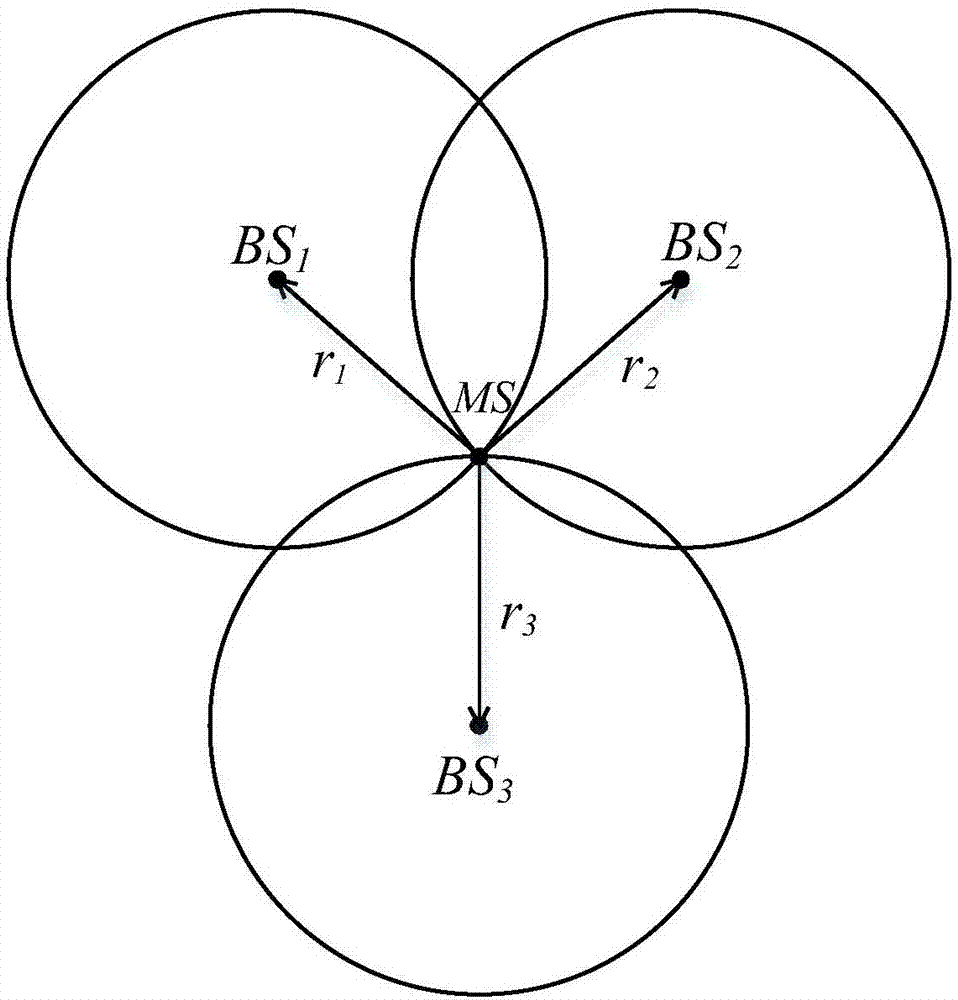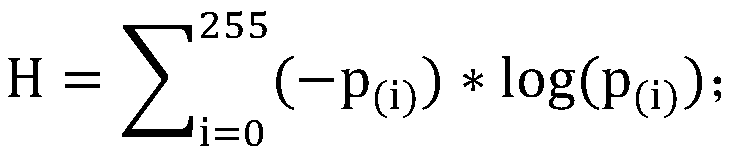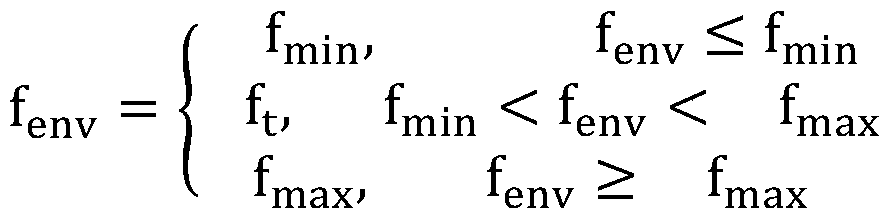Patents
Literature
66 results about "Security industry" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
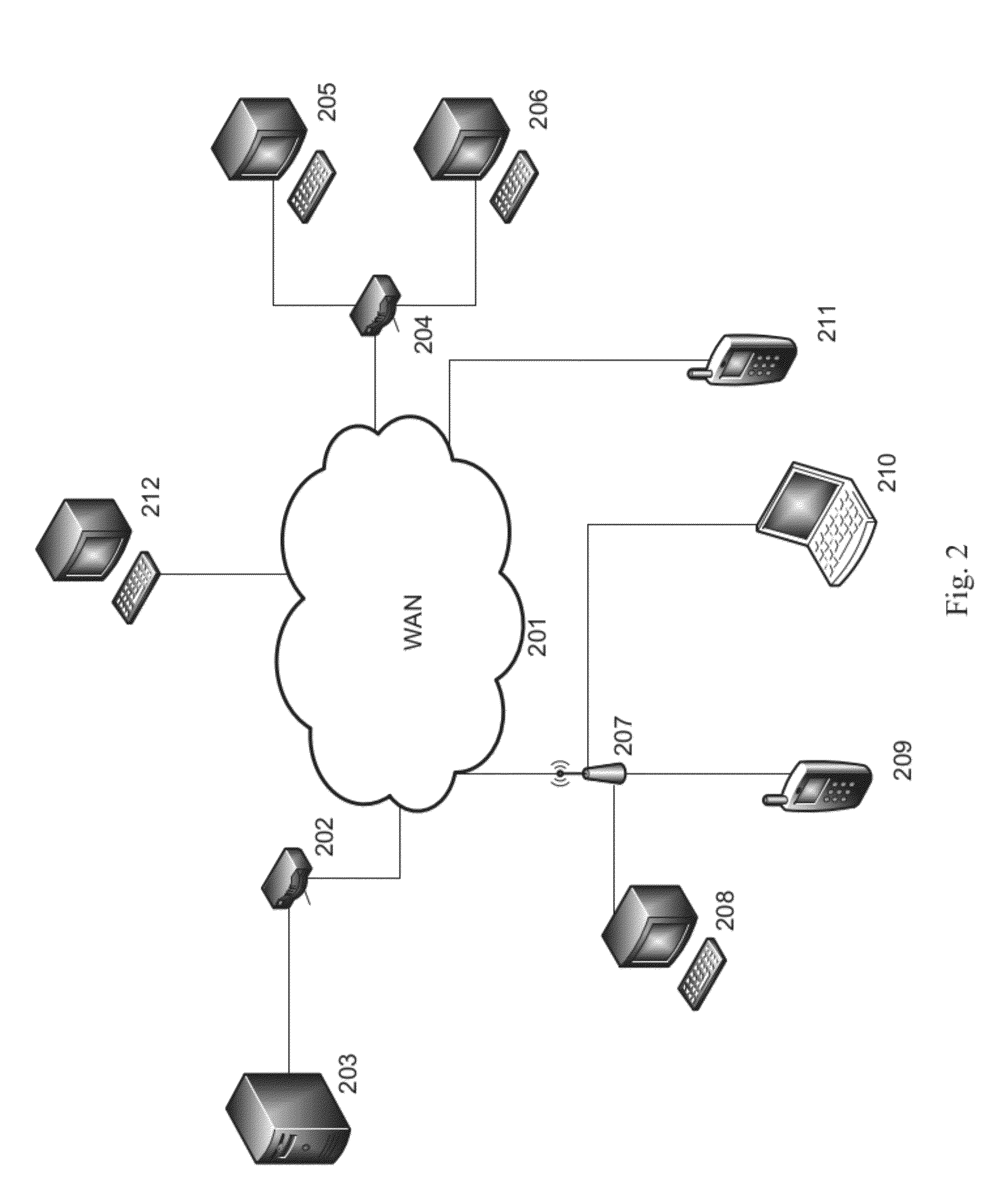
UWB-technology-based indoor pedestrian navigation method
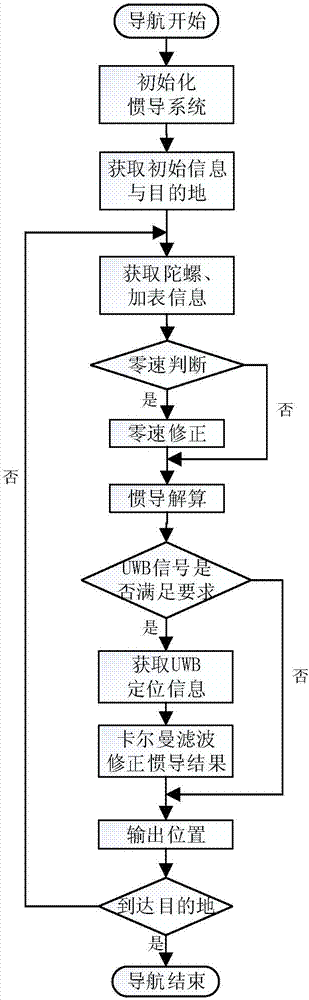
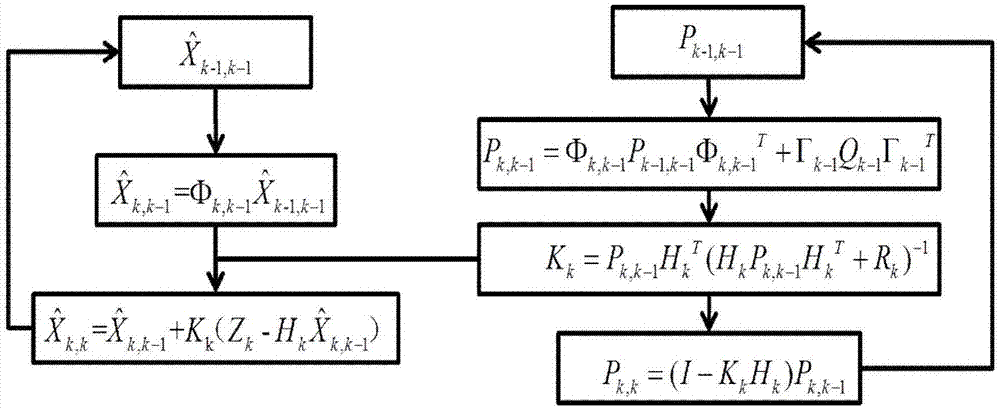
The invention discloses a UWB-technology-based indoor pedestrian navigation method. An inertial navigation system based on zero-velocity correction is used to carry out navigation, thereby suppressing divergency of an inertial navigation positioning error with time. A UWB base station is configured at a key node in the area in an optimized manner; and Kalman filtering is carried out by using UWB positioning data and zero-velocity-correction-based inertial navigation positioning data, thereby realizing correction of an inertial navigation positioning result effectively. The UWB-technology-based indoor pedestrian navigation method is suitable for position monitoring of the special crowd, for real-time positioning of the staff in a special industry like the fire-fighting and security industries, and for navigation positioning of common pedestrians in an area with no satellite signal coverage.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
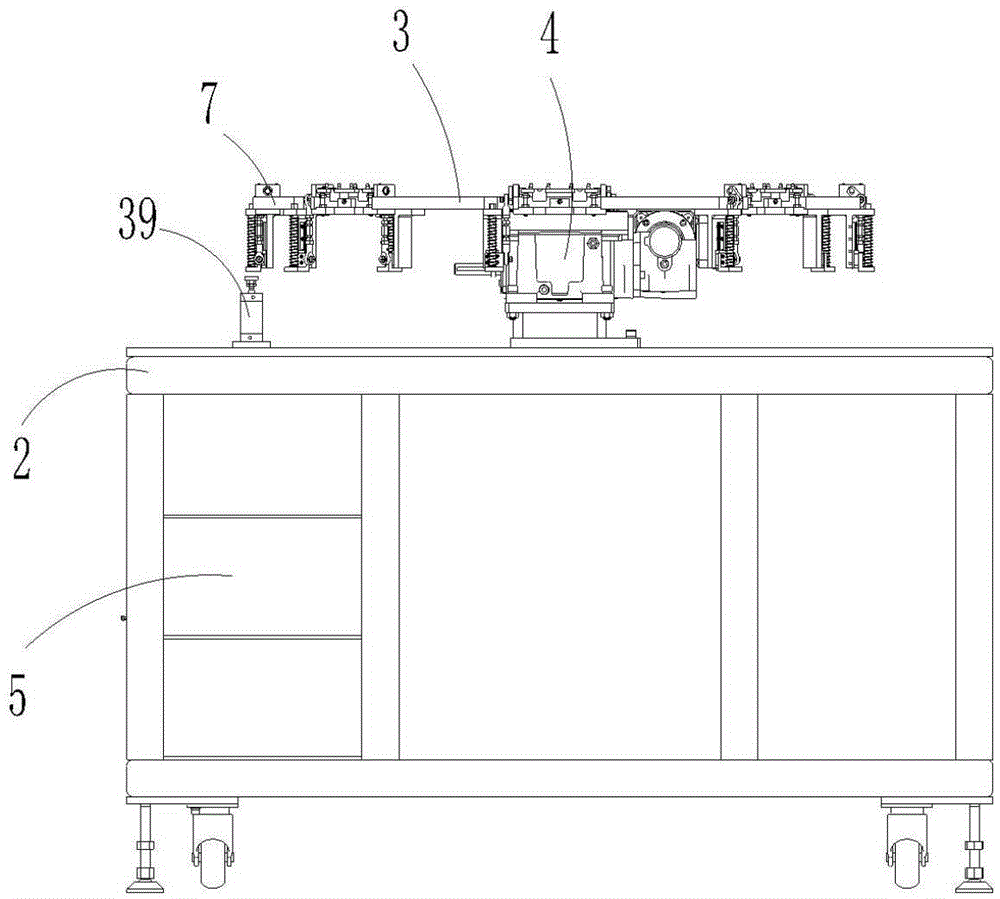
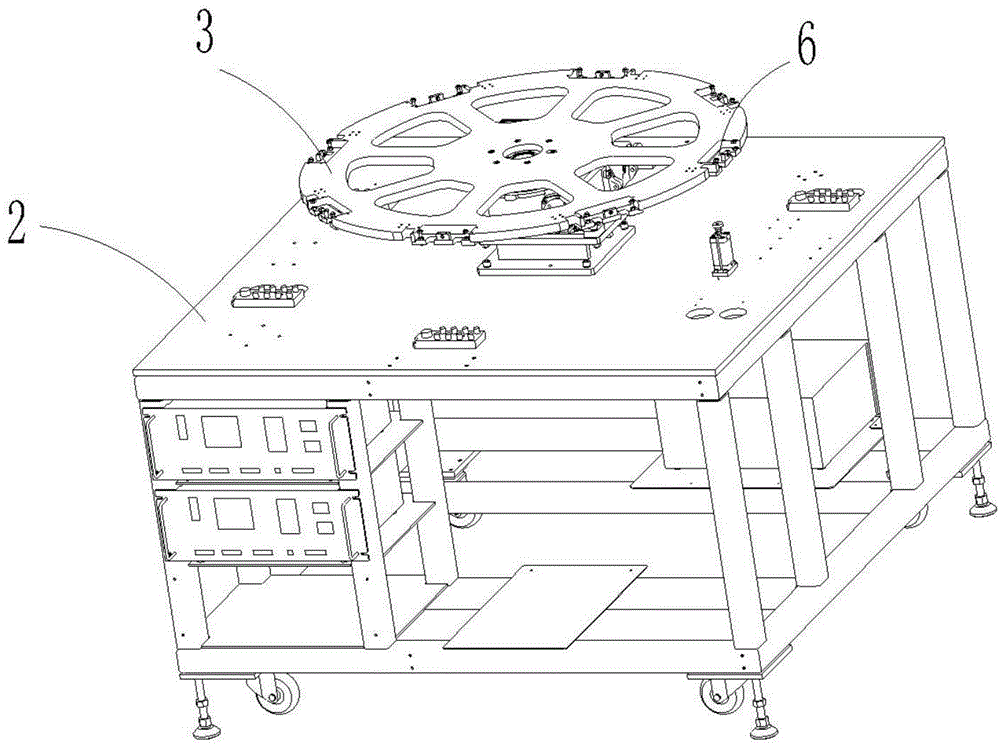
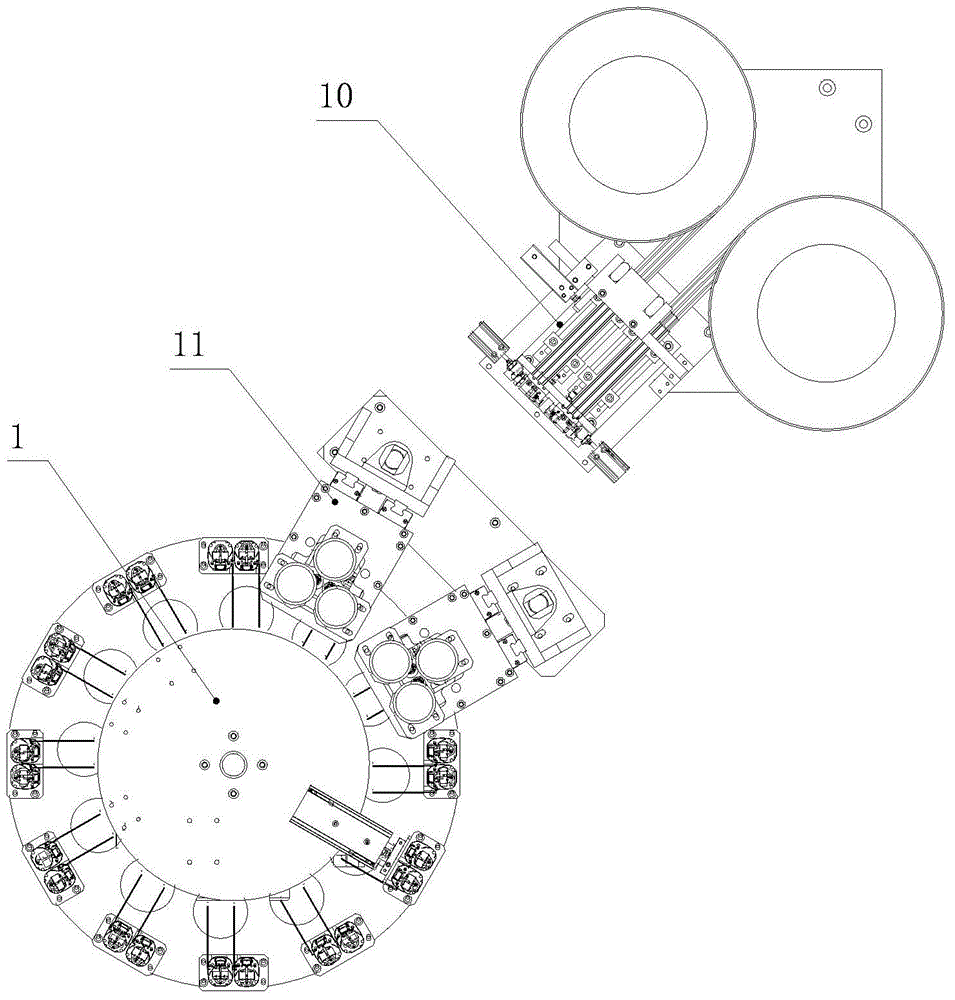
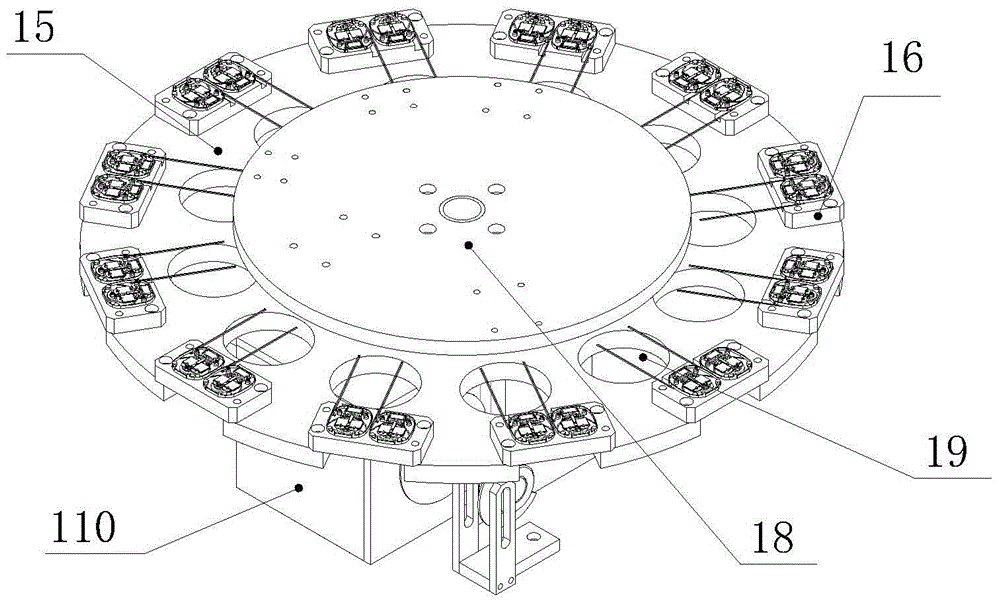
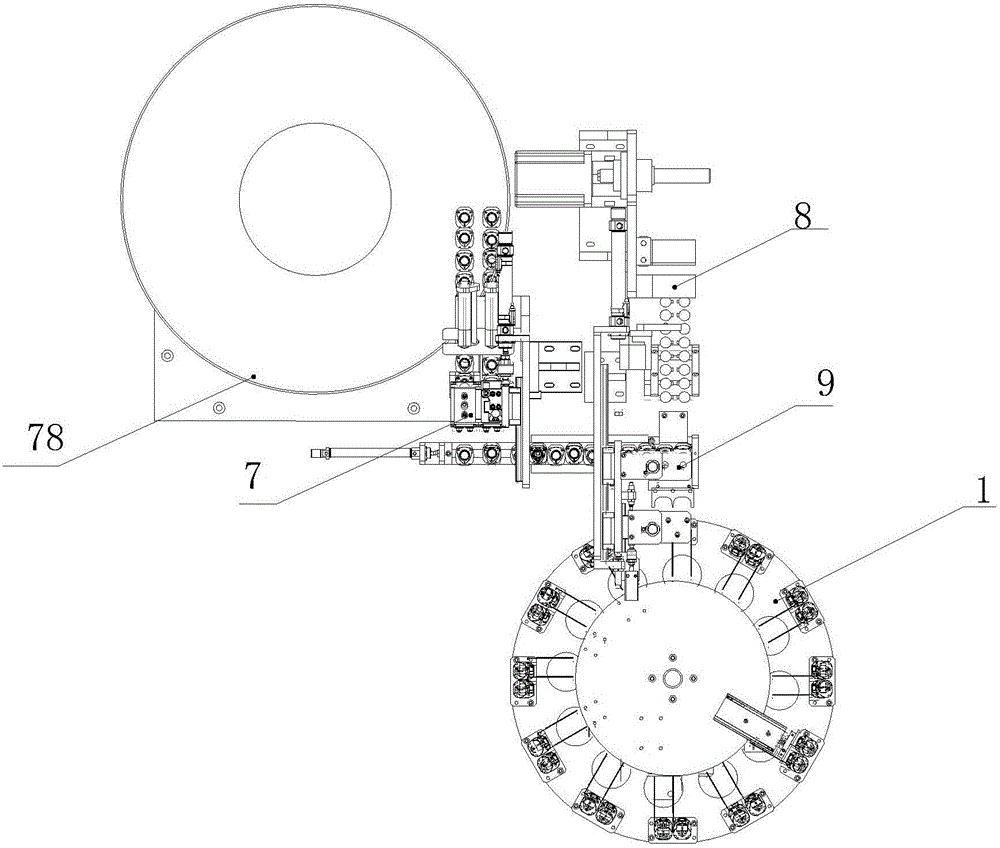
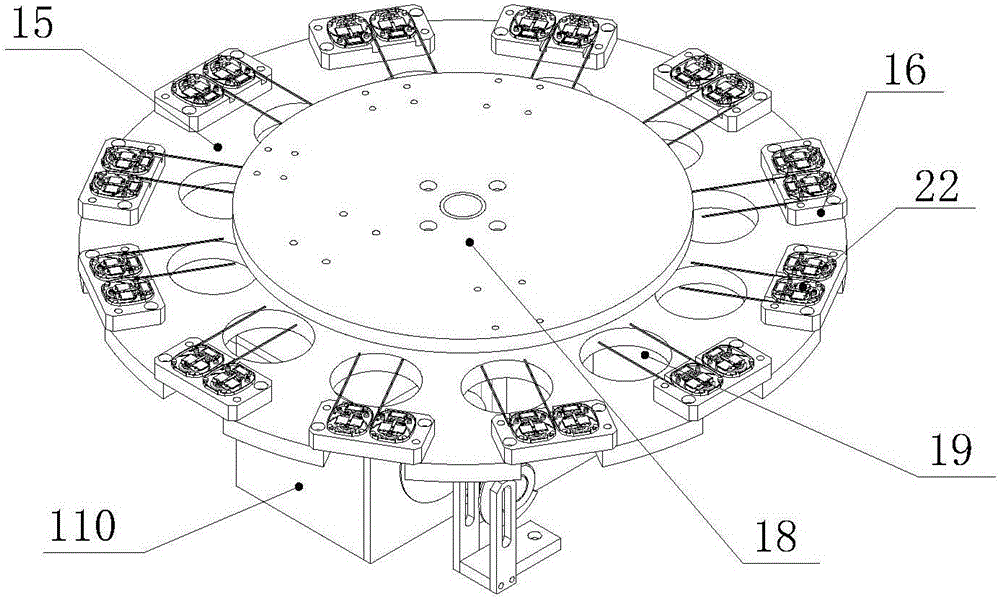
Security industry camera core assembly based automatic assembly system and method
ActiveCN104801968AImprove assembly efficiencyHigh degree of automationAssembly machinesCircular discCore component
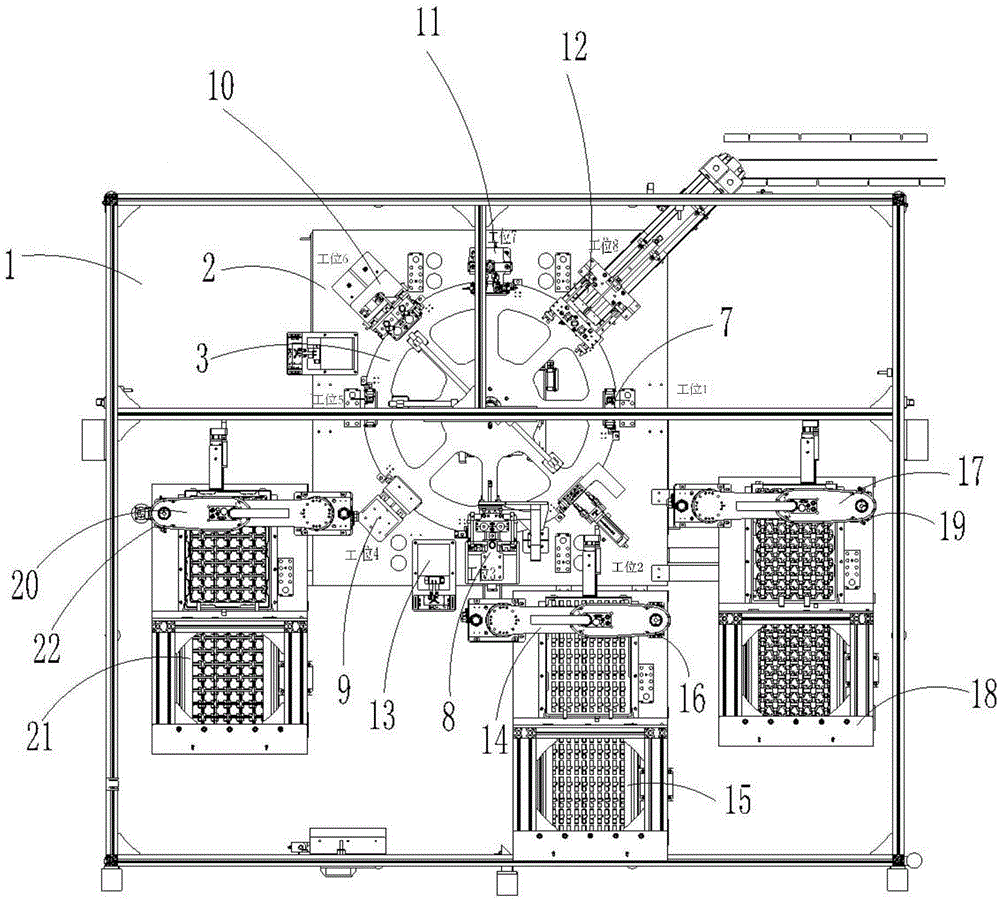
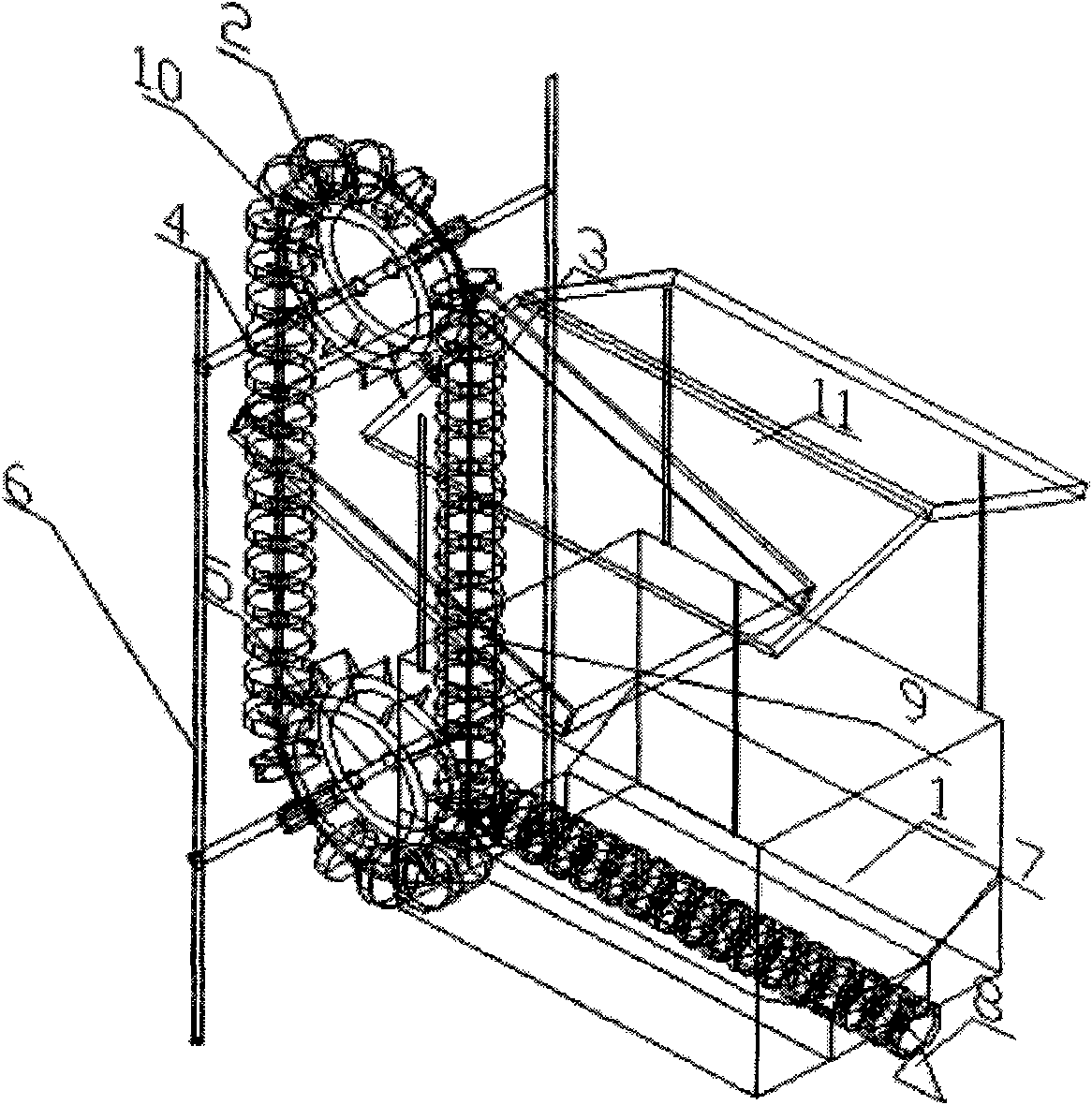
