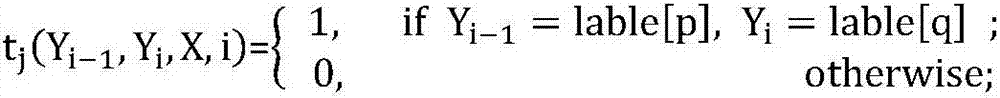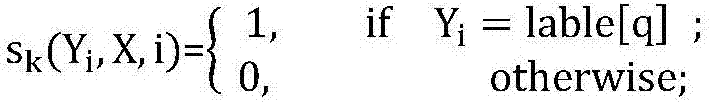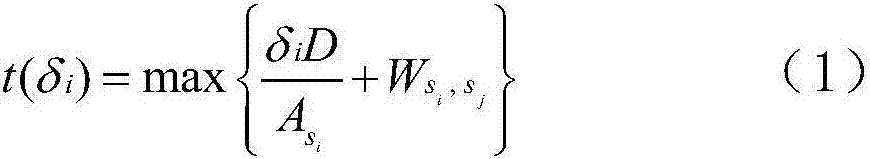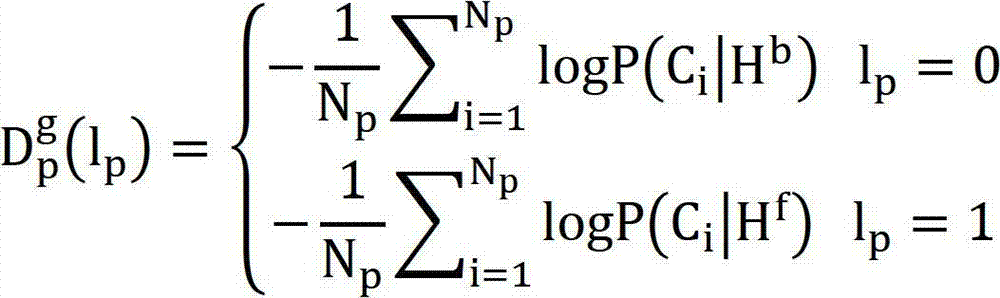Patents
Literature
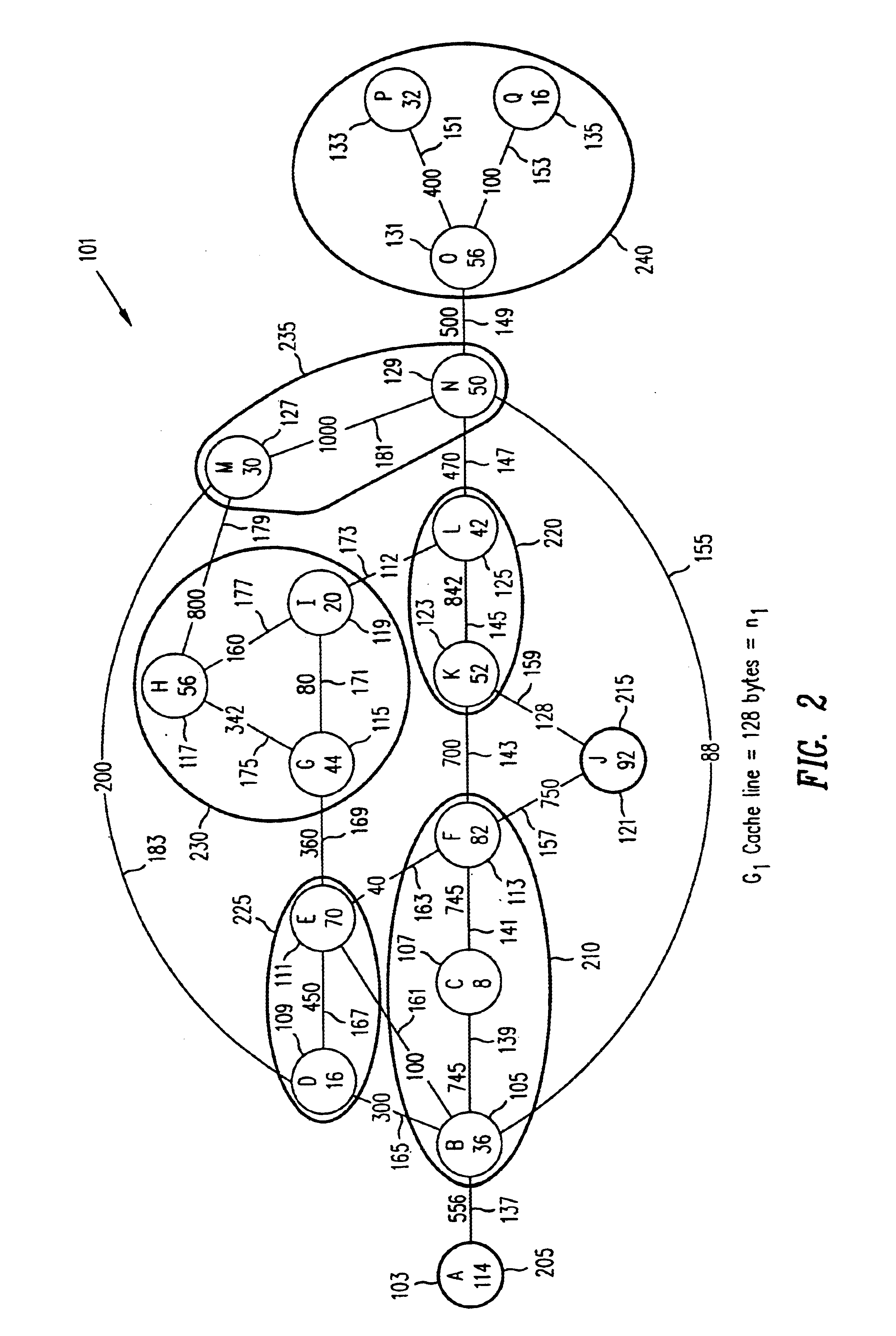
840 results about "Undirected graph" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
Undirected graph definition. An undirected graph is graph, i.e., a set of objects (called vertices or nodes) that are connected together, where all the edges are bidirectional. An undirected graph is sometimes called an undirected network. In contrast, a graph where the edges point in a direction is called a directed graph. When drawing an...
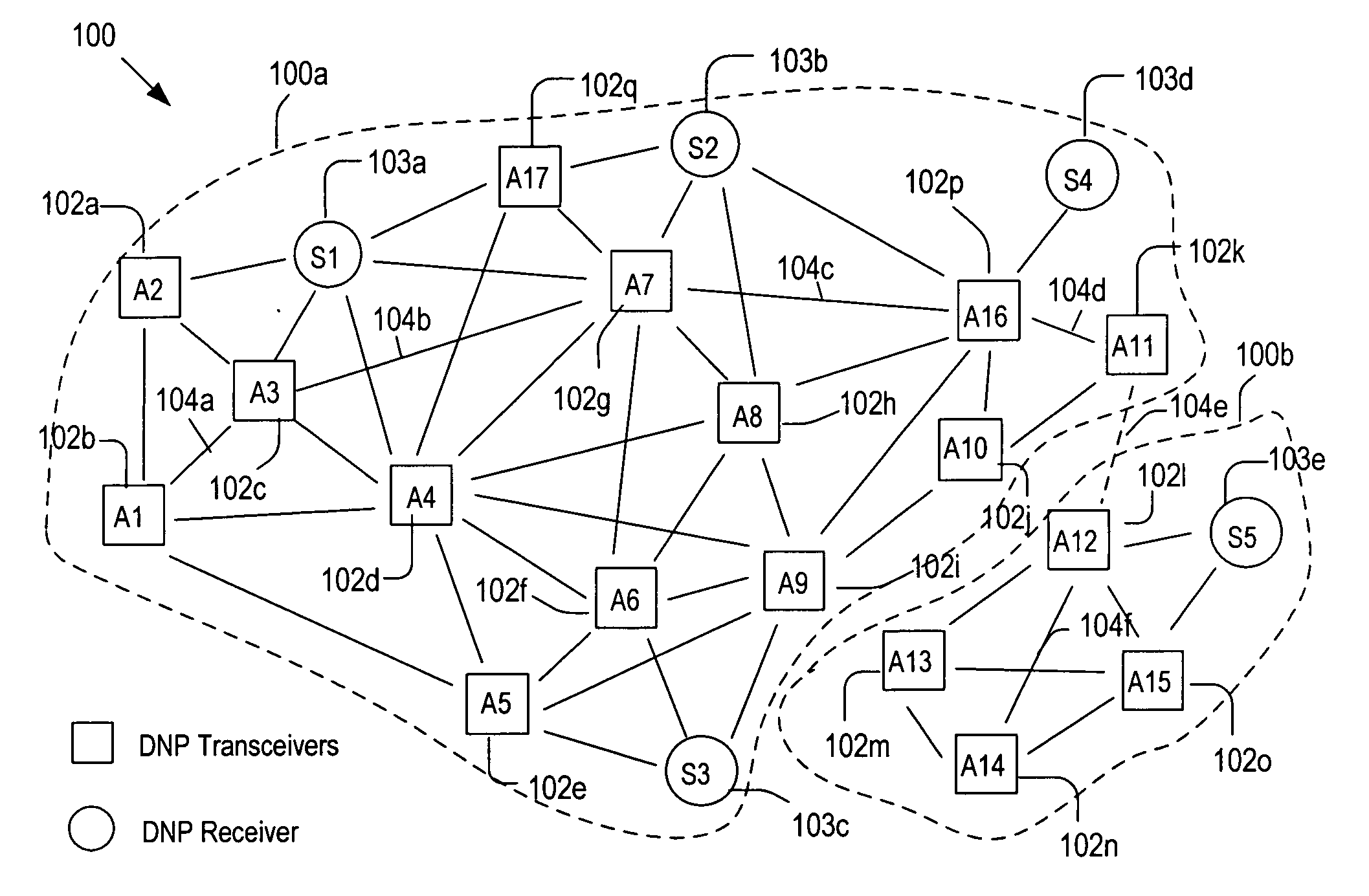
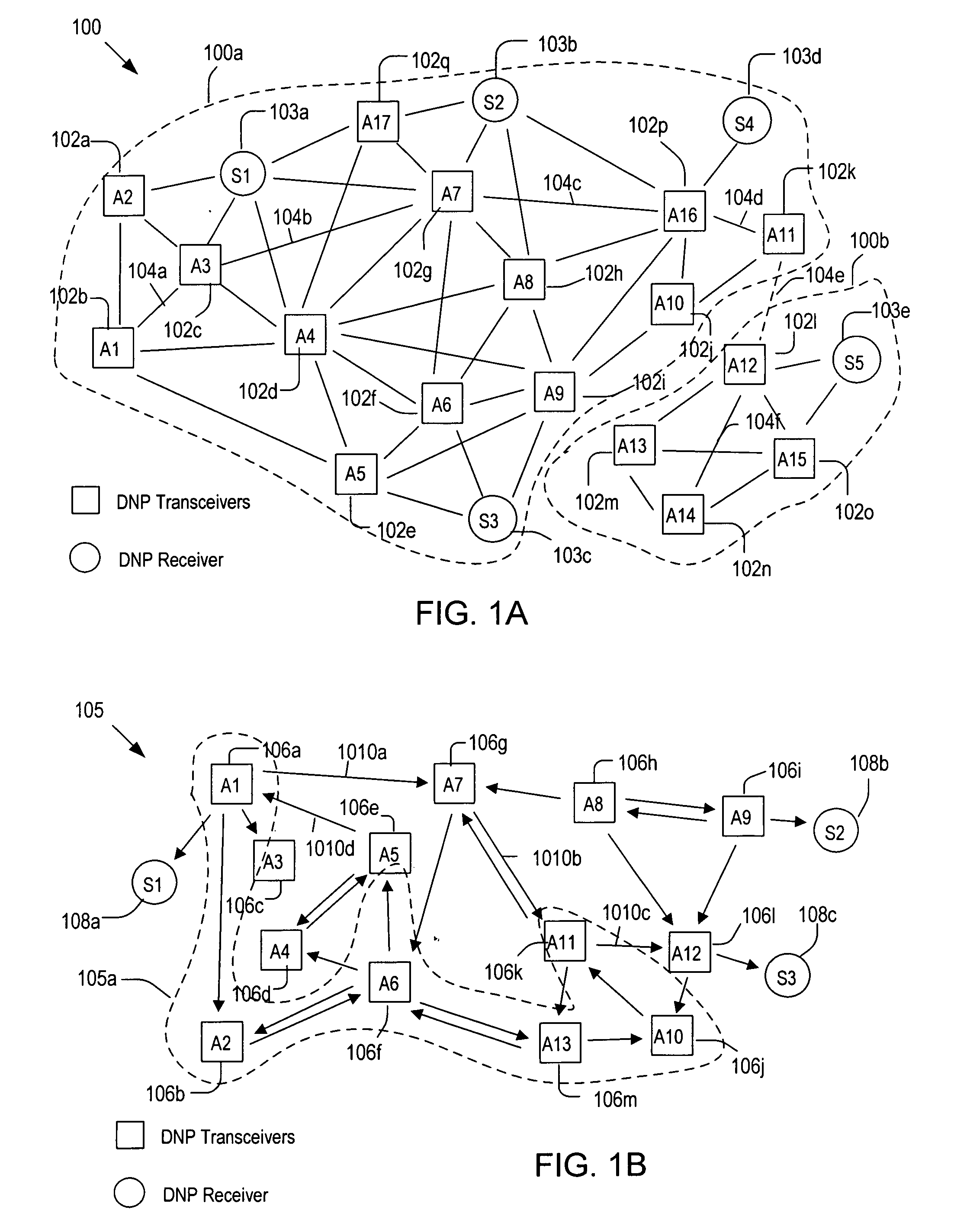
Methods of networking interrogation devices for structural conditions
InactiveUS20060287842A1Vibration measurement in solidsSpecial data processing applicationsDirected graphUndirected graph
Methods of operating an interrogation system that has a plurality of patches attached to a host structure. Each patch is capable of generating a diagnostic wave and / or developing a sensor signal in response to the diagnostic wave. In each method, a Euclidean undirected graph is generated by forming a plurality of paths, wherein each path connects two of the patches and the length of the path is shorter than a preset limit. Then, a directed graph is generated by assigning a propagation direction of the diagnostic wave to each path. Structural condition index (SCI) values are measured by use of the directed graph and, based on the SCI values, the host structure is scanned for anomalies. The directed graph is reconfigured to enhance accuracy in determining the shape and location of the anomalies.
Owner:ADVANCED STRUCTURE MONITORING
Path planning method of passable area divided at unequal distance
InactiveCN103528585AOvercome memory spaceOvercome timeNavigational calculation instrumentsUndirected graphPlanning approach
The invention belongs to the technical field of path or flight path planning of robots as well as low-altitude flight aircrafts, specifically relates to a path planning method of a passable area divided at unequal distance, and is used for solving the problem that existing planning algorithm has large time complexity in time and space complexity. The path planning method comprises the following steps of: calculating convex extreme points of each barrier curve; dividing the passable area by using each convex extreme point as a horizontal line; abstracting each small area obtained by dividing into a peak of a graph; forming an undirected graph by all peaks; finding out a peak serial number corresponding to the small area at which a starting point and a final point are located; finding out all paths for the undirected graph by breadth-first or depth-first scanning; finding out an actual to-be-travelled path of a moving object according to the situation on an actual map. The path planning method disclosed by the invention has the beneficial effect of overcoming the problems of algorithms of A* and the like on memory space and operation time, and overcoming a convergence problem of an ant colony algorithm at the same time. Besides, time complexity and space complexity are improved greatly in comparison with other algorithms.
