Patents
Literature
93 results about "Transaction logic" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Transaction Logic is an extension of predicate logic that accounts in a clean and declarative way for the phenomenon of state changes in logic programs and databases. This extension adds connectives specifically designed for combining simple actions into complex transactions and for providing control over their execution. The logic has a natural model theory and a sound and complete proof theory. Transaction Logic has a Horn clause subset, which has a procedural as well as a declarative semantics. The important features of the logic include hypothetical and committed updates, dynamic constraints on transaction execution, non-determinism, and bulk updates. In this way, Transaction Logic is able to declaratively capture a number of non-logical phenomena, including procedural knowledge in artificial intelligence, active databases, and methods with side effects in object databases.
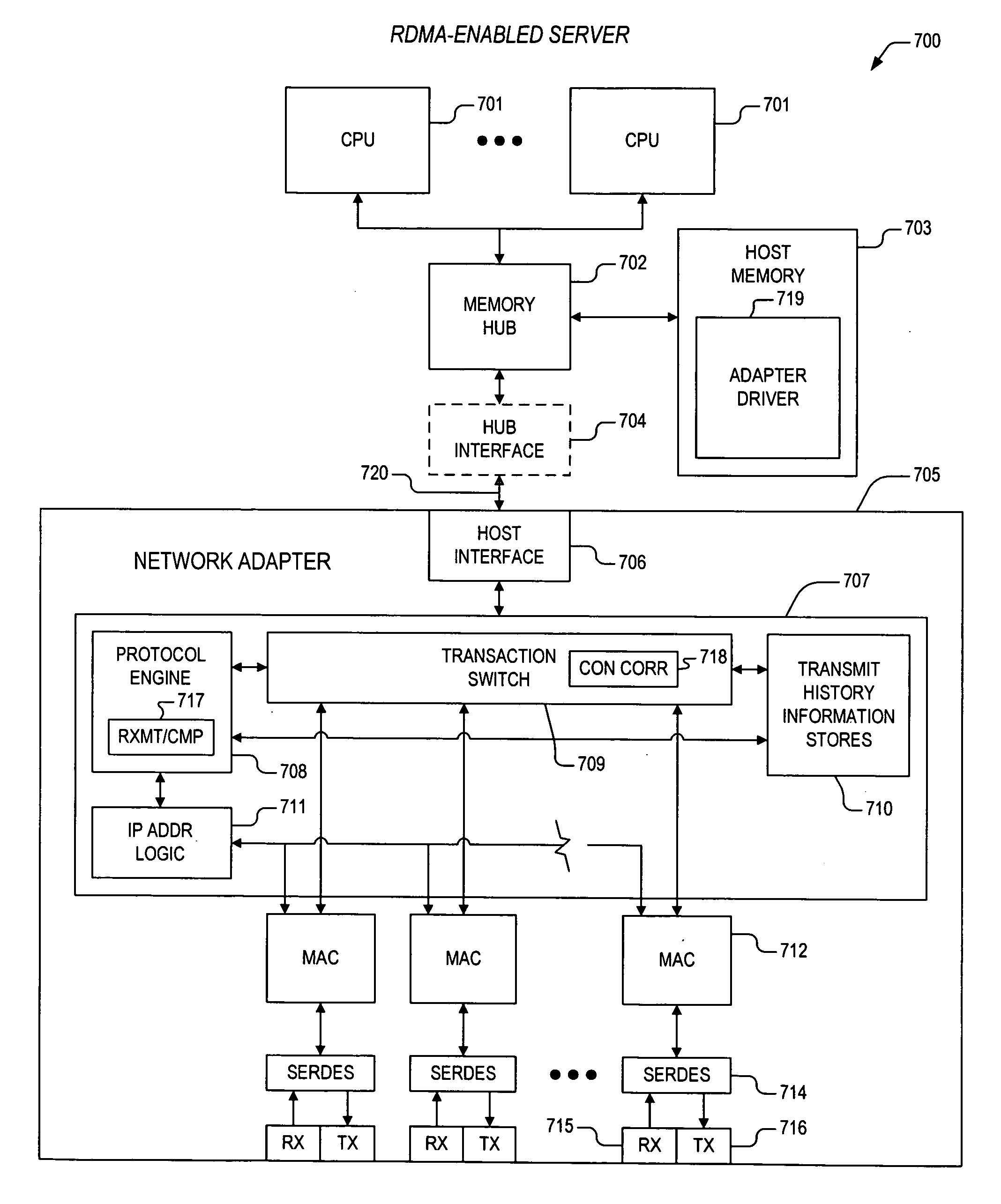
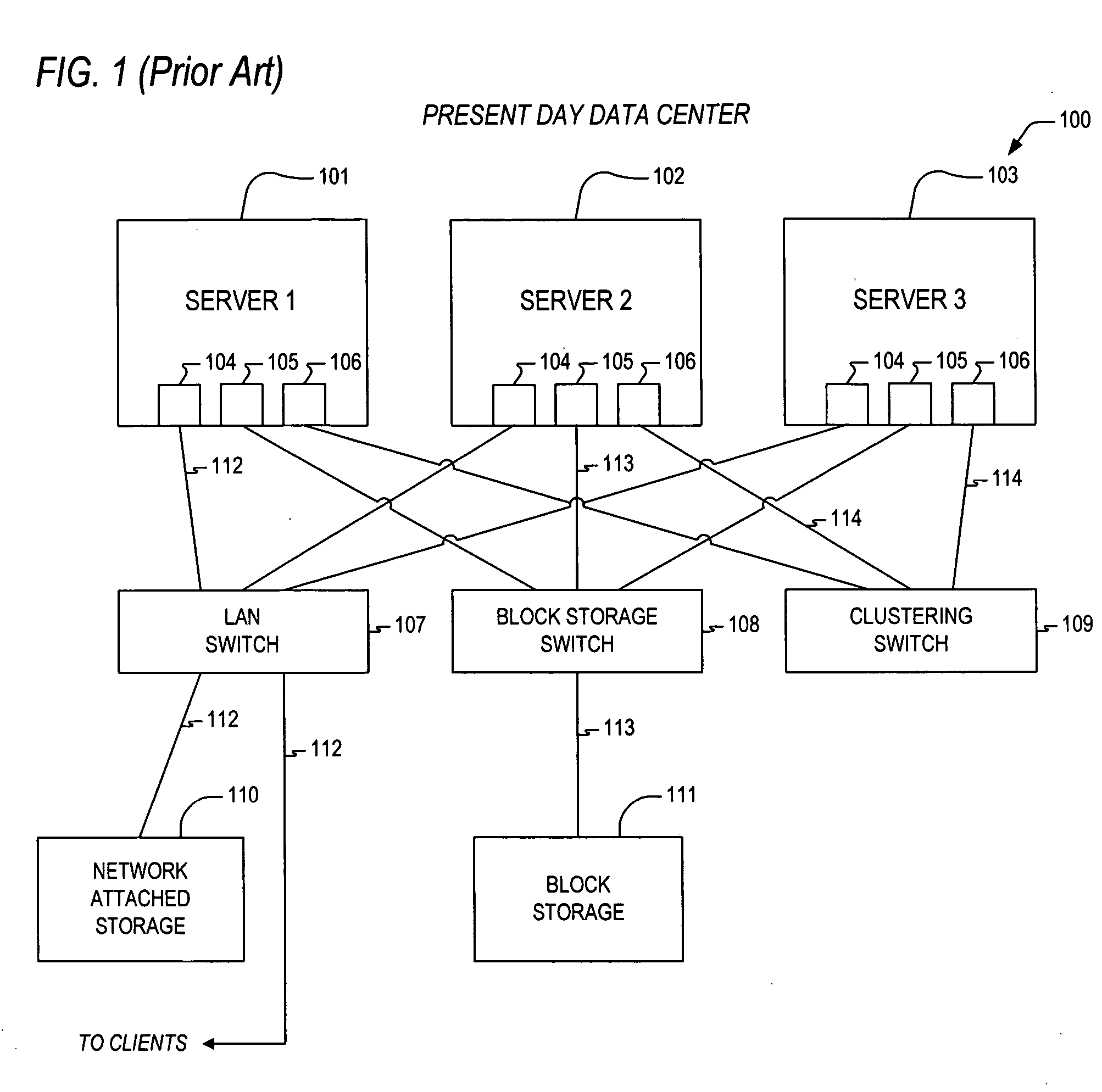
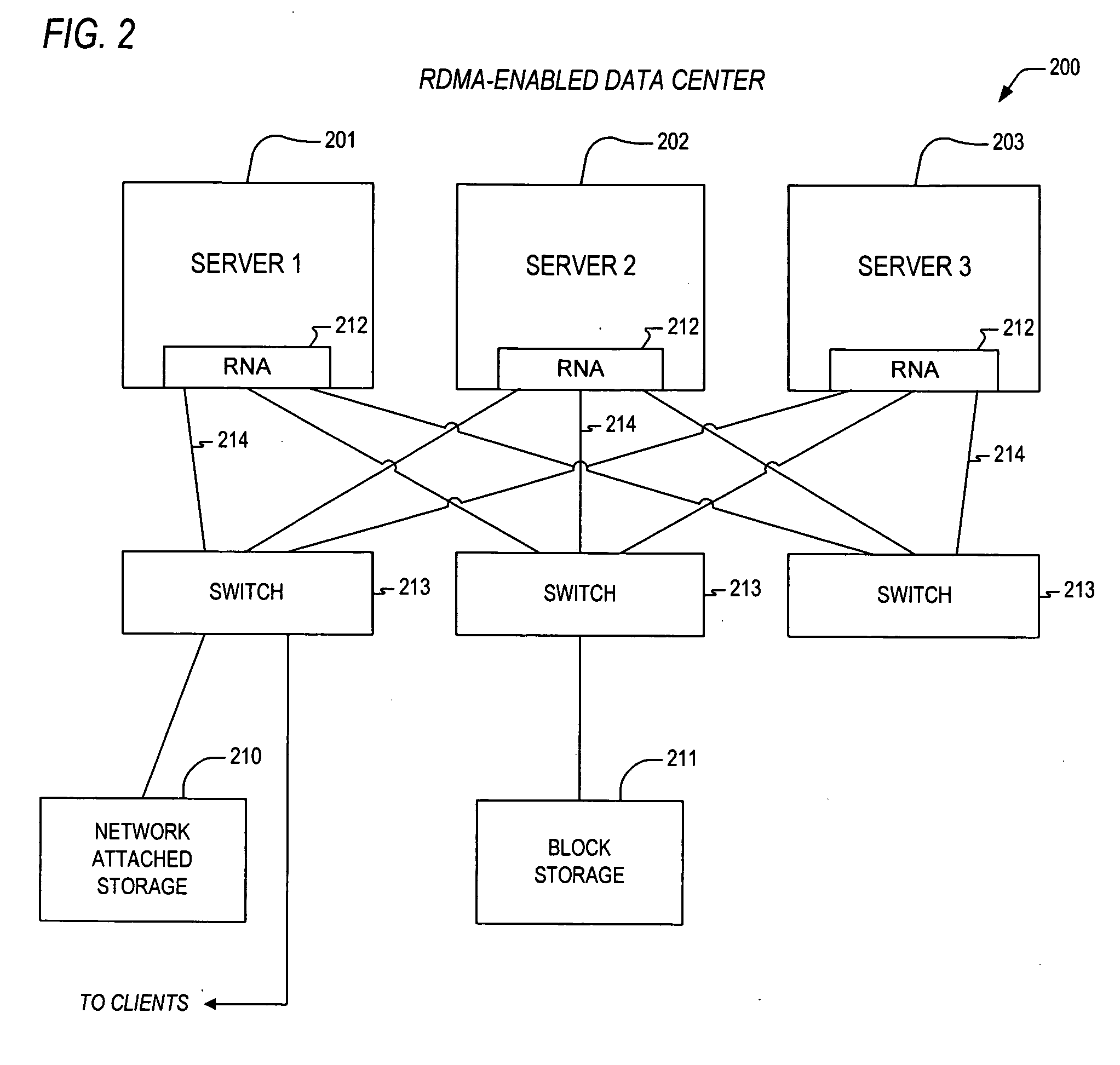
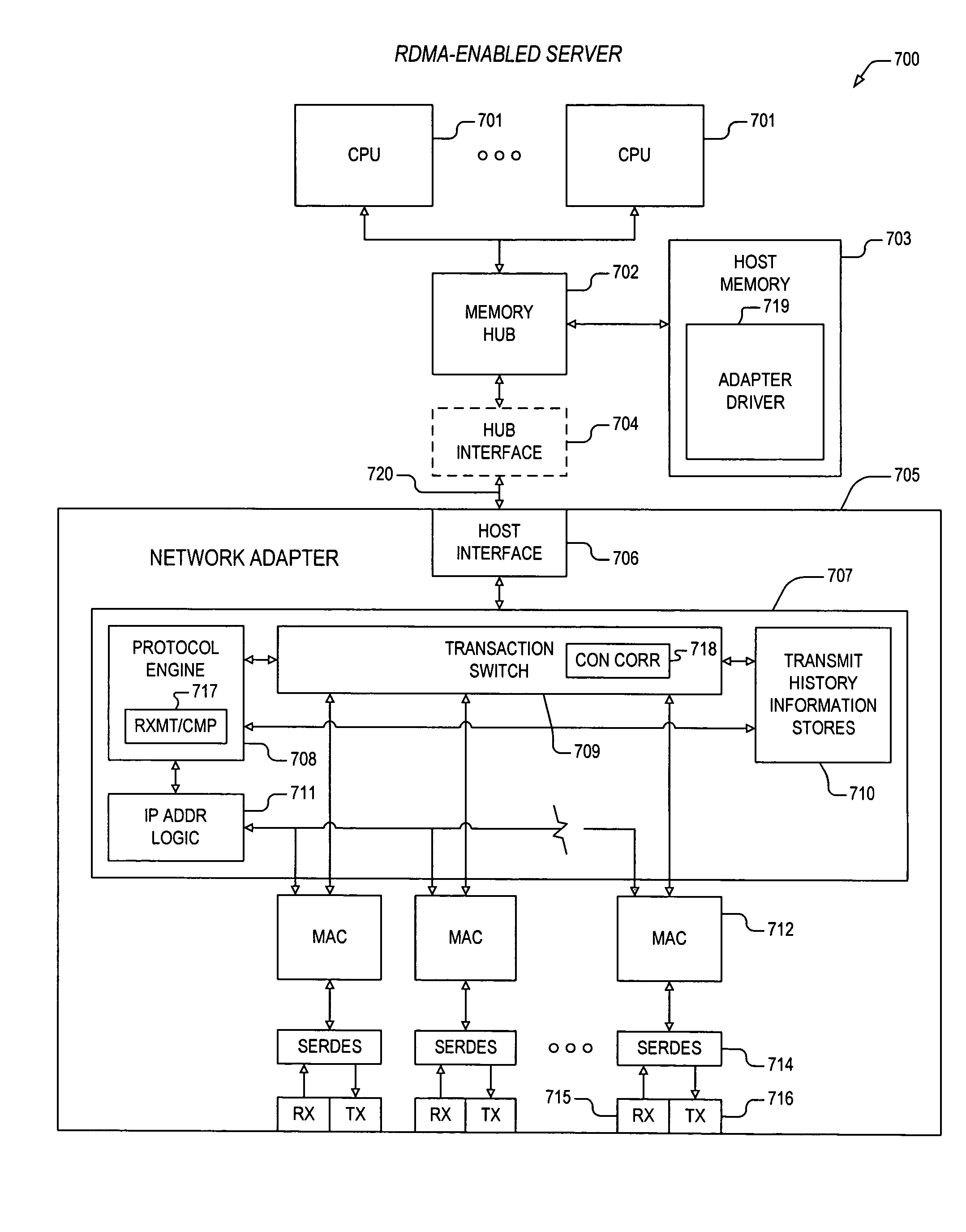
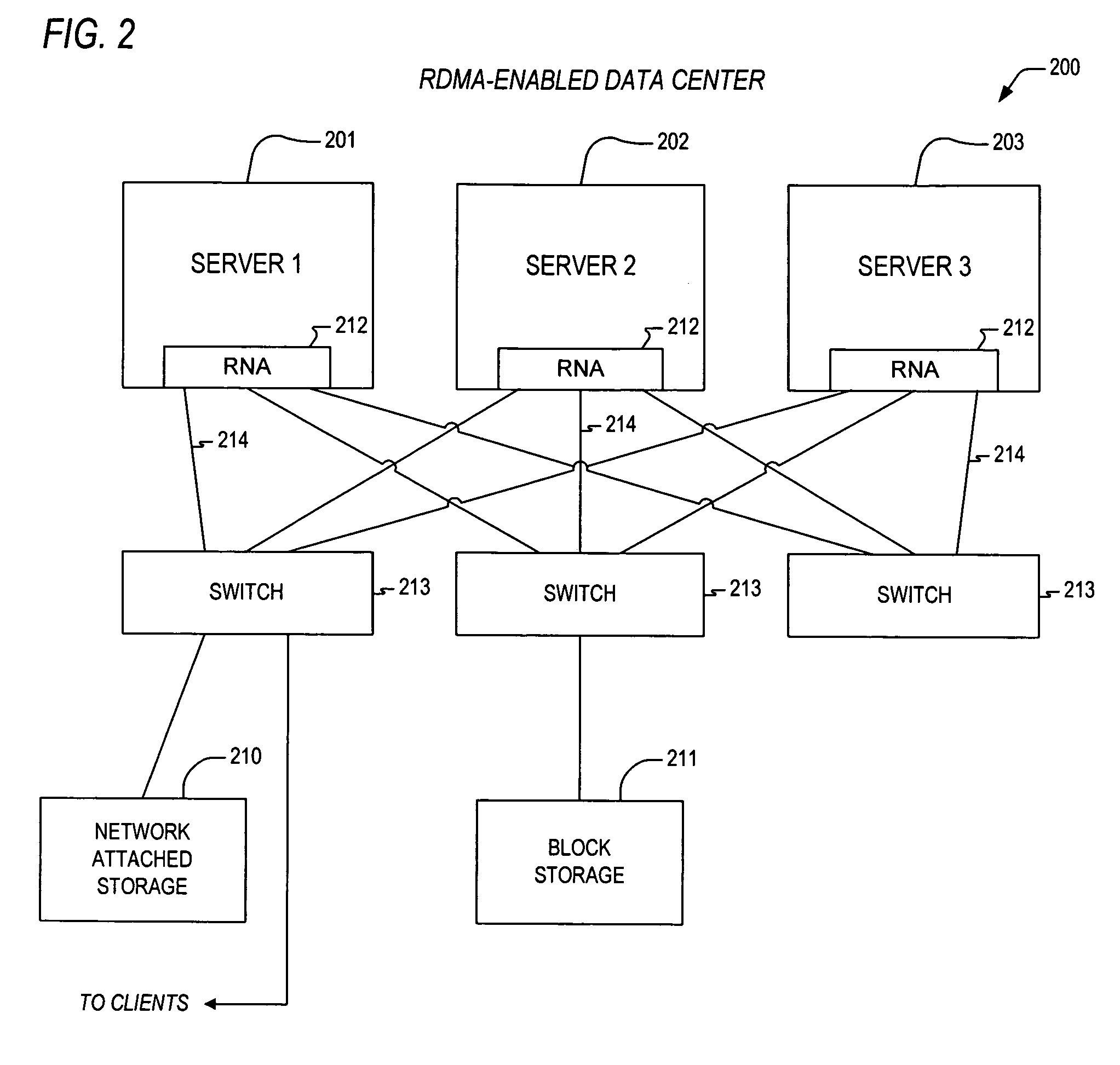
Apparatus and method for out-of-order placement and in-order completion reporting of remote direct memory access operations
InactiveUS20070208820A1Multiple digital computer combinationsTransmissionRemote direct memory accessNetwork structure
A mechanism for performing RDMA operations over a network fabric. Apparatus includes transaction logic to process work queue elements, and to accomplish the RDMA operations over a TCP / IP interface between first and second servers. The transaction logic has out-of-order segment range record stores and a protocol engine. The out-of-order segment range record stores maintains parameters associated with one or more out-of-order segments, the one or more out-of-order segments having been received and corresponding to one or more RDMA messages that are associated with the work queue elements. The protocol engine is coupled to the out-of-order segment range record stores and is configured to access the parameters to enable in-order completion tracking and reporting of the one or more RDMA messages.
Owner:INTEL CORP
Apparatus and method for packet transmission over a high speed network supporting remote direct memory access operations
ActiveUS20060230119A1Efficient and effective rebuildDigital computer detailsTransmissionRemote direct memory accessTerm memory
A mechanism for performing remote direct memory access (RDMA) operations between a first server and a second server over an Ethernet fabric. The RDMA operations are initiated by execution of a verb according to a remote direct memory access protocol. The verb is executed by a CPU on the first server. The apparatus includes transaction logic that is configured to process a work queue element corresponding to the verb, and that is configured to accomplish the RDMA operations over a TCP / IP interface between the first and second servers, where the work queue element resides within first host memory corresponding to the first server. The transaction logic includes transmit history information stores and a protocol engine. The transmit history information stores maintains parameters associated with said work queue element. The protocol engine is coupled to the transmit history information stores and is configured to access the parameters to enable retransmission of one or more TCP segments corresponding to the RDMA operations.
Owner:INTEL CORP
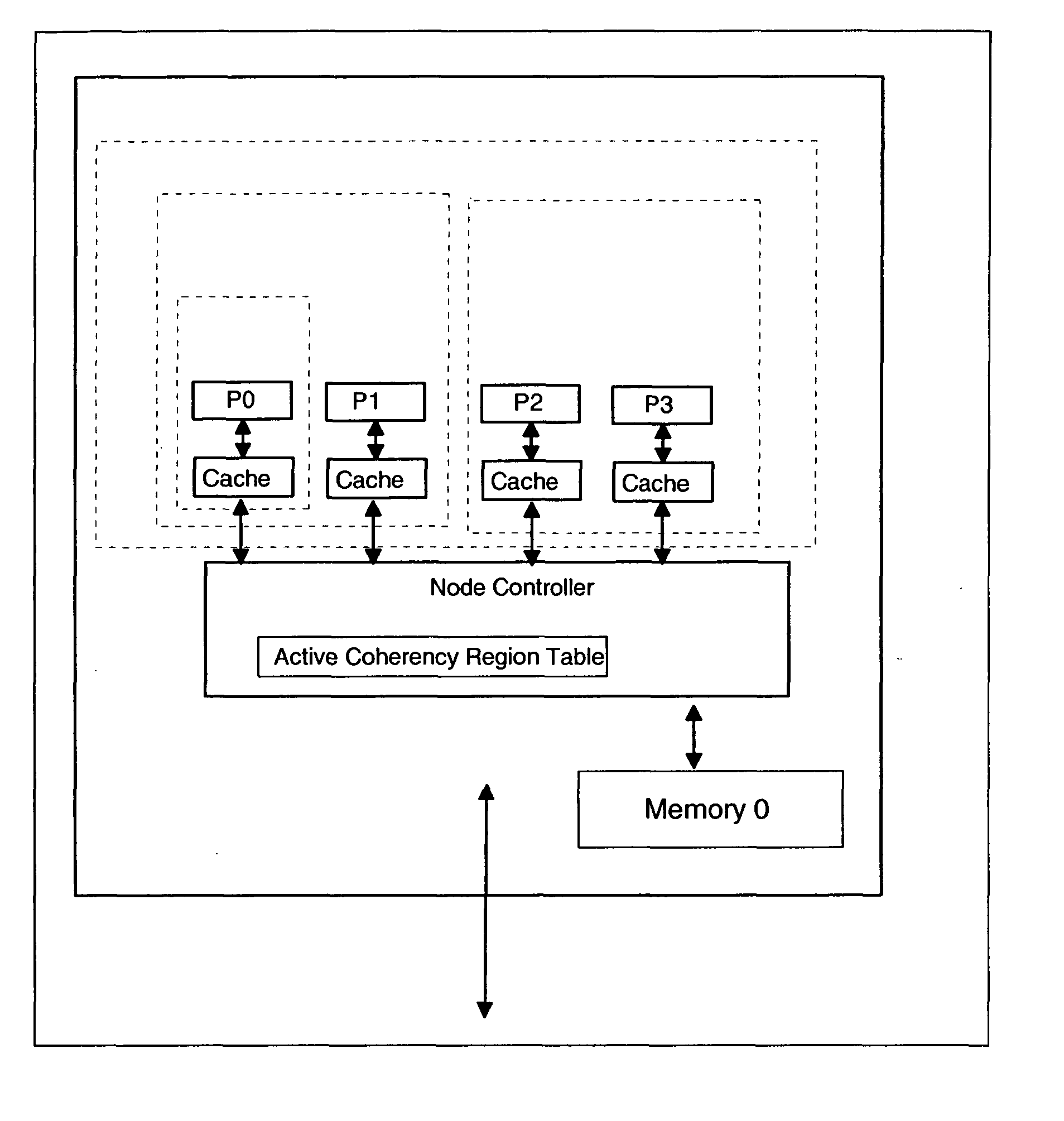
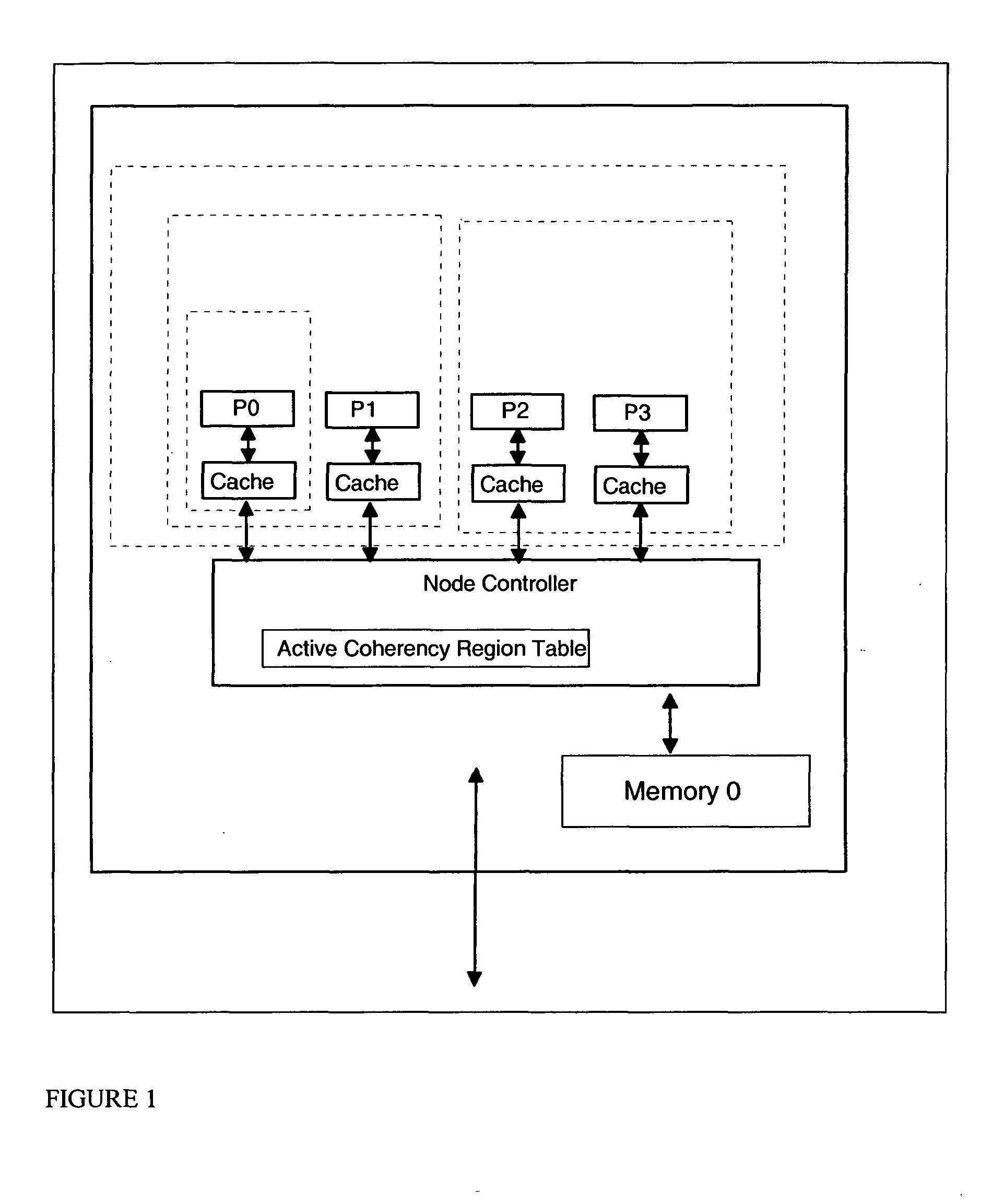
Multiprocessor computer system having multiple coherency regions and software process migration between coherency regions without cache purges
InactiveUS20050021913A1Eliminate needMemory architecture accessing/allocationMemory adressing/allocation/relocationMulti processorPhysics processing unit
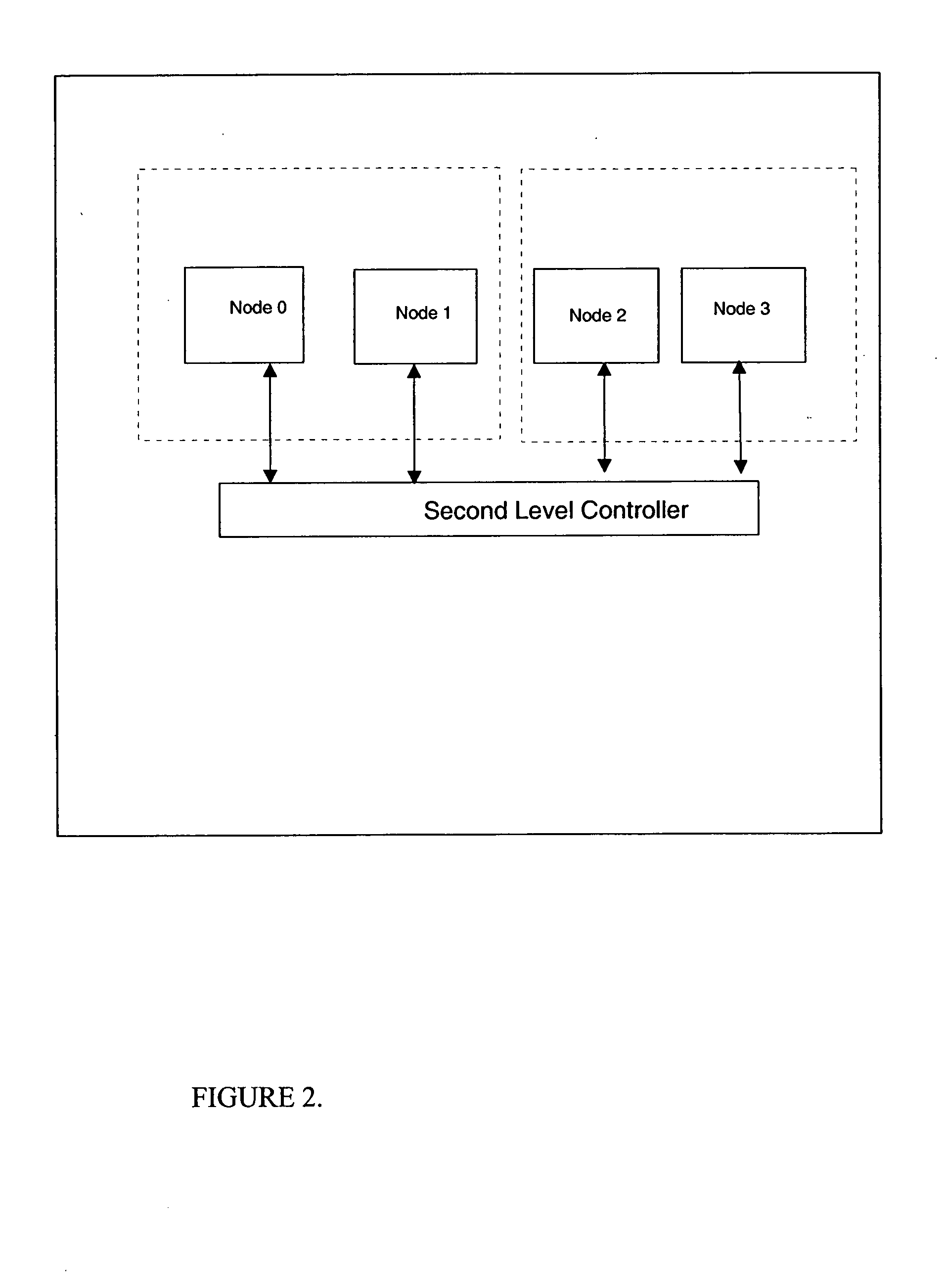
A multiprocessor computer system has a plurality of processing nodes which use processor state information to determine which coherent caches in the system are required to examine a coherency transaction produced by a single originating processor's storage request. A node of the computer has dynamic coherency boundaries such that the hardware uses only a subset of the total processors in a large system for a single workload at any specific point in time and can optimize the cache coherency as the supervisor software or firmware expands and contracts the number of processors which are being used to run any single workload. Multiple instances of a node can be connected with a second level controller to create a large multiprocessor system. The node controller uses the mode bits to determine which processors must receive any given transaction that is received by the node controller. The second level controller uses the mode bits to determine which nodes must receive any given transaction that is received by the second level controller. Logical partitions are mapped to allowable physical processors. Cache coherence regions which encompass subsets of the total number of processors and caches in the system are chosen for their physical proximity. A distinct cache coherency region can be defined for each partition using a hypervisor.
