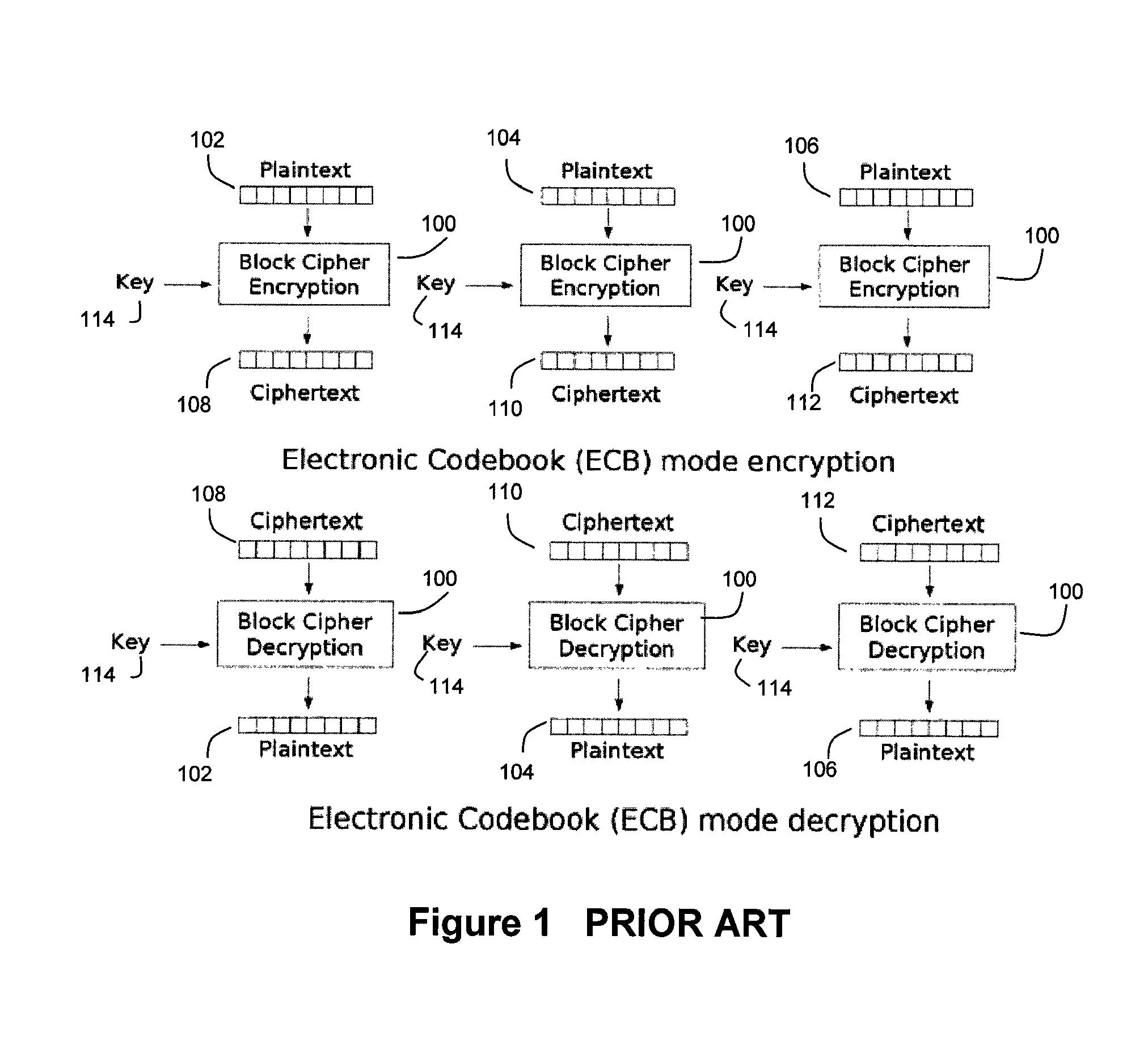
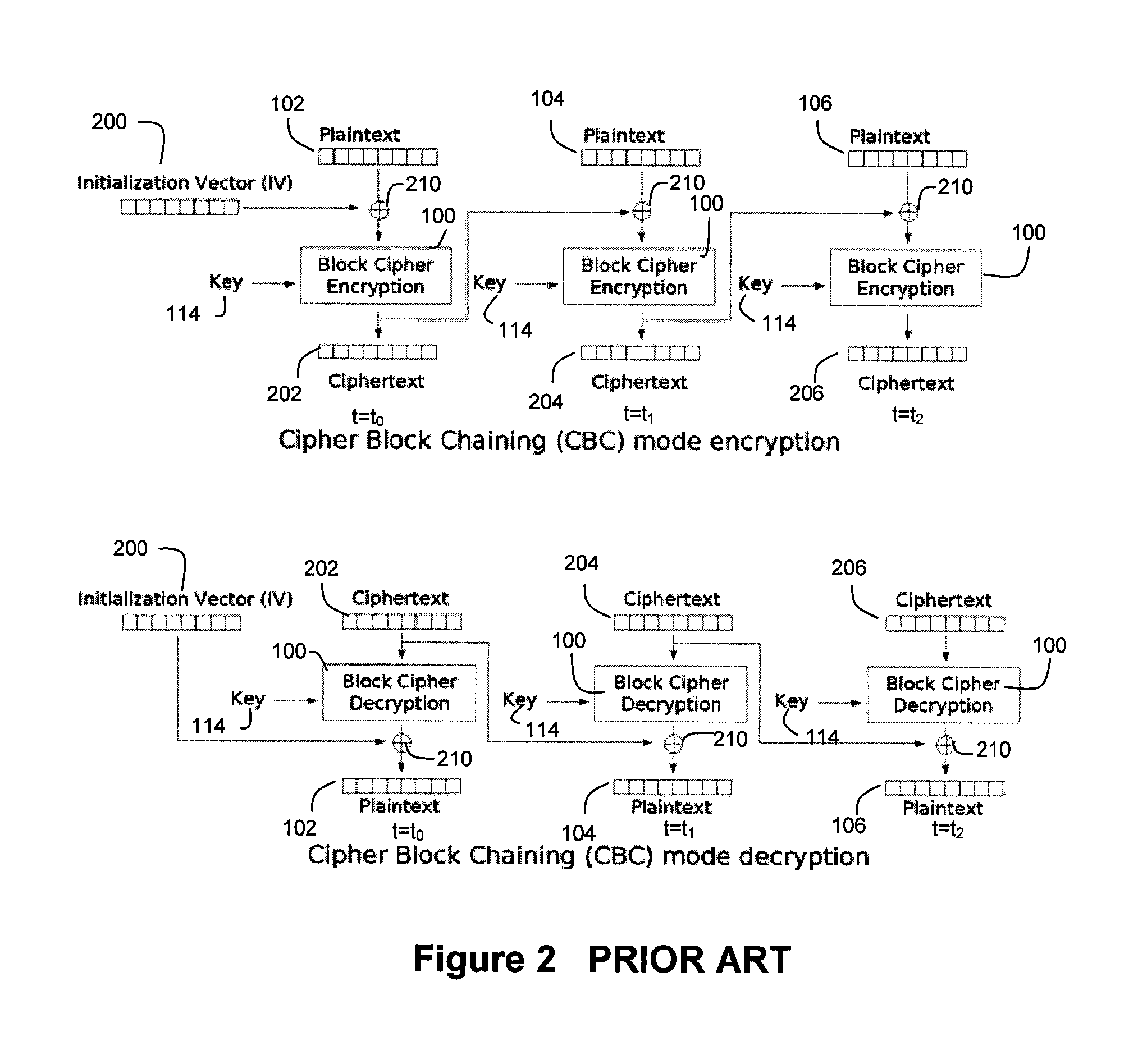
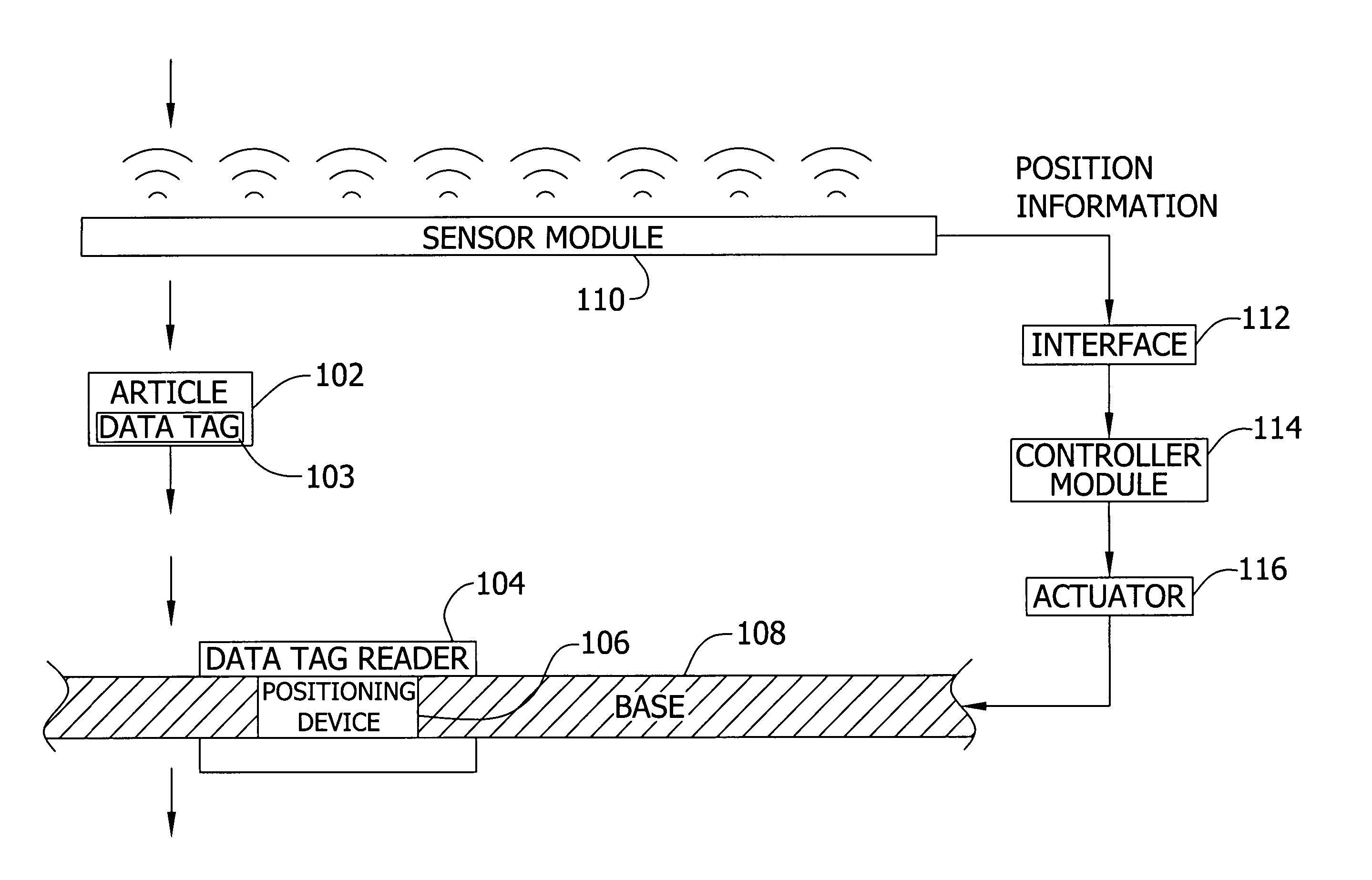
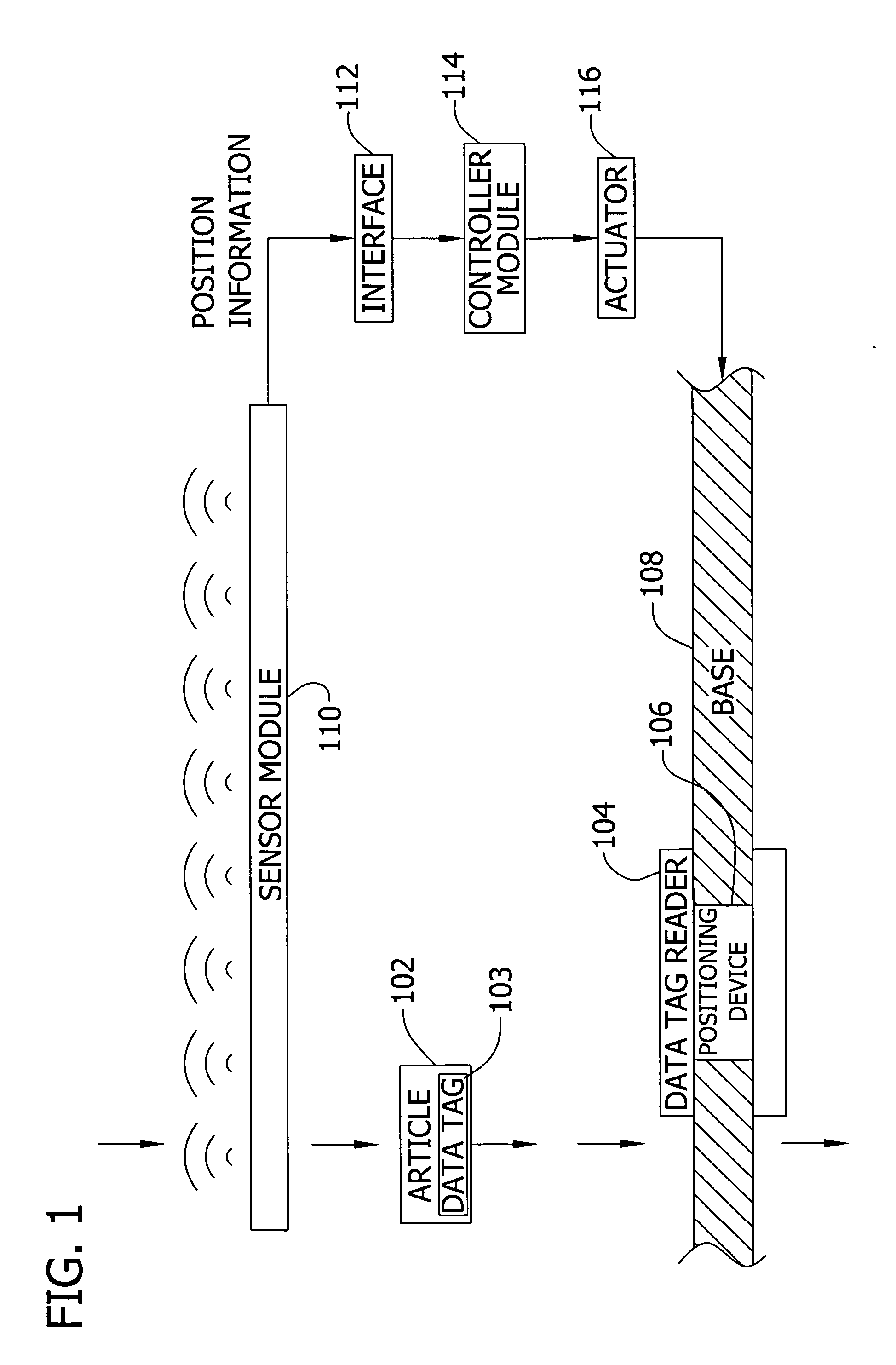
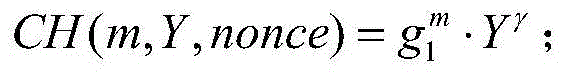Patents
Literature
1680 results about "Data labeling" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
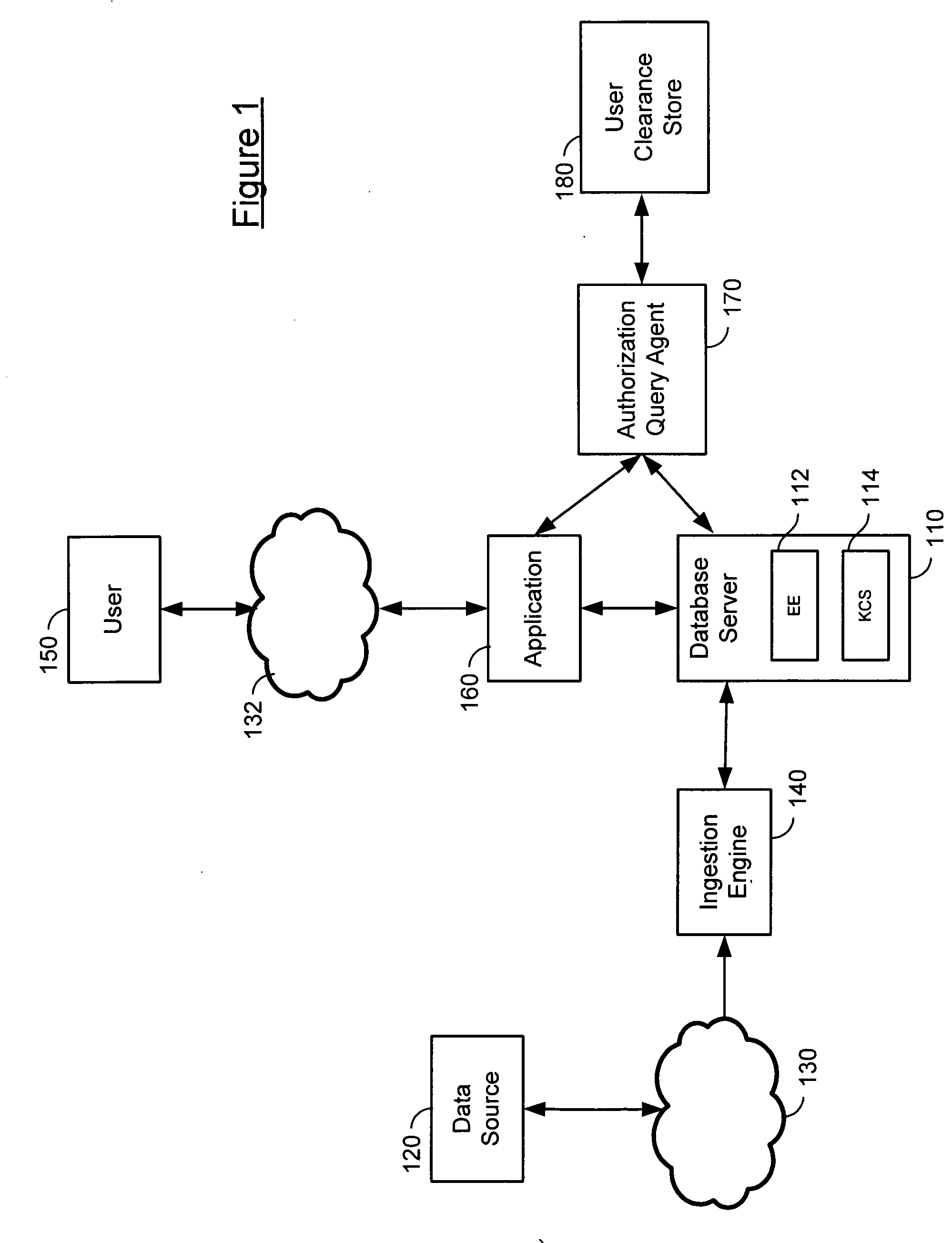
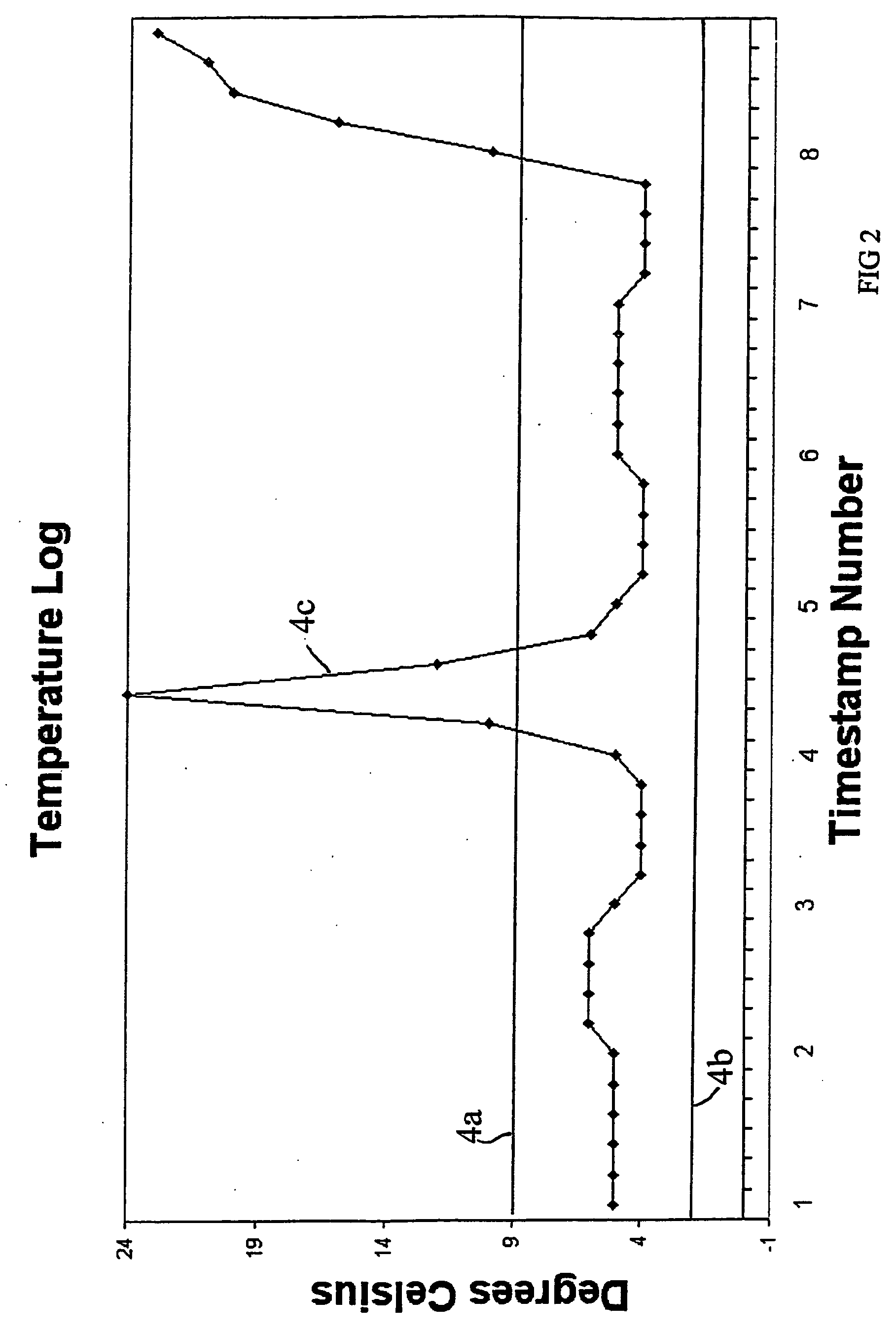
Data labeling ensures that users know what data they are handling and processing. For example, if an organization classified data as confidential, private, sensitive, and public, it would also use labeling to identify the data. These labels can be printed labels for media such as backup tapes.
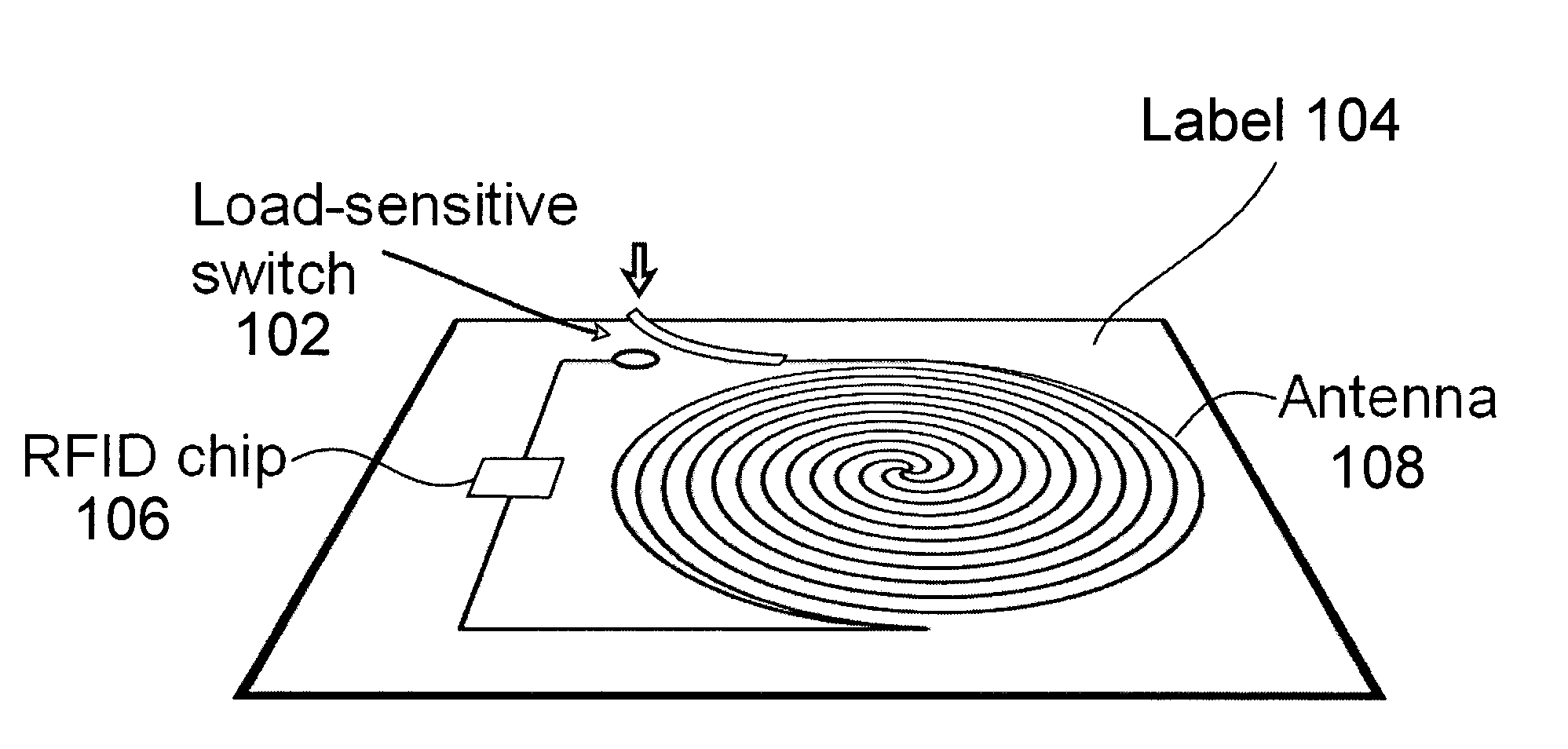
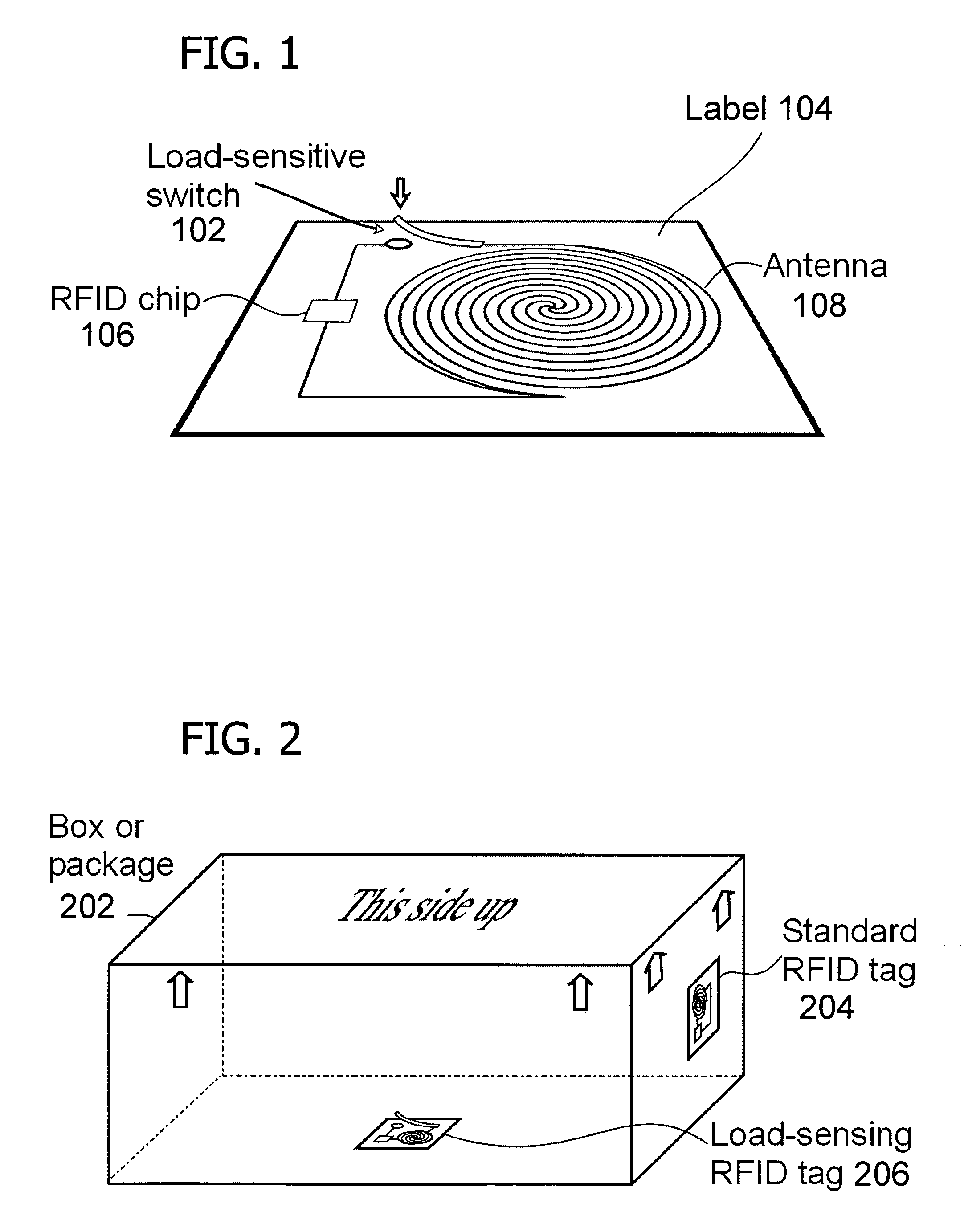
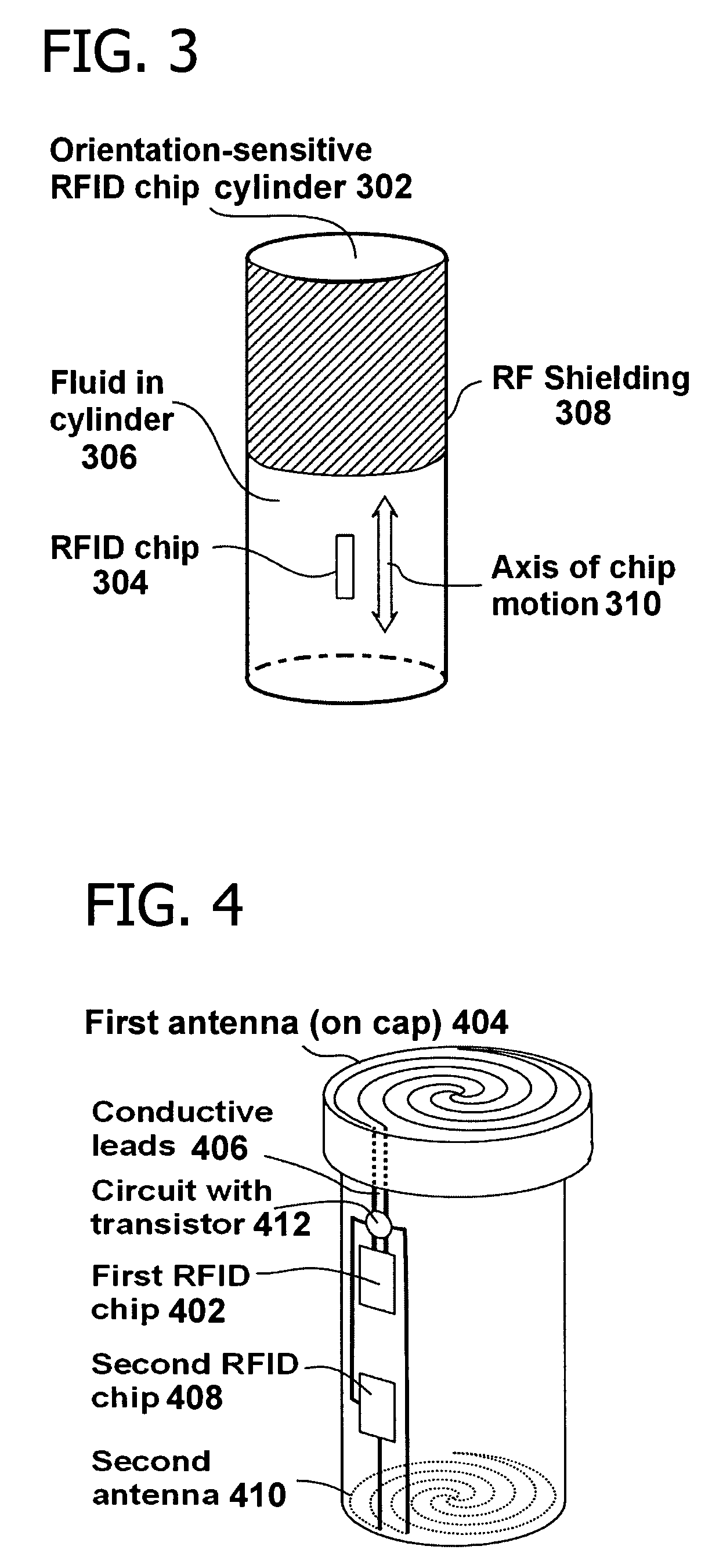
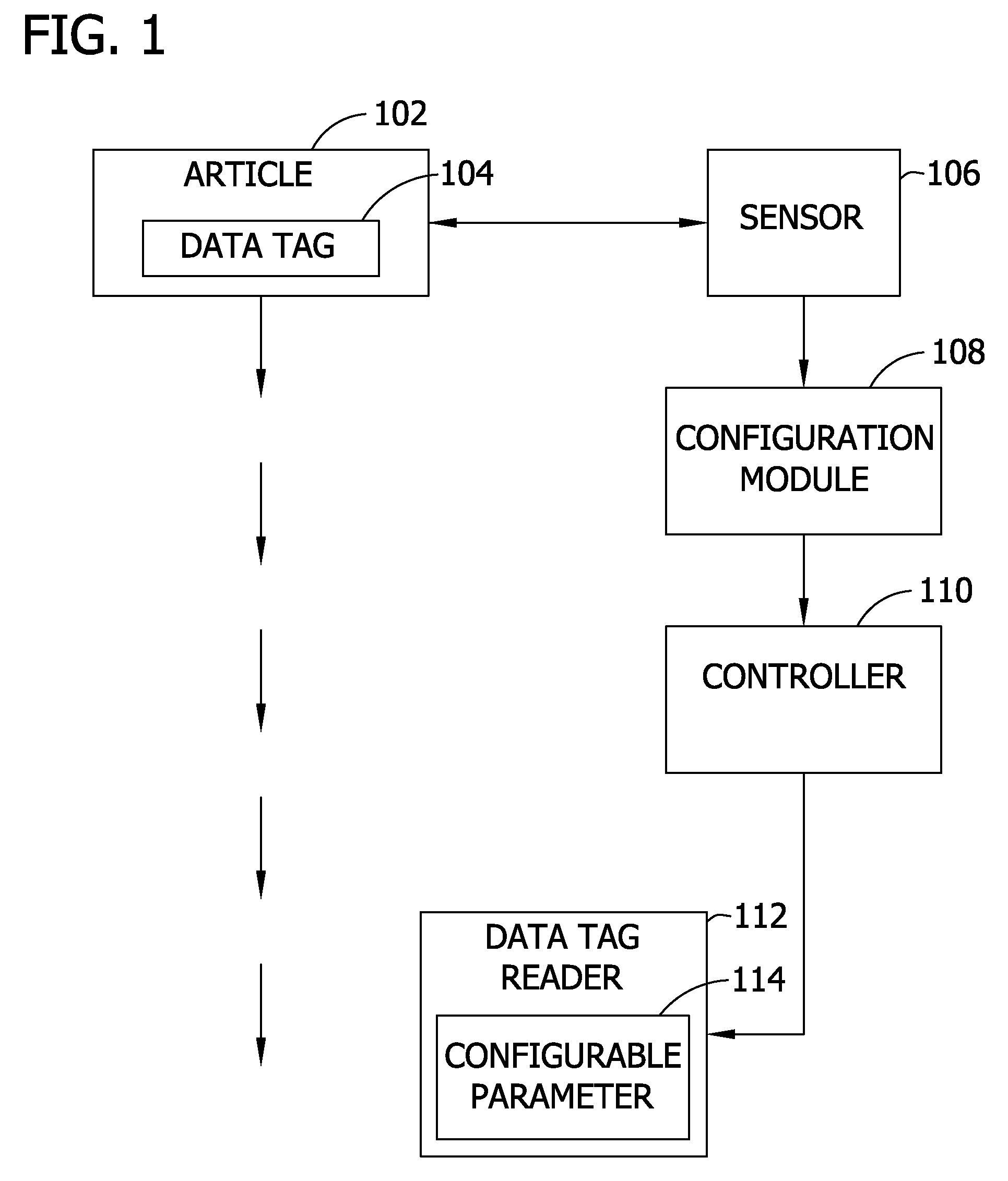
Activating a data tag by load or orientation or user control
ActiveUS7151455B2Facilitate communicationFire alarm electric actuationRecord carriers used with machinesRadio frequencyUser control
Mechanically and reversibly activating or deactivating a radio frequency identification (RFID) data tag. An RFID tag includes an RFID chip for storing an RFID code, an antenna for communicating a radio frequency (RF) signal, and a mechanical switch coupling the RFID chip to the antenna. Closing the mechanical switch enables the RFID chip and the antenna to communicate the RFID code via the RF signal.