Owner:ZHONGBEI UNIV
Method and device for detecting network hot topics found based on maximal clique
InactiveCN102346766AImprove practicalityVerify validitySpecial data processing applicationsUndirected graphOne-hot
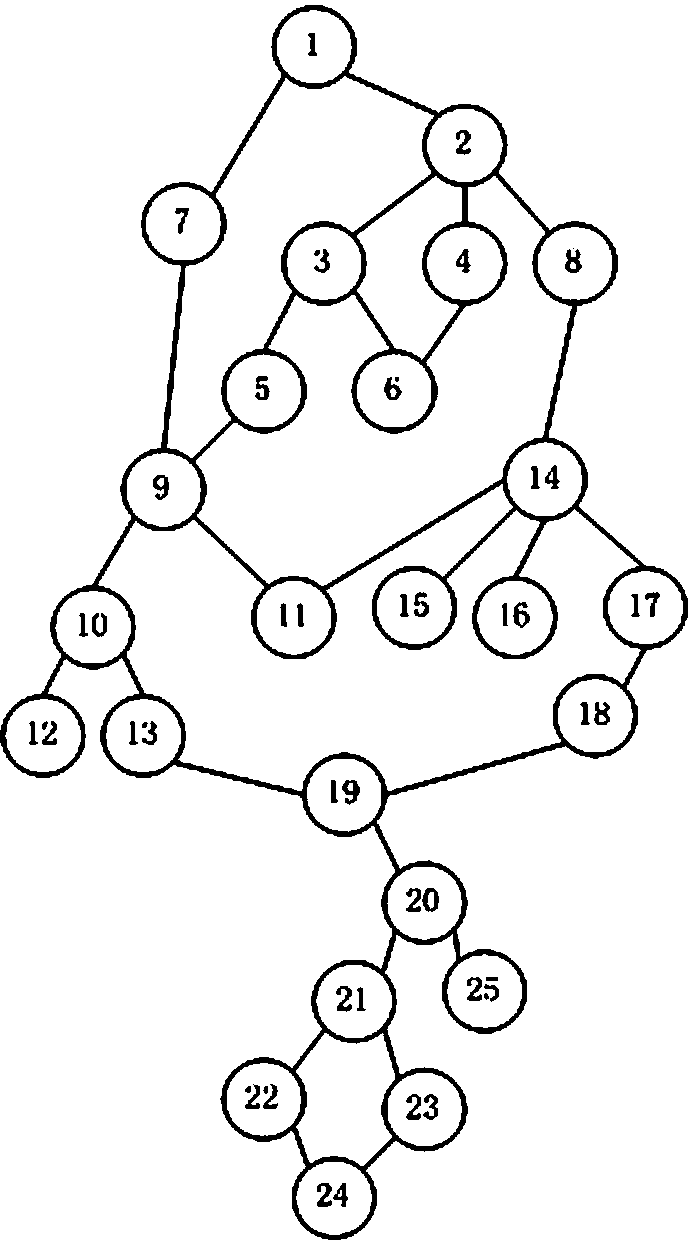
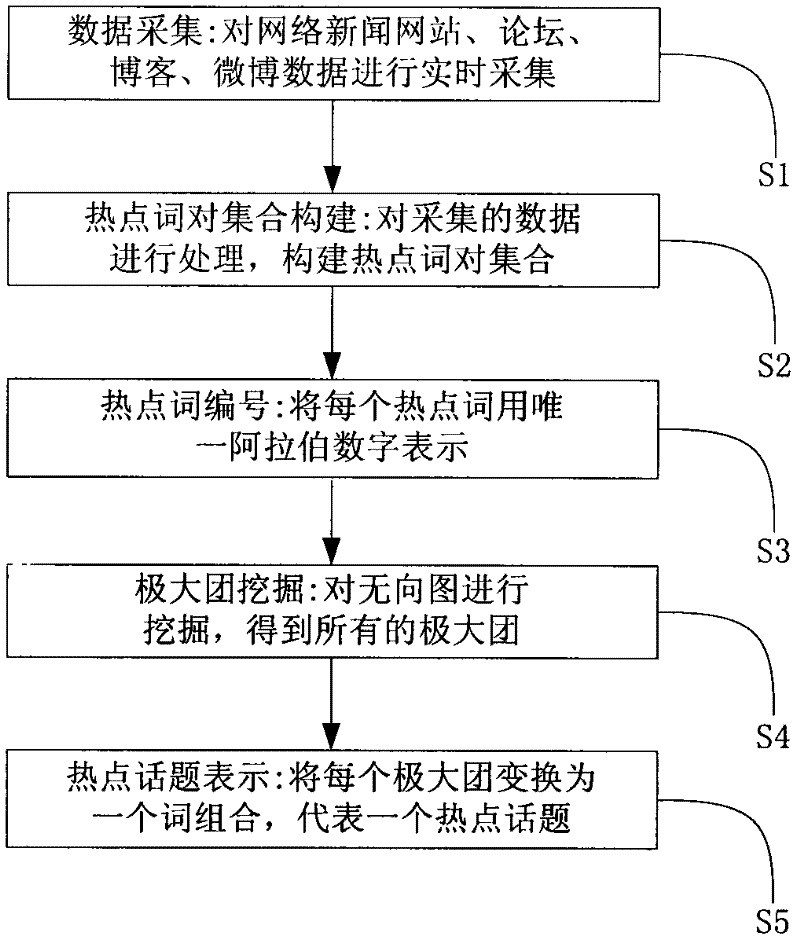
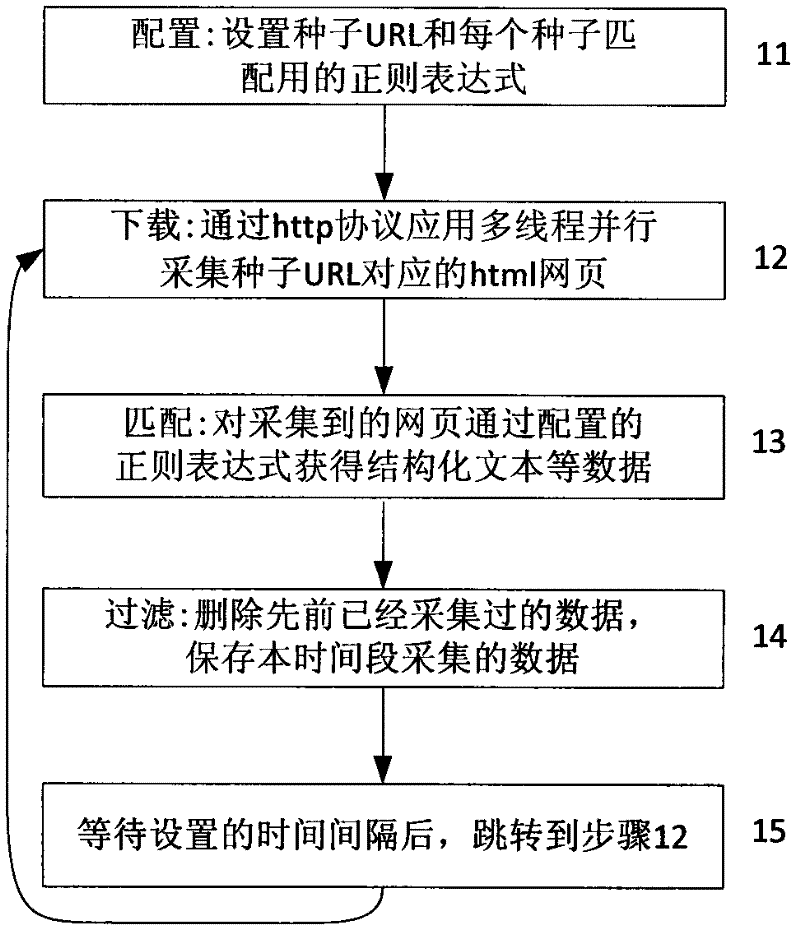
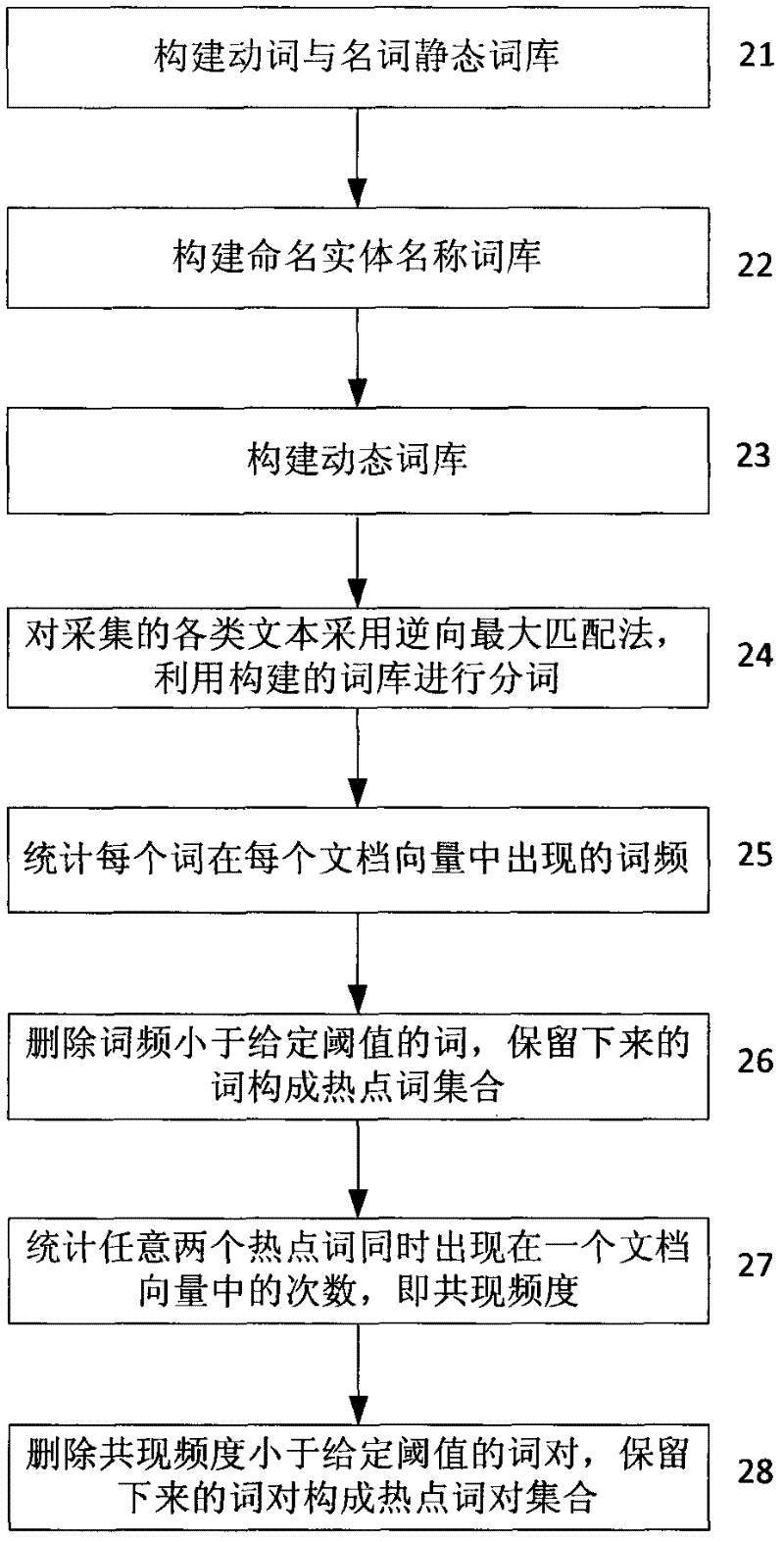
The embodiment of the invention discloses a method and device for detecting network hot topics found based on a maximal clique. The method comprises the following steps of: acquiring data of a network news website, a forum, a blog and a microblog in a real time; carrying out word segmentation, word frequency statistics and other processing on the acquired data to find all hot point word pairs and construct a hot point word pair set; expressing each hot-point word by using a unique serial number; viewing the hot point word pair set as an undirected graph and excavating the undirected graph to obtain all maximal cliques; and transforming each maximal clique into a word combination for expressing one hot point topic. The invention also discloses a device for detecting the network hot topics. According to the embodiment of the invention, the hot point topics in the network can be accurately found in a real time, the detection speed and precision of the hot point topics are improved and higher practical value is obtained.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Methods of networking interrogation devices for structural conditions
InactiveUS7668665B2Vibration measurement in solidsSpecial data processing applicationsDirected graphUndirected graph
Owner:ADVANCED STRUCTURE MONITORING
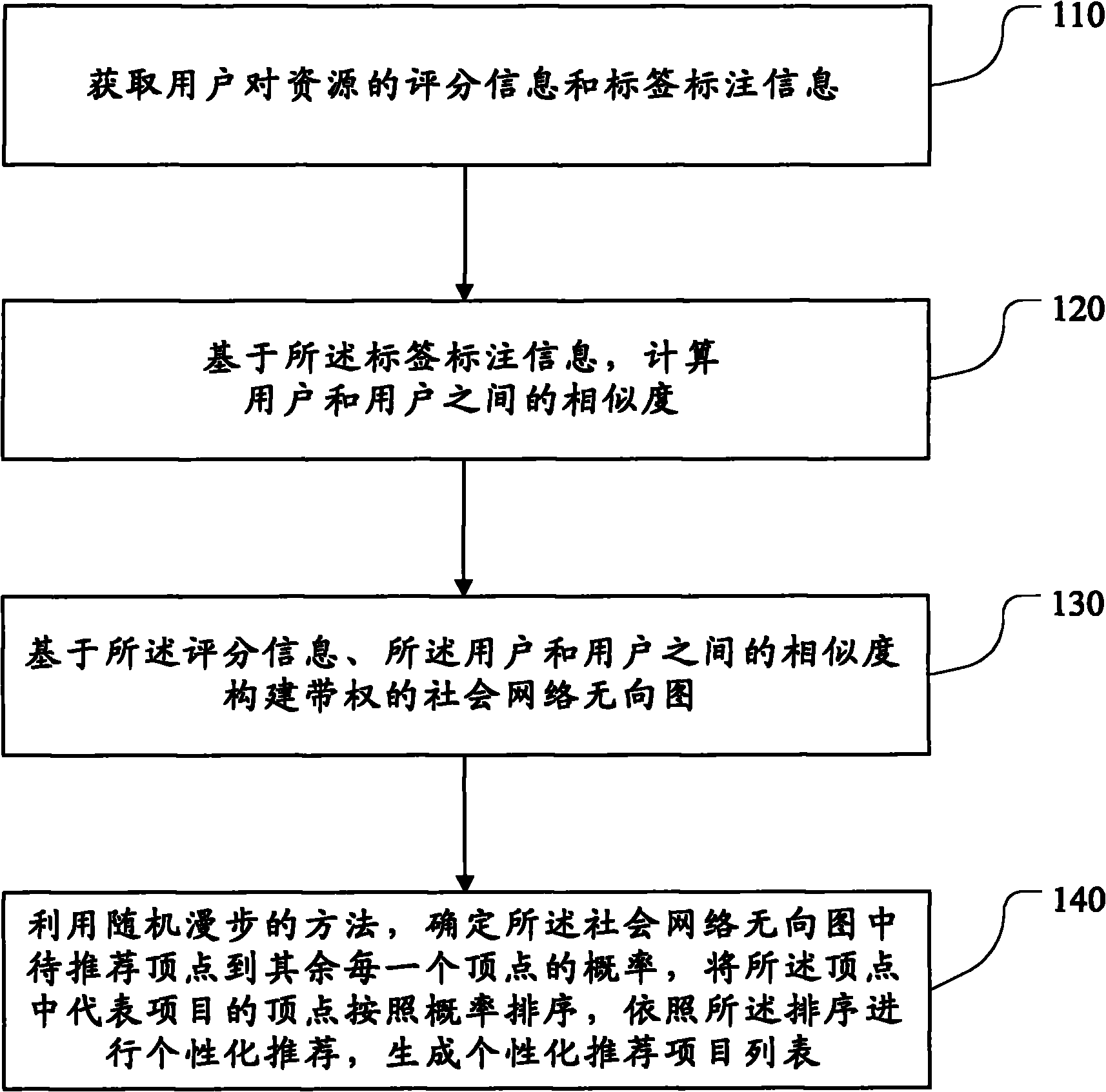
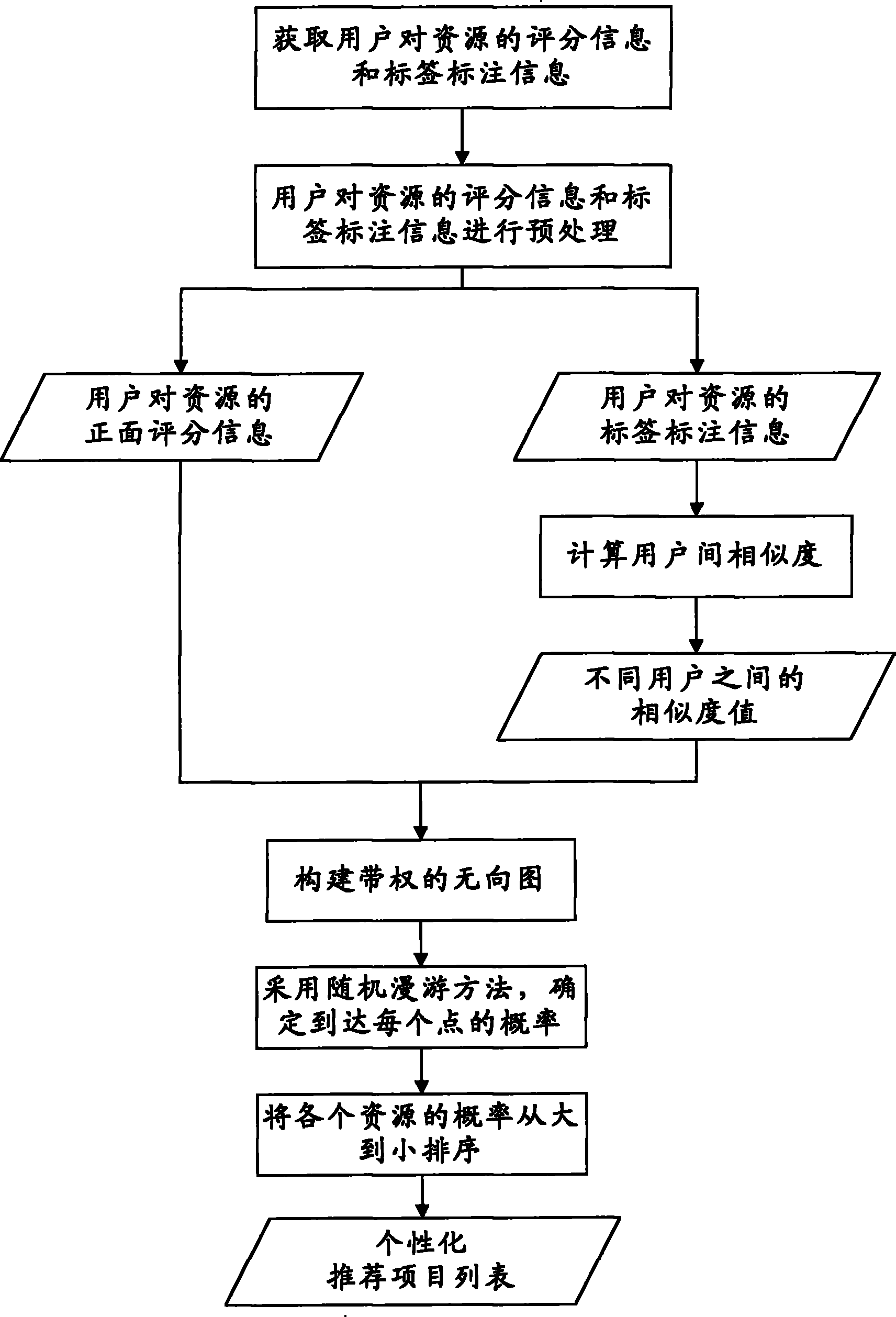
Personalized recommended method based on picture under social network and system thereof
InactiveCN101944218APersonalized recommendations work wellImprove accuracyCommerceSpecial data processing applicationsPersonalizationUndirected graph
The invention discloses a personalized recommended method based on a picture under a social network and a system thereof. The method comprises: obtaining scoring information and label marking information to resource of users; based on the label marking information, calculating similarity between the users; based on the marking information and the similarity between the users, building a weighted social network undirected graph; determining the probability from a vertex to be recommended in the social network undirected graph to each reset vertex by a random walk method; sorting the vertex of a representative item in the vertexes according to the probability; and according to the sorting, generating the personalized recommended item list. The invention can accurately provide the personalized recommendation relevant to user preferences to different users by introducing the similarity.
Owner:PEKING UNIV
Method of, system for, and computer program product for providing efficient utilization of memory hierarchy through code restructuring
InactiveUS6839895B1Reducing memory hierarchy access costReducing cache missSoftware engineeringProgram controlCode refactoringUndirected graph
Code restructuring or reordering based on profiling information and memory hierarchy is provided by constructing a Program Execution Graph (PEG) corresponding to a level of the memory hierarchy, partitioning this PEG to reduce estimated memory overhead costs below an upper bound, and constructing a PEG for a next level of the memory hierarchy from the partitioned PEG. The PEG is constructed from control flow and frequency information from a profile of the program to be restructured. The PEG is a weighted undirected graph comprising nodes representing basic blocks and edges representing transfer of control between pairs of basic blocks. The weight of a node is the size of the basic block it represents and the weight of an edge is the frequency of transition between the pair of basic blocs it connects.
