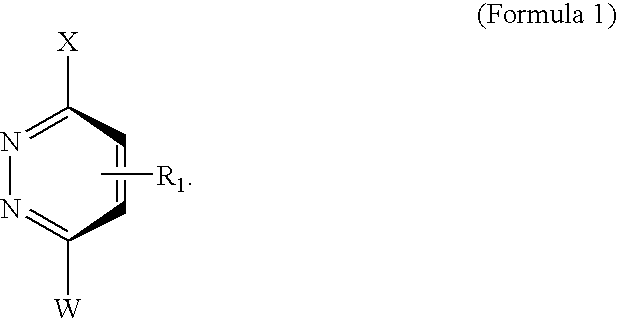Patents
Literature
158 results about "Mimicry" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
In evolutionary biology, mimicry is an evolved resemblance between an organism and another object, often an organism of another species. Mimicry may evolve between different species, or between individuals of the same species. Often, mimicry functions to protect a species from predators, making it an antipredator adaptation. Mimicry evolves if a receiver (such as a predator) perceives the similarity between a mimic (the organism that has a resemblance) and a model (the organism it resembles) and as a result changes its behaviour in a way that provides a selective advantage to the mimic. The resemblances that evolve in mimicry can be visual, acoustic, chemical, tactile, or electric, or combinations of these sensory modalities. Mimicry may be to the advantage of both organisms that share a resemblance, in which case it is a form of mutualism; or mimicry can be to the detriment of one, making it parasitic or competitive. The evolutionary convergence between groups is driven by the selective action of a signal-receiver or dupe. Birds, for example, use sight to identify palatable insects, whilst avoiding the noxious ones. Over time, palatable insects may evolve to resemble noxious ones, making them mimics and the noxious ones models. In the case of mutualism, sometimes both groups are referred to as "co-mimics". It is often thought that models must be more abundant than mimics, but this is not so. Mimicry may involve numerous species; many harmless species such as hoverflies are Batesian mimics of strongly defended species such as wasps, while many such well-defended species form Mullerian mimicry rings, all resembling each other. Mimicry between prey species and their predators often involves three or more species.
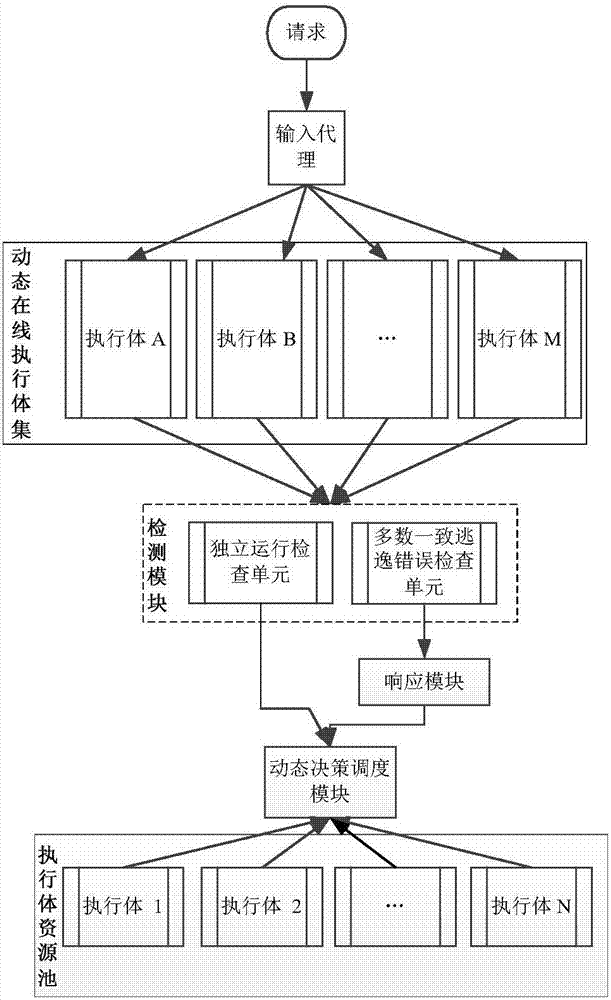
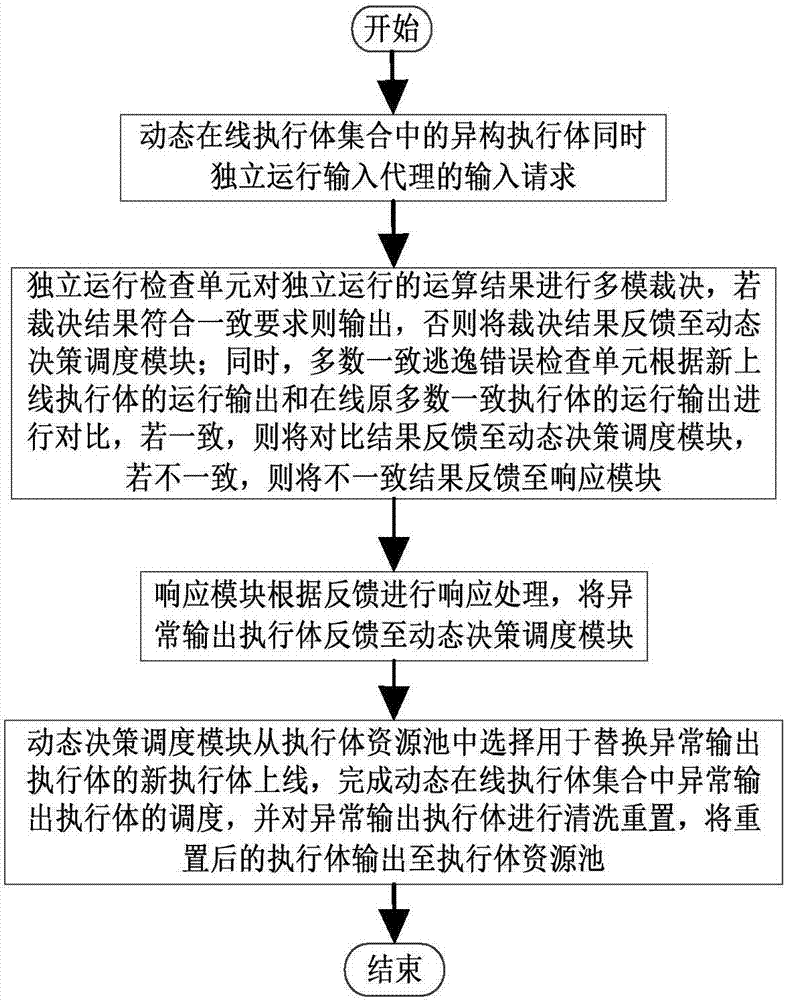
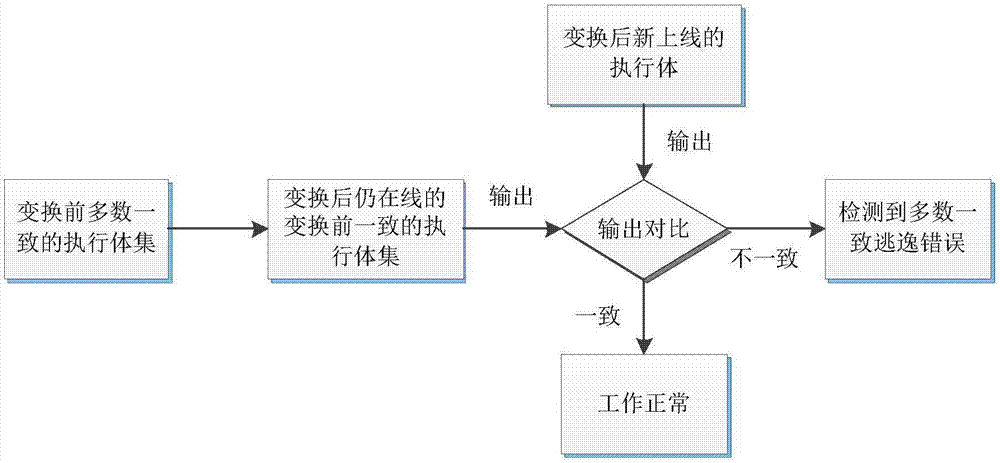
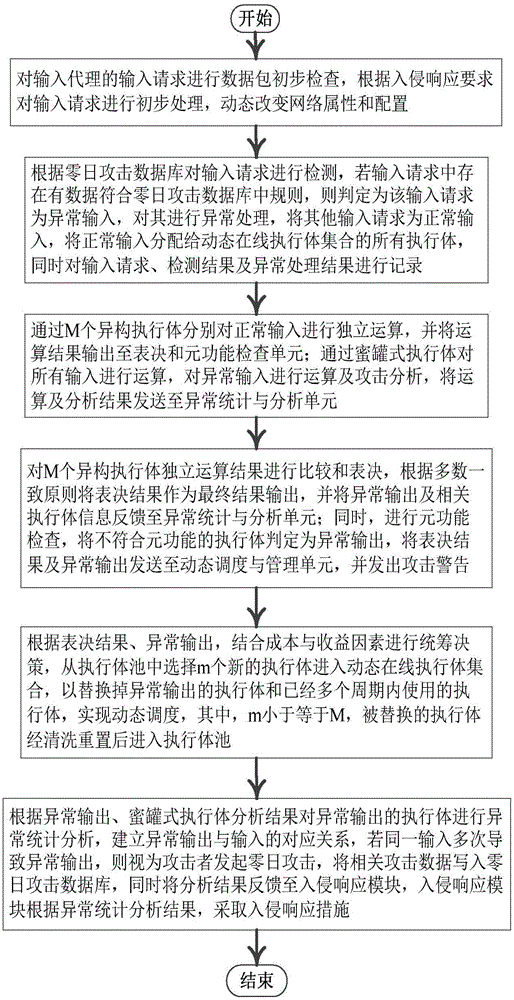
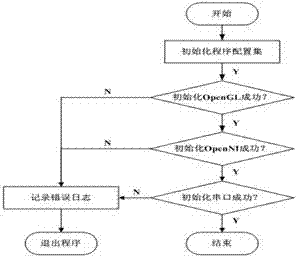
Majority consistent escape error processing device based on mimicry security defense zero-day attack and method thereof
ActiveCN106874755AGuaranteed robustnessGuaranteed survivabilityPlatform integrity maintainanceResource poolError processing
The invention relates to a majority consistent escape error processing device based on mimicry security defense zero-day attack and a method thereof. The method comprises: a heterogeneous executive in a dynamic online executive assembly independently operating an input request; performing multimode adjudication on an operation result, if an adjudication result meets a consistency requirement, outputting the adjudication result, if not, feeding back the adjudication result to a dynamic decision dispatching module; comparing new online executive operation output with online original majority consistent executive operation output, respectively feeding back results to the dynamic decision dispatching module and a responding module; the responding module processing the response according to feedback, and feeding back abnormal output executive to the dynamic decision dispatching module; and the dynamic decision dispatching module selecting new executive to be online from an executive resource pool, and cleaning and resetting offline executives. The method is used to provide means of detection and response when majority of mimicry defense online executives are attacked, and solves security threat a mimicry defense system faces, so as to enhance robustness of the mimicry system.
Owner:THE PLA INFORMATION ENG UNIV
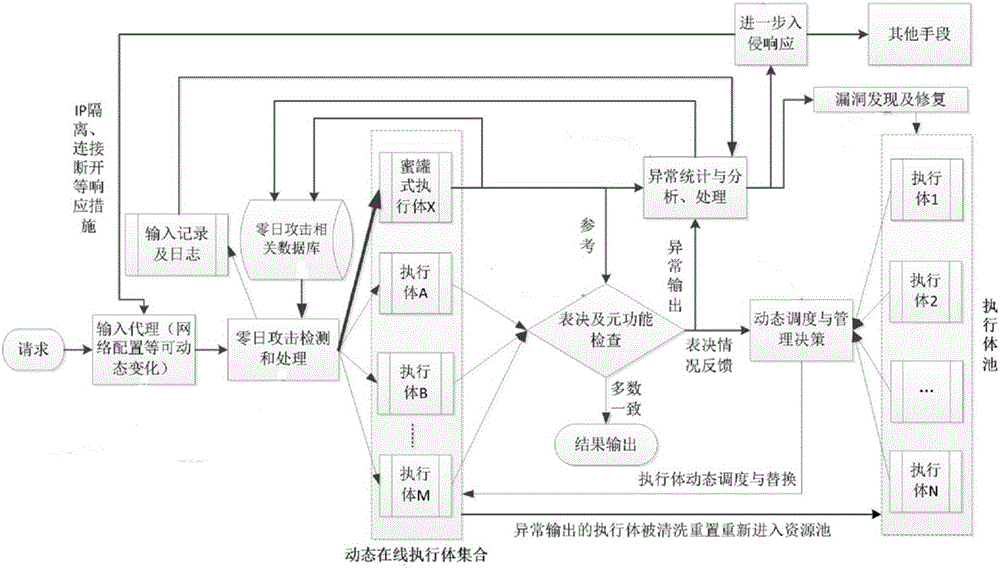
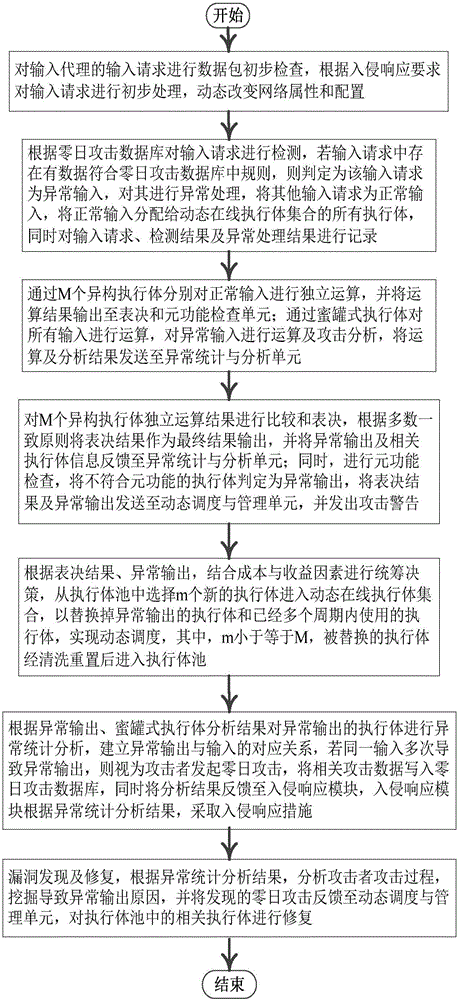
Mimicry defense architecture based zero-day attack detection, analysis and response system and method thereof
The invention relates to a mimicry defense architecture based zero-day attack detection, analysis and response system and a method thereof. The method comprises the steps of performing attack detection and processing on the input, cheating and inducing an attacker through honeypot type executing bodies, and performing meta-function inspection on the output of each executing body; performing statistical analysis on abnormal output by combining abnormal information, updating a zero-day attack database, feeding back an analysis result to an intrusion response module, and preventing persistent attacks of the attacker; performing dynamic adjustment and management on an online executing body by combining voting conditions, executing body dispatching, the executing body with abnormal output and the like, and selecting executing bodies from an executing body resource pool to get into a dynamic online executing body set; and analyzing a zero-day vulnerability in the executing body with abnormal output according to an anomaly statistical analysis result, and repairing the related executing bodies in the executing body pool. According to the invention, functions and the flexibility of mimicry defense architecture are enhanced, values of the abnormal output are sufficiently utilized, and the threat and the defense cost of zero-day attacks are reduced.
Owner:THE PLA INFORMATION ENG UNIV
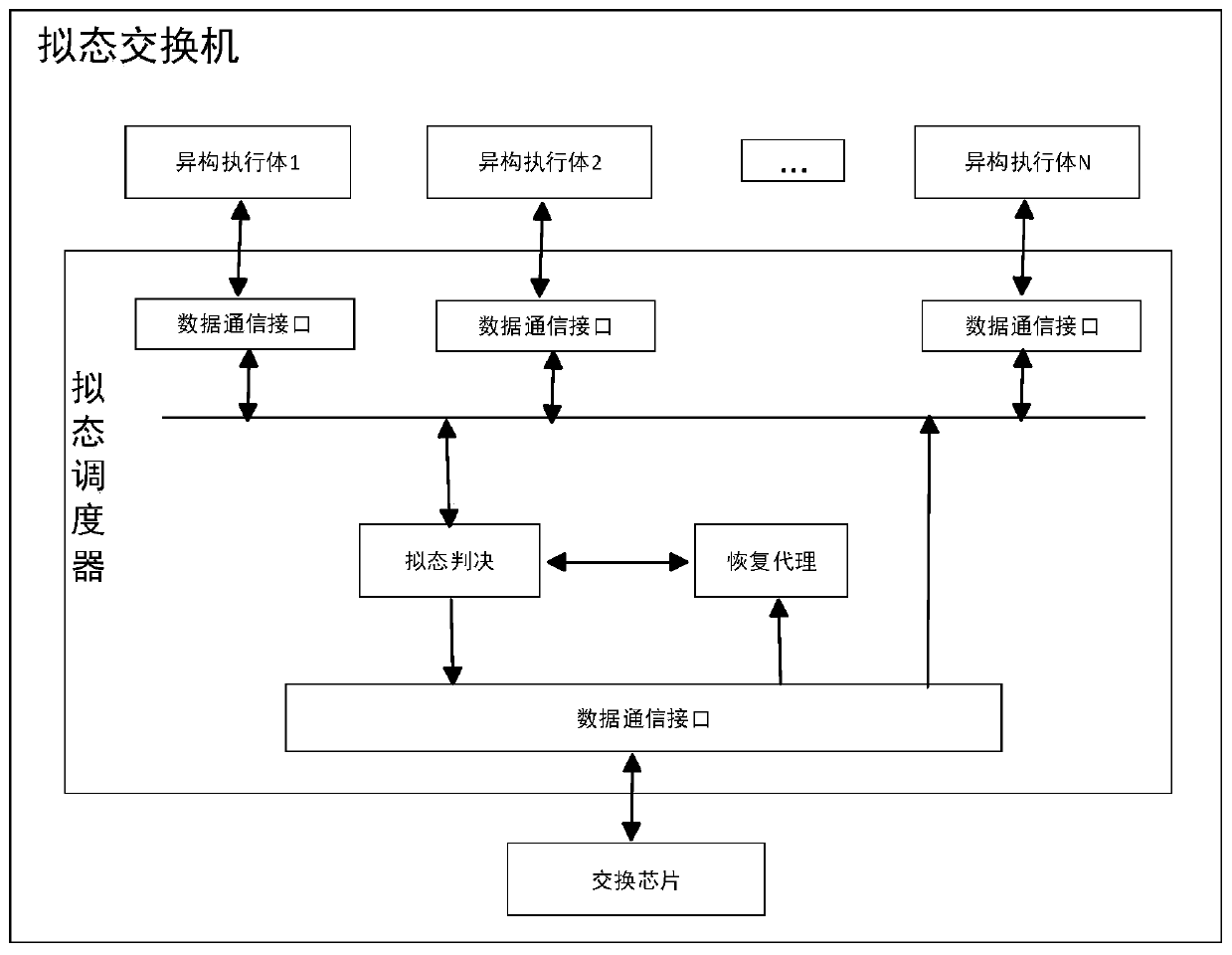
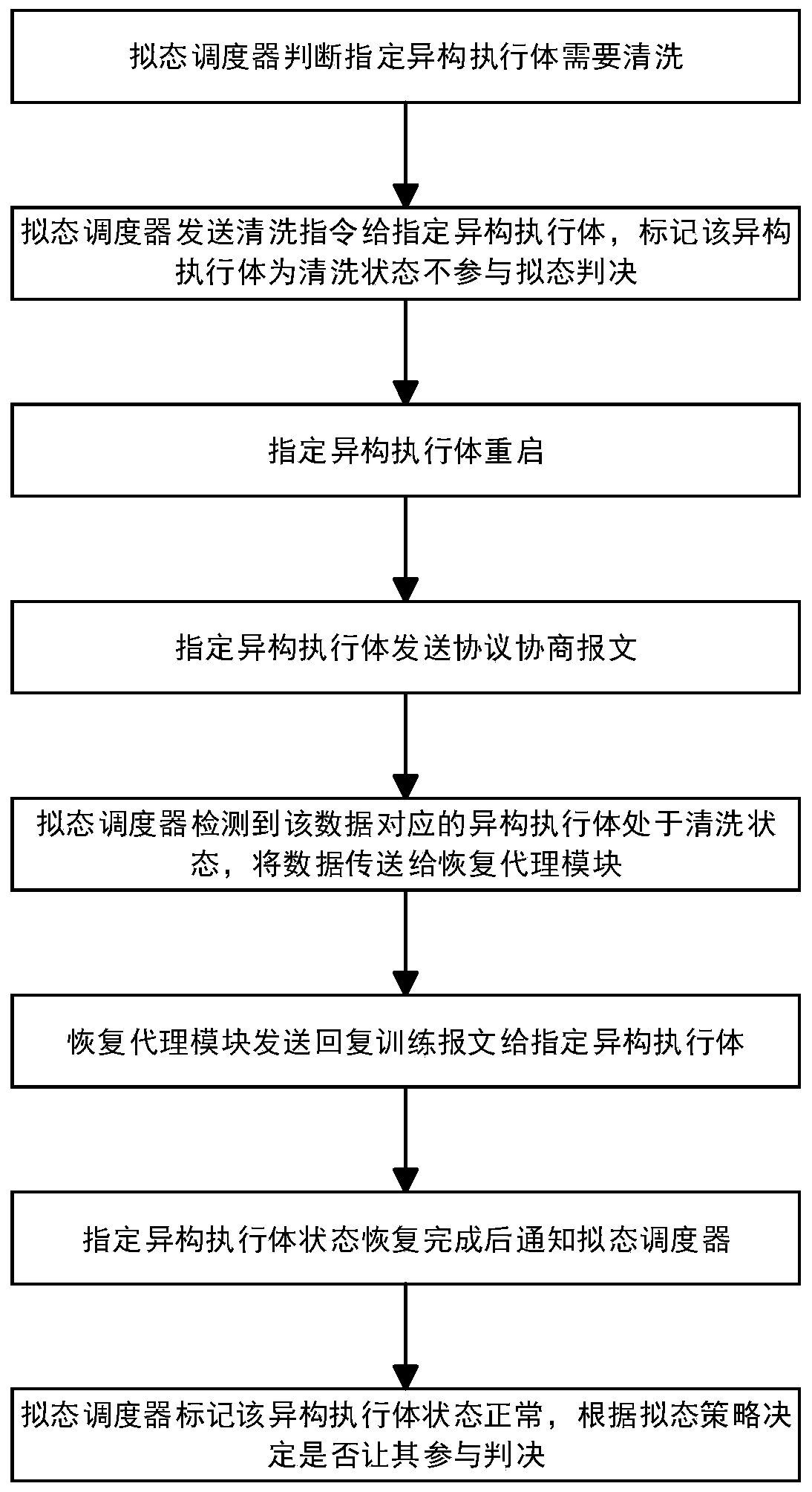
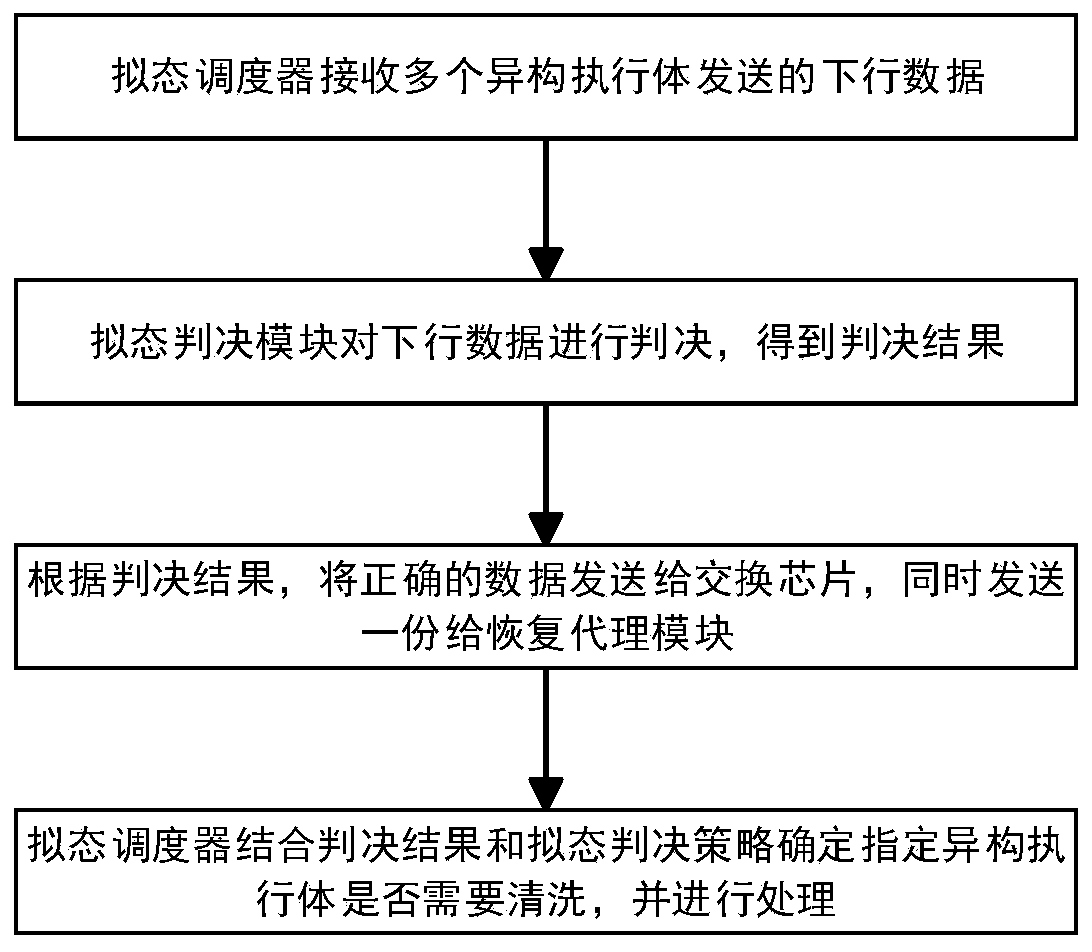
Mimicry switch heterogeneous executor cleaning recovery method and device
ActiveCN111049677AImprove reliabilityImprove stabilityDatabase distribution/replicationData switching networksMimicryProtocol stack
The invention discloses a heterogeneous executor cleaning recovery method and device in a mimicry switch. The method comprises the steps that a mimicry scheduler judges downlink data from a pluralityof heterogeneous executors, and marks a to-be-cleaned specified heterogeneous executor; specifying a heterogeneous execution body to restart, and then specifying the heterogeneous execution body to send a normal protocol negotiation message to try to interact with the mimicry scheduler; the mimicry scheduler detects whether the specified heterogeneous executor is in a cleaning state or not according to the protocol negotiation message, the message sending process is repeated until the state of the specified heterogeneous executor is recovered, and the mimicry scheduler is notified; and the mimicry scheduler marks that the state of the specified heterogeneous executor is normal. According to the method, under the condition that protocol stacks on the heterogeneous executors do not need to be modified, the normal working state can be quickly restored when one or more heterogeneous executors are attacked by the outside or the inside of the heterogeneous executors is abnormal, and the method has important guiding significance for the cleaning and restoring technology of the multimode heterogeneous executor architecture system.
