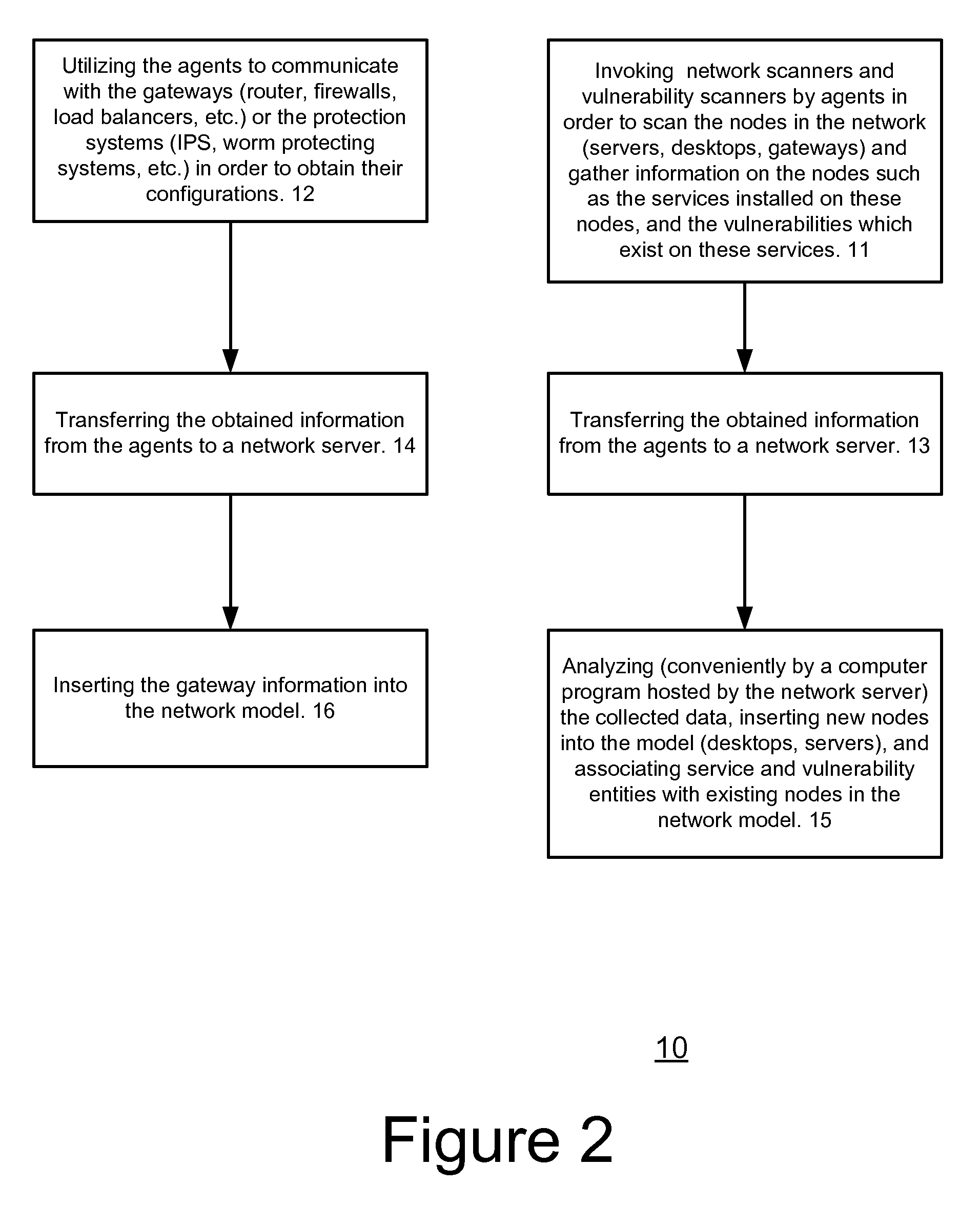
Method for evaluating a network
A method for evaluating access rules violations, the method includes: receiving, a model of a computer network; and determining security metrics associated with a violation of an access rule in response to: the model of the computer network, multiple network nodes of the computer network accessible according to at least one violated access rule or according to the network model, at least one vulnerability associated with the multiple network nodes, and damage associated with an exploitation of the at least one vulnerability.
Owner:SKYBOX SECURITY
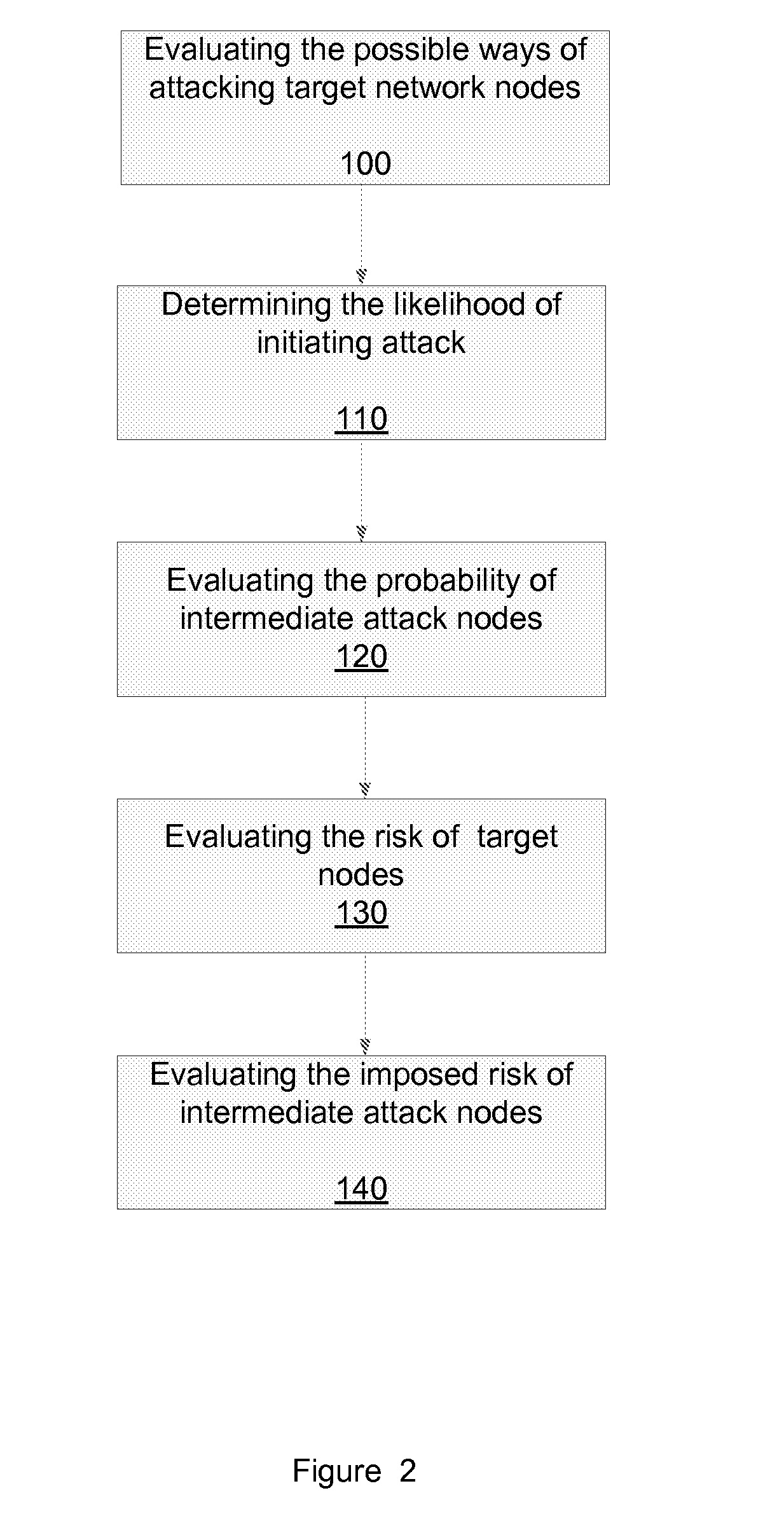
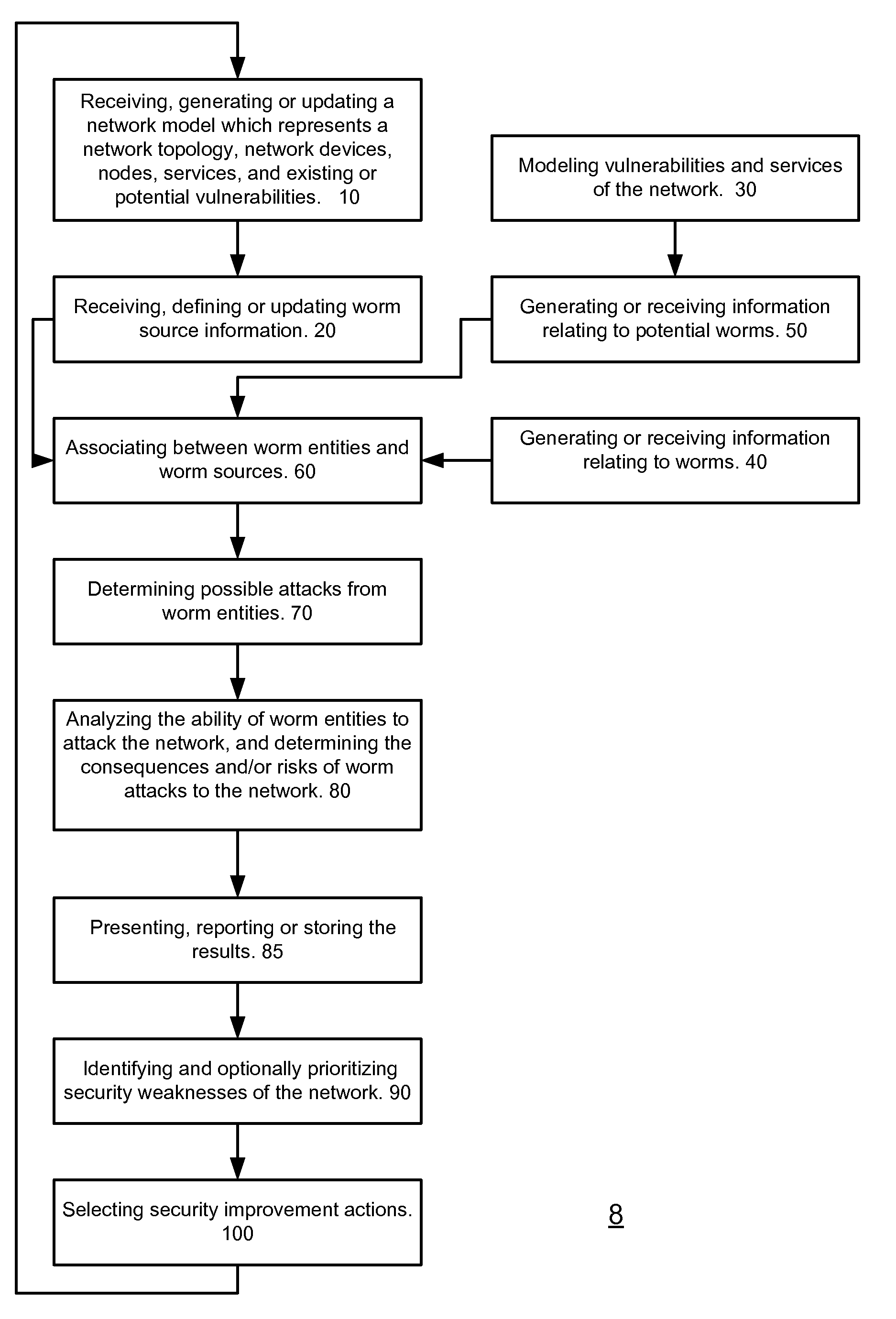
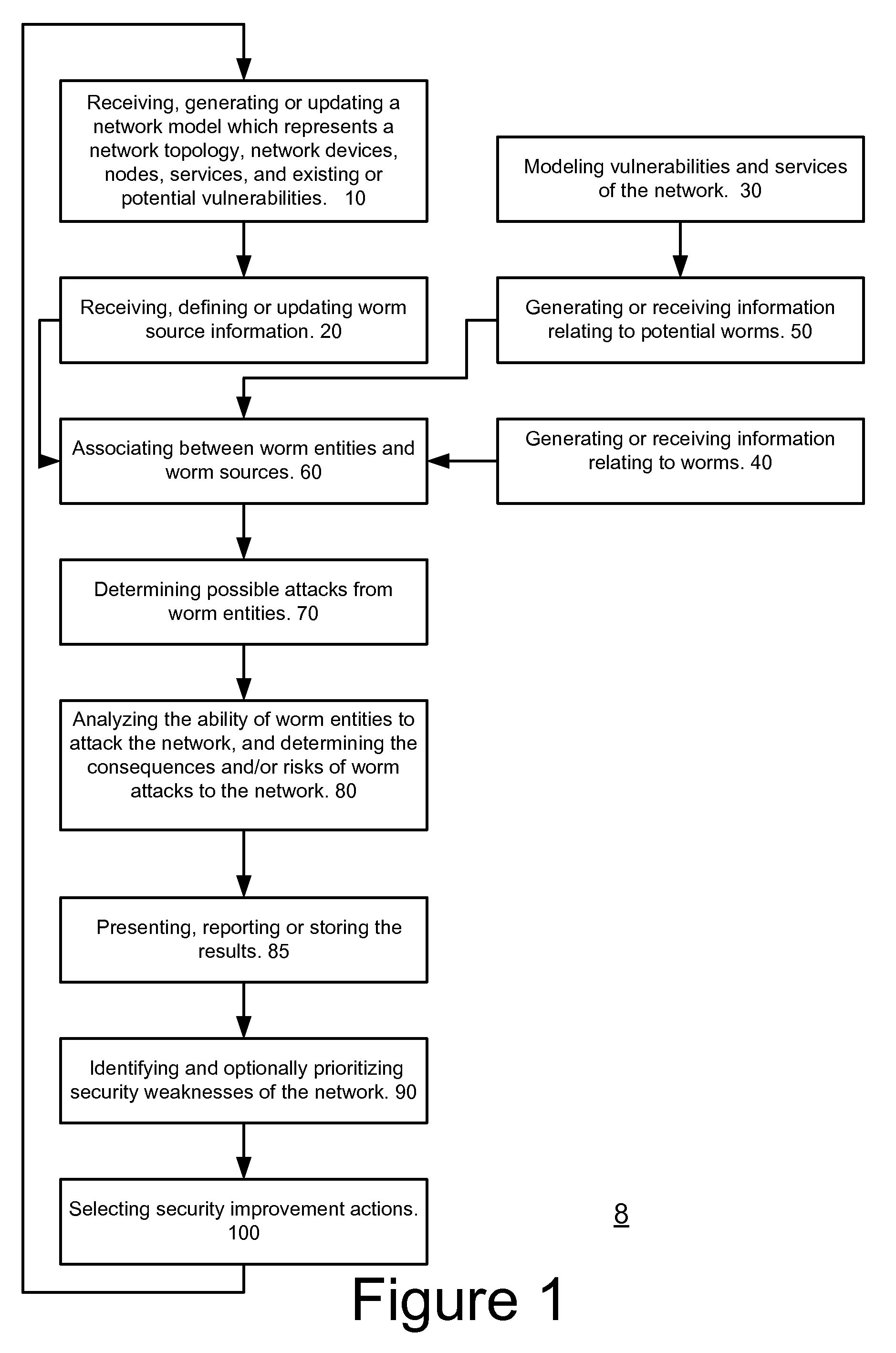
System, method and computer readable medium for evaluating potential attacks of worms
ActiveUS20080005555A1Good attackMemory loss protectionUnauthorized memory use protectionSecurity metricSystems approaches
A method for evaluating potential attacks of worms, the method includes: associating, in response to information representative of a network and of worm entities, between worm entities and potential worm sources to provide associated worm sources; determining potential worm attacks that start from the associated worm sources; and evaluating at least one potential worm attack security metric associated with the potential worm attacks.
Owner:SKYBOX SECURITY
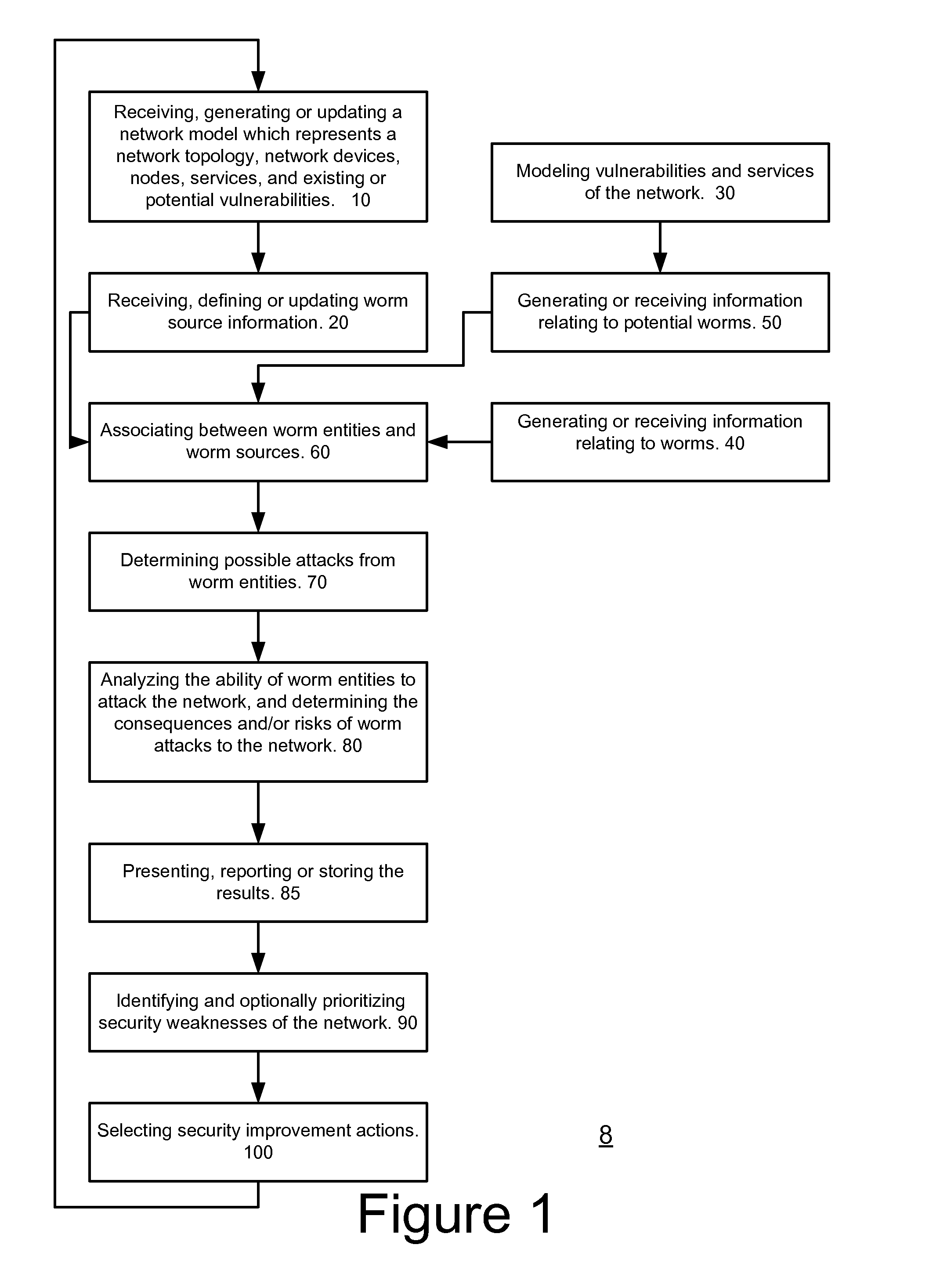
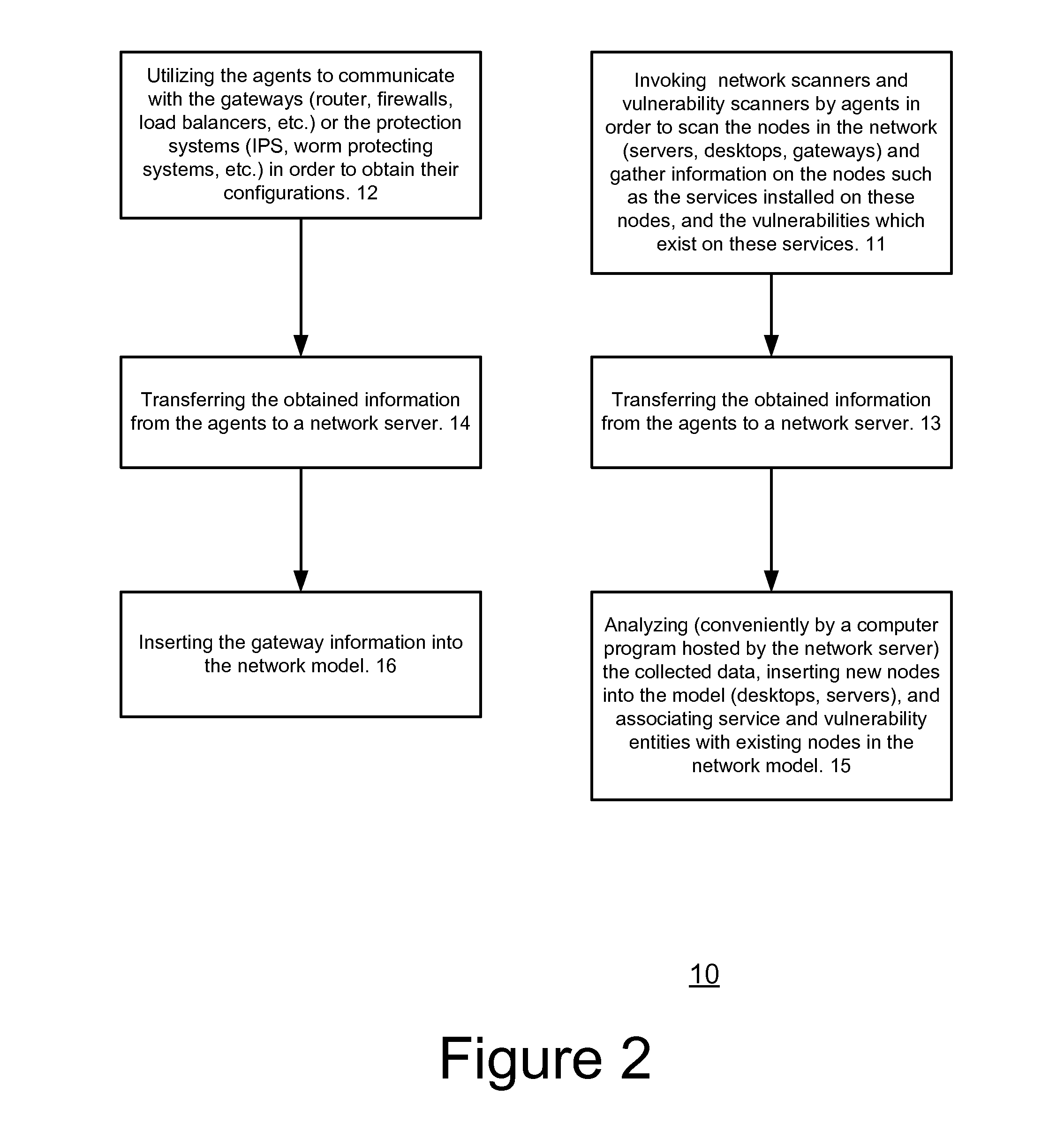
System, method and computer readable medium for evaluating potential attacks of worms
ActiveUS8359650B2Memory loss protectionUnauthorized memory use protectionSecurity metricComputer security
A method for evaluating potential attacks of worms, the method includes: associating, in response to information representative of a network and of worm entities, between worm entities and potential worm sources to provide associated worm sources; determining potential worm attacks that start from the associated worm sources; and evaluating at least one potential worm attack security metric associated with the potential worm attacks.
