Annular mimicry architecture without protocol state, defense method and readable storage medium
A protocol state, loop technology, applied in the field of mimic defense systems, can solve the problems of unguaranteed security, reduced agent efficiency, system performance bottlenecks, etc., to achieve the effect of simplified functions, improved efficiency, and improved security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
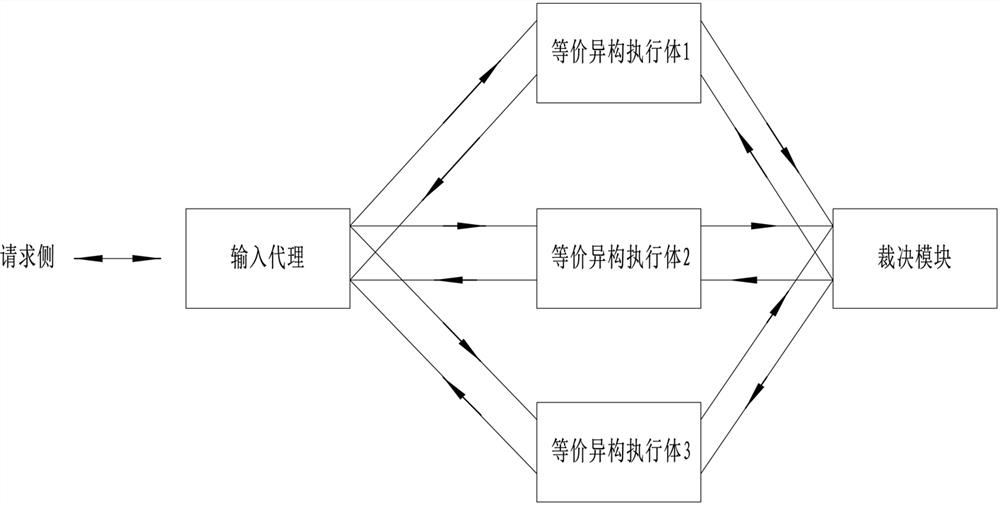
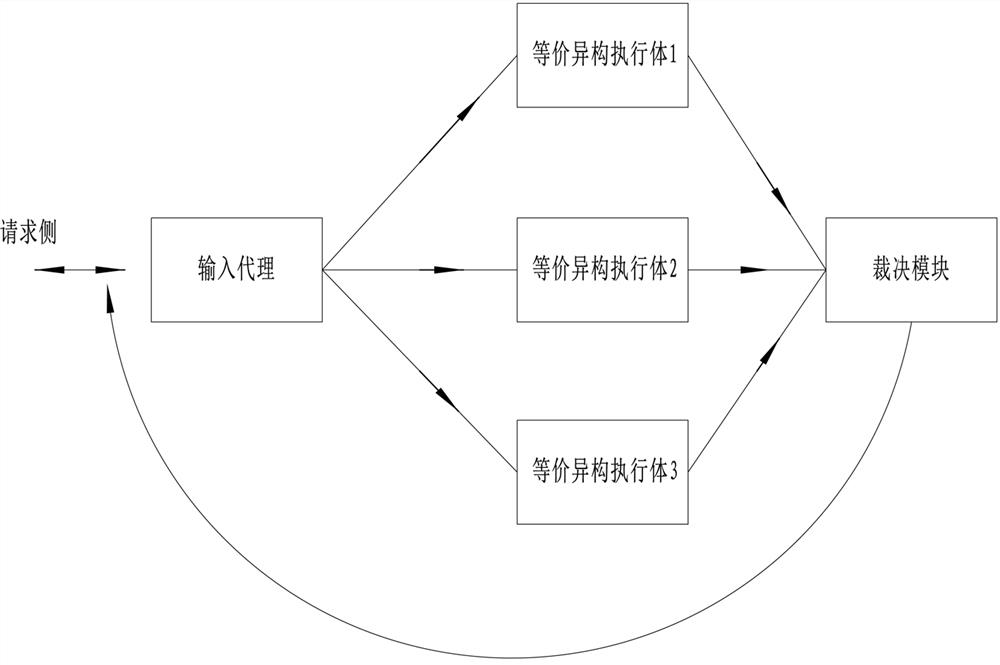
[0029] Such as figure 2 As shown in , a ring-like mimic architecture without protocol state, including input agent, equivalent heterogeneous executive, arbiter and feedback controller, the output side of the input agent communicates with each equivalent heterogeneous through a one-way communication channel Communication is established between execution bodies of different structures, and the output side of each equivalent heterogeneous execution body establishes communication with the arbiter through a one-way communication channel, and the output side of the arbiter is connected to a one-way request side communication channel. The arbiter also establishes a connection with the feedback controller. The feedback controller controls the state of each equivalent heterogeneous execution body. The input agent is an independent simple module with the functions of protocol normalization and message copying and distribution, such as FPGA or simple hardware circuit.
[0030] When per...
Embodiment 2
[0042] A readable storage medium, on which computer instructions are stored, and when the computer instructions are executed by a processor, the described mimic defense method is realized.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com