Data processing apparatus security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
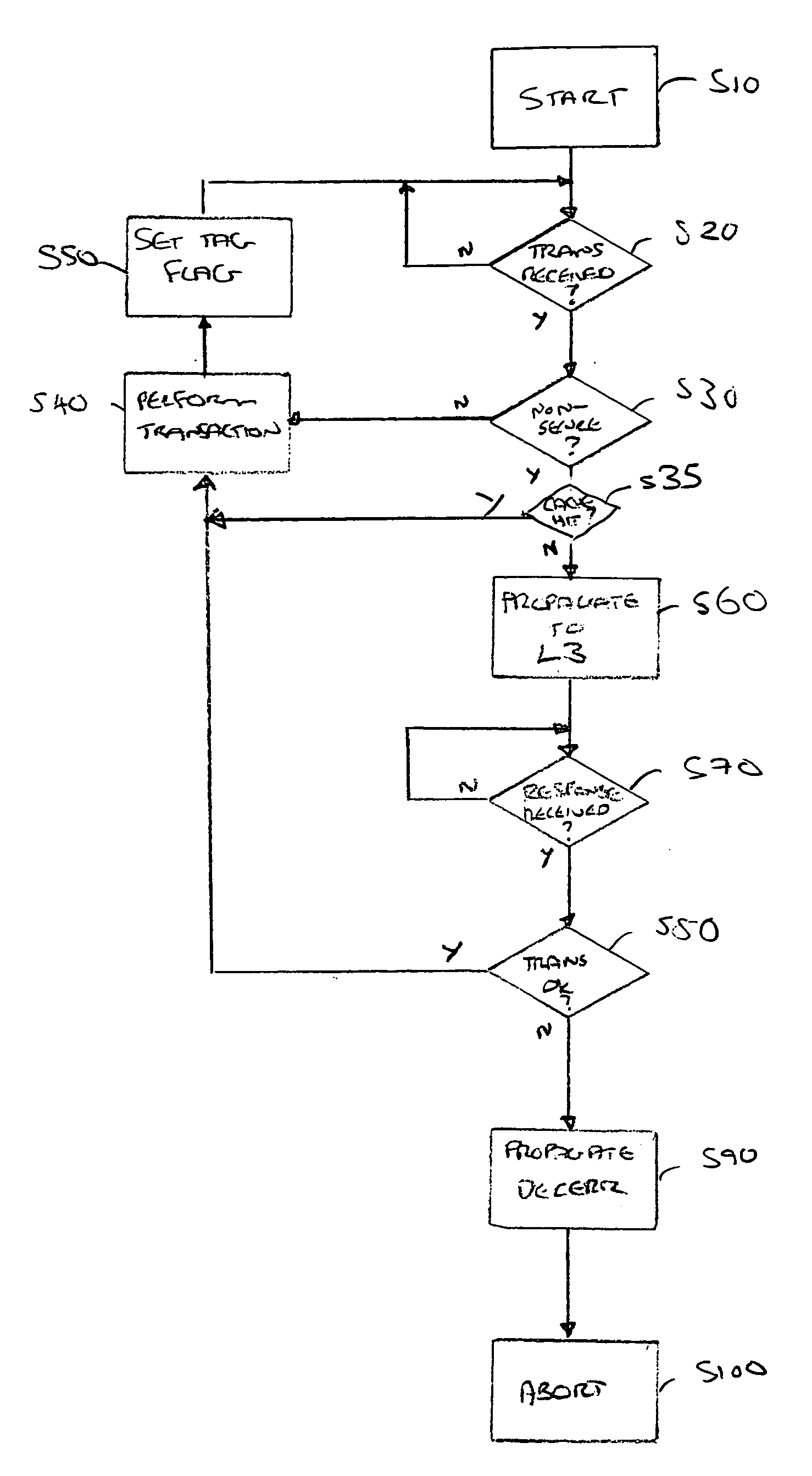
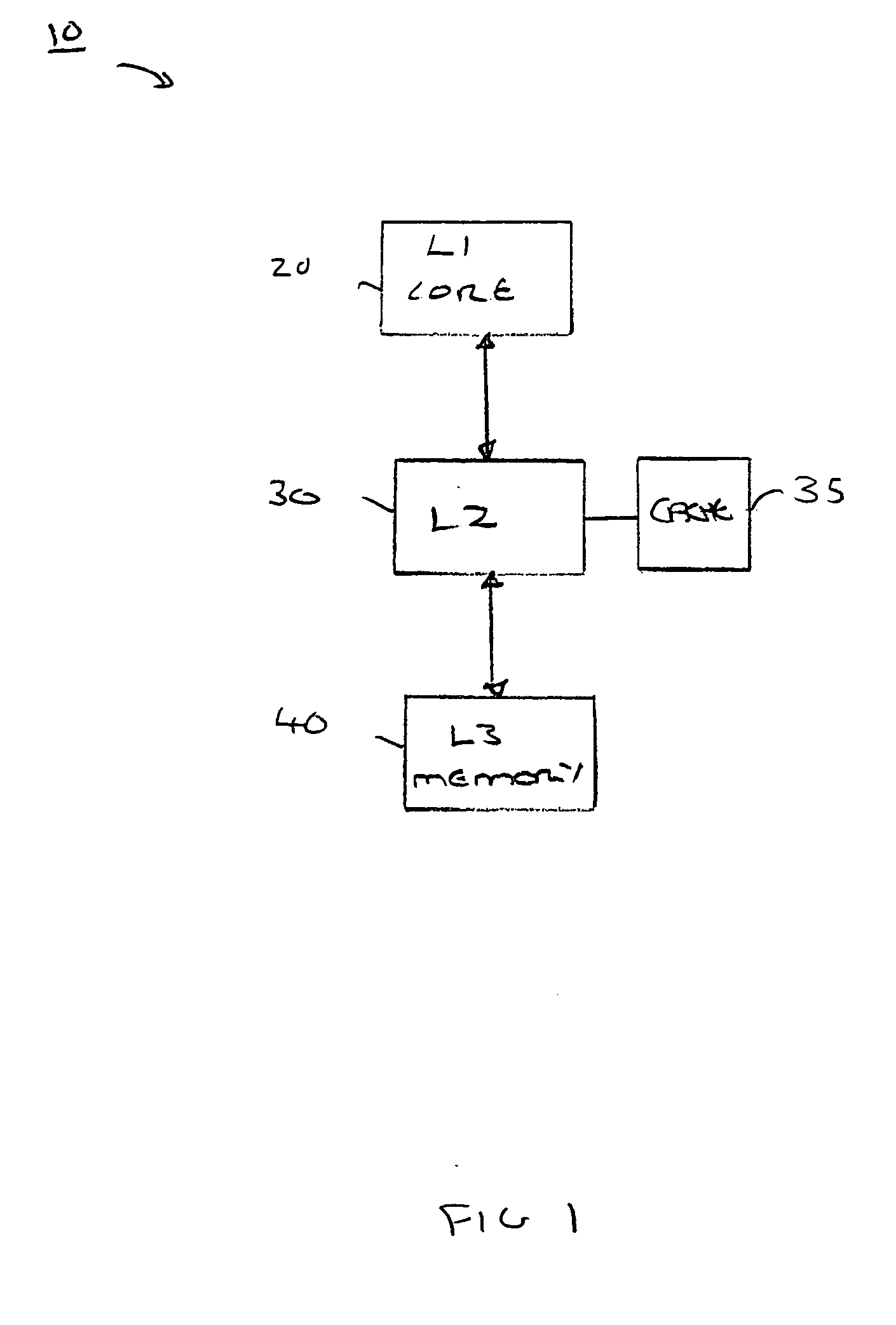
[0049]FIG. 1 illustrates a data processing system according to an embodiment. The data processing system, generally 10, comprises a level 1 processor core 20. Coupled with the level 1 processor core 20 is a level 2 memory 30 having a cache 35 and a level three memory 40.
[0050] The level 1 processor core 20 is operable to execute a sequence of instructions that are applied to data values supplied to the processor core 20. Instructions and data to be processed by the processor core 20 are stored in the level three memory 40. Hereafter, the term data value will be used to refer to both instructions and data.
