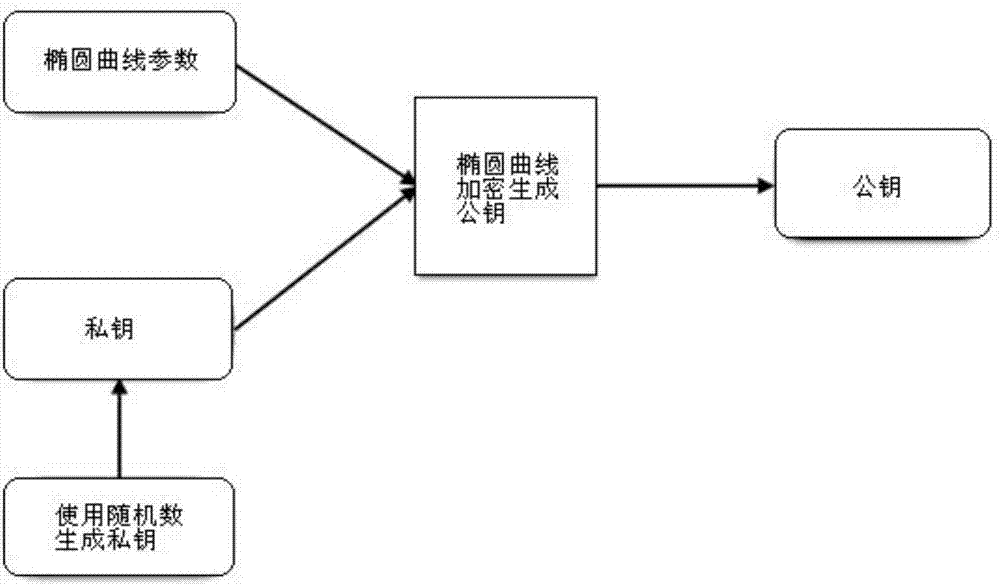
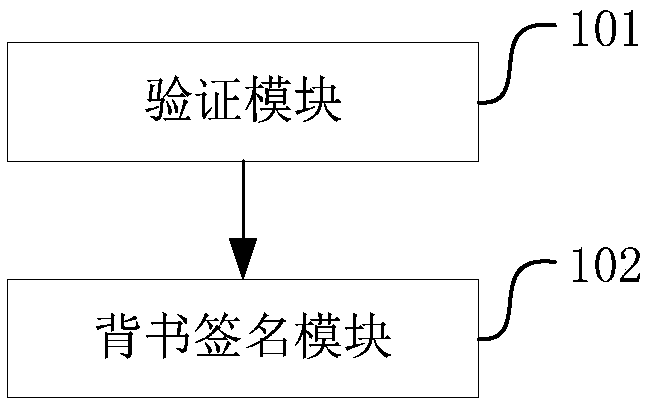
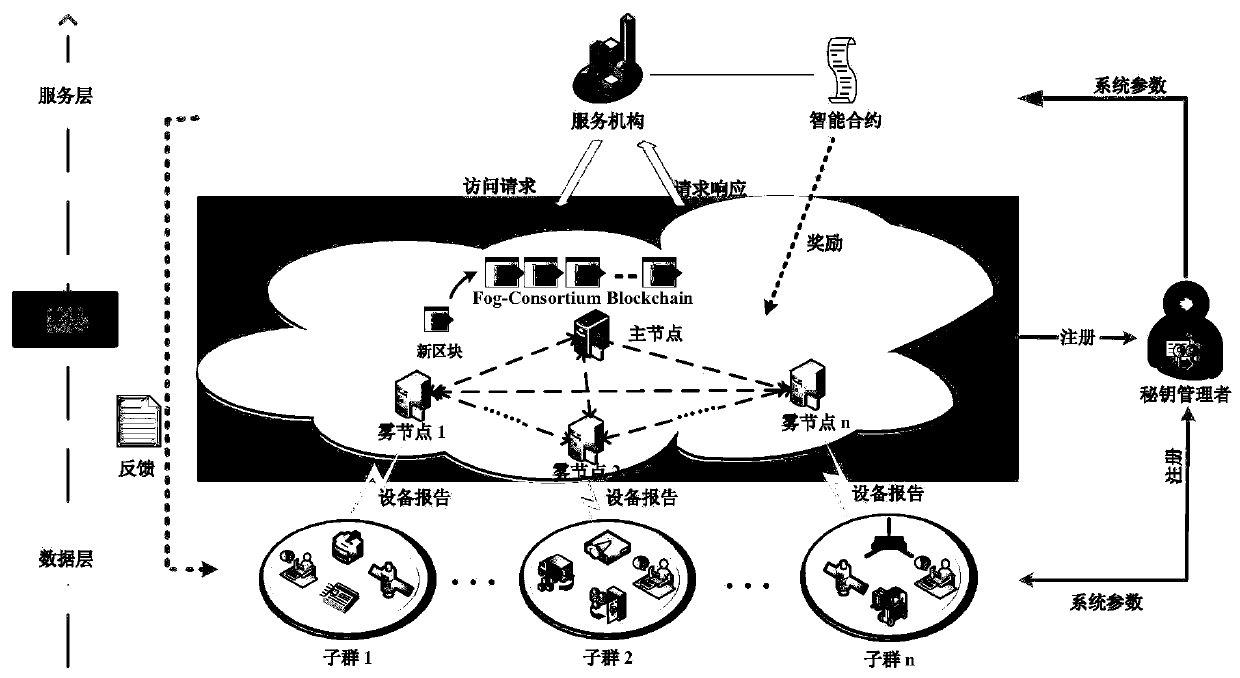
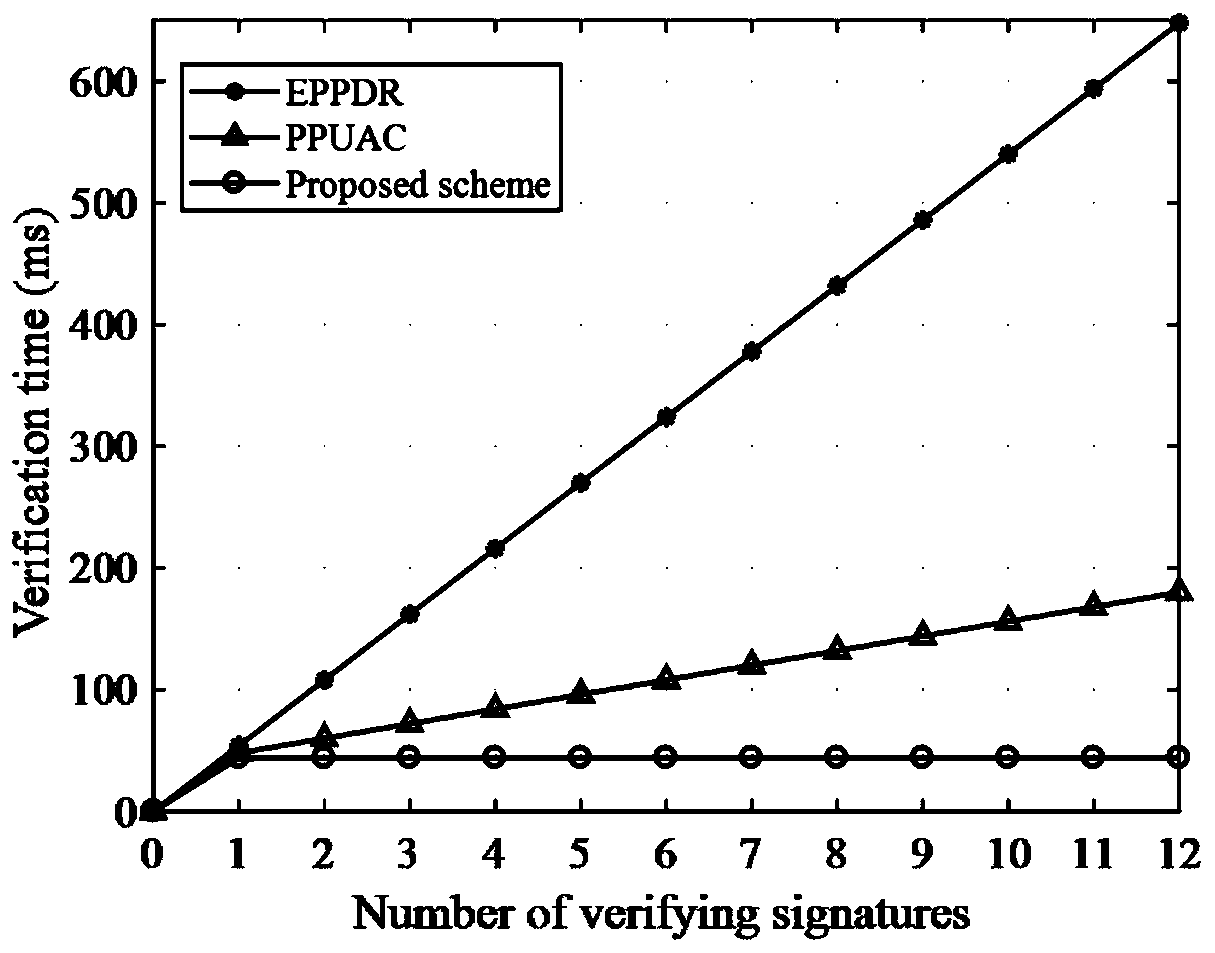
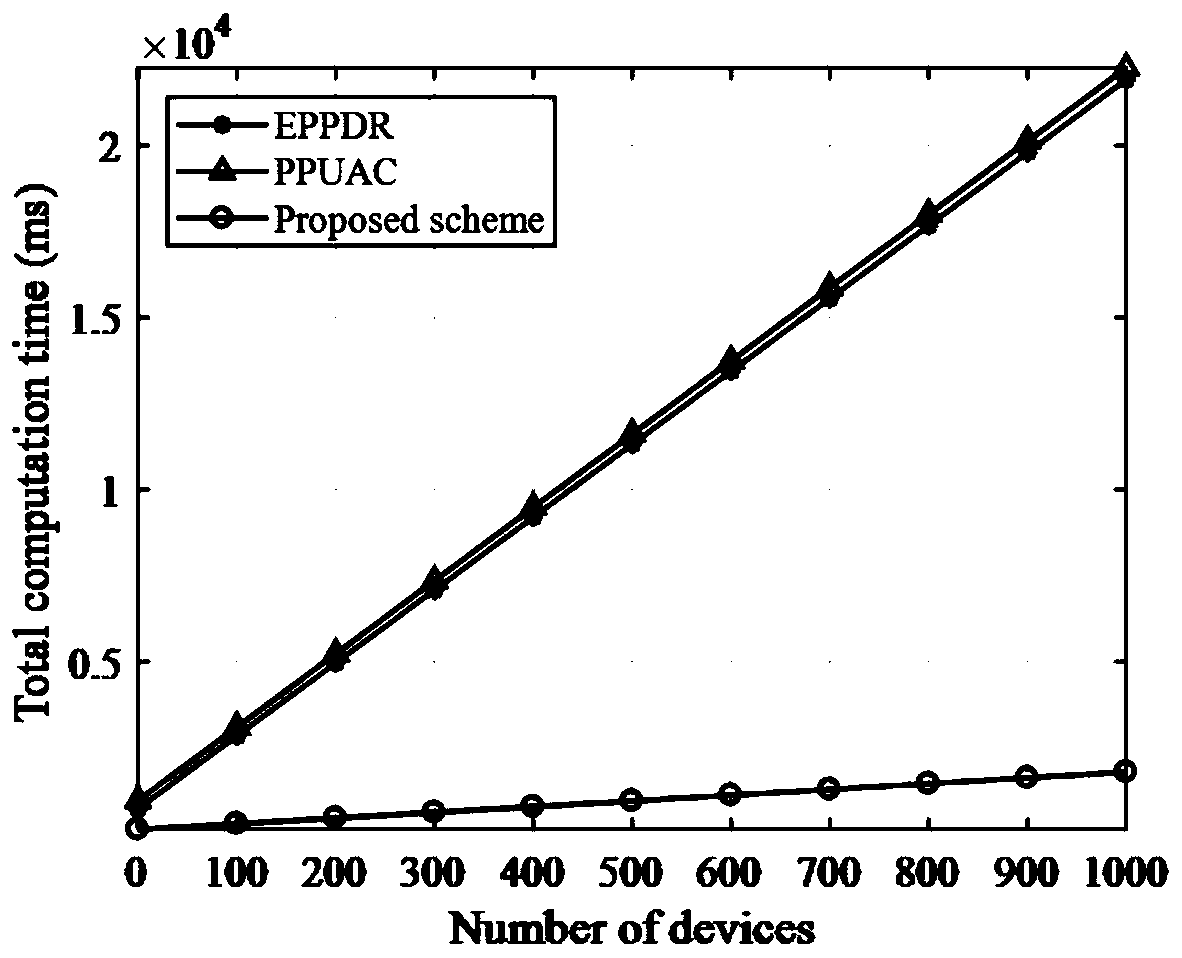
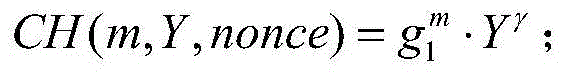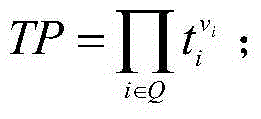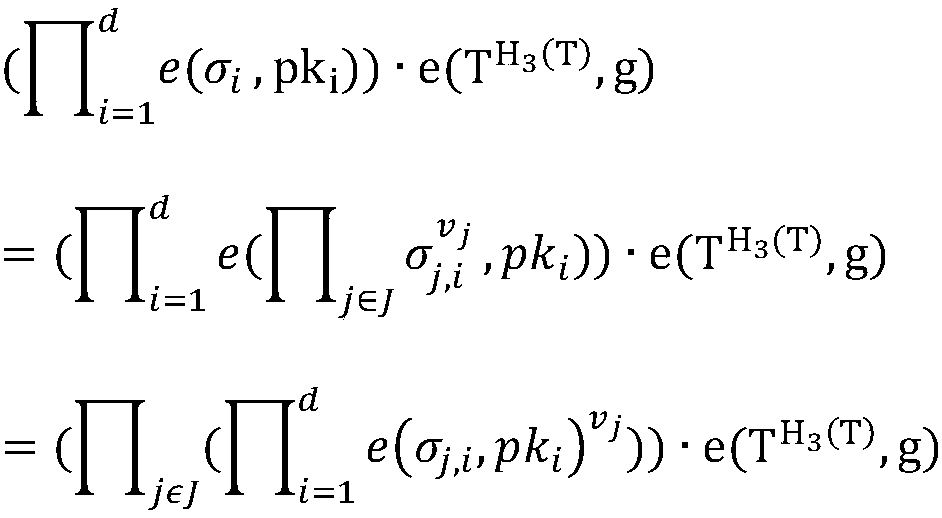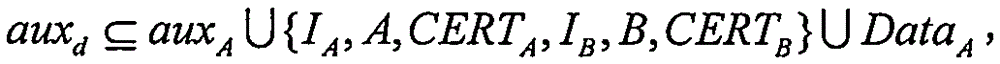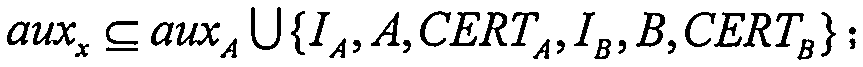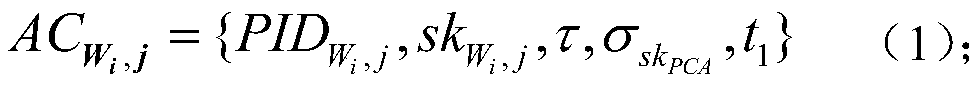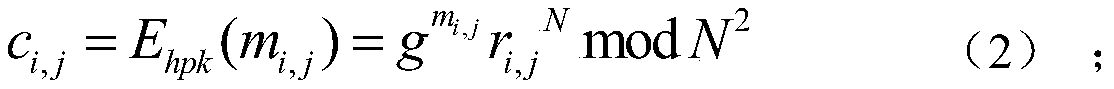Patents
Literature
92results about How to "Protect identity privacy" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
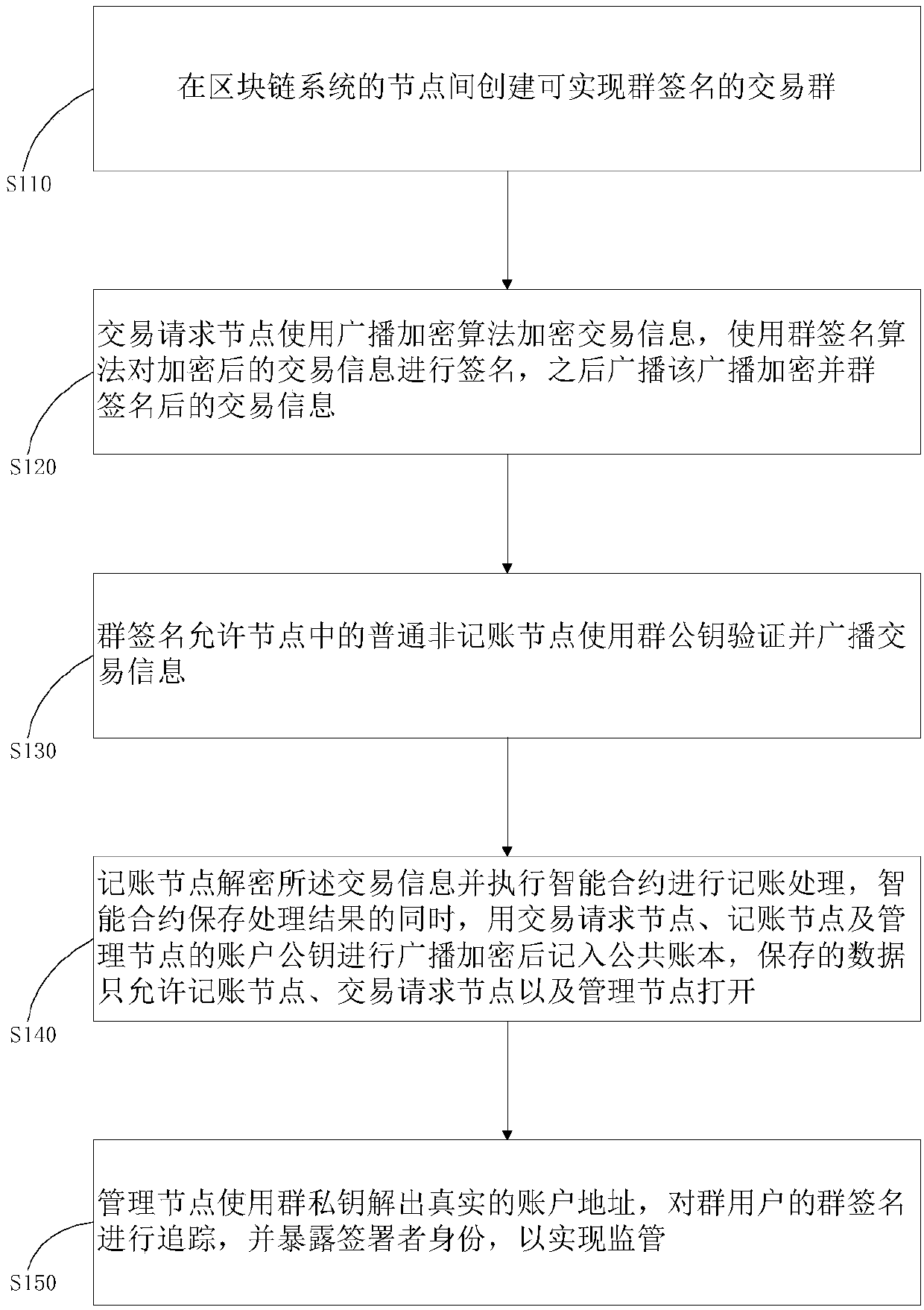
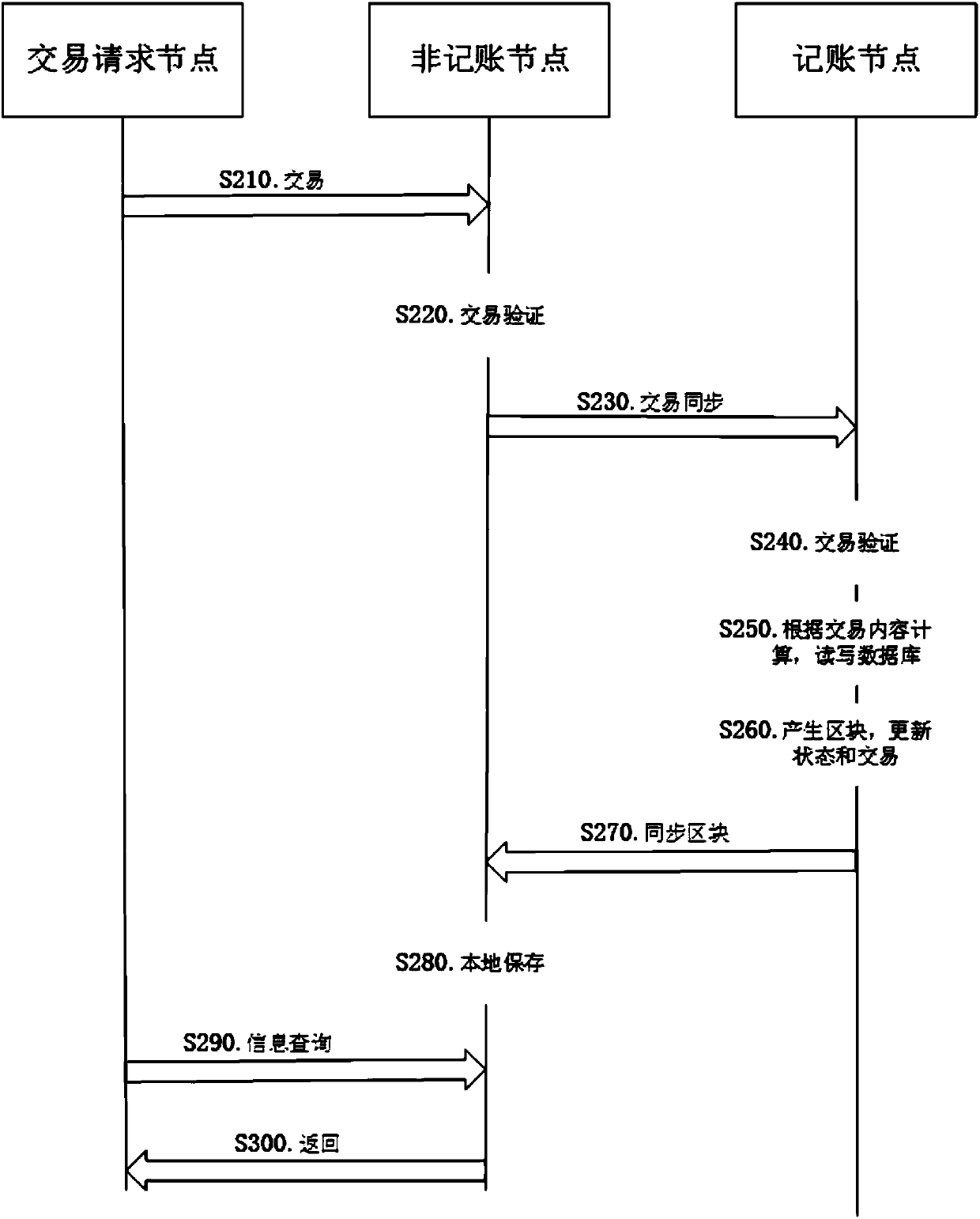
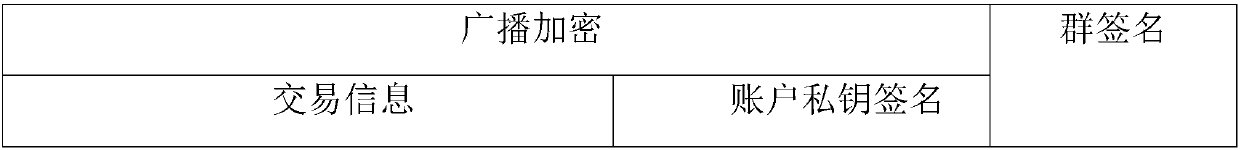
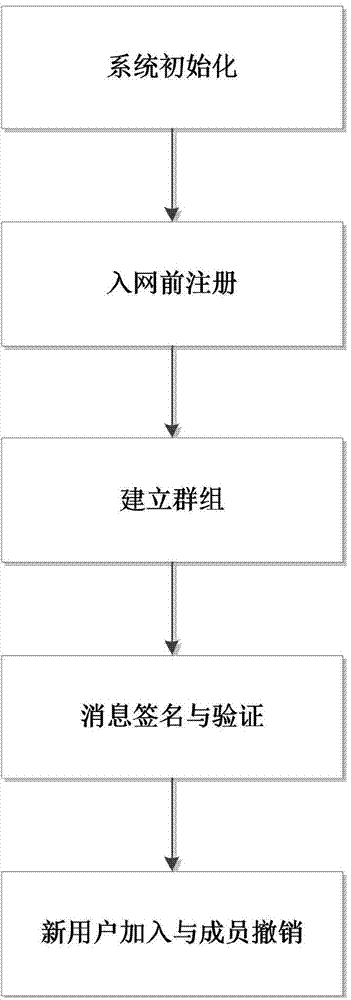
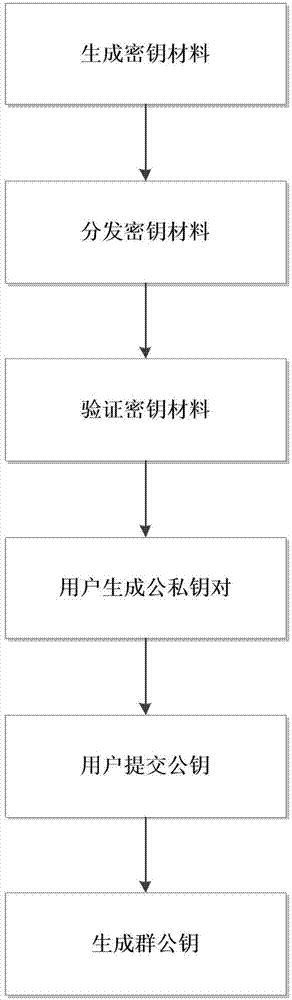
Method and system for privacy protection of block chain transaction
ActiveCN107911216ARealize regulationSupport reviewKey distribution for secure communicationFinancePublic accountPrivacy protection
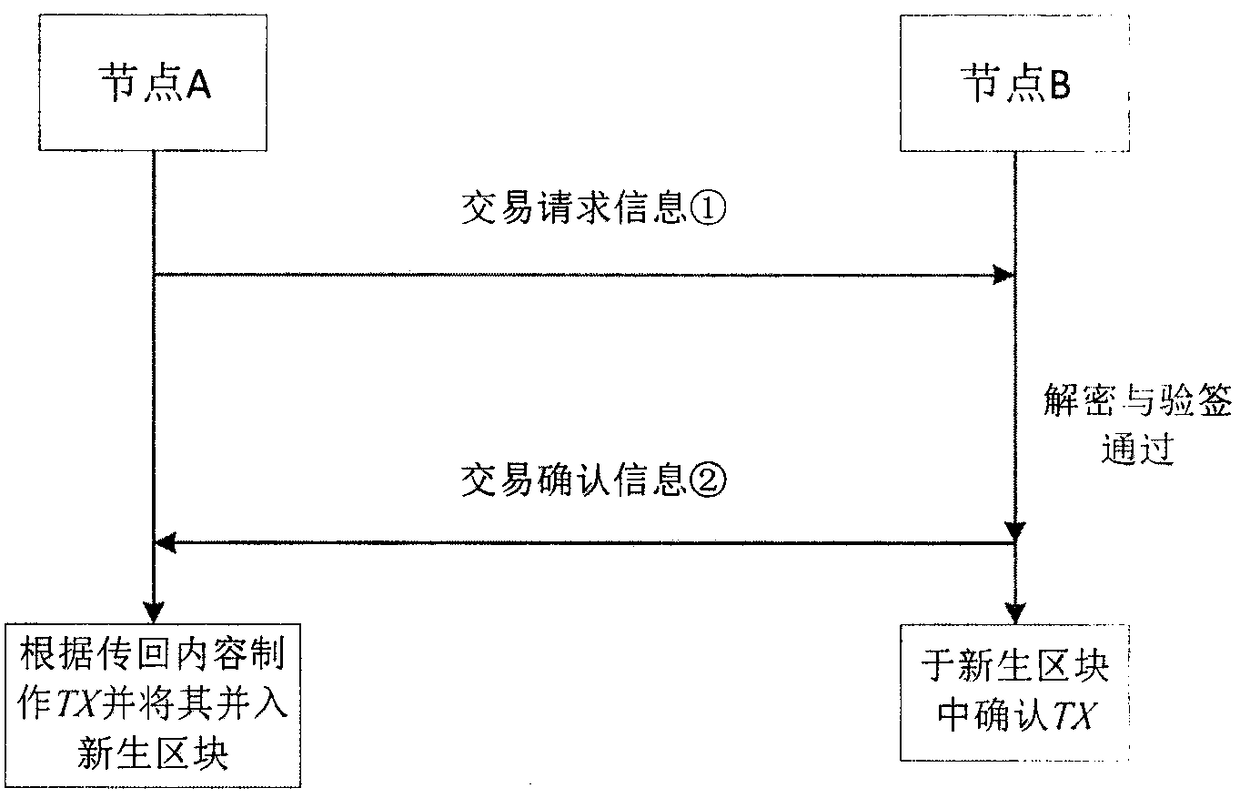
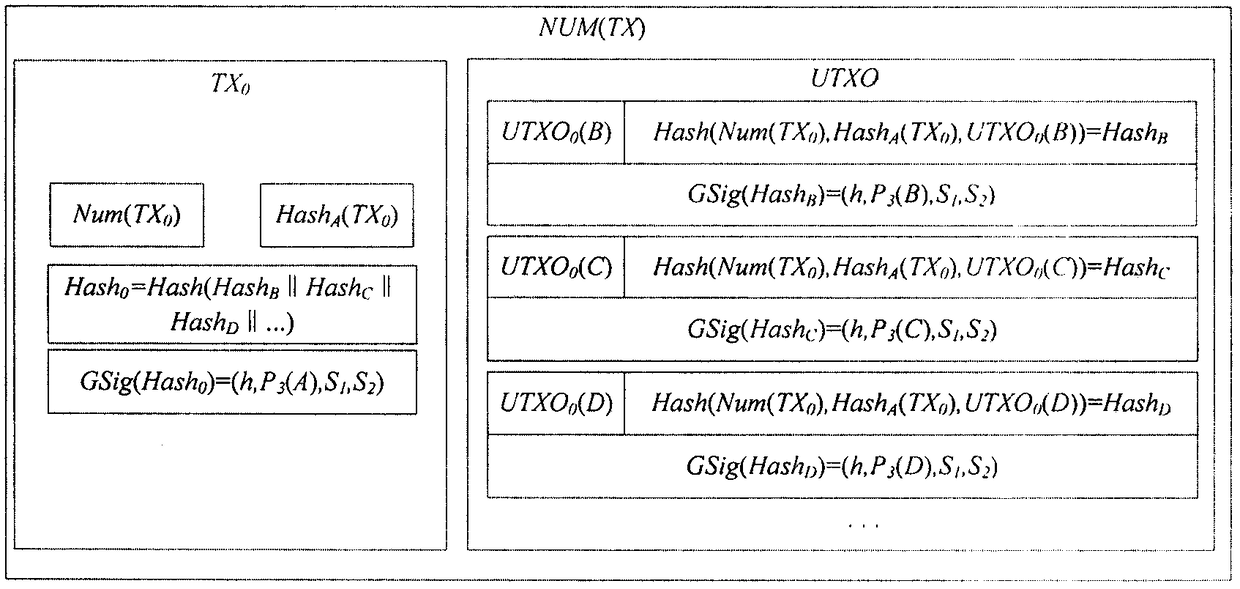
The invention provides a method and system for privacy protection of block chain transaction. The method comprises: a transaction group is established between nodes of a block chain system, a user establishes an account at a node, and the node generates public and private key information of the account and then joining of a group is carried out; a transaction request node encrypts transaction information by using a broadcast encryption algorithm, carries out group signature processing on the encrypted transaction information, and then broadcasts the transaction information after broadcast encryption and group signature processing; a common non-account-recording node verifies the transaction information and then broadcasts the transaction information, an account-recording node decrypts thetransaction information and performs an intelligent contract to carry out account recording, broadcast encryption is carried out and then the information is recorded into a public account book, wherein the stored data are only allowed to be opened by the account-recording node, the transaction request node and an administration node. With the broadcast encryption algorithm and group signature technology, a privacy protection problem in the block chain system is solved and the traceability of the transaction is ensured.
Owner:JUZIX TECH SHENZHEN CO LTD +1
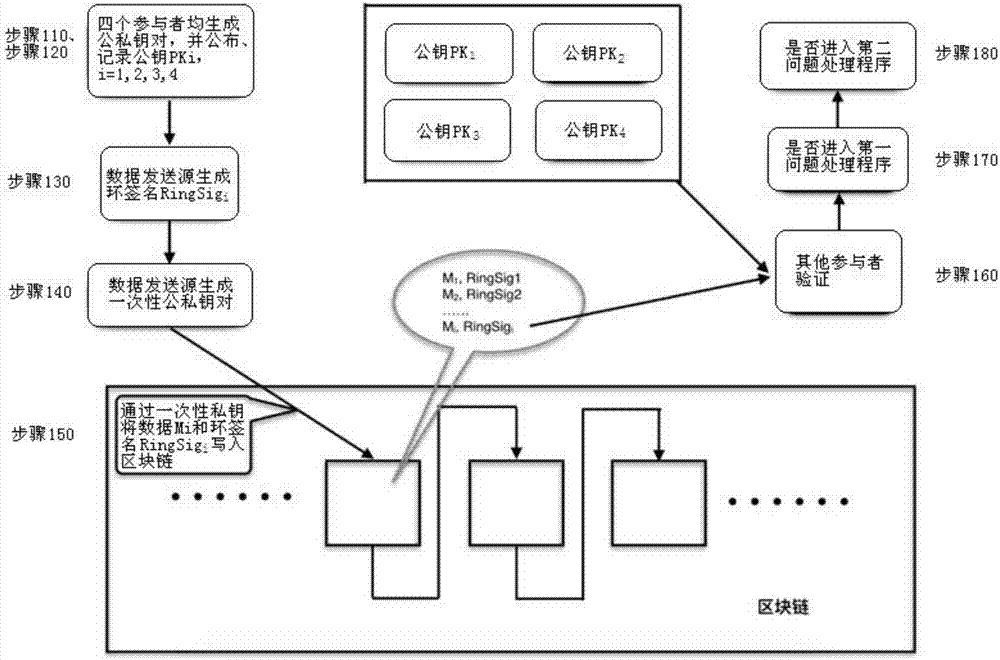
Multiparty data sharing method and system for protecting privacy data sending source
ActiveCN107453865AGuaranteed not to be exposedIdentity privacy data is not exposedKey distribution for secure communicationMultiple keys/algorithms usageBlockchainData sharing
The invention discloses a multiparty data sharing method for protecting privacy of a data sending source. A plurality of participants are jointly connected with a block chain and share data. The method comprises the steps that S1, the participants generate public and private key pairs; S2, the participants publish public keys corresponding to own identities and record all published public keys; S3, the data sending source generates a ring signature based on all public keys, a private key of the data sending source and to-be-sent data and writes the data and the ring signature into a block chain through a one-time private key; and S4, other participants reads the data and the ring signature, verify the ring signature based on the public keys, the data and the ring signature, employ the data if the verification result indicates legality, and do not employ the data if the verification result indicates illegality. The invention also discloses a corresponding system. According to the method and the system, the identity privacy data of a data sharer is prevented from being exposed, and data receivers believe that the data sharer really has the data sharing authority or even realizes responsibility investigation.
Owner:ZHONGAN INFORMATION TECH SERVICES CO LTD
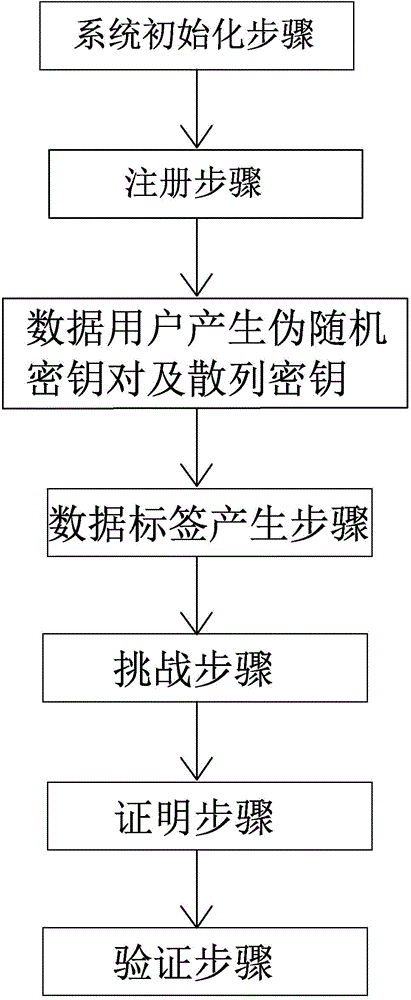
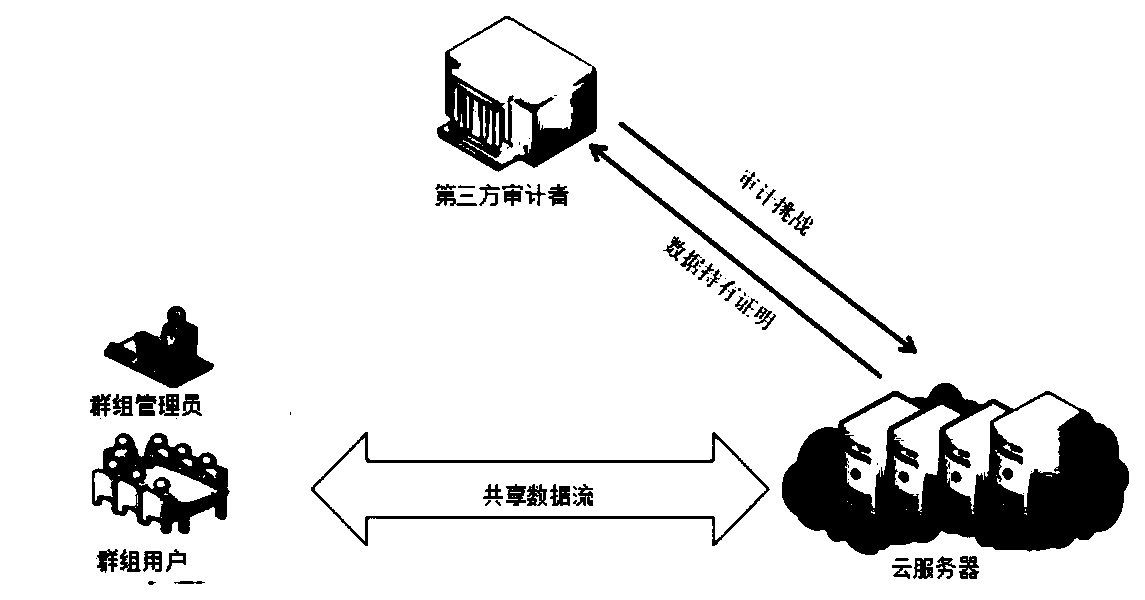
Efficient privacy protecting audit scheme based on chameleon hash function of cloud storage
InactiveCN104601605AImplement integrity verificationRealize privacy protectionTransmissionData labelingUser privacy
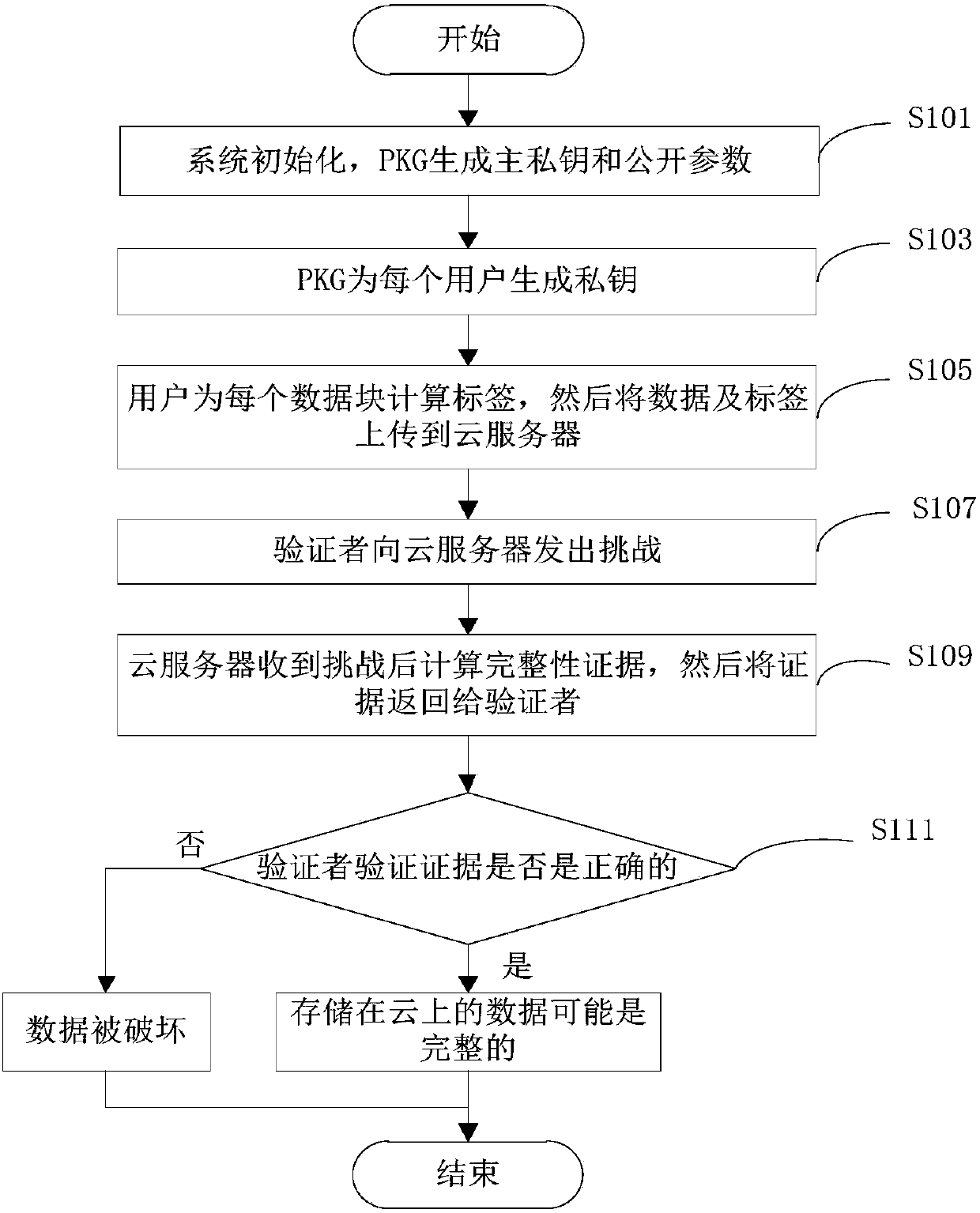
