Patents
Literature
232 results about "Mission critical" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
A mission critical factor of a system is any factor (component, equipment, personnel, process, procedure, software, etc.) that is essential to business operation or to an organization. Failure or disruption of mission critical factors will result in serious impact on business operations or upon an organization, and even can cause social turmoil and catastrophes.
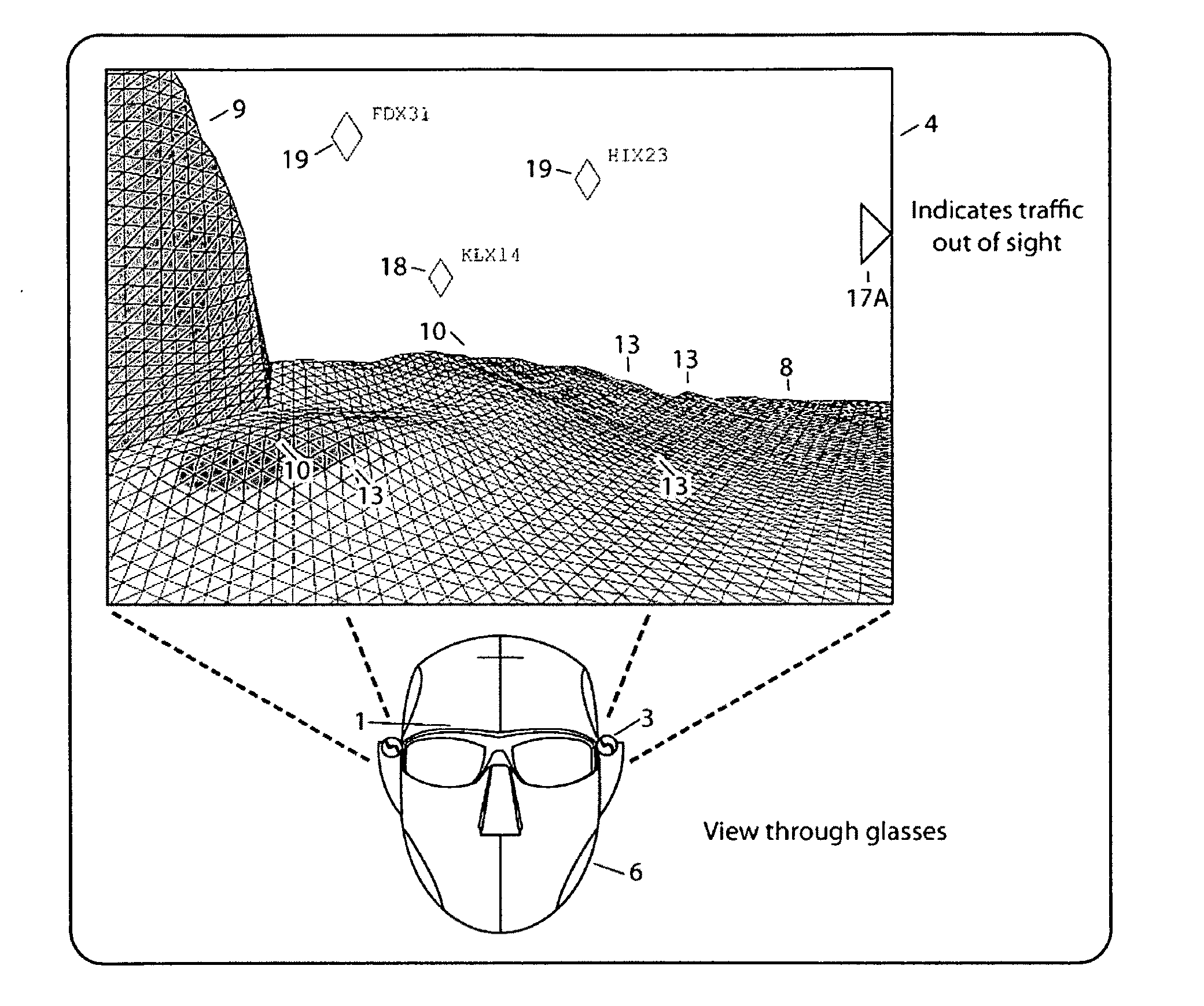
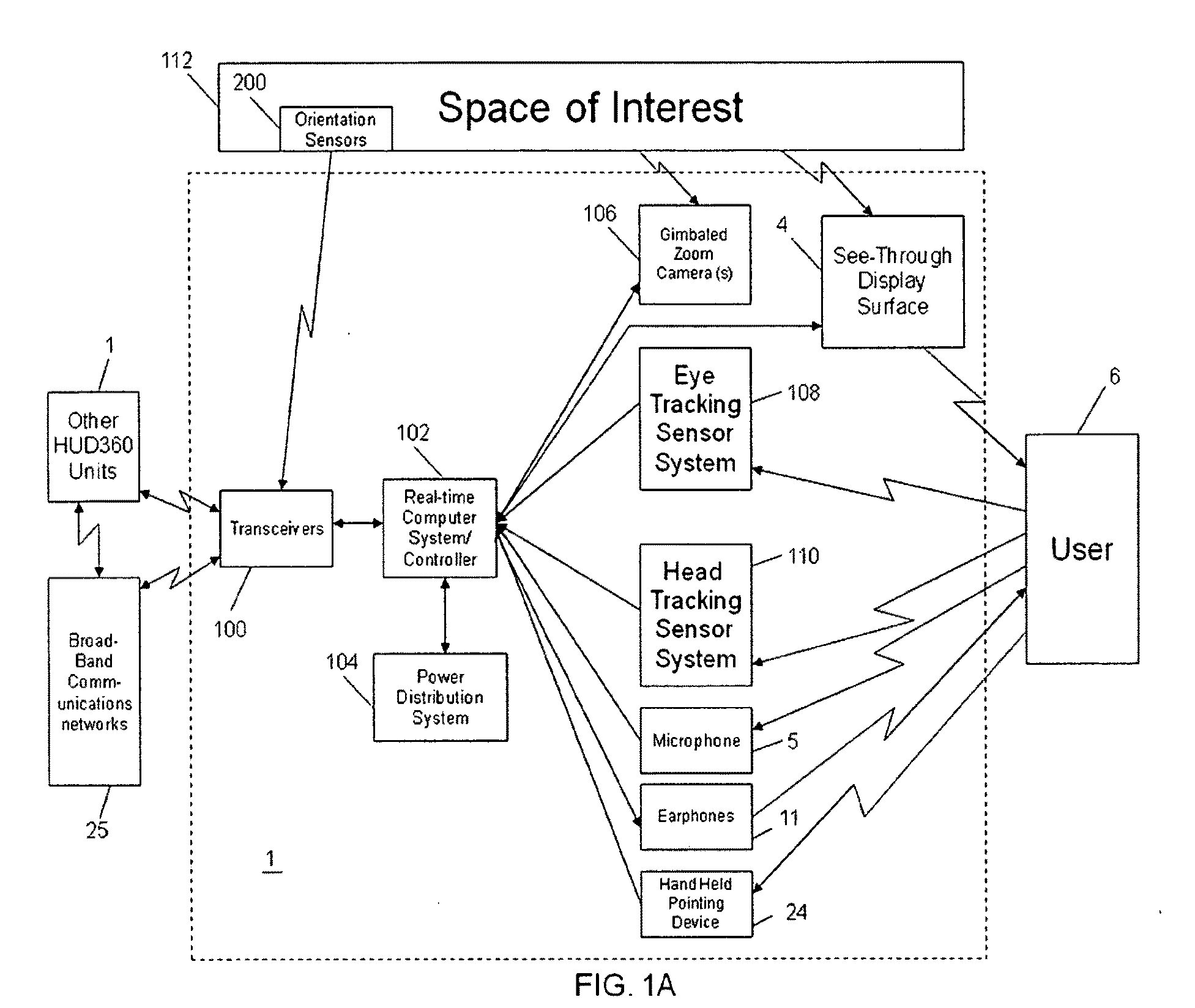
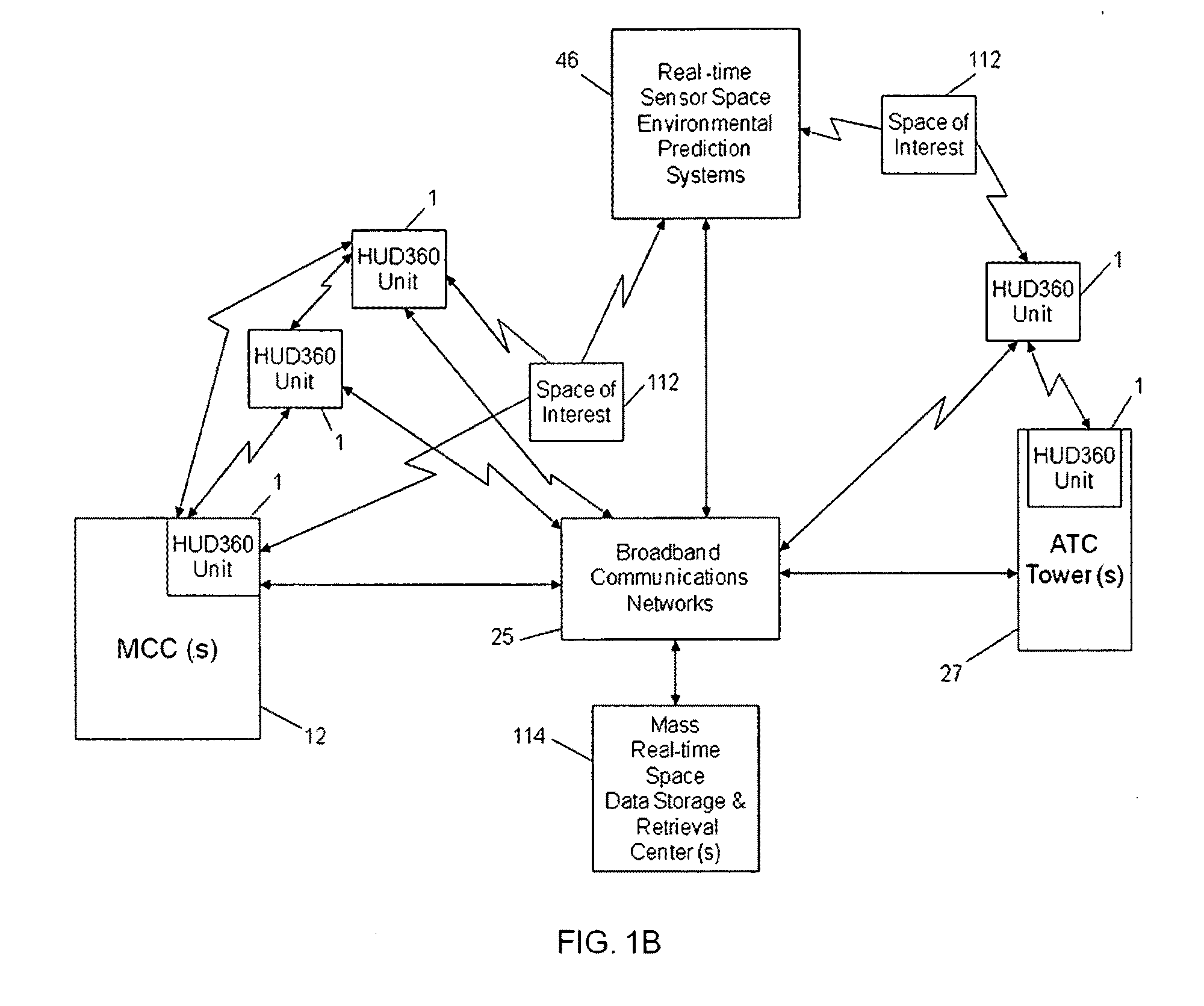
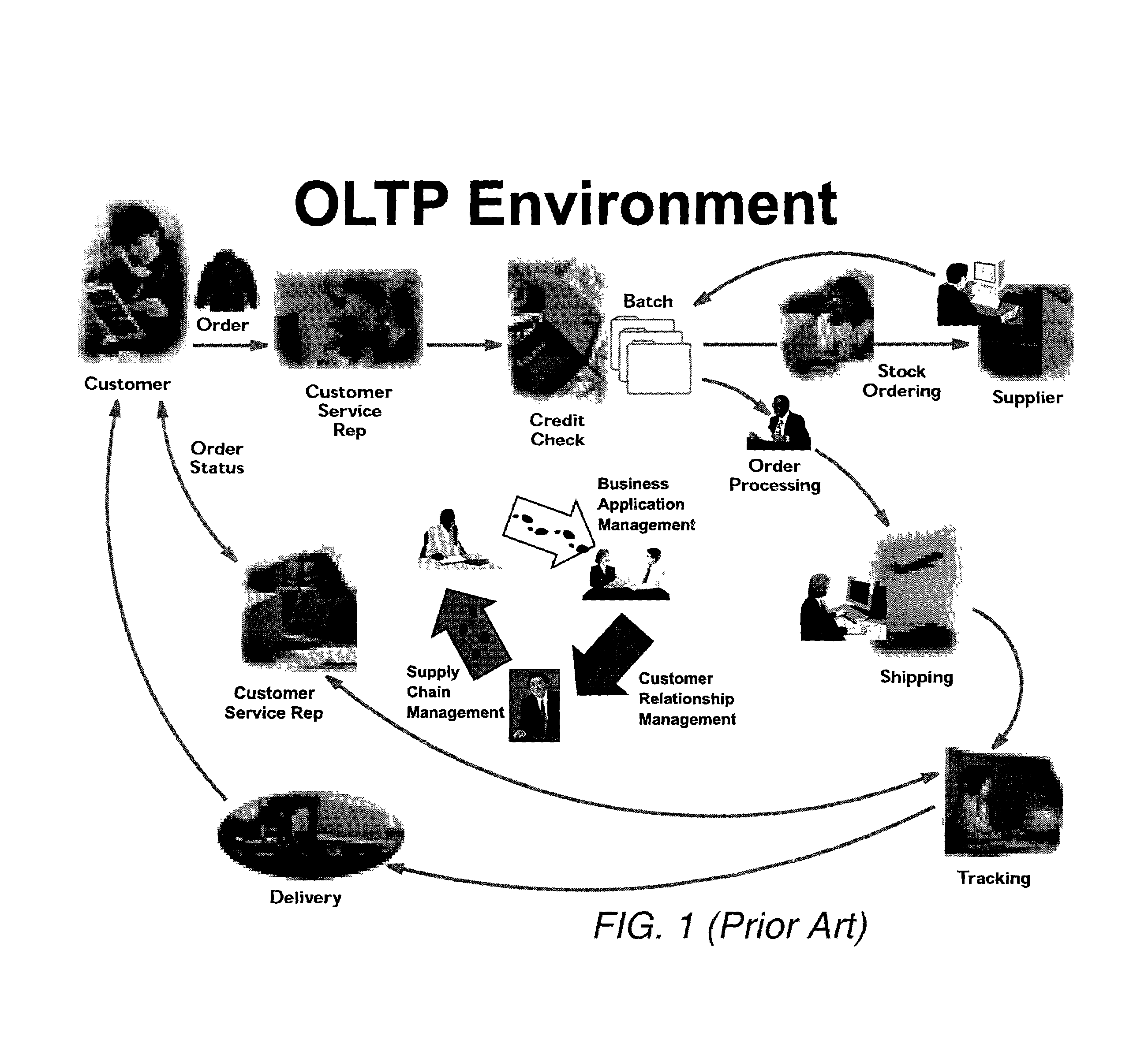
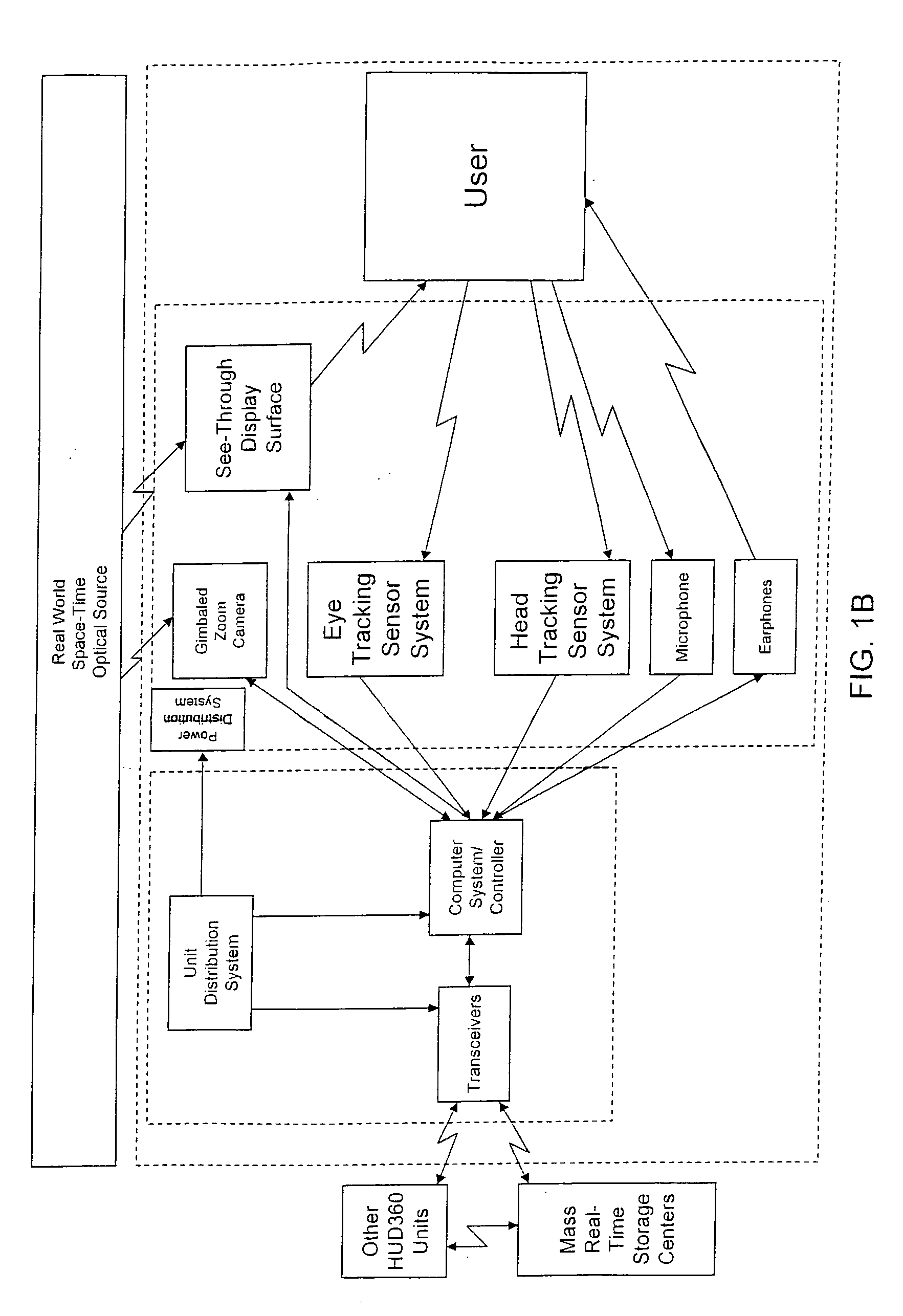
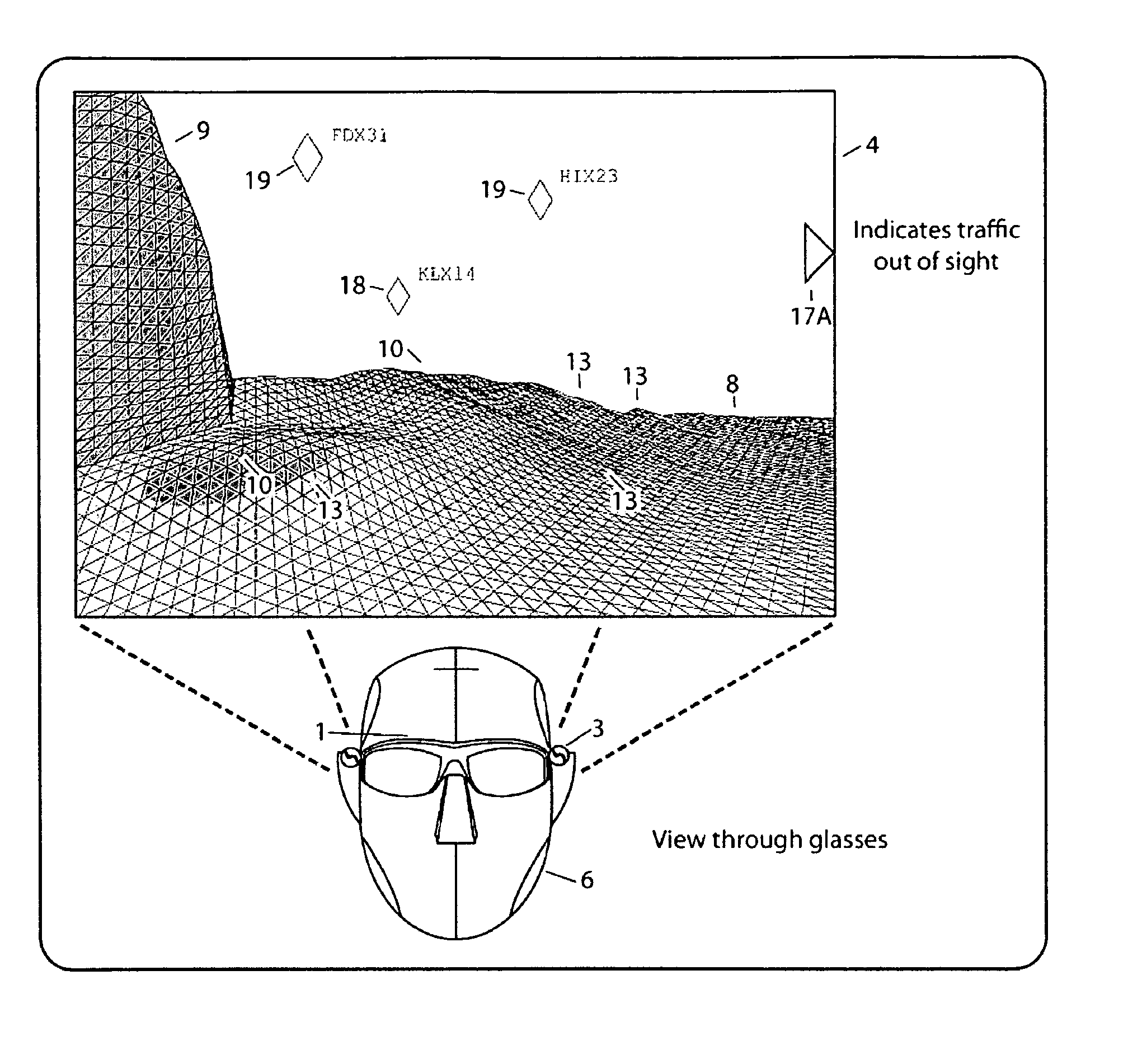
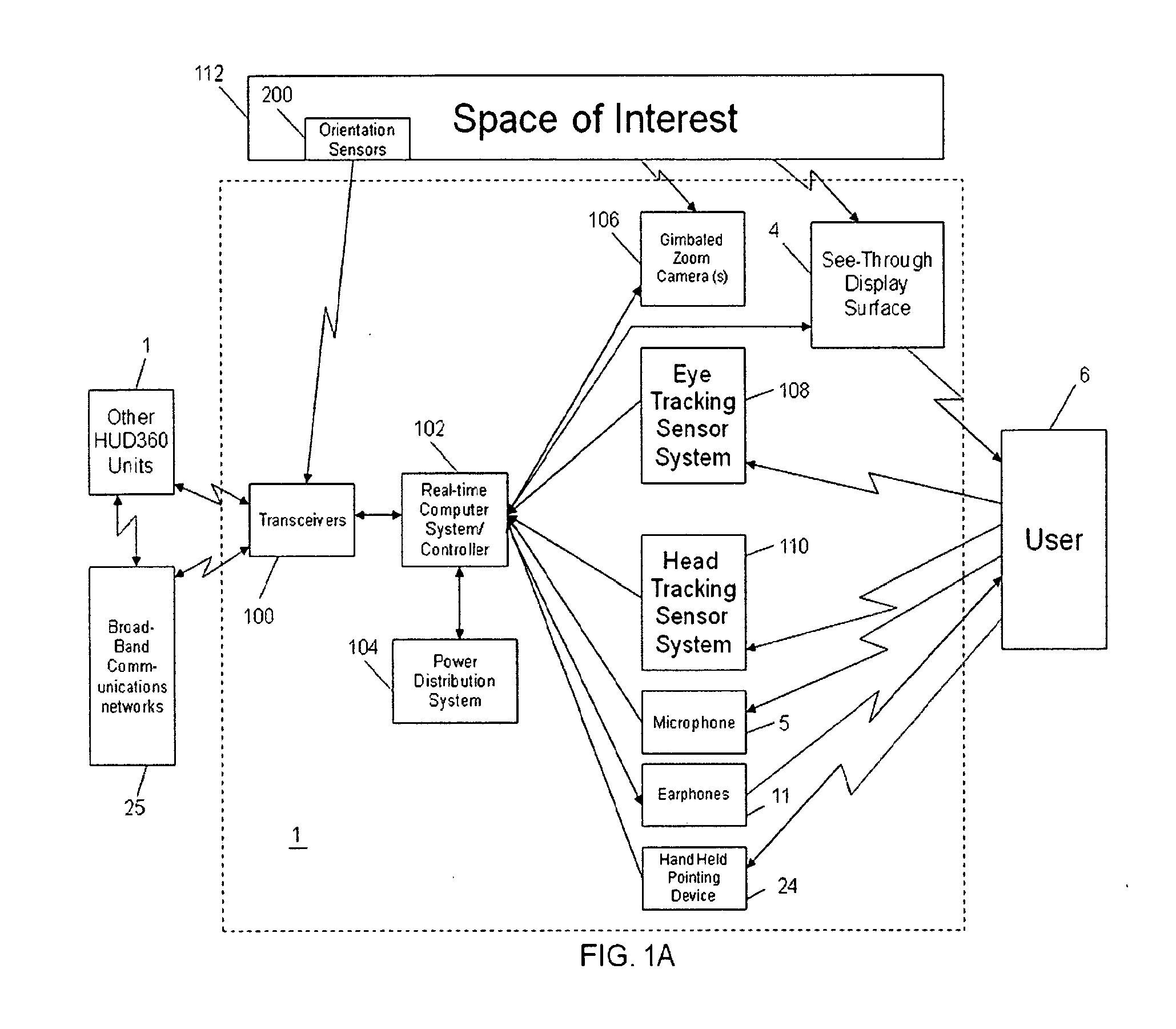
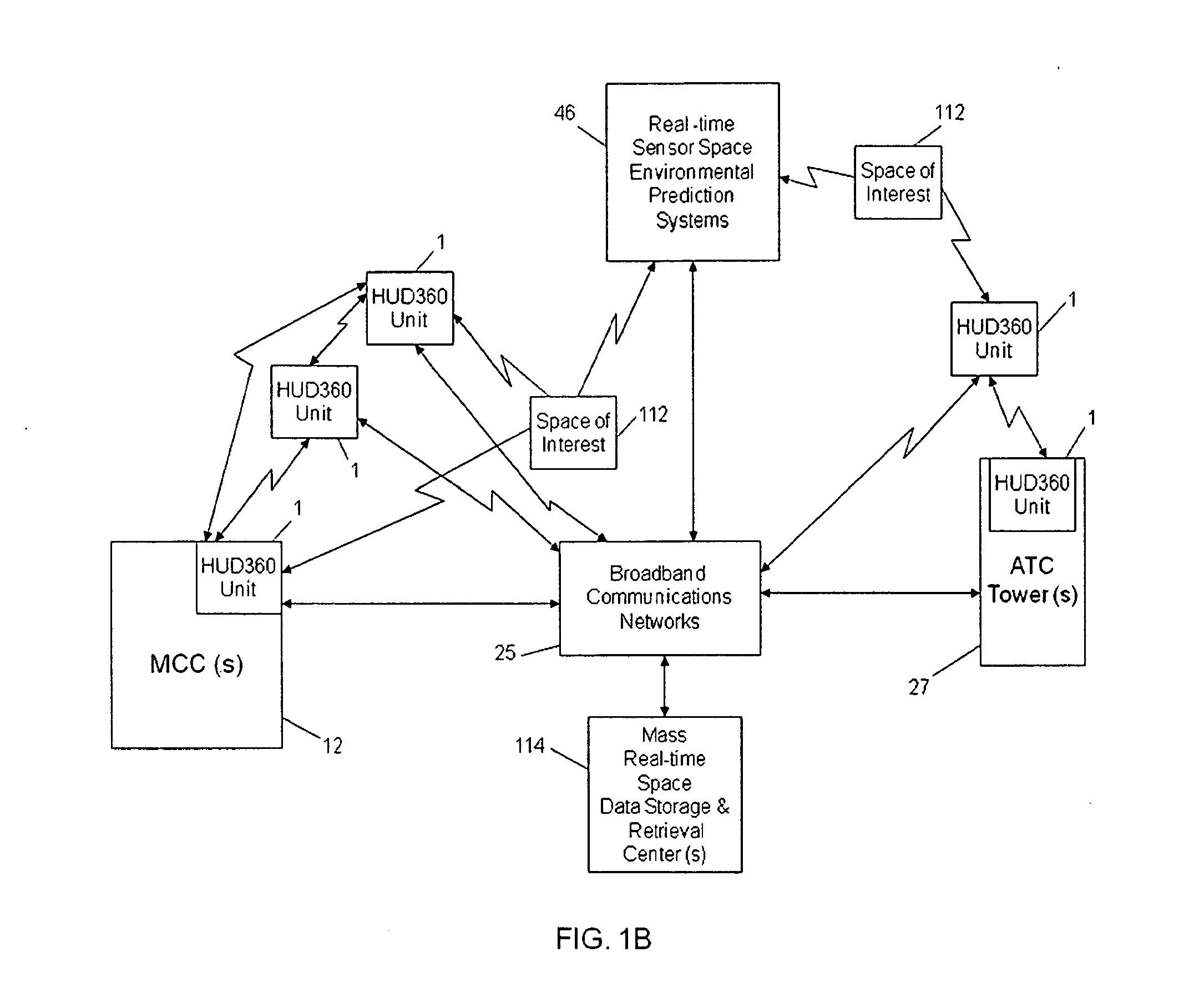
Computer-aided system for 360º heads up display of safety/mission critical data
InactiveUS20100238161A1Improve assessmentSatisfy safety performance requirementsCathode-ray tube indicatorsInput/output processes for data processingHead-up displayDisplay device
A safety critical, time sensitive data system for projecting safety / mission critical data onto a display pair of Commercial Off The Shelf (COTS) light weight projection glasses or monocular creating a virtual 360° HUD (Heads Up Display) with 6 degrees of freedom movement. The system includes the display, the workstation, the application software, and inputs containing the safety / mission critical information (Current User Position, Total Collision Avoidance System—TCAS, Global Positioning System—GPS, Magnetic Resonance Imaging—MRI Images, CAT scan images, Weather data, Military troop data, real-time space type markings etc.). The workstation software processes the incoming safety / mission critical data and converts it into a three dimensional space for the user to view. Selecting any of the images may display available information about the selected item or may enhance the image. Predicted position vectors may be displayed as well as 3D terrain.
