Method for protecting privacy of vehicle ad hoc network based on signcryption
A vehicle ad hoc network and privacy protection technology, applied in the direction of services based on specific environments, communication between vehicles and infrastructure, network topology, etc., can solve the problem that security and personal privacy are not fully guaranteed and are unlikely to be accepted and participation in VANET, restricting the development and application of VANET, to achieve the effect of ensuring security, improving efficiency, and preventing illegal attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The technical solutions in the embodiments of the present invention will be described clearly and in detail below with reference to the drawings in the embodiments of the present invention. The described embodiments are only some of the embodiments of the invention.
[0043] The technical scheme that the present invention solves the problems of the technologies described above is:
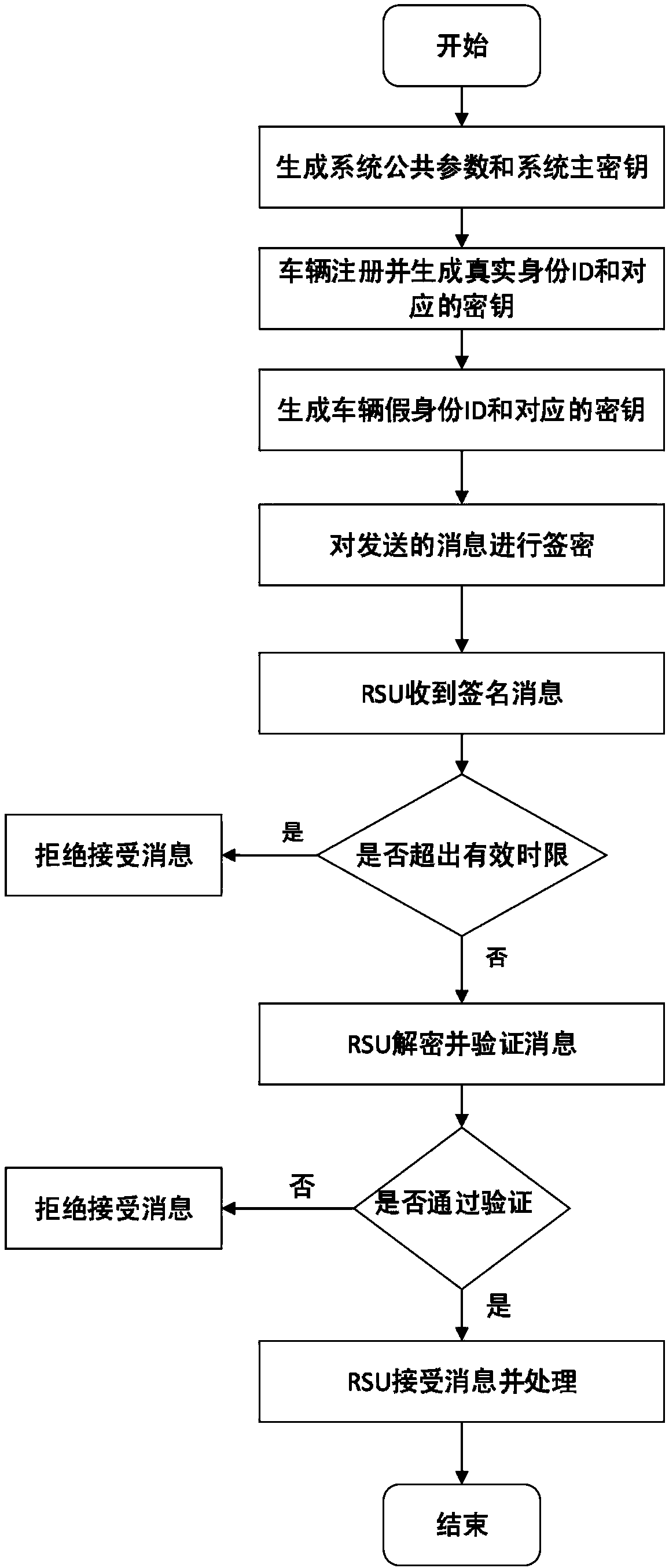
[0044] The signcryption-based vehicle ad hoc network privacy protection mechanism provided by the present invention includes the following steps, see figure 2 :
[0045] 1. A method for protecting privacy in a vehicle ad hoc network based on signcryption, comprising the following steps
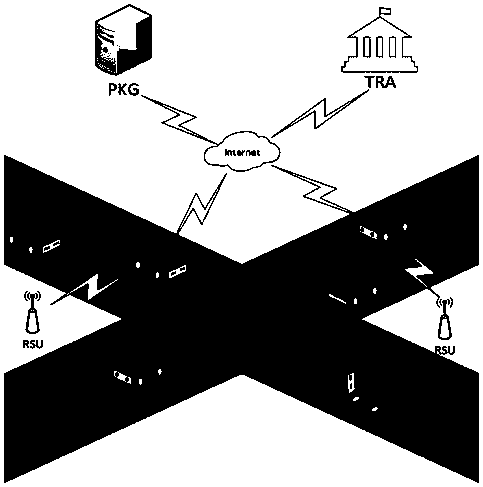
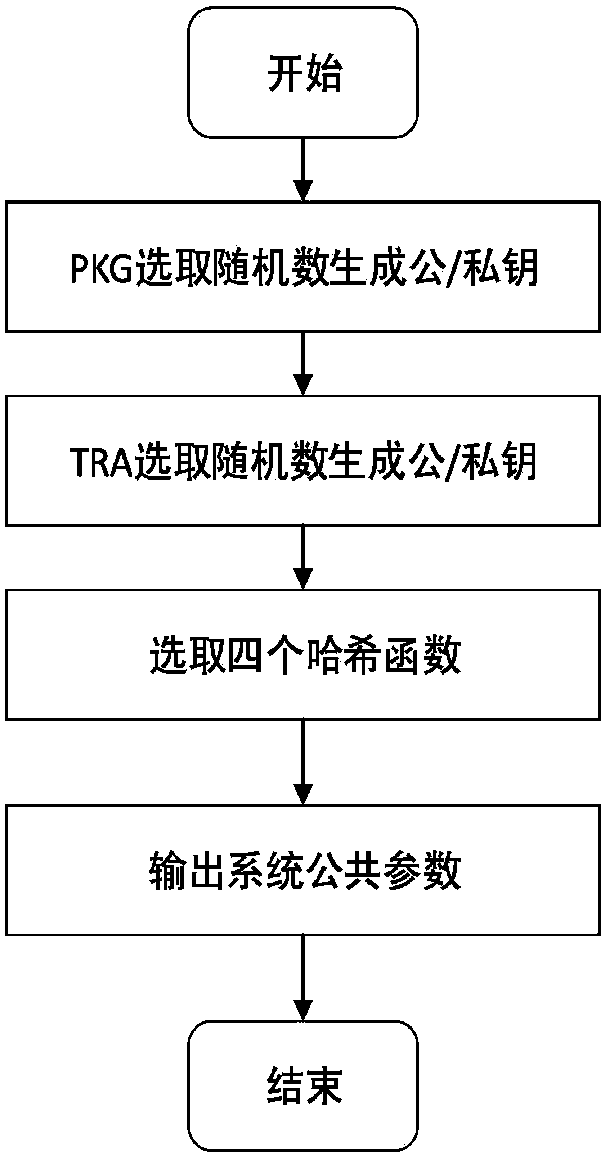
[0046] S1: System initialization, the key generation center (Private Key Generator, PKG) and the trusted authority center (TrustedAuthority) generate system public parameters, where the system public parameters include two order p bilinear groups G and G T , the generator g in G and the bilinear map e: G...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com