The invention provides an efficient privacy protecting audit scheme based on the chameleon hash function of cloud storage. The scheme includes (1) a system initialization step; (2) a registration step; (3) a pseudo-random key pair and hash key generation step for data users; (4) a data label generation step; (5) a challenge step; (6) a proof step; (7) a validation step. According to the scheme, on the basis of the decidable Diffie-Hellman problem and a chameleon digital signature, a privacy protecting public audit scheme is established, and high efficiency, low safety assumptions and wide application range are provided; according to a cloud server, the identity privacy of the data users is protected, and the outsourcing data integrity is protected; according to auditors, the data user privacy is protected in the whole auditing process.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
A vehicle networking architecture based on block chain and a working method thereof
ActiveCN109068299ASolve the centralization problemSolve the problem of mutual distrust between entitiesParticular environment based servicesUser identity/authority verificationUndirected graphIn vehicle
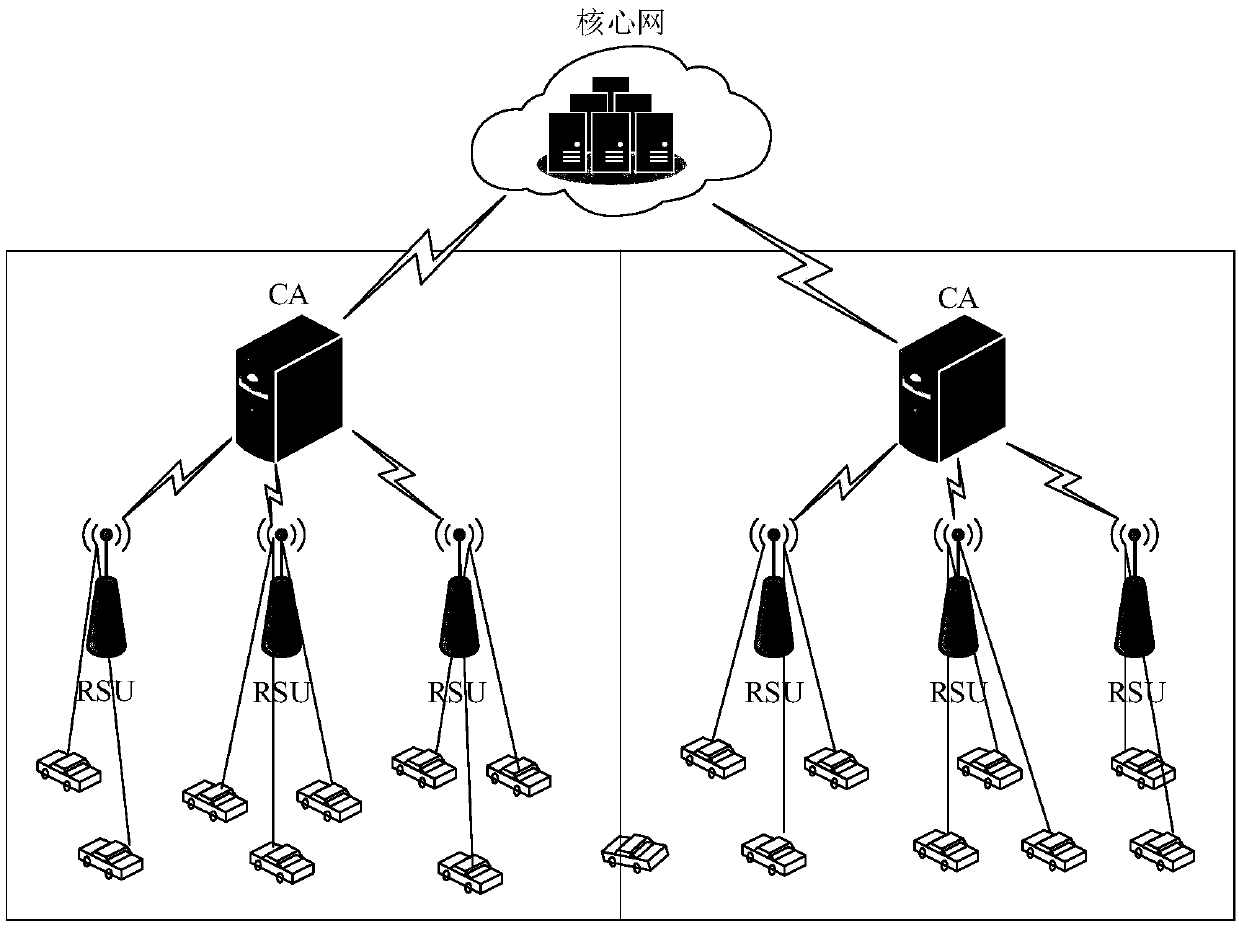
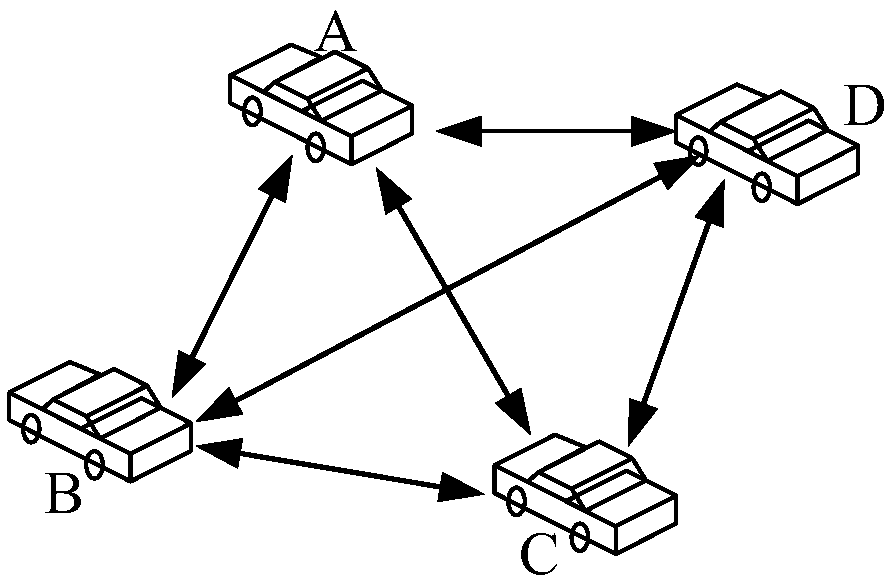
The invention discloses a vehicle networking structure based on a block chain and a working method thereof. The vehicle networking structure comprises an interconnected vehicle entity, a vehicle-mounted unit OBU, a roadside unit RSU, a core network and a block chain network. It has the typical characteristics of decentralization, distribution, collective maintenance and incapability of tampering.It can effectively solve the problem of centralization of traditional vehicle networking architecture and mutual distrust between entities. At that same time, the invention provides an undirected graph generation method, an identity privacy protection method and a location privacy protection method when the beacon information is uploaded by a vehicle, thereby solving the problem of identity and location privacy disclosure of a vehicle networking architecture based on a block chain.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
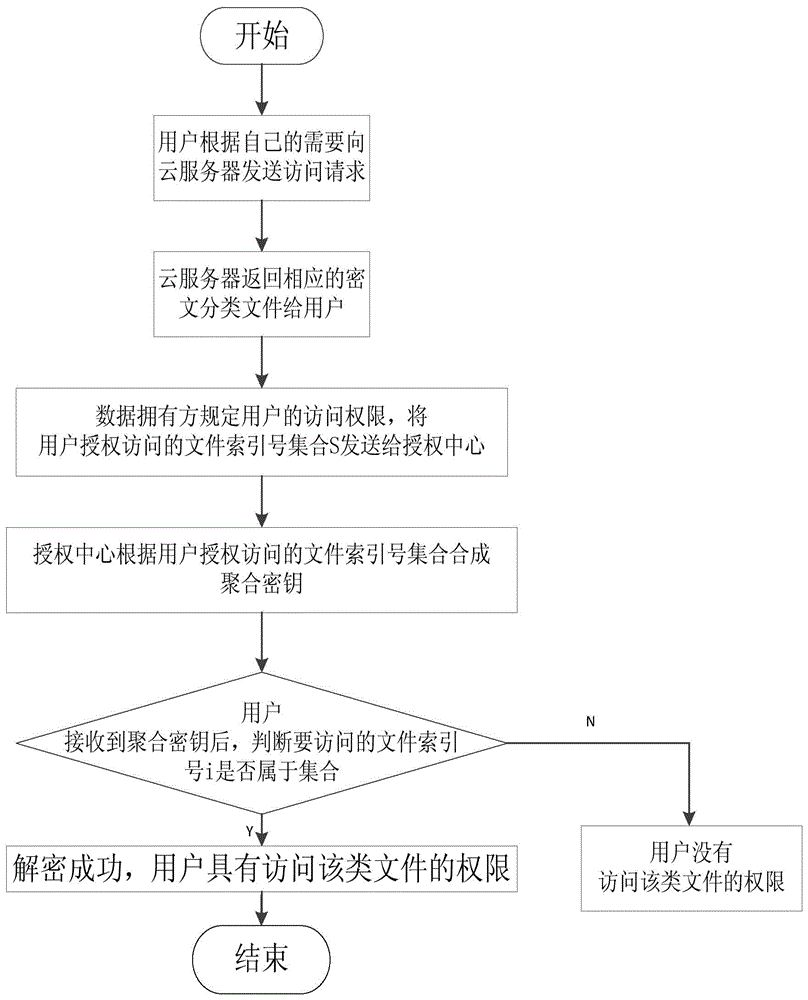
Data sharing based file access and permission change control method
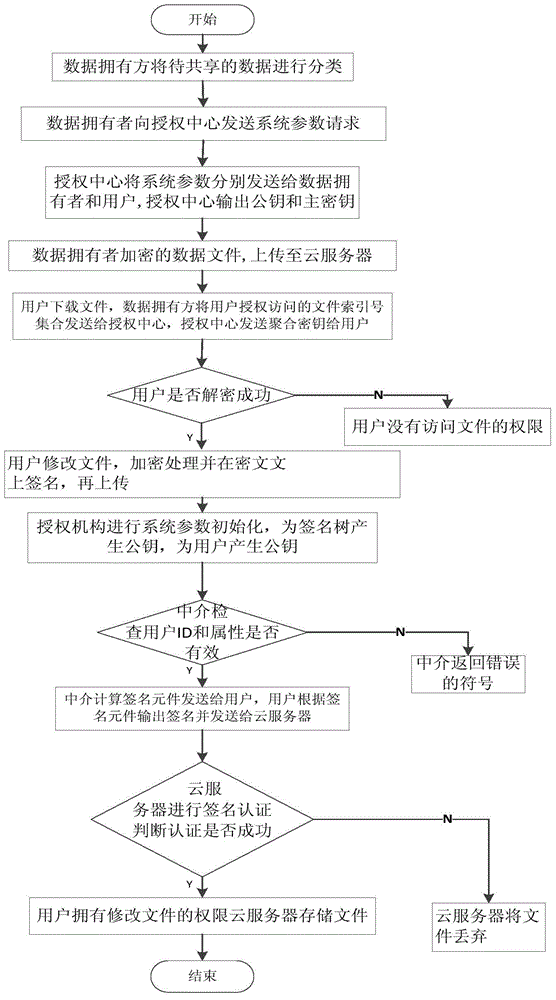
ActiveCN104468615AReduce computational complexityReduce storage spacePublic key for secure communicationUser identity/authority verificationComputation complexityCiphertext
The invention discloses a data sharing based file access and permission change control method. The data sharing based file access and permission change control method mainly solved the problem that the prior art is low in access efficiency, complicated in computation and is not applicable to file modification of users and comprises the achieving steps that 1 a data owner conducts classification processing on data files according to attributes and performs encryption and uploading; 2 the users access classified files according to the demands and a cloud server returns corresponding files to the users; 3 an authorization center synthesizes aggregate secret keys and transmits the aggregate secret keys to the users, and the users use the aggregate secret keys to decrypt encryption files; 4 the users modify the accessed files, encrypt the modified files, attach signatures to the modified files and upload the modified files; 5 the cloud server conducts attribute based signature verification on the users, stores the files if verification succeeds, otherwise abandons the files if the verification does not succeed. The data sharing based file access and permission change control method has the advantages of being high in read-write performance and efficiency, low in computing complex and reliable in storage and can be used for data sharing and access control based on privacy protection in a cloud computing environment.
Owner:XIDIAN UNIV
Intelligent medical data storage method based on multi-level blockchain system architecture
ActiveCN110727737AImprove efficiency andHigh robustness and fault toleranceDatabase distribution/replicationDigital data protectionBlockchainEncryption system