Owner:SKYBOX SECURITY
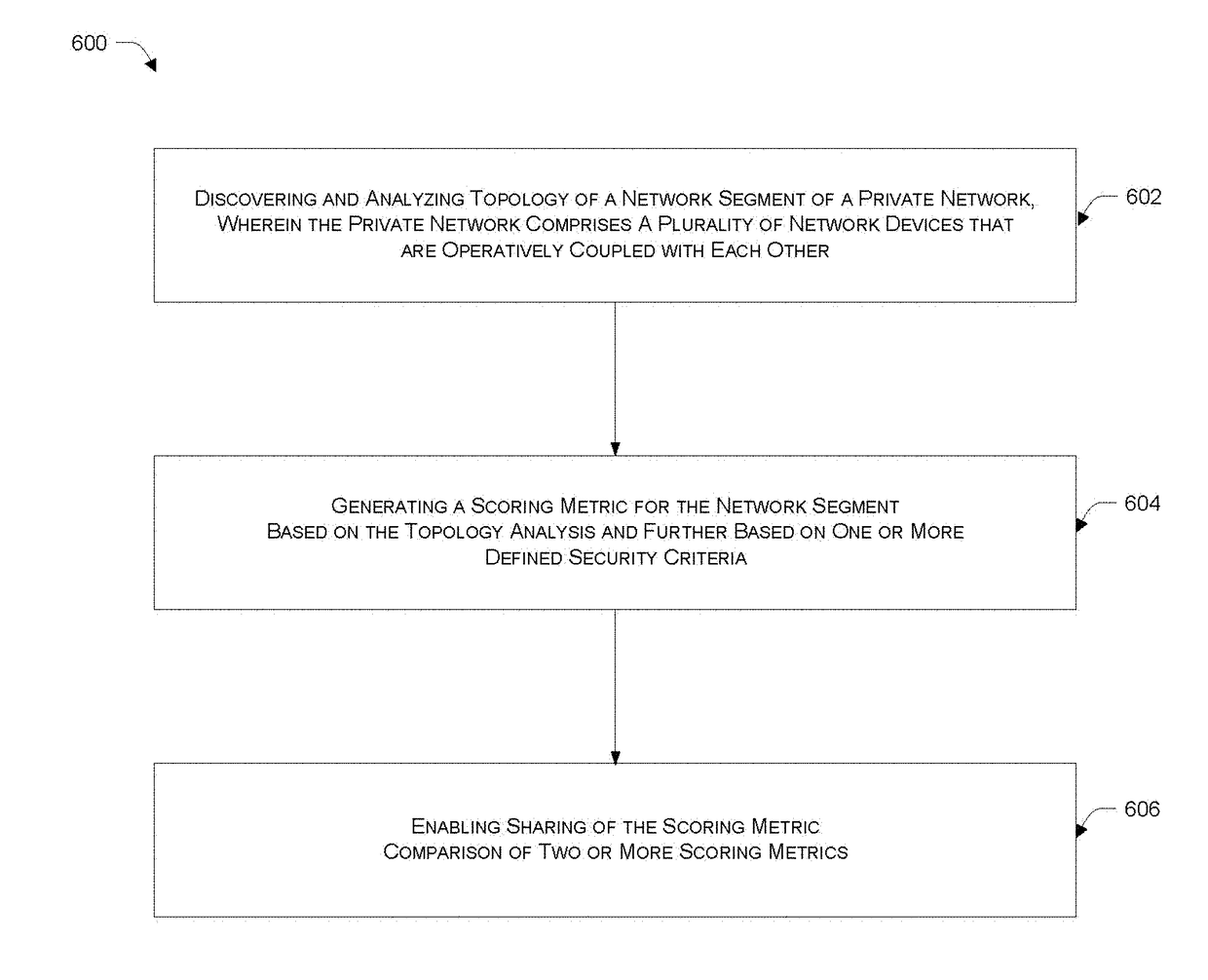
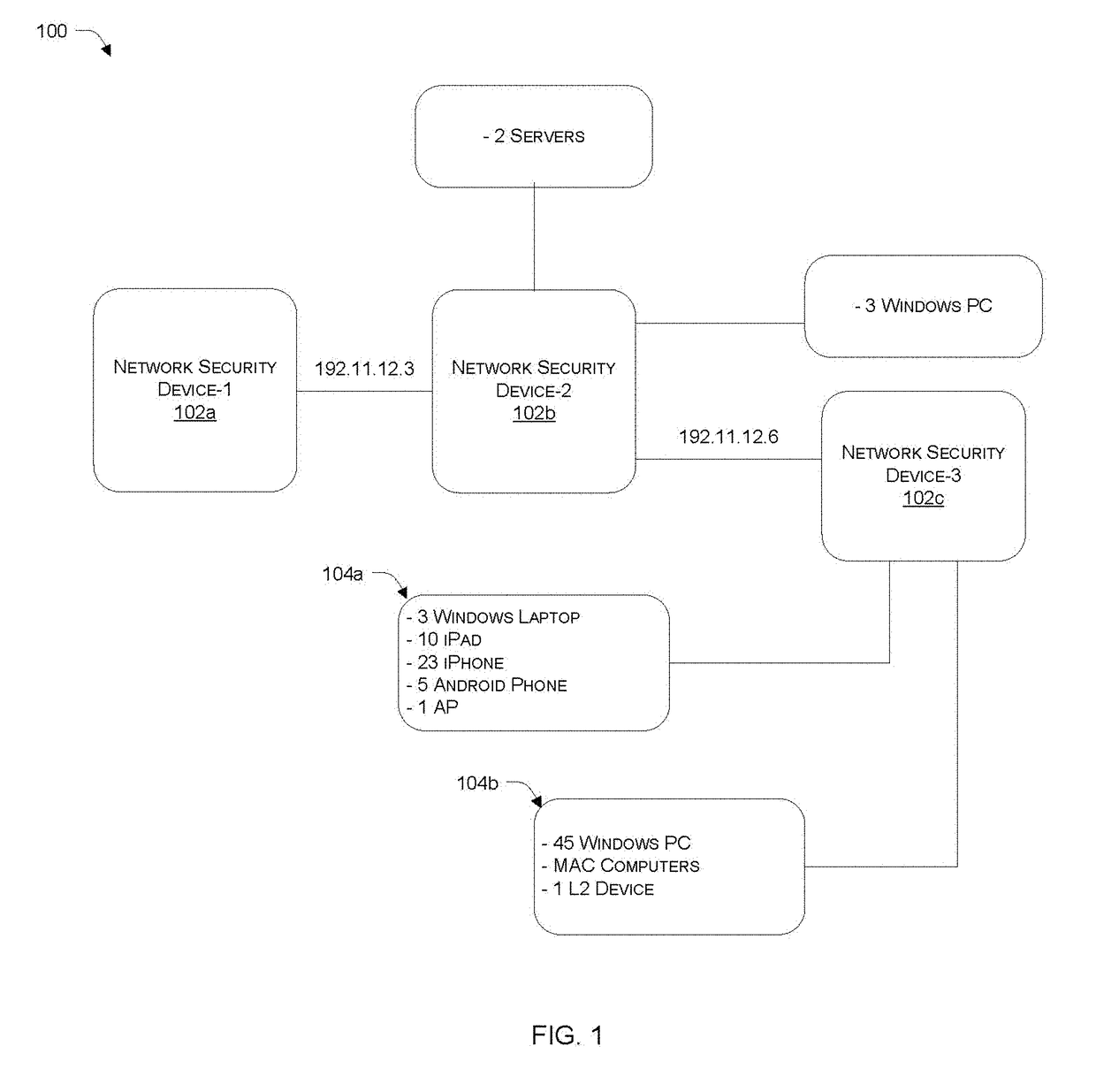
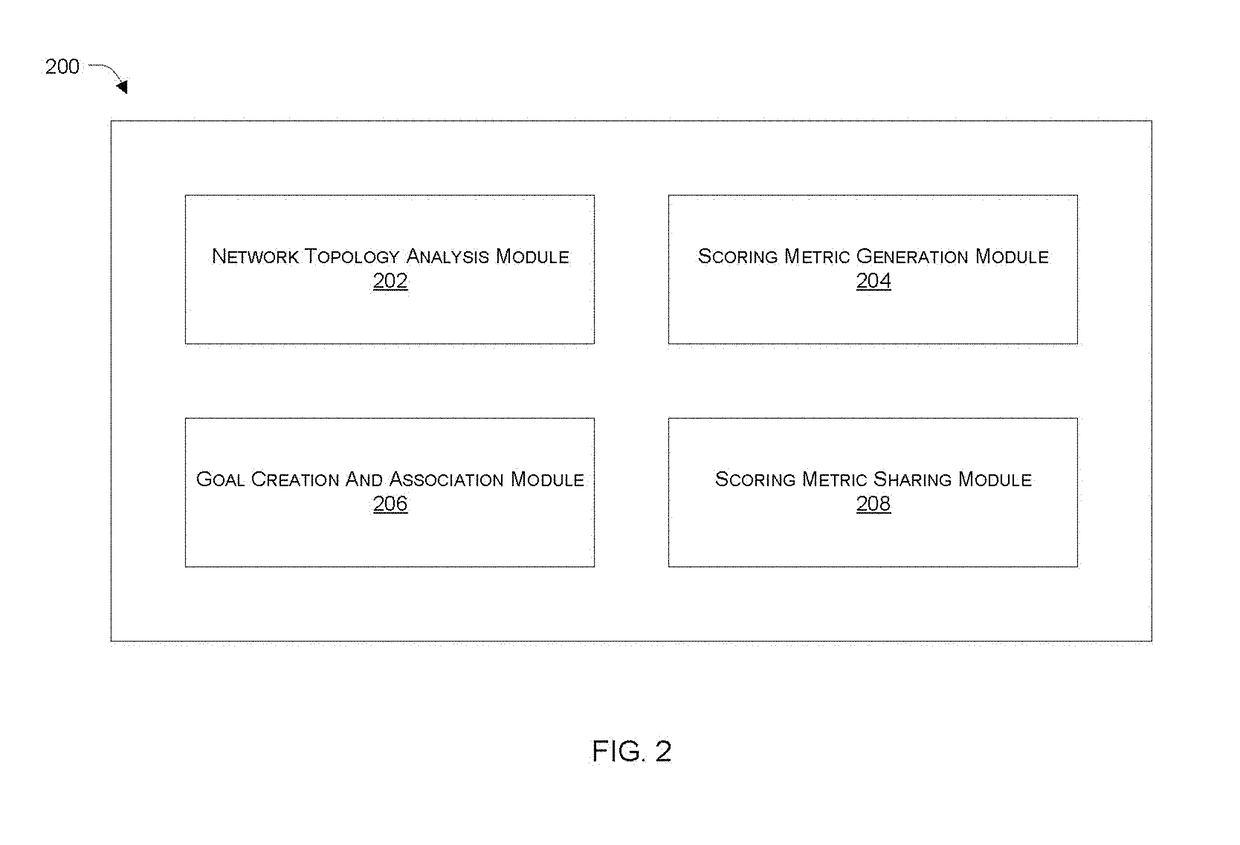
Network security framework based scoring metric generation and sharing
Systems and methods are described for analysing, sharing and comparing security configurations. According to one embodiment, a security metric for a network segment of a private network is generated based on determination and analysis of network assets, network topology, and one or more defined security criteria representing security features being implemented by one or more network security devices that form part of the network segment, wherein the scoring metric is a quantitative representation of protection level and / or exposure level of the network segment. In an embodiment, the security metric can be shared and compared with security metrics of other network segments.
Owner:FORTINET
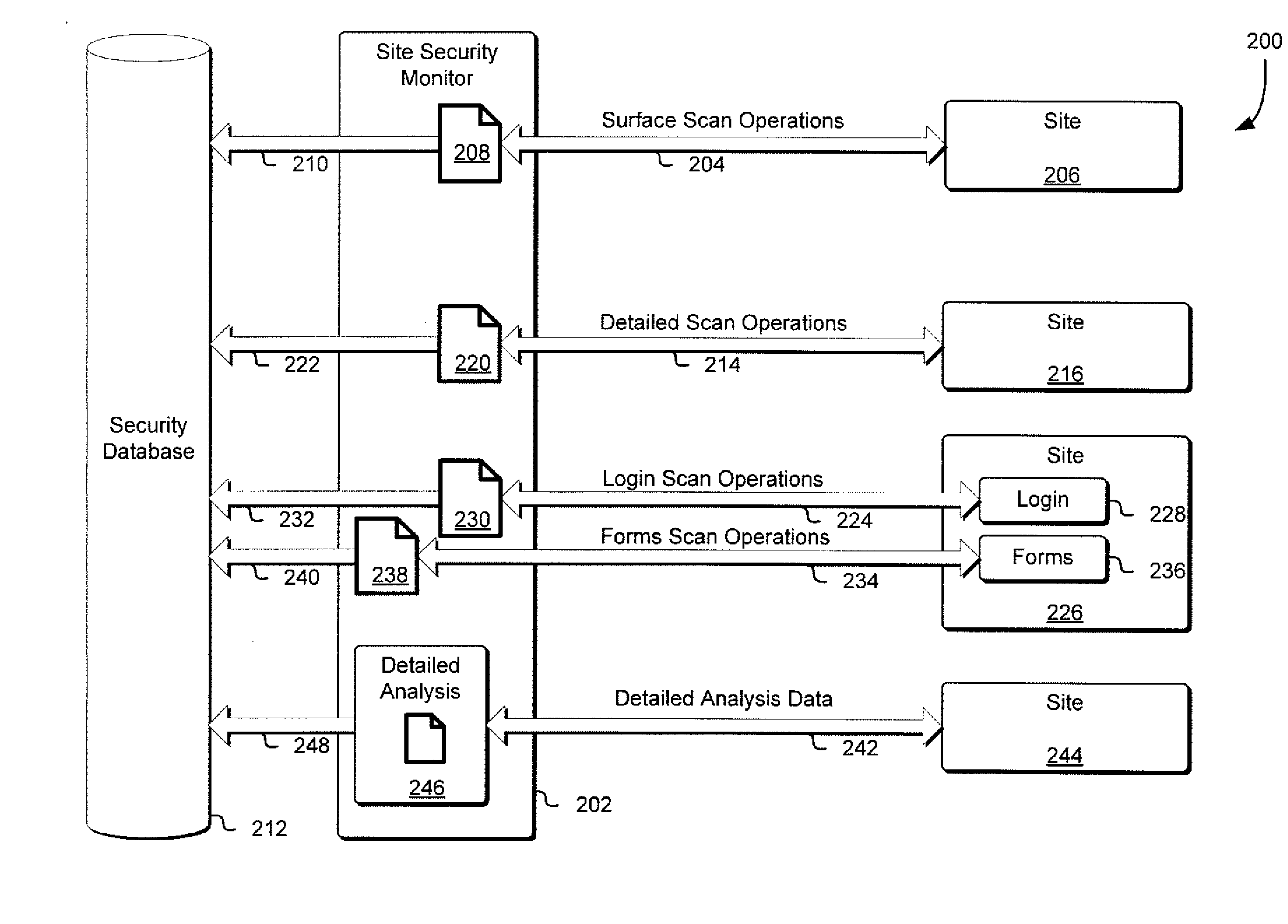
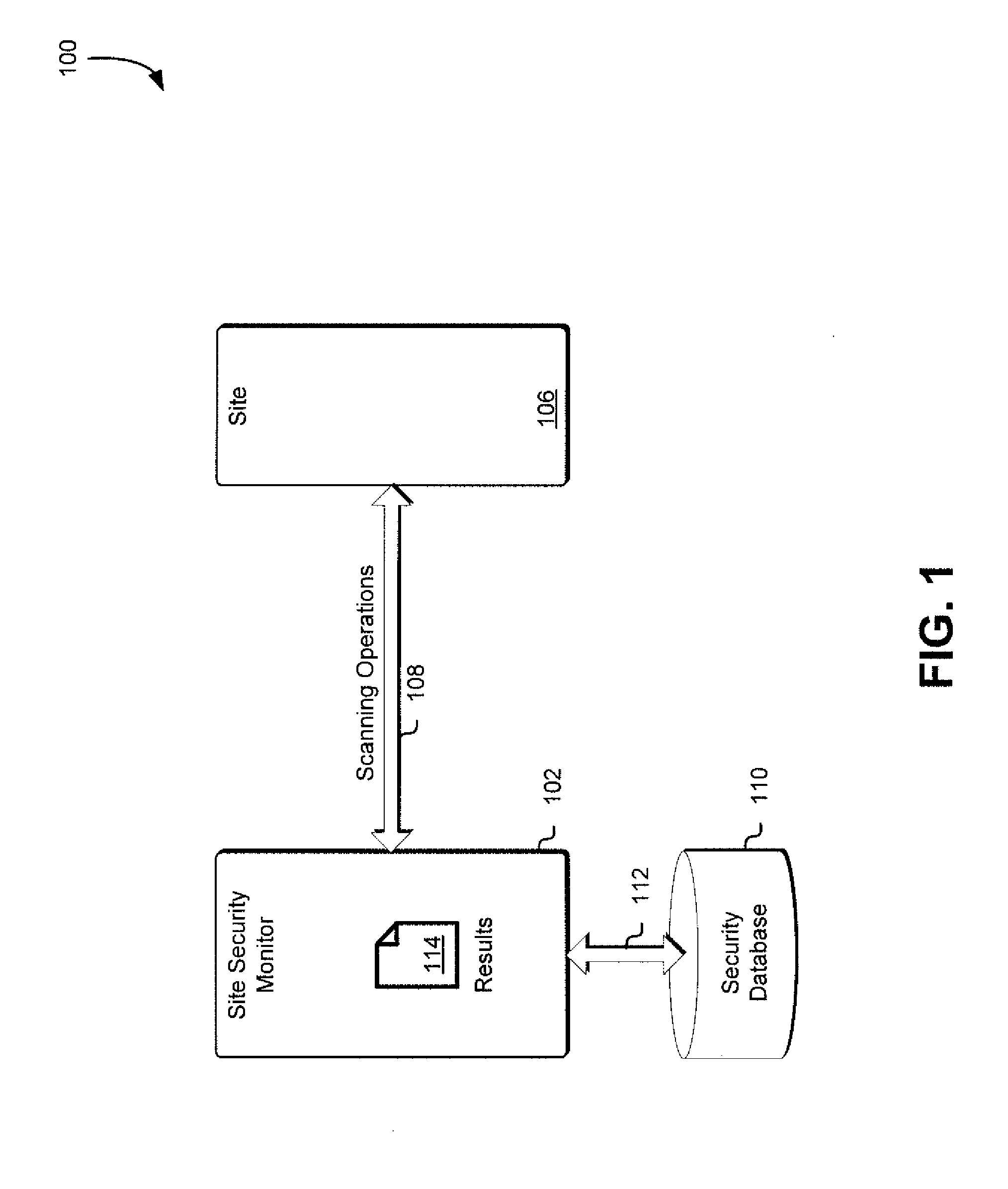
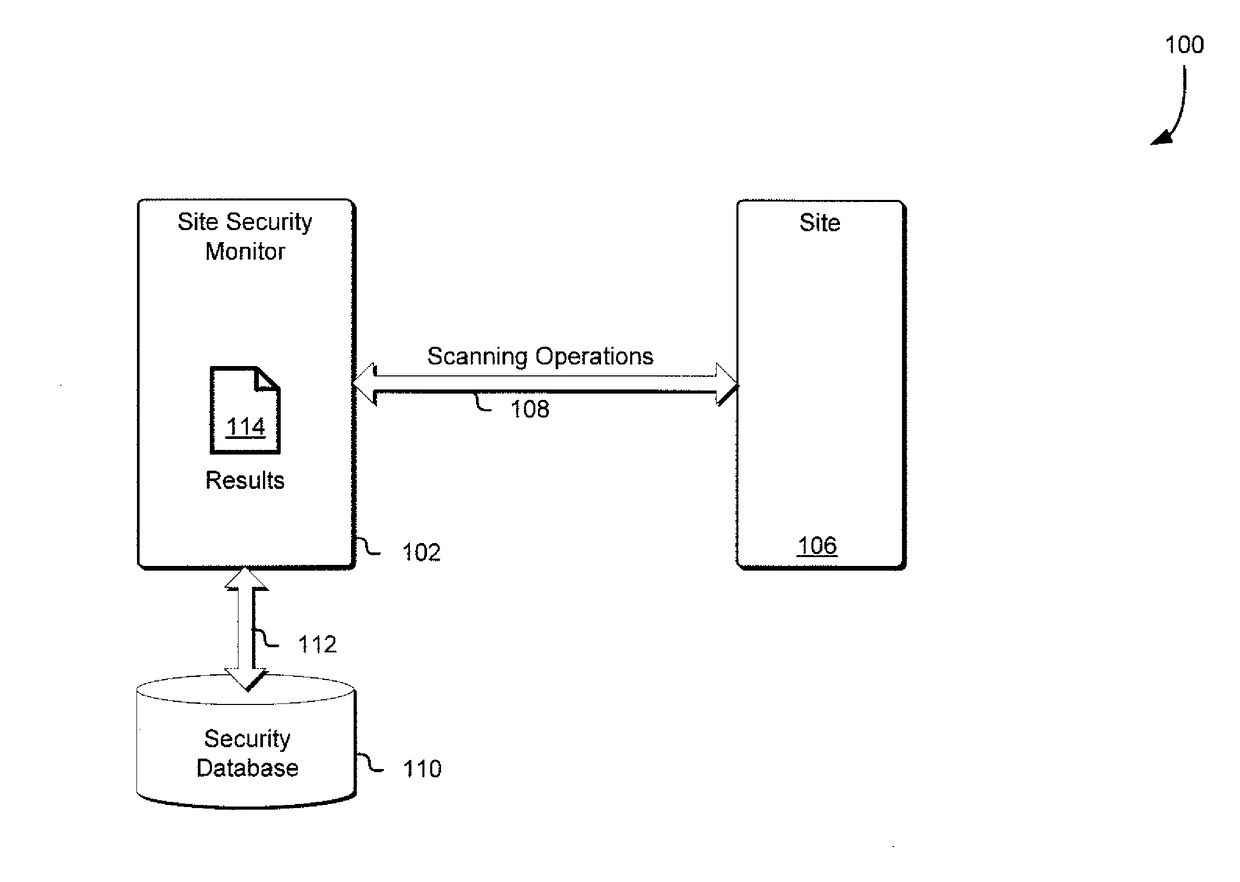
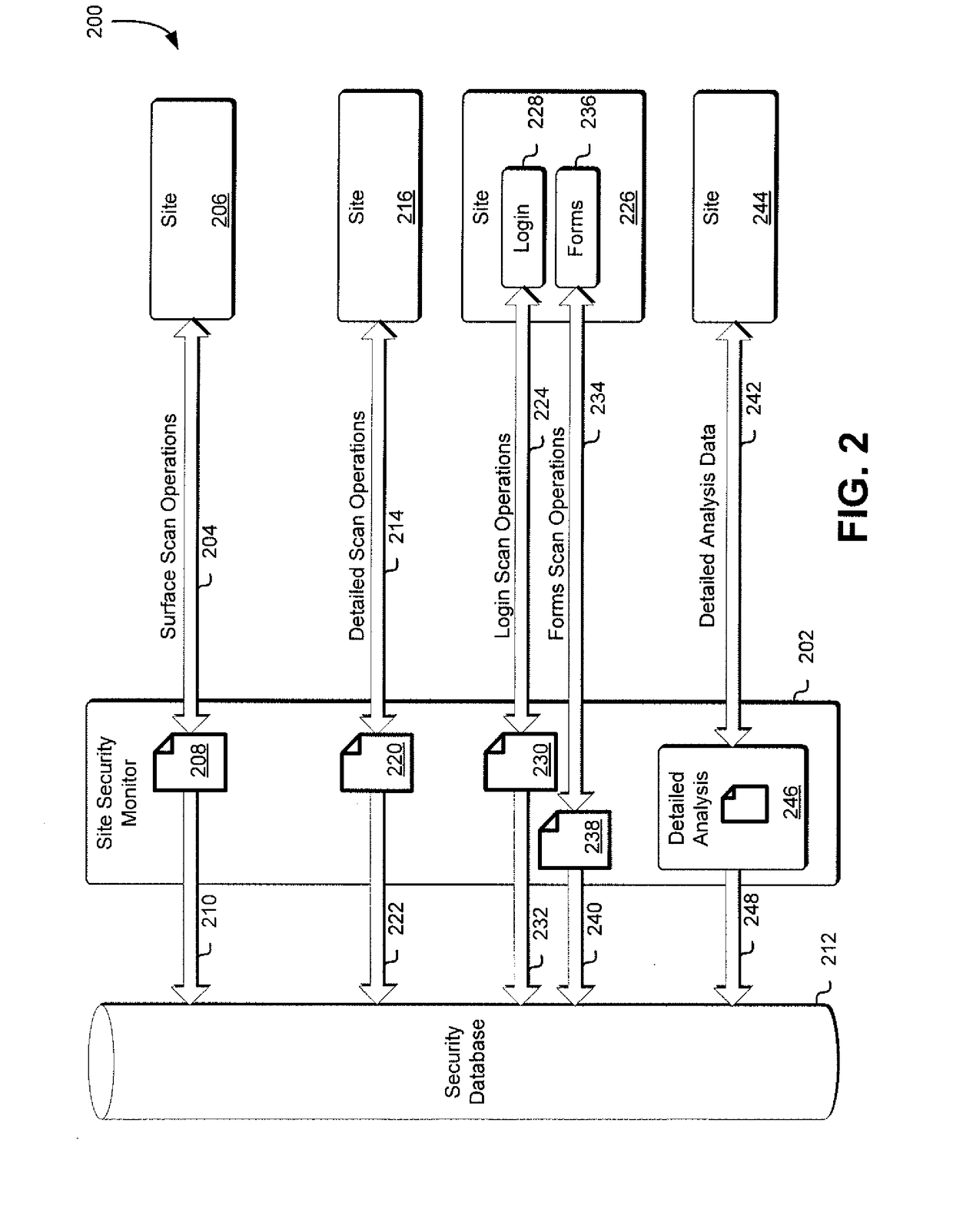
Site security monitor
Techniques for monitoring site security are disclosed herein. Sites are scanned for security metric values associated with one or more security metrics. Normalized values for those scanned security metric values are calculated based on previously obtained values associated with one or more other security metrics associated with other scanned sites. Site security metrics are then calculated for the sites based on a subset of the normalized values and based at least in part on a comparison to other scanned sites.