Owner:IBM CORP
Table recognizing method and table recognizing system
ActiveUS20150093021A1Improve recognition accuracyImprove efficiencyImage analysisCharacter and pattern recognitionUndirected graphAlgorithm
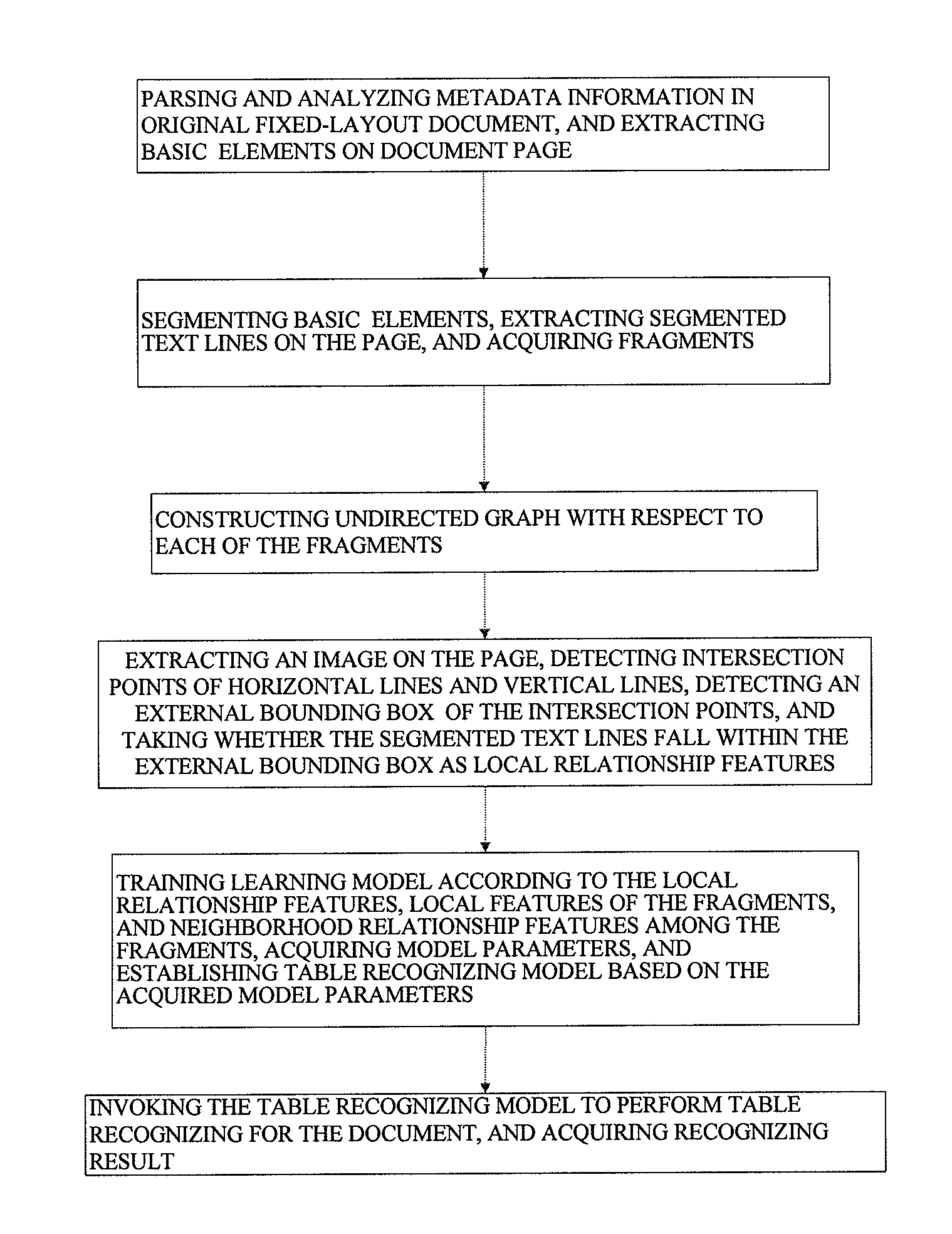
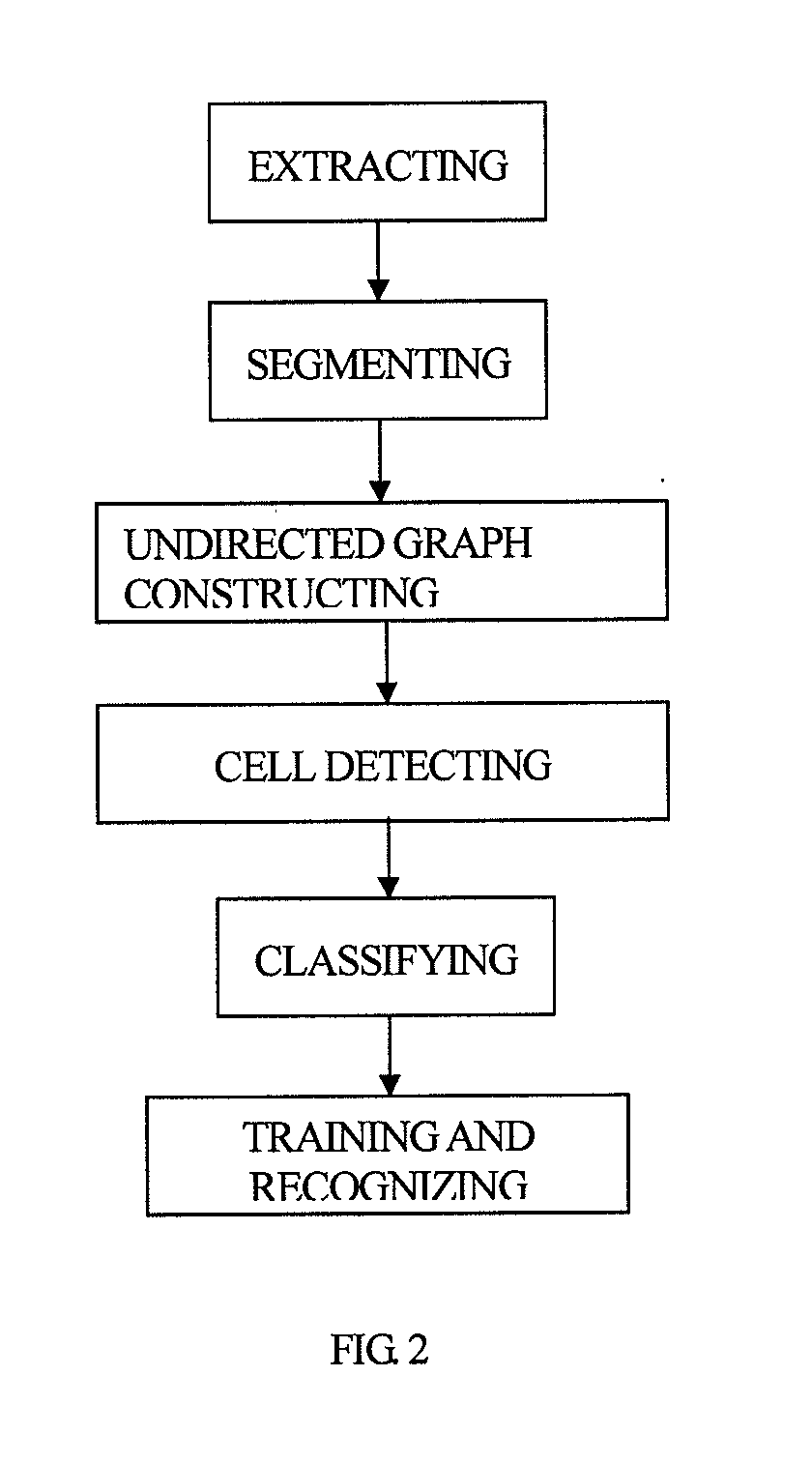
Provided is a table recognizing method, comprising: parsing and analyzing metadata information in an original fixed-layout document, and extracting basic elements on a page of the document; segmenting the basic elements, extracting segmented text lines on the page, and acquiring fragments; constructing an undirected graph with respect to each of the fragments; extracting an image on the page, detecting intersection points of horizontal lines and vertical lines, detecting an external bounding box of the intersection points, and taking whether the segmented text lines fall within the external bounding box as local relationship features; training a learning model according to the local relationship features, local features of the fragments, and neighborhood relationship features among the fragments, acquiring model parameters, and establishing a table recognizing model; and invoking the table recognizing model to perform table recognizing for the document, and acquiring a recognizing result.
Owner:NEW FOUNDER HLDG DEV LLC +1
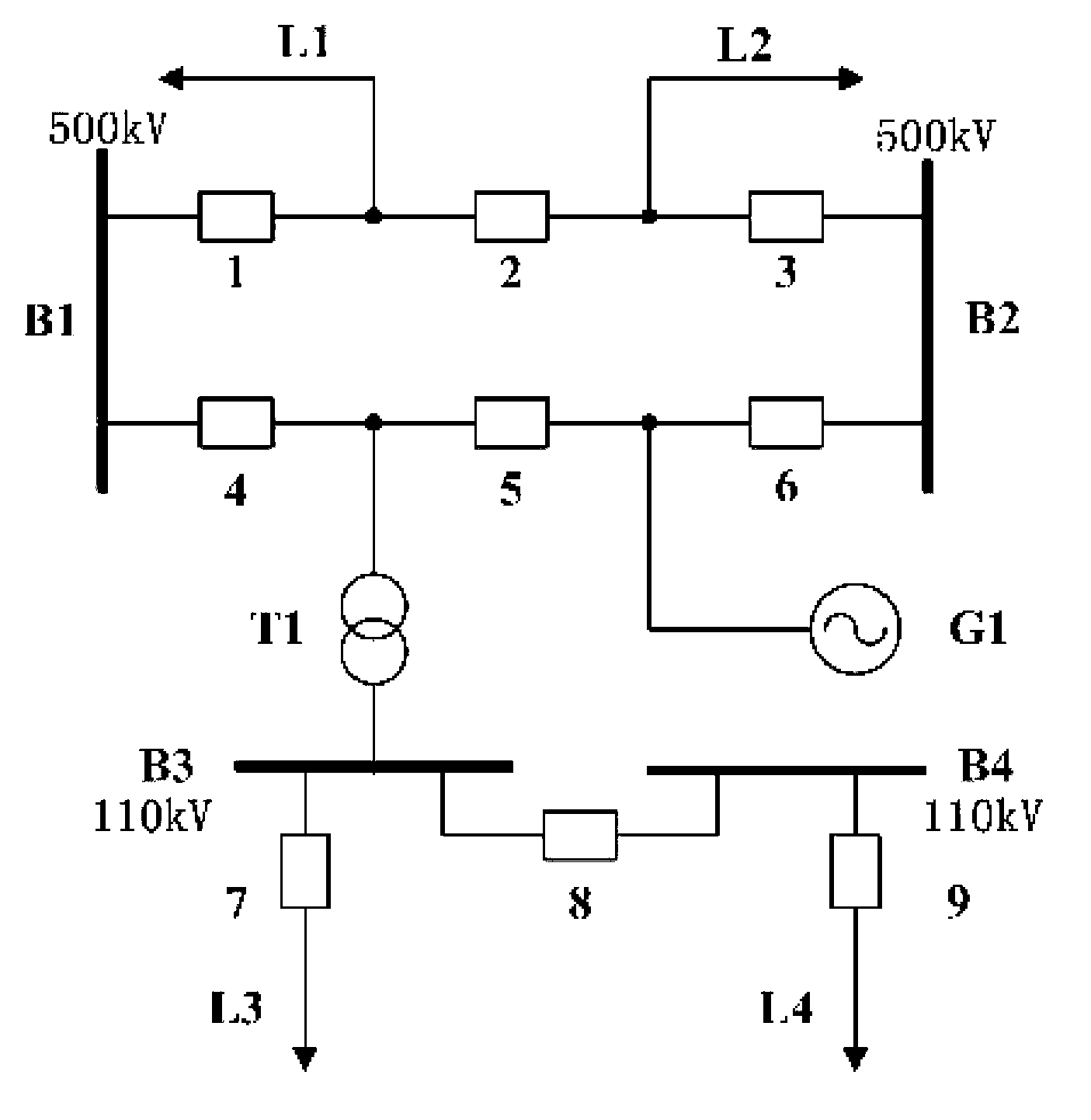
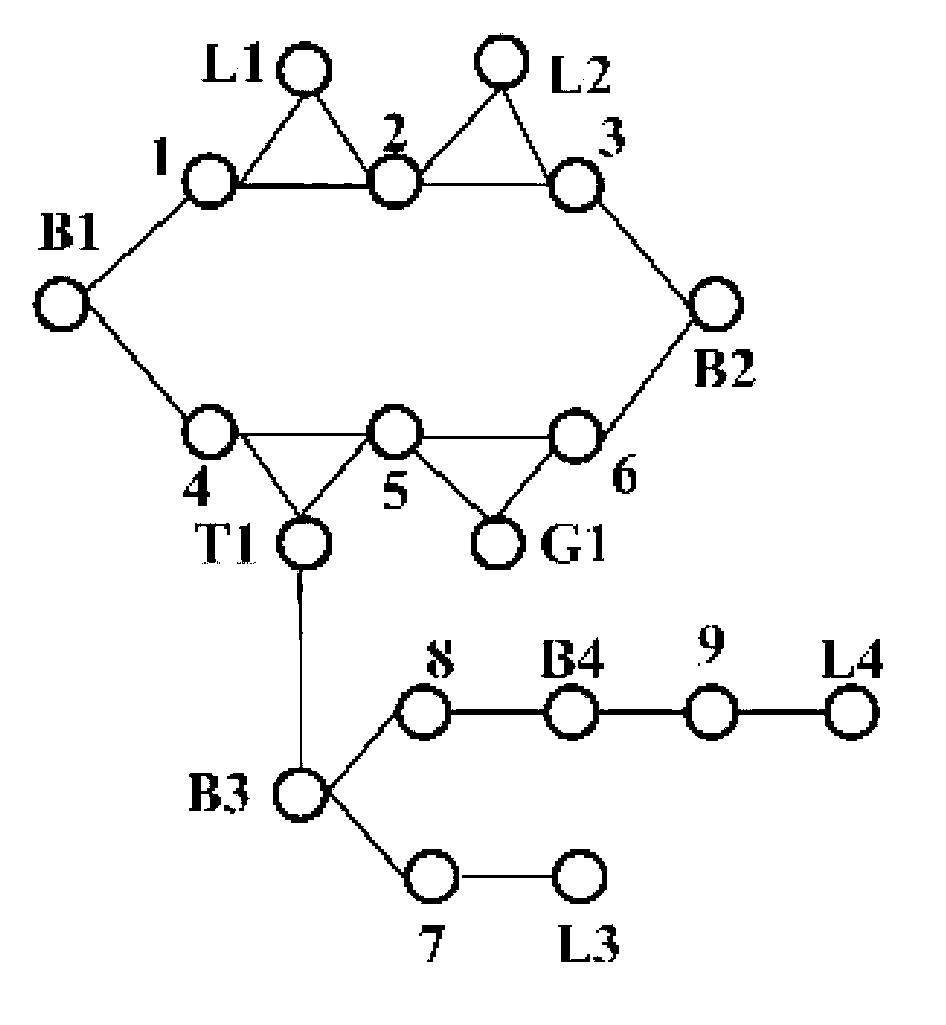
Intelligent substation fault diagnosis method combining topology and relay protection logic
InactiveCN103020713AIncrease profitHigh precisionInference methodsInformation technology support systemWhole bodyTransition function
The invention discloses an intelligent substation fault diagnosis method combining topology and relay protection logic. The intelligent substation fault diagnosis method combining the topology and the relay protection logic comprises the following steps of: analyzing network topology modeling processes of a primary system and a secondary system of an intelligent substation; equivalently replacing all groups with a node quantity of 3 by a group node; simplifying an undirected graph; providing a logical inference method in fit with a Petri net principle according to an extension coefficient, a transition function and a transition function; searching logical relation of the primary system and the secondary system by using the entire intelligent substation system as a whole body; and carrying out a fault diagnosis reasoning process through the logical relation of the primary system and the secondary system. The intelligent substation fault diagnosis method is applied to the fault diagnosis reasoning of an intelligent substation, has the advantages of simple, efficient and rapid network topology constructing and searching process, practical fault diagnosis process and accurate result, and can be used for laying a good foundation for operations, such as fault diagnosis and the like, of the intelligent substation.
Owner:SHANDONG UNIV
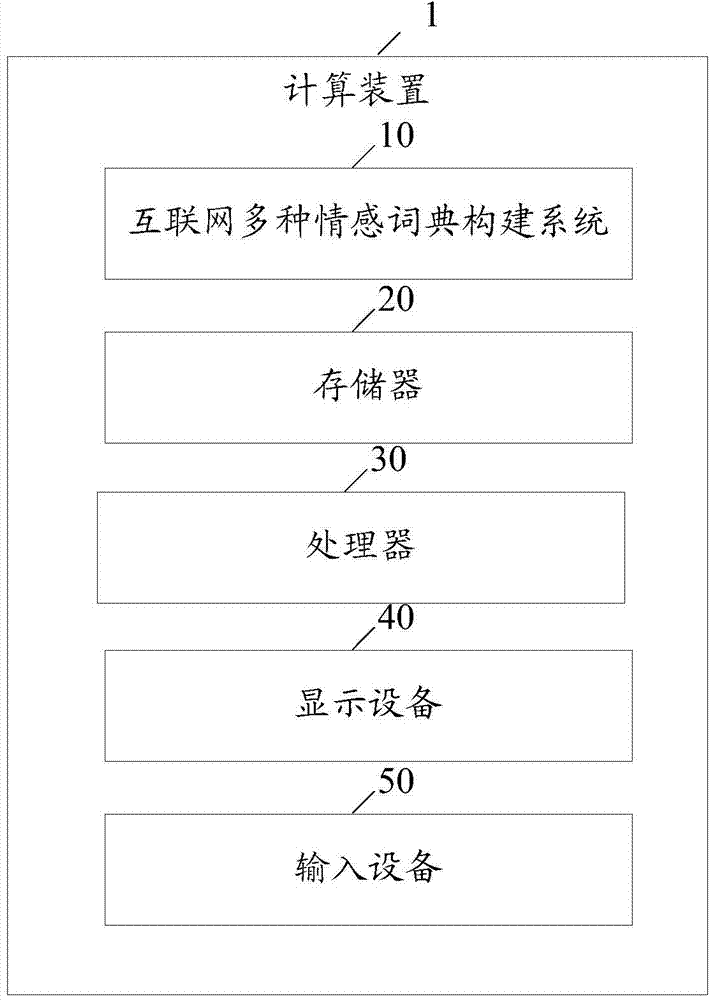
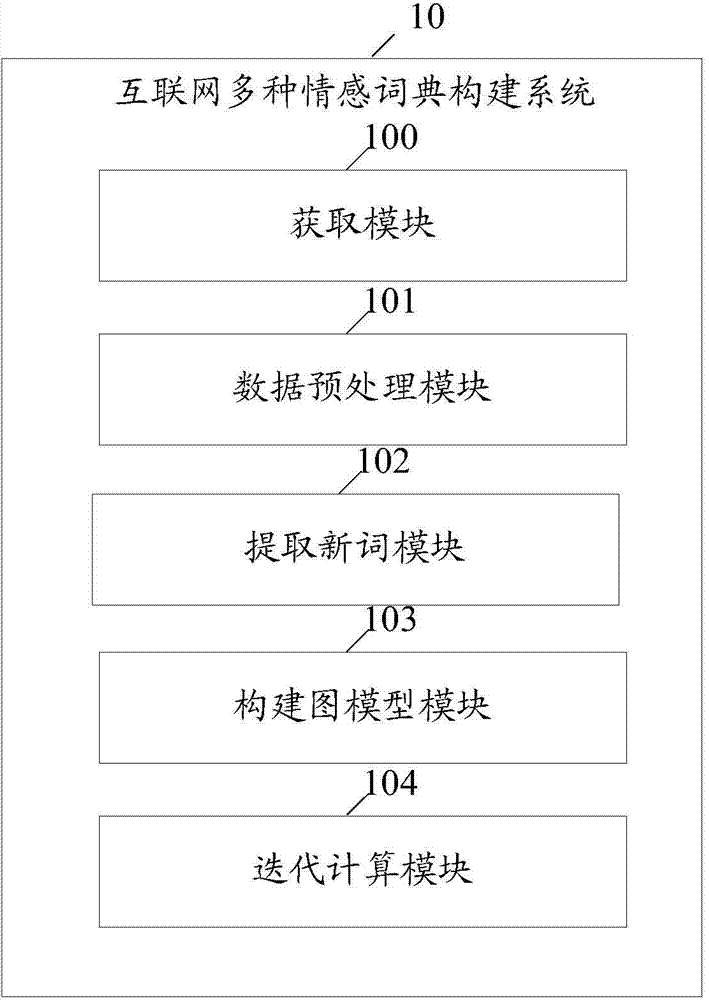
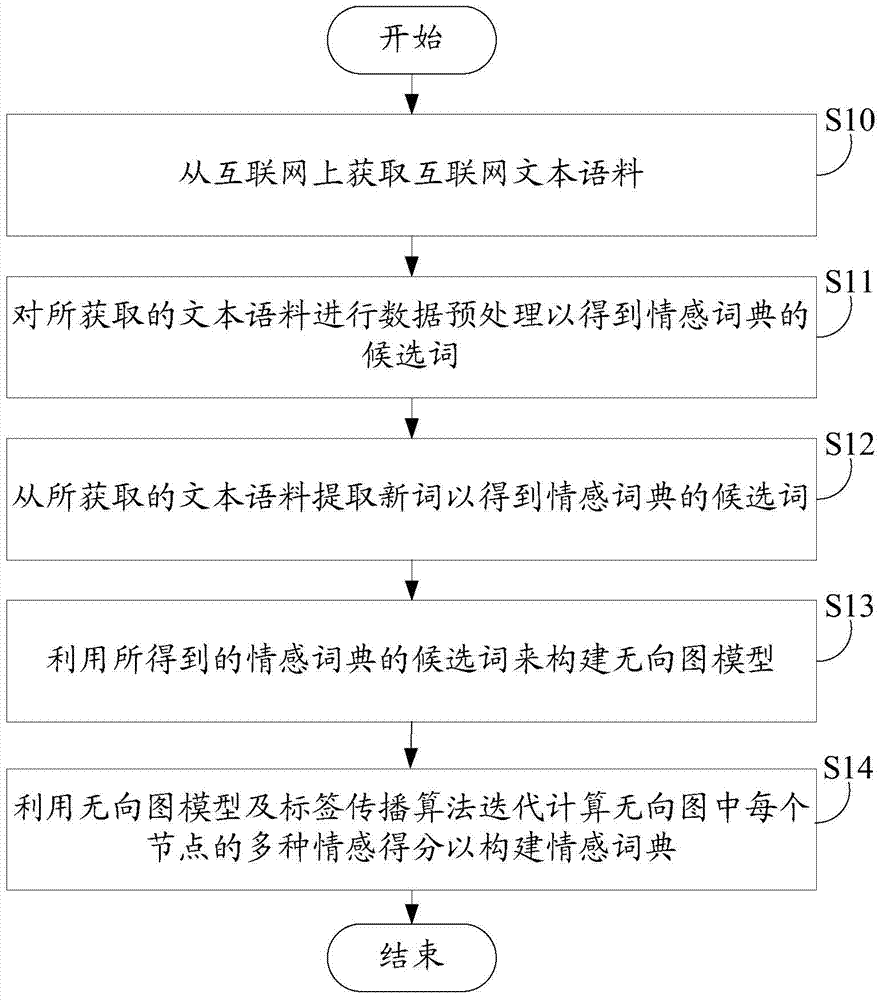
Method and system for constructing multi-emotion dictionary for internet
InactiveCN103544246AEmotion recognition yields rich resultsSpecial data processing applicationsPattern recognitionUndirected graph
Provided are a method and system for constructing a multi-emotion dictionary for the internet. The method includes the steps that internet text linguistic data are obtained from the internet; data preprocessing is carried out on the obtained text linguistic data to obtain candidate words of the emotional dictionary; new words are extracted from the obtained text linguistic data to obtain candidate words of the emotional dictionary; an undirected graph model is constructed by means of the obtained candidate words of the emotional dictionary; iterative computation is conducted on multiple motion scores of each node in an undirected graph by means of the undirected graph model and a label propagation algorithm to construct the emotion dictionary. According to the method and system, different seed words can be adopted to construct emotion dictionaries with different emotions, and therefore the results of emotion recognition are richer.