The invention discloses an intelligent medical data storage method based on a multi-level blockchain system architecture. According to the method, an existing single-chain or double-layer blockchain system design is abandoned, a multi-layer blockchain system architecture is provided based on a Hyperledger Fabric platform to solve the storage problem of medical data, efficient management of large-scale medical data is achieved, and the efficiency and expandability of the system are greatly improved. Meanwhile, a dual-key encryption system combining public key encryption and symmetric encryptionis adopted, storage and sharing of medical data are achieved under the condition that privacy of the patient is protected, and great convenience is provided for medical institutions, patients and scientific research institutions.
Owner:NANJING UNIV OF POSTS & TELECOMM
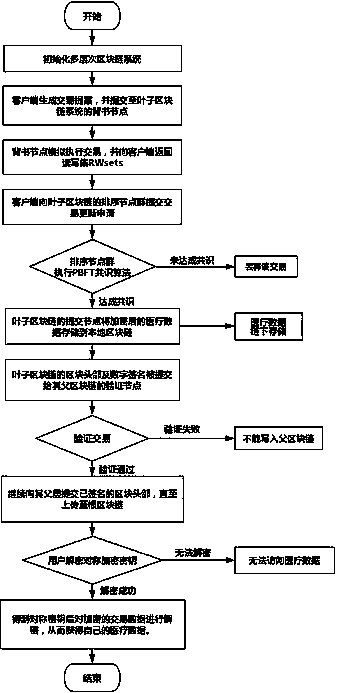
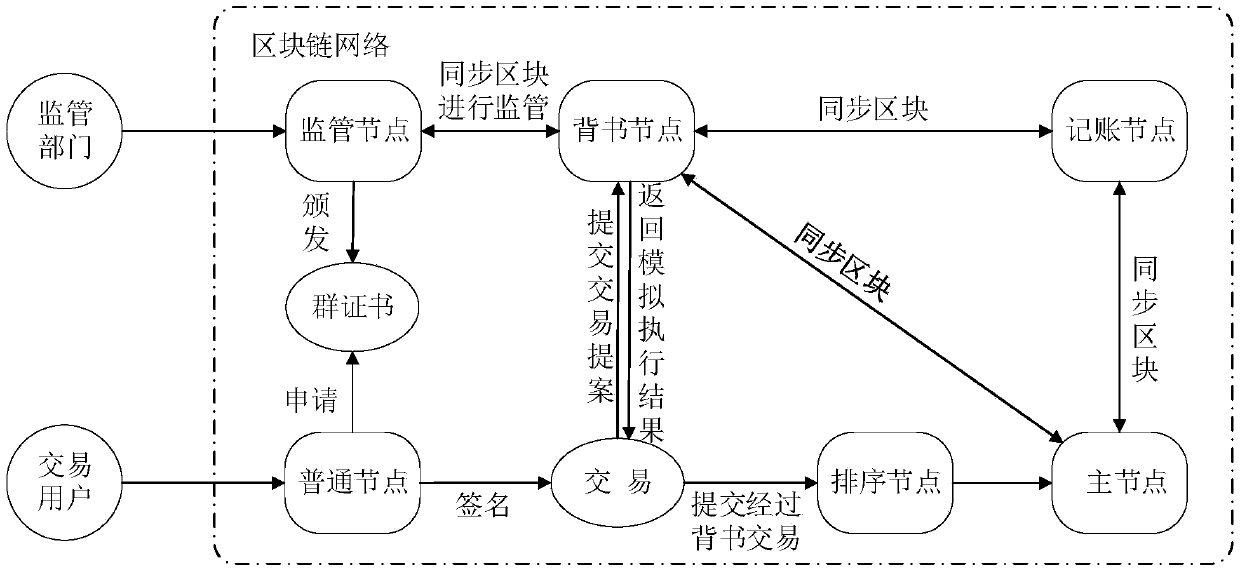
Permission block chain privacy protection and supervision method based on group signatures
InactiveCN109636599AProtect identity privacyGood anonymityFinanceDigital data protectionPrivacy protectionIdentity privacy
The invention discloses a permission block chain privacy protection and supervision method based on group signatures. In a transaction process, whether the endorsement verification of the endorsementnode, the sequencing service of the sequencing node and the consensus process of the main node and the accounting node can only verify the legality of the identities of the two parties of the transaction, and cannot correspond the signature to the real identity of the user, so that the identity privacy of the user is guaranteed. After the transaction is completed, the supervision department can synchronize the block with other nodes through the supervision node, then open the signature contained in the transaction, and enable the signature to correspond to the real identity of the transactionuser, so as to supervise the block chain.
Owner:GUANGXI NORMAL UNIV
Internet of Vehicles system based on block chain and working method
ActiveCN110446183AAvoid participationReduce participationParticular environment based servicesUser identity/authority verificationInvestigation methodsPrivacy protection
The invention provides an Internet of Vehicles system based on a block chain. The system comprises a certificate issuing mechanism, a vehicle-mounted unit deployed on a vehicle, a block chain networktaking a roadside unit as a peer node, and a cloud server for providing cloud service for the vehicle-mounted unit and the roadside unit. The working process of the system comprises four stages of vehicle registration, vehicle authentication, vehicle announcement and vehicle forwarding. The system provided by the invention has the characteristics of distribution, data collective maintenance, no tampering and conditional privacy protection. Meanwhile, a vehicle identity privacy protection method, a malicious vehicle responsibility investigation method and a transaction data storage method are provided, so that the problems of dependence on trusted third parties and mutual trust between entities in the traditional Internet of Vehicles architecture can be effectively solved.
Owner:XIAN UNIV OF POSTS & TELECOMM
Crowdsourcing resource distributed anonymous allocation method based on block chain and allocation system thereof
PendingCN110069345AAvoid single point of failureAvoid serious problems with failureKey distribution for secure communicationFinanceChain networkDistributed computing
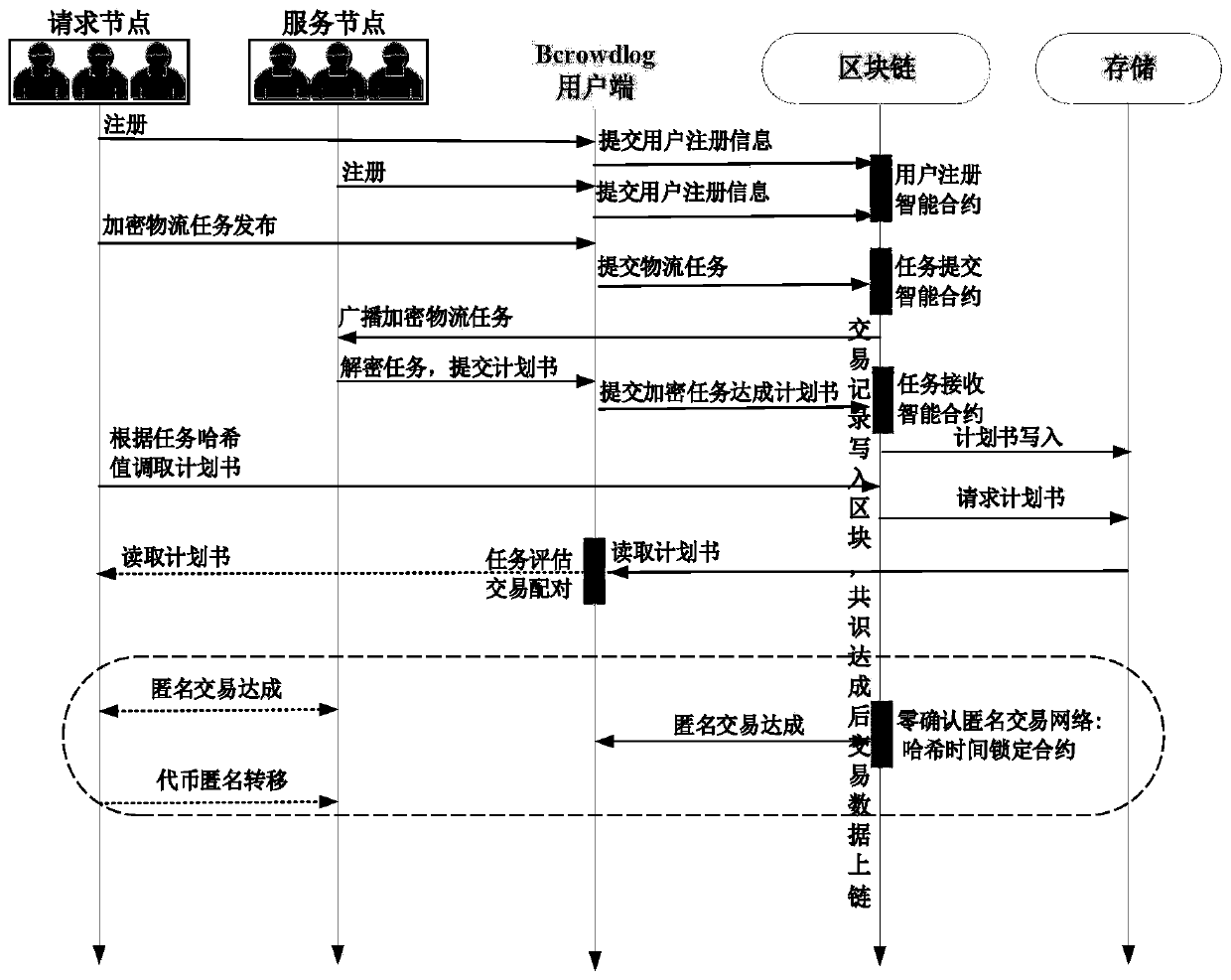
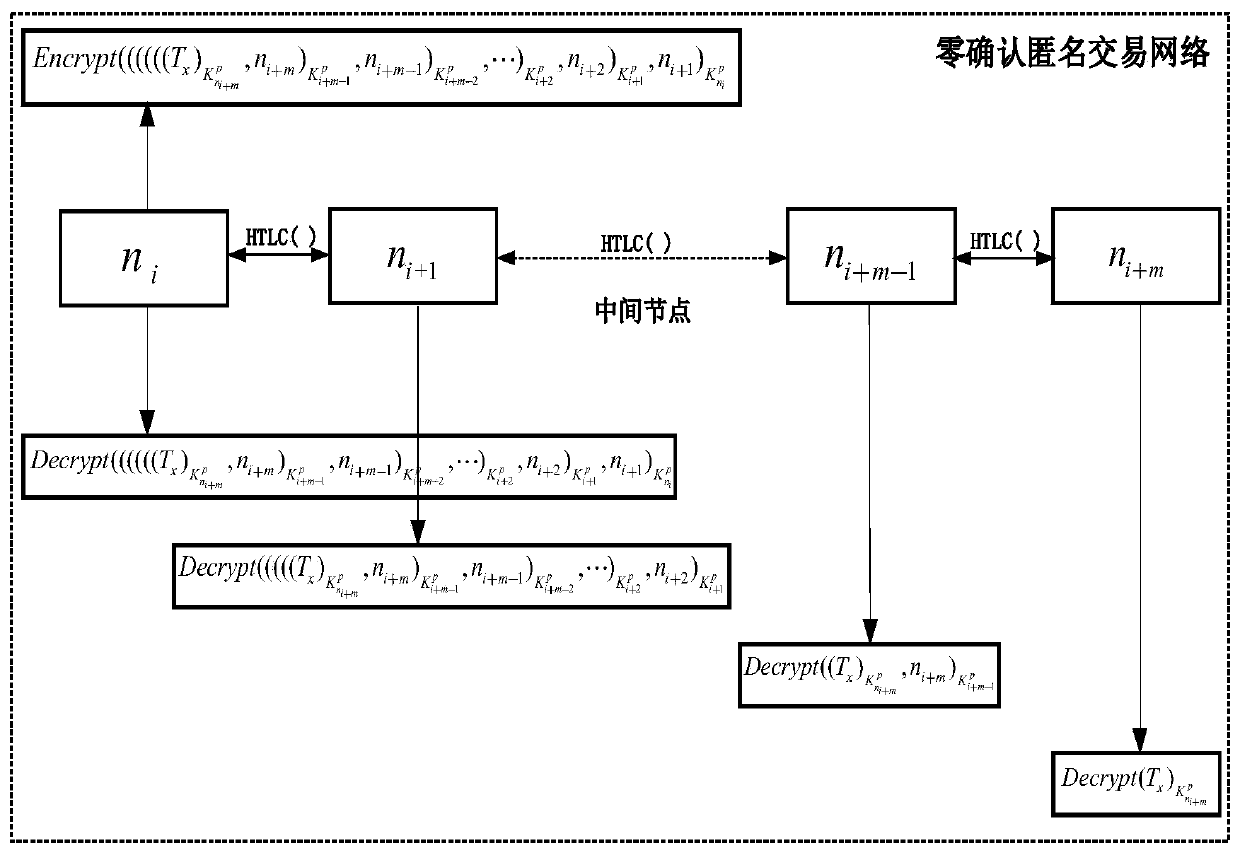
The invention discloses a crowdsourcing resource distributed anonymous allocation method based on a block chain and an allocation system thereof, hereinafter referred to as a crowdsourcing resource anonymous allocation system, comprising the following steps: user registration; linking the user registration information; creating a task release intelligent contract on the block and recording task release information; making a plan on the premise of the service node; enabling the request node to select the most excellent service node from the achievement of the plan; and creating a Hash time locking contract on the block and establishing an onion route to realize anonymous communication of the two parties of the transaction. According to the invention, the Hash time locked smart contract is introduced into the block chain network, zero confirmation transaction chaining is realized, and the transaction amount in unit time is greatly improved. In addition, an onion route from the request node to the service node can be constructed through a payment channel established by the Hash time locking contract, so that anonymous transactions of the request node and the service node are realized.
