Electric power information network security measuring method based on security log data mining
A network security and power information technology, applied in the field of information security, can solve problems such as low accuracy and low efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
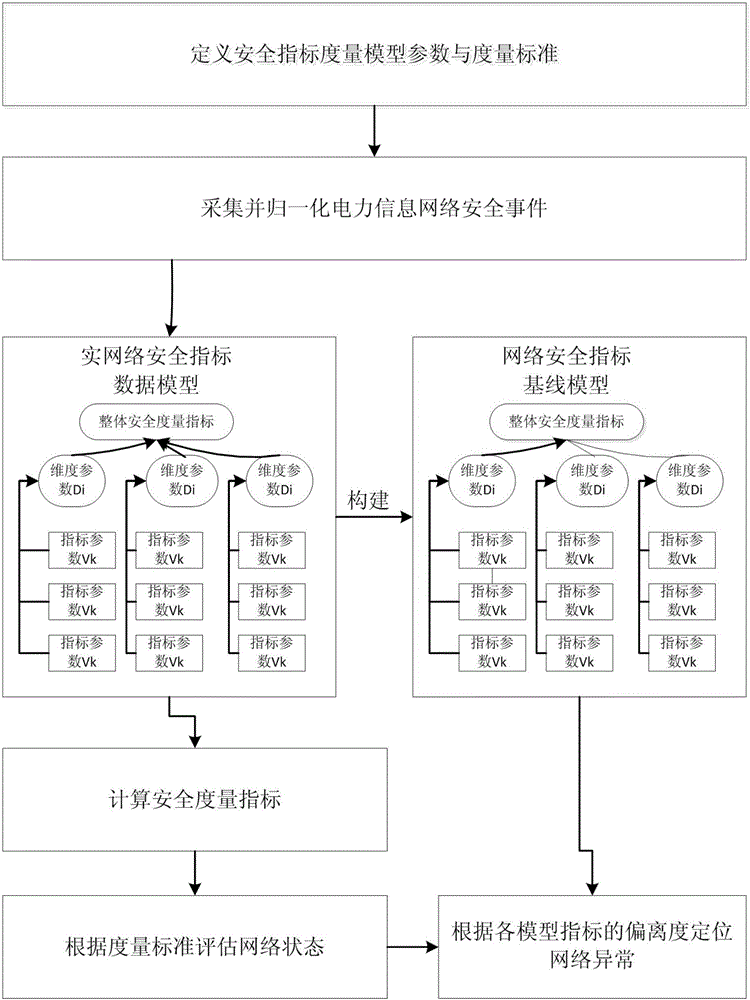
[0042] A power information network security measurement method based on security log data mining, which includes:
[0043] Step 1. Define the security index measurement model parameters and metric standards; define the security indicator measurement model parameters and metric standards. The security indicator measurement model parameters include defining the address range of security events, defining the time range of security events, and defining model dimension parameters D i , Define the indicator parameter V k ; Defining metrics includes defining the classification of safety indicators and the proportion of safety indicator variables.
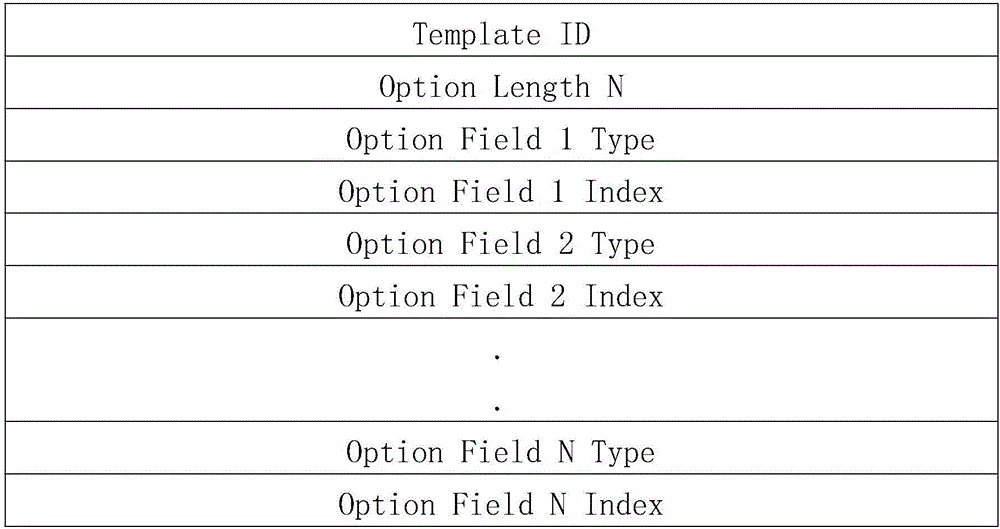
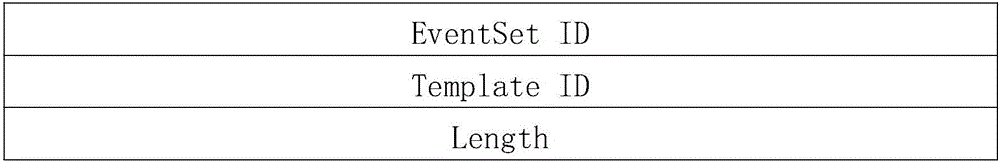
[0044] Step 2. Collect the heterogeneous security events of the power information network, and use the template-based scalable security event paradigm format to normalize and cache the security events to form a standardized security event; Step 2 uses the template-based scalability The security event normalization format normalizes and caches se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com