Owner:PURPLE MOUNTAIN LAB
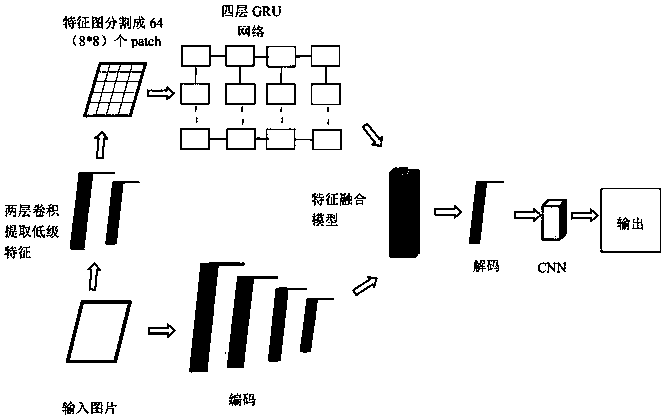
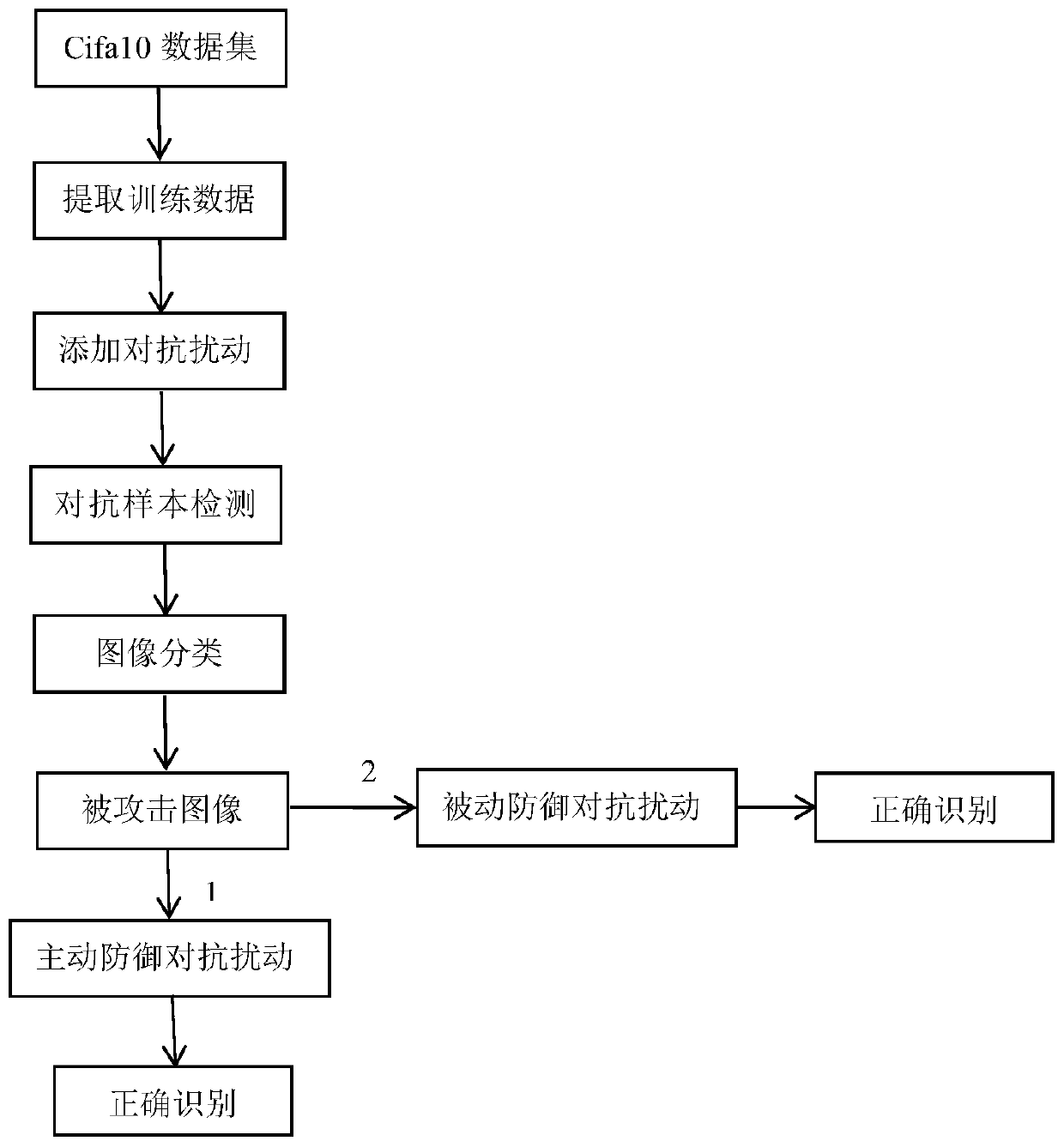
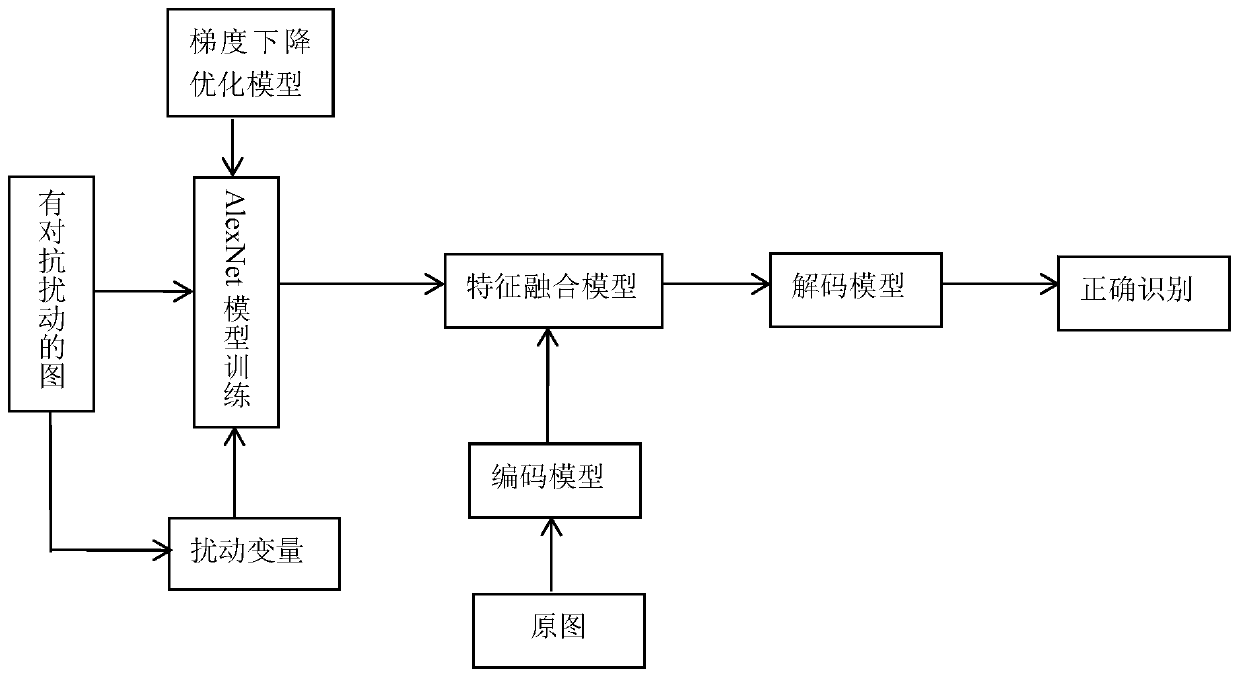
Mimicry defense method for deep learning model confrontation attack
ActiveCN110647918AReduce training timeImprove defenseCharacter and pattern recognitionPlatform integrity maintainanceFeature extractionEngineering
The invention discloses a mimicry defense method for deep learning model confrontation attack. The method comprises the following steps: 1) preparing a confrontation sample; 2) training a confrontation sample detector; 3) detecting the confrontation sample; 4) defensing confrontation disturbance, specifically actively defensing confrontation disturbance and deactively defensing confrontation disturbance. According to the method, the defects of manual feature extraction and pixel block division are avoided, the process is simplified, the training efficiency is improved, the data updating speedand accuracy are improved, and the data processing efficiency is improved.
Owner:ZHEJIANG UNIV OF TECH
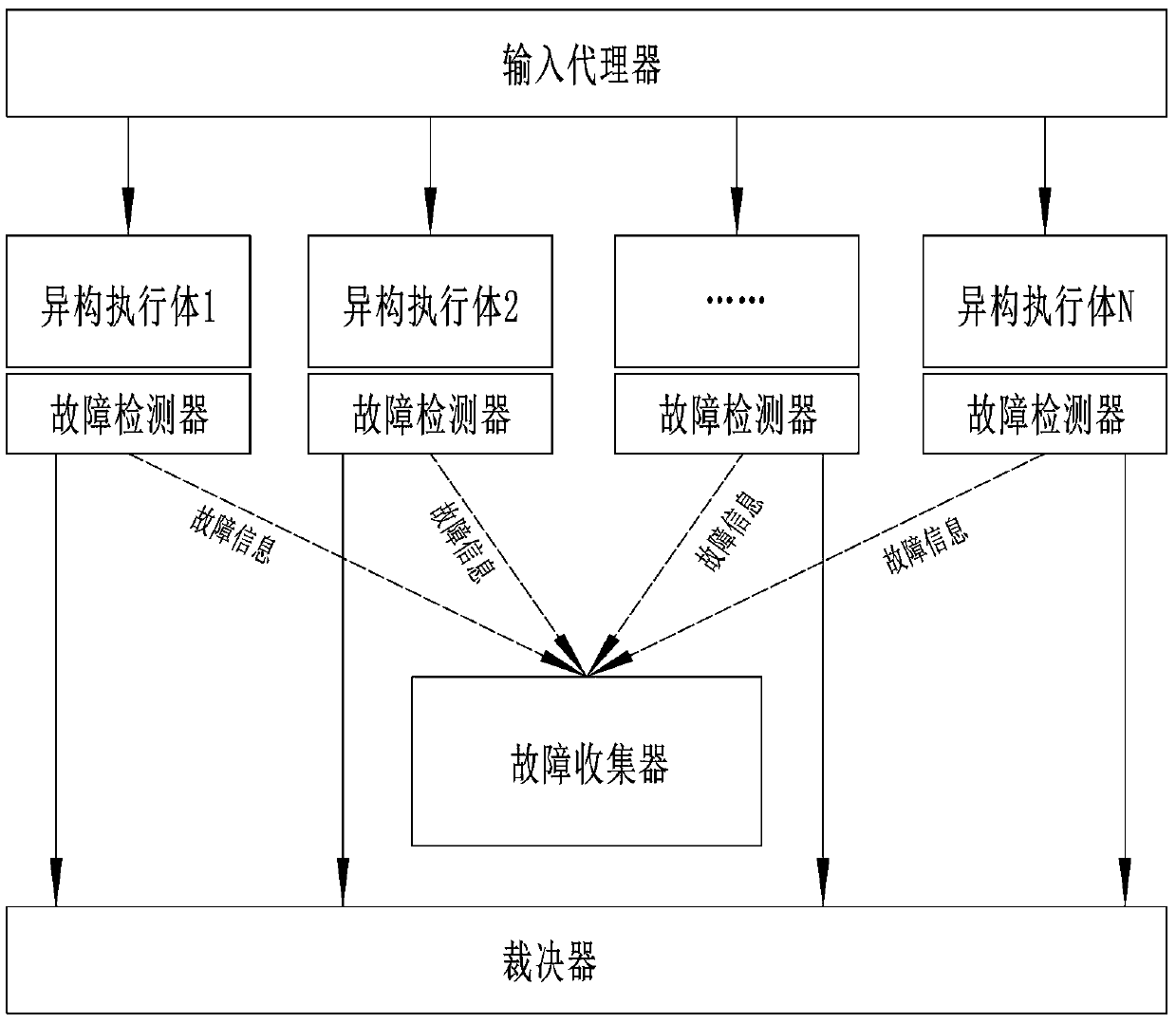
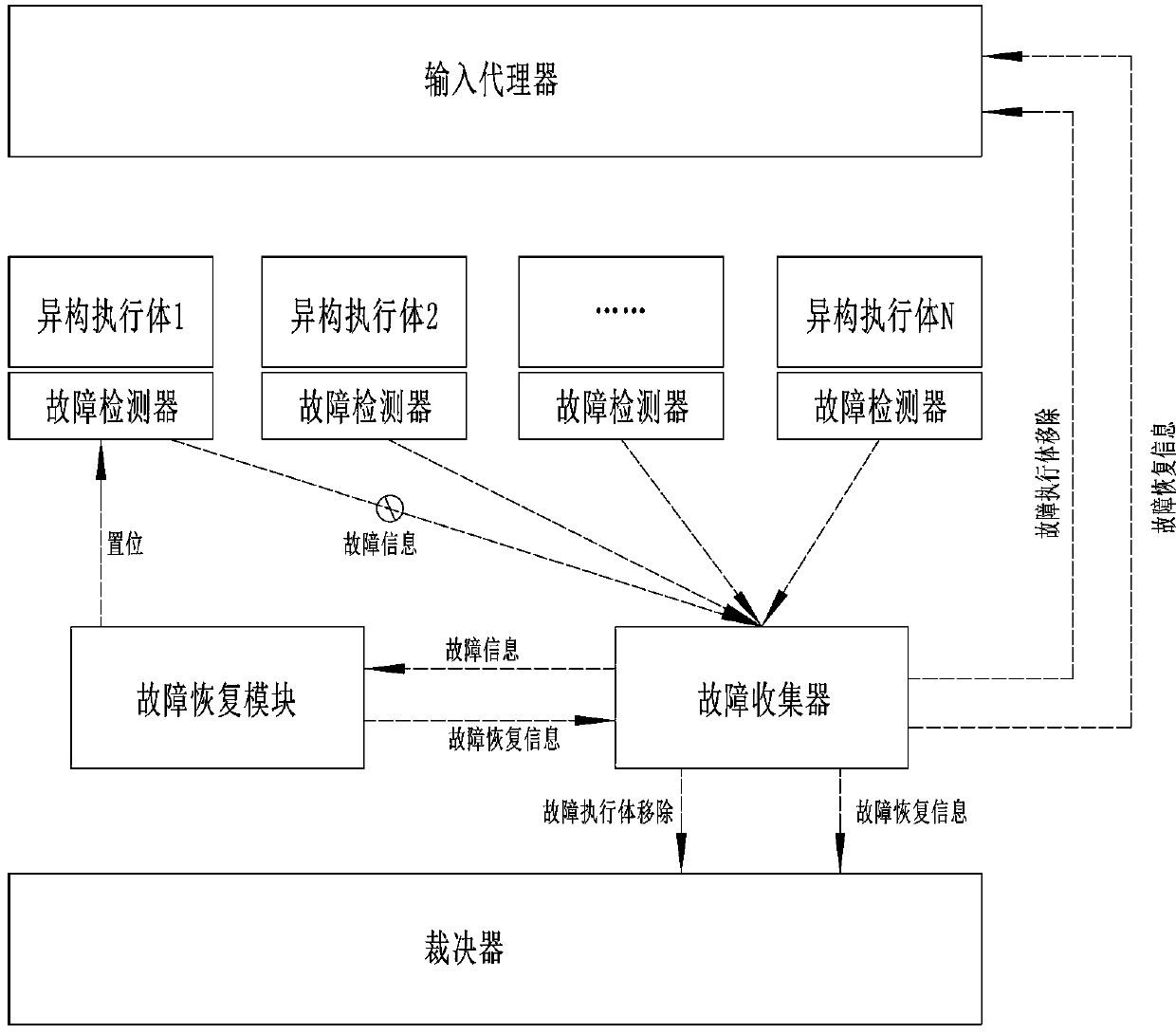
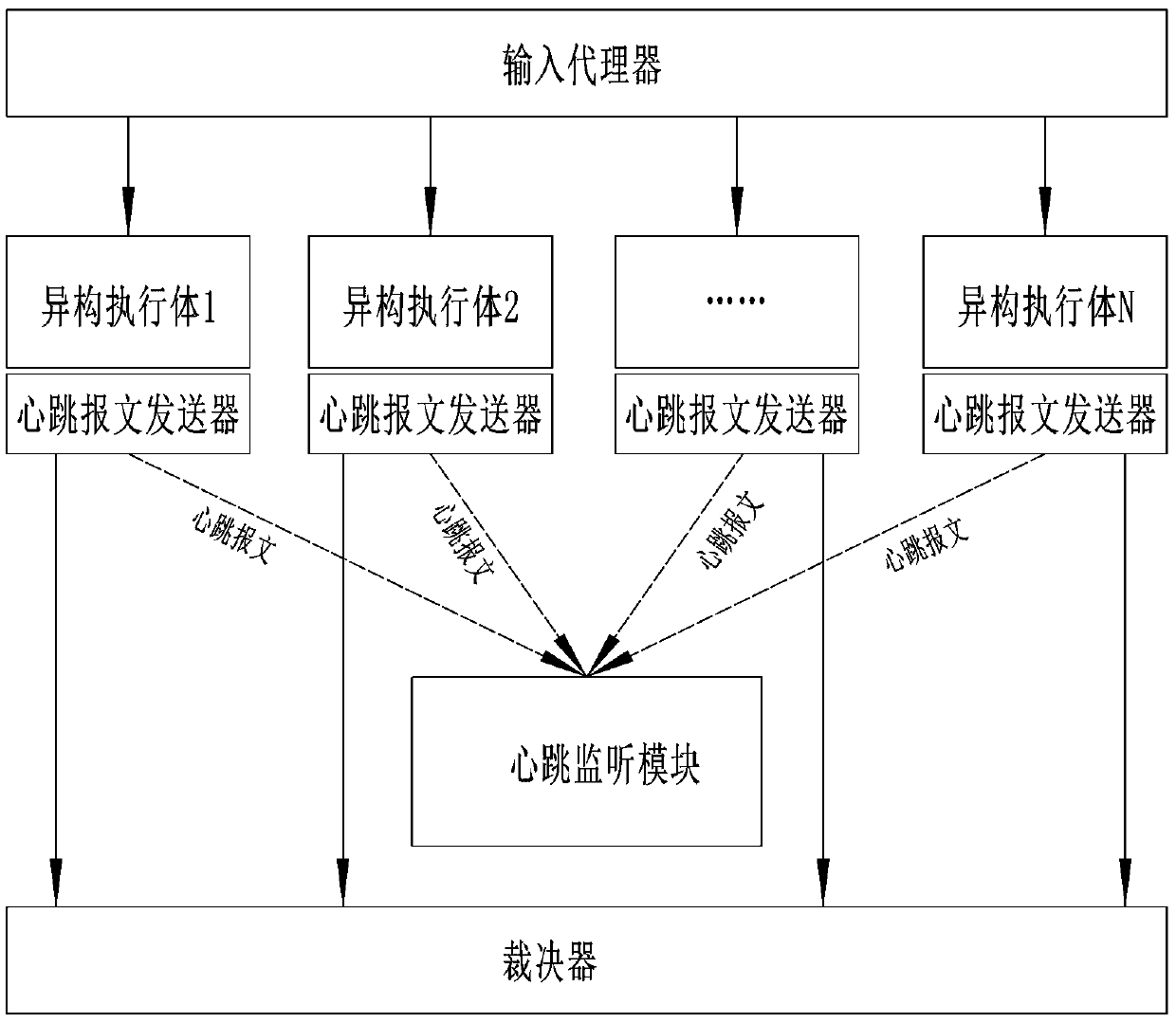
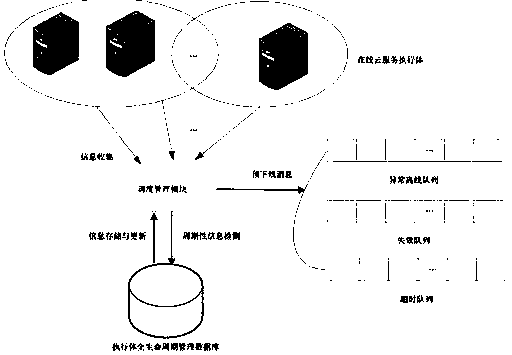
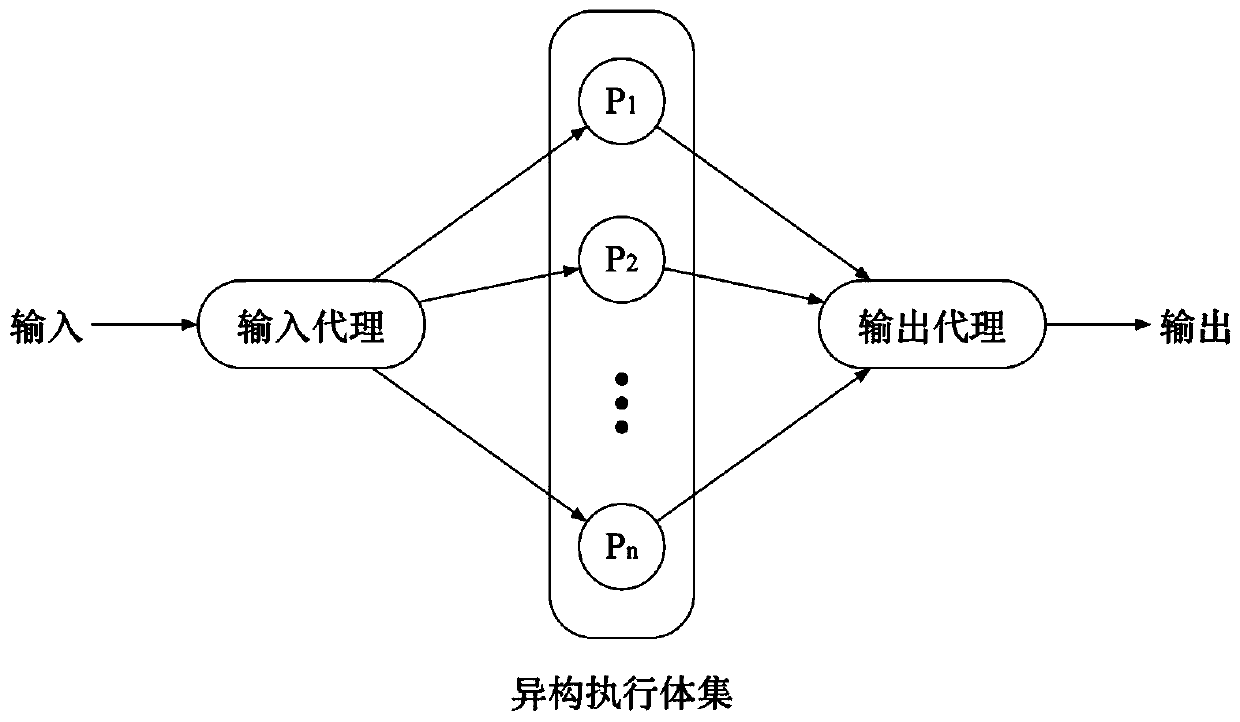
Efficient mimicry defense system and method
The invention provides an efficient mimicry defense system and method, and the system comprises an input agent, a heterogeneous execution body pool, a decision device, a fault detector, a fault collector, and a fault recovery module. The method comprises the following steps that 1, a fault detector detects the software and hardware running state of a heterogeneous execution body in real time and sends detected fault information to a fault collector, and then the fault collector transmits the fault information to a judgment device, an input agent device and a fault recovery module; step 2, theadjustor removes adjustments to the fault heterogeneous executor message; 3, the input agent removes the distribution of the input messages of the fault heterogeneous executor; and 4, the fault recovery module sends a setting command to the faulted heterogeneous execution body or resets the heterogeneous execution body in a hardware mode.