Owner:CALLAHAN CELLULAR L L C
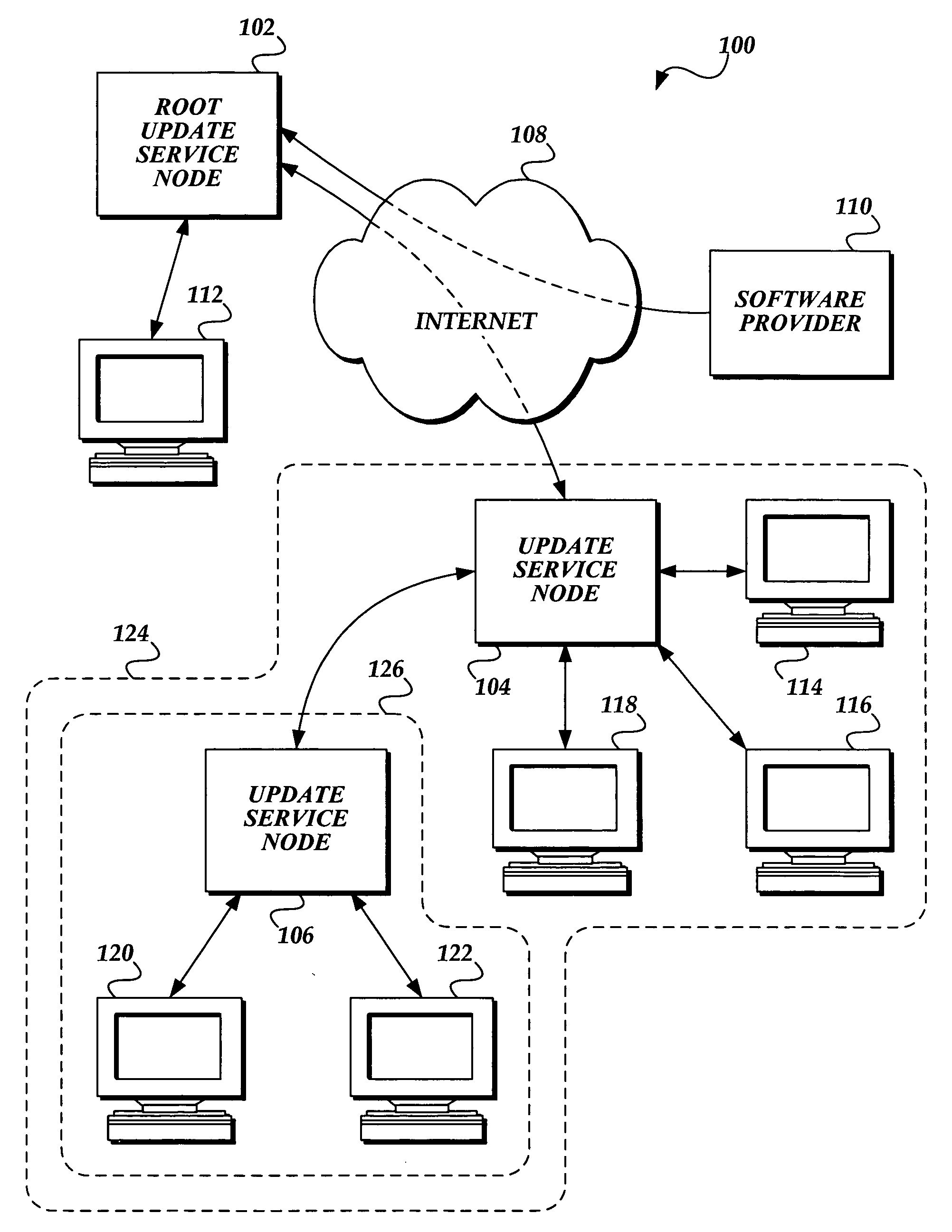
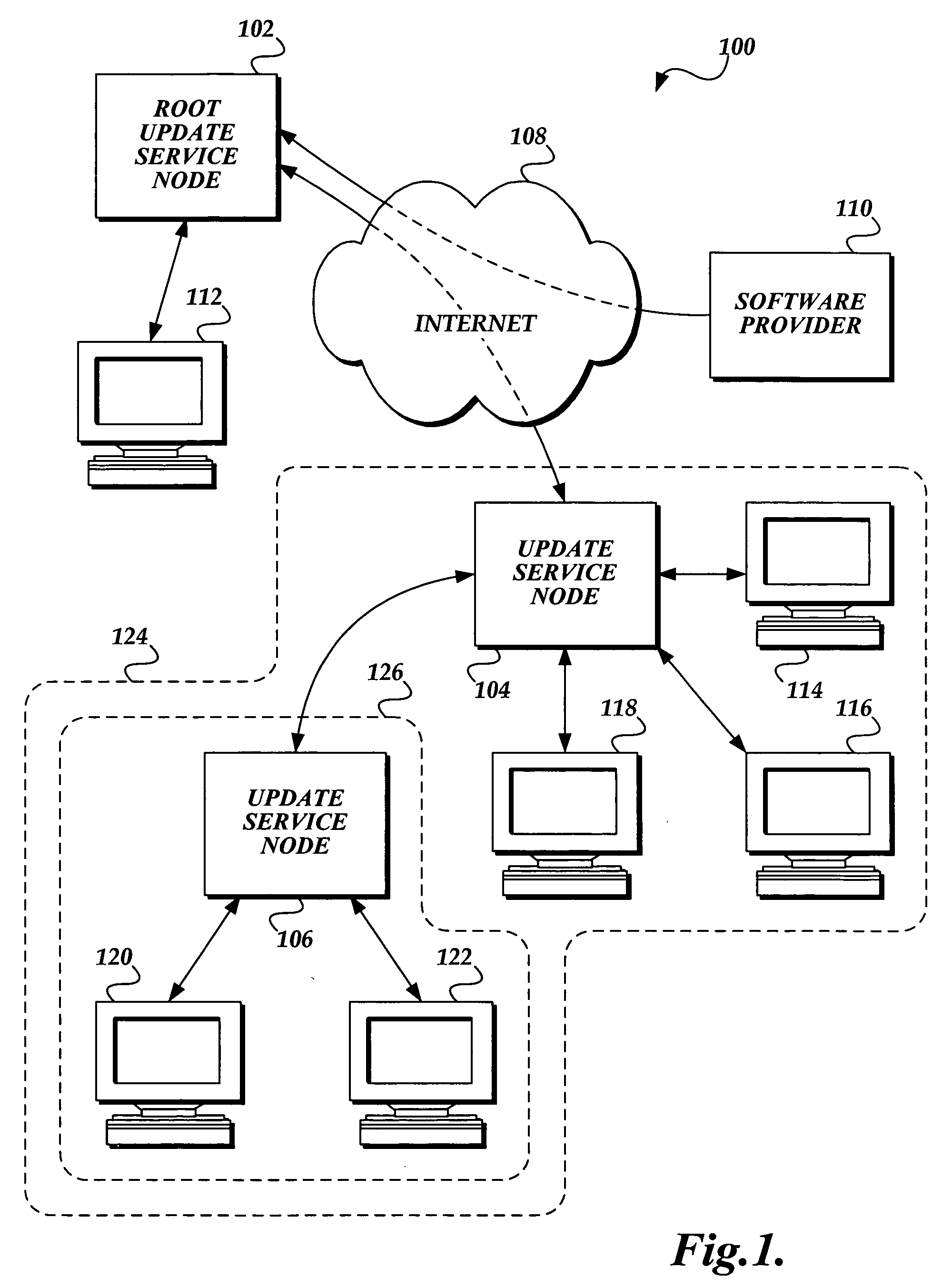
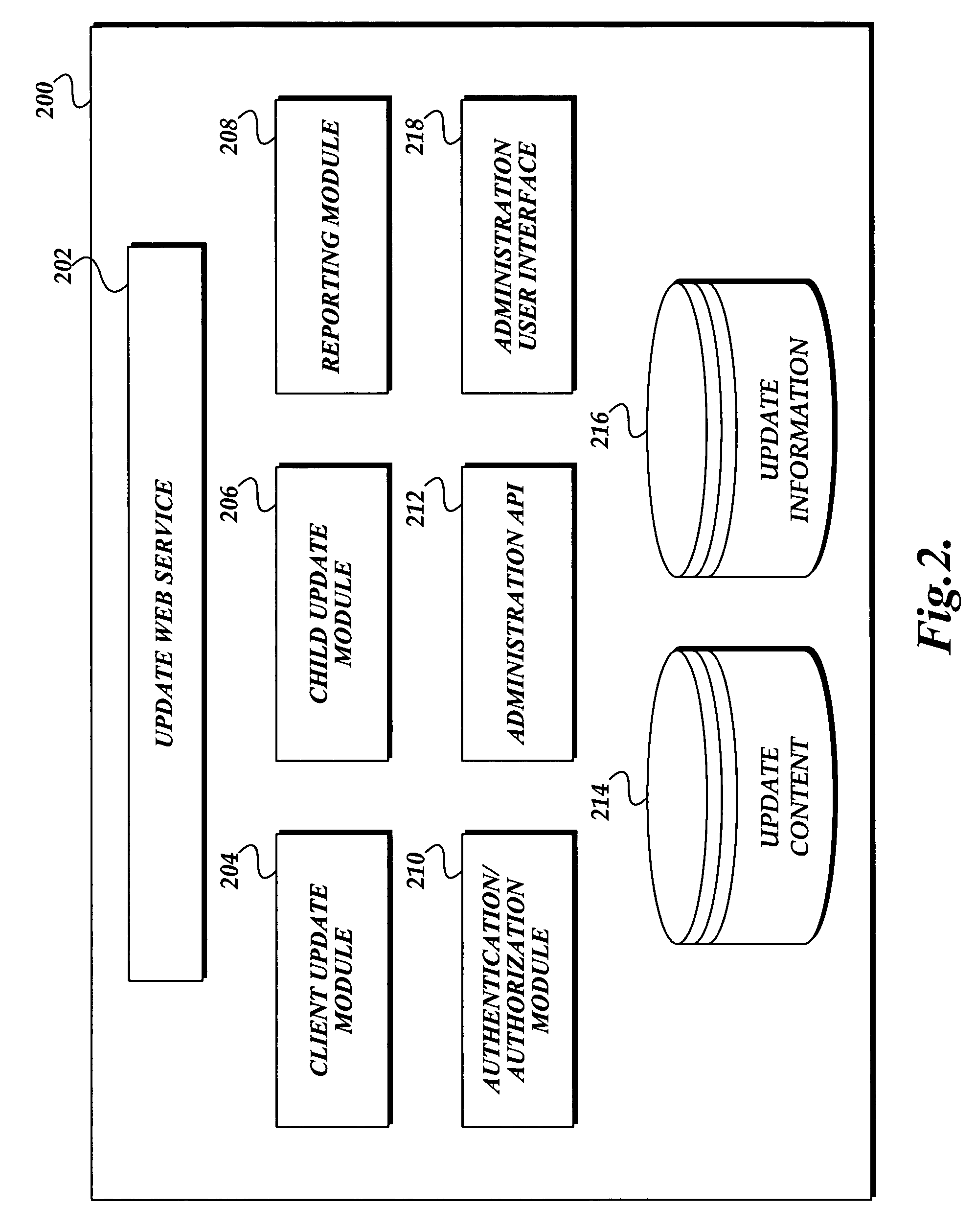
Tag-based schema for distributing update metadata in an update distribution system
ActiveUS20050228798A1Error detection/correctionDigital data processing detailsInformation processingSoftware update
A tag-based structure for communicating software update metadata information to client computers and to update service nodes is presented. An update metadata file includes: an identifier tag including a software update identifier that uniquely identifies the software update; zero or more general properties tags that carry general property information relating the software update; zero or more localized properties tags that carry localized property information organized according to language; zero or more relationship tags that identify dependency relationships the current software update, as described in the update metadata, has with other software updates; zero or more applicability rules tags that carry information for determining the applicability of the software update to a client computer; zero or more files tags that carry information relating to the software update's payload files; and handler specific data tags that carry information directed to the software handler for installing the software update.
Owner:MICROSOFT TECH LICENSING LLC
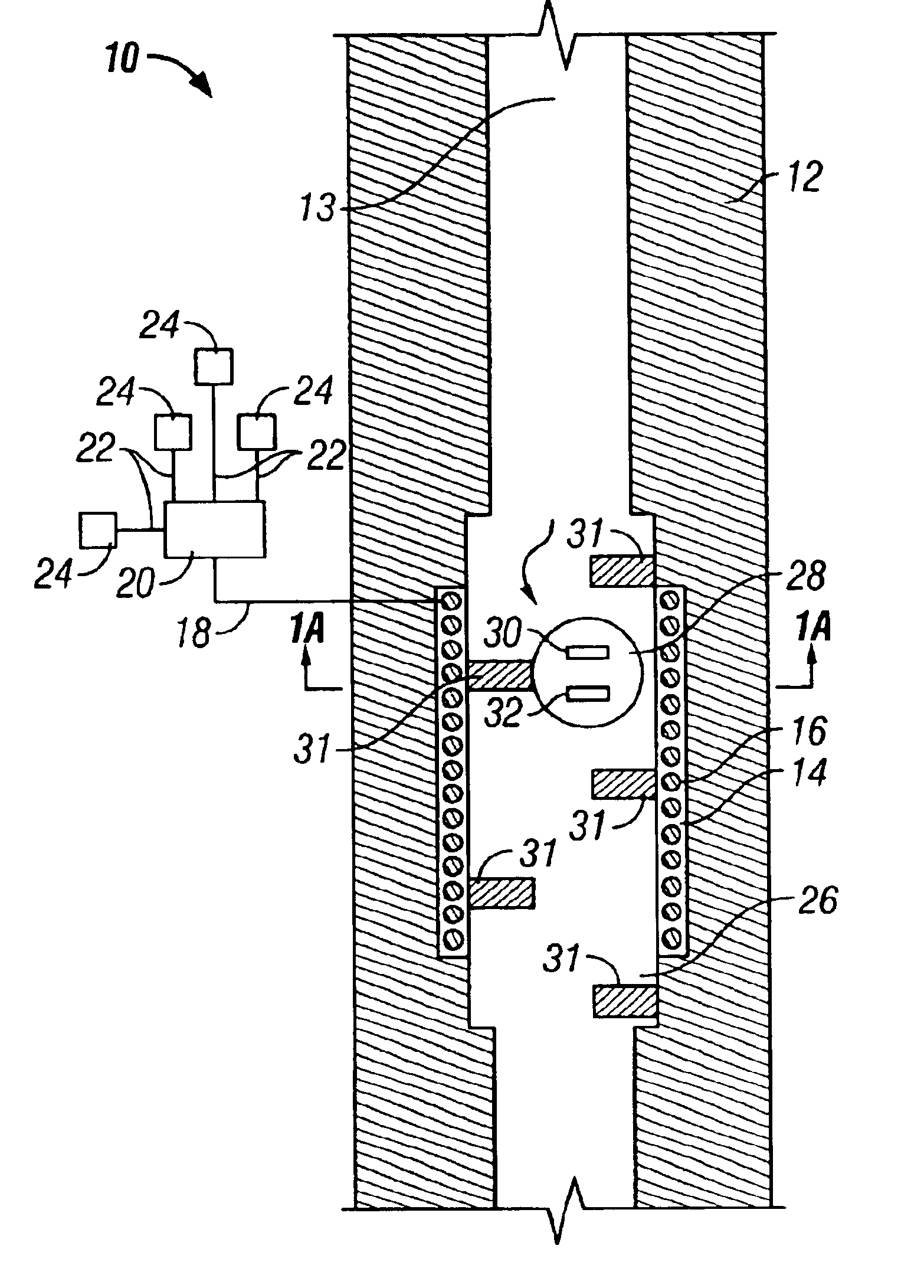
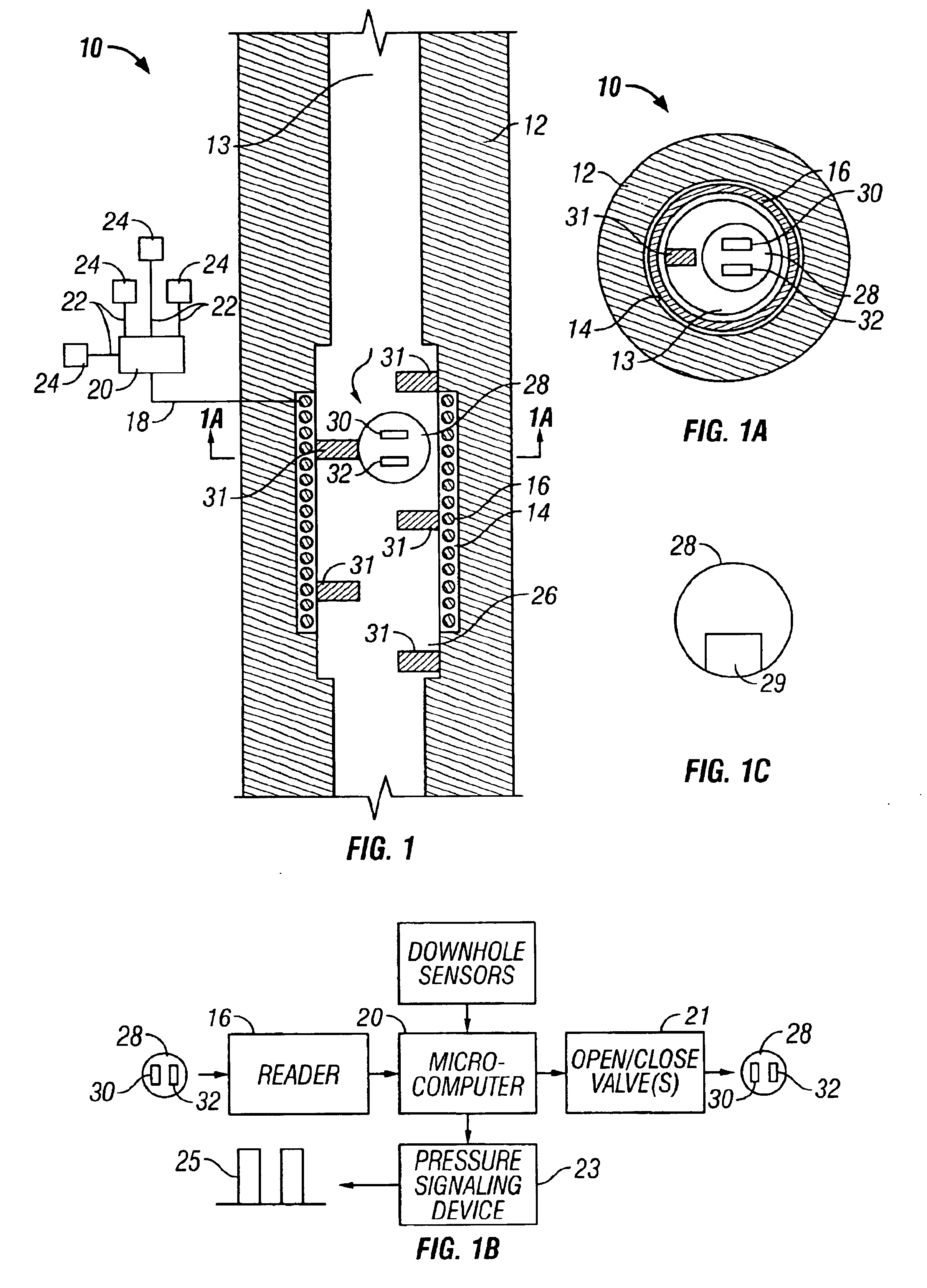
Universal downhole tool control apparatus and methods
A method and apparatus for internal data conveyance within a well from the surface to a downhole tool or apparatus and for returning downhole tool data to the surface, without necessitating the provision of control cables and other conventional conductors within the well. One embodiment involves sending telemetry elements such as tagged drop balls or a fluid having specific chemical characteristics from surface to a downhole tool as a form of telemetry. The telemetry element or elements are provided with identification and instruction data, which may be in the form of data tags, such as RF tags or a detectable chemical constituent. The downhole tool or apparatus is provided with a detector and microcomputer and is capable of recognizing the telemetry element and communicating with it or carrying out instructions that are provided in the telemetry data thereof.