Owner:REALTIME
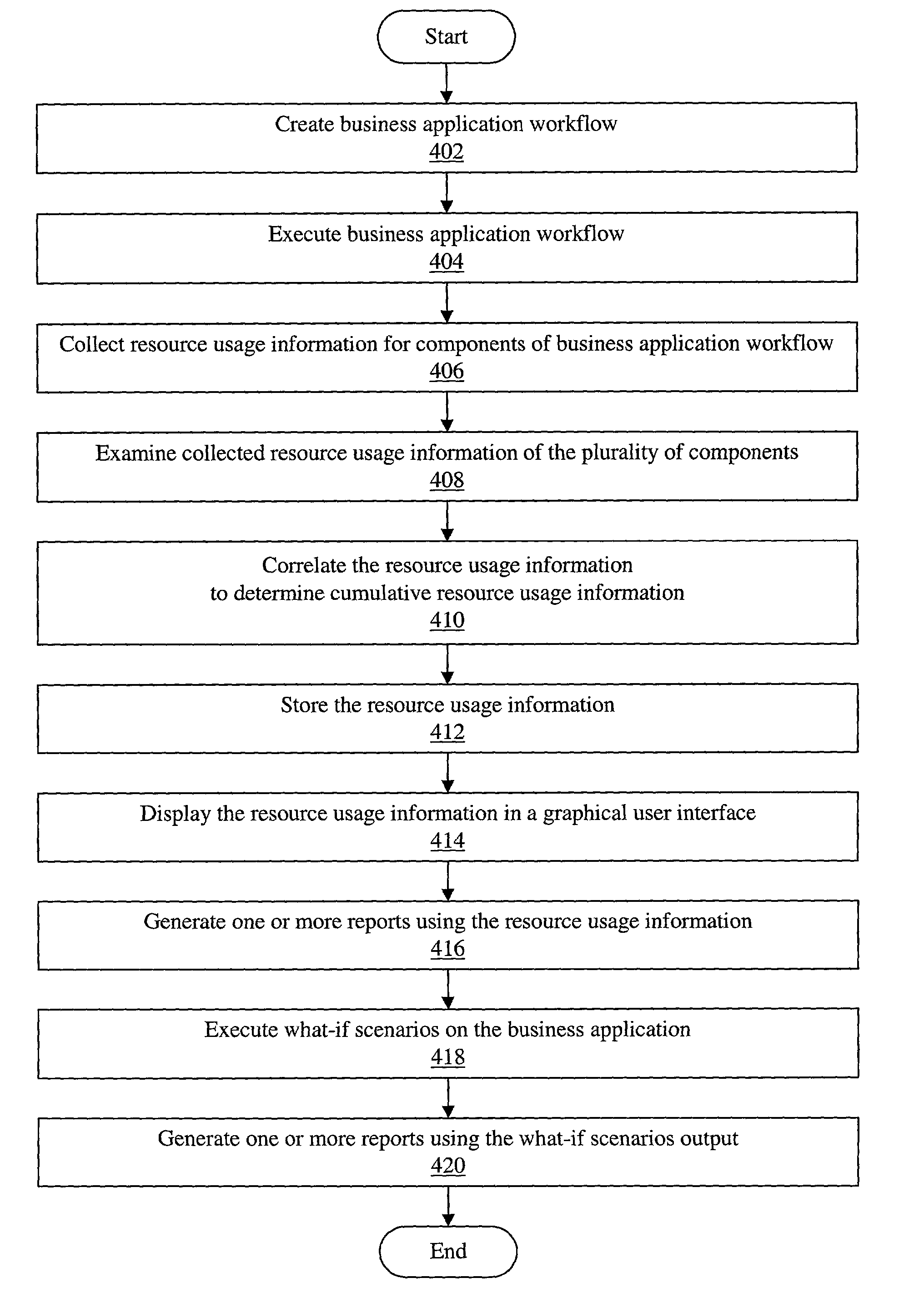
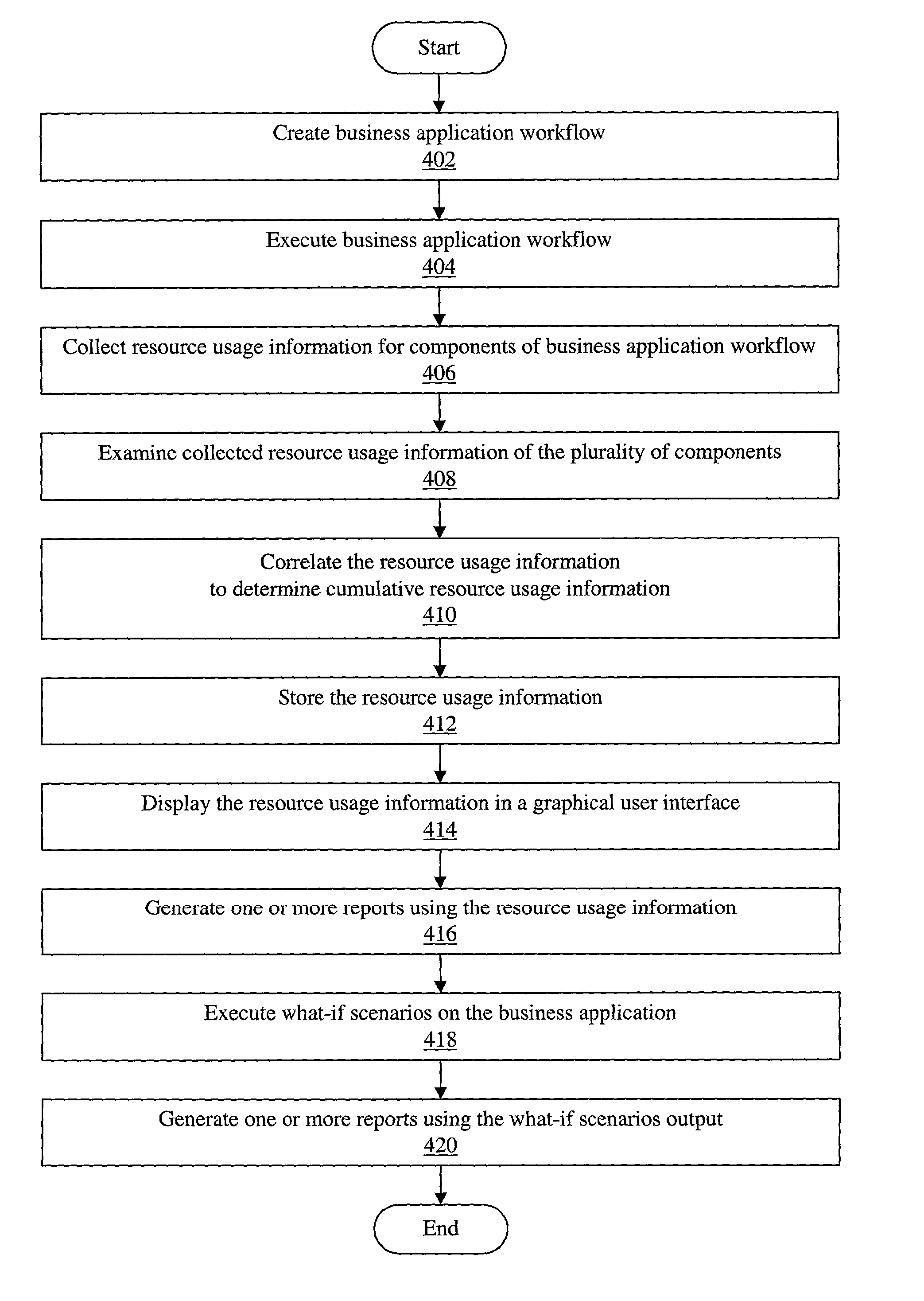
System and method for application performance management
InactiveUS7350209B2General purpose stored program computerHardware monitoringComputer resourcesUser interface
Owner:BMC SOFTWARE
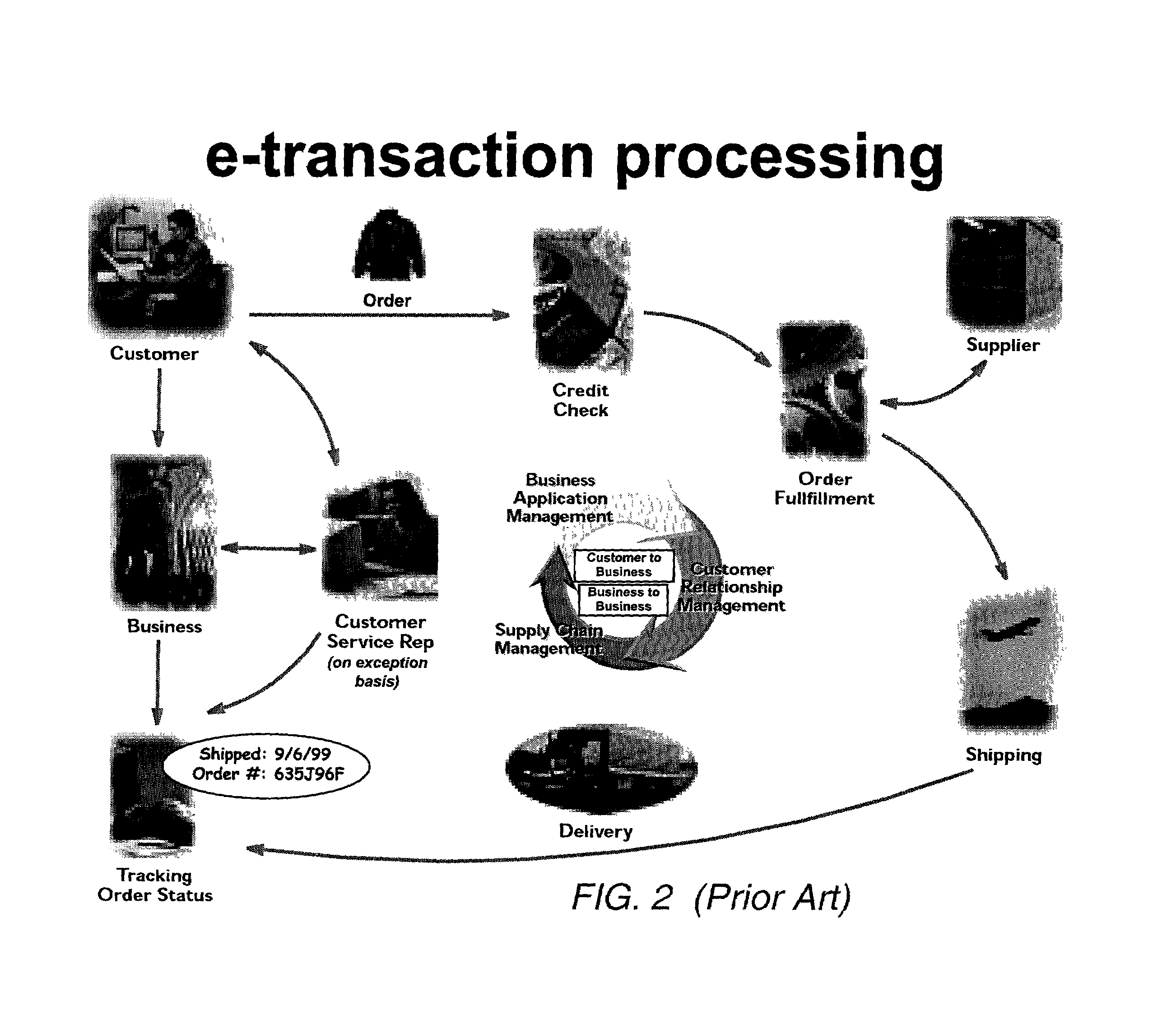
Computer-aided system for 360 degree heads up display of safety/mission critical data
InactiveUS20100240988A1Satisfy safety performance requirementsGuaranteed uptimeCathode-ray tube indicatorsDiagnostic recording/measuringHead-up displayDisplay device
A safety critical, time sensitive data system for projecting safety / mission critical data onto a display pair of Commercial Off The Shelf (COTS) light weight projection glasses or monocular creating a virtual 360° HUD (Heads Up Display) with 6 degrees of freedom movement. The system includes the display, the workstation, the application software, and inputs containing the safety / mission critical information (Current User Position, Total Collision Avoidance System—TCAS, Global Positioning System—GPS, Magnetic Resonance Imaging—MRI Images, CAT scan images, Weather data, Military troop data, real-time space type markings etc.). The workstation software processes the incoming safety / mission critical data and converts it into a three dimensional space for the user to view. Selecting any of the images may display available information about the selected item or may enhance the image. Predicted position vectors may be displayed as well as 3D terrain.
Owner:REALTIME
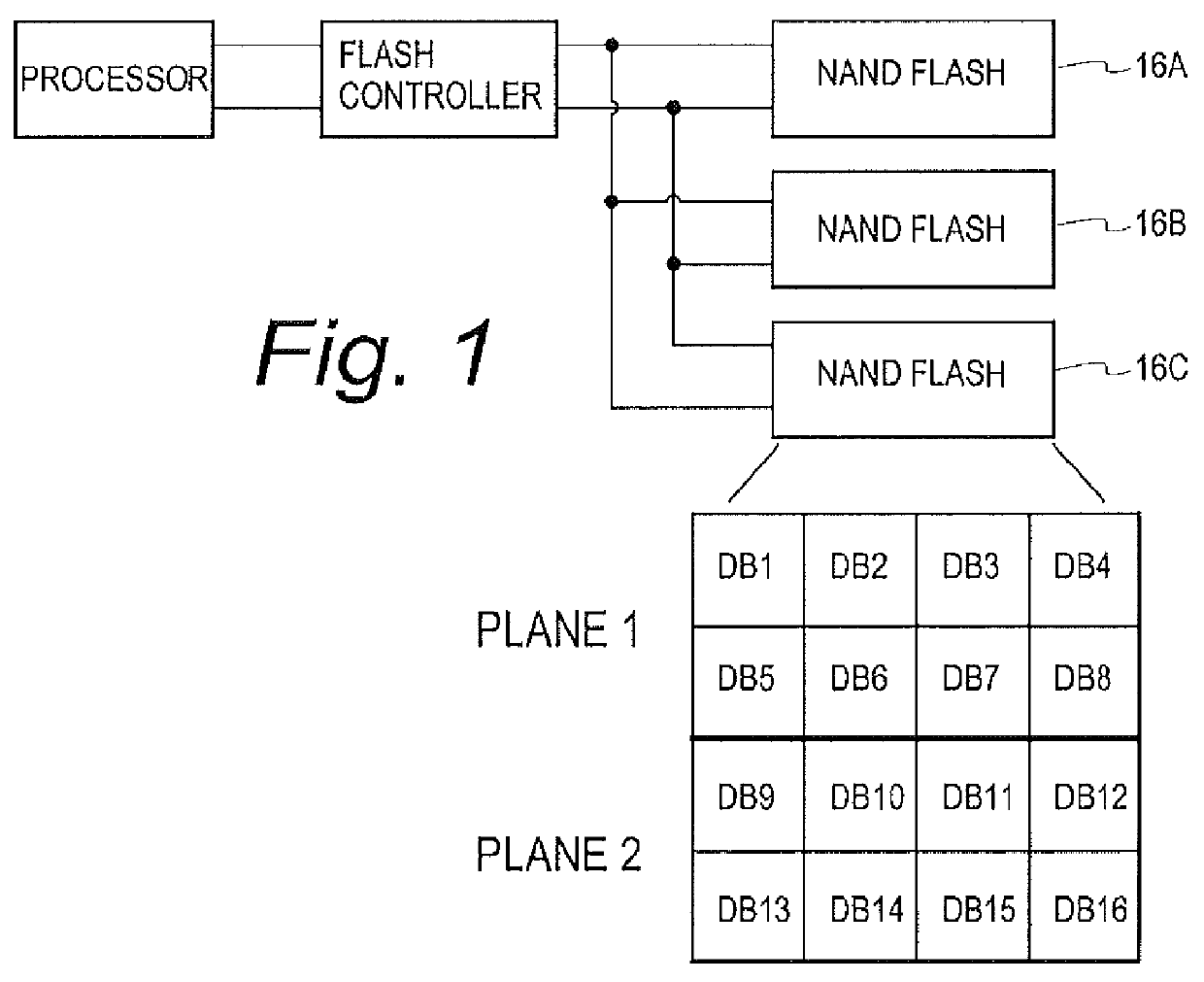
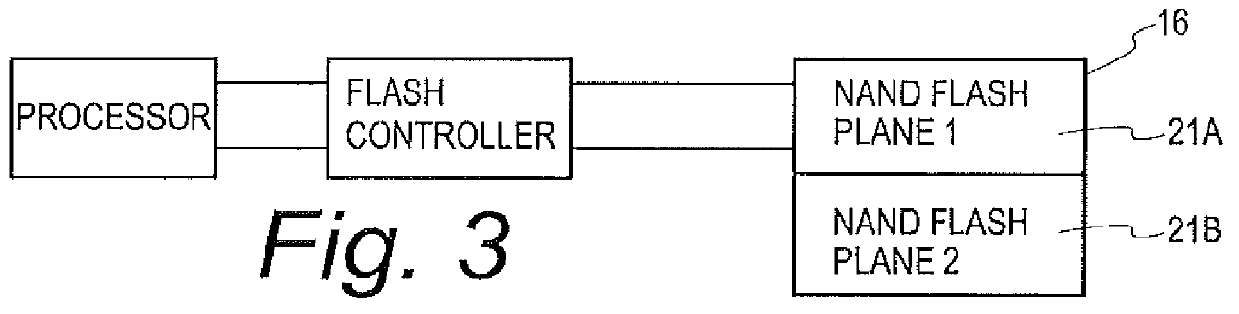
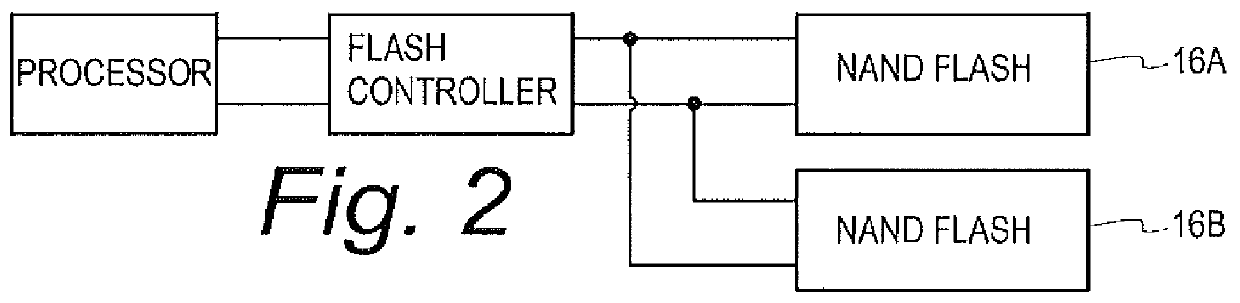
Mission critical NAND flash
InactiveUS20120226934A1Data storage is reliableAccurate contentMemory systemsRedundant hardware error correctionComputer hardwareComputer architecture
A flash controller reliably stores data in NAND FLASH by encoding data using an encoding algorithm, and storing that data across multiple pages of the memory. In one embodiment, true data is accepted by the controller, and the controller in turn creates coded data that is the bit-for-bit complement of the true data. The true data and the coded data are then written to the NAND FLASH on a page by page basis. A property of the coding techniques used is that, in at least some cases, detected errors can be corrected.
Owner:GREENTHREAD
Method and system for network management with backup status gathering
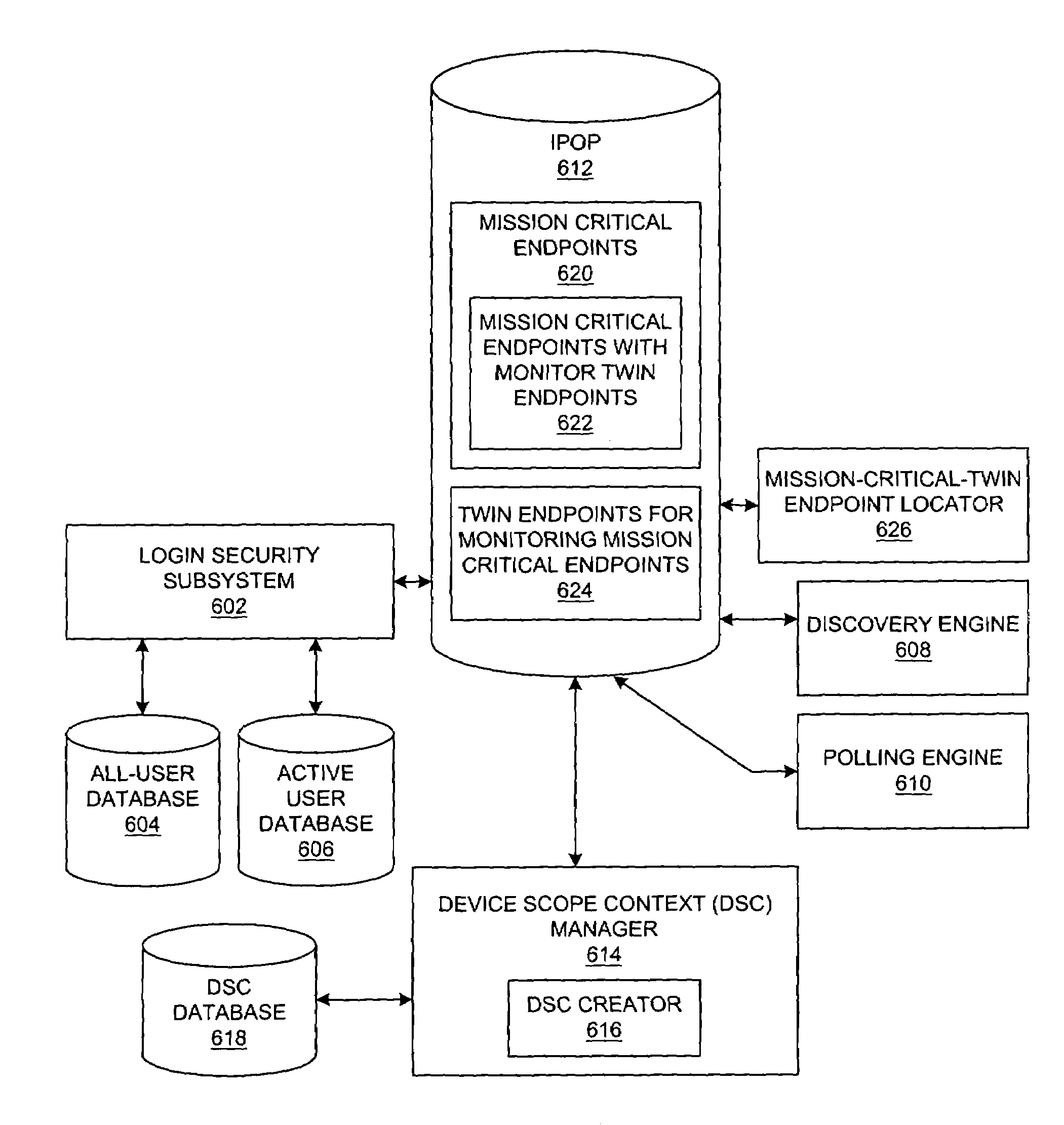
A method, system, apparatus, and computer program product are presented for management of a distributed data processing system. Resources within the distributed data processing system are dynamically discovered, and the discovered resources are adaptively monitored using the network management framework. A network or system administrator configures some mission critical endpoints with multiple network interface cards (NICs) and specifies mission critical endpoints, non-mission critical actions, etc. During status collection activities associated with network or system management activities, the categorization of an endpoint as a mission-critical or non-mission critical endpoint affects the manner in which the status collection activity is performed. Applications can request the performance of actions at endpoints without regard to the categorization of the endpoint or without regard to the categorization of the requested action, and the network management system routes the action based on whether or not the specified endpoint is a mission critical endpoint. A non-mission-critical endpoint is associated with a mission-critical endpoint based on the non-mission-critical endpoint's communication history with the mission critical endpoint. The management system may use the status of a non-mission-critical endpoint as a reflection of the status of a mission-critical endpoint.