Owner:SYNOPSYS INC
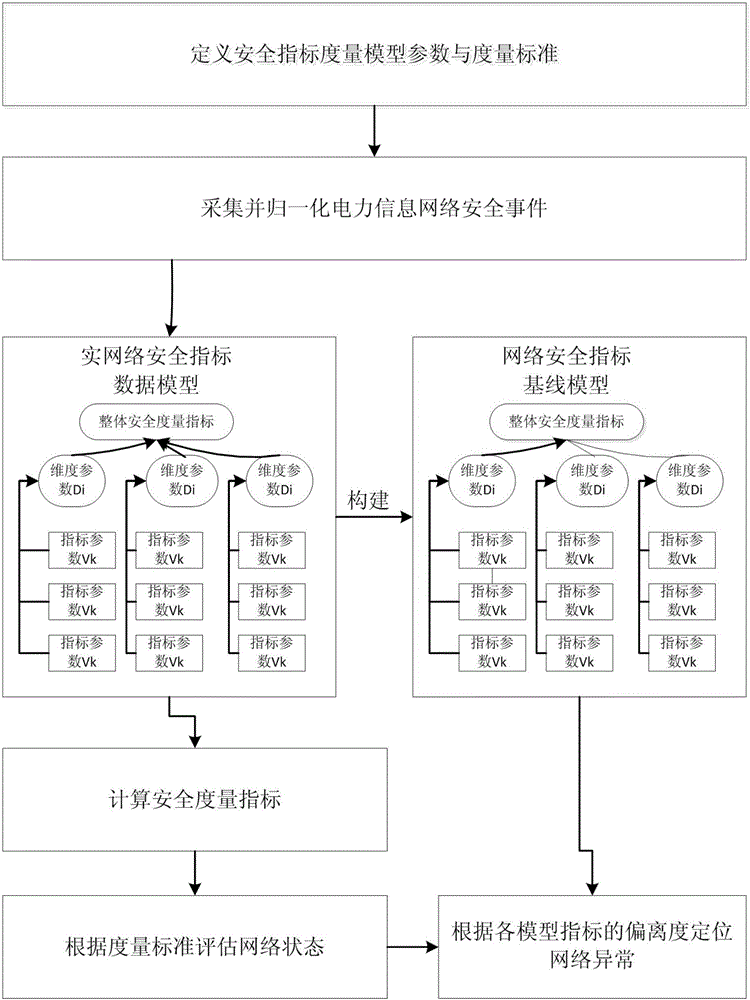
Electric power information network security measuring method based on security log data mining
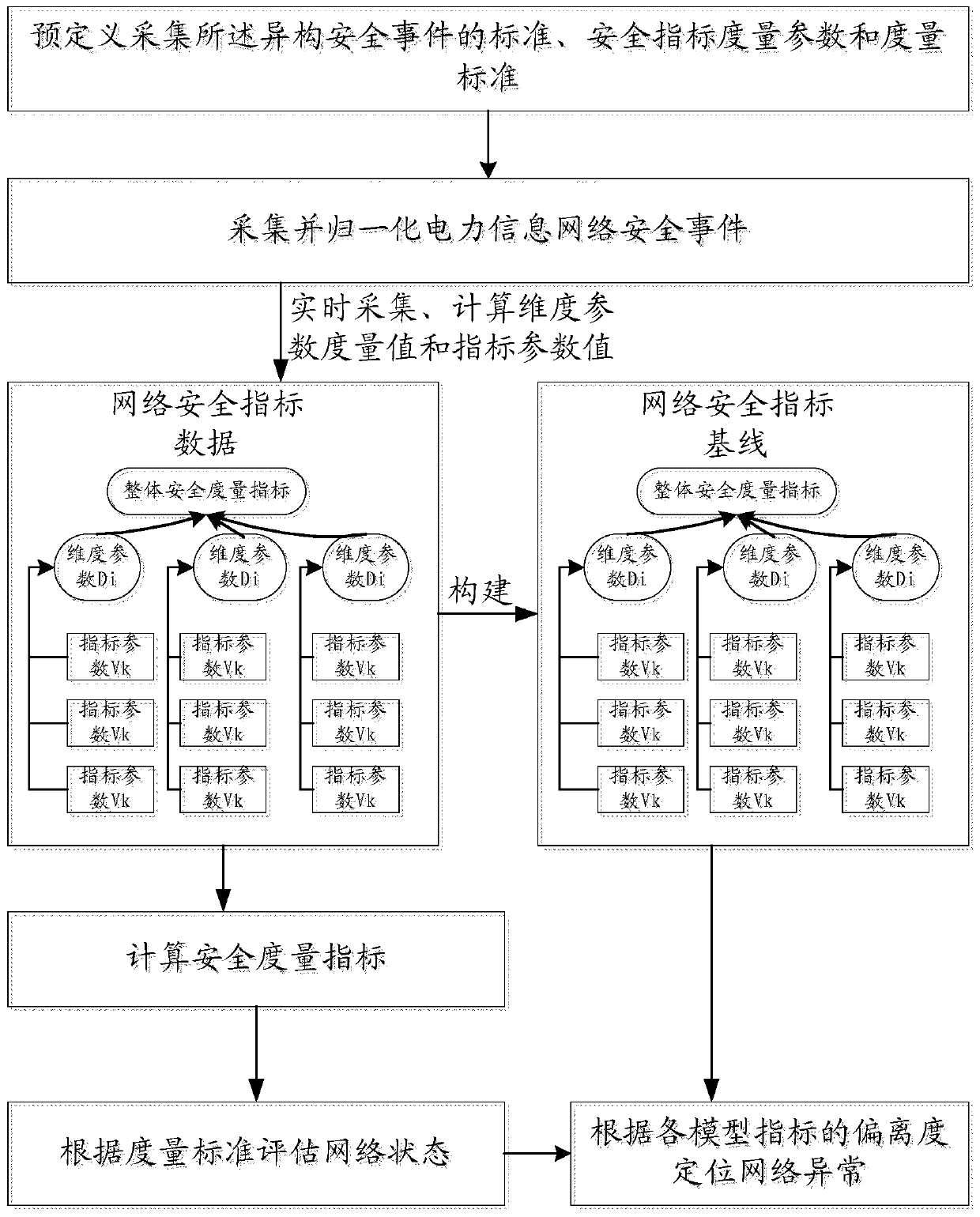
The invention provides an electric power information network security measuring method based on security log data mining. The electric power information network security measuring method comprises the steps of defining a security index measurement model parameter and a measurement standard; acquiring electric power information network heterogeneous security events, normalizing the security events by means of an extensible security event standard format which is defined based on a template, and buffering the security events, thereby forming standard security events; in mass standard security events, grouping the security events according to a dimension parameter Di, extracting a parameter which reflect network safety operation condition according to an index parameter Vk, and obtaining a real-time network security index data model; dynamically updating the network security index data baseline model according to fitting between the network security index historical data and the network security index real-time data; calculating a network security measurement index; and obtaining a network abnormity position through the network security measurement index. The electric power information network security measuring method settles the technical problems such as low accuracy, low efficiency and no effective facility for performing security problem positioning in prior art.
Owner:GUIZHOU POWER GRID INFORMATION & TELECOMM
Reporting and Management of Computer Systems and Data Sources
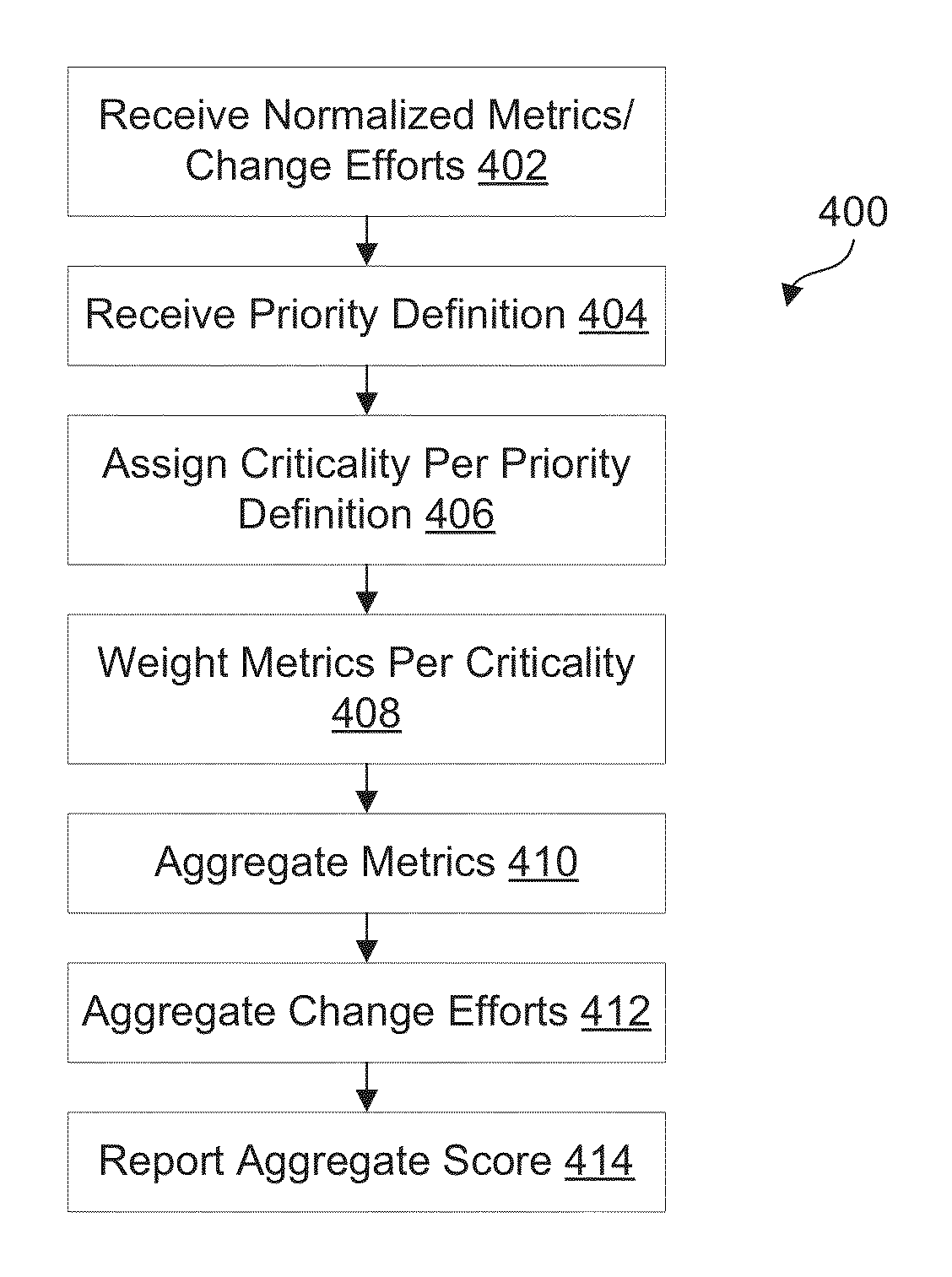
A system and method are provided for managing data, such as for example security or other business data. For the example of security data, security data is received from a plurality of assets that may or may not be remotely located. A plurality of security metrics are computed and normalized according to thresholds. Security metrics are aggregated to generate an aggregate score, this may include weighting the metrics according to metric priorities. A change effort corresponding to each metric is also received and a corresponding change effort for the aggregate score is calculated. Aggregate scores and aggregate change efforts are analyzed to generate risk reduction recommendations. Upon instruction, metrics corresponding to an aggregate score may be displayed including recommendations of metrics for risk reduction. The recommended metrics may be selected according to analysis of change-to-effort ratios for the metrics.
Owner:WALMART APOLLO LLC
An attack detection method oriented to network system security metrics
The invention relates to an attack detection method oriented to network system security metrics, which relates to the network security field. From the network system itself, and starting from networksystem security metrics, by establishing a baseline of network information system security utility, by measuring and evaluating the identification characteristic, traffic characteristic and utility influence of network system, comparing the actual utility with the expected utility, we can find the abnormity of network system, detect and discover the network attack in time, make up the deficiency of detection based on attack characteristic, and improve the veracity of attack detection. By effectively using metrics in a network system environment, a suitable set of metric is selected and data iscollected in a real project according to that set of metrics, According to the collected data to determine whether a network attack has occurred, through the use of network system measurement resultsto provide decision-making support for the detection of network attacks, for the evaluation object to actively find security issues, detection and judgment of network attacks to provide a basis.