Owner:河南信大网御科技有限公司 +2
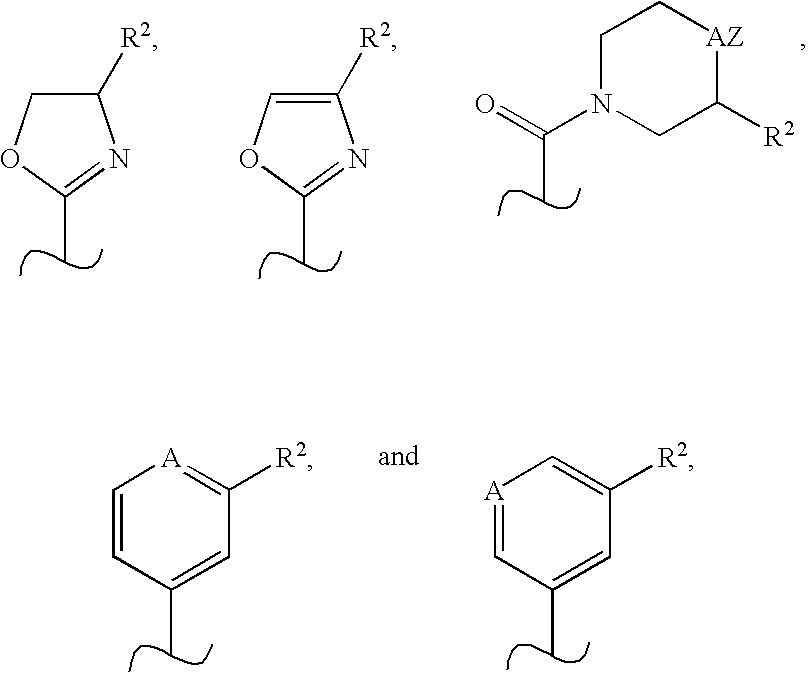
Novel scaffolds for beta-helix mimicry
Functionalized pyridazine derivatives having a low molecular weight and pharmaceutical compositions thereof are useful as alpha-helix mimetics and for treating conditions and / or disorders mediated by alpha-helix-binding receptors and proteins.
Owner:THE SCRIPPS RES INST
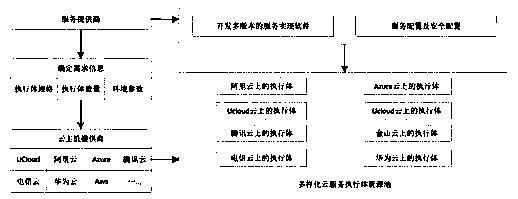
Cloud service executor dynamic reconstruction method based on mimicry defense
ActiveCN110324417AGuaranteed running stabilityReduce loadTransmissionResource poolOptimal scheduling
The invention provides a cloud service executor dynamic reconstruction method based on mimicry defense. The method comprises the steps of step 1, building a heterogeneous cloud service executor mirrorimage resource pool; step 2, constructing a pre-offline executor information queue according to a cloud service executor scheduling triggering mechanism; and step 3, realizing seamless switching between a new online execution body and a pre-offline execution body by adopting an execution body offline and online mechanism. According to the method, dynamic reconstruction of the cloud service executor is realized through mimicry defense, the optimal scheduling problem of the executor is solved, the robustness and dynamics of the cloud service executor are improved, and the security of cloud services based on mimicry defense is enhanced.
Owner:河南信大网御科技有限公司 +1
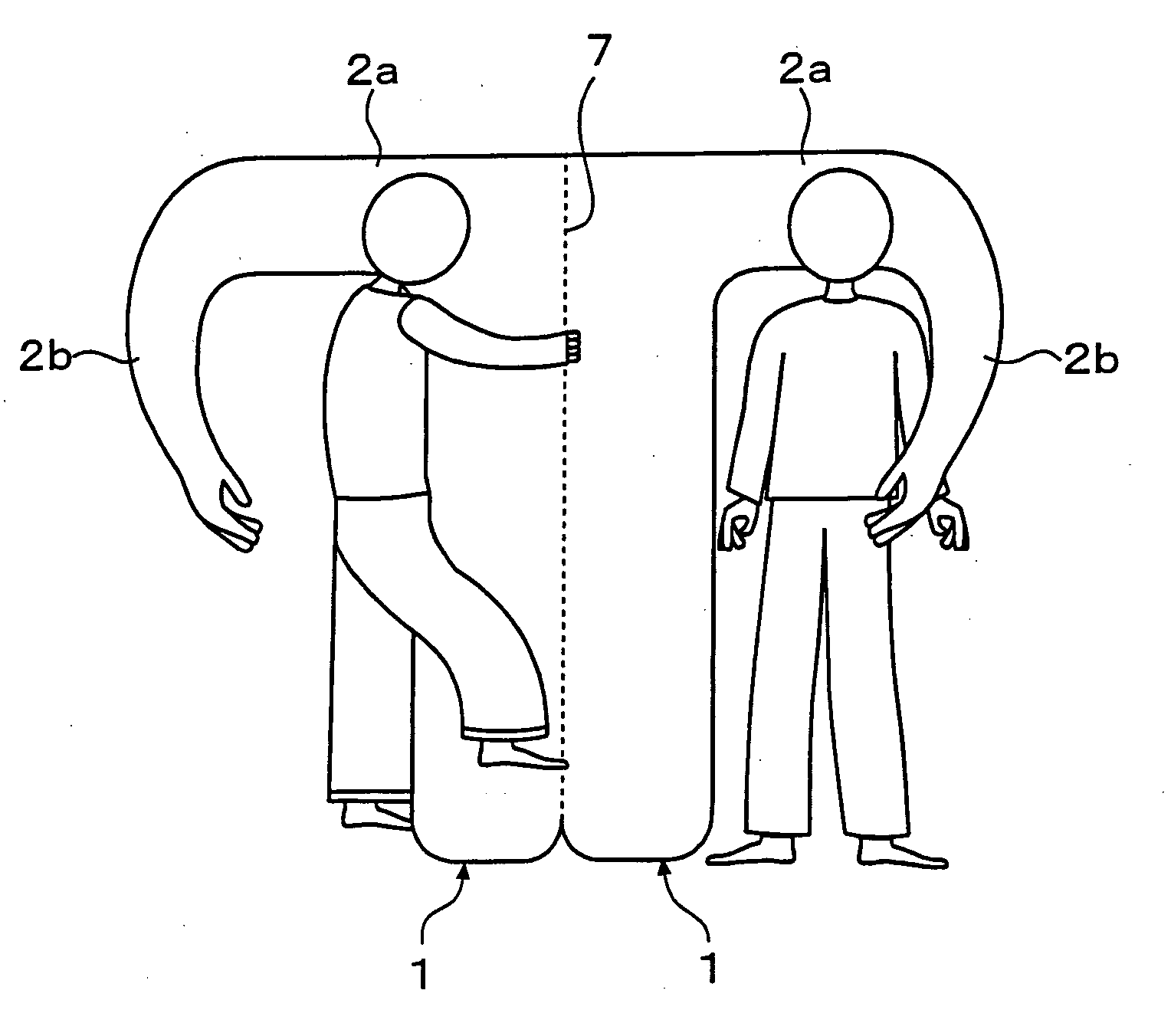
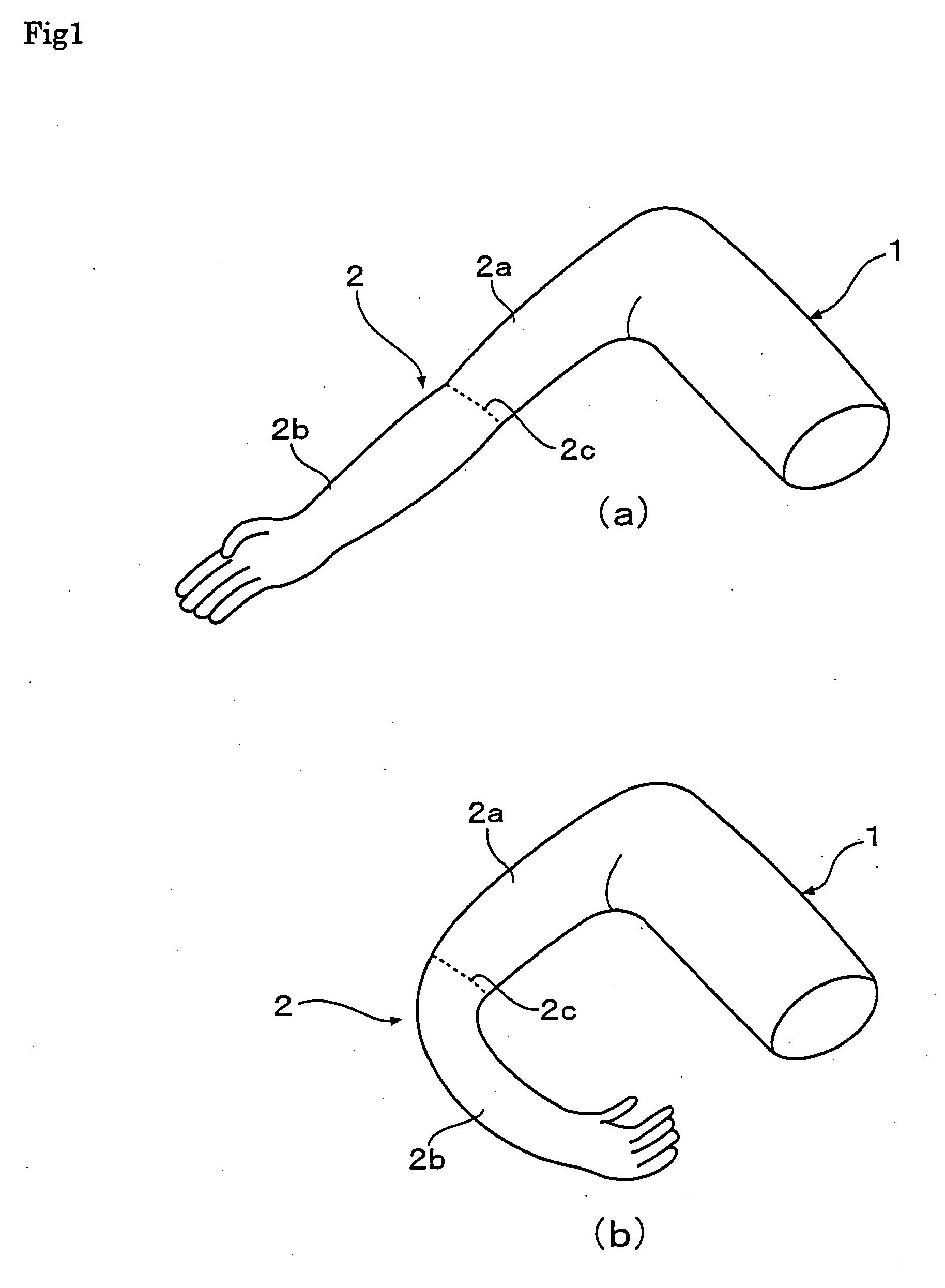
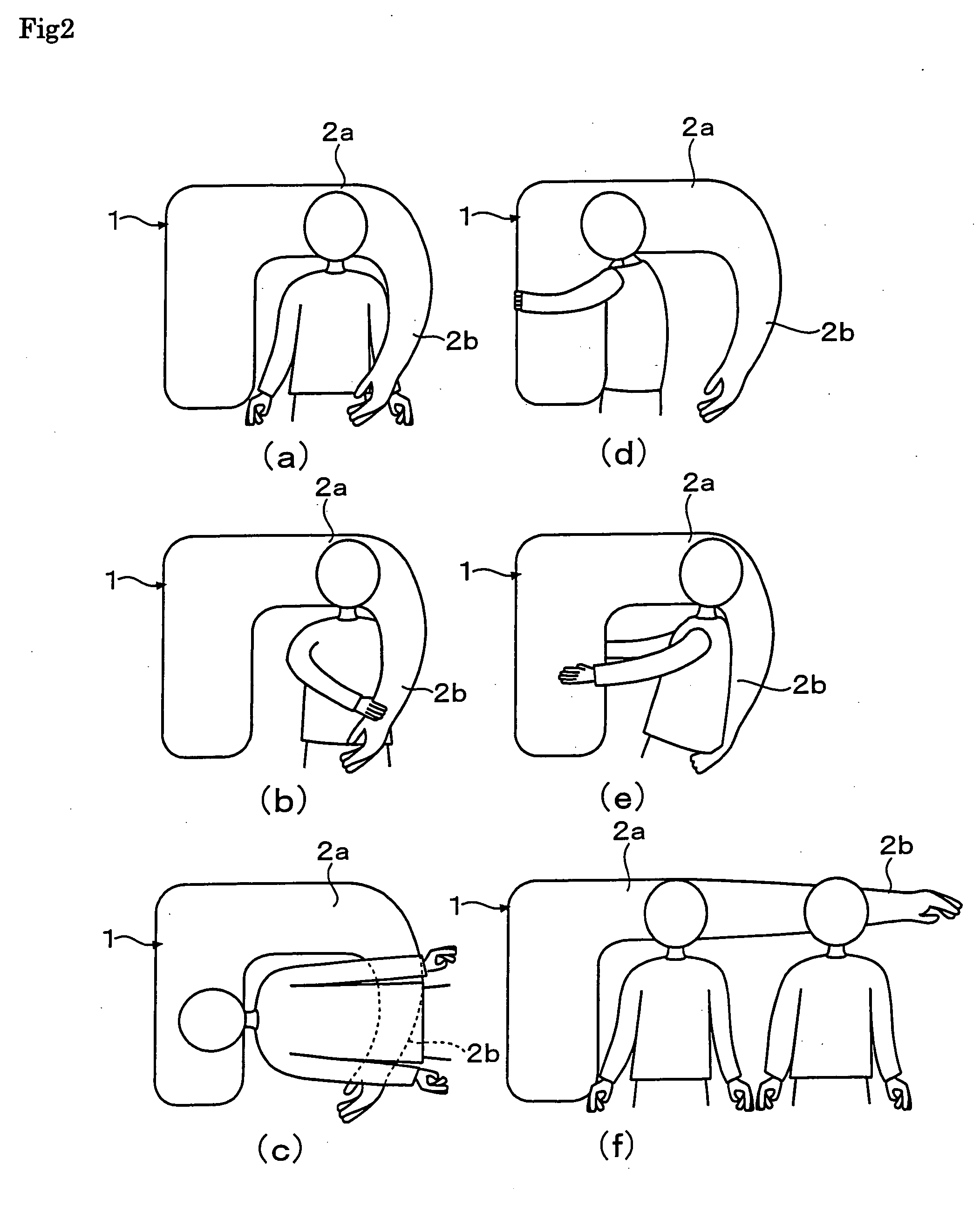
Substitutive pillow
The present invention provides a substitutive pillow, which feels like a real arm pillowing one's head and provides a variety of modes of use. In a substitutive pillow formed in mimicry of human torso and arm, the arm part includes an upper arm part 2a mimicking a human upper arm and a forearm part 2b mimicking a human forearm which is capable of bending relatively with the upper arm part 2a. By this structure, this pillow feels like a real arm pillowing one's head and gives unity and ease, with which the users sleep well. Further, it can be suitable for various modes of use.
Owner:ACTINTERIOR CORP
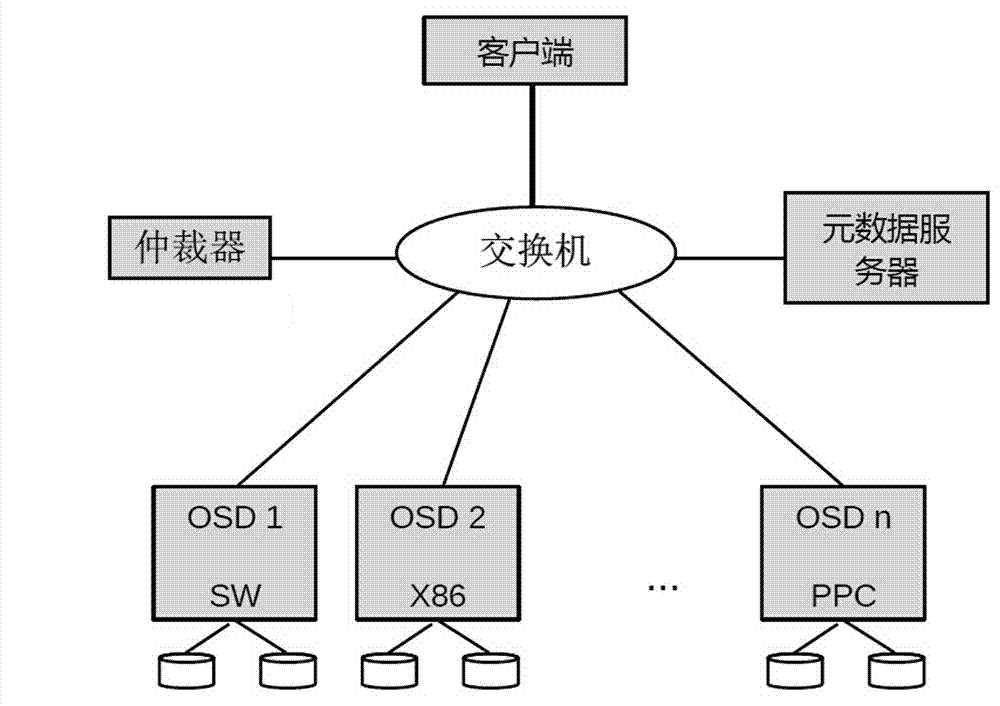
Distributed storage system construction method based on mimicry defense
ActiveCN111031096AData request impactPrevent tamperingTransmissionEnergy efficient computingOperational systemSource code
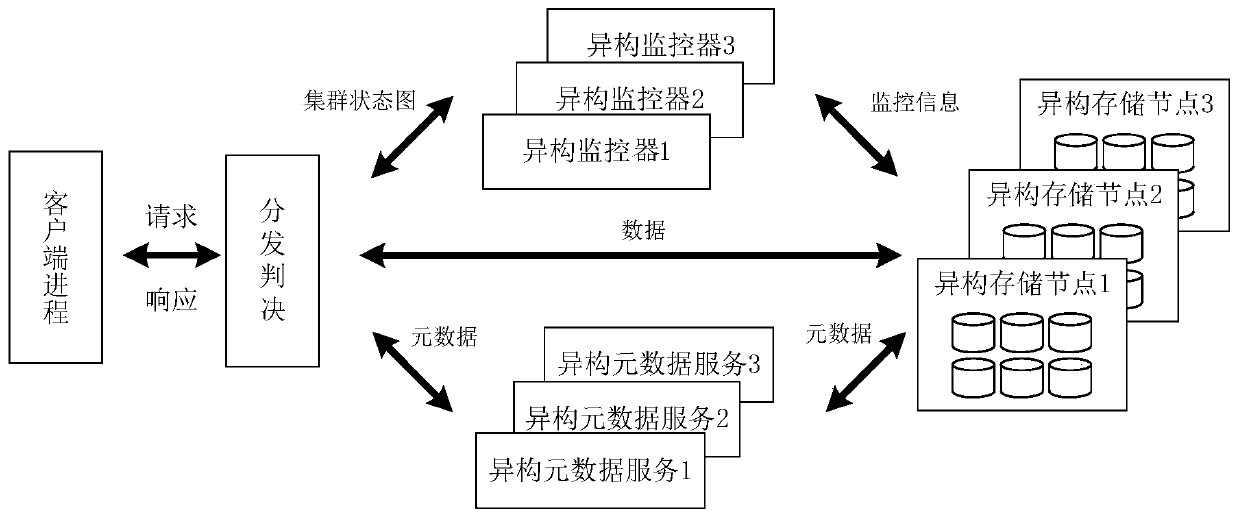
The invention provides a mimicry defense-based distributed storage system construction method. The mimicry defense-based distributed storage system construction method comprises the steps of source code transplantation: carrying out source code transplantation on a distributed storage system; storage system building: building a distributed storage system based on mimicry defense; system write operation: performing distributed storage system write operation based on mimicry defense; system reading operation: performing distributed storage system reading operation based on mimicry defense; andconsistency guaranteeing: guaranteeing the data consistency of the distributed storage system based on mimicry defense. According to the invention, heterogeneous redundancy design is carried out on aclient process, a monitor, metadata service and object storage service, so that the data are prevented from being tampered and damaged, and the system security is improved.