Owner:IBM CORP
Distributed system and method for guaranteeing transaction consistency and linear consistency
ActiveCN109977171AGuaranteed Conflict Serializable SchedulingEfficient fusionDatabase updatingDatabase distribution/replicationExecution planTimestamp
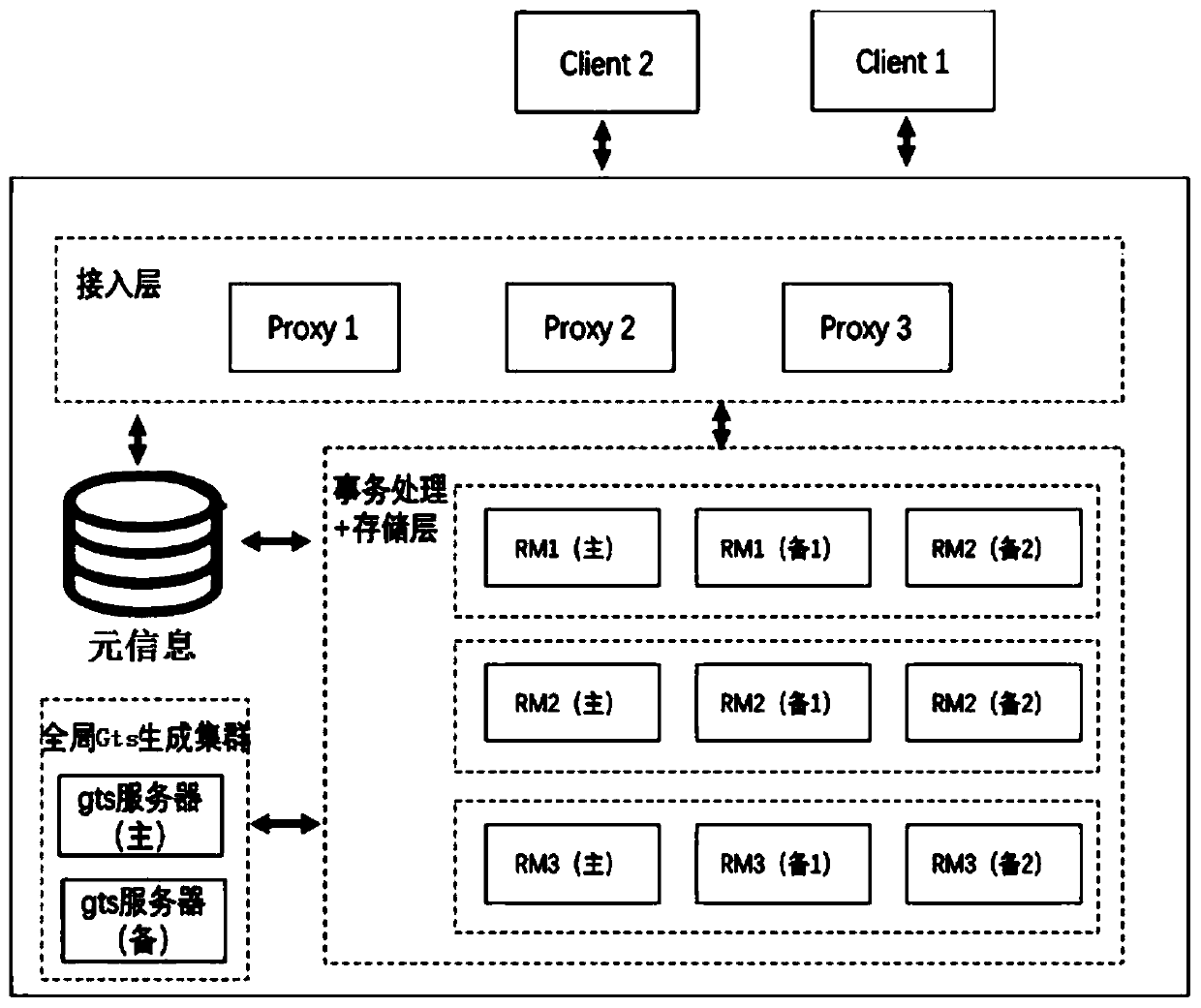
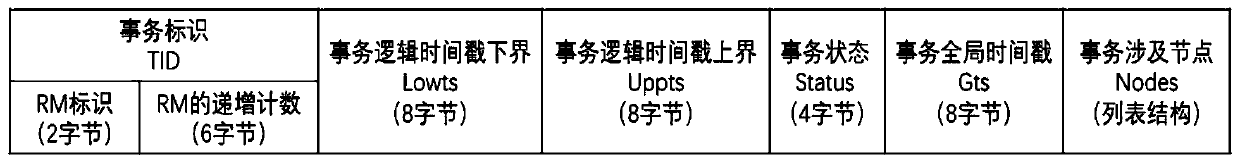
The invention relates to a distributed system and method for guaranteeing transaction consistency and linear consistency. The distributed system comprises a plurality of clients and a database servercomposed of an access layer, a meta-information management cluster, a global Gts generation cluster and a transaction processing and storage layer. The client is used for providing an interface for interaction with the database server for a user and sending a user request to the database server; the access layer is used for receiving the request sent by the client and analyzing to generate an execution plan; the meta-information management cluster is used for managing the distributed cluster; the global Gts generation cluster is used for generating a global timestamp and uniquely sorting global transactions in the distributed system to realize linear consistency; and the transaction processing and storage layer comprises a plurality of resource management nodes and is used for executing the transaction logic according to the execution plan sent by the access layer, and an obtained result is returned to the client through the access layer. The method and the system can be widely appliedto the field of data processing.
Owner:RENMIN UNIVERSITY OF CHINA
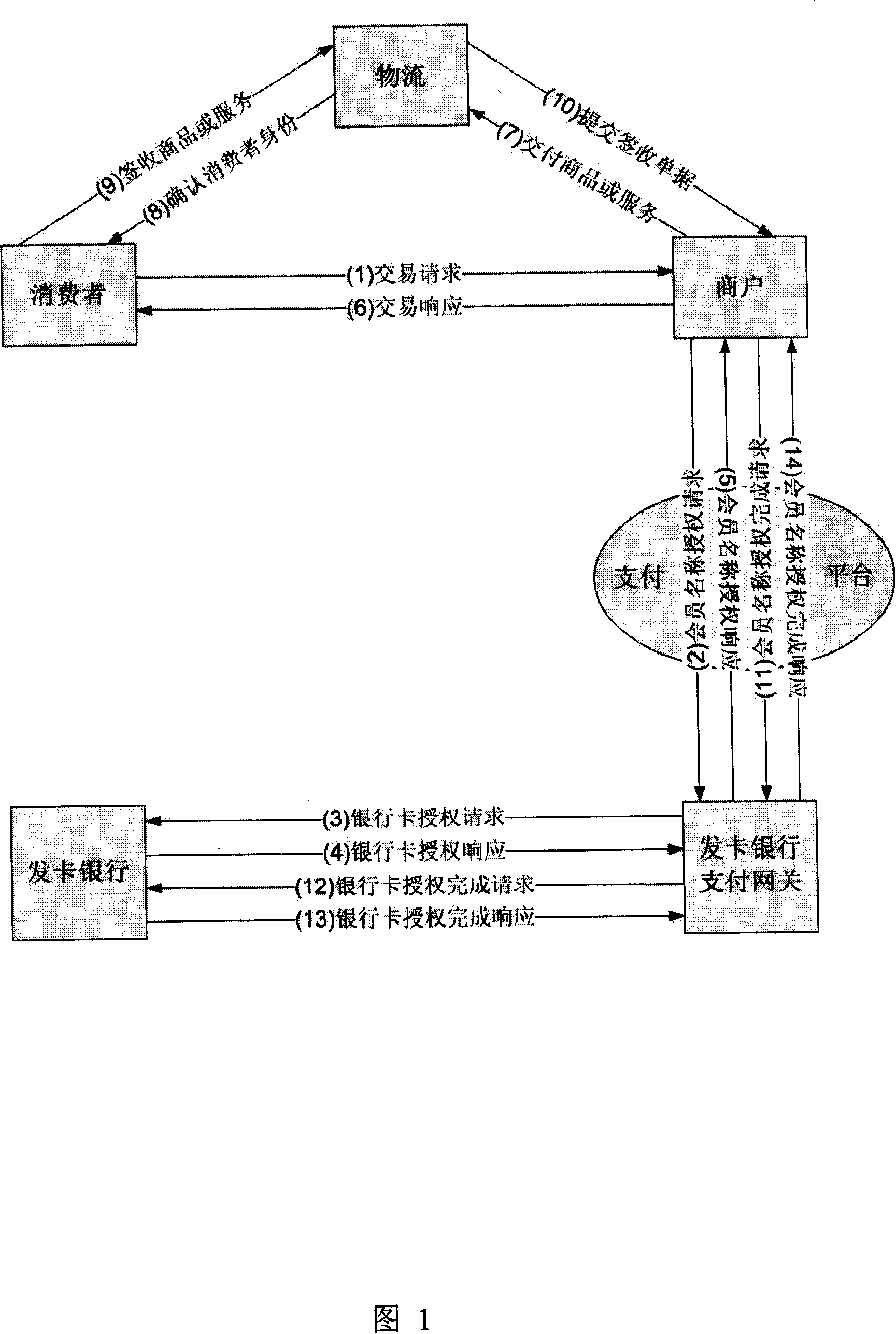
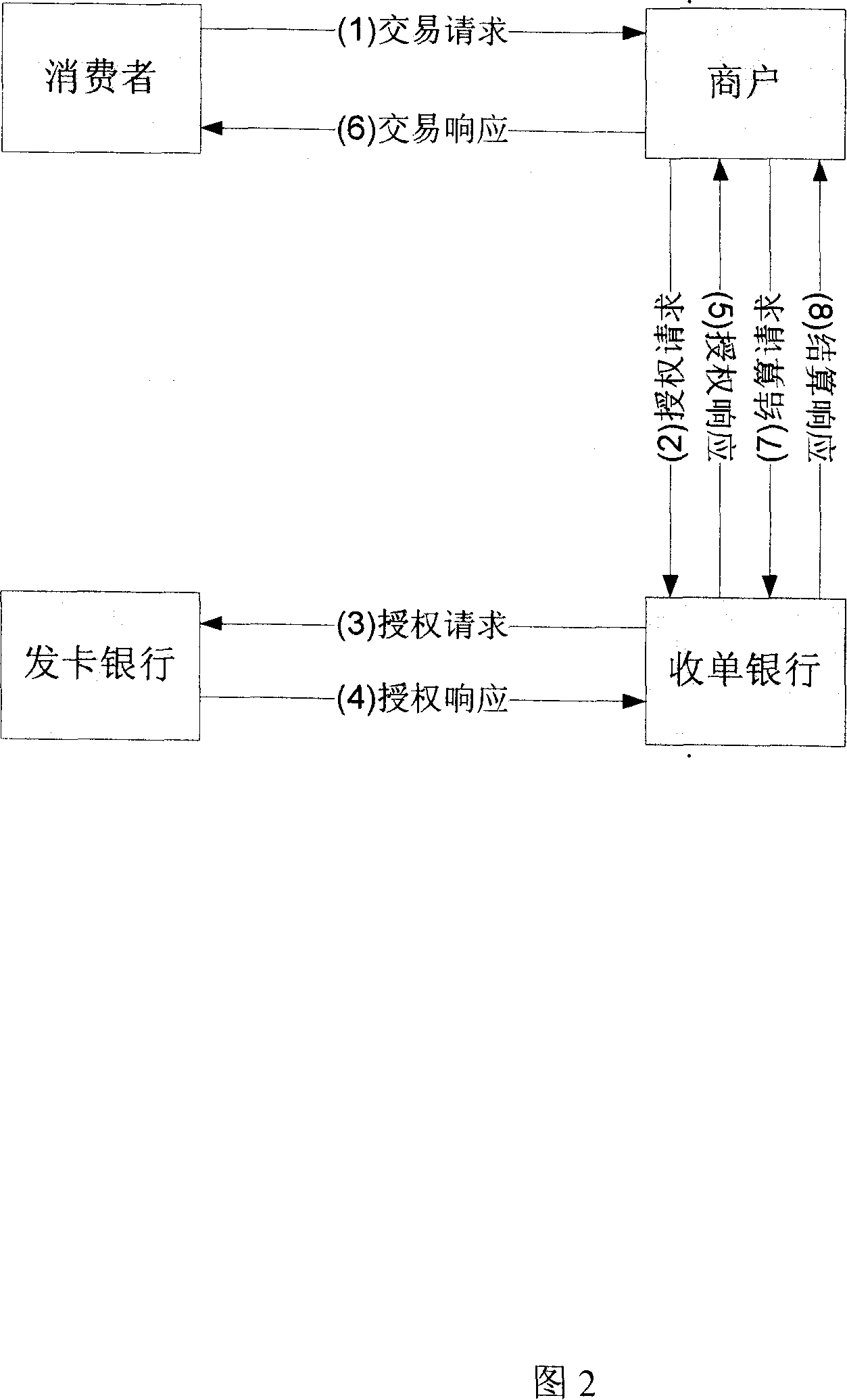
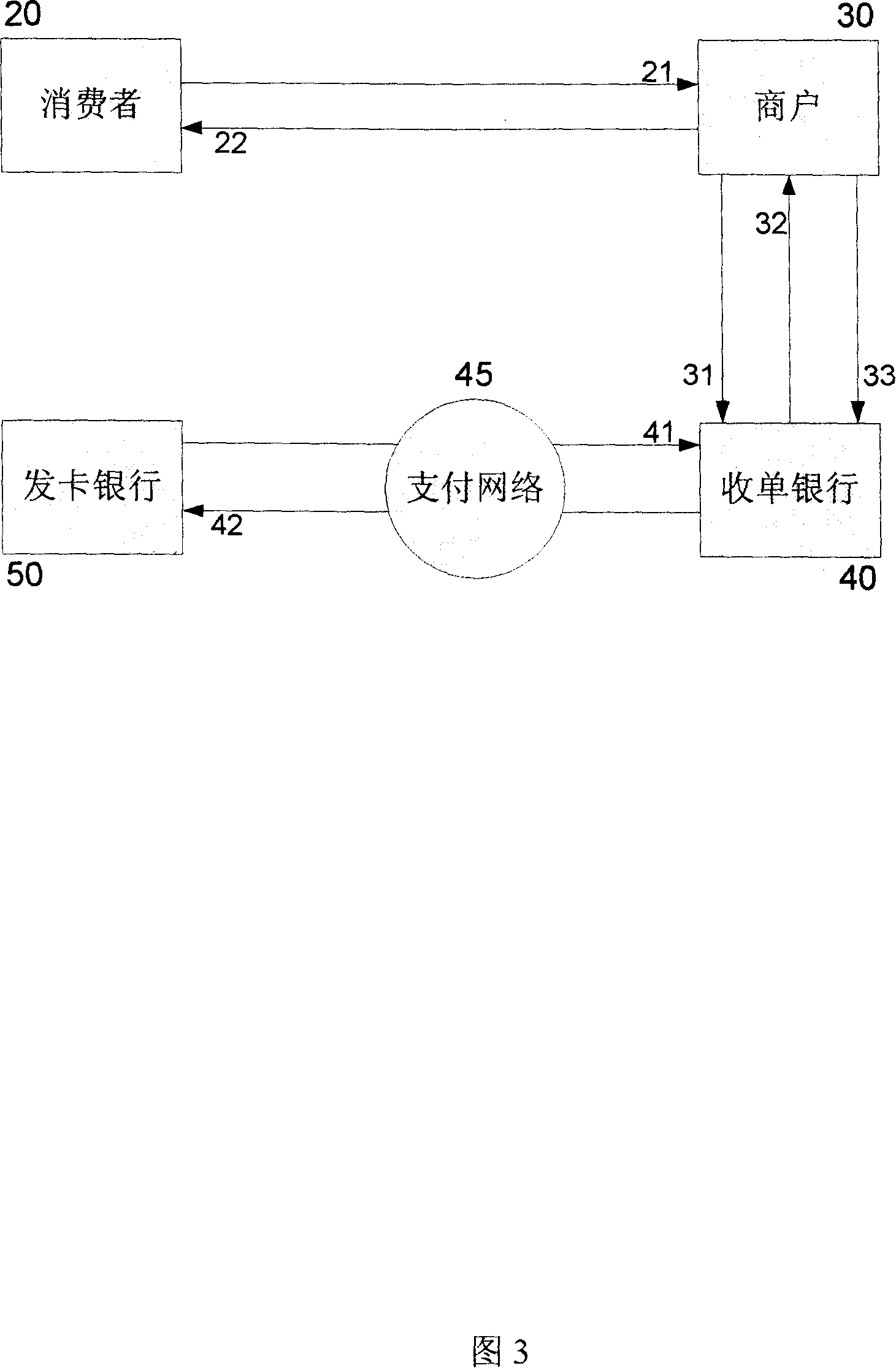
Member name and bank card binding electronic business system and method
InactiveCN101071490AExpand user baseSimple processPayment architectureCommerceIssuing bankThird party
This invention relates to a method and system of e-commerce through the consumer registering the businesses number name. A system and method to achievement e-commerce transactions In a public network through Member Name, including,at least terminal devices for consumer, commercial tenants pay device, the card issuing bank payment gateway devices, payment platform devices and the third party logistics unit. Its property is through bundling with the establishment of the card issuing bank payment gateway Member name and their bank cards card number, when consumers apply for e-commerce transactions to the business community, need not submit personal information of bank cards will be able to activate the e-commerce transactions logic, the logic coverage of the state of e-commerce transactions, through unbundling transactions steps to improve the authenticity of transactions, reliability, safety; passage of this invention, consumers can break through the traditional limitations of electronic commerce terminal devices, more convenient, flexible in e-commerce, without worrying about their bank cards leaked confidential information, while businesses can be more convenient and credible conduct of e-commerce; card-issuing banks can develop electronic commerce based on depay without changing existing business processes.
Owner:田小平
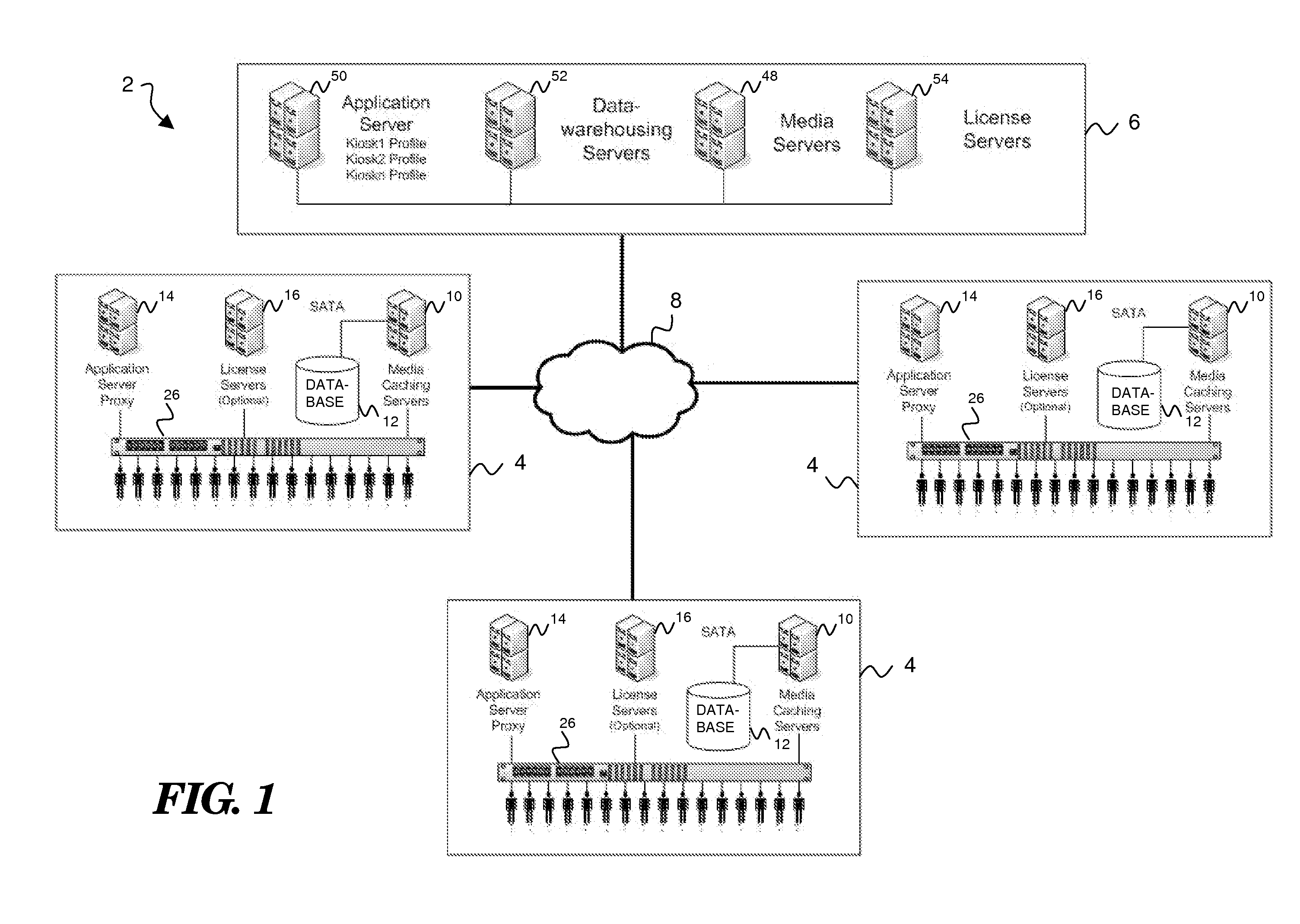
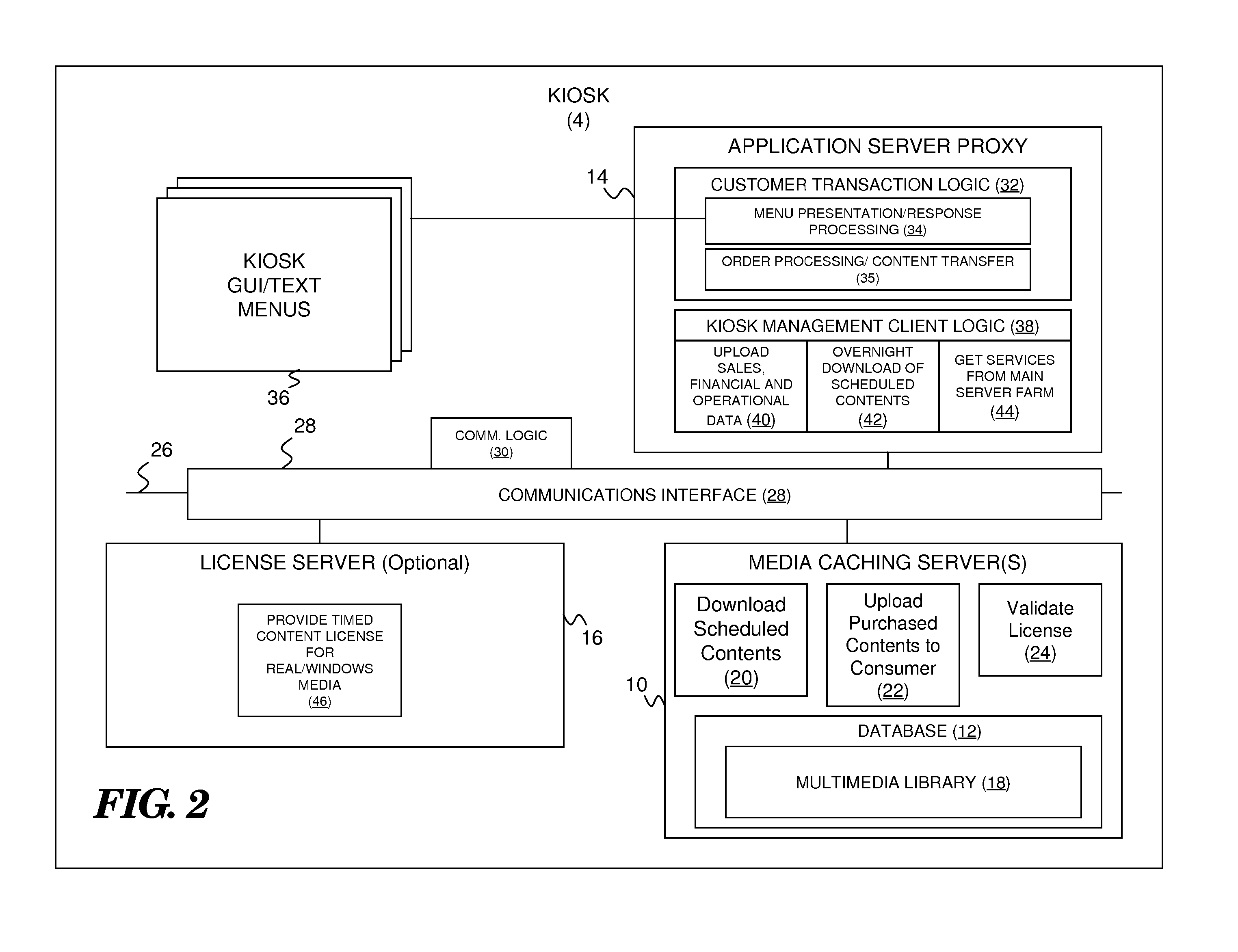
Electronic Sell-Through Of Multimedia Content Through Points-Of-Sale
InactiveUS20070174140A1Buying/selling/leasing transactionsCommunication interfaceElectronic communication
A point-of-sale system for electronic sell-through of multimedia content comprises a kiosk for customer selection and transfer of multimedia content to a customer device. The kiosk may include a local multimedia library containing multimedia content in machine-readable form, a customer communication interface adapted to facilitate electronic communication between the kiosk and a customer device, and customer transaction logic adapted to facilitate customer selection and transfer of multimedia content in the multimedia library to the customer device via the communication interface. A main server may be provided that communicates with the kiosk and other kiosks of like kind in order to oversee kiosk operations and update the local multimedia libraries.