The invention relates to automatic assembly systems, particularly to a security industry camera core assembly based automatic assembly system and method. The security industry camera core assembly based automatic assembly system comprises an operation area; an operation frame is arranged in the operation area; an operation disk is arranged above the operation frame, wherein the operation disk and the operation frame are fixed; the rotation of the operation disk is controlled by an indexer; a controller is arranged in the operation frame; the edge of the operation disk is provided with at least six operation position assemblies which are distributed uniformly; the operation area comprises a turnover positioning fixture, a lens feeding robot assembly, a base feeding robot assembly, a lateral side nailing assembly, a PCB (Printed Circuit Board) feeding robot assembly, a rotary table fixture calibration assembly, a PCB nailing assembly, a bolt detection assembly, a discharging assembly and a screw feeding and distribution assembly. According to the security industry camera core assembly based automatic assembly system and method, the assembly efficiency is improved, the degree of automation is high, the product quality is improved, and the labor cost is reduced.
Owner:SIASUN ROBOT & AUTOMATION LIMITED BY SHARE
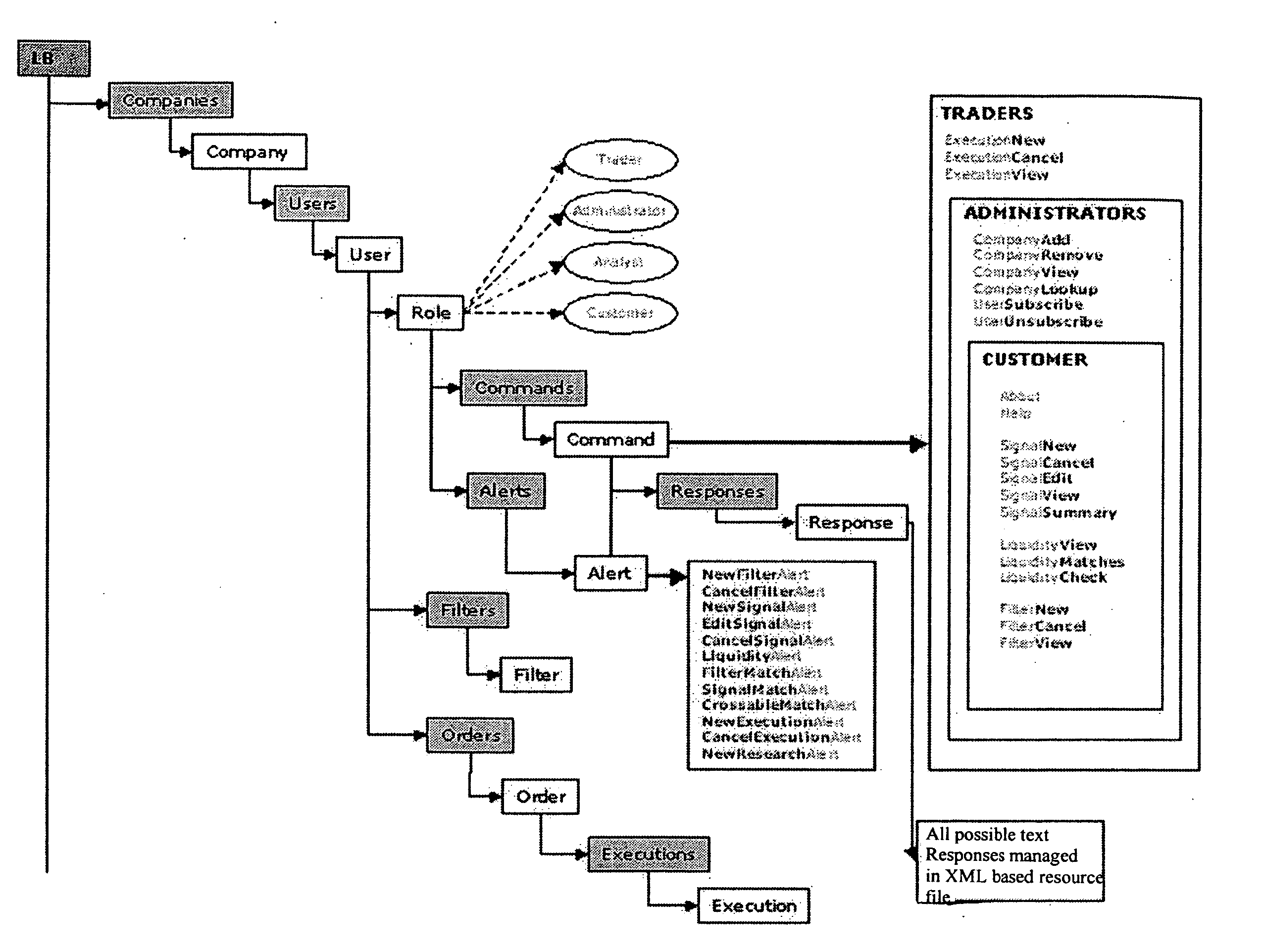
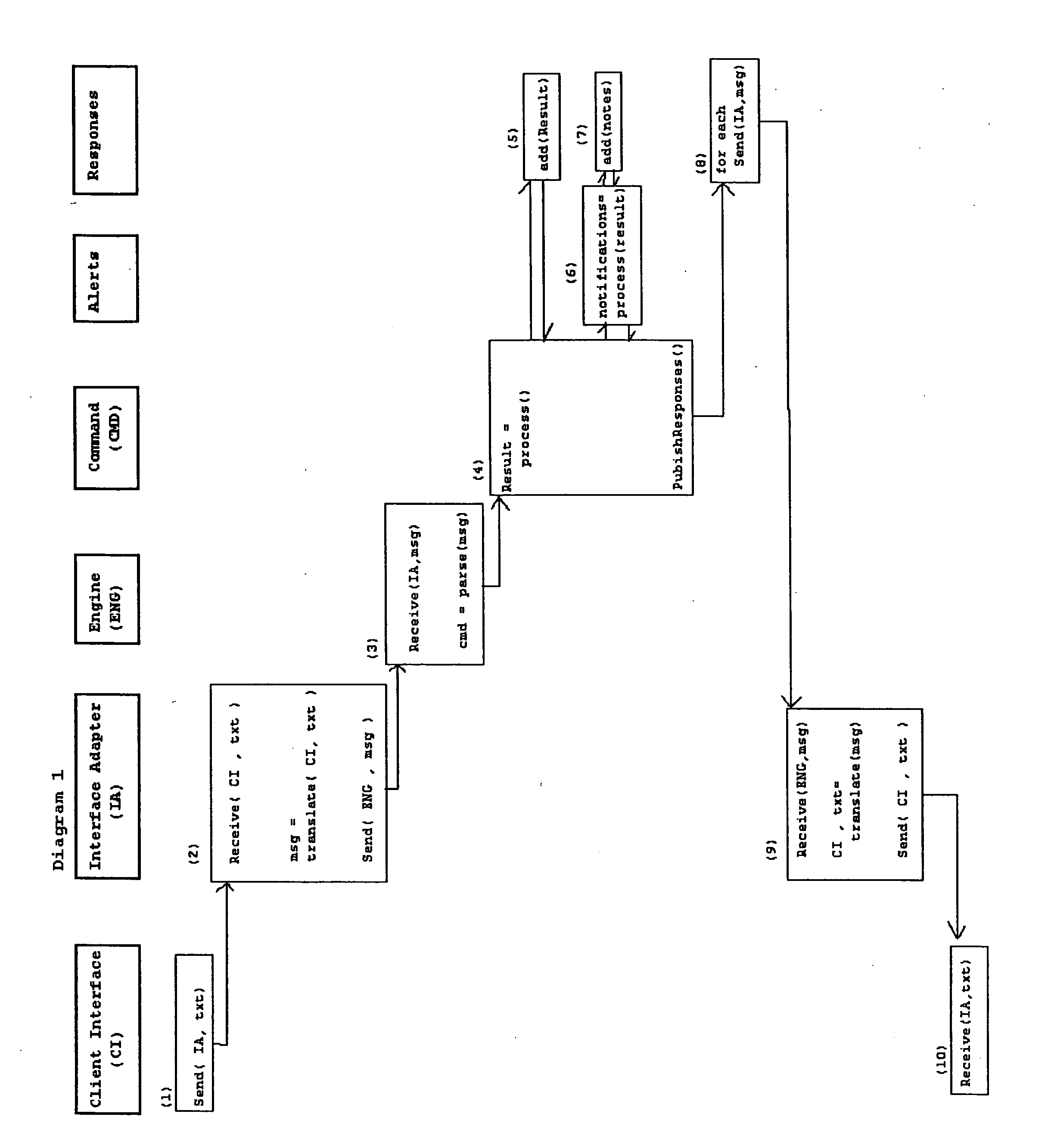
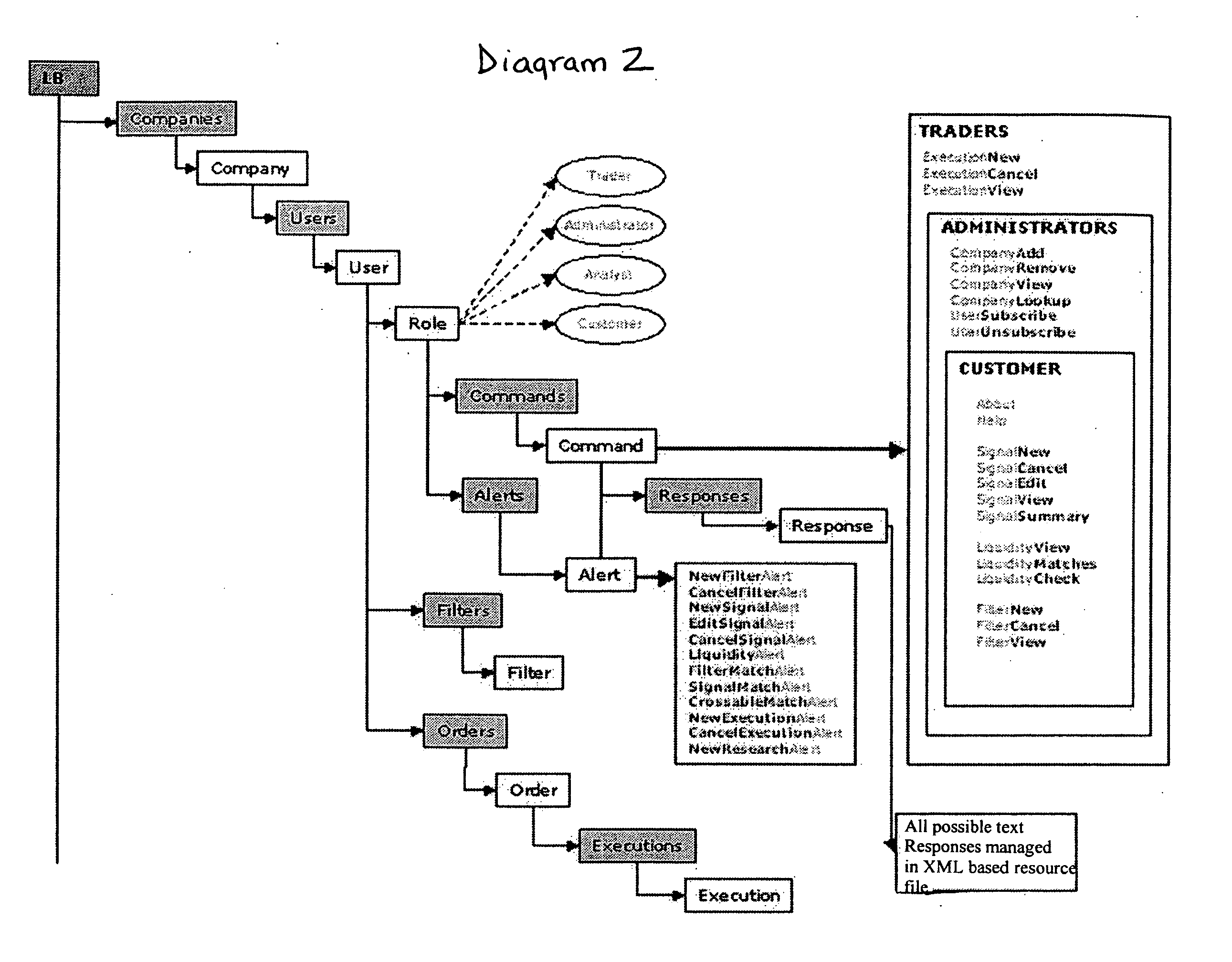
Liquidity book system and method
A system is disclosed for providing services related to the securities industry to customers of broker-dealers. The system comprises a broker-dealer services module providing for at least one of indications of liquidity and / or interest, order entry, order management, and order crossing. The system further comprises a service transport media module enabling formulation of an electronic message provided in a first format as a function of at least one of an instant message, cellular text message, e-mail message, interactive voice response message, and a hypertext markup language message. The system further comprises a plurality of system components enabling implementing the services, the system components comprising one or more of a database, a messaging engine, an interface adapter, a client interface and an order clearing interface, wherein the system electronically receives the electronic message and substantially automatically transforms the message into a second format and executes commands represented in the electronic message.