Owner:JIANGSU UNIV
Method for protecting privacy of vehicle ad hoc network based on signcryption
InactiveCN107682149AEffective calculationProtect identity privacyKey distribution for secure communicationParticular environment based servicesDigital signatureSigncryption
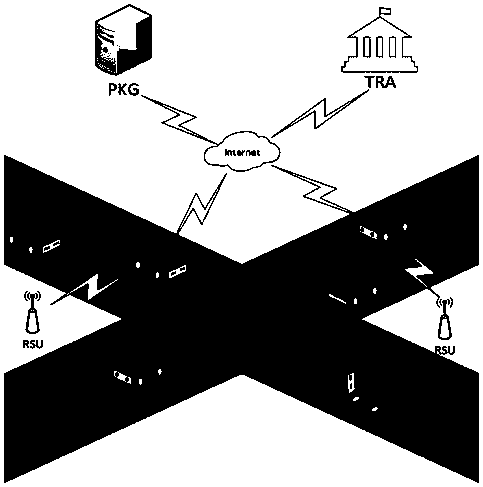
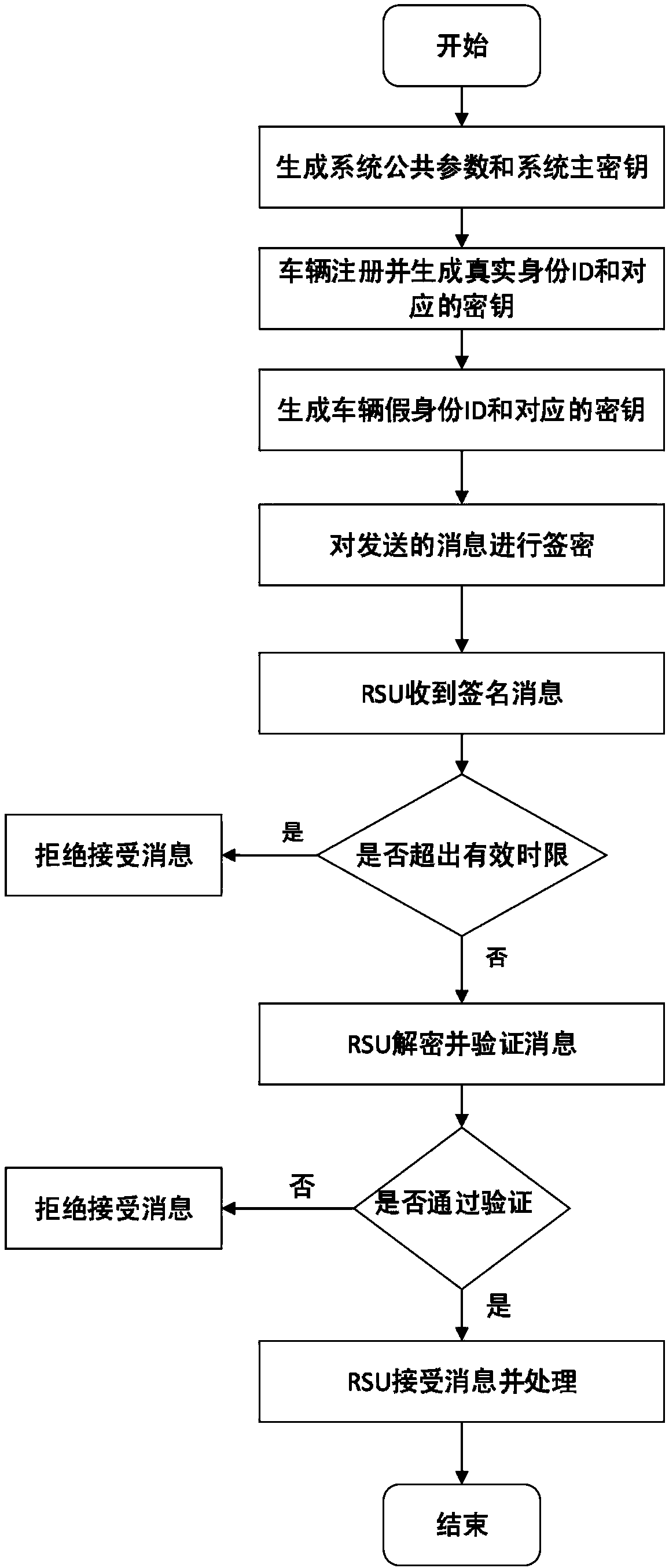
The invention request to protect a method for protecting privacy of a vehicle ad hoc network based on signcryption. The method is used for solving a privacy protection problem when a vehicle node (OBU) under an environment of the Internet of vehicles communicates with a road side unit (RSU). On the basis of a digital signature mechanism and a pseudonym mechanism, the invention provides a signcryption mechanism which is an integrated scheme synthesizing encryption and signature; in the method, privacy protection on the vehicle node is achieved via the pseudonym mechanism. Under the environmentof the Internet of vehicles, the vehicle node sends own identity information to a TRA to generate a pseudonym, a secret key generation center generates a secret key corresponding to a private key of the pseudonym, the vehicle node uses the generated pseudonym and the secrete key to perform signcryption on a message and sends the message to the road side unit, after receiving the message, the roadside unit uses the private key to decrypt the message and verify the same, and the message is accepted if the verification is passed.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
Internet of vehicles group key management method oriented to multiple services and privacy protection
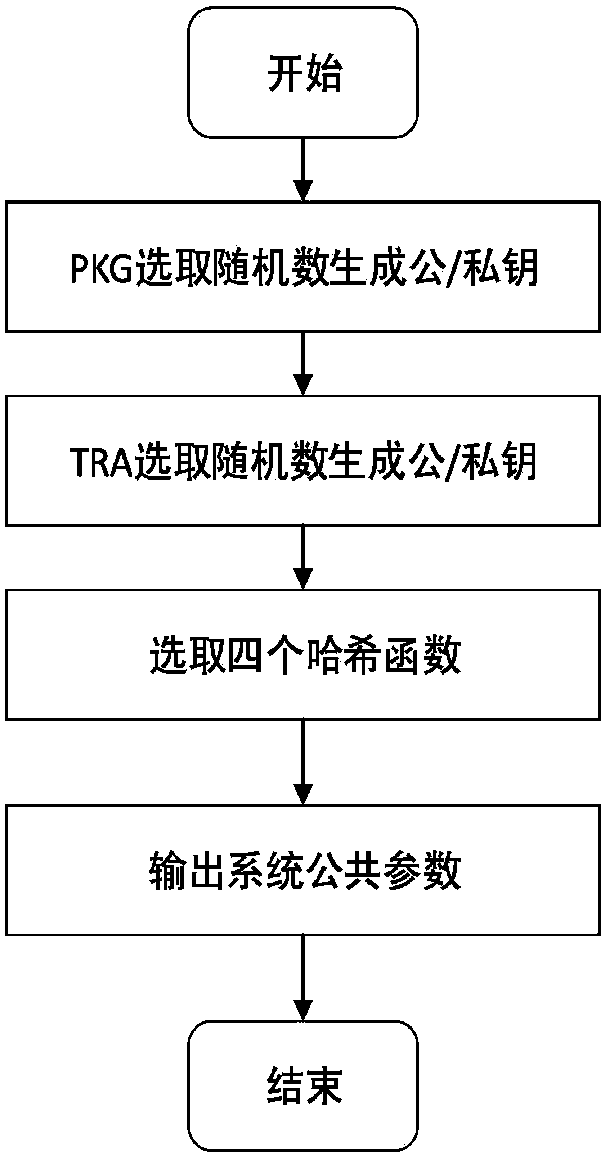
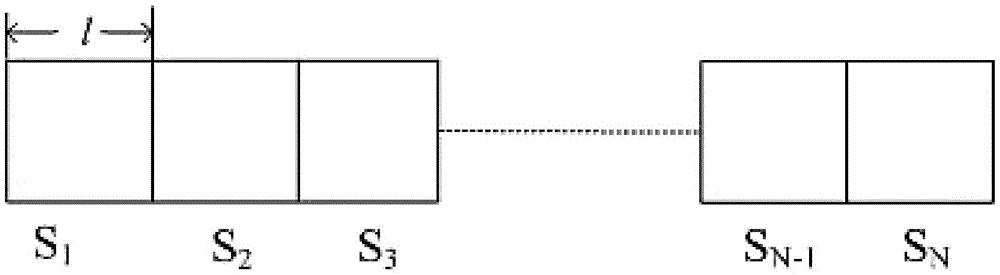
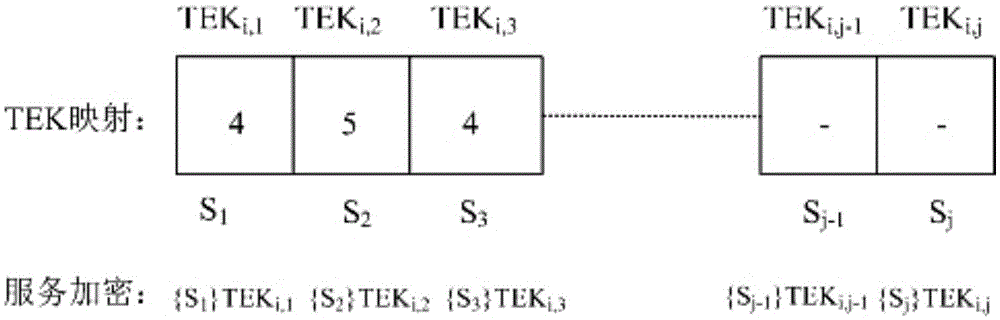
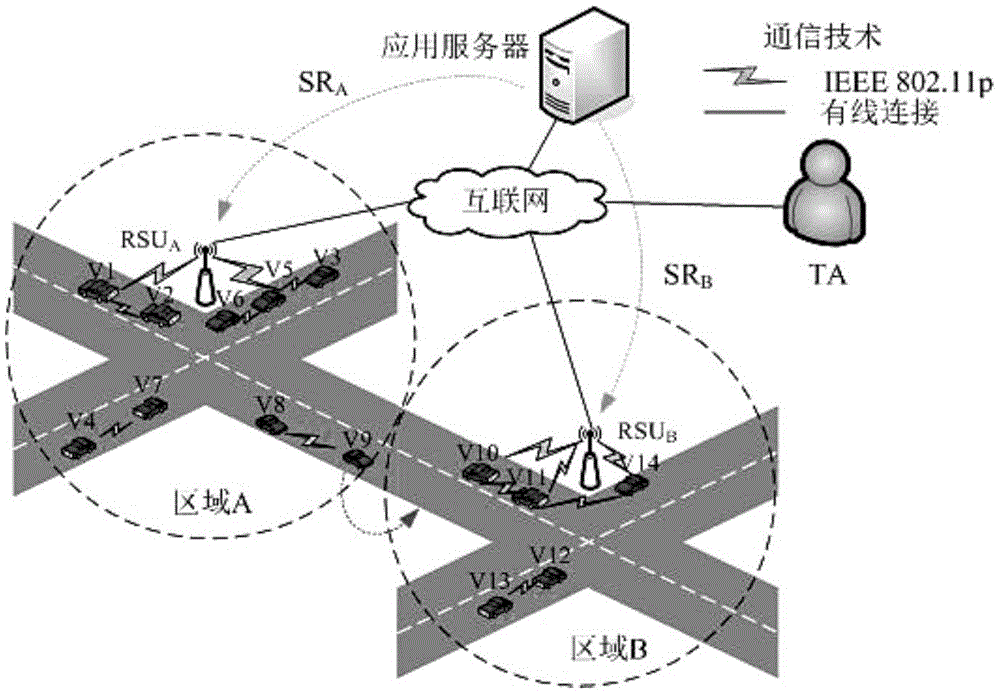
ActiveCN105554105ASolve the problem of multiple groups ordering multiple servicesProtect identity privacyTransmissionComputer networkPrivacy protection
The invention discloses an Internet of vehicles group key management method oriented to multiple services and privacy protection. The method sequentially comprises the following steps: (1) establishing a two-layer network model of Internet of vehicles (colons are deleted); (2) describing a scene in which multiple groups subscribe multiple services in the Internet of vehicles based on the network model in the step (1); (3) protecting identity privacy of vehicles through a pseudonym mechanism, wherein TA can reveal real identities of the vehicles when service disputes occur; (4) using key update slot KUS by a TEK update strategy; and (5) after turnover of the vehicles, performing TEK update in a target region to ensure backward security, and performing TEK update in an original region to ensure forward security. Through adoption of the method, the identity privacy of the vehicles, non-repudiation of vehicle subscription services and service continuity during inter-regional turnover of the vehicles can be ensured.
Owner:ANHUI UNIVERSITY
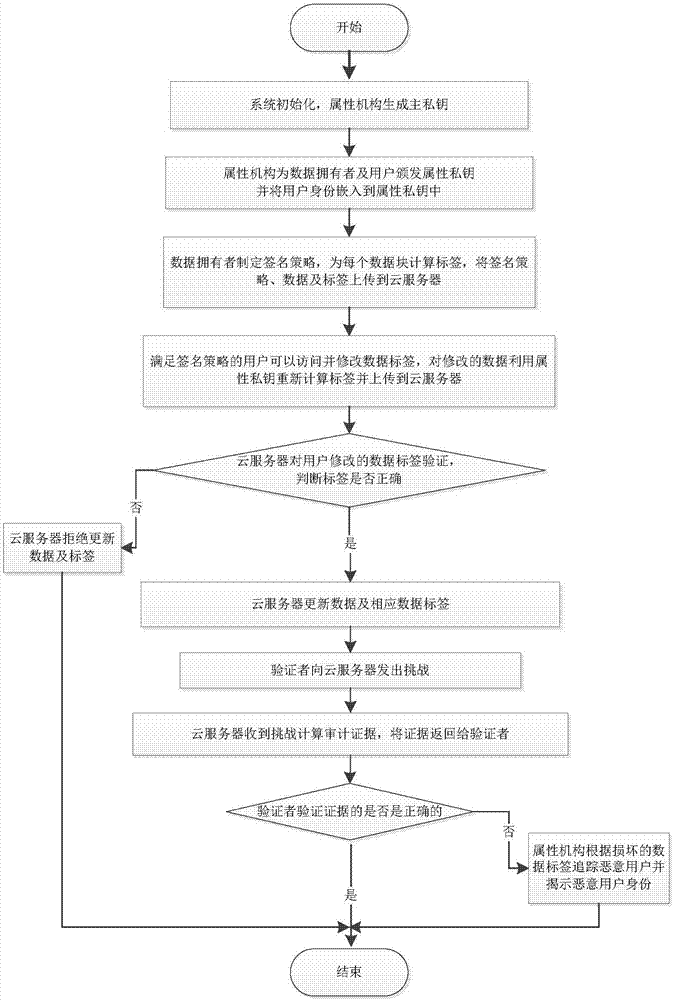
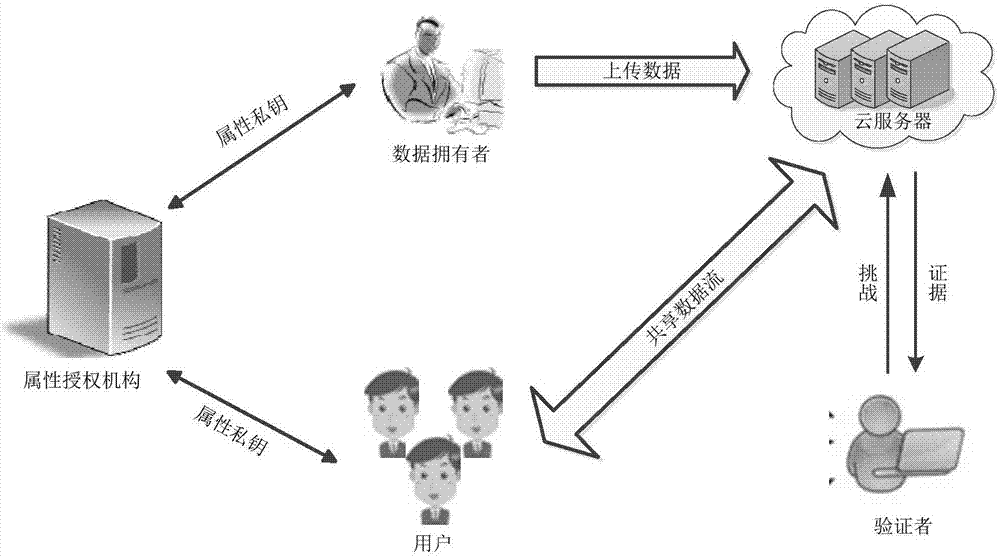
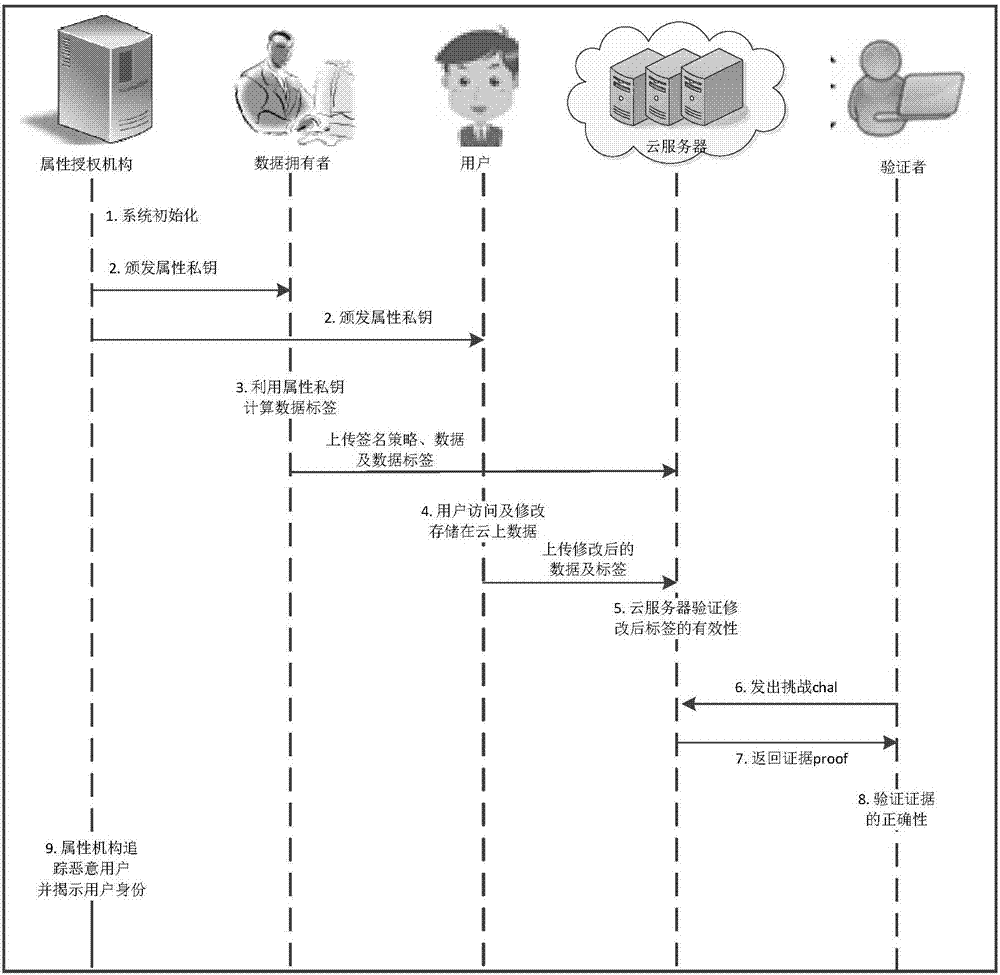
Traceable effective open auditing method and system in cloud storage data sharing
ActiveCN107147720AProtect identity privacyEnable traceabilityKey distribution for secure communicationShared environmentData sharing
The invention discloses a traceable effective open auditing method in cloud storage data sharing, and a cloud computing application system. The method comprises the following steps: initializing the system, generating a main private key and open parameters by using an attribute mechanism, allocating an attribute private key to each user, and embedding the user identity in the attribute private key; formulating a signature strategy by a data owner, generating a label for a data block, and uploading the label to a cloud server; modifying the data by a user satisfying the signature strategy; verifying the label of the modified data by the cloud server; sending challenge to the cloud server by a verifier; calculating auditing evidence by the cloud server, and returning the auditing evidence to the verifier; verifying the correctness of the evidence by the verifier; and tracing the malicious user. According to the traceable effective open auditing method disclosed by the invention, the privacy of the user identity is protected in a multi-user data sharing environment, the traceability of the malicious user is realized at the same time, and the storage overhead for tracing is a constant.
Owner:ANHUI UNIVERSITY
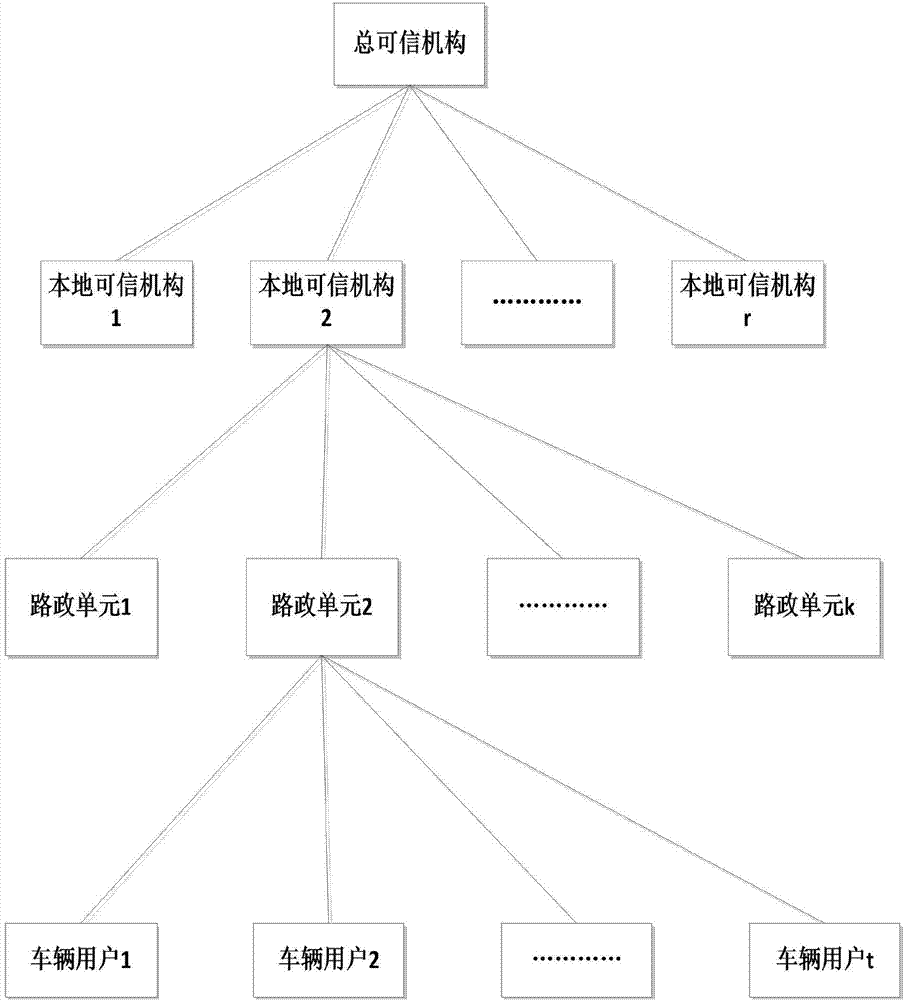
Group signature method with efficient revocation in vehicle networking
ActiveCN104753683AImprove real-time update efficiencyEfficient undoUser identity/authority verificationIn vehicleBroadcasting
The invention discloses a group signature method with efficient revocation in vehicle networking with an aim to mainly solve the problem that revocation of group members affects key pairs of group members without revocation in the prior art. According to the technical scheme, the group signature method includes: 1, initiating a system and generating parameters and public key pairs of a general trusted mechanism, a local trusted mechanism and a road administration unit; 2, vehicle users registering in the local trusted mechanism before access to the networking and receiving blind certificates; 3, the road administration unit establishing groups, the vehicle users in the jurisdictional scope submitting the blind certificates and joining in the groups after identity legitimacy is verified; 4, after the group members join in the groups, subjecting messages to signing and broadcasting, and anybody verifying the messages; 5, when new users join in the groups or in case of revocation of the members, the road administration unit calculating and publishing new public keys. With the method, efficient and safe joint and revocation in the road administration in the vehicle networking and anonymity of the users to the road administration can be realized, and track on user mobile trajectories is avoided.