Owner:TSINGHUA UNIV +1
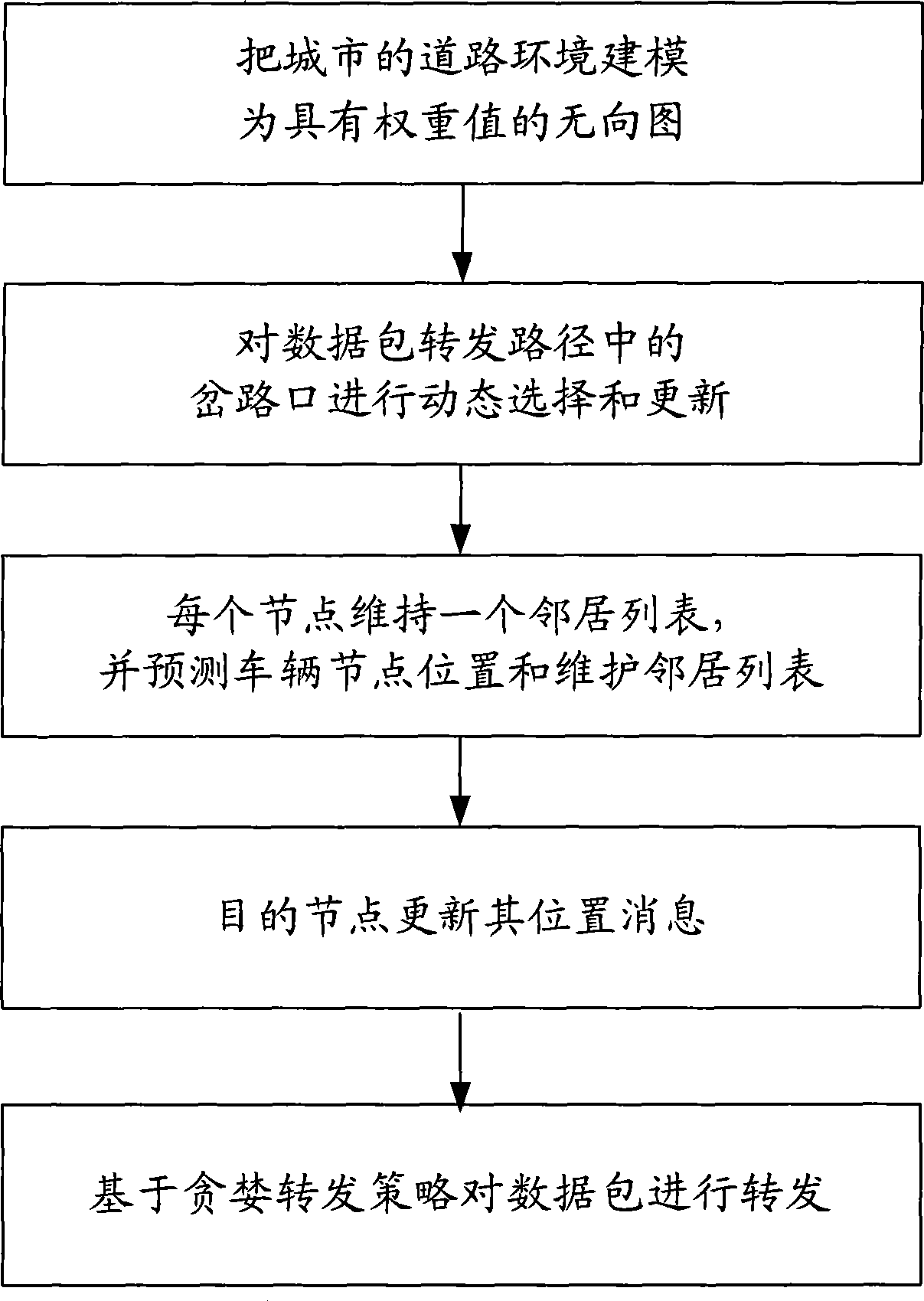
Method for data packet greedy forwarding in vehicle-mounted Ad hoc network
InactiveCN101369982AReduce maintenance workloadImprove effectivenessData switching by path configurationWireless communicationUndirected graphRound complexity
A data packet greedy-algorithm forwarding method for vehicle-mounted Ad hoc network fitting urban environment comprises following steps: (1) modeling urban road environment as undirected graph possessing weight, (2) dynamically selecting and updating fork in data packet forwarding path, (3) each node maintains a neighbor list and predicating and maintaining neighbor list, (4) updating position information of target node,(5) forwarding data packet based on greedy-algorithm forwarding policy. The inventive method fully utilizes characteristic of vehicle-mounted Ad Hoc network node, excels present algorithm in data packet delivery rate, time delay, average hop number and total data quantity of physical layer; the operation step is simple and easy, computation is not complex, demand for real time transmission is satisfied.
Owner:BEIJING UNIV OF POSTS & TELECOMM
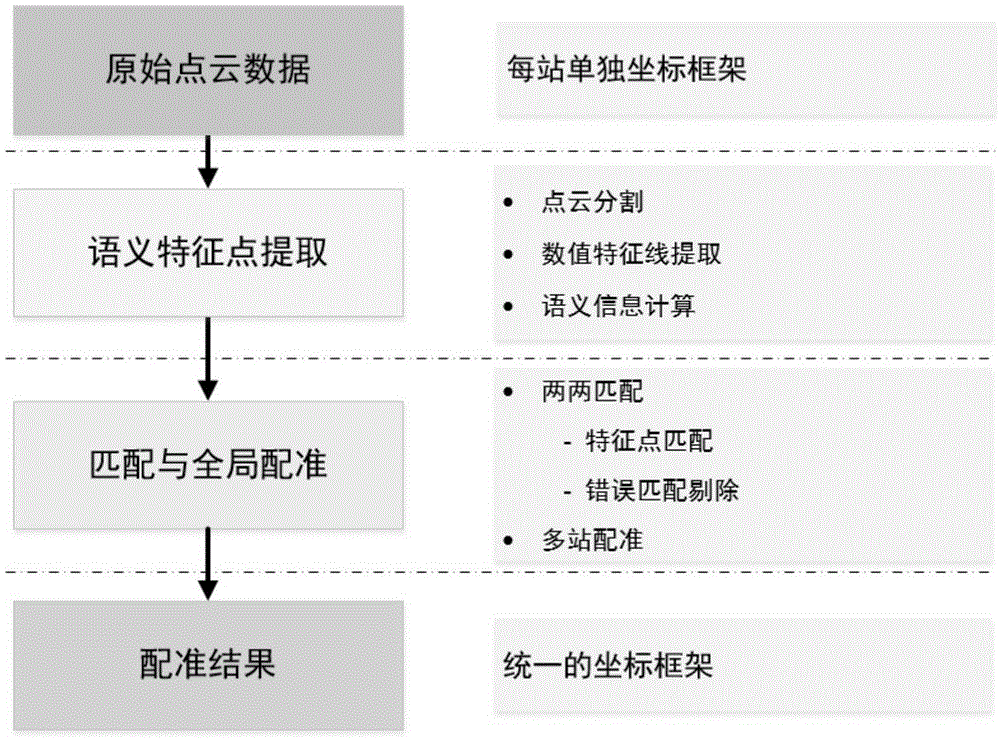
Method suitable for multi-view-angle automatic registration of ground laser point cloud data of multiple stations
InactiveCN105427317ASolve the difficulties in the registration process such as automatic selectionRealize global automatic registrationImage enhancementImage analysisGeometric consistencyPoint density
The invention relates to a method suitable for multi-view-angle automatic global registration of ground laser point cloud data. The method involves two key modules: a module for extracting semantic feature points and a module for feature matching. The method comprises: step 1, extracting the semantic feature points: obtaining the semantic feature points in a series of modes of data slicing, distance clustering, geometric element fitting and the like; step 2, matching the semantic feature points: matching the semantic feature points by constructing a triangular geometric constraint condition and a semantic constraint condition, and removing error matching in a geometric consistency clustering mode; and finally, constructing a weighted undirected graph by taking a reciprocal of a feature point number as a weight, and finally obtaining global registration parameters of all stations by taking a minimum spanning tree of the weighted undirected graph as a registration path, thereby realizing global optimal registration. According to the invention, the method suitable for multi-view-angle automatic global registration of the ground laser point cloud data is constructed; the method can effectively resist influences of noise, point density and coverage; and the method improves the laser scanning operation efficiency, thereby having very high practical values.
Owner:WUHAN UNIV
Simplifying a graph of correlation rules while preserving semantic coverage
InactiveUS20140074764A1Simplify pluralityMathematical modelsKnowledge representationNODALUndirected graph
A method, system and computer program product for simplifying a plurality of correlation rules of a graph. The method includes the steps of: receiving correlation rules; creating an undirected graph; removing redundant edges from the undirected graph; splitting nodes in the undirected graph; replacing a probability that an edge that connects two nodes to a seed value; modifying the seed value by adding a first value to said seed value and adding a second value to the first value; determining a maximum modified seed value; adding the maximum modified seed value to a probability that the uncertain edge connects two nodes; removing any temporary certain edge; and running a minimum spanning tree algorithm on said modified undirected graph.
Owner:IBM CORP
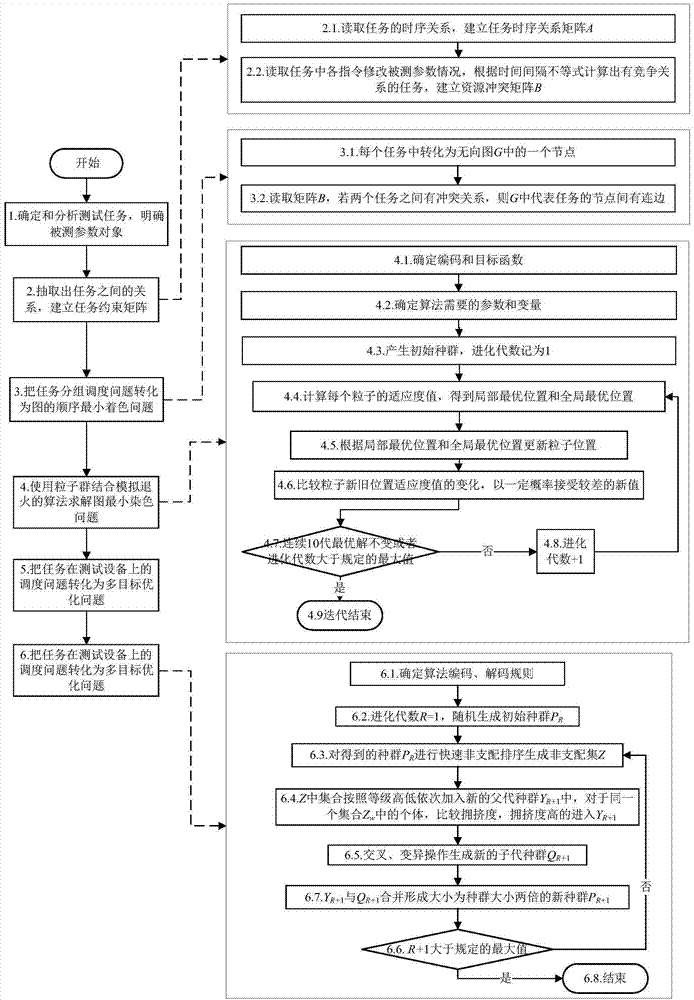
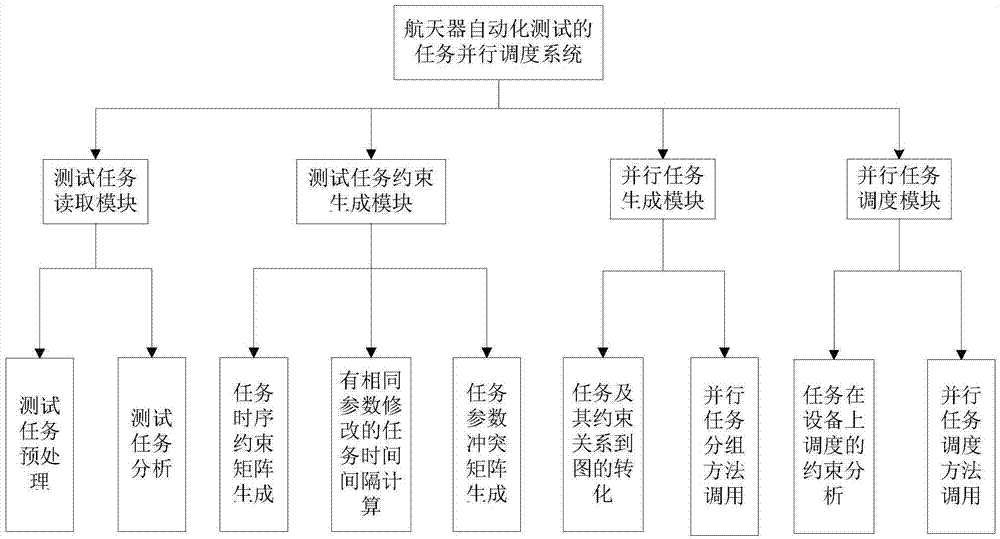
Two-stage scheduling method of parallel test tasks facing spacecraft automation test
InactiveCN104239213AEasy to callEasy to handleConcurrent instruction executionSoftware testing/debuggingColoring problemDegree of parallelism
The invention relates to a two-stage scheduling method of parallel test tasks facing a spacecraft automation test, which belongs to the field of parallel tests. The method comprises the following stages: in the first stage, the test tasks, task instructions and tested parameters are analyzed and determined, a constraint relation between the tasks is defined, a time sequence constraint matrix and a parameter competitive relation matrix are established, the tasks and the constraint relation between the tasks are changed into undirected graphs, a parallel task scheduling problem is changed into a minimum coloring problem in the sequence of the tops of the graphs, a method based on the combination of a particle swarm and simulated annealing is used for solving, and then a test task group with the maximal degree of parallelism is obtained; in the second stage, the obtained test task group with the maximal degree of parallelism is distributed on limited test equipment, and then an optimal scheduling scheme is obtained. According to the two-stage scheduling method, the constraint relation among a plurality of test tasks is quickly established, the independence between the test tasks is analyzed, the degree of parallelism of the test tasks is increased, the optimal scheduling of the tasks on the equipment is realized when constraint conditions are satisfied, and the test efficiency is improved.