Owner:BLOCK ORDERS EXECUTION
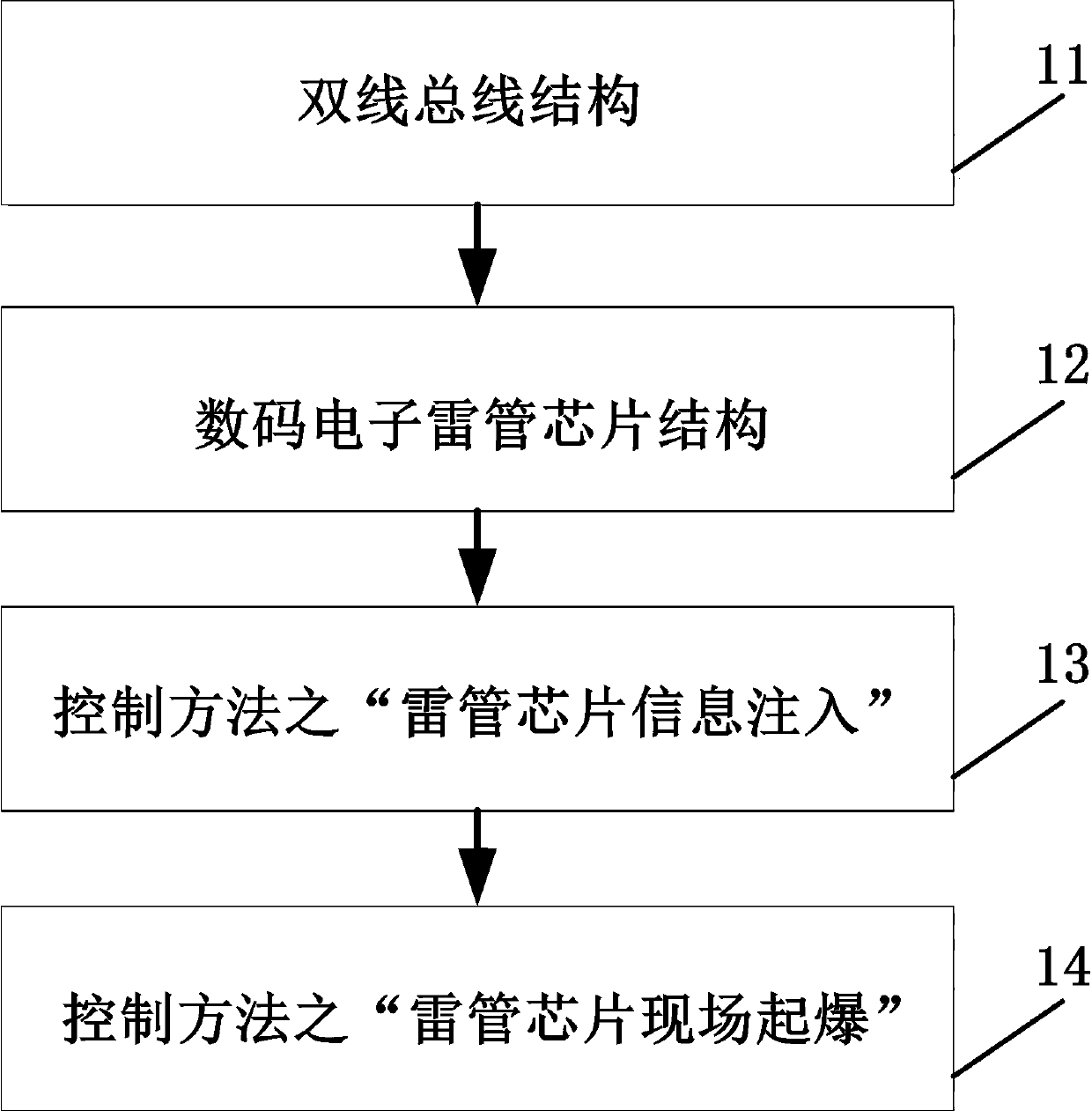
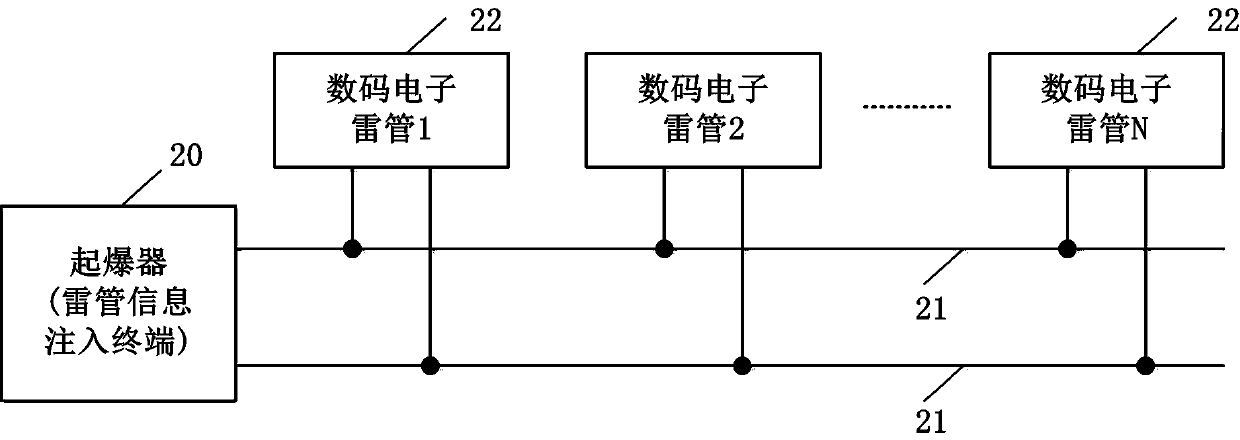
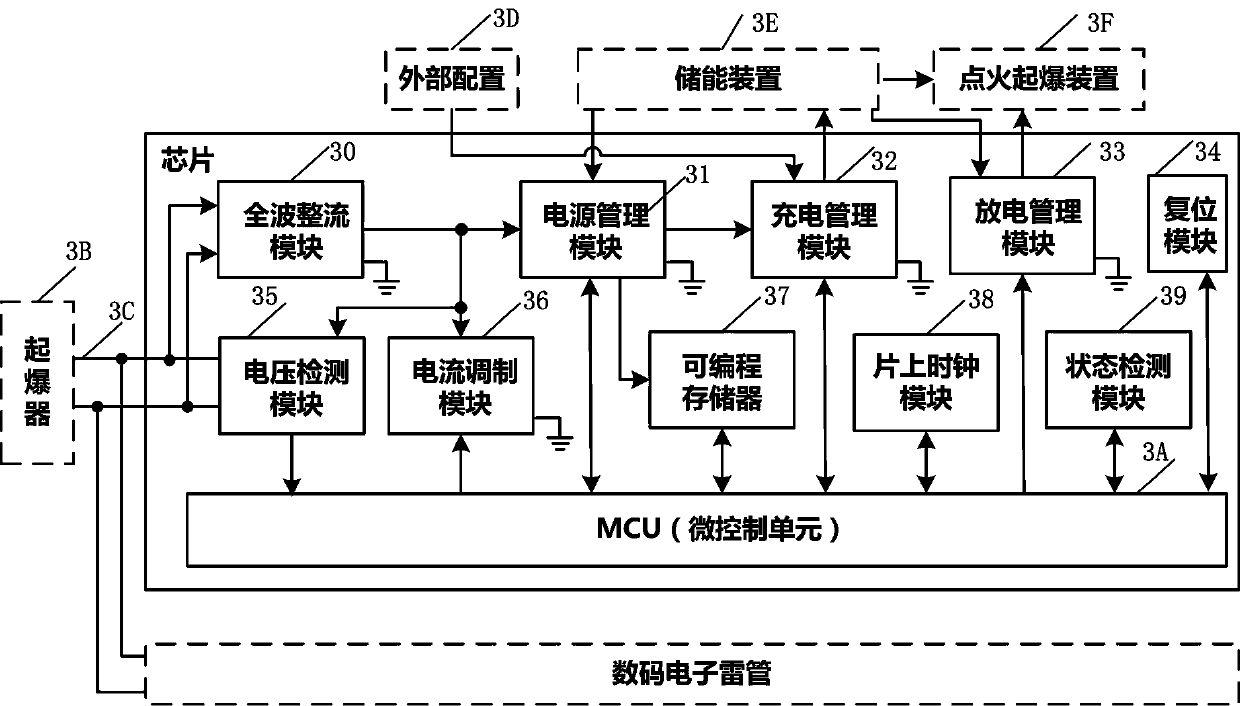
Digital electronic detonator chip based on double-wire bus and control method
ActiveCN109696097AImprove Clock Frequency AccuracyStandardize the control processBlastingDetonatorCommunications security
The invention relates to a digital electronic detonator chip based on a double-wire bus and a control method. The chip adopts the non-polar and one-leader-multiple-follower half-duplex type double-wire bus with communication and power supply functions, and communication of an amplitude and pulse width modulation modes is supported; during pulse width modulation communication, a downlink communication standard pulse width value can be configured according to needs, and a uplink communication standard pulse width value is fixed; the chip comprises all the function modules for completing the detonation operation and a communication instruction set, a charging voltage value can be externally configured; the chip control method is composed of 'detonator chip information injection and detonatorchip on-site detonation'; and through the mode, the digital electronic detonator chip and the control method can meet requirements and practical application demands of the latest Chinese public security industry standard, namely the 'Industrial Electronic Detonator Information Management General Rule(GA1531-2018) ', the anti-interference performance and the communication safety reliability are improved, the application scene is expanded, the configurability and the detonation safety of the chip are improved, the control process is standardized, improper operation is avoided, and the comprehensive cost is reduced.
Owner:华夏世昌(北京)科技有限公司
Peer based doctrine performance framework
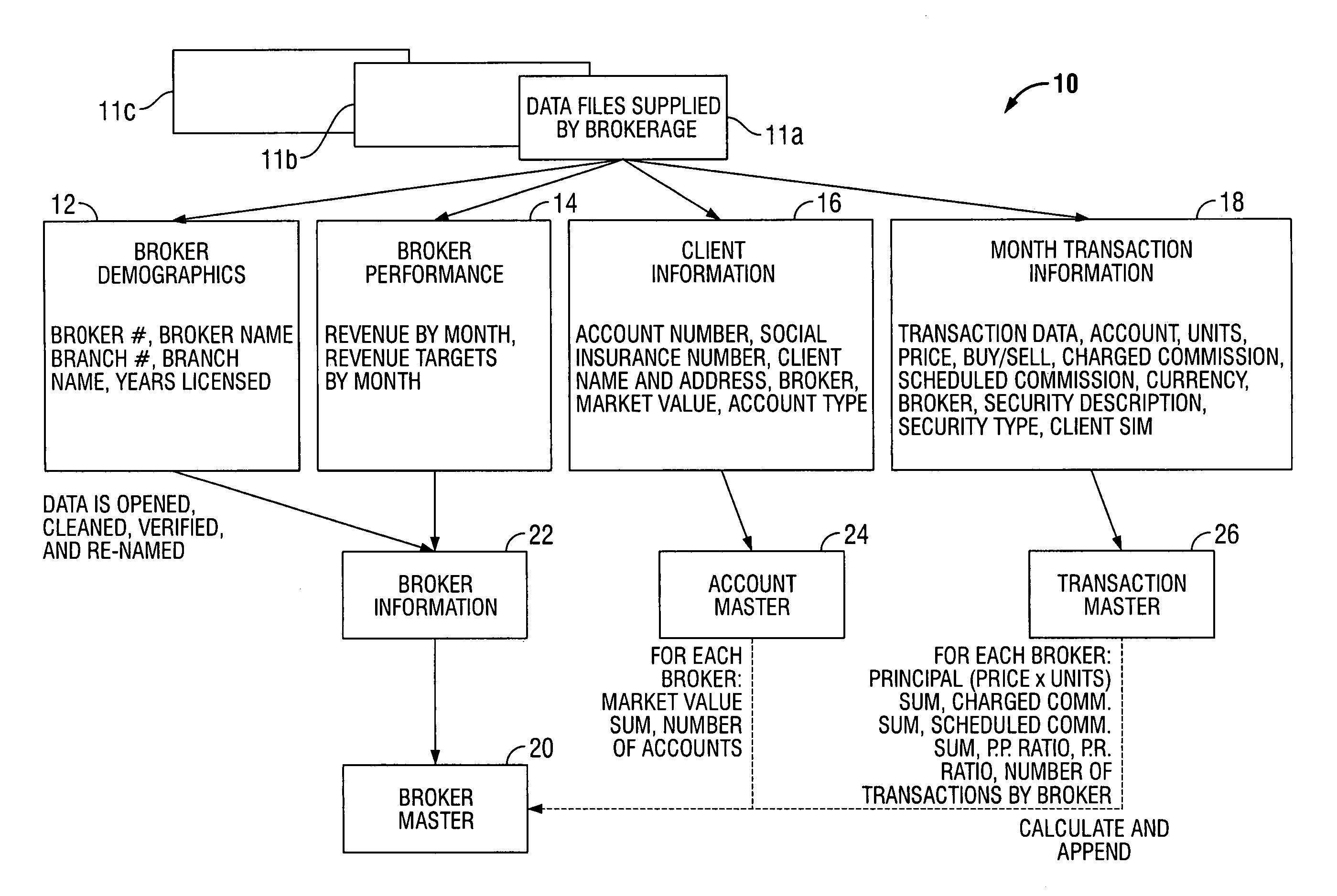
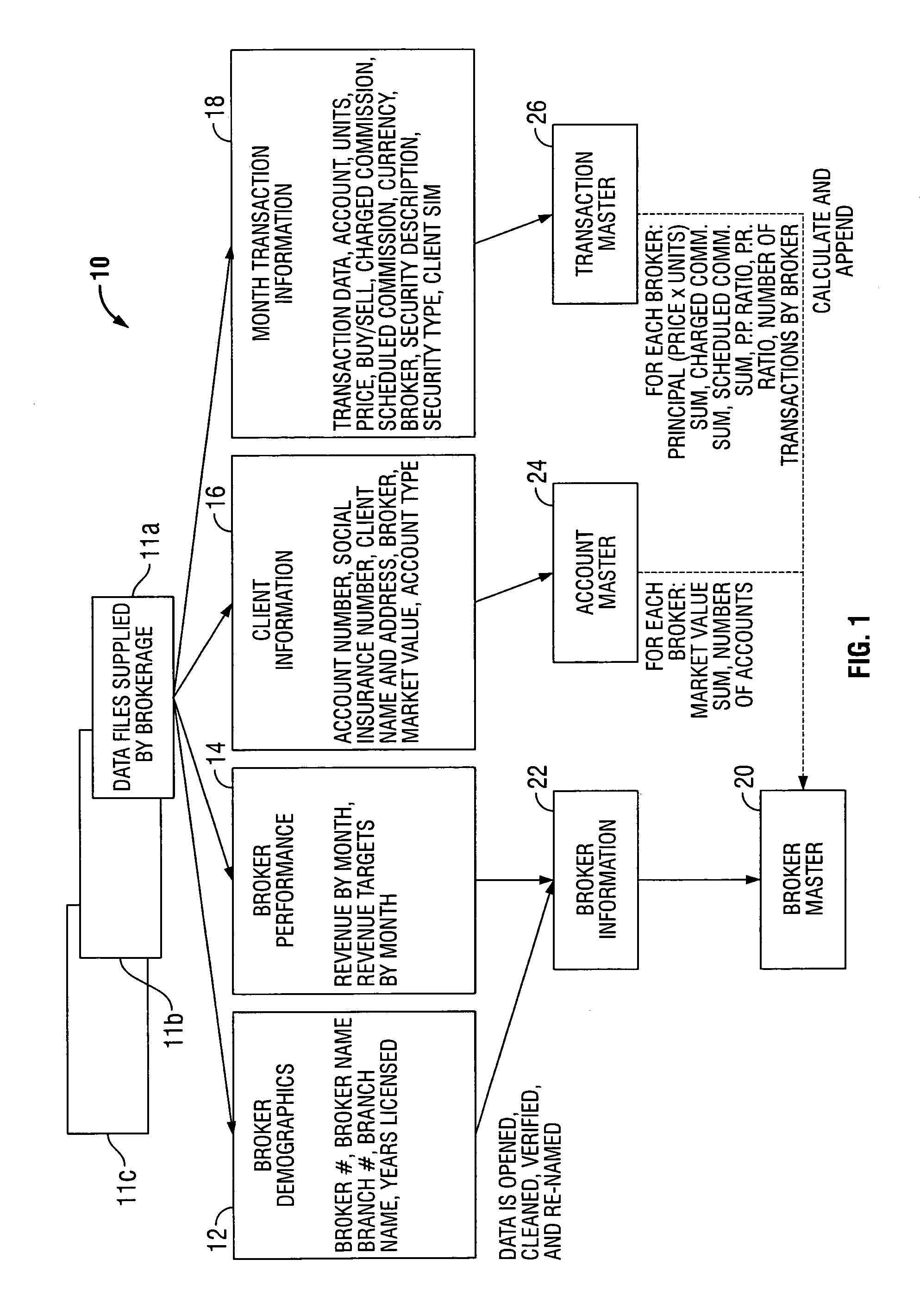
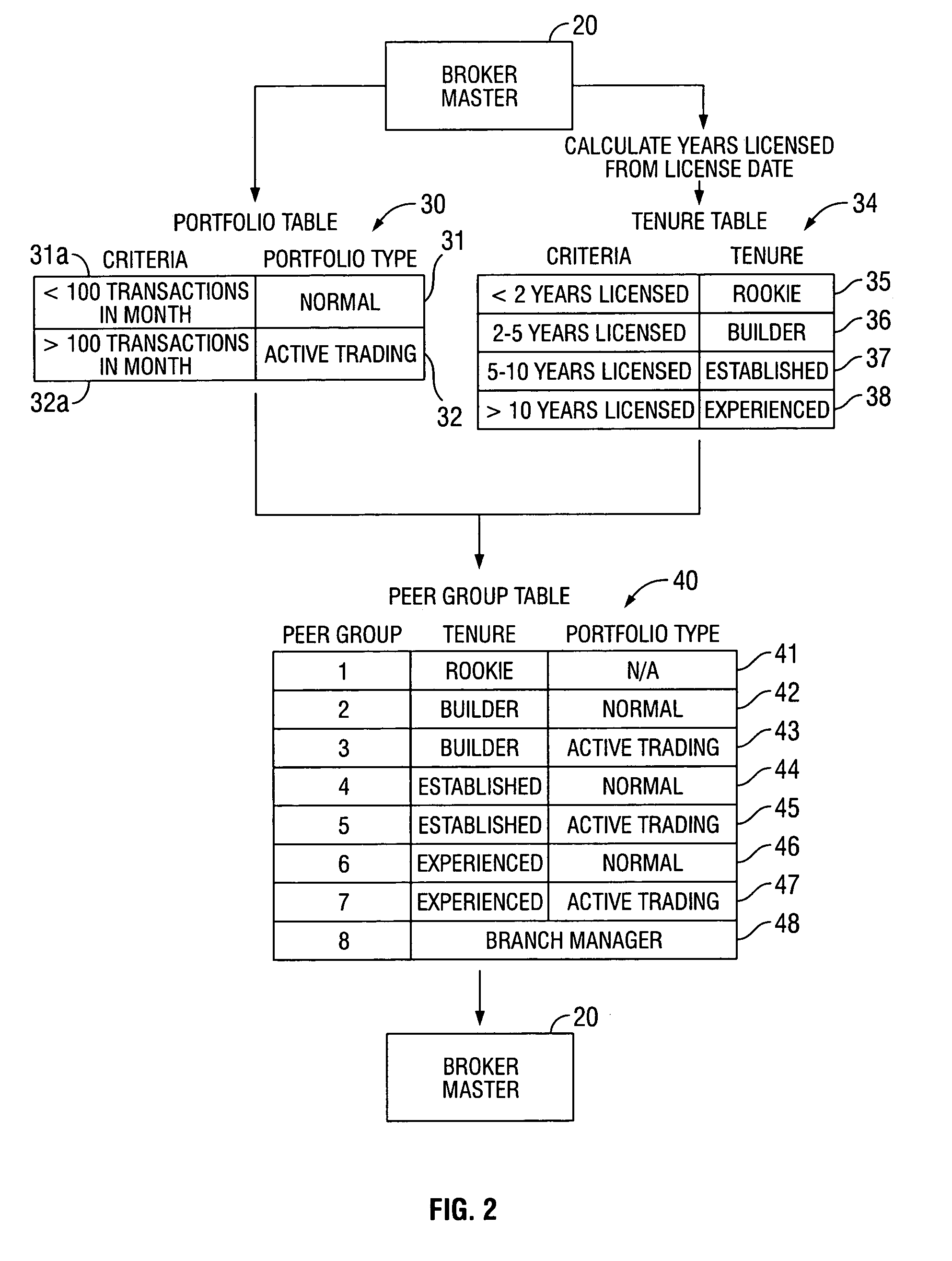
InactiveUS7028006B1High priceEasy to manageFinanceSpecial data processing applicationsStatistical databaseDemographic data
A securities transaction performance framework for developing an evaluation system directed toward the securities industry. The framework comprises a compilation of Broker demographics, a compilation of Broker performance data, a compilation of Client Portfolio information, and a compilation of periodic Transaction data including volume of Transactions, commission charged, and associated Broker information. The data compilations interface with a Broker Master to correlate a Broker to a statistical database as requested by the user. The Broker Master correlates financial statistics from Transaction data to Broker demographics and performance data so as to provide a performance evaluation system. Transaction data is stored in a secure environment and is able to provide historical analysis upon request of the end user.
Owner:MCKINSEY PM CO
Ventilation and air-drying system for grain store of grain depot
InactiveCN102090227ASimple structureEasy to operateAgriculture tools and machinesConveyorsGrain storageSocial effects
The invention relates to a grain air-drying and ventilation system for a grain store of a grain depot in the grain storage security industry, which aims to solve the problems of high cost of grain storage, air-drying, ventilation and the like, difficulties in the gathering and warehousing of grains in cloudy and rainy days, high labor intensity and waste of time. The scheme is that: a cylindrical hoisting device is arranged on the outer wall of the grain store of the grain depot; the lower part of the grain store of the grain depot forms an inverted prismatoid; an axial screw is arranged on the lowest part of the inverted prismatoid; an inclined air-drying surface is formed on the grain store of the grain depot; the upper part of the grain store of the grain depot realizes the ventilation and air-drying of the grains by utilizing natural wind and sunshine; and the axial screw is arranged at the wall bottom of the grain store of the grain depot to convey the grains of the inverted prismatoid to the cylindrical hoisting device, and the hoisting device hoists the grains at the bottom onto the inclined air-drying surface on the grain store, so the grains are air-dried on the inclined air-drying surface, slide down by self weight and are ventilated for mould prevention, corrosion prevention and temperature reduction by the natural wind. The system has a simple, novel and unique structure, is simple and convenient to use and operate, ensures low labor intensity and remarkable economic efficiency and social effects, can realize the mechanization and automation of a grain air-drying system and greatly improve the labor efficiency, and is a great innovation in the grain storage industry.
Owner:HENAN POLYTECHNIC UNIV
Search method of real-time vertical search engine for security industry
InactiveCN103793418AImprove efficiencyTimely search resultsWeb data indexingSpecial data processing applicationsOpinion analysisThe Internet
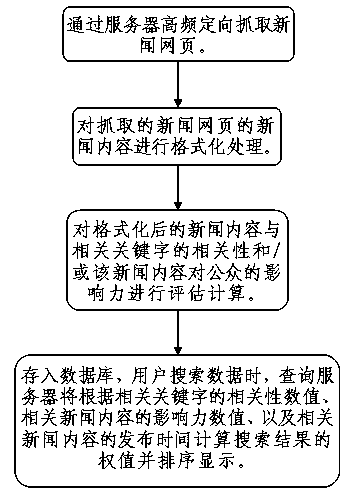
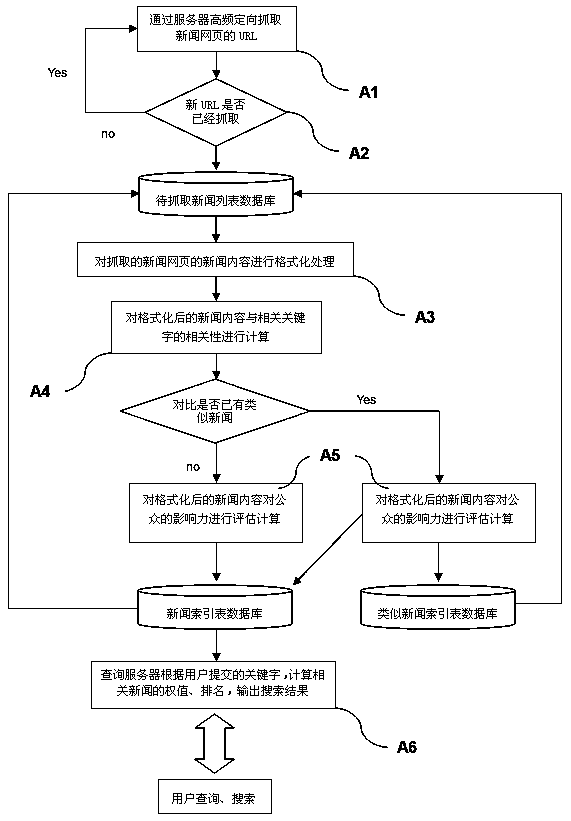
The invention relates to a search method of a real-time vertical search engine for a security industry. The search method comprises performing high-frequency directional fetching on news web pages through a server; performing formatting processing on news content of the fetched news web pages; performing evaluation calculation on the relevance of the formatted news content and relevant keywords and the influence on the public of the news content; storing results into a database and calculating weights of the search results according to multiple parameters and sorting and displaying the search results through a system when users search data. Accordingly, the passive synchronization of the search engine information and an information source can be achieved and the problems that the general search engine by the traditional search method is poor in timeliness and repeated in information are solved; the directional collection is only performed on an industry representative financial news release source of the Internet and accordingly the efficiency is high and the search results are timely and accurate; in addition, the search method is combined with a public opinion analysis technology and accordingly the search results can be sorted in multiple modes and the display effect is humanized.