Owner:WARNER BROS ENTERTAINMENT INC
Apparatus and method for packet transmission over a high speed network supporting remote direct memory access operations
A mechanism for performing remote direct memory access (RDMA) operations between a first server and a second server over an Ethernet fabric. The RDMA operations are initiated by execution of a verb according to a remote direct memory access protocol. The verb is executed by a CPU on the first server. The apparatus includes transaction logic that is configured to process a work queue element corresponding to the verb, and that is configured to accomplish the RDMA operations over a TCP / IP interface between the first and second servers, where the work queue element resides within first host memory corresponding to the first server. The transaction logic includes transmit history information stores and a protocol engine. The transmit history information stores maintains parameters associated with said work queue element. The protocol engine is coupled to the transmit history information stores and is configured to access the parameters to enable retransmission of one or more TCP segments corresponding to the RDMA operations.
Owner:INTEL CORP
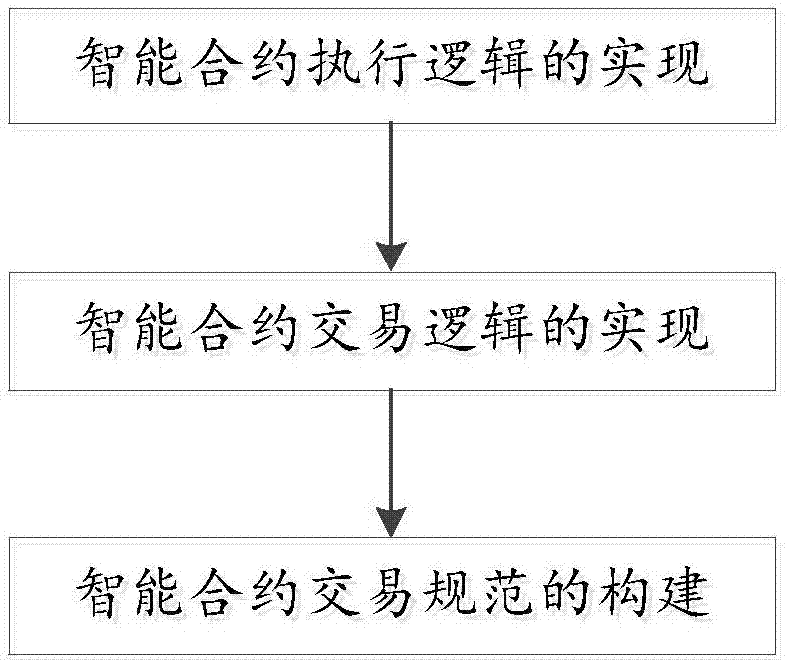
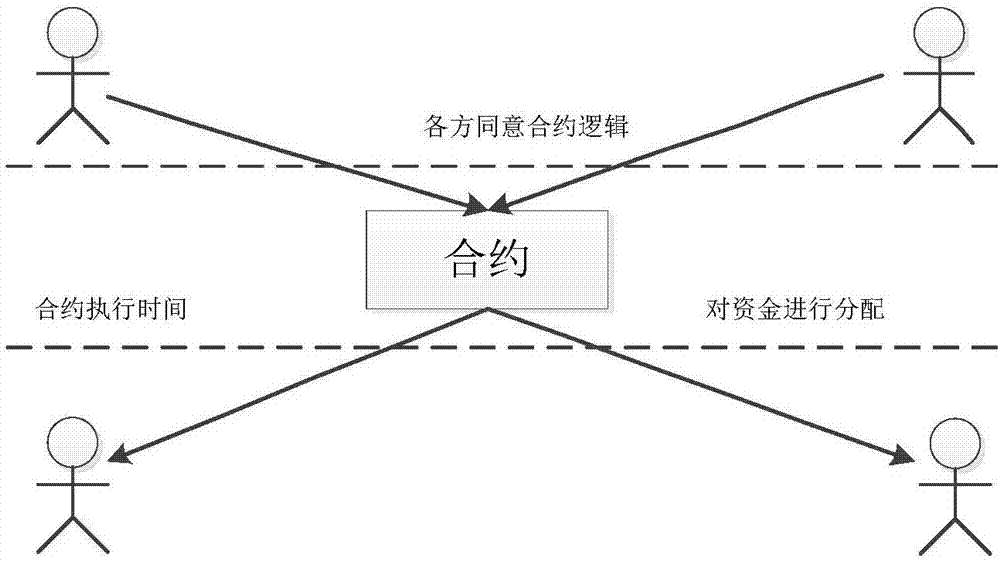
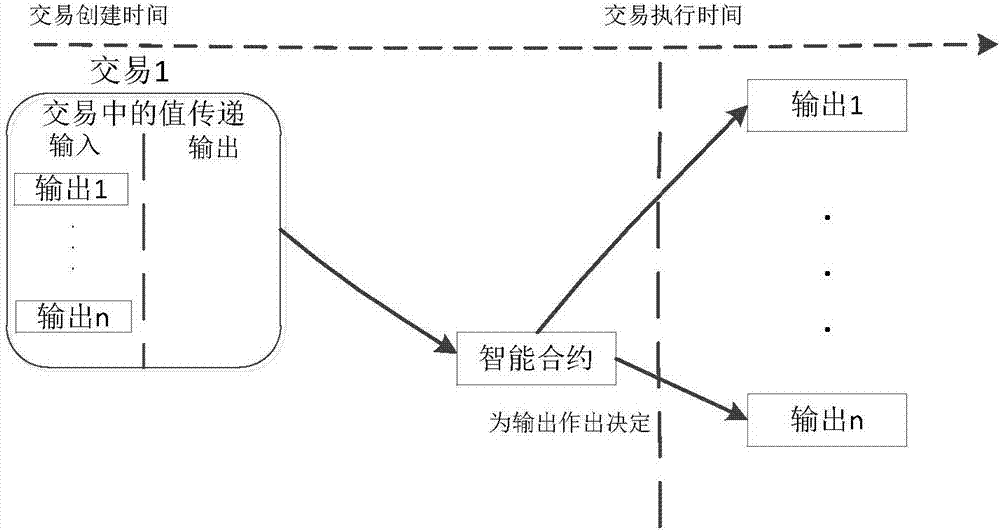
Smart contract type implementation mode of quantum chain system
The invention relates to a smart contract type implementation mode of a quantum chain system. The smart contract type implementation mode includes the realization of smart contract execution logic, the realization of smart contract transaction logic, and the construction of smart contract transaction specification. The smart contract type implementation mode is advantageous in that the execution of a smart contract is highly reliable; even if the parties of the smart contract do not trust each other, the transaction of the smart contract can also be carried out; a mediator is not needed to mediate between the parties; and block chain books in the quantum chain system can be executed automatically without the need for additional personnel.
Owner:钱德君
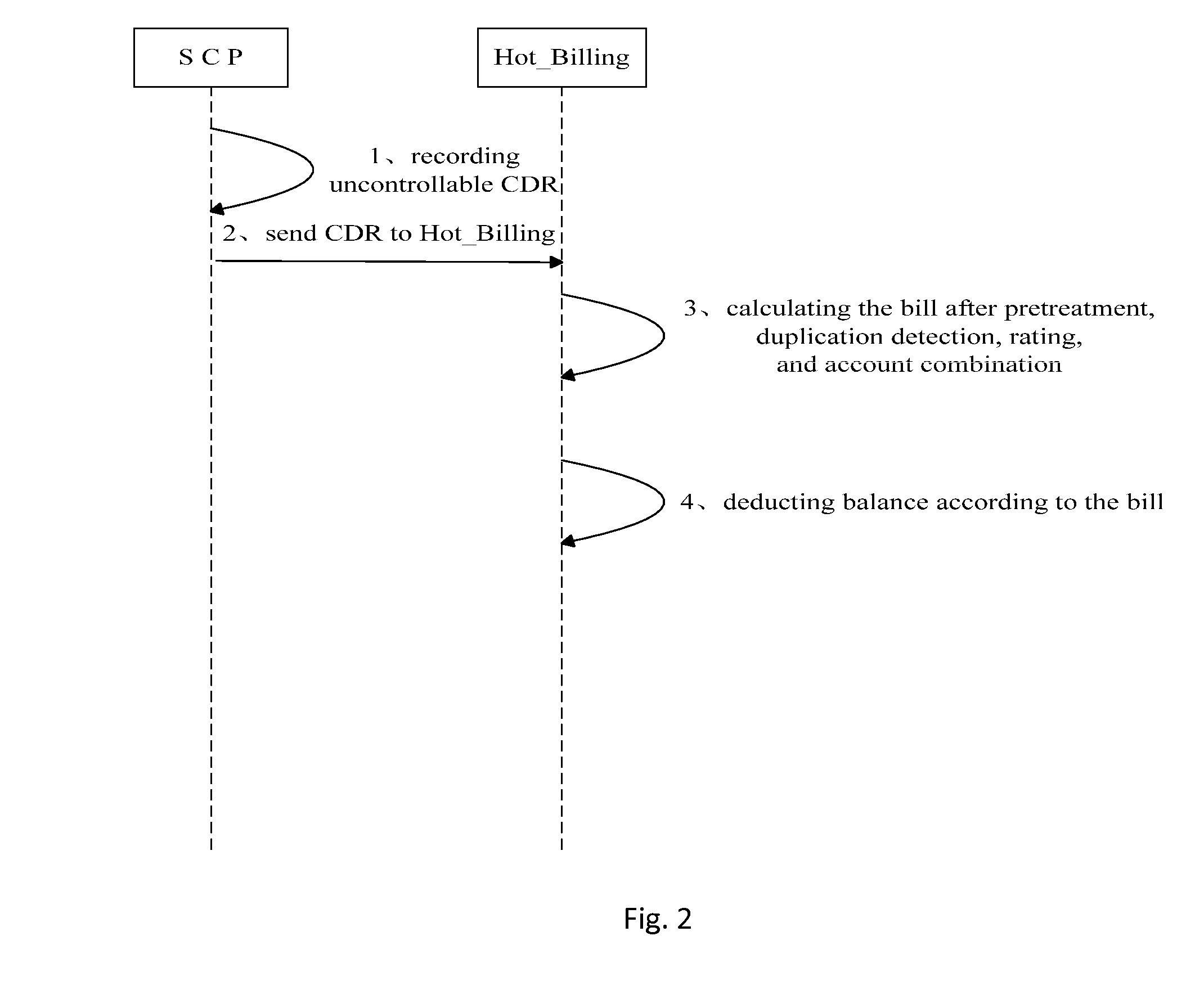
Application Method of Online Charging System in Arrears Risk Control System
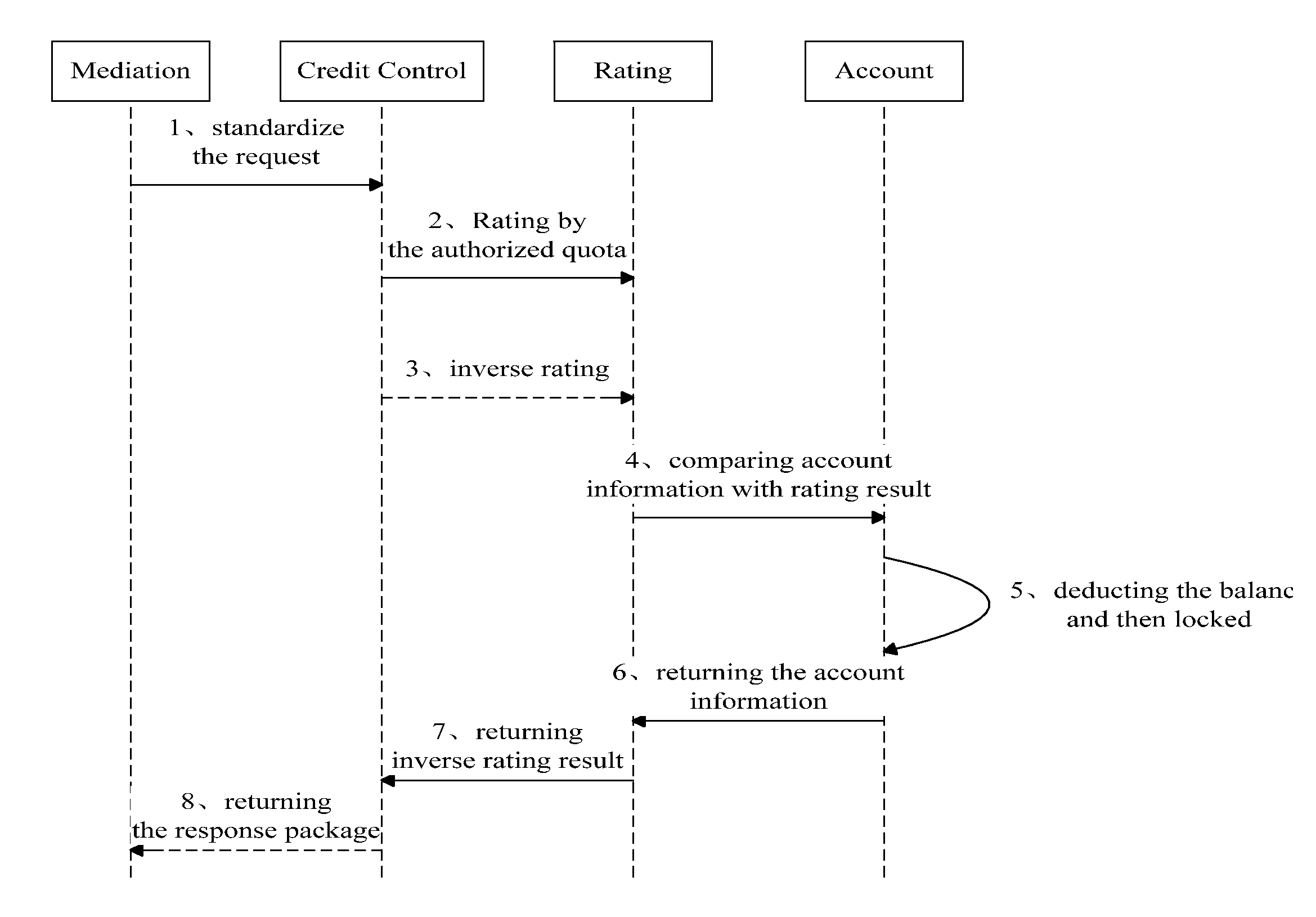
An application method of On-line Charging System in Arrears Risk Control System: 1) The subsystem of OCS, Mediation, communicates with CC Client, receives a credit control request raised by the CC Client and processes with a fault-tolerant management. 2) The Credit Control analyses call request, identifies a type of service and request, selects necessary service transaction logic, and judges an authorized quota of the service, after receiving the quota, the Credit Control requests for real time forward modeling from the Rating. 3) After receiving a price of the service, the Credit Control requests real time inversion from the Rating and meanwhile transfers the price to the Rating. 4) The Rating requests account comparison from the Account after receiving the price. 5) The Account compares the price with a customer's account information to make decision of subsistence lock, if there is enough balance in the account, then the fee of the price will be deducted from the balance and then locked. 6) The Account returns the account information of the compared result. 7) The Rating inverses the authorization amount according to the compared result returned by the Account, and send back to the Credit Control. 8) The Credit Control constructs a service relevant responding package according to the authorization amount, and sends the responding package to the Mediation to complete the OCS processing flow.
Owner:LINKAGE TECH GROUP +1
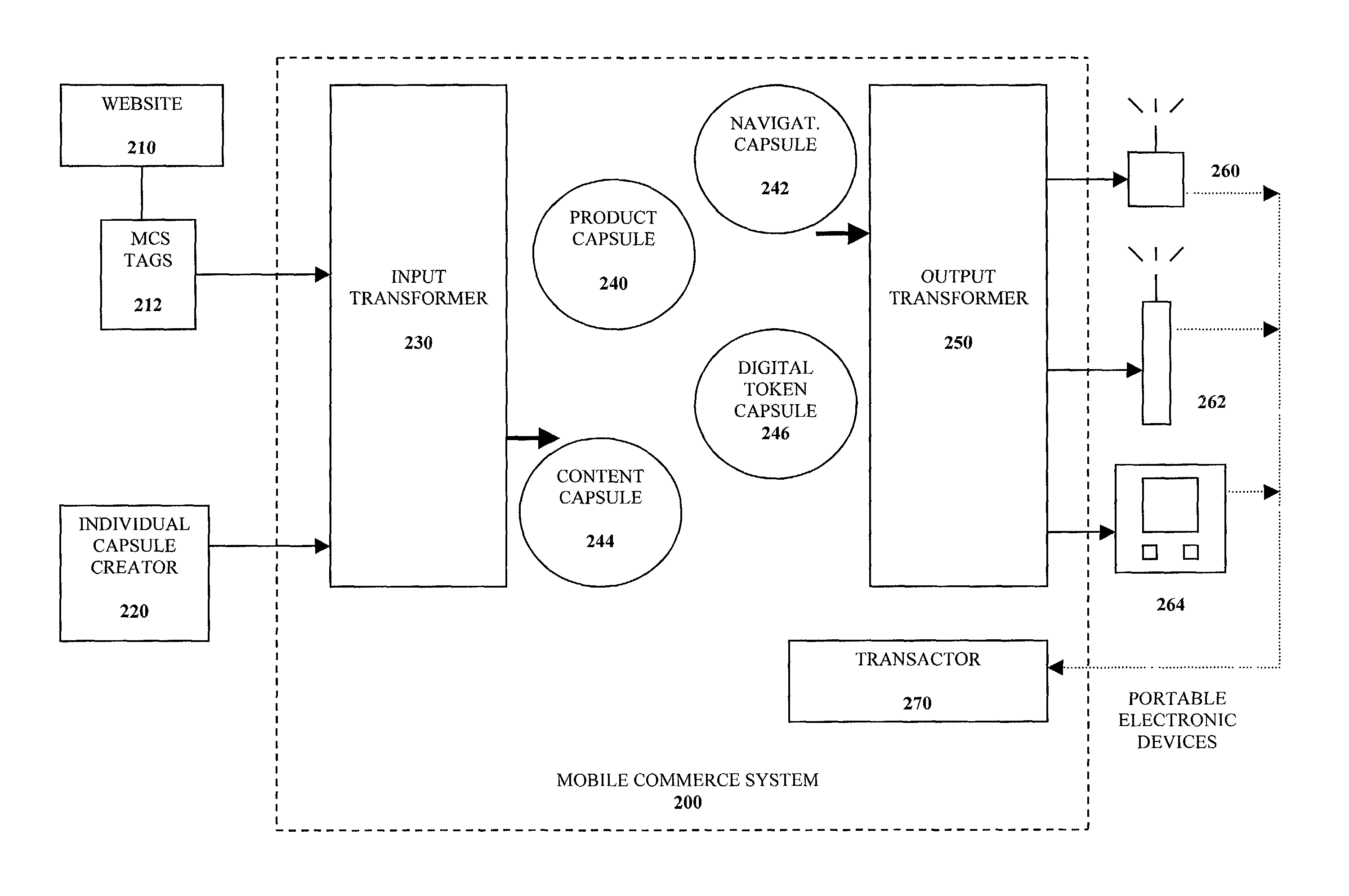
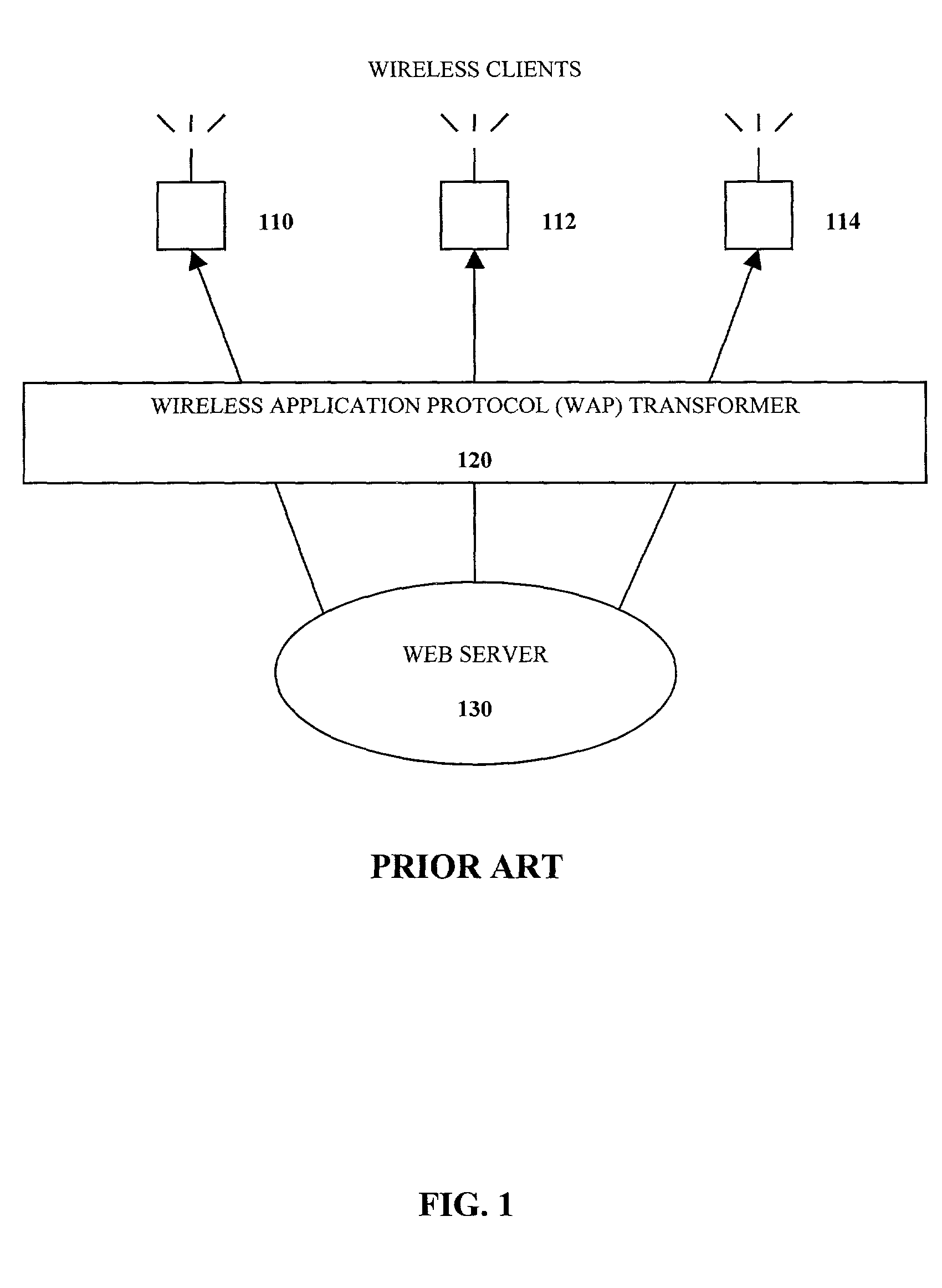
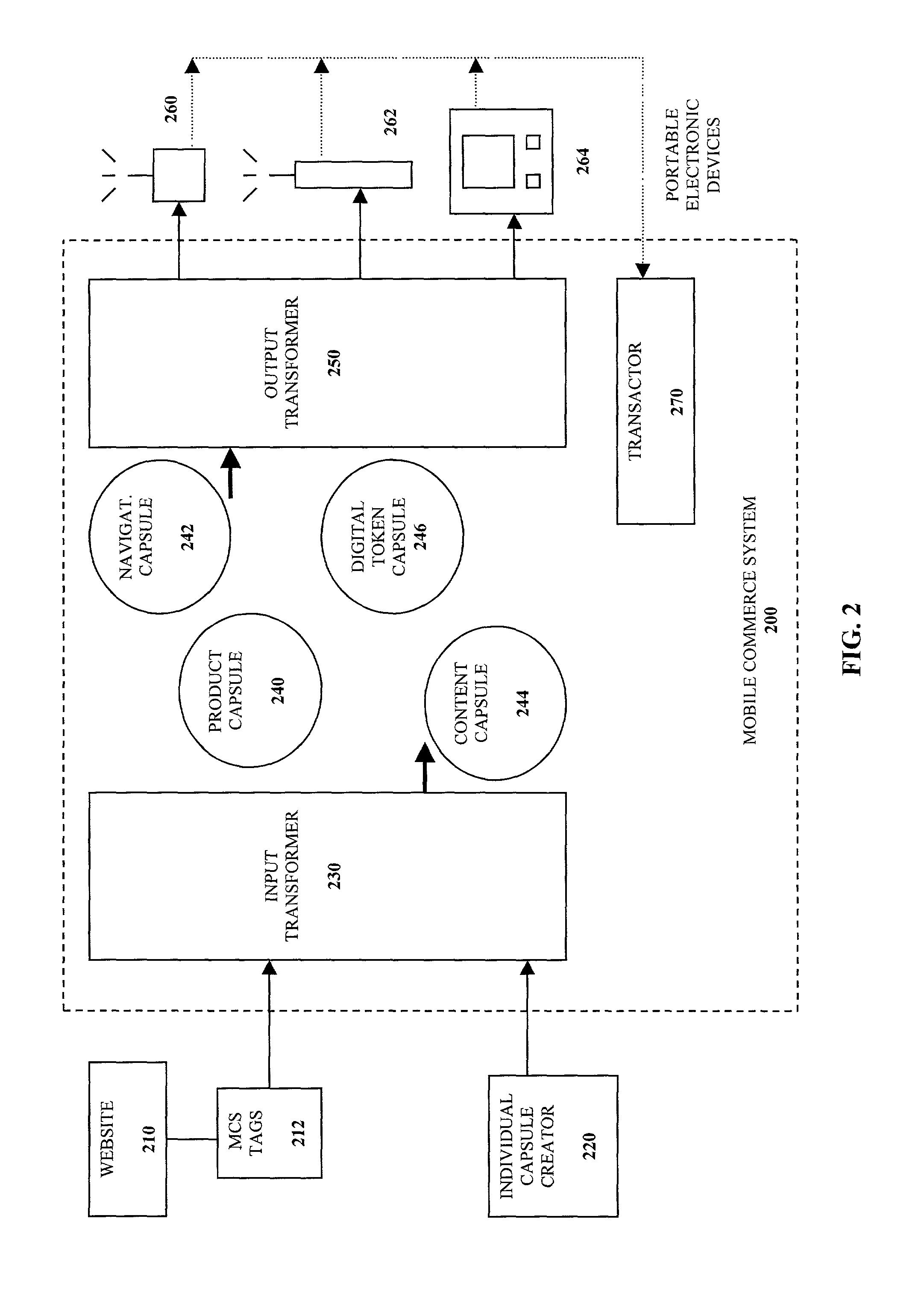
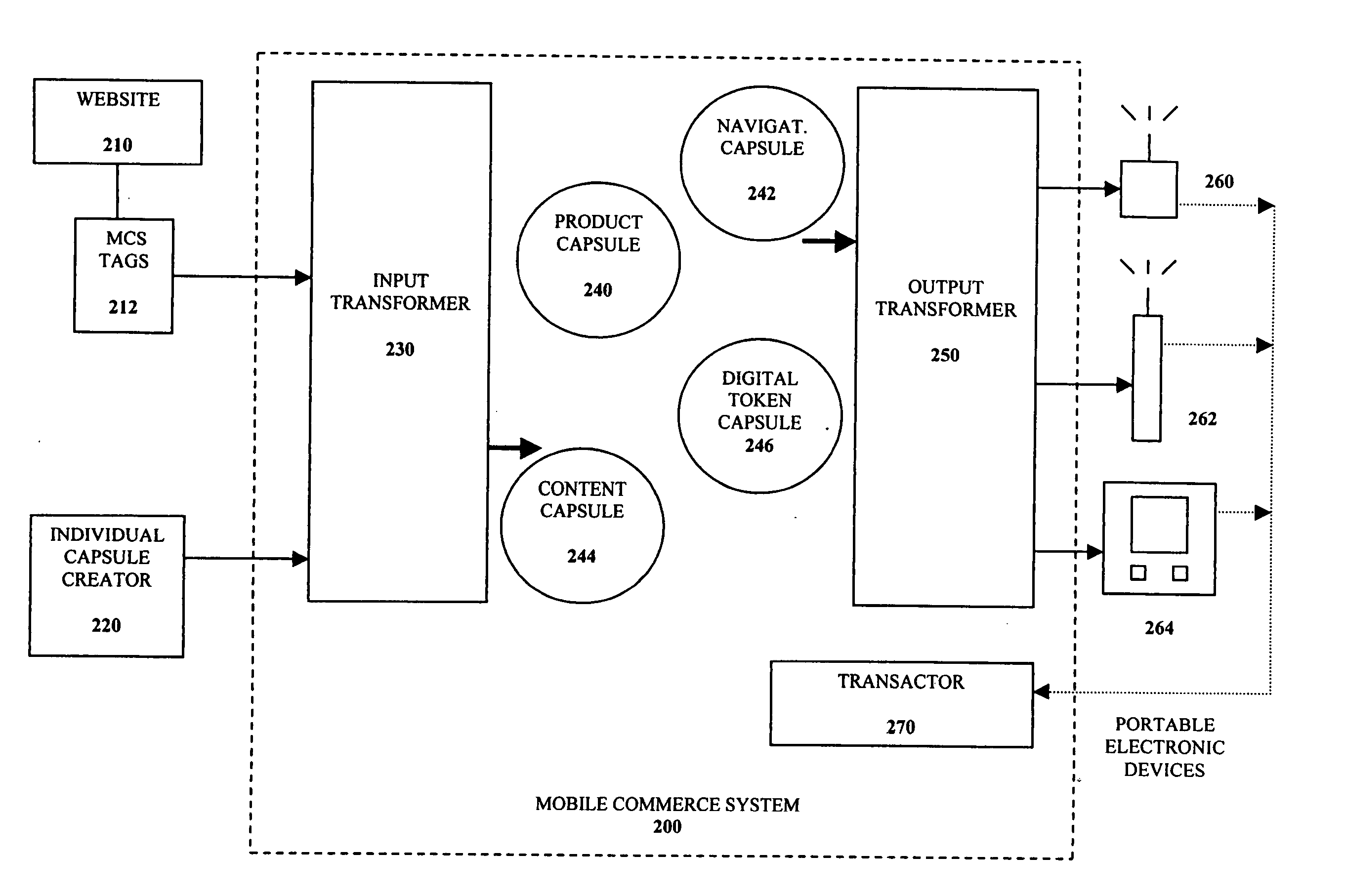
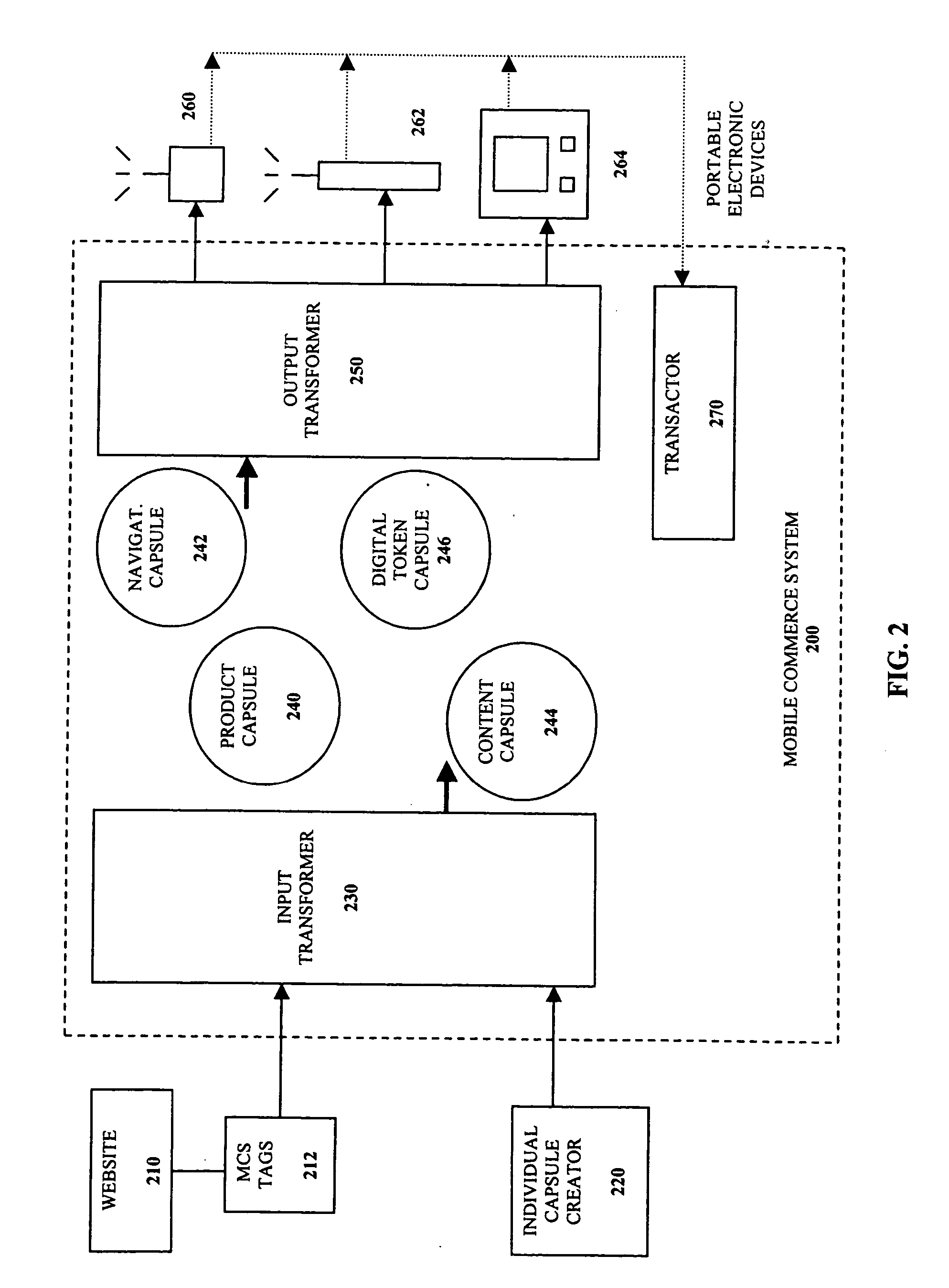
Self-contained business transaction capsules
InactiveUS7107236B2Computer security arrangementsBuying/selling/leasing transactionsDatabaseTransaction logic
A self-contained business transaction capsule to conduct a wireless transaction includes data regarding the wireless transaction. Transaction logic is provided to complete the wireless transaction. The self-contained business transaction capsule is adapted to be broadcasted to and stored on a portable electronic device.