Owner:SCHLUMBERGER TECH CORP
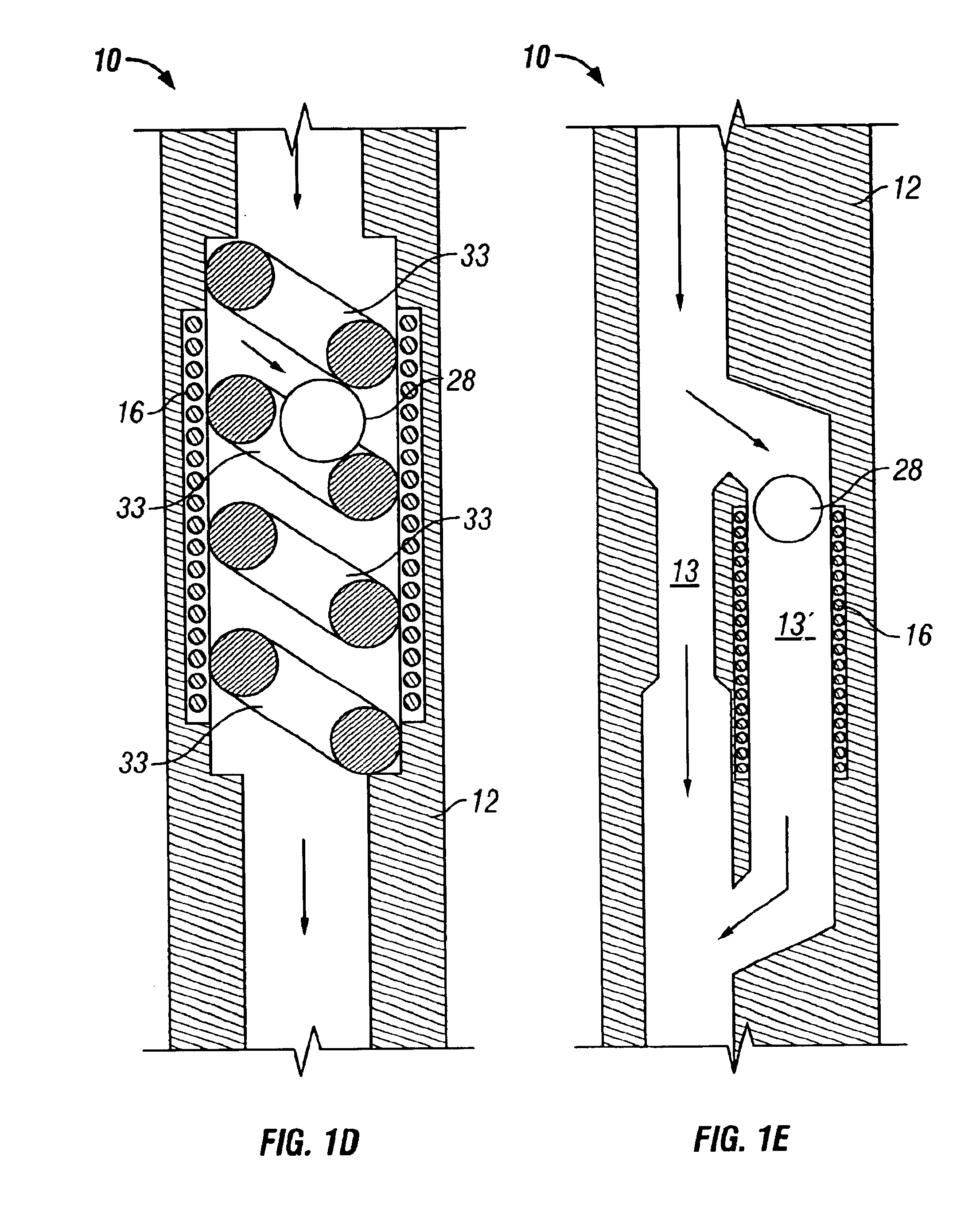
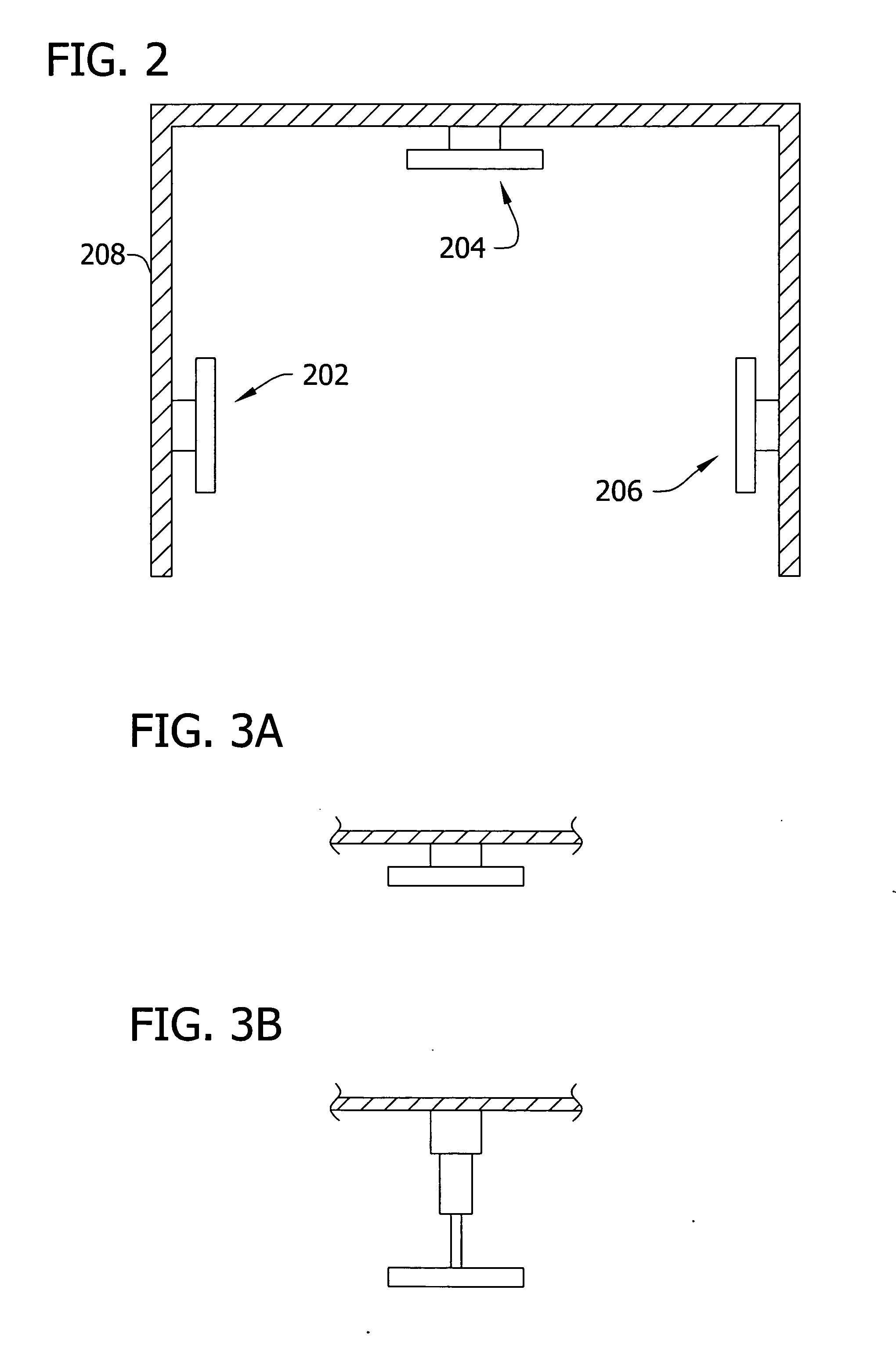
Self-adjusting portals with movable data tag readers for improved reading of data tags
ActiveUS7221269B2Easy to readImprove readabilityCo-operative working arrangementsSensing record carriersComputer hardwareLocation Equipment
Owner:AI-CORE TECH LLC
Asset tracking within and across enterprise boundaries
InactiveUS6237051B1Hand manipulated computer devicesSpecial service for subscribersRelational databaseGeolocation
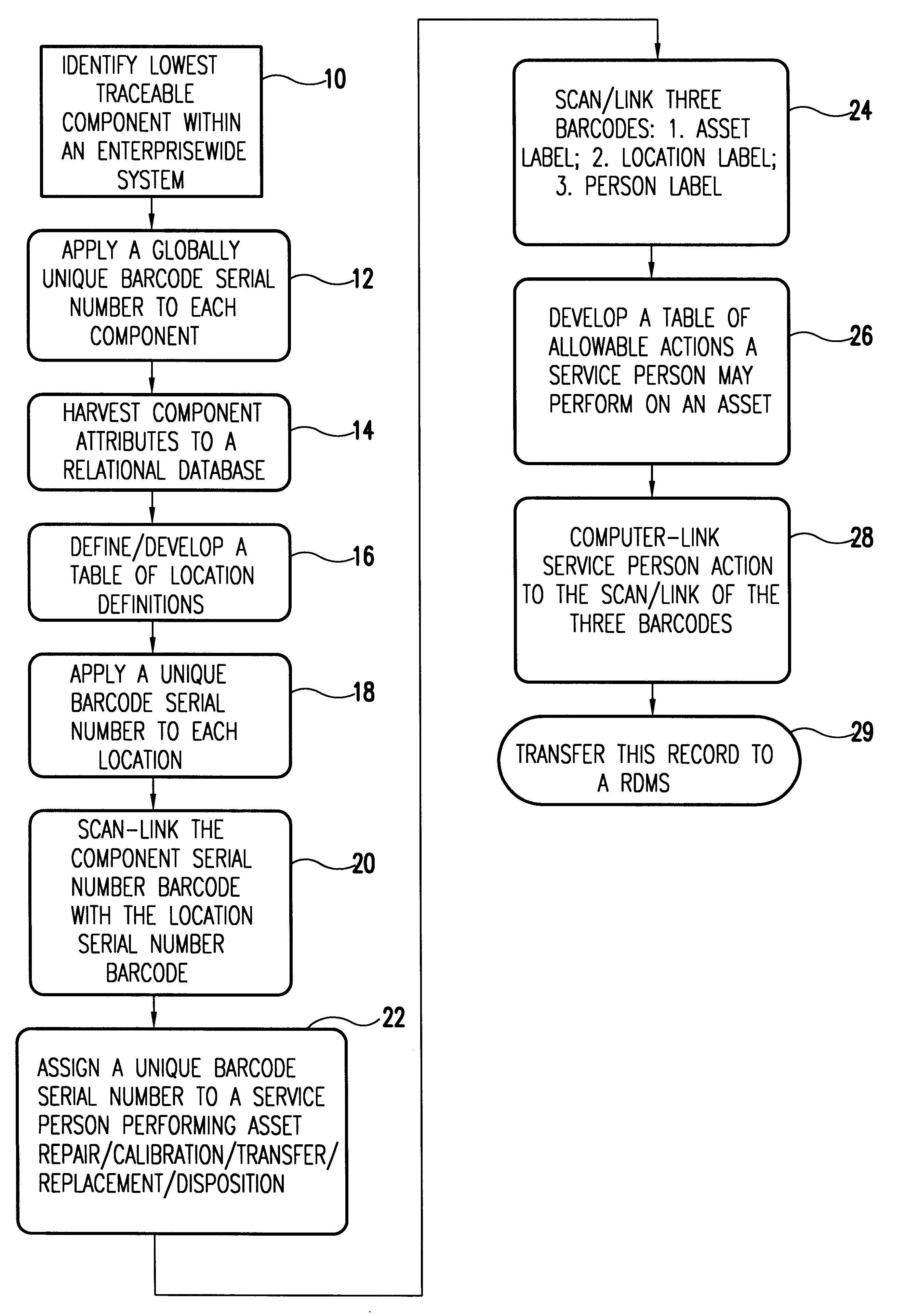
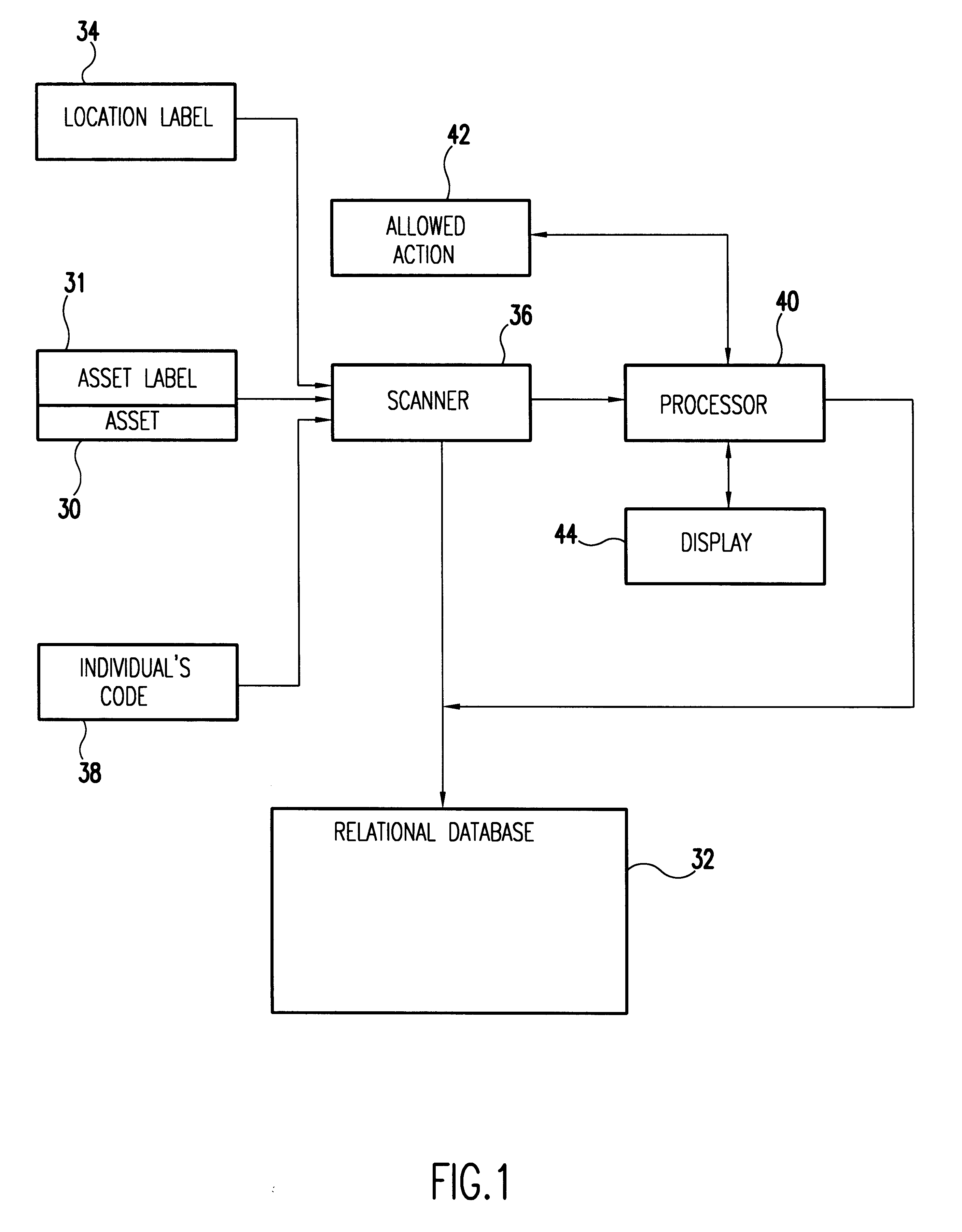
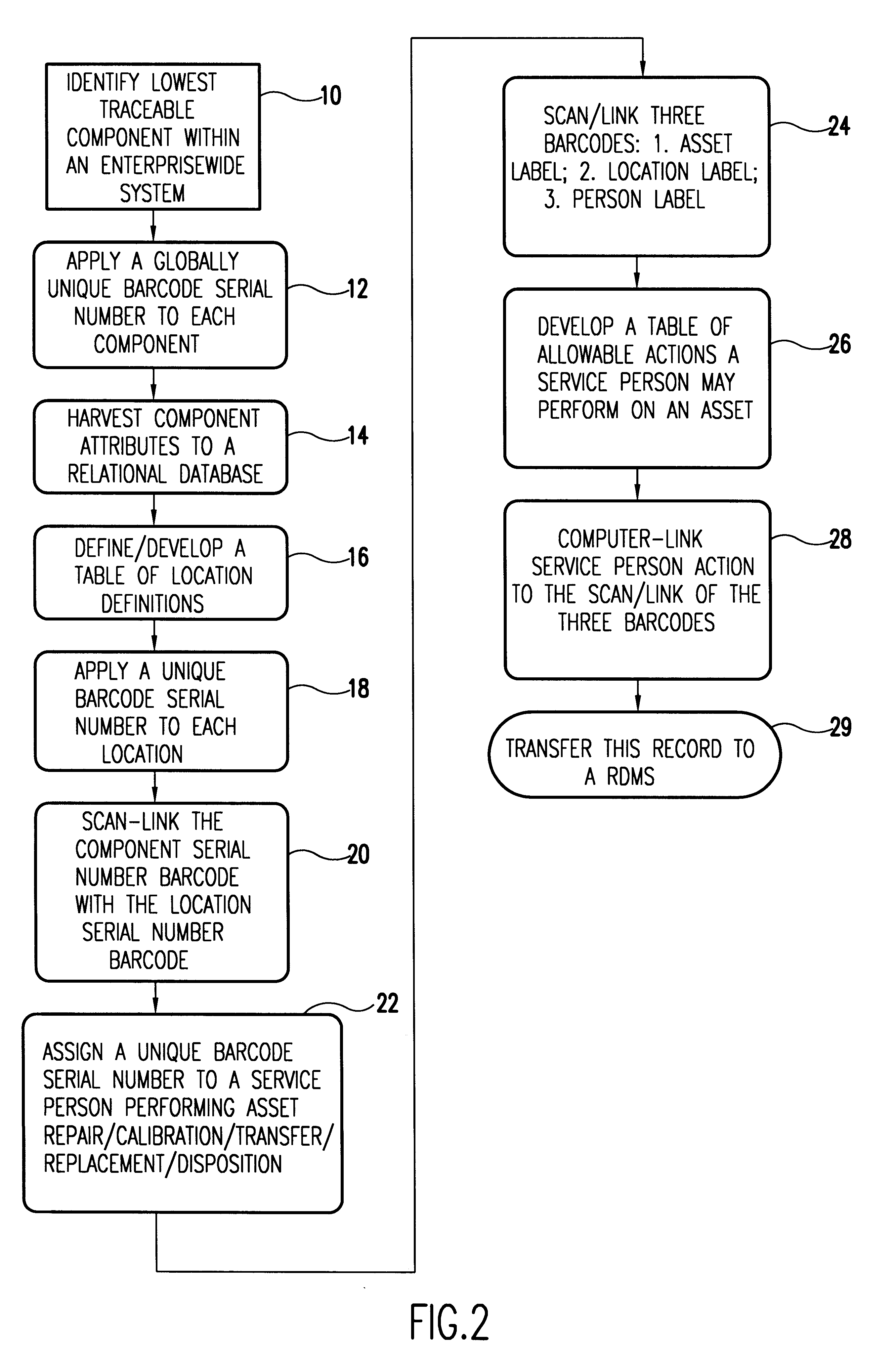
A unique data label is affixed to each tracked asset and a unique data label for each location in the enterprise, both real and virtual locations. Location history data of the asset is related to other asset data in a relational data base. Assets typically include system components down to the least repairable / replaceable unit (LRU). The data label, in the preferred embodiment of the invention, is a code label using a code that ensures each label is unique to the asset or location to which it is attached. Here the word location is an inclusive term. It includes the geographical location and the identity of the building in which the asset is housed. Location also includes the identity of the system of which a component is a part and, if relevant, location within the system. It includes also any real or virtual location of interest for subsequent analysis and is ultimately defined by the nature of the system being tracked.People assigned to install, upgrade, maintain, and do other work on the system are identified and this identifying data is entered into the data base along with each activity performed on the system and its components. Preferably, in response to a scanned asset label, a menu of allowable activities is presented so that the person assigned to do a task associated with the asset can easily make entries into the data base of the code assigned to the task performed. With asset data, asset location, and task record (including the person performing the task), entered into the relational data base, it is relatively easy to track the components of complex systems in a large enterprise over time and build complex relational records.
Owner:RATEZE REMOTE MGMT LLC +1
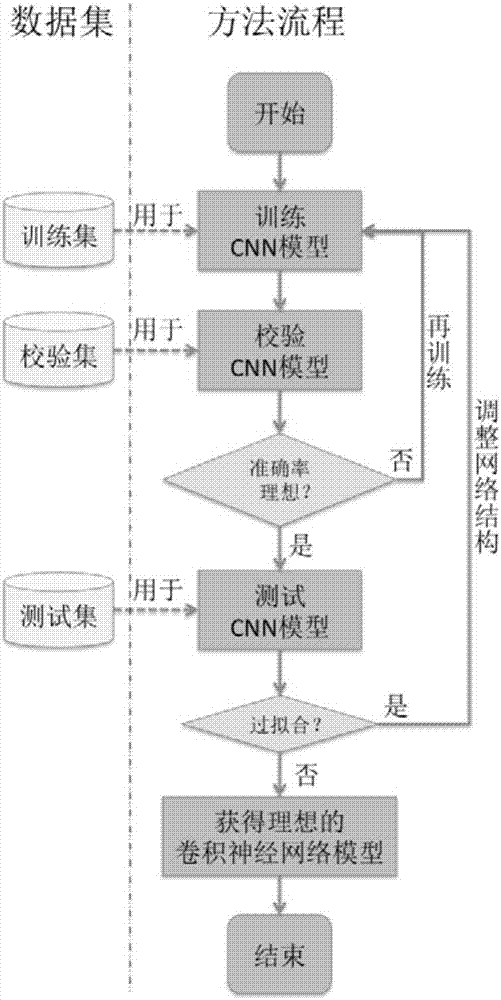
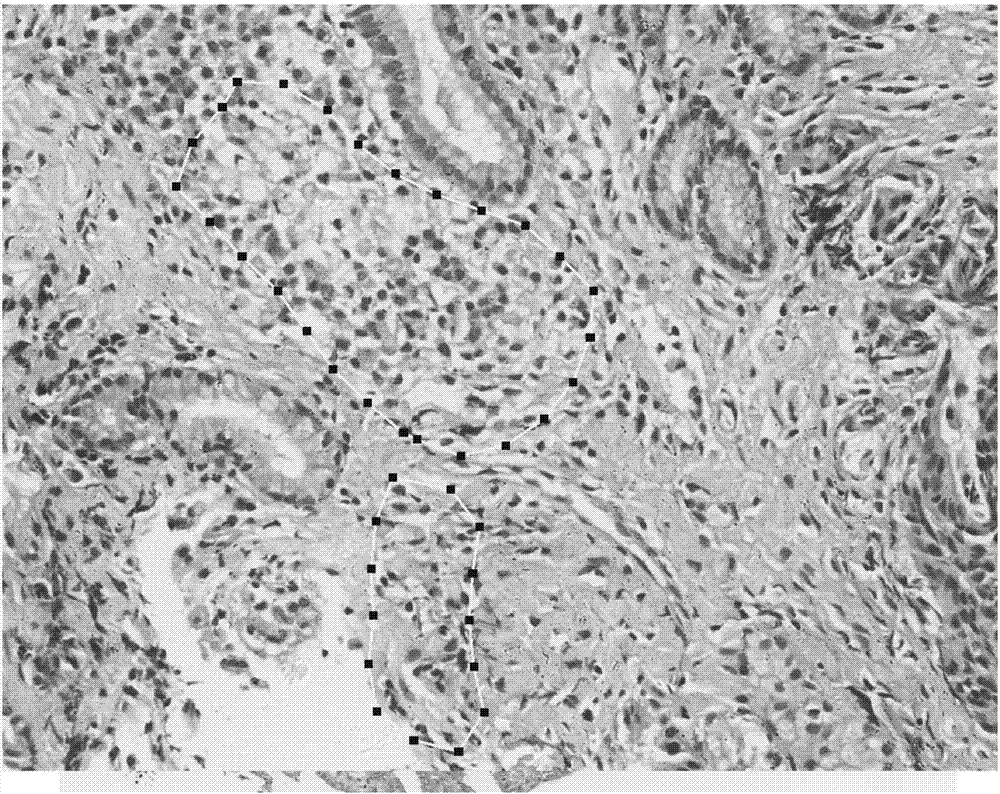
Big data deep learning-based stomach cancer pathological diagnosis support system and method
InactiveCN107368670AImprove accuracyAvoid uneven distributionImage enhancementImage analysisStomach cancerImaging data
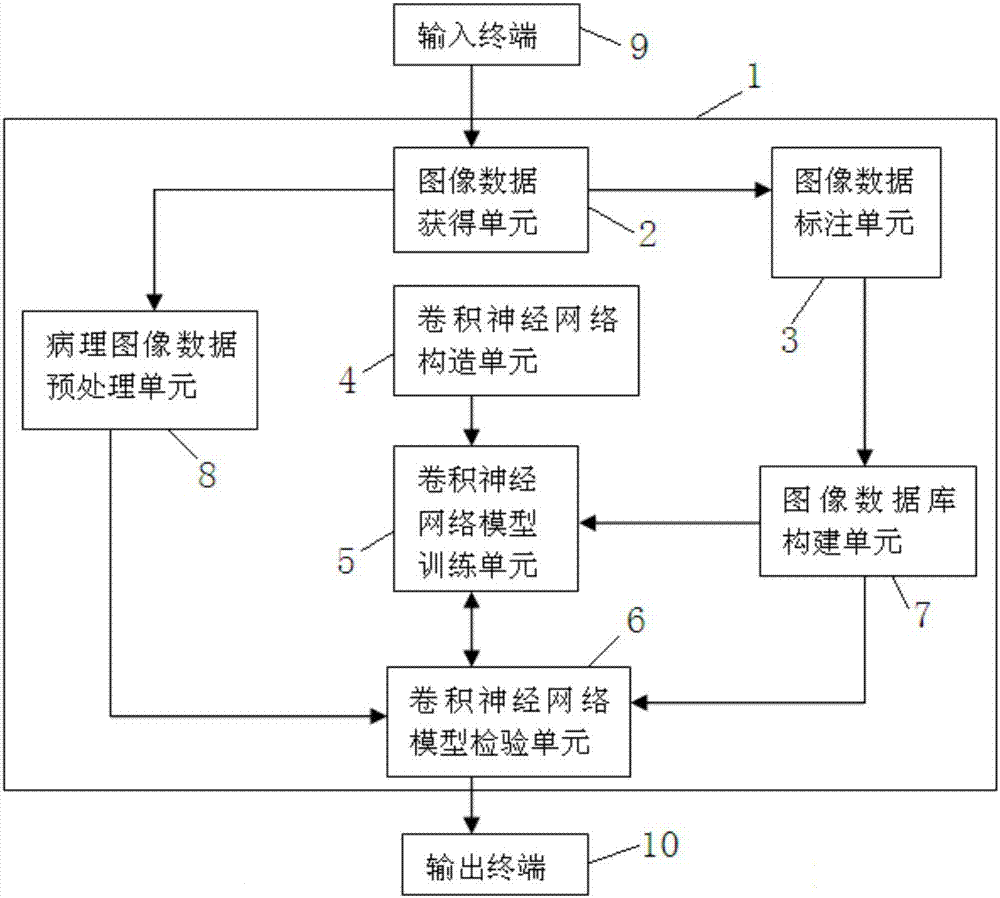
The invention discloses a big data deep learning-based stomach cancer pathological diagnosis support system and method. The system comprises an image data obtaining unit, an image data labeling unit, an image database construction unit, a convolutional neural network (CNN) construction unit and a convolutional neural network training unit, wherein the image data obtaining unit is used for obtaining stomach normal tissue slice images and pathological slice images of definite stomach cancer cases as input image data; the image data labeling unit is used for labeling the input image data; the image database construction unit is used for classifying and arranging the labeled image data provided by the image data labeling unit so as to construct a pathological image database; the convolutional neural network (CNN) construction unit is used for constructing a first convolutional neural network model; and the convolutional neural network training unit is used for obtaining an ideal convolutional neural network model. Through the stomach cancer pathological diagnosis support system and method, accurate and efficient intelligent slice reading can be realized so as to assistant the clinical stomach cancer pathological diagnosis work and improve the correctness, work efficiency and work persistent state.
Owner:万香波 +11
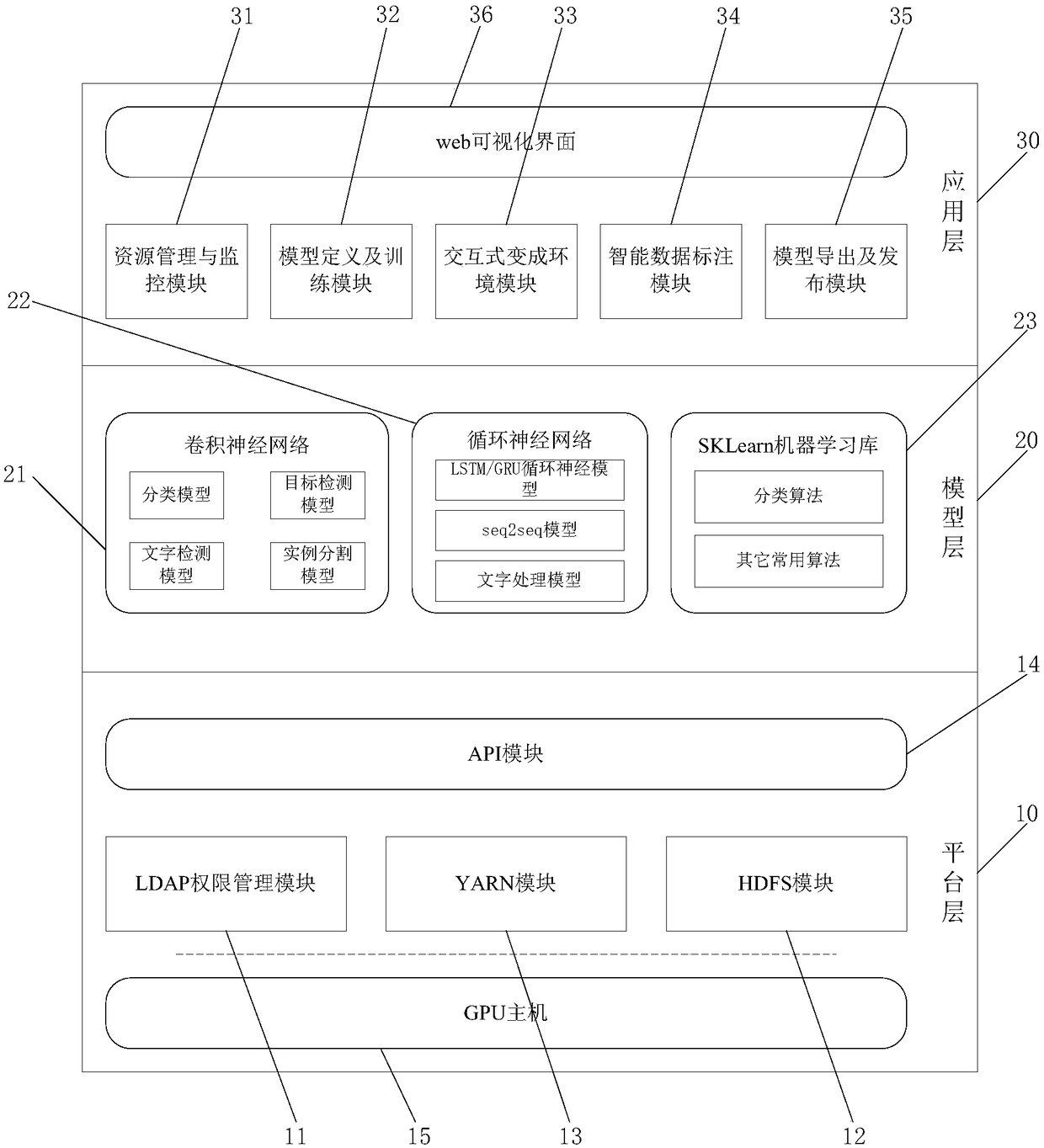
Artificial intelligent platform system based on deep learning
ActiveCN108881446AEfficient storageResource isolationTransmissionNeural learning methodsResource managementSmart data
The invention discloses an artificial intelligent platform system based on deep learning. The artificial intelligent platform system comprises a platform layer, a model layer and an application layer;the platform layer is used for permission managing, distributed storing, CPU computing resource managing, distributed computing and training and task scheduling; the model layer is used for providinga machine learning model and a deep learning model; and the application layer is used for resource managing and monitoring, model defining and training, interactive programming environment providing,intelligent data labeling and model deriving and publishing. The AI platform system is developed through an engineering means to increase the utilization rate of hardware resources of a GPU and the like, reduce the hardware input cost, help an algorithm engineer to more conveniently apply various deep learning technologies to free the algorithm engineer from tedious environment operation and maintenance, provide efficient storing of massive training data and isolate user resources, and therefore access permission control is more secure; training data and training tasks are managed in a unified mode, and the machine learning process is standardized and processed; and data labeling is automated, and the model iteration efficiency is improved.
Owner:北京深智恒际科技有限公司
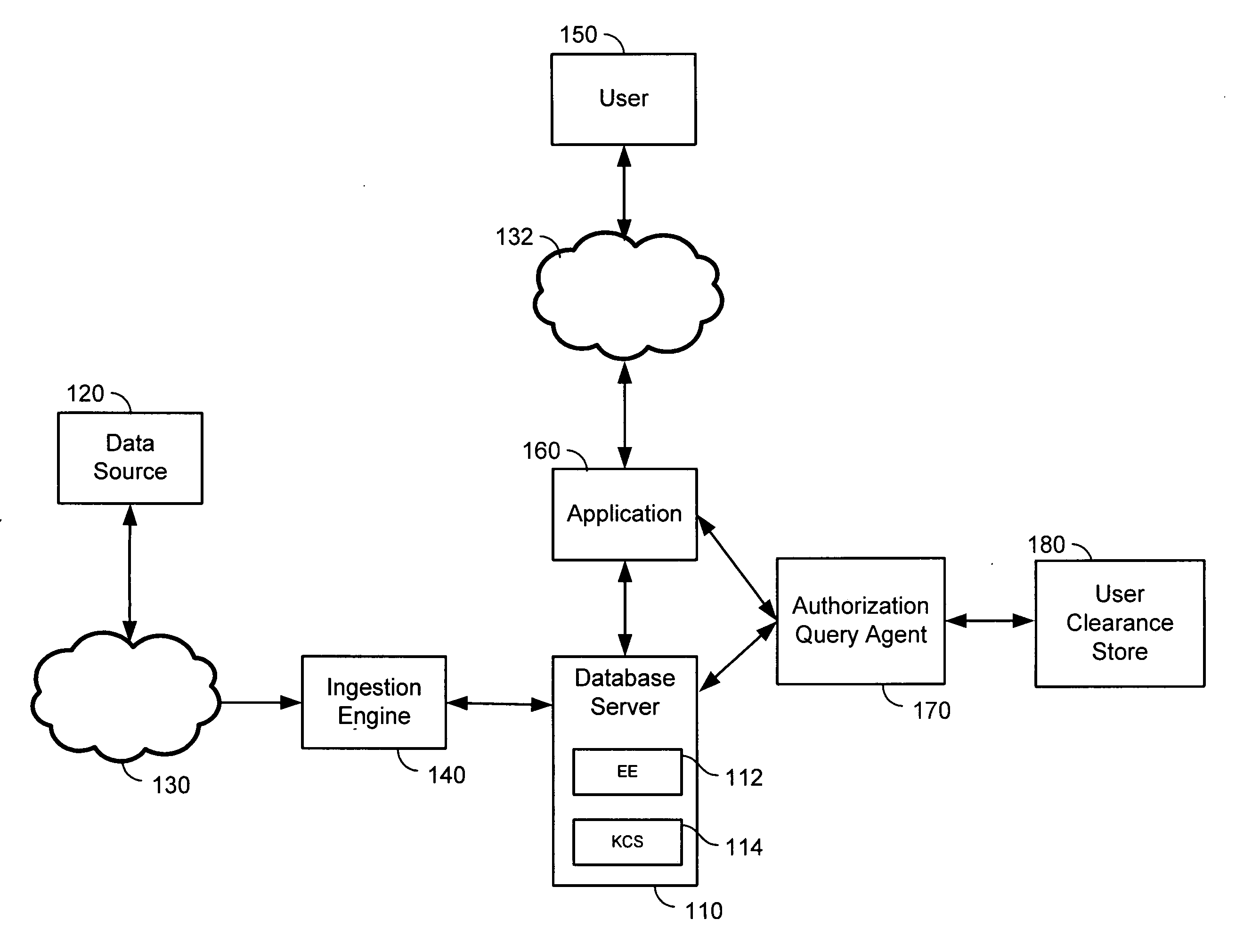
Multilevel secure database
InactiveUS20060206485A1Data processing applicationsComputer security arrangementsData streamEncryption
Row level security (RLS) and cell level security (CLS) are implemented in a database to provide secure dynamic access to database data. Encryption keys are created based on either security classification meta-data tags associated with the individual fields of an incoming data stream or on the security classification of the source network. Without prior knowledge of the incoming data security classification, the present system may generate encryption keys and, if necessary, security classification meta-data on the fly.