Owner:GOOGLE LLC
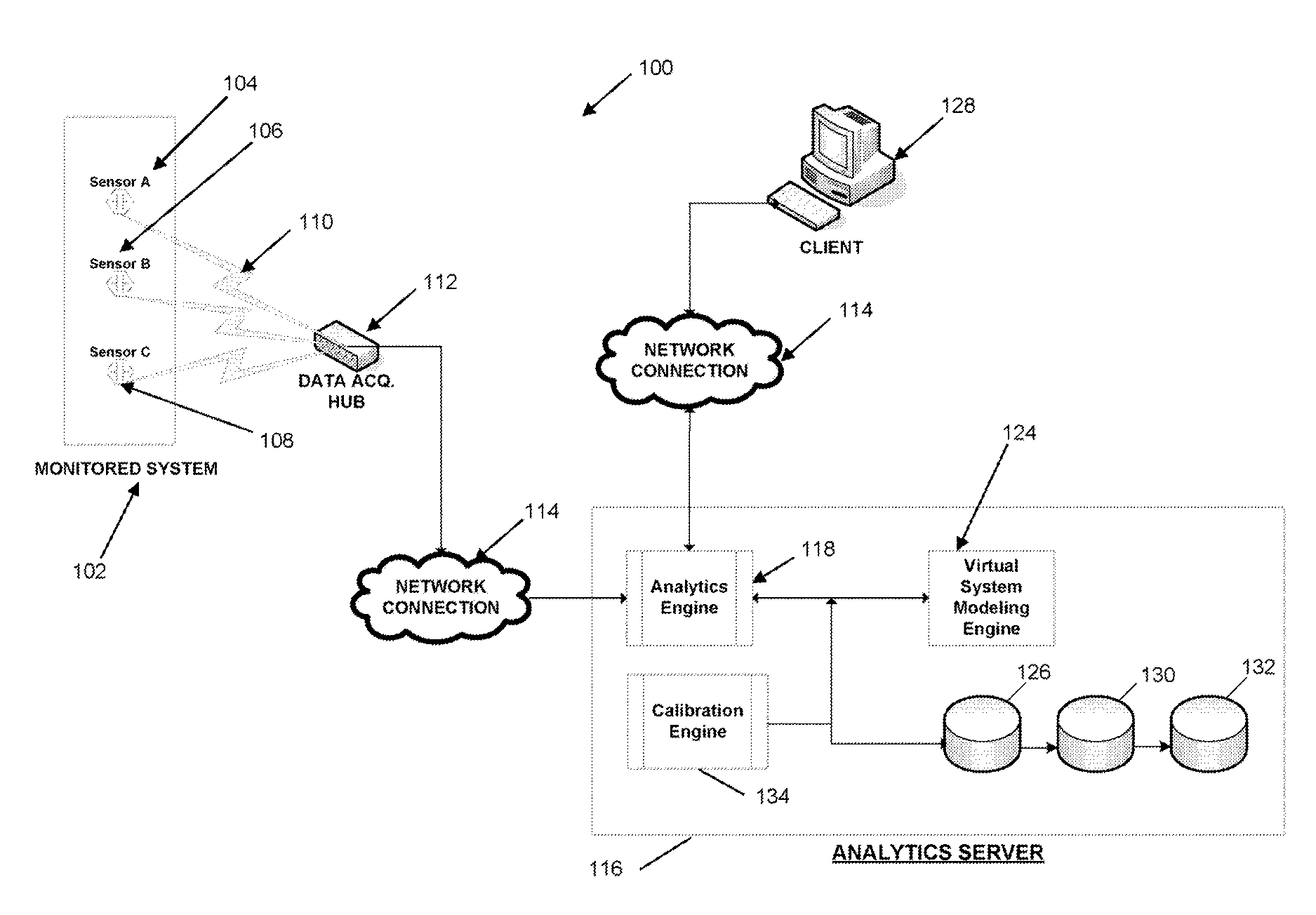
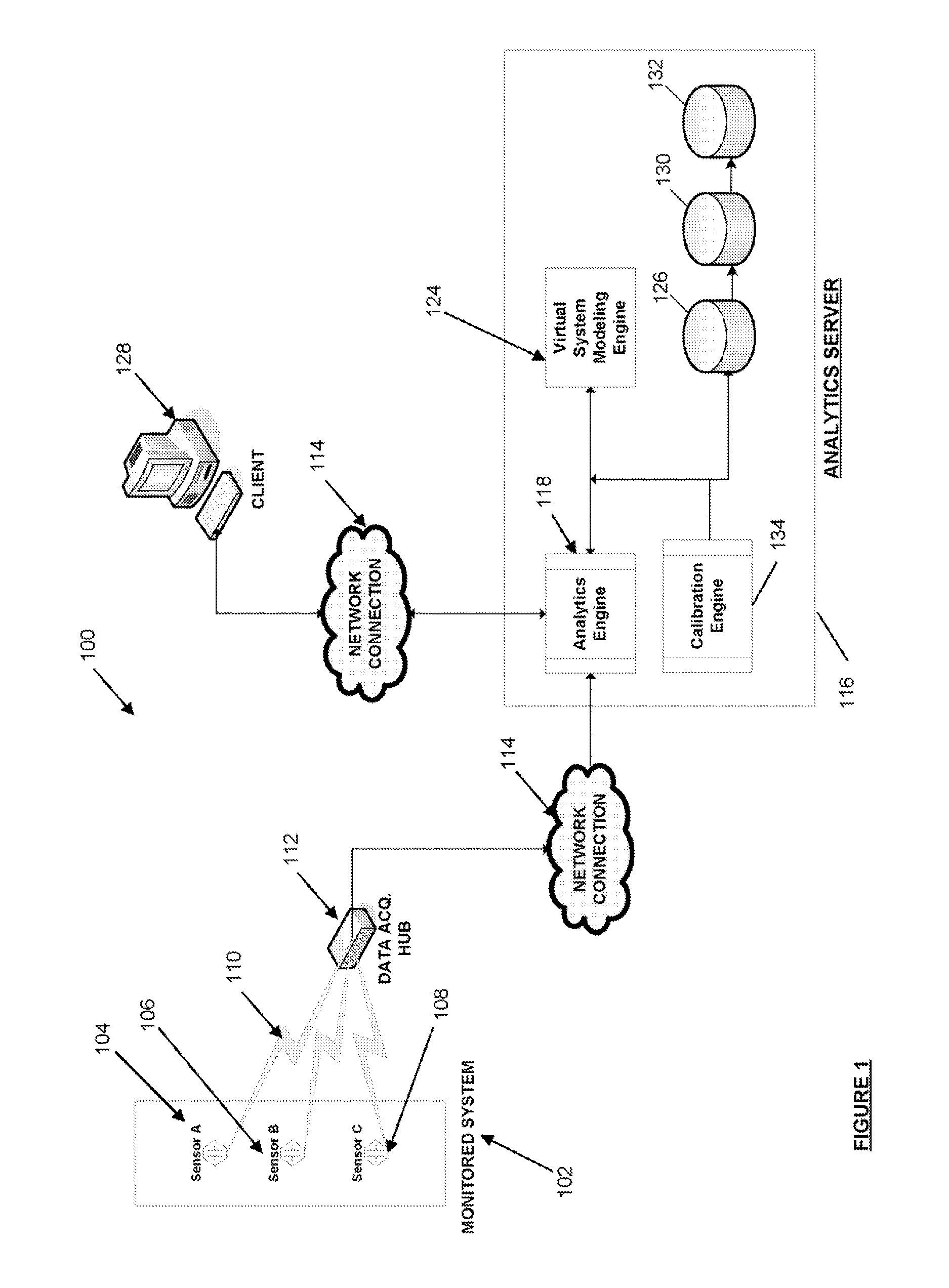
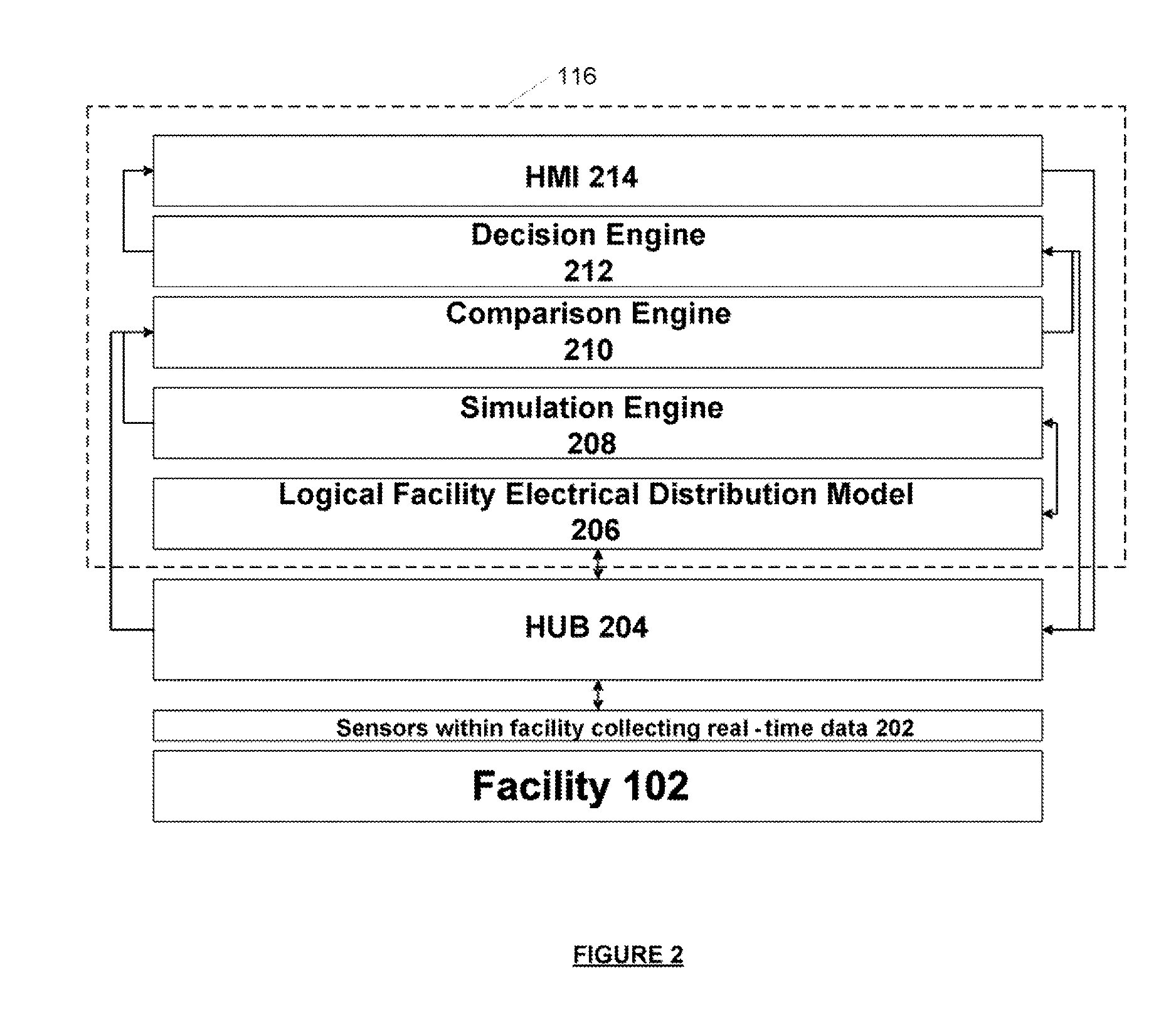
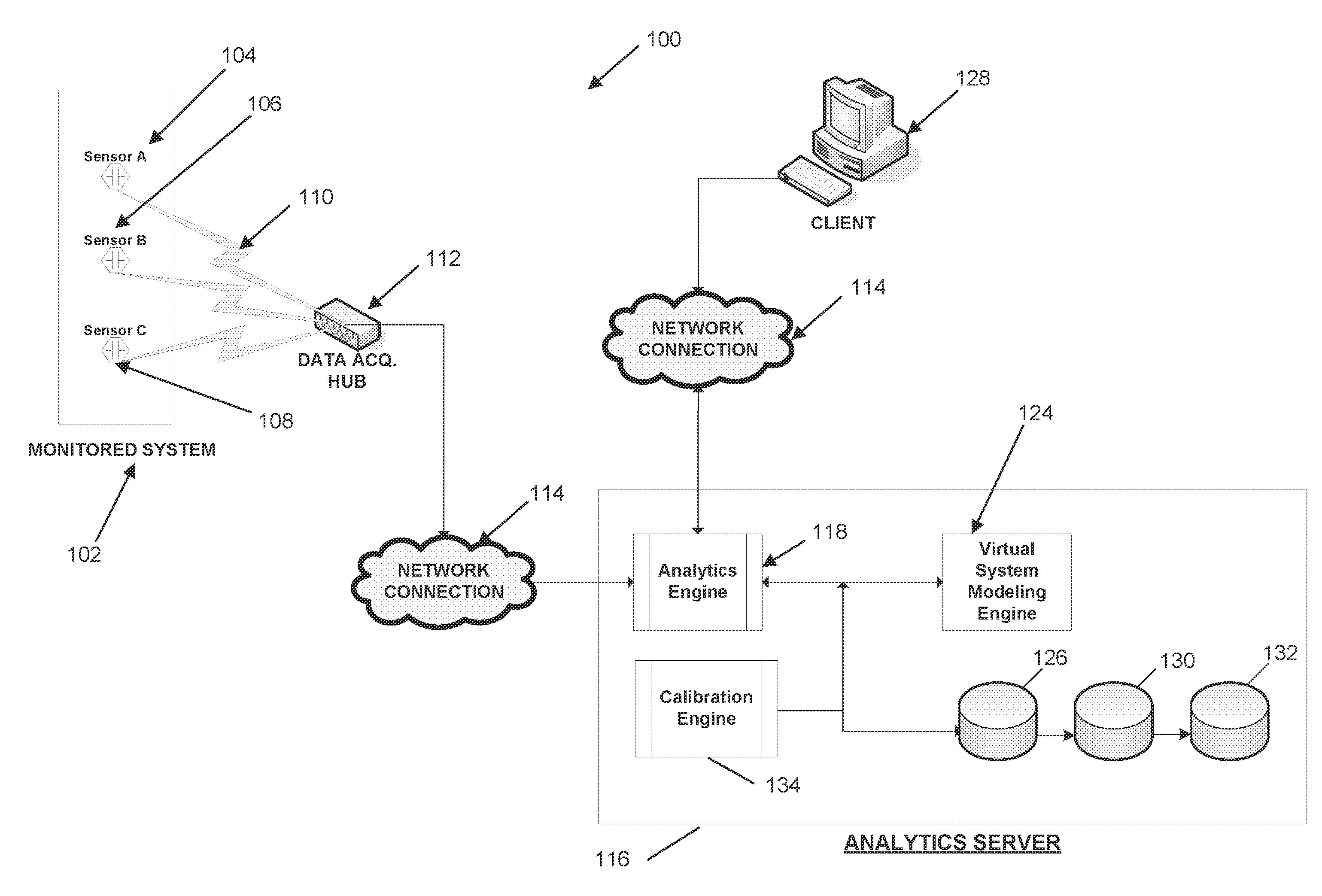
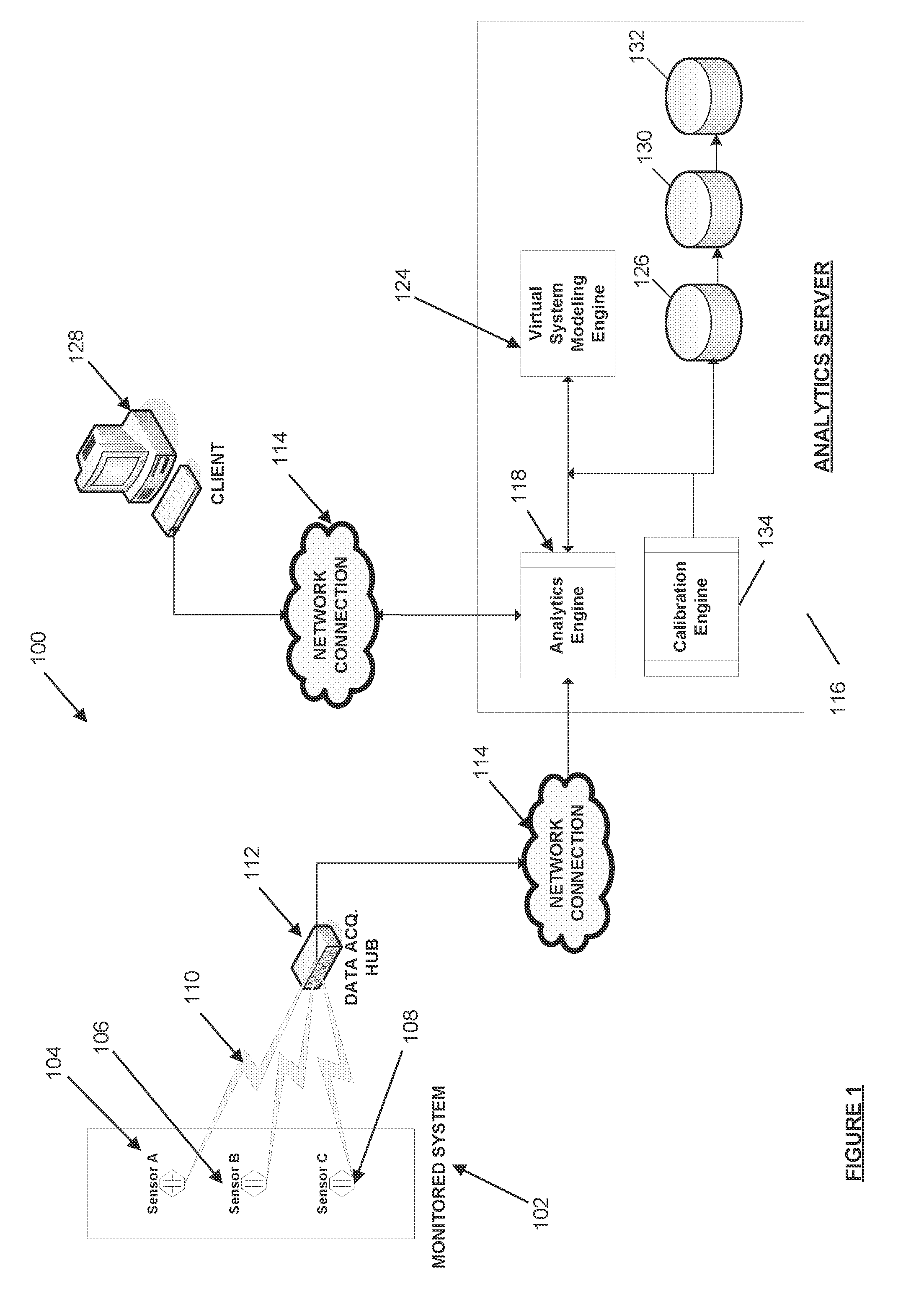
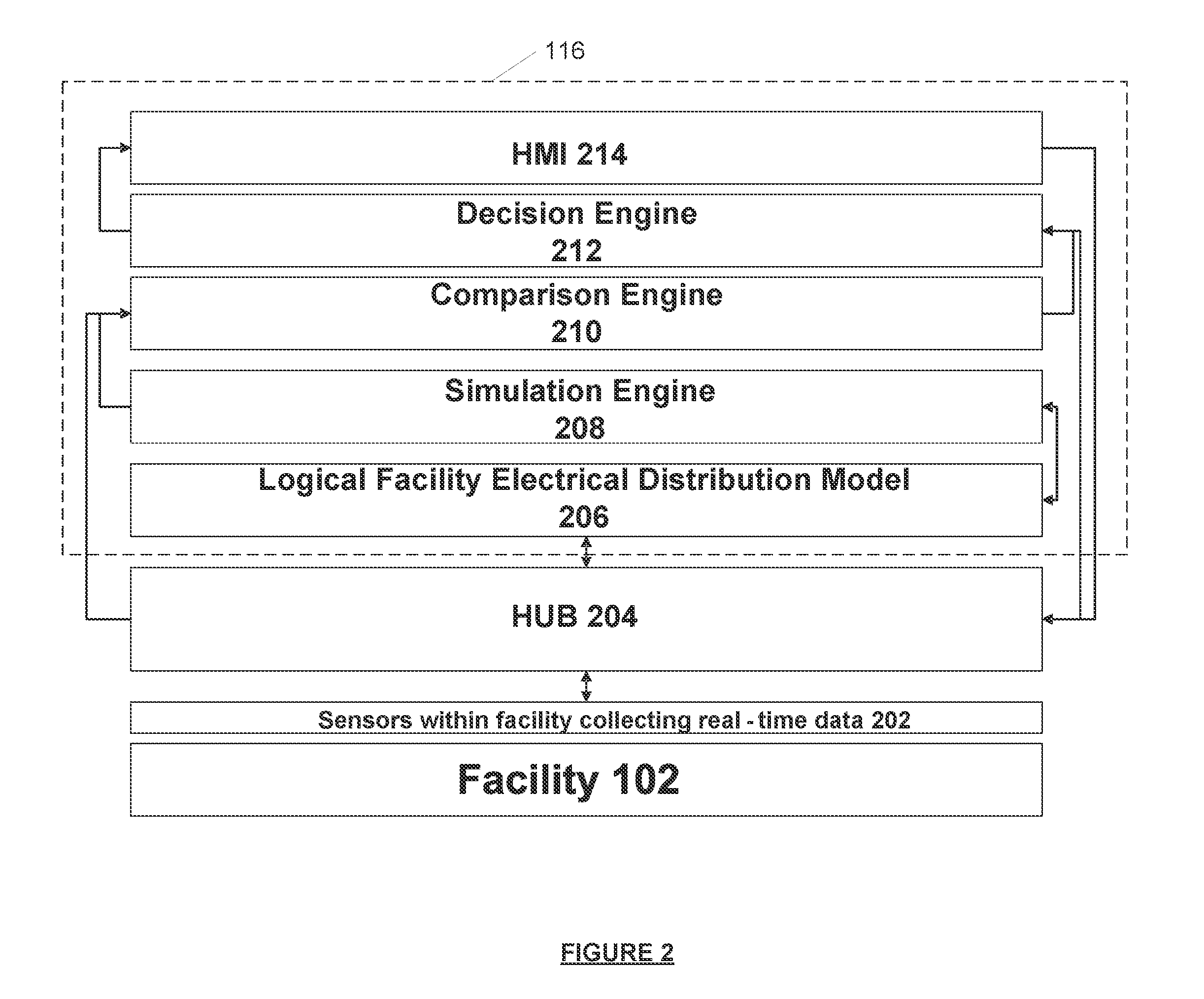
Systems and methods for real-time DC microgrid power analytics for mission-critical power systems
Systems and methods for performing power analytics on a microgrid. In an embodiment, predicted data is generated for the microgrid utilizing a virtual system model of the microgrid, which comprises a virtual representation of a topology of the microgrid. Real-time data is received via a portal from at least one external data source. If the difference between the real-time data and the predicted data exceeds a threshold, a calibration and synchronization operation is initiated to update the virtual system model in real-time. Power analytics may be performed on the virtual system model to generate analytical data, which can be returned via the portal.
Owner:POWER ANALYTICS CORP
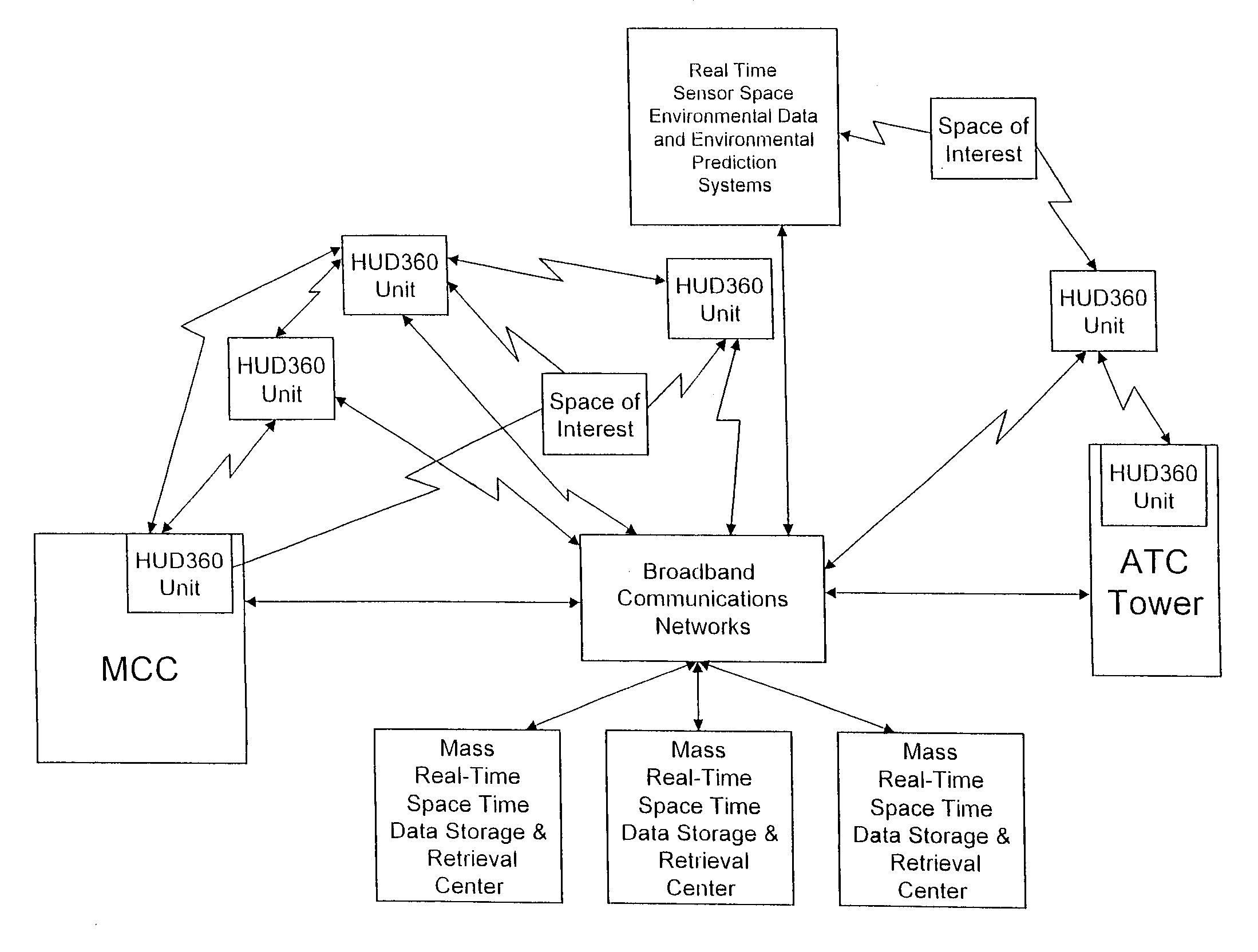
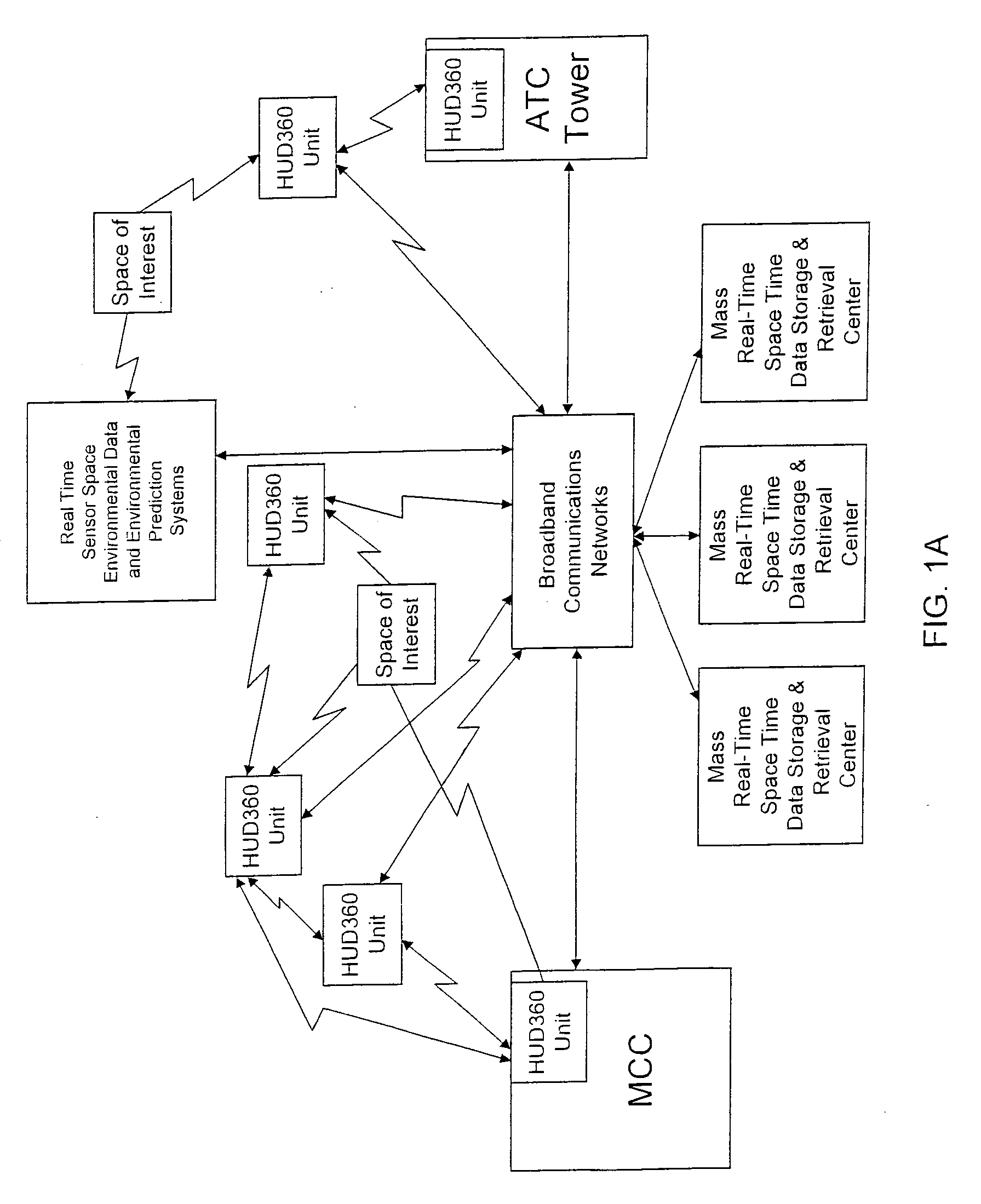
Computer-aided system for 360° heads up display of safety/mission critical data
InactiveUS20140240313A1Input/output for user-computer interactionCathode-ray tube indicatorsTerrainHead-up display
A Heads-Up-Display (“HUD”) system for projecting safety / mission critical data onto a display pair of light weight projection glasses or monocular creating a virtual 360 degree is disclosed. The HUD system includes a see-through display surface, a workstation, application software, and inputs containing the safety / mission critical information (Current User Position, Total Collision Avoidance System—TCAS, Global Positioning System—GPS, Magnetic Resonance Imaging—MRI Images, CAT scan images, Weather data, Military troop data, real-time space type markings etc.). The workstation software processes the incoming safety / mission critical data and converts it into a three-dimensional stereographic space for the user to view. Selecting any of the images may display available information about the selected item or may enhance the image. Predicted position vectors may be displayed as well as three-dimensional terrain.
Owner:REALTIME
System and method for application performance management
ActiveUS20030009507A1General purpose stored program computerHardware monitoringComputer resourcesApplication software
An improved method and system for complex and integrated application performance management which tracks end-to-end computer resource consumption of a first business application workflow in an enterprise system. The first business application workflow may include a plurality of components. The plurality of components may further include one or more component types. A second or subsequent business application workflow may be embedded or linked as a component of the first business application workflow. Resource usage information of the plurality of components (including resource usage information of underlying units of work of the plurality of components) may be correlated to determine cumulative resource usage information for the first business application workflow. The resource usage information may be displayed in a graphical user interface. User input may be received indicating one or more of the following for the first business application workflow: an application name, a natural business unit, and a mission-critical ranking.