Owner:BEIHANG UNIV
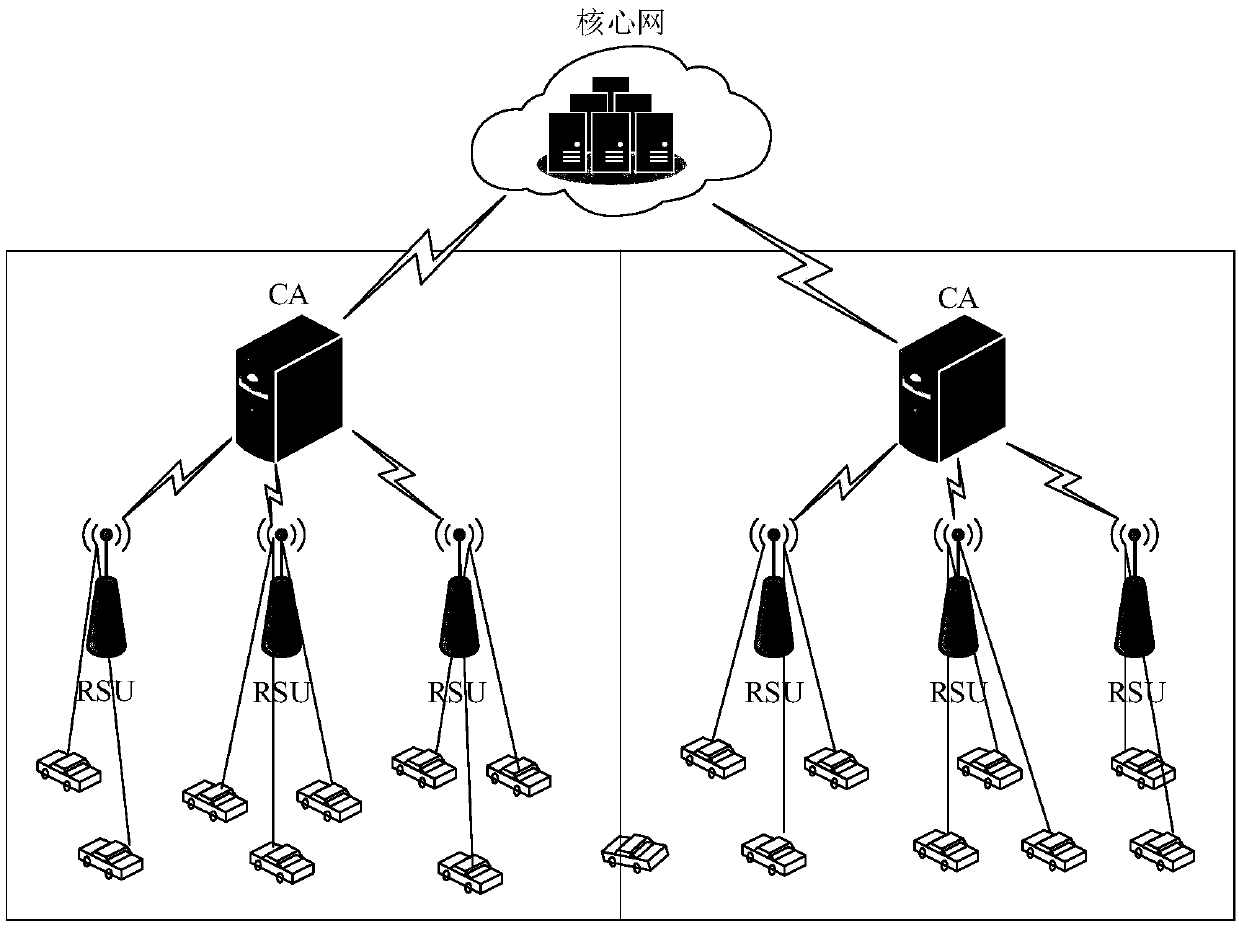
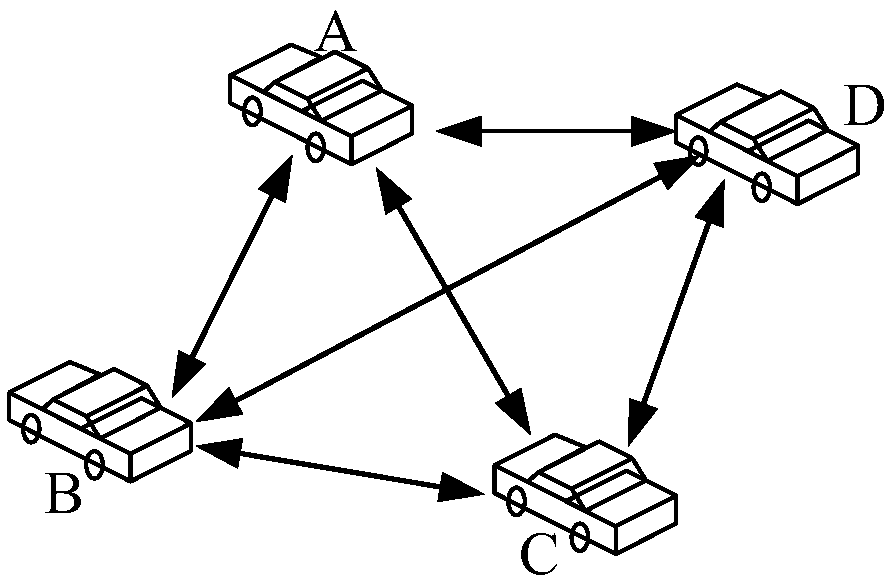
A vehicle networking architecture based on block chain and a working method thereof
ActiveCN109068299ASolve the centralization problemSolve the problem of mutual distrust between entitiesParticular environment based servicesUser identity/authority verificationUndirected graphIn vehicle
The invention discloses a vehicle networking structure based on a block chain and a working method thereof. The vehicle networking structure comprises an interconnected vehicle entity, a vehicle-mounted unit OBU, a roadside unit RSU, a core network and a block chain network. It has the typical characteristics of decentralization, distribution, collective maintenance and incapability of tampering.It can effectively solve the problem of centralization of traditional vehicle networking architecture and mutual distrust between entities. At that same time, the invention provides an undirected graph generation method, an identity privacy protection method and a location privacy protection method when the beacon information is uploaded by a vehicle, thereby solving the problem of identity and location privacy disclosure of a vehicle networking architecture based on a block chain.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
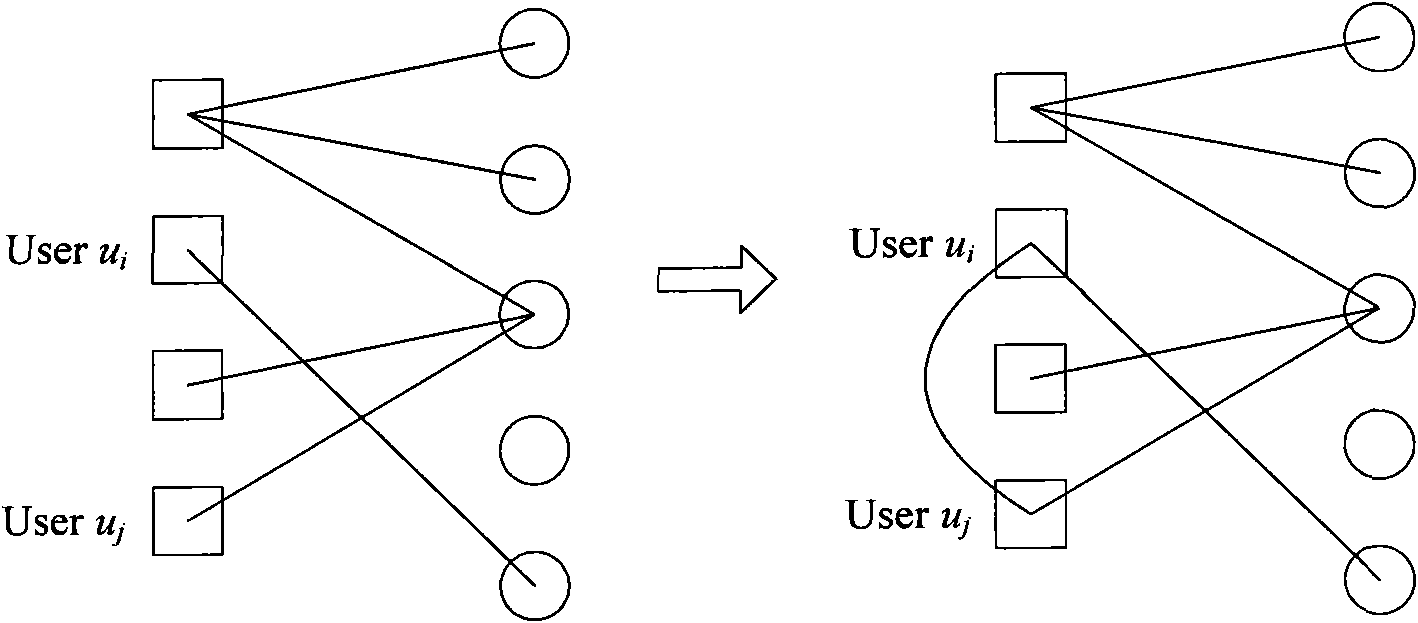
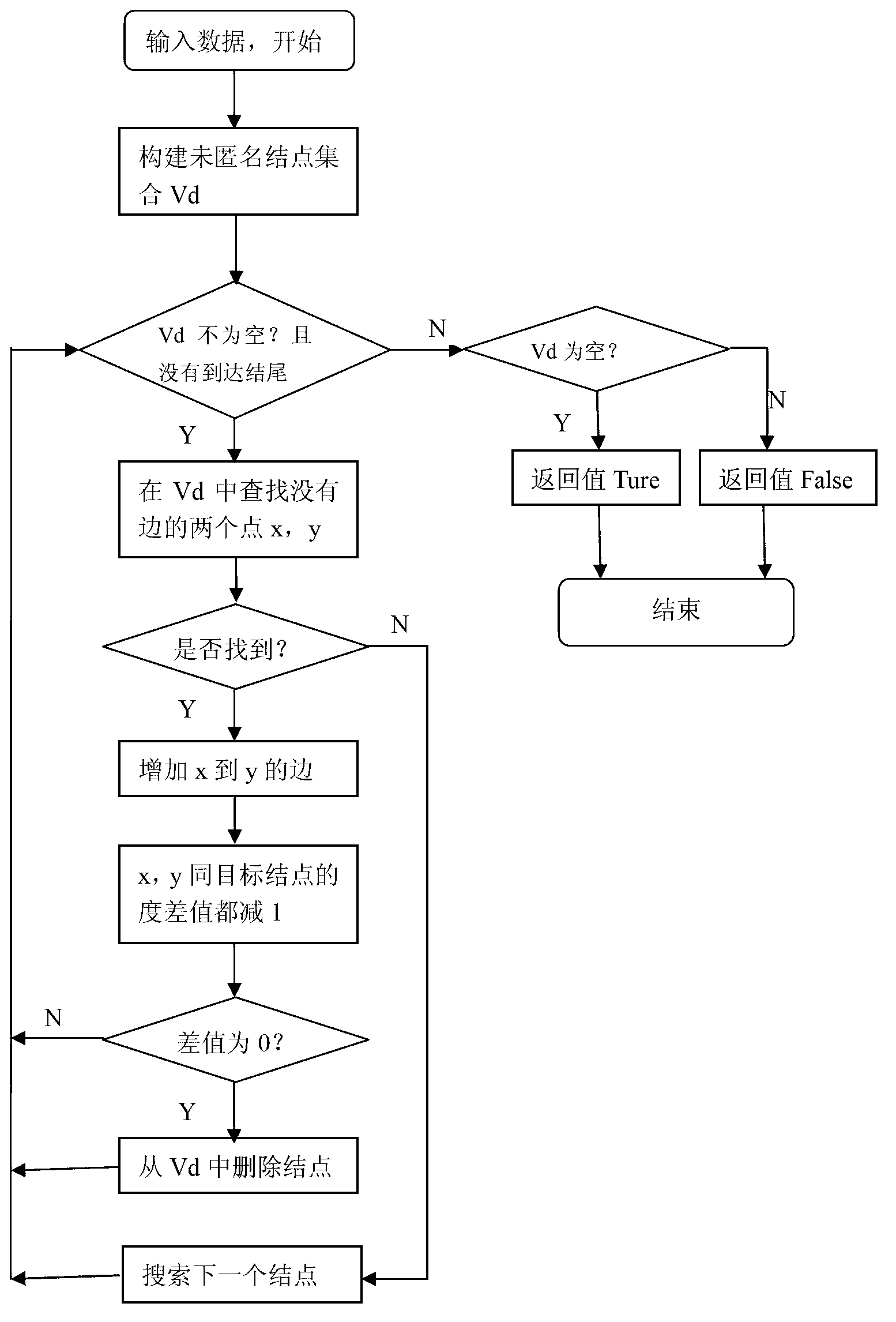
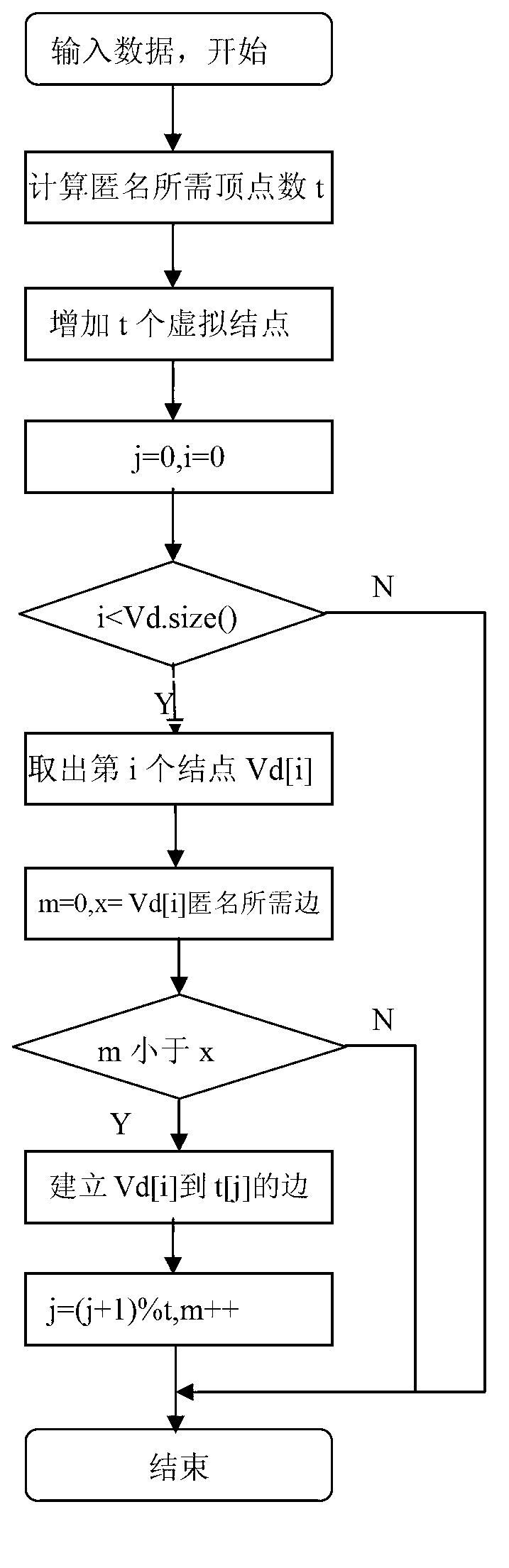
Privacy protecting method for social network based on undirected graph modification
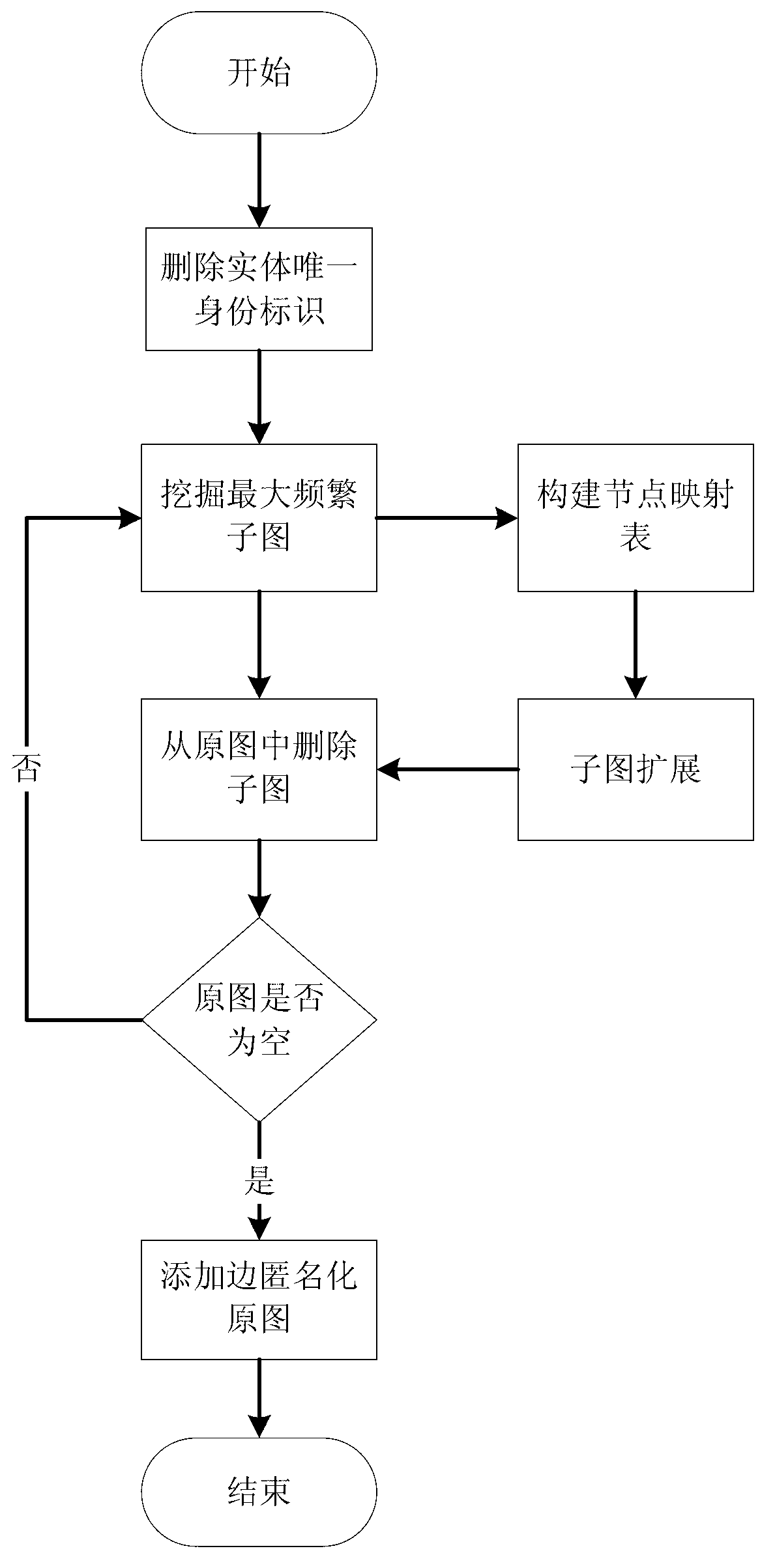
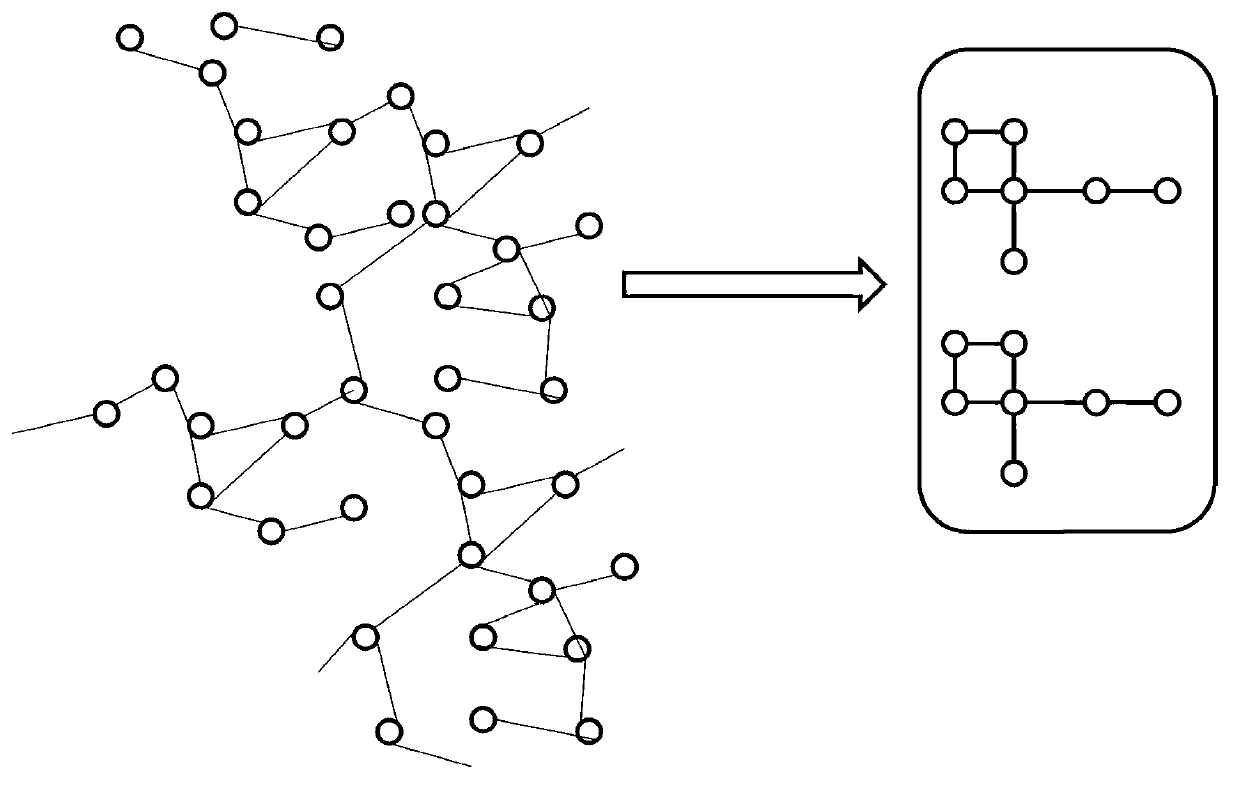
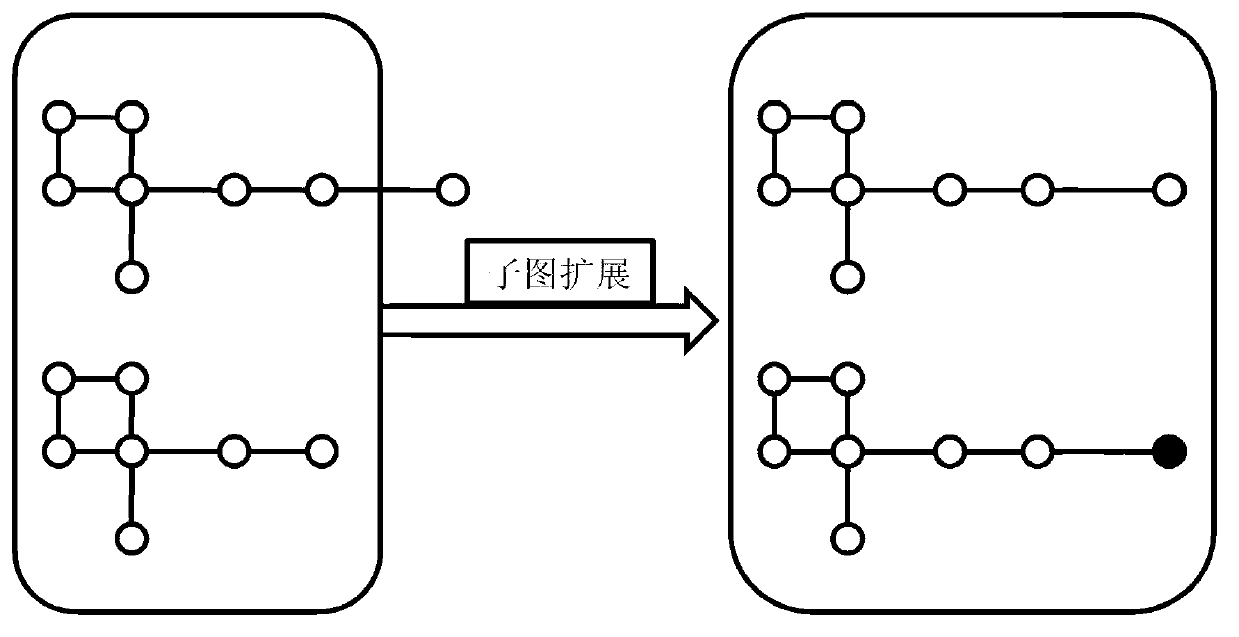
ActiveCN103218397AAvoid repositioningProtect personal privacyDigital data protectionSpecial data processing applicationsNODALUndirected graph
The invention discloses a privacy protecting method for a social network based on undirected graph modification. The method comprises the following steps: (1) establishing an undirected graph of the social network; (2) digging the maximum frequent subgraph; (3) establishing a node mapping relation; (4) iteratively expanding the subgraph and improving the mapping table; and (6) forming an anonymity isomorphic graph by adding mapping lines and virtual nodes to the undirected graph. According to the method, the virtual nodes are added, so that each node has other nodes symmetrical thereto, so that re-positioning of user identity is avoided, and personal privacy safety of the user is effectively protected. In addition, the local structure of the social network is finely modified, social network graph data can be externally and safely issued, so that the method is suitable for researching characteristic analysis and statistics of the local structure of the social network, and promotes data digging technology in research and application in the field of social network.