Owner:XIDIAN UNIV
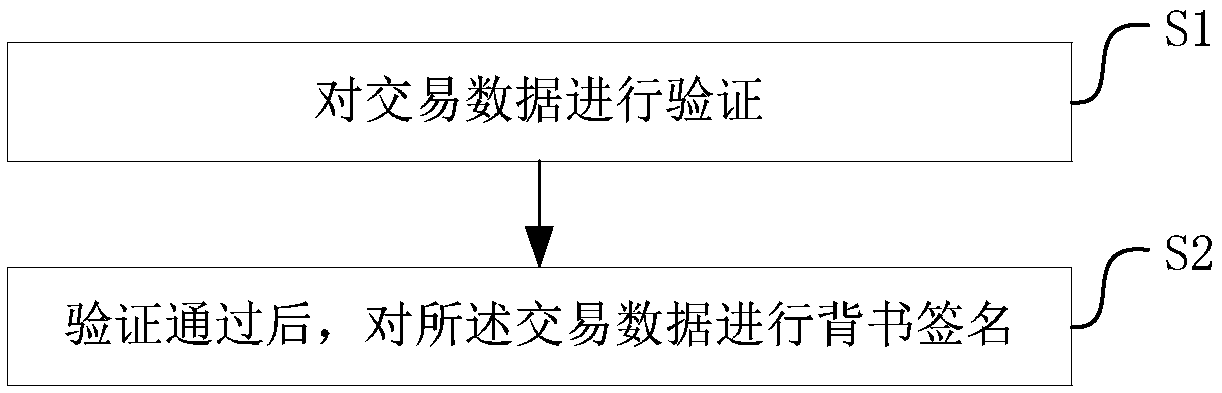
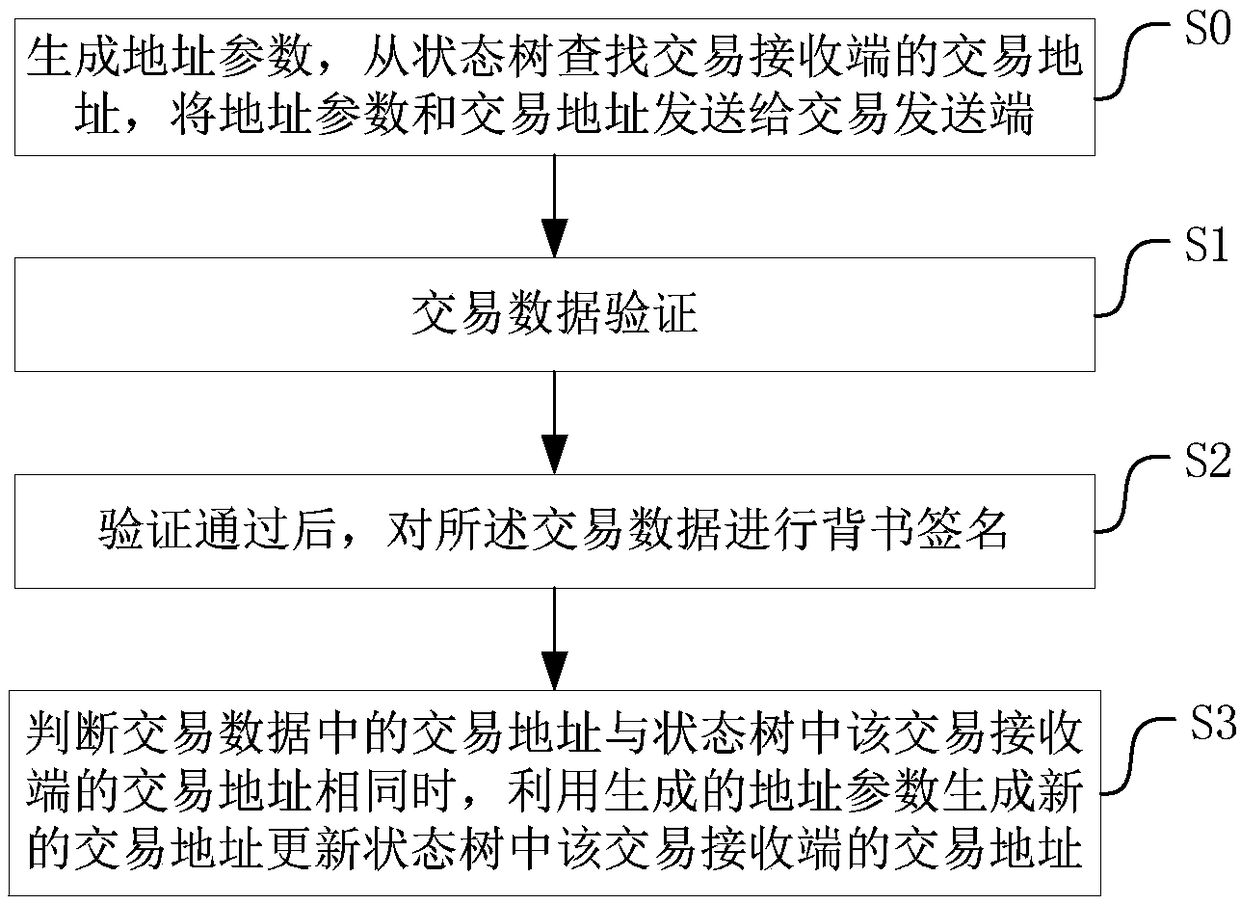
Block chain data processing method and device as well as computer readable storage medium
ActiveCN108647964AProtect identity privacyQuick searchPayment protocolsEnergy efficient computingChain structureTransaction data
The invention discloses a block chain data processing method and device as well as a computer readable storage medium, capable of quickly retrieving all the transaction data of the same client and protecting privacy of a user at the same time. The block chain data processing method comprises the following steps: after the transaction data passes verification, carrying out endorsement signature onthe transaction data, wherein the transaction data comprises a transaction address of a transaction receiving terminal and an address parameter generated during the current transaction, the transaction address is generated by utilizing an address parameter generated by the transaction receiving terminal during previous transaction, and the address parameter generated during the current transactionis used for generating a transaction address for the next receiving transaction of the transaction receiving terminal; and after cochain of the transaction data, forming one chain structure by all the received transaction data of the same transaction receiving terminal. By adopting the method of the embodiment of the invention, all the transaction data of the same client can be quickly retrieved,and identity and privacy of the user are also protected.
Owner:郑杰骞
Security distributed aggregation and access system and method based on fog alliance chain
ActiveCN111372243AReduce transmission overheadResist curiosityPublic key for secure communicationSecurity arrangementData integrityConfidentiality
The invention discloses a security distributed aggregation and access system and method based on a fog alliance chain, and aims to solve the problem that most of current data aggregation schemes are designed based on a centralized mode, face single-point faults and tampering threats, and have security and performance improvement space. In order to solve the challenge, a distributed aggregation framework is designed in combination with fog computing and an alliance chain, single-point faults and tampering crisis are solved, and powerful support is provided for safe collection, communication andstorage of data. Meanwhile, a Paillier homomorphic algorithm of a threshold version is fused, a safe access control mechanism with a fault-tolerant function is designed, and confidentiality and privacy of data on a chain are guaranteed. Meanwhile, an efficient anonymous authentication method is provided, and identity privacy and data integrity can be guaranteed. Finally, the comparative analysisresult of the method and the existing method shows that the method can resist malicious attacks and ensure the system security, and compared with other existing methods, the method has lower calculation and communication costs.
Owner:NANJING UNIV OF POSTS & TELECOMM
Identity-based privacy protection integrity detection method and system in cloud storage
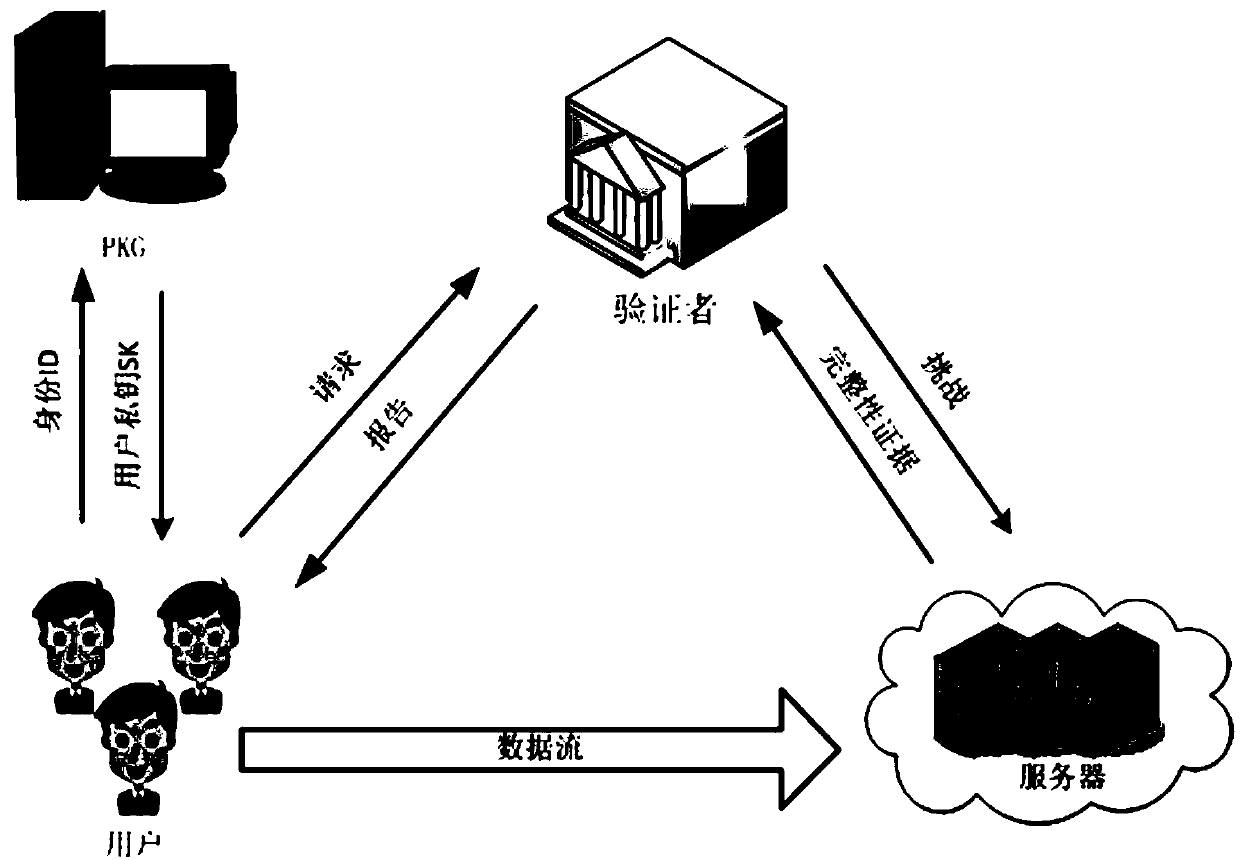
ActiveCN107948143AReduce overheadReduce public key certificate management workUser identity/authority verificationThird partyData integrity
The invention discloses an identity-based privacy protection integrity detection method and system in a cloud storage. The method comprises the following steps of (1) a system initialization stage that a trusted third-party PKG generates a main private key and a public parameter; (2) a secret key extraction stage that the trusted third-party PKG generates a private key for a user according to useridentity; (3) a label generation stage that the user generates a data label for each data block by using the private key and uploads data and the corresponding data label to a cloud server; (4) a challenge inquiry stage that a verifier sends a challenge to the cloud server; (5) an evidence generation stage that the cloud server computes an integrity evidence according to challenge information andreturns the integrity evidence to the verifier; and (6) a verification stage that the verifier verifies the data integrity according to the evidence. According to the method and the system, the public key certificate management and calculation cost of the system is reduced based on an identity signature, and meanwhile, the identity privacy and the data privacy of the user are protected in a process of verifying the data integrity, and the safety of the system is improved.
Owner:ANHUI UNIVERSITY
A block chain privacy protection scheme and system based on SM9 algorithm
InactiveCN109409884ASolve problems that are difficult to apply to real-world scenariosSolve application problemsDigital data protectionProtocol authorisationChain structurePrivacy protection
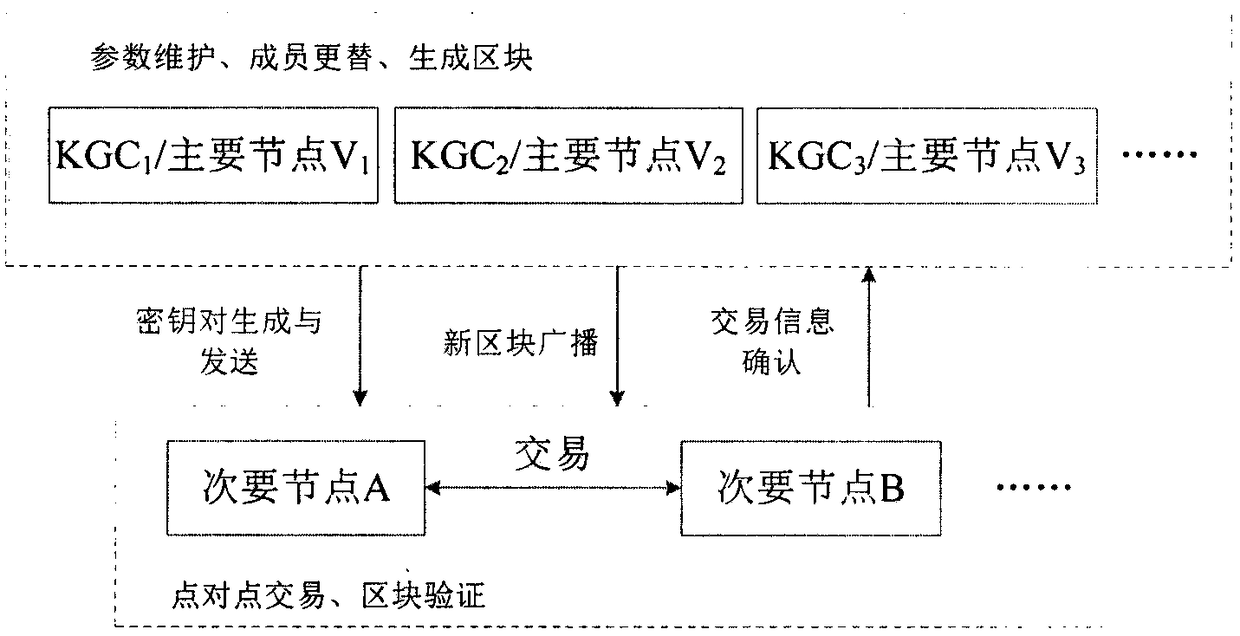
The invention discloses a block chain privacy protection scheme and a block chain privacy protection system based on an SM9 commercial cryptographic algorithm in China, belonging to the field of blockchain security and privacy protection. This invention provides an inter-node transaction platform based on federation chain, defines the permissions and functions of various nodes in the platform, and supports node transaction, information verification, parameter maintenance, block generation and other functions. This invention describes an improved SM9 multi-KGC (Key Generation Center) signaturealgorithm, which improves the working mode of single KGC in SM9 algorithm, adapts to the federation chain structure, and adopts this algorithm to determine the identity of the opposite party in the transaction between nodes. A group signature scheme based on SM9 algorithm is proposed. The identity verification of SM9 algorithm is improved to group signature verification, which effectively protects the identity privacy of the signatory. The transaction information is signed by the node through the algorithm and written into the block chain after the transaction, which can effectively hide theidentity information of both parties of the transaction, protecting the privacy of the node and ensuring the legitimacy of the transaction.
Owner:BEIJING ANRUSHAN CULTURE TECH
Block chain-based food safety multi-interest subject credit evaluation method
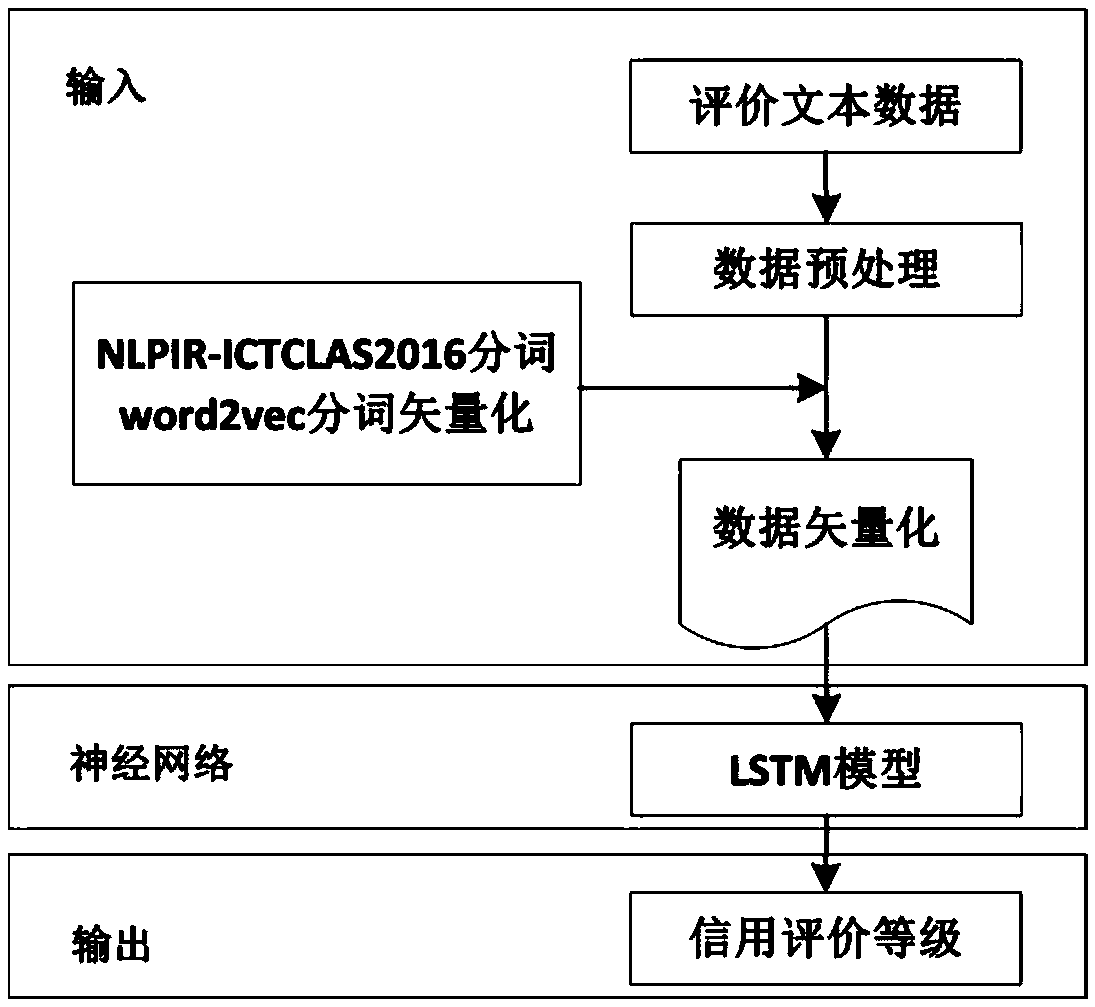
InactiveCN108717606AEasy to supervise and manageReduce regulatory costsResourcesCommerceFood supplySmart contract
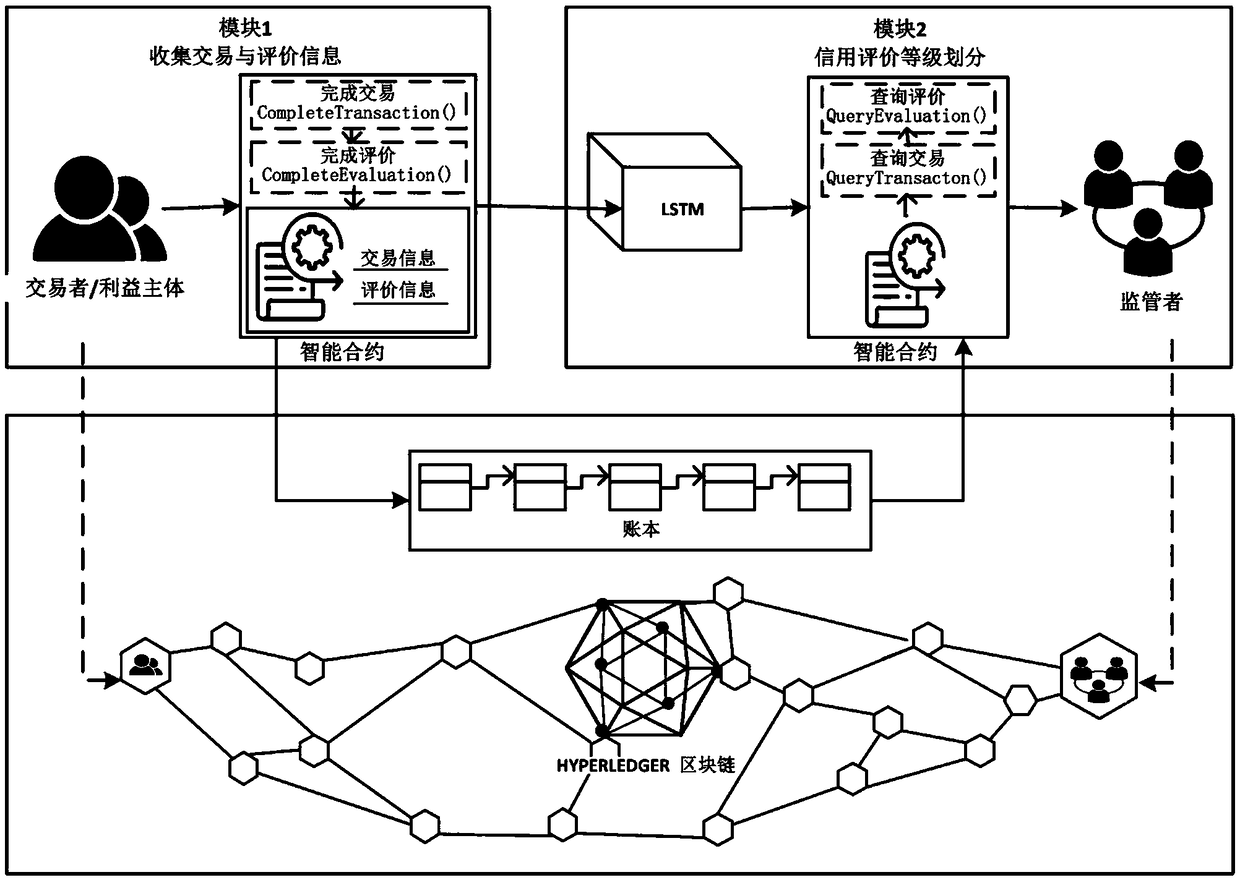
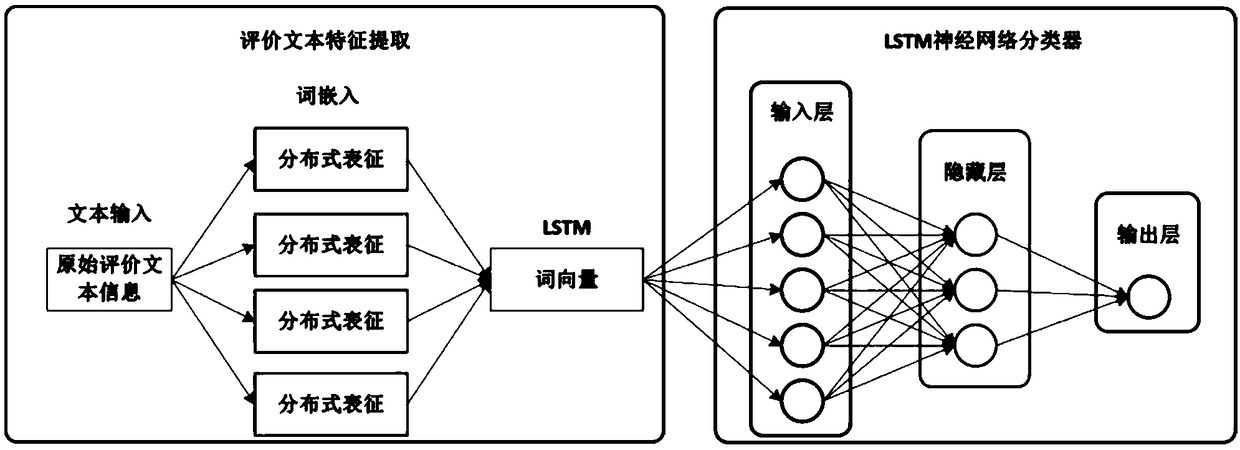
The invention provides a block chain-based good safety multi-interest subject credit evaluation method. According to the method, a Hyperledger block chain is taken as a bottom support technology of the credit evaluation method, multi-interest subjects (traders) on food supply chains and supervisors are endowed with different identity authorities, and the traders are endowed with identity anonymityand evaluation result publicity and transparency during the evaluation; and the supervisors collect evaluation information, for transactions, of the multi-interest subjects on the food supply chainsthrough intelligent contracts, carry emotion analysis on the fed back evaluation information by adoption of a deep learning algorithm long and short term memory (LSTM) model, and feed credit evaluation results back to both parties of the transactions. According to the method, the efficiency and correctness of traditional credit evaluation systems are improved and the effectiveness of food safety supervision is enhanced.
