Information system-oriented mimicry defense system and method, and medium
A technology of information system and defense system, applied in the direction of transmission system, electrical components, etc., can solve the problems of inability to resist system loopholes and backdoors, poor linkage effect of new network attack methods, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be described in detail below in conjunction with specific embodiments. The following examples will help those skilled in the art to further understand the present invention, but do not limit the present invention in any form. It should be noted that those skilled in the art can make several changes and improvements without departing from the concept of the present invention. These all belong to the protection scope of the present invention.
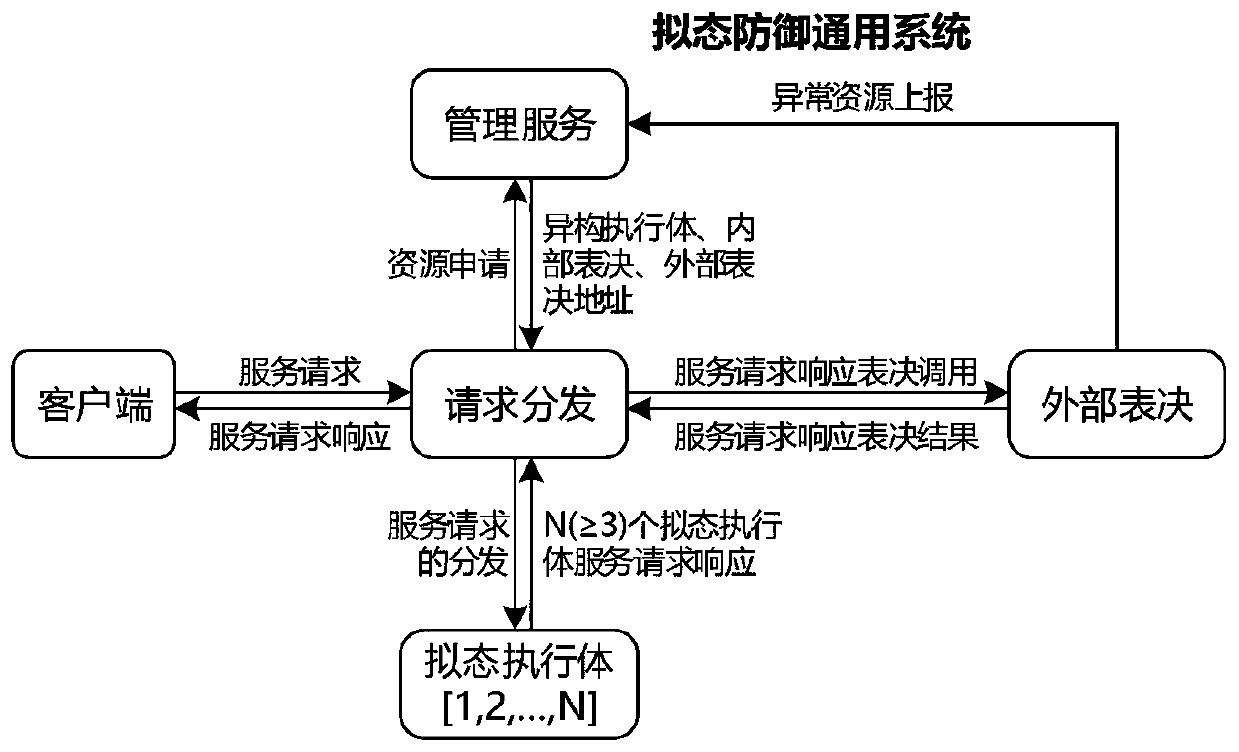
[0048] Such as figure 1 , the request distribution module receives the service request from the client, and distributes the service request to the mimic executive, and the mimic executive executes to get the service request response, and the external voting module votes on the service request response, and returns the voting result to the client; The management module monitors and manages the mimic executive body.
[0049] According to the information system-oriented mimic defense method provided by th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com