Owner:BMC SOFTWARE
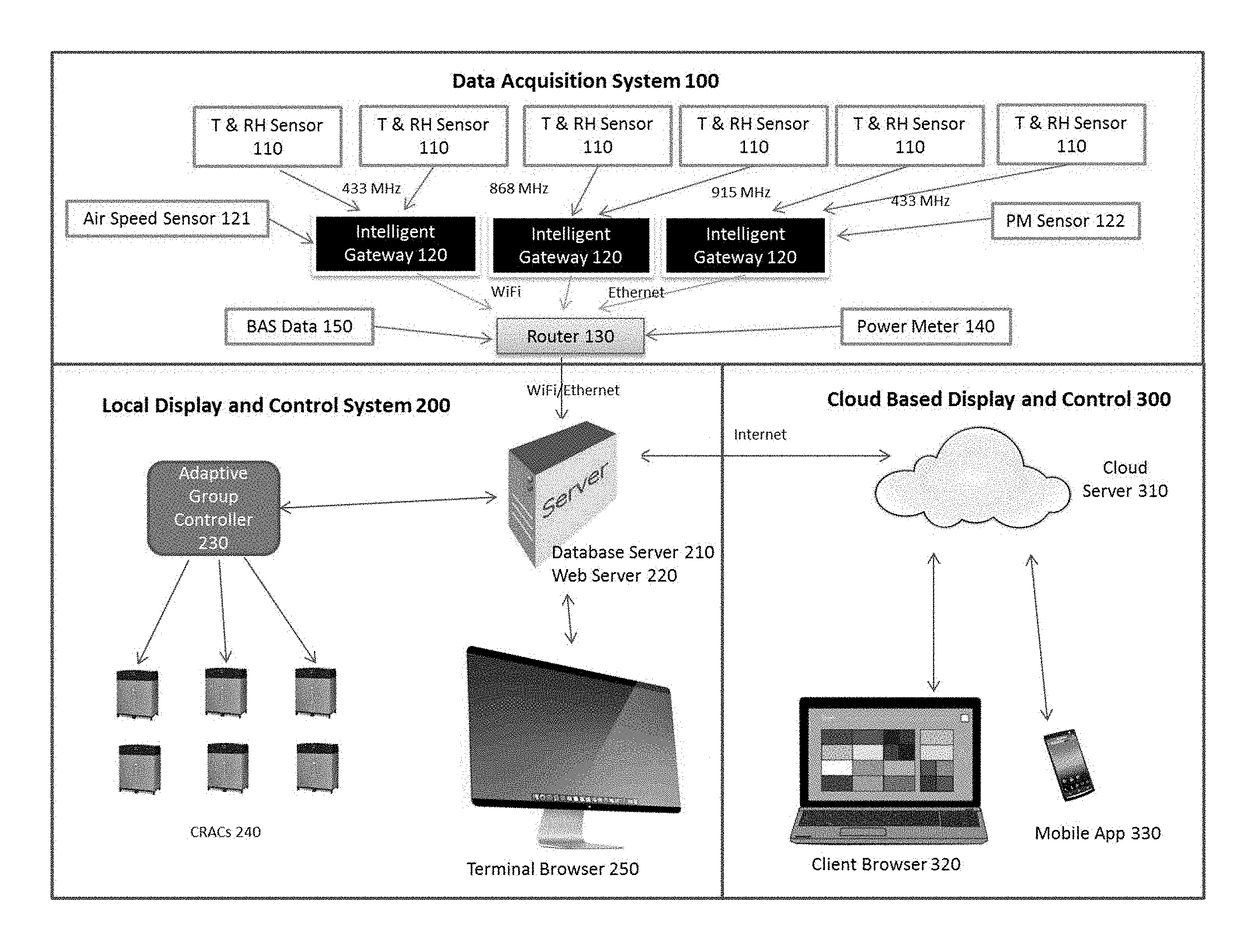
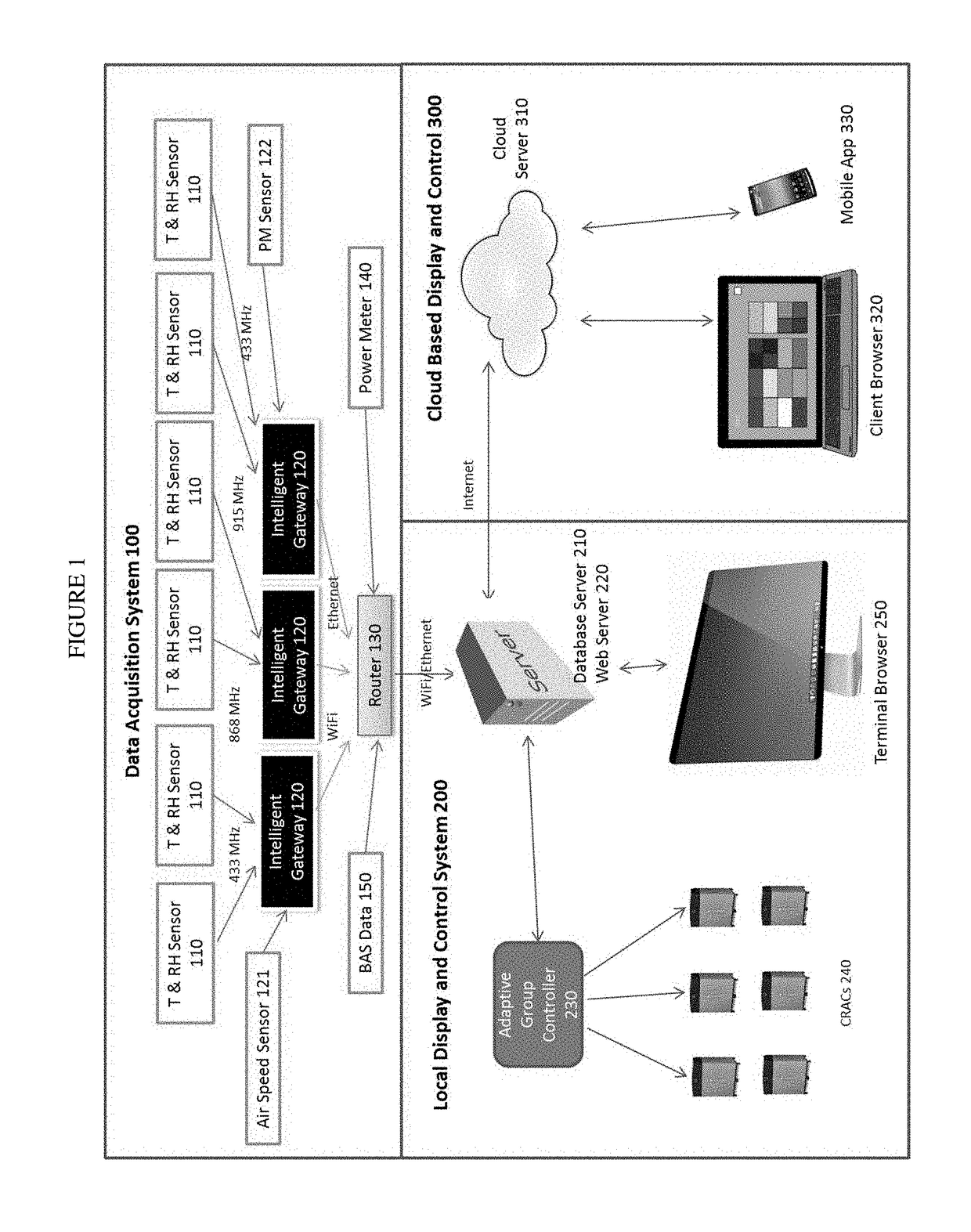
Intelligent mission critical environmental monitoring and energy management system
InactiveUS20170176033A1Process safetyEnergy efficiencyProgramme controlMechanical apparatusDashboardUser management
The present invention is a complete solution for mission critical facilities to create a safe environment and energy efficient CRAC system. The invented system collects mission critical facility volume environmental and energy data in real time, and uses big data analytics to provide adaptive group control to CRACs. The data is visualized in 2D and 3D graphs, dashboard, history curves and reports locally and through the cloud. The present invention also provides user management to allow authorized users to view and control the racks / servers owned or rented by these users. The present invention is comprised of four companion patents: 1) A Battery-powered Wireless Long Life Temperature and Humidity Sensor Module, 2) An Intelligent Multi-channel Wireless Data Acquisition Gateway, 3) Mission critical facility Three Dimension Temperature Contour Generator, and 4) An Adaptive Automatic CRAC Master Control Method.
Owner:ARCHIMEDES CONTROLS CORP
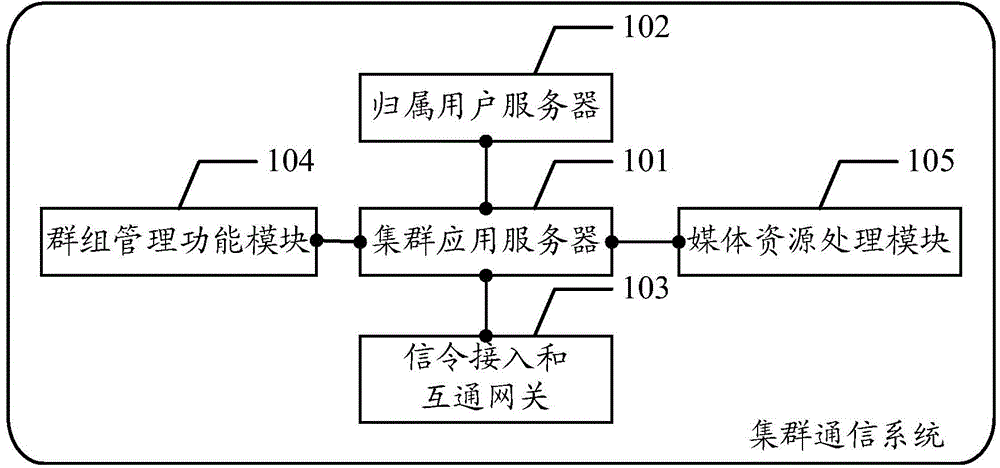
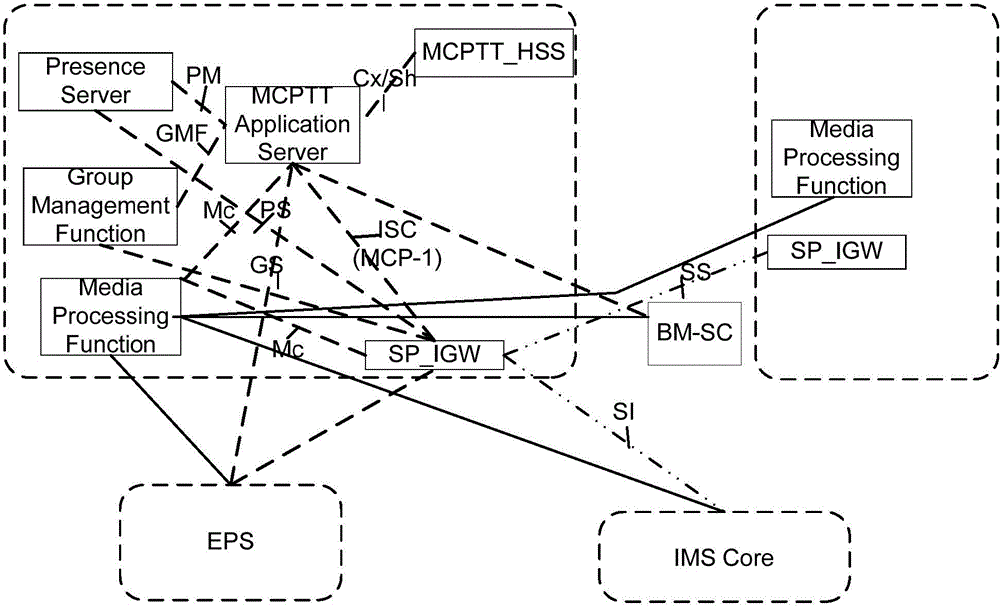
Trunk communication system, server and communication method
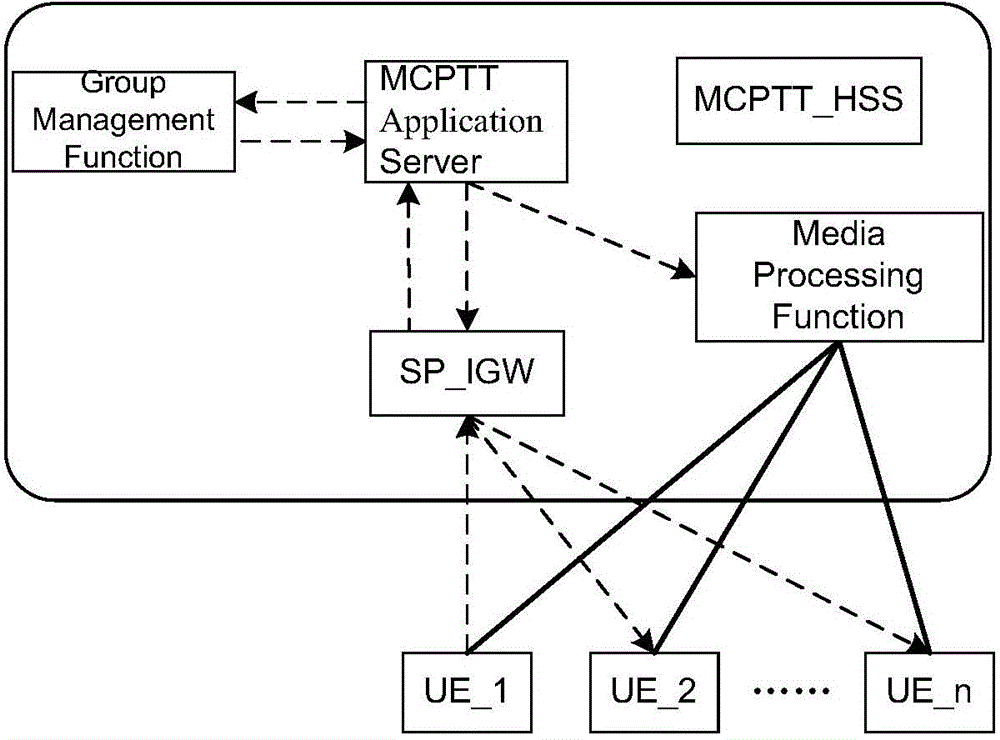
ActiveCN104618349AReduce network element entitiesSimple logical structureConnection managementBroadcast service distributionApplication serverCommunications system
The embodiment of the invention discloses a trunk communication system, a server and a communication method. The trunk communication system in the embodiment of the invention comprises a trunk application server, a home subscriber server, a signaling access and intercommunication gateway, a group management function module and a media resource processing module, wherein the trunk application server is used for receiving a call request of a first subscriber terminal forwarded by the signaling access and intercommunication gateway and transmitting a query message to the trunk management function module after determining that the call request is group call service; the group management function module is used for querying corresponding group information according to the query message; the trunk application server is also used for indicating the media resource processing module to establish carrier for the first subscriber terminal and other group members in the group information after receiving a return message of the group information and initiating a session setup request to the other group members in the group information. According to the embodiment of the invention, logic entity partitioning and system allocation are performed on an MCPTT (Mission Critical Push To Talk) frame to facilitate trunk delay optimization.
Owner:SHANGHAI HUAWEI TECH CO LTD
Method and apparatus for implementing a workgroup server array
InactiveUS6715100B1Unnecessary network traffic can be reducedReduce in quantityError detection/correctionFailoverHigh availability
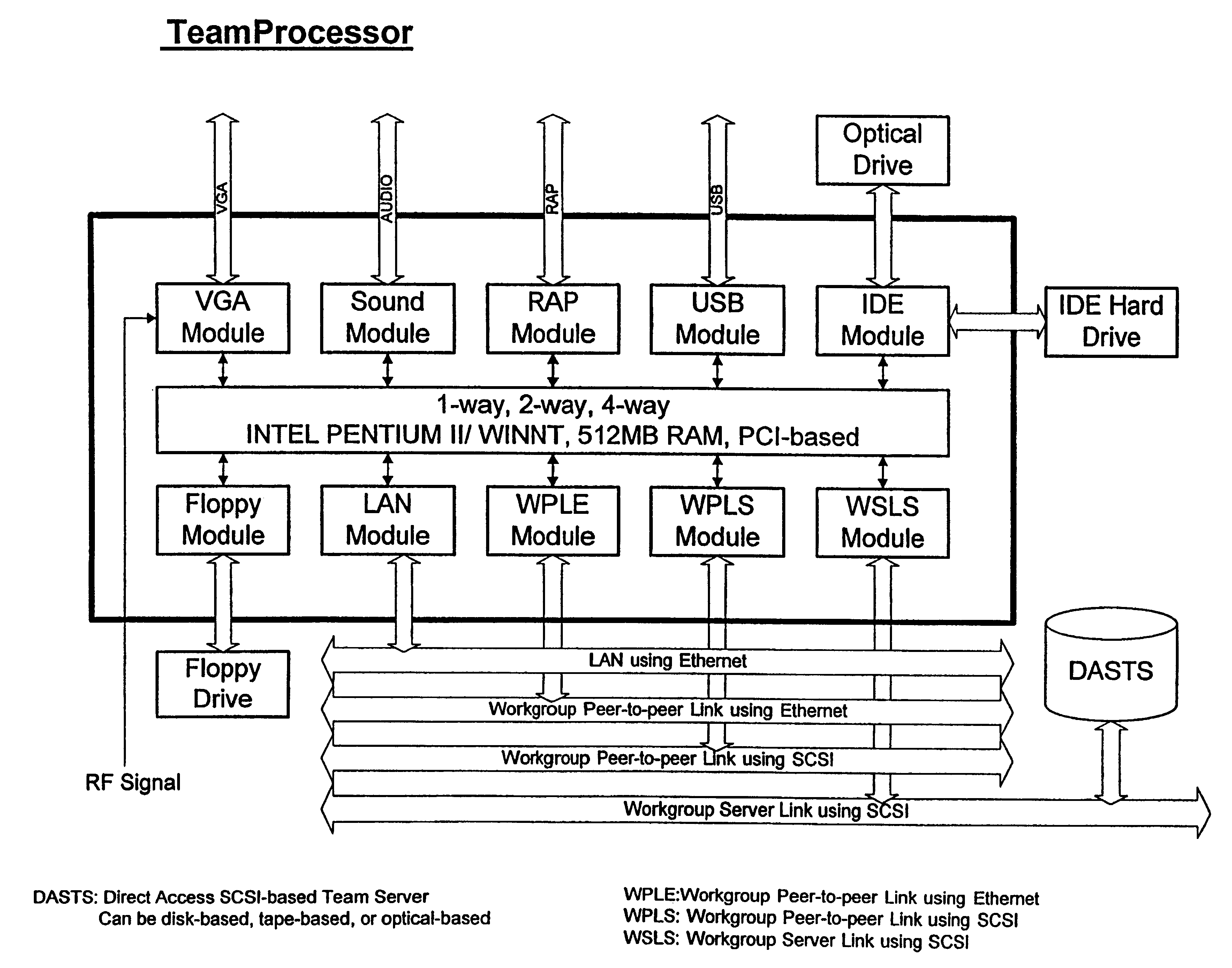
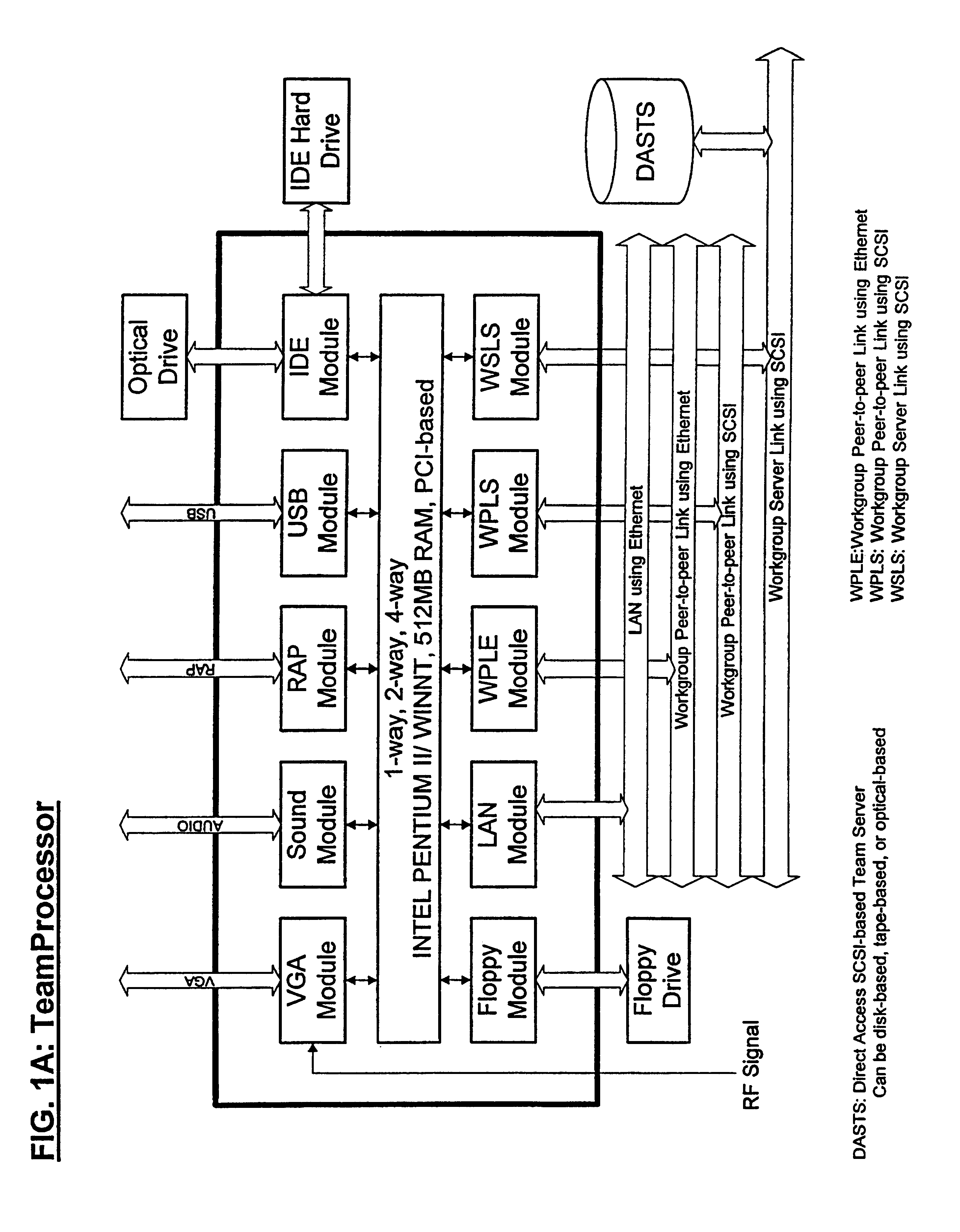
A method and apparatus for implementing a workgroup server array ideal for web-based Intranet, Extranet and Internet applications. The inventive server array comprises a plurality of team / workgroup computers (408) equipped with work-group-based direct-access servers and modular controlling devices (1), creating workgroup-based fault-tolerant and fail-over capabilities, providing console-based monitoring and management support, and accommodating highly available and scalable web-based applications with optimal performance. These workgroup server arrays can be used as the basic building blocks to construct large-scale server clusters, so that more users can be served concurrently. Furthermore, workgroup-server-array-based architecture is created for building various highly available, scalable and mission critical server clusters, which enable distributed computing services for enerris-based Intranet, Extranet and Internet mission critical applications.
Owner:HWANG IVAN CHUNG SHUNG
Decision based system for managing distributed resources and modeling the global optimization problem
InactiveUS20090043809A1Digital data processing detailsForecastingGlobal optimization problemService component
A decision support system called Mounties that is designed for managing applications and resources using rule-based constraints in scalable mission-critical clustering environments. Mounties consists of four active service components: (1) a repository of resource proxy objects for modeling and manipulating the cluster configuration; (2) an event notification mechanism for monitoring and controlling interdependent and distributed resources; (3) a rule evaluation and decision processing mechanism; and (4) a global optimization service for providing decision making capabilities. The focus of this paper is on the design of the first three services that together connect and coordinate the distributed resources with the decision making component.
Owner:IBM CORP
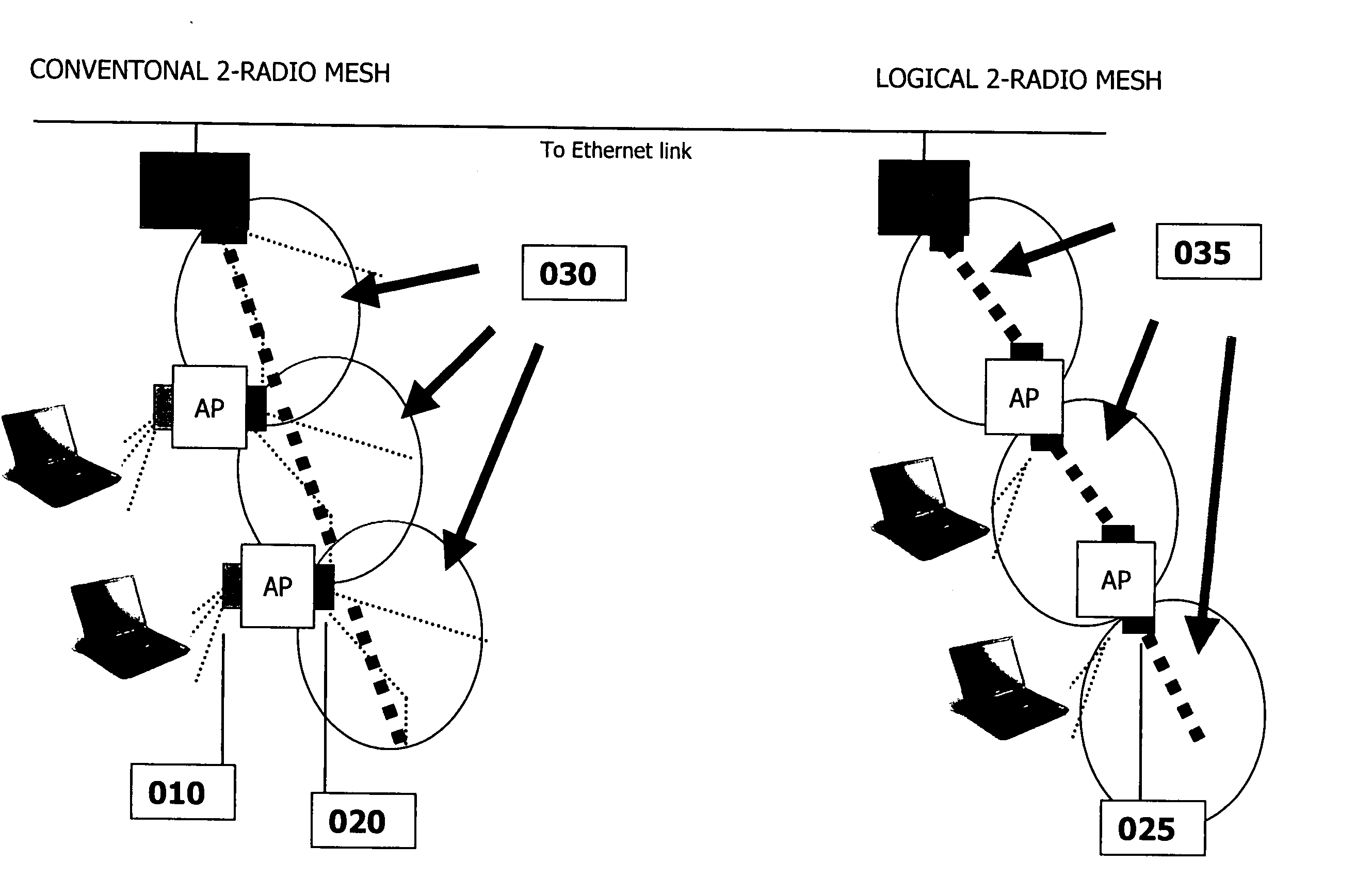
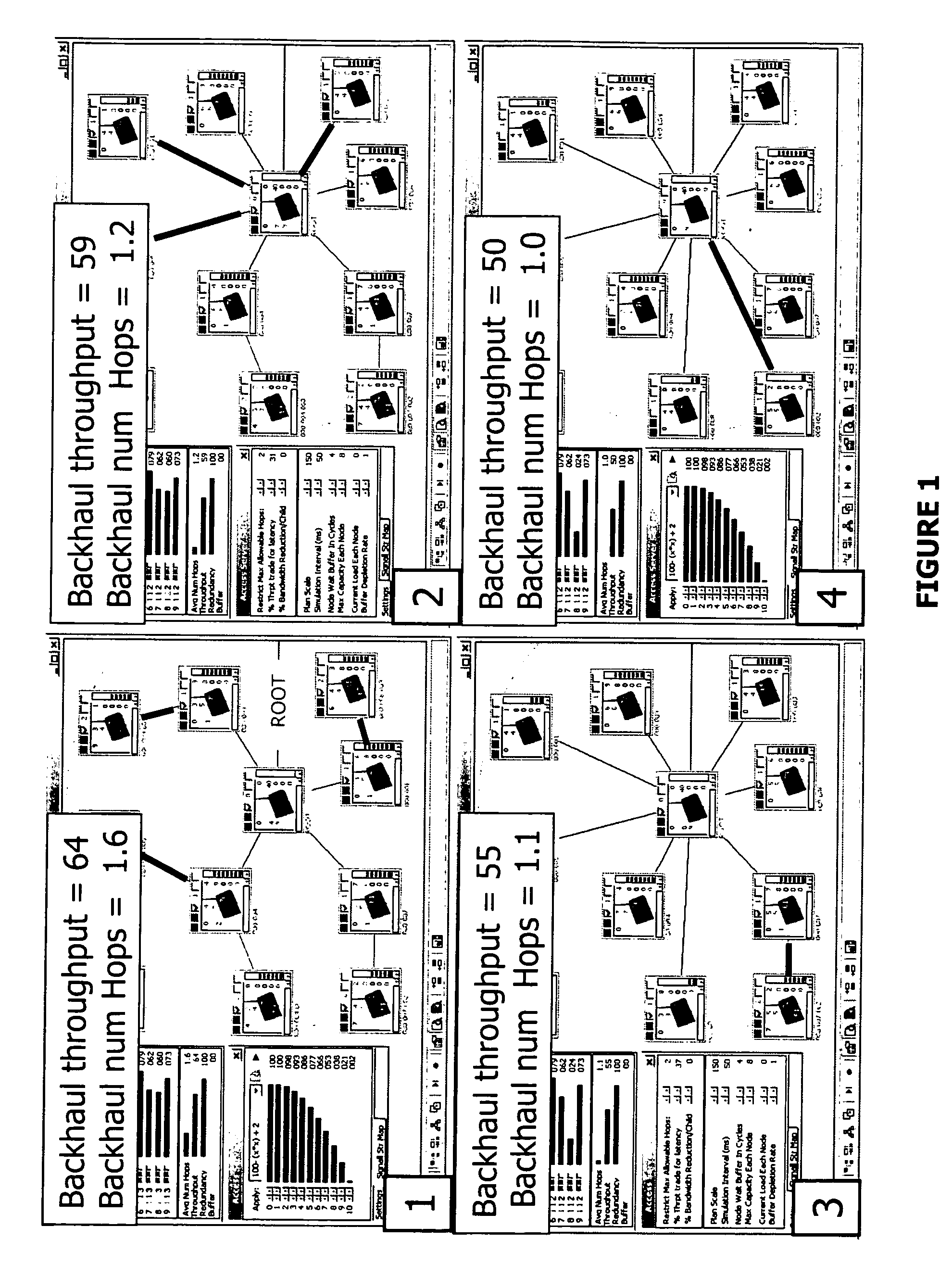
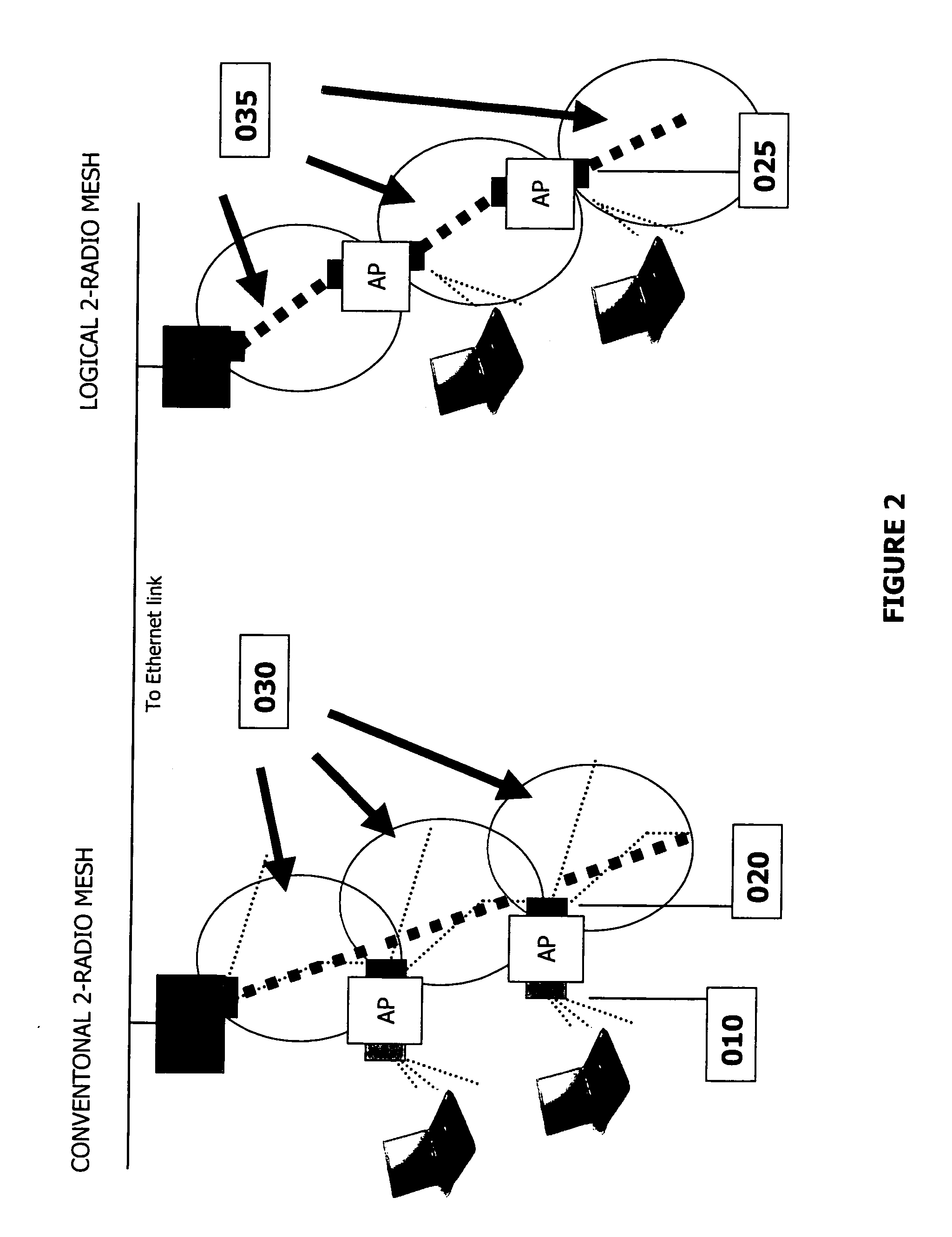
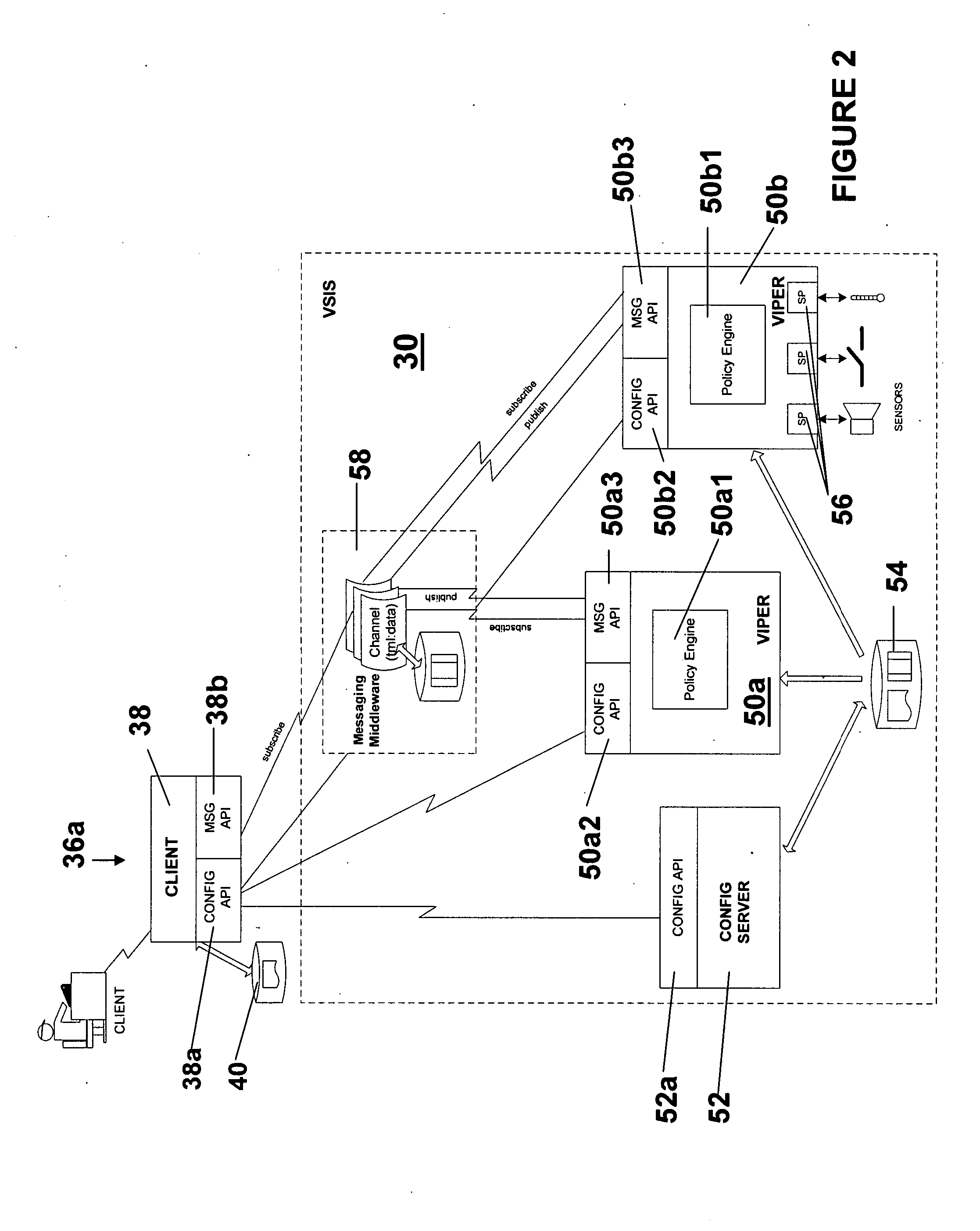
Multiple-radio mission critical wireless mesh networks
InactiveUS20050232179A1Impervious to noiseImprove performanceEmergency connection handlingFrequency-division multiplex detailsWireless mesh networkDistributed computing
An approach using 2 logical radios to achieve high performance in multihop mesh networks is introduced. The advantages of frequency re-use, reduced channel interference over 1 radio approaches is discussed. An approach is developed to extend the logical 2-radio system to (physical) 3-radio and 4-radio systems are explained as extensions of the logical 2-radio methodology. The ability need to support both multiple radio systems and 1-radio ad hoc mesh systems in one framework is described in the context of emergency response systems. Some unique benefits of the logical 2-Radio concept related to other mesh architectures are highlighted.