Owner:ZHUHAI FOXX NETWORK TECH
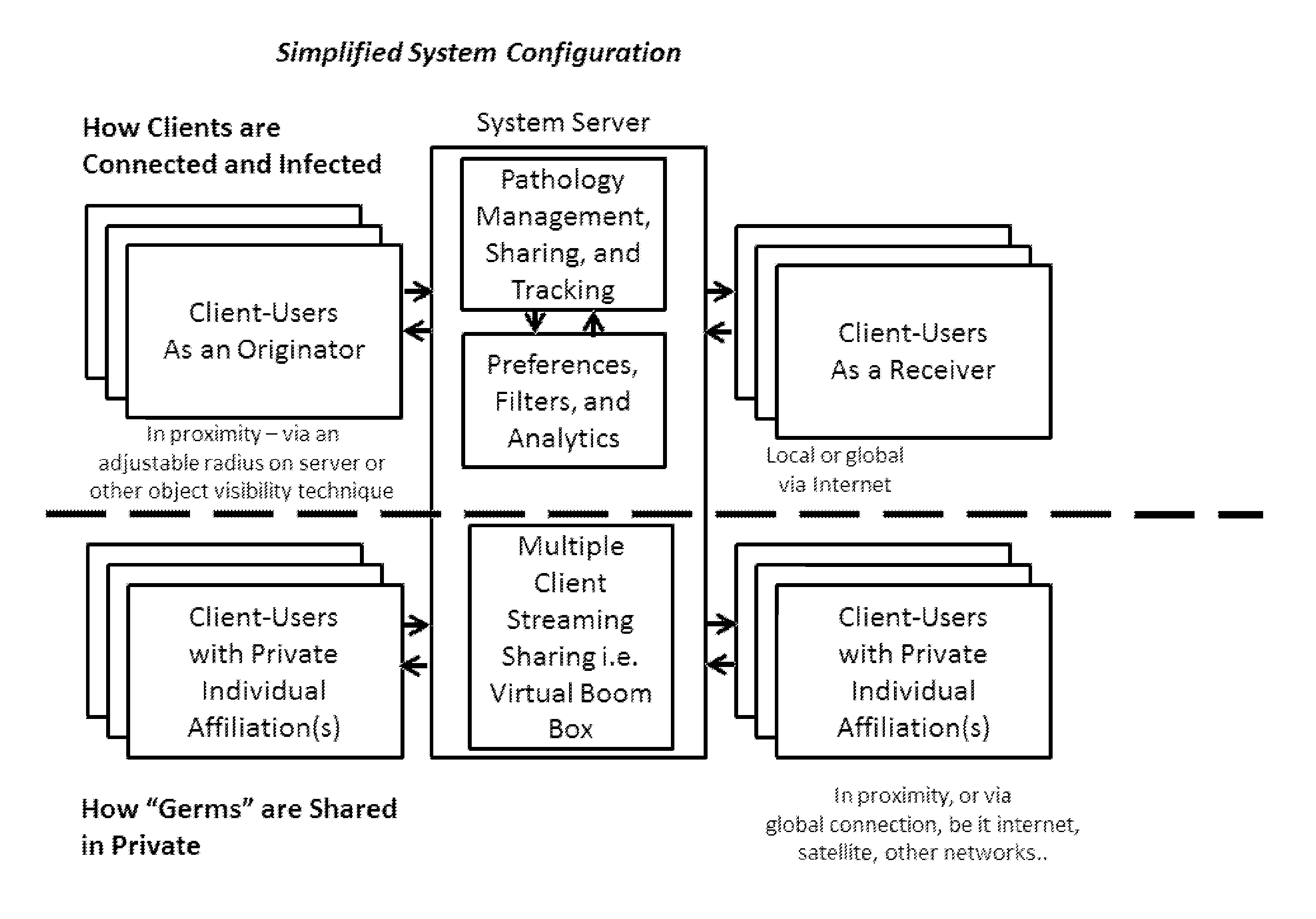
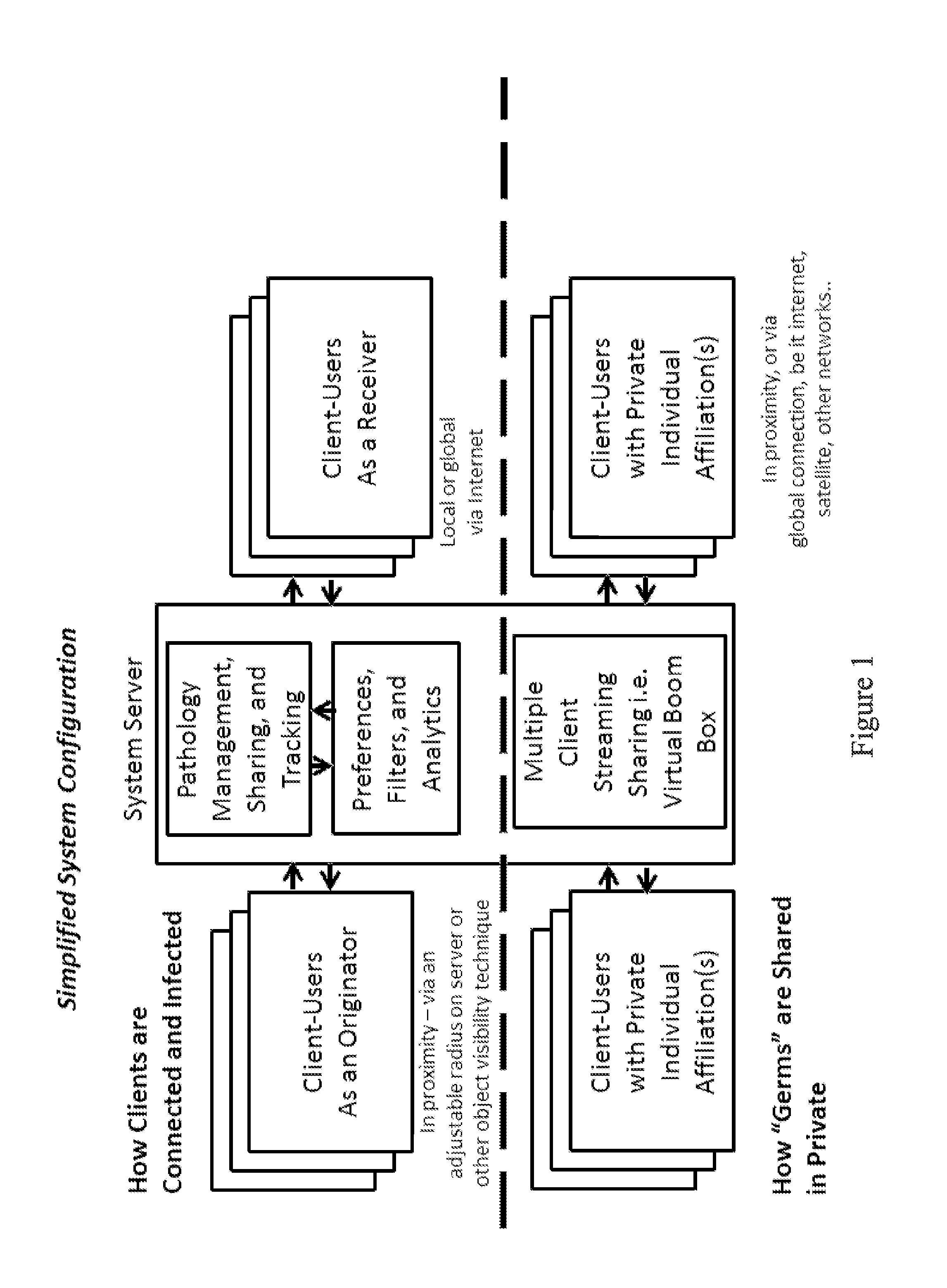
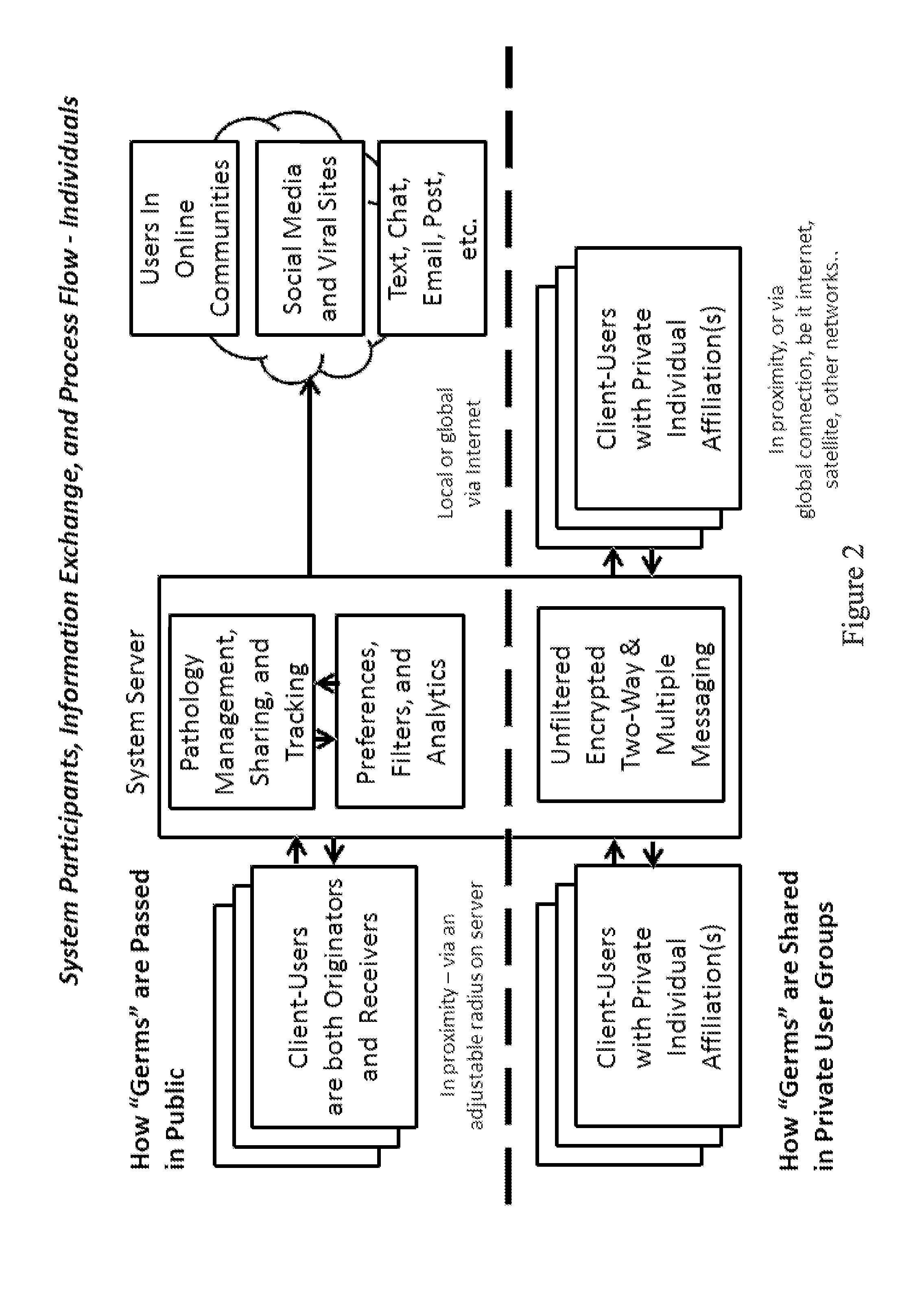
Method and apparatus to anonymously communicate encrypted content between mobile devices in proximity and in expanded user communities in a contagious, viral manner
InactiveUS20140257953A1Promote disseminationFacilitates local transmission and viral disseminationAdvertisementsInformation dispersalSocial media
An information dissemination method and apparatus facilitates transmission of information to primary receivers and re-transmission to secondary receivers using native mobile devices, without necessarily depending on friends lists or the internet. The chain of transmission “links” can be tracked and logged, and users in the chain can be rewarded for participating. The information, referred to as “germs,” can be generated, propagated and spread in a viral manner, wherein the germs are filtered and exchanged among users in close proximity, within a pre-registered user group, or through the internet. Embodiments can be used for one-to-one and one-to-many communications in the social media, advertising, and / or security industries, and do not require client-users to know each other or be on friends lists. Preference settings, rules, behavior tracking algorithms, semantic data analytics, and manual censorship can be individually or collectively utilized in the peer selection and filtered germ dissemination processes.
Owner:VYRAL LIMITED LIABILITY
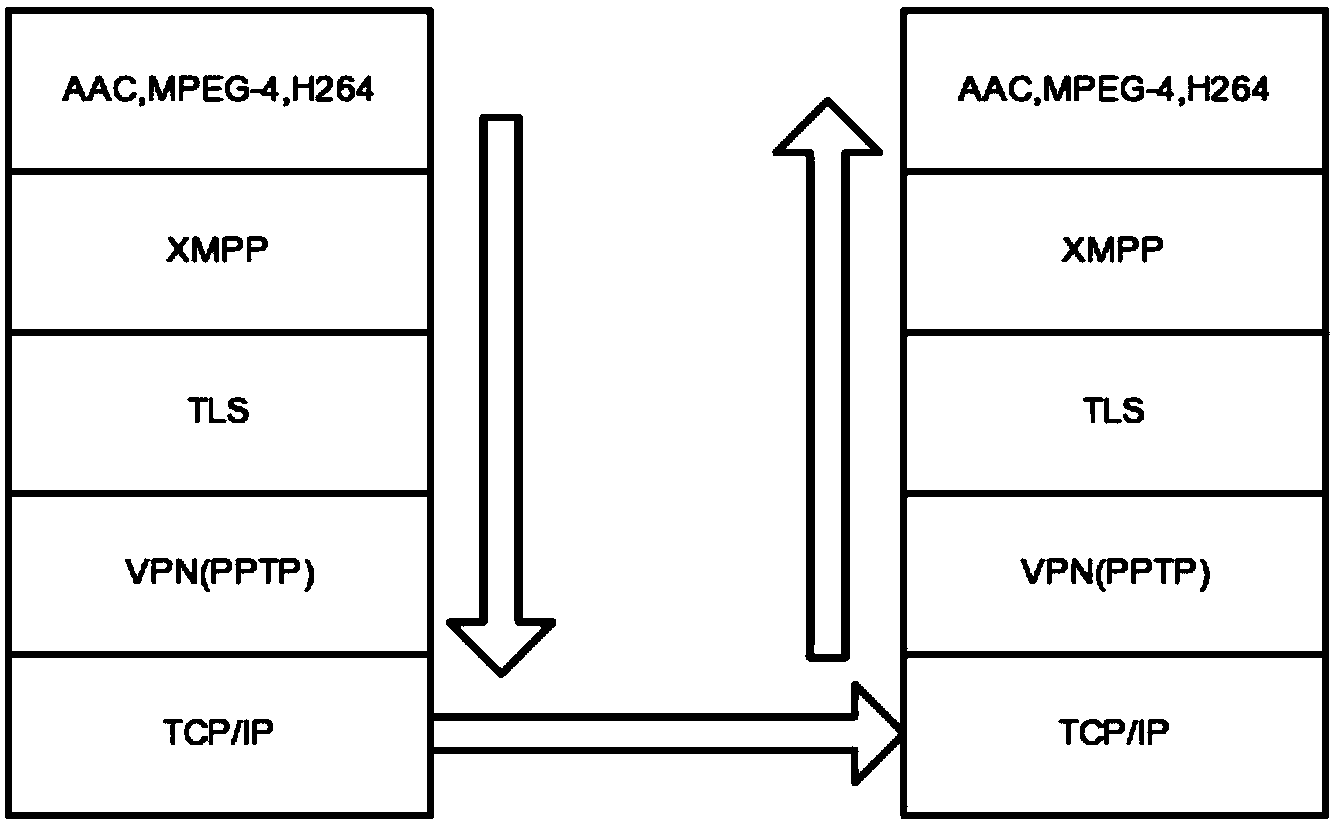
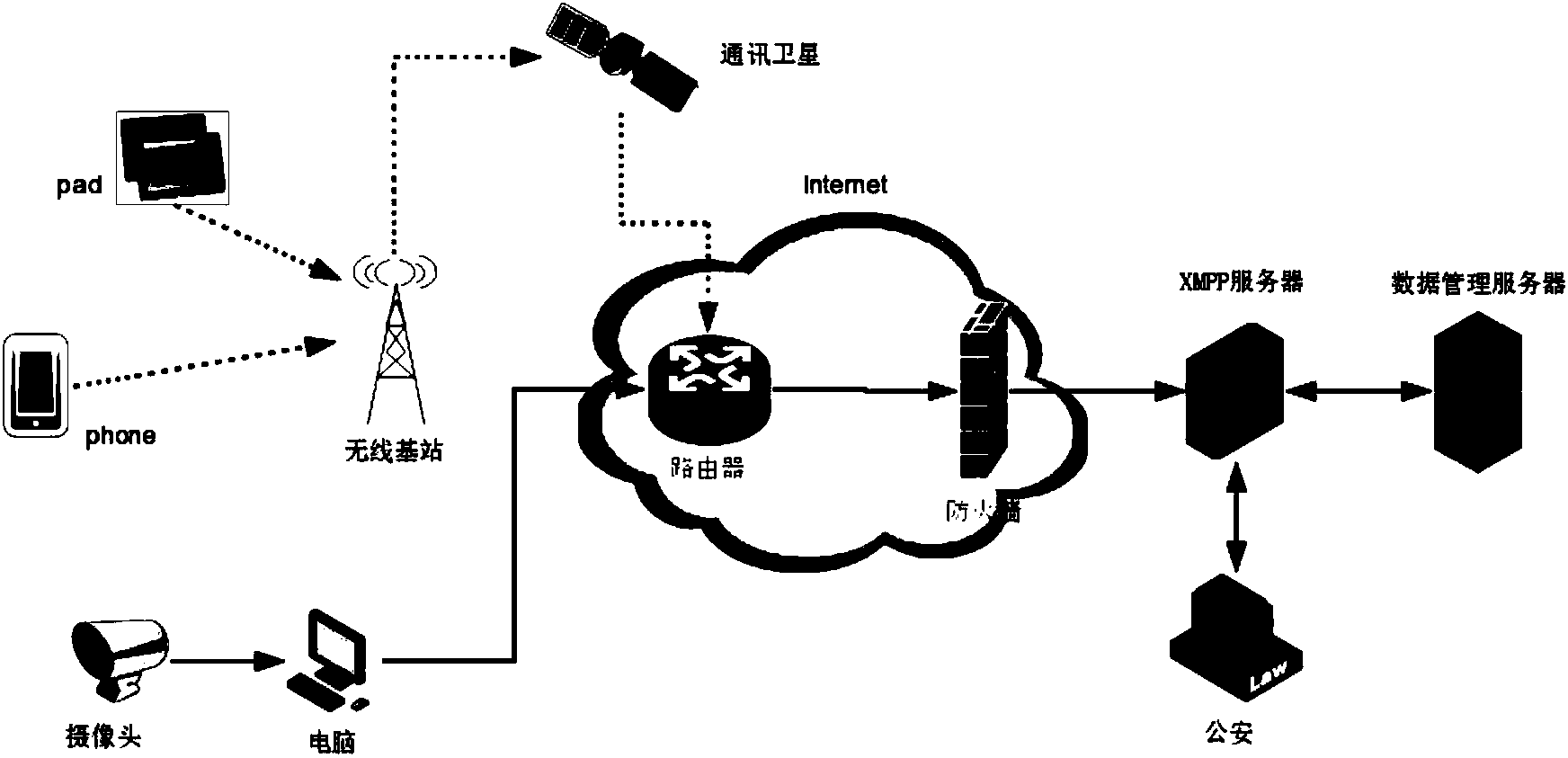
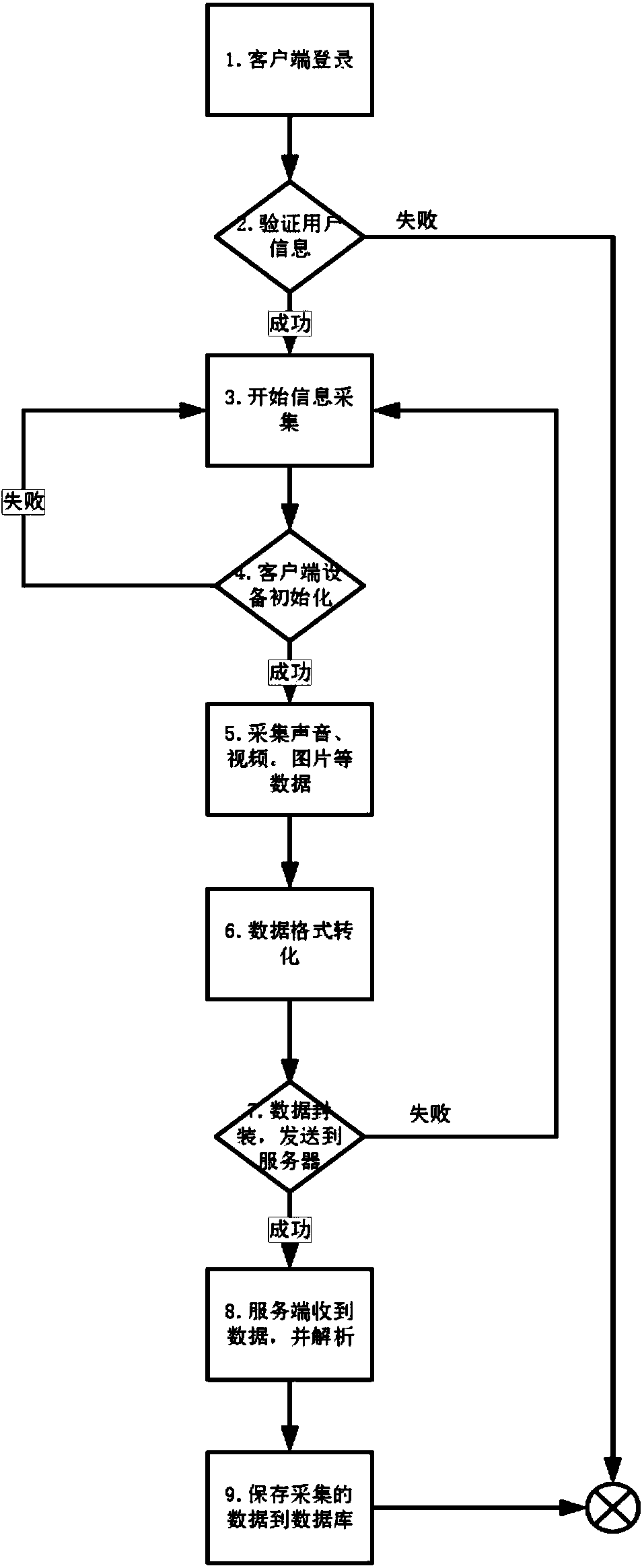
Security industry data collecting method and system implemented on basis of XMPP
InactiveCN104243477AGuaranteed data collection needsEnsure safetyTransmissionData streamData management
The invention discloses a security industry data collecting method and system implemented on the basis of an XMPP. The method includes the following steps that a client-side is connected to an XMPP server, the XMPP server verifies a real name or a police number submitted by the client-side, connection succeeds if the real name or the police number passes verification, and connection fails if the real name or the police number does not pass verification; the client-side carries out initialization on information collecting equipment, stores the collected information to be data flow, carries out format conversion and compression on the data flow, and packages the data flow by the utilization of the XMPP, the packaged data flow is inserted into XML data flow, and the XML data flow is encrypted according to a DES and then transmitted to the XMPP server; the XMPP server receives the encrypted data, decrypts the data to be the XML data flow for analysis, and restores the XML data flow to be a resource file; the analyzed resource file is stored to a data management server so that other client-sides of a security system can search for the file. People in the security industry can apply the method with the fixed and mobile client-sides utilized for collecting data whenever and wherever conveniently, and working efficiency is improved.