Owner:ZHEJIANG UNIV
Relationship prediction method based on knowledge map
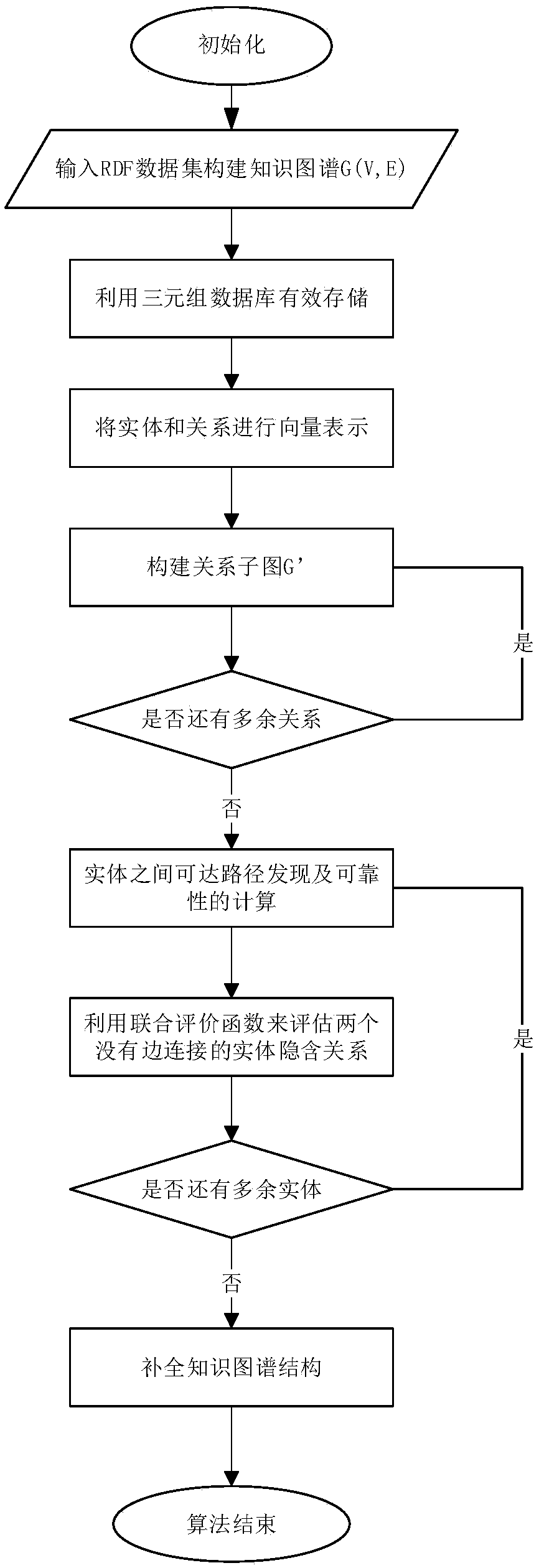
InactiveCN108694469AOptimization is hard to trainDisadvantages of Optimal ComputingForecastingSpecial data processing applicationsJoint evaluationData set
The invention relates to a relationship prediction method based on a knowledge map, and uses an undirected graph to represent the knowledge map, and provides an improved hybrid relationship predictionalgorithm combining a bidirectional relationship path and an embedded type. The method comprises the following steps: (1) constructing a valid knowledge map of a triplet data set and initializing parameters; (2) training each entity and relationship in the knowledge map with the TransE algorithm, and embedding the entity and relationship into a low-dimensional vector space; 3) extracting the relationship label of each triplet and constructing a subgraph of each relationship; (4) on each relationship subgraph, finding a reachable path between every two entities through iterating, dividing thesubgraph according to the graph structure, and calculating the reliability of each reachable path; (5) iterating every two entities without the direct edge join, and evaluating whether there is a hidden relationship between the two entities through the constructed joint evaluation function and loss function; and (6) complementing the knowledge map structure.
Owner:HARBIN ENG UNIV
Interest and network structure double-cohesion social network community discovering method
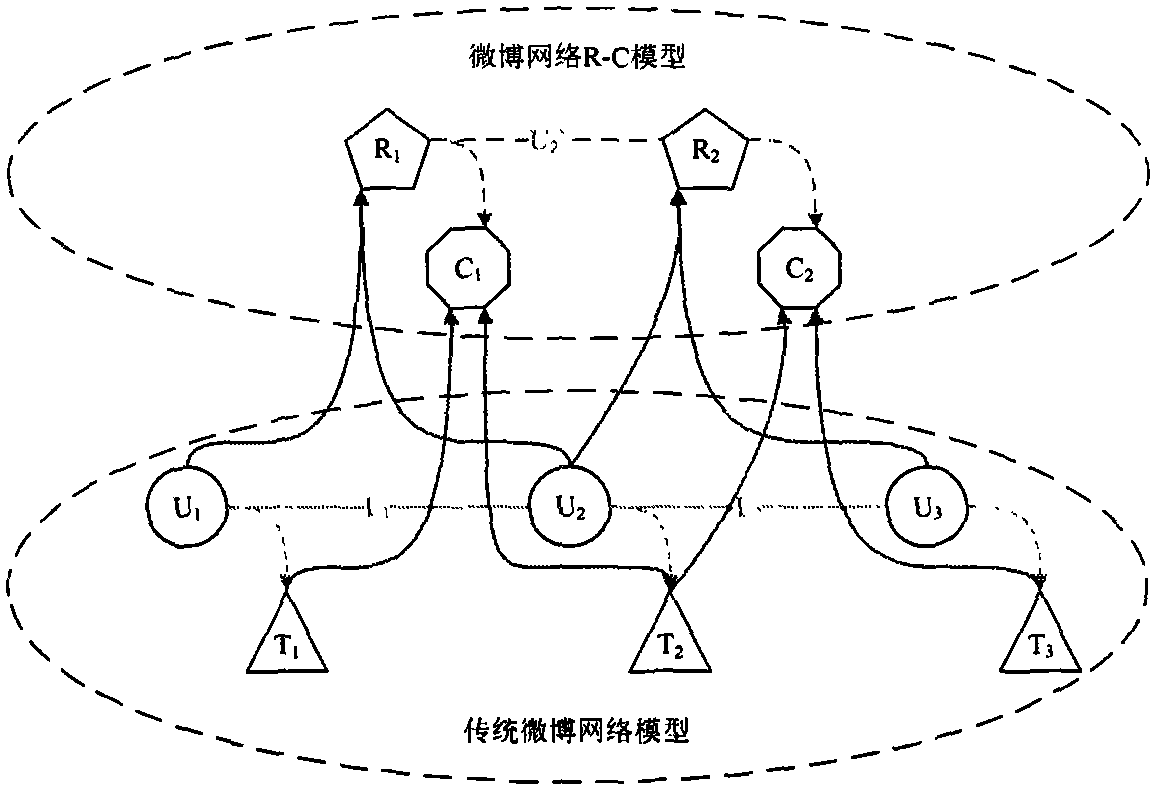
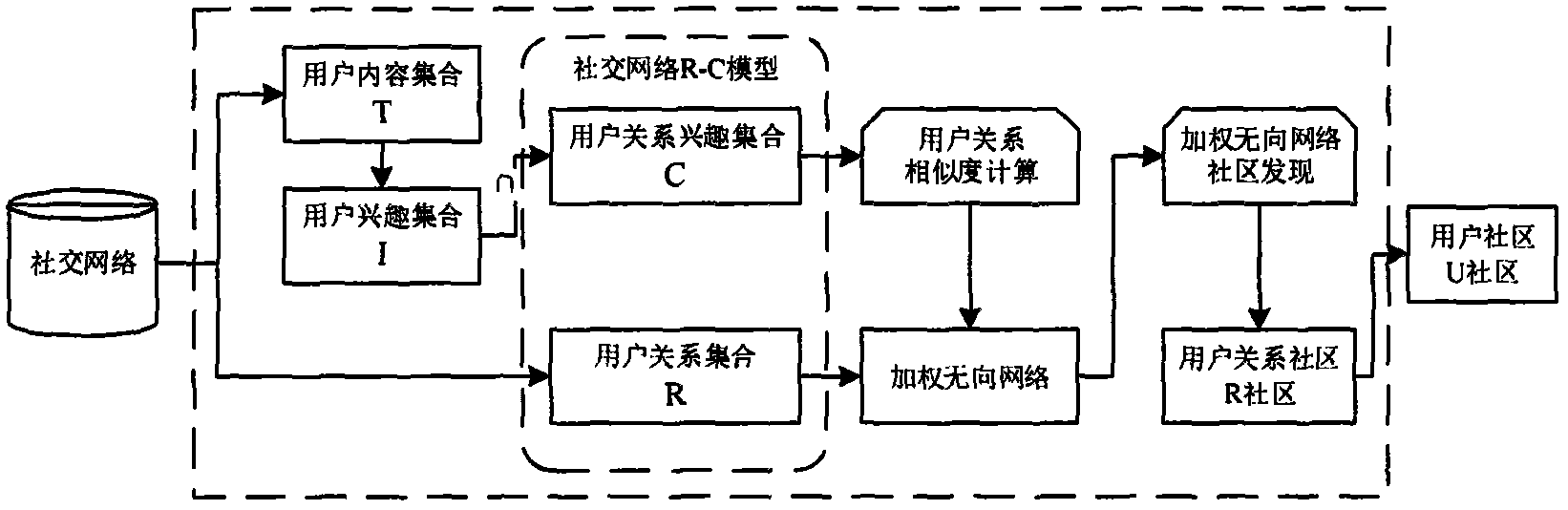
InactiveCN104268271AMining the truthReal community structureData processing applicationsSpecial data processing applicationsUndirected graphNetwork structure
The invention discloses an interest and network structure double-cohesion social network community discovering method which comprises the steps of: firstly, archiving content issued by users in a social network, extracting interest characteristics of each user by using an existing interest characteristic extraction method, and further obtaining interest characteristic collection of each user relationship by adopting intersection operation to form a social network R-C model; on the basis, calculating interest characteristic similarity of two user relationships having two common users by adopting an existing similarity calculation method; then, forming a social network weighted undirected graph by regarding a user relationship in the R-C model as a node, regarding whether a common friend exists between two user relationships as a border, and regarding the interest characteristic similarity among the user relationships as a weight value of the border; then, excavating user relationship community by adopting an existing weighted undirected network community discovering algorithm; finally, mapping the user relationship in the user relationship community into associated users directly to form a social network user community.