Owner:BEIJING INST OF COMP TECH & APPL
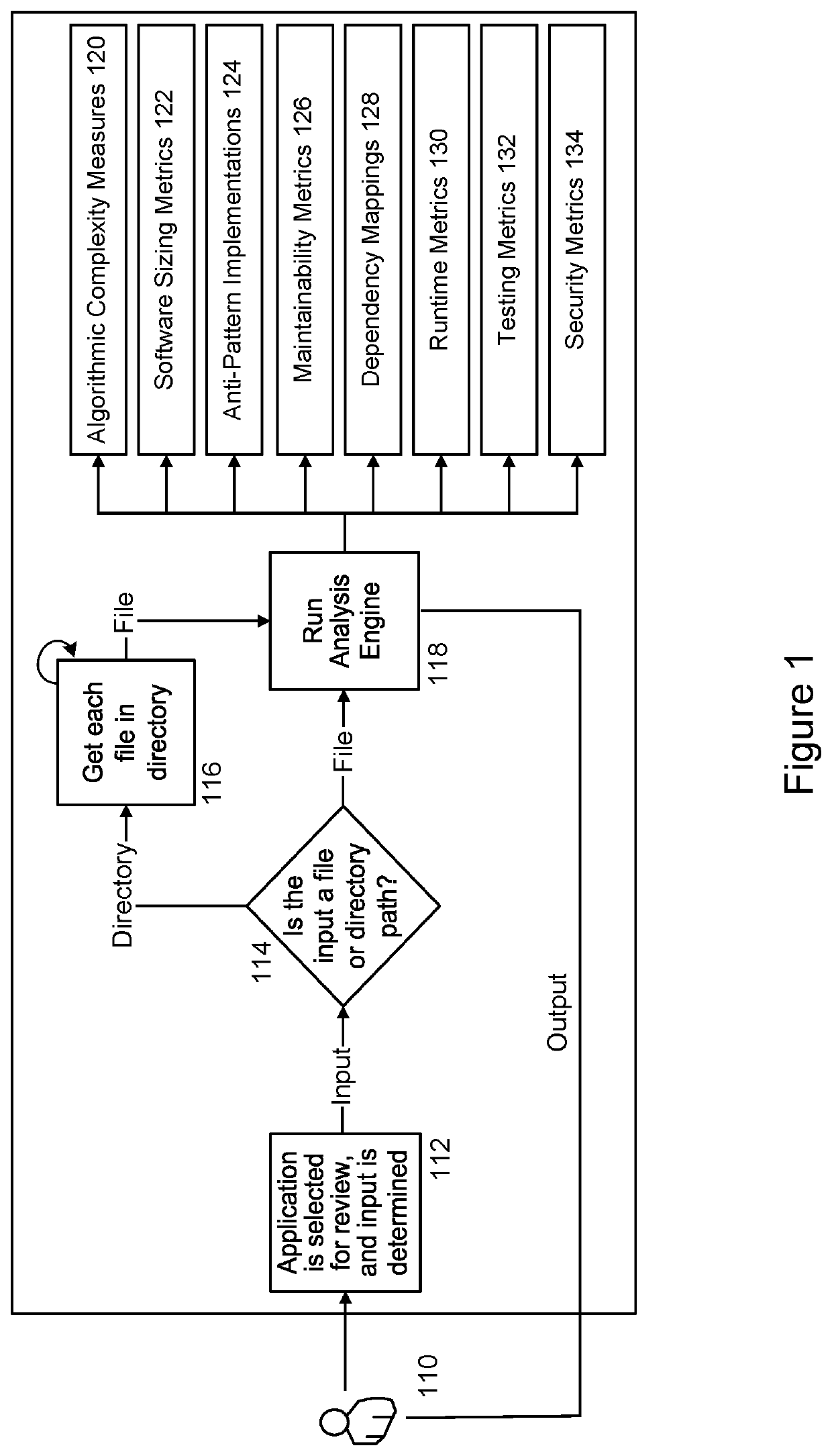
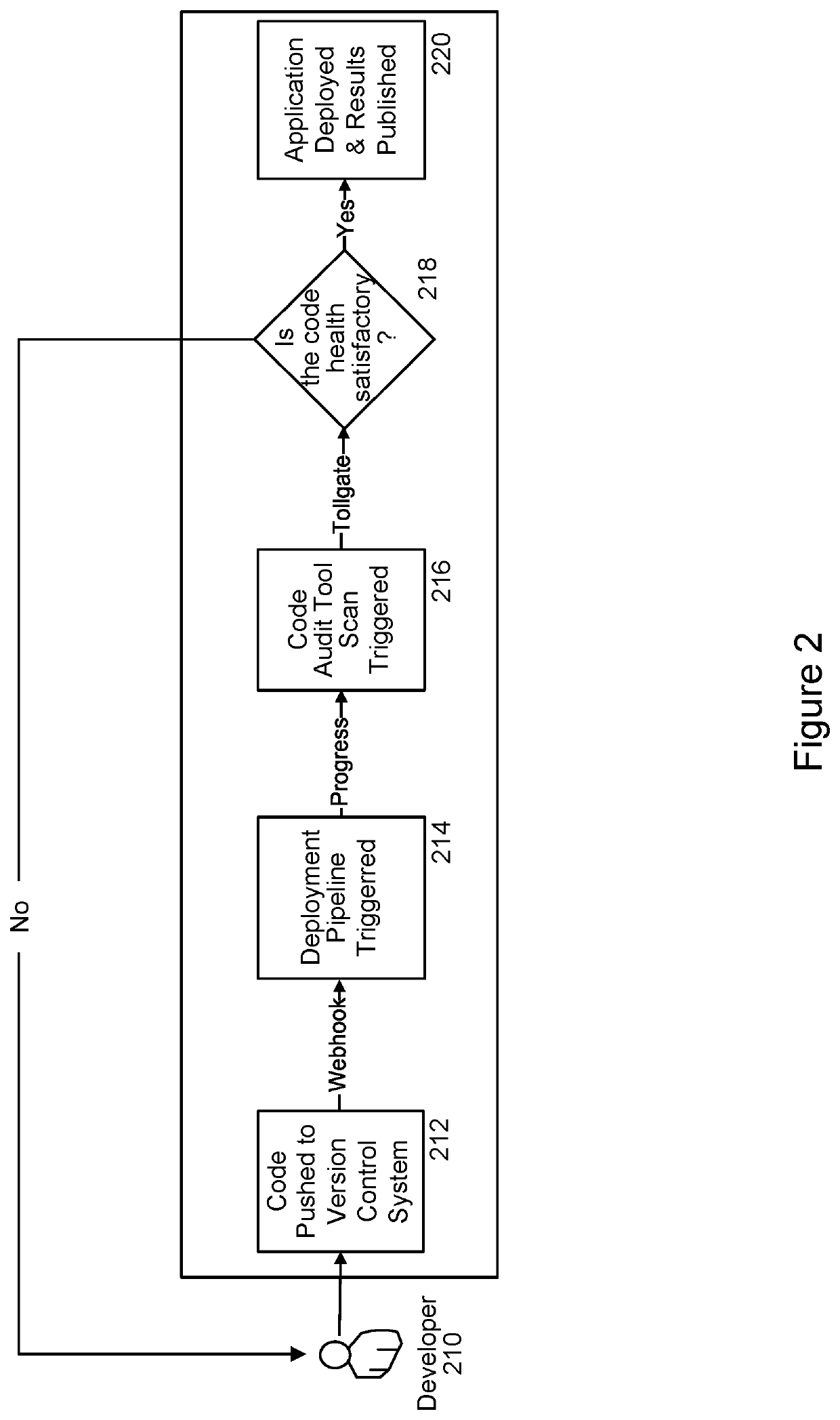
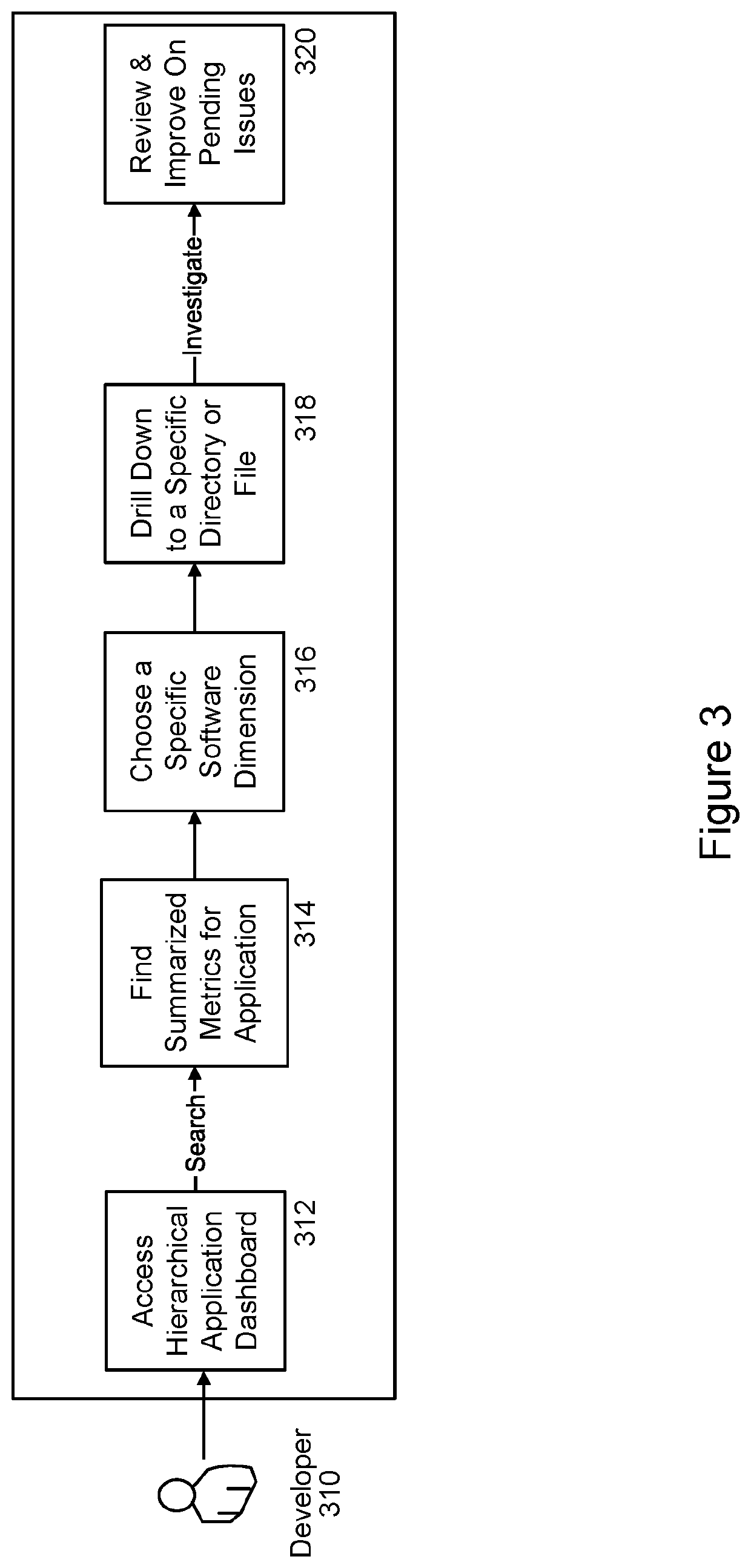
System and method for implementing a code audit tool
PendingUS20210406004A1Improve code health determinationGood for healthReverse engineeringSoftware metricsSecurity metricMaintainability
An embodiment of the present invention is directed to a code audit tool that intelligently analyzes and profiles code, such as Python code, based on a variety of previously unmeasured factors and metrics including a set of software dimensions, such as Algorithmic Complexities; Software Sizing Metrics; Anti-Pattern Implementations; Maintainability Metrics; Dependency Mappings; Runtime Metrics; Testing Metrics; and Security Metrics. Once this analysis is complete, a standardized report card or other scoring interface may be generated. This may include analytical findings as well as suggestions and recommend steps so that developers can make informed decisions, enhance their code bases and improve the score assigned to their code.
Owner:JPMORGAN CHASE BANK NA
Efficient prevention of fraud
InactiveCN105210092ADigital data authenticationDigital video signal modificationSecurity metricSecurity Measure
This disclosure is directed to methods and systems for managing difficulty of use and security for a transaction. A transaction manager operating on a computing device may determine a range of possible steps for a transaction comprising security measures available for the transaction. The transaction manager may identify a threshold for a security metric to be exceeded for authorizing the transaction, the security metric to be determined based on performance of steps selected for the transaction. The transaction manager may select for the transaction at least one step from the range of possible steps, based on optimizing between (i) a difficulty of use quotient of the transaction from subjecting a user to the at least one step, and (ii) the security metric relative to the determined threshold.
Owner:EYELOCK
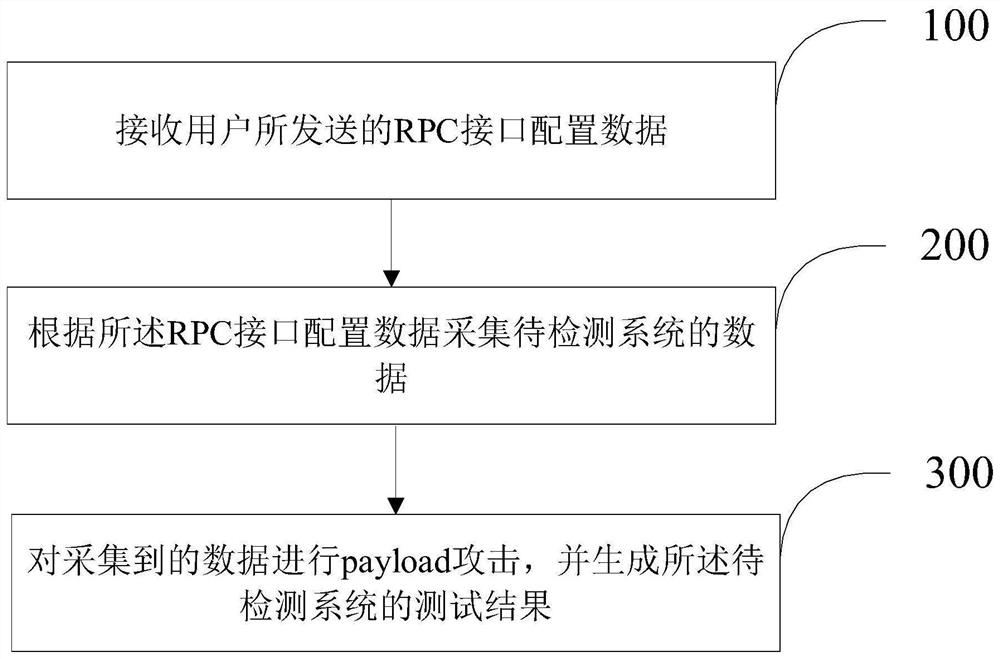
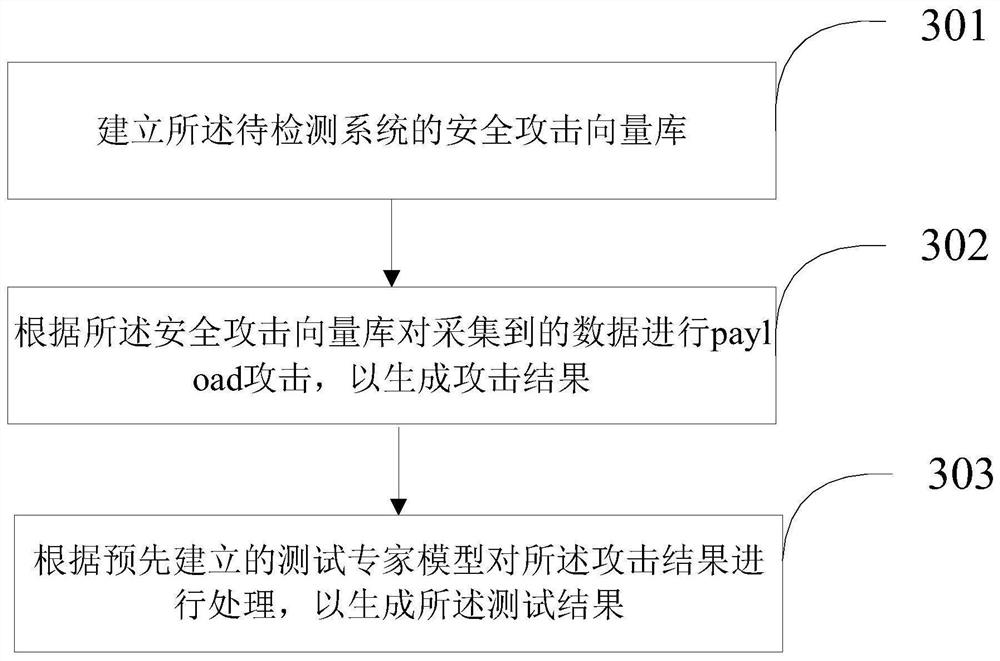
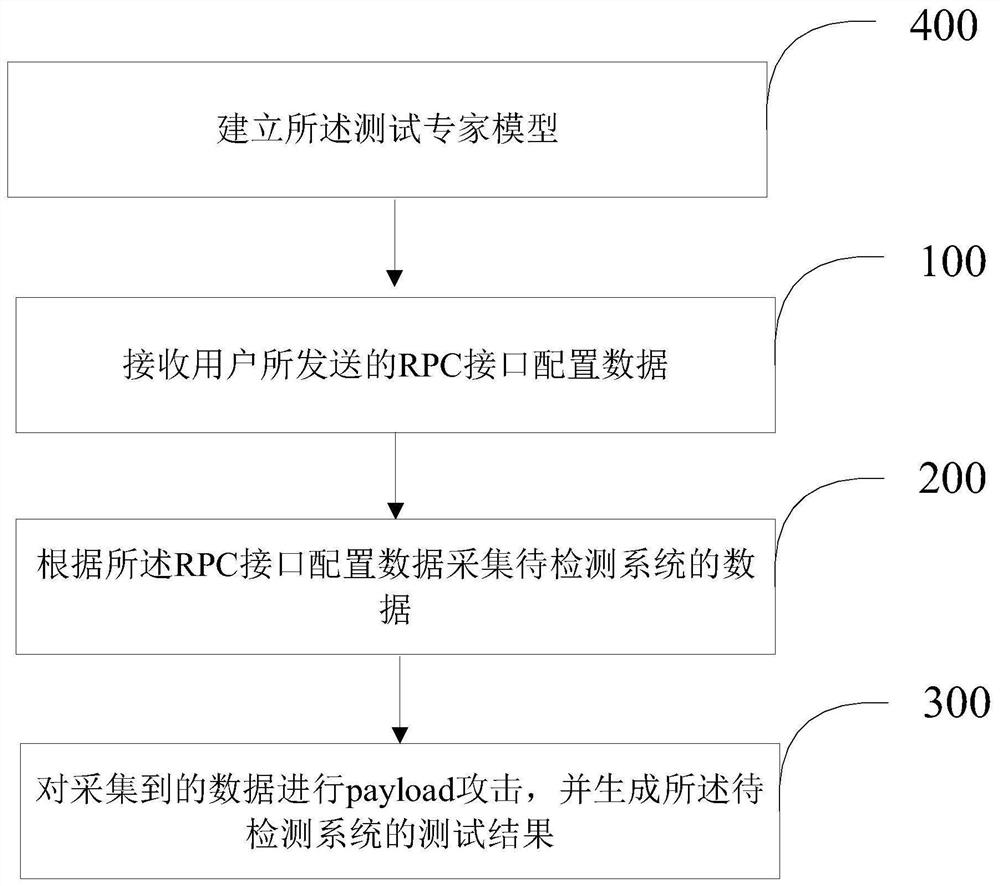
Vulnerability detection method and device based on background RPC interface
PendingCN113569255AReduce false alarm rateLowering the Barriers to Safety TestingPlatform integrity maintainanceTransmissionSecurity metricAttack
The invention belongs to the technical field of big data, and provides a vulnerability detection method and device based on a background RPC interface, and the method comprises the steps: receiving RPC interface configuration data sent by a user; collecting data of a to-be-detected system according to the RPC interface configuration data; and carrying out a payload attack on the collected data, and generating a test result of the to-be-detected system. According to the method and device, the security test threshold can be greatly reduced, manual test by development testers is not needed, the security index condition of the system, finer-grained vulnerability description, specific vulnerability detailed information and a vulnerability rectification scheme can be obtained, the obtained data can be subjected to overall data analysis and data mining, and manual inspection and analysis of the security vulnerability test are not needed.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
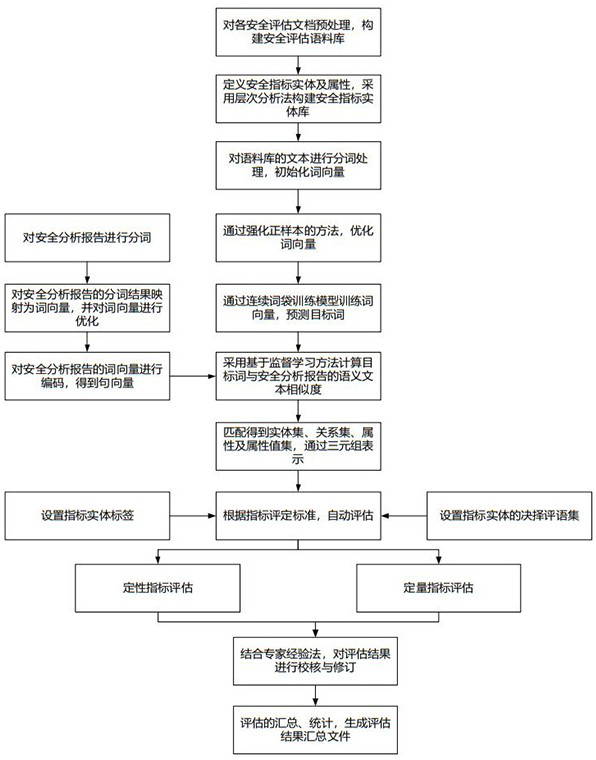
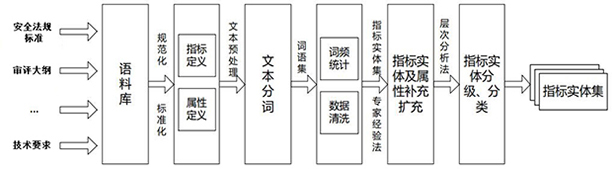
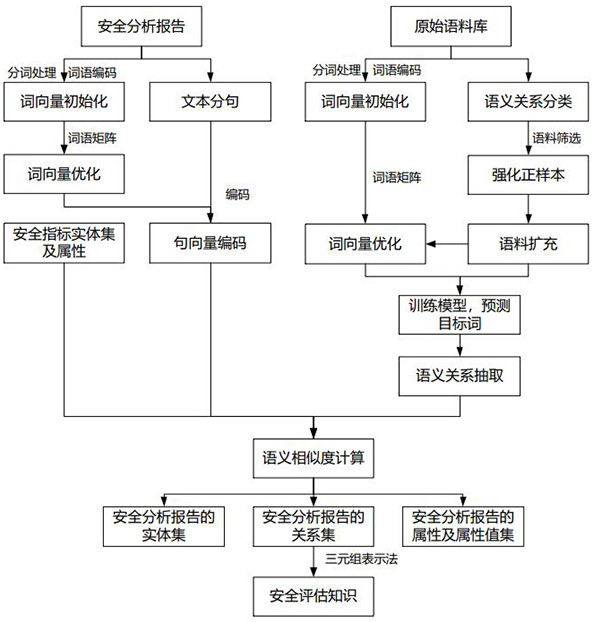
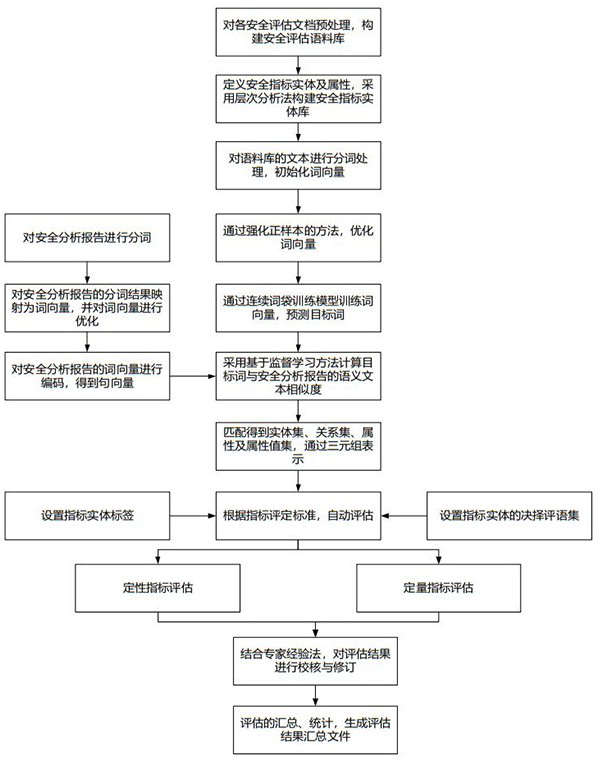
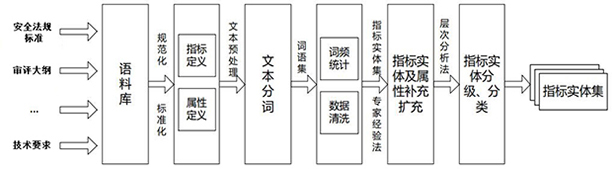
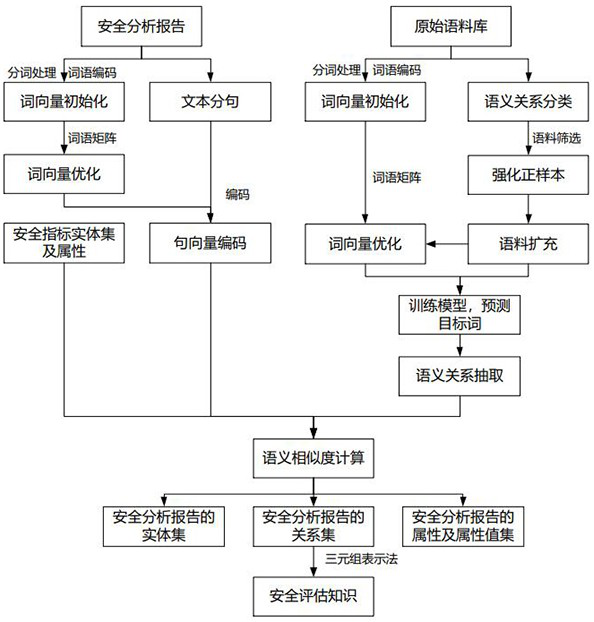
Security analysis and automatic evaluation method based on index threshold value and semantic analysis
The invention discloses a safety analysis and automatic evaluation method based on an index threshold value and semantic analysis. The method comprises the following steps: firstly, extracting a semantic relationship from an unstructured security analysis report, a regulation standard and other security analysis original corpus, and constructing a normalized security knowledge base; meanwhile, a safety index entity set is constructed according to the dimensions of activities, items and the like, and the safety index set is classified and divided in a layered mode; based on a semantic similarity calculation method, safety index entities and threshold attributes are identified and extracted from corpora such as regulatory standards, technical requirements and judgment bases, and the safety index entities and monitoring data attributes can be identified and extracted from a safety analysis report; and according to a semantic analysis result, automatic benchmarking and judgment can be carried out on a safety index satisfaction condition, and an expert experience method can be combined to carry out re-checking on an index initial judgment result. According to the method, the requirements of users on rapid, accurate and intelligent safety analysis and automatic evaluation of different activities and items are met, and the safety evaluation efficiency and accuracy can be effectively improved.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
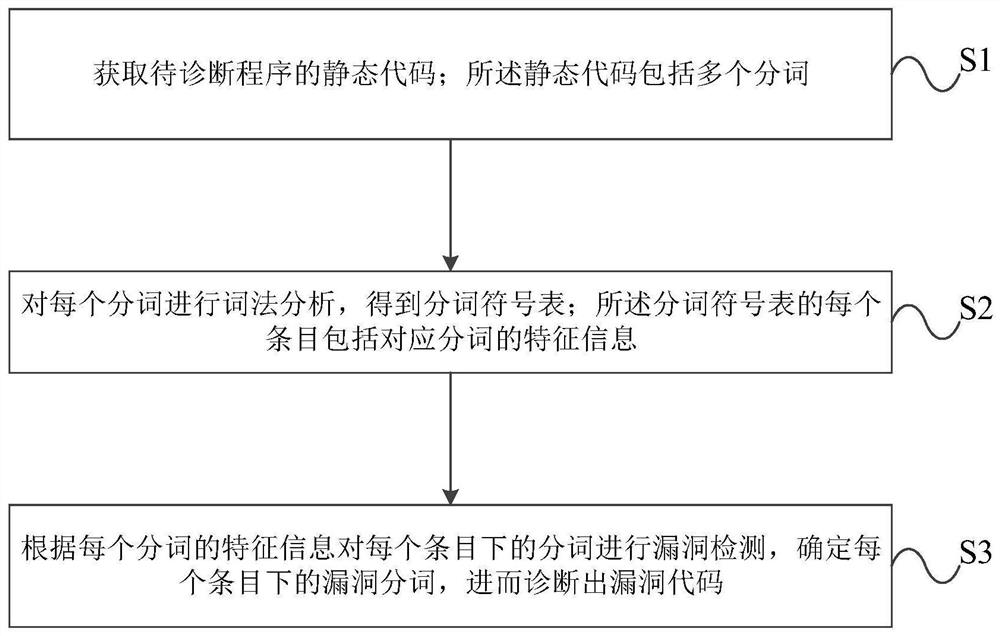
Static code security diagnosis method and device
PendingCN112464237ACharacter and pattern recognitionNatural language data processingDiagnostic programSecurity metric
A static code security diagnosis method and device provided by the embodiment of the invention can be applied to the technical field of information security. The method comprises the steps of obtaining a static code of a to-be-diagnosed program; performing lexical analysis on each segmented word to obtain a segmented word symbol table; and performing vulnerability detection on the segmented wordsunder each entry according to the feature information of each segmented word, determining vulnerability segmented words under each entry, and further diagnosing vulnerability codes. On the basis of atext analysis technology, a lexical analyzer is constructed, lexical analysis is carried out on static codes to obtain a symbol table corresponding to the codes, and under the condition that developers do not need to carry out manual operation, the security index condition of application codes, finer-grained vulnerability description, specific vulnerability detailed information and a vulnerabilityrectification scheme are obtained, the obtained data can be subjected to vulnerability overall data analysis and data mining, and security code vulnerability test inspection and analysis do not needto be conducted manually.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
System and method for predicting failure in a power system in real-time
PendingUS20220308573A1Data processing applicationsContigency dealing ac circuit arrangementsSecurity metricElectric power system
A system and a method for predicting failure in a power system in real-time. The method comprises obtaining, by a processing unit, state estimation data corresponding to electrical quantities of the power system received from one or more sources in real-time, extracting a feature vector from the received state estimation data based on contingency analysis information using a trained machine learning model, wherein the feature vector corresponds to one or more parameters pertaining to the power system in real-time, determining a security index for the received state estimation data based on the extracted feature vector using the trained machine learning model and, predicting a failure of the power system based on the determined security index.