Owner:MASSCLOUDS
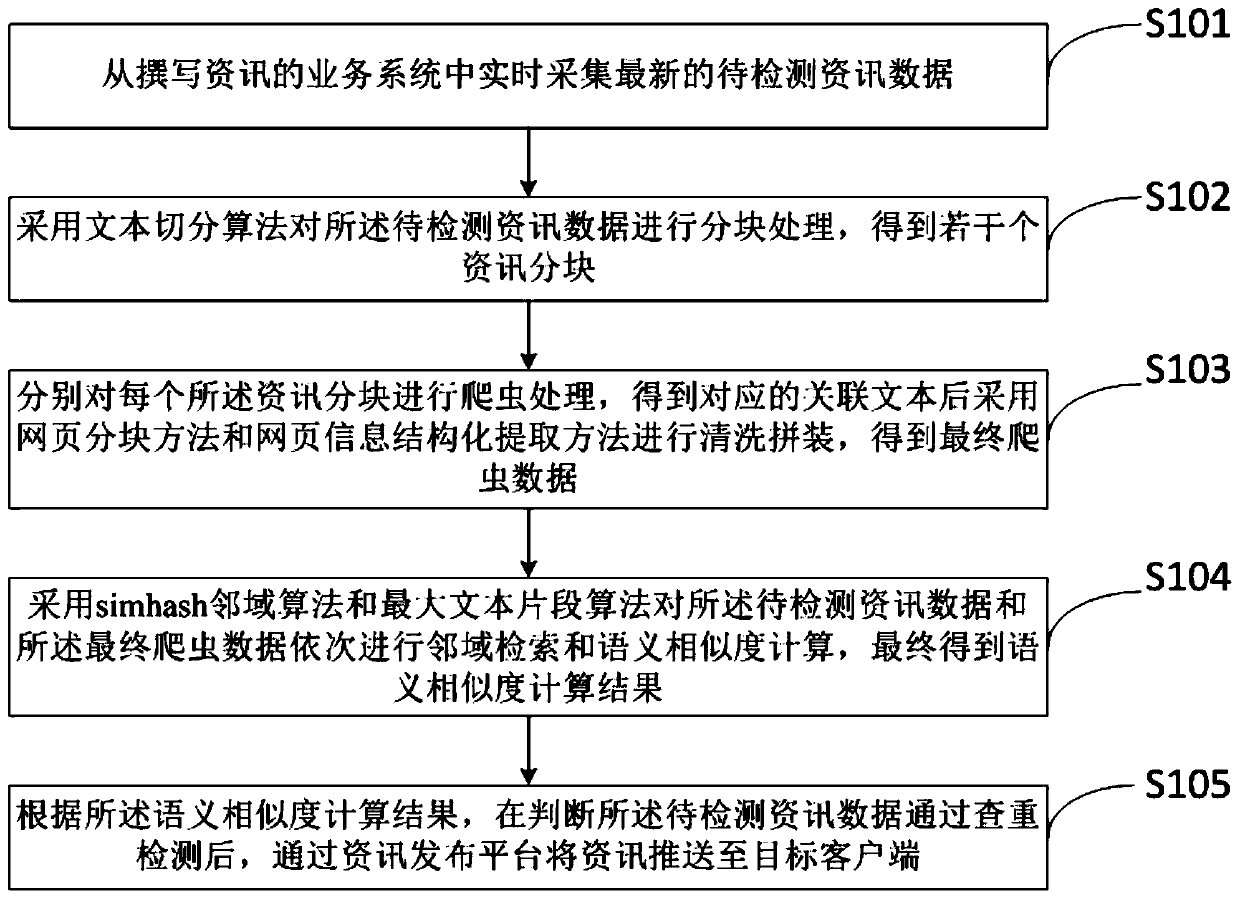
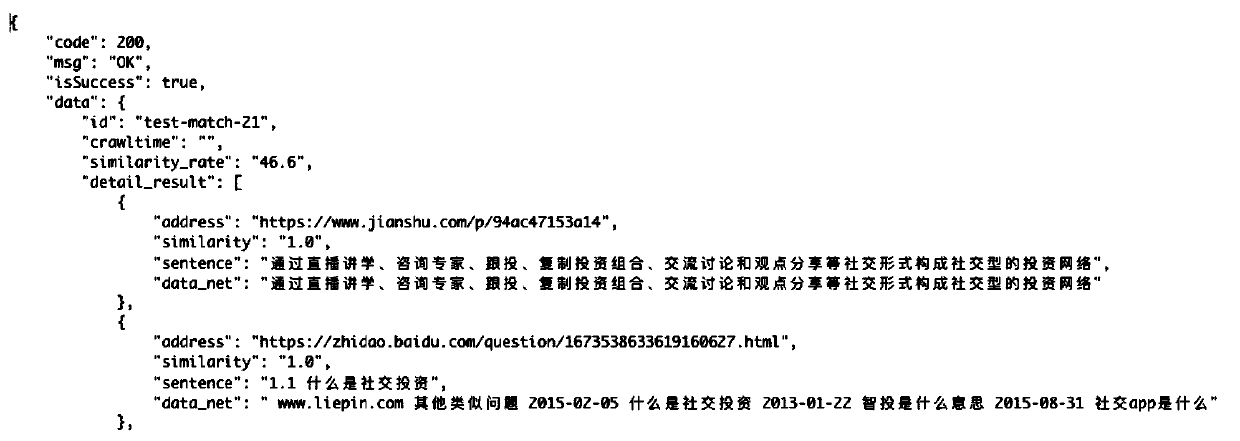
Security information duplicate checking method and system based on semantic analysis
PendingCN110321466ASolve the problem of original detectionHigh precisionFinanceWeb data indexingWeb pageData mining
The invention discloses a security information duplicate checking method and system based on semantic analysis. The method comprises the steps of collecting latest to-be-detected information data in real time from an information writing service system; blocking the to-be-detected information data by adopting a text segmentation algorithm to obtain a plurality of information blocks; conducting crawler processing on each information block, conducting cleaning and splicing through a webpage blocking method and a webpage information structured extraction method after corresponding associated texts are obtained, and obtaining final crawler data; and sequentially performing neighborhood retrieval and semantic similarity calculation on the information data to be detected and the final crawler data by adopting a simhash neighborhood algorithm and a maximum text fragment algorithm to finally obtain a semantic similarity calculation result. According to the method, a simhash algorithm and a maximum text fragment algorithm are provided and organically combined with a crawler system, the problem of original detection of security industry information is solved on the premise that a text library does not need to be established, and duplicate checking accuracy and efficiency are improved.
Owner:GF SECURITIES CO LTD
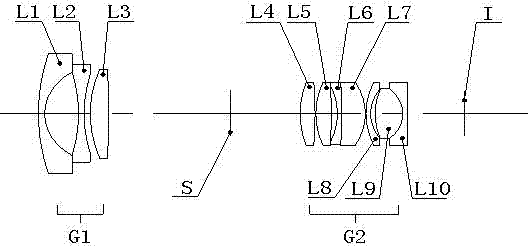
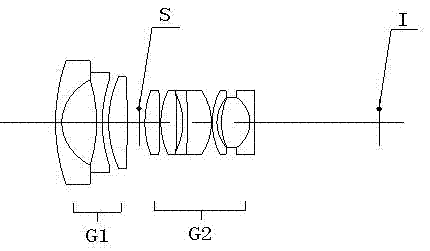
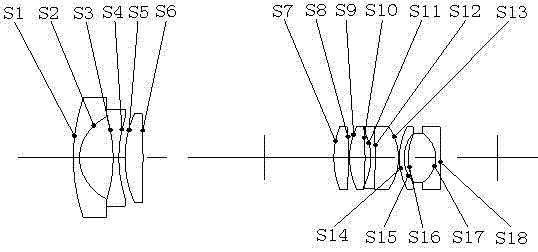
High-resolving force optical zoom lens with large target surface
The invention relates to a high-resolving force optical zoom lens with a large target surface, and belongs to the field of optical and mechanical integration. The high-resolving force optical zoom lens with the large target surface sequentially comprises a first lens group G1 with negative power, a diaphragm and a second lens group G2 with positive power from an object side to an image side. The focal length of the lens is charged through moving the second lens group G2, and the change of the position of the zoomed image surface is compensated through moving the first lens group G1 to ensure that the position of the inner image surface within the whole zooming range is unchangeable. The target surface of the optical zoom lens is 1 / 2 cun, wherein the cun is a unit of length. In the whole focal length section, values of an optical modulation transfer function (MTF) of the lens are all more than 0.3 at a place of 1301p / mm, which ensures that the resolving force can realize high definition corresponding to mega pixel within the whole focal length section, thereby adapting to the development tendency of a security industry, and having wide market prospects.
Owner:FUZHOU DEV ZONE HONGFA OPTOELECTRONICS TECH
Intelligent digital security system
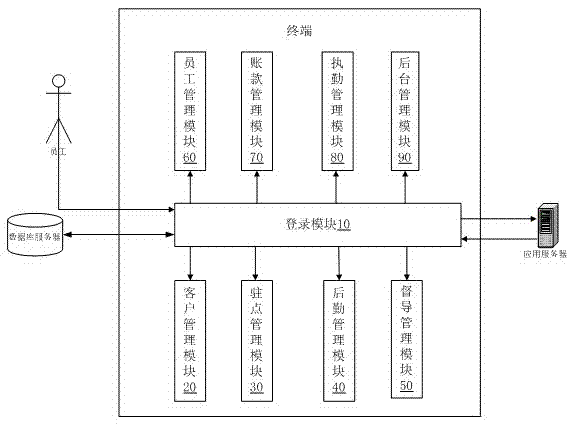
InactiveCN106940831AImprove efficiencyAchieve integrationResourcesInternal managementLogistics management
An intelligent digital security system comprises a terminal and a database server connected with the terminal. The terminal comprises a login module, a customer management module, a stationary point management module, a logistics management module, a supervisory management module, an employee management module, a fund management module, a duty management module and a background management module. The intelligent digital security system provides a big data interactive platform of the security industry, achieves real data integration and sharing by integrating the data, improves worker deployment and emergency treatment capabilities, customizes a functional module, improves an internal management process module, and strengthens the management system and flows of a company to achieve compact and standardized management and improve business capabilities.
Owner:上海英盾保安服务有限公司
Security industry oriented intelligent public opinion monitoring method and system
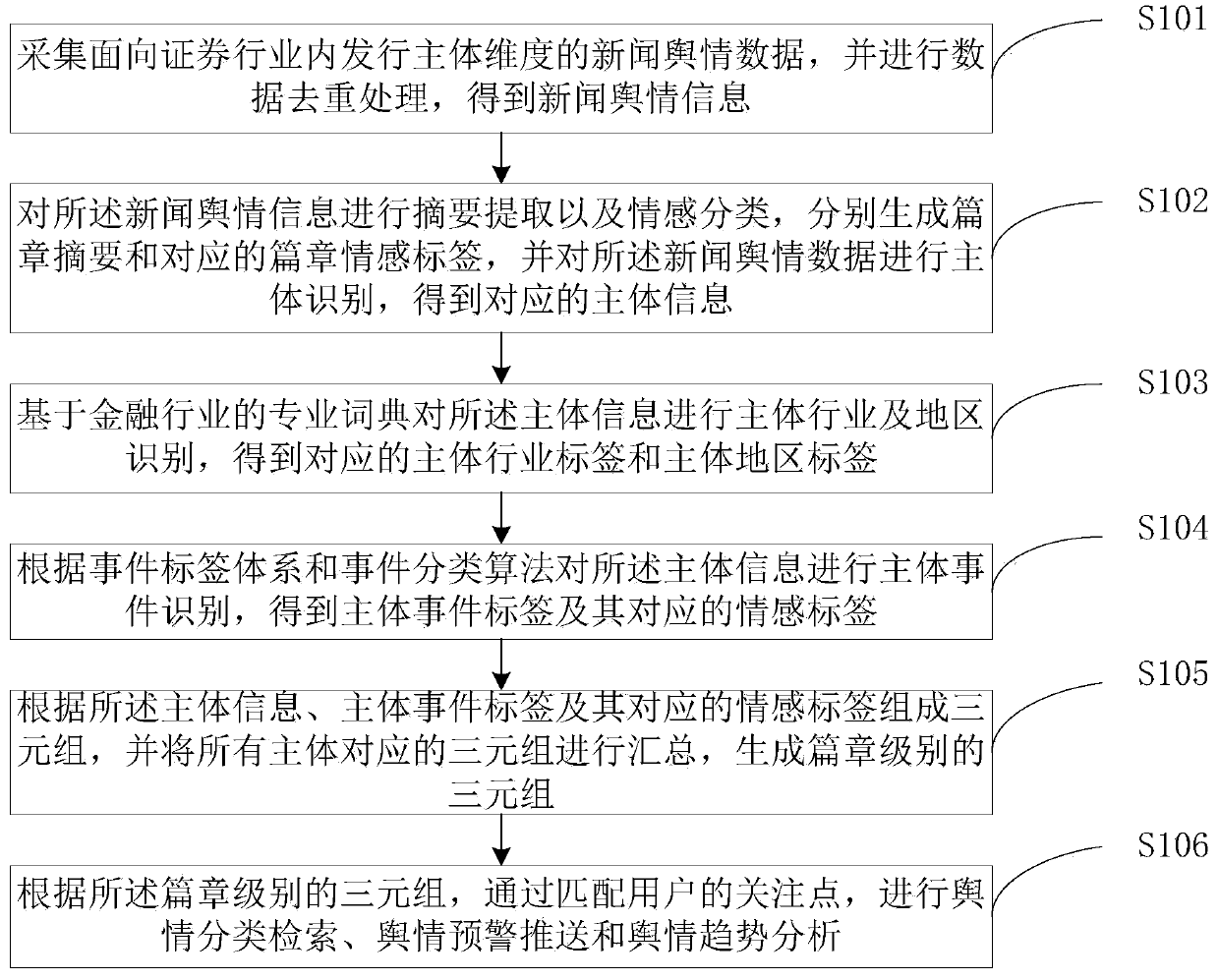
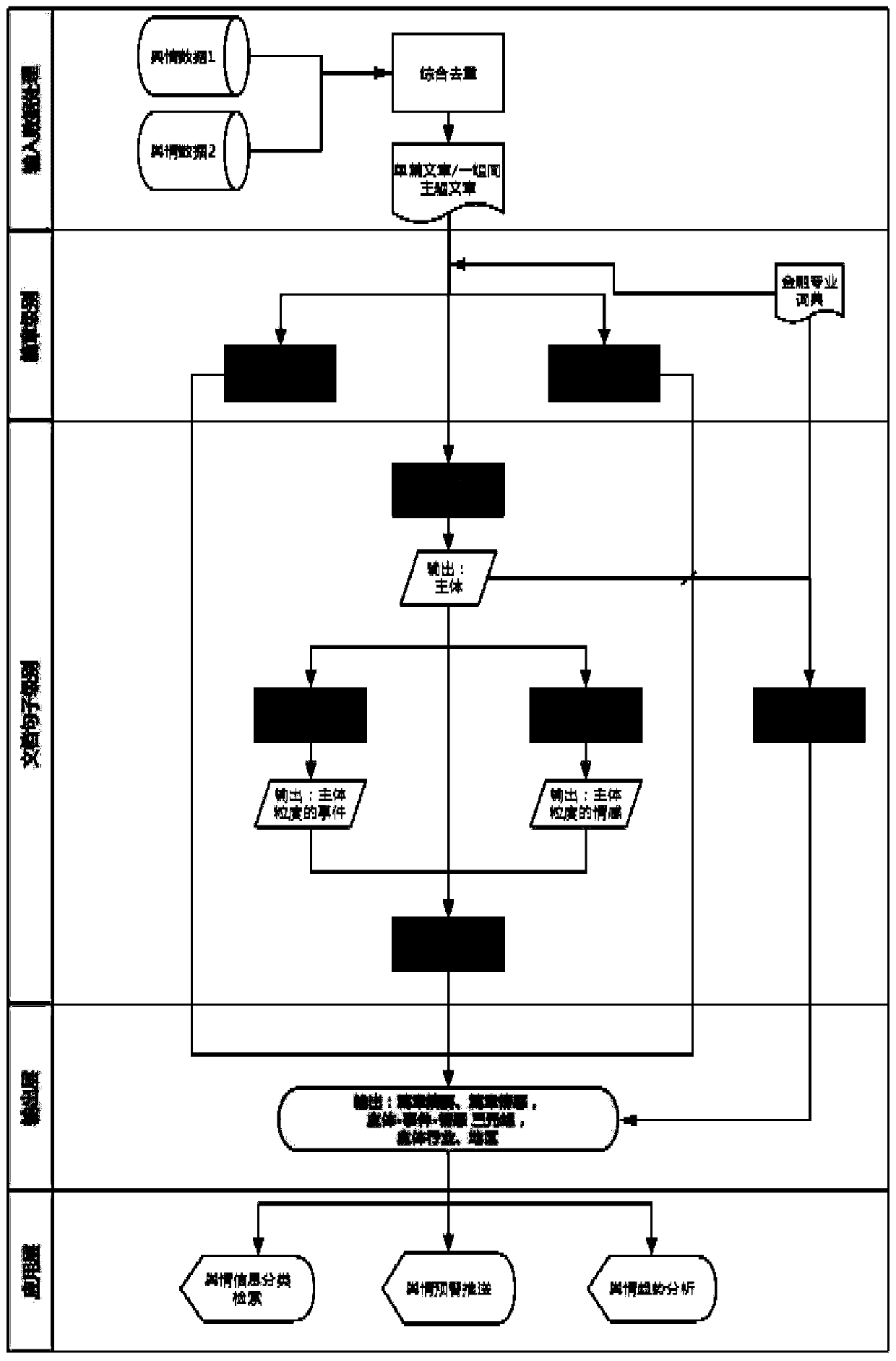
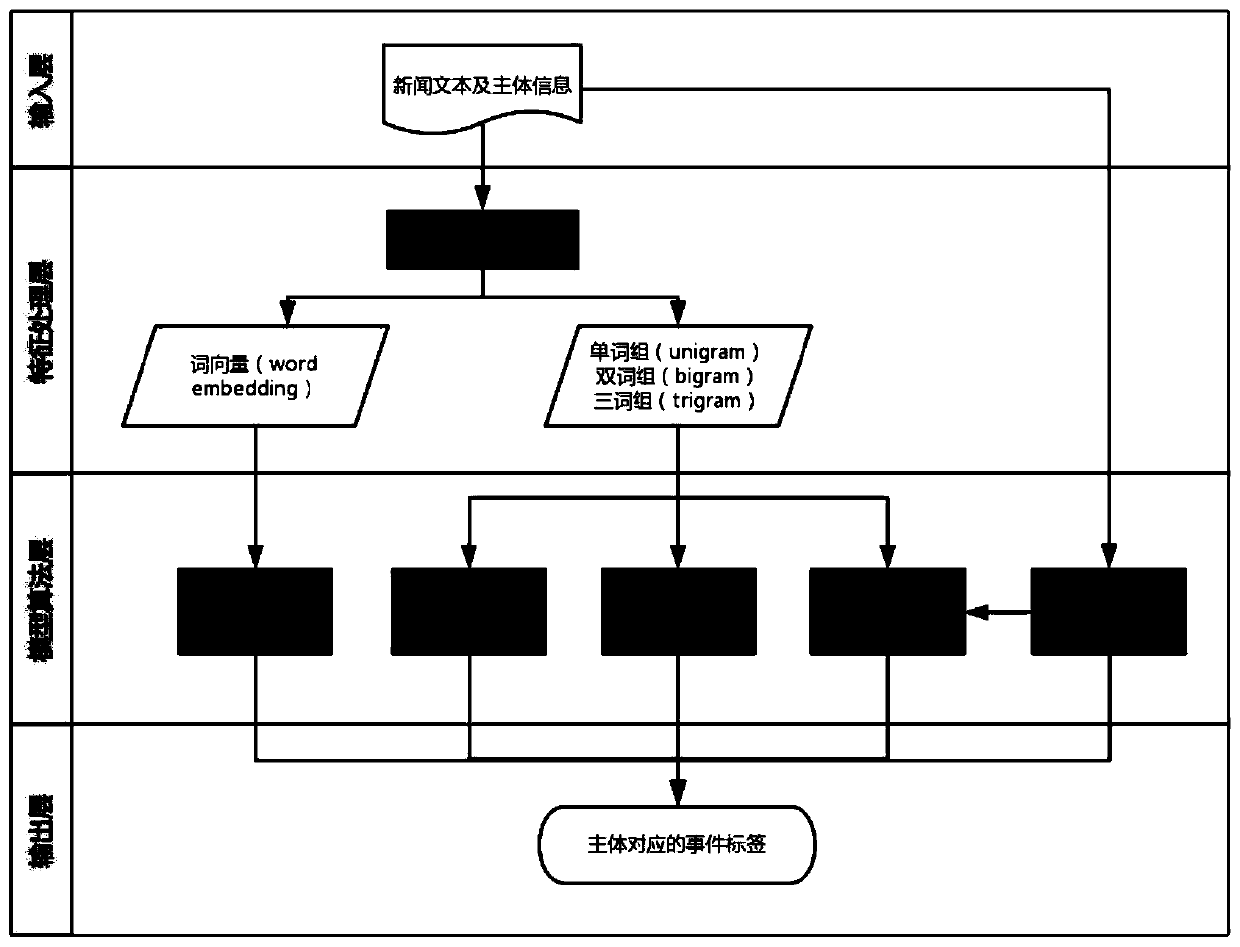
PendingCN109992661AImprove accuracyImprove efficiencyCharacter and pattern recognitionNatural language data processingBody identificationBody area
The invention discloses a security industry-oriented intelligent public opinion monitoring method and system, and the method comprises the steps: collecting news public opinion data for issuing a maindimension in the security industry, carrying out the data duplication removal, and obtaining news public opinion information; carrying out abstract extraction and sentiment classification on the newspublic opinion information, generating a chapter abstract and a chapter sentiment label, and carrying out main body identification on the news public opinion data to obtain corresponding main body information, a main body industry label and a main body area label; performing main event identification on the main body information according to the event tag system and an event classification algorithm to obtain a main body event tag and a corresponding emotion tag; and forming a triple according to the main body information, the main body event tags and the emotion tags, and summarizing the triple corresponding to all the main bodies to generate a chapter-level triple. The public opinion information can be extracted in multiple dimensions, the accuracy and efficiency of system classification are improved through the event label system and the fusion algorithm, and the effect of accurate and efficient public opinion monitoring is achieved.
Owner:GF SECURITIES CO LTD +1
Vocational and technical training system for security industry application technology
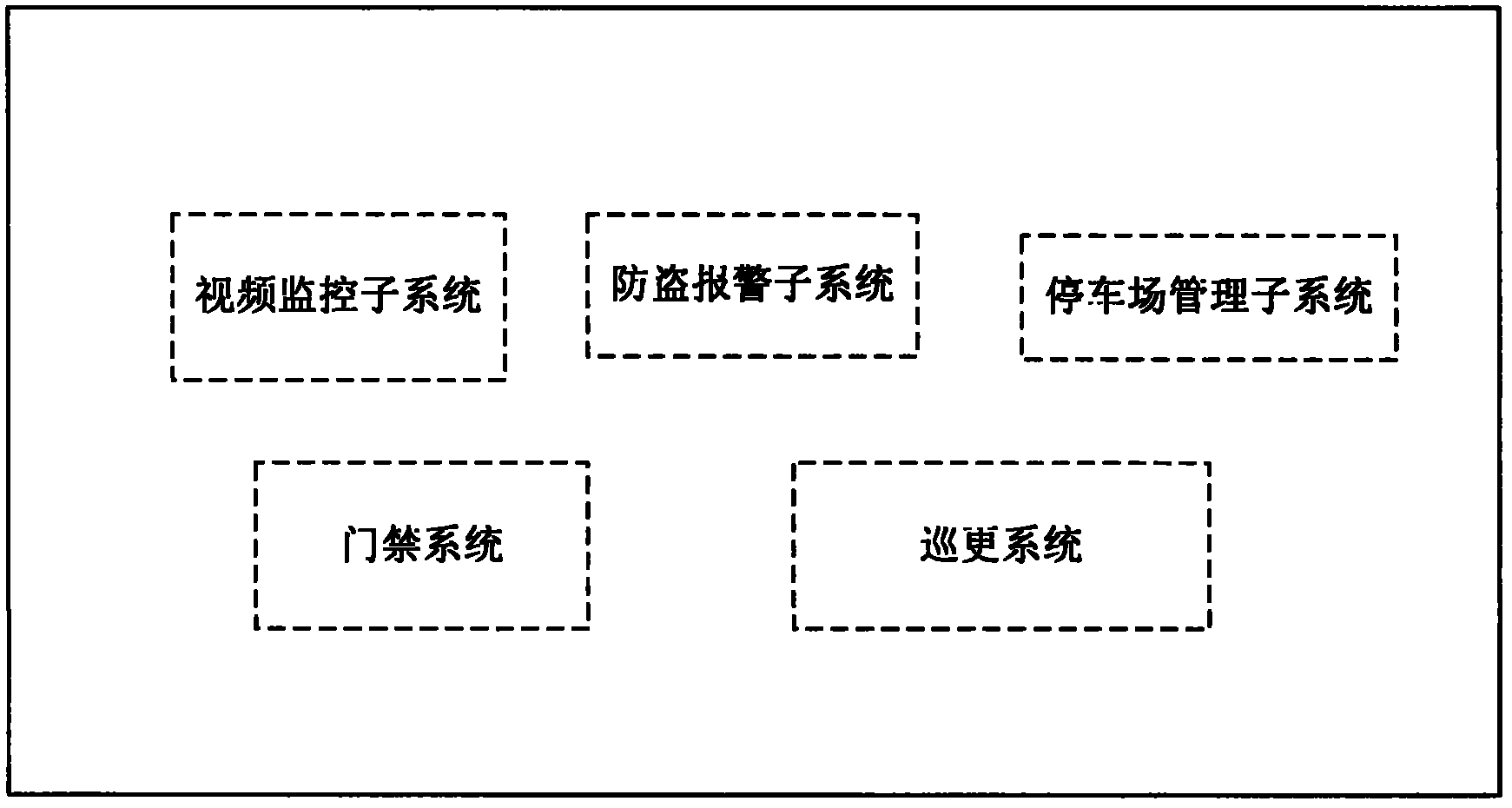
InactiveCN102521907AEasy to operateImprove hands-on abilityClosed circuit television systemsIndividual entry/exit registersVideo monitoringCard reader
The invention relates to a vocational and technical training system for security industry application technology, comprising subsystems of video surveillance, anti-theft alarm, building intercom, access control, night watching, park management and the like, wherein the video surveillance subsystem comprises a 22X infrared all-in-one machine, a high-sensitivity day and night type camera, an IP type network camera, a wide dynamic camera, an integrated camera, an intelligent high speed sphere, an infrared small hemisphere, a spiral small hemisphere, an IP type network video server, and a digit hard disk video recorder; the anti-theft alarm subsystem comprises a front-end alarm detector which comprises an infrared alarm detector, a door magnetic, an infrared shooting detector, and a vibration alarm detector; the access control subsystem comprises an entrance guard controller, a card reader, an electric control lock and an access control card; the night watching subsystem comprises a night watching rod, a communication base, night watching spots, personnel spots, an event log, and management software; and the park management subsystem comprises vehicle identity judgment, access control, automatic license plate identification, parking plot search, parking plot guidance, meeting reminding, image display, vehicle type checking, time calculation, fee collection and checking, voice intercom, and automatic card acquisition.