Owner:ROAMING MESSENGER
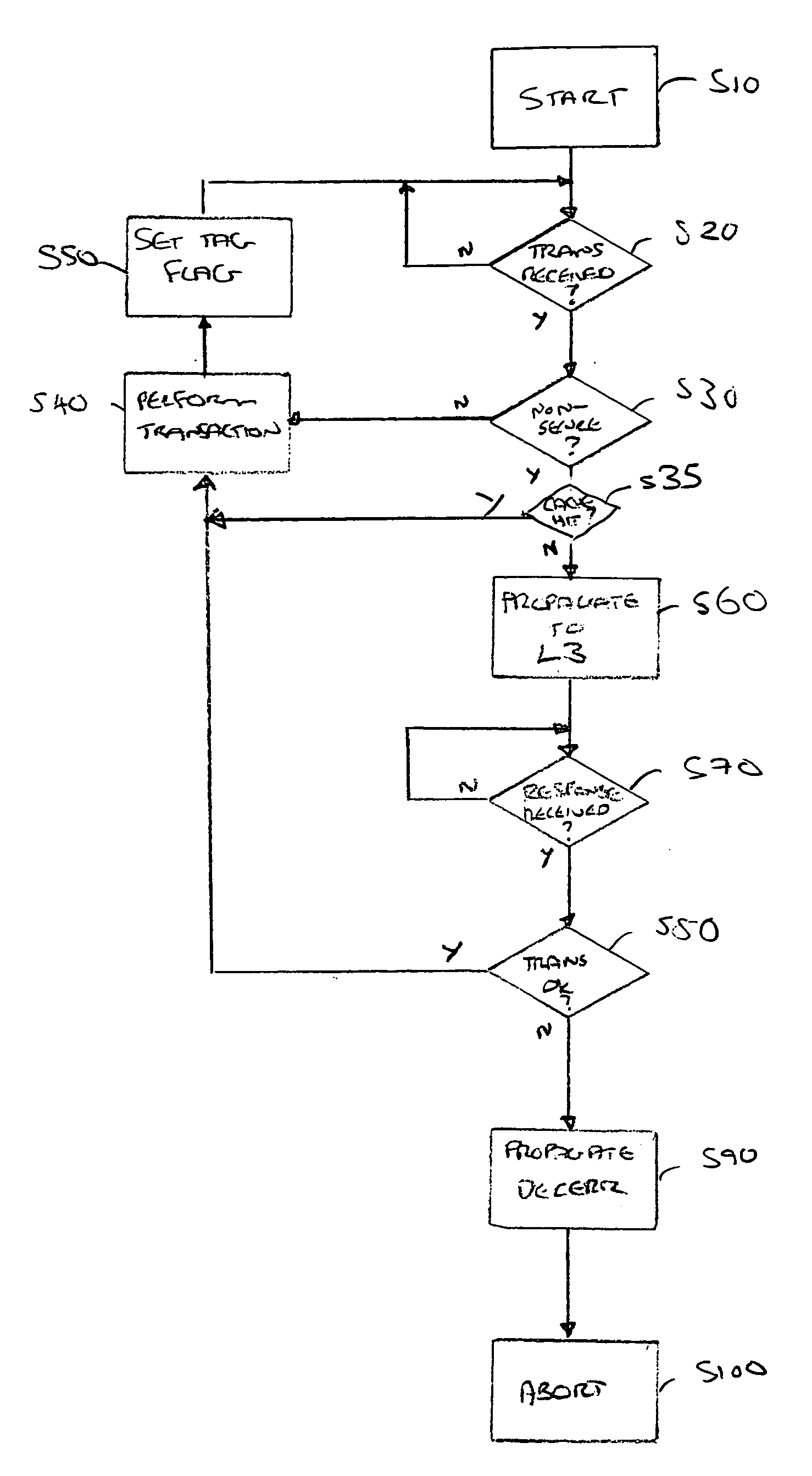
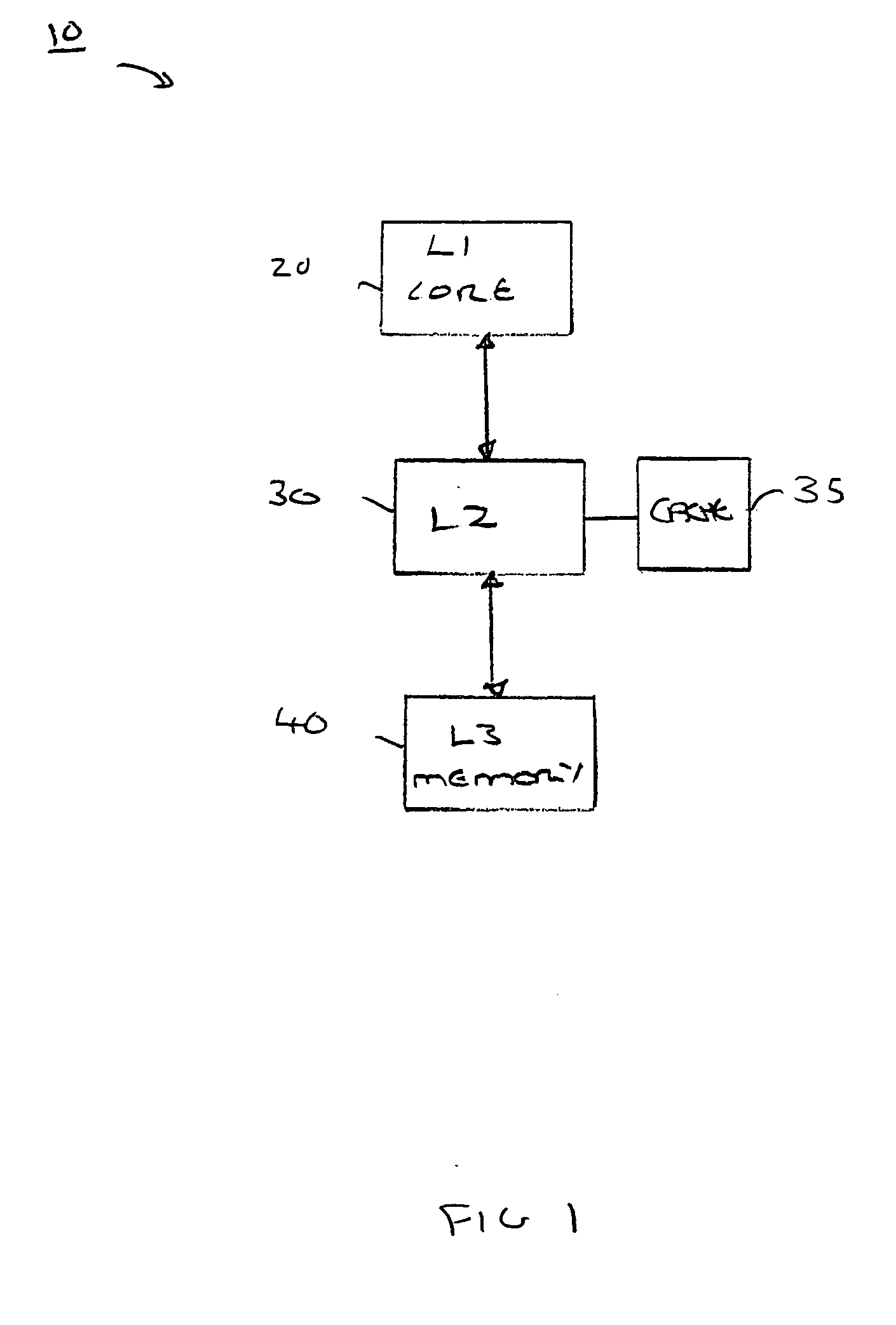
Data processing apparatus security
ActiveUS20060184804A1Reduce riskBlock completeUnauthorized memory use protectionHardware monitoringData accessSecurity properties
A data processing apparatus operable to access data values, each data value being associated with a respective address value is disclosed. The data processing apparatus comprises: a processor operable to process an instruction which causes a data access request; a main memory operable to store data values, said main memory having a region of secure data values; a cache operable to store previously accessed data values; and cache interface logic comprising: data transaction logic operable to receive a data access request from said processor requesting a data value be accessed in said cache, said data access request having an address value and a security attribute associated therewith; and security determination logic operable, in the event that said security attribute indicates a non-secure data access request, to determine whether said non-secure data access request is associated with said region of secure data values by interrogating a data region allocation table and, in the event that said data region allocation table provides an indication that said address value is not associated with said secure data region, to enable said data access request to complete. By determining whether the non-secure data access request is not associated with the region of secure data, it is possible to ensure that no non-secure data accesses occur for address values within a secure region.
Owner:ARM LTD
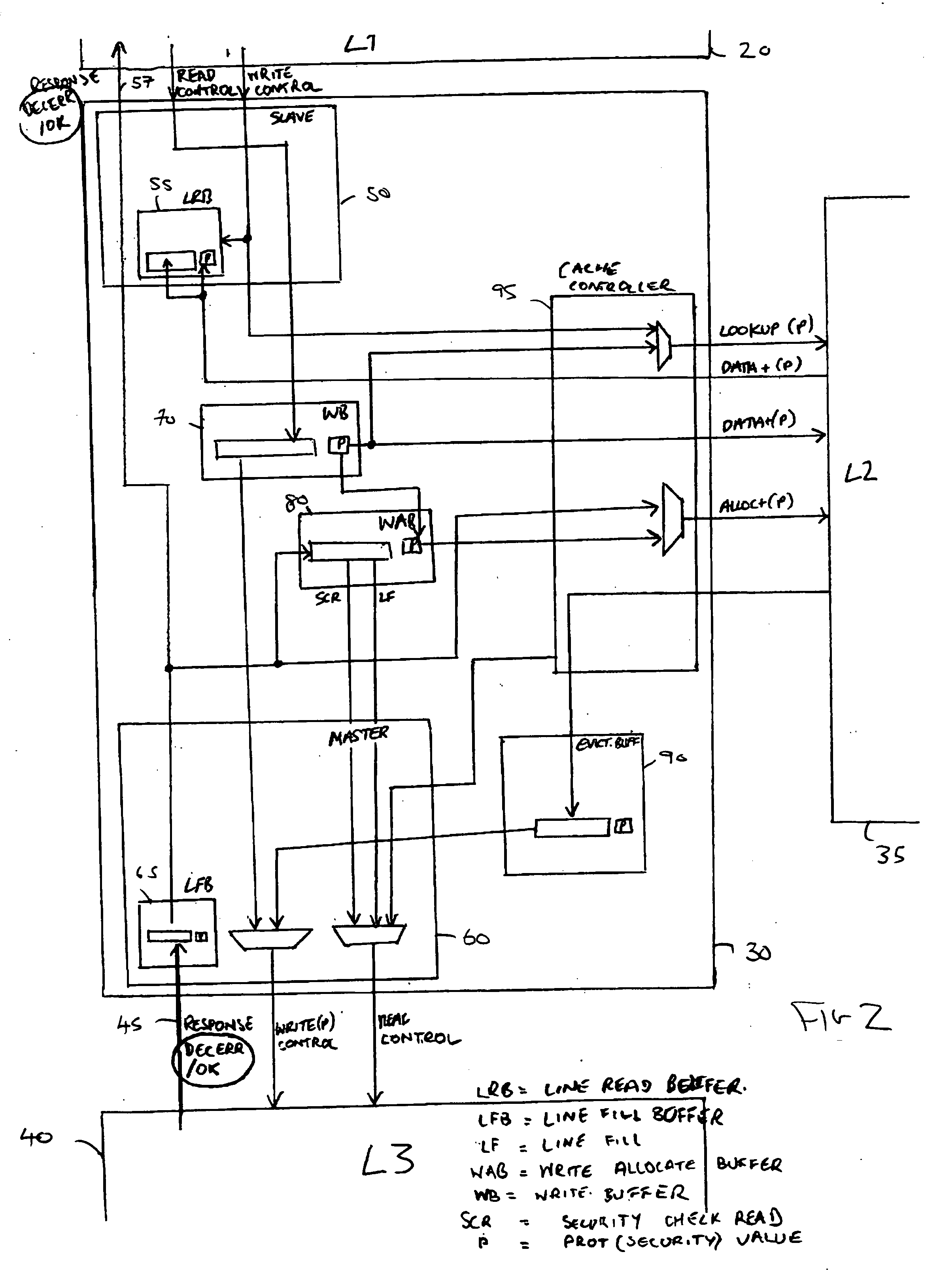
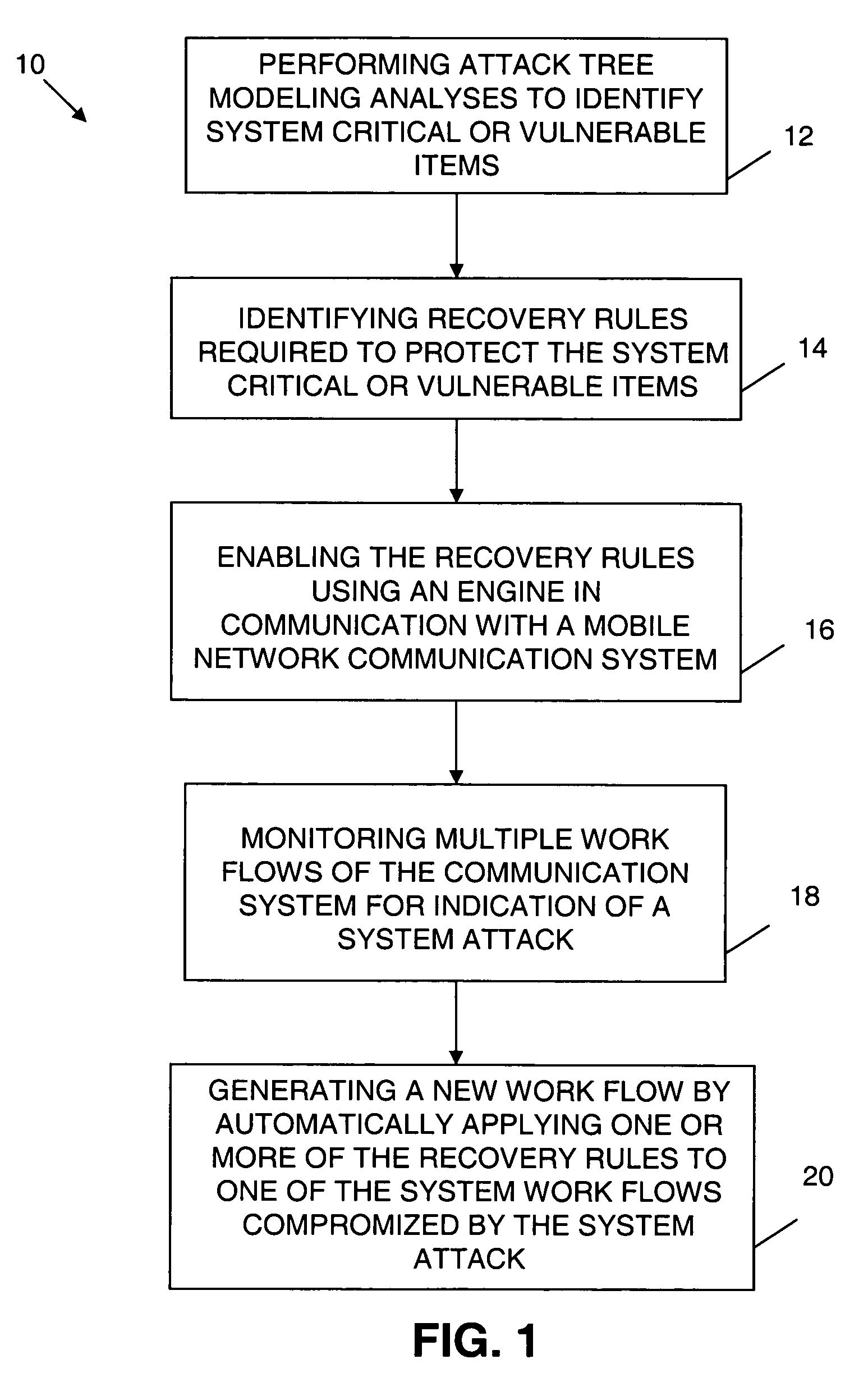
Mobile network dynamic workflow exception handling system
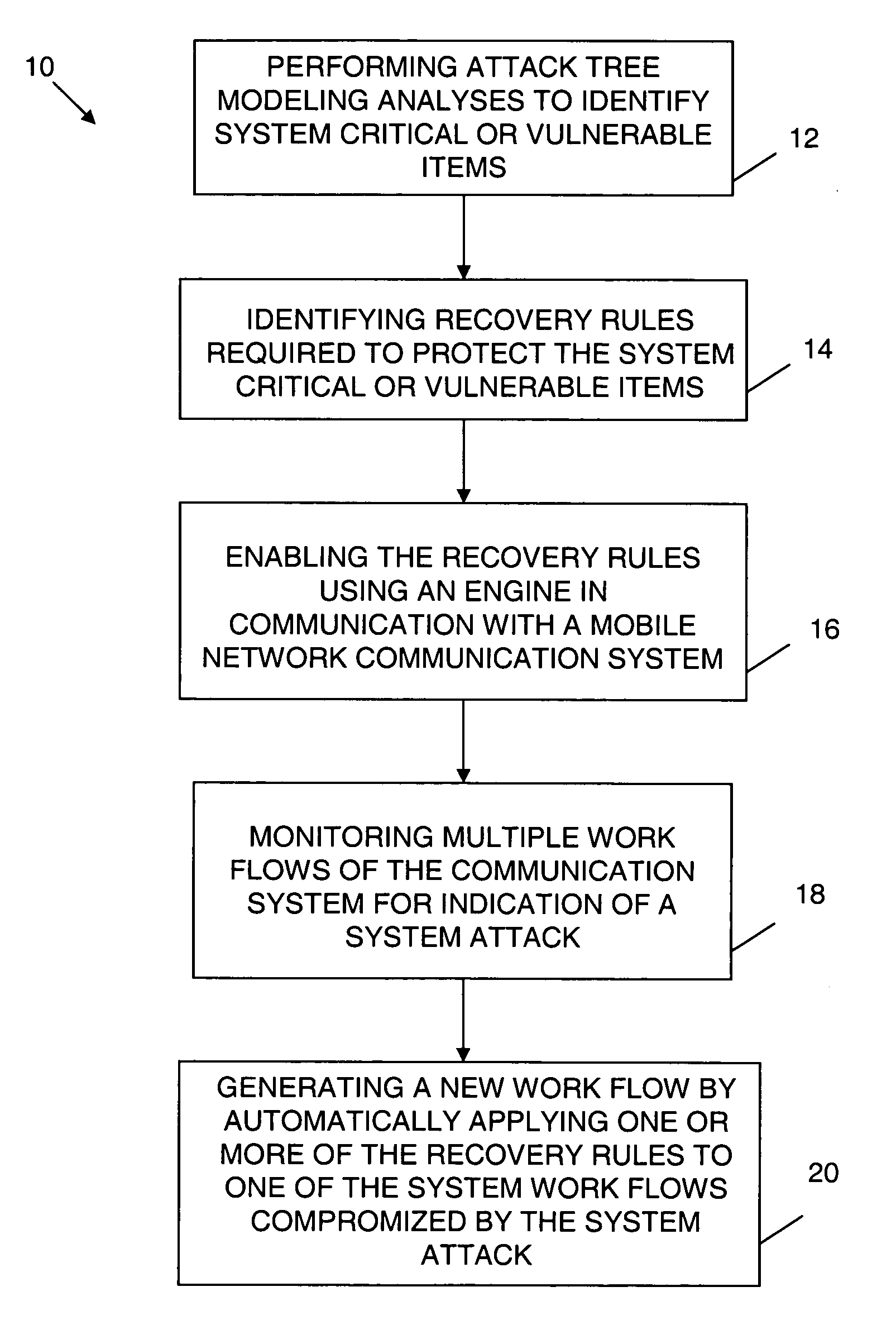
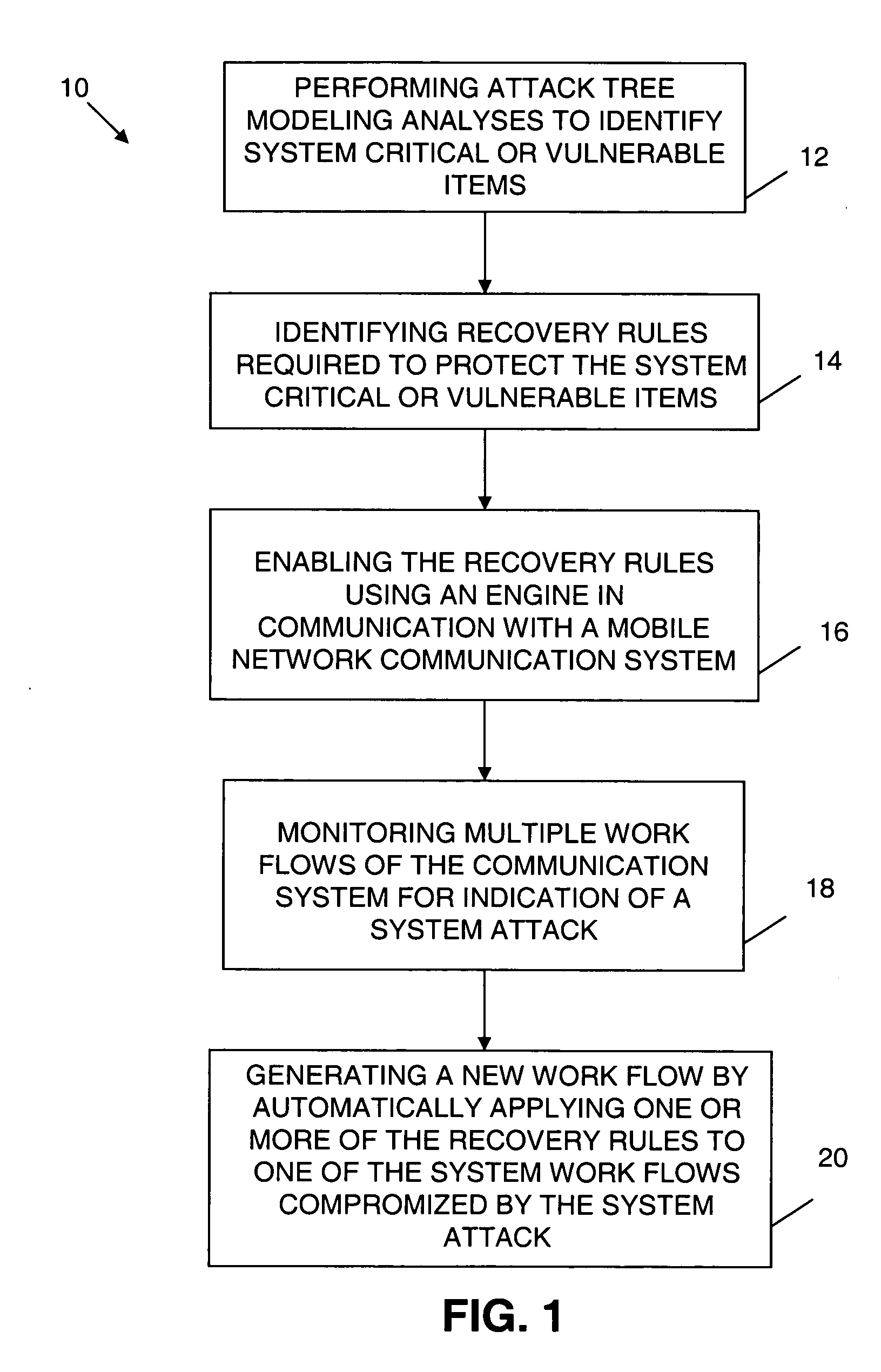
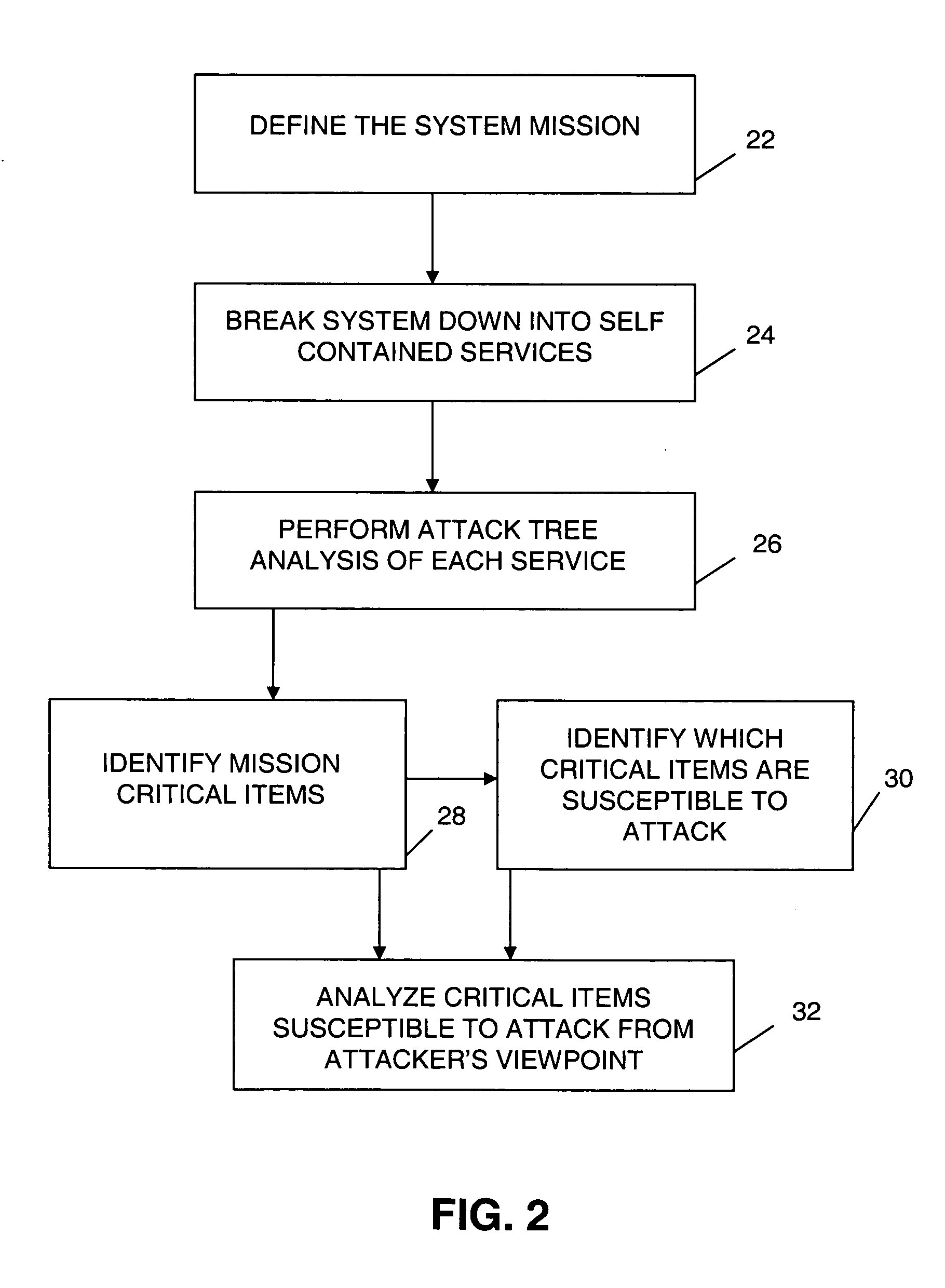
ActiveUS20060259341A1Promote recoveryImprove survivabilityDigital computer detailsResourcesNetwork communicationHandling system
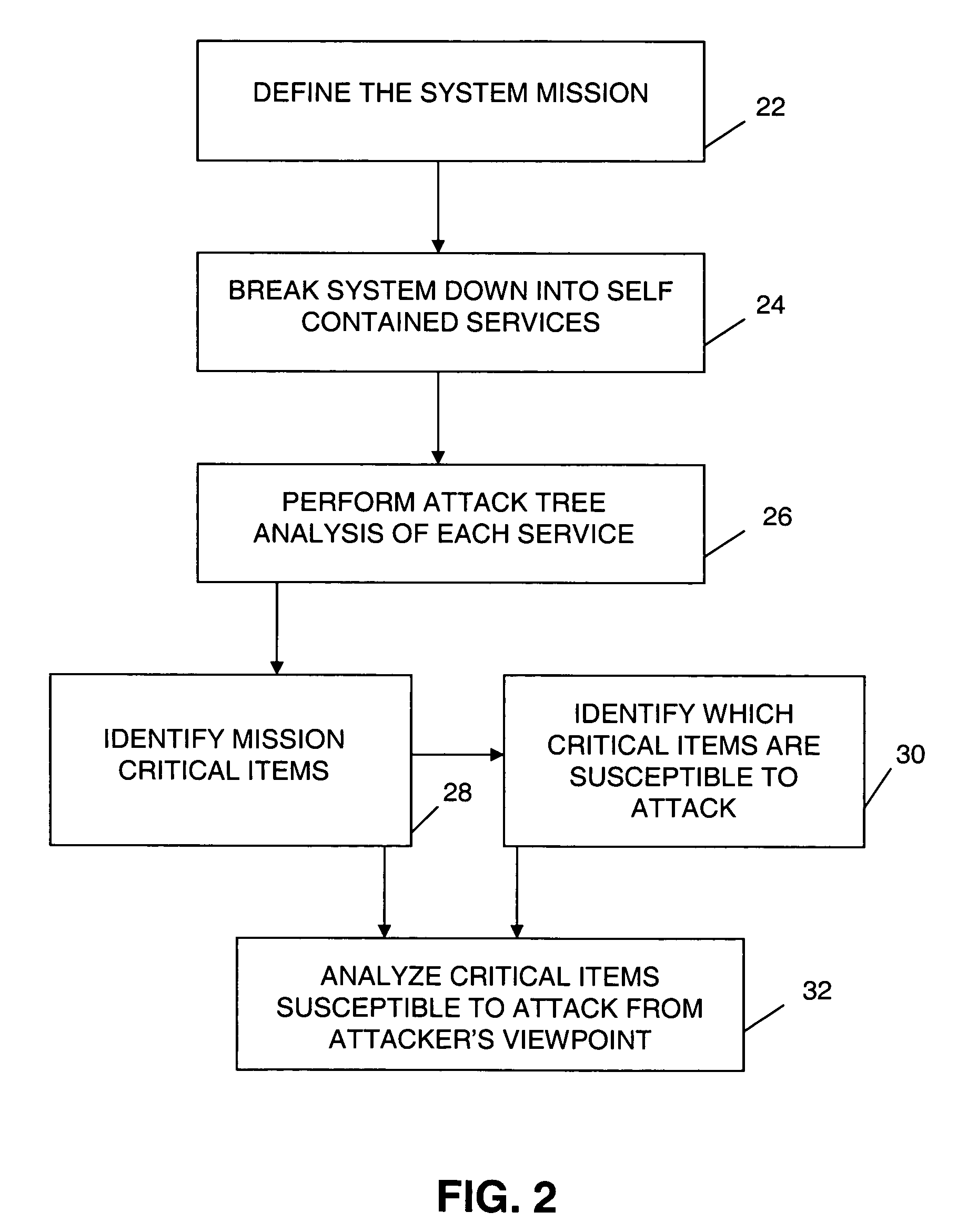
An exception handling system and method are provided for dynamically recovering from a workflow exception occurring in a mobile network communication system. The system has multiple workflows and at least one mission critical item. An attack tree modeling analyses is performed to identify the mission critical item. Another operation includes writing a plurality of forward recovery rules to protect the mission critical item using a transaction datalog fragment of transaction logic. The recovery rules are enabled through an engine in communication with the mobile network communication system. The multiple workflows are monitored for indication of a system attack on any one of the multiple workflows. A new workflow is automatically generated upon detection of the system attack. The exception handling system is overlayed on the mobile network.