Owner:DYNAMIC MESH NETWORKS
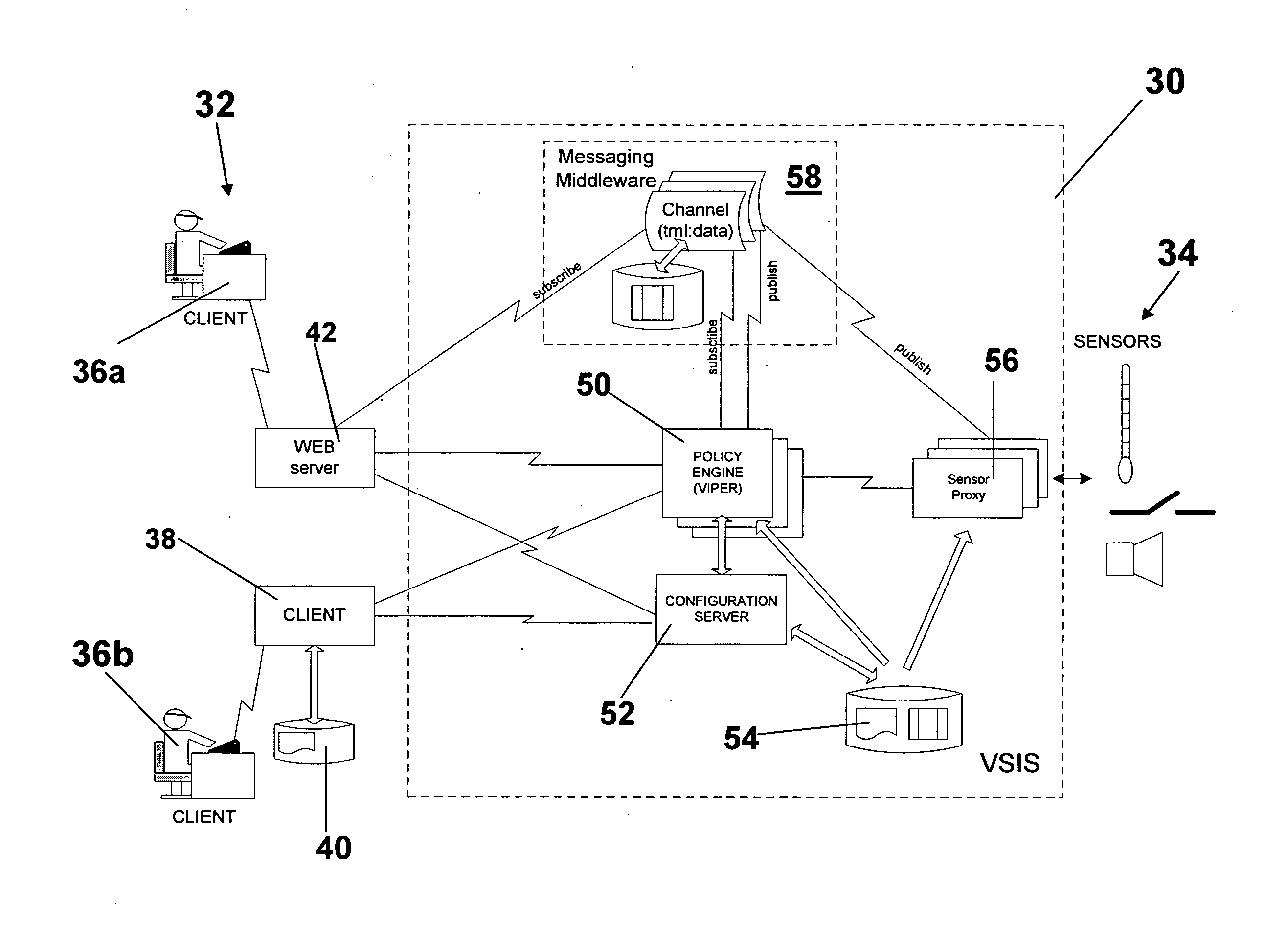
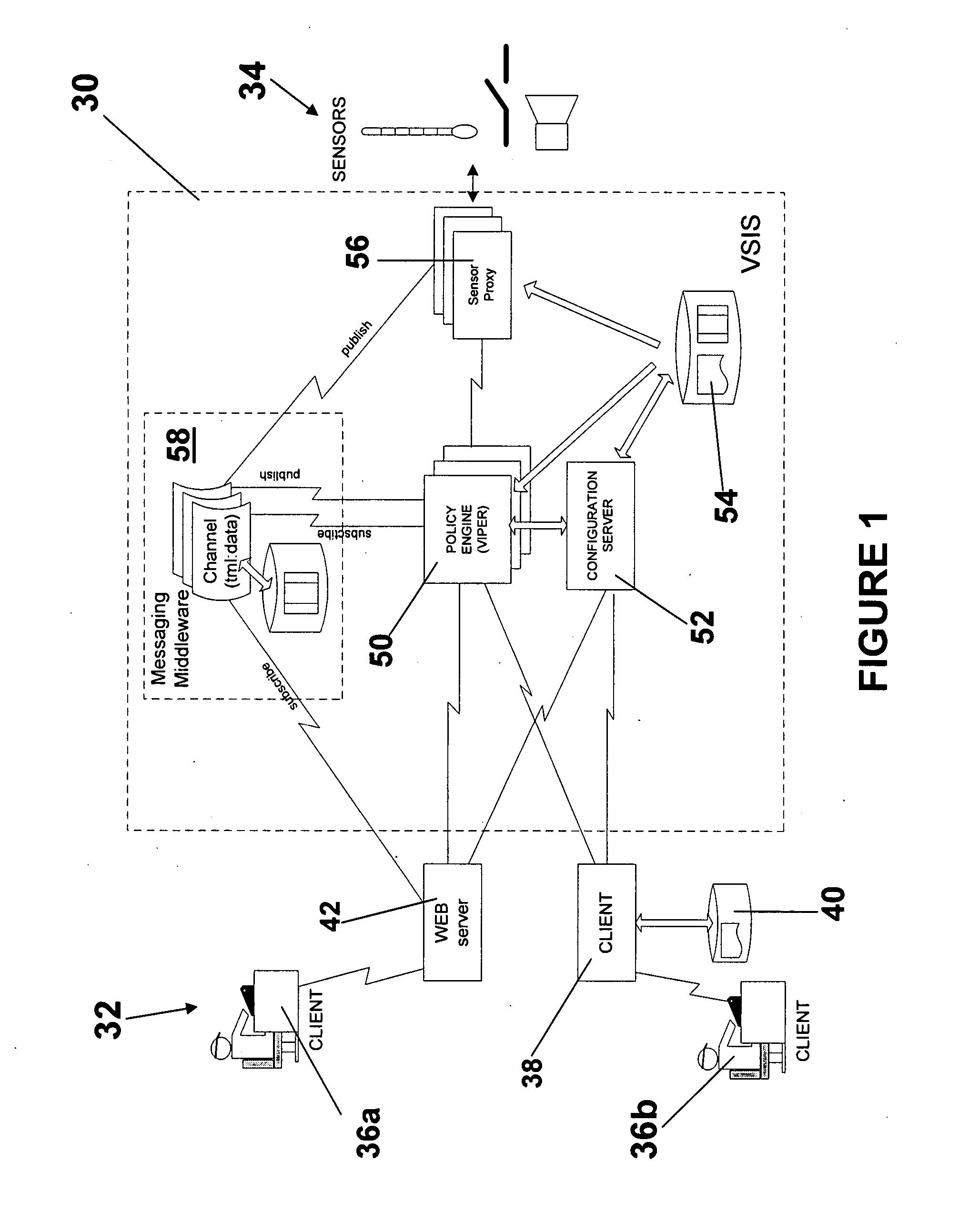
Software enabled video and sensor interoperability system and method
ActiveUS20080052757A1Loss of performanceLoss of functional utilityDigital computer detailsMeasurement arrangements for variableOperational systemEngineering
A novel method and software system design are presented for interchanging sensors from different vendors in a plug and play manner to drive mission critical applications within a sensor based architecture, policy based framework, event-based architecture. This technique is applicable to sensors directly attached to a computer, or sensors attached to a network, or sensors attached to a controller node which is attached to a network or directly attached to a computer.
Owner:VIALOGY
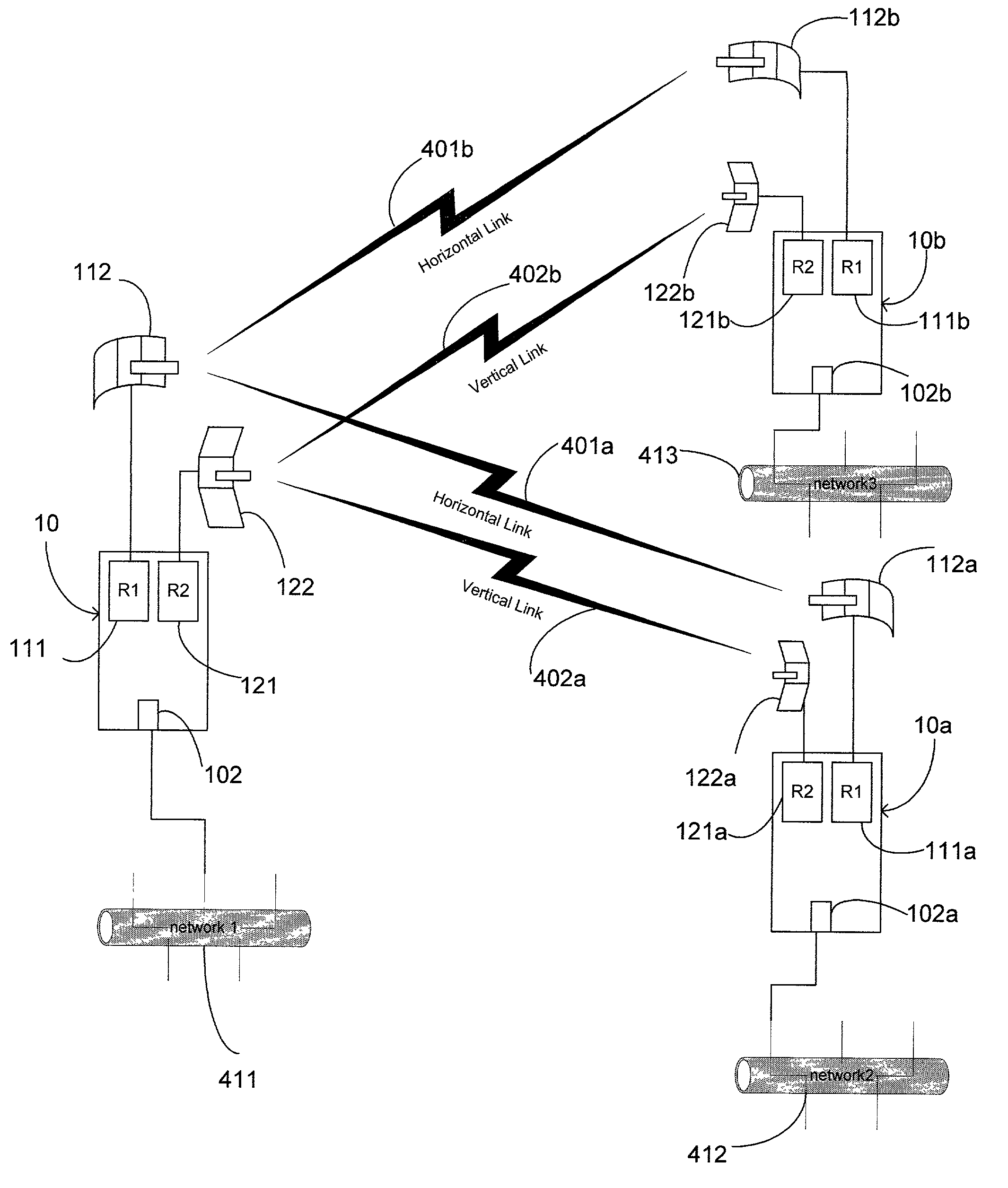
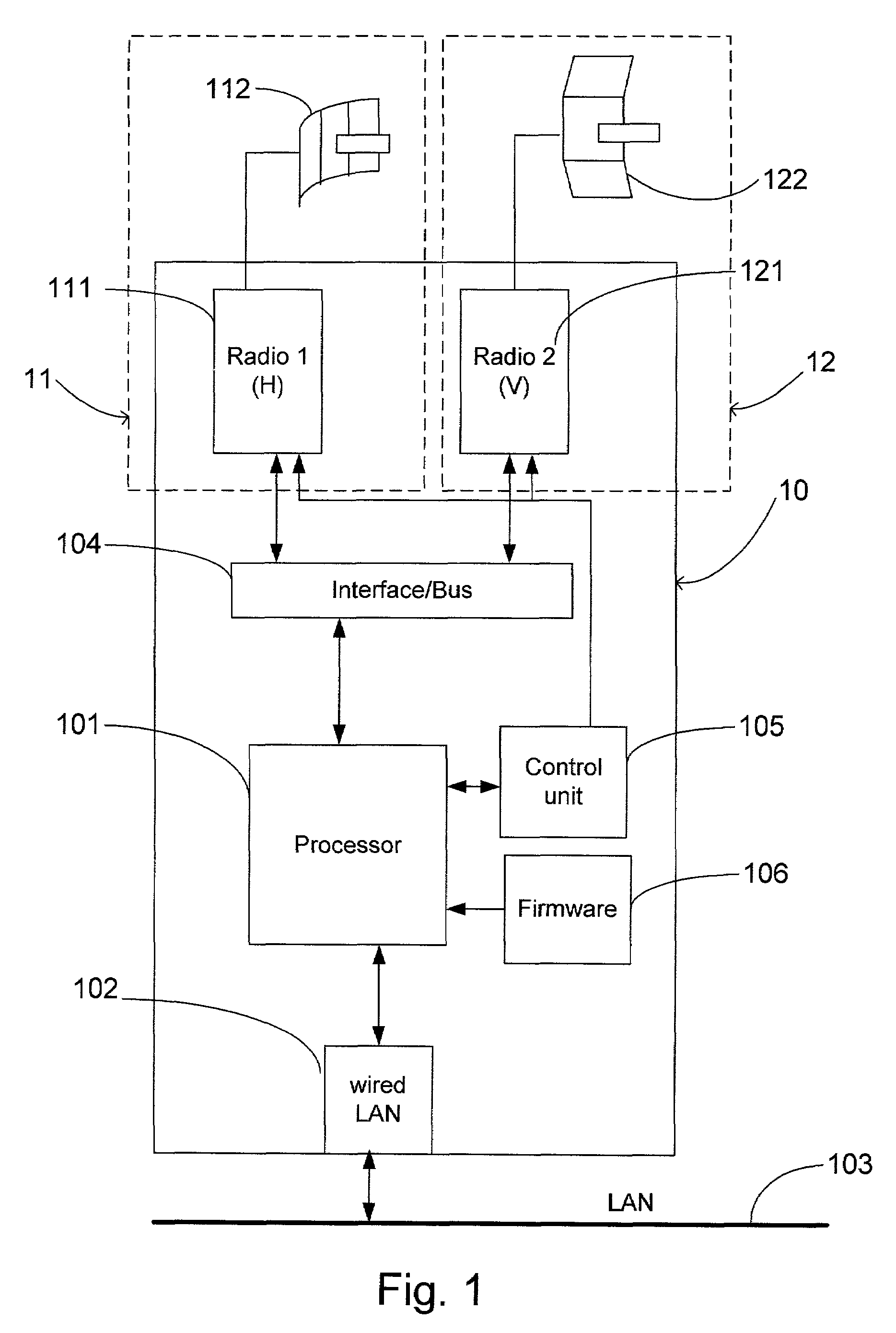
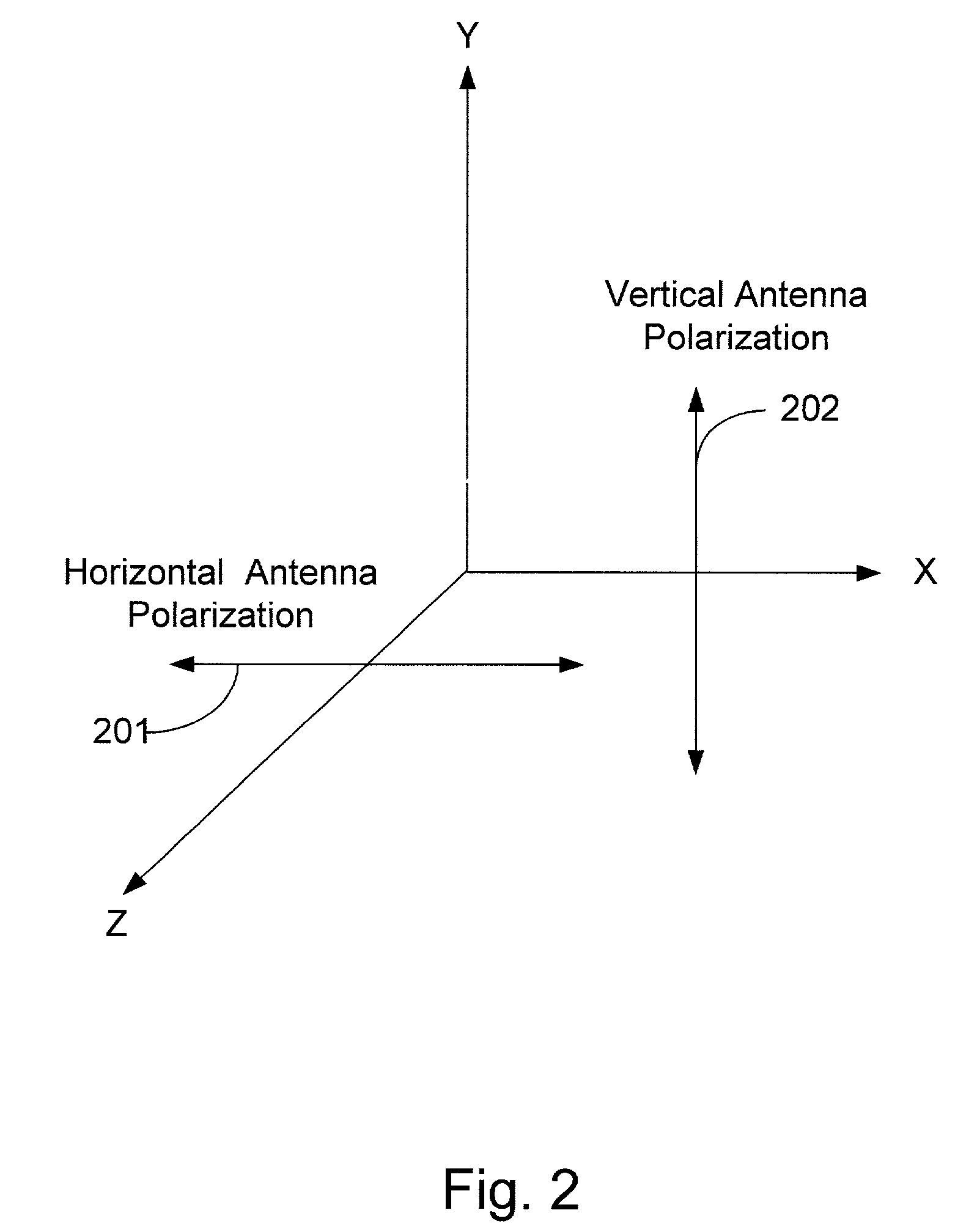
Dual channel redundant fixed wireless network link, and method therefore
InactiveUS7167723B2Improve reliabilityLow costNetwork traffic/resource managementData switching by path configurationTelecommunications linkNetwork link
A dual channel redundant wireless network link formed by the Redundant Fixed Wireless Network Link device 10 of the present invention provides a very high reliable network element for mission critical wireless network application. Redundant Fixed Wireless Link device (10) with two wireless networking radio channel (11, 12) turned on simultaneously, and running networking service feature is working as Service Equipment (SE). Both wireless networking radio channel (11, 12) of the SE have the same directional wireless network coverage area. The two wireless networking radio channels (11, 12) are separated by cross polarization of antenna at same radio frequency, or different radio frequency characteristics. One Redundant Fixed Wireless Link device (10) with one of its two wireless networking radio channel (11, 12) turned on and communicating with said SE, and loaded with networking client feature is acting as Client Equipment (CE). The link quality monitor feature of the CE is monitoring the communication link between the SE and CE. When the current link quality is low or the link is down, the CE automatically switches on the alternate wireless networking radio channel (11, 12) to maintain the network communication between the SE and CE. One SE may communicate with plurality of CE in the same wireless network coverage area.
