Path sharing method and system for privacy protection
A privacy protection and sharing system technology, applied in transmission systems, digital transmission systems, encryption devices with shift registers/memory, etc., can solve problems such as threats to user privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0098] This embodiment describes the installation of each module in the system of the present invention and the specific implementation of the method of the present invention;
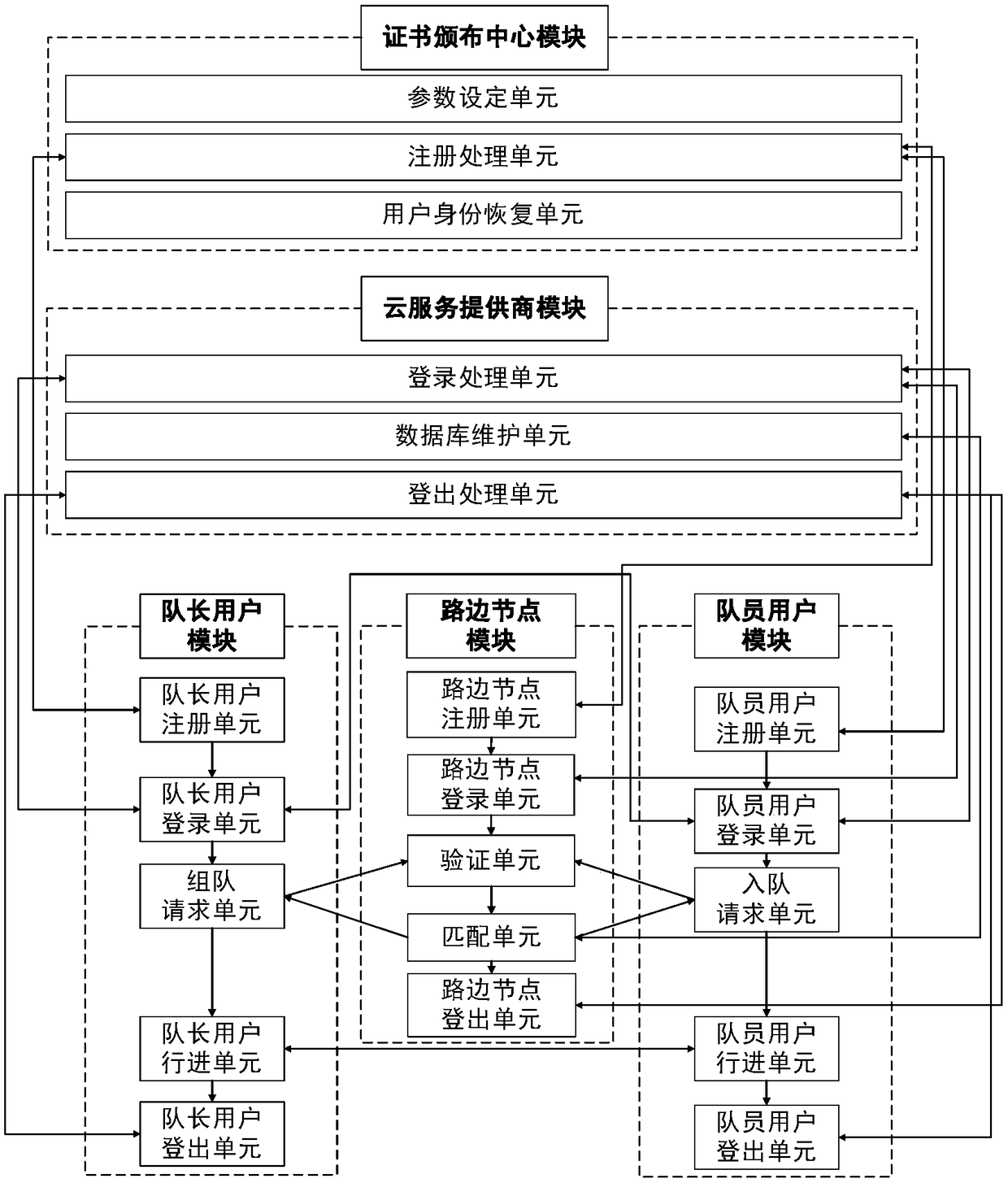
[0099] The certificate issuing center module is installed on a desktop computer; the server module is installed on Alibaba Cloud's cloud server; the roadside node module is installed on a desktop computer; the