IMSI privacy protection method in 5G high-security terminal
A security terminal and privacy protection technology, applied in the field of IMSI privacy protection inside 5G high-security terminals, can solve problems such as leakage of user identity, and achieve the effect of wide application, solving identity privacy protection, and protecting identity privacy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
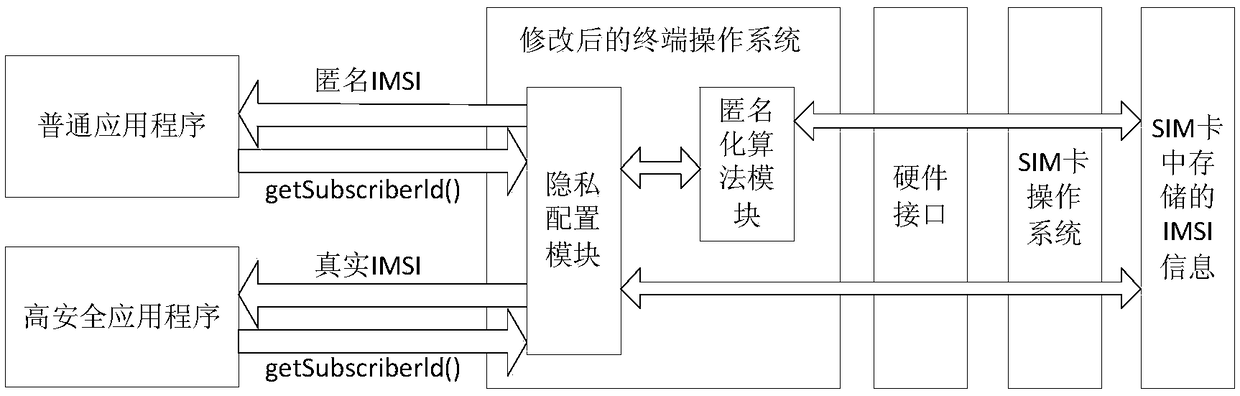
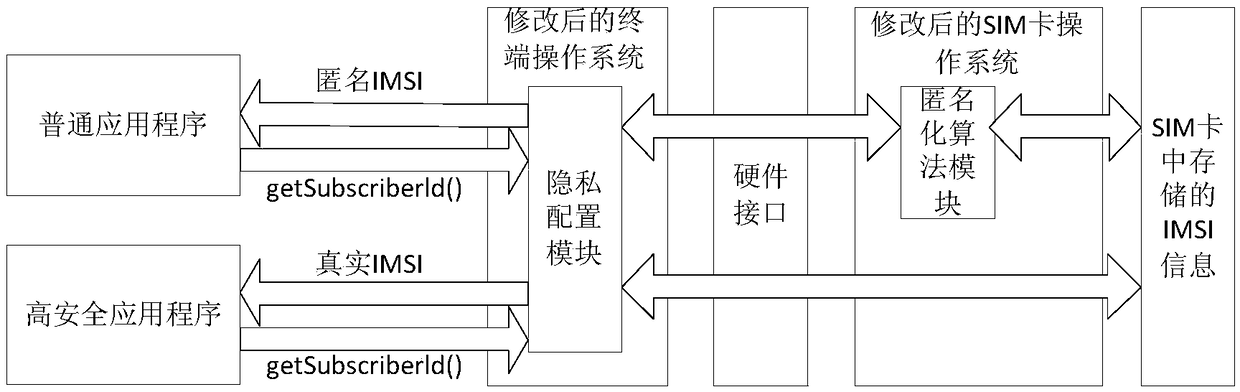
[0013] In the current ordinary terminal, the application program reads the IMSI information stored in the SIM card, and only needs to call an API interface function. Aiming at the possibility that reading IMSI information by an application program in an ordinary terminal may lead to leakage of user identity privacy, the present invention provides a privacy protection method for IMSI information in a high-security terminal. The main purpose is to protect the anonymity of the IMSI through the anonymization algorithm to prevent the leakage of the real IMSI information and other sensitive information stored in the SIM card.
[0014] In order to realize the privacy protection function of the present invention, two functional modules need to be added in the terminal: an anonymization algorithm module and a privacy configuration module. The main function of the anonymization algorithm module is to anonymize the IMSI information to ensure the privacy and security of the IMSI informati...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com