Owner:SIEMENS AG
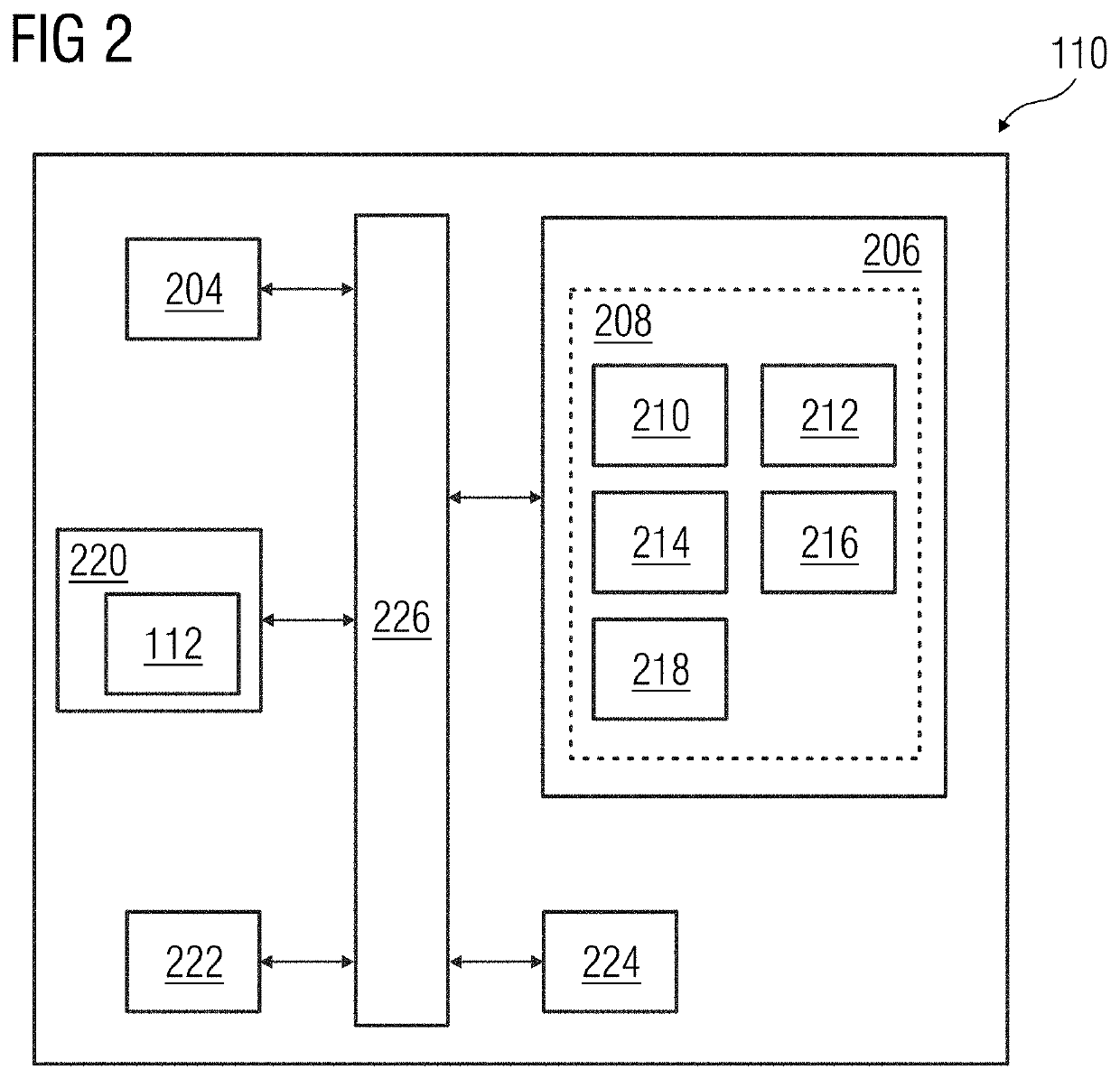
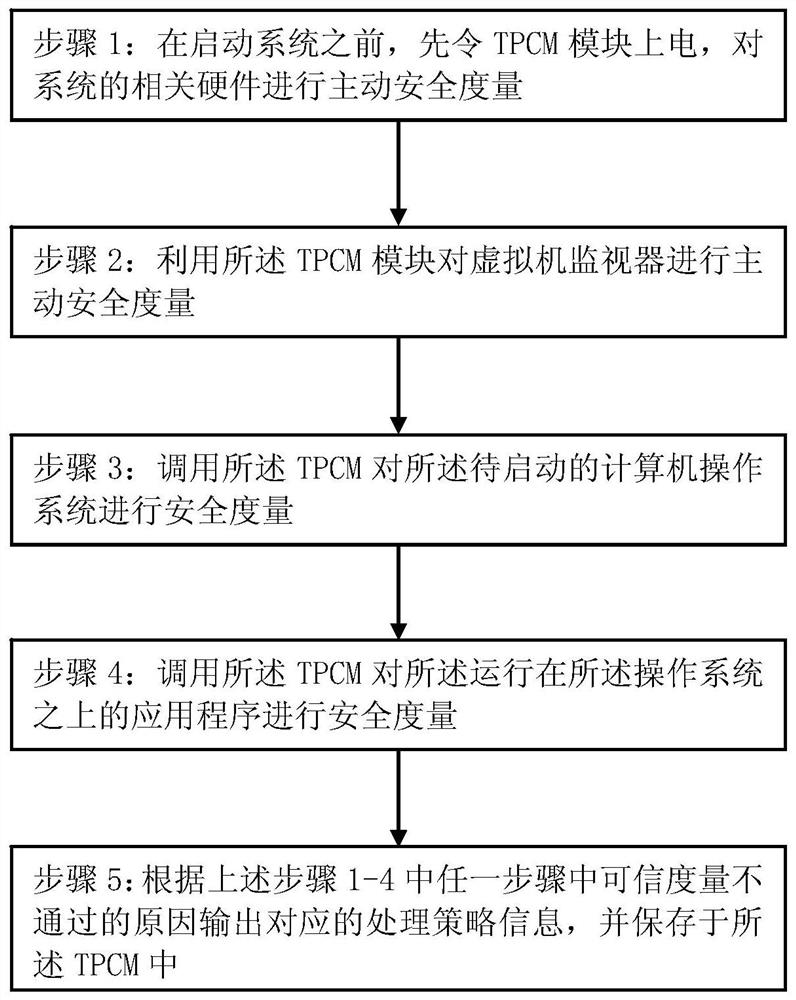
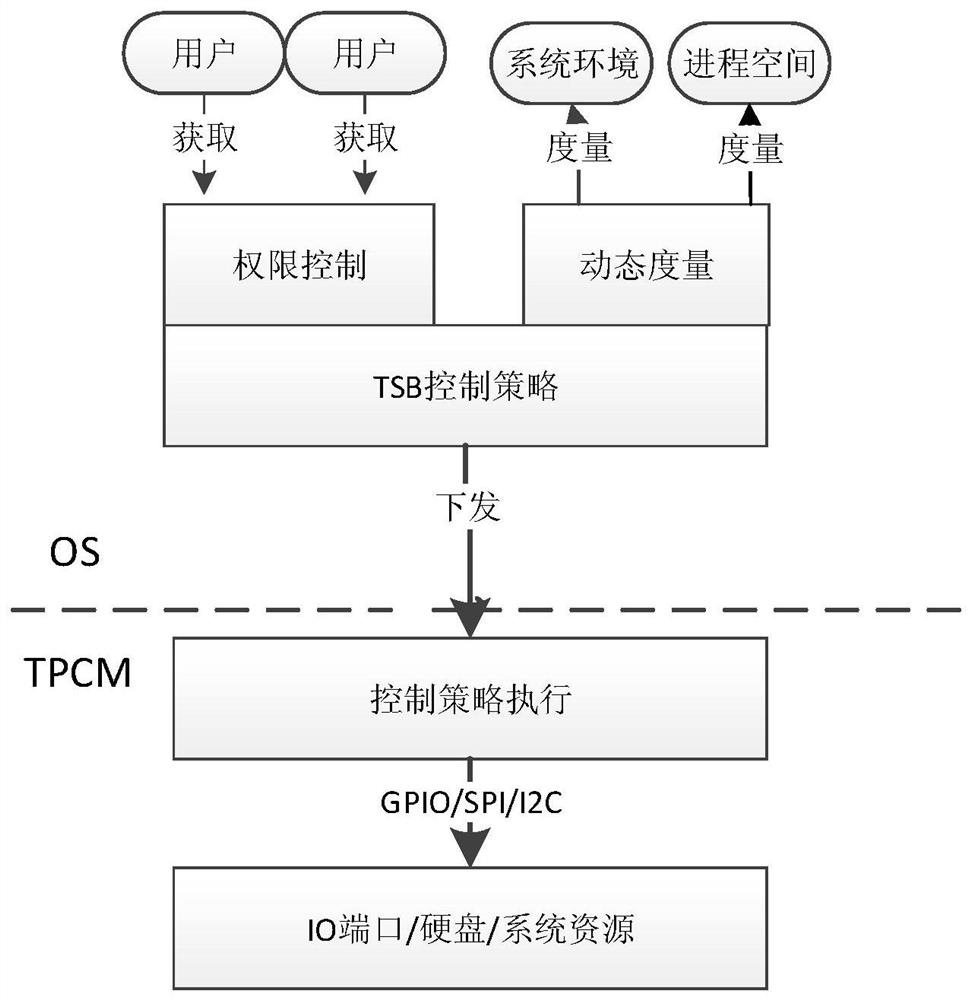
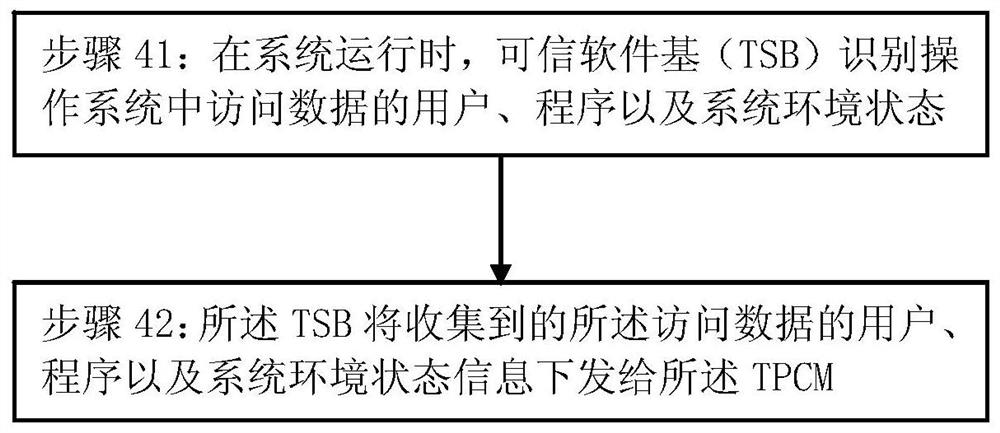
A security control method
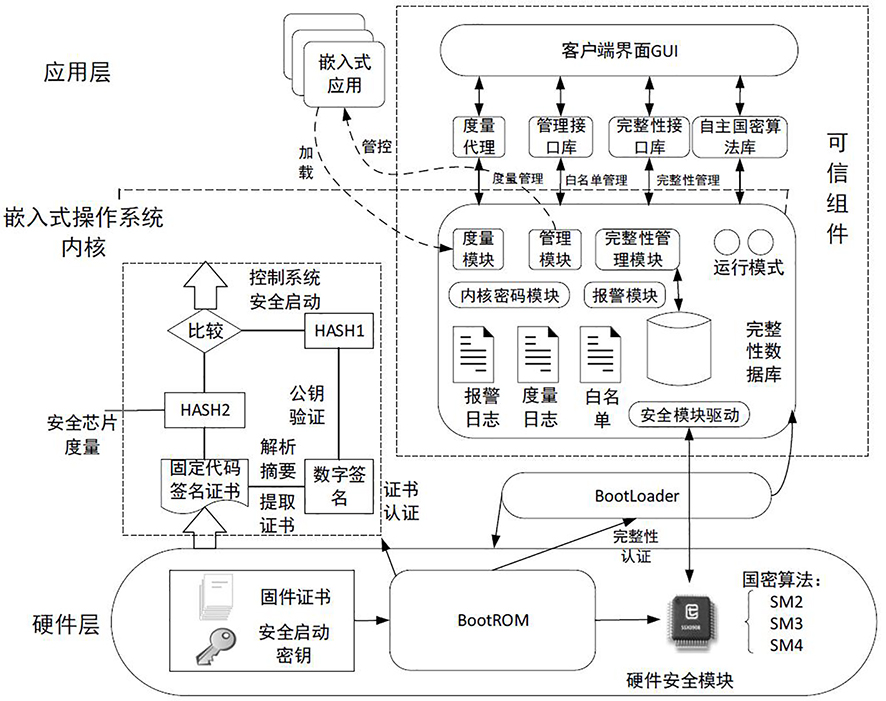
The invention relates to a safety control method, which can not only measure the active safety of the hardware and operating system of the system during the system startup process, but also measure the operating environment of the system and the security of data and other factors during the normal operation stage of the operating system. For measurement, TPCM will retain the measured abnormal information and log information of unsafe factors, and will aggregate them to the trusted management center for audit and identify potential risks. The technical solution of this embodiment can further improve the security of the system.
Owner:BEIJING KEXIN HUATAI INFORMATION TECH
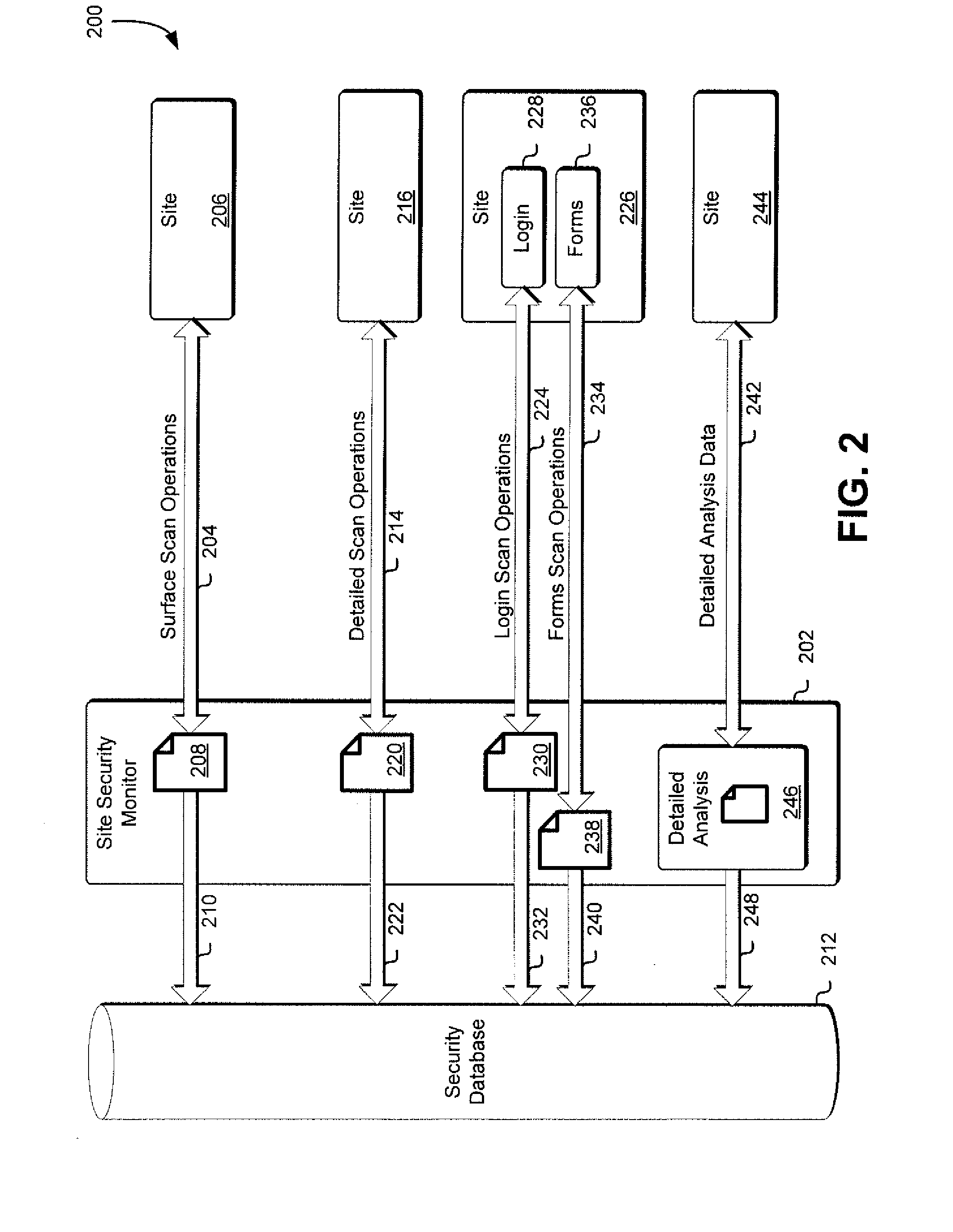
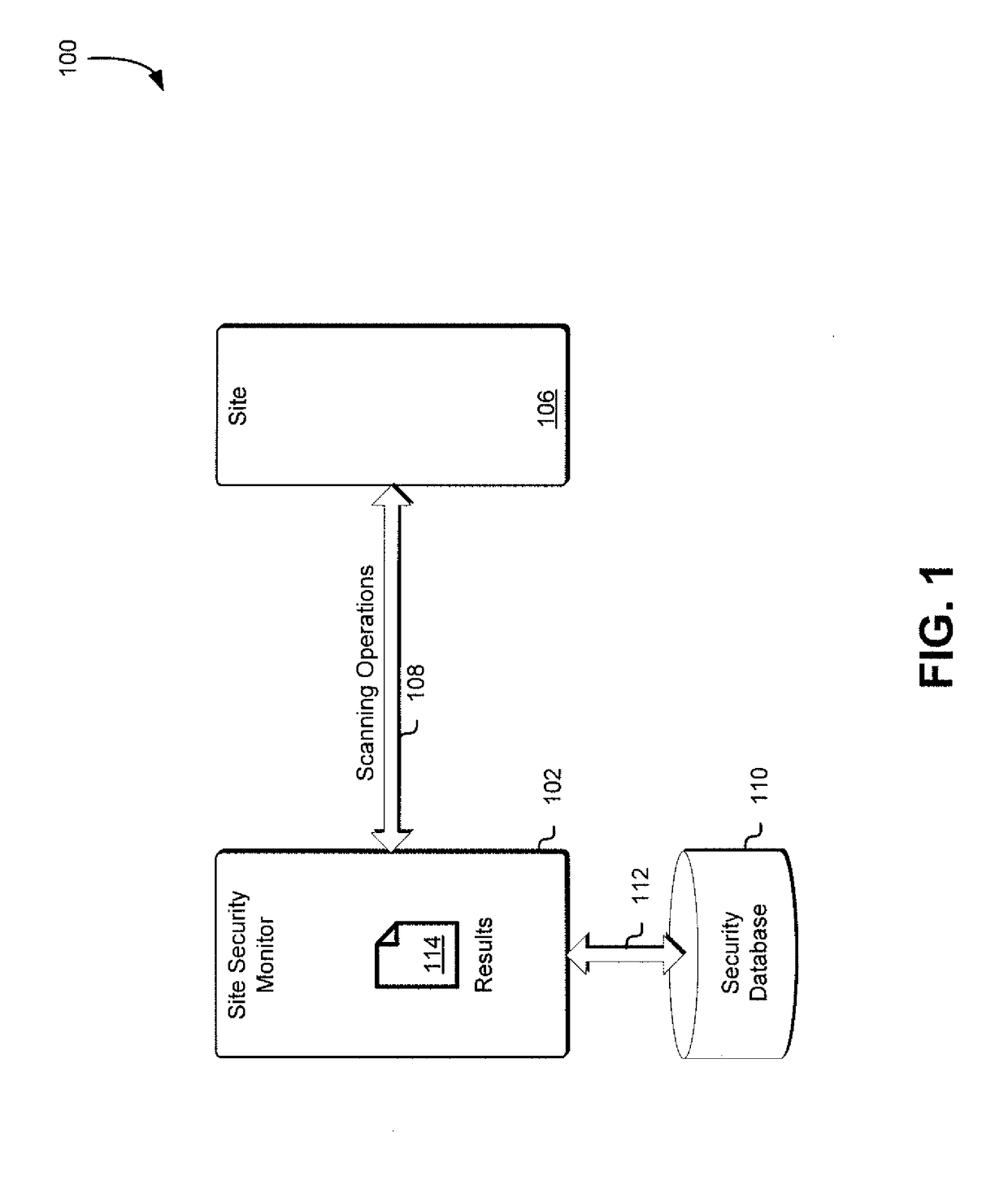
Site security monitor
Techniques for monitoring site security are disclosed herein. Sites are scanned for security metric values associated with one or more security metrics. Normalized values for those scanned security metric values are calculated based on previously obtained values associated with one or more other security metrics associated with other scanned sites. Site security metrics are then calculated for the sites based on a subset of the normalized values and based at least in part on a comparison to other scanned sites.
