Multi-recipient anonymous encryption apparatus under hybrid mechanism
An encryption device and receiver technology, applied in the field of information security, can solve the problems such as the inability to guarantee the anonymity of the recipient identity, the lack of security proof, and the indistinguishability of encryption.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
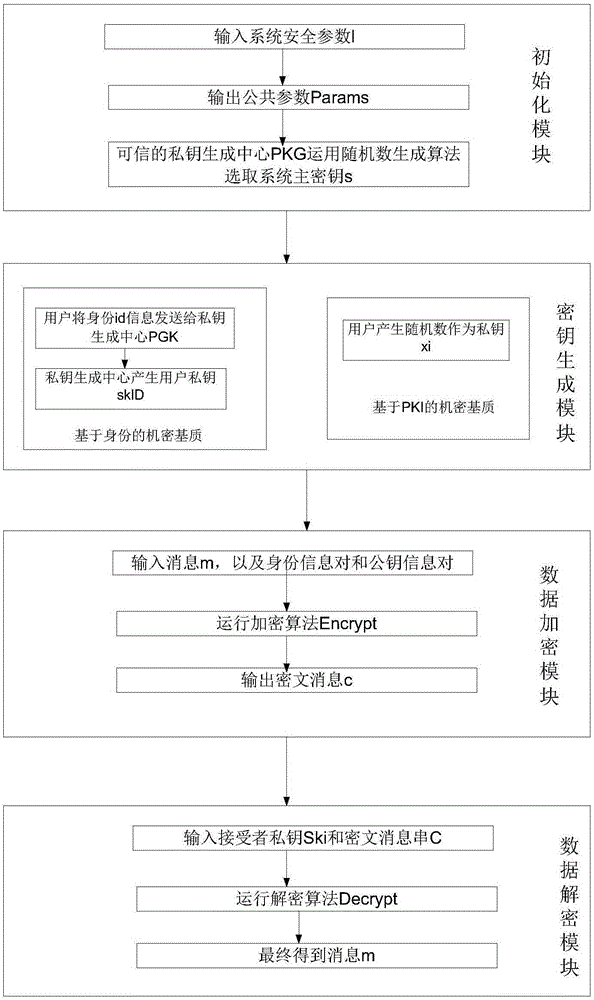
[0049] Such as figure 1 and figure 2 As shown, the present invention is a multi-recipient anonymous encryption device under a hybrid mechanism.
[0050] This embodiment includes a credible private key generation center PKG and n recipients, among all n recipients, l recipient is a recipient under the identity-based cryptographic system, and its identity set is {ID 1 , ID 2 ,...ID l}; the other n-l receivers are receivers based on the PKI cryptosystem, and their public key certificate set is {PK l+1 , PK l+2 ,...PK n}.
[0051] The implementation process of this embodiment includes the following steps:
[0052] 1. The trusted private key generation center PKG selects the security parameters and the appropriate hash function algorithm from the integer group, runs the bilinear pairing operation, and generates the system public parameter Params.
[0053] 2. PKG performs the key generation process:
[0054] (1) Based on the identity encryption process, PKG uses the system...
Embodiment 2
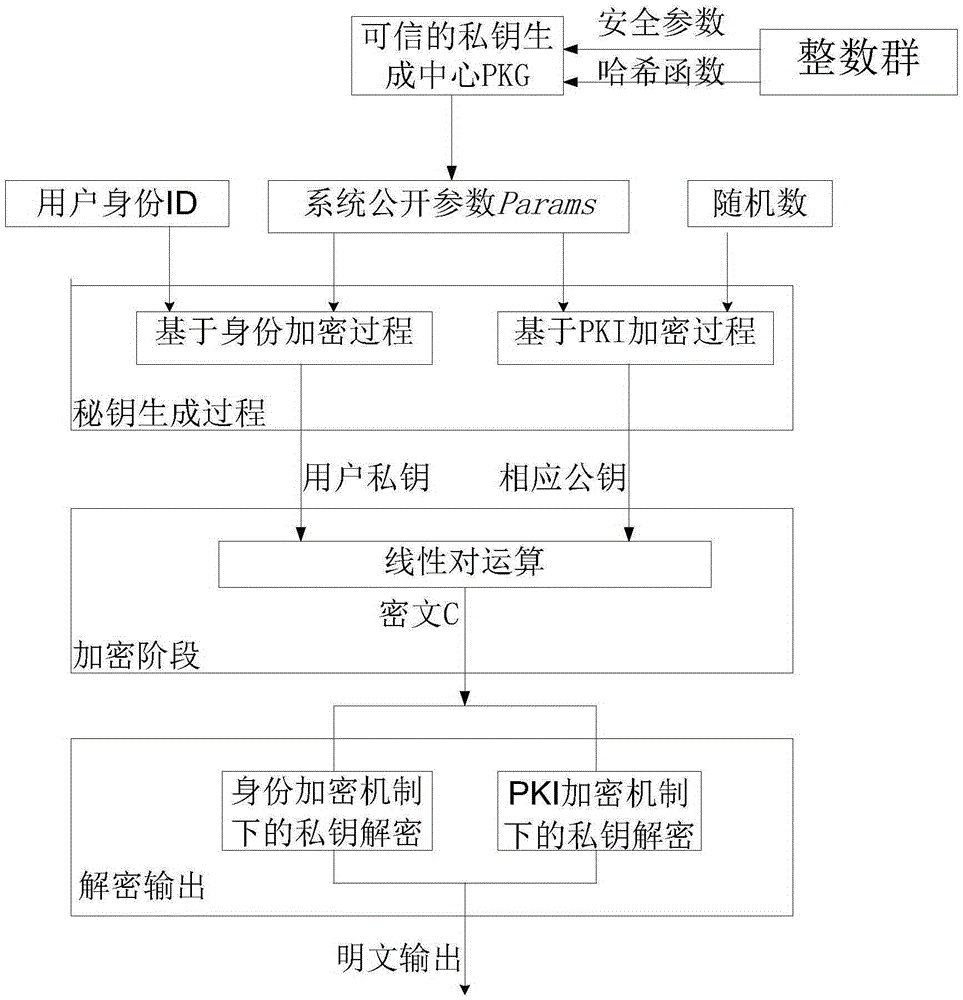
[0085] Such as figure 1 Shown, except following difference, all the other are identical with embodiment 1:
[0086] In step 2, this process is divided into two kinds of cryptographic mechanisms and described separately, that is, the identity-based encryption mechanism and the PKI-based encryption mechanism. First, the trusted center PKG generates system parameters, and then determines the public parameters of the system, selects and outputs Public parameters, the specific implementation of this function includes the following three steps:
[0087] 1: The trusted center generates system security parameters λ∈Z * , run the corresponding algorithm to generate two additive cyclic groups G with order q 1 and the multiplicative cyclic group G 2 .Run the random generation algorithm to generate G 2 Generator P and generate a bilinear mapping algorithm e:G 1 ×G 1 →G 2 .
[0088] 2: Select three hash functions: H:G 1 → {0, 1} * , H 1 :G 2 → Z q and l is the length of the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com