Owner:刘赵峰
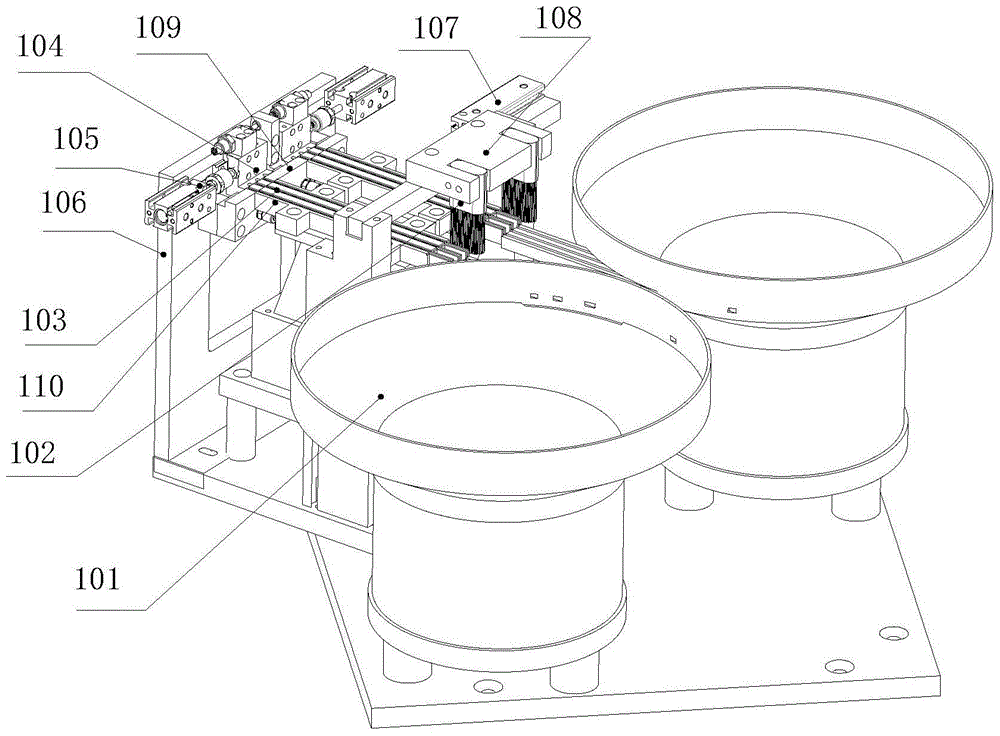
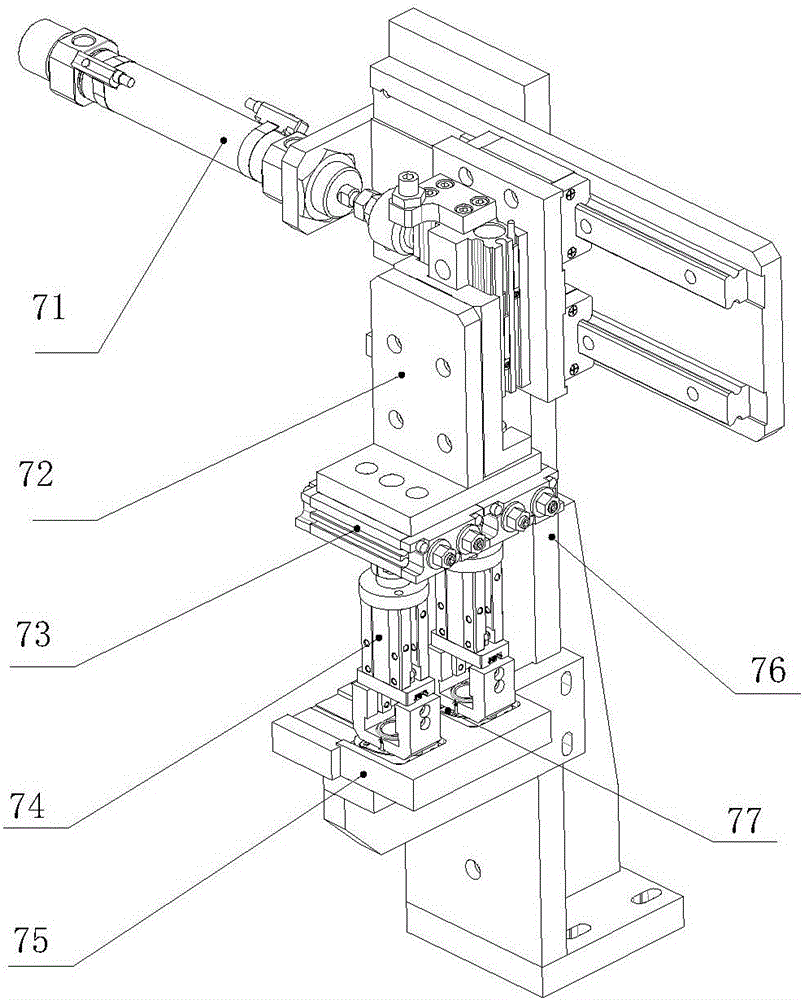
Screw feeding cutting locking device of IR-CUT assembly
InactiveCN106392599AReliable functionReliable cooperationMetal working apparatusSurveillance cameraRotating disc
The invention relates to the technical field of monitoring cameras in the security industry, and discloses a screw feeding cutting locking device of an IR-CUT assembly. The screw feeding cutting locking device comprises a main work table, a screw sorting and feeding cutting assembly and a screw locking assembling assembly; the main work table comprises a station rotating disc capable of rotating, a base and a lens cover subject to cover closing are arranged on the station rotating disc, the screw sorting and feeding cutting assembly is arranged on one side of the main work table and used for sorting the screws and conveying the screws, and the screw locking assembling assembly is arranged between the screw sorting and feeding cutting assembly and the main work table and used for locking screws, in other words, the screw locking assembling assembly is used for completing fixation between the lens cover and the base obtained after cover closing. Locking and fixing of the base and the lens cover which are subject to cover closing can be reliably completed.
Owner:深圳市华一自动化设备有限公司
Intelligent safe-guard system
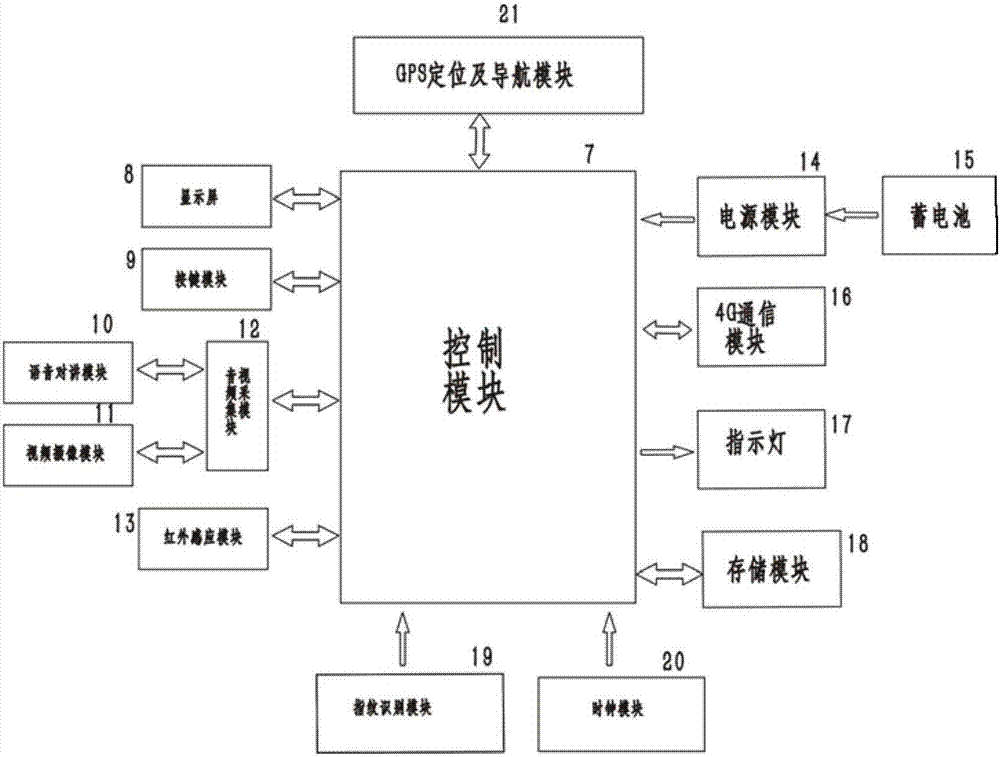
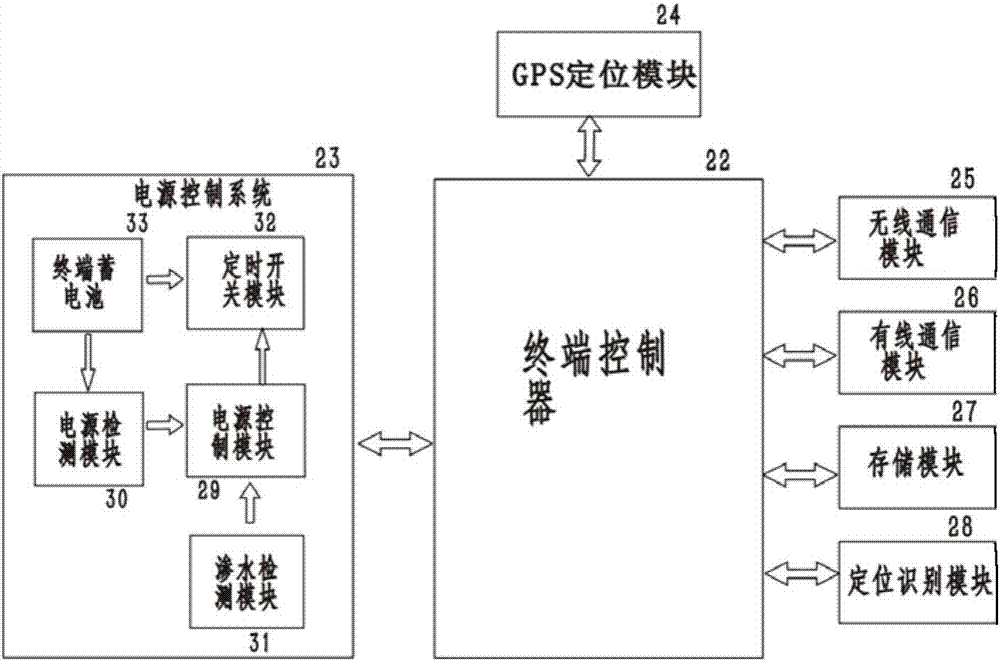
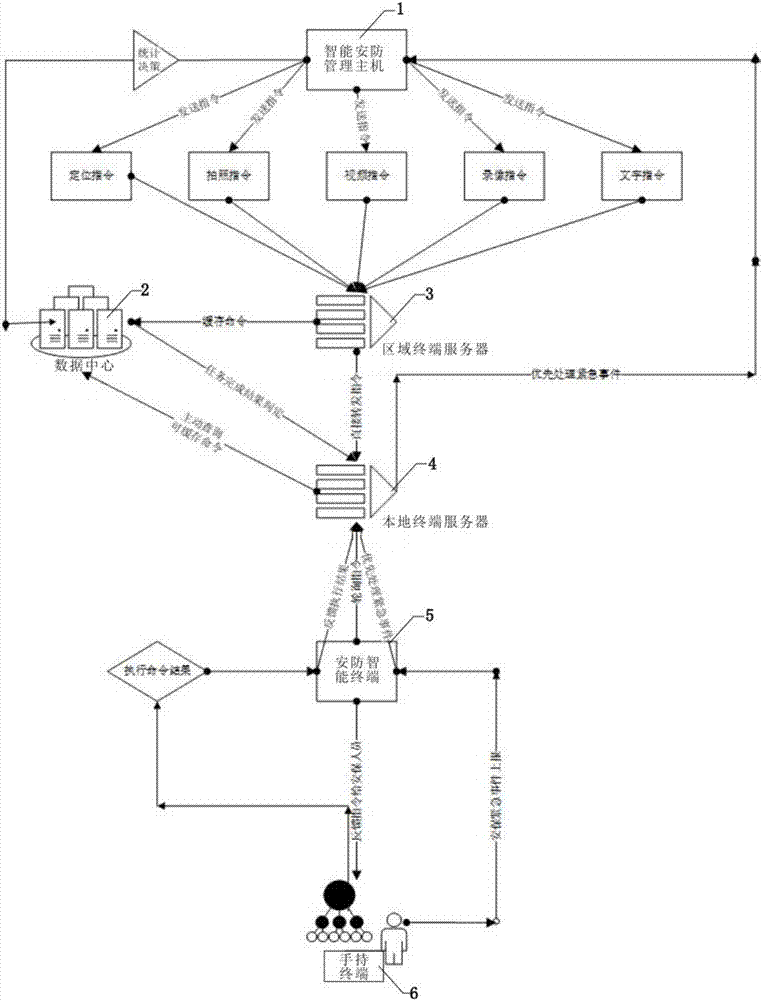
InactiveCN107452084AStay wirelessReduce usageChecking time patrolsAlarmsTerminal serverRemote control
The invention discloses an intelligent safe-guard system which comprises an intelligent safe-guard managing host computer, a data center, a regional terminal server, a local terminal server, an intelligent safe-guard terminal and a safe-guard handheld terminal. In a running process, the present 4G or wireless local area network is utilized to mainly apply the intelligent safe-guard system to security industry, public security department, transportation industry, cultural tourism, and the like. The system is integrated with an interphone, a law enforcement recorder and a patrol tapper, so that the additional cost of the equipment is greatly saved. The global talkback, positioning and tracking functions can be realized through the network, the visual operation and remote control function of the administrator can be realized and the middle management cost can be saved. The supervision and administration are more standard, scientific and visual. All the data can be well documented through the records, such as, voice, picture, video, positioning and tracking.
Owner:重庆赛弗迪智能科技有限公司
Instruction front-end system and corresponding instruction front-end interactive method
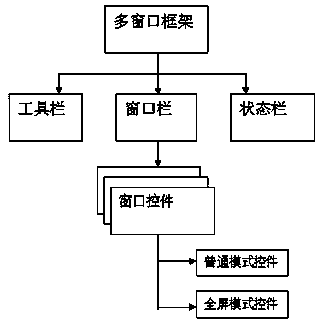
ActiveCN104020996AImprove compatibilityImprove ease of useSpecific program execution arrangementsBanking industryOperational system
The invention relates to the field of computer instruction front-end interaction, and provides an instruction front-end system and a corresponding instruction front-end interactive method. The instruction front-end system is achieved by utilizing the JavaScript language, a multi-window frame is adopted, and the multi-window frame comprises a tool bar, a window bar and a status bar. The instruction front-end system is compiled by completely adopting the JavaScript language, the good browser compatibility is achieved, the system can operate in various mainstream browsers, an operation system is not limited and required, and user use convenience and user experience are improved. Meanwhile, two main instruction types on a host system are achieved through the system, that is, a common command line interactive instruction and a full-screen gap filling type instruction are fully supported. The system is used as an instruction interactive terminal of civil aviation CRS, ICS and DCS hosts, and can fully support the civil aviation air ticket distribution business and the airline flight control and departure business. The system can be suitable for other industries with instruction interaction as the main operation mode, such as the banking industry, the insurance industry and the securities industry.