Owner:EAST CHINA INST OF COMPUTING TECH
Mimicry judgment method, device and system
ActiveCN109450900AImprove effectivenessImprove securityTransmissionLookup tableCommunications protocol
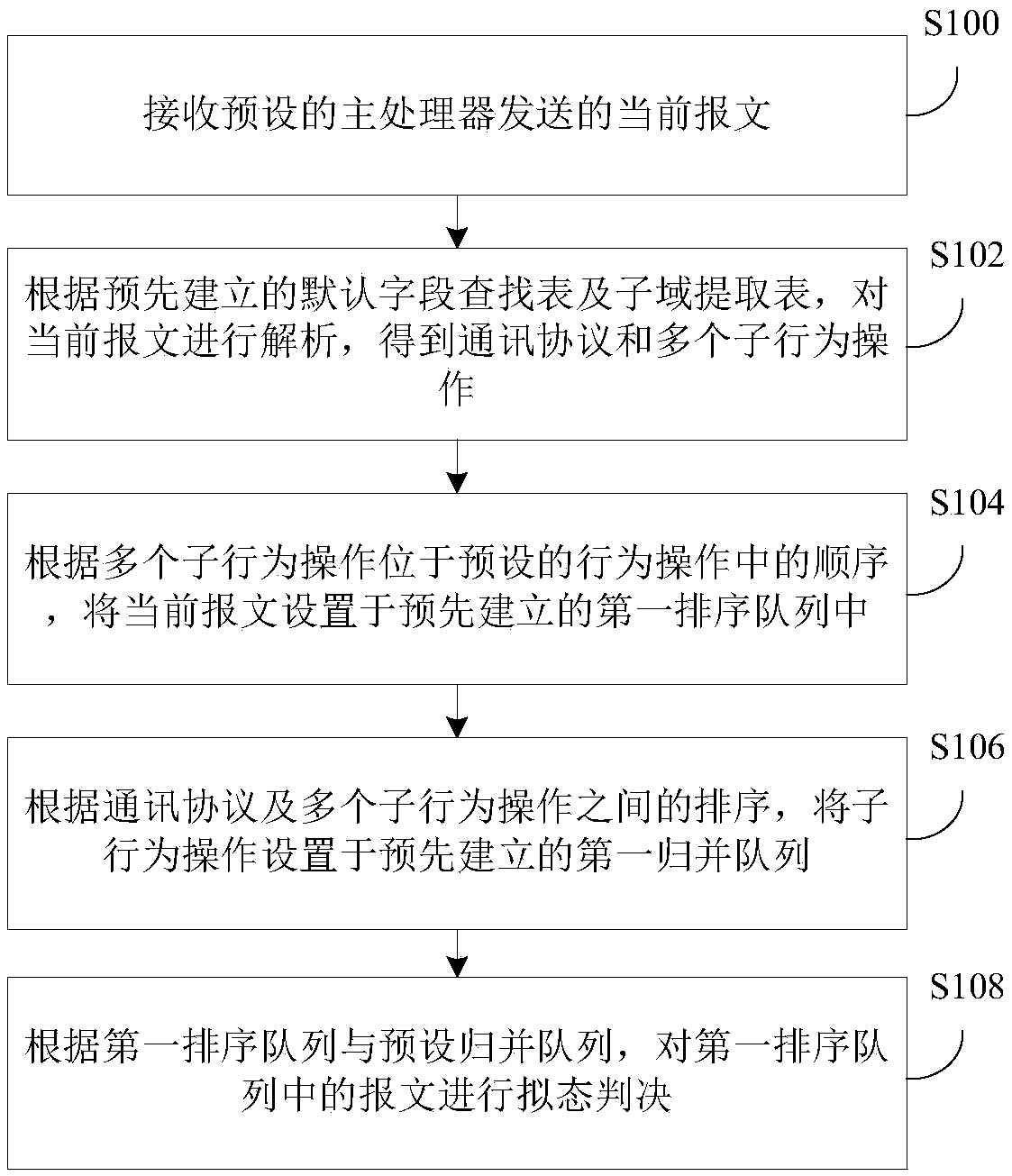
The invention provides a mimicry judgment method, device and system, wherein the method is applied to a chip in connection with a heterogeneous multi-core processor. The method comprises the followingsteps: receiving a preset current message sent by a main processor; according to a preestablished default field lookup table and a subfield extraction table, analyzing the current message and obtaining a communication protocol and a plurality of sub-behavior operations; according to the sequence of the plurality of sub-behavior operations located in the preset behavior operation, arranging the current message to a preestablished first ordered queue; according to sorting between the communication protocol and the plurality of sub-behavior operations, arranging the sub-behavior operation to a preestablished first merging queue; and performing mimicry judgment on the message in the first ordered queue according to the first ordered queue and the preset merging queue. The mimicry judgment method, device and system in the invention improves the validity of the mimicry judgment, thereby improving the safety of the network space.
Owner:天津市滨海新区信息技术创新中心 +1
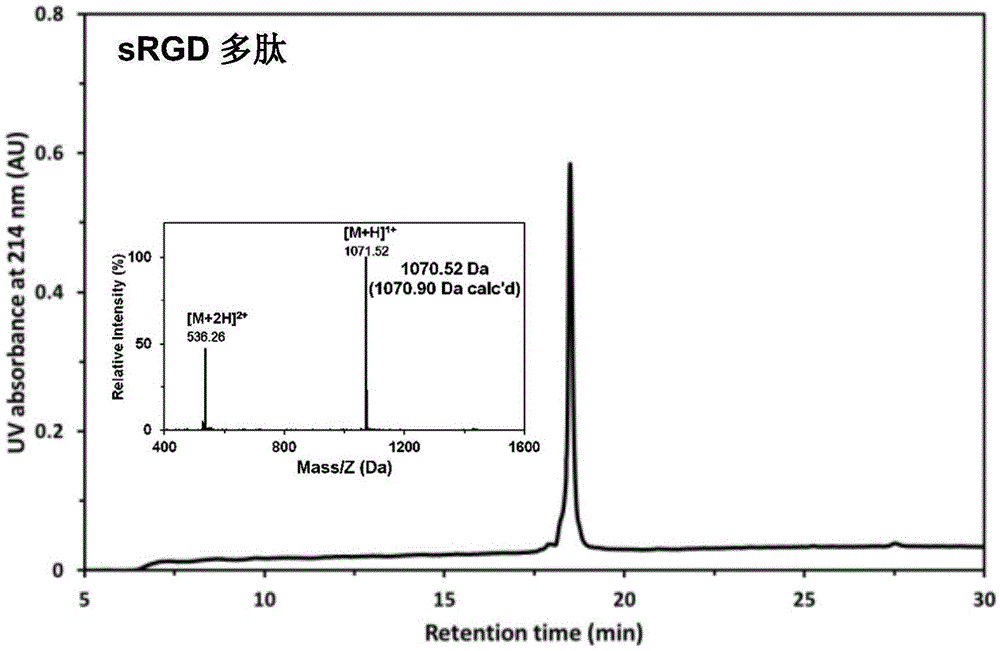
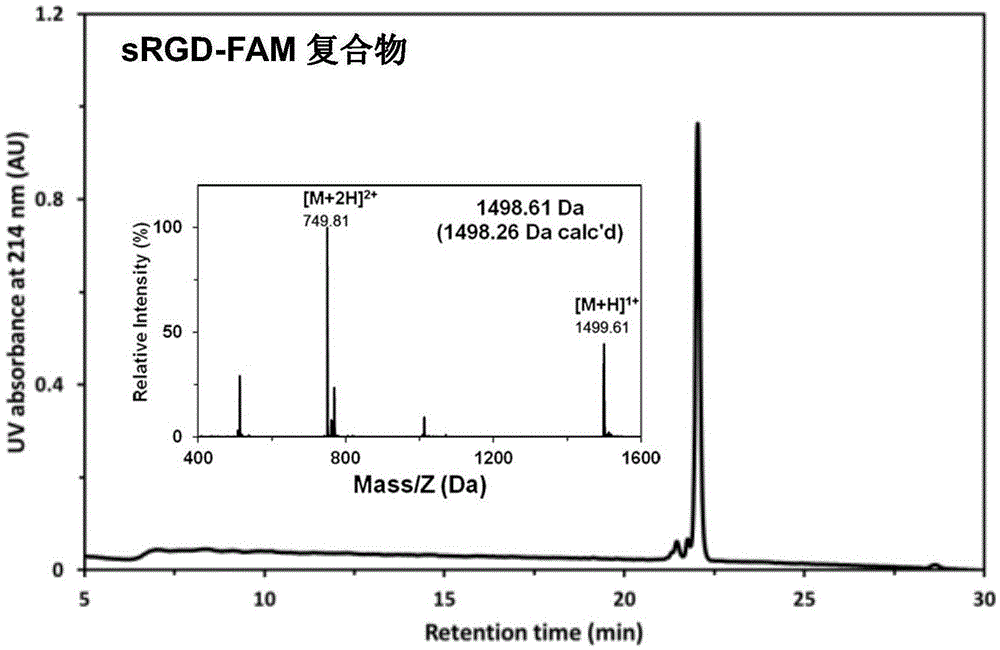
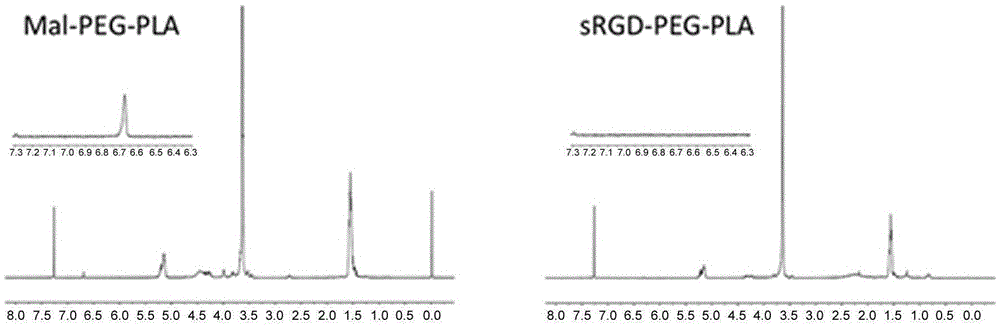
Stapled-RGD polypeptide, and applications thereof in tumor targeting delivery
InactiveCN106699845AStrong penetrating powerPowerfulOrganic active ingredientsPeptidesTumor targetBinding peptide
The invention belongs to the field of pharmacology, and relates to stapled-RGD polypeptide, and applications thereof in tumor targeting delivery. Multifunctional targeting polypeptide molecule stapled-RGD with high combination activity with integrin and biological membrane barrier penetration capacity is designed and prepared based on binding peptide cyclization technology; and preparation of fluorescein, drugs, and high molecule carriers modified by the multifunctional targeting polypeptide molecule stapled-RGD, and applications of the fluorescein, the drugs, and the high molecule carriers in tumor imaging and construction of targeted therapy targeted drug delivery systems are disclosed. It is shown by results that specific uptaking of model drugs carried by stapled-RGD by positive cells, tumor mimicry vessels, and tumor ball tissues of expressed integrin is realized, higher tumor targeting capacity, imaging functions, and membrane barrier cell penetration capacity are achieved; nano targeted drug delivery systems constructed by the high molecule carriers modified by stapled-RGD can be used for delivering carried model drugs to target tissues, antitumor drug effect is improved obviously; and stapled-RGD possesses a promising application prospect in mediating drugs, nano targeted drug delivery system membrane barrier penetration, active target searching, tumor diagnosis, and targeted therapy.
Owner:FUDAN UNIV
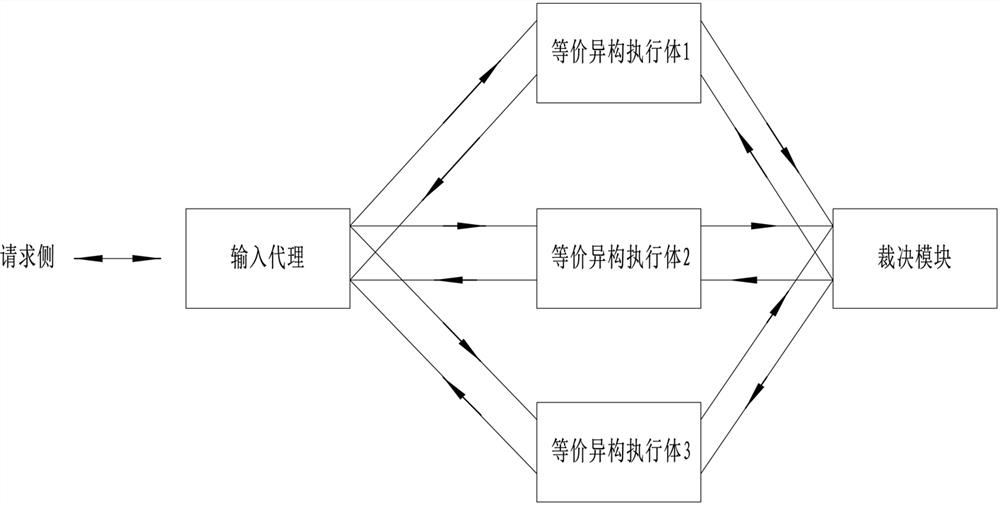
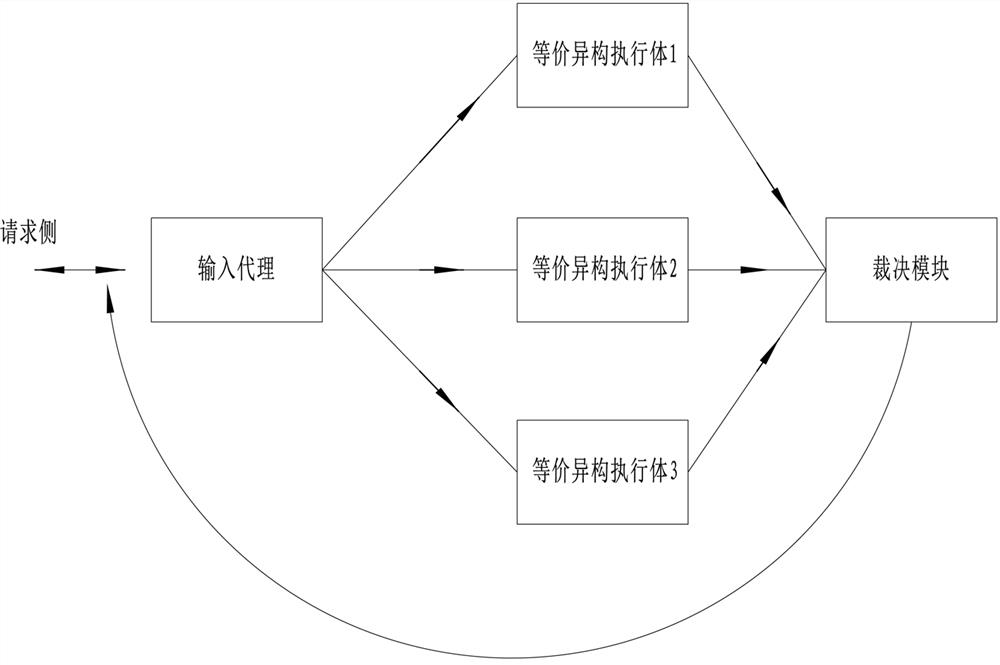
Annular mimicry architecture without protocol state, defense method and readable storage medium
The invention provides a mimicry defense method for an annular mimicry architecture without a protocol state. The method comprises the following steps that: a request side sends request information toan input agent, and the input agent copies and distributes the request information to each equivalent heterogeneous execution body through a one-way communication channel after normalizing a protocol; each equivalent heterogeneous execution body processes the request information and sends response information to a judgment module through a one-way communication channel; and the judgment module judges the response information, sends the response information to a request side through a one-way request side communication channel if judgment succeeds, and sends the judgment information to a feedback controller if judgment fails so as to adjust the state of each heterogeneous execution body. According to the mimicry defense method, the requirement on the input agent is reduced, the structure of the agent is simplified, the agent is prevented from becoming a performance bottleneck, the problem that the agent is easily attacked is solved, and the security of the whole mimicry architecture isimproved.
Owner:河南信大网御科技有限公司 +1
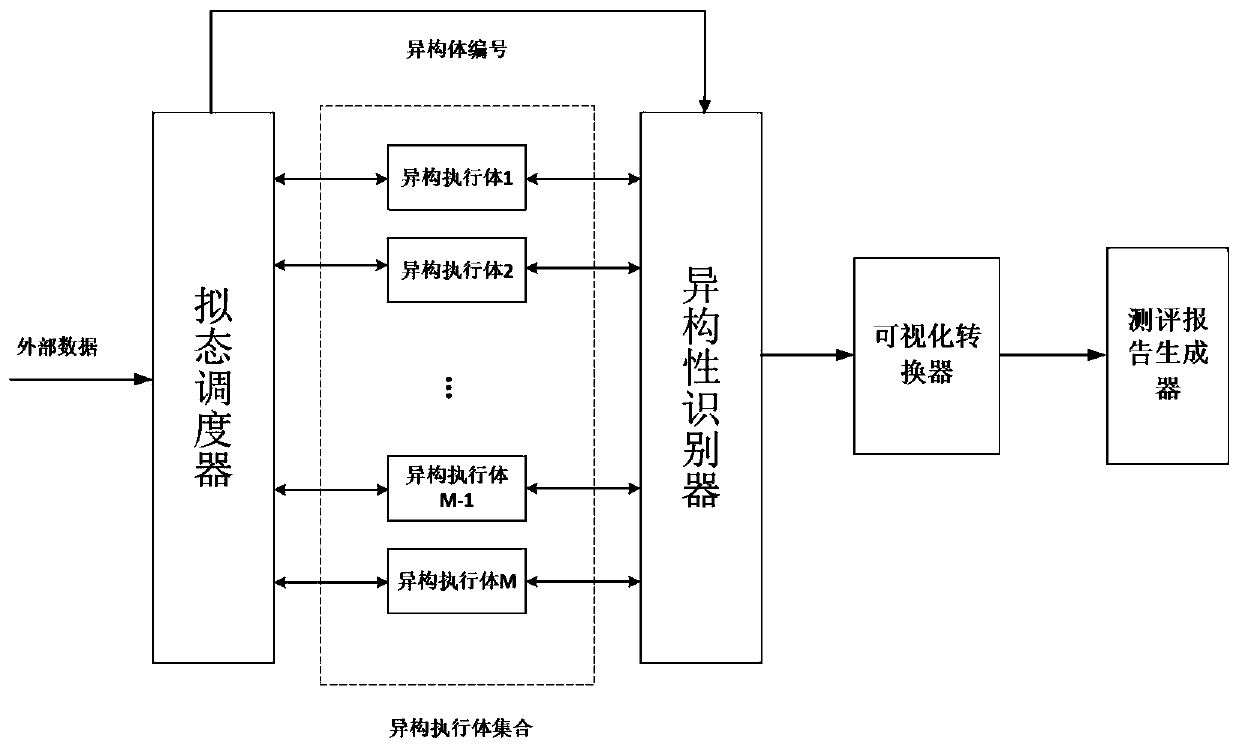
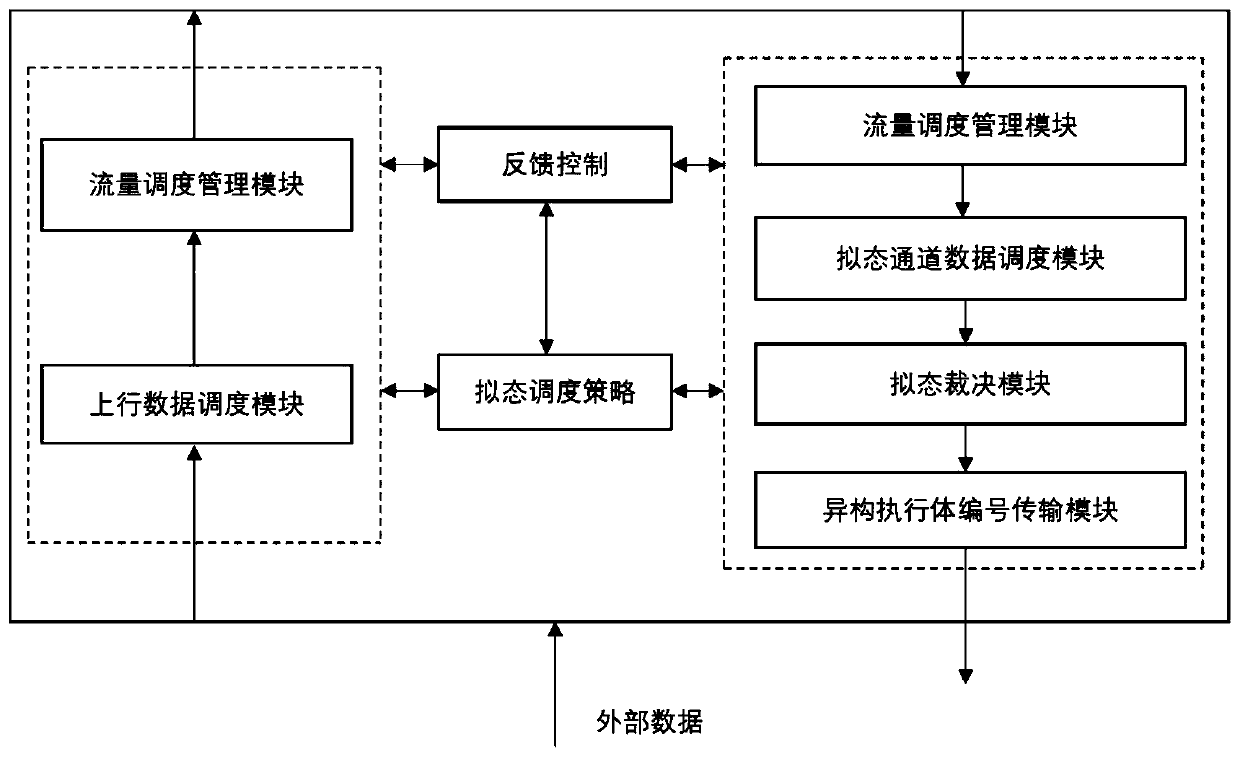
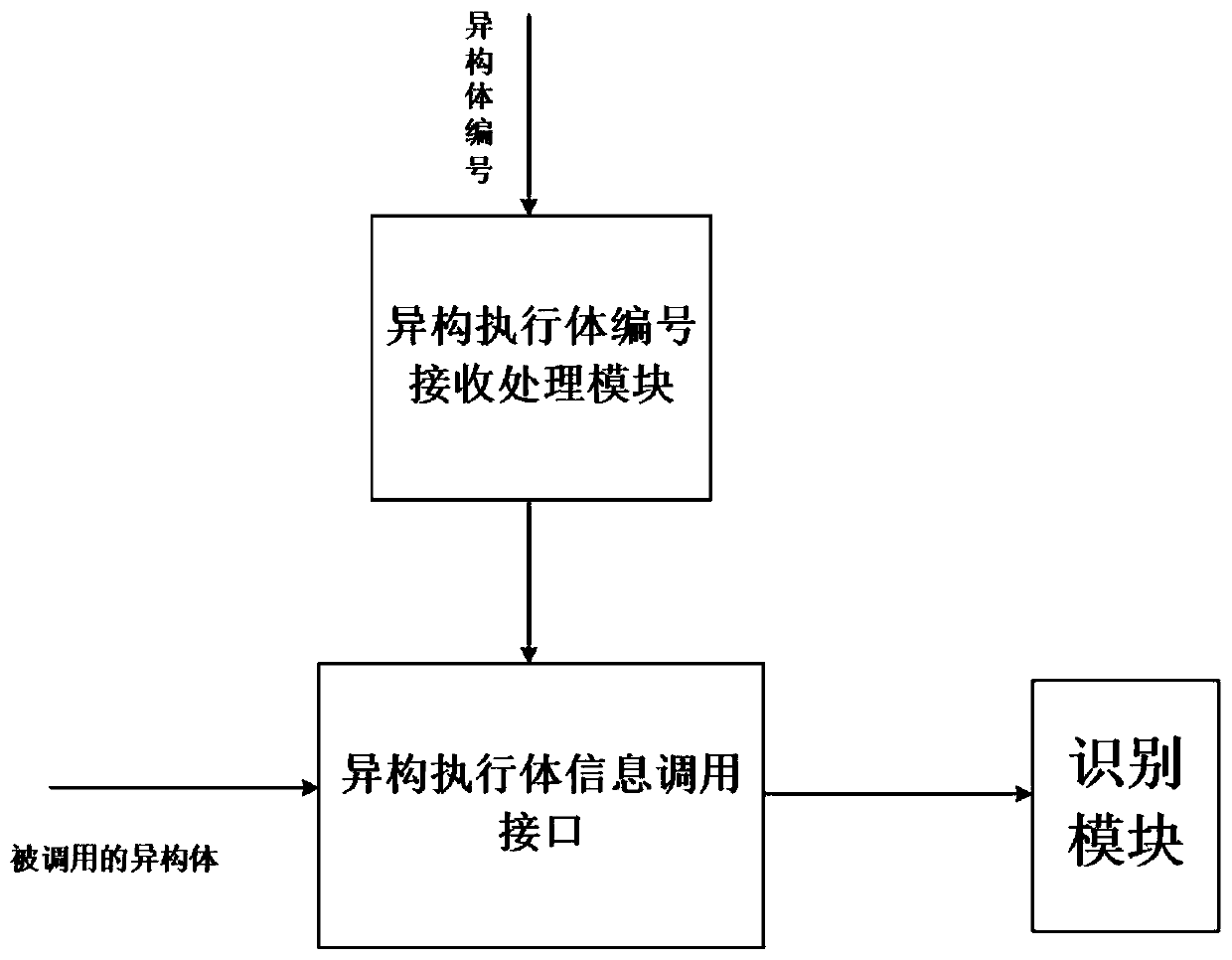
Heterogeneity testing device and method based on a DHR architecture mimicry defense platform
InactiveCN110445787AVerify securityEfficient and stableData switching networksTest fixtureComputer science
The invention provides a heterogeneity testing device and method based on a DHR architecture mimicry defense platform. The device part comprises a mimicry scheduler, a heterogeneity executor set and aheterogeneity recognizer. The device disclosed by the invention is based on the existing test method for verifying the characteristics of the mimicry system; verification and judgment for the types of the heterogeneous executors are added, the stability, safety and performance rationality of the heterogeneous executors can be verified more efficiently, and a detailed test report is automaticallygenerated, so that the requirement for evaluating the heterogeneity of the mimicry safety information system is met.