Owner:MICROSOFT TECH LICENSING LLC
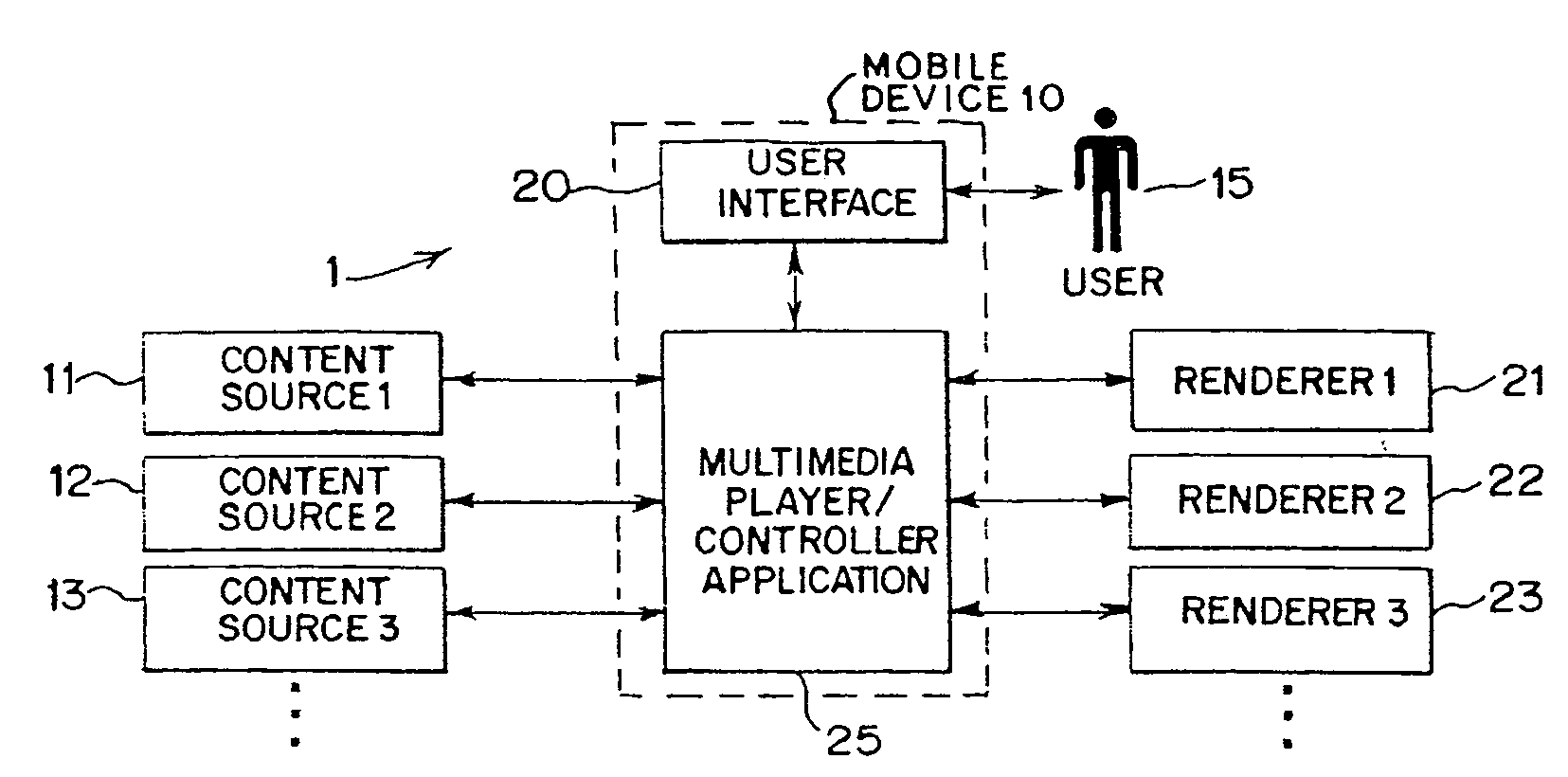
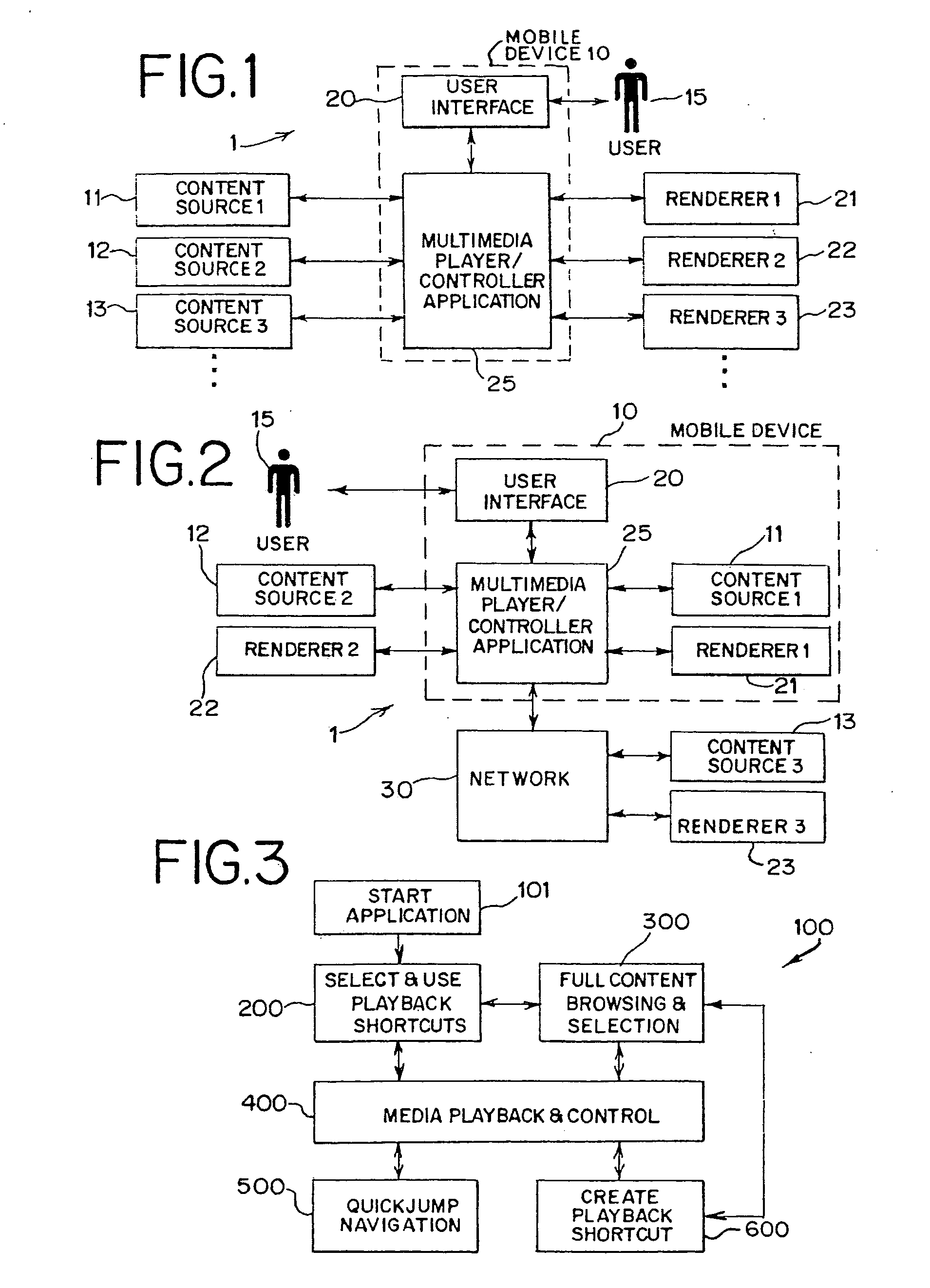
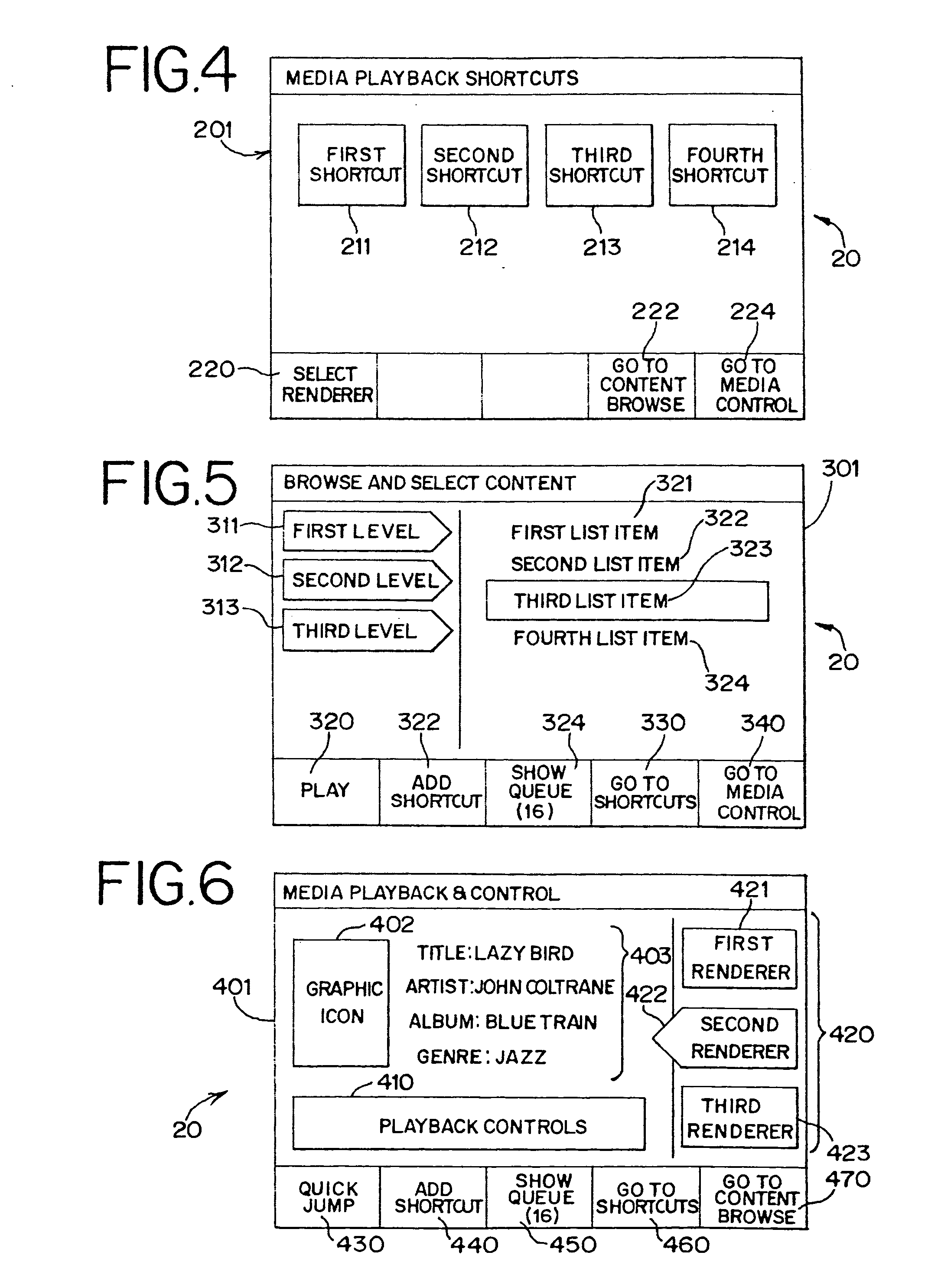
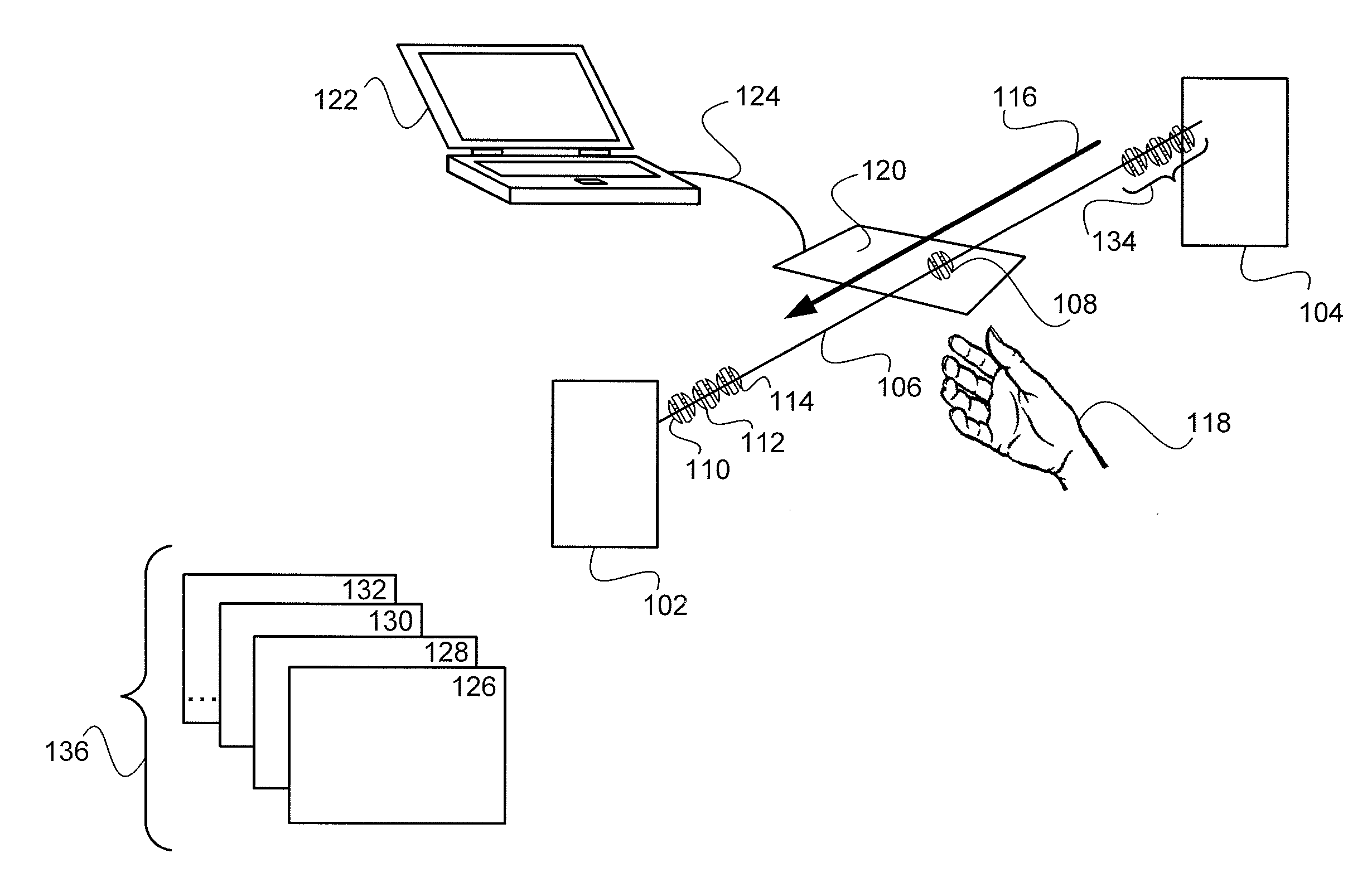
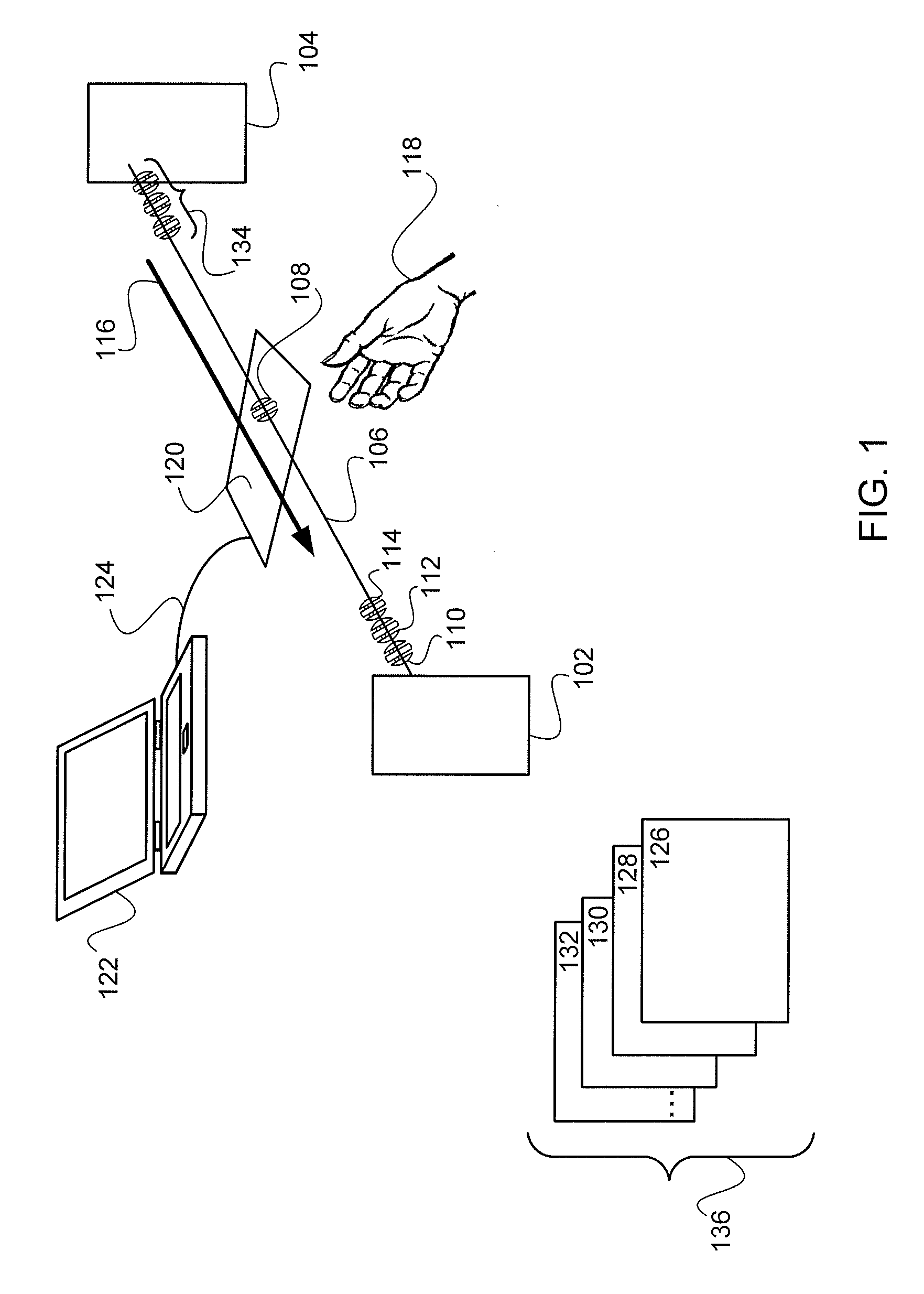
System and method for browsing, selecting and/or controlling rendering of media with a mobile device
InactiveUS20100169778A1Reduce needCathode-ray tube indicatorsSpecial data processing applicationsComputer graphics (images)Mobile device
A system and a method enable browsing, selecting and / or controlling rendering of media with a mobile device. Content from multiple content sources is aggregated, and a default content source and / or a default rendering device used for subsequent media selection are established. Individual media playback shortcuts are associated with specific default rendering devices. A user may navigate within a collection of content without a need to repeat full content browsing and selection. A user interface of a multimedia player and / or playback controller on the mobile device displays active metadata tags. By selecting an active metadata tag, the user may access a list of associated metadata tag values. By selecting a tag value, the user may select a set of content associated with the tag value for rendering.
Owner:MUNDY L STARLIGHT +3
Uhf timing system for participatory athletic events
ActiveUS20090184806A1Digital data processing detailsGymnastic exercisingTiming systemComputer science
A participatory athletic event timing system based on backscattering modulation in the UHF band and including wirelessly encoding writable data tags with participant's bib numbers or a calculated derivative thereof for timing participants in a participative athletic event, and attaching the data tags to the participant's bibs for distribution of the bibs and data tags to participants so as to eliminate the need for matching data tags with bibs and maintaining the sequenced order of the matched data tags and bibs. In a preferred embodiment, when participants register for the event, they are assigned an ID number and a bib printed with that number and having attached to the bib one or more data tag encoded in the tags memory the ID number or a calculated derivative thereof. Before the start of the event, the athlete pulls the data tag from the bib and attaches it to their shoe. Antennas suitably designed and adapted for use with the data tags in participative athletic events are used to communicate with the data tags.
Owner:CHRONOTRACK SYST
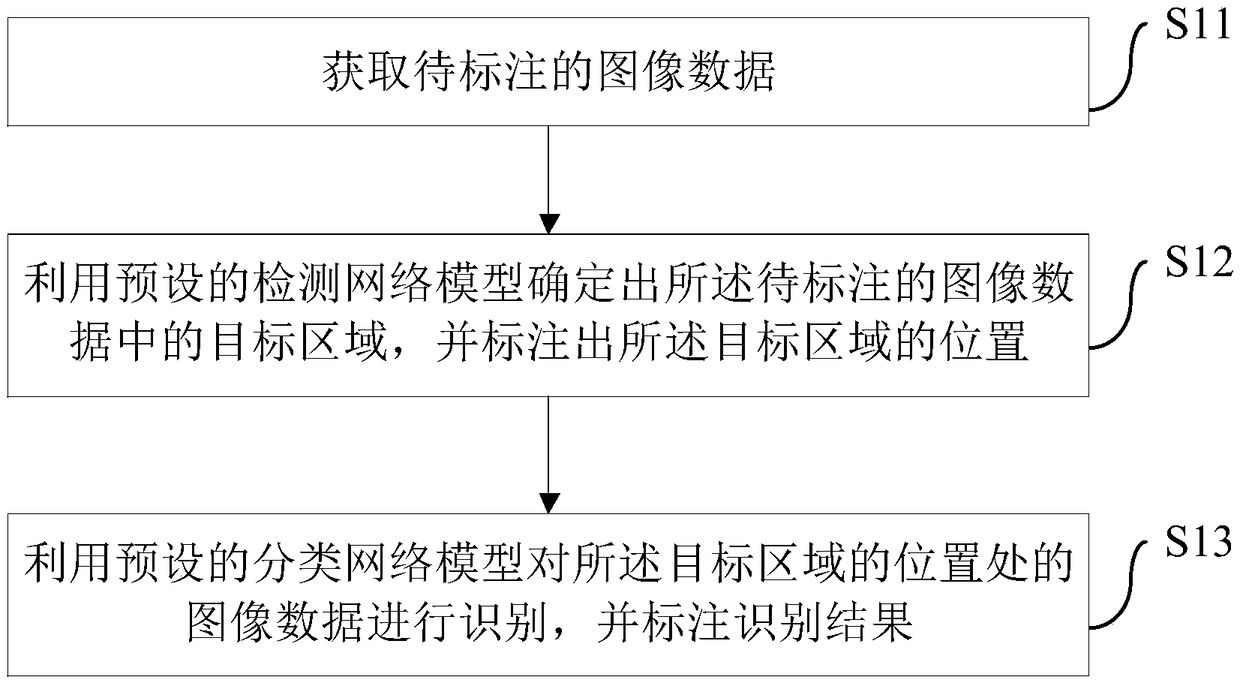
Method and apparatus for labeling image data
PendingCN108985214AEfficient automatic labelingAccurate automatic labelingImage enhancementImage analysisNetwork modelImaging data
Embodiments of the present application provide a method and an apparatus for labeling image data, wherein the method comprises the following steps: obtaining image data to be labeled; determining a target region in the image data to be labeled by using a preset detection network model, and marking a position of the target region; using the preset classification network model to recognize the imagedata at the position of the target area, and labeling the recognition result. The pre-trained detection network model is adopted to find and label the target area, and then the classification networkmodel trained in advance is used to identify and label whether the image data in the target area is the target object or not, thus solving the technical problems of poor accuracy and low efficiency in the existing data labeling methods, and achieving the technical effect of automatically labeling a large amount of image data efficiently and accurately.
Owner:杭州吉吉知识产权运营有限公司
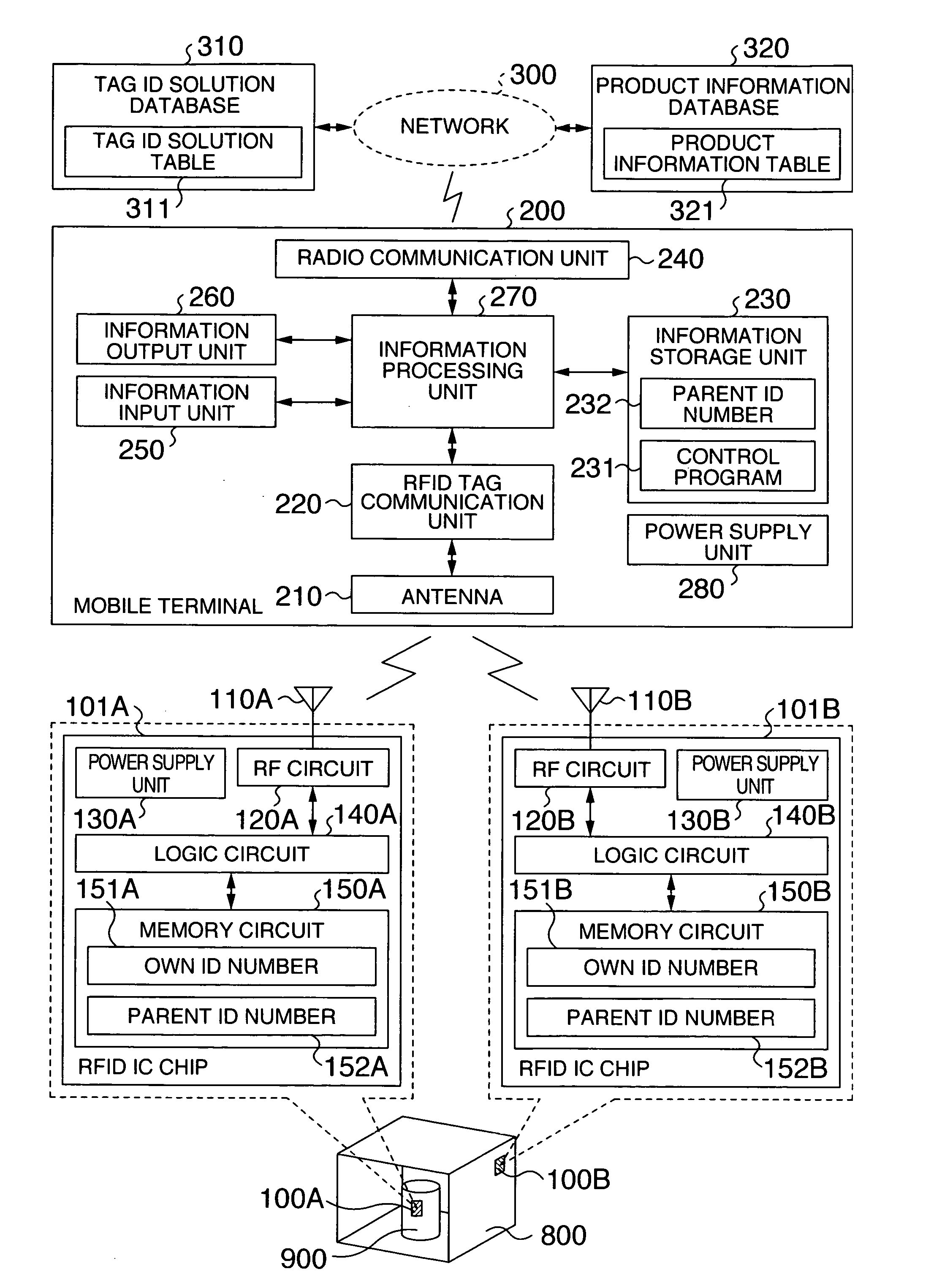
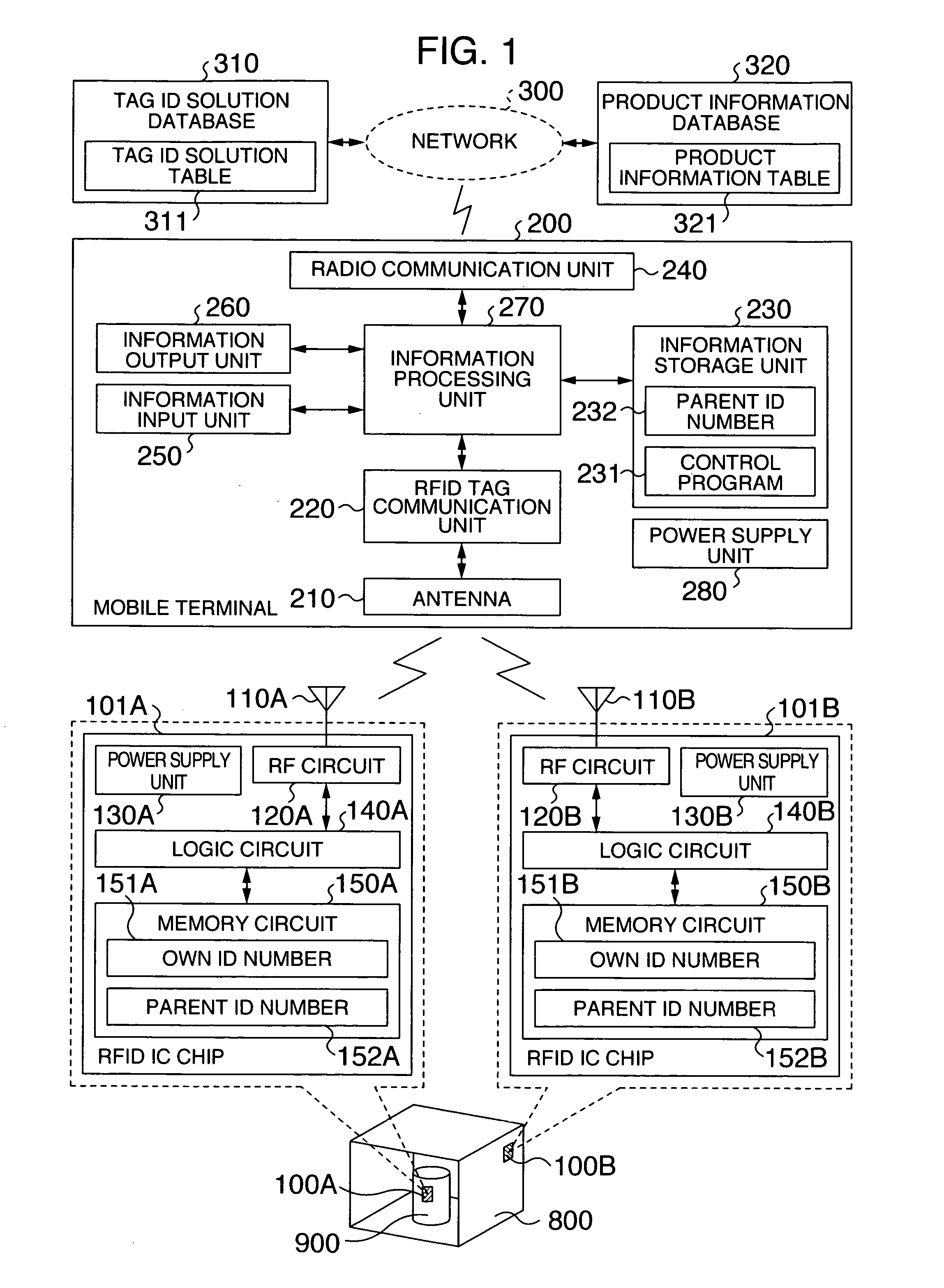
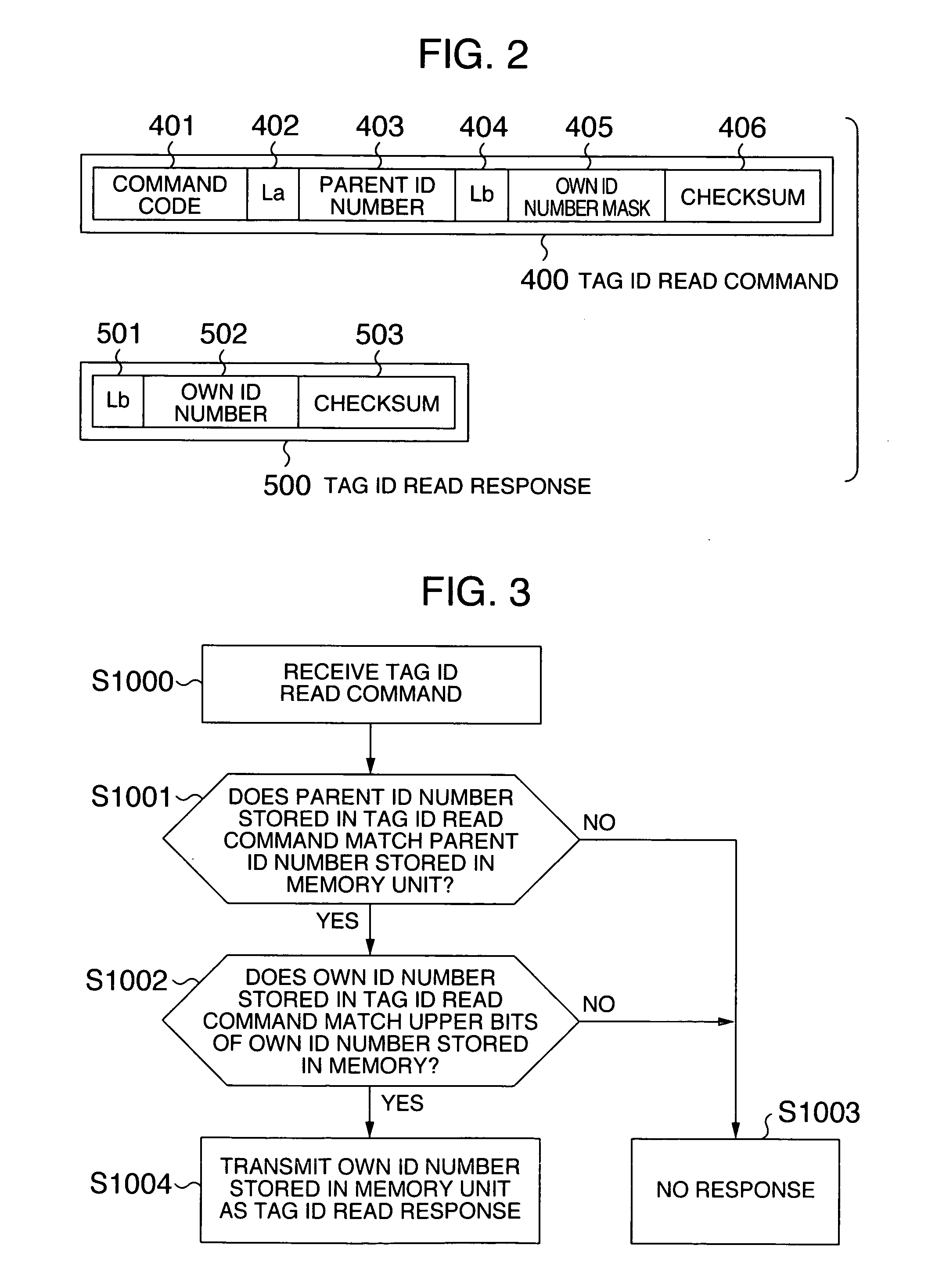
Radio frequency identification (RFID) tag, portable terminal, and server for RFID tag
InactiveUS20060145817A1Electric signal transmission systemsHand manipulated computer devicesComputer hardwareMemory circuits
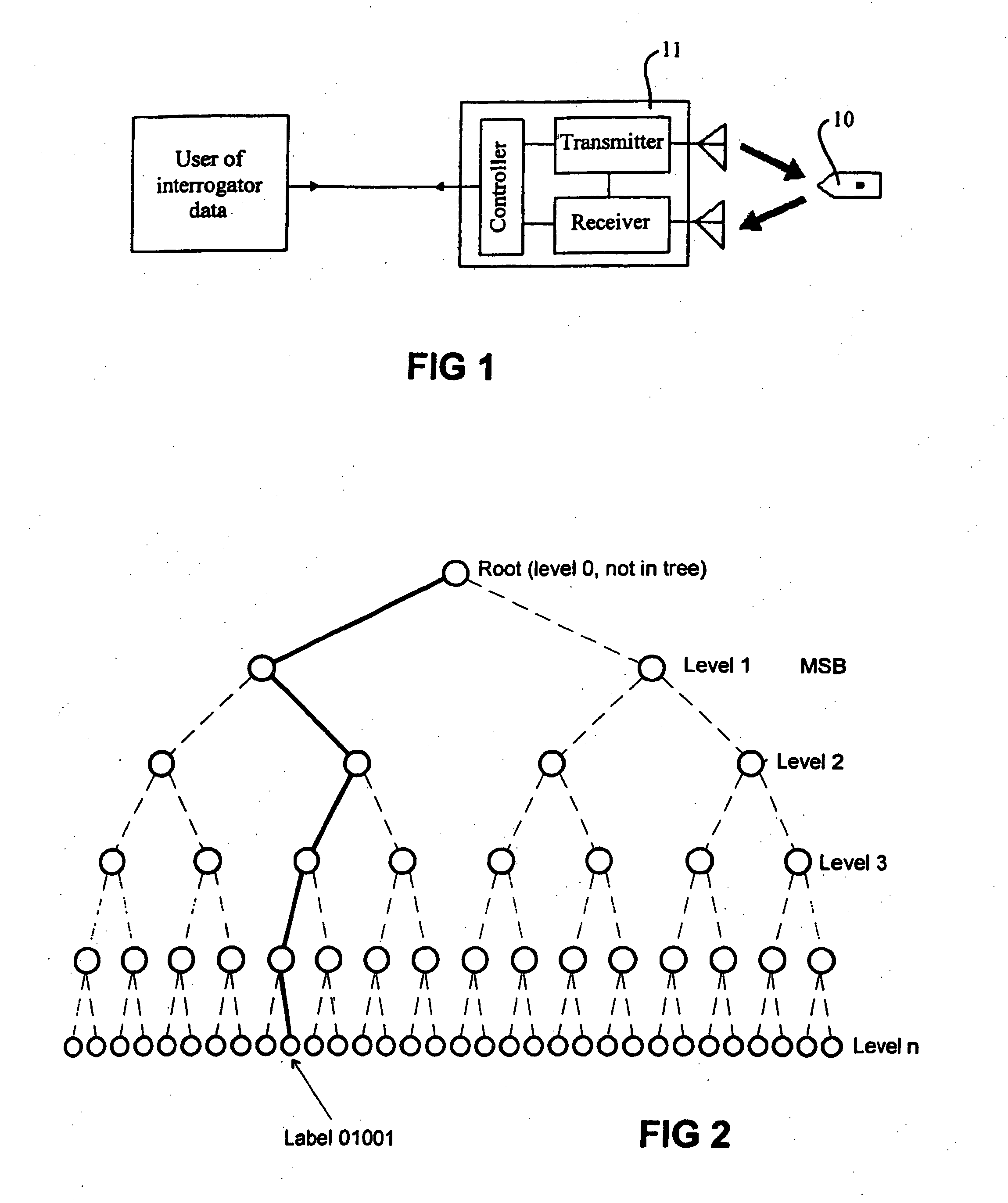
A hierarchical structure is established among a plurality of RFID tags, such that ID numbers can be read only from RFID tags which belong to a particular layer. RFID tag can control whether permission should be given to read its ID number therefrom to protect the ID number. Data held in the RFID tag can be read from the outside. RFID tag comprises a memory circuit having a function of holding data, and a logic circuit having a function of processing a control command received from outside. Memory circuit stores an own ID nmber for identifying the RFID tag itself, and a parent ID number for identifying a second RFID tag. When RFID tag receives an ID number read command which contains first data as a parameter from outside, the logic circuit outputs the own ID number to outside only when the first data matches the parent ID number.