Owner:THE BOEING CO
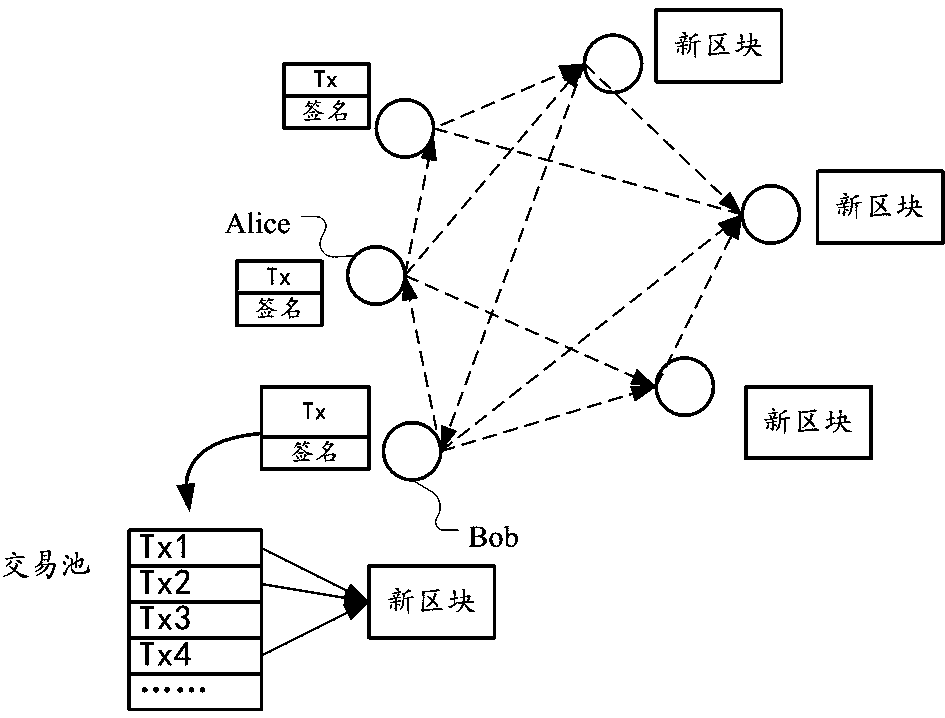
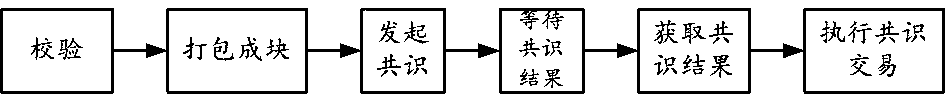
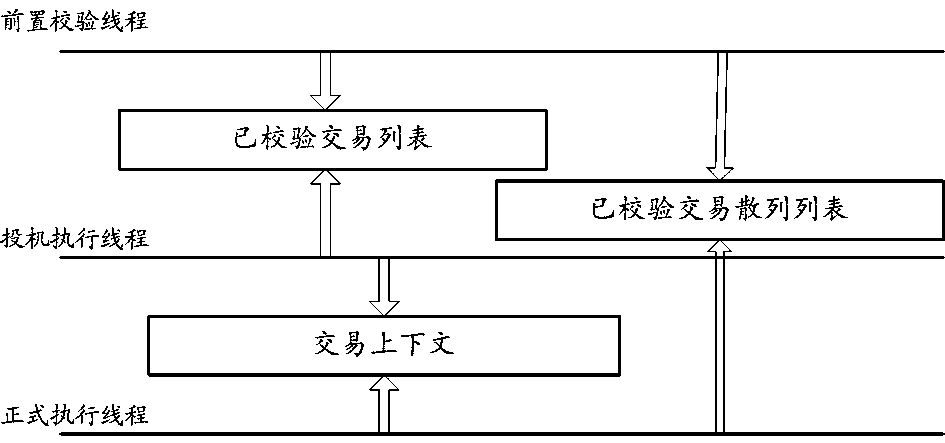
Method and device for executing transaction in block chain
ActiveCN111047449AImprove execution efficiencyReduce conflictFinanceUnauthorized memory use protectionProgramming languageSpeculative execution
The embodiment of the invention provides a method and a device for executing a transaction in a block chain. The method includes speculative execution before the transaction is consensus, and formal execution based on the consensus. The speculation execution process comprises the following steps: firstly, reading a locally recorded first transaction; executing transaction logic in the first transaction, and recording a variable operation request corresponding to an execution result in a memory; marking the transaction as a commissioned transaction. The formal execution process comprises the steps of obtaining a consensus and to-be-executed second transaction; judging whether the second transaction is a transaction executed by the speculation or not, and if so, obtaining a corresponding variable operation request which is not submitted yet; judging whether speculation execution of the second transaction conflicts with consensus-based transaction execution or not according to the variable operation request; and if no conflict exists, directly submitting the variable operation corresponding to the variable operation request. Therefore, the execution efficiency of the transaction is improved.
Owner:ALIPAY (HANGZHOU) INFORMATION TECH CO LTD
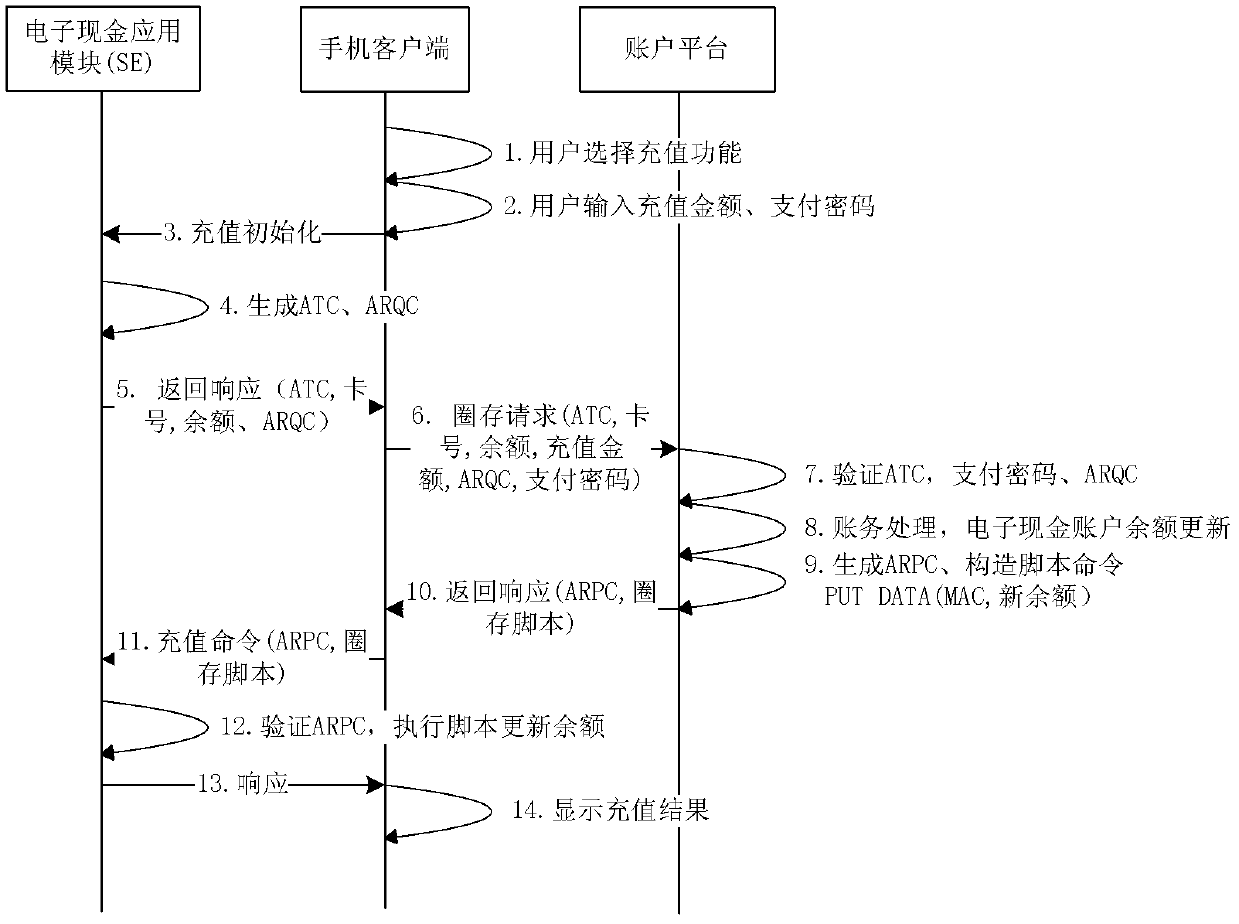
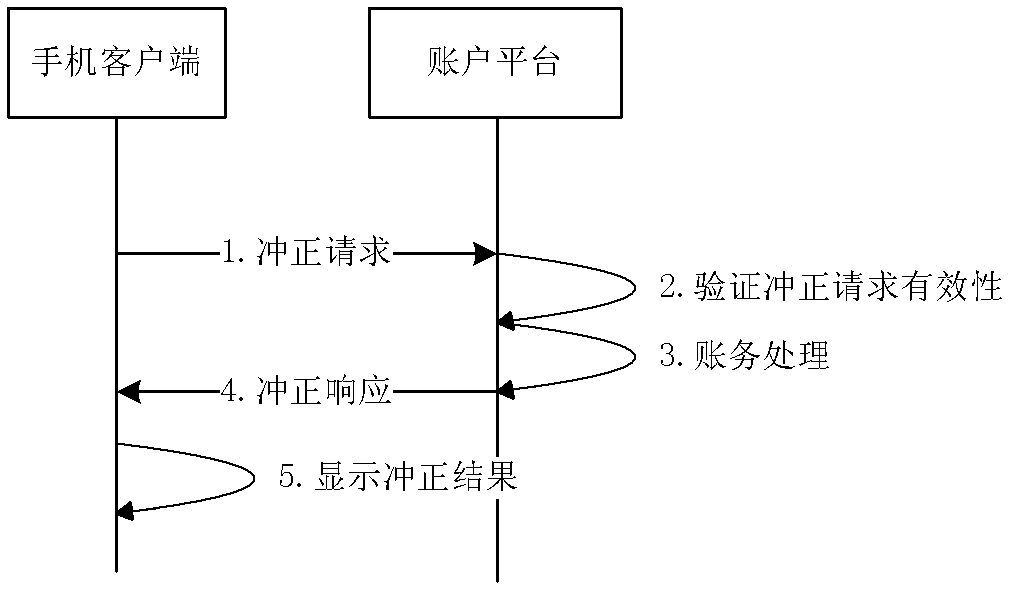
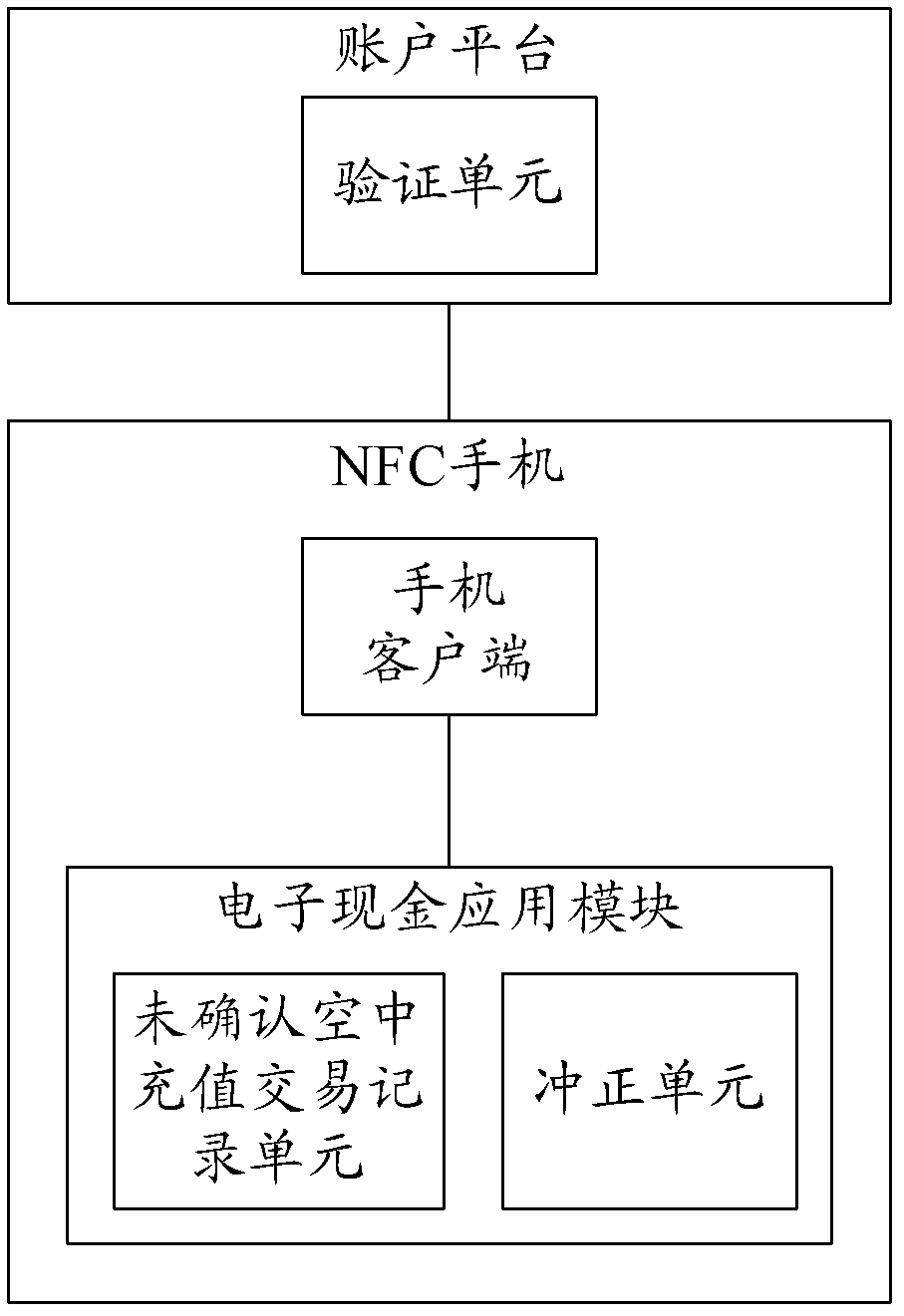
Over-the-air electronic cash loading method, system and device for NFC (near field communication) mobile phone
ActiveCN103310557AEnhanced interactionNo lossCash registersSubstation equipmentElectronic cashComputer terminal
The invention discloses an over-the-air electronic cash loading method, an over-the-air electronic cash loading system and an over-the-air electronic cash loading device for an NFC (near field communication) mobile phone. An unconfirmed over-the-air recharging transaction record is set, and is stored in a card, transaction logic is controlled through the card, interaction between a mobile phone client and the card is added in an over-the-air loading reversing flow, and over-the-air loading reversing logic is controlled mainly through the card. According to the technical scheme, the problems of over-the-air electronic cash loading on the NFC mobile phone and the problem of high tampering rate of over-the-air loading reversing transactions can be solved; and moreover, after an over-the-air loading reversing failure, the unconfirmed over-the-air recharging transaction record can also be read through the mobile phone client or a POS (point-of-sale) terminal, and the loading reversing transactions can be initiated to an account platform, so that the capital loss of a user is avoided.
Owner:CHINA MOBILE COMM GRP CO LTD
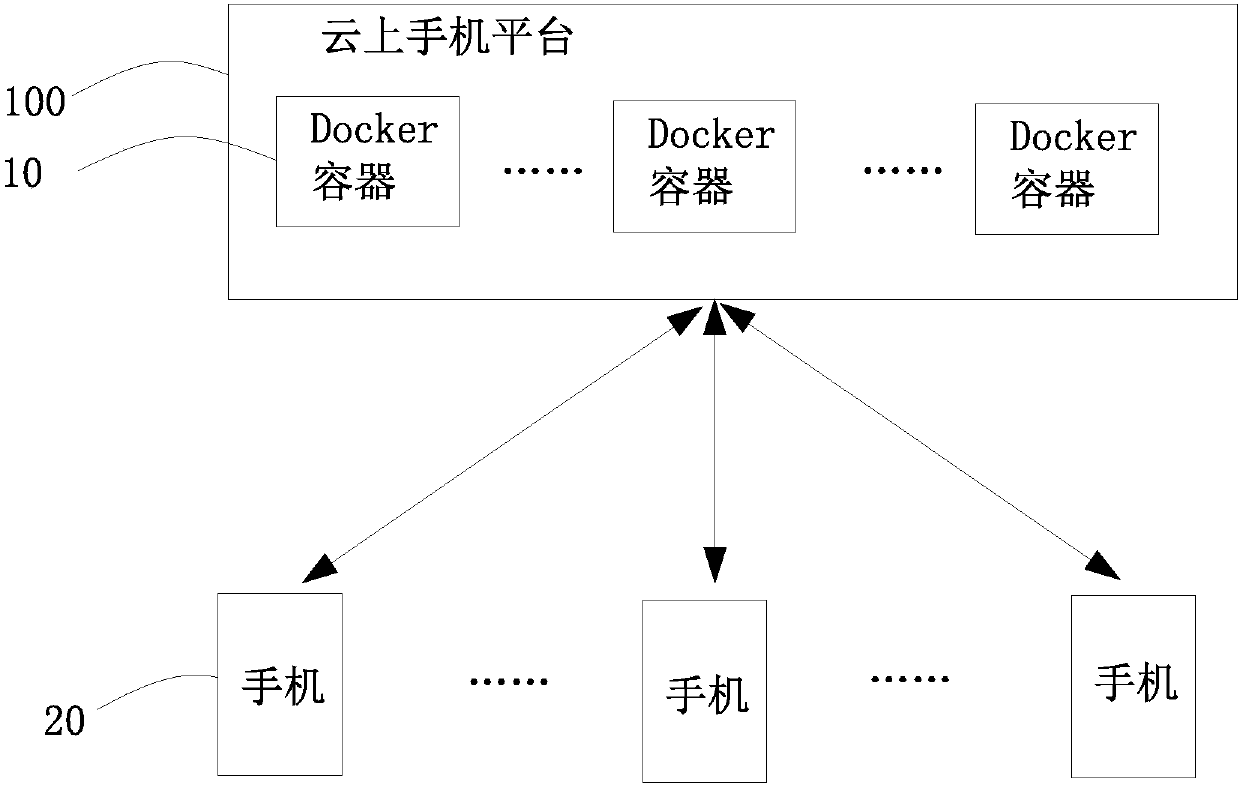
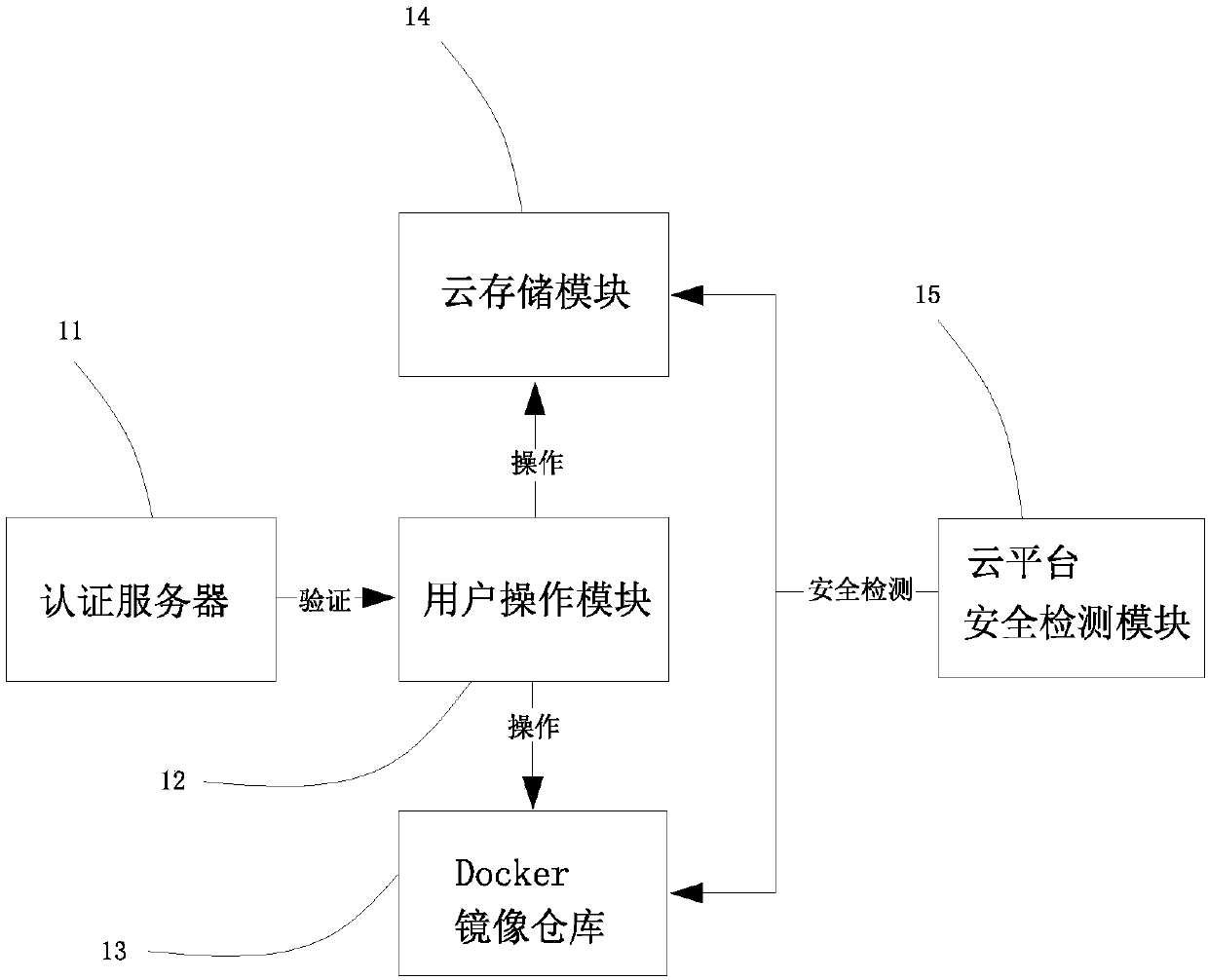
A cloud mobile phone system based on a Docker container
ActiveCN109922106AEasy to handleAvoid Privacy LeakageTransmissionRedundant hardware error correctionMirror imageMobile device
The invention relates to a cloud mobile phone system realized based on a Docker container. The system comprises a cloud mobile phone platform and a mobile phone, the cloud mobile phone platform is used for providing cloud service for the mobile phone, the cloud mobile phone platform comprises a plurality of Docker containers, each Docker container corresponds to a different mobile phone, or the plurality of Docker containers correspond to the same mobile phone. According to the invention, the mobile phone device and the transaction logic are separated through the Docker technology; A functionof switching a mobile phone system according to a use scene is provided for a user, the user can conveniently use a special system mirror image to process affairs, different business processing logicsare isolated, and privacy disclosure and inconvenience in use caused by the fact that various kinds of information are gathered to one system are prevented; Moreover, the mirror image used by the user can be stored in the cloud end, so that the user can download the mirror image from the cloud end to the mobile phone equipment for use at any time, and the user can process different transactions on a plurality of mobile phone equipment.