Owner:ZHANG FRLIN ZHIGANG
Business method and processing system
InactiveUS20050049937A1Efficient and effectiveMaximize achieved pricingMarketingSpecial data processing applicationsTarget engagementHandling system
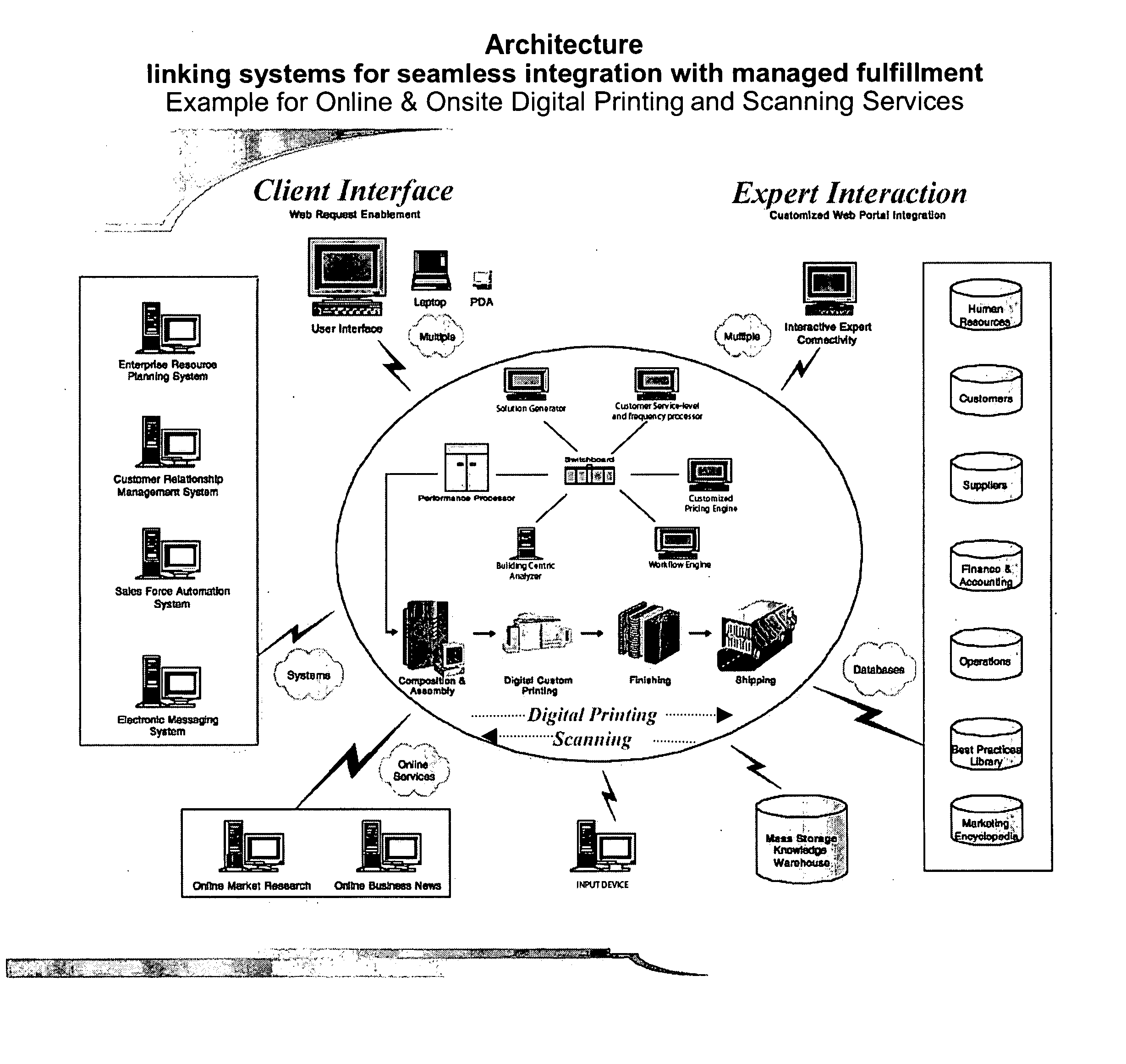
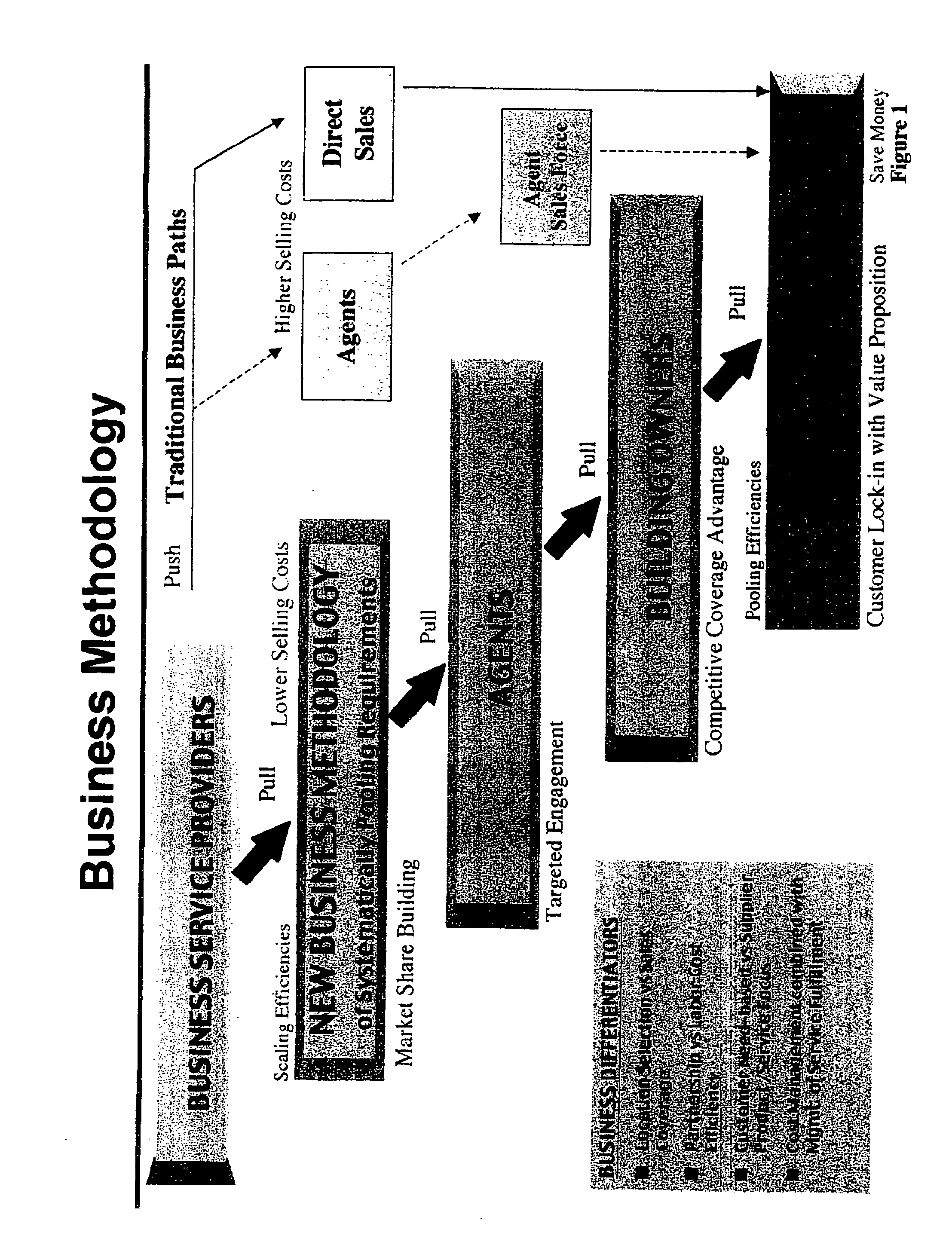
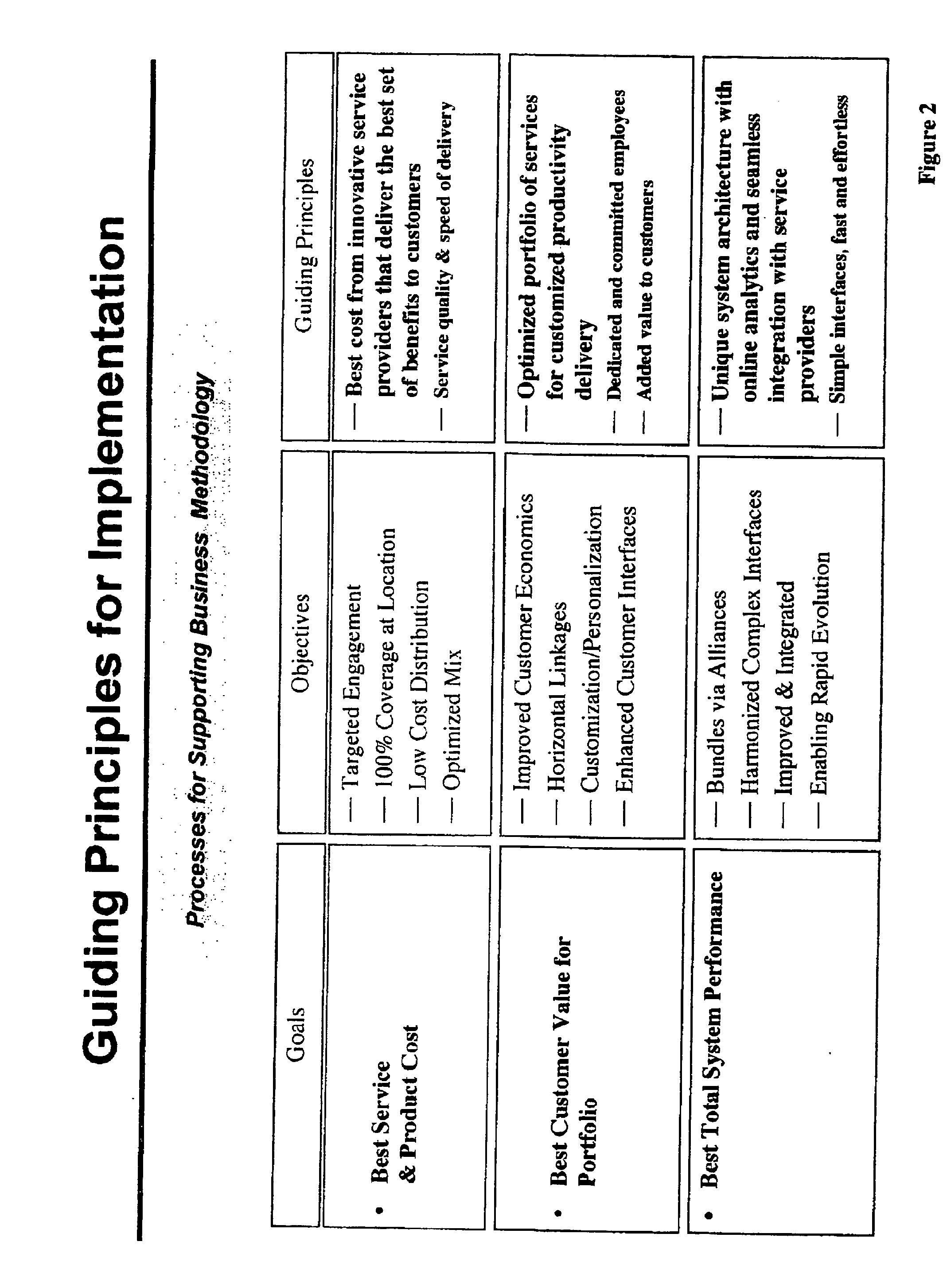
A business method and a system that focuses on offering, coordinating, fulfilling and delivering an array of knowledge and productivity services that corporate customers require in today's context, the knowledge / business service combinations representing of mission-critical services with intellectual knowledge embodied, the fulfillment of which is done for a cluster of clients located in large commercial office buildings, government buildings or universities. The method of the invention provides for pooling of the requirements of various end users for scale-advantaged efficiencies in the processing and service delivery, and sharing such economies of scale generated with the building owners / property managers, who provide the venue from which to operate and enable such pooling to take place, and also with the tenant occupants / users, thus creating a market pull. The fulfillment of specific services is done by outsourcing to individual service providers who are established experts in their respective fields and who have virtual access to new business opportunities according to the method of the invention. The invention includes a market niche identification process and a networked processing system that delivers multiple-custom services to multiple-tenant users in multiple buildings / locations simultaneously, either directly and indirectly, and either with or without human intervention, and providing economies of scale and scope to all users, thus making it possible to offer such services at market-exchange pricing without the need for binding agreements. The processing system tracks utilization in a portfolio management style, by type of service as well as by user, for total spend-rates as well as by accrued savings, and for benchmarking purposes. The business method includes agents to facilitate targeted engagement of multi-tenant buildings from a location, size, networking, occupancy and potential point of view to build a network of multiple-buildings for even greater economies of scale and scope. The invention also includes applications related to wireless communications and choiceboards
Owner:SANDERS AARON
Application-based enhancement to inter-user priority services for public safety market
InactiveUS20090144740A1Maximum capacity/effectivenessGood serviceEmergency connection handlingNetwork traffic/resource managementAccess networkApplication software
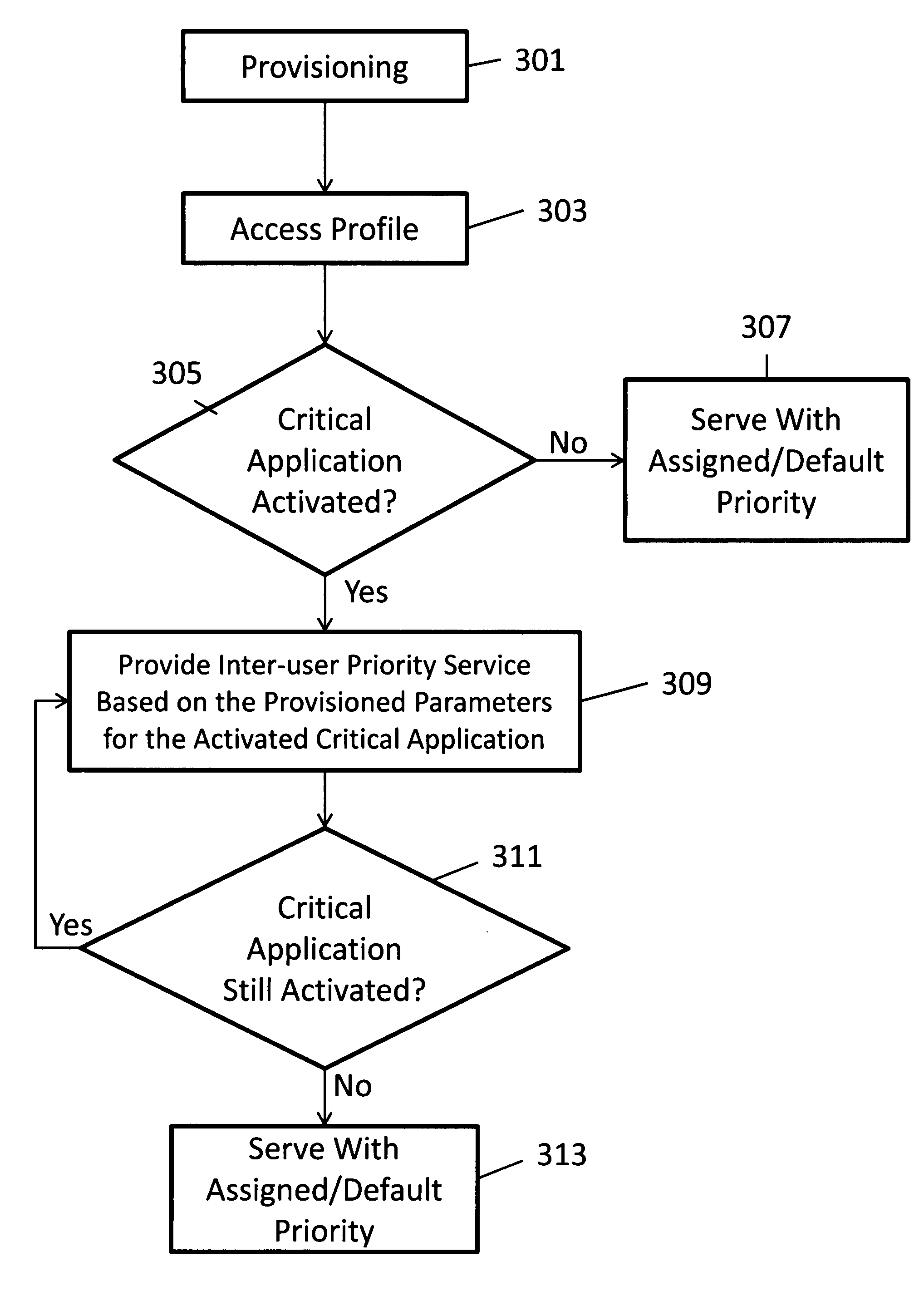
A system and method for application based enhancement to the traditional per-user based inter-user priority services is provided. This method includes provisioning a user's profile, not only with an assigned inter-user priority, but also with zero, one or more specified and provisioned applications that are considered as critical applications which require special preferential treatment by the access network. The method continues with accessing the inter-user priority profile associated for sessions established for the user. The system then recognizes that a session may have been assigned to at least one provisioned critical application. The system may then provide inter-user priority services operative to provide the specified preferential treatment for at least the critical applications associated with the session when the critical application(s) are activated. In this form, the critical applications are better served including protection again congestion and availability of resources whenever they are needed. This system may grant preferential treatment on a session and / or application basis so that there will be no impact on other general applications when no critical applications are activated. This is especially useful for public safety implementation where protecting the mission-critical communication is a fundamental requirement.
Owner:LUCENT TECH INC
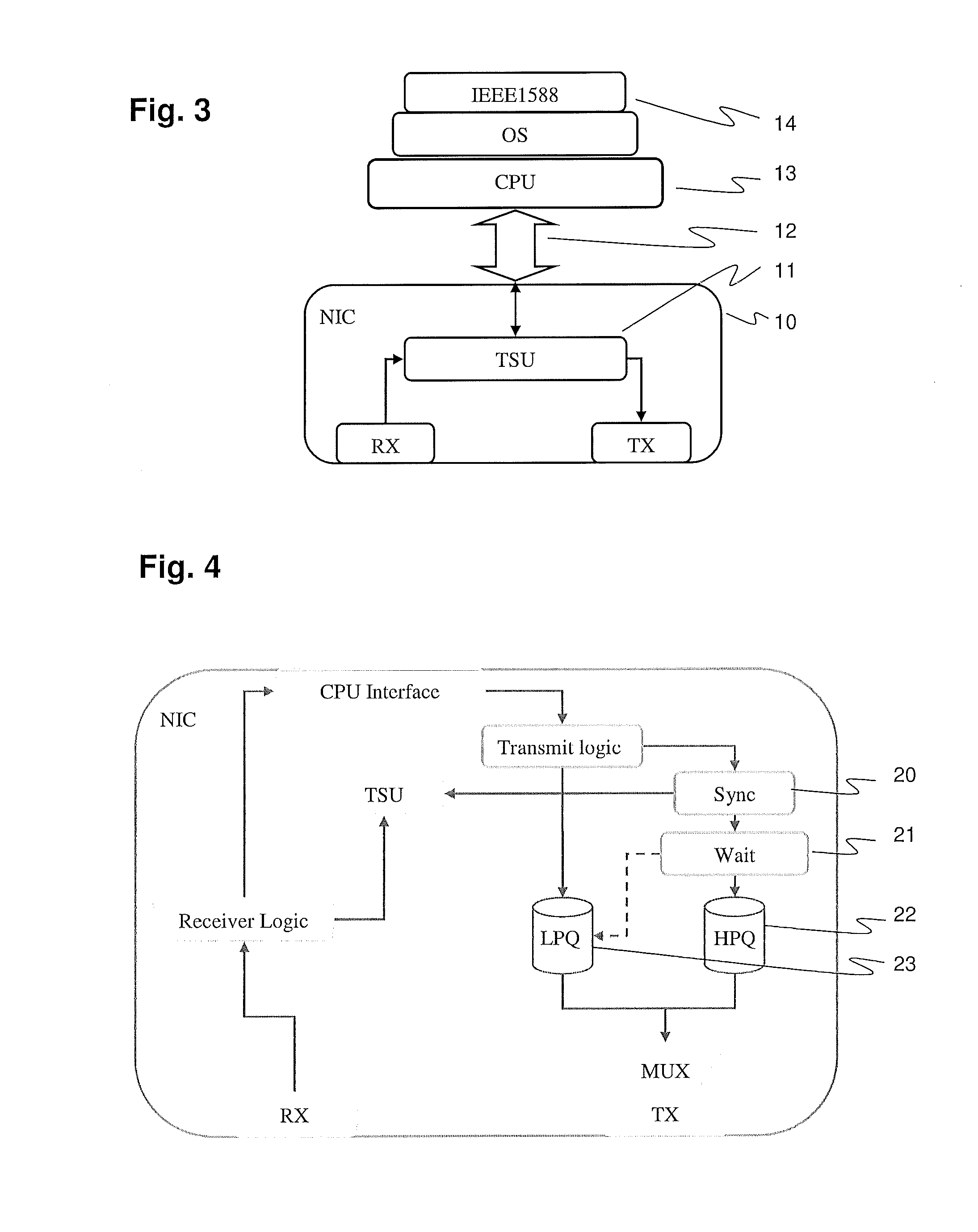
Secure clock synchronization
ActiveUS20120163521A1Synchronisation information channelsTime-division multiplexSlave clockComputer science
The present disclosure provides a secure one-step IEEE 1588 clock using either a symmetric or asymmetric protection scheme. Clocks of mission-critical or highly-available devices in industrial automation systems connected to a communication network are synchronized by sending, by a master clock, a synchronization message, e.g., a single message of the one-step-clock type according to IEEE 1588, including a time stamp, and by receiving and evaluating, by a slave clock, the synchronization message. A synchronization component or module of the master clock prepares, or composes, prior to a projected send time, a synchronization message including a time stamp of the projected send time, and secures the synchronization message in advance of the projected send time. Securing the synchronization message occurs by suitable cryptographic means allowing for authentication of the time stamp at a receiving slave clock. At the projected send time, the secured synchronization message is transmitted.
Owner:HITACHI ENERGY SWITZERLAND AG
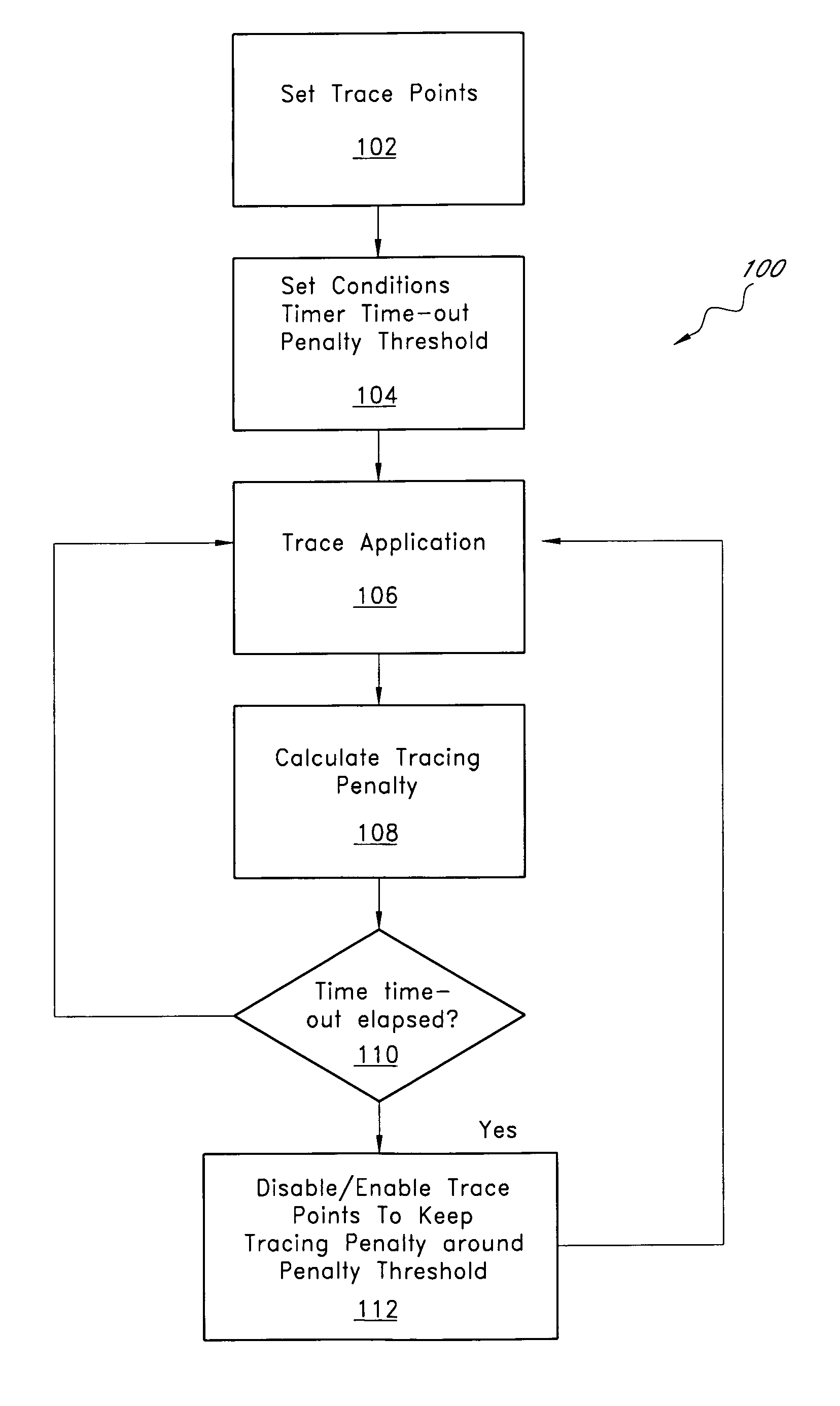
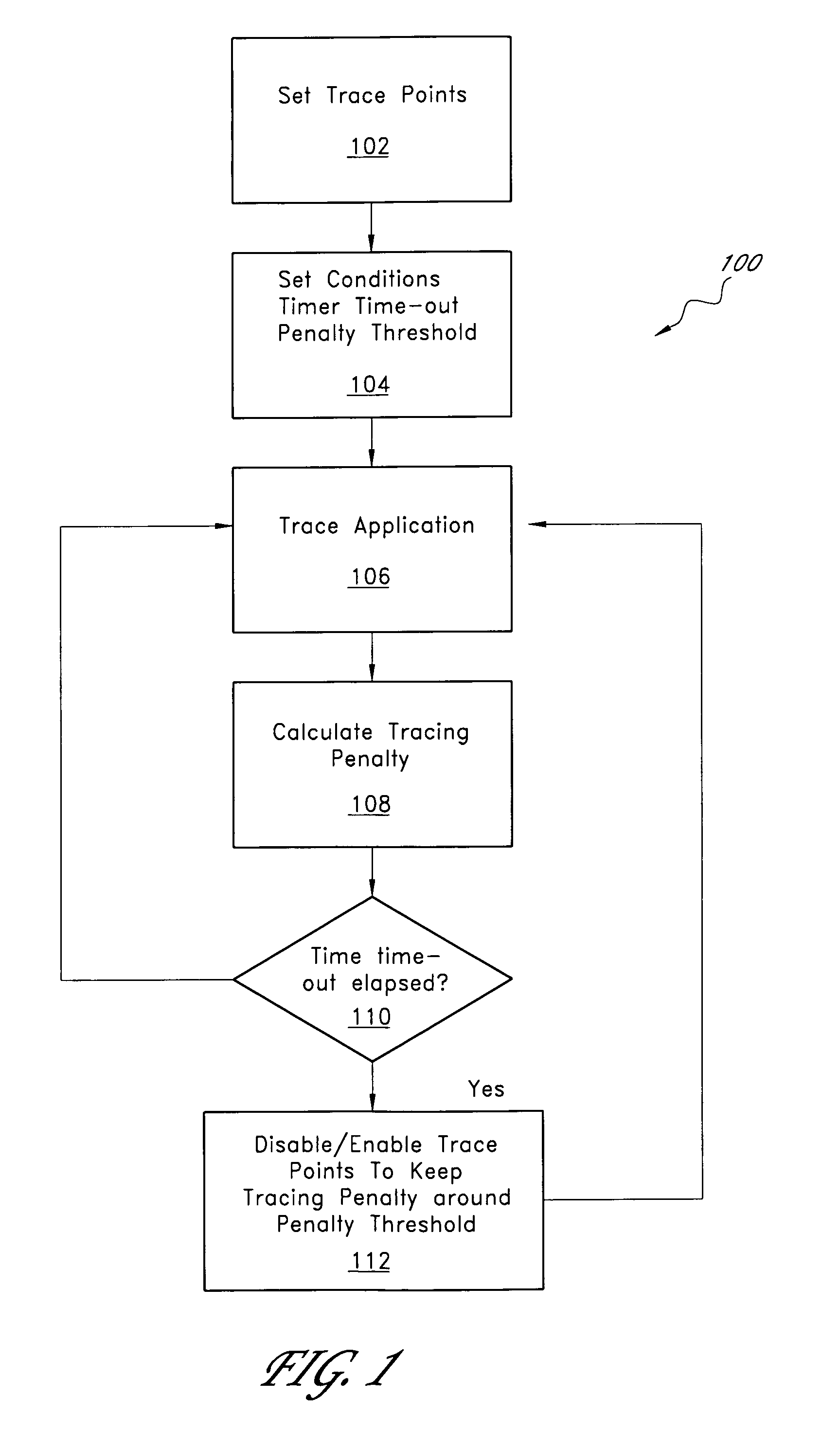
System and method for automated tuning of program execution tracing
ActiveUS7827539B1Simple processMaintain balanceError detection/correctionSpecific program execution arrangementsTime criticalParallel computing
A tracing system that provides automated tuning of execution tracing by adjusting the collection of trace data is described. In one embodiment, the user sets an initial tracing profile for a tracing program. In addition, the user sets an upper limit for the tracing performance penalty. The auto-tuning system monitors the performance penalty induced by tracing and, when the performance impact is excessive, removes trace points that are causing the most impact on performance. Auto tuning is especially useful for performing software recording in mission-critical and / or time-critical applications, such as servers, real-time applications, etc. The system typically adjusts relatively quickly such that most users do not feel the influence of the tracer.