team leader user module and team member user module are installed on a laptop computer Above; the connection diagram of each module and unit is as follows figure 1 Shown
[0100] When step one is implemented, the operations of each sub-step are as follows:
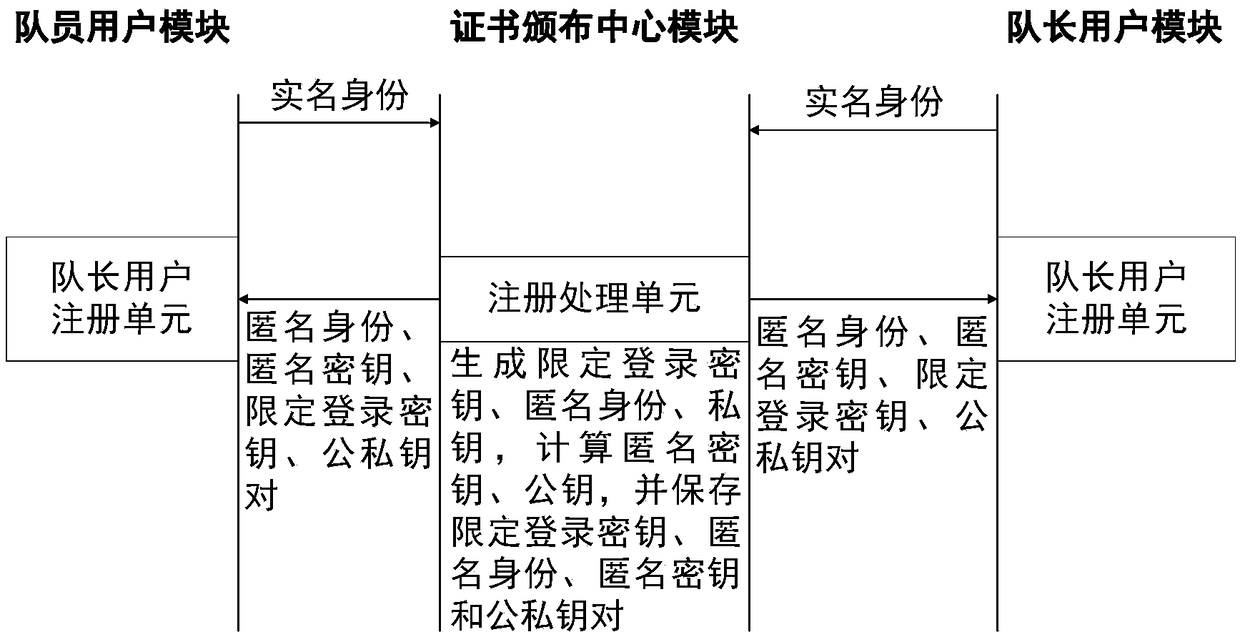
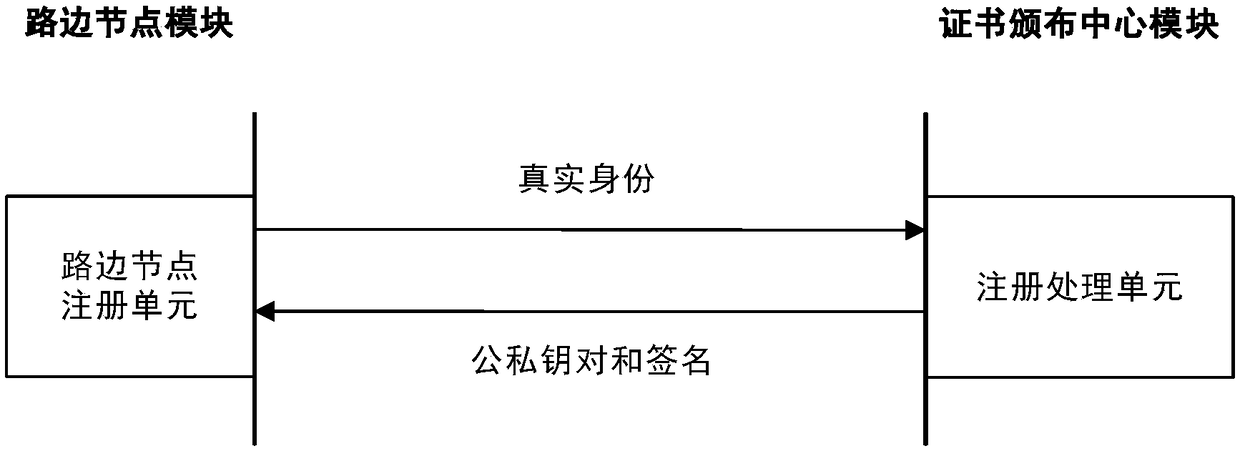
[0101] Step 1.1 The parameter setting unit generates multiplication cyclic group 1, multiplication cyclic group 2, and multiplication cyclic group 3 of the same order, selects the generators of the first two multiplication cyclic groups, generates bilinear mapping function 1, and selects two random numbers as Private key, calculate the correspondin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com