Owner:CHINA STANDARD SOFTWARE
Incentive compatibility listing power transaction system and transaction method
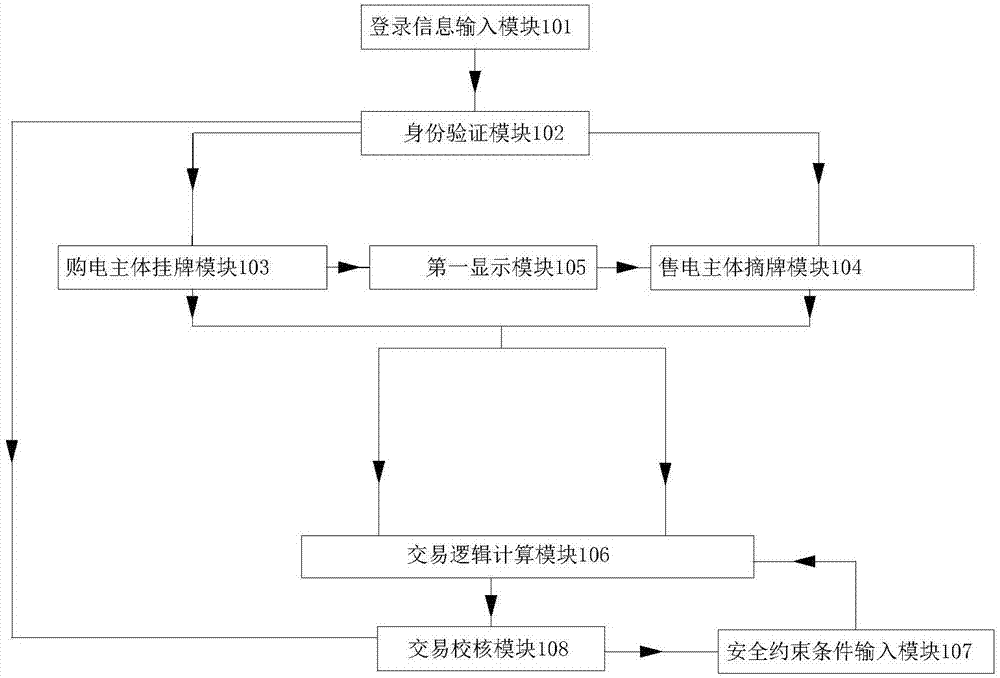
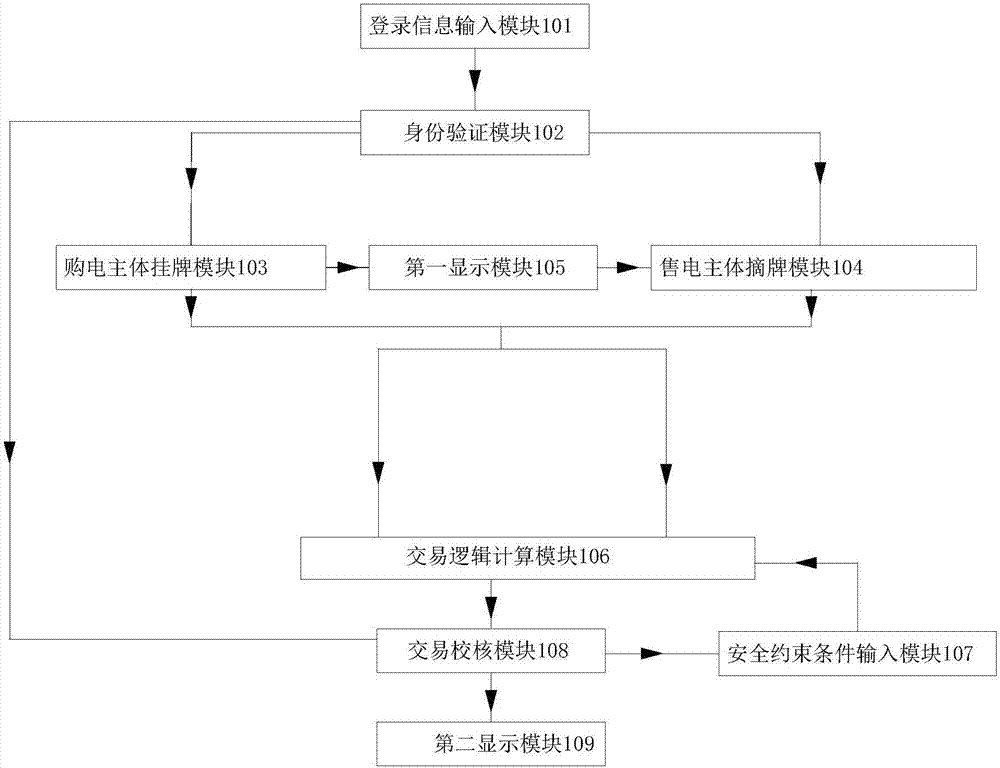
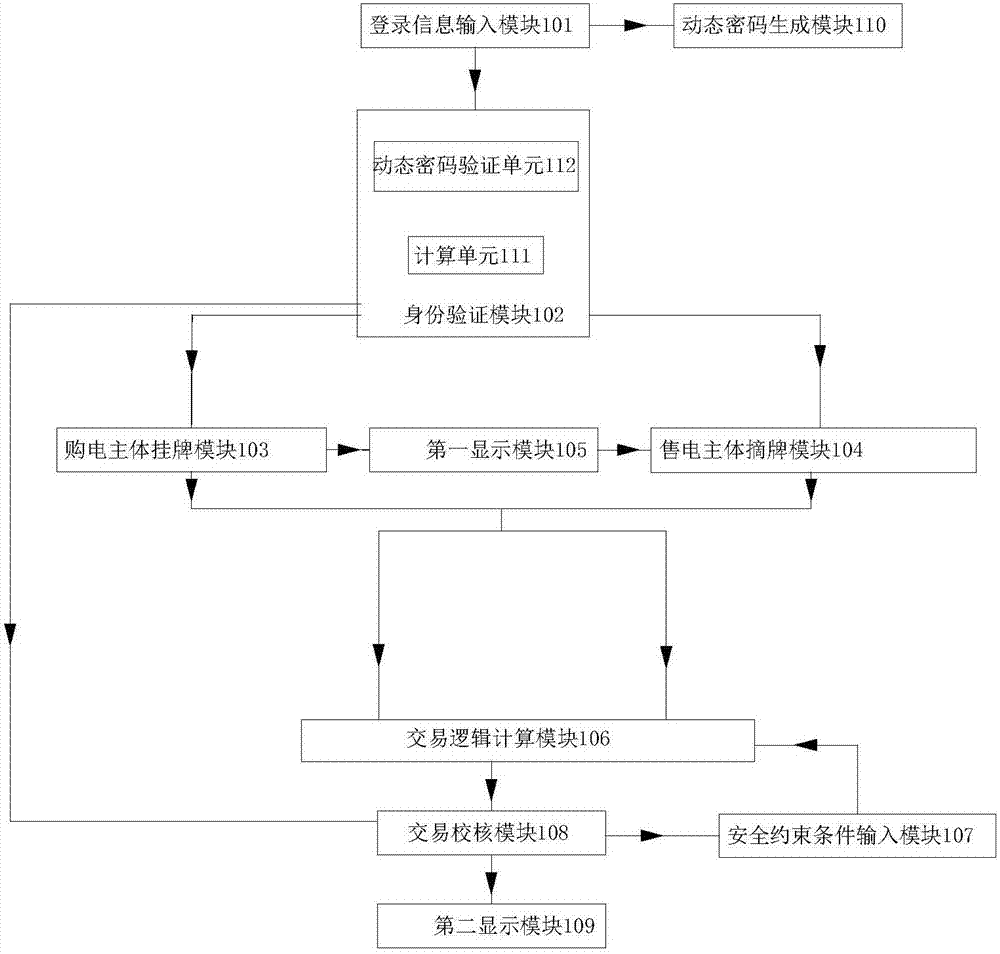
ActiveCN107507102AReduce electricity costsReduce wasted waterDiscounts/incentivesBuying/selling/leasing transactionsElectricity priceElectricity market
The invention relates to an incentive compatibility listing power transaction system and a transaction method, and belongs to the power market transaction system technical field; the system comprises a registration information input module, an ID verification module, a power purchasing body listing module, a power selling body delisting module, a first display module, a transaction logic calculating module, a safety constrained condition input module and a transaction checking module; the system uses an incentive compatibility principle to mainly excite the market body in three aspects: actively participating the market, truly reporting demands and prices, and standardizing transaction behaviors; in delisting transaction, in order to invoke bidder bidding enthusiasm, the excitation method based on price difference return is employed, so the price difference volume of trade between listing power price and delisting power price can be compensated to the power selling body according to certain returning coefficient, thus encouraging the power selling body to offer a lower price, actively promoting delisting transaction valid deals, and forming a multi-party win-win mechanism.
Owner:昆明电力交易中心有限责任公司
Energy Internet transaction account book management method and system based on blockchain
InactiveCN108830711ATo achieve the effect of optimal configurationReduce processing costsFinancePayment protocolsThird partyByzantine fault tolerance
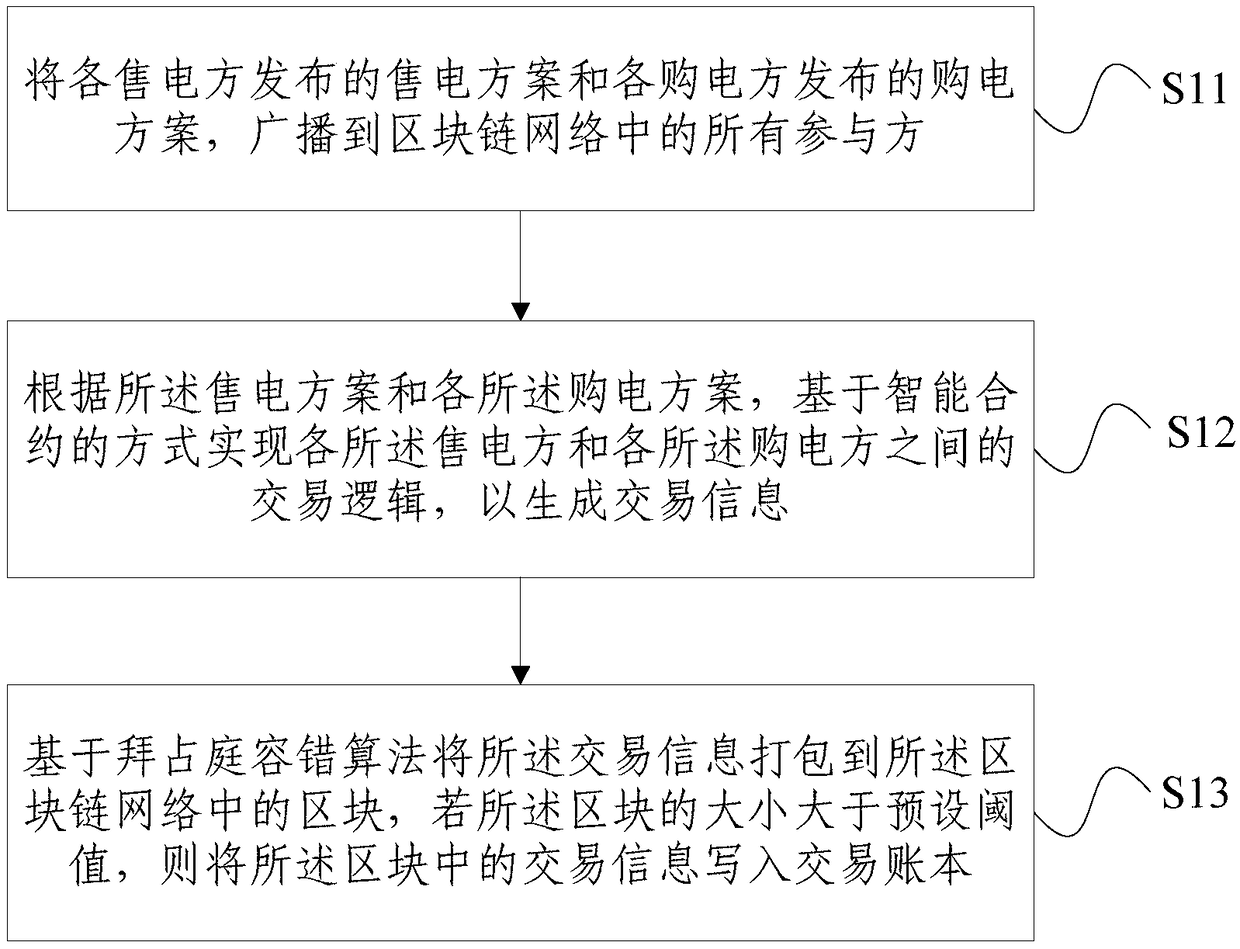
The invention provides an energy Internet transaction account book management method and system based on a blockchain. The method comprises the following steps of S11, broadcasting the electricity sell plan issued by each electricity seller and the electricity purchase plan issued by each electricity purchaser to all participants in a blockchain network; S12, according to the electricity sell planand the electricity purchase plan, realizing transaction logic between each electricity seller and each electricity purchaser based on an intelligent contract mode to generate transaction information; and S13, packaging the transaction information into blocks in the blockchain network based on a Byzantine fault tolerance algorithm. In the invention, based on the energy transaction of the blockchain network, because of the characteristic of the blockchain, decentralized transaction is realized, third party participation is not needed, manpower cost is saved, the transaction information is written into the transaction account book, and the transaction information is transparent and can not be tampered.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER CO LTD JIAXING POWER SUPPLY CO +2
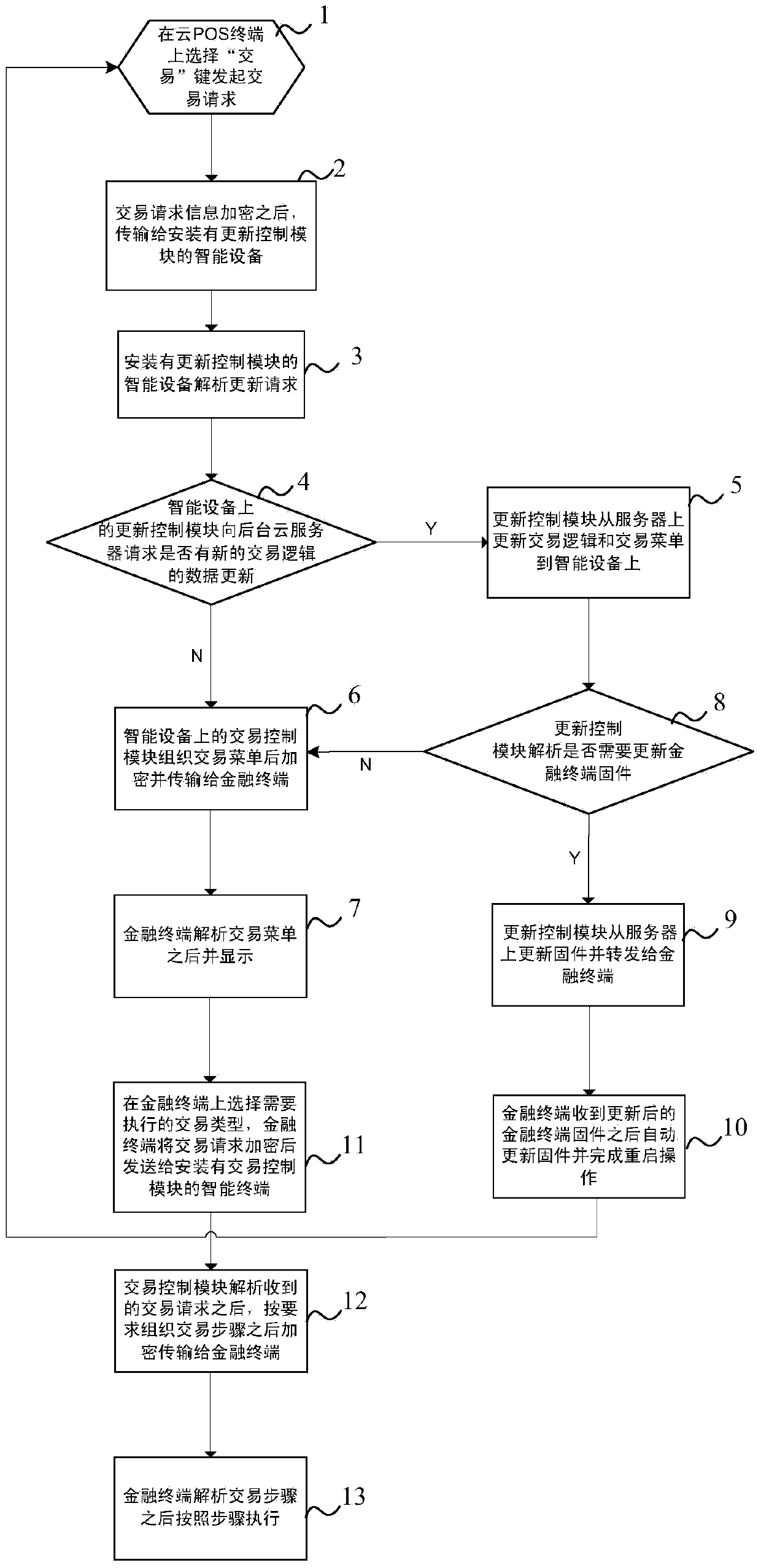
Cloud POS (Point Of Sale) terminal based on intelligent device and application, and implementation method thereof
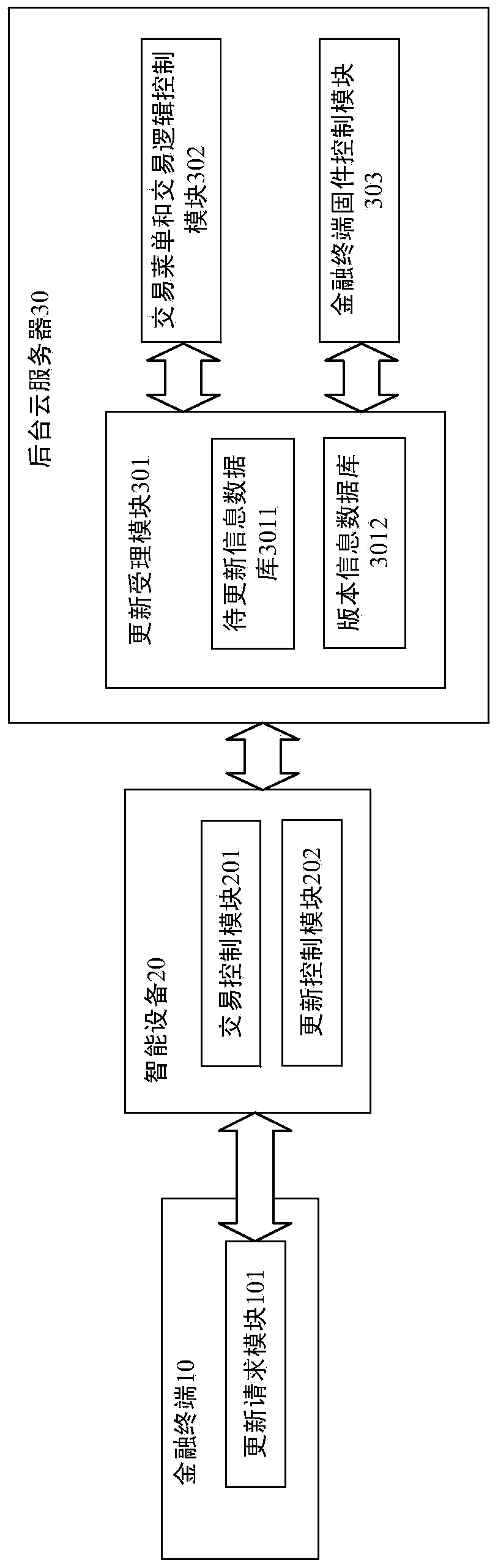
The invention discloses a cloud POS (Point Of Sale) terminal based on intelligent device and application, and an implementation method thereof. The cloud POS terminal comprises an updating request module for initiating an updating request, a transaction control module and an updating control module, wherein the updating request module is in communication connection with the updating control module, the updating control module encrypts the updating request and further transmits the updating request to a background cloud server; the background cloud server comprises an updating acceptation module with a to-be-updated information database and a version information database, a transaction menu and transaction logic control module and a finance terminal firmware control module, wherein the transaction menu and transaction logic control module extracts transaction menu and transaction logic, which need to be updated, from the to-be-updated information database, and transmits the extracted information to the updating request module; the finance terminal firmware control module extracts finance terminal firmware, which needs to be updated, from the to-be-updated information database, and further transmits the extracted finance terminal firmware to the updating request module. By such architecture and mode, users are helped to build a set of powerful, safe, reliable and low-cost cloud POS terminal system.
Owner:SHANGHAI FUIOU PAYMENT SERVICE
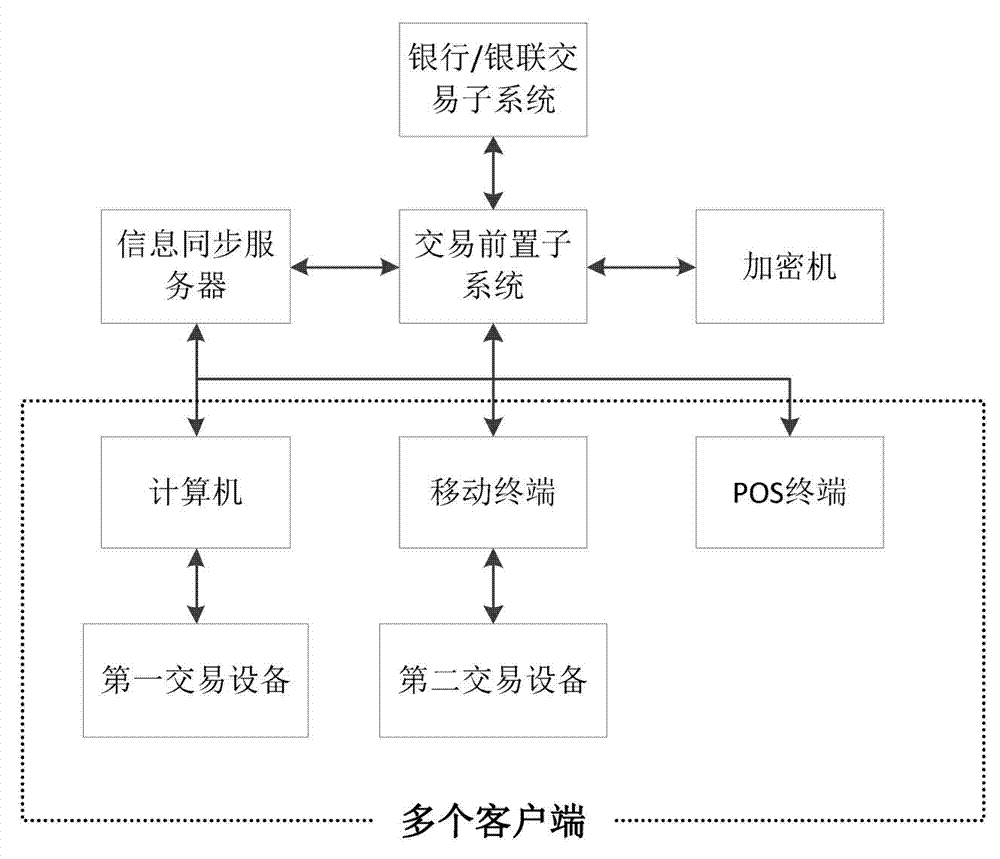
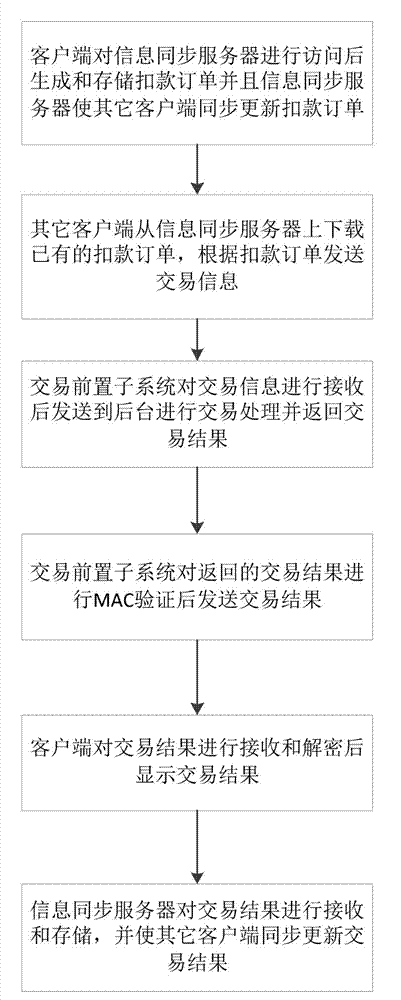
Asynchronous terminal delivery transaction payment system and method
InactiveCN102855559AImprove cohesionImprove smooth performancePayment architecturePayment transactionPayment order
The invention discloses an asynchronous terminal delivery transaction payment system and method. The system comprises a plurality of clients, an information synchronization server and a transaction front-end subsystem. The method comprises the following steps that: the clients generate cut payment orders and other clients synchronize the cut payment orders through the information synchronization server; the other clients download the cut payment orders for performing transaction payment from the information synchronization server; the transaction front-end subsystem transmits the transaction information to a background for transaction processing; the transaction front-end subsystem performs transaction logic processing on the returned transaction results; the clients decrypt and display the transaction results; and the other clients synchronize the transaction results through the information synchronization server. According to the system and the method, convenience can be brought to the clients, and the connection between the links in payment transaction is improved. The asynchronous terminal delivery transaction payment system and method are widely applied to the financial industry.
