Internet of vehicles group key management method oriented to multiple services and privacy protection
A technology of privacy protection and management method, applied in the field of wireless communication, to achieve the effect of protecting identity privacy and realizing forward security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0071] Embodiment 1, set forth the present invention in detail below by present embodiment, concrete process is:
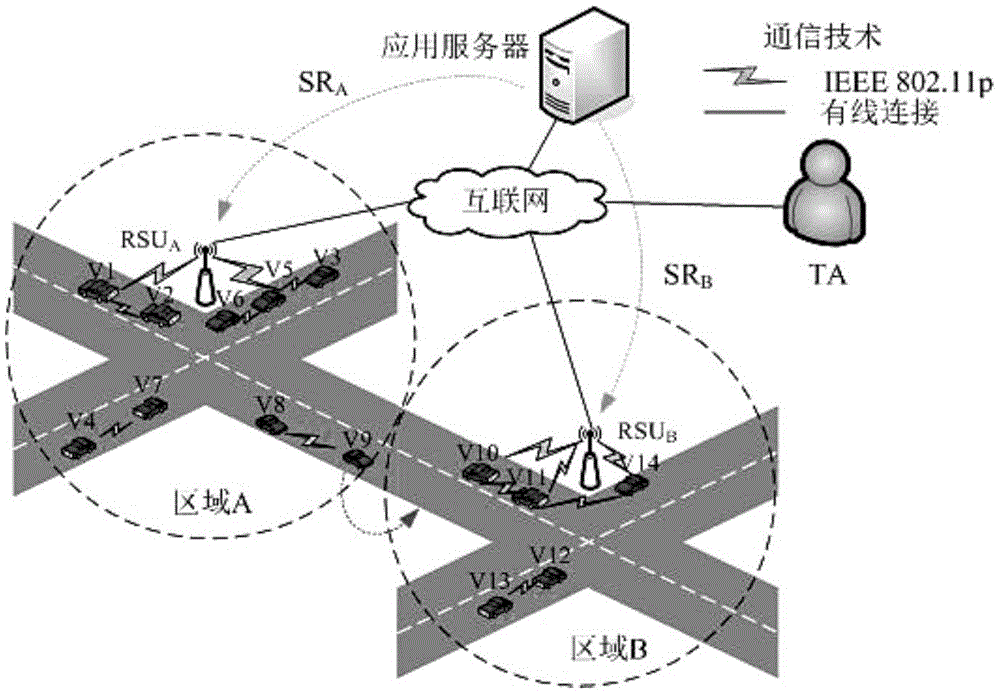
[0072] like figure 1 As shown, when the vehicle V i Leaving area A and entering area B, in order to maintain the subscribed service, update the handover key to ensure forward and backward security. The handover key update process is as follows:
[0073] (1)RSU A Signal processing process:
[0074] (11)V i RSU detected A signal P A Weak and RSU B signal P B Very strong (P A B ), V i Generate a random number N 2 , and use RSU A public key PKR A Encrypted N 2 , EncPKR A (N 2 ). Then put your current pseudonym information PID i , public key PK i , ordered service set SG i , the current timestamp T i and EncPKR A (N 2 ) as message M, and with N 2 As a key to generate a message authentication code HMAC(N 2 ,M), and finally send Message5.
[0075] Message5: (M=PID i ||PK i ||SG i ||EncPKR A (N 2 )||T i , HMAC(N 2 ,M))
[0076] (12)RSU ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com