Owner:BEIJING TECHNOLOGY AND BUSINESS UNIVERSITY
Supervisable anonymous authentication method based on zero knowledge proof
ActiveCN109450645AGuaranteed anonymityProtect identity privacyKey distribution for secure communicationUser identity/authority verificationAnonymous authenticationIdentity privacy
The invention discloses a supervisable anonymous authentication method based on zero knowledge proof, comprising three types of participants: a CA, a user and a verifier, wherein the CA generates an issuer key pair and a group key, the CA allocates a pair of private keys to the user during registration of the user, and meanwhile the CA issues a relevant certificate to the user according to the attribute information submitted by the user; when the user presents the certificate, the verifier specifies an attribute that needs to be presented on the certificate of the user, and the user signs thecertificate and hides attribute values that do not need to be presented; and the verifier verifies the signature, if the signature passes the verification, the certificate presented by the user is valid, or otherwise, the certificate presented by the user is invalid. By adoption of the supervisable anonymous authentication method disclosed by the invention, the anonymity of the user is also ensured while increasing a mandatory supervision function, thereby greatly improving the identity privacy of the user compared with the general identity supervision scheme. By adoption of the supervisable anonymous authentication method disclosed by the invention, a supervisable function is also added.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP
Multi-recipient anonymous encryption apparatus under hybrid mechanism
InactiveCN105763528AImprove sexual functionEasy to set upKey distribution for secure communicationKey generationKey generation center
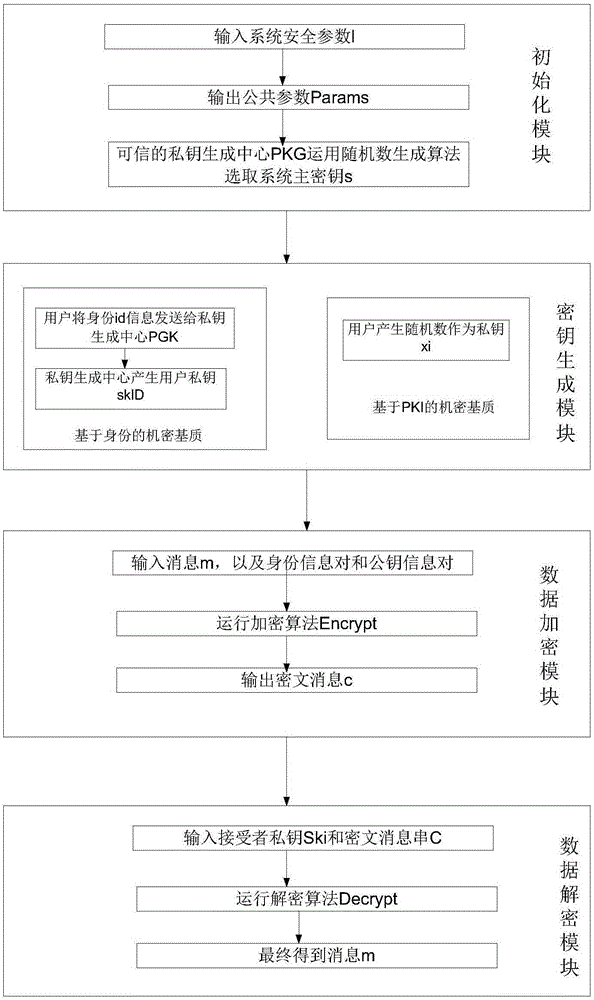
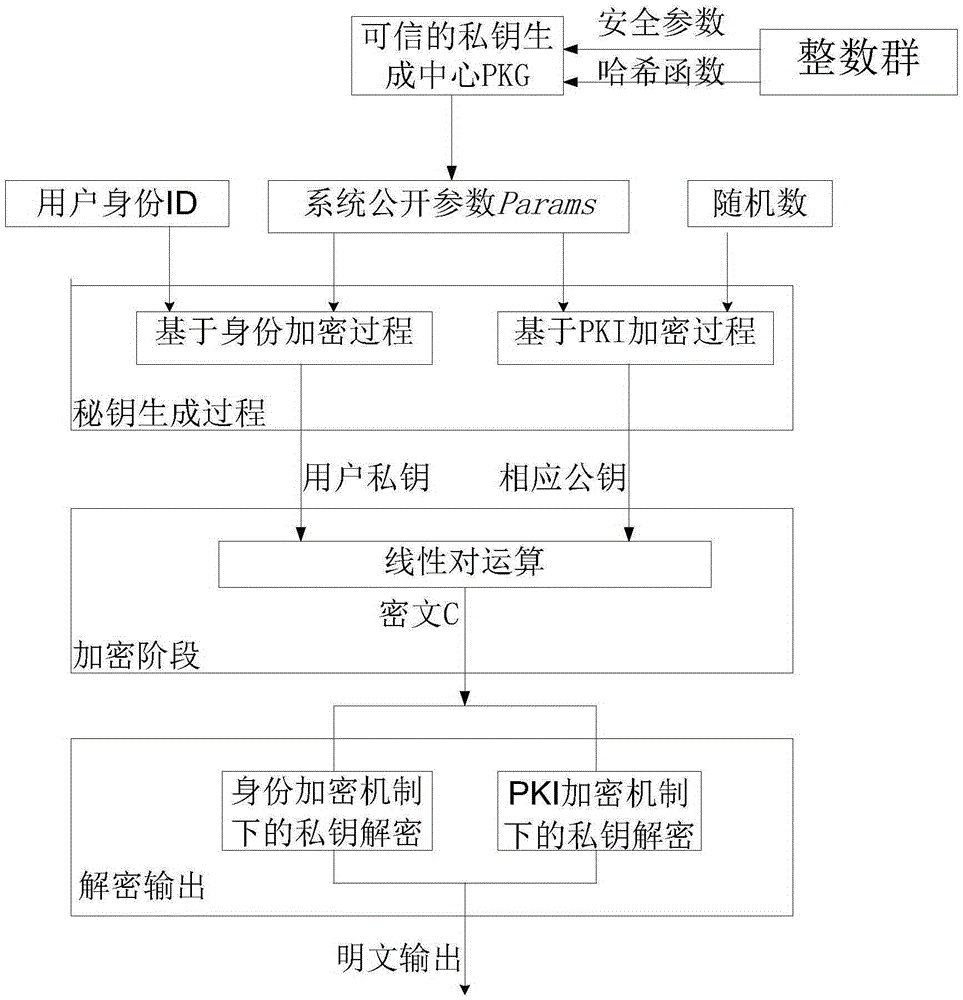
The invention relates to a multi-recipient anonymous encryption apparatus under a hybrid mechanism. The apparatus comprises a trusted private key generation center PKG, an identity set on the basis that the membership scale is 1 under an identity cipher system, and a public key certificate set on the basis that the membership scale is n-1 under a PKI cipher system. The apparatus is realized by the following steps: 1, the trusted private key generation center PKG selecting security parameters from an integer group and proper Hash function algorithms, running a bilinear pairing operation, and generating system public parameters Params; 2, the PKG carrying out a secret key generation process: (1), based on an identity encryption process, the PKG generates user private keys by use of the public parameters Params and identity IDs of a system, and (2), based on a PKI encryption process, selecting proper random numbers as private keys by use of a random number generation algorithm, and calculating corresponding public keys; 3, in an encryption phase, carrying out corresponding linear pairing operation to generate complete cipher; and 4, performing decryption respectively under two systems by use of respective private keys, and finally outputting plaintexts.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
Blockchain certificate processing method and system
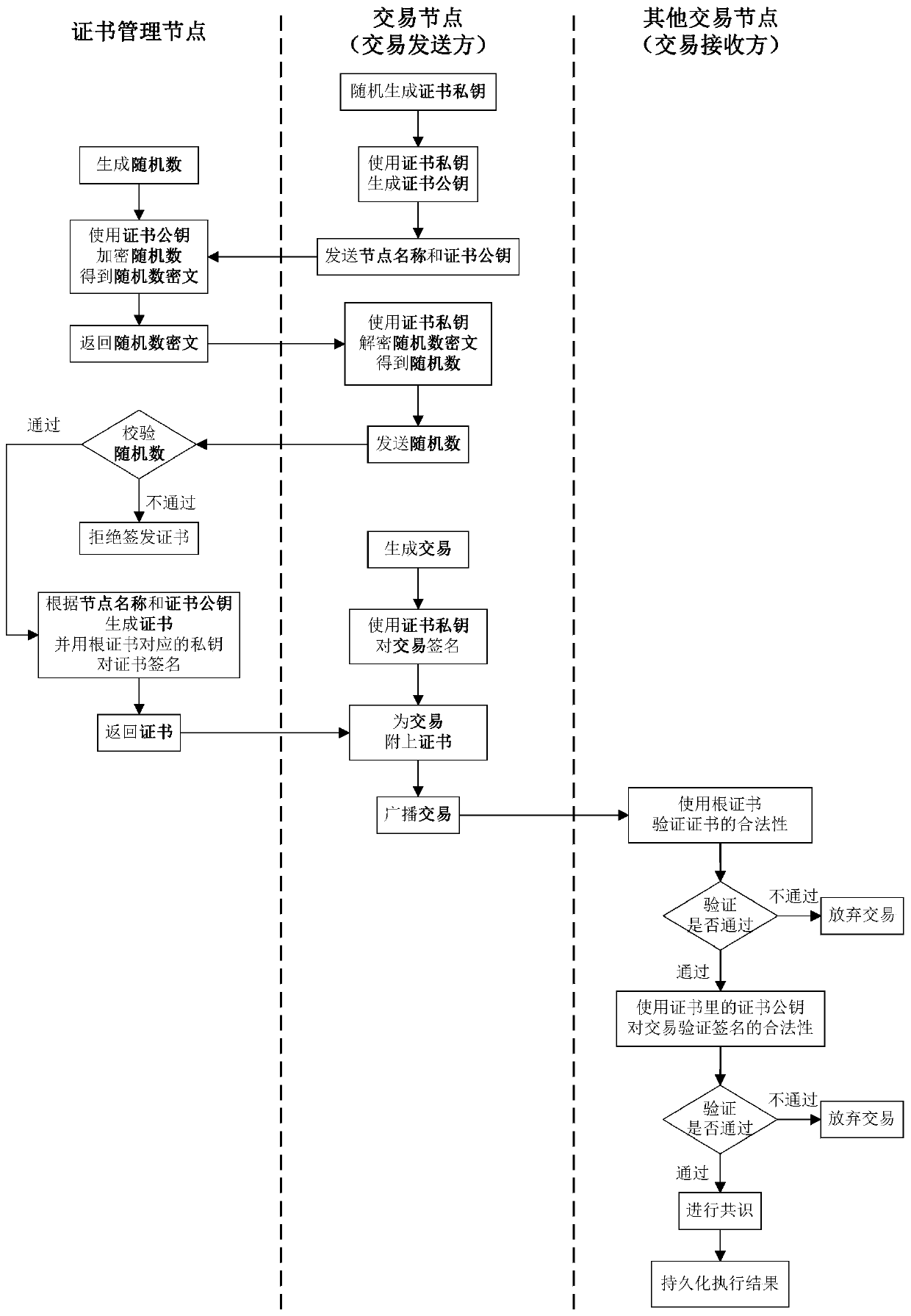
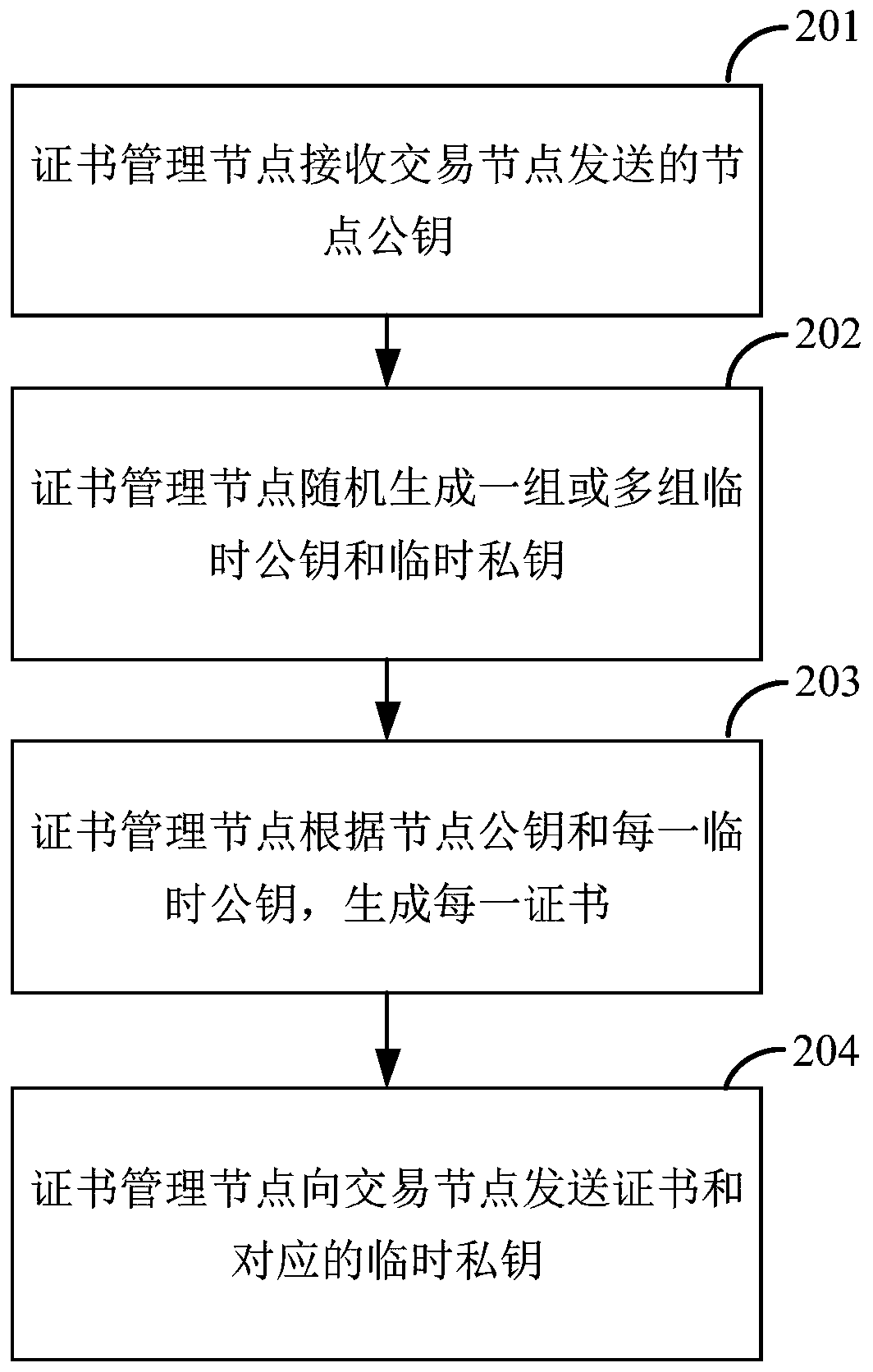
ActiveCN109767218AImprove processing efficiencyProtect user identity privacyPayment protocolsBlockchainThird party
The invention discloses a blockchain certificate processing method and system. The method comprises the steps that a certificate management node receives a node public key sent by a transaction node;The certificate management node randomly generates one or more groups of temporary public keys and temporary private keys; The certificate management node generates each certificate according to the node public key and each temporary public key; And the certificate management node sends the certificate and the corresponding temporary private key to the transaction node. According to the invention,one or more groups of temporary public keys and temporary private keys can be generated; According to the technical scheme, the method comprises the steps that a transaction node receives a node public key and generates a plurality of certificates according to the node public key and each temporary public key, when a plurality of transactions are generated, the transaction node attaches differentcertificates to each transaction, the user identity privacy is protected while the high processing efficiency is ensured, the association relationship between the transactions is prevented from beingmastered by a third party, and thus the security of the block chain is achieved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
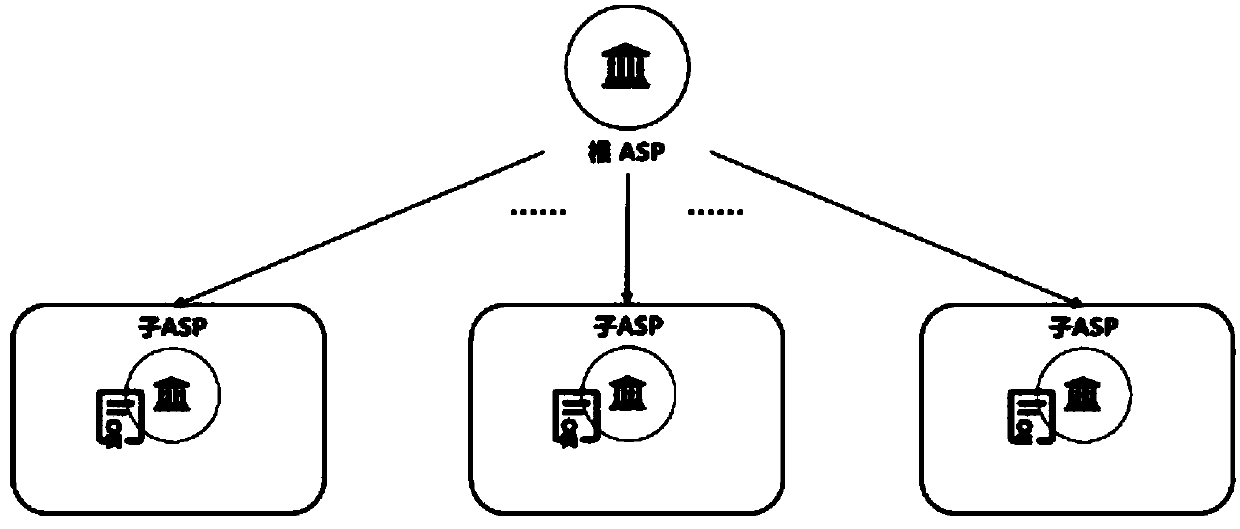
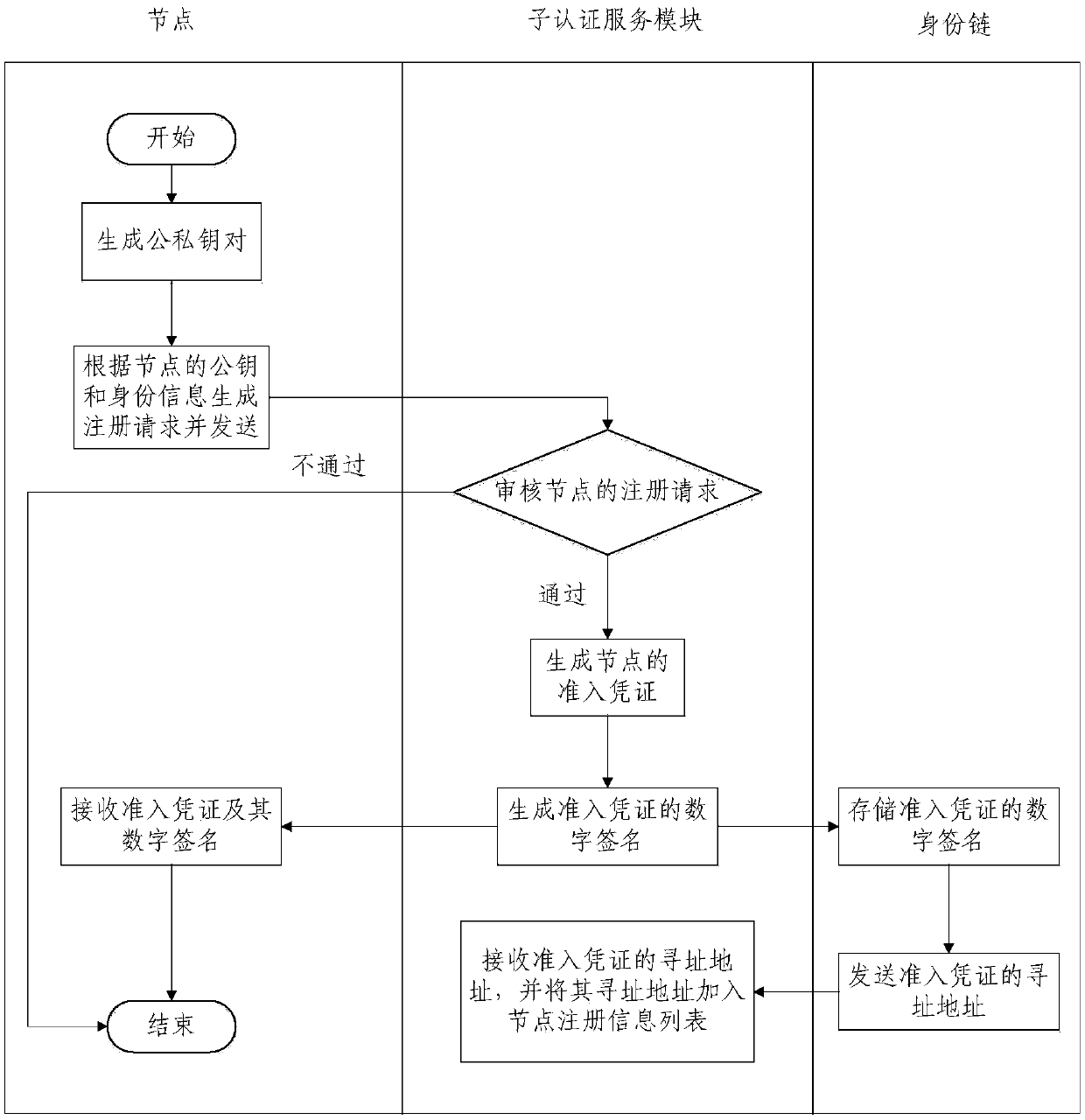
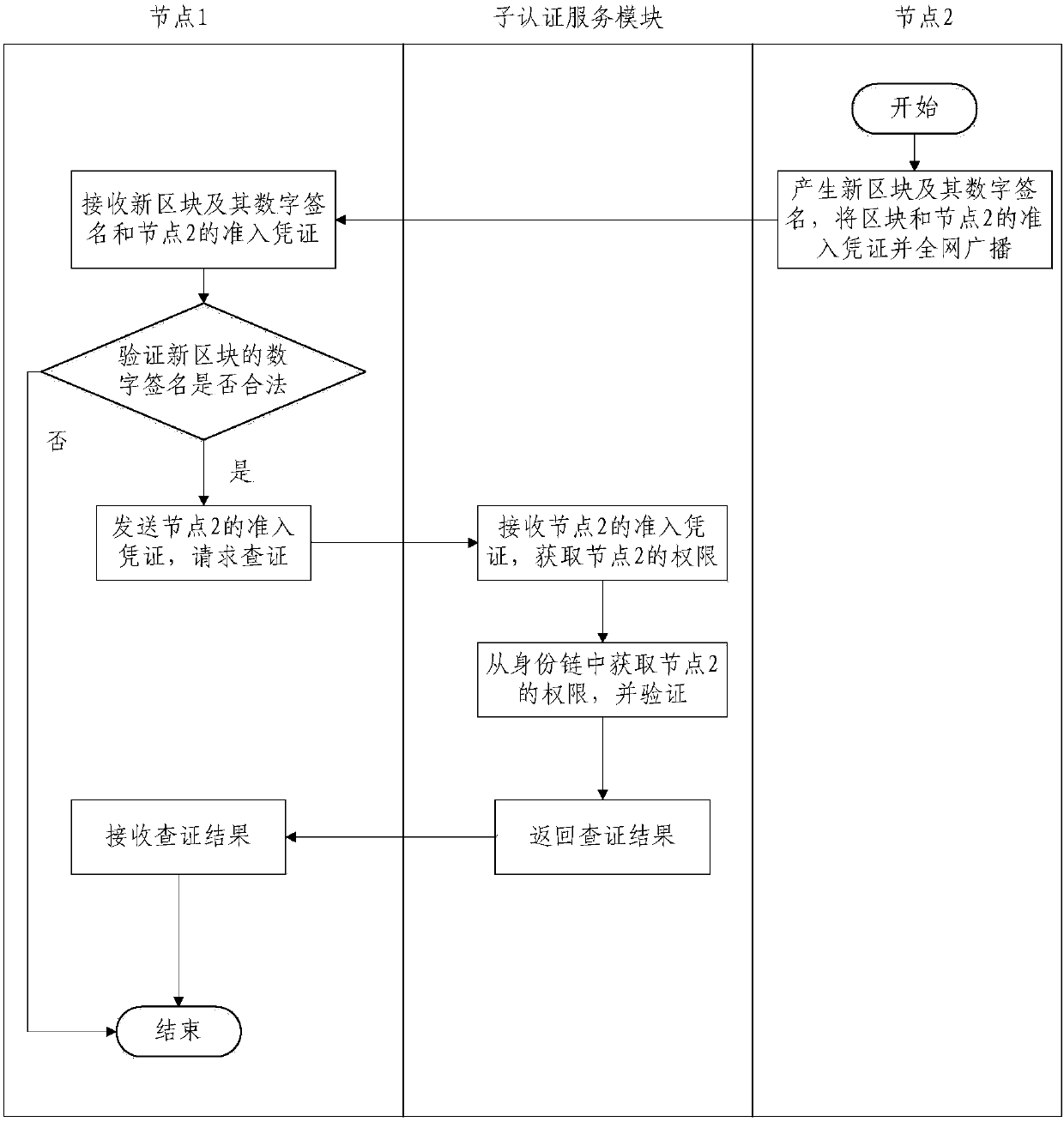
Block chain authentication service device and node admission and user authentication method
ActiveCN109962890AProtect identity privacyPrivacy protectionUser identity/authority verificationDigital identityDigital signature
The invention provides an authentication service device of a block chain, a node admission method and a user authentication method. The device comprises a root authentication service module and a plurality of sub authentication service modules, and all the sub-authentication service modules are used for jointly maintaining a second block chain used for storing the node of the first block chain andthe registration information of the user. The node admission method comprises the following steps: generating an admission voucher of a node and a digital signature thereof, and writing the digital signature of the admission voucher into a second block chain; and verifying the identity and the authority of the node according to the second block chain. The user authentication method comprises thesteps of generating a digital identity card of a user and a digital signature thereof, and writing the digital signature of the digital identity card into a second block chain; and the identity of thefirst user is verified, and when the identity of the first user passes the verification, the first user is allowed to verify the identity of the second user according to the second block chain. According to the authentication service device, the node admission method and the user authentication method provided by the invention, the privacy of the user can be effectively protected.