Owner:GUANGDONG JUNXIANG BUSINESS SERVICE
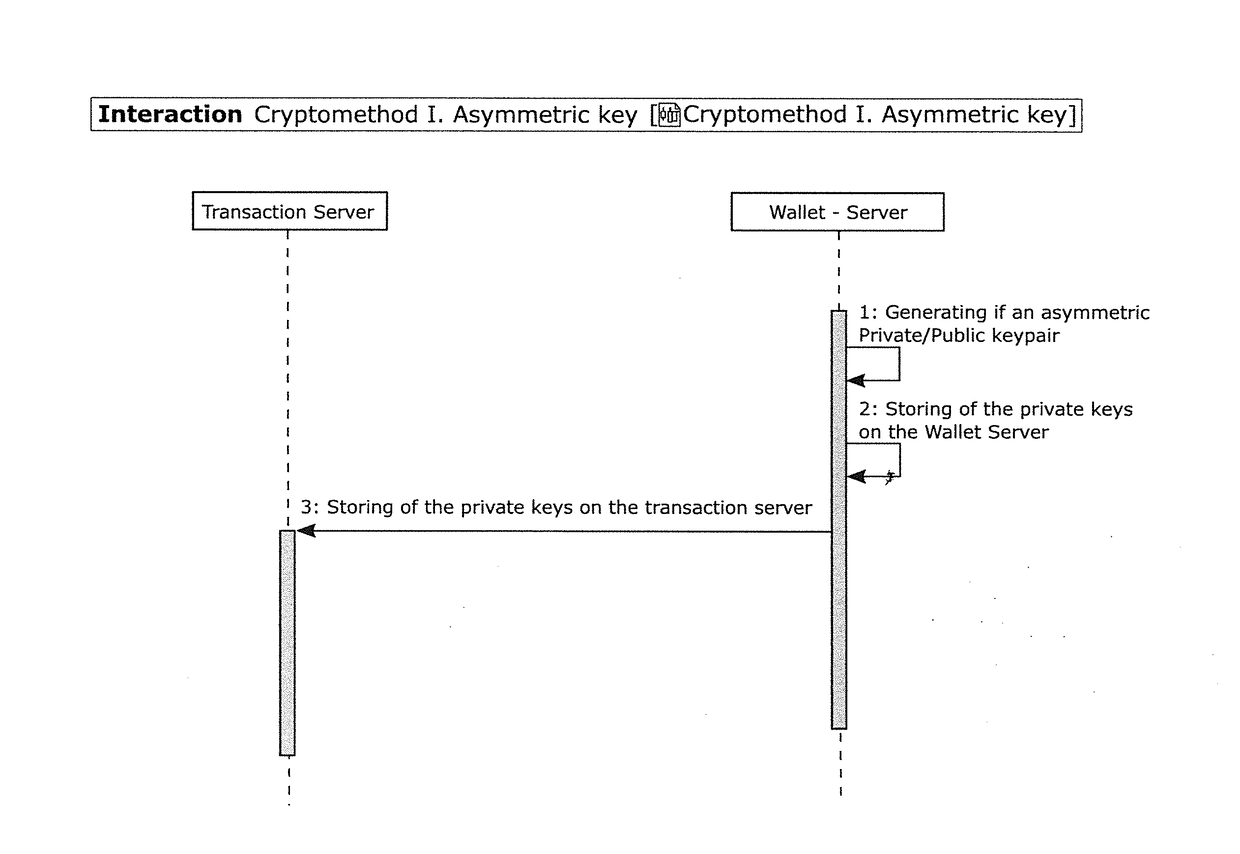
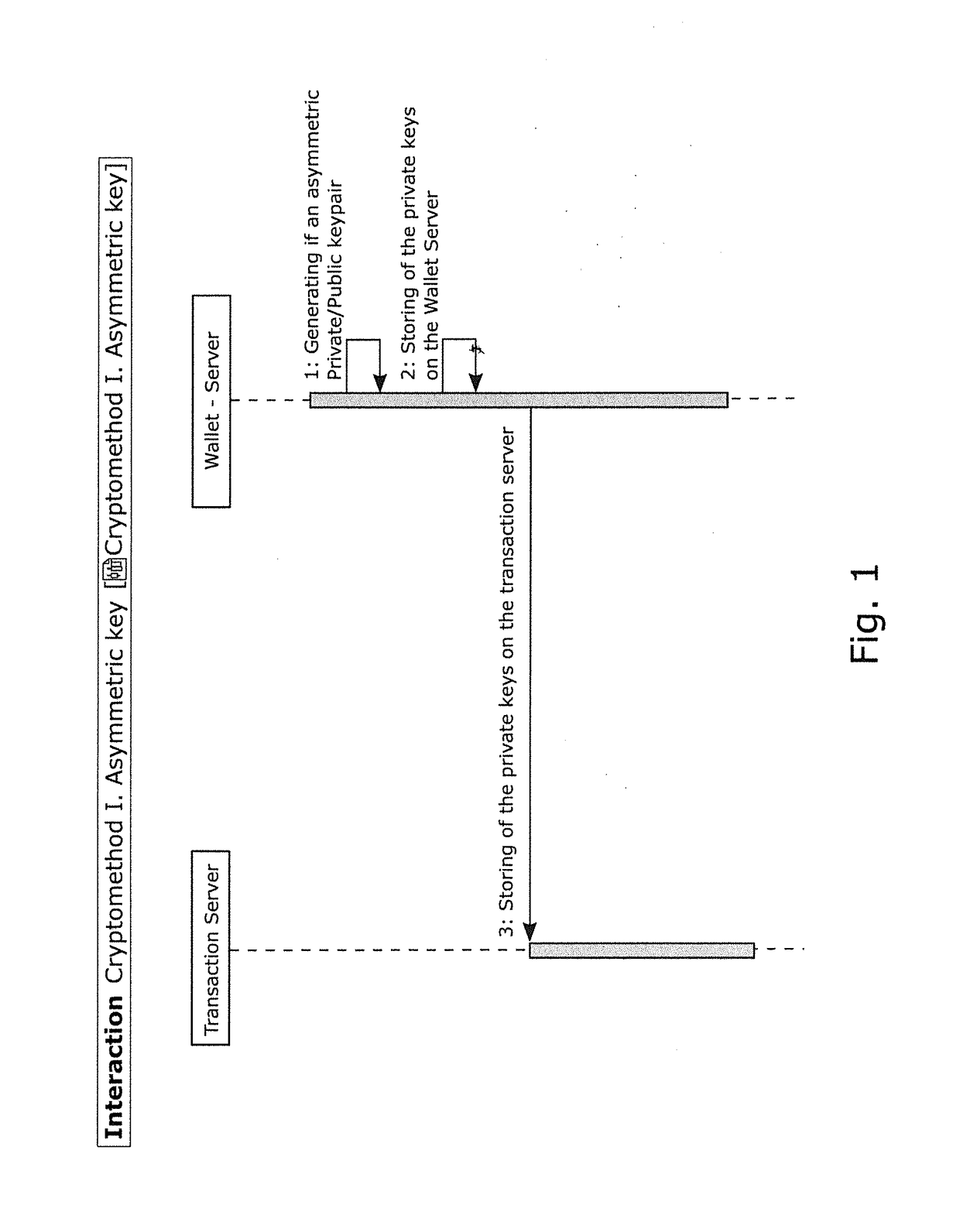
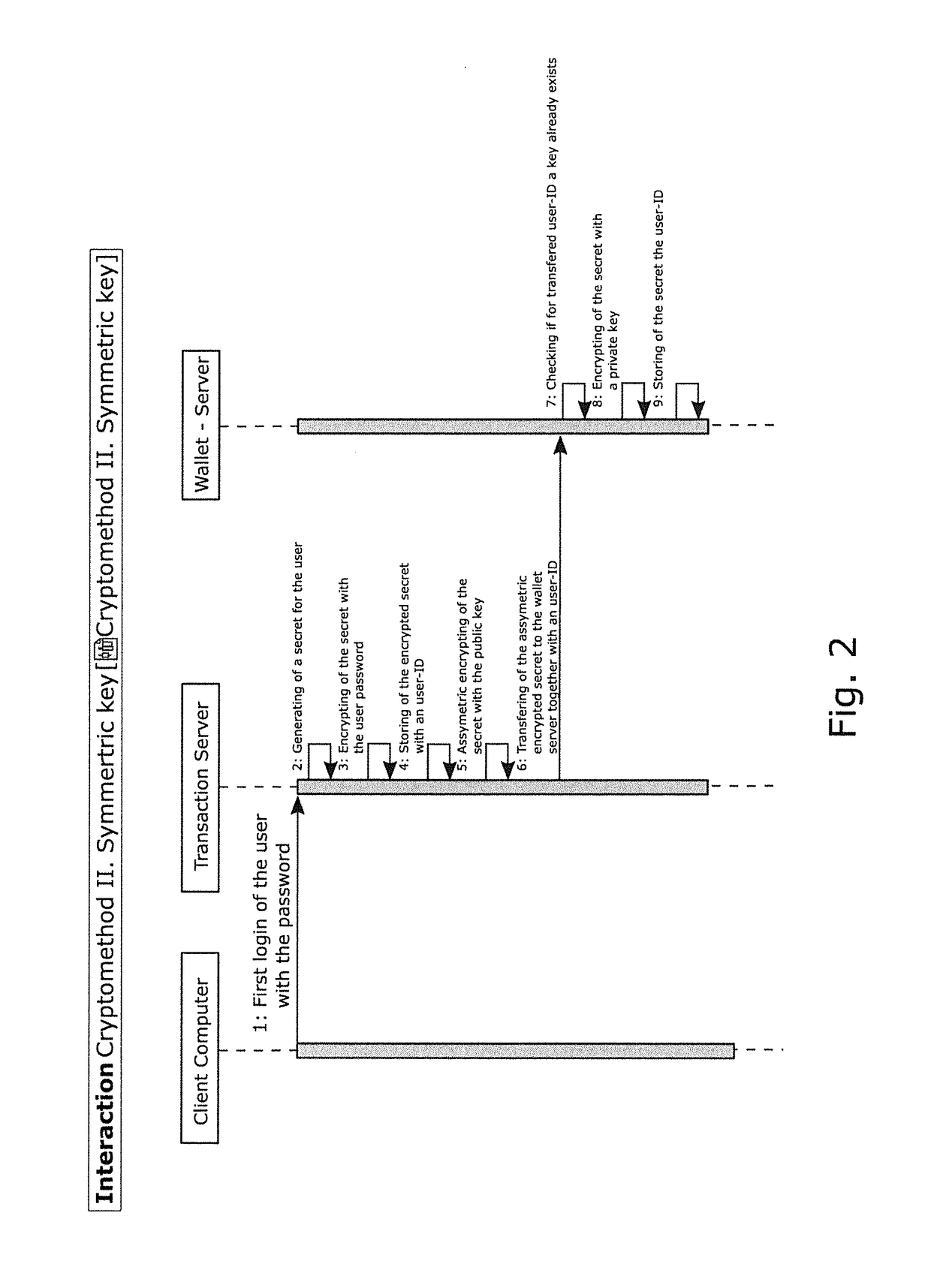
Method and device for protecting access to wallets in which crypto currencies are stored
A method is provided for securing access to wallets in which crypto currencies and / or their secrets are stored. The method uses a transaction server on which transaction logic runs to perform a transaction with a client device controlled by a user. A user password and a unique ID are assigned to each user with a wallet server on which the wallets are managed, For the termination of a transaction, the access from the transaction server to the wallet server is based on the user password, an asymmetric server key pair, and a symmetric user key per user.
Owner:DRAGLET
Payment mode selection method and mobile terminal
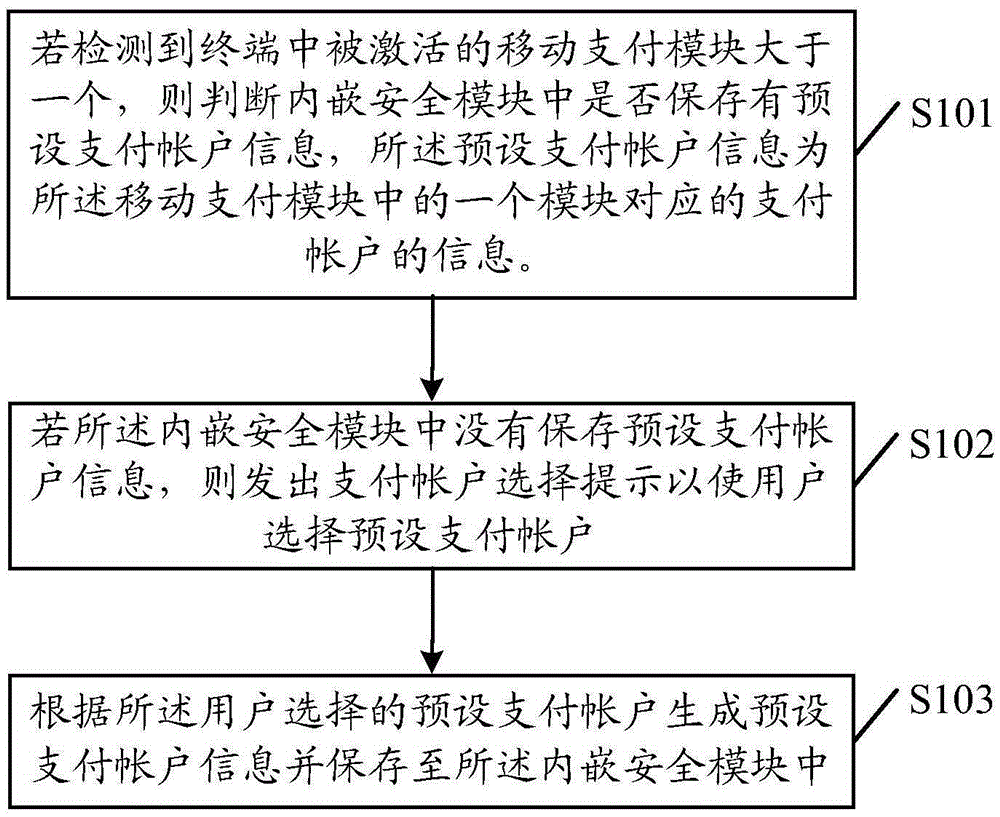
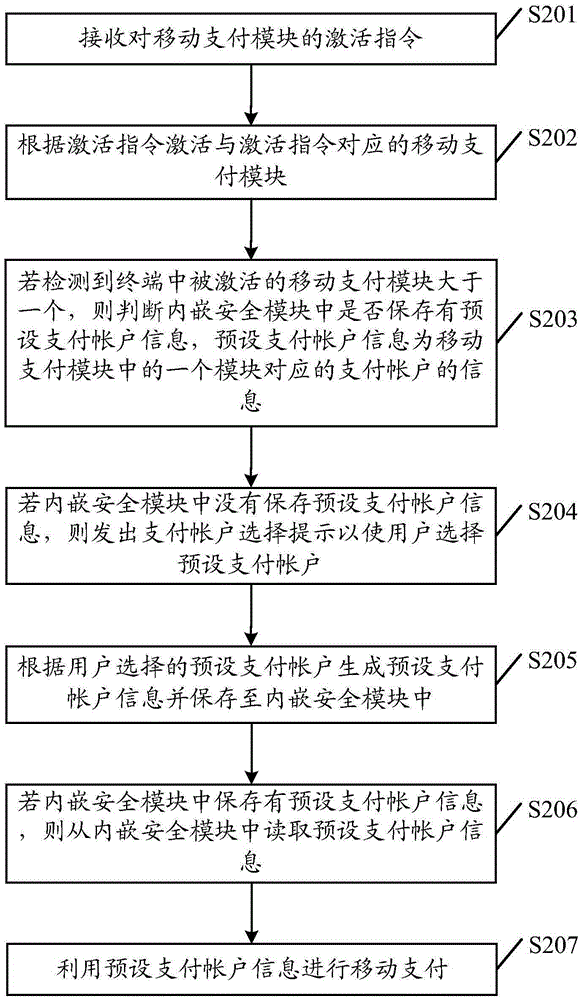
InactiveCN105405009AActive and selectiveCorrect trading logicPayment schemes/modelsFinancial transactionPayment order
The embodiment of the invention discloses a payment mode selection method and a mobile terminal. The payment mode selection method comprises steps: if the number of activated mobile payment models in a terminal is detected to be more than one, whether default payment account information is stored in an embedded safety module is judged, wherein the default payment account information is the information of a payment account corresponding to one module in the mobile payment models; if the default payment account information is not stored in the embedded safety module, a payment mode selection prompt is given to enable the user to select a default payment account; and according to the default payment account selected by the user, default payment account information is generated and stored in the embedded safety module. Thus, when the number of the activated payment models is more than one, the user actively selects one payment module for payment, correct transaction logic can be ensured, smooth transaction can be carried out, and active selectivity on the payment accounts by the user during the transaction process is stronger.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
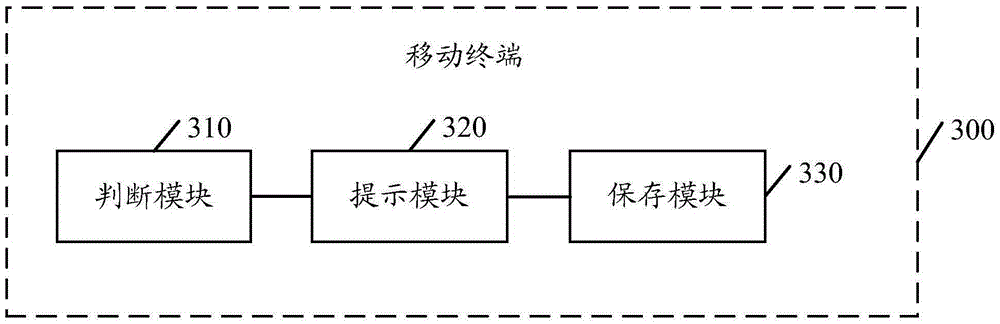
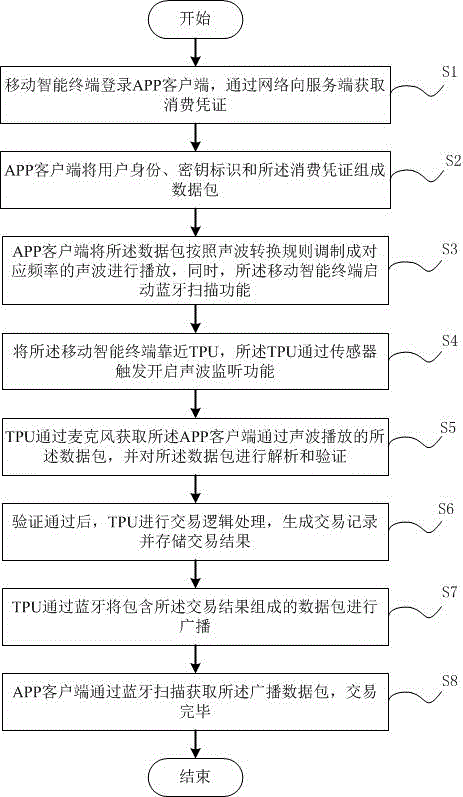
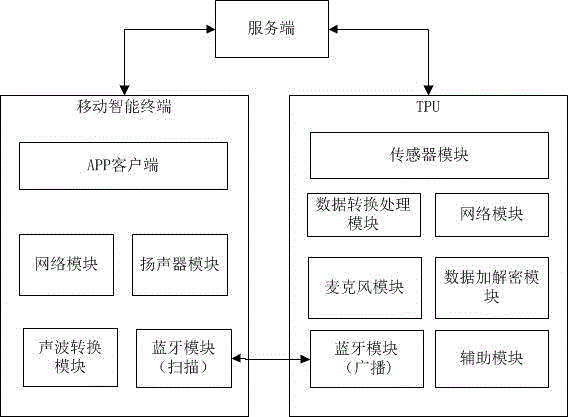
Mobile payment method and system based on the combination of sound wave and Bluetooth
InactiveCN105913249AImprove experienceImprove transaction securityPayment architectureBroadcast packetData information
The present invention provides a mobile payment method and system based on the combination of sound wave and Bluetooth, belonging to the field of the mobile payment. The method comprises: an APP client plays a data package through a mobile intelligent terminal sound wave; a TPU monitors the sound wave and obtains the data package played by the sound wave through a microphone, the data package is analyzed and verified; the transaction logic processing is performed after the verification passes; the TPU broadcasts the data package including the transaction processing result through the Bluetooth, the APP client scans the obtained broadcast data package through the Bluetooth, and the transaction is completed. The mobile payment method and system based on the combination of sound wave and Bluetooth employ the combination of the sound wave and the Bluetooth to complete a closed complete communication mechanism so as to further improve the accuracy and the payment speed of the mobile payment data information transmission based on the combination of the sound wave and the Bluetooth and lift the user experience.
Owner:咪付(广西)网络技术有限公司
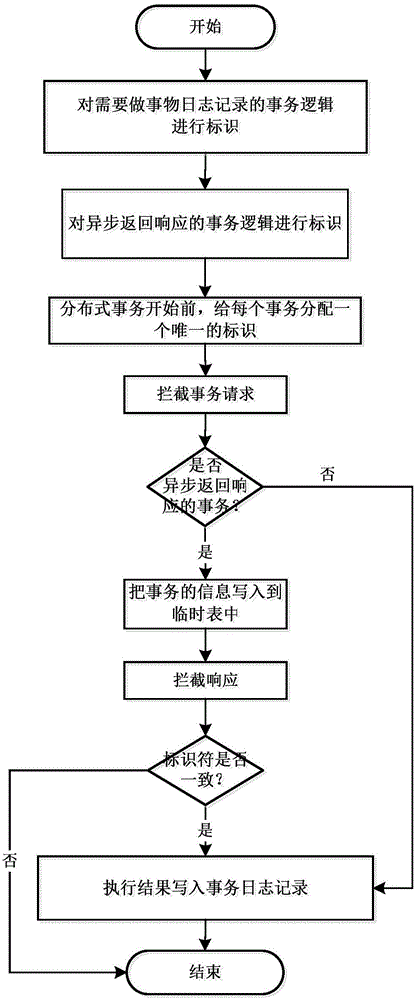
Event log recording method applicable to distributed system
ActiveCN104572415AReduce workloadEasy to manageHardware monitoringMultiprogramming arrangementsUnique identifierTransaction log
The invention relates to the technical field of distributed calculation, in particular to an event log recording method applicable to a distributed system. The event log recording method comprises the following steps of indentifying event logics needing event log recording and event logics needing asynchronous return response in all event logics in the distributed system first; before an event begins, distributing a unique identifier to the event; when the event begins, judging whether the event is an event needing asynchronous return response, and if not, directly executing the event logic and writing the event log into an event log record according to the result; if so, writing the event formation into a temporary table as one record, and then continuously executing the event; finally, intercepting all the received responses, taking the corresponding record out in the temporary table if an identifier in the response is consistent with the identifier of certain record in the temporary table, upgrading an event execution result in the response to the record, and then writing into the event log record. According to the event log recording method disclosed by the invention, the problems of dispersed logs, nonuniform formats and difficulty in management when a traditional distributed system executes events are solved; the event log recording method disclosed by the invention can be used for event log recording of the distributed system.
Owner:G CLOUD TECH
Mobile network dynamic workflow exception handling system
An exception handling system and method are provided for dynamically recovering from a workflow exception occurring in a mobile network communication system. The system has multiple workflows and at least one mission critical item. An attack tree modeling analyses is performed to identify the mission critical item. Another operation includes writing a plurality of forward recovery rules to protect the mission critical item using a transaction datalog fragment of transaction logic. The recovery rules are enabled through an engine in communication with the mobile network communication system. The multiple workflows are monitored for indication of a system attack on any one of the multiple workflows. A new workflow is automatically generated upon detection of the system attack. The exception handling system is overlayed on the mobile network.
Owner:THE BOEING CO
Performing direct cache access transactions based on a memory access data structure
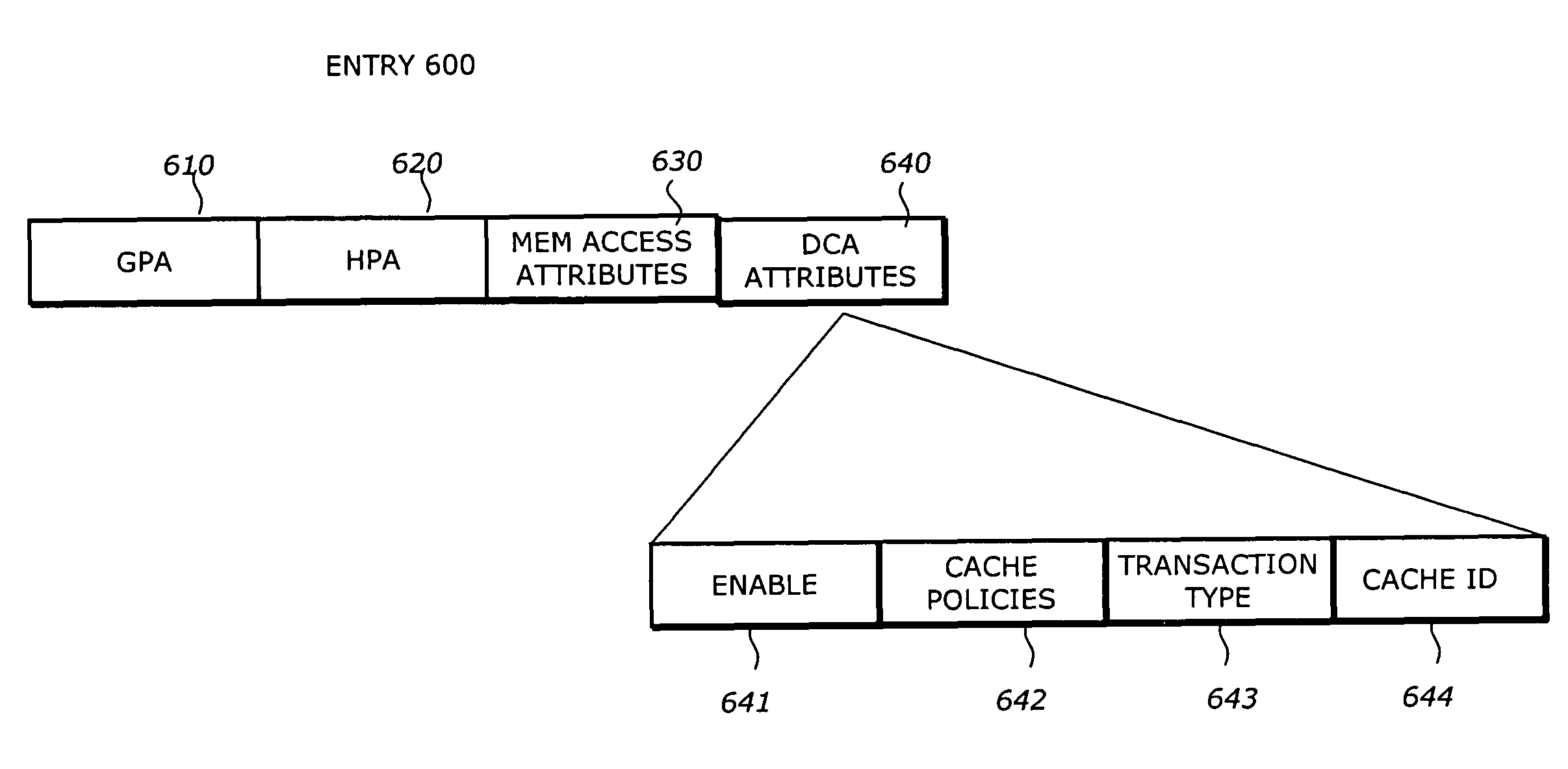
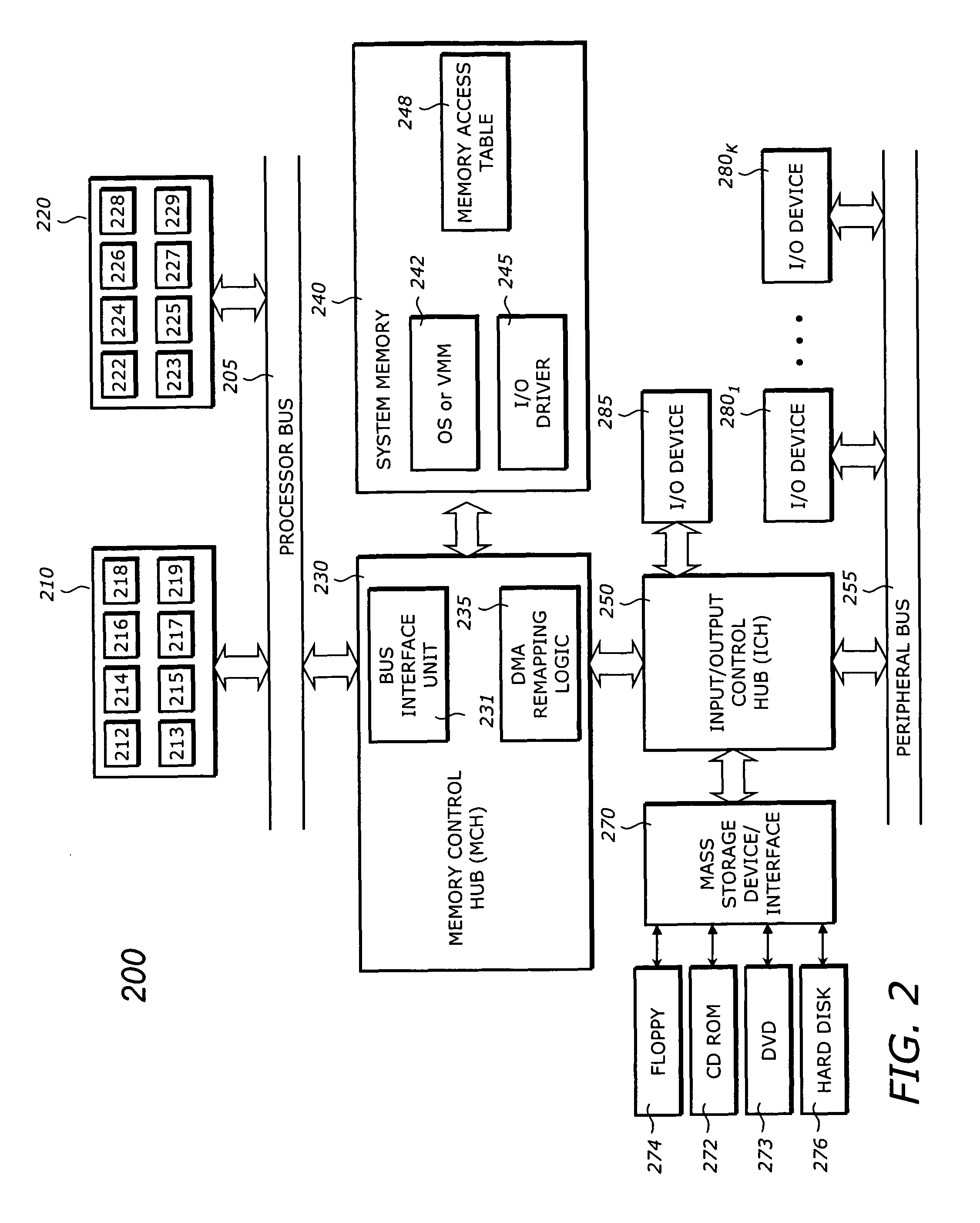
InactiveUS7937534B2Memory adressing/allocation/relocationUnauthorized memory use protectionCache accessParallel computing
Owner:INTEL CORP
Self-contained business transaction capsules
InactiveUS20070005456A1Acutation objectsBuying/selling/leasing transactionsBroadcastingComputer science
A self-contained business transaction capsule to conduct a wireless transaction includes data regarding the wireless transaction. Transaction logic is provided to complete the wireless transaction. The self-contained business transaction capsule is adapted to be broadcasted to and stored on a portable electronic device.
