Traceable effective open auditing method and system in cloud storage data sharing
A data sharing and cloud storage technology, applied in the field of cloud computing security, can solve the problems of destroying the usability of shared data, high communication overhead, dishonesty of users in the group, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
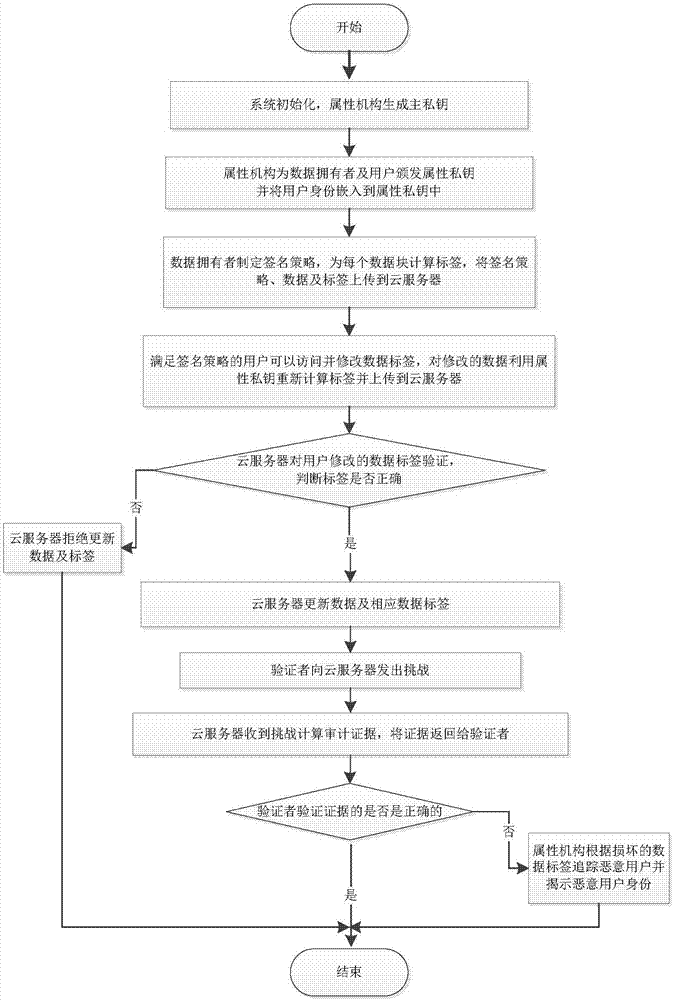
[0066] It should be noted that, in the case of no conflict, the embodiments in the present application and the features in the embodiments can be combined with each other. The present invention will be described in detail below with reference to the accompanying drawings and examples.
[0067] Explanation and description of technical terms in the present invention:
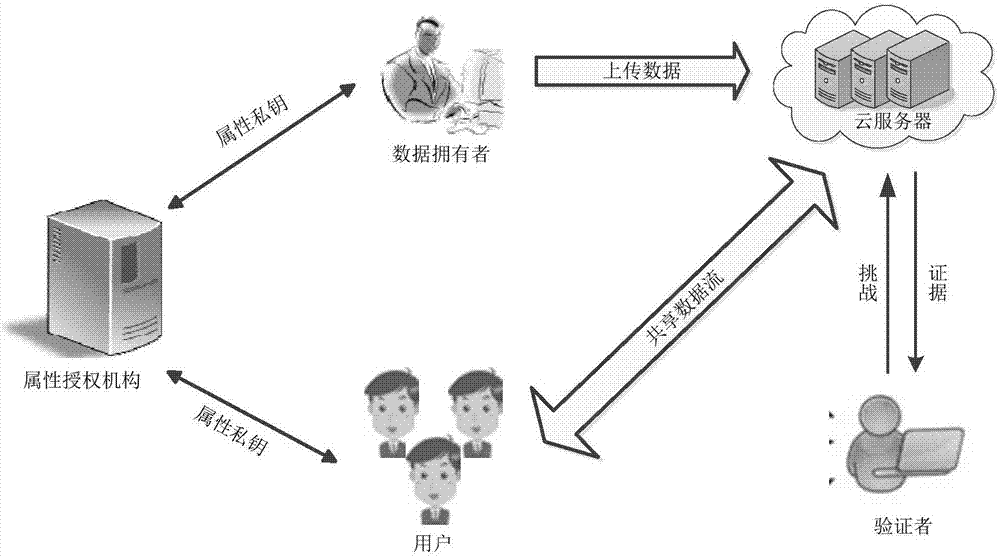
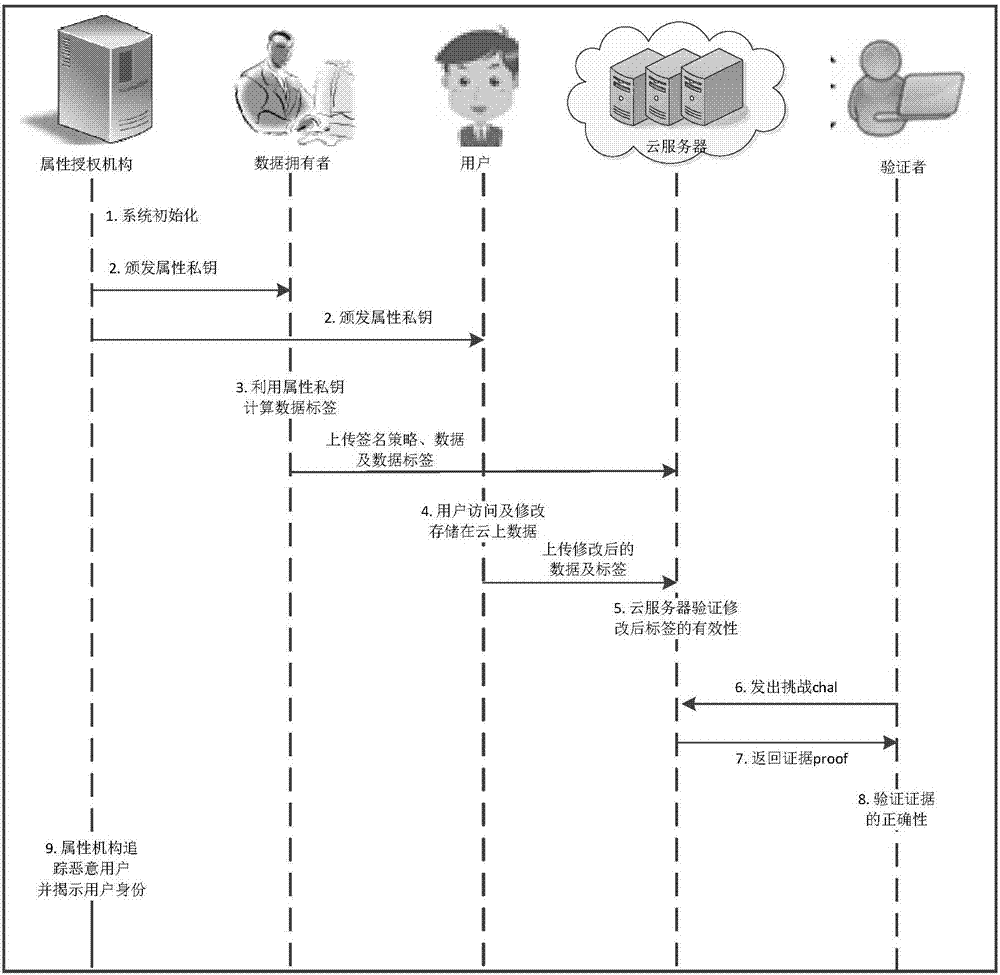
[0068] Attribute authority: perform attribute authentication on users, and issue attribute private keys to users according to user attributes;
[0069] Data owner: The owner of the data formulates a signature policy for the data, calculates the data block label for each data block, and uploads the signature policy, data and data block label to the cloud server;
[0070] User: Users who meet the signature policy can access and modify the data uploaded by the data owner;
[0071] Cloud server: a distributed storage system with a large number of storage and computing resources, providing users with data storage, co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com