Owner:HITACHI LTD
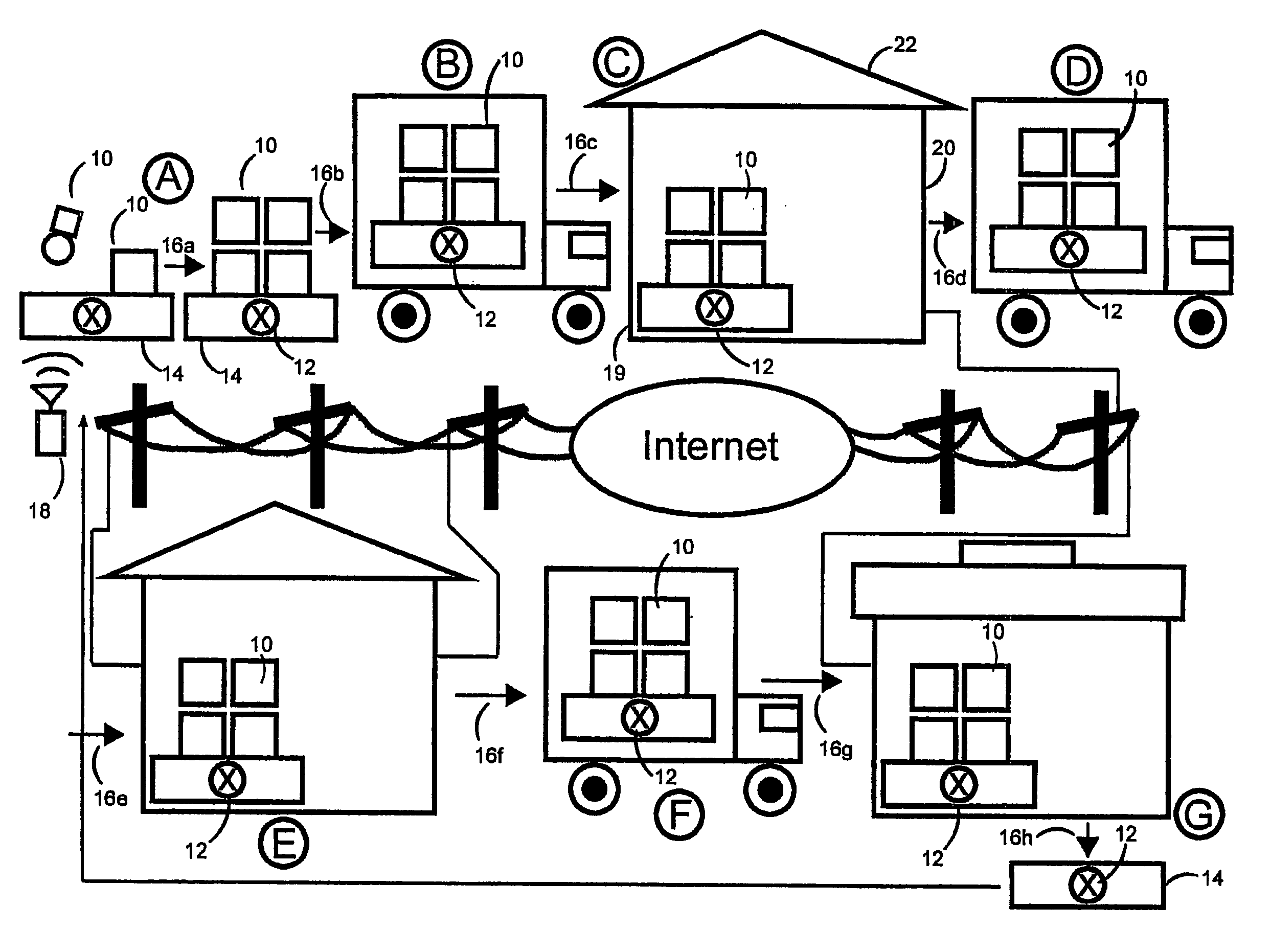
Interrogation, monitoring and data exchange using RFID tags
InactiveUS20050219039A1Electric signal transmission systemsDigital data processing detailsTransceiverComputer science
A method and apparatus for identification and monitoring of, and obtaining data relating to, products moving along a distribution path, including at least one RFID tag mountable to a product, or product carrier, and a plurality of interrogators spaced apart along the distribution path, wherein each interrogator of the plurality of interrogators cooperates in RF communication with the RFID tag when the RFID tag is in proximity to the each interrogator along the distribution path. Each interrogator interrogates the RFID tag during the RF communication so as to obtain unique data, unique to the RFID tag. The RFID tag and each interrogator each includes a transceiver and memory, the memory.
Owner:IDENTEC SOLUTIONS INC
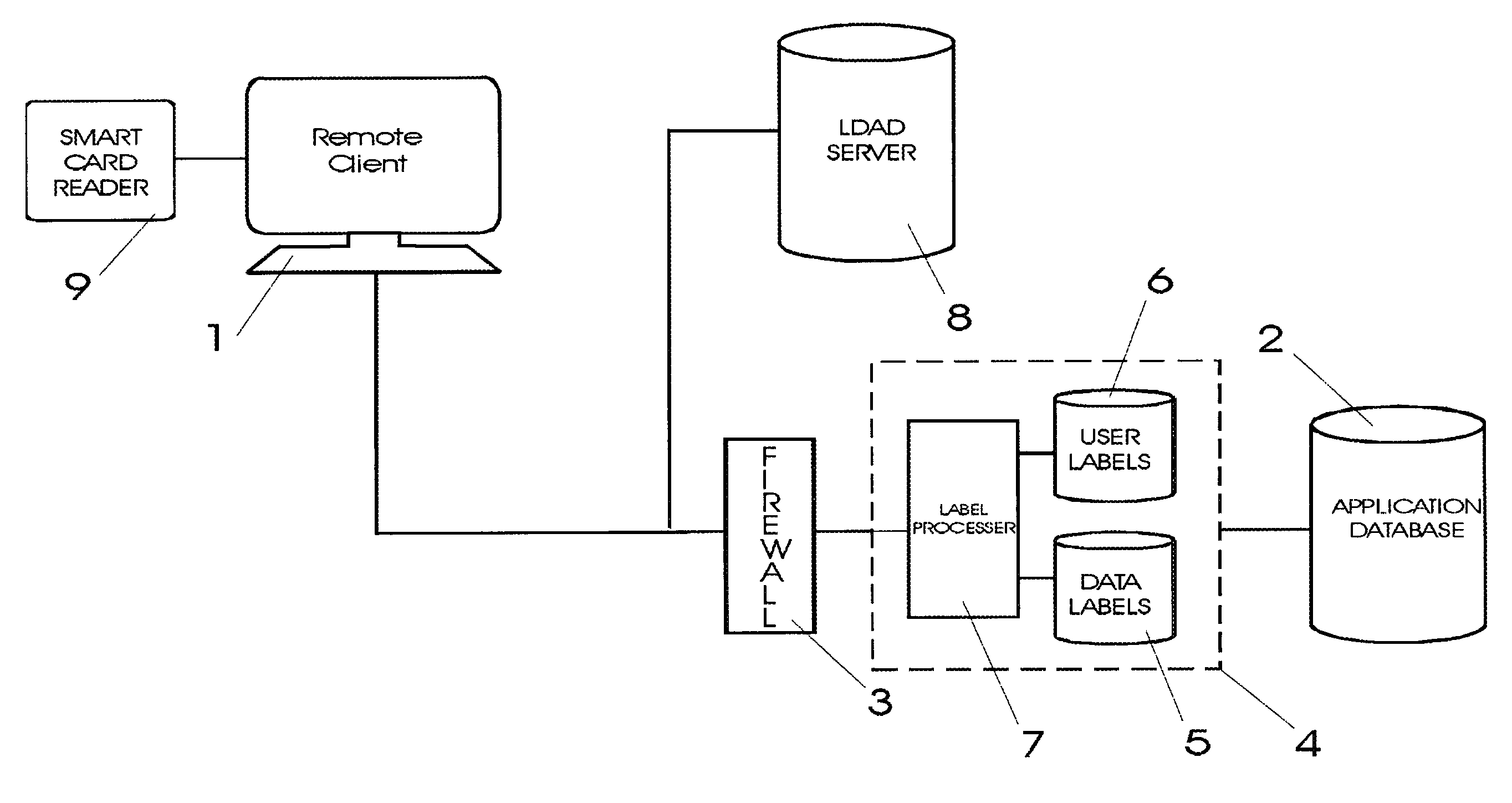
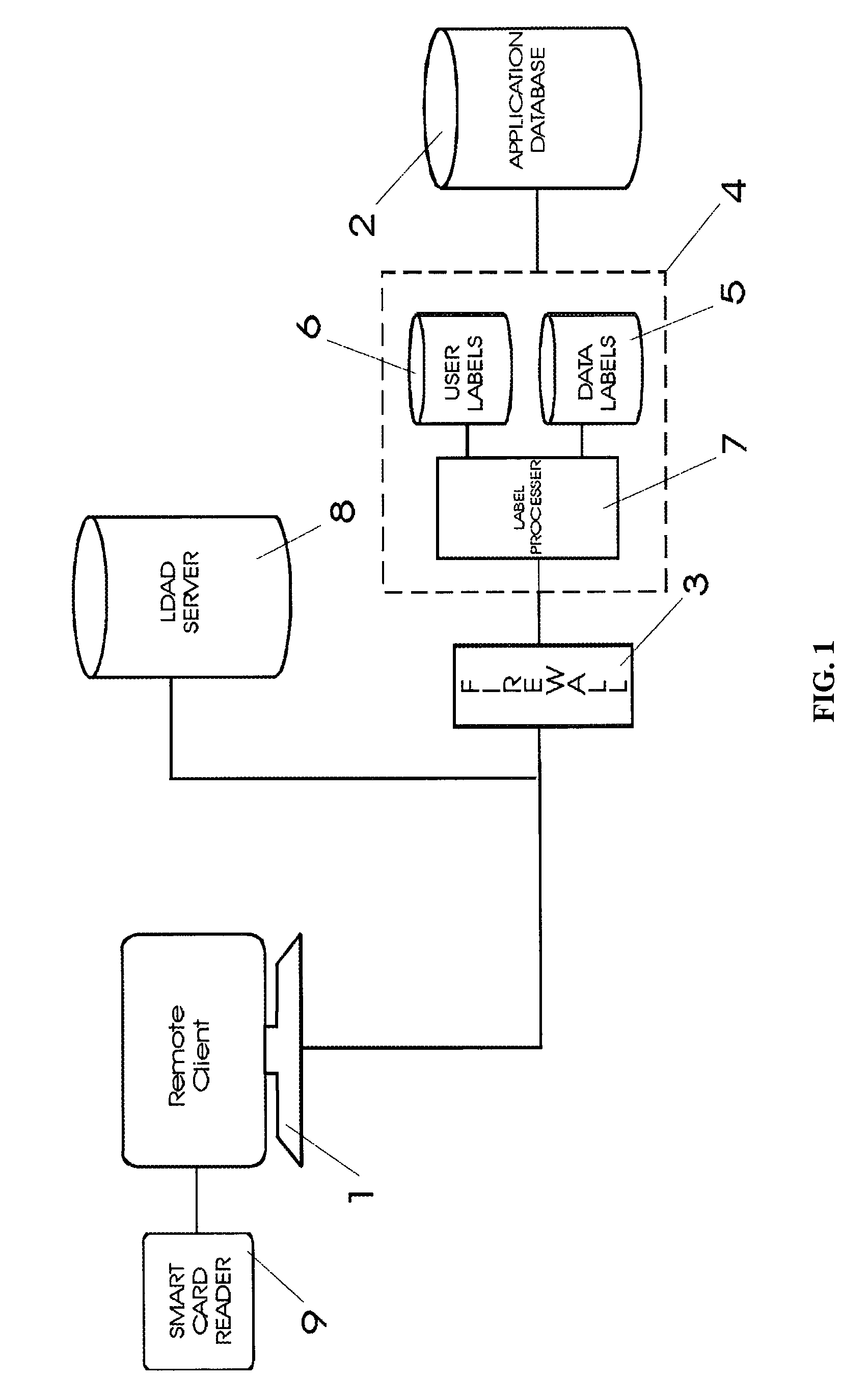
Multi-level and multi-category data labeling system
A security apparatus and method that provides Multi-Level and Multi-Category Mandatory Access Control (MAC) for controlling access to data within a database at the granularity of the data record. The access control mechanism is implemented so that it has no impact on the database. A standard labeling technology is used in which access to data is dependent on the label of the accessing entity and the label of the data being accessed. The data labels designate security access requirements for data within the database and are stored or generated in a label server that intercepts access requests to the database from remote users. User labels define user access rights and are retrieved or generated and linked to all access requests. The label server compares the user labels linked to an access request with the data label for the data requested to determine if user access is granted or denied.
Owner:FLYNTZ TERENCE T
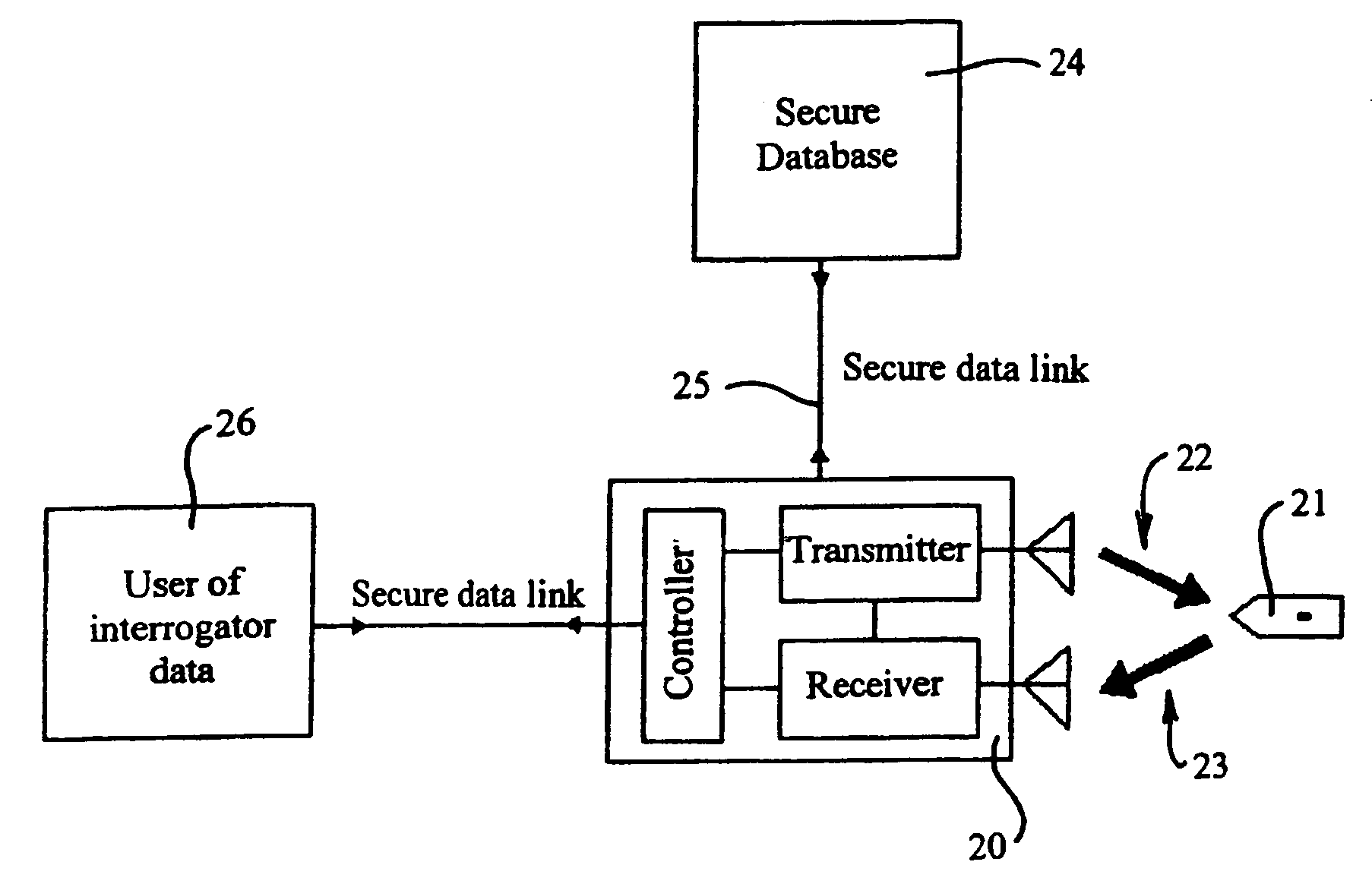
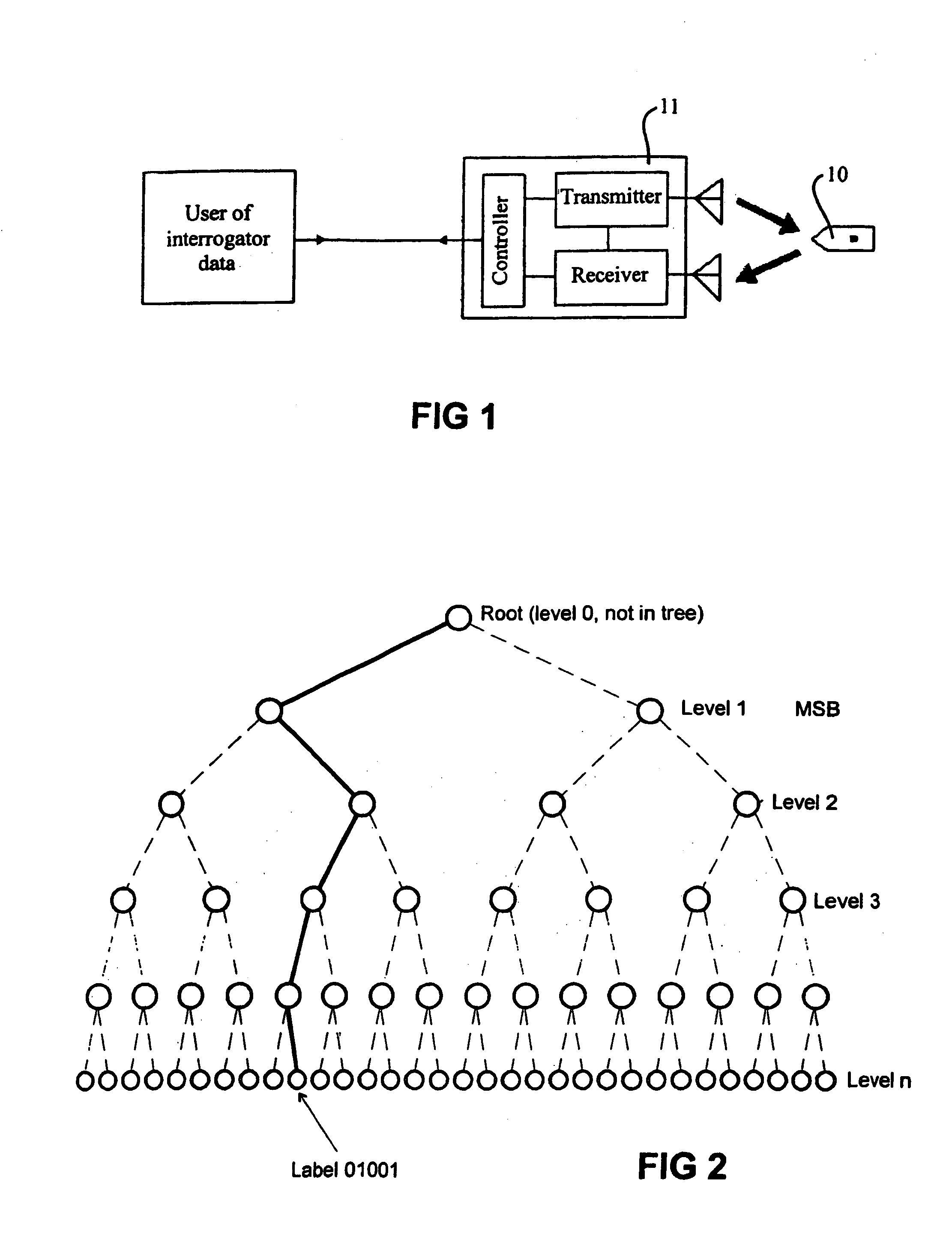
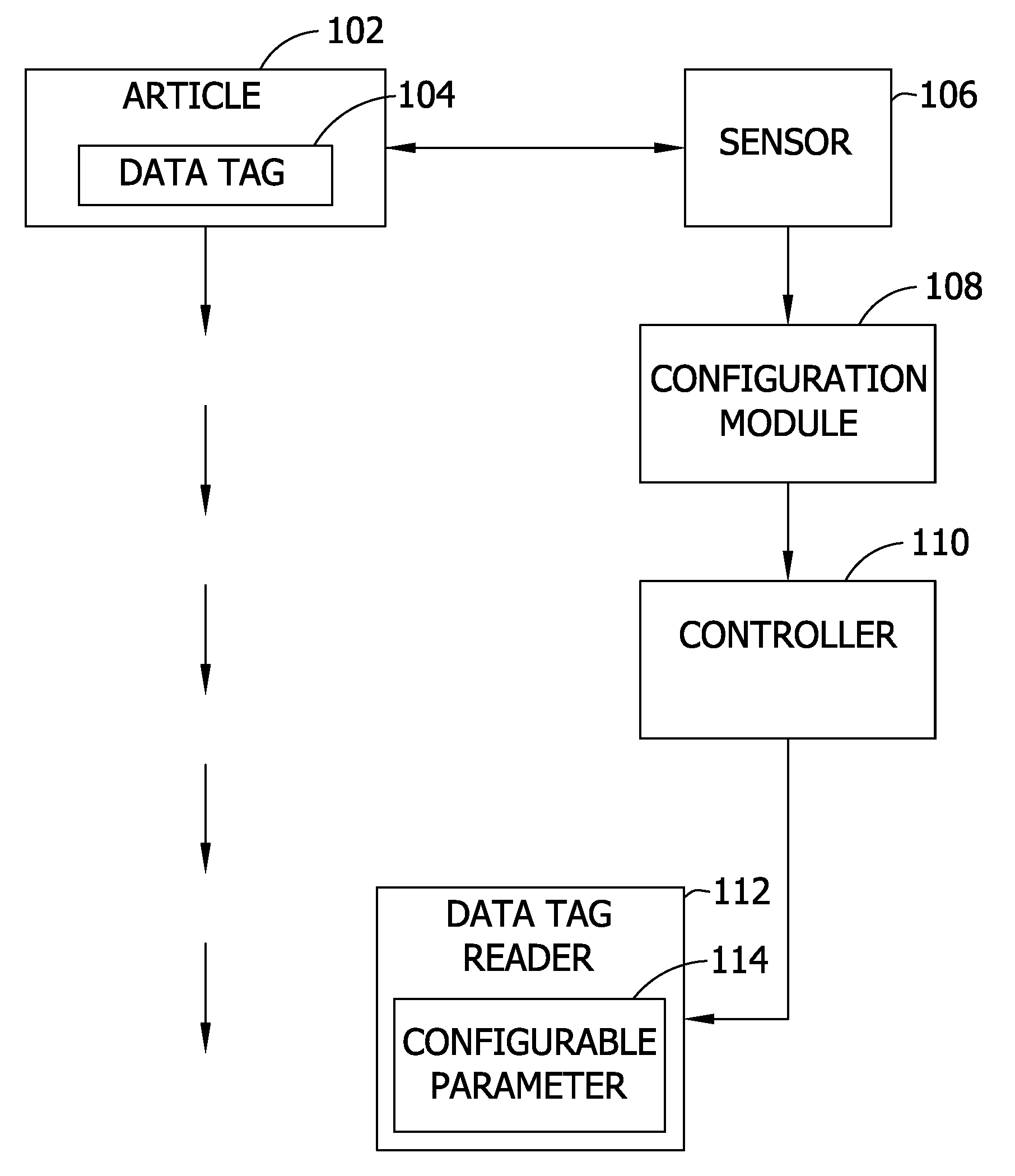
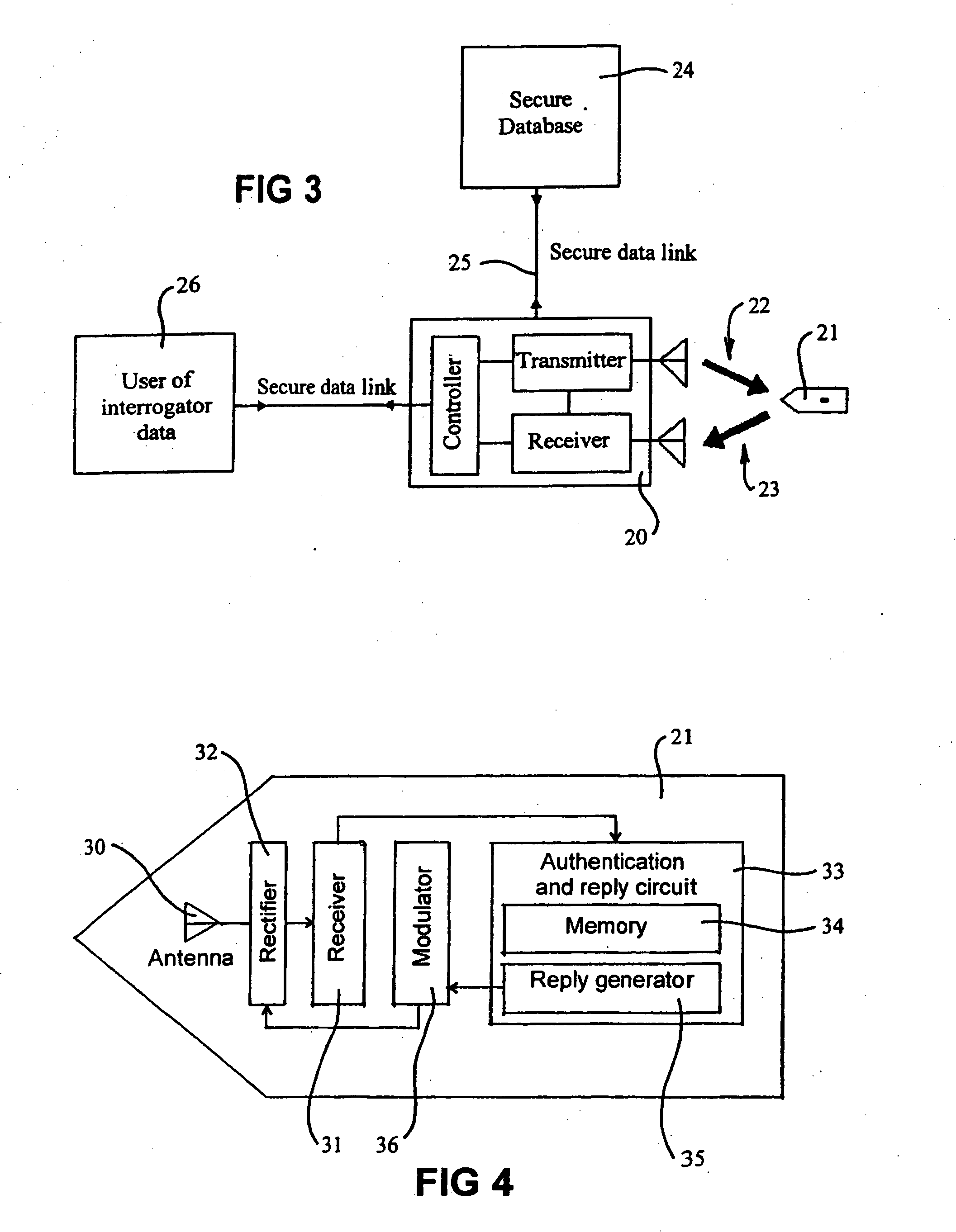
Secure data tagging systems
InactiveUS7187267B2Defeat effortSimple and low cost tagElectric signal transmission systemsMultiple keys/algorithms usageSecure communicationData stream
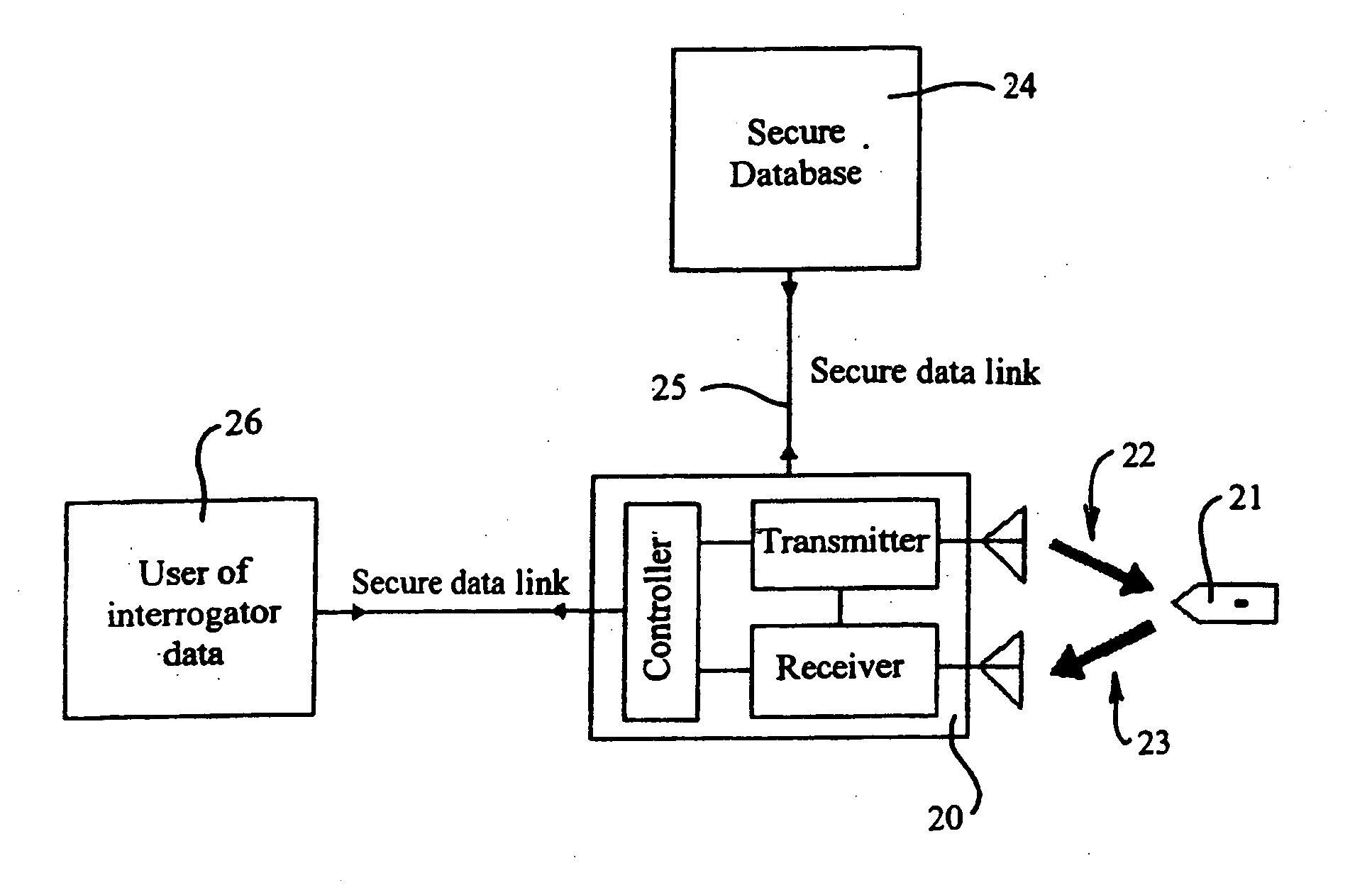
A system is disclosed for secure communication between an interrogator and an RFID tag. The system includes means for singulating the tag in a population of RFID tags and means for extracting from the tag, identity data adapted to uniquely identify the tag. The system further includes means for securely communicating the identity data to a secure database, means for providing authentication data by the database and means for securely communicating the authenticating data to the interrogator. The system also includes means for providing a further communication between the tag and the interrogator, and wherein at least one stream of data between the tag and the interrogator includes random data generated via a random physical process. The tag and database may each include means for maintaining a count of secure authentications. The count may be separately maintained by the tag and database and may be incremented following each secure authentication. A method for secure communication between an interrogator and an RFID tag is also disclosed.