Owner:INST OF INFORMATION ENG CAS
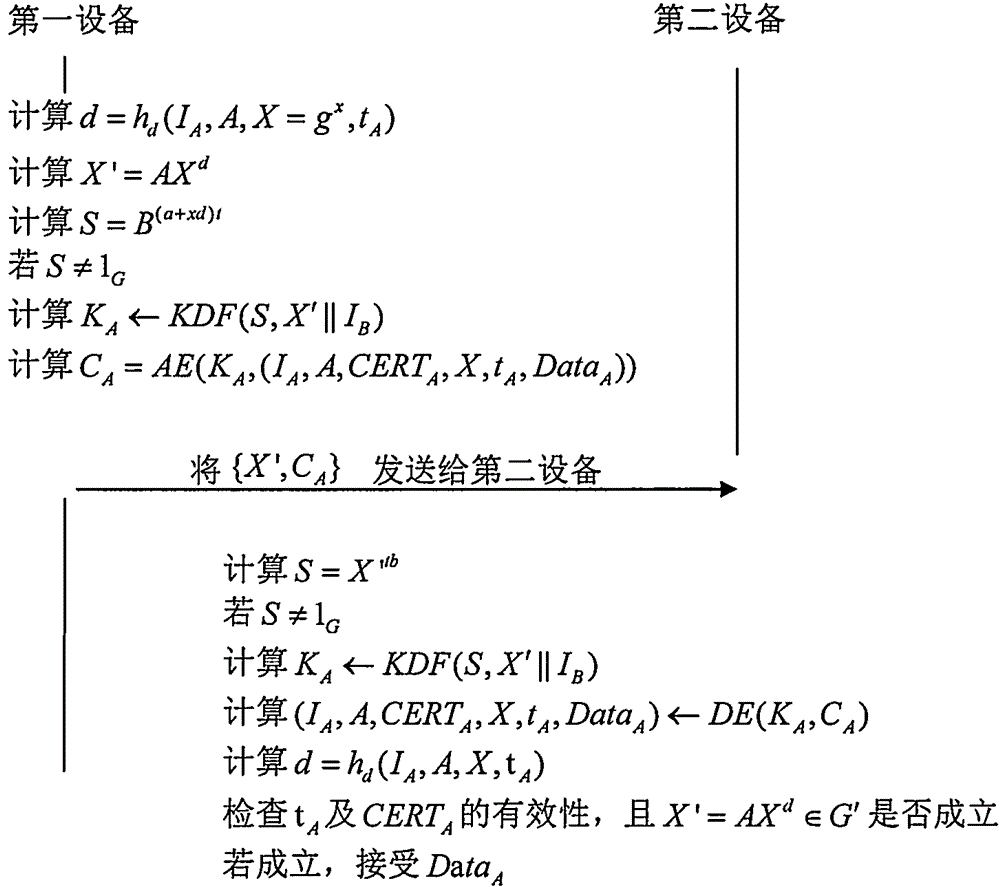
Signcryption method with hidden identity and strong security
ActiveCN105306212AProtect identity privacyDoes not compromise securityPublic key for secure communicationUser identity/authority verificationSigncryptionModular exponentiation
The invention provides a signcryption method with hidden identity and strong security. The signcryption method comprises the steps that: a first device calculates X' = AXd, wherein X = gx and d = hd (X, auxd), determines a preset shared key S according to a DH-index x, a private key a and a public key B = gb of a second device, determines KA based on S, determines CA = (IA, A, CERTA, X, DataA)) according to KA, and sends [X CA]' to the second device; the second device determines the preset shared key S according to the received X' and the private key b of the second device, determines KA based on S, and decrypts CA according to KA to obtain (IA, A, CERTA, X, DataA); and if a public key certificate CERTA is valid and X' = AX d is effective, DataA is accepted. In the signcryption method provided by the invention, the identity and the public key information of the first device are hidden, the first device only needs to operate 2.5 modular exponentiations, and the second device only needs to operate 1.5 modular exponentiations. In addition, the bandwidth consumed by the method provided by the invention is less than an existing signcryption scheme, and the leakage of a temporary DH-index x does not affect the security of the scheme of the invention.
Owner:赵运磊
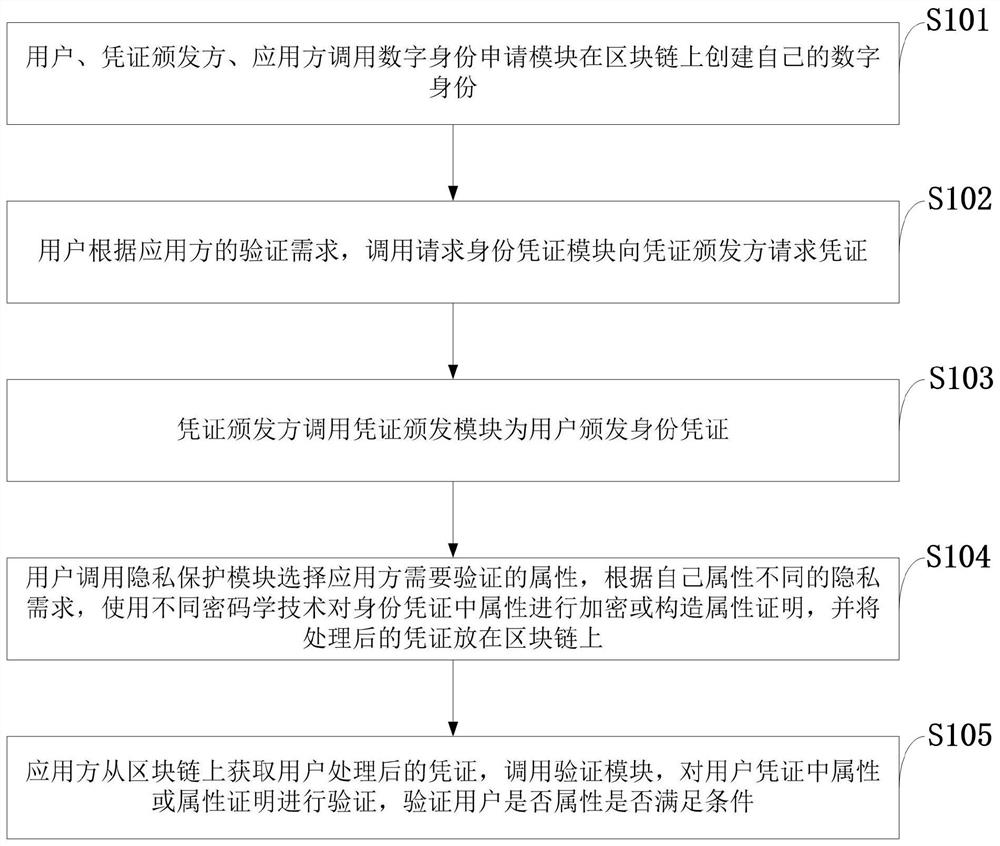
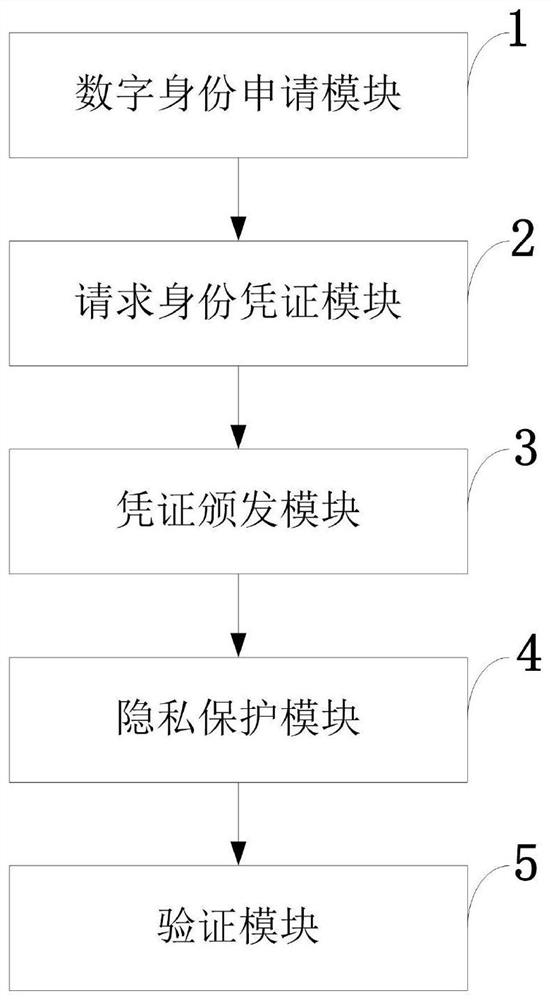
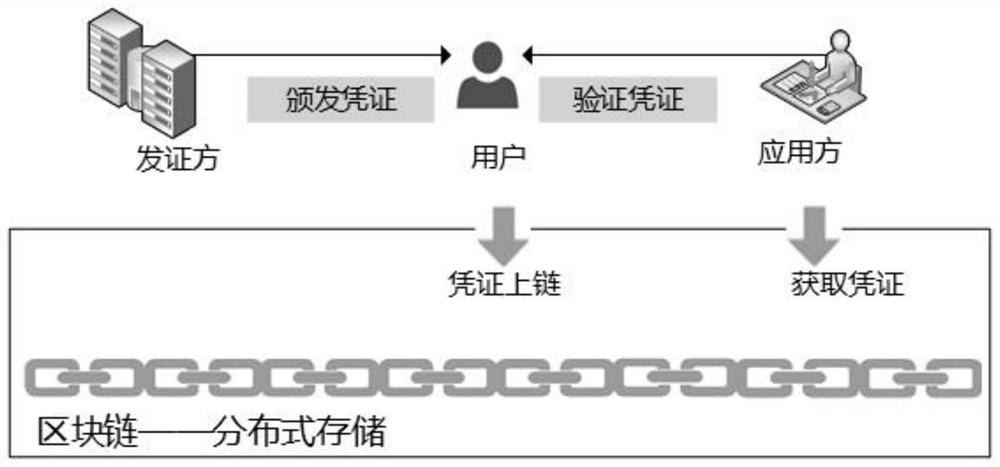
Trusted distributed identity authentication method and system, storage medium and application
ActiveCN113098838AProtect identity privacyImprove practicalityUser identity/authority verificationDigital identityPrivacy protection
The invention belongs to the technical field of information security authentication, and discloses a trusted distributed identity authentication method and system, a storage medium and application, and the method comprises the steps that: a digital identity application module is called to create a digital identity on a block chain; a request identity credential module is called to request a credential issuing party for a credential; the voucher issuing party calls a voucher issuing module to issue an identity voucher to the user; a user calls a privacy protection module to select attributes needing to be verified by an application party, encrypts the attributes in the identity credentials or constructs attribute certification by using different cryptographic technologies according to privacy requirements of different attributes of the user, and puts the processed credentials on a block chain; and the application side obtains the voucher processed by the user from the block chain, calls a verification module, verifies the attribute or attribute proof in the user voucher, and verifies whether the attribute of the user meets a condition or not. And while the identity privacy of the user is protected, the practicability of the digital identity authentication is improved, and the application range of the digital identity authentication is expanded.
Owner:XIDIAN UNIV +1
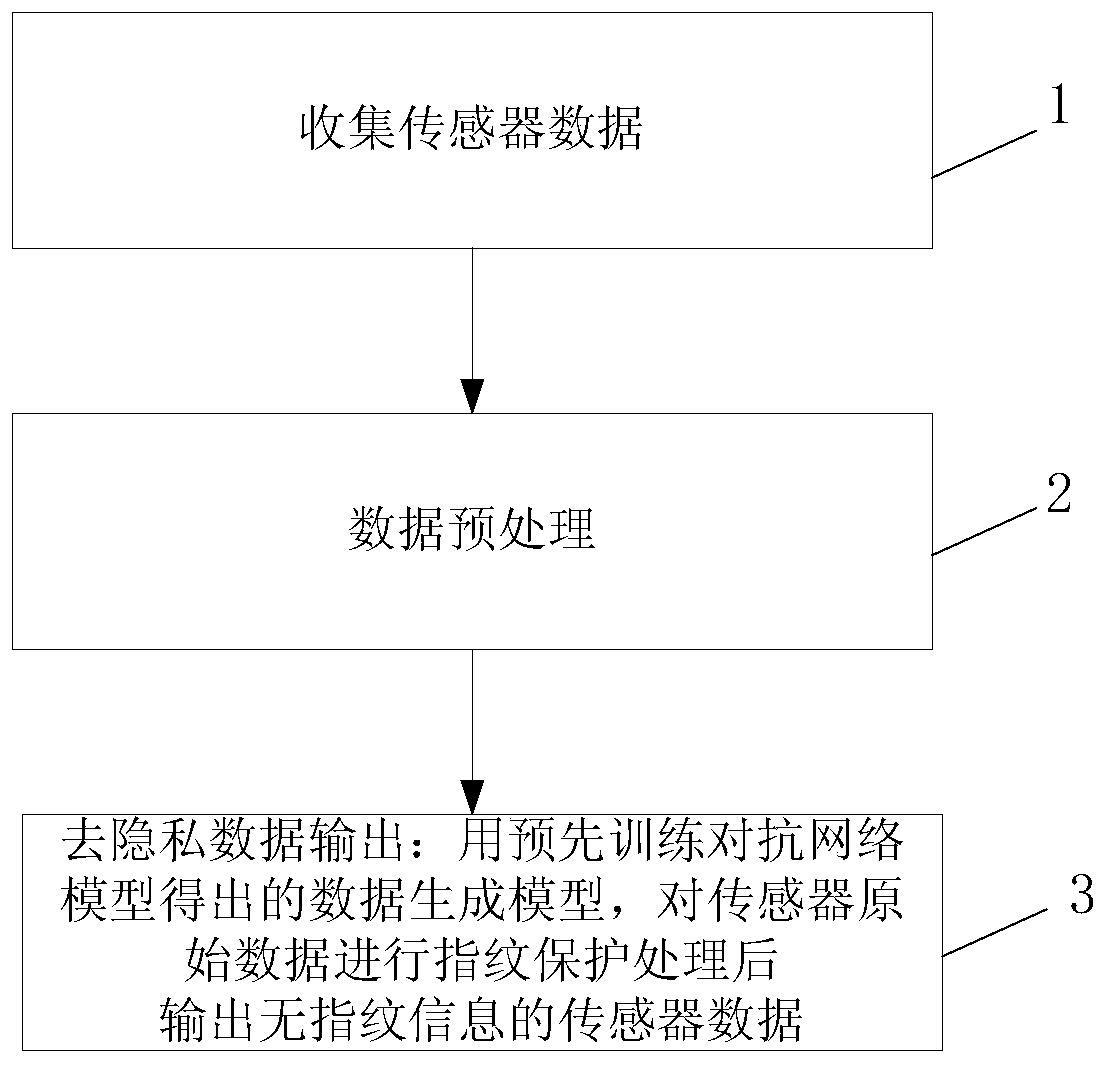
Mobile intelligent device sensor fingerprint protection method
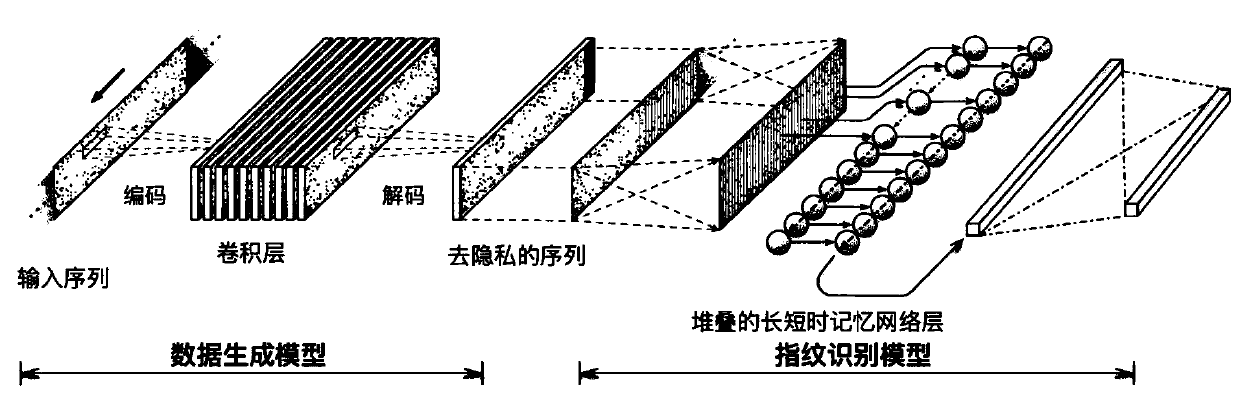
ActiveCN109766683AAchieve protectionProtect identity privacyCharacter and pattern recognitionDigital data authenticationNetwork modelReal-time computing
The invention discloses a mobile intelligent equipment sensor fingerprint protection method. The method comprises the following steps: step 1, collecting sensor data: obtaining original data of a motion sensor of mobile intelligent equipment; Step 2, data preprocessing: processing the acquired original data of the motion sensor to enable the data lengths of the data to be consistent and uniformlydistributed on a time axis; Step 3, fingerprint protection data confrontation training based on the neural network: performing fingerprint protection confrontation training on the fingerprint recognition neural network model through the training data; And step 4, data output: preprocessing the sensor original data acquired in real time according to the step 2, performing fingerprint protection processing on the preprocessed sensor original data through the trained fingerprint recognition neural network model, and outputting sensor data without fingerprint information according to an output scene after processing. The method can successfully protect the fingerprint information of different equipment sensors, can control the utility loss, and does not influence the use of related sensors.
