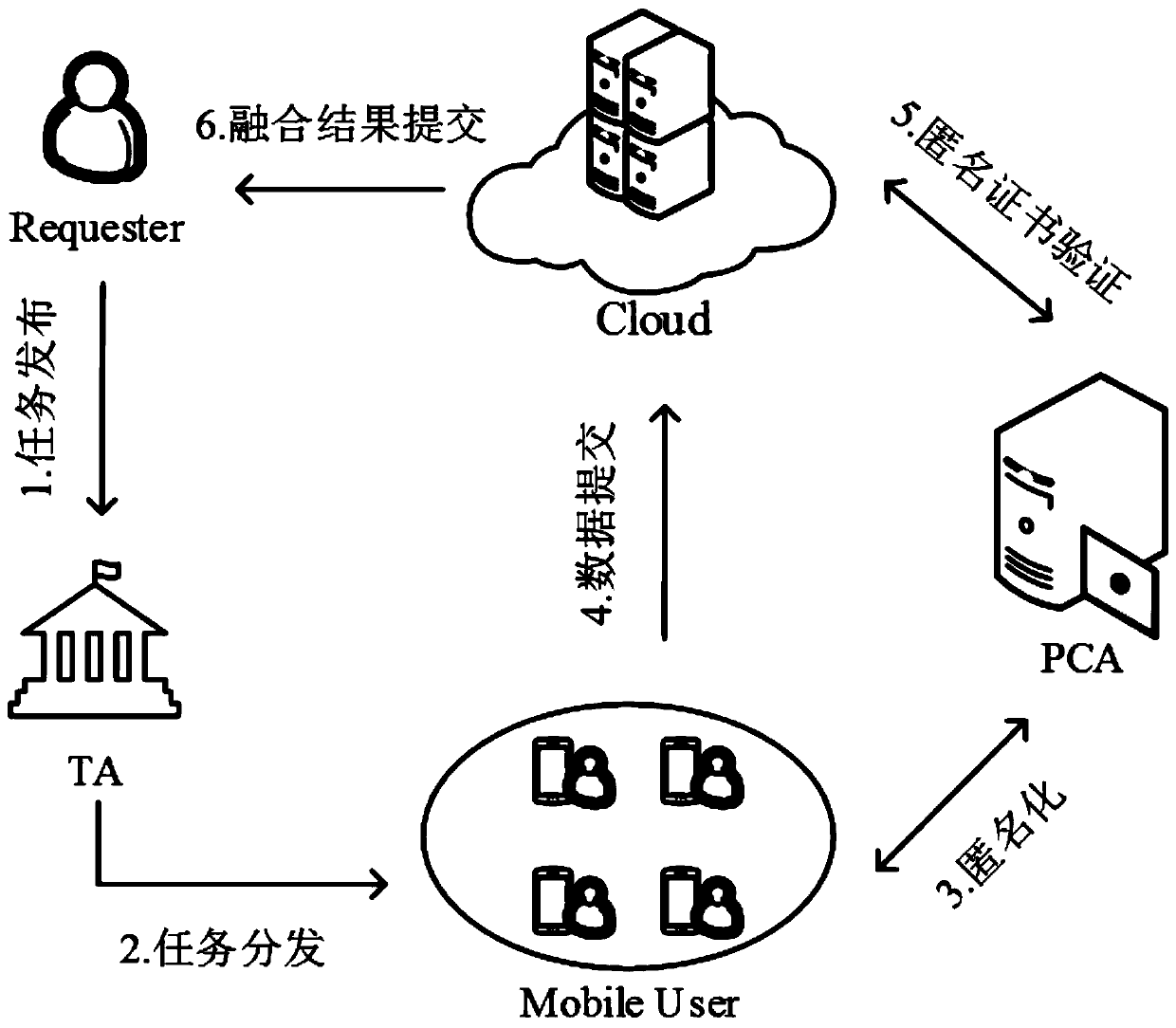
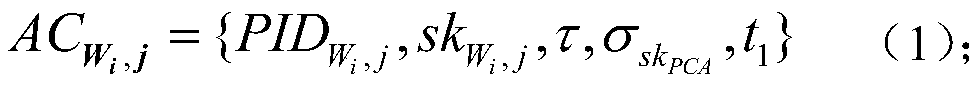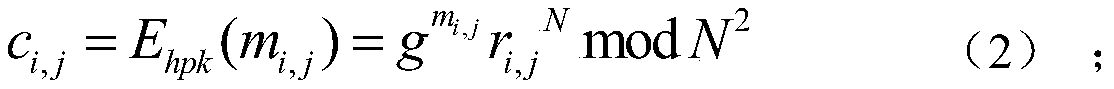Privacy information protection method based on cloud assistance in crowd sensing
A privacy information and crowd-sensing technology, applied in the field of privacy information protection, can solve problems such as the inability to protect user privacy information, privacy leakage, and inability to effectively prevent attacker data.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] Paillier public key cryptosystem is a probabilistic public key encryption system invented by Paillier. Its security is based on the difficult problem of judging the composite residual class. The encryption algorithm is a homomorphic encryption algorithm that supports arbitrary multiple addition homomorphic operations. Like other encryption schemes, it mainly contains 3 algorithms: KeyGen, Encrypt and Decrypt.
[0041] Key generation algorithm KeyGen: Let p, q be two large prime numbers satisfying gcd(pq,(p-1)(q-1))=1, and N=pq, randomly selected Let L(x)=(x-1) / N, then the public key is pk=(N,g), the private key is sk=λ(N)=lcm(p-1,q-1), where N is Open the mold, g is the open base.
[0042] Encryption algorithm Encrypt: For any plaintext m∈Z N ,choose randomly The encryption process is:
[0043] c=E pk (m)=g m r N modN 2 ;
[0044] Decryption algorithm Decrypt: For any ciphertext The decryption process is:
[0045]
[0046] Since the Paillier public-key encryption algorith...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com