Owner:EAST CHINA INST OF COMPUTING TECH
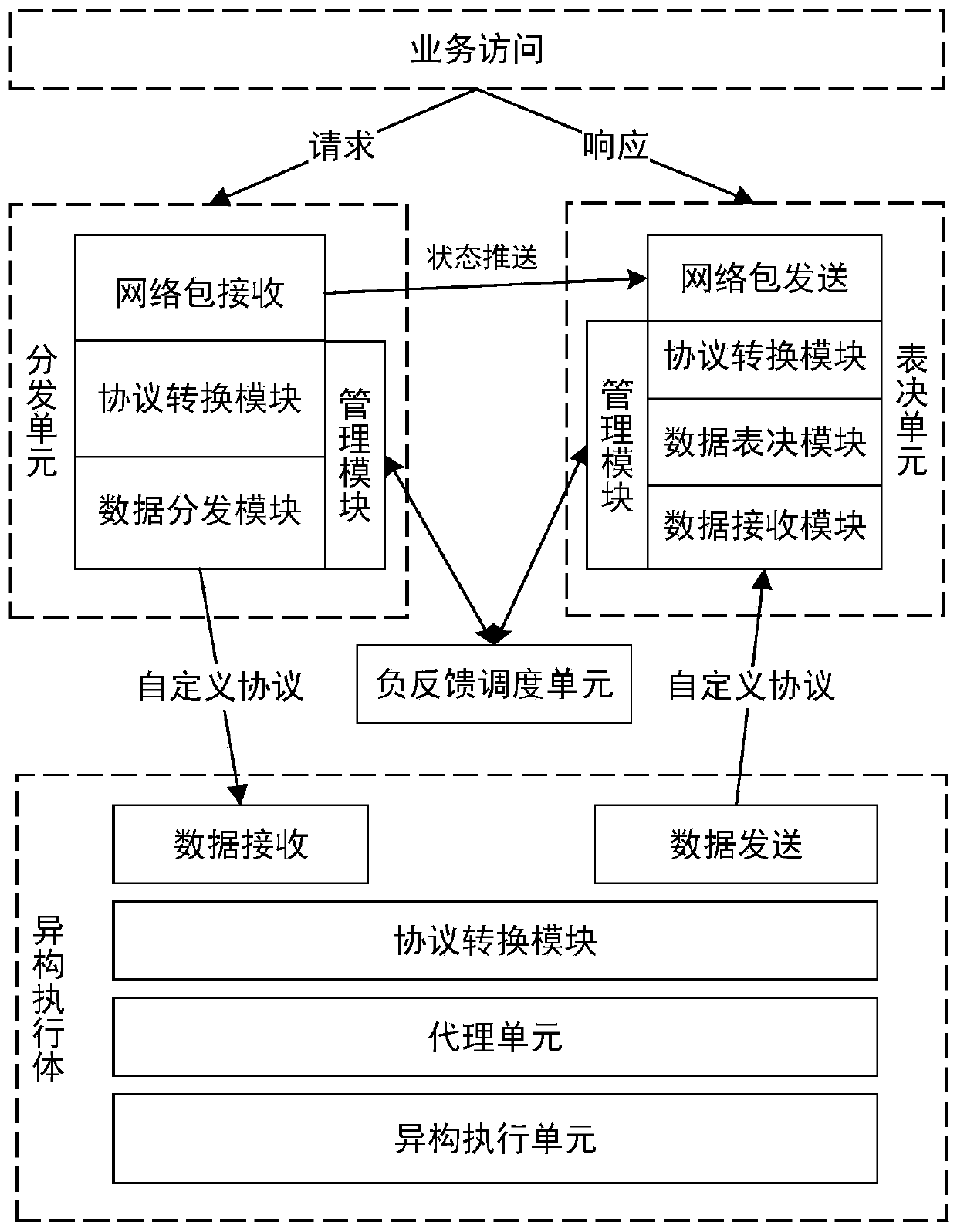
Universal mimicry distribution voting scheduling device and method based on user-defined protocol
The invention discloses a universal mimicry distribution voting scheduling device and method based on a user-defined protocol. The universal mimicry distribution voting scheduling device comprises a distribution unit, a heterogeneous executive body, a voting unit and a negative feedback scheduling unit; the distribution unit comprises a network packet receiving module, a protocol conversion module, a data distribution module and a management module; the heterogeneous execution body comprises a data receiving module, a protocol conversion module, a heterogeneous execution unit and a data sending module; and the voting unit comprises a data receiving module, a data voting module, a protocol conversion module, a network packet sending module and a management module. The invention provides a set of mimicry structure framework with universality, which is beneficial to rapidly, simply and conveniently developing various mimicry defense devices; compared with a traditional defense mechanism,the security can be greatly improved, so that higher-level security protection can be implemented on the system; and the distribution unit and the voting unit are separated, so that the safety of thevoter can be improved, the overall defects of the mimicry defense equipment are overcome, and the system-level safety is further guaranteed.
Owner:上海拟态数据技术有限公司 +1
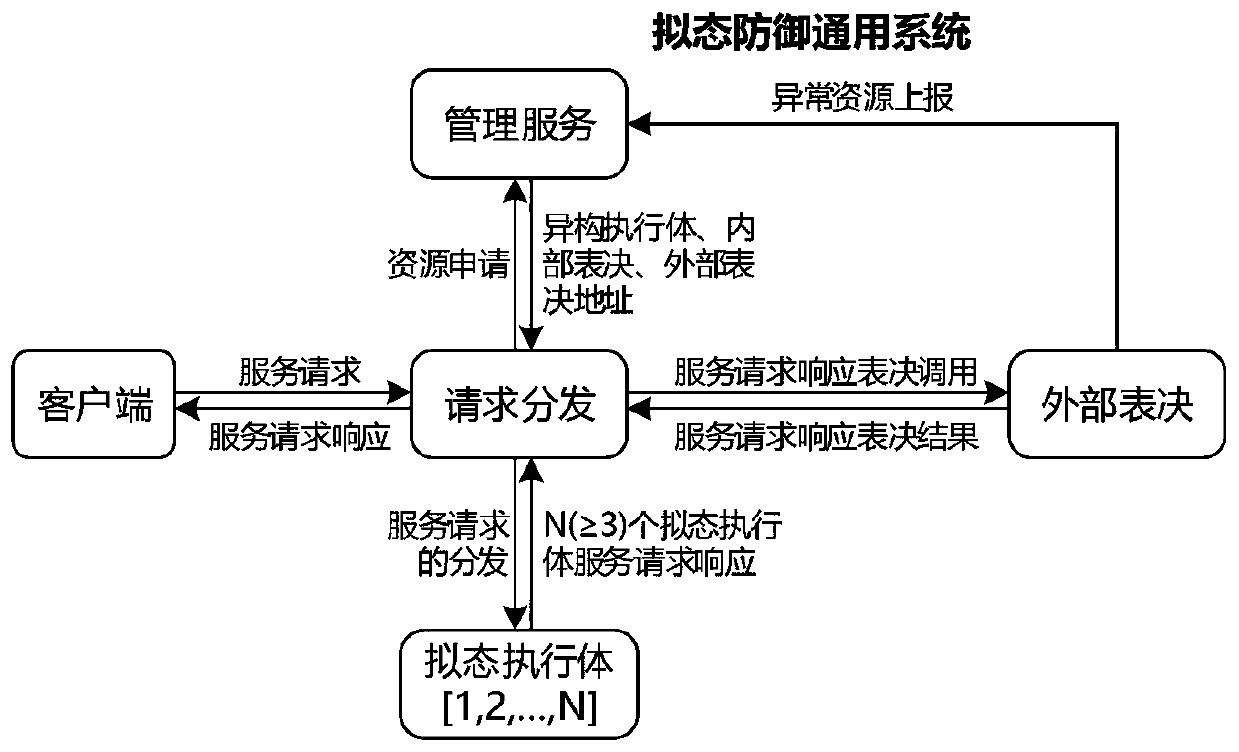
Information system-oriented mimicry defense system and method, and medium
The invention provides an information system-oriented mimicry defense system, which comprises a request distribution module for receiving a request sent by an information system user, distributing therequest to a mimicry execution module, and forwarding a voted response result of the mimicry execution module to the information system user; a mimicry execution module, responding to the request toobtain a response result; an external voting module, used for carrying out consistency voting on the response result from the mimicry execution module; and a management service module used for managing and scheduling the mimicry execution module. According to the invention, heterogeneous maximization of the mimicry execution module is realized through dynamic scheduling of the mimicry execution module by the management service. Entrance-level security protection executed on a service request is completed through a traditional defense means, and result-level security protection is completed through external voting. Entrance-level and result-level security protection can realize active defense by most of attack means.
Owner:EAST CHINA INST OF COMPUTING TECH
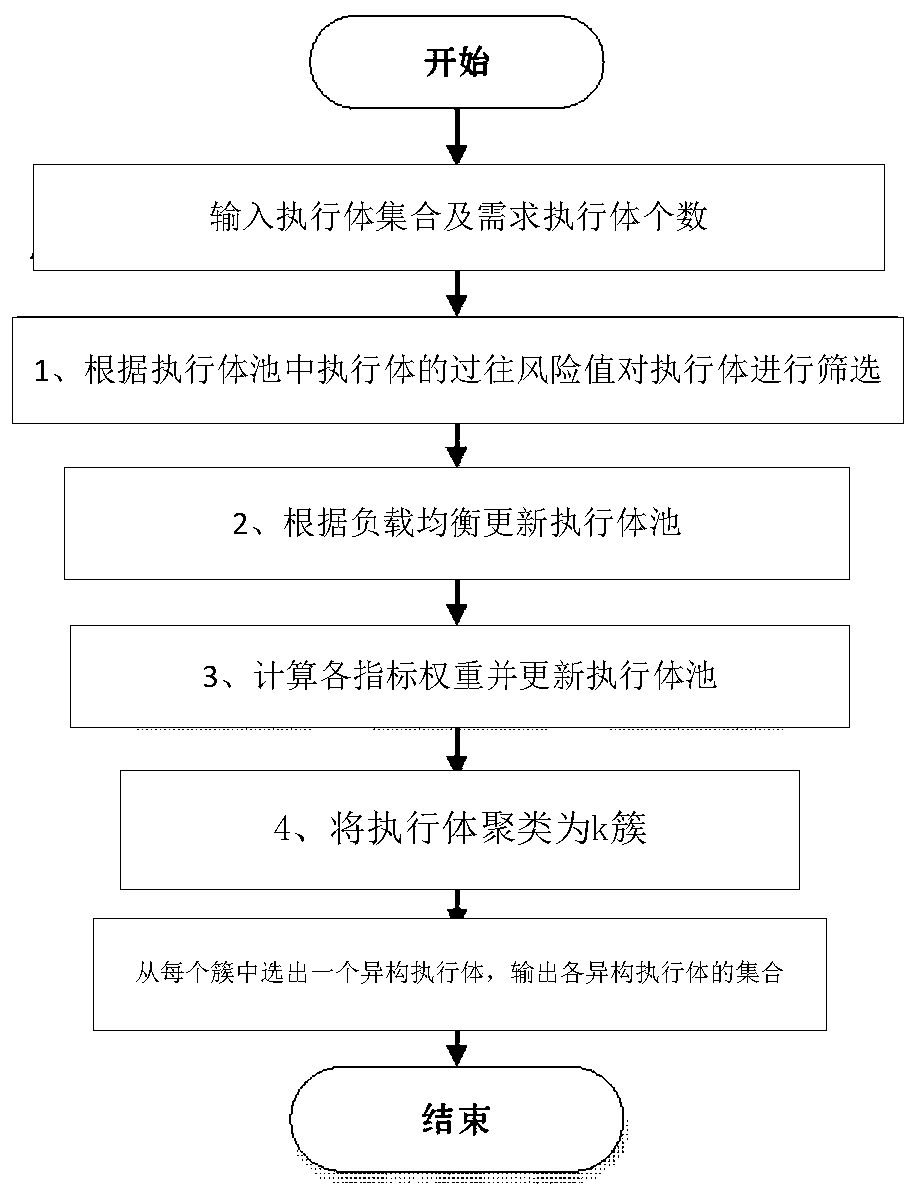
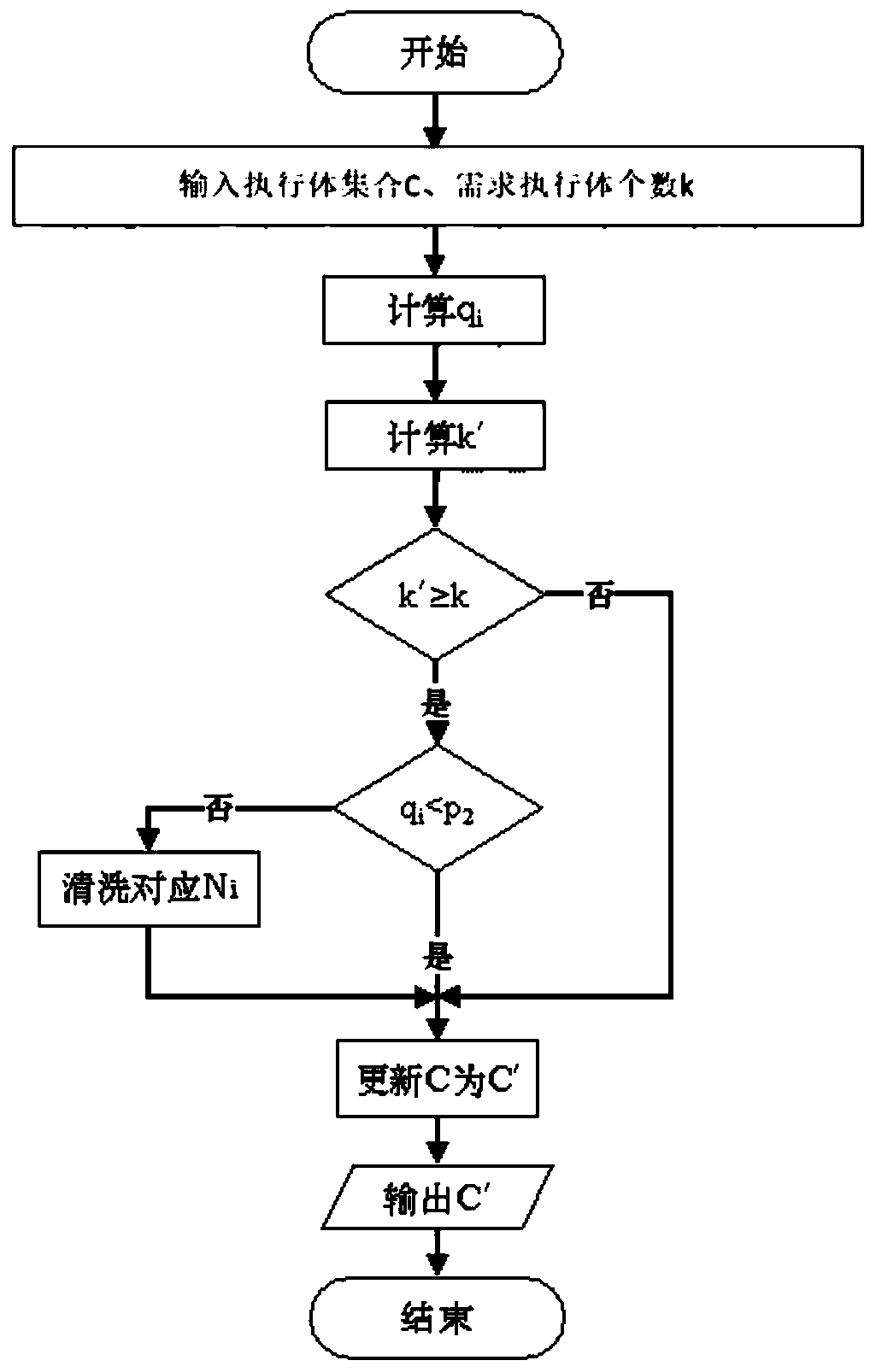
Mimicry scheduling method and system for general operation environment and medium
ActiveCN110673951AIncrease the difficultyMaximize heterogeneityResource allocationManagement processMimicry
The invention provides a mimicry scheduling method and system for a general operation environment and a medium, and the method comprises: a data preprocessing step of inputting an execution body set Cand the number k of required execution bodies, carrying out the preliminary screening of the execution body set C according to the historical risk value of each execution body in the execution body set C, and obtaining an updated execution body set C'; and a load balancing screening step of calculating the performance and load of the node where the executor is located according to the obtained updated executive set C', calculating the load weight and load difference of the node, guiding the selection of an alternative executor set when a new task arrives through the load weight, calculatingthe probability that each executor in the alternative executor set allocates the task through the load difference, and selecting a candidate executor set C'' in combination with heterogeneous features. According to the invention, mimicry is applied to a general operation environment, heterogeneous maximization of a distribution management process is realized, and isomorphism errors are avoided.