Owner:SYNOPSYS INC
A chip-based control protection device embedded safety protection system and method
ActiveCN113065140BImprove network securityData processing applicationsPlatform integrity maintainanceSecurity metricChip operating system
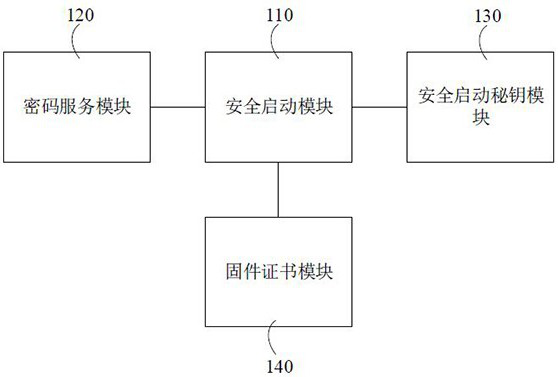
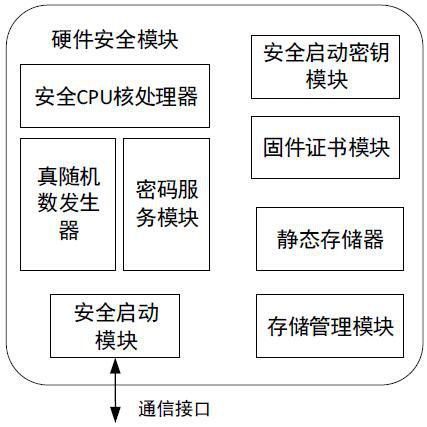
This application relates to a security protection system and method embedded in a chip-based control protection device. The system includes a secure boot module, a password service module, a secure boot secret key module, and a firmware certificate module. The password service module is used to store cryptographic algorithms, secure boot The secret key module is used to store the asymmetric key of the signed device firmware, the firmware certificate module is used to store the firmware certificate proving the legitimacy of the firmware; the secure boot module is used to use the cryptographic service module as the The stored asymmetric key and the firmware certificate stored in the firmware certificate module perform security measurement on the component to be loaded, and start the chip operating system after the security measurement passes. By using the cryptographic service module as the root of trust and securely starting the chip operating system, it can actively protect the information security of the power grid protection terminal and improve the network security of the power grid protection terminal.
Owner:CHINA SOUTHERN POWER GRID DIGITAL GRID RES INST CO LTD
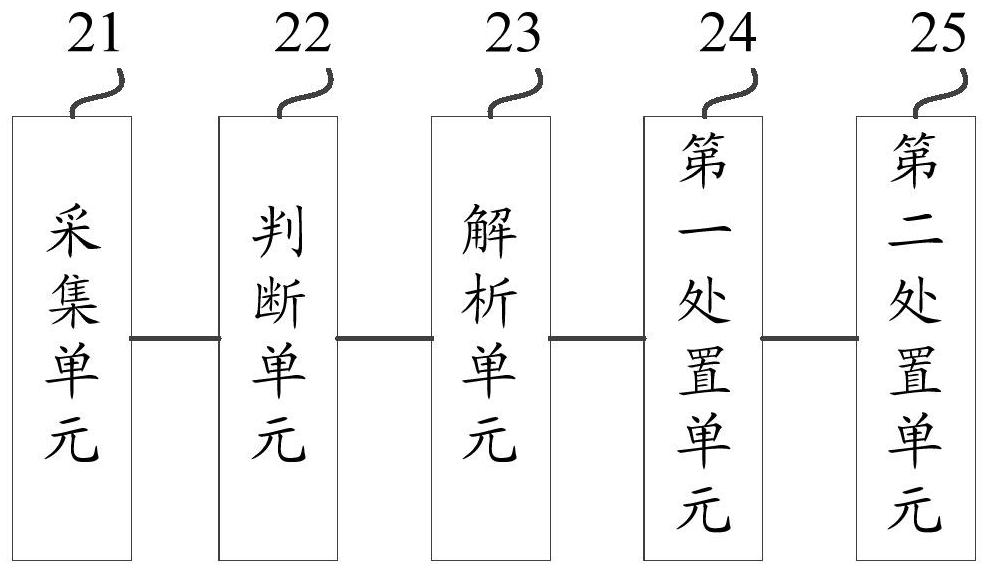
Vehicle protection method and device and computer readable storage medium
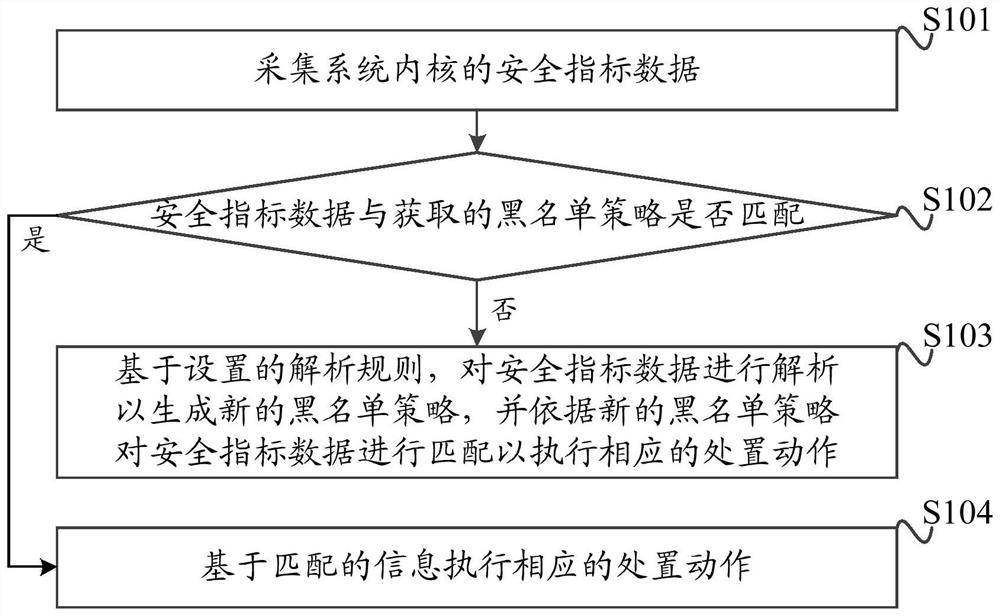
InactiveCN113221106AInterrupt or end safe behavior in a timely mannerBlocking safe behaviorPlatform integrity maintainanceSafety indexSecurity metric
The embodiment of the invention discloses a vehicle protection method and device and a medium. The method comprises the steps of collecting safety index data of a system kernel; judging whether the security index data is matched with the acquired blacklist strategy; if the security index data is not matched with the acquired blacklist strategy, analyzing the security index data based on a set analysis rule to generate a new blacklist strategy, and matching the security index data according to the new blacklist strategy to execute a corresponding processing action; and if the safety index data is matched with the acquired blacklist strategy, executing a corresponding treatment action based on the matched information, thereby ensuring that factors influencing the vehicle safety are blocked or ended in time. According to the technical scheme, the processing device of the vehicle can analyze the safety index data based on the obtained blacklist strategy, and timely discover factors which threaten the vehicle safety, so that the processing action is adopted, and the terminal vehicle can effectively block behaviors which influence the vehicle safety.
Owner:杭州安恒信息安全技术有限公司
A security analysis and automatic evaluation method based on indicator threshold and semantic parsing
The invention discloses a security analysis and automatic evaluation method based on index threshold and semantic analysis. First, extract semantic relationships from unstructured security analysis reports, regulations and standards, and other security analysis original corpora to build a standardized security knowledge base; at the same time, build security indicator entity sets according to dimensions such as activities and events, and classify and hierarchically divide security Indicator set; based on the semantic similarity calculation method, it can identify and extract security indicator entities and threshold attributes from corpora such as regulations, standards, technical requirements, and judgment basis, and can identify and extract security indicator entities and monitoring data attributes from security analysis reports; Semantic parsing results can automatically benchmark and determine the satisfaction of safety indicators, and can review and verify the initial judgment results of indicators in combination with expert experience. This method meets the needs of users for fast, accurate and intelligent safety analysis and automatic evaluation of different activities and events, and can effectively improve the efficiency and accuracy of safety evaluation.
Owner:THE 28TH RES INST OF CHINA ELECTRONICS TECH GROUP CORP
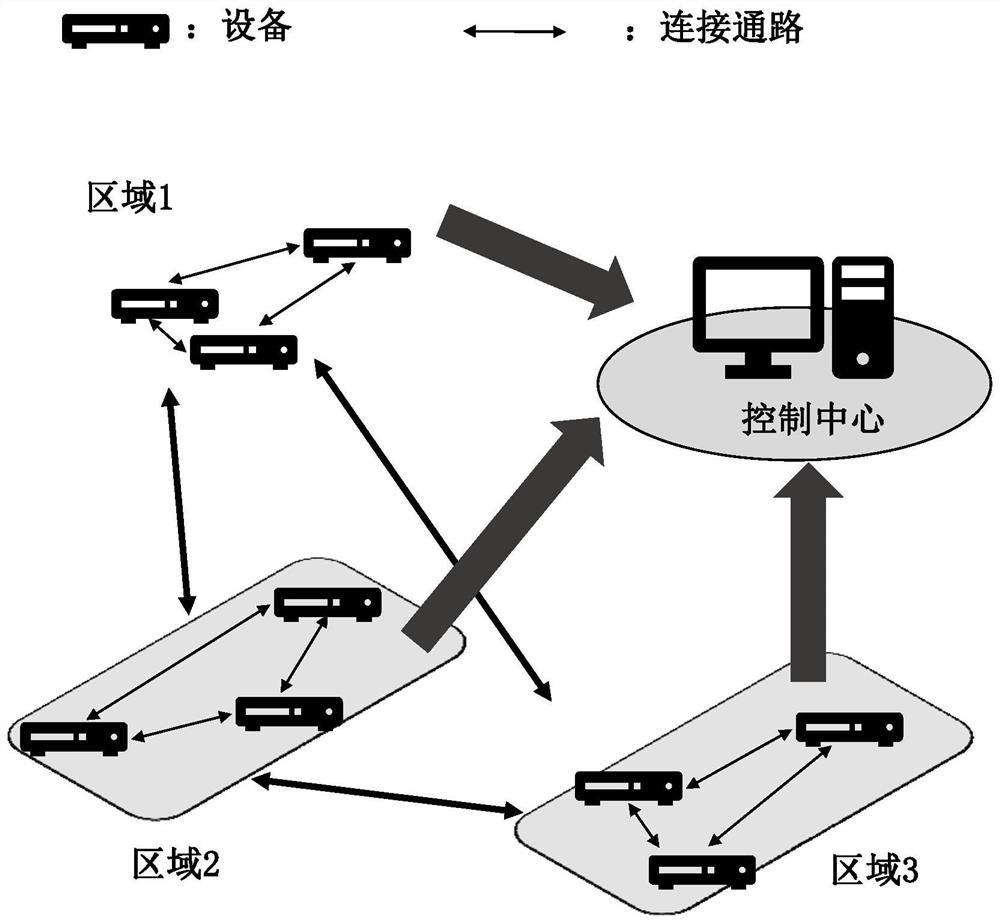
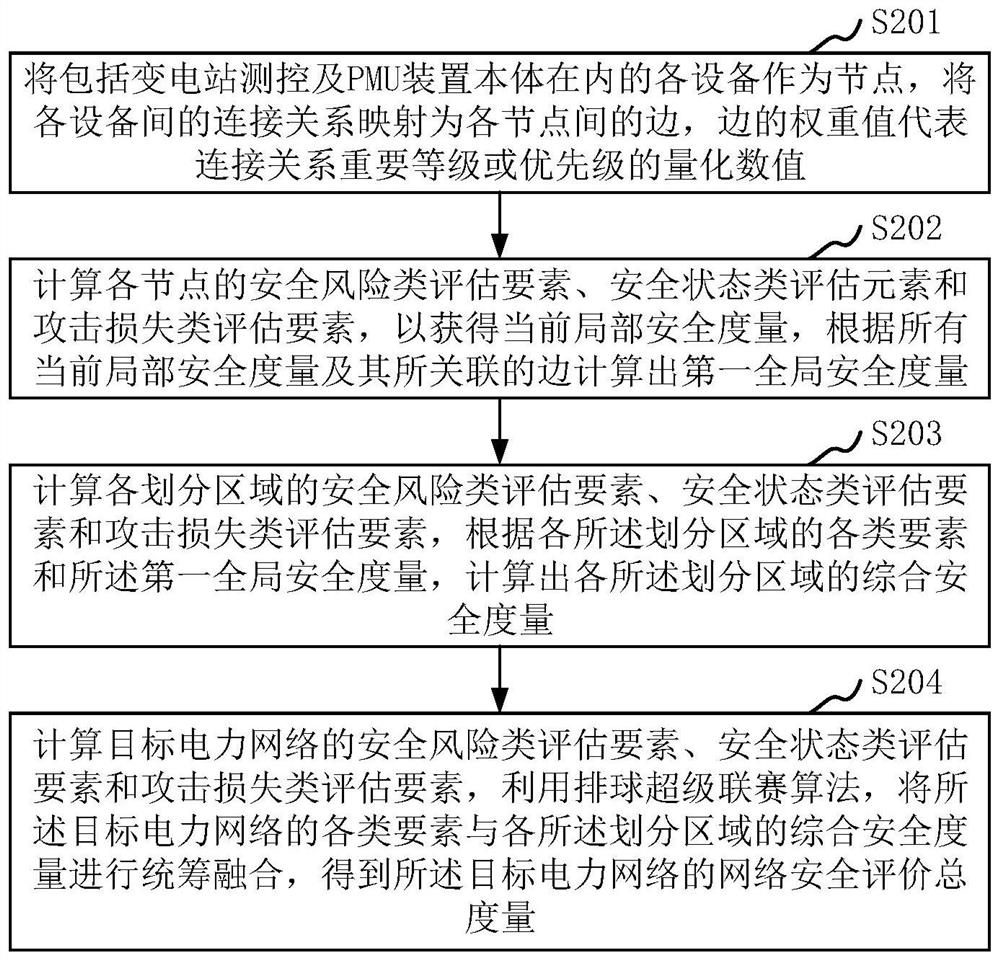
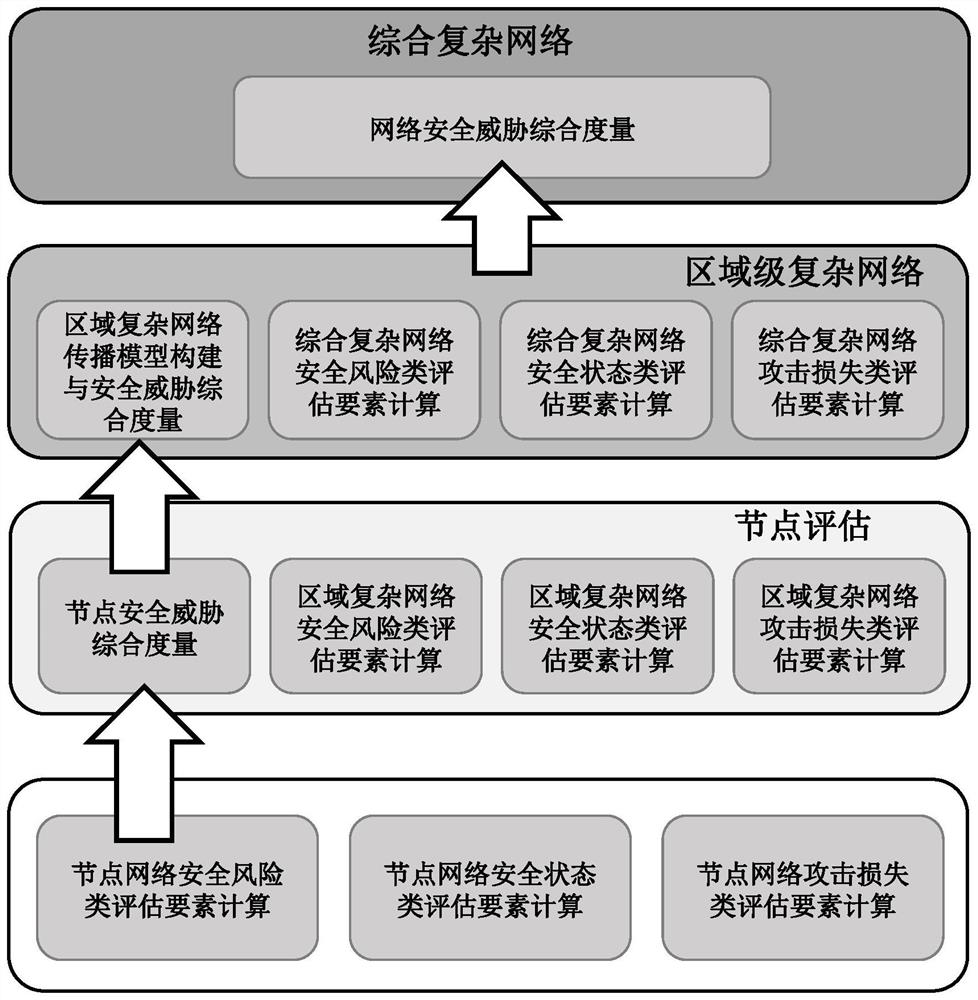
Power grid safety evaluation method and device, computer equipment and storage medium
The invention relates to a power grid safety evaluation method and device, computer equipment, a storage medium and a computer program product. According to the invention, the operation safety and stability of the power grid system can be improved. The method comprises the following steps: taking each device of a transformer substation as a node, mapping a connection relationship among the devices as an edge among the nodes, and calculating security risk class, security state class and attack loss class evaluation elements of each node to obtain a current local security measure; calculating a first global security metric according to all the current local security metrics and the associated edges thereof; calculating various evaluation elements of each divided area, and calculating comprehensive security measurement of each divided area according to the various elements of each divided area and the first global security measurement; and calculating various evaluation elements of the target power network, and carrying out overall fusion on the various elements of the target power network and the comprehensive security measurement of each divided region by using a volleyball super-match algorithm to obtain a network security evaluation total measurement of the target power network.