Owner:BEIJING UNIV OF CIVIL ENG & ARCHITECTURE
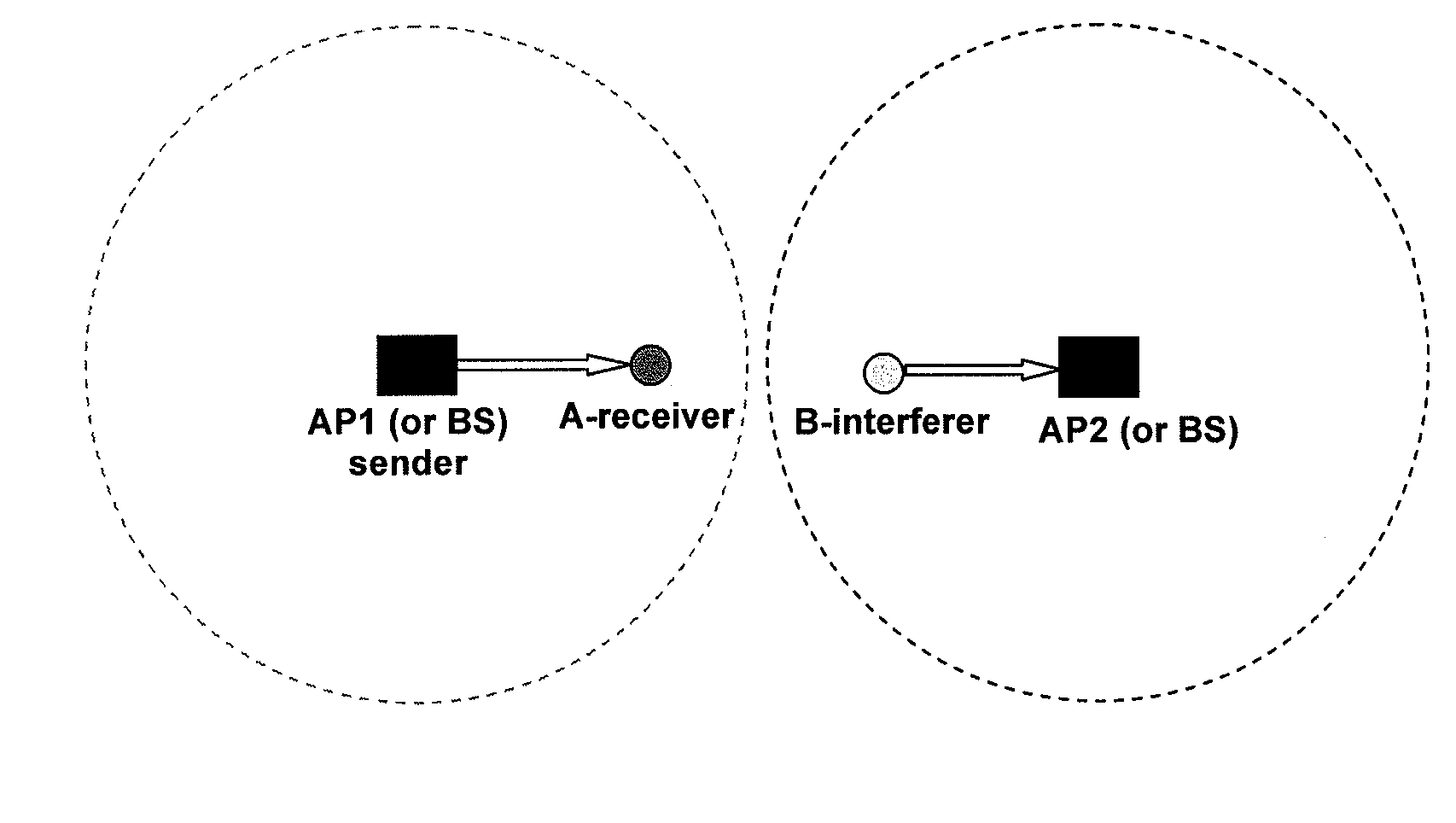
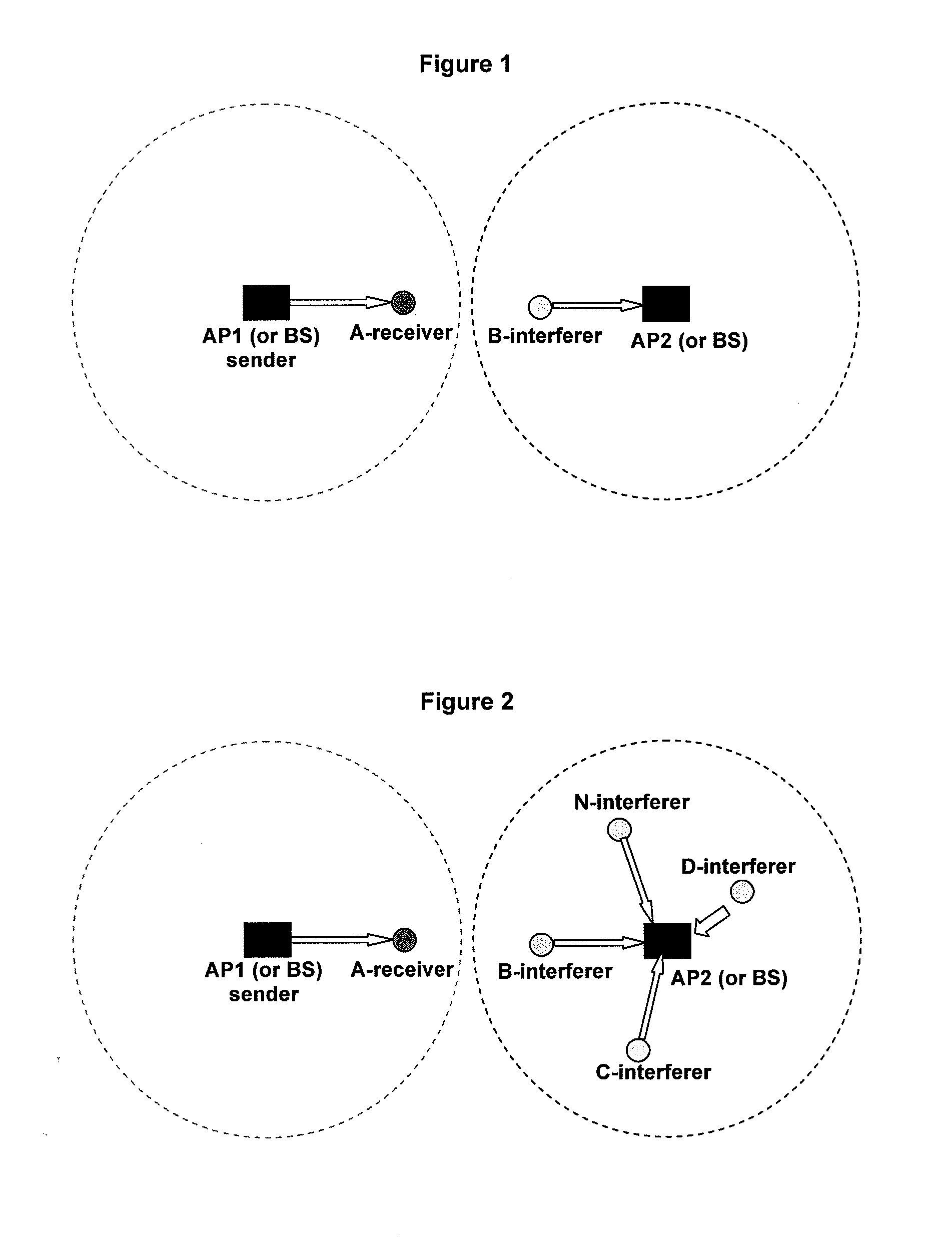
Network interference evaluating method, dynamic channel assignment method and apparatus used in wireless networks
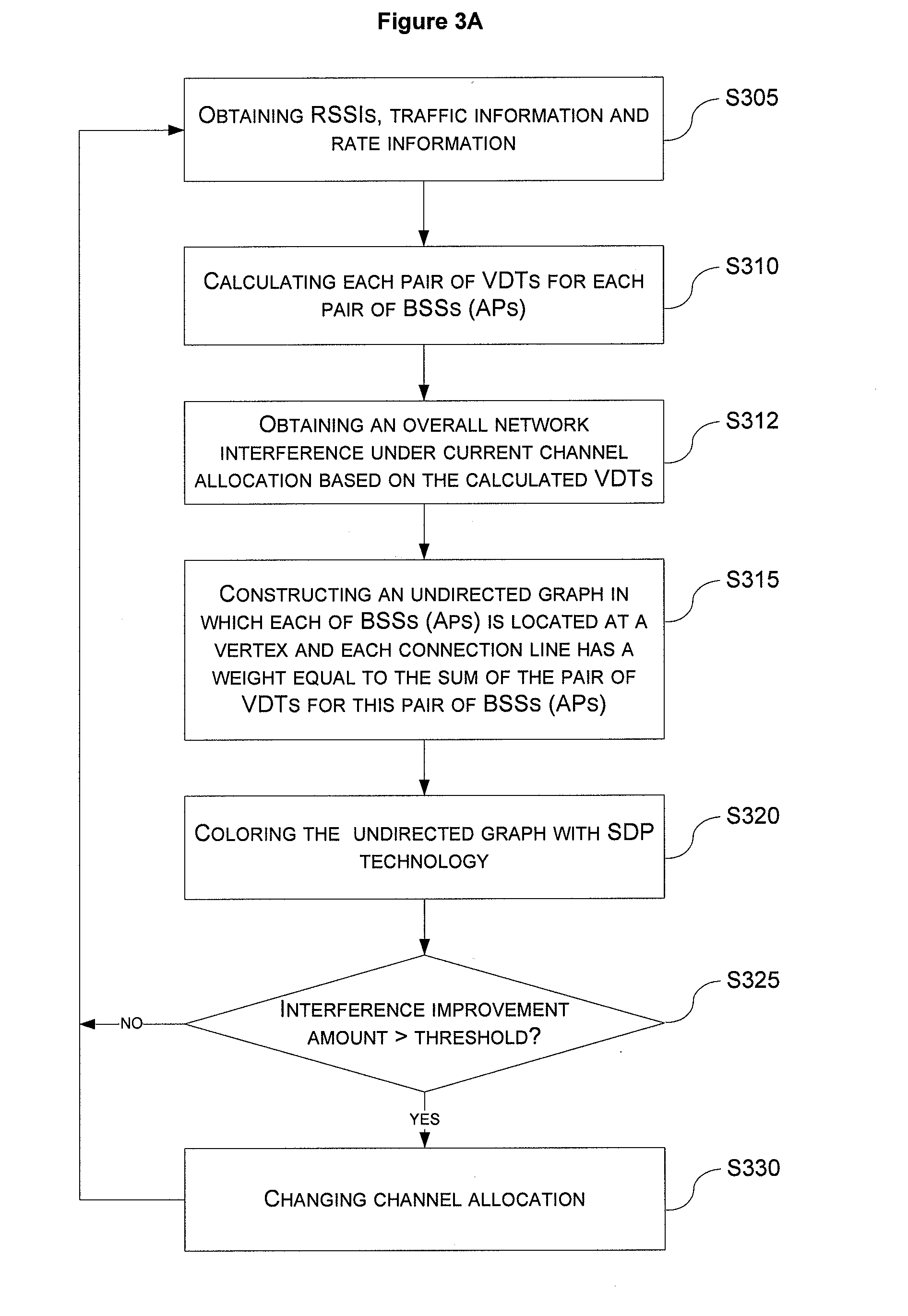
InactiveUS20100008316A1Simple software upgradeAvoiding simplifying assumptionError preventionTransmission systemsDynamic channelCurrent channel
There are disclosed a network interference evaluating method, a dynamic channel assignment method and apparatus used in wireless networks. The dynamic channel assignment method used in a wireless network, comprising steps of: calculating each pair of visual delayed time for each pair of basic service sets based on received signal strength indicators, traffic information and rate information, and evaluating an overall network interference under a current channel allocation based on the calculated visual delayed time; constructing an undirected graph so that each basic service set is located at a vertex, and each connection line between each pair of basic service sets has a weight obtained from the pair of visual delayed time for this pair of basic service sets; coloring the undirected graph to get a new channel allocation approach and an optimized minimal overall network interference under this new channel allocation approach; comparing a difference between the evaluated overall network interference under the current channel allocation and the optimized minimal overall network interference with a predetermined threshold; and changing channel allocation for the basic service sets according to the new channel allocation approach if the difference is larger than the predetermined threshold.
Owner:NEC (CHINA) CO LTD
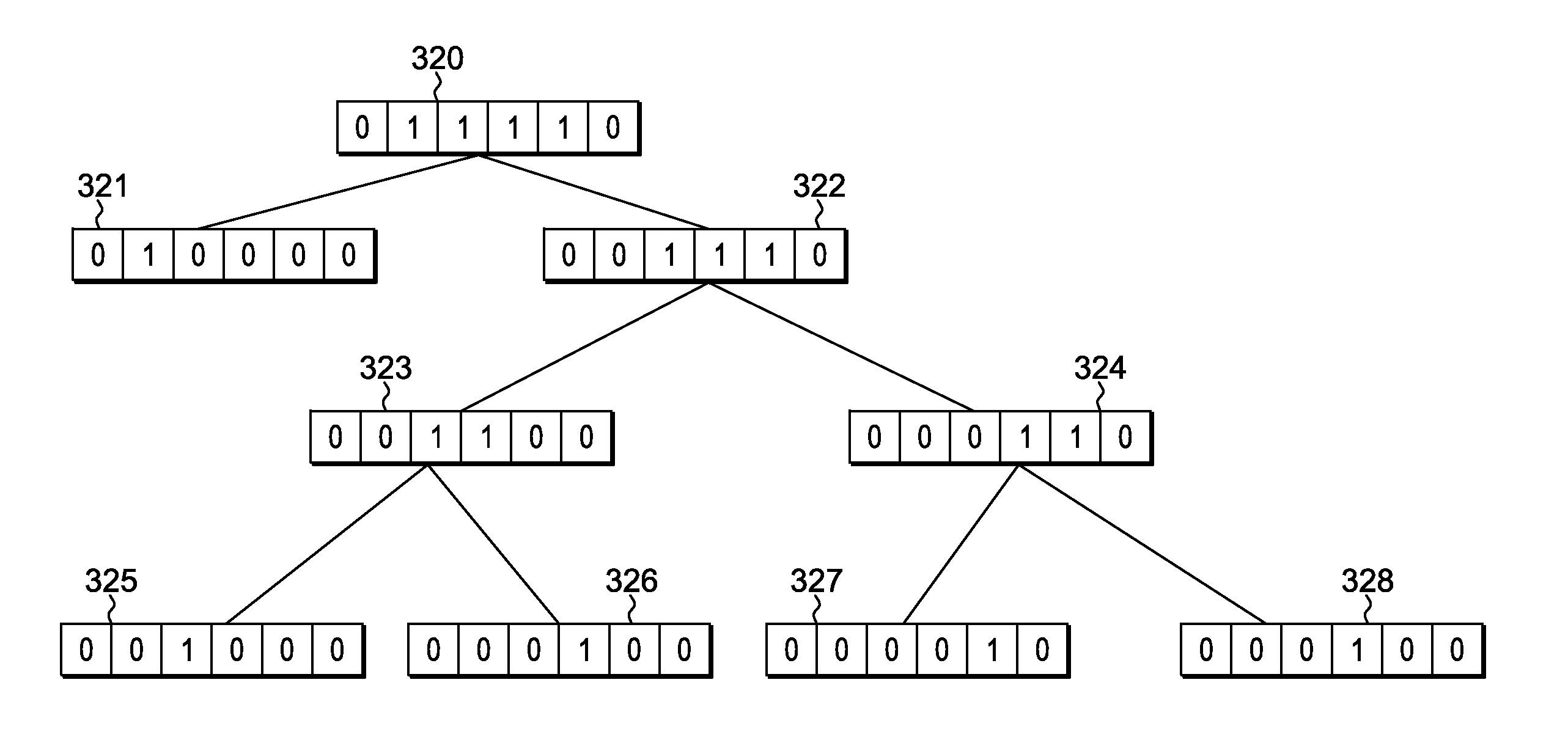
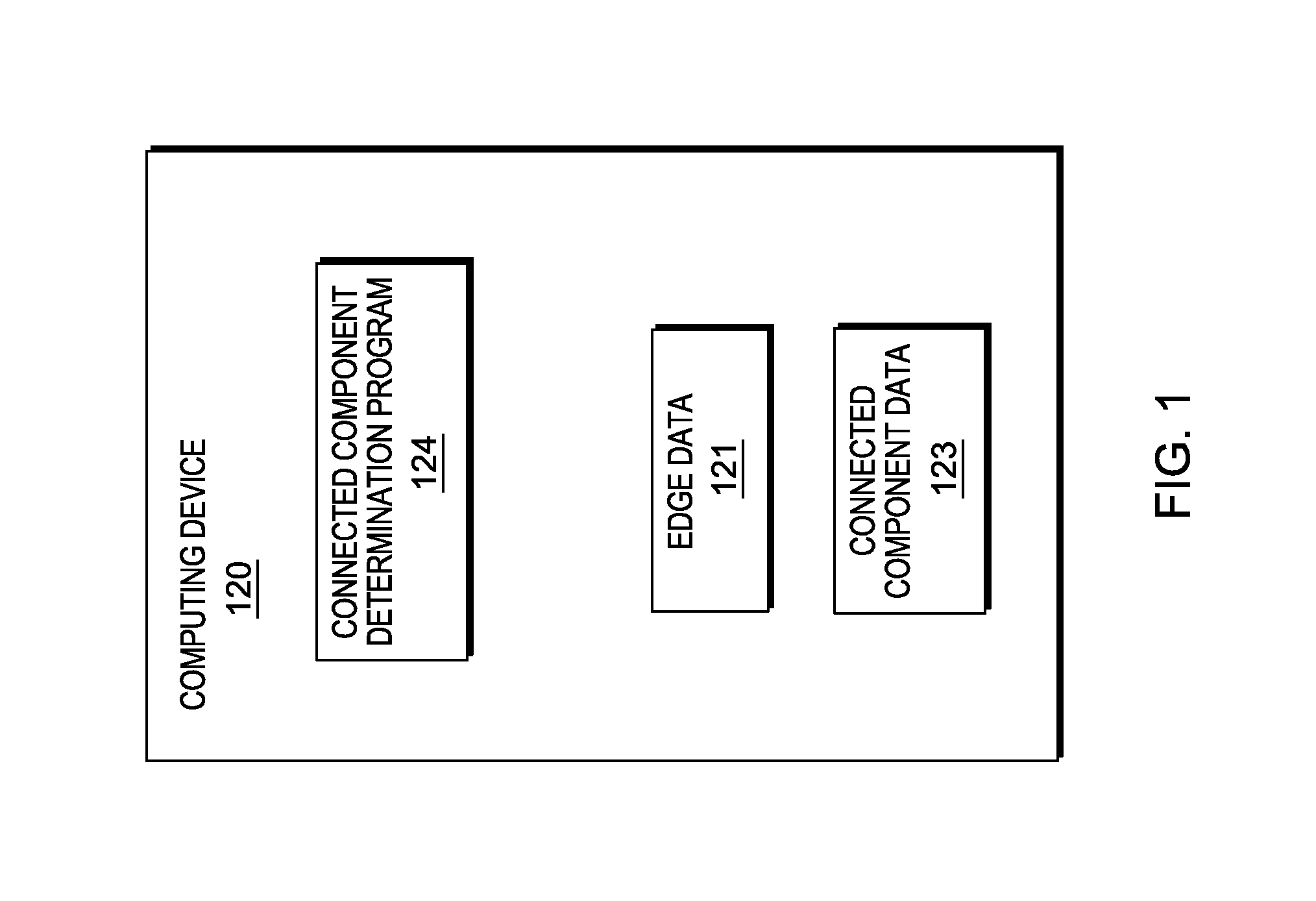
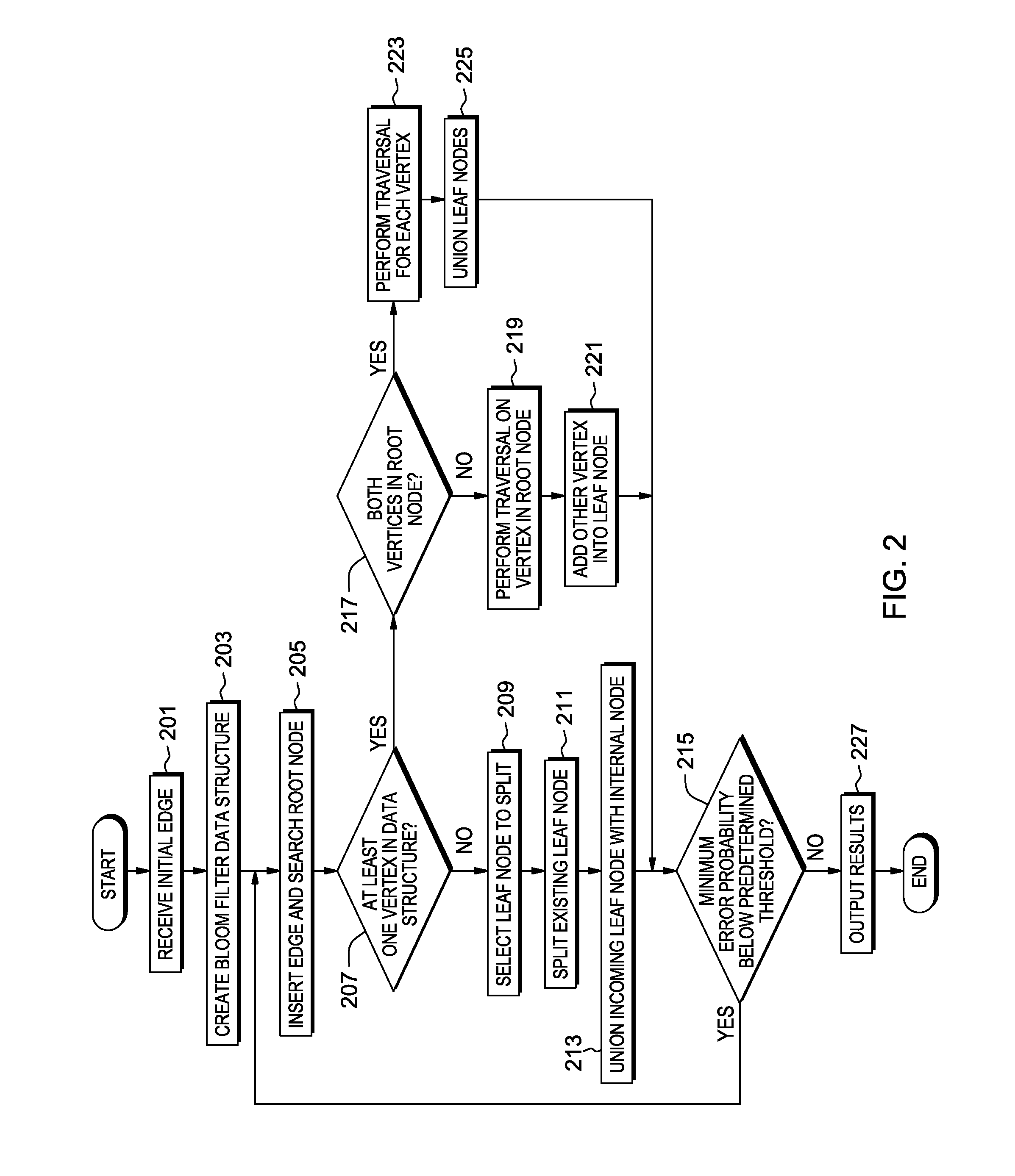
Probabilistically finding the connected components of an undirected graph
InactiveUS20150324410A1Digital data information retrievalSpecial data processing applicationsUndirected graphBloom filter
A method for probabilistically finding the connected components of an undirected graph. The method includes identifying a first edge, having a first and second vertex, and inserting information detailing the first and second vertex of the first edge into a bloom filter associated with a root node of a bloom filter data structure. A first node, connected to the root node, is created, comprising an associated bloom filter containing information associated with the first and second vertex of the first edge. The method includes identifying a second edge, having a first and second vertex, and inserting information detailing the first and second vertex of the second edge into a bloom filter associated with the root node of the bloom filter data structure. A second node, connected to the root node, is created, comprising an associated bloom filter containing information associated with the first and second vertex of the second edge.