Owner:EAST CHINA INST OF COMPUTING TECH
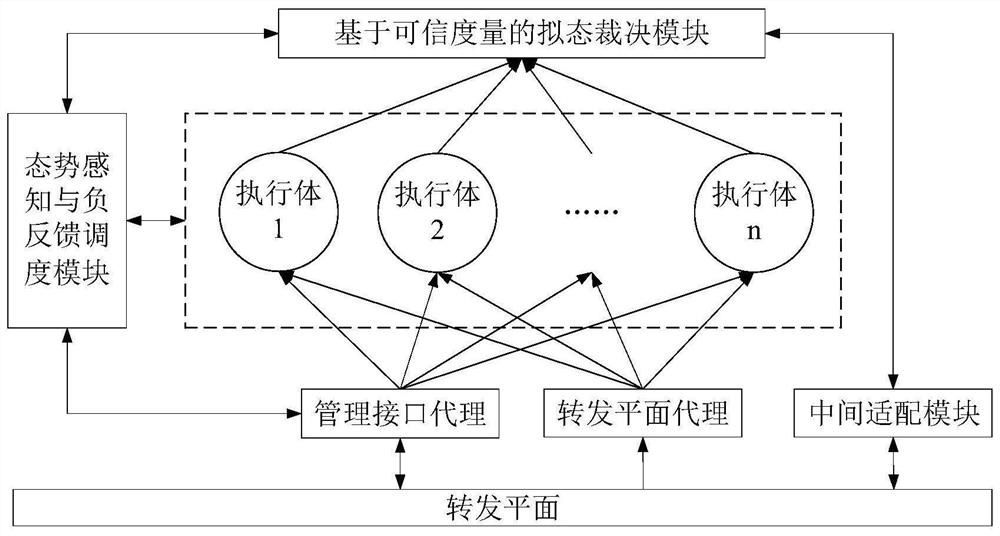
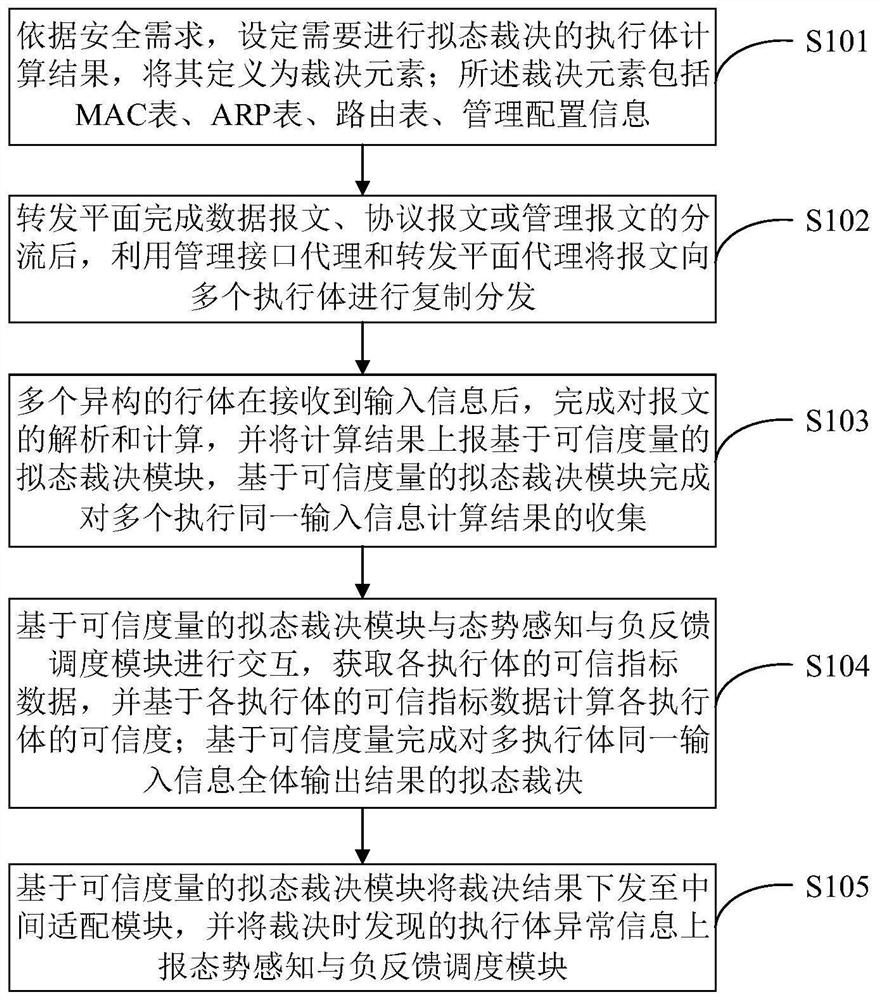
Mimicry switch judgment system and method based on trusted measurement
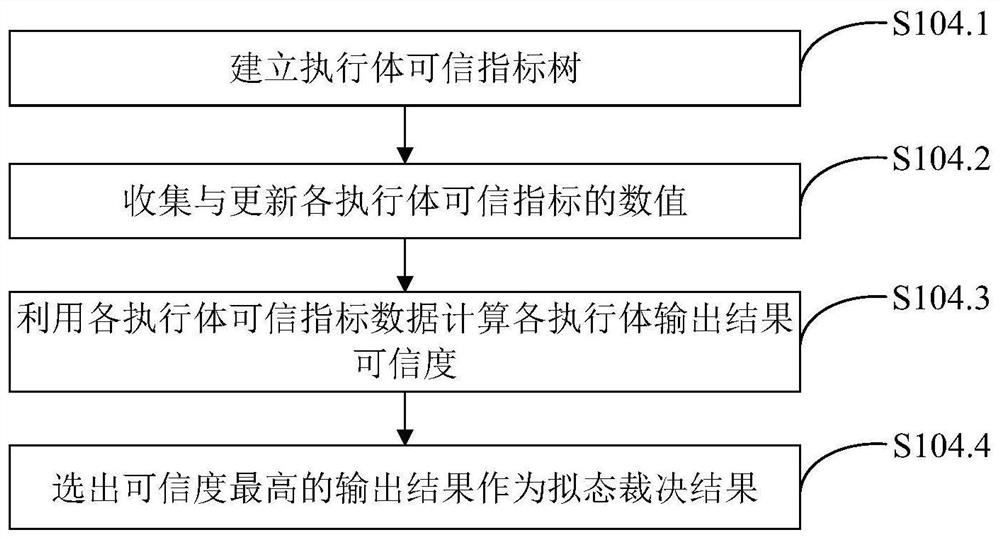
ActiveCN111884996AReduce security threatsImprove the level of security protectionData switching networksComplex mathematical operationsDecision systemInformation Harvesting
The invention belongs to the technical field of network security, and discloses a mimicry switch decision system based on trusted measurement, and the system comprises a forwarding plane, a managementinterface agent, an intermediate adaptation module, a forwarding plane agent, a plurality of heterogeneous actuators, a trusted measurement-based mimicry decision module and a situation awareness andnegative feedback scheduling module. The invention further discloses a mimicry switch judgment method based on trusted measurement. The mimicry switch judgment method comprises the steps: setting mimicry switch judgment elements; distributing input information; collecting output information; carrying out mimicry decision based on credibility measurement; issuing a judgment result, sensing the threat situation of the switch, and scheduling an executor; the mimicry decision based on credibility measurement comprises the following steps: establishing an executive credible index tree; collectingand updating the credible index data of the executive body; calculating the credible weight of the output result of each executive body; and calculating the credibility of each output result. The method can effectively reduce the influence of unknown loopholes and potential backdoors, and improves the safety protection level of a local area network.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
Mimicry honeypot fingerprint confusion system and method and SDN network architecture thereof
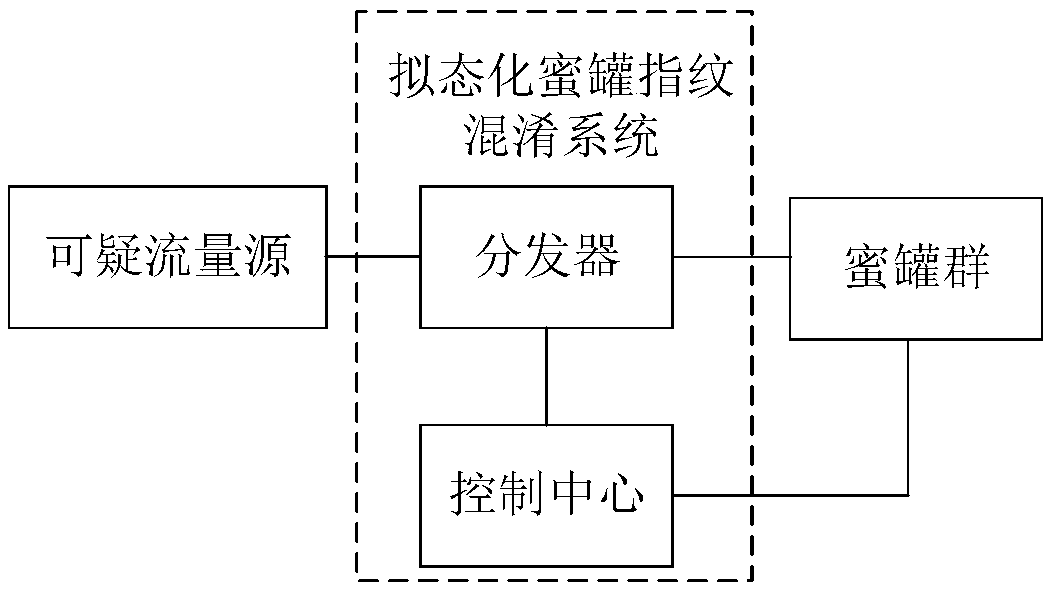
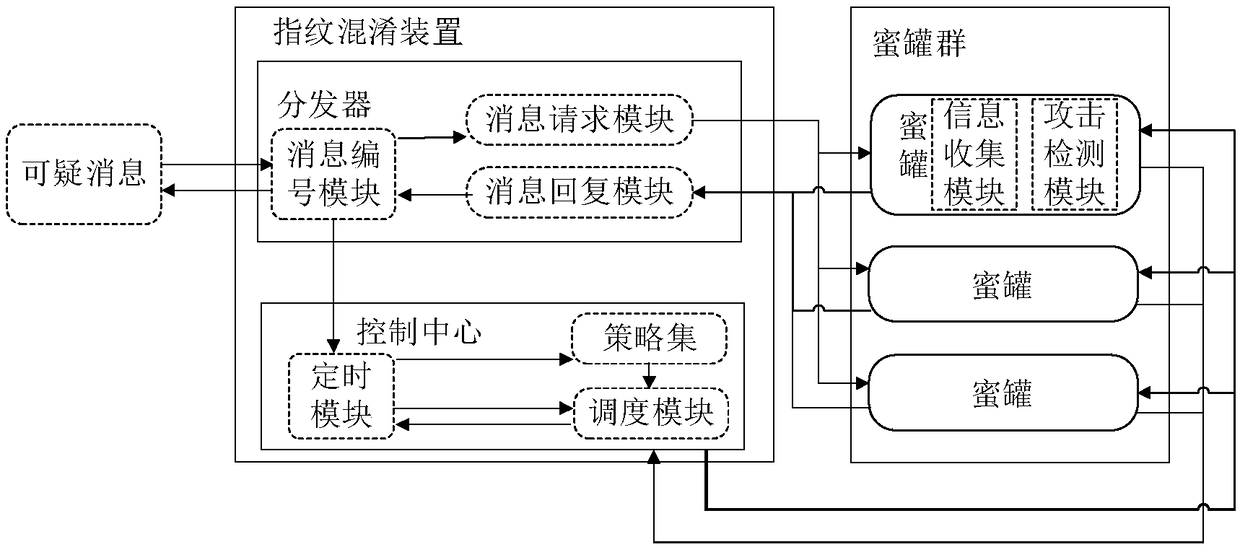
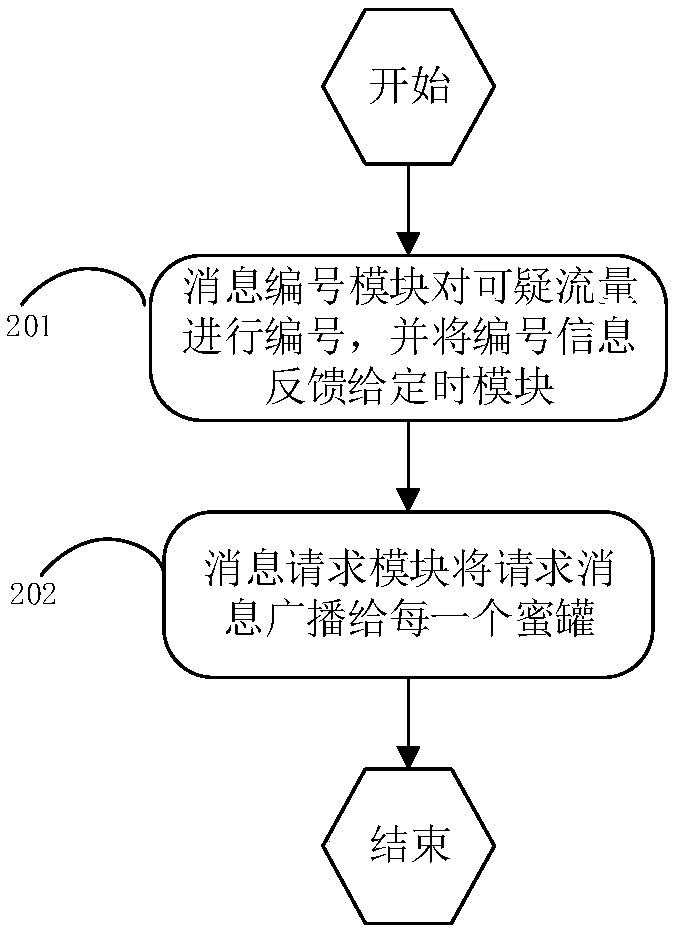
ActiveCN109246108AReduce fingerprint recognition rateAvoid influenceTransmissionCommunications securityNetwork architecture
The invention belongs to the technical field of communication safety, and especially relates to a mimicry honeypot fingerprint confusion system and method and an SDN network architecture thereof. Thesystem comprises a control center which is deployed on a distributor and is used for maintaining the working state of a honeypot, dynamically generating a honeypot scheduling rule according to the suspicious traffic behavior characteristics fed back by the honeypot, and starting and closing the corresponding honeypot according to the scheduling rule; a distributor which is deployed between a honeypot group and a suspicious traffic source and is used for receiving the outputted suspicious traffic, recording the suspicious traffic, broadcasting the suspicious traffic to each honeypot in the honeypot group, receiving response messages from the honeypots, and transmitting the response messages to the suspicious traffic source as false response messages for replying to a corresponding attacker,wherein the honeypot group contains multiple types of honeypots. The method utilizes a dynamic transformation mechanism to comprehensively schedule a plurality of honeypots, reduces the influence onthe safety performance of the network from a condition that a single honeypot system is controlled by the attacker, and improves the reliability of the entire system.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
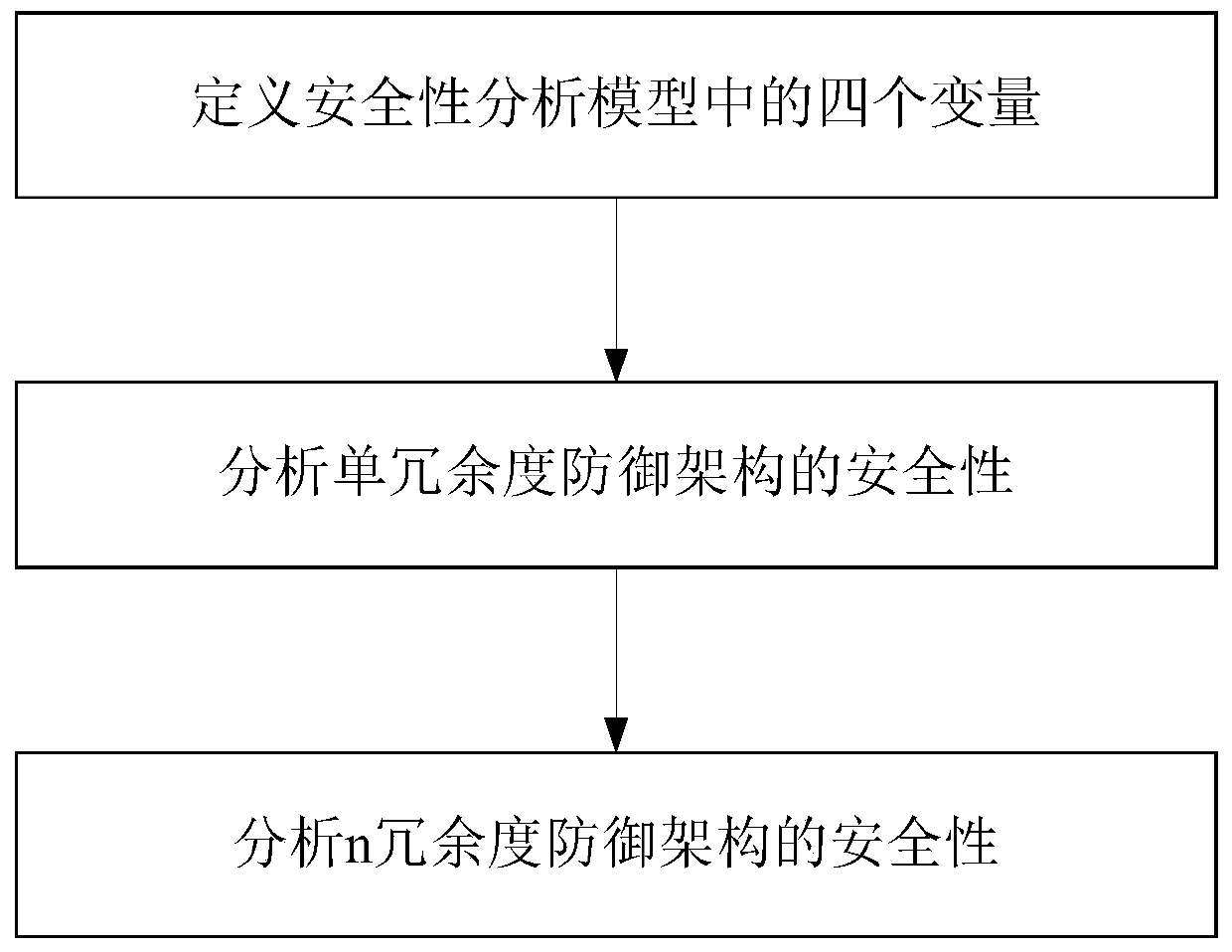
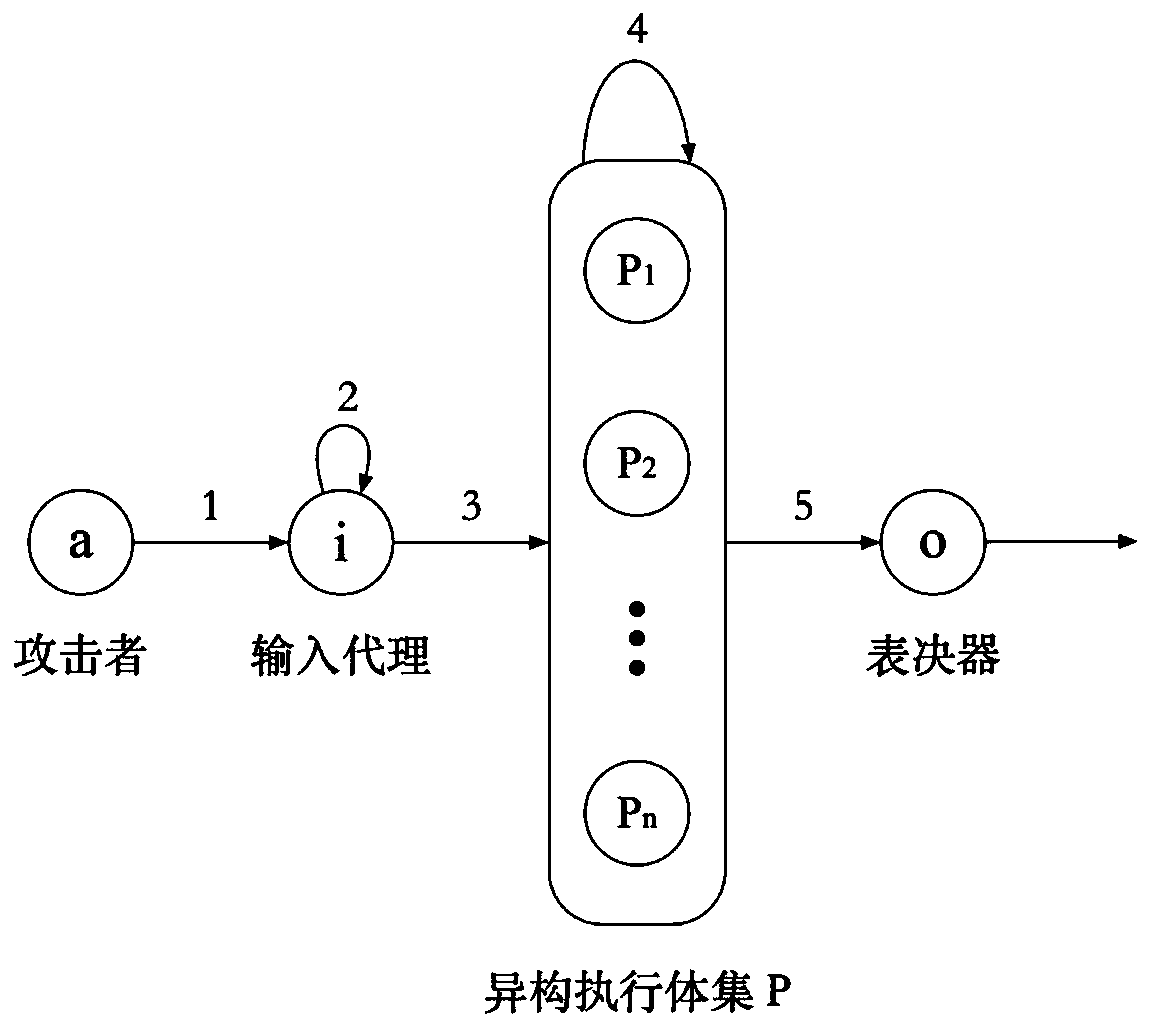
Security analysis method for mimicry defense architecture
ActiveCN110830462AAnalytical results are reliableAnalysis results are efficientData switching networksSecurity analysisMimicry
The invention discloses a security analysis method for a mimicry defense architecture. The method comprises the following steps: defining the dynamic transformation period of an executor in a securityanalysis model, the time required for successful attack implementation, the probability that the executor shows difference after being attacked, and the probability that an attacker successfully transfers the attack; analyzing the security of the single redundancy defense architecture; obtaining the probability of invading the input proxy component, the probability that the attack continues to stay in the input agent component, the probability that the attack invades into the heterogeneous execution body set from the input agent component, the probability that the attack continues to stay inthe heterogeneous execution body set, the probability that the attack invades into the voter component from the heterogeneous execution body set and the probability that an attacker successfully invades into the voter component from the input agent component are set; and analyzing the security of the n redundancy defense architecture to obtain general values corresponding to the six probability values. According to the method, different parameters are used for analyzing the security defense effectiveness of the mimicry defense system, and a theoretical analysis basis is provided for the security of the mimicry defense model.
Owner:NANJING UNIV OF SCI & TECH
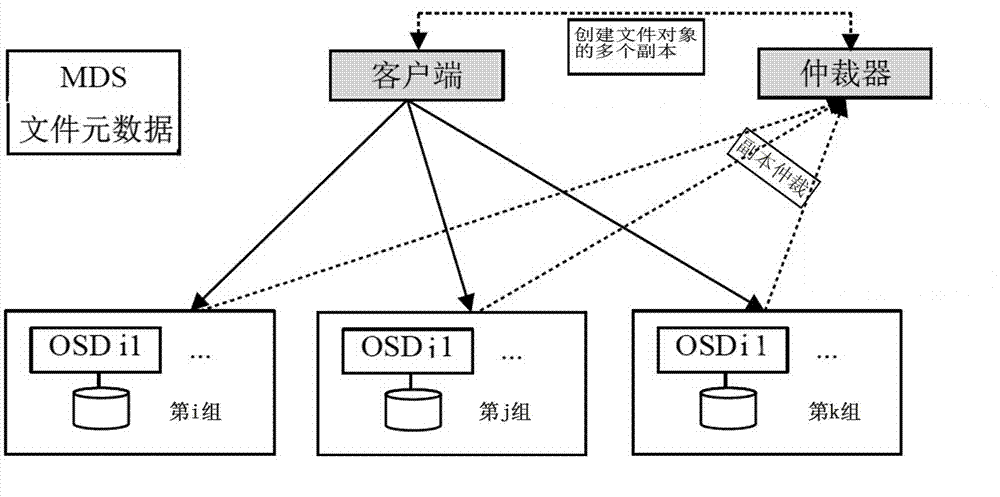
Mimicry tamper-proof method of distributed file system
InactiveCN104766025ATampering smallIncrease randomnessDigital data protectionSpecial data processing applicationsTamper resistanceDistributed File System
The invention discloses a mimicry tamper-proof method of a distributed file system and accordingly the problem that files are tampered with in the distributed file system in the prior art is solved. The mimicry tamper-proof method comprises the following steps of step 1, creating a plurality of copies for every file object to be written in different types of data nodes respectively and step 2, adding an arbitrator to evaluate every copy, selecting reserved copies according to different purposes respectively and deleting the other copies. According to the mimicry tamper-proof method of the distributed file system, a hijacker can only obtain file objects in a certain data node even if the data node is hijacked; every file object is only a fragment of an actual file and accordingly the hijacker is difficult to determine a file to which the object belongs and the position of the object in the file and accordingly the hijacker is difficult to accurately tamper with the file; the modification on the file objects by the hijacker does not necessarily adopted by the arbitrator and accordingly the security of the file system is greatly improved.