Owner:GUANGZHOU POWER SUPPLY BUREAU GUANGDONG POWER GRID CO LTD
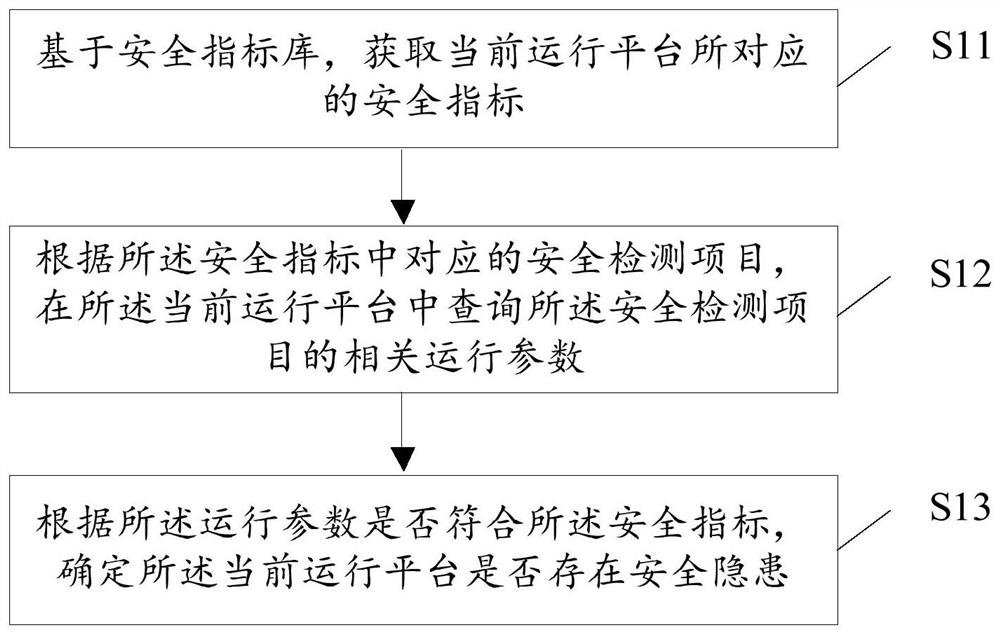
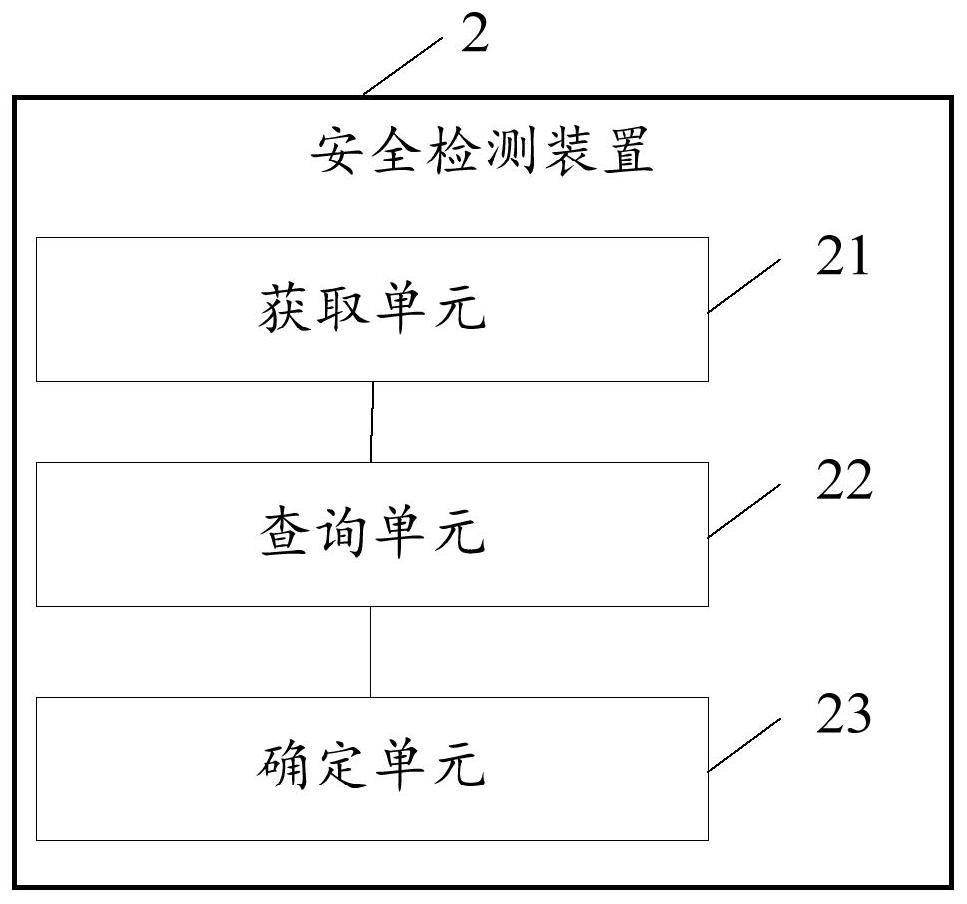
Security detection method and device, electronic equipment and storage medium
PendingCN113672923AImprove adaptabilityVersion controlPlatform integrity maintainanceSecurity metricSecurity index
The embodiment of the invention discloses a security detection method and device, electronic equipment and a storage medium, relates to the technical field of computers, and the adaptability of the security detection method can be improved. The method comprises the steps of obtaining a security index corresponding to a current operation platform based on a security index library; according to a corresponding security detection item in the security index, querying related operation parameters of the security detection item in the current operation platform; and determining whether the current operation platform has potential security hazards or not according to whether the operation parameters accord with the security indexes or not. The method is suitable for a security detection process.
Owner:BEIJING ANTIY NETWORK SAFETY TECH CO LTD
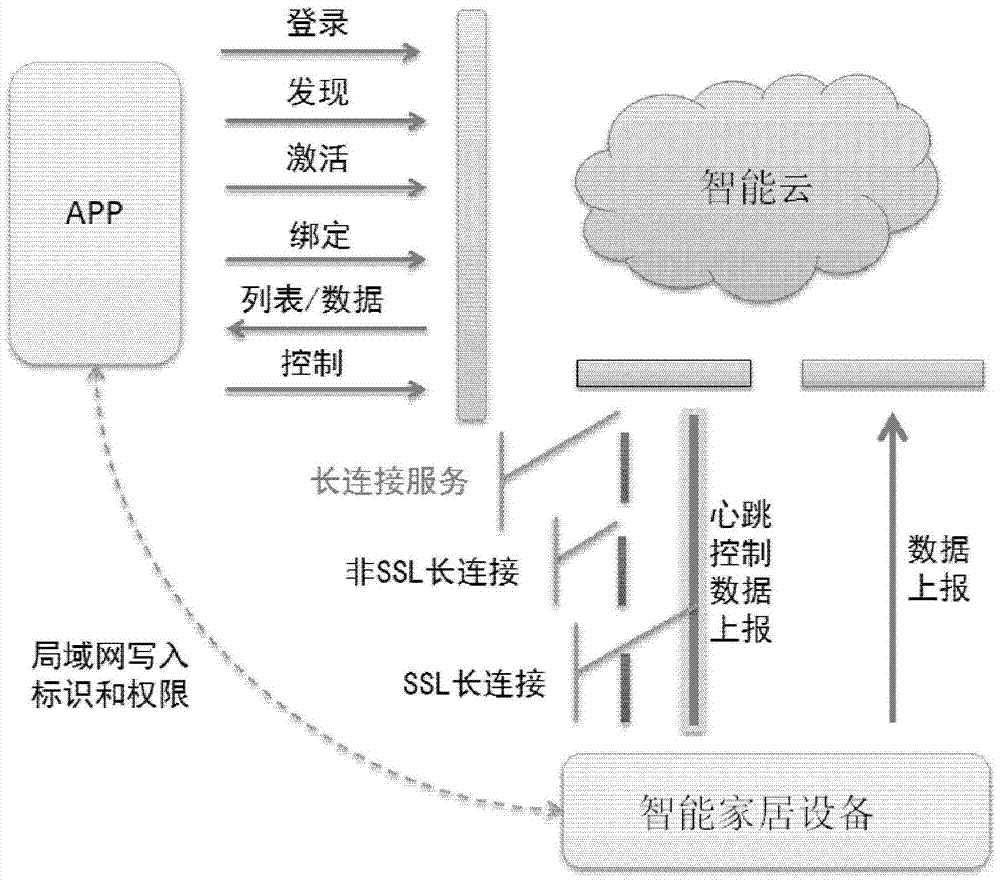
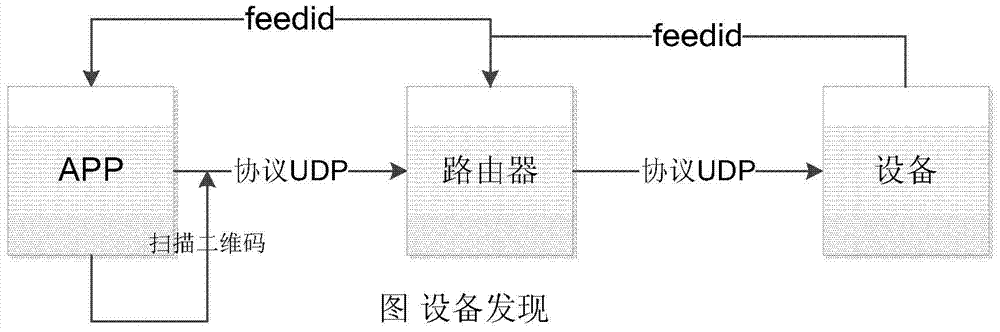
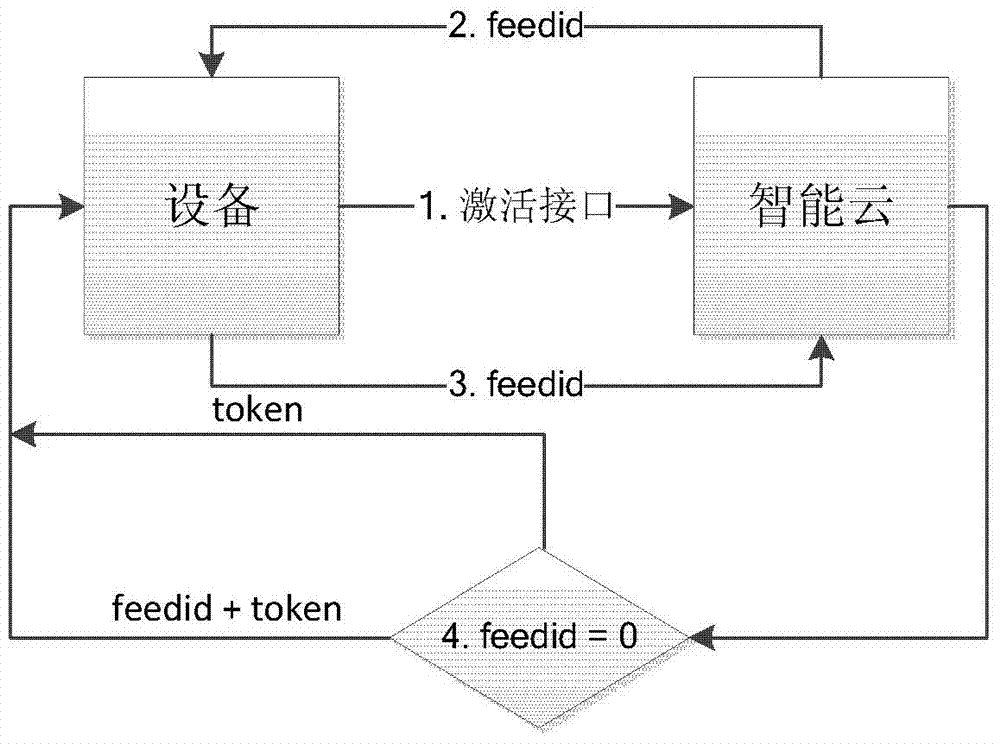
System and method for securely controlling smart home devices based on smart cloud
The invention discloses a system and a method for safely controlling smart home devices based on smart clouds. A system for safely controlling smart home devices based on smart clouds, the system comprising: smart home devices, the smart home devices have smart WiFi modules that meet the agreed protocol to connect to a WiFi network connected to the smart cloud; the smart cloud , the smart cloud stores data from the smart home devices and performs big data analysis; and APP, the APP is configured to log in to the smart cloud, and obtain the smart home information in the current environment from the smart cloud The list of devices and the data, and communicate with the smart home device via the smart cloud, wherein the smart cloud provides services to the smart home device and the APP through a long connection.
Owner:BEIJING JINGDONG SHANGKE INFORMATION TECH CO LTD +1
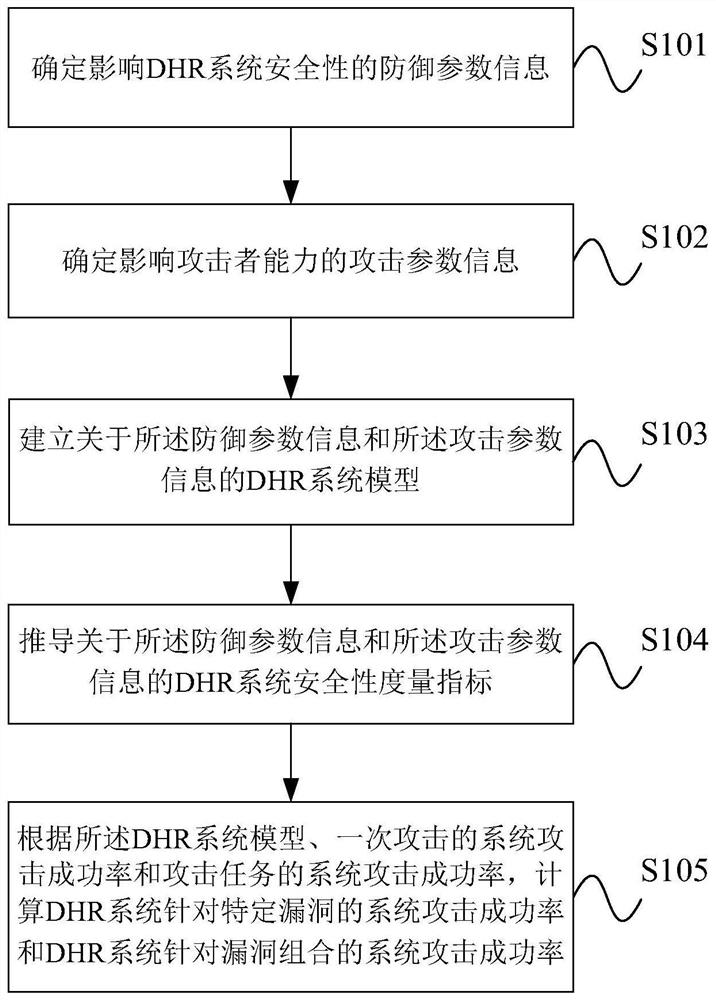
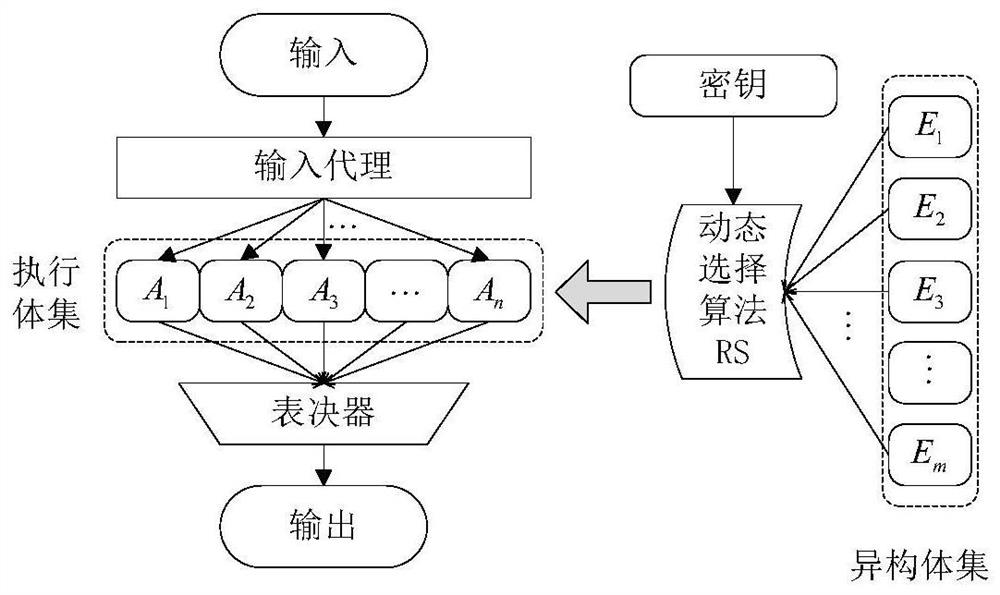
Security Modeling and Quantification Method for Cyberspace Mimic Defense Based on Vulnerability Consistency Rate
The invention provides a security modeling and quantification method for network space mimicry defense based on the vulnerability consistency rate. The method comprises: step 1: determining the defense parameter information that affects the security of the DHR system; step 2: determining the attack parameter information that affects the attacker's ability; step 3: establishing the DHR system about the defense parameter information and the attack parameter information Model; step 4: deriving the DHR system security metrics about the defense parameter information and the attack parameter information, the metrics include: the system attack success rate of an attack and the system attack success rate of the attack task; step 5 : According to the DHR system model, the system attack success rate of an attack and the system attack success rate of an attack task, calculate the system attack success rate of the DHR system for a specific vulnerability and the system attack success rate of the DHR system for a combination of vulnerabilities. A mathematical model is established for the DHR system, and the security of the system is represented by indicators such as output consistency rate and system attack success rate, and the security and anti-attack ability of the DHR system are analyzed by solving the model.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
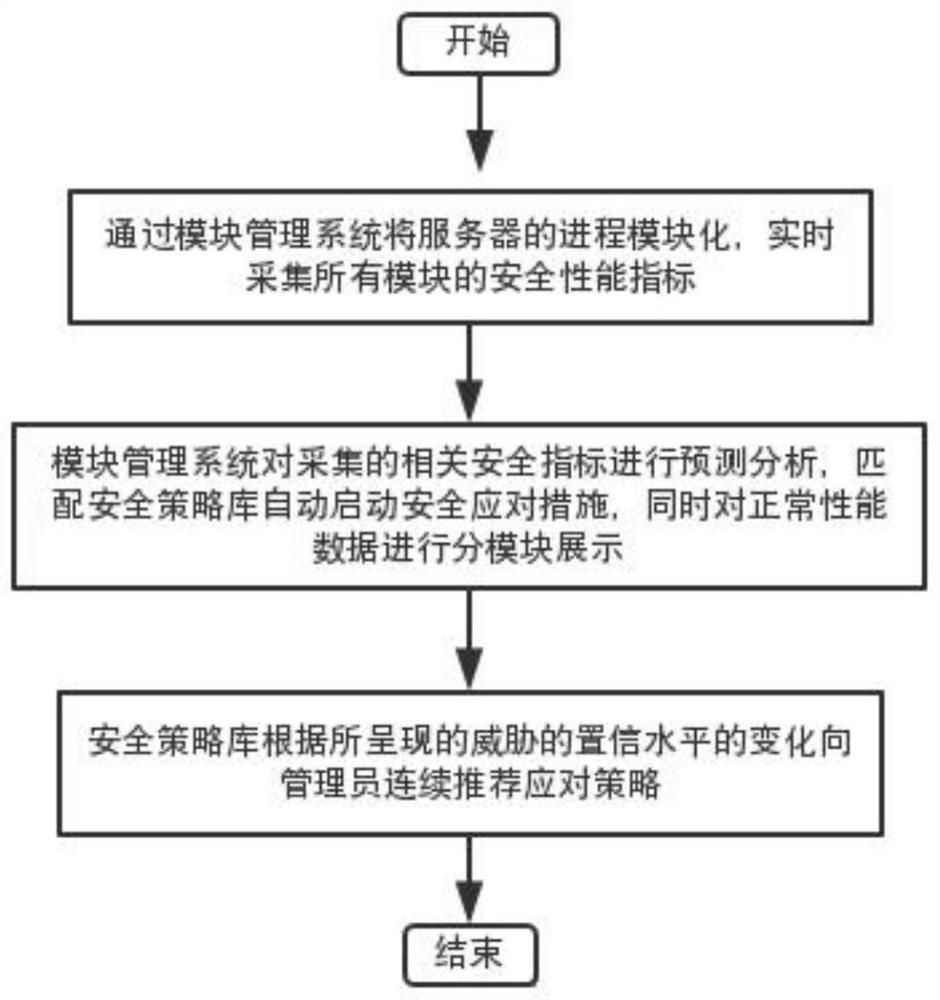
Method capable of automatically responding to security issues in modular environment
ActiveCN112398778AImprove processing efficiencyReduce processing timeTransmissionSecurity metricSafety property
The invention discloses a method capable of automatically responding to a security problem in a modular environment. The method is characterized by comprising the following steps of performing modularization on a process of a server through a module management system, and acquiring security performance indexes of all modules in real time; the module management system automatically predicts and analyzes the acquired related safety indexes, matches a safety strategy database to automatically start safety countermeasures, and displays normal performance data in a modular manner; the security policy database continuously recommends coping policies to an administrator in accordance with changes in confidence levels of the presented threats. The system is advantaged in that a modular managementsystem is used, and the safety performance indexes of the detection object are modularized; monitoring objects with normal safety performance index data can be displayed in different modules, coping strategies can be continuously and dynamically provided for safety threat events, safety event processing efficiency is greatly improved, and meanwhile the processing time is saved.