Owner:TRAVELSKY
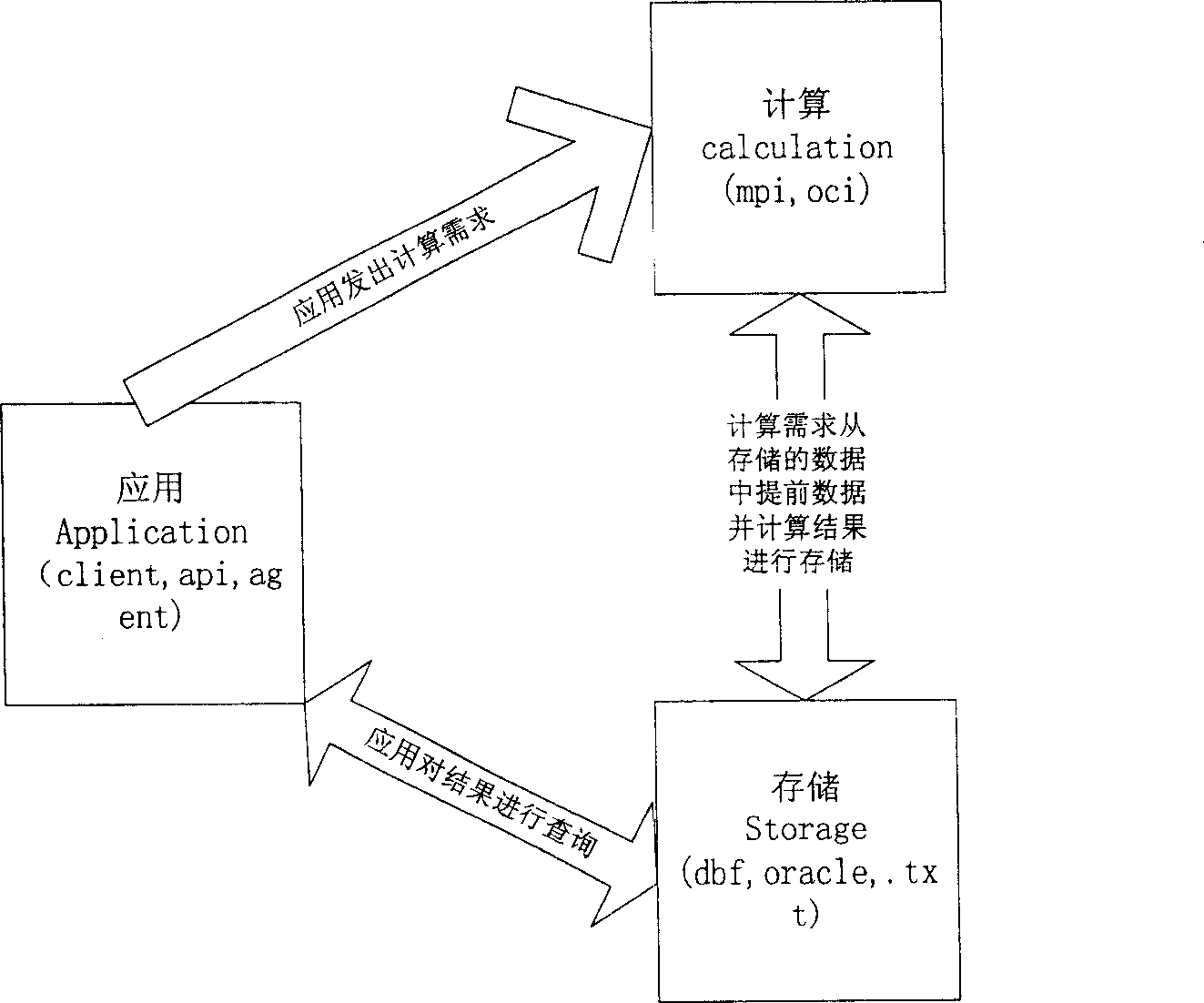
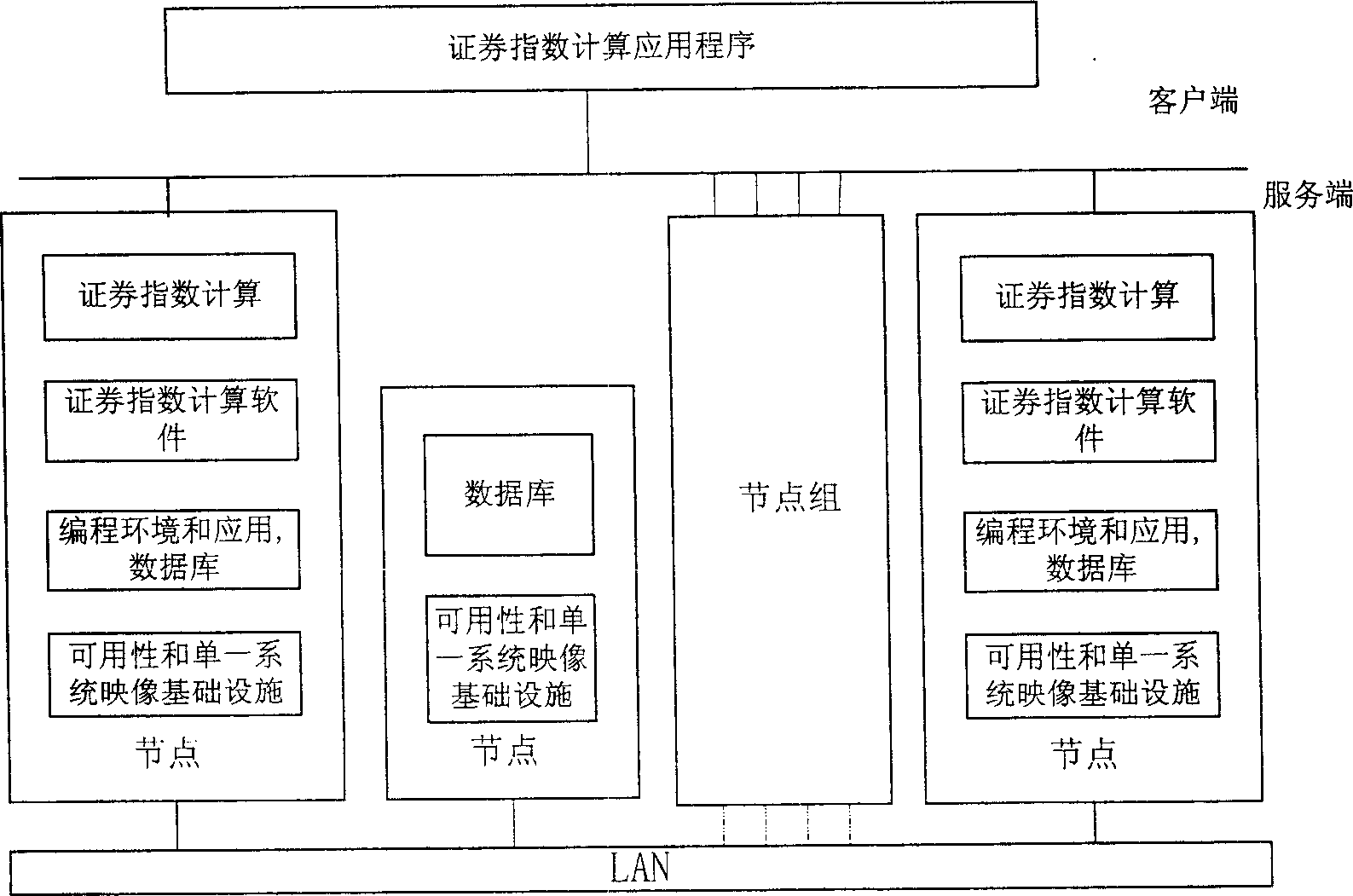
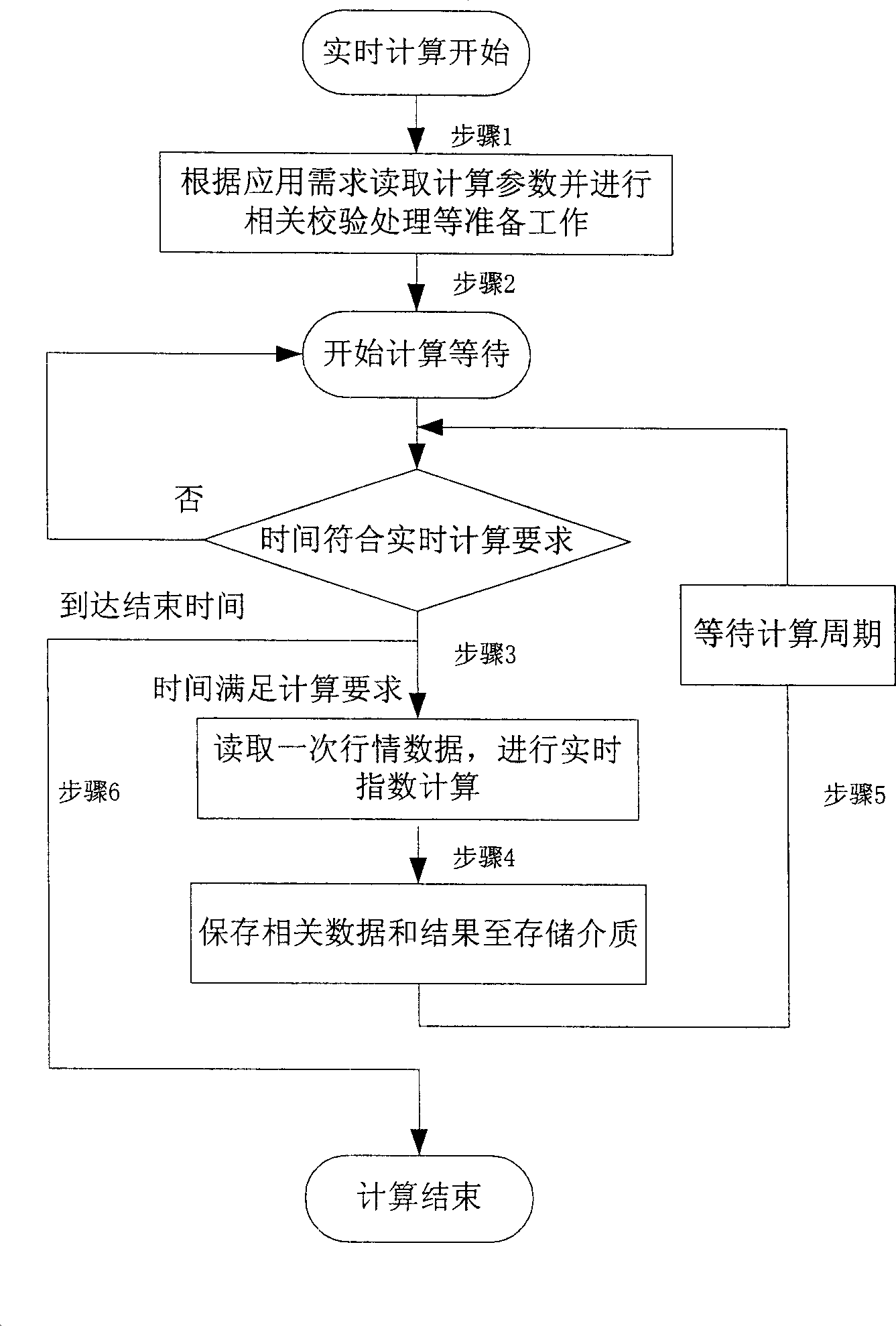
Security industry index computing system and method
This invention relates to a security industry index computing system and method. Wherein, it divides the index computing system by A / C / S structure into application, computation and storage parts that are mutual and depended with each other, whole system is realized as client / server mode with database for data share. In server, it applies Linux cluster system and parallel algorithm for real-time and back-track calculation, and uses disk array for reliable storage on important data; in client, it can query and demonstrate. Besides, it applies real-time computation program for real-time business data acquisition; in back-track computation, it makes full use of multi-node treatment capacity, and gathers result for storage in database.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
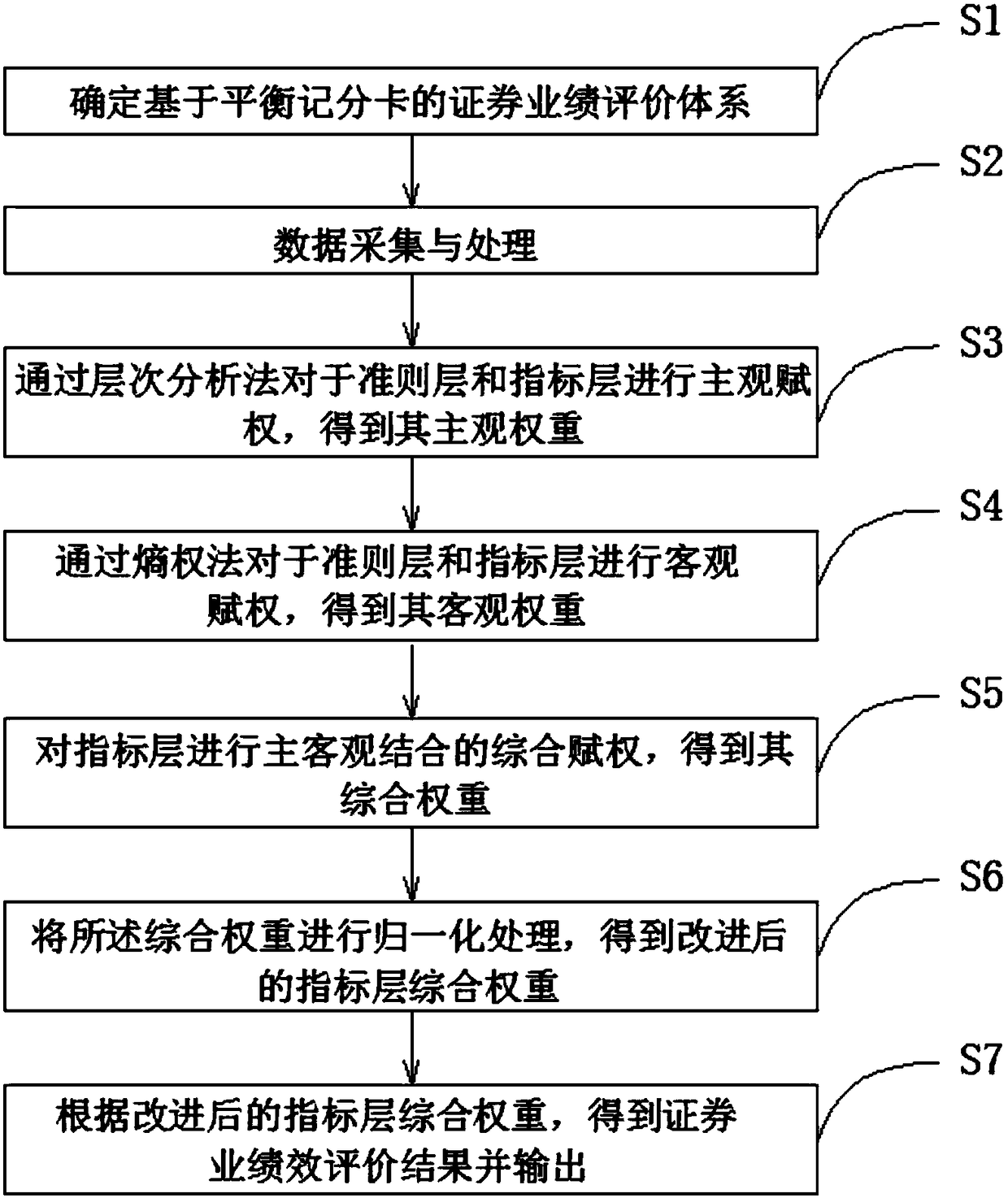
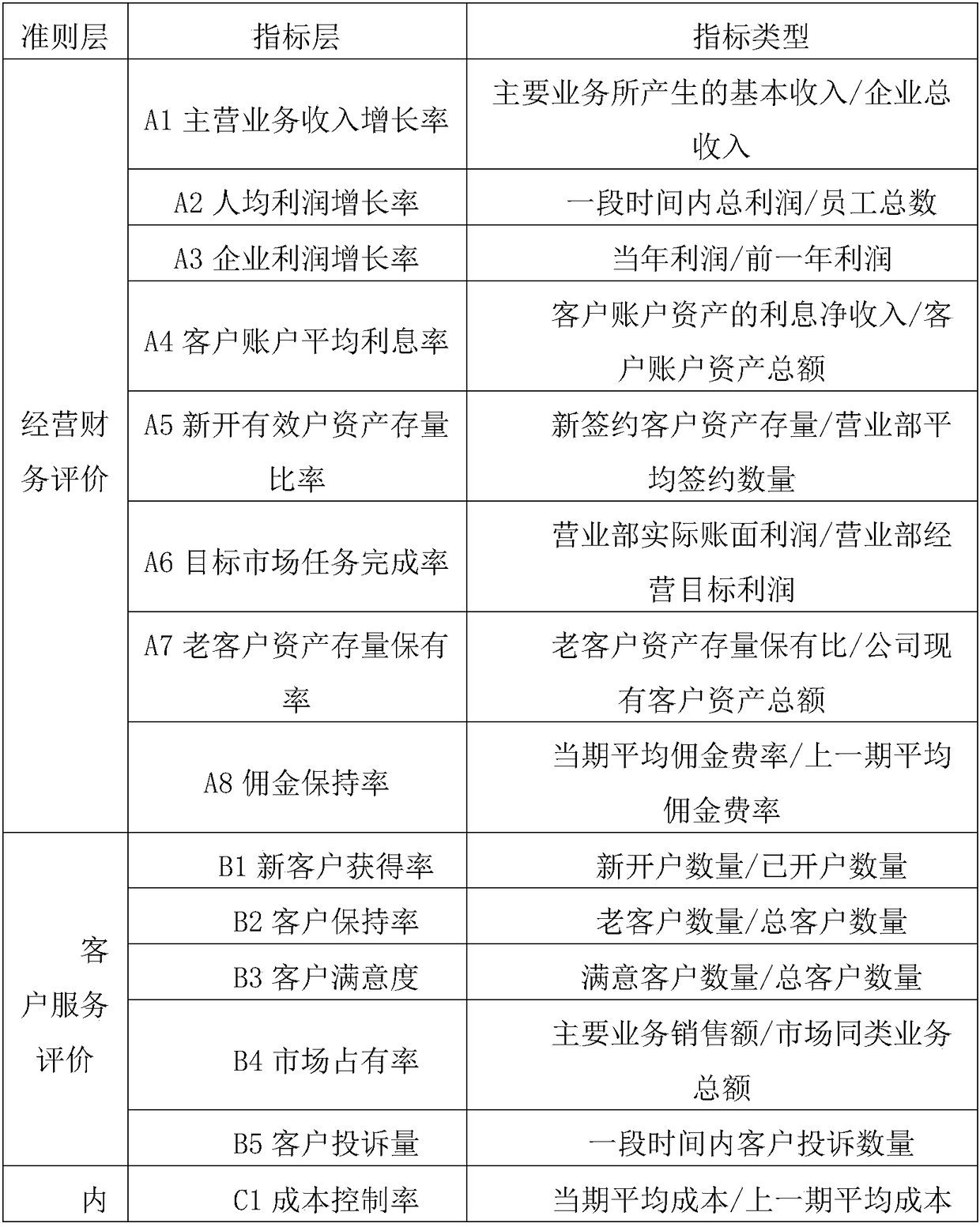
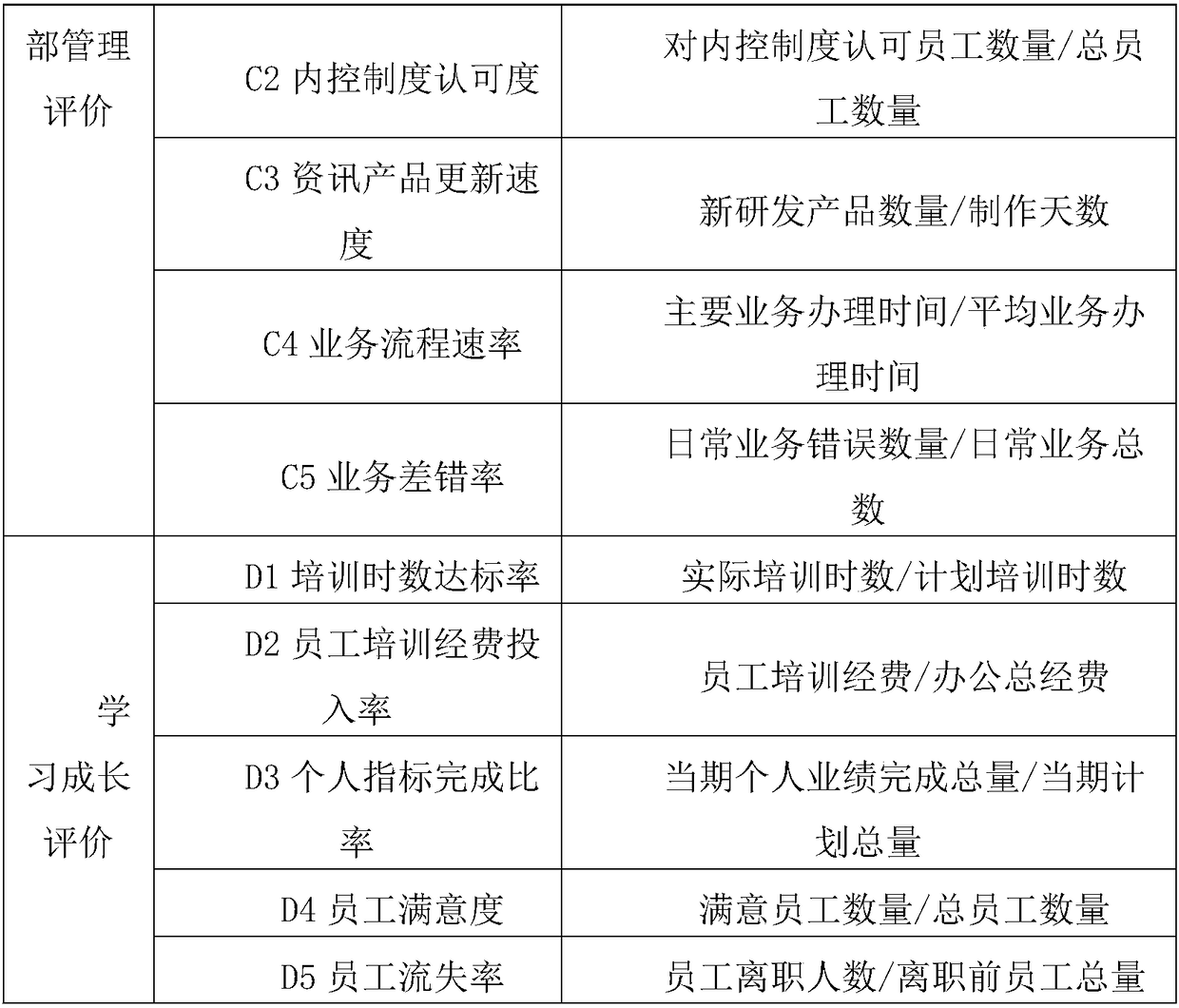
Securities industry performance evaluation method, system and device, and storage medium
InactiveCN108537436AHigh reference valueConducive to business allocationFinanceResourcesEvaluation resultEntropy weight method
The present invention discloses a securities industry performance evaluation method, system and device, and a storage medium, belonging to the technical field of securities industry business type evaluation. The method comprises the steps of: determining a securities industry performance evaluation system based on a balanced scorecard; performing data collection and processing; employing an analytic hierarchy process to perform subjective weight of a criterion layer and an index layer; employing an entropy weight method to perform objective weight for the criterion layer and the index layer; performing comprehensive weight of subjective and objective combination to the index layer, and obtaining a comprehensive weight of the index layer; performing normalization processing of the comprehensive weight to obtain an improved index comprehensive weight; and according to the improved index layer comprehensive weight, obtaining a securities industry performance evaluation result, and performing output. According to the technical scheme, the securities industry performance evaluation method, system and device, and the storage medium are suitable for performance evaluation of various businesses of securities, are high in accuracy and are close to actual situations.
Owner:宿州学院
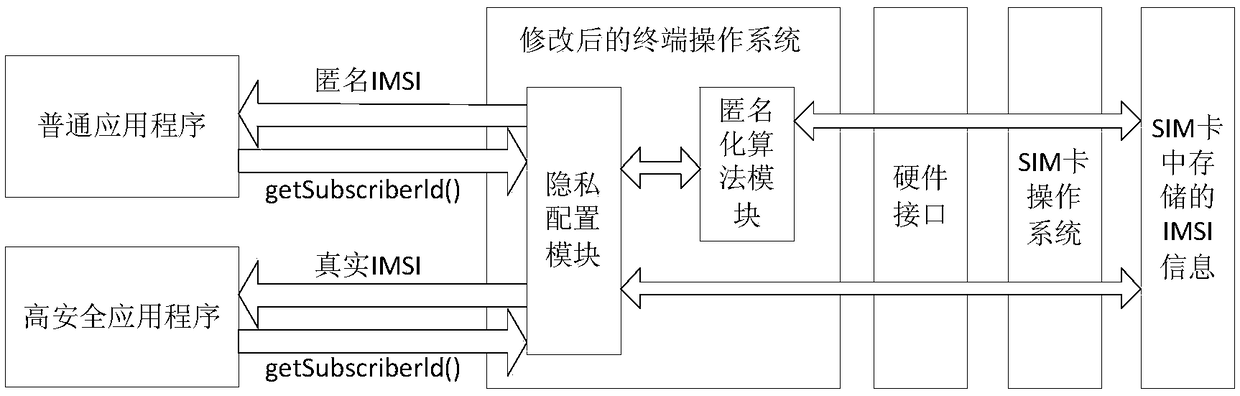
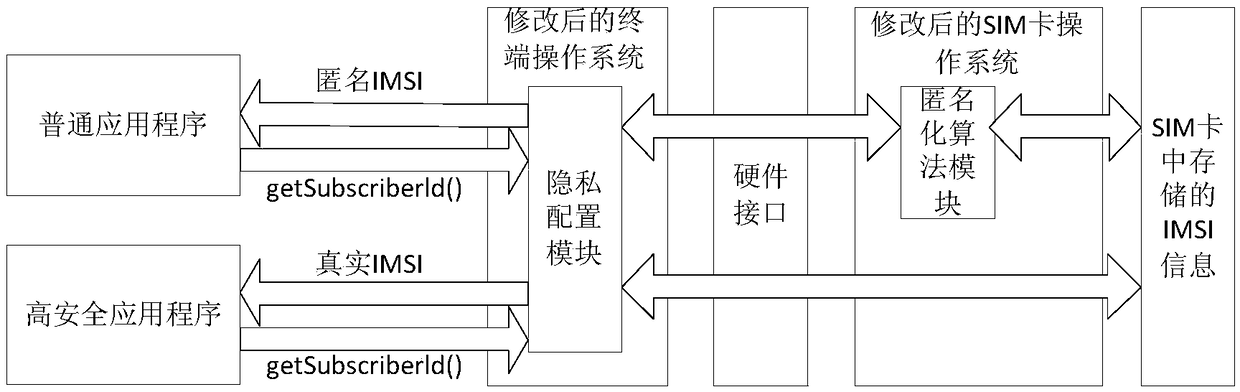
IMSI privacy protection method in 5G high-security terminal
InactiveCN108632817AProtect identity privacyGuaranteed privacyTransmissionSecurity arrangementPrivacy protectionG-network
The invention discloses an IMSI privacy protection method in a 5G high-security terminal. An anonymization algorithm module and a privacy configuration module are additionally provided in the terminal, wherein the main function of the anonymization algorithm module is to perform anonymous processing on IMSI information, and the main function of the privacy configuration module is to selectively activate or close the anonymization algorithm module for application programs of different security levels. According to the IMSI privacy protection method provided by the invention, the privacy of theIMSI is ensured in the high-security terminal by using the anonymization algorithm so as to reduce the possibility of an attacker of capturing the IMSI information through the application programs ofthe terminal, so that the identity privacy of a user of the high-security terminal is protected. The application range of the method is wide, the method is not only suitable for the high-security terminals in the current 4G network, but also is suitable for the high-security terminals in the future 5G network. The requirements of identity privacy protection of users in the high-security industriescan be satisfied. The anonymization algorithm can also be extended to protect the identity information of other terminals.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP +1
Intelligent zipper and processing device thereof
The invention discloses an intelligent zipper. The intelligent zipper comprises a zipper body, wherein the zipper body is provided with a zipper head and a pull-tab, the zipper head is provided with a meshing opening and a guiding opening, and the pull-tab is arranged on the upper end of the zipper head and is in clearance fit with the zipper head. The intelligent zipper is characterized in that the pull-tab is connected with a pull ring, a PCBA board is arranged in the pull ring, a chip into which terminal client information can be implanted is built in the PCBA board, and the chip is provided with a GSM / GPRS module with a positioning function. According to the intelligent zipper, the latest single chip MT6260 is adopted, the quadruple-frequency universal subminiature GSM / GPRS module with low power consumption and the positioning function is developed and implanted into the chip of the zipper, and then the terminal client information according to the zipper selling is implanted into the chip, and the intelligent zipper has the functions of remote prevention of burglary, and position monitoring, and can be widely applied to the fields including the smart home, the medical terminal, the security industry, the mobile communication transmission, the remote monitoring, the personal positioning and checking attendance, personnel management, terminal data transmission and the like.
Owner:王丽华
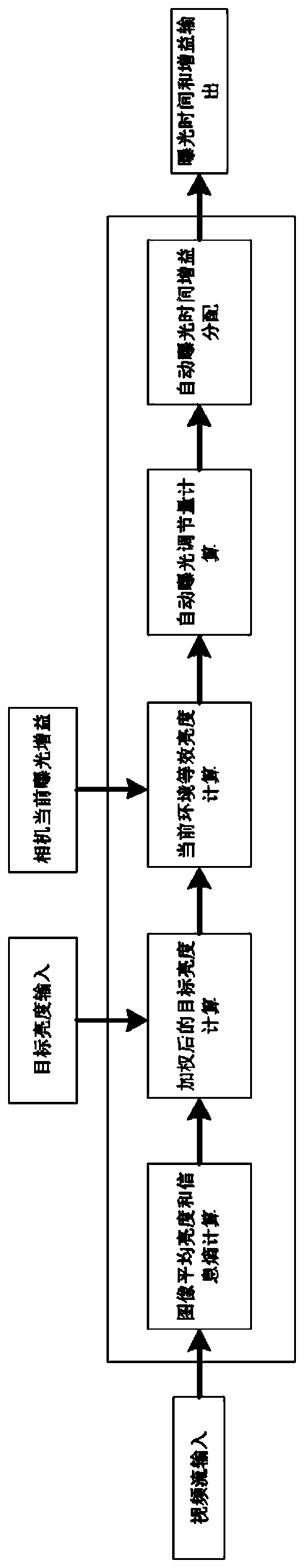
Camera automatic exposure method based on ambient brightness and image information entropy
ActiveCN110602414AMeet the needs of the video surveillance fieldSolve the scene adaptability problemTelevision system detailsColor television detailsVideo monitoringGraphics
The invention provides a camera automatic exposure method based on ambient brightness and image information entropy. The camera automatic exposure method comprises the steps of S1, calculating averagebrightness of a graph and the information entropy of an image; calculating the average brightness and the image information entropy of the image according to the brightness histogram of the graph; and S2, obtaining the brightness of the automatic exposure target through weighted calculation by utilizing the image information entropy. The invention provides a camera automatic exposure method basedon ambient brightness and image information. The method is already realized in a 3559A processor + IMX305 image sensor scheme. Tests show that the camera automatic exposure method effectively solvesthe problem of scene adaptability in a traditional AE method, good results can be obtained no matter whether a wide dynamic scene, a high contrast scene or a scene with rich details are processed, andthe requirements of the current intelligent security industry in the field of video monitoring are fully met.