Owner:TAGSYS
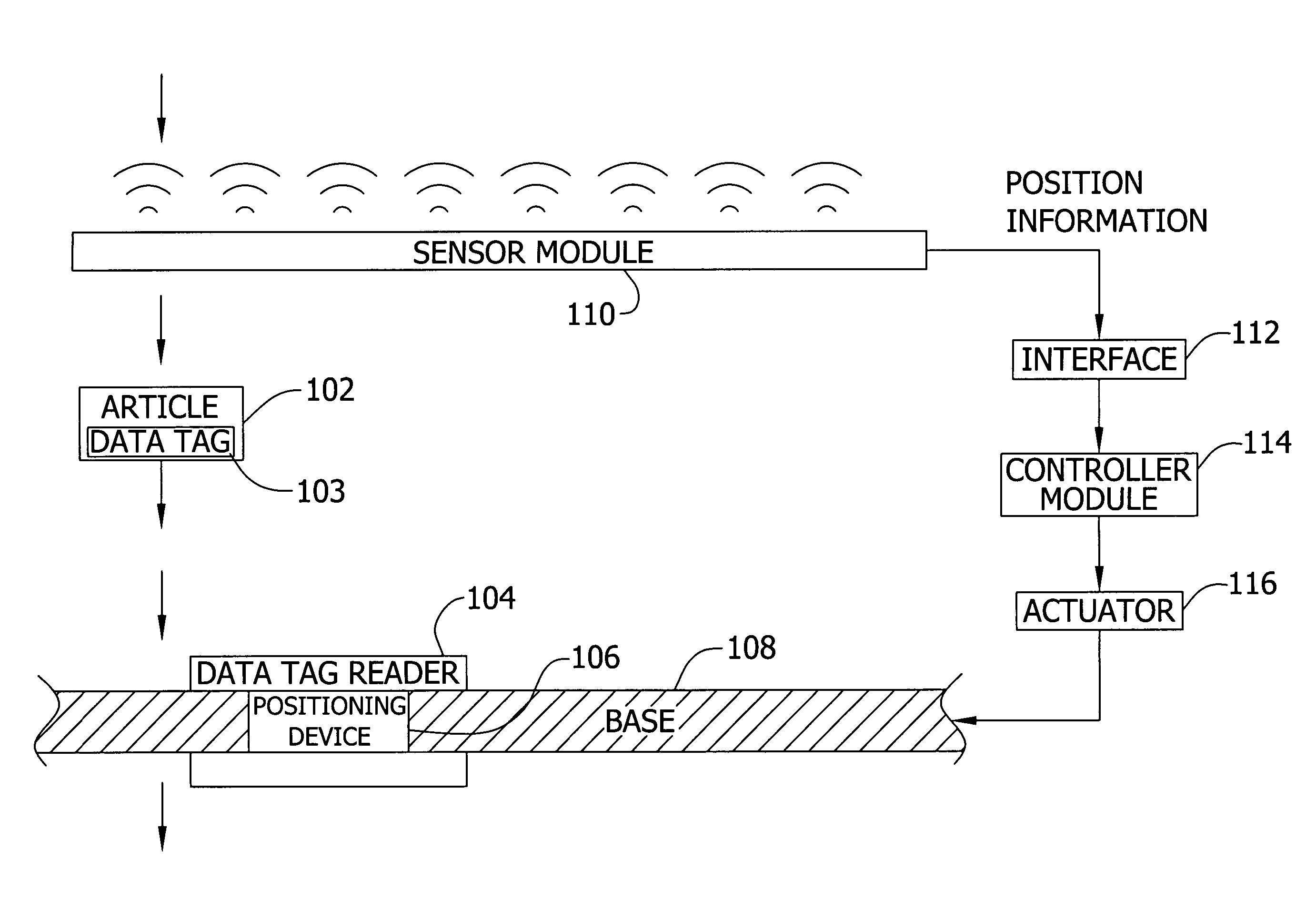
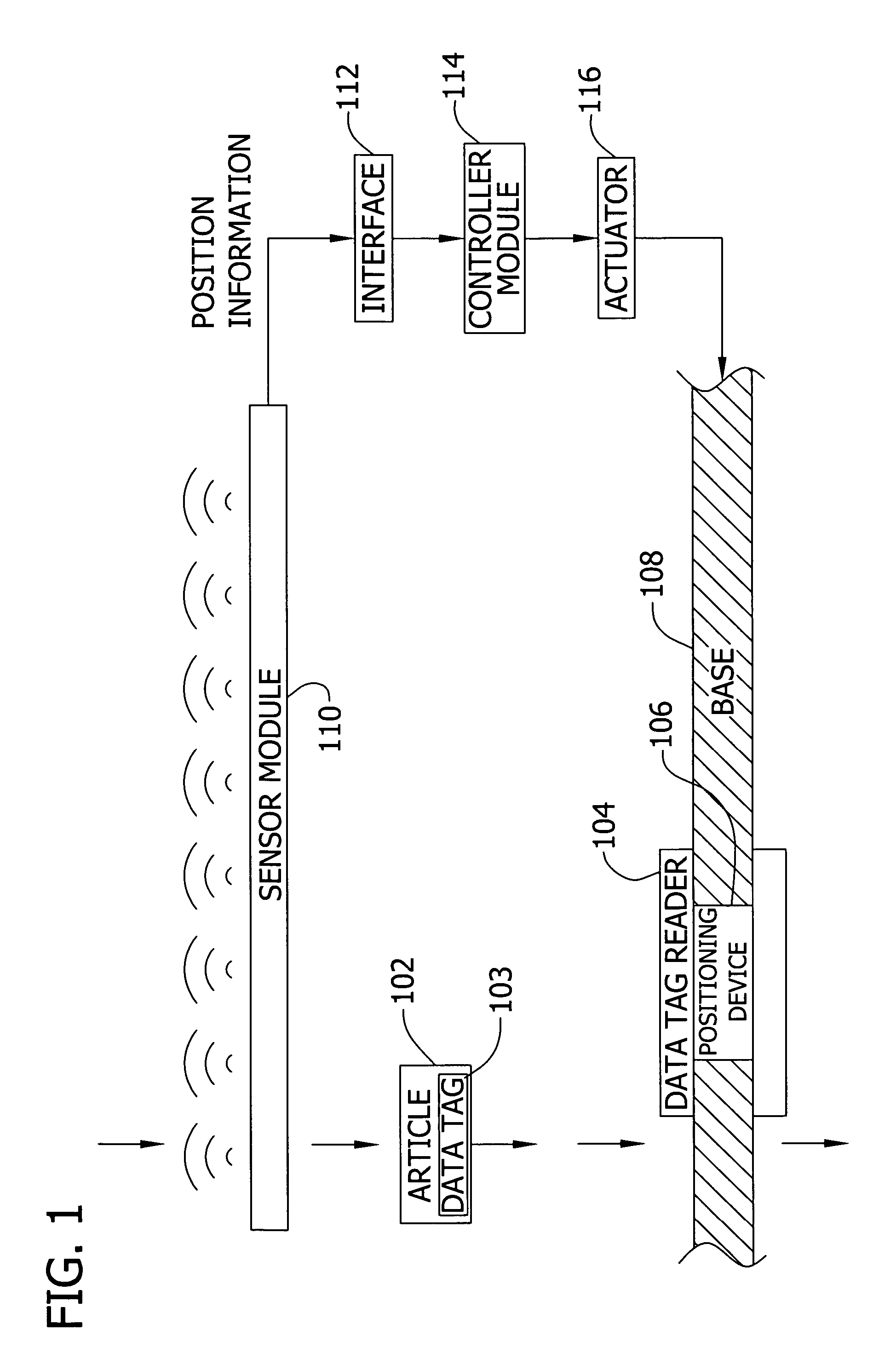
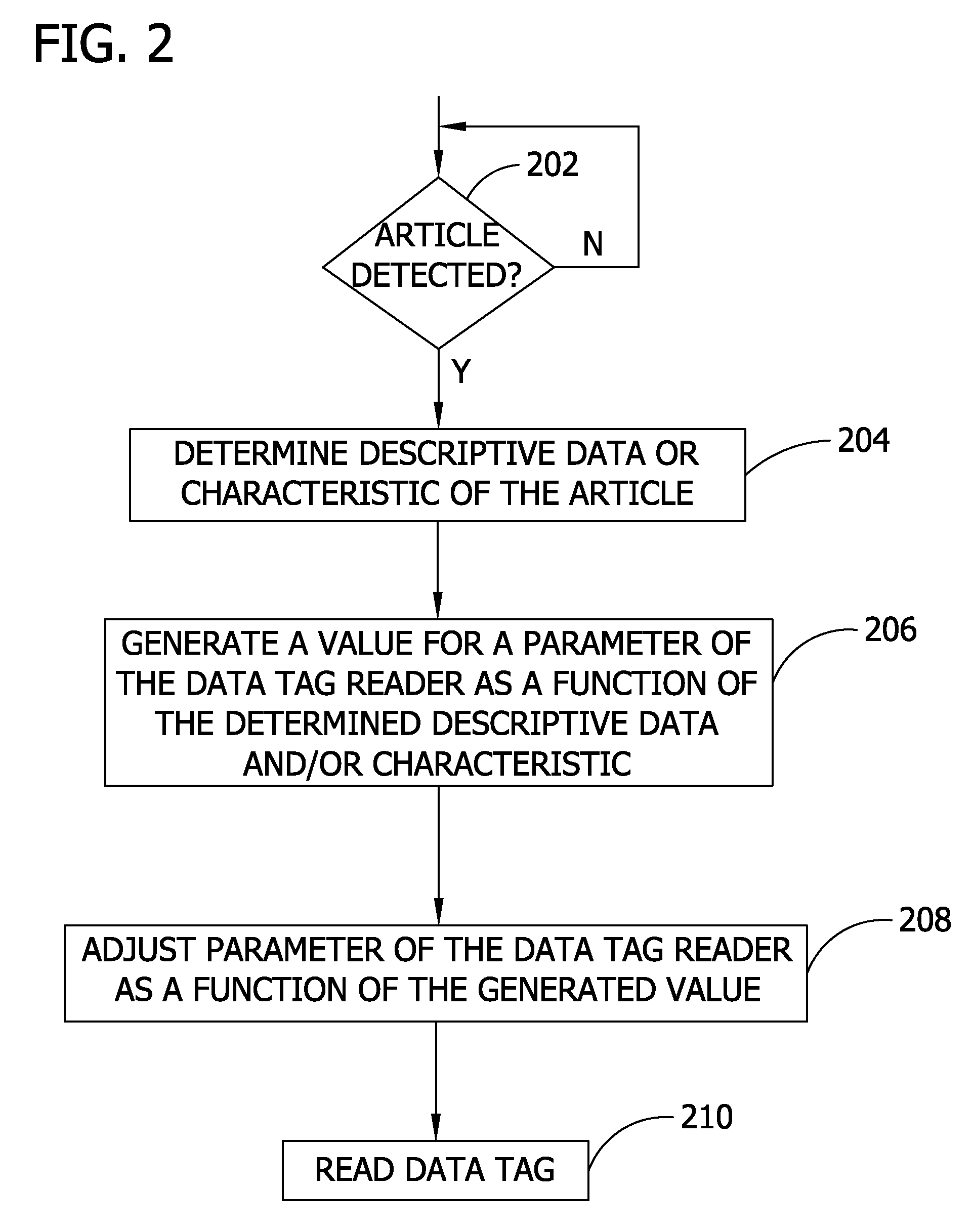
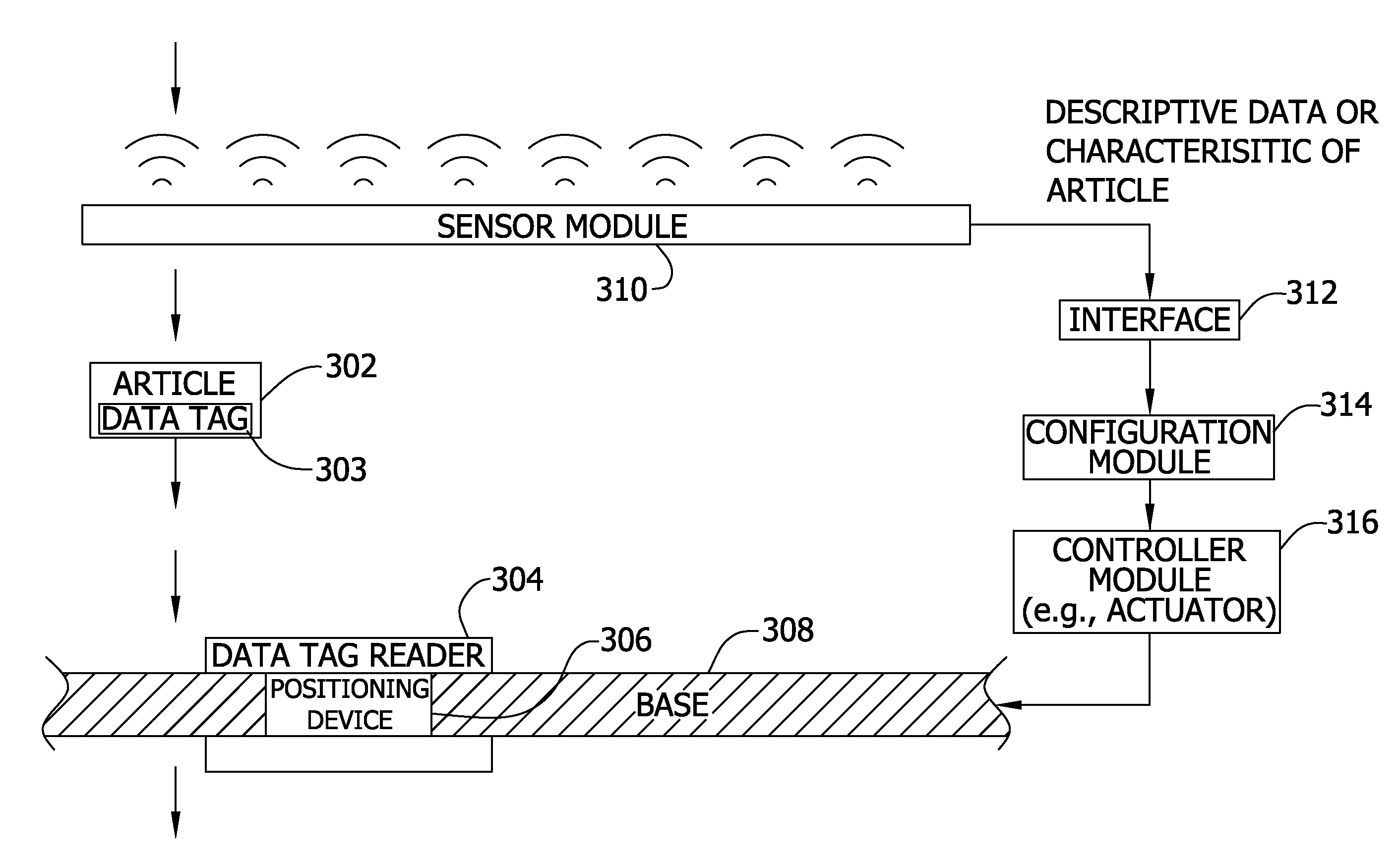
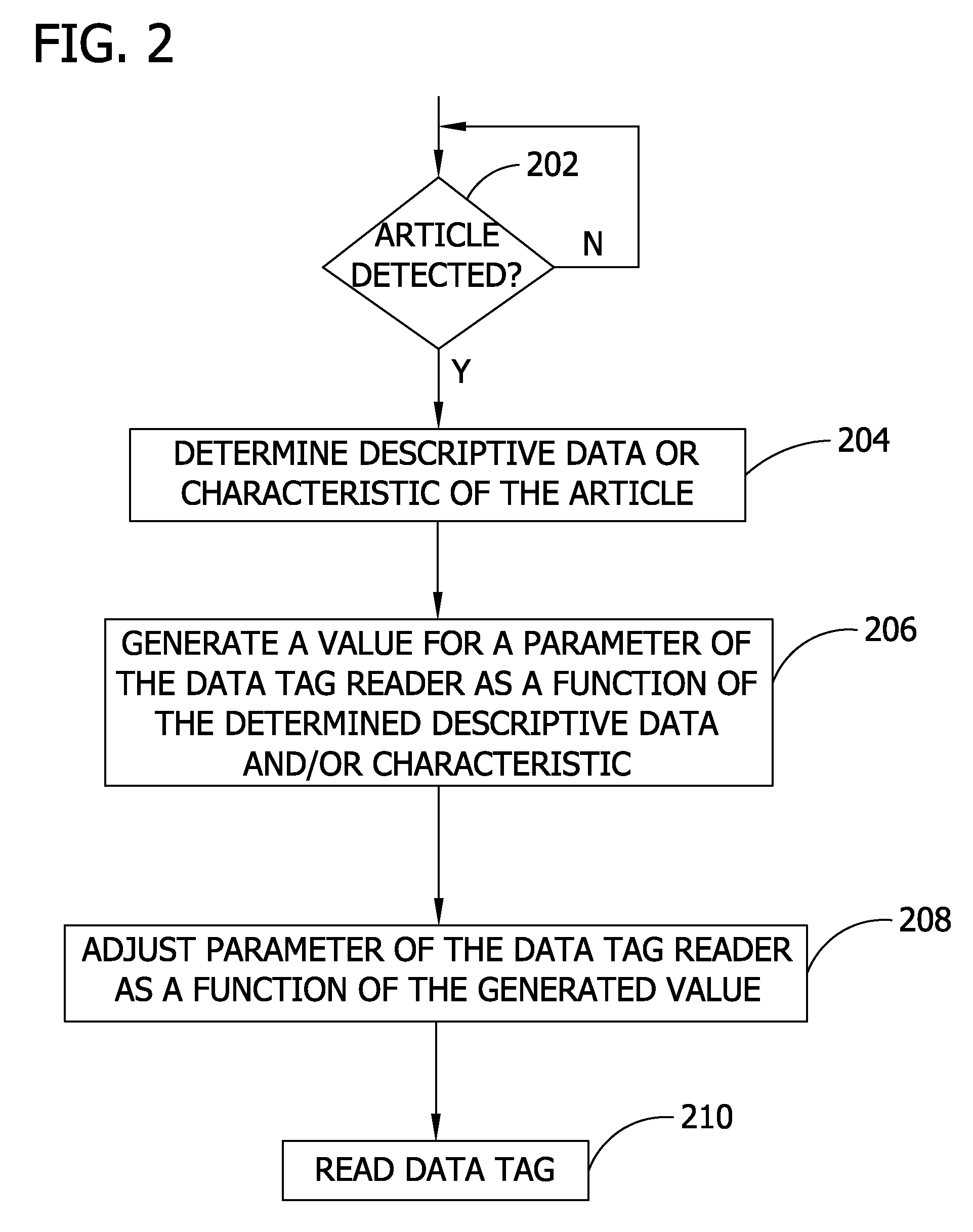
Adjusting data tag readers with feed-forward data
ActiveUS20060290472A1For signal receptionMemory record carrier reading problemsSubscribers indirect connectionComputer hardwareData labeling
Owner:AI-CORE TECH LLC
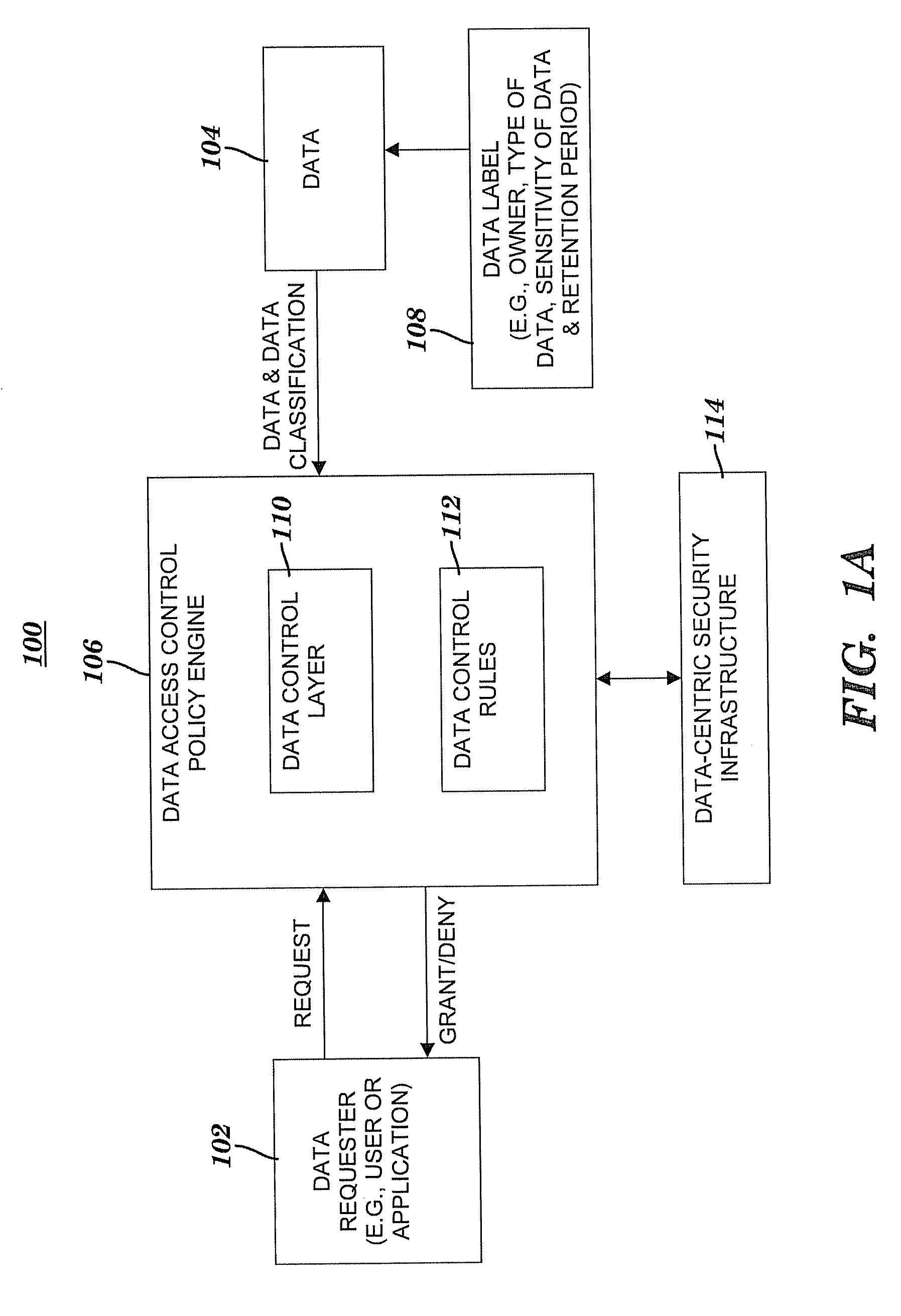
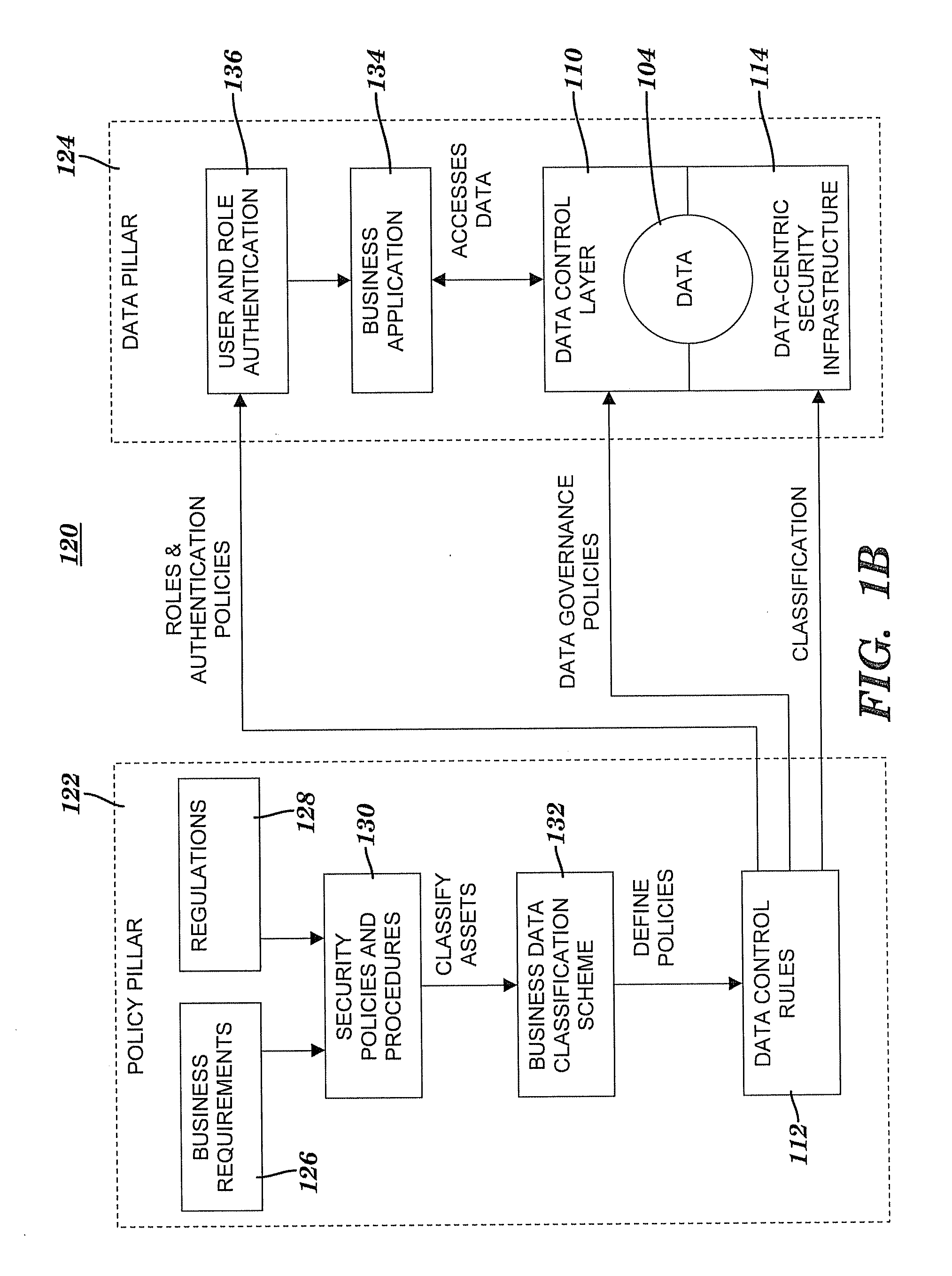
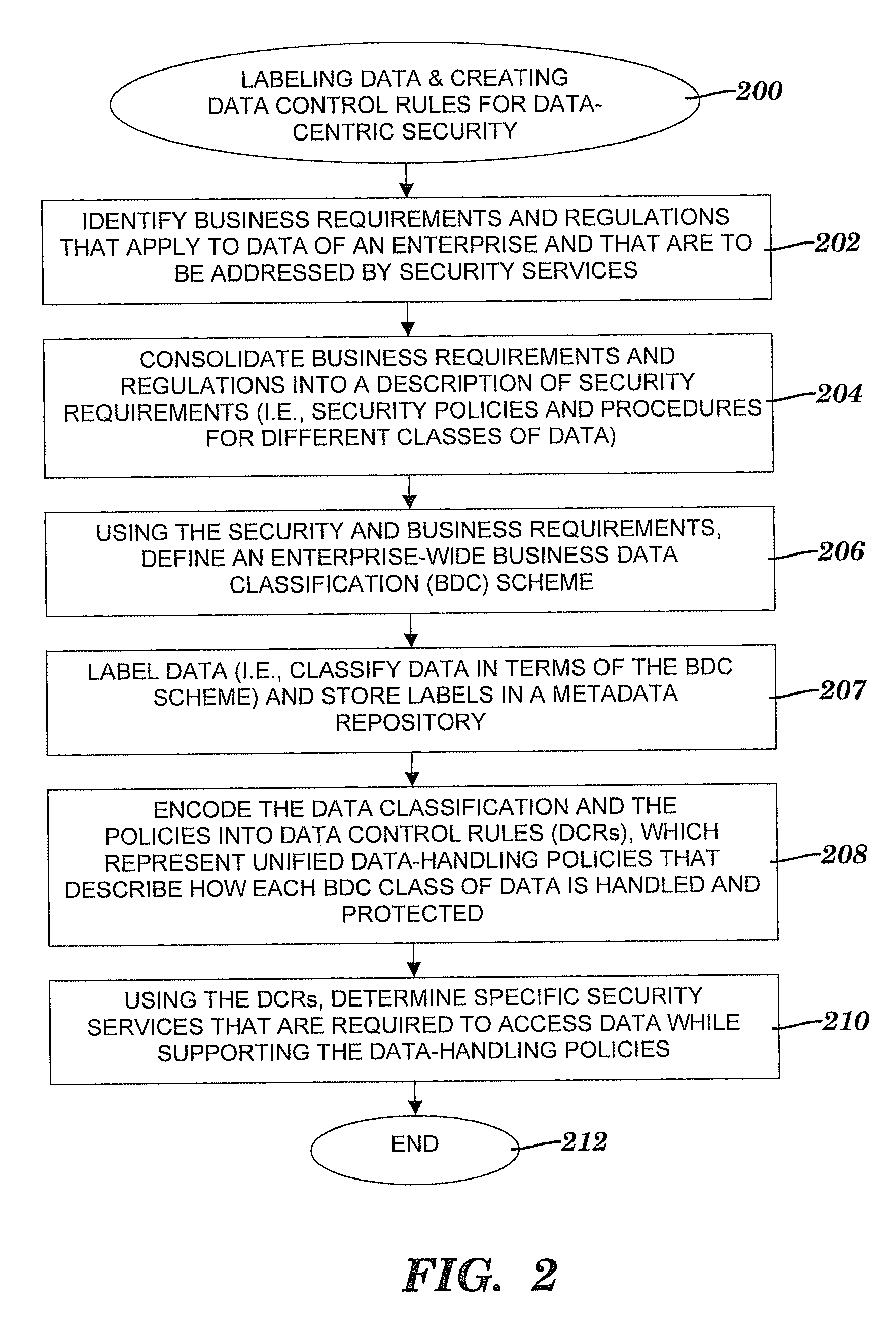
Method and system for controlling access to data via a data-centric security model
InactiveUS20090198697A1Facilitates effective collaborationLow costDigital data processing detailsComputer security arrangementsData controlMultiple attribute
A method and system for controlling access to data via a data-centric security model. A business data classification scheme is defined as a hierarchy that includes data types aligned with business operations. A data element is labeled with a data label. The data label includes multiple attributes associated with a data-centric security model. A first attribute is a data type of the data element. A second attribute includes security requirements. Data control rules are automatically generated for an enforcement of the security requirements. The enforcement grants or denies to a user an access to the data element via a predefined action. The enforcement is based on a predefined association among the predefined action, a predefined role that includes the user, the data type and, optionally, a purpose for performing the predefined action.
