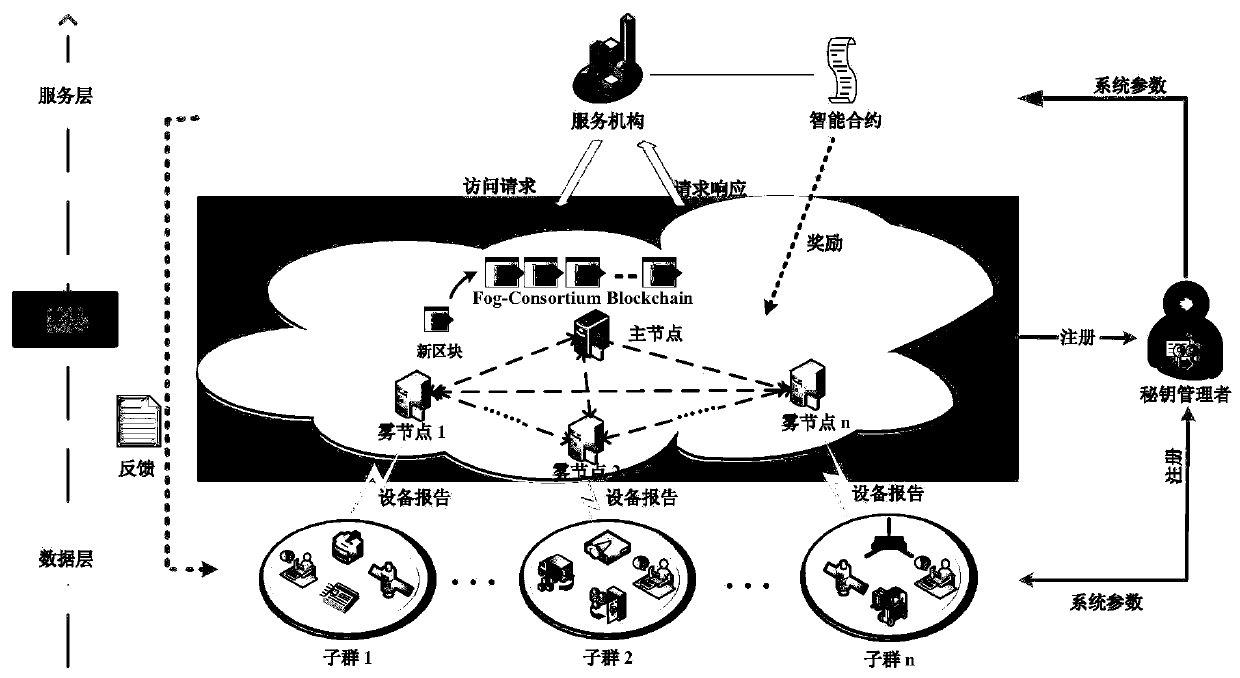
Security distributed aggregation and access system and method based on fog alliance chain
An access method and distributed technology, applied in the field of wireless network and information security, can solve problems such as single point of failure and illegal tampering
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
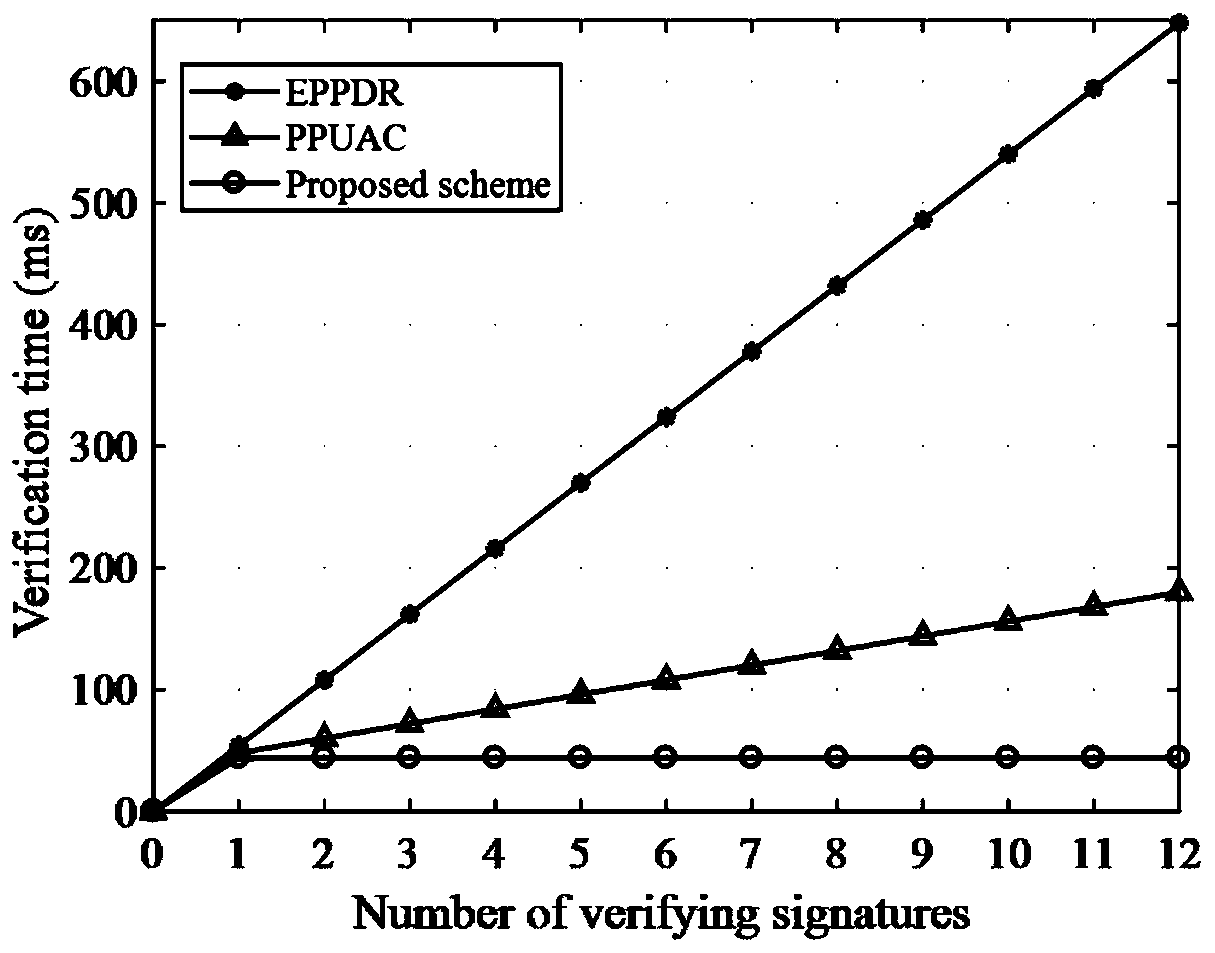
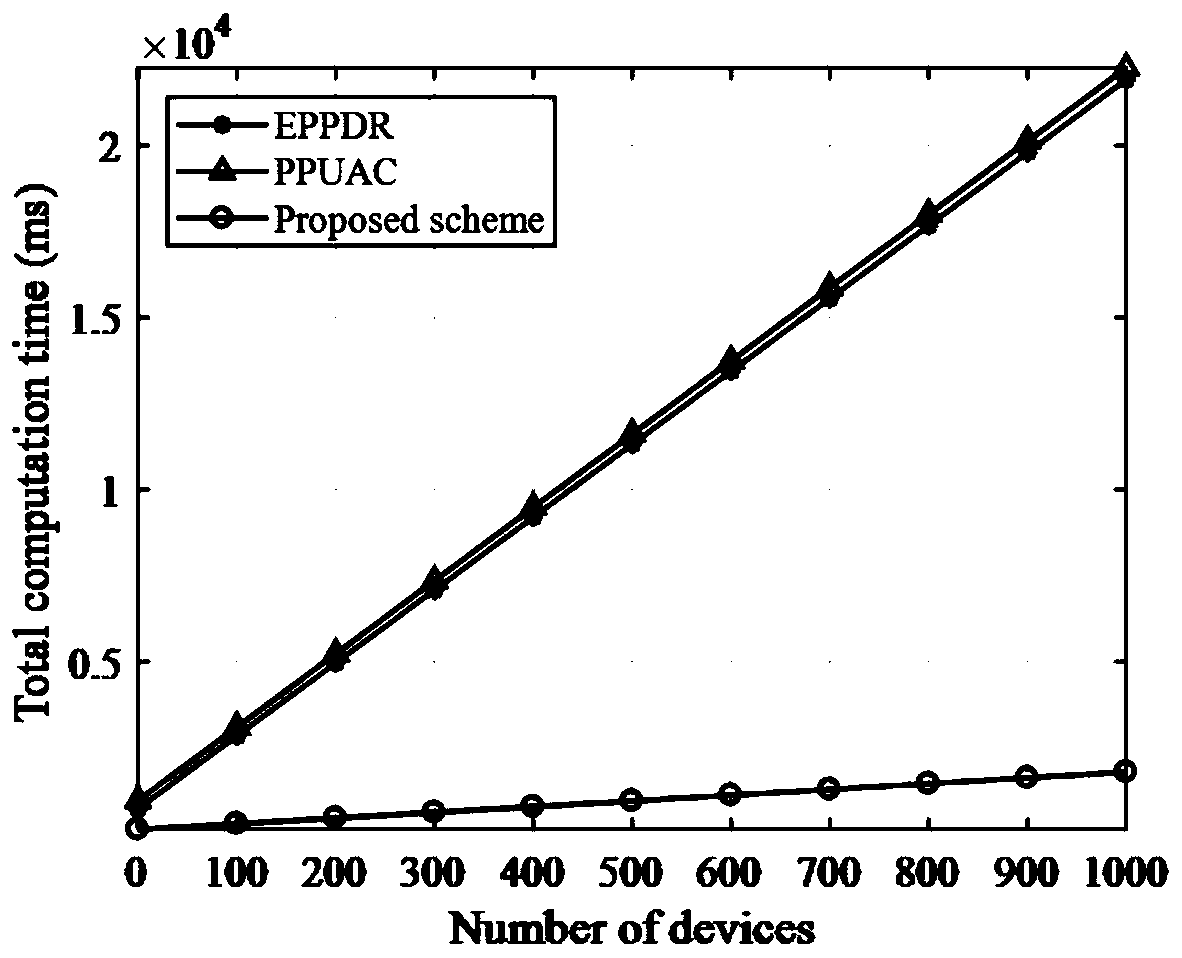
[0137] Based on the application of the secure distributed aggregation and access method based on the alliance chain designed by the present invention in actual scenarios, figure 2 Depicts the comparison between the design method of the present invention and the other two schemes: EPPDR scheme and PPUAC scheme in terms of verification overhead. It can be seen from the figure that the design method of the present invention significantly shortens the verification time compared to the other two methods, and with As the number of signatures increases, the design method of the present invention can highlight the advantage of low verification overhead; in addition, image 3 Depicts the comparison of the total computational cost between the design method of the present invention and the SEPPDR and PPUAC methods. The design method of the present invention significantly reduces the consumption of computing resources compared to the EPPDR scheme and the PPUAC scheme. This is mainly due to ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com