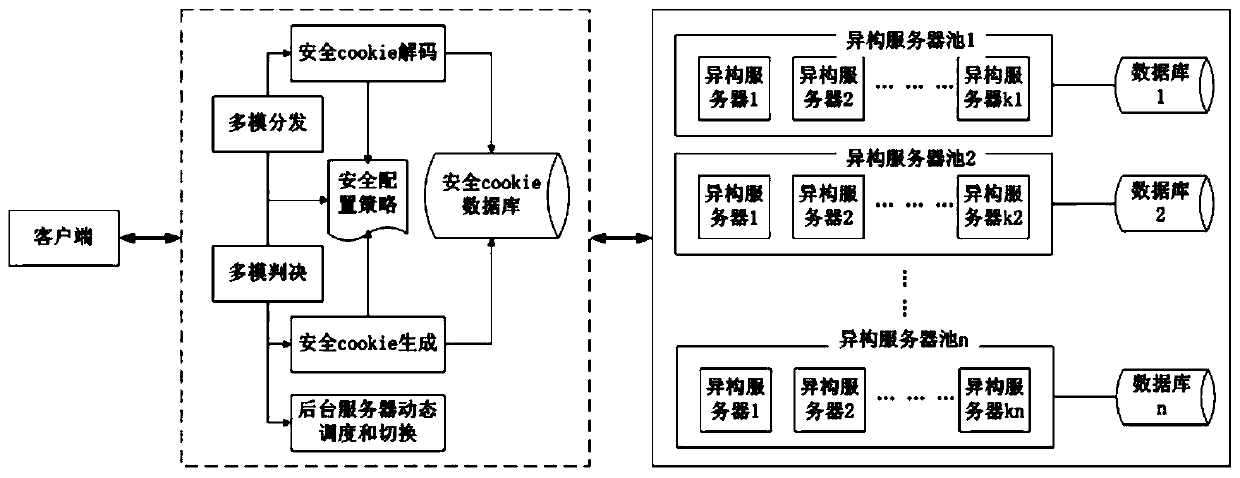
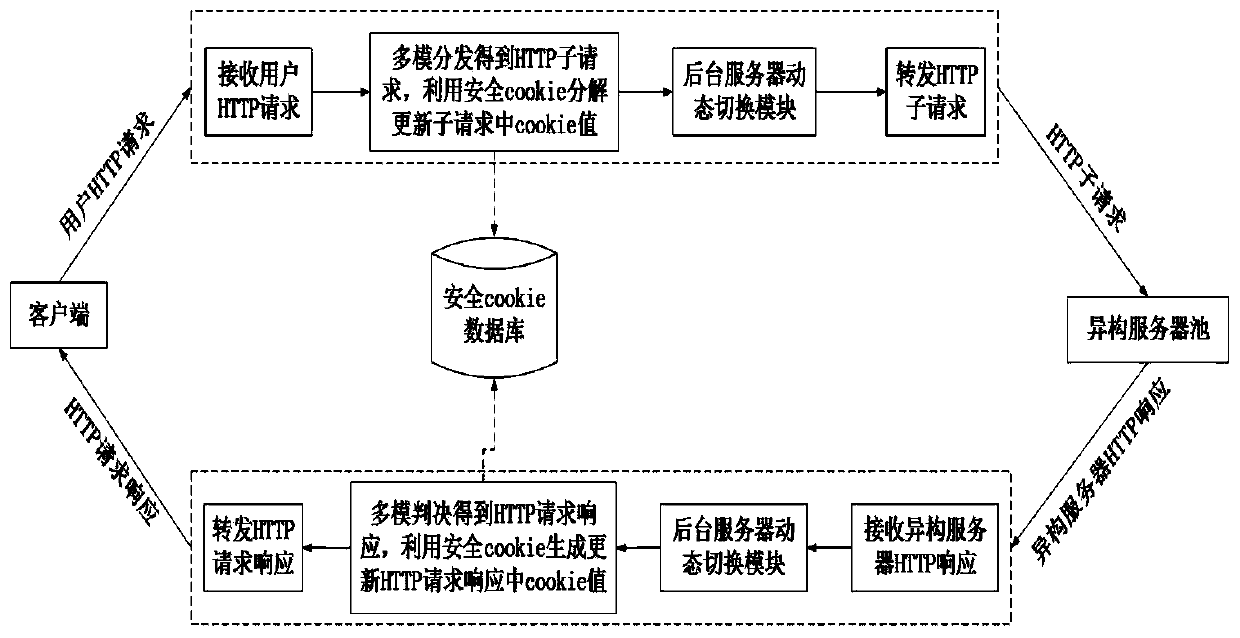
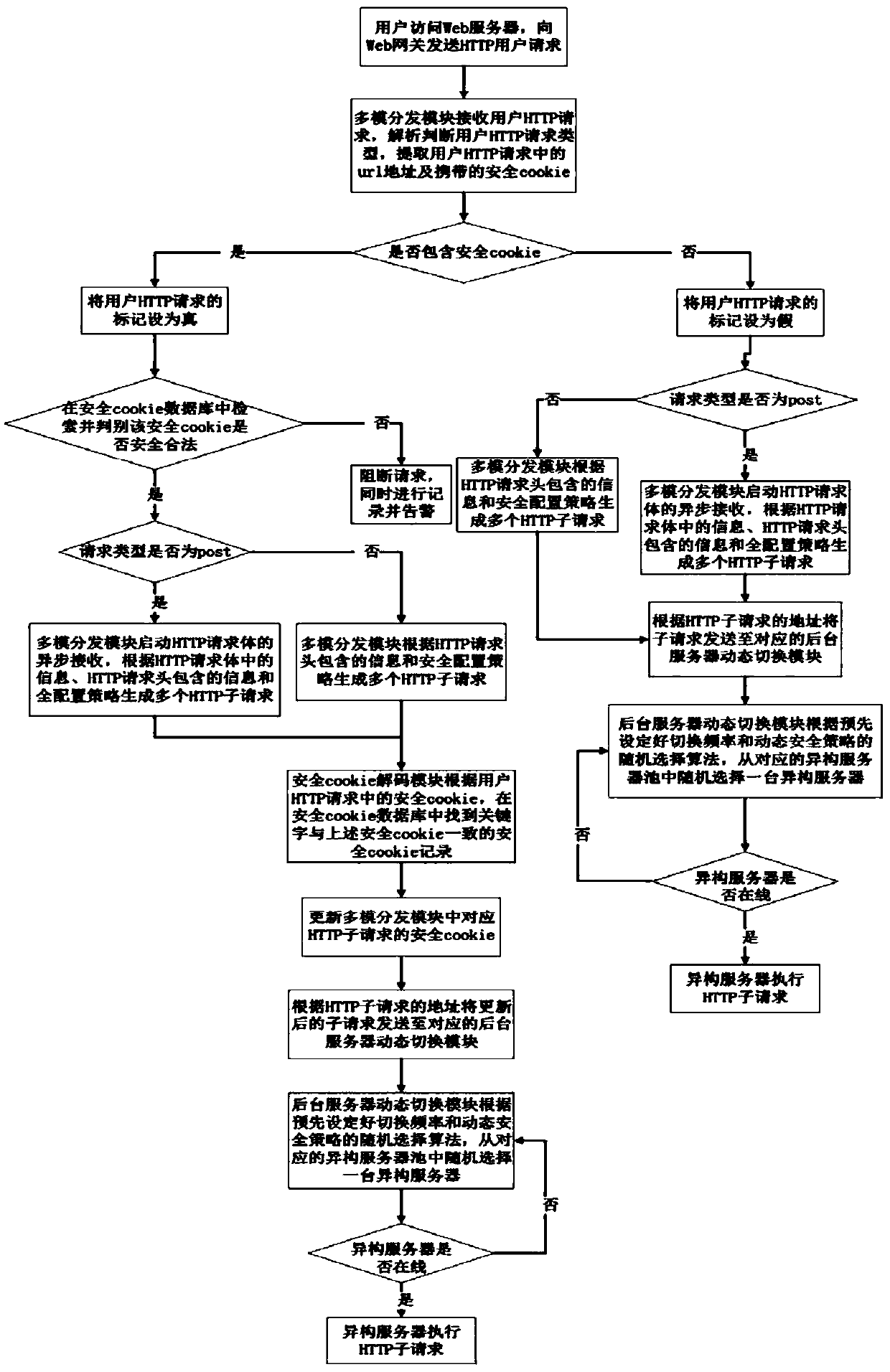
Mimicry Web gateway system and mimicry Web gateway method for carrying out dynamic scheduling by adopting random selection
A technology of random selection and dynamic scheduling, applied in the computer field to reduce risks and losses, and increase the difficulty of attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0065] Embodiment 1: User HTTP request generates HTTP sub-request (user HTTP request contains security Cookie)
[0066] The client sends a user HTTP request to the web gateway, and the content of the request is as follows:
[0067] GET / test HTTP / 1.1
[0068] Host:acm.hdu.edu.cn
[0069] Upgrade-Insecure-Requests: 1
[0070] …
[0071] Cookie: UID=69mti5j53m9qh1
[0072] The multi-mode distribution module in the web gateway receives the user's HTTP request, analyzes and judges the type of the user's HTTP request, and extracts the URL address and the security cookie carried in the user's HTTP request. Since there is a secure cookie, the secure cookie flag contained in the user HTTP request is set to true, and the secure cookie database is retrieved to determine whether the secure cookie is safe and legal. If it is legal, it is judged whether the request type is POST. Since the user HTTP request type is GET, multiple HTTP subrequests are generated according to the informat...
Embodiment 2
[0096] Embodiment 2, user HTTP request generates HTTP sub-request (user HTTP request does not include security Cookie):
[0097] The client sends a user HTTP request to the web gateway, and the content of the request is as follows:
[0098] GET / test HTTP / 1.1
[0099] Host:acm.hdu.edu.cn
[0100] Upgrade-Insecure-Requests: 1
[0101] …
[0102] The multi-mode distribution module in the web gateway receives the user's HTTP request, analyzes and judges the type of the user's HTTP request, and extracts the URL address and the security cookie carried in the user's HTTP request. Since there is no secure cookie, the flag that the user's HTTP request contains a secure cookie is set to false. Determine whether the request type is POST. Since the user’s HTTP request type is GET, multiple HTTP sub-requests are generated according to the information contained in the HTTP request header and the security configuration policy (HTTP request header generation related parameters), and the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com