Mimicry switch judgment system and method based on trusted measurement
A method of adjudication, a technology of credibility, applied in the field of network security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The present invention will be further explained below in conjunction with accompanying drawing and specific embodiment:
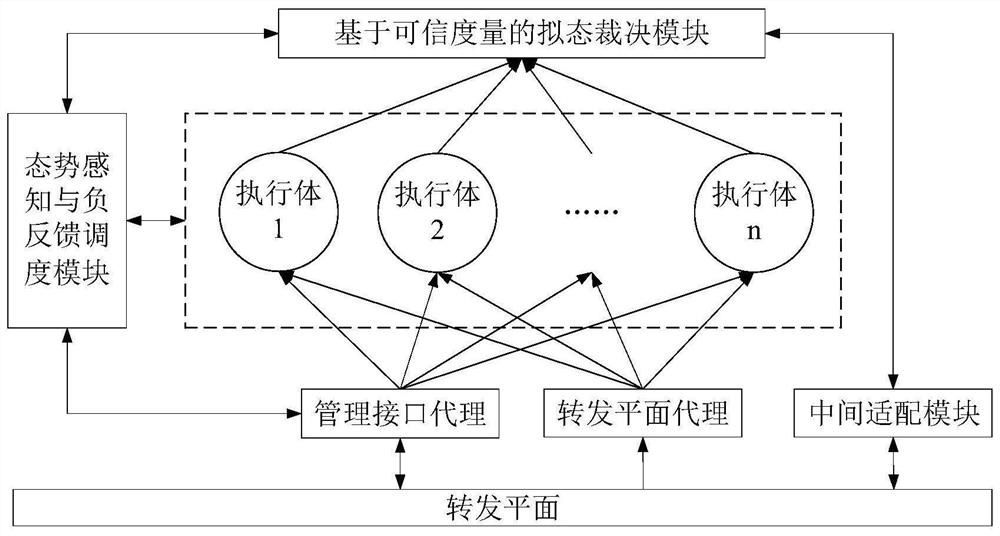
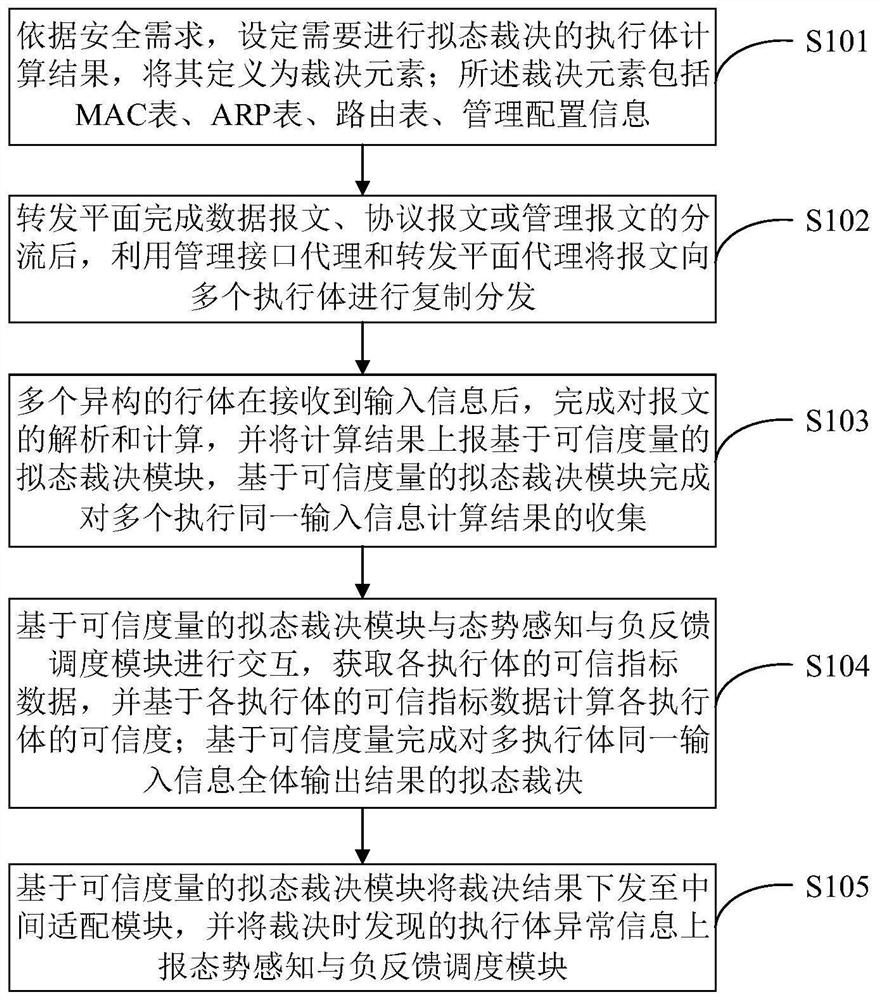
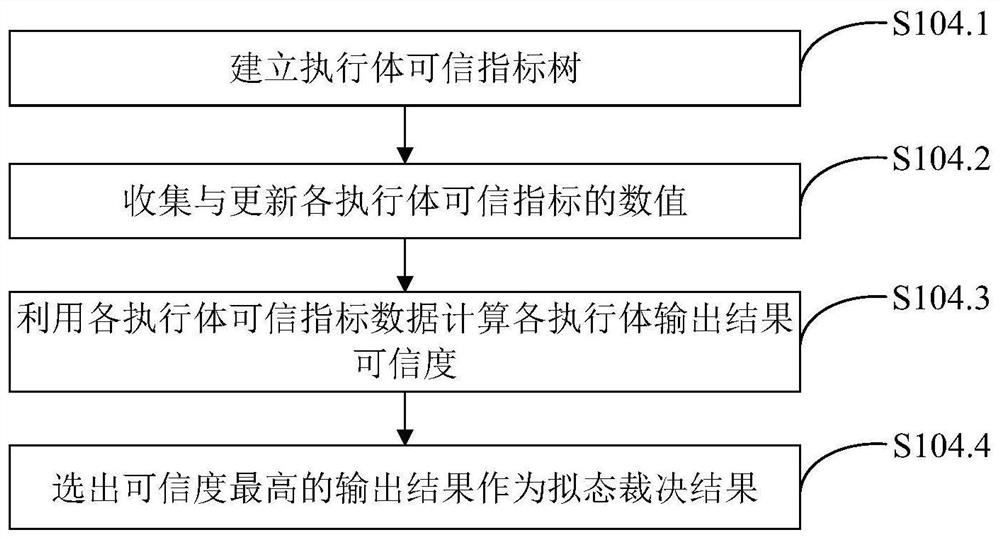
[0055] Such as figure 1 As shown, a mimetic switch arbitration system based on trusted metrics, including forwarding plane, management interface agent, intermediate adaptation module, forwarding plane agent, multiple heterogeneous executives (switch network operating systems), based on trusted metrics The Mimic Judgment Module and Situational Awareness and Negative Feedback Scheduling Module:
[0056] The forwarding plane is used to complete the forwarding of data messages, the reporting of protocol messages and the access of management systems;
[0057] The management interface agent is used to complete the distribution of management configuration information to multiple executives, realize the single presentation of multiple executives to the management user, and simultaneously realize the access of the management user to the situation awareness a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com