Owner:IBM CORP
Optimized SNS (social network service) graph data publication privacy protection method
ActiveCN103279713AImprove protectionReduce lossesDigital data protectionUndirected graphSocial graph
The invention discloses an optimized SNS graph data publication privacy protection method. The method includes firstly abstracting SNS data into an undirected graph and generating a degree sequence for the undirected graph; secondly, dividing the degree sequence into groups to build an anonymous degree sequence; and lastly, performing the processes of edge adding and vertex adding on the anonymous degree sequence. Therefore, every individual or group in the SNS data can have at least k other individuals or groups with the same attribute, and an attacker can only position the at least k individuals or groups according to background information, further the individual or group privacy information of participants of the SNS can be protected effectively. With a high efficiency, the optimized SNS graph data publication privacy protection method can be applied to the privacy protection treatment of large-scale SNS data. Besides, the optimized SNS graph data publication privacy protection method has little information loss during the data reconstruction treatment.
Owner:GUANGXI NORMAL UNIV
Named entity recognition method for conditional random field based on word vector representation
InactiveCN106980609AEnhance expressive abilityImprove generalization abilityNatural language data processingSpecial data processing applicationsConditional random fieldGraphics
The invention provides a named entity recognition method for a conditional random field based on word vector representation and belongs to the field of natural language processing technology. A conditional random field algorithm based on word vector representation, a conditional random field algorithm adopting fusion word vector representation and an online named entity recognition system adopting B / S physical design and providing a graphic interaction interface are included in the method. Through the method, a biomedical named entity of a biomedical text to be analyzed by a user can be recognized, semantic representation characteristics of word vectors are brought into play in the recognition process with little dependency on artificial feature participation, the problem that the conditional random field is only valid to discrete feature representation is solved, and the advantages of the conditional random field algorithm, which is a discriminant undirected graph model, are also brought into play; the method provides named entity interactive relationship data retrieval service for the user and also provides a correction function on an automatic analysis result for the user.
Owner:DALIAN UNIV OF TECH
Estimating influence
Estimating influence is provided. For example, estimating influence includes determining an objective influence measure, which can be applied to various applications (e.g., search using objective influence). In some embodiments, estimating influence includes receiving a subject graph, in which the subject graph includes two or more subject nodes, in which each subject node corresponds to a subject; in which the subject graph is a directed graph, or if the subject graph is an undirected graph, then each undirected edge is interpreted as two directed edges in opposite directions; and determining an objective influence measure based on the subject graph for each first subject node of the subject graph, in which the determination is based at least on part on a function of inward scores and outward scores, in which inward scores are computed from one or more paths leading to the first subject of a length of at least one, and outward scores are computed from one or more paths leading from the first subject of a length of at least one, in which a path is a sequence of contiguous edges with a length equal to its number of edges, in which at least one of the inward paths or outward paths is of length greater than one.
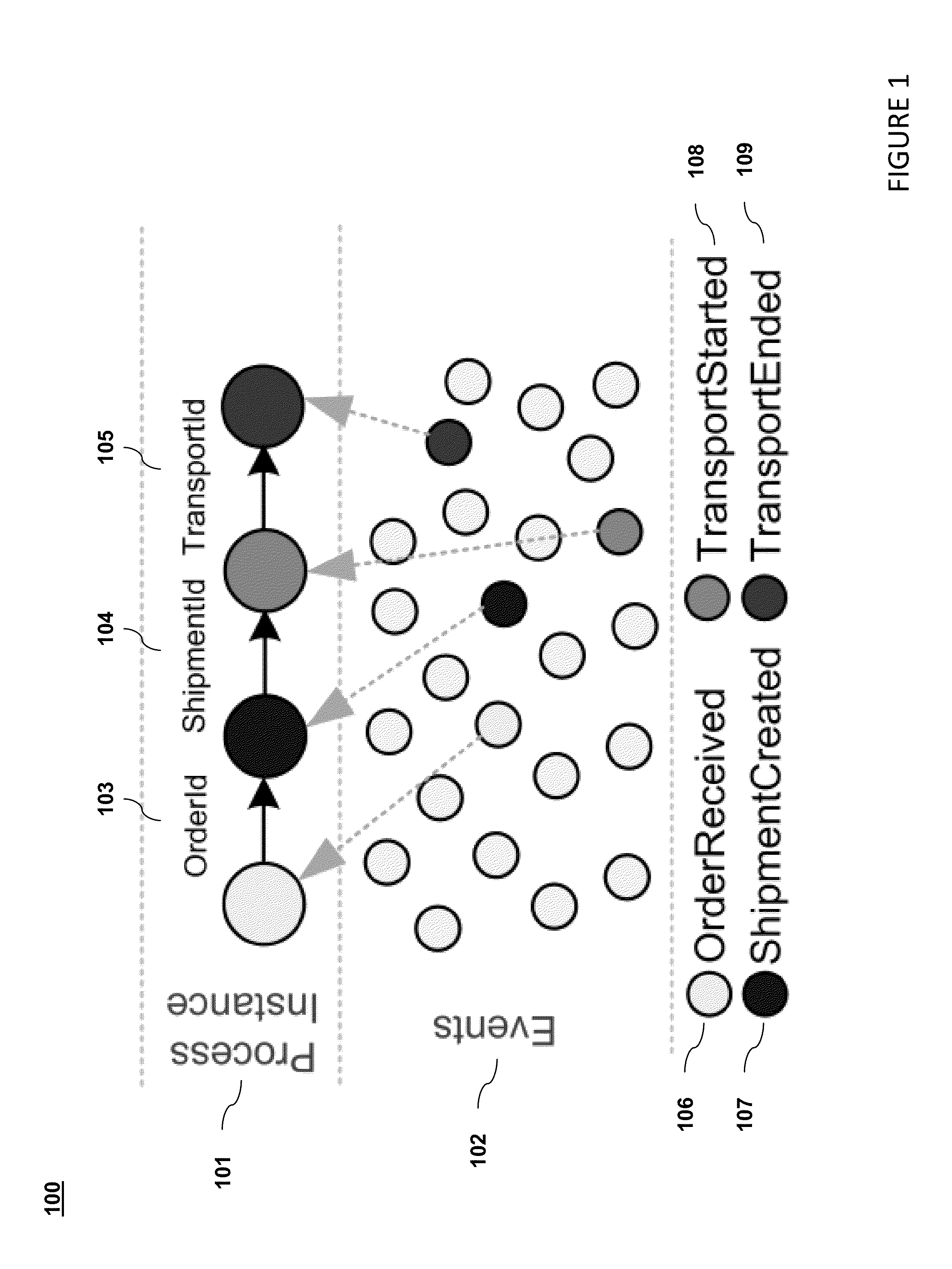
Owner:APPLE INC
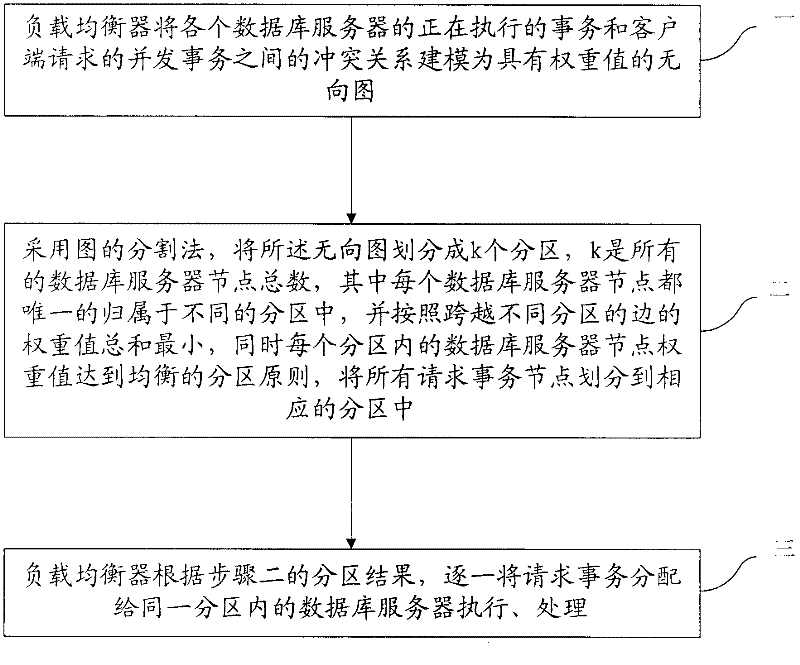
A load balancing method and device for a database cluster system
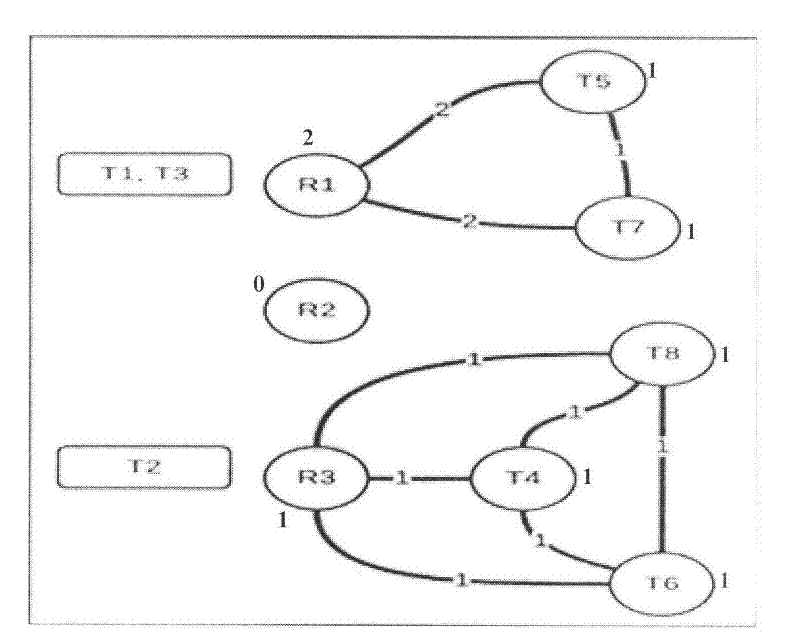
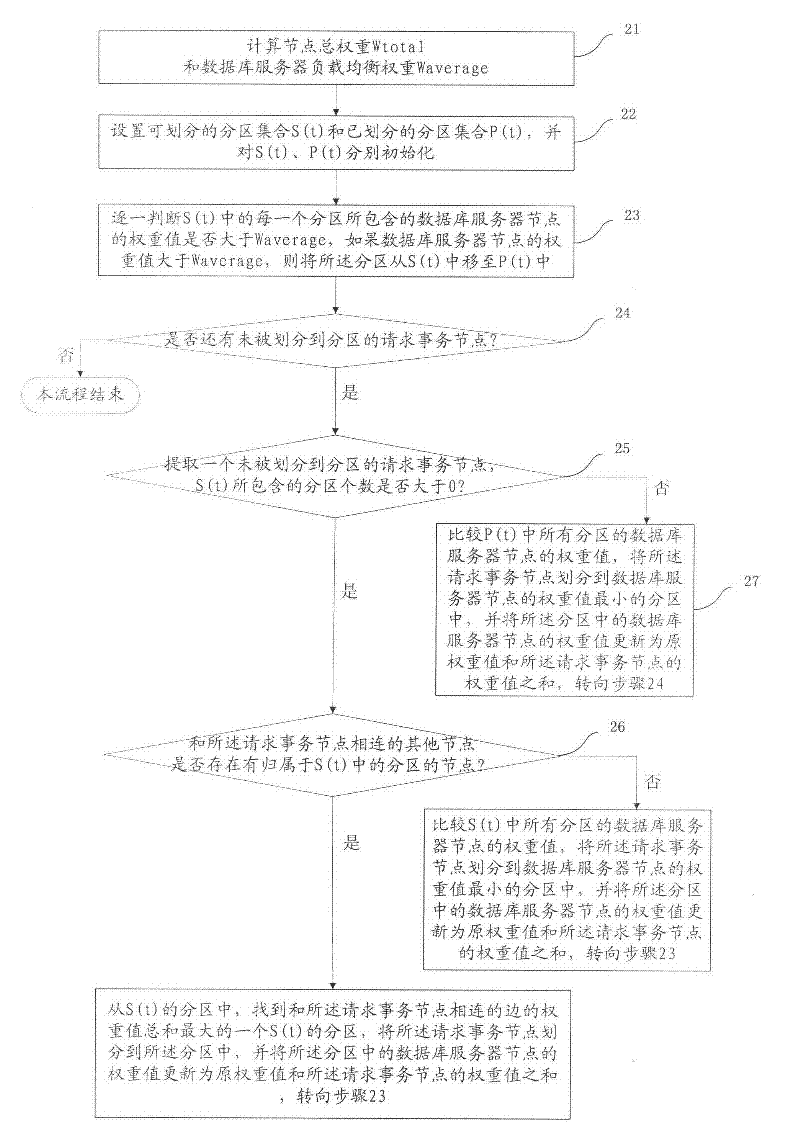
InactiveCN102299959AReduce abort rateAvoid data overloadTransmissionSpecial data processing applicationsUndirected graphCluster systems
The invention discloses a load balance realizing method of a database cluster system and a device. The method comprises the following steps that: a load balancer models a conflict relationship between a being executed affair of each database server and a concurrent affair requested by a client side to form an undirected graph with a weighted value; the undirected graph is partitioned into k subregions by using a graph partitioning method, and partitioning all the requested affair nodes into the corresponding subregions according to the partitioning principle that the sum of the weighted values of sides crossing different subregions is the minimum, and meanwhile, the weighted value of the database server node in each subregion reaches balance, wherein k is the total number of all database server nodes; and assigning the requested affairs to the database server in the same subregion one by one according to a partitioning result to be executed and processed. The load balance realizing method of the database cluster system and the device belong to the technical field of information, which can assign affairs with the conflict relationship to the least one database server as much as possible, and meanwhile, enables the database servers to reach load balance.
Owner:BEIJING UNIV OF POSTS & TELECOMM
Keyword extraction method and keyword extraction apparatus
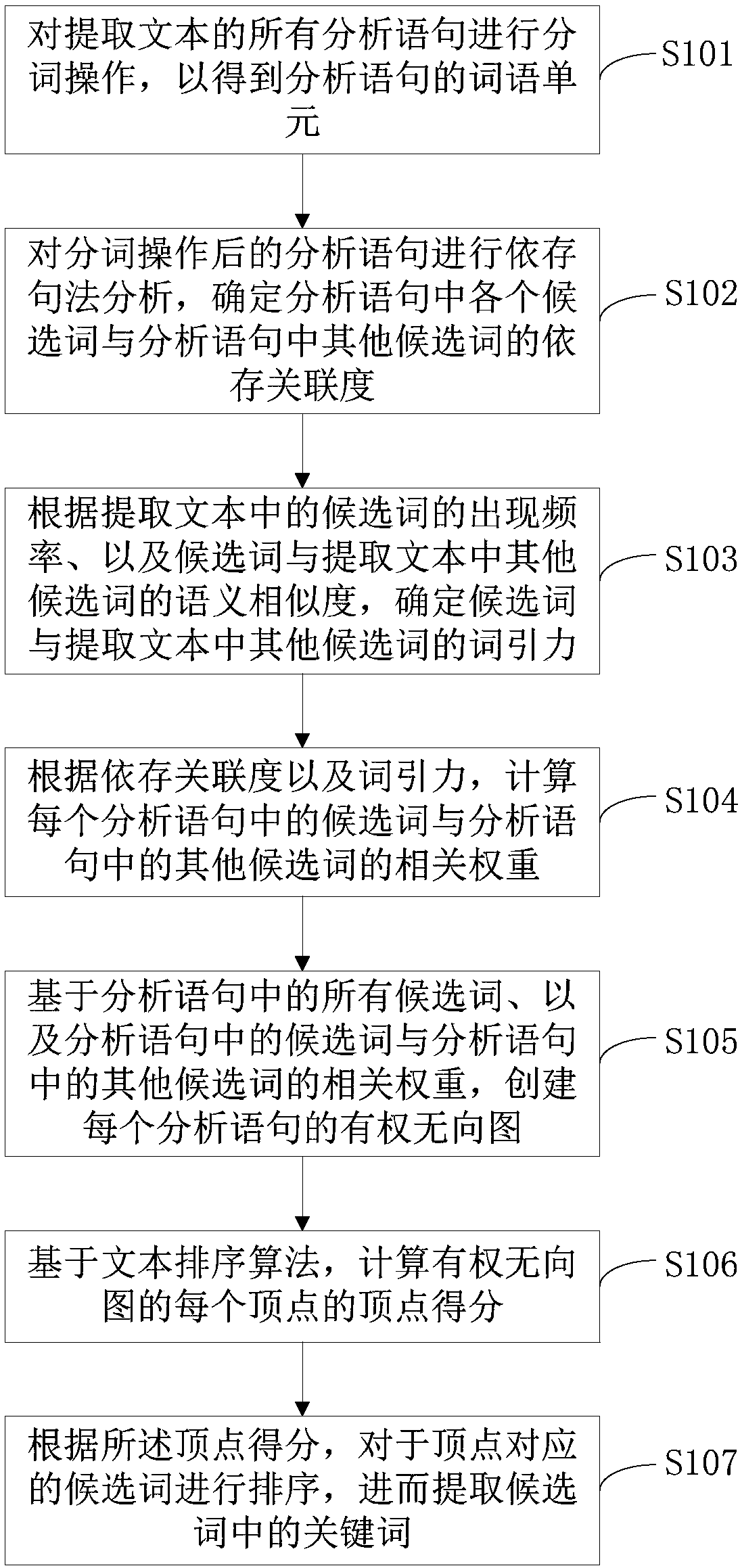