Owner:BEIJING YOUTEJIE INFORMATION TECH
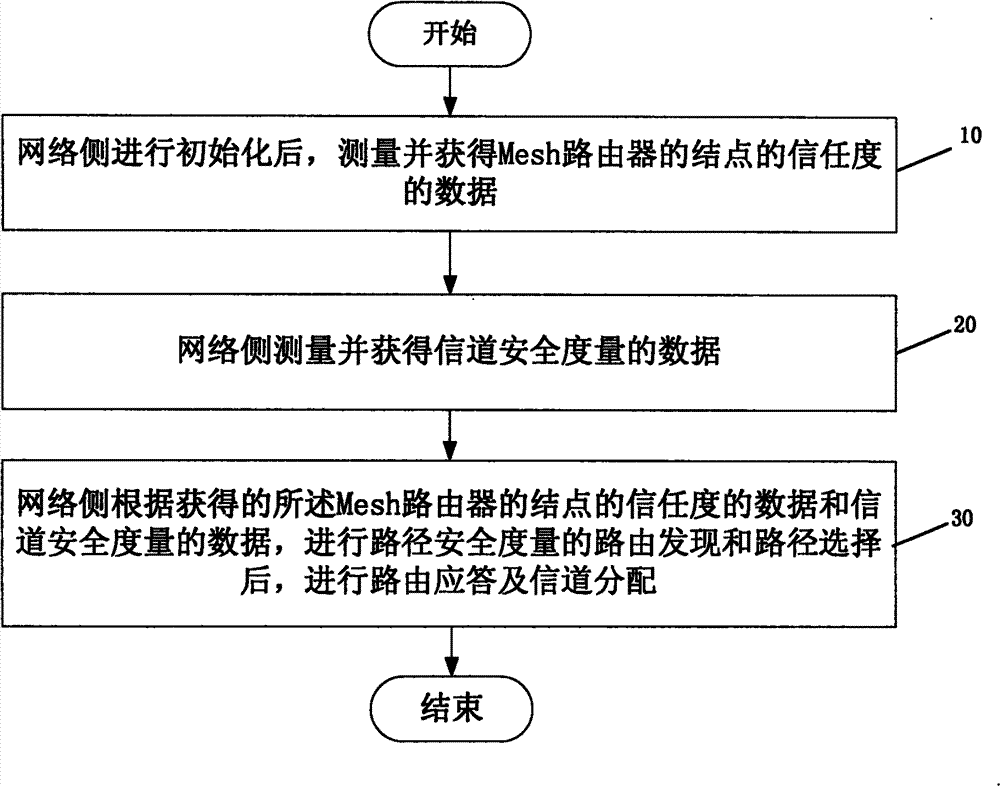
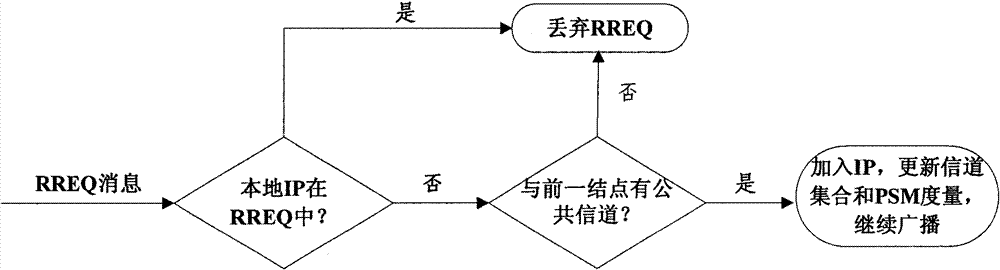
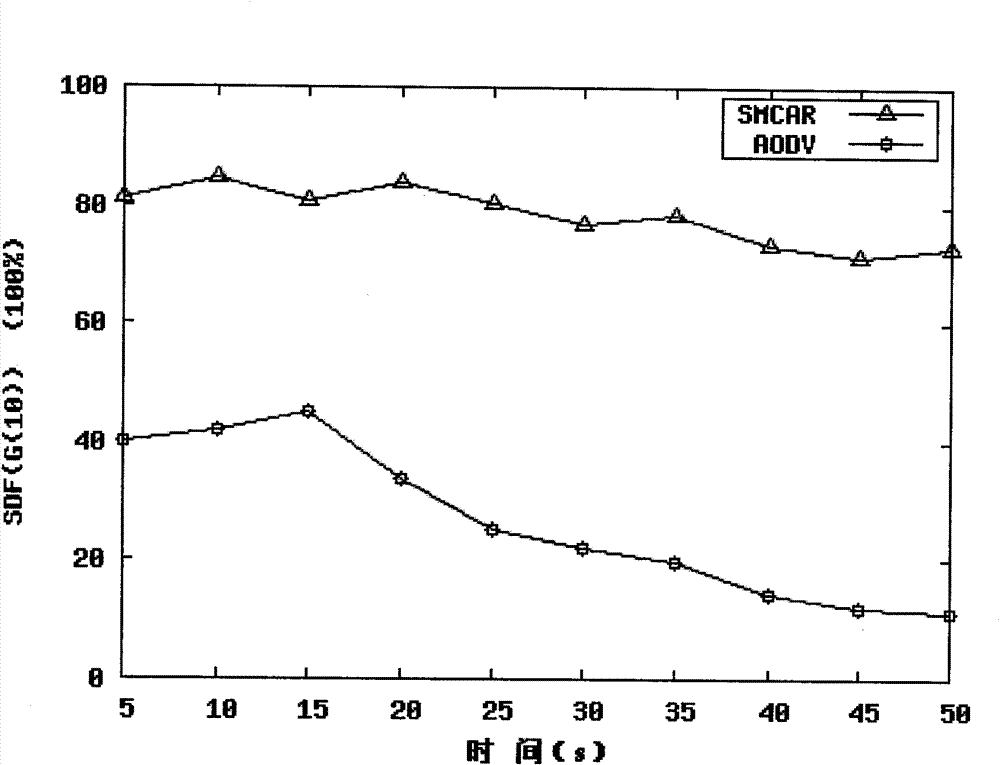
Method for secure routing and channel allocation in cognitive Mesh network
InactiveCN101848461BFacilitate the commercialization processExtended Cognitive Access BandwidthNetwork topologiesSecurity arrangementSecurity metricSecure transmission
Owner:THE PLA INFORMATION ENG UNIV
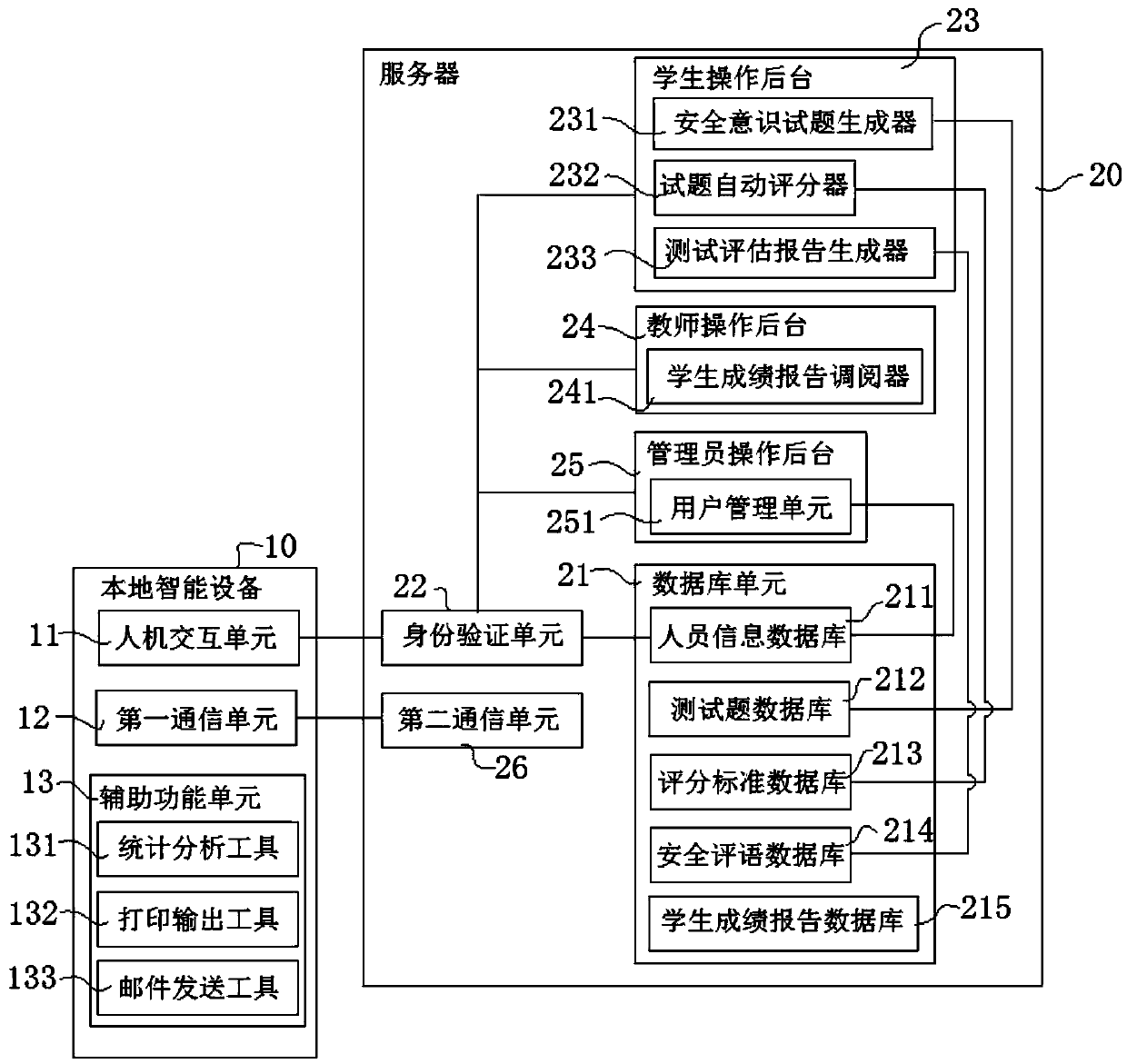
Student safety awareness evaluation system and method
PendingCN111105119AAdapt to Educational RequirementsImprove the scientific nature of dimensionsResourcesSecurity metricSafety index
The invention discloses a student safety consciousness evaluation system and a method. According to the method, an evaluation framework based on multiple scale indexes such as security thought, security skills, security mentality and security behaviors is formed; education feedback guiding significance is achieved in the form of a safety consciousness evaluation report, an index system based on safety indexes is established, the dimension scientificity of investigation is improved, and the education requirements of schools in grades and levels are met. A B / S mode is adopted in hardware, only asmall amount of service logic is achieved on a front-end browser, main transaction logic is achieved on a server side, a three-layer structure is formed, and the expenditure cost of system maintenance and upgrading is reduced.
Owner:汪佳炀
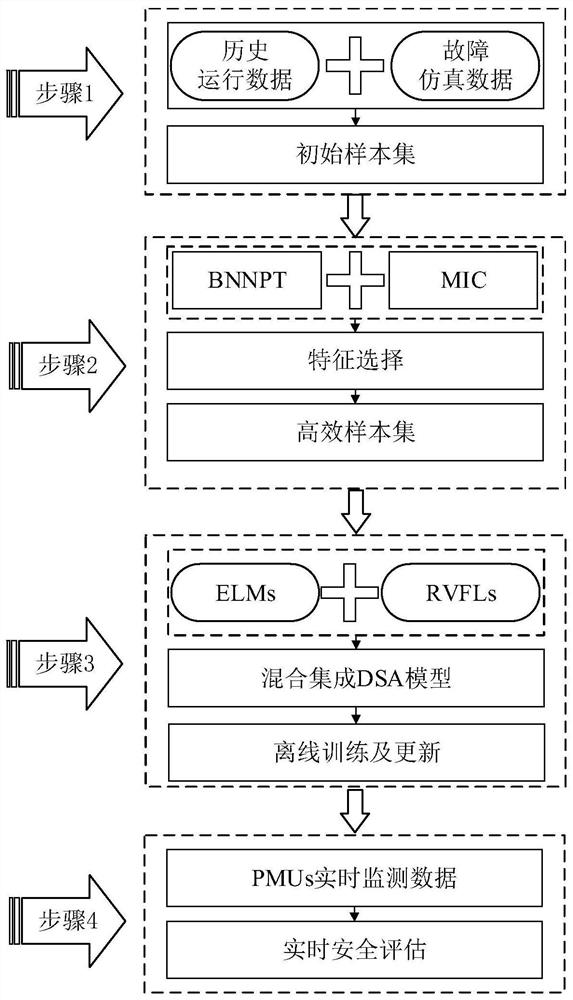
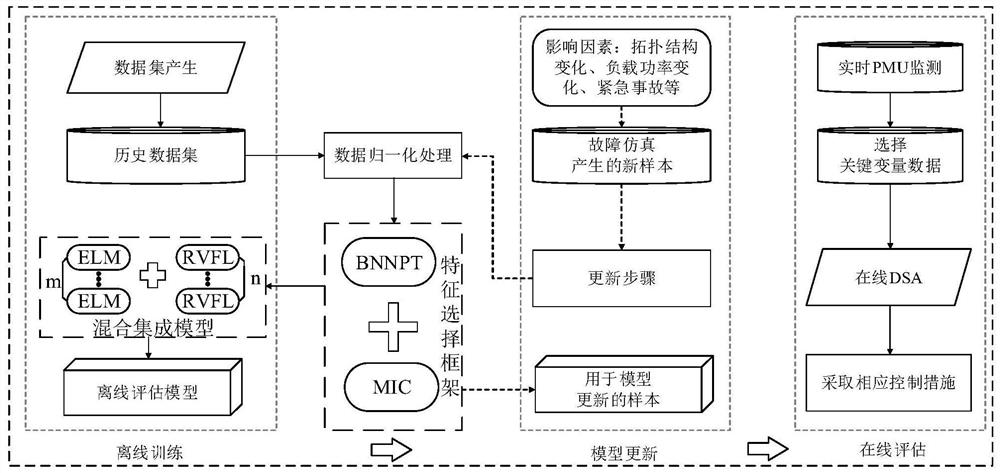
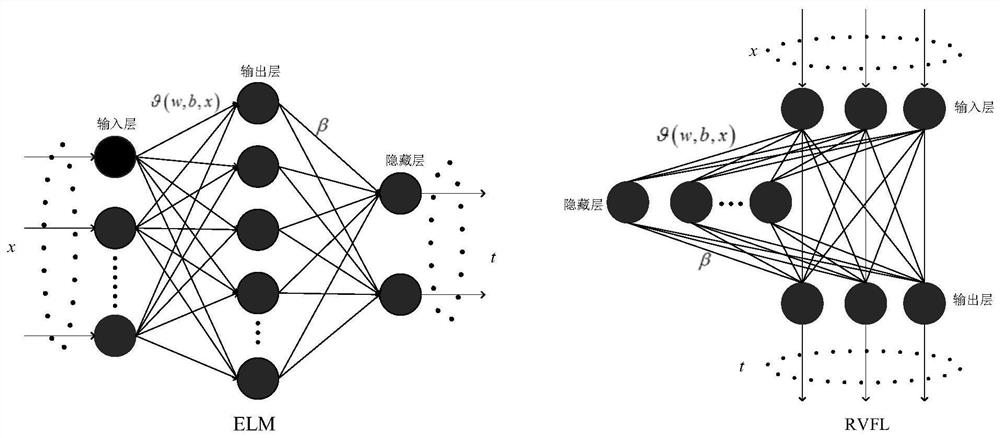
A Dynamic Security Assessment Method of Power System Based on Hybrid Integrated Model
ActiveCN111585277BEfficient screeningReduce dimensionalityCharacter and pattern recognitionNeural architecturesSecurity metricSystem failure
Owner:CHINA THREE GORGES UNIV
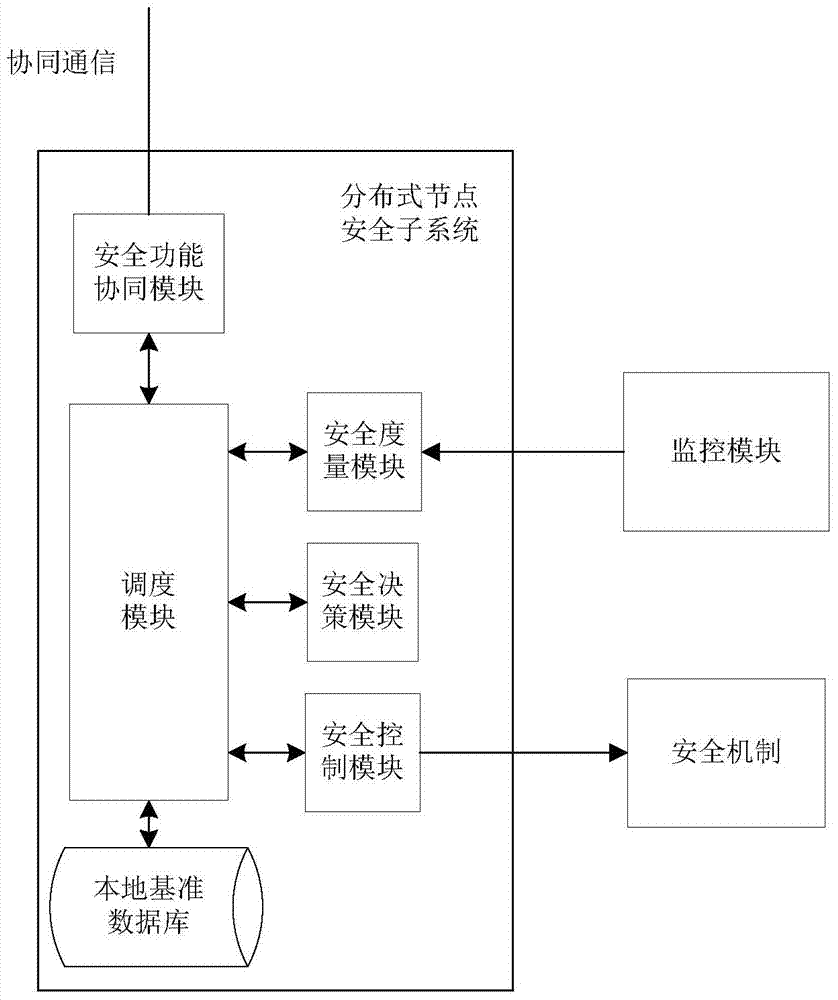
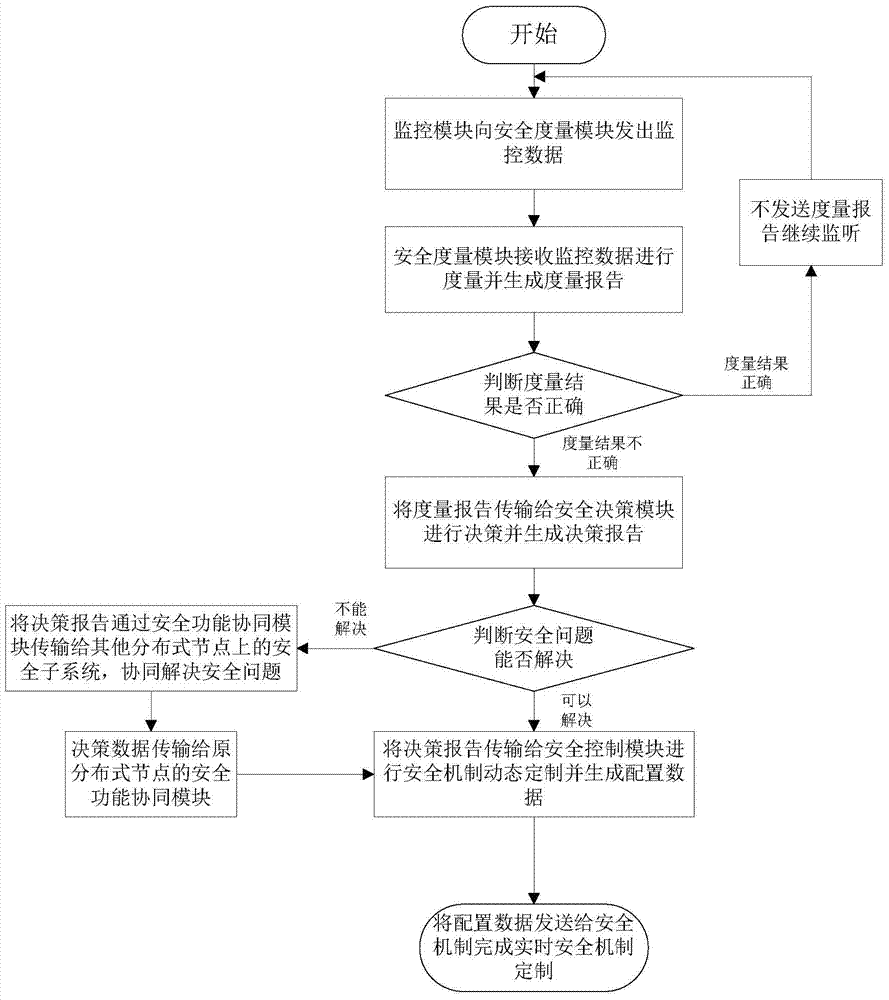
A security monitoring method in a distributed network environment
The invention discloses a safety monitoring method in a distributed network environment, and relates to the safety monitoring problem in the field of information safety. The invention consists of three parts: a monitoring module, a safety module and a safety mechanism, wherein the safety module is composed of a safety function coordination module, a safety control module, a safety measurement module, a safety decision module and a local reference database. In the present invention, the monitored dynamic data is delivered by the monitoring module, and then measured by the safety measurement module, which is used to measure the safety of the behavior of the monitoring node; the safety decision-making module determines the qualitative safety problem according to the measurement result; the safety control module dispatches the monitored data according to the decision-making result The security mechanism in the system implements the response strategy; the security function coordination module is responsible for communicating with the security measurement module, the security decision-making module and the security control module to realize the security function collaboration. The invention can dynamically customize security policies for the distributed network environment, and maintain the security of monitoring nodes in the distributed network environment.
Owner:BEIJING UNIV OF TECH
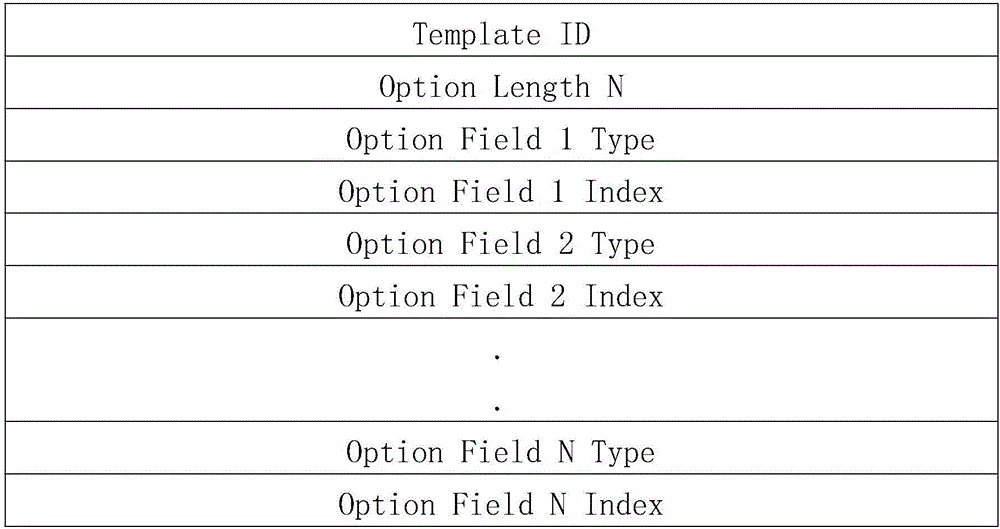
An indexed security measurement method based on power information network security event mining
The invention discloses indexed security measurement system and device based on power information network security event mining. The method and device are characterized in that the power information network heterogeneous security events are acquired on real time and normalized through a pre-defined template; the real-time data of index parameters Vk of the normalized standard safety events are acquired on real time, and the measurement value Ei of the dimension parameter Di and the whole network security measurement index H can be obtained according to the data. According to the method and device, the pre-defined security measurement strategy can be performed for adapting to complex network demand; an automatic, indexed and intelligent security measurement system is created based on the real-time characteristic and comprehensiveness of the security event data, and therefore, network security state and effectiveness can be accurately evaluated.
Owner:STATE GRID CORP OF CHINA +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com