Owner:BMC SOFTWARE ISRAEL LTD
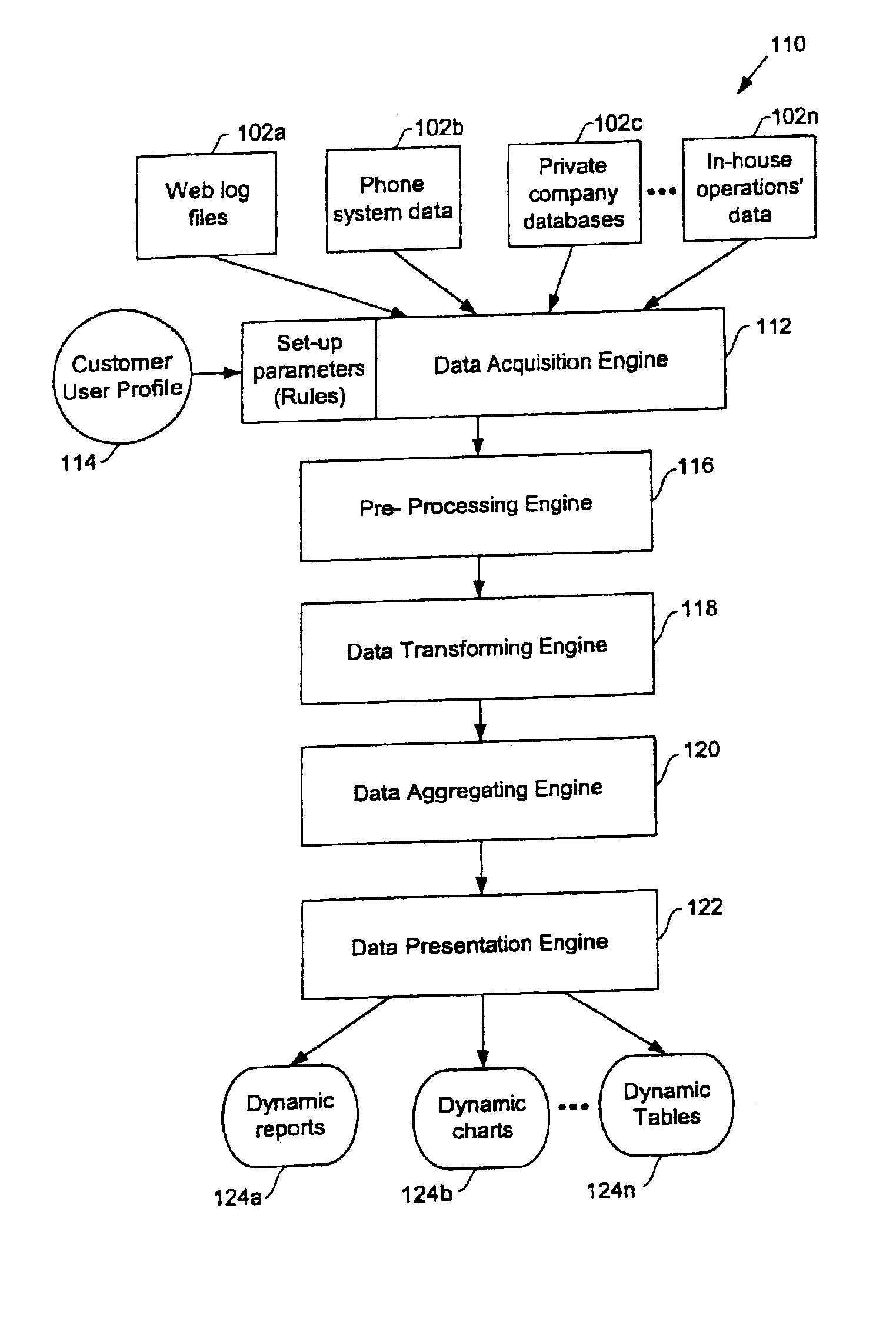
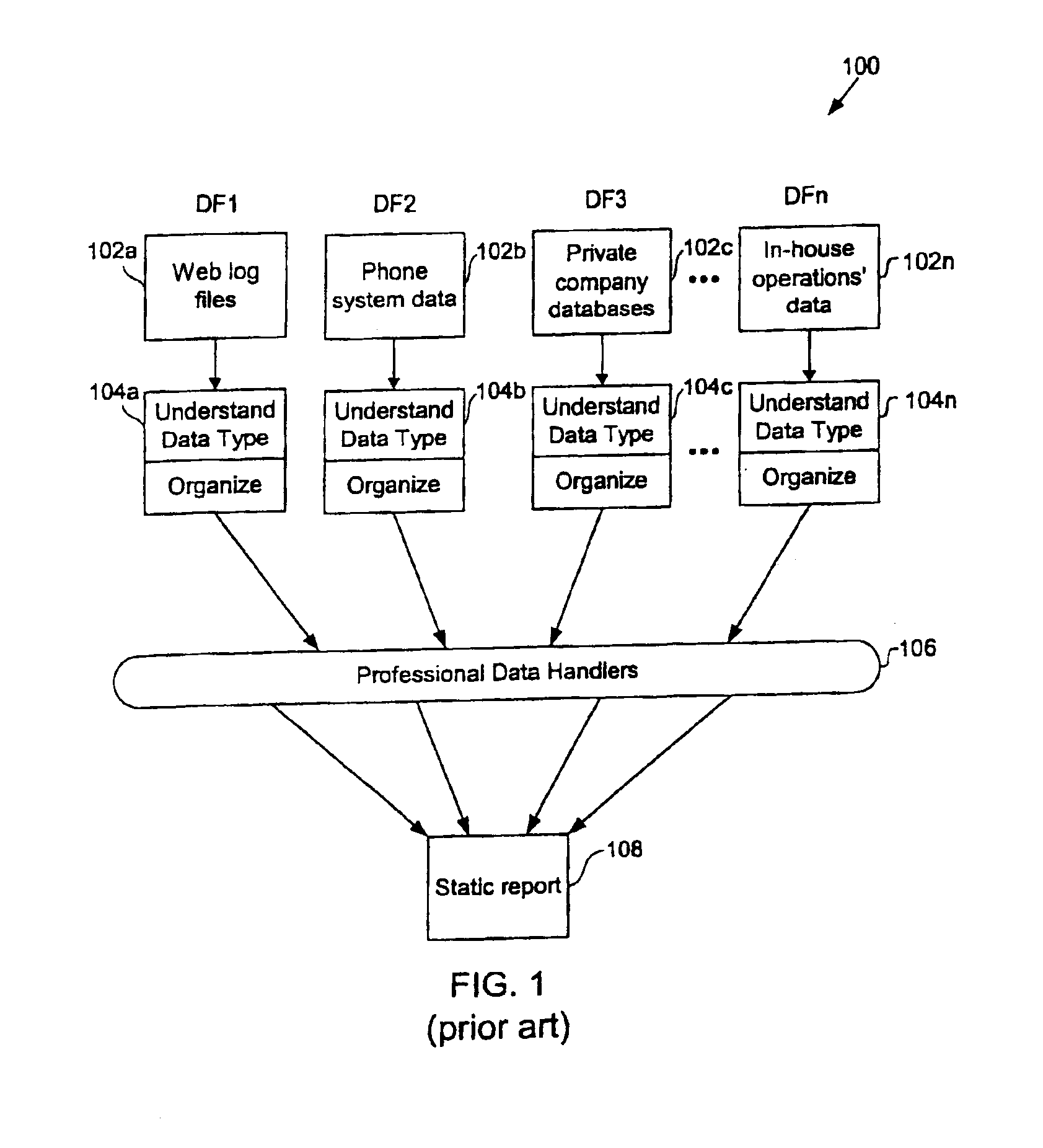
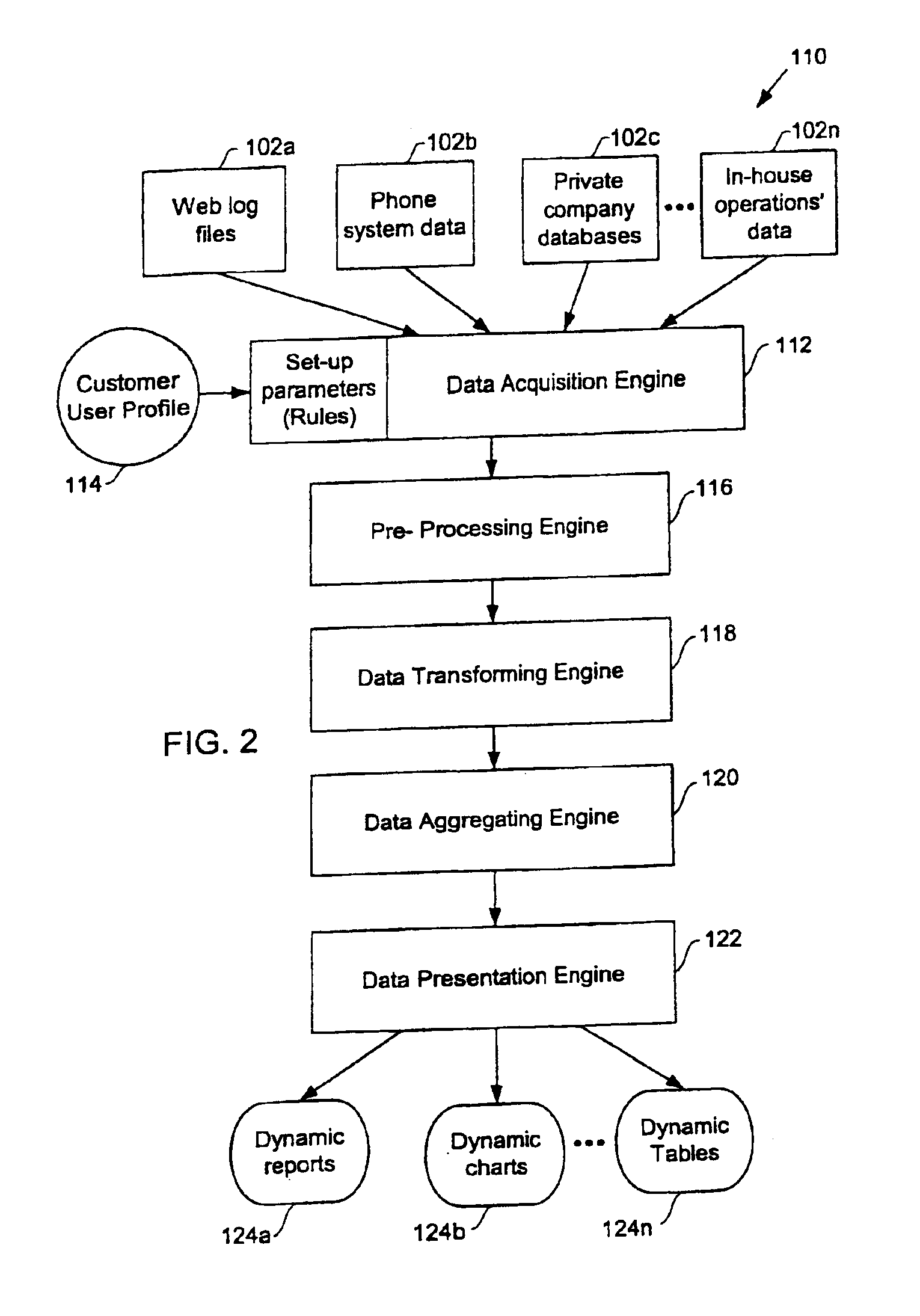
Methods for dynamically accessing, processing, and presenting data acquired from disparate data sources
InactiveUS6959306B2Minimize timeEliminate needDigital data information retrievalError detection/correctionProgram instructionData source
Methods for acquiring and transforming data for business analysis, and computer readable media having program instructions for enabling the same are provided. One exemplary method identifies a set of data sources to be accessed for a user, loads the raw data from each of the accessed set of data sources to raw data type specific locations then verifies the integrity of the acquired raw data. Next the acquired raw data of each of the raw data type specific locations is transformed to a uniform data type and then stored as processed data into processed data type specific locations. Some notable advantages of the discussed methods of acquiring and presenting data for business analysis purposes is the ability to efficiently extract, organize and present the data as requested by a customer over a world wide computer network. Examples of such efficiency include the ability to convert data acquired from disparate sources to a uniform format, thus allowing centralization of the data and eliminating the need to continually access various data sources to provide requested reports. The customer can thus be provided with dynamic reports in real-time, thereby allowing for time sensitive and mission critical business decisions to be made with current data.
Owner:NIELSEN COMPANY US LLC THE A DELAWARE LIMITED LIABILITY
Systems and methods for real-time DC microgrid power analytics for mission-critical power systems
InactiveUS20120191440A1Single network parallel feeding arrangementsAnalogue computers for nuclear physicsAnalysis dataReal-time data
Systems and methods for performing power analytics on a microgrid. In an embodiment, predicted data is generated for the microgrid utilizing a virtual system model of the microgrid, which comprises a virtual representation of a topology of the microgrid. Real-time data is received via a portal from at least one external data source. If the difference between the real-time data and the predicted data exceeds a threshold, a calibration and synchronization operation is initiated to update the virtual system model in real-time. Power analytics may be performed on the virtual system model to generate analytical data, which can be returned via the portal.
Owner:POWER ANALYTICS CORP
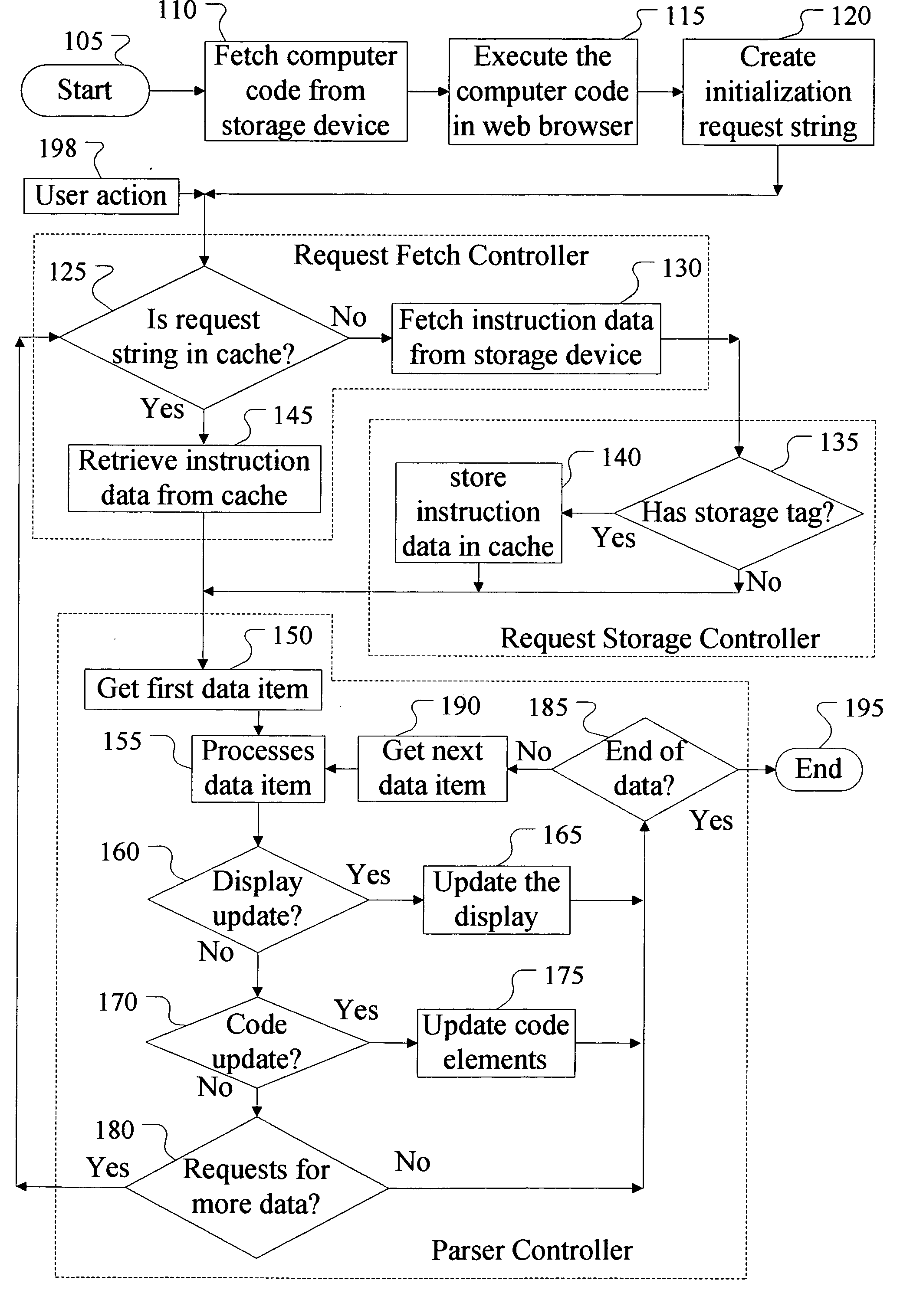
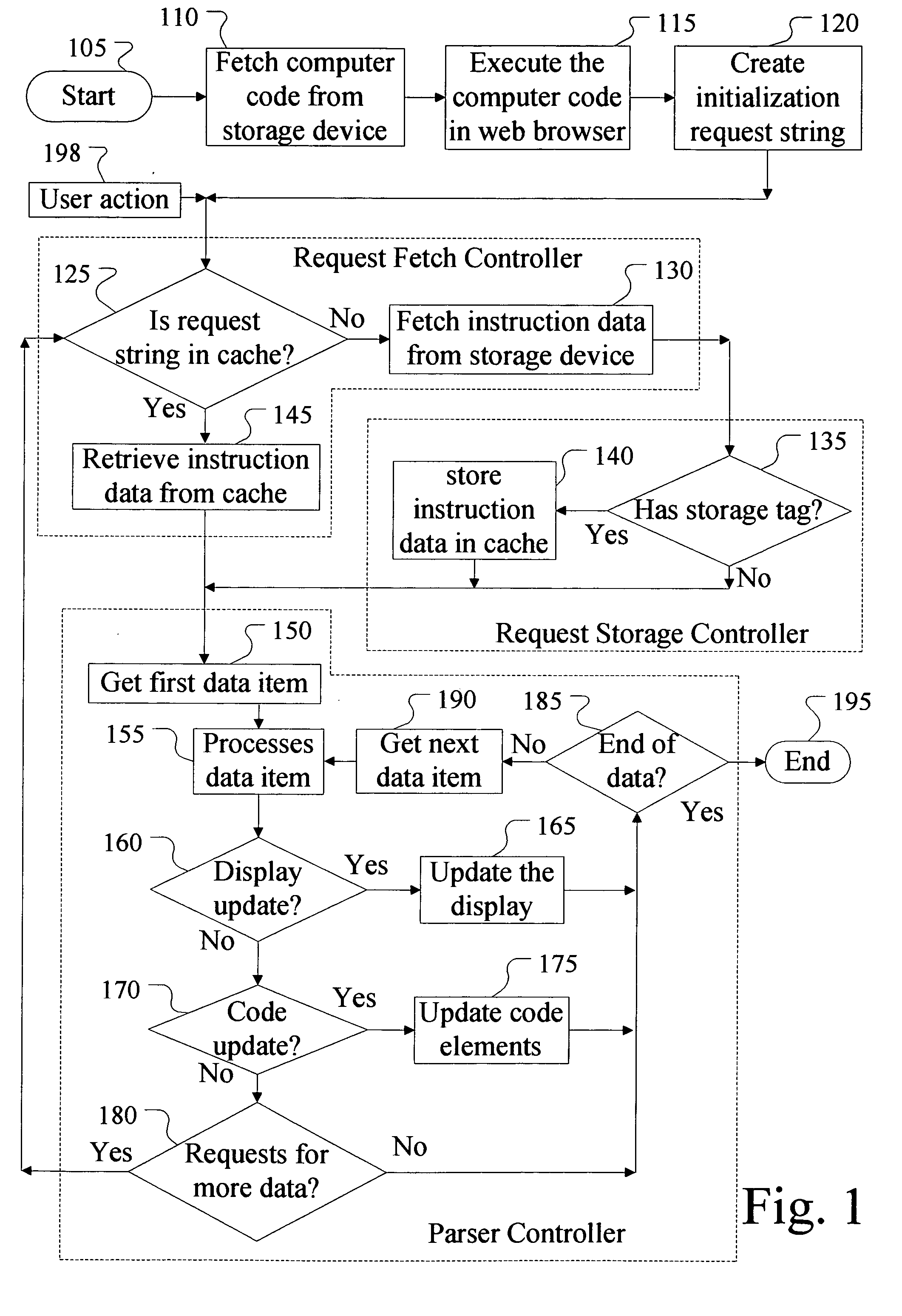
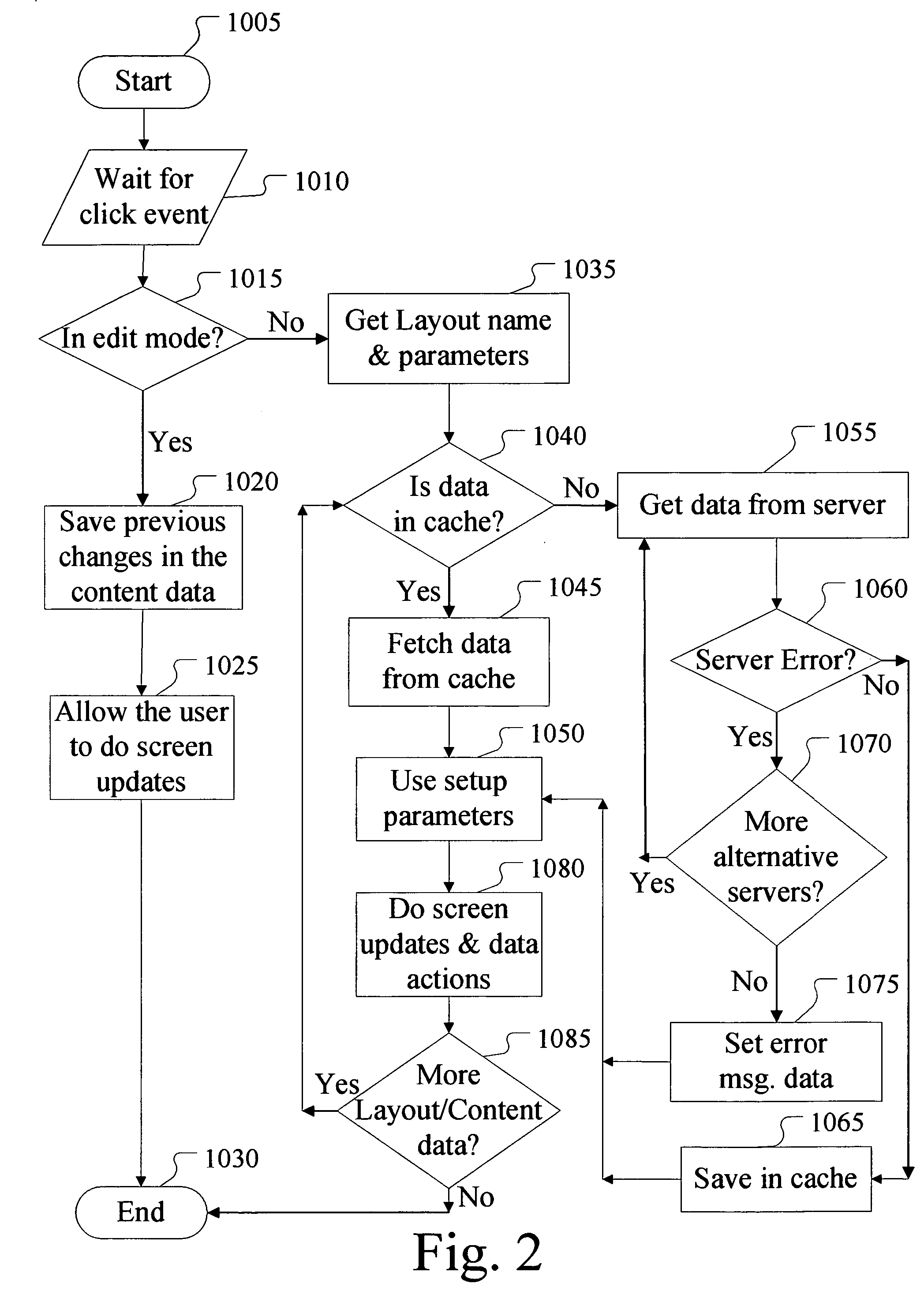
Method for creating editable web sites with increased performance & stability
InactiveUS20060031751A1Natural language data processingWebsite content managementWeb siteClient-side
A method, apparatus and computer program product for creating stable and editable web sites, which use efficient bandwidth, with fast response time and smooth web page transitions. The method creates a web page in the client's machine browser by combining layout instructions & content data. When navigating to a web page, the browser will try to fetch the layout or content data from the local cache, if not exists then the data will be fetched from a web server. This method allows cached layout data to be reused with different content data and edited web pages to be saved as content data. The method can also be used on mission critical systems as it gives the client computer the ability to smoothly overcome many server failures, by redirecting the client to an alternative server.
Owner:EHUD SHAI
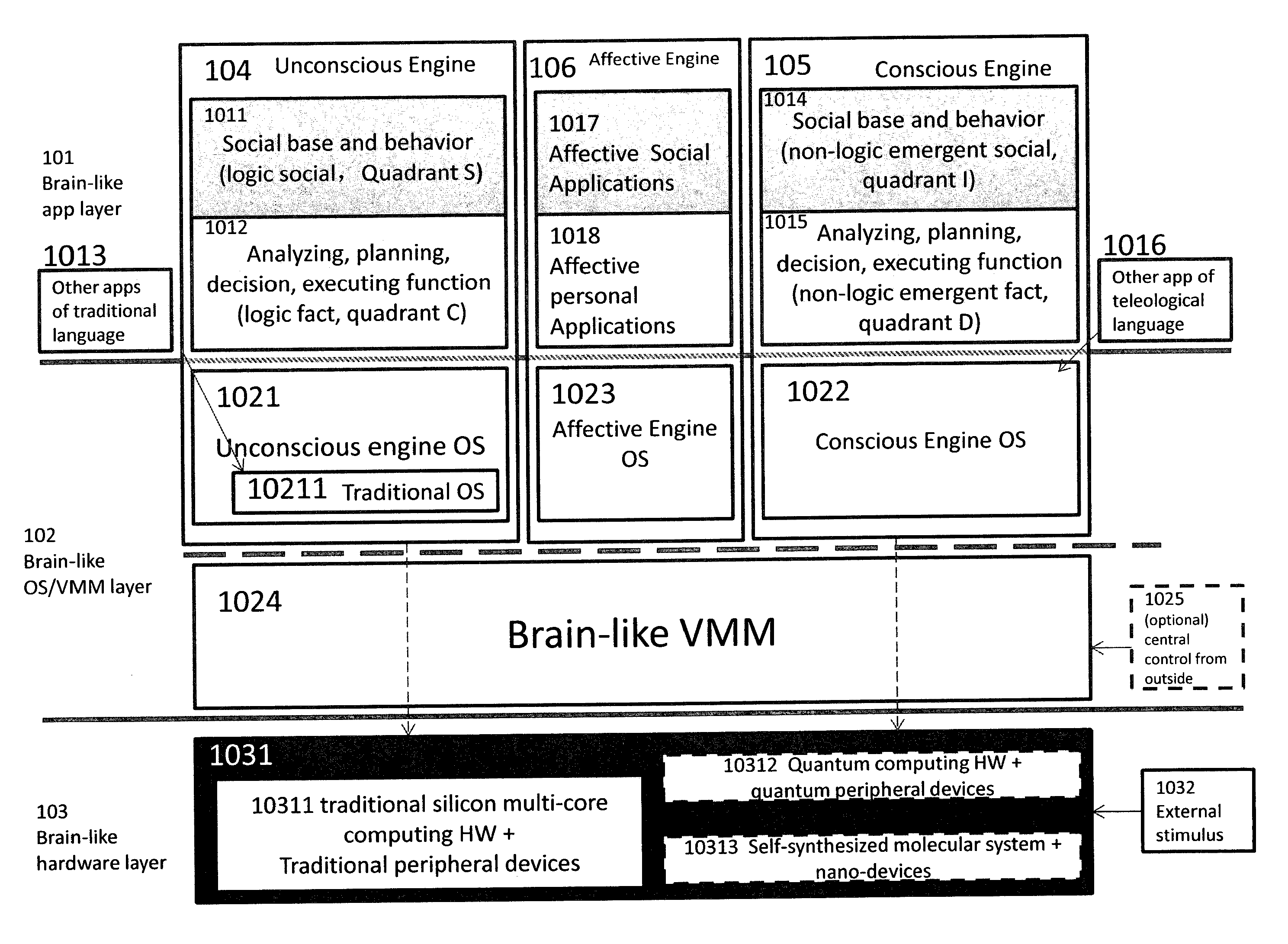
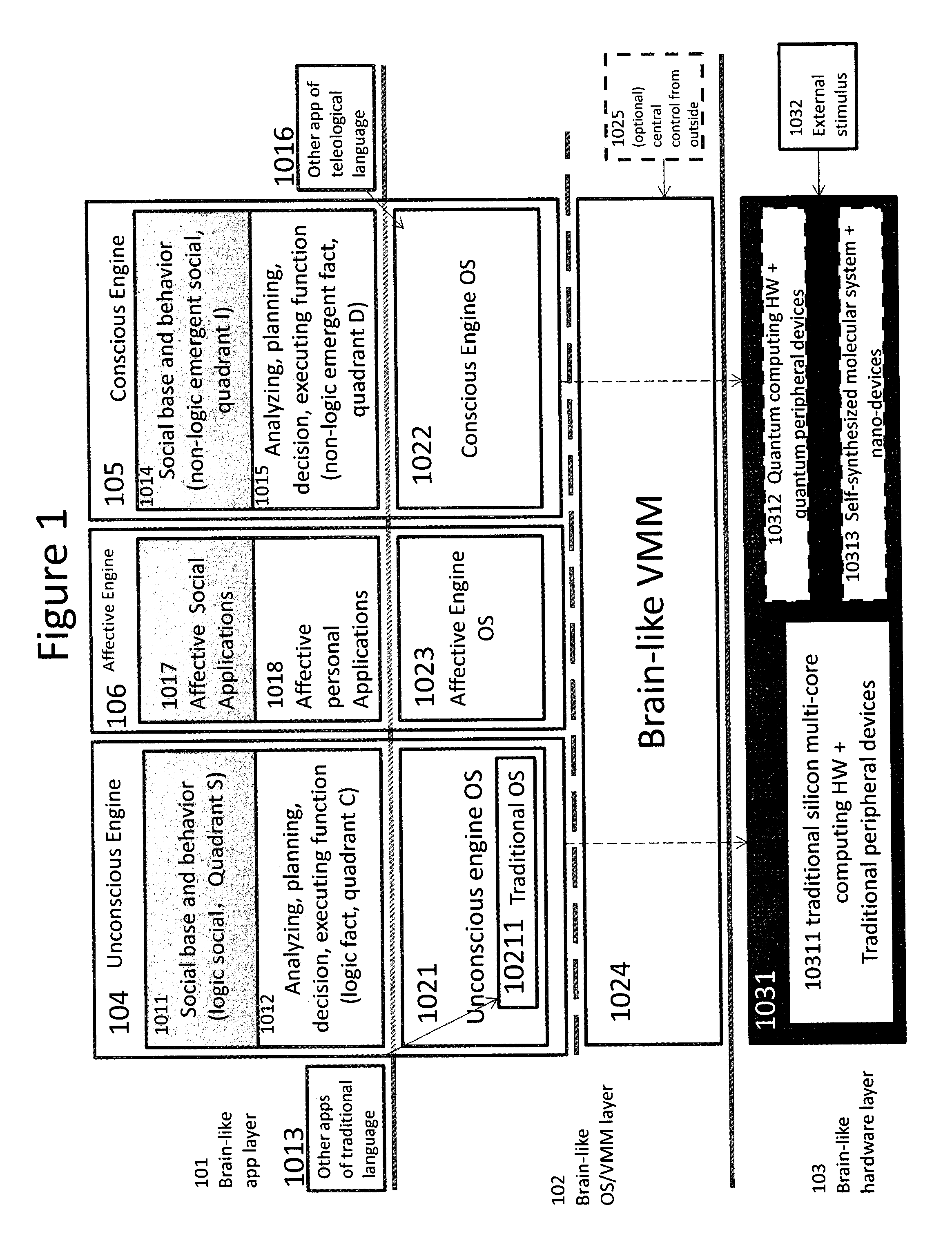
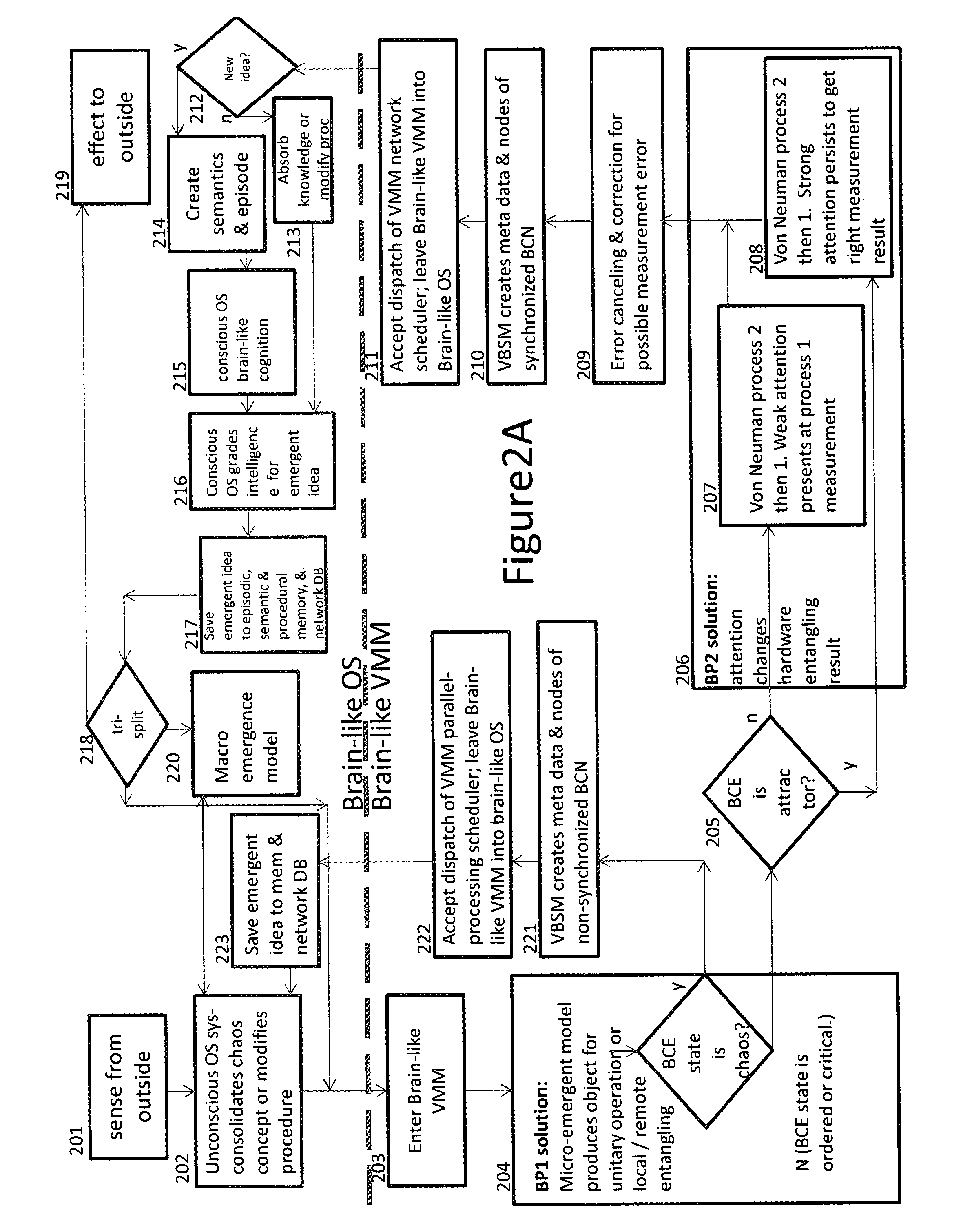
Methods and systems of brain-like computing virtualization
The invention discloses the technology of brain-like computing virtualization. Brain-like computing means the computing technology to mimic human brain and generate human intelligence automatically with computer software. Here the unconscious engine and conscious engine are used to define human left and right brain, while the virtualization technology is used for software to run on future hardware, such as quantum computer and molecular computer. The applied domain areas include quantum gate and adiabatic quantum simulation, brain-like autonomic computing, traditional multi-core-cluster performance service, software development / service delivery systems, and mission-critical business continuity / disaster recovery.