Owner:THE PLA INFORMATION ENG UNIV
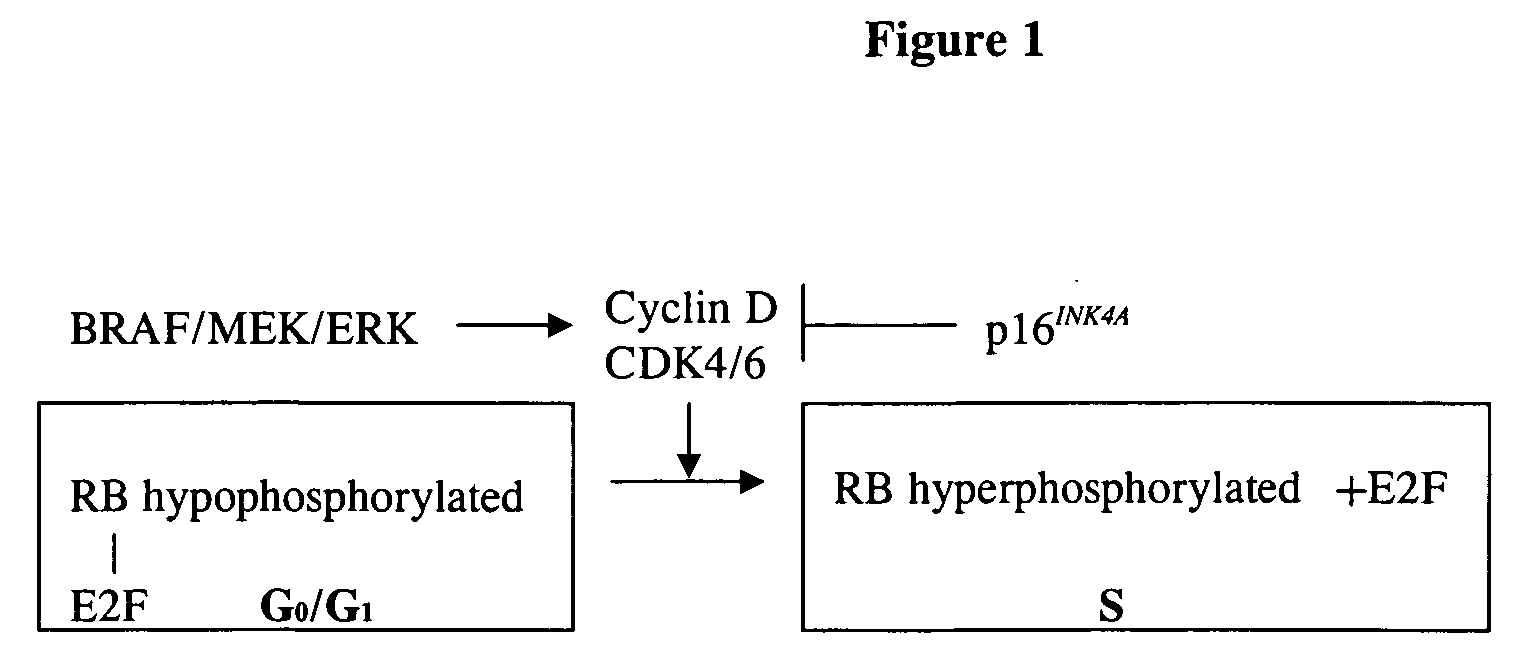
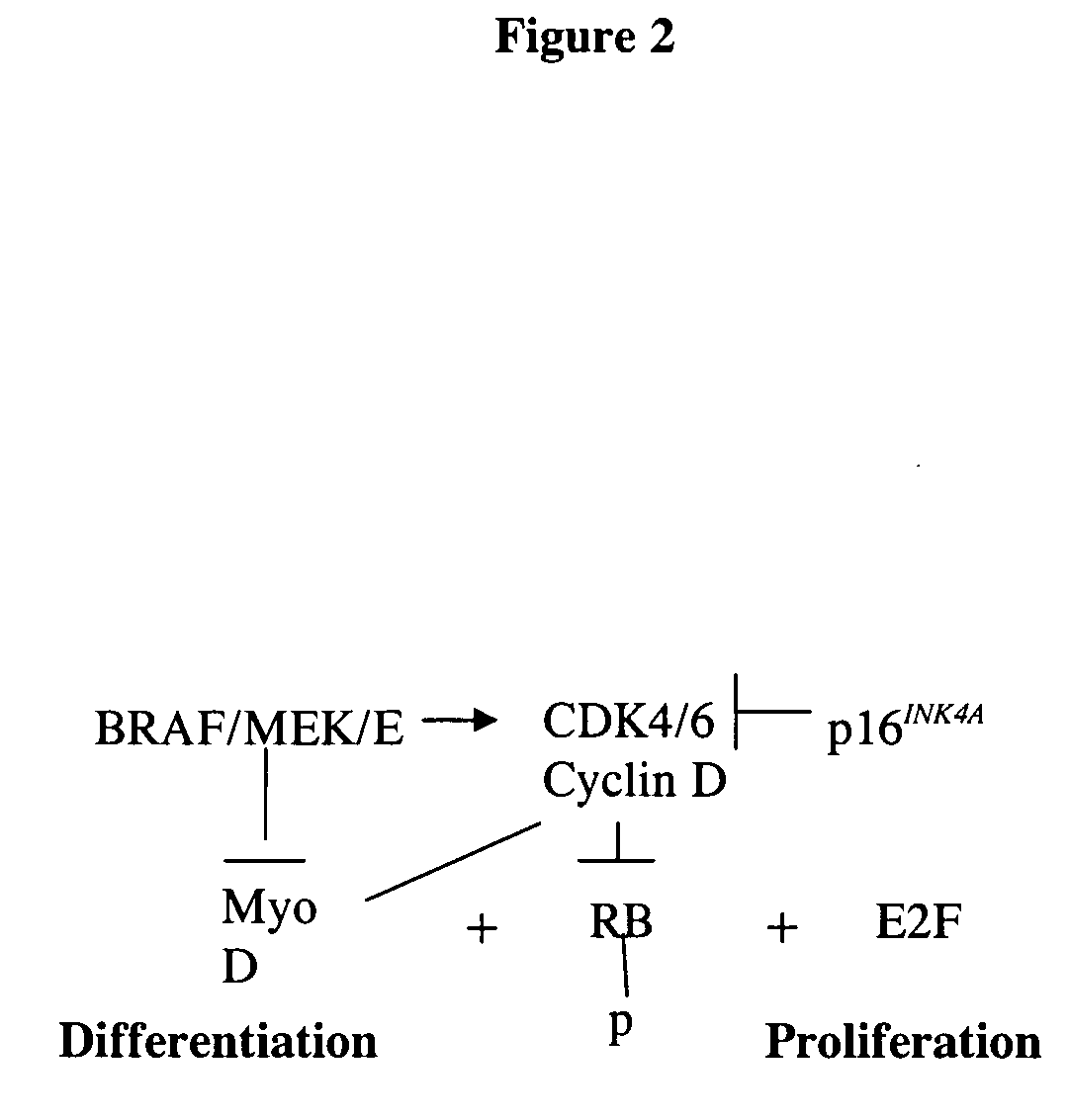
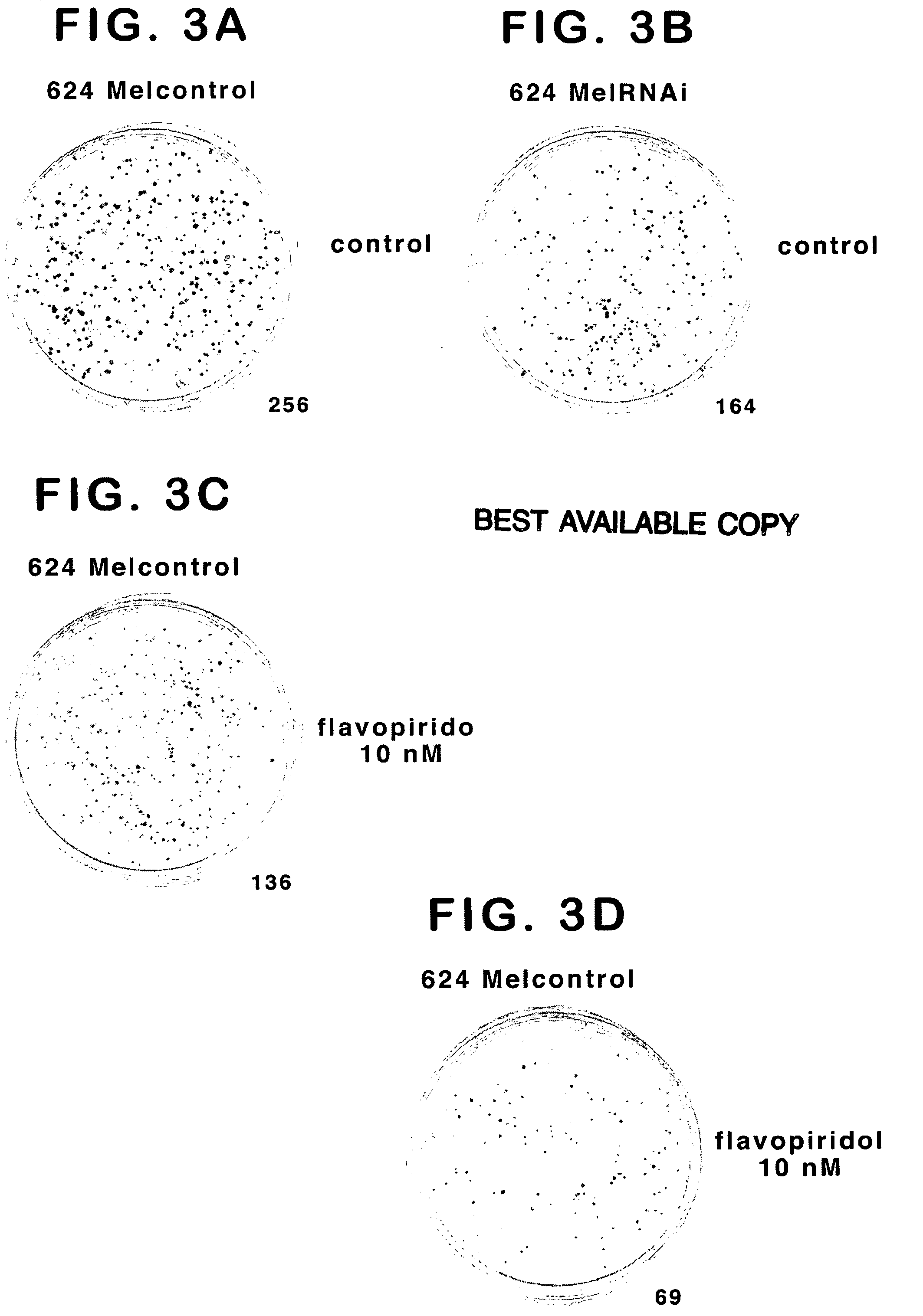
Treatment of cancer by simultaneous inhibiton of BRAF and restoration or mimicry of p16INK4A activity
InactiveUS20060134068A1Growth inhibitionHigh activityBiocideOrganic active ingredientsMelanomaWild type
Provided is a method for inhibiting growth of a tumor cell which comprises oncogenically activated BRAF and defective p16INK4A by inhibiting activated BRAF and restoring functional p16INK4A. Also provided is a method for sensitizing the foregoing tumor cell to cytotoxic or cytostatic effect of a chemotherapeutic agent or radiation by further contacting the cell with such an agent. Also provided is a method for treating cancer, especially melanoma, by simultaneously inhibiting expression or activity of activated BRAF and restoring or mimicking the activity of wild-type p16INK4A.
Owner:MT SINAI SCHOOL OF MEDICINE
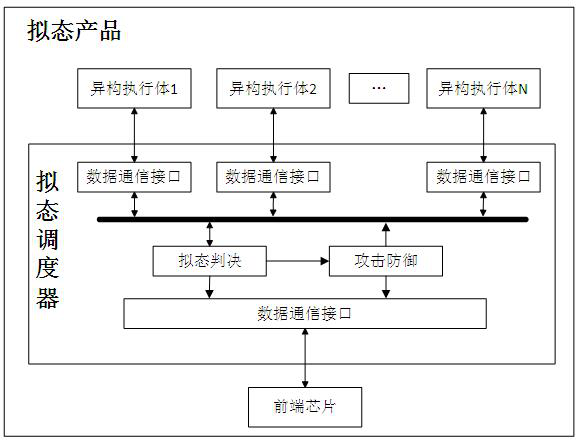
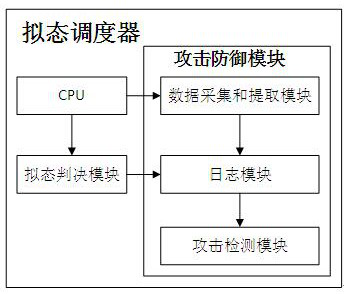
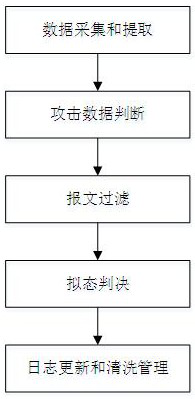
Attack defense device and method based on mimicry defense, equipment and medium
The invention discloses an attack defense device and method based on mimicry defense, equipment and a medium. The device comprises a mimicry scheduler and a plurality of heterogeneous executors; the heterogeneous executive receives and processes the message data sent by the mimicry scheduler; the mimicry scheduler comprises a mimicry judgment module and an attack defense module and is used for receiving message data sent by the front-end chip and forwarding the message data to the heterogeneous executor to realize data distribution, mimicry judgment and cleaning management of the heterogeneous executor; the mimicry judgment module performs mimicry judgment on downlink data of the heterogeneous executor and sends a mimicry judgment result to the attack defense module; and the attack defense module performs acquisition, extraction and log storage on the message data sent by the front-end chip, and performs log updating, attack defense detection and attack data filtering according to a mimicry judgment result of the mimicry judgment module. According to the invention, attack detection judgment is carried out on the message data and the abnormal message data is effectively filtered, so that the isomer executor cleaning frequency is reduced.
Owner:PURPLE MOUNTAIN LAB
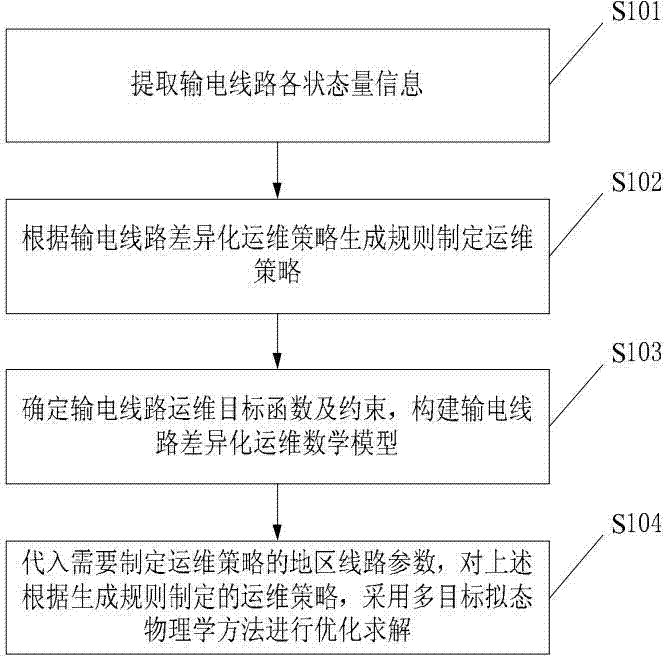
Power transmission line operation and maintenance optimization method and system based on multi-target mimicry physics
The invention discloses a power transmission line operation and maintenance optimization method and system based on multi-target mimicry physics. The method comprises the following steps: generating a power transmission line differentiation operation and maintenance strategy; inputting the operation and maintenance strategy into a power transmission line differentiation operation and maintenance mathematical model; operating the multi-target mimicry physics to solve a differentiation operation and maintenance mathematical problem; and developing a power transmission line differentiation operation and maintenance optimization software module, and realizing the automatic regulation and the regeneration of the operation and maintenance strategy. When the invention is adopted, the power transmission line operation and maintenance strategy can be optimized, power transmission line operation and maintenance workload can be lowered, and the invention is high in automation degree and favorable in economic benefit.
Owner:JIANGMEN POWER SUPPLY BUREAU OF GUANGDONG POWER GRID +1
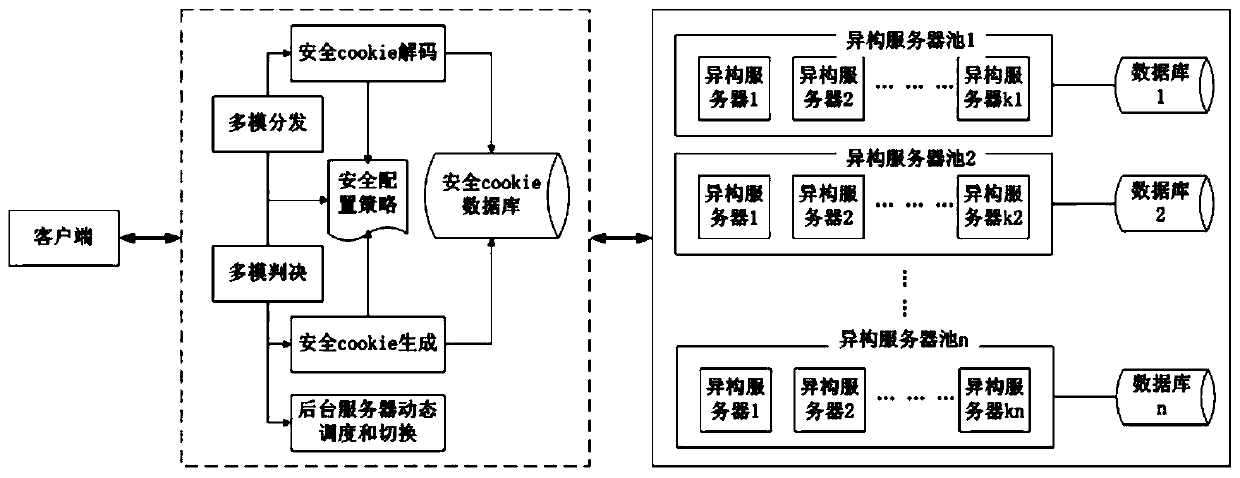
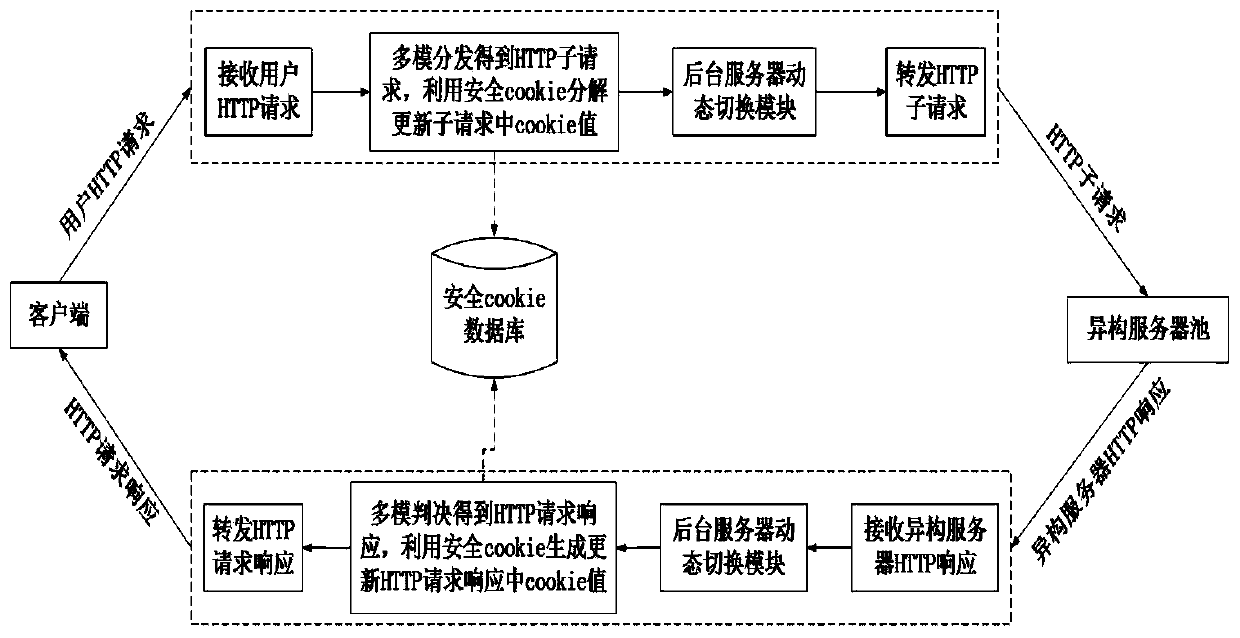
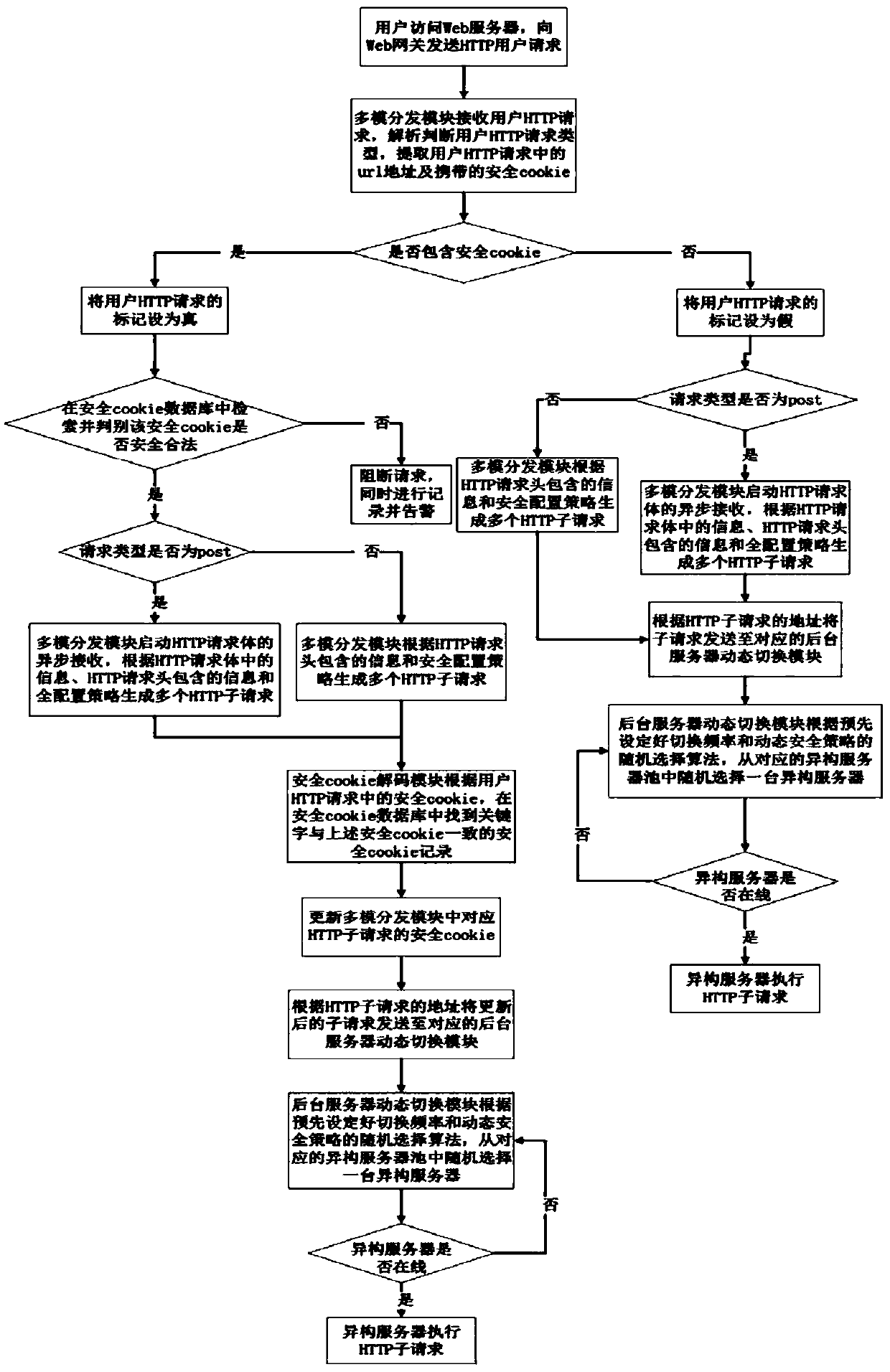
Mimicry Web gateway system and mimicry Web gateway method for carrying out dynamic scheduling by adopting random selection
The invention discloses a mimicry Web gateway system and a mimicry Web gateway method for carrying out dynamic scheduling by adopting random selection. The system comprises a system module distribution module, a multimode judgment module, a security Cookie generation module, a security Cookie decoding module, a heterogeneous server pool group, a background server dynamic switching module group, adatabase synchronization module, a security Cookie database group and a security configuration strategy. According to the invention, heterogeneous integration is carried out on the server, dynamic switching of the executor group is realized by utilizing a random selection technology, and a mimic Web gateway system is realized through Cookie mapping. According to the Web gateway based on dynamic heterogeneous redundancy, the background executor is dynamically switched by utilizing the dynamic scheduling and heterogeneous redundancy technology, the risk and loss of attacking a website system arereduced, the attack behavior can be more accurately judged, and countermeasures are taken in time.