Owner:UNIV OF SCI & TECH OF CHINA
Anonymous authentication method and system for trust in decentralized mobile crowdsourcing
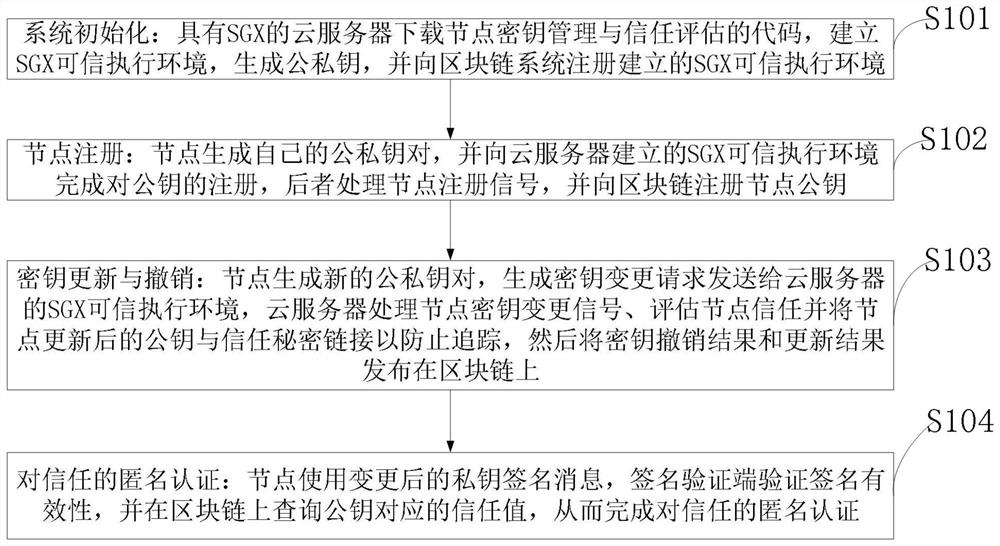
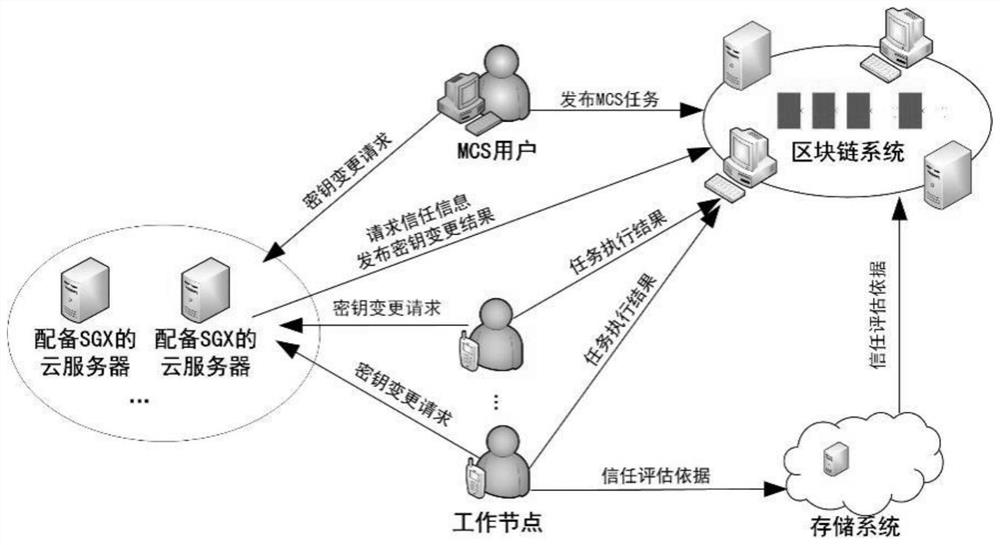
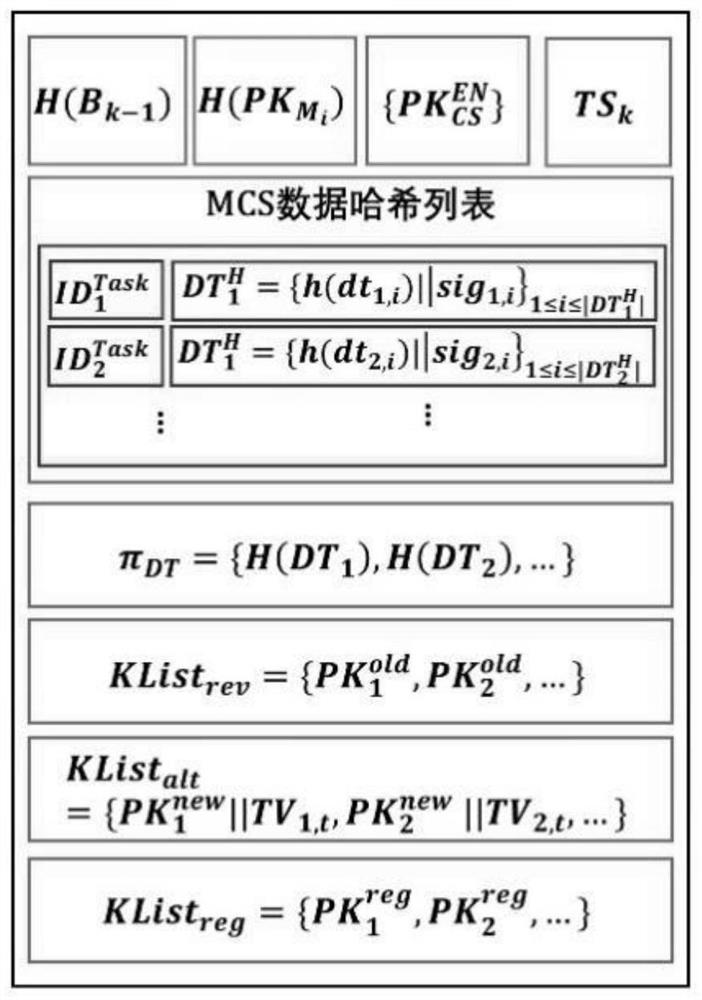
ActiveCN112187712AProtect identity privacySupport mutual verification and trustUser identity/authority verificationDigital data protectionInternet privacyEngineering
The invention belongs to the technical field of data processing, and discloses an anonymous authentication method and system for trust in decentralized mobile crowdsourcing. The method comprises the steps: generating a new public and private key pair at a node registered in a blockchain system, generating a key change request, transmitting the key change request to a trusted execution environmentof a cloud server, enabling the cloud server to process a node key change signal, secretly linking a trust evaluation result, and issuing a key change result on the blockchain system; performing trustauthentication on the signature node via the signature verification node through the blockchain system by using the changed private key signature message. All public key signature mechanisms such asRSA and the like are selected according to needs, and a trust evaluation scheme based on behaviors is included and is not limited to use of a Bloom filter. A feedback-based trust evaluation scheme isincluded, and a game theory-based method, a machine learning-based scheme and a trust theory-based method can be adopted for weight calculation.
Owner:XIDIAN UNIV
Cloud sharing data integrity auditing method capable of tracking user identities
ActiveCN110048836ASupport undoReduce calculationKey distribution for secure communicationDigital data protectionData integrityInternet privacy
The invention discloses a cloud sharing data integrity auditing method capable of tracking user identity, which belongs to the field of information security and comprises the following steps of: generating a secret key, adding a user, generating an authenticator, generating a proof, verifying the proof, tracking the identity, and revoking the user. According to the invention, the authenticator corresponding to the data block is generated based on the group signature algorithm, so that a group administrator can track the source of the data block when necessary, the identity privacy of the useris ensured not to be leaked to others, and the joining and canceling of the group user can be well supported. The method is suitable for the situation that cloud shared data is disputed or a malicioususer uploads wrong data, and a data source is needed to be tracked in a group environment.
Owner:NANJING UNIV OF AERONAUTICS & ASTRONAUTICS
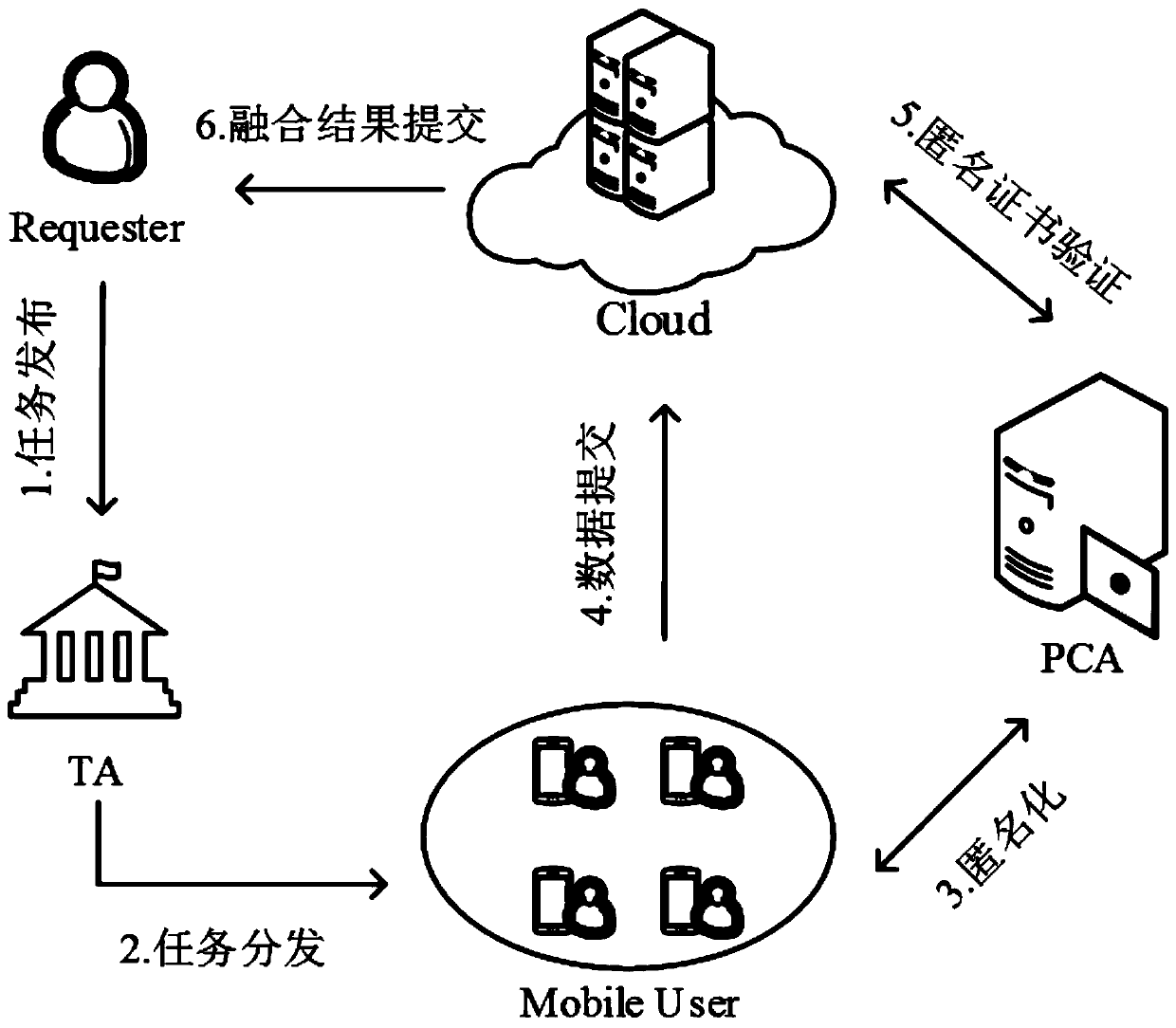
Privacy information protection method based on cloud assistance in crowd sensing
PendingCN111263357AEasy to hideProtect identity privacySecurity arrangementSensing dataInternet privacy
The invention discloses a privacy information protection method based on cloud assistance in crowd sensing. The method comprises the steps that TA registers a mobile user, a requester, a cloud and PCAin a system, and generates an RSA secret key for the requester, the cloud, the mobile user and the PCA; the requester generates an own Paillier homomorphic encryption public key and private key, andsends the task tau and the public key hpk to the TA; after receiving {tau, hpk} from the requester, the TA sends the {tau, hpk} to the participant; the user requests a plurality of pseudonyms from thePCA as anonymous certificates; after receiving the pseudonym, the user decrypts the information by using a private key ski of the user, executes the task and submits sensing data; the cloud verifiesthe anonymous certificate after receiving the message sent from the user; after the cloud verification succeeds and the interaction with the PCA is completed, statistical summation operation is carried out on all the received data; and after the requester receives the data sent by the cloud, the fusion result is decrypted by using the homomorphic encryption private key of the requester. Accordingto the method, the privacy information of the mobile user can be well protected.
Owner:XUZHOU COLLEGE OF INDAL TECH
Path sharing method and system for privacy protection
ActiveCN109309681AProtection securityGuaranteed confidentialityEncryption apparatus with shift registers/memoriesUser identity/authority verificationLocation sharingTeam communication
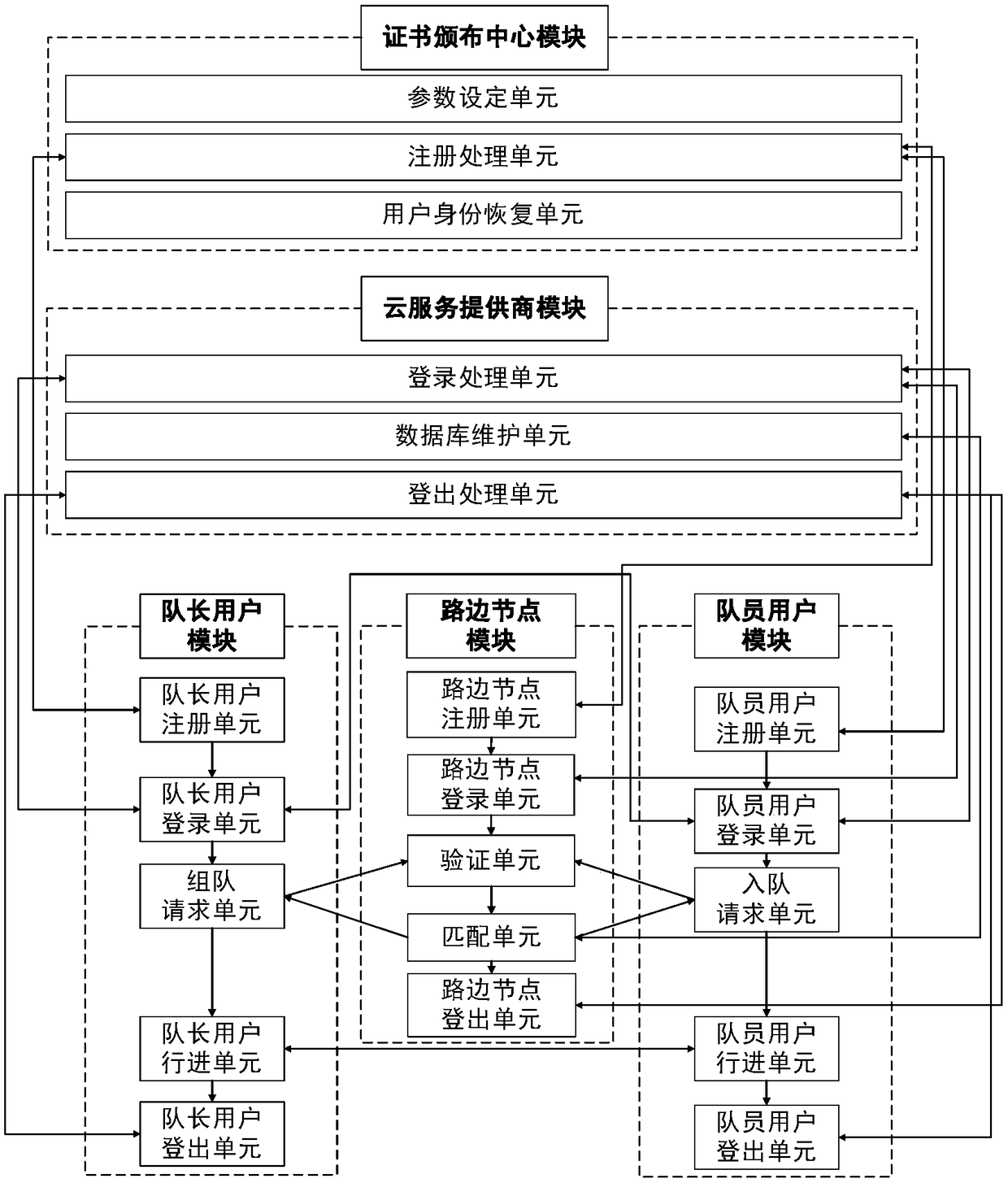
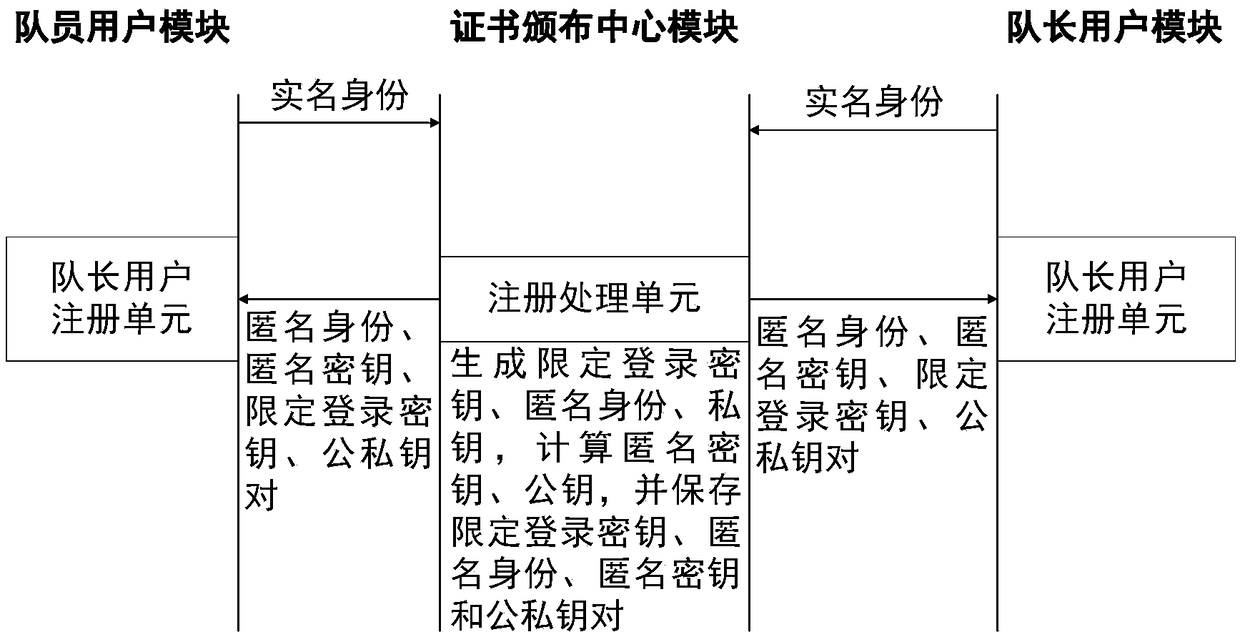
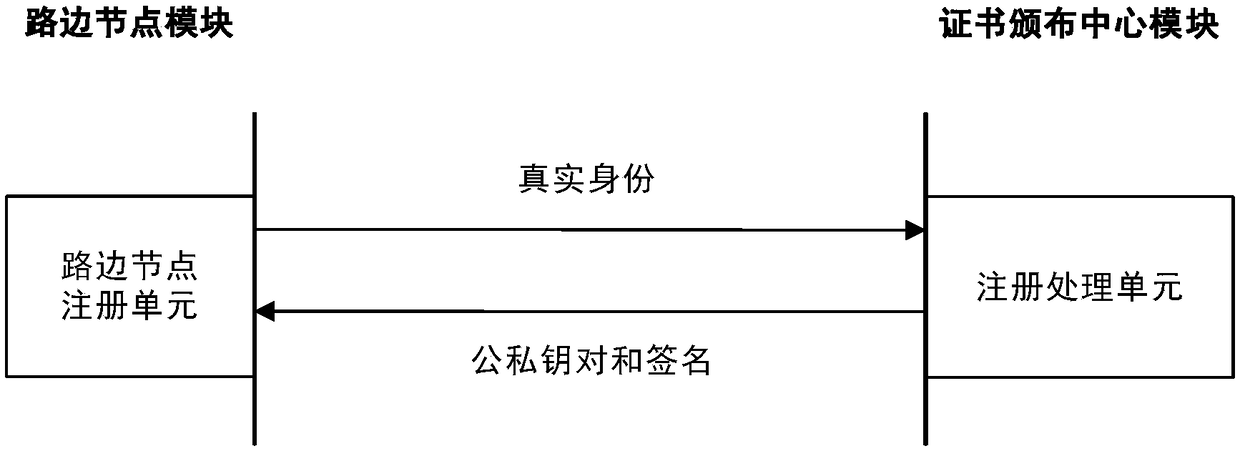
The invention discloses a path sharing method and system for privacy protection, and belongs to the technical field of anonymous authentication and privacy protection. The method comprises the following steps that a user registers with a certificate issuing center, and a queue leader user sends a team request to a roadside node and sends a team name, a team communication key and a destination to members of the team; a team member user sends a team adding request to the roadside node; and the roadside node anonymously authenticates the identity of the user, verifies the request, matches the queue leader user and the team member user, uploads team information after team formation to a cloud service provider, acquires path information, and returns the path information and team information tothe user, and the users in the team share avatars, positions and tracks in real time. The method and the system have the beneficial effects that user privacy, including identity, location and track isprotected, and team member camouflage attacks, team peek attacks and multiple group attacks of opponents are resisted. Compared with an existing location sharing method, the path sharing method has the advantage that the computing overhead and communication overhead are reduced. Compared with an existing path sharing system, the path sharing method has the advantage that security and privacy protection is provided.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
IMSI privacy protection method in 5G high-security terminal
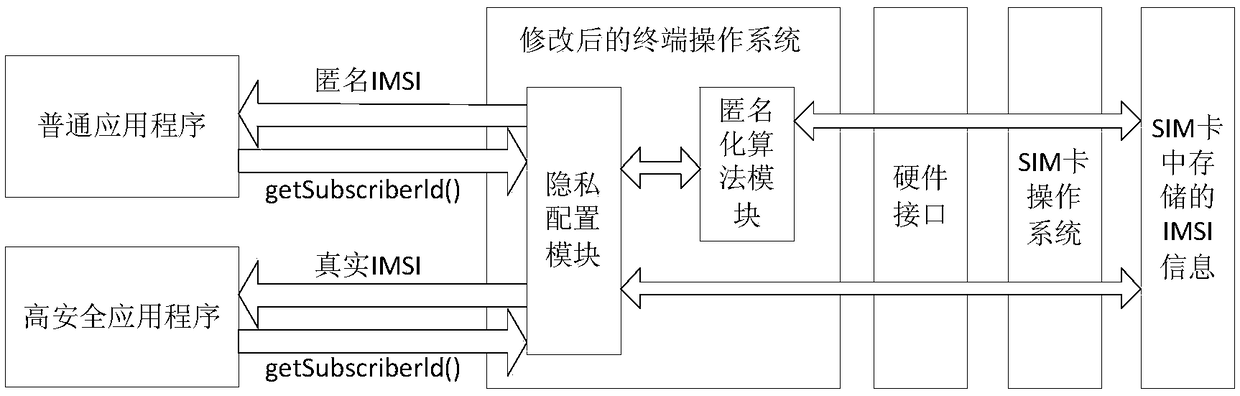
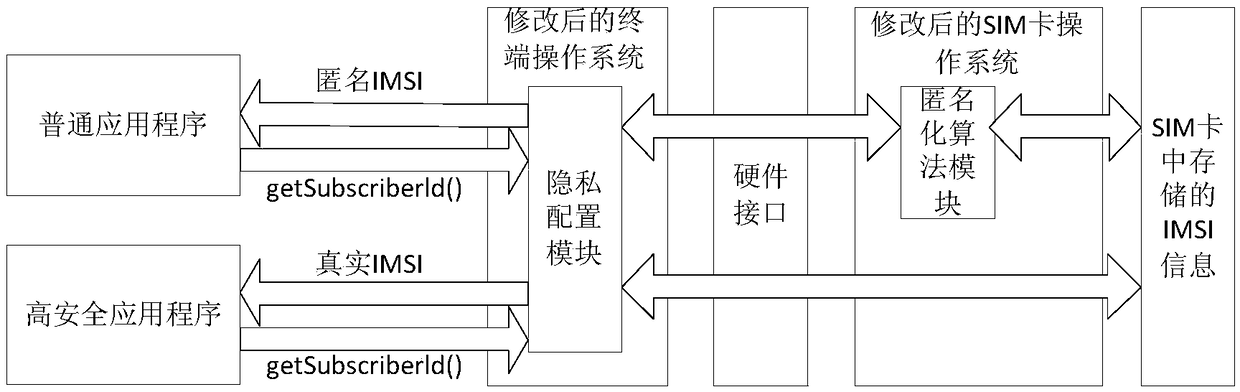
InactiveCN108632817AProtect identity privacyGuaranteed privacyTransmissionSecurity arrangementPrivacy protectionG-network
The invention discloses an IMSI privacy protection method in a 5G high-security terminal. An anonymization algorithm module and a privacy configuration module are additionally provided in the terminal, wherein the main function of the anonymization algorithm module is to perform anonymous processing on IMSI information, and the main function of the privacy configuration module is to selectively activate or close the anonymization algorithm module for application programs of different security levels. According to the IMSI privacy protection method provided by the invention, the privacy of theIMSI is ensured in the high-security terminal by using the anonymization algorithm so as to reduce the possibility of an attacker of capturing the IMSI information through the application programs ofthe terminal, so that the identity privacy of a user of the high-security terminal is protected. The application range of the method is wide, the method is not only suitable for the high-security terminals in the current 4G network, but also is suitable for the high-security terminals in the future 5G network. The requirements of identity privacy protection of users in the high-security industriescan be satisfied. The anonymization algorithm can also be extended to protect the identity information of other terminals.
Owner:NO 30 INST OF CHINA ELECTRONIC TECH GRP CORP +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com