Owner:WARP 9
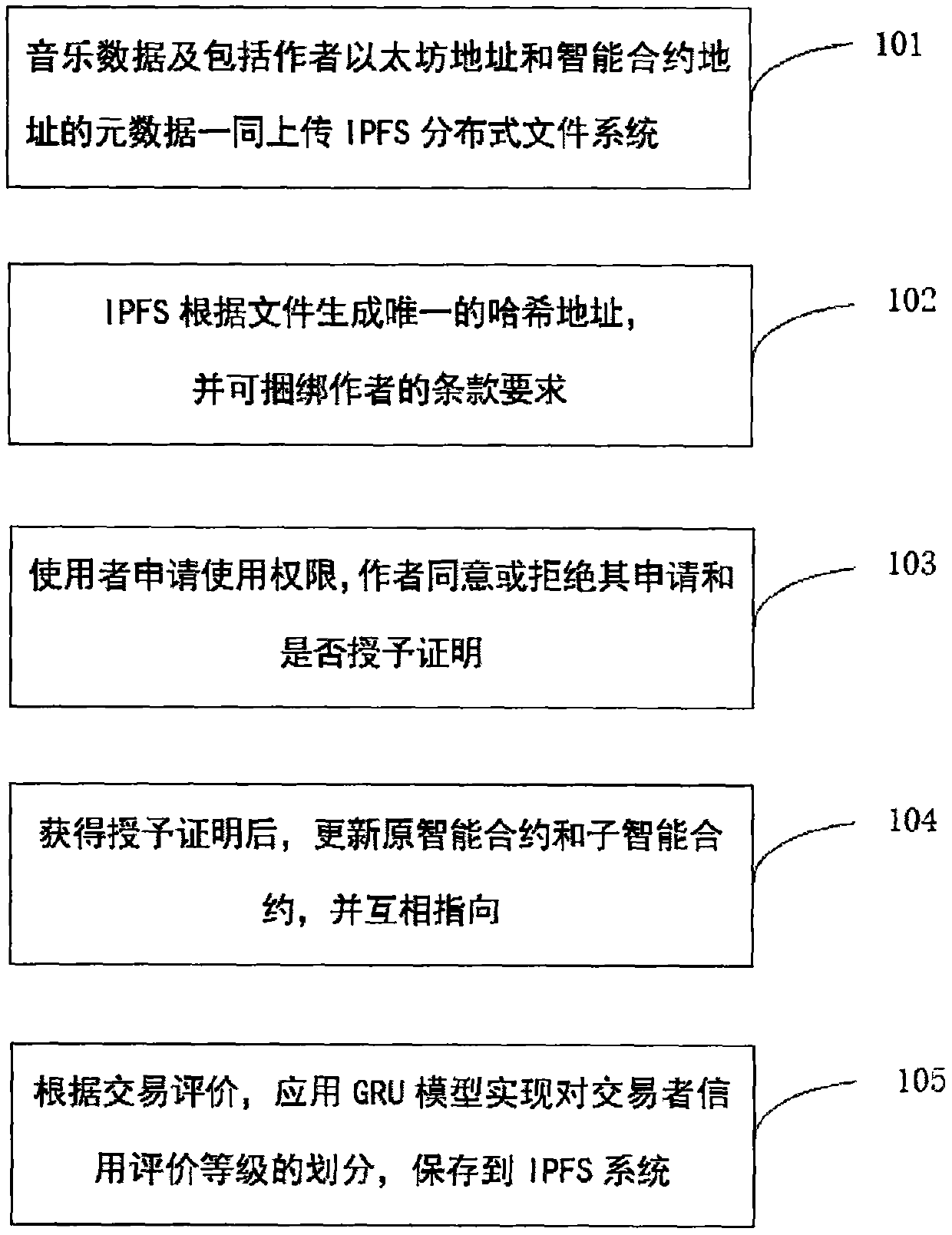
Music copyright protection system based on blockchain smart contract
ActiveCN110851796AMaintain integrityTrusted and secure traceabilityPayment protocolsProgram/content distribution protectionNerve networkDigital content
The invention discloses a music copyright protection system based on a blockchain smart contract, so as to track the original source and use information of music content. The method is implemented bythe following steps: storing music on an IPFS (The InterPlanetary File System) distributed server, and storing a hash value in an intelligent contract, so that safe and reliable storage of data is realized; completing transaction logic through an intelligent contract, so that data transaction activities are orderly carried out on the distributed blockchain network; establishing a reputation scoreby using a GRU (Gated Recurrent Unit) neural network; storing digital content and transaction comment information by utilizing an IPFS distributed system, so that a credit evaluation system of a userand a data sharing platform based on a blockchain + IPFS are established, and credible and safe traceability and transparency of authorization and sharing of secondary use of music are provided.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
Intelligent authentication
InactiveUS20160098710A1Efficiently employedImprove securityFinanceProtocol authorisationInternet privacyAuthentication system
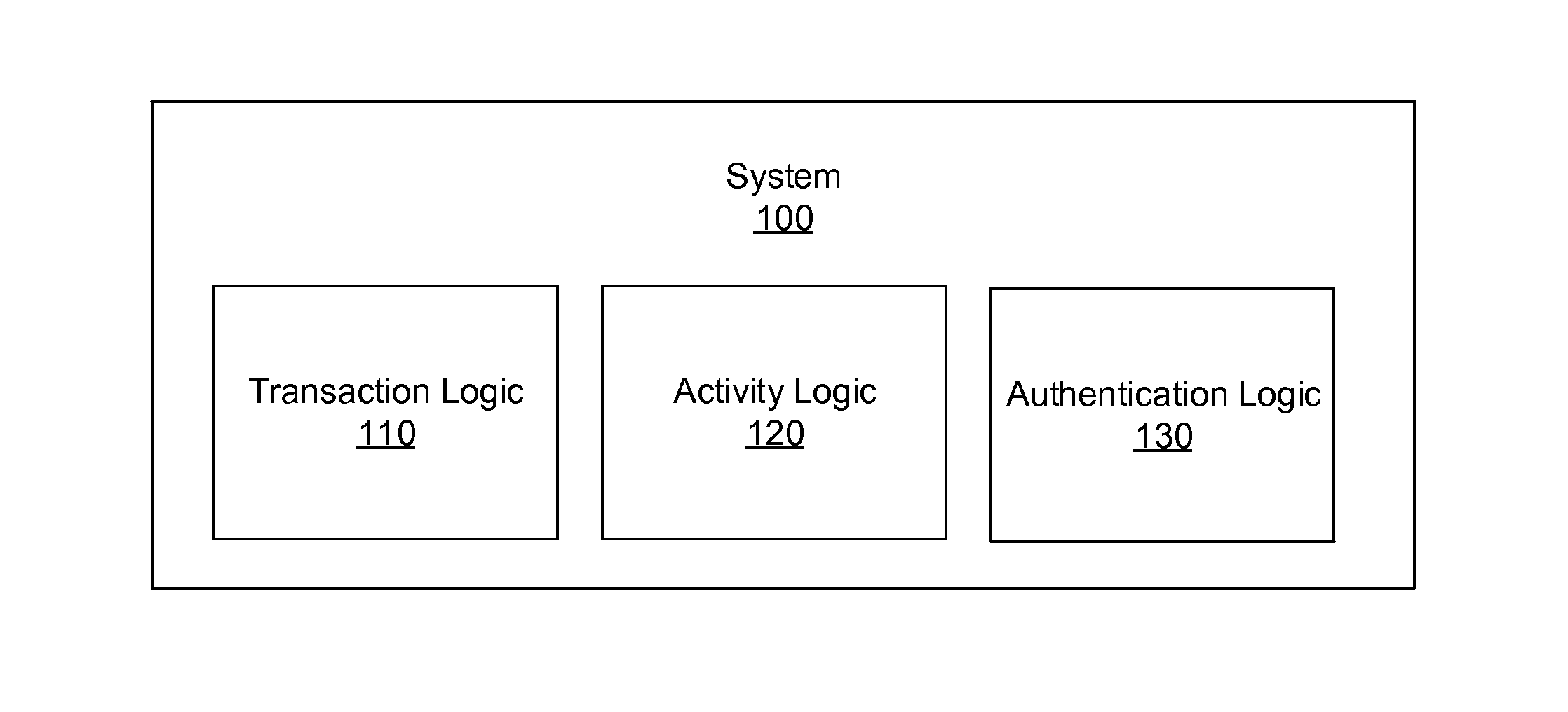
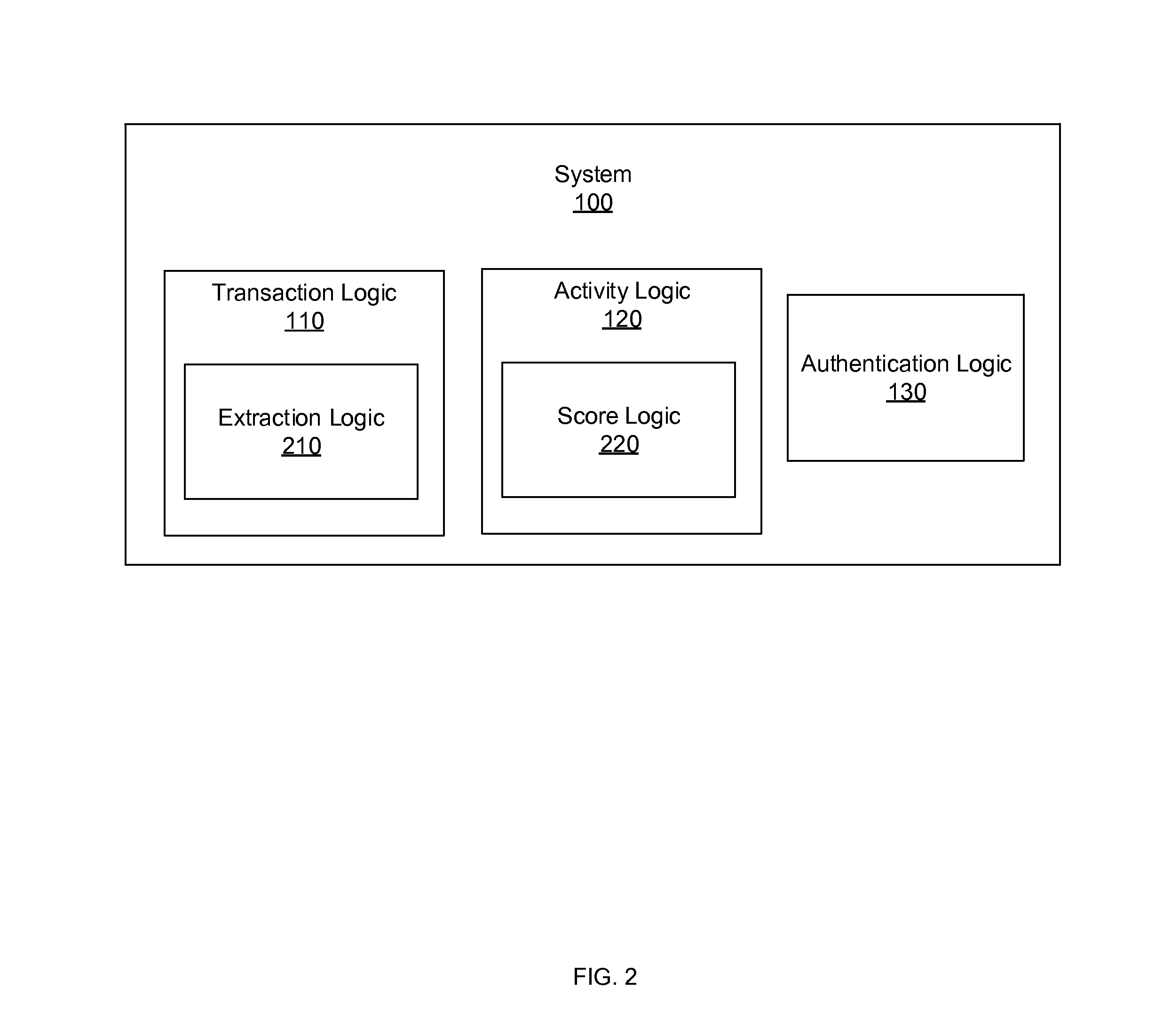
Systems, methods, and other embodiments associated with intelligent authentication. According to one embodiment, a system includes a transaction logic configured to receive transaction metadata associated with an attempted transaction. The transaction logic is also configured to identify a user attempting the attempted transaction. The system further includes an activity logic configured to access an activity log associated with the user. The activity log includes values corresponding to previous transactions made by the user and any additional information provided by 3rd party feeds. The activity logic is also configured to compare transaction metadata to the values. The system also includes an authentication logic configured to select an authentication level for the transaction based, at least in part, on the comparison.
Owner:WELLS FARGO BANK NA
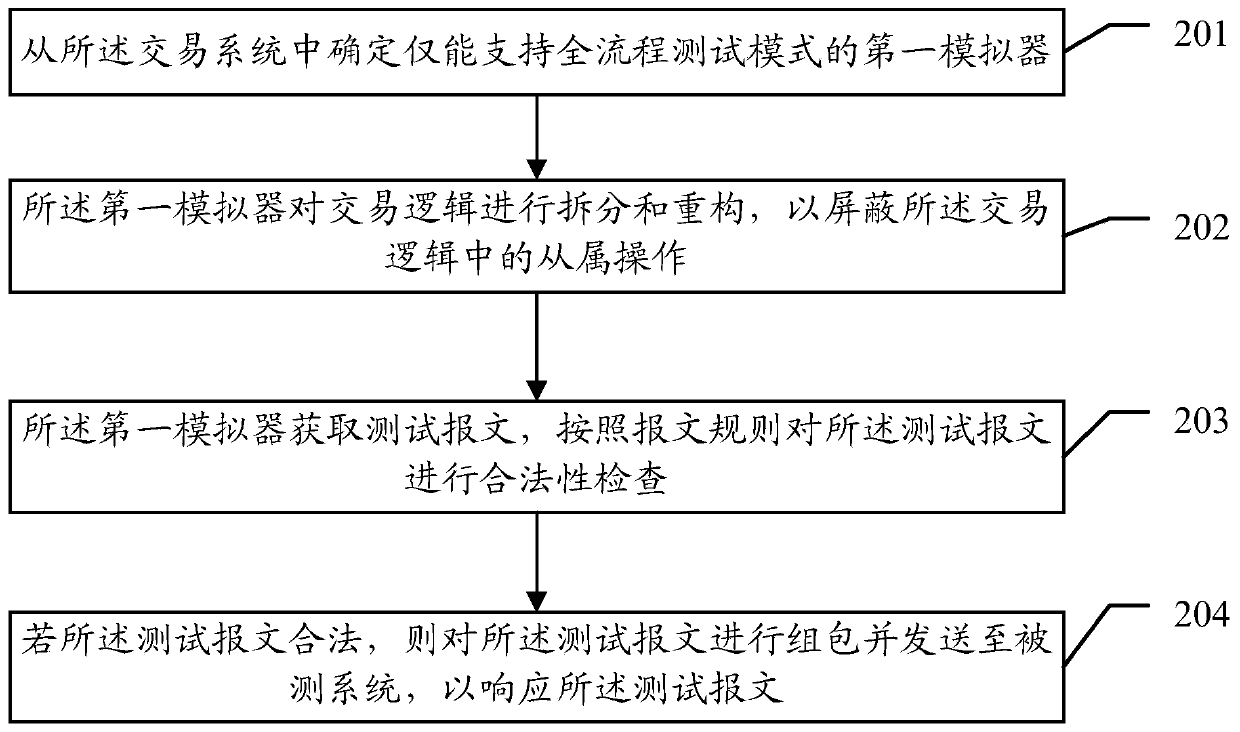
Simulation transaction test method, simulator, equipment and storage medium
ActiveCN110309022AReduce entryLegitimacy check optimizationFinanceFunctional testingProgramming languageTransaction logic
The invention relates to the field of performance testing of transaction systems, and provides a simulation transaction test method, a simulator, equipment and a storage medium. The simulation transaction test method comprises the steps that a first simulator splits and reconstructs transaction logic so as to shield subordinate operations in the transaction logic, wherein the transaction logic comprises statistical mining, data mining, technical indexes and transaction signals, and the subordinate operation refers to unnecessary operation in the transaction logic; the first simulator obtains atest message, and checks the legality of the test message according to a message rule, and the test message is a message used for the first simulator to test a tested system; and if the test messageis legal, the test message is packaged and sent to a tested system so as to respond to the test message. By adopting the scheme, unnecessary steps can be automatically shielded, so that the correlation dependence is reduced, and the input of meaningless fields is reduced.
Owner:PING AN BANK CO LTD
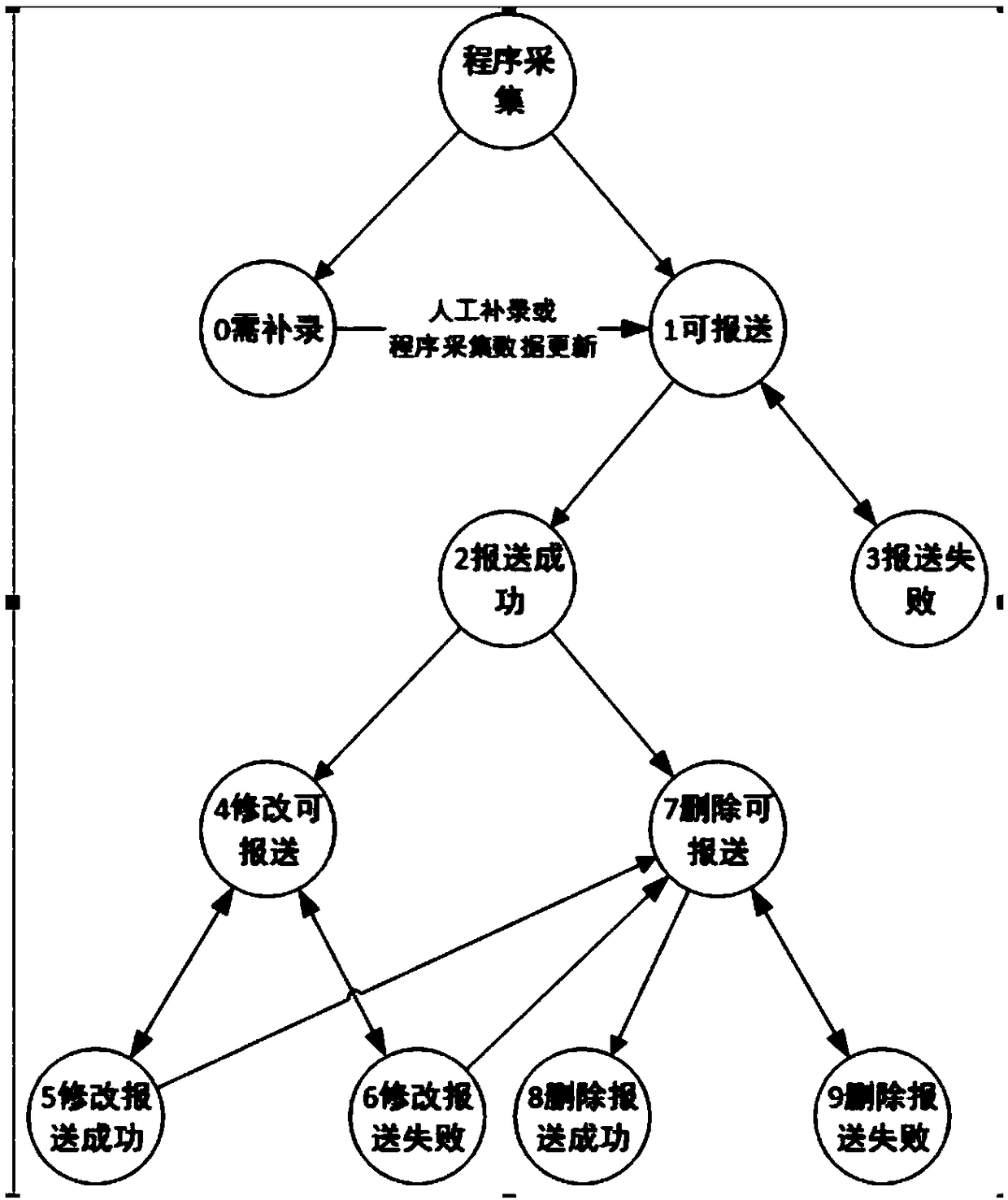
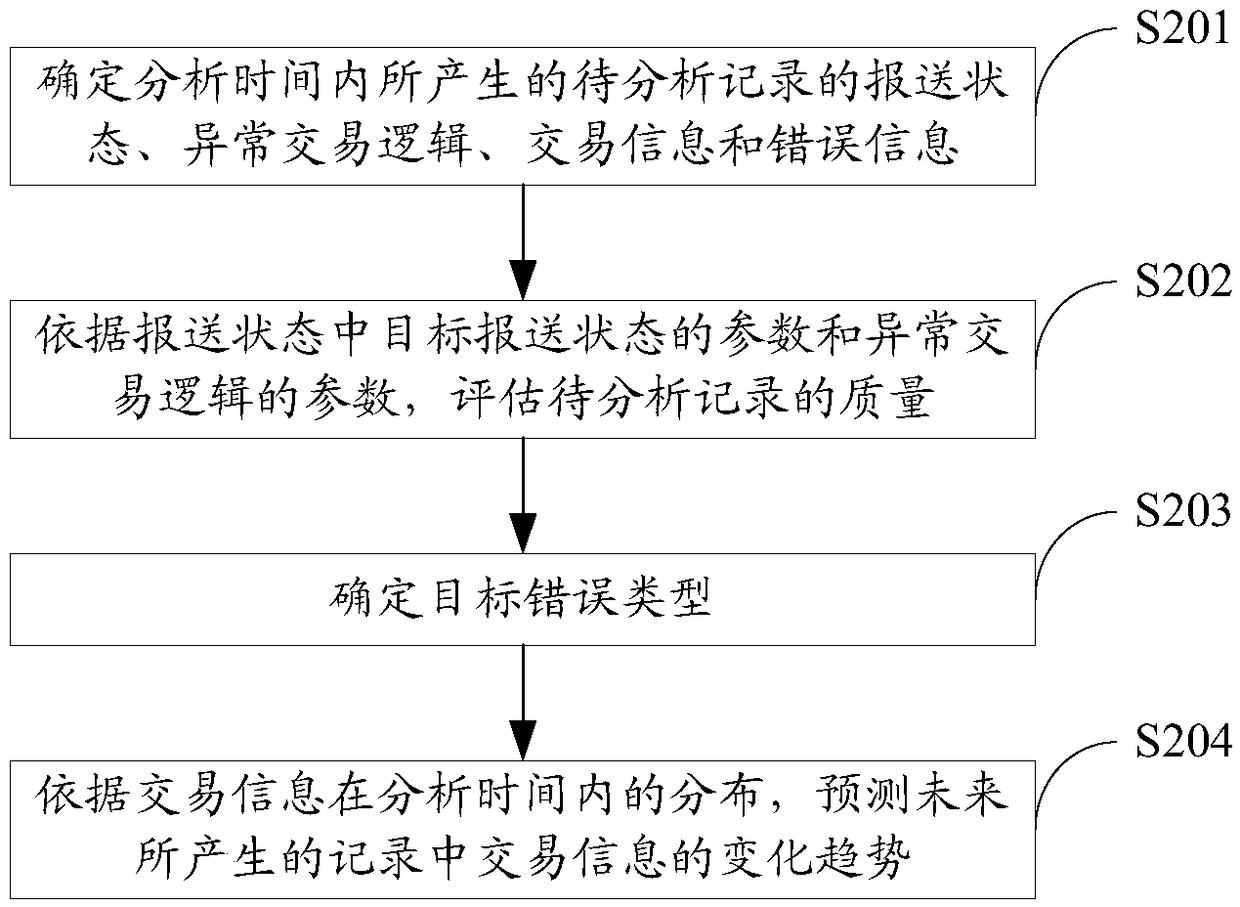
Data analysis method and device
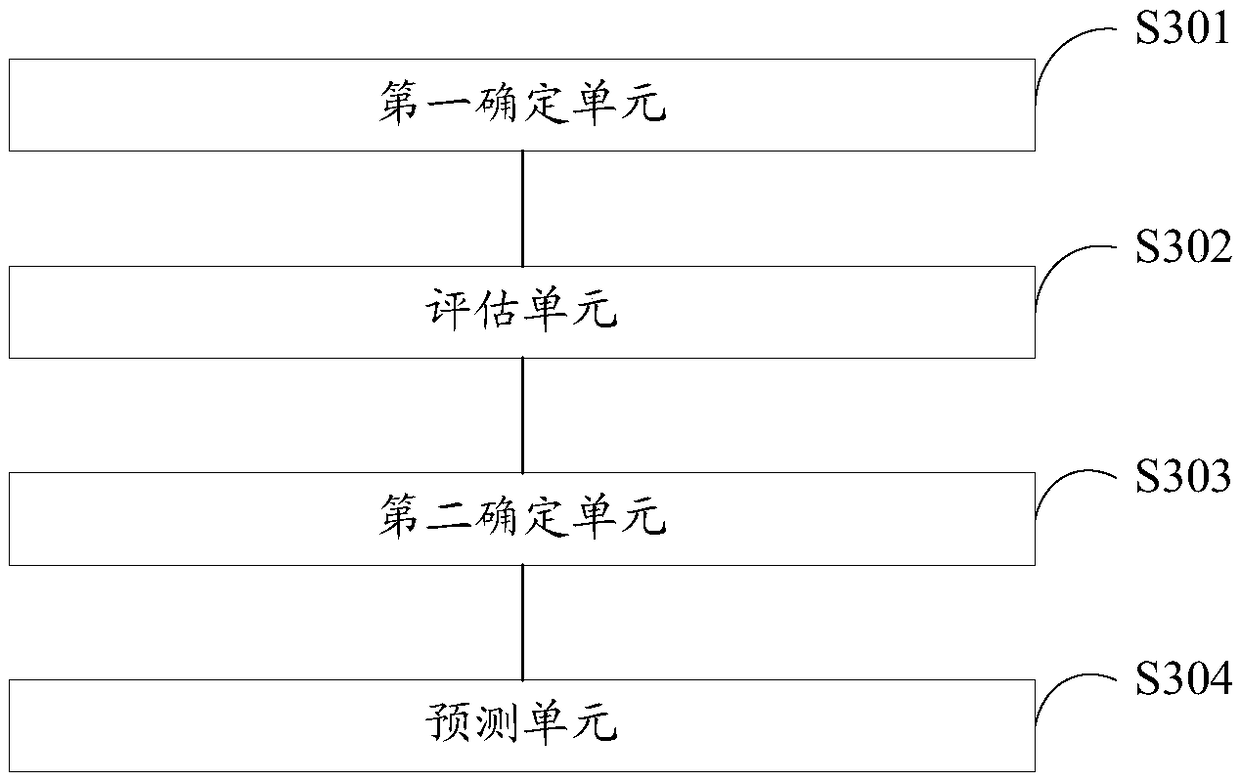
The invention discloses a data analysis method and device. The method comprises the following steps: determining the reporting state, abnormal transaction logic, transaction information and error information of to-be-analyzed records generated in the analysis time, wherein the error information includes an error type of the error data existing in the to-be-analyzed records fed back by an externalsupervision department; evaluating the quality of the to-be-analyzed records according to the parameters of a target reporting state in the reporting state and the parameters of the abnormal transaction logic; determining the target error type, wherein the target error type is an error type with the number of occurrence of errors in the error message being greater than a preset number threshold value; and predicting the change trend of the transaction information in the records generated in the future according to the distribution of the transaction information in the analysis time. The embodiment of the present invention can improve the modification efficiency of the error data, provide data support for the upgrading of the data transmission system and provide data support for the decision-making of the business personnel.
Owner:BANK OF CHINA
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com