Owner:IBM CORP
Spreadsheet system and method for managing photos
InactiveUS20100058163A1Text processingStill image data browsing/visualisationDrag and dropObject based
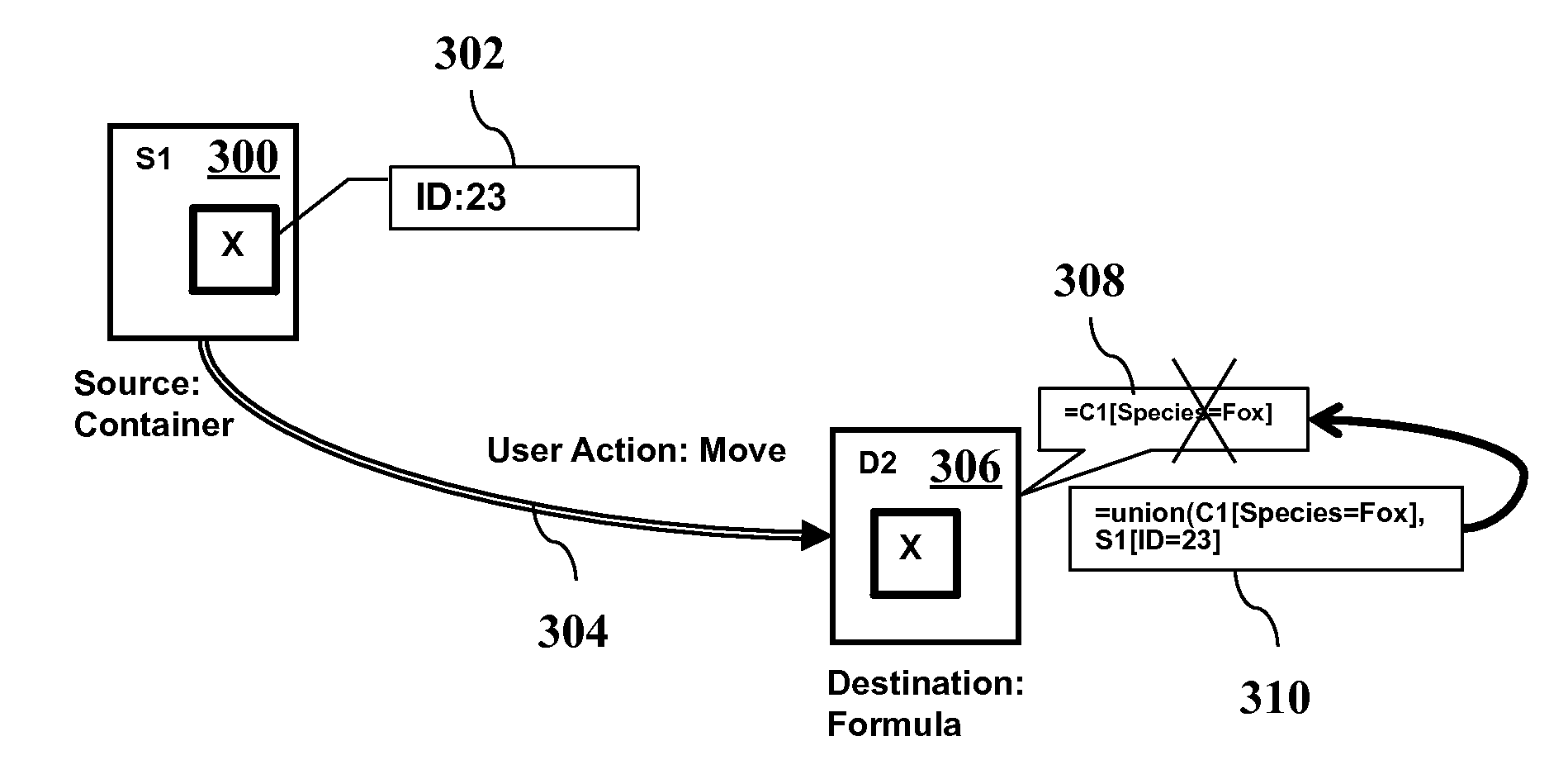
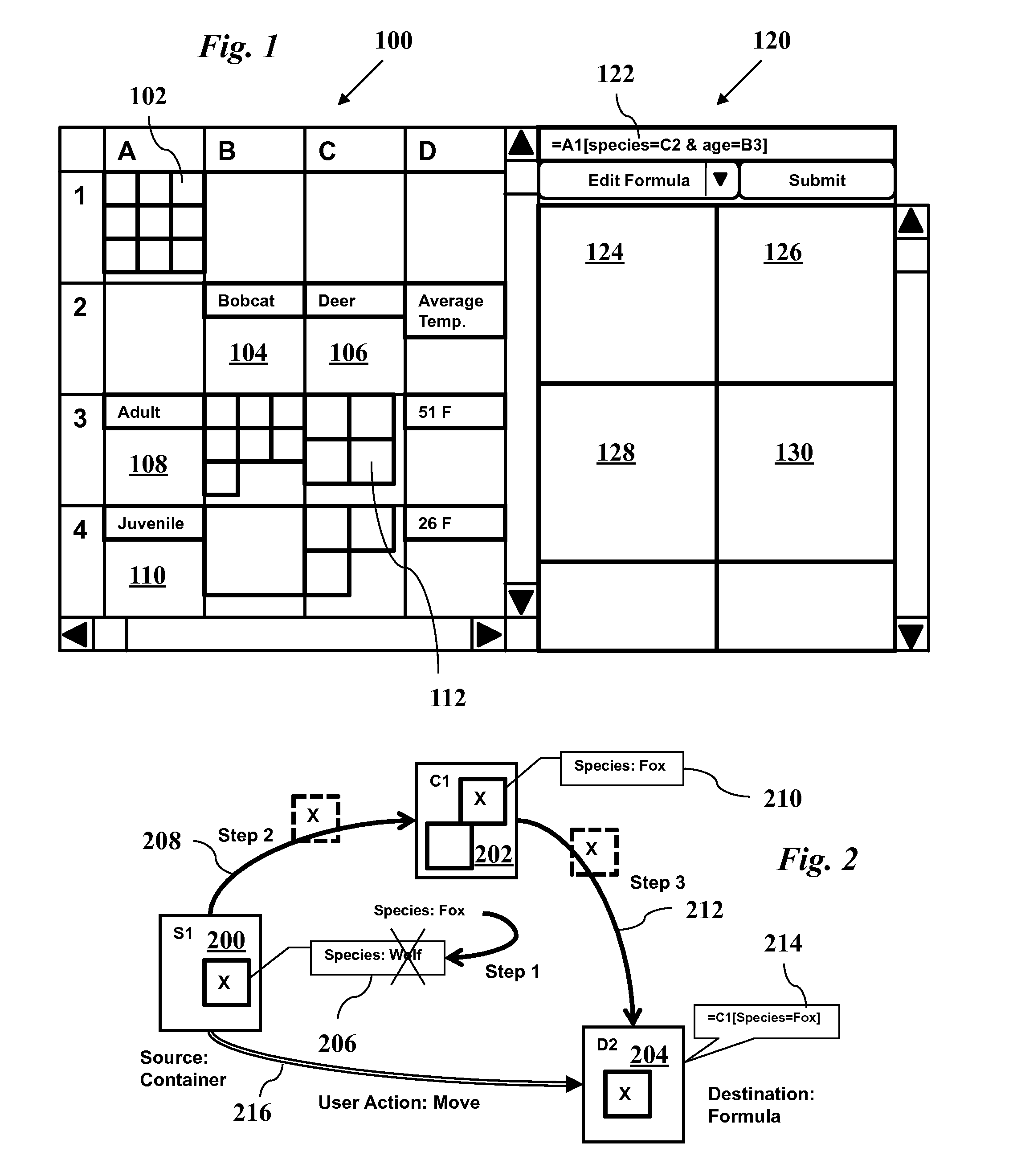
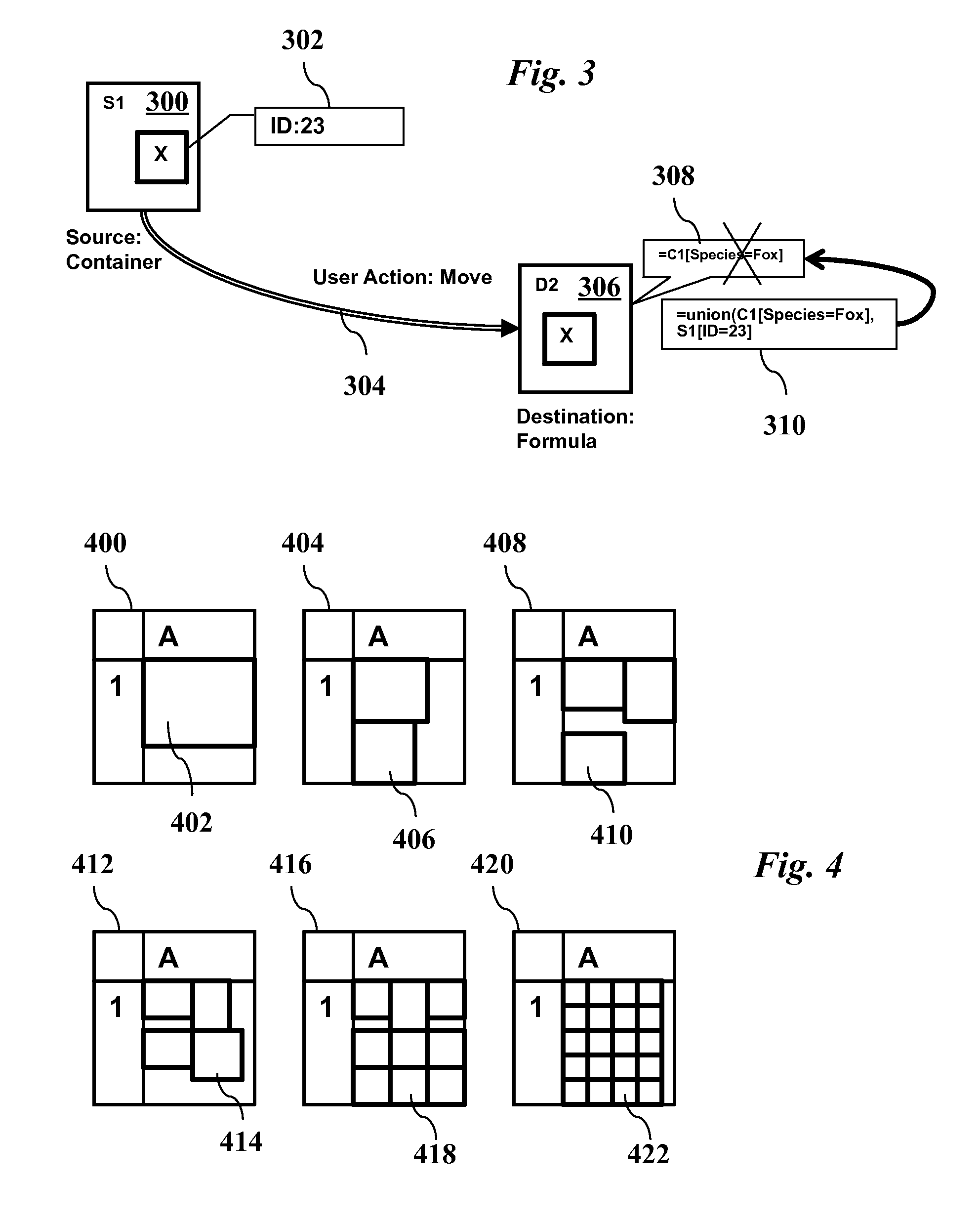
A spreadsheet system stores objects and formulas in the cells of the spreadsheet, along with metadata tags. Each cell may contain multiple objects (such as a group of photos). Drag-and-drop user actions automatically change tags associated with the moved objects based on a formula stored in the target cell if a forcing semantics mode is active, or automatically change a formula stored in the target cell if a non-forcing semantics mode is active. A formula in a cell selects a set of objects and may include set operators such as union, intersection, and minus. The formula may also filter sets to select a subset based on specified tag attributes of objects. The display of the spreadsheet adaptively selects a subset of objects to render in a cell and appropriately scales photos for optimal viewing.
Owner:THE BOARD OF TRUSTEES OF THE LELAND STANFORD JUNIOR UNIV
Method and system for high throughput blockwise independent encryption/decryption
ActiveUS8379841B2Computational complexity increaseReduce throughputMultiple keys/algorithms usageComputer security arrangementsData segmentLogical block addressing
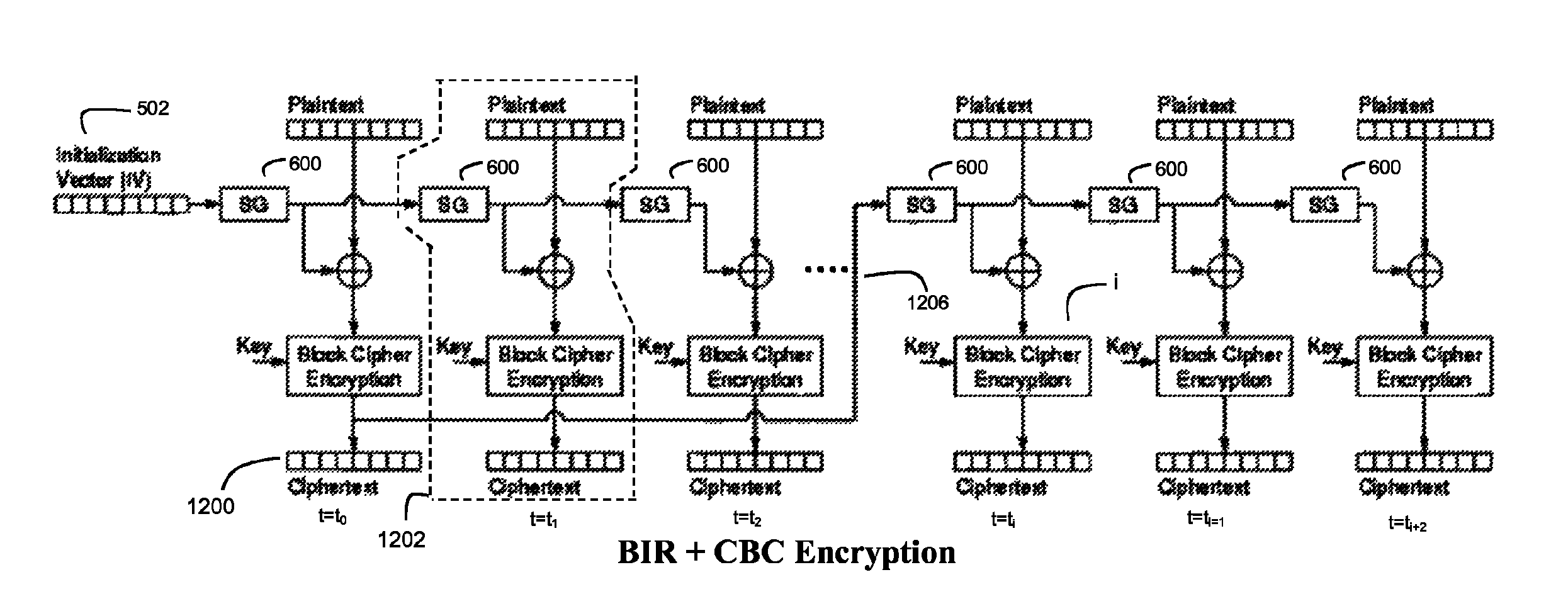
An encryption technique is disclosed for encrypting a data segment comprising a plurality of data blocks, wherein the security and throughput of the encryption is enhanced by using blockwise independent bit vectors for reversible combination with the data blocks prior to key encryption. Preferably, the blockwise independent bit vectors are derived from a data tag associated with the data segment. Several embodiments are disclosed for generating these blockwise independent bit vectors. In a preferred embodiment, the data tag comprises a logical block address (LBA) for the data segment. Also disclosed herein is a corresponding decryption technique as well as a corresponding symmetrical encryption / decryption technique.
Owner:IP RESERVOIR
Self-adjusting portals with movable data tag readers for improved reading of data tags
ActiveUS20060092014A1Improve readabilityEasy to readCo-operative working arrangementsSensing record carriersComputer hardwareLocation Equipment
Owner:INTELLECTUAL VENTURES ASSETS 190 LLC
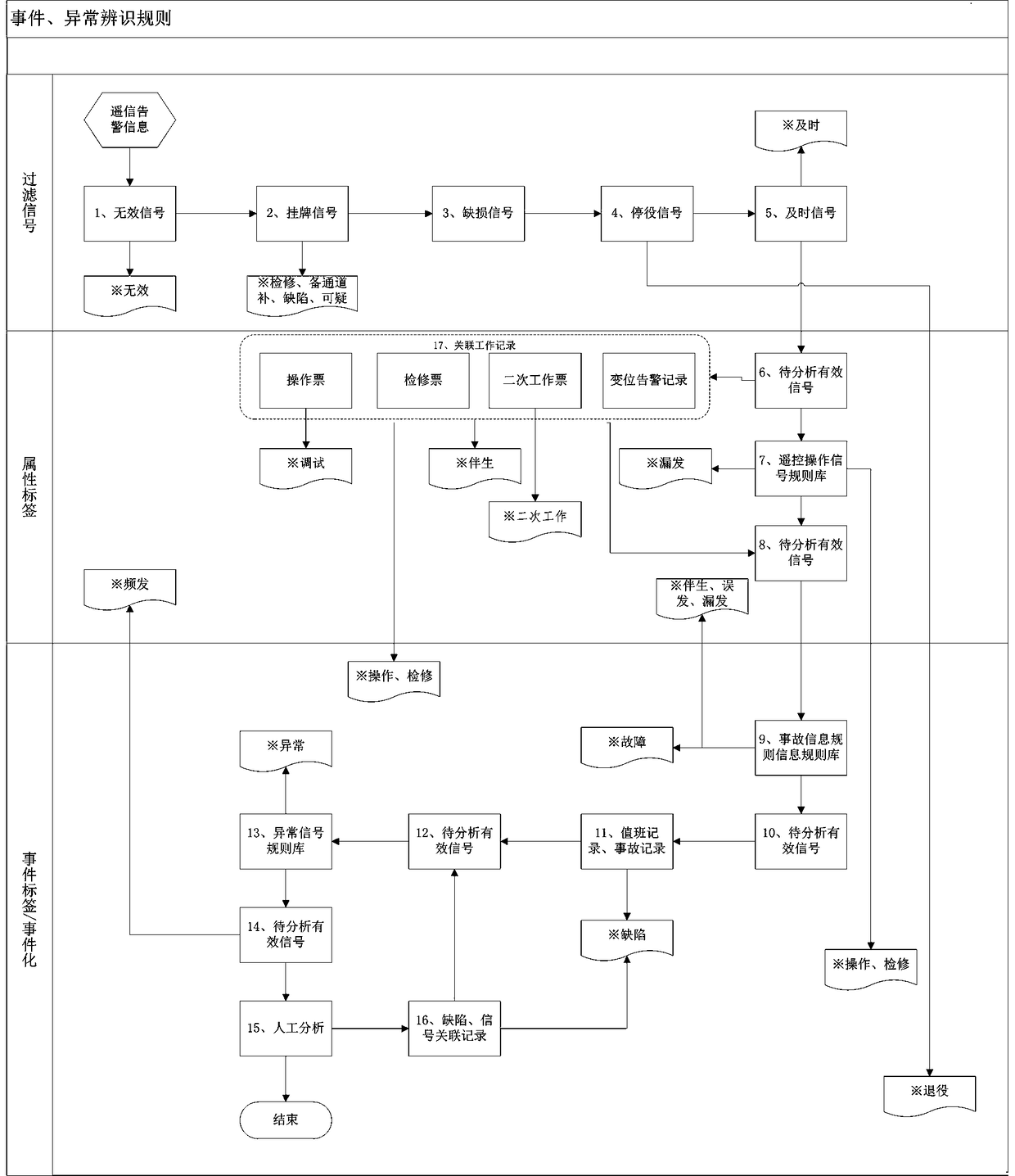
Accident monitoring, anomalous event identifying and multi-dimensional analysis method
ActiveCN108847968AGuaranteed operational safetyImprove centralized monitoring operation efficiencyData switching networksPower gridAnalysis method
The invention relates to an accident monitoring, anomalous event identifying and multi-dimensional analysis method and relates to an analysis method. As the construction of the power grid continues togrow and the number of power equipment increases, accurate and rapid analysis of faults and anomalies cannot be achieved. The method in the invention comprises the following steps: 1) establishment of a fault and anomaly rule base; 2) tagging analysis; 3) fault event identification; 4) anomalous event identification. The technical solution establishes an intelligent review mechanism by monitoringalarm information; the daily information is automatically tagged according to the information such as alarm level, monitoring operation information, maintenance and the like by using a data label technology; the effective alarm information is extracted; the fault and anomalous information corresponding to the information is identified from mass data in combination with the fault and anomalous information rule base; meanwhile, the residual information is pushed to manual review for special analysis, thereby improving the efficiency and the accuracy.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +2
Adjusting data tag readers with feed-forward data
ActiveUS7623036B2For signal receptionMemory record carrier reading problemsSubscribers indirect connectionWorld Wide WebData labeling
Owner:AI-CORE TECH LLC
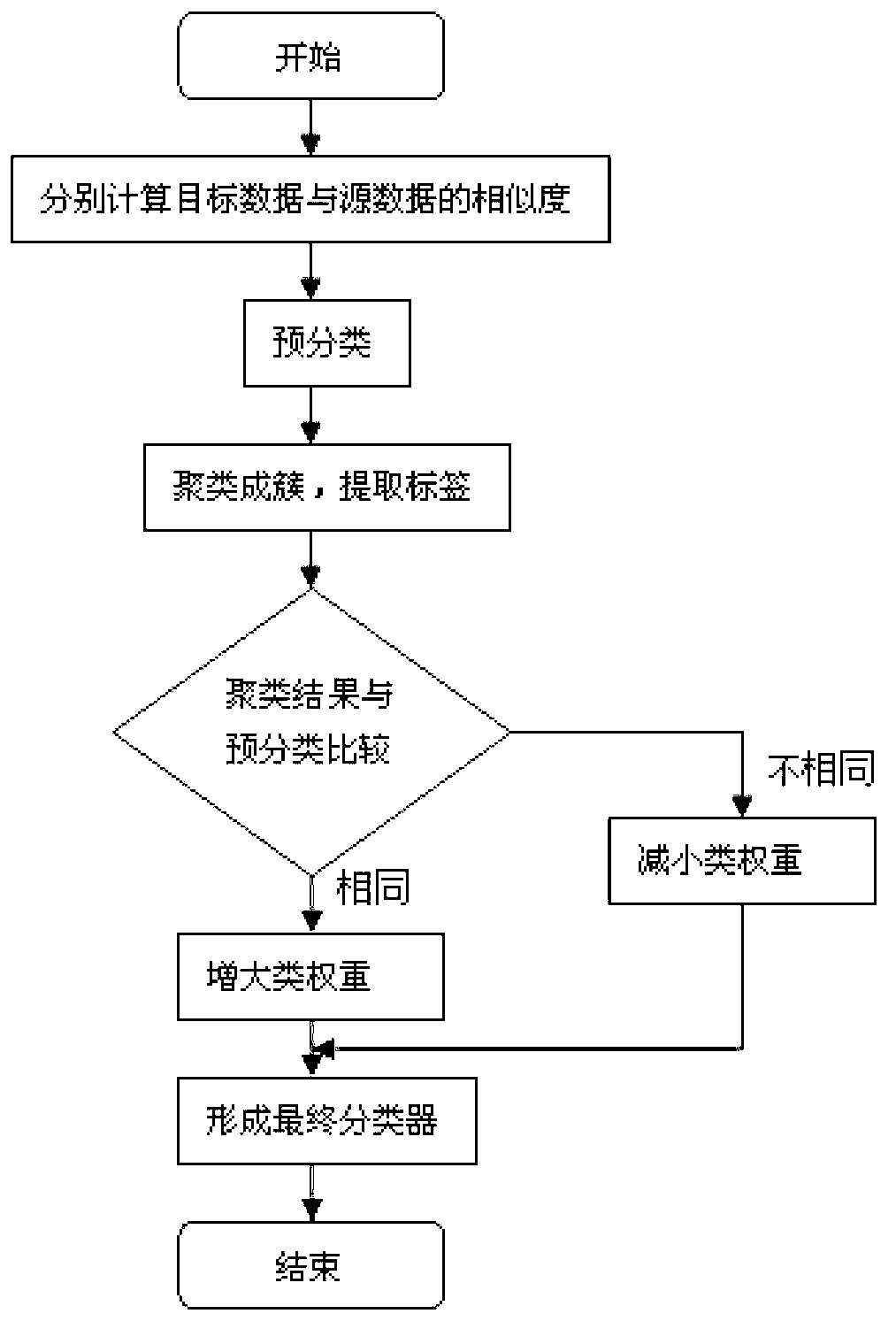
Transfer learning method based on semi-supervised clustering
ActiveCN103020122AImprove efficiencyHigh precisionSpecial data processing applicationsAlgorithmClassification methods
The invention provides a transfer learning method based on semi-supervised clustering. The transfer learning method based on the semi-supervised clustering comprises the following steps: calculating similarity and average similarity of data in each class of target data and auxiliary data; according to the average similarity, obtaining a similarity weight vector of the target data and a class tag; taking the vector with the maximum weight as a tag of the target data; with the target data as a centroid, performing K-means clustering into clusters, wherein the tag, having the maximum proportion of data in each cluster to the total data of the class to which the cluster belongs, is taken as a cluster tag; comparing a classification result with a pre-classification result; and in the finally-formed similarity weight vector of the target data, selecting a data tag with the maximum weight as the data tag of the target data so as to form a final classifier. The invention provides the transfer learning method based on the semi-supervised clustering, which can transfer a classifying method and a classifying technology from one field to another field and can improve the precision of the classification result.
Owner:HARBIN ENG UNIV
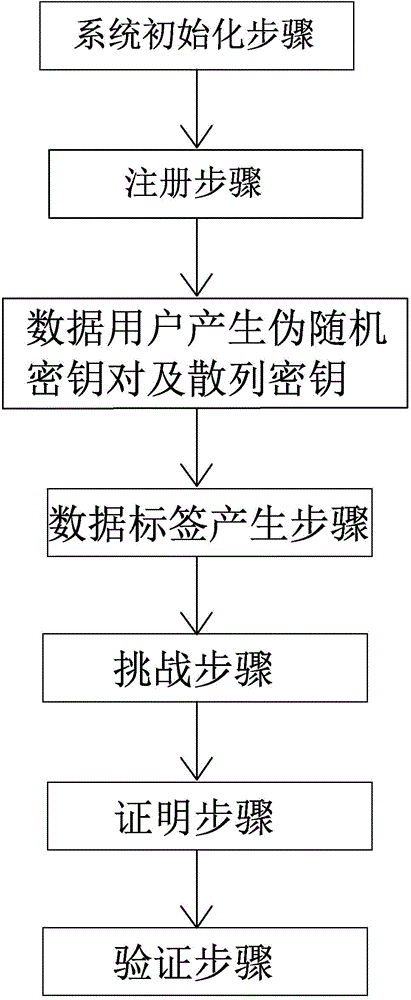
Efficient privacy protecting audit scheme based on chameleon hash function of cloud storage
InactiveCN104601605AImplement integrity verificationRealize privacy protectionTransmissionData labelingUser privacy
The invention provides an efficient privacy protecting audit scheme based on the chameleon hash function of cloud storage. The scheme includes (1) a system initialization step; (2) a registration step; (3) a pseudo-random key pair and hash key generation step for data users; (4) a data label generation step; (5) a challenge step; (6) a proof step; (7) a validation step. According to the scheme, on the basis of the decidable Diffie-Hellman problem and a chameleon digital signature, a privacy protecting public audit scheme is established, and high efficiency, low safety assumptions and wide application range are provided; according to a cloud server, the identity privacy of the data users is protected, and the outsourcing data integrity is protected; according to auditors, the data user privacy is protected in the whole auditing process.