Owner:TIANJIN TIANDY DIGITAL TECH
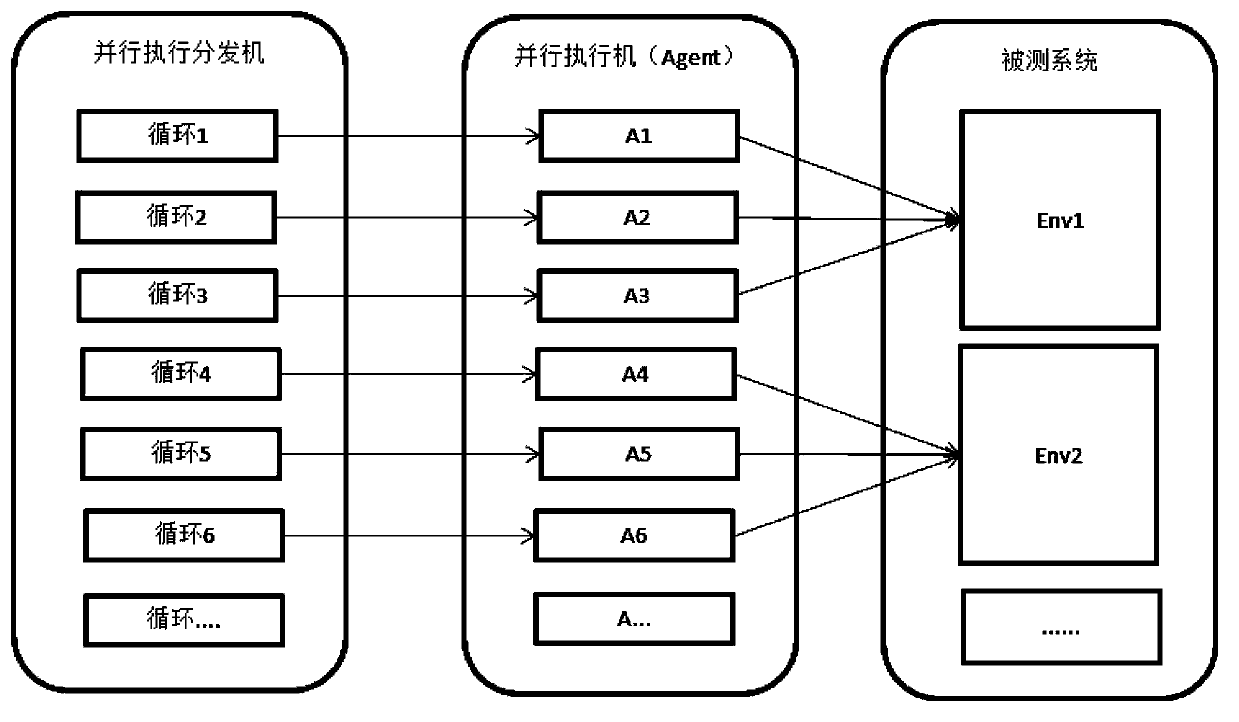
Parallel automated testing system for test case in futures and security industry
ActiveCN103391225AAvoid blockingShorten test timeData switching networksSecurity industryData resources
The invention discloses a parallel automated testing system for a test case in the futures and security industry. The system comprises a testing queue, a distribution machine, a plurality of actuating machines and a resource database, wherein the testing system calls test data from the resource database for supporting the operation of the test case after a testing check command, transmitted by the actuating machines, of the test case is received by the testing system, and a testing result is generated; the actuating machines monitor the operation condition of the test case, and a testing result is obtained and returned to the distribution machine; after the test is completed, the occupied testing data resources are released and marked into an available state again; and the state of the operated test case is changed, the test case is deleted from the testing queue, and parallel testing of a plurality of test cases are completed after all test cases in the testing sequence are successfully tested, that is, the testing queue is empty. The parallel automated testing system for the test case in the future and security industry has the advantages that the utilization ratio of a tested system is increased, various testing resources are sufficiently used, and the actuating efficiency is obviously improved.
Owner:大商所飞泰测试技术有限公司
System and method for facilitating connections and compliance involving service providers in the securities industry
The present invention generally relates to facilitating connections and compliance between individuals, business entities and service providers in the securities industry. Specifically, this invention relates to a system and method for facilitating the virtual connection of service providers in the securities industry with broker dealers, registered investment advisory firms private equity groups, hedge funds, other service providers and consultants through a computer based system that processes related communications and data via one or more networks and may be delivered to a user through one or more computing devices.
Owner:HOUGH JERVIS BENNETT
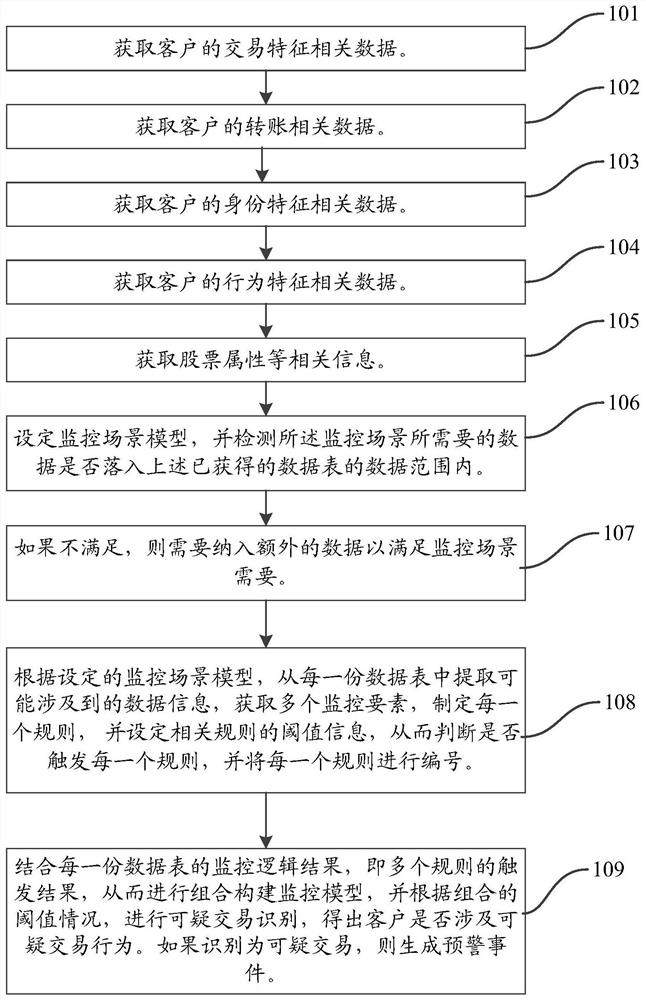
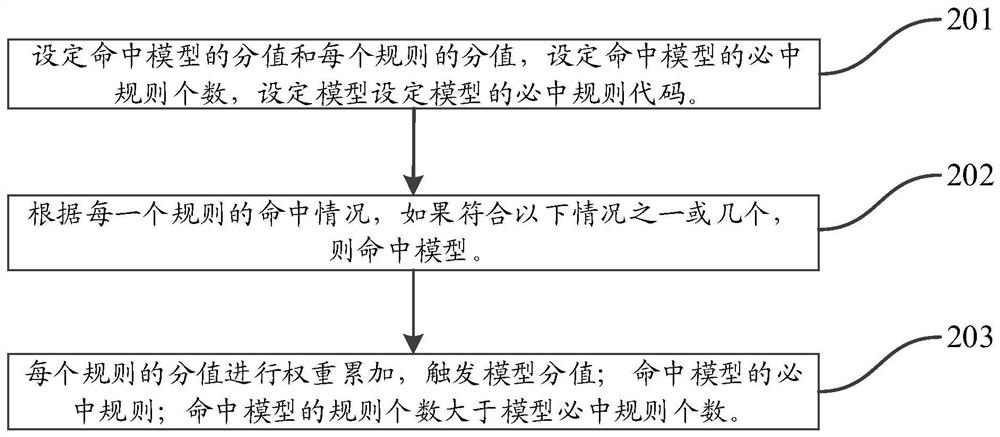
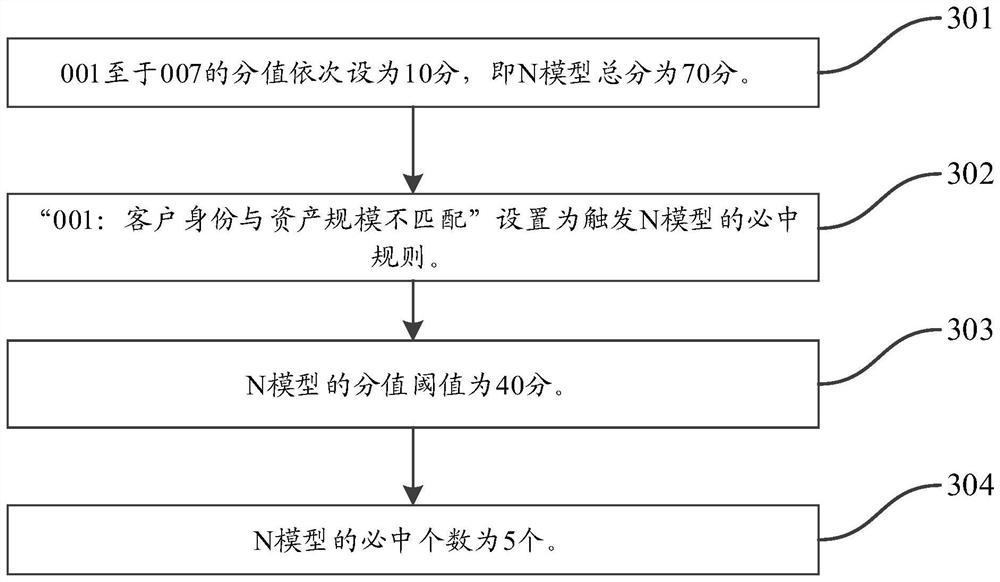
System, method and device for realizing suspicious transaction scene model identification processing based on combination construction, processor and storage medium thereof
PendingCN113592505AIncrease diversityFlexible thinking designFinanceProtocol authorisationFinancial transactionData needs
The invention relates to a system for realizing identification processing of an anti-money laundering suspicious transaction scene model in the securities industry based on combination construction, and the system comprises: a data feature collection module, which is used for collecting various data needed by the suspicious transaction scene model for behavior identification processing; a monitoring scene construction module, which is used for constructing a monitoring scene model according to a system preset rule by using the collected data; and a suspicious transaction behavior identification module, which is used for carrying out identification processing on suspicious transaction behaviors according to the combined triggering result of the monitoring scene model. The invention further relates to a corresponding method and device, a processor and a storage medium thereof. By adopting the system, the method, the device, the processor and the storage medium of the invention, the diversity of monitoring data is broadened comprehensively, new monitoring rules are continuously added, threshold values constructed by combination are continuously optimized and corrected, anti-money laundering suspicious transaction clients are screened in a multi-view manner, and the system, the method, the device, the processor and the storage medium have important significance for the identification work of an actual anti-money laundering suspicious model.
Owner:GUOTAI JUNAN SECURITIES
Source tracing method of same source code
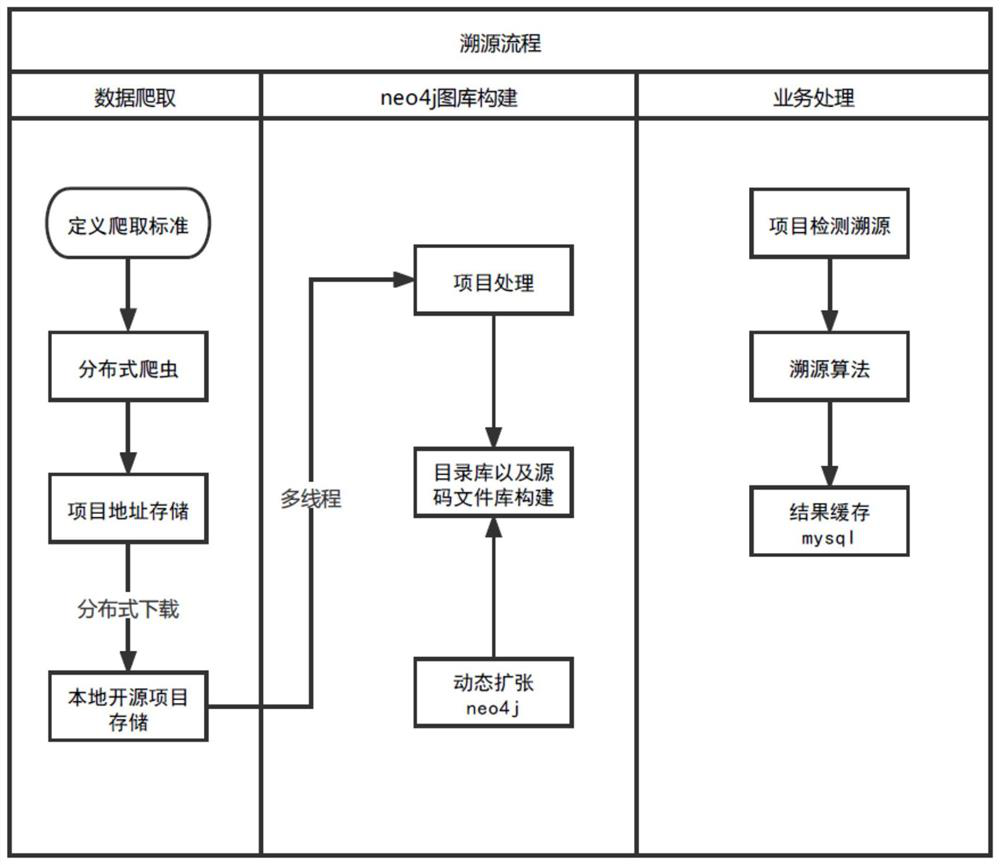
PendingCN113987427ADetection speedSolve the problem of the full amount of detectionPlatform integrity maintainanceProgram/content distribution protectionAlgorithmTheoretical computer science
The invention relates to a source tracing method of a same source code, which comprises the following steps of: establishing a standardized vulnerability knowledge base in a crawler mode, obtaining open source codes meeting specifications, preprocessing open source code results, and storing the preprocessed open source code results; constructing a Neo4j graph database; and carrying out business processing. Therefore, the detection speed can be improved based on the graph library association relationship between the content hash value of the source code and the directory hash value. The problem of full detection of collision between binary files and files is solved, and the speed is increased by more than 10 times, so that engine support is further provided for open source software supply chain security detection. Through multi-dimensional clustering, whether a certain module or a subclass of the module is adopted can be distinguished according to a calculated result score, and the problem that a detection result of a supply chain is inaccurate due to an inclusion relation between open source project modules is solved. More accurate open source items and versions can be provided, so that vulnerability detection in the security industry of the software industry is more accurate.
Owner:苏州棱镜七彩信息科技有限公司
Device integrating various back-end functions of high-definition video monitoring system
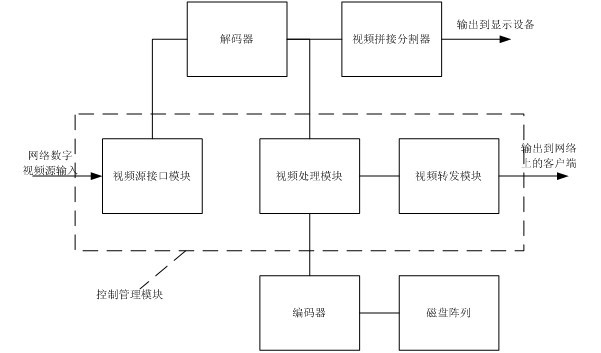
InactiveCN102082949ASolve the problem that only a single brand camera can be connectedSolve the problem that only a few brands of cameras are supportedClosed circuit television systemsDigital video signal modificationDigital videoComputer module
The invention discloses a device integrating various back-end functions of a high-definition video monitoring system, which comprises a control management module, a decoder, an encoder and a hard disk array, wherein a digital video source is inputted to the control management module, outputted to the decoder through the control management module, outputted to display equipment for displaying after being decoded by the decoder, and simultaneously outputted to the control management module, the control management module outputs input information of the decoded digital video source to a network client side and simultaneously outputs the input information of the digital video source to the encoder, and then the input information of the digital video source is inputted to the hard disk array to be stored after being encoded by the encoder. The device thoroughly solves the problem that all high-definition video monitoring end-back equipment in a security industry can only be connected with a single brand of cameras or only support several brands of cameras; simultaneously the device integrates the main application functions of the back end of the high-definition video monitoring system and can also be applied together with vehicle snapping systems, such as an electronic police, a security mount and the like, thereby realizing data exchange visit and interexchange.
Owner:武汉经纬视通科技股份有限公司
A clip-type commodity anti-theft device applied to the electronic commodity anti-theft industry
The invention provides a clamping type commodity anti-theft device applied to an electronic commodity security industry, comprising a first rotatable clamp arm and a second clamping match component, wherein the first rotatable clamp arm and the second clamping match component are matched for clamping a commodity; the anti-theft device is provided with an eccentric wheel for driving the first clamp arm to rotate so as to match with the second clamping match component or separate the clamping match from the second clamping match component; the anti-theft device is further provided with a handlefor operating the eccentric wheel to rotate; and the anti-theft device is further provided with a lock for locking the handle at a current position when the anti-theft device is in a clamping state, wherein the lock is a magnetic lock. The clamping type commodity anti-theft device applied to the electronic commodity security industry is simple in structure and operation, capable of being fixed onsurfaces of leather commodities, such as uppers of shoes, boots and any part of leather garments by clamping, without damaging the leather commodities. Furthermore, the clamping type commodity anti-theft device applied to the electronic commodity security industry can be widely applied to various kinds of commodities with parts capable of being clamped for fixing the anti-theft device.
Owner:HANGZHOU CENTURY CO LTD
Lens cover pad pasting and covering device of IR-CUT assembly
InactiveCN106405858AImprove continuityReduce articulationOptical elementsCamera lensSurveillance camera
The invention relates to the technical filed of monitoring cameras in the security industry, and discloses a lens cover pad pasting and covering device of an IR-CUT assembly. The lens cover pad pasting and covering device includes a main workbench, a lens cover direction-split assembly, a lens cover conveying assembly and a lens cover pad pasting and covering assembly, the main workbench includes a station rotary disc capable of rotating, a base is arranged on the station rotary disc, the lens cover direction-split assembly is arranged at one side of the main workbench to split the direction of the lens cover, the lens cover conveying assembly conveys the direction-split lens cover and is arranged between the lens cover direction-split assembly and the main workbench, and the lens cover pad pasting and covering assembly is arranged at one side of the lens cover conveying assembly for pad-pasting the direction-split lens cover and moving the lens cover to the base on the station rotary disc for covering cooperation. The lens cover pad pasting and covering device can reliably complete the functions of lens cover direction splitting, conveying, pad pasting, and covering cooperation with the base.
Owner:深圳市华一自动化设备有限公司
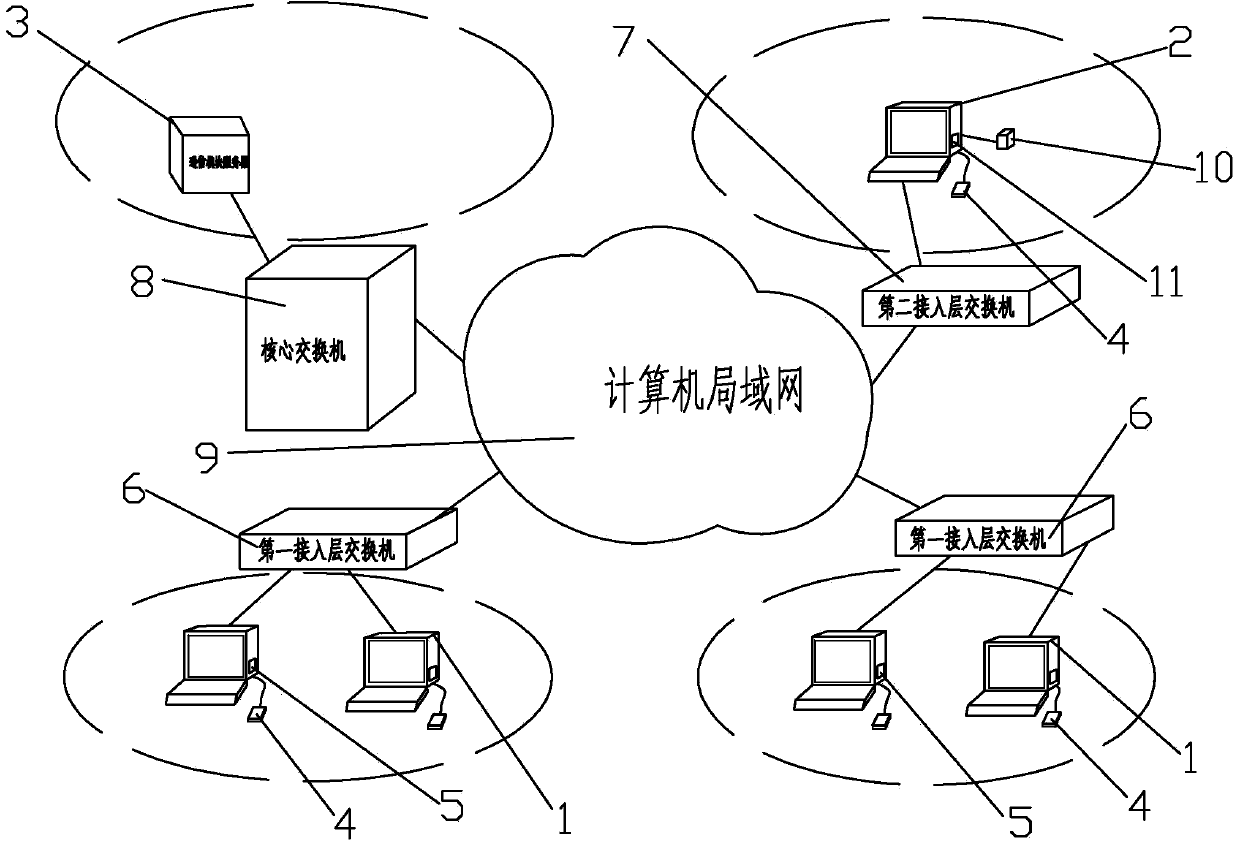
One-button alarm system based on computer network and operating method thereof
The invention discloses a one-button alarm system based on a computer network and an operating method of the one-button alarm system. The one-button alarm system comprises a working computer, a security room computer and a communication module server, wherein the working computer and the security room computer are respectively connected with a USB interface alarm button and are respectively and internally provided with an alarm module; the working computer is connected with a first access layer switch through a cable; the security room computer is connected with a second access layer switch through a cable; the communication module server is connected with a core switch through a cable; the first access layer switch, the second access layer switch and the core switch are connected with a computer local area network through cables. The one-button alarm system is a basic technology in the field of security industry technical prevention, an alarm message can be given to security personnel on duty only by triggering the button in case of emergency, related personnel can deal with the dangerous case in time, and the dangerous case is stopped or prevented from spreading.
Owner:钟初雷 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com