Owner:TRANSOFT SHANGHAI
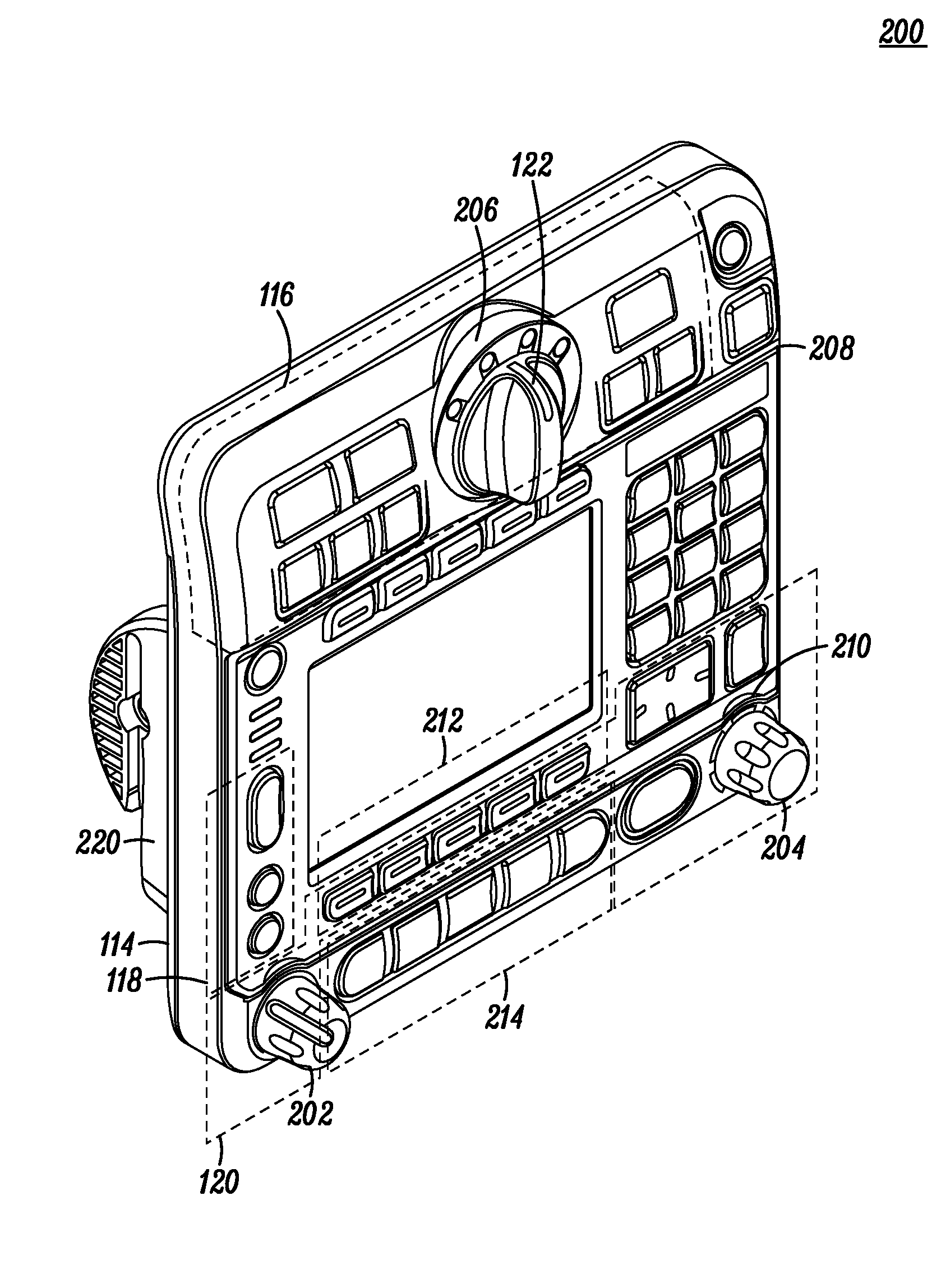
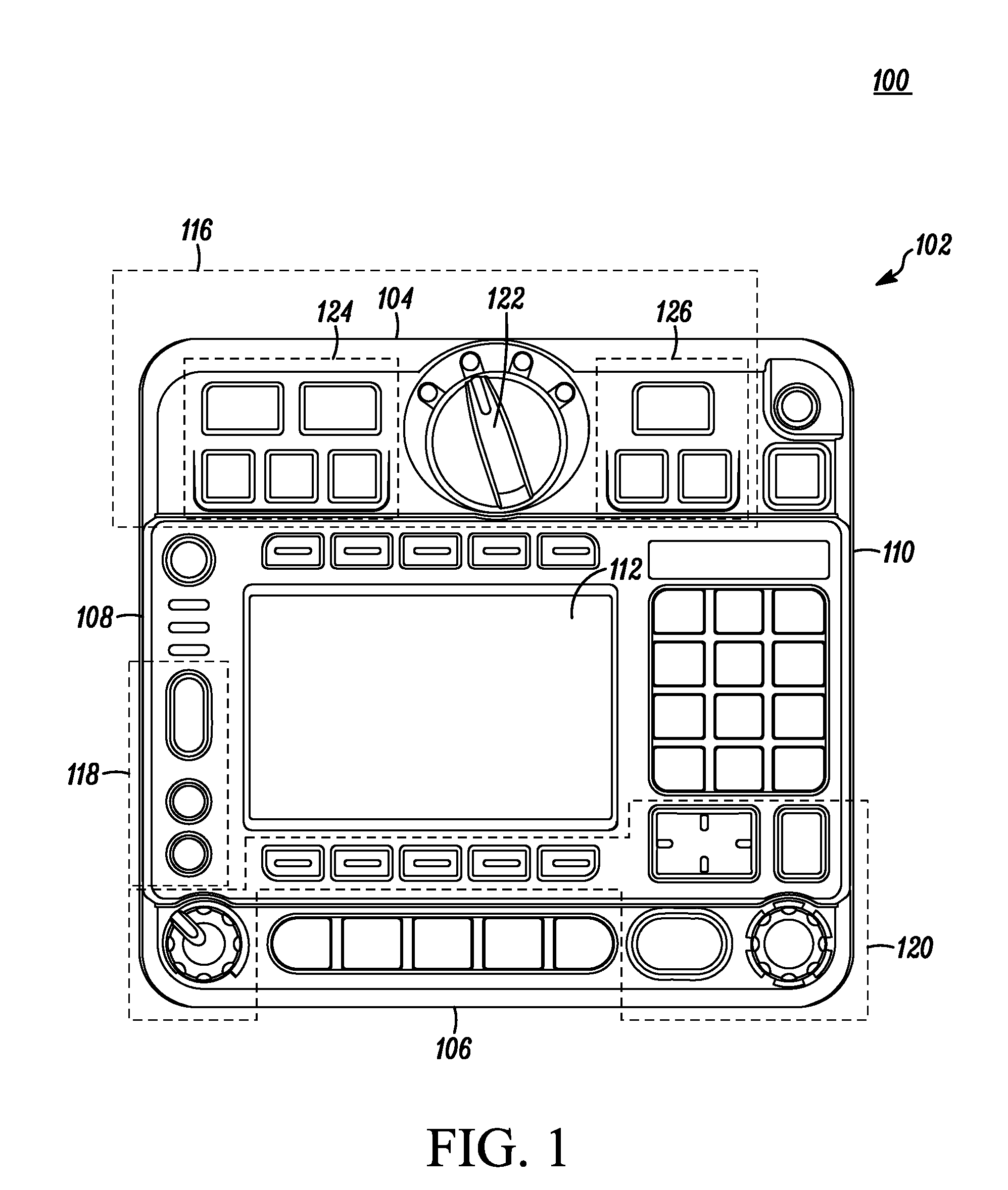
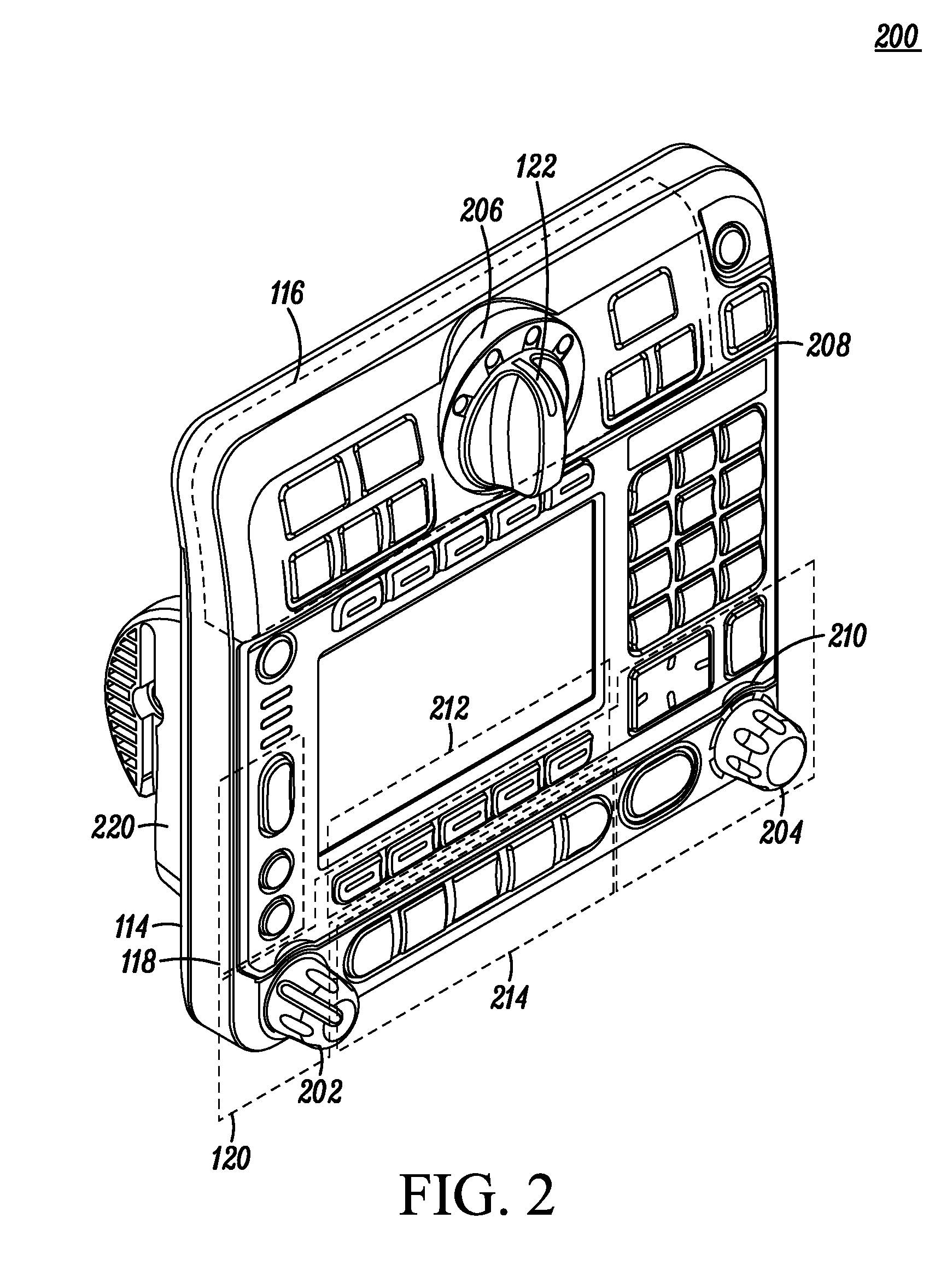
User interface for a vehicle installed communication device
A radio communication device (100) for use in a public safety vehicle is provided with a user interface that combines tactile landmarks in the form of global tactile landmarks and local tactile landmarks along with affordances to orient a user's hand and fingers in conjunction with a sequential task flow interface) for mission critical tasks. Communication device (100) comprises a housing (102) having mission critical controls (116) comprising a pursuit dial (122) mounted on a circular platform (206) with siren controls (124) and light controls (126) grouped on either side of the platform. The mission critical controls (116) are laid out in a manner that provides a sequential user flow across escalating urgency. Ridges (208, 210), chamfered edges (402, 404) and edge reliefs (502) provide further affordances so that a user can intuitively position hand and fingers to locate various controls without having to visually focus on the communication device, thus allowing the user to focus on the current mission.
Owner:MOTOROLA SOLUTIONS INC
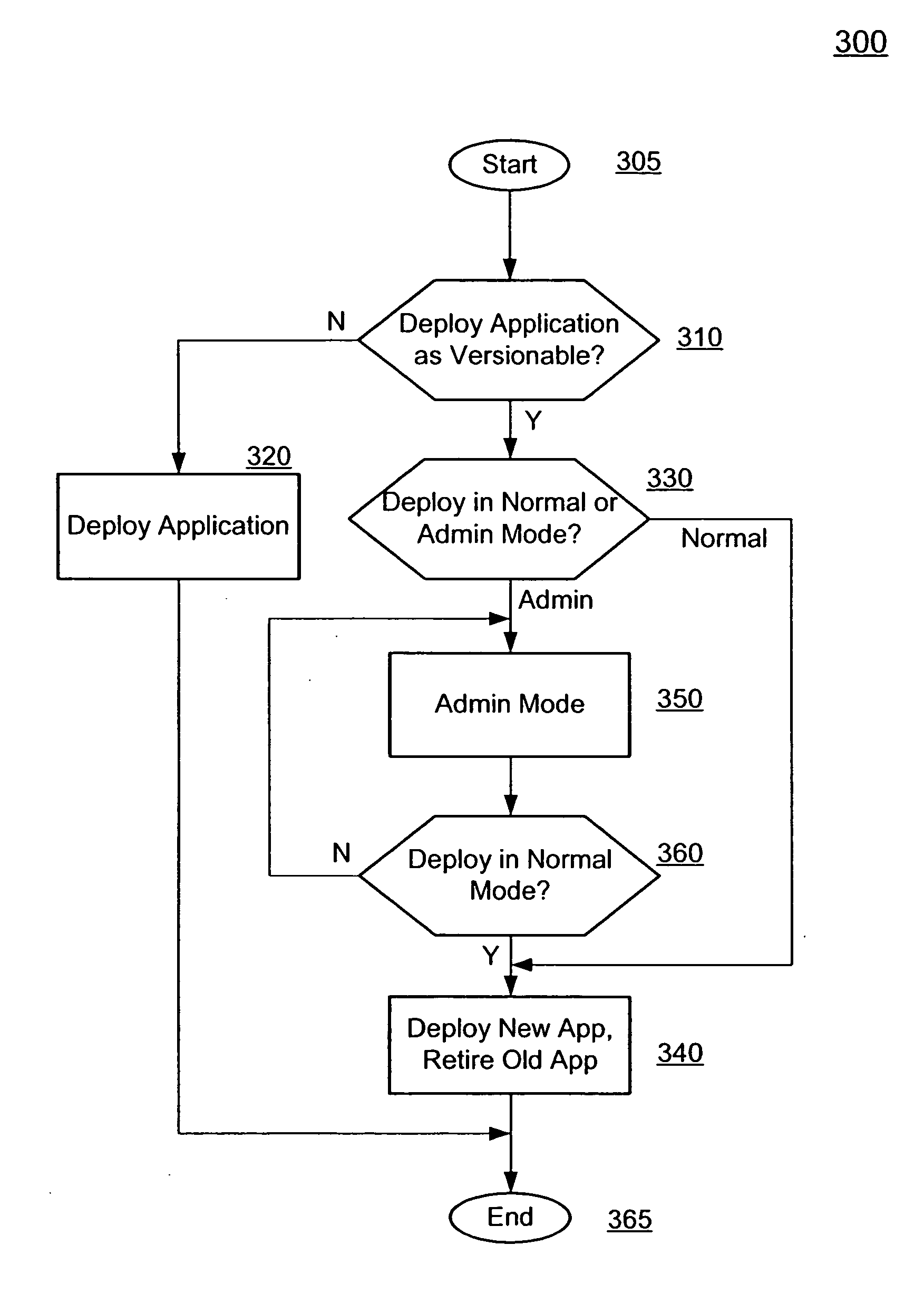
Production redeployment through application versioning
InactiveUS20050262494A1SaveIncrease flexibilitySoftware engineeringProgram loading/initiatingFailoverApplication software
In one embodiment, application versioning and production redeployment support is designed to handle application upgrade needs in mission-critical, production environments. With multiple application versions, application availability to both existing and new clients is not interrupted during the process of application upgrade. It also provides the ability to test a new application version before opening it to general public as well as the ability to roll back to previous safe versions if there are any errors in the currently active version. Clients see consistent application versions, irrespective and transparent of all failure conditions, including admin or managed server restarts and / or failover. Administrators can monitor and manage application versions easily with the management Console. Being a software-based solution, it improves upon traditional application upgrade solution by eliminating the need of hardware load-balancers and duplicate cluster / domain configurations and their associated resource requirements and by providing sophisticated management capabilities.
Owner:BEA SYST INC
Earthquake and Displacement Early Warning System
Novel solutions, which can include devices, systems, methods, than can measure earthquakes and other displacement events. Some solutions feature the integration of real-time, high-rate global navigation satellite system (“GNSS”) displacement information with acceleration and / or velocity data within a single device to create very high-rate displacement records. The mating of these two instruments allows the creation of a new, very high-rate displacement measurement device that has the full-scale displacement characteristics of GNSS and high-precision dynamic motions of seismic technologies. Such a device can be used for earthquake early warning studies and other mission critical applications, such as volcano monitoring, building, bridge and dam monitoring systems.
Owner:TRIMBLE INC
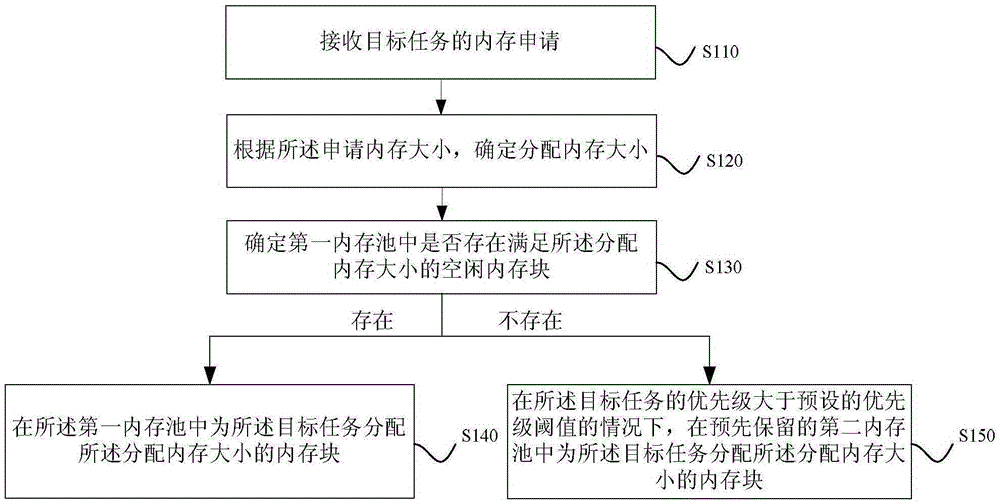
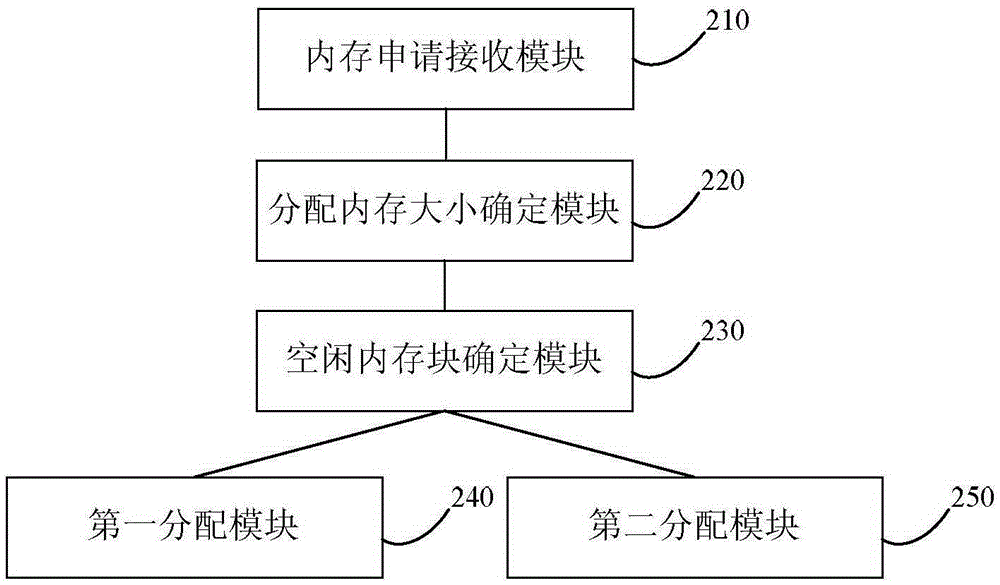
Method and device for distributing memory
ActiveCN105302738AGuaranteed diagnosisImprove securityMemory adressing/allocation/relocationDistributed memoryParallel computing
The embodiment of the invention discloses a method and device for distributing memory. The method for distributing the memory comprises the following steps that a memory request of a target task is received; the capacity of the distributed memory is determined according to the capacity of requested memory; whether a free memory block meeting the capacity of the distributed memory exists in a first memory pool or not is determined; if yes, the memory block with the capacity of the distributed memory is distributed to the target task in the first memory pool; otherwise, the memory block with the capacity of the distributed memory is distributed to the target task in a preserved second memory pool under the condition that the priority of the target task is higher than a preset priority threshold value. According to the technical scheme, when the memory in the first memory pool is used up, the system can distribute the preserved memory to a critical task with higher priority, the basic management capacity and diagnosis capacity of the system are guaranteed, and the safety and reliability of the system are improved.
Owner:KYLAND TECH CO LTD
Reliable execution using compare and transfer instruction on an smt machine
ActiveUS20100281239A1Digital computer detailsConcurrent instruction executionLockstepComputer architecture
A system and method for efficient reliable execution on a simultaneous multithreading machine. A processor is placed in a reliable execution mode (REM) to detect possible errors during execution of a mission critical software application. Only two threads may be configured to operate in this mode. Floating-point store and integer-transfer unary instructions may be converted to new binary instructions. Each new instruction has two source operands, each one corresponding to a different thread is specified by a same logical register number as a single source operand of the original unary instruction. All other instructions are replicated, wherein the original instruction and its twin are assigned to different threads. Simultaneous multi-threaded (SMT) floating-point logic may only be able to provide lockstep execution when it communicates using the new instruction with instantiated integer independent clusters. The new instruction cannot begin until both source operands are ready, which are subsequently compared to determine any mismatches or errors.
Owner:ADVANCED MICRO DEVICES INC
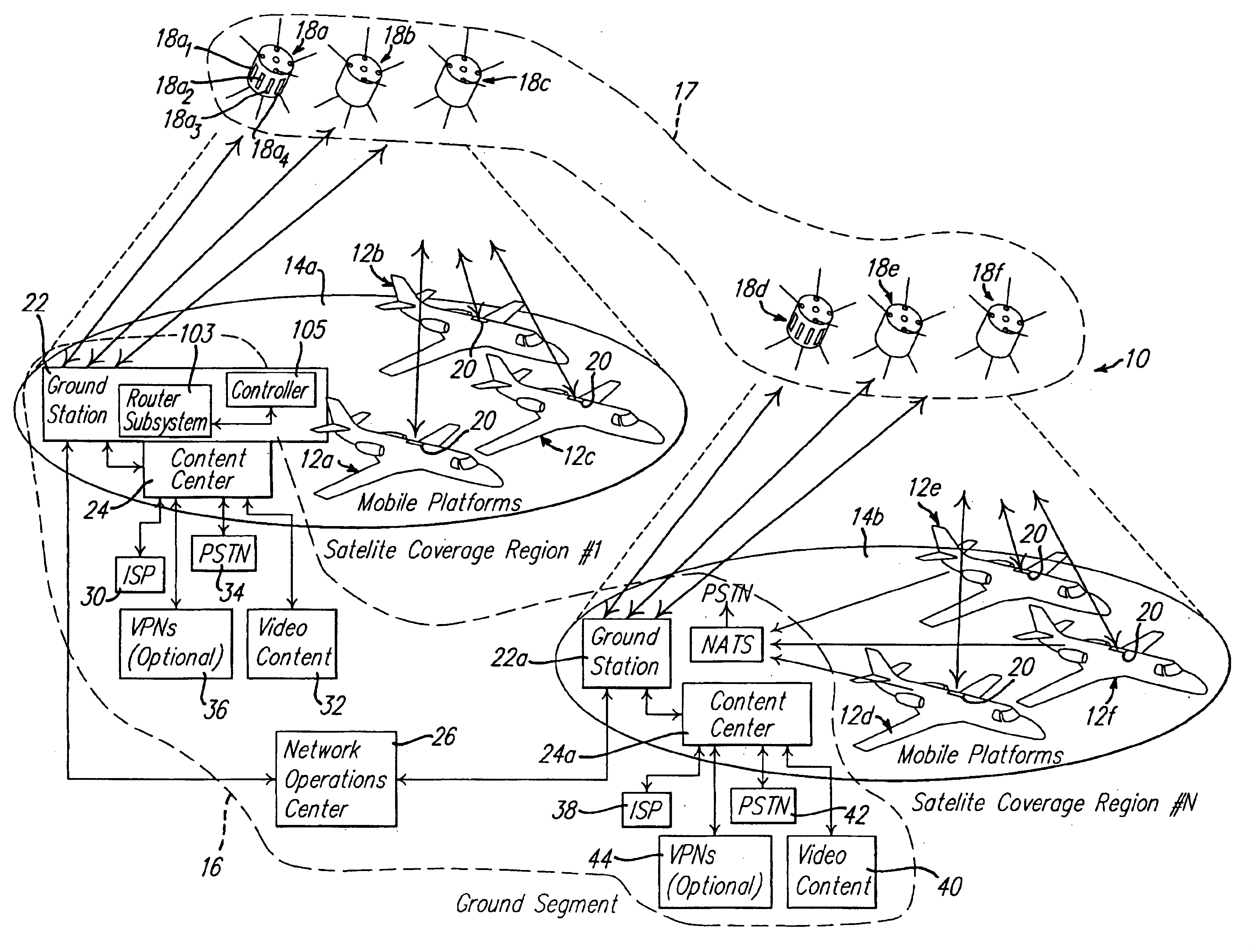
Communications system and method employing forward satellite links using multiple simultaneous data rates
InactiveUS6847801B2Improve communication efficiencyMaximize its transmission rateRadio/inductive link selection arrangementsRadio transmission for post communicationCommunications systemNetwork packet
A communication system and method for transmitting data to mobile platforms using multiple simultaneous channels operating at multiple data rates. Each mobile receiver has the capability to receive multiple transmit channels at multiple data rates. Aircraft report their position to a ground based controller which determines which communication channel can be operated without substantial loss of data. Data packets destined for each aircraft are preferably routed to the highest data rate channel that can be received by that aircraft without substantial loss of data. This maximizes the overall system efficiency and throughput. High priority and mission critical data may be transmitted to the aircraft using low data rate channels to increase link availability.
Owner:THE BOEING CO
Specially adapted serving networks to automatically provide personalized rapid healthcare support by integrating biometric identification securely and without risk of unauthorized disclosure; methods, apparatuses, systems, and tangible media therefor
ActiveUS10984128B1Improve privacyReconcile and reduce and resolve mismatchMedical data miningWeb data indexingCyber operationsBiometric data
These solutions concern transforming a communication network into a scalable network to also automate personalized rapid healthcare support. They integrate biometric identification capabilities into a network entity of, or a resource communicably connectible with, a serving network by using computers to mediate biometric identification and location data. Network operators will provide always on enhanced emergency connectivity for mobility and roaming for user equipment to leverage biometric identification for rapid healthcare support and to produce a unified result set, without risk of undue disclosure of raw biometric data or of selected portions of health profile information. These techniques also support personalized, urgency-supported, healthcare to optimize biometrically-link identifiers / network keys (PUSH TO BLINK), even over a visited operator's IP services. Some facilitate backwardly compatibility across 2G, 3G, 4G, and other networks, whether a mission critical communication, even one with intermodal content via backhaul, is sent via a network that is wireless in any part, or not.
Owner:HOFFER STEVEN MILES
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com