Owner:NORTH CHINA UNIVERSITY OF TECHNOLOGY
System and method for selective information and resource sharing
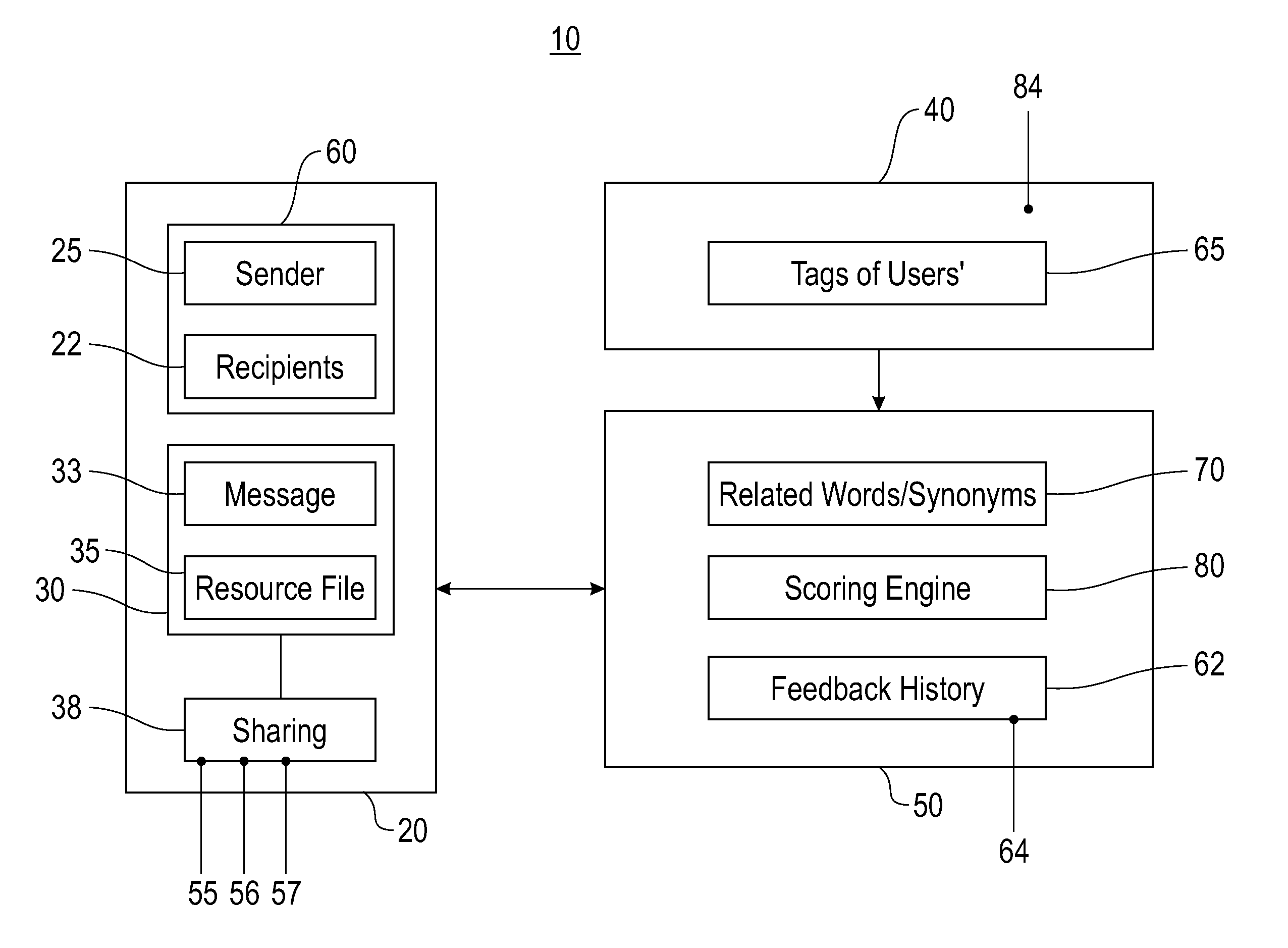
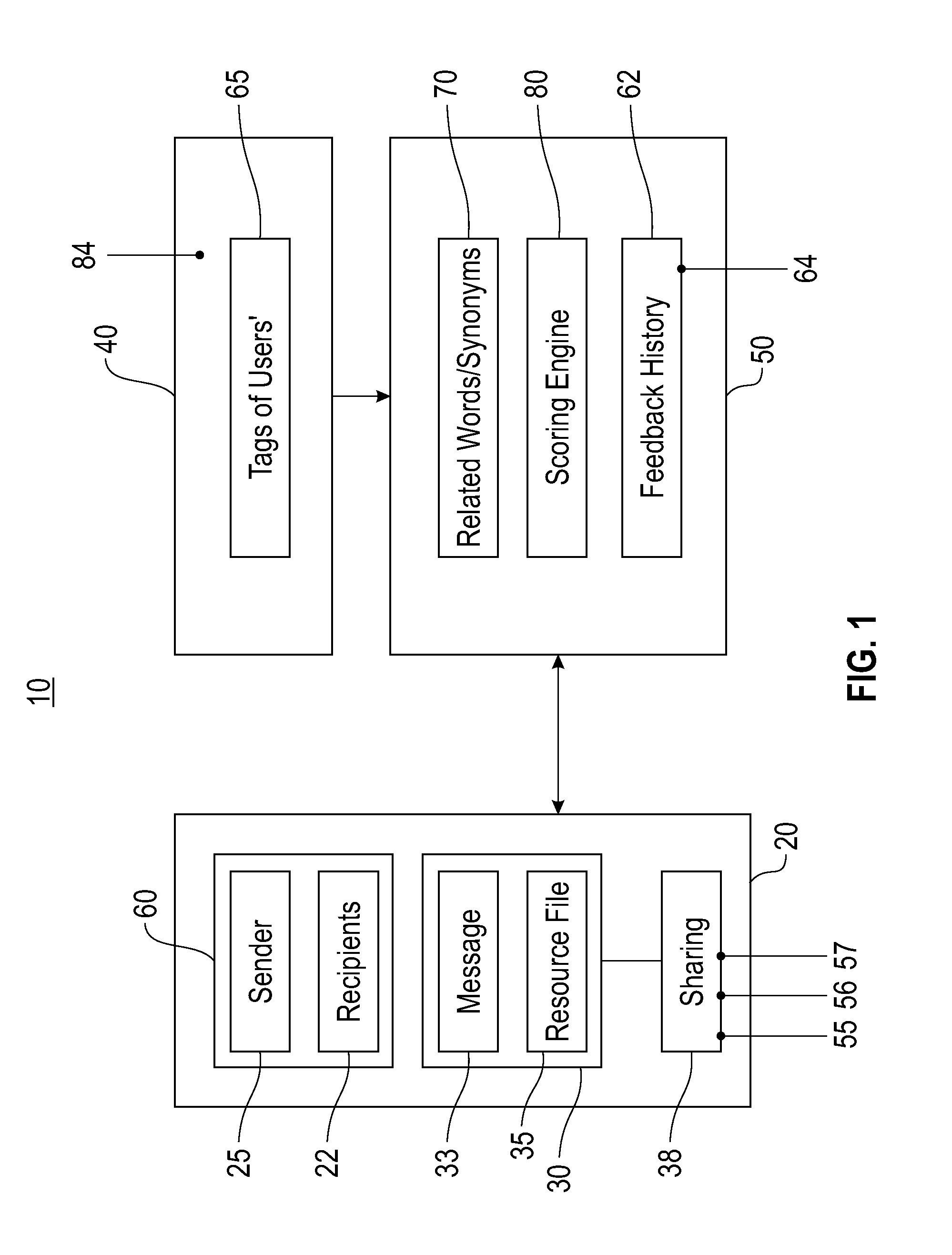
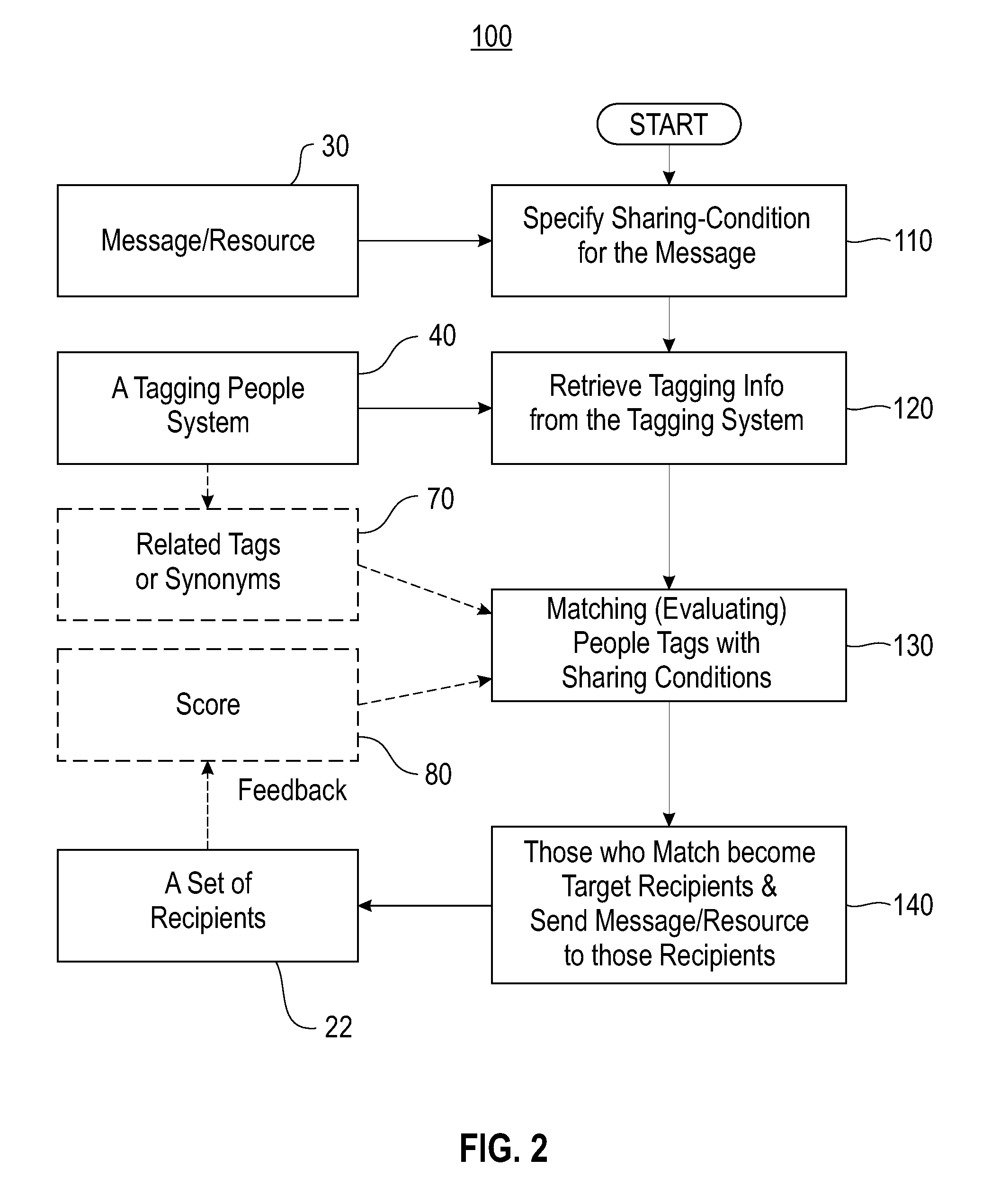
A method and system of automatically identifying a set of relevant and qualified recipients to share electronic data is disclosed. The system includes an electronic network configured to store and transmit the electronic data files. The electronic data files include one or more data tags defining a sharing condition that targets potential recipients of the data files or permits access to the data files. A people-tagging system provides an electronic platform including keyword lists (tags) defined by recipient users collaboratively. A matching tool includes software matching recipient users to the data files when the recipient users are associated with keyword lists that satisfy the sharing condition. The method includes tagging a data file by one or more keywords and using a people-tagging system where the recipient users define a list of tags on topics of interest. Recipient users are matched to data files when user lists of tags satisfying the sharing condition.
Owner:IBM CORP
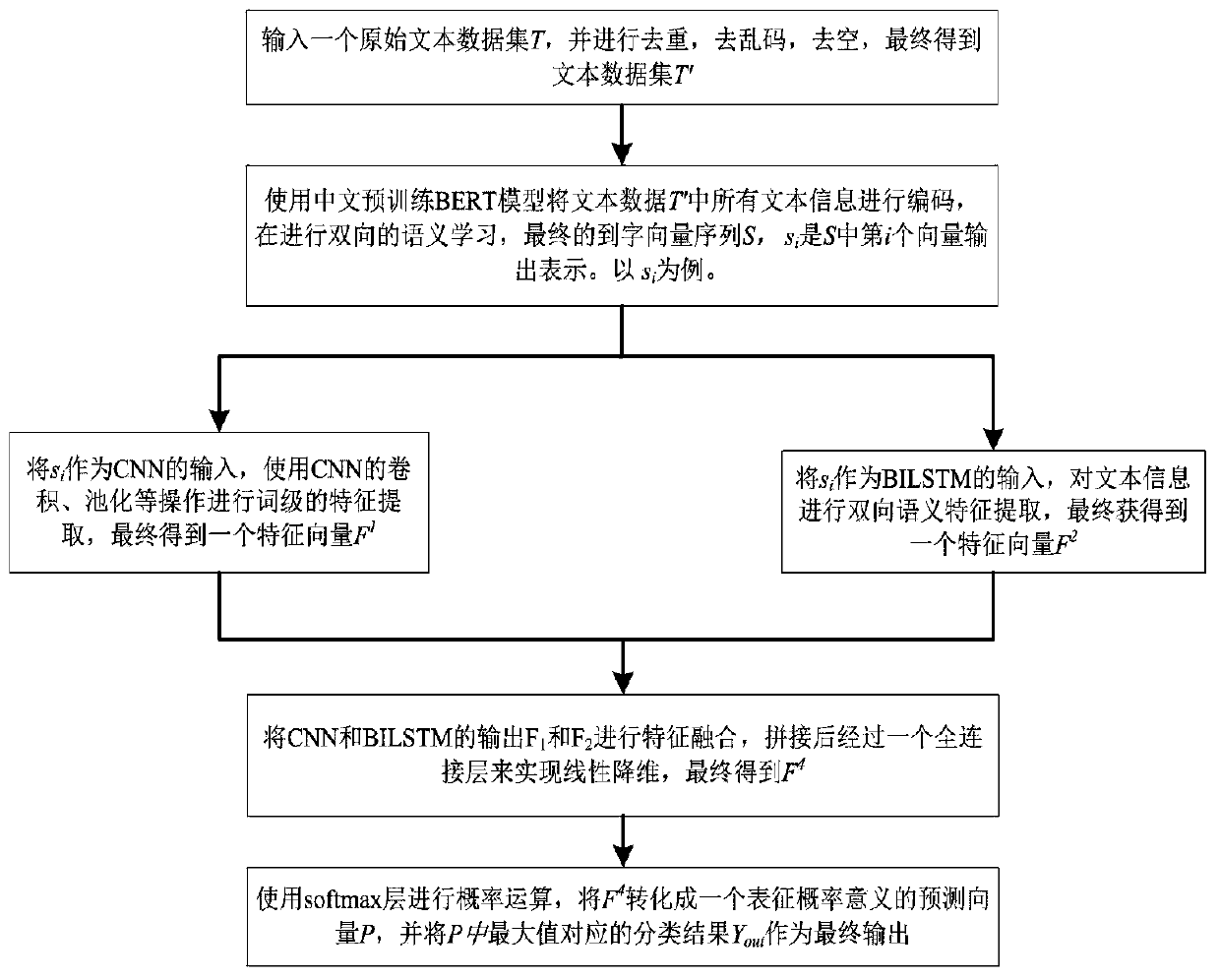
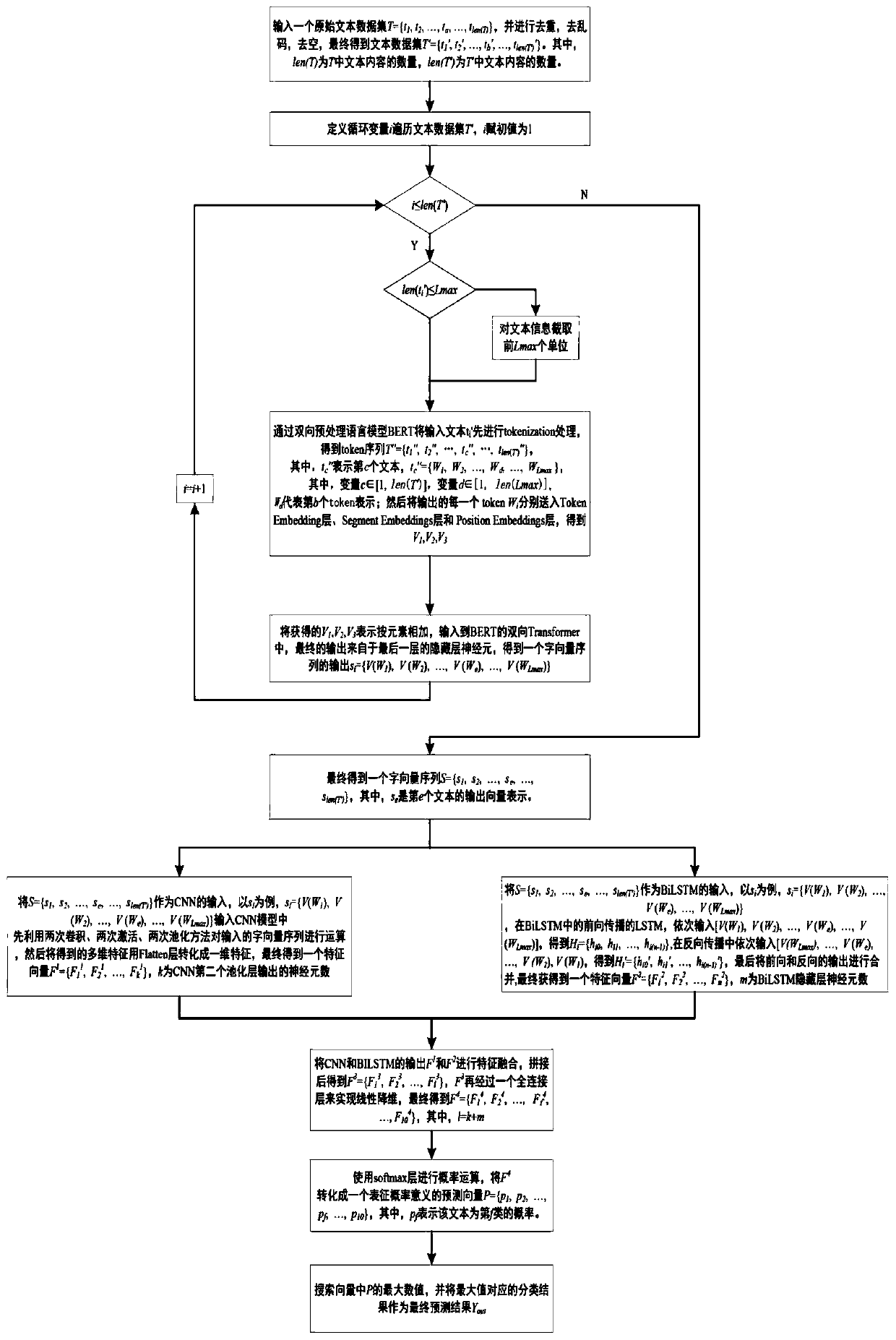
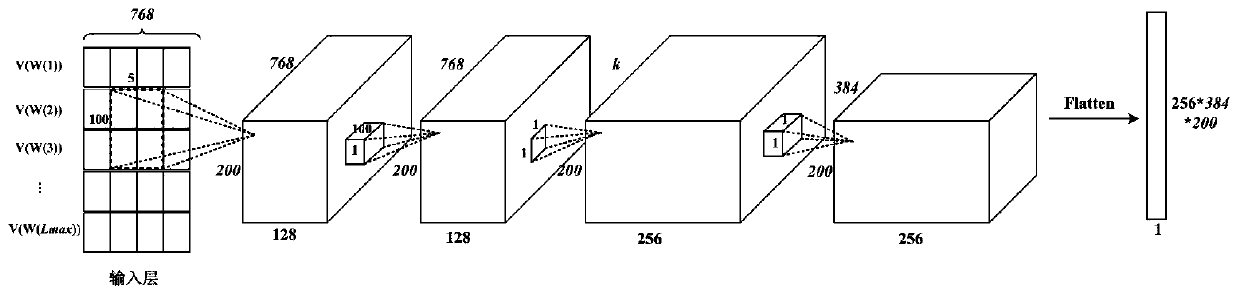
Automatic text classification method based on BERT and feature fusion
ActiveCN110413785AHigh precisionImprove encoding performanceNeural architecturesPhysical realisationPrediction probabilityClassification methods
The invention discloses an automatic text classification method based on BERT and feature fusion. The method comprises the following steps: firstly, cleaning text data, realizing conversion from a text to a dynamic word vector through BERT, extracting features of the text by utilizing CNN and BiLSTM, and respectively transmitting a word vector sequence output by the BERT to a CNN network and a BiLSTM network; then, splicing the output of a CNN network and the output of a BiLSTM network together, carrying out feature fusion, and finally, outputting a final prediction probability vector througha full connection layer and a softmax layer. The method is suitable for the general supervised text label prediction problem, and can effectively improve the prediction accuracy of the text data labels with prominent sequence information and local features.
Owner:HUAIYIN INSTITUTE OF TECHNOLOGY
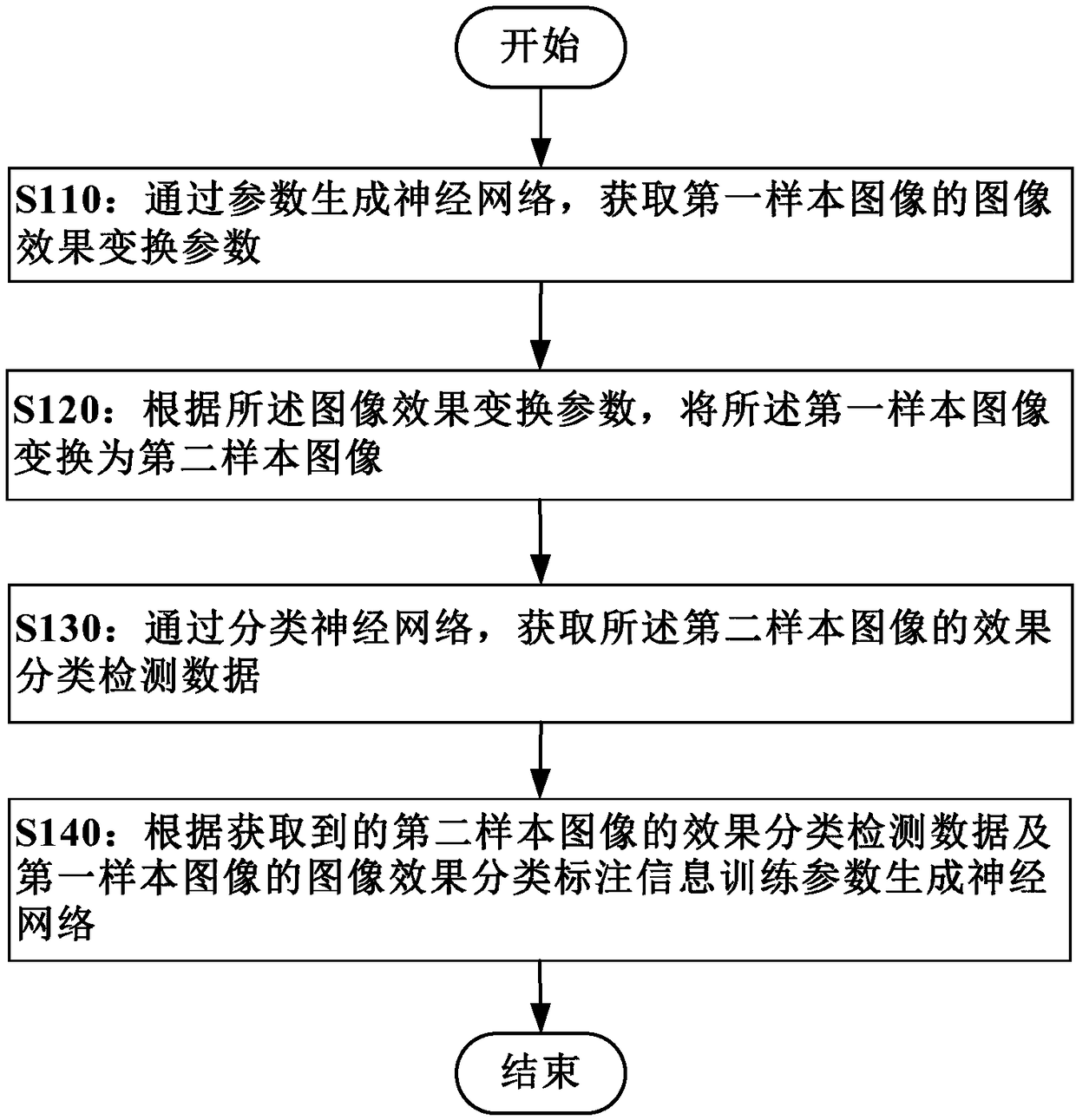
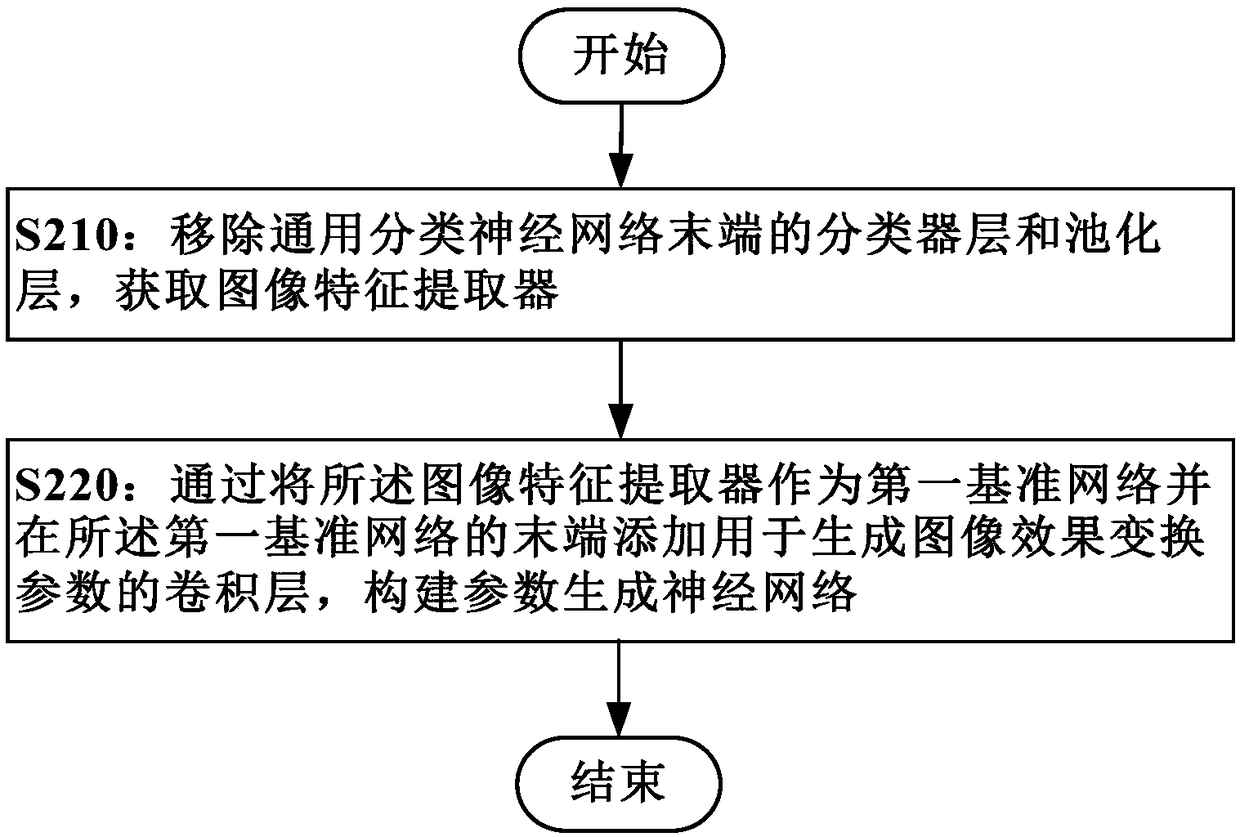
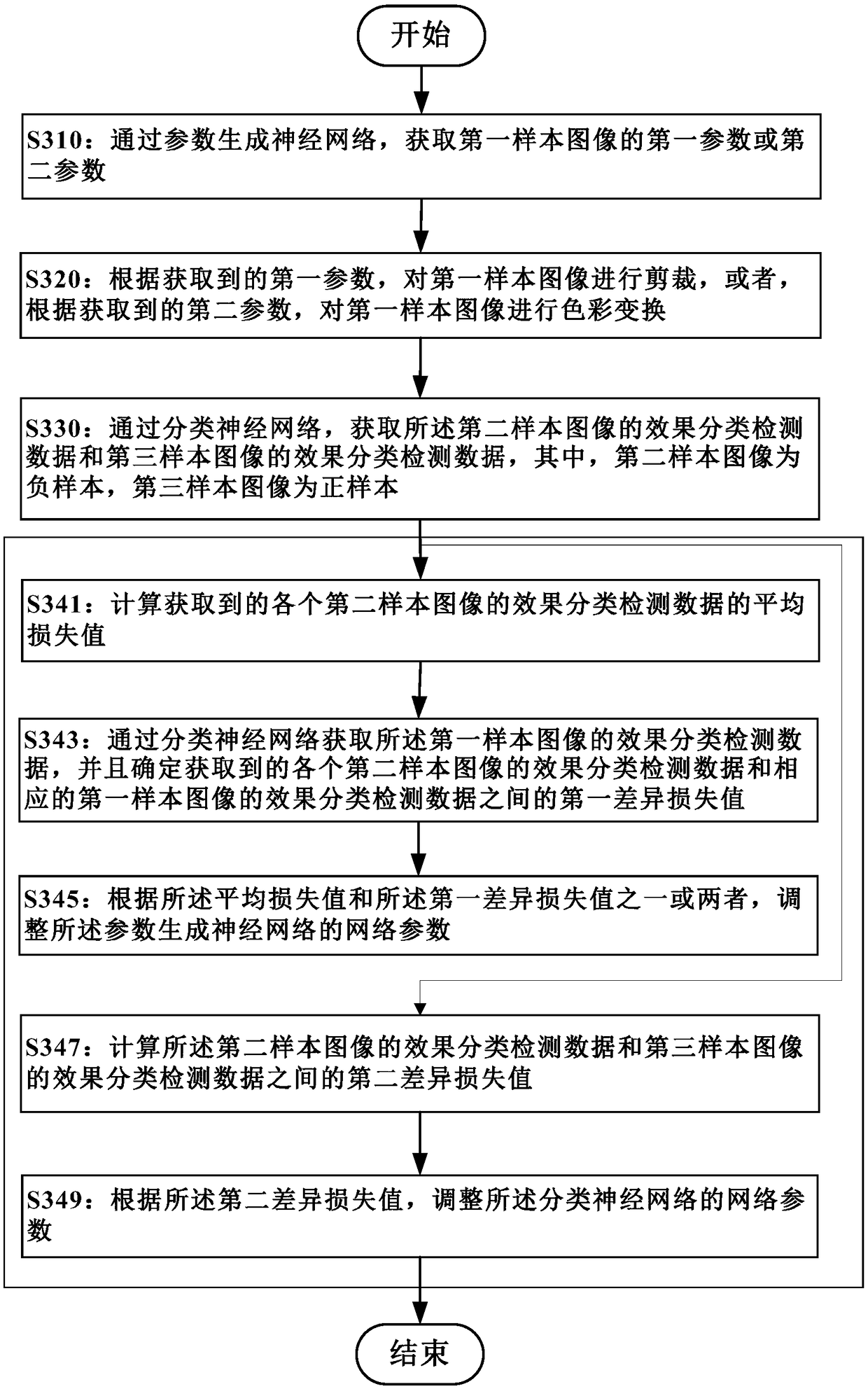
Network training method and device, image processing method and device, storage medium and electronic equipment
ActiveCN108229526AQuality improvementGet automaticallyCharacter and pattern recognitionImaging processingTransformation parameter
Embodiments of the invention provide a network training method and device, an image processing method and device, a storage medium and electronic equipment. The neural network training method comprises the following steps of: generating a neural network through parameters, obtaining an effect transformation parameter of a first sample image, and transforming the first sample image into a second sample image; obtaining effect classification and detection data of the second sample image through a classification neural network; and training the parameters to generate the neural network accordingto the effect classification and detection data of the second sample image and image effect classification labeling information of the first sample image. On the basis of a generative adversarial network, simple and object labeling data of image effect classification is taken as supervision information of training, accurate image effect parameter data labeling does not need to be carried out on selected sample images, and parameters for generating image effect transformation parameters are trained through a weak supervised learning manner so as to generate neural networks.
Owner:BEIJING SENSETIME TECH DEV CO LTD
Secure data tagging systems
InactiveUS20050017844A1Improve security levelSimple and low cost tagElectric signal transmission systemsTicket-issuing apparatusSecure communicationData stream
A system is disclosed for secure communication between an interrogator and an RFID tag. The system includes means for singulating the tag in a population of RFID tags and means for extracting from the tag, identity data adapted to uniquely identify the tag. The system further includes means for securely communicating the identity data to a secure database, means for providing authentication data by the database and means for securely communicating the authenticating data to the interrogator. The system also includes means for providing a further communication between the tag and the interrogator, and wherein at least one stream of data between the tag and the interrogator includes random data generated via a random physical process. The tag and database may each include means for maintaining a count of secure authentications. The count may be separately maintained by the tag and database and may be incremented following each secure authentication. A method for secure communication between an interrogator and an RFID tag is also disclosed.
Owner:TAGSYS
Administering contracts over data network
A method for administering performance of a contract over a data network includes storing a lien waiver and receiving an application for payment over the data network from a contract participant based on performance under the contract. The stored lien waiver is retrieved and sent to the participant via the data network upon approval of the application for payment. The at least one data tag may be included in the lien waiver prior to storing the lien waiver.
Owner:HART BUSINESS SOLUTIONS
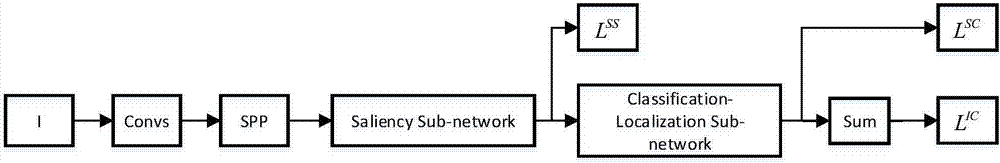
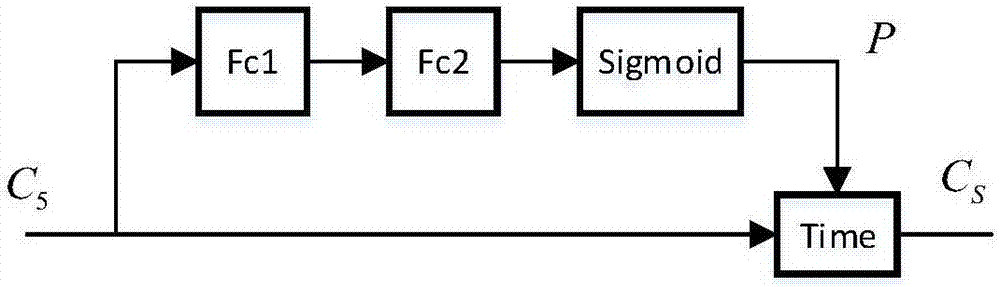
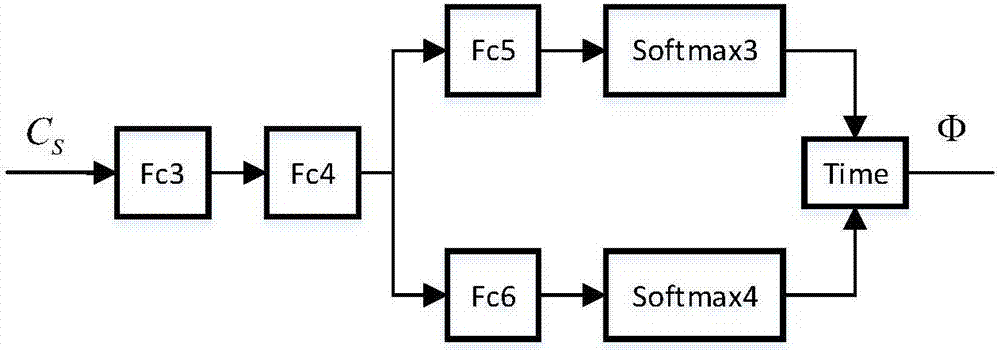
End-to-end weak supervision target detection method based on salient guidance
InactiveCN107203781AReduce workloadImprove performanceCharacter and pattern recognitionWorkloadData labeling
The invention discloses an end-to-end weak supervision target detection method based on salient guidance. According to the method, a deep neural network is constructed, and a salient sub-network of a target box is added on the basis of a weak supervised classifier network; meanwhile, seed target areas with related categories are selected according to the criterion of context difference by the aid of a category-related salient map trained with a weak supervision method, and the salient sub-network and a classifier sub-network are supervised and trained. Compared with existing weak supervision target detection methods, the method has the advantages that better performance is obtained, meanwhile, only training of image-grade labels is required, and the workload of training data labeling is reduced.
Owner:ZHEJIANG UNIV
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com