Owner:HANGZHOU DIANZI UNIV
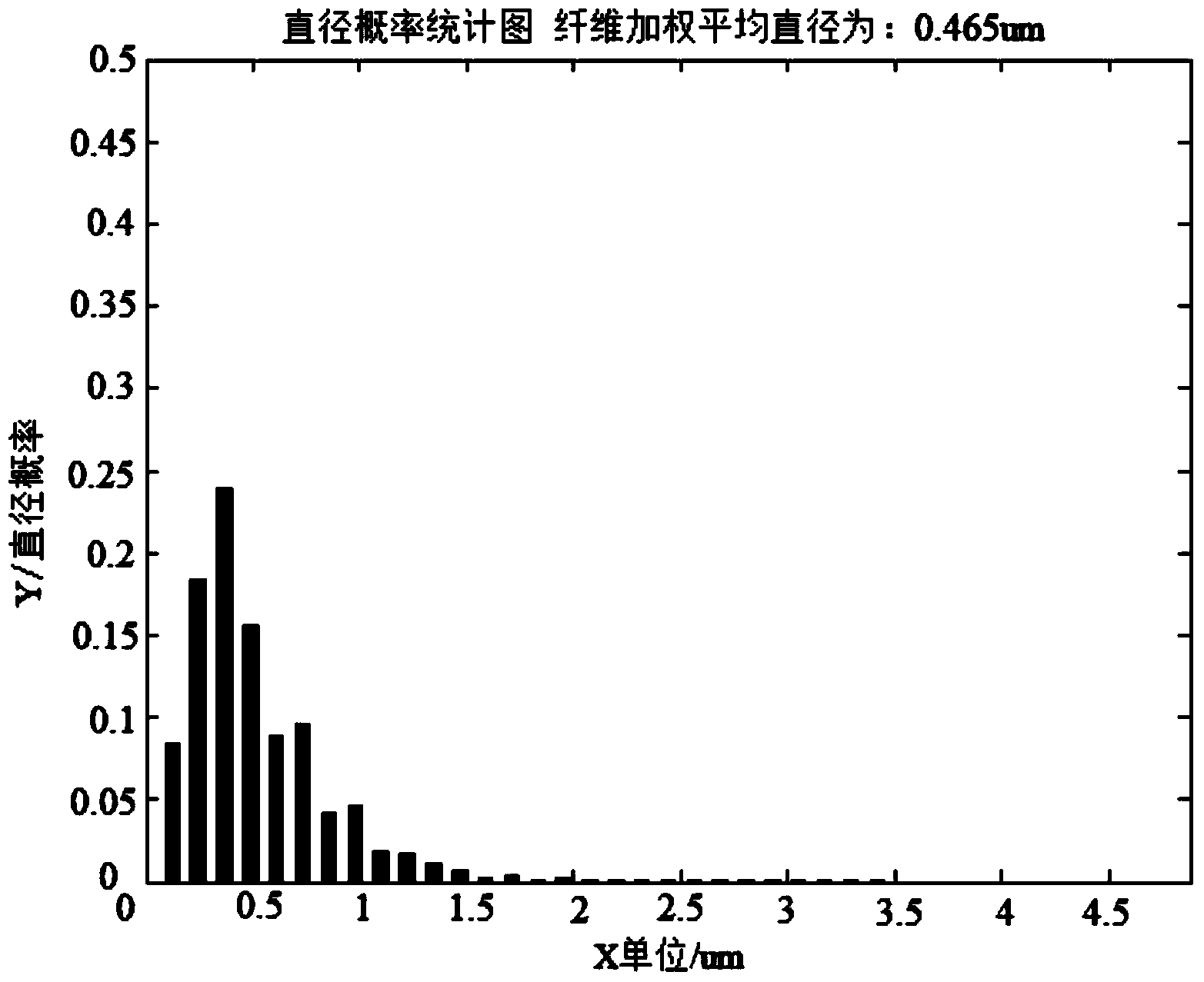
Mimicry reconstruction and performance computing method of fiber filter medium structure
ActiveCN103971395AWork around application limitationsShorten the timeCharacter and pattern recognition3D-image renderingImaging processingPerformance computing
The invention discloses a mimicry reconstruction and performance computing method of a fiber filter medium structure, and belongs to the technical field of fiber structure mimicry reconstruction. The mimicry reconstruction process comprises the steps: first, obtaining fiber filter medium images; second, setting the best threshold value and performing binarization processing; third, performing center line detection on binary images; fourth, performing four-opposite-angle direction comparison on pixel points of the center line and obtaining the gyration radius di and the gyration direction df; fifth, performing three-dimensional gyration and obtaining a fiber filter medium mimicry reconstruction image. According to the mimicry reconstruction and performance computing method, by inputting a series of relevant parameters, filter efficiency curves and pressure loss curves of fiber filter media at different wind speeds are obtained by means of the empirical formula. According to the method, microcosmic single-layer structure images in real fiber filter media are used as the basis, mimicry reconstruction is performed on the obtained images by means of the simple and rapid image processing method, and a mimicry reconstruction model can simulate the real fiber filter medium structure realistically.
Owner:ANHUI UNIVERSITY OF TECHNOLOGY
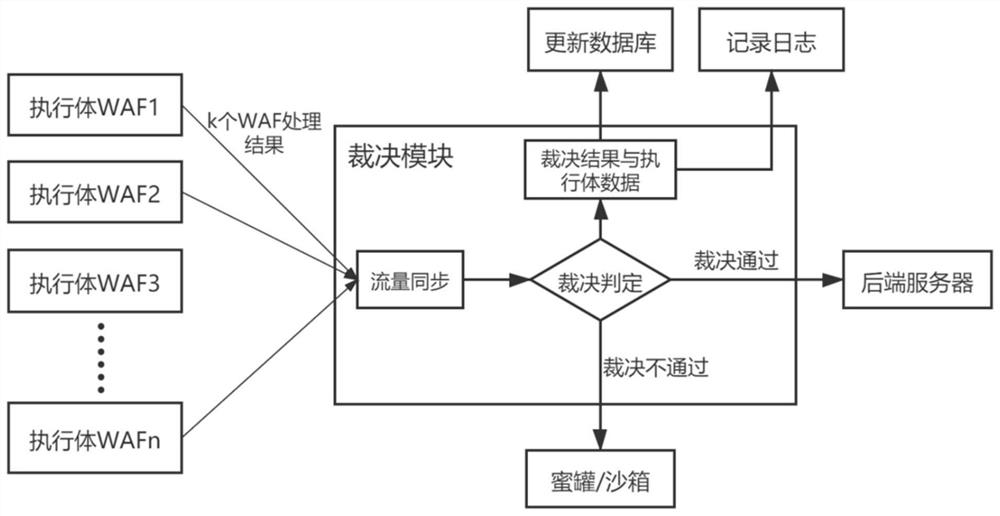
Judgment method of executive in mimicry WAF
The invention discloses a judgment method for an executor in a mimicry WAF, and the method can carry out the judgment of a plurality of processing results with the same flow, thereby discovering and blocking an unknown attack. The flow synchronization module, the multi-mode judgment module, the judgment result and data recording module and the like are mainly designed to realize a judgment function in the mimicry WAF, the mimicry WAF can identify unknown attacks through the judgment function, and the unknown attacks are blocked through operations such as offline self-cleaning of a WAF executor, so that the mimicry WAF has an active defense capability. The method comprises the steps that firstly, a flow synchronization module synchronizes k heterogeneous WAF processing results, then a multi-mode judgment module judges judgment of the processing results, records the judgment results and data into logs and updates corresponding values of a database, and finally, when the judgment resultsare passed, flow is sent to a back-end server, and when the judgment results are not passed, the flow is sent to a honeypot or a sandbox.
Owner:ZHEJIANG UNIV
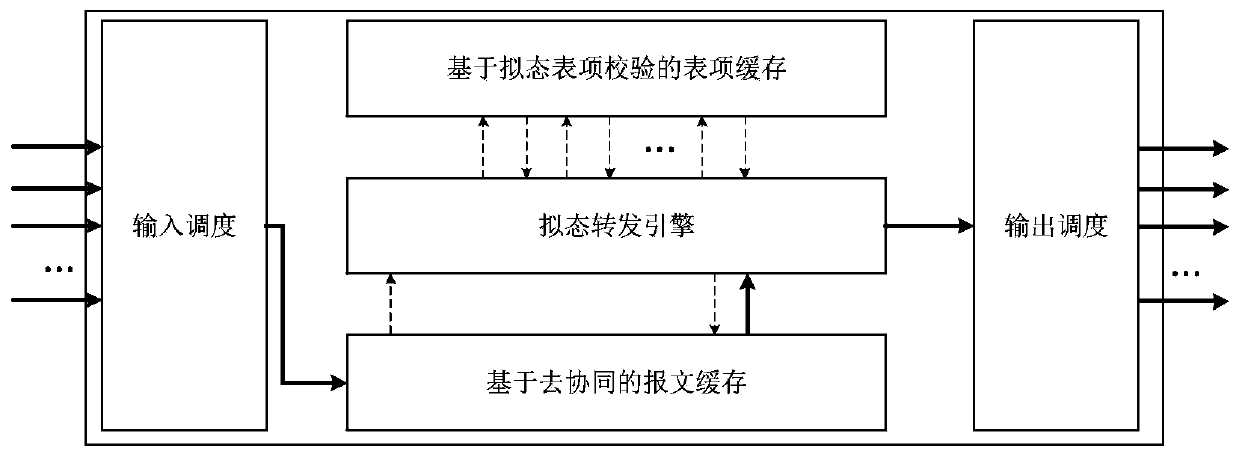
Mimicry thought-based security exchange chip, implementation method and network exchange equipment
ActiveCN110177046AImprove securityImprove reliabilityData switching networksNetwork packetNetwork switch
The invention belongs to the technical field of network switching, and particularly relates to a mimicry thought-based security switching chip, an implementation method of the security switching chipand network switching equipment, and the method comprises the following steps: carrying out scheduling processing on message data of each port according to input scheduling; aiming at each piece of message data, extracting a message header and caching the message data; parsing through a heterogeneous parsing algorithm, and carrying out mimicry judgment on a parsing result; generating a message descriptor according to the judgment result, wherein the message descriptor at least comprises message feature information related to the message forwarding strategy behavior; searching for a mimicry table item verification-based table item cache to obtain forwarding strategy behavior data and updating a message descriptor; and extracting corresponding message data from the cached message data, and sending the extracted message data to a corresponding port in the form of a data packet. The security and reliability of the switch chip are enhanced by introducing such technologies as de-collaborative caching, mimic forwarding engines and mimic table item checking, and the method has important guiding significance for the development of the network switching technology.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU
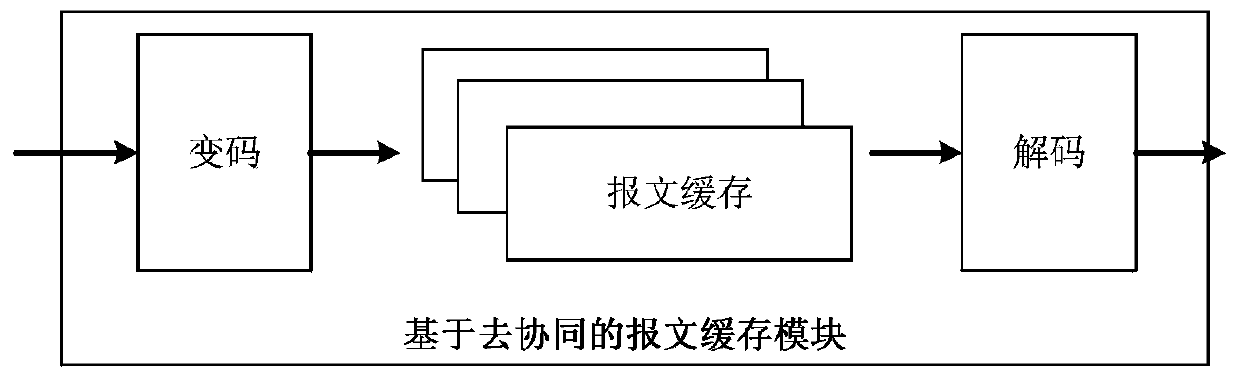
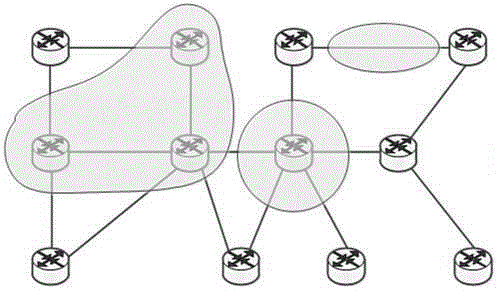
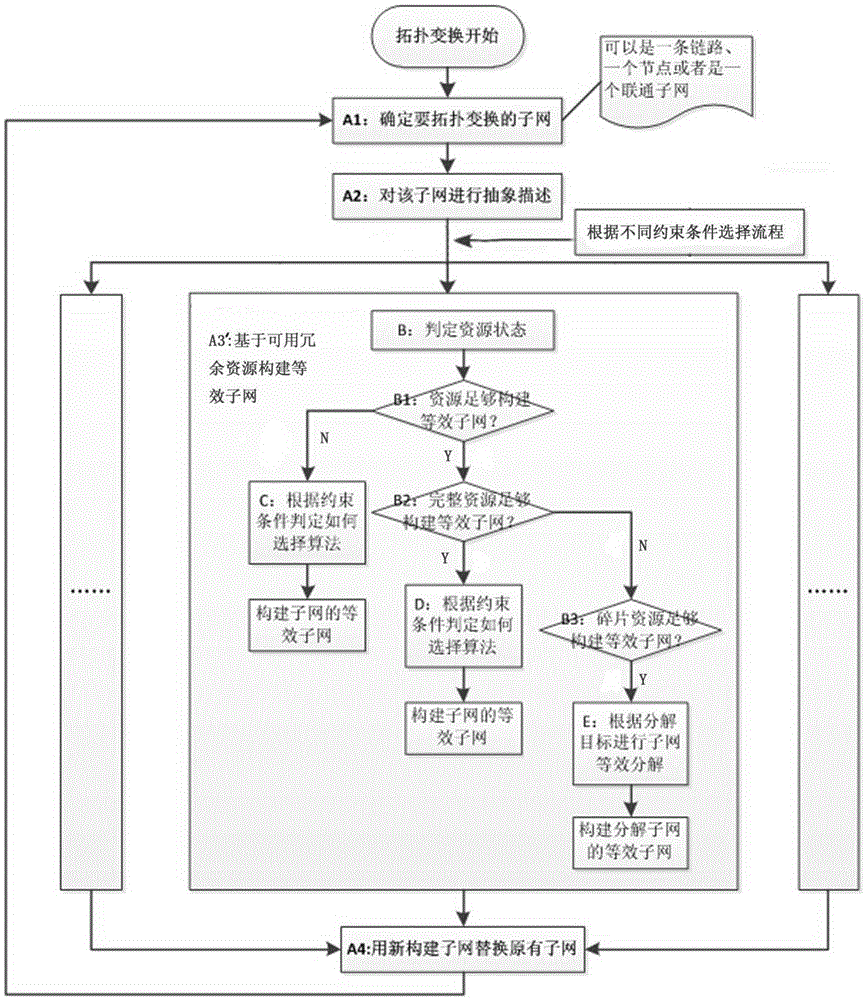
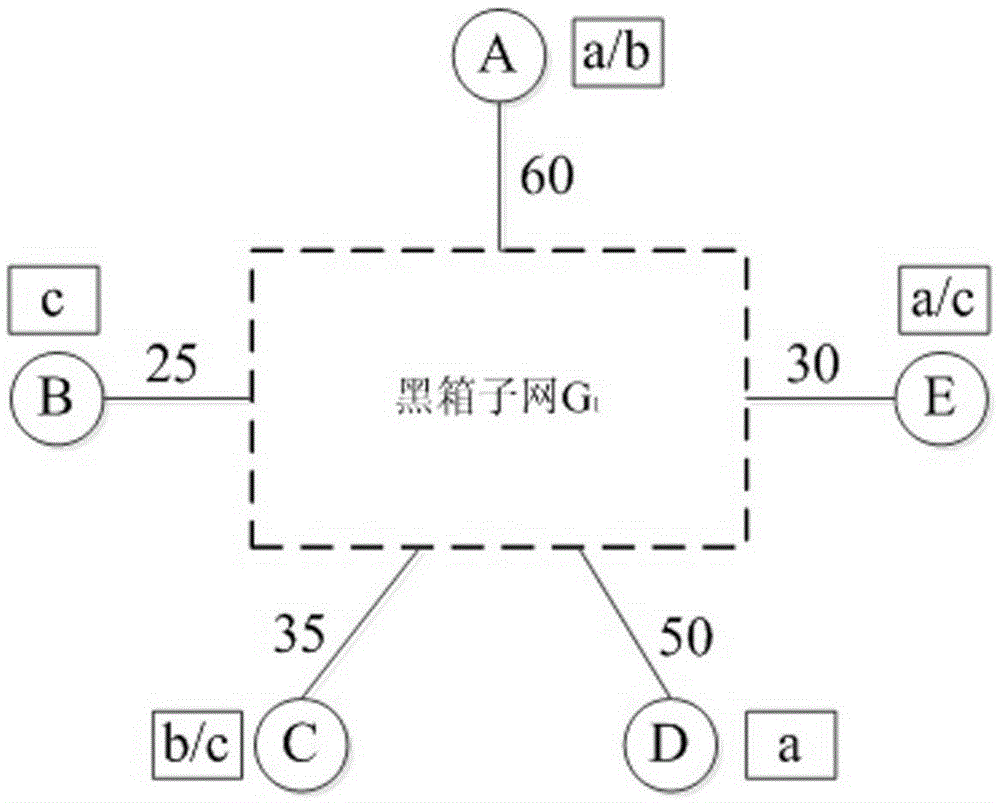
Mimicry network topology transformation method
ActiveCN105306251AReduce difficultyReduce network sizeData switching networksNetwork sizeNetwork structure
The invention discloses a mimicry network topology transformation method, which is used for overcoming problems to be solved in dynamical change of a network structure in the prior art. The mimicry network topology transformation method disclosed by the invention comprises the following steps: once equivalent transformation step of a local subnet comprises: A1, determining the local subnet to be performed with topological equivalent transformation; A2, using a network description method to carry out abstract description on the local subnet determined in A1; A3, establishing an equivalent subnet of the local subnet described in A2 based on a constraint condition; and A4, using the established subnet to replace the original subnet. Compared with the prior art, the mimicry network topology transformation method disclosed by the invention has the following advantages: 1. the method is used for achieving an overall network topology transformation effect by carrying out topological equivalent transformation on the local network subnet for multiple times, since the target of the topology transformation is the subnet in the network instead of the entire network, the network scale of the topology transformation is greatly reduced, and the difficulty of the topology transformation is reduced.
Owner:SHANGHAI REDNEURONS +1
Human skeleton point parameter acquisition device applied to humanoid motion mimicry and recognition method thereof
PendingCN106981075AStrong real-time collectionImprove recognition accuracyImage enhancementImage analysisSystem requirementsHuman skeleton
The invention discloses a human skeleton point parameter acquisition device applied to humanoid motion mimicry and a recognition method thereof. The method is characterized by acquiring a depth image, recognizing human joint points by using the depth image by an OpenNI bone recognition algorithm library, extracting spatial coordinates, and providing control data for a robot controller by means of filtering, spatial vector calculation, and leg posture recognition. In view of a problem that posture recognition is influenced by environment so as to be low in recognition accuracy and poor in real-time performance, a new action recognition method based on human skeleton predefining is provided for human-machine interaction posture classification. The method give full scope to an advantage that the Kinect can obtain a depth image feature, organically combines 2bitBP characteristics, constitutes a skeleton predefined posture type, performs posture classification by using an improved support vector machine, and is good in real-time performance, high in recognition accuracy, and good in robustness in the case of illumination variation. The recognition efficiency and accuracy can meet a natural human-machine interaction system requirement.
Owner:江西制造职业技术学院
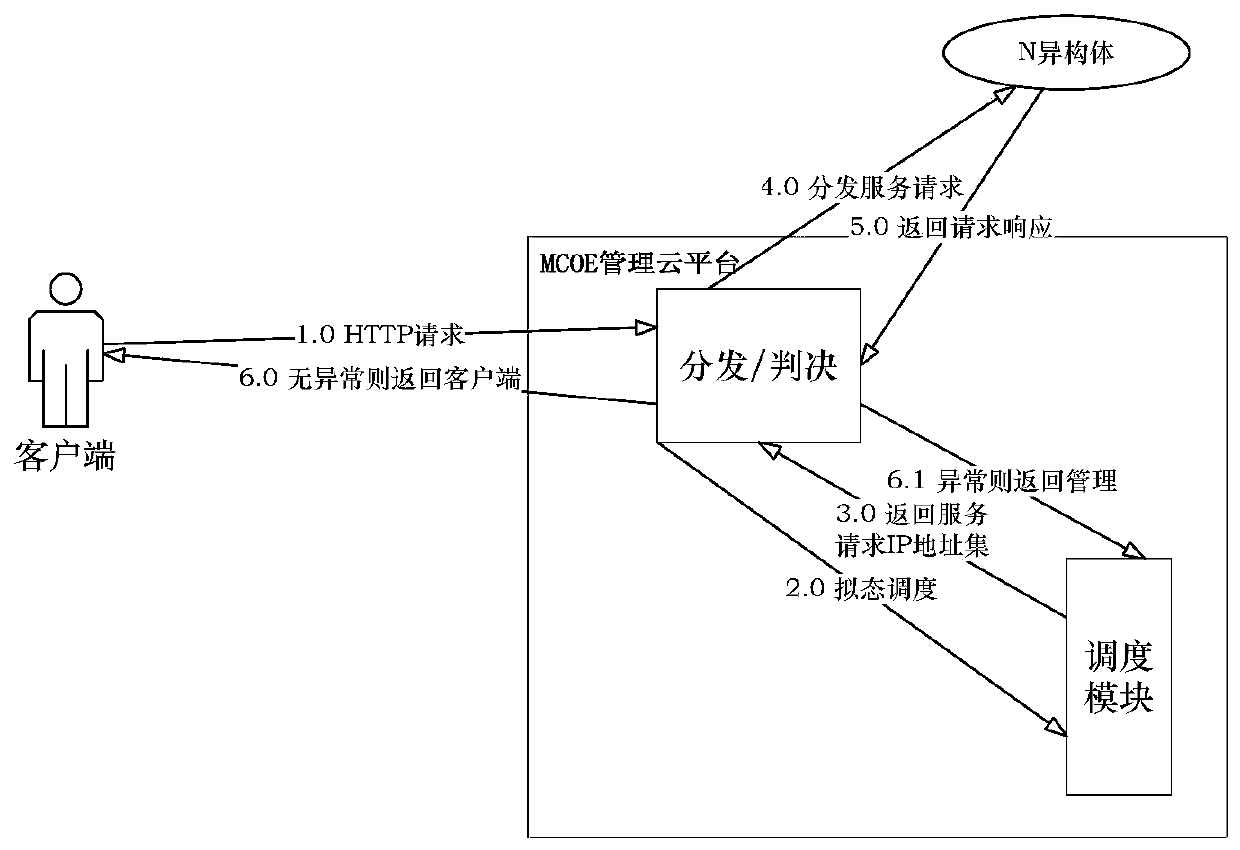
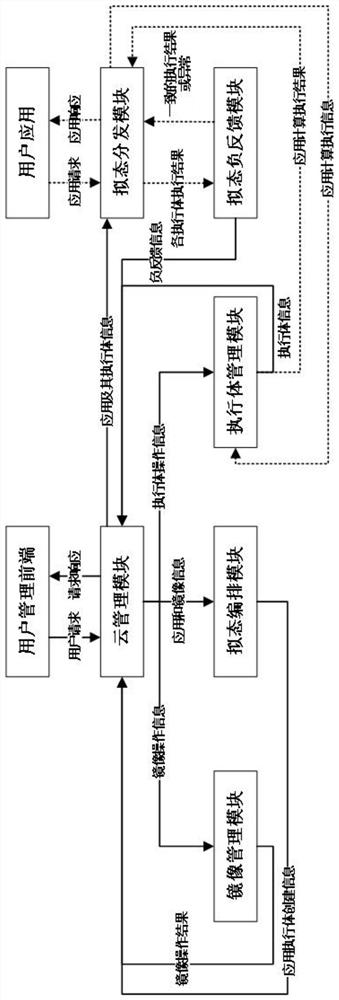
Mimicry defense system based on SaaS platform
ActiveCN112153024AImprove securitySimplify Mimic Application DeploymentTransmissionSoftware simulation/interpretation/emulationNegative feedbackEngineering
The invention provides a mimicry defense system based on an SaaS platform. The mimicry defense system comprises a cloud management module for processing a user request and feeding back a processing result; a mirror image management module which is used for maintaining a mirror image remote warehouse and storing and deleting the uploaded mirror images; a mimicry arrangement module which is used forscheduling resources required for creating the heterogeneous executors of the application and generating information required for creating each heterogeneous executor; an executive management modulewhich is responsible for creating and deleting a heterogeneous executive; a mimicry distribution module which is used for sending the user request to each heterogeneous executive body to obtain an executive result and sending the executive result to the mimicry negative feedback module; and a mimicry negative feedback module which is used for carrying out consistency judgment on the execution result and taking the execution result judged to be consistent as a processing result of the corresponding user request to respond. Through centralized management of the cloud management module, the complexity of mimicry application deployment and management of a user is simplified, and the security of the cloud platform is improved.
Owner:EAST CHINA INST OF COMPUTING TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com