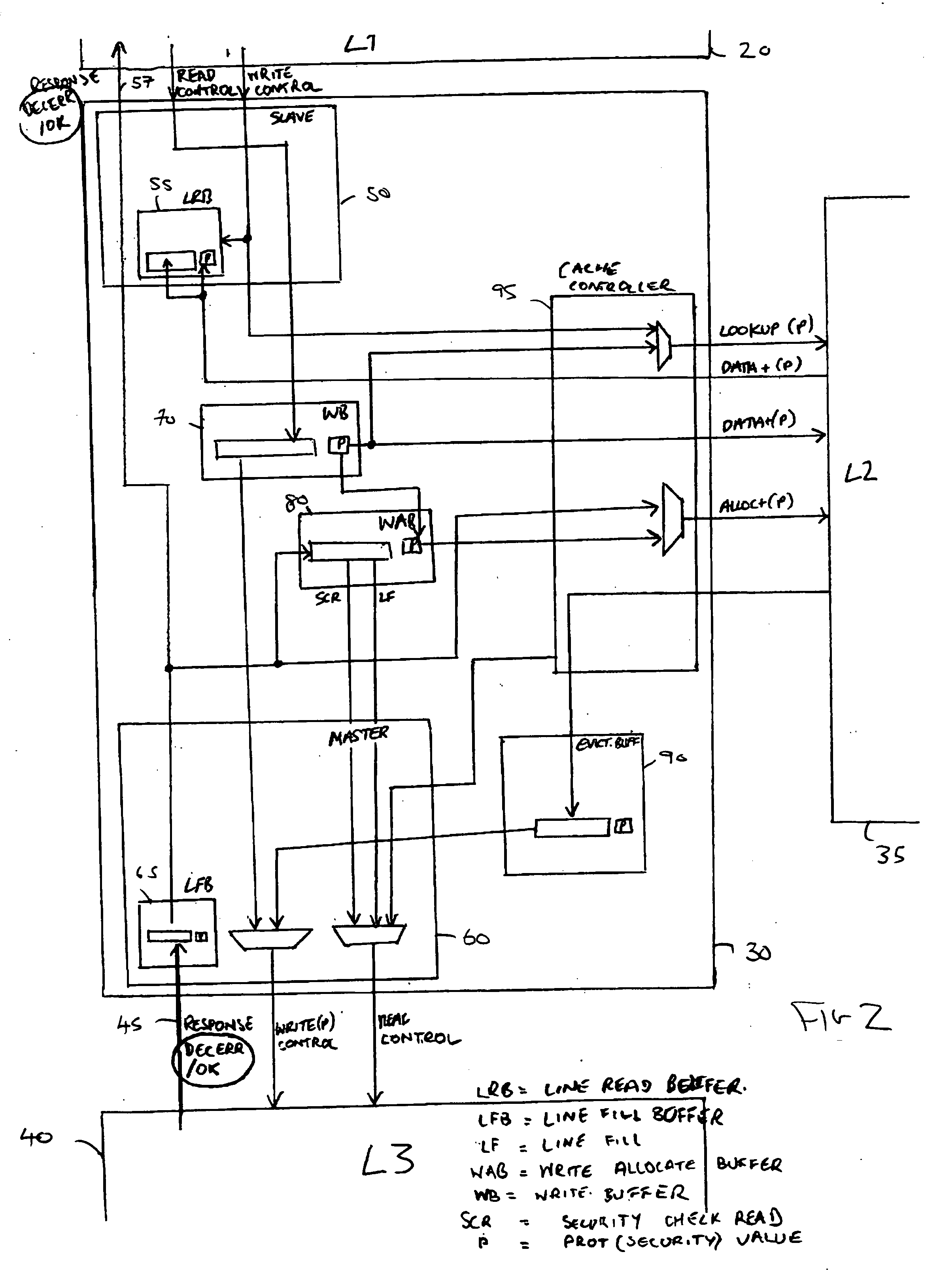
[0051] The level 2 memory 30 includes the cache 35 arranged to store data values so that they are subsequently readily accessible by the processor core 20 using a reduced number of access cycles when compared to an equivalent access to the level three memory 40. The cache 35 stores a data value associated with a memory address until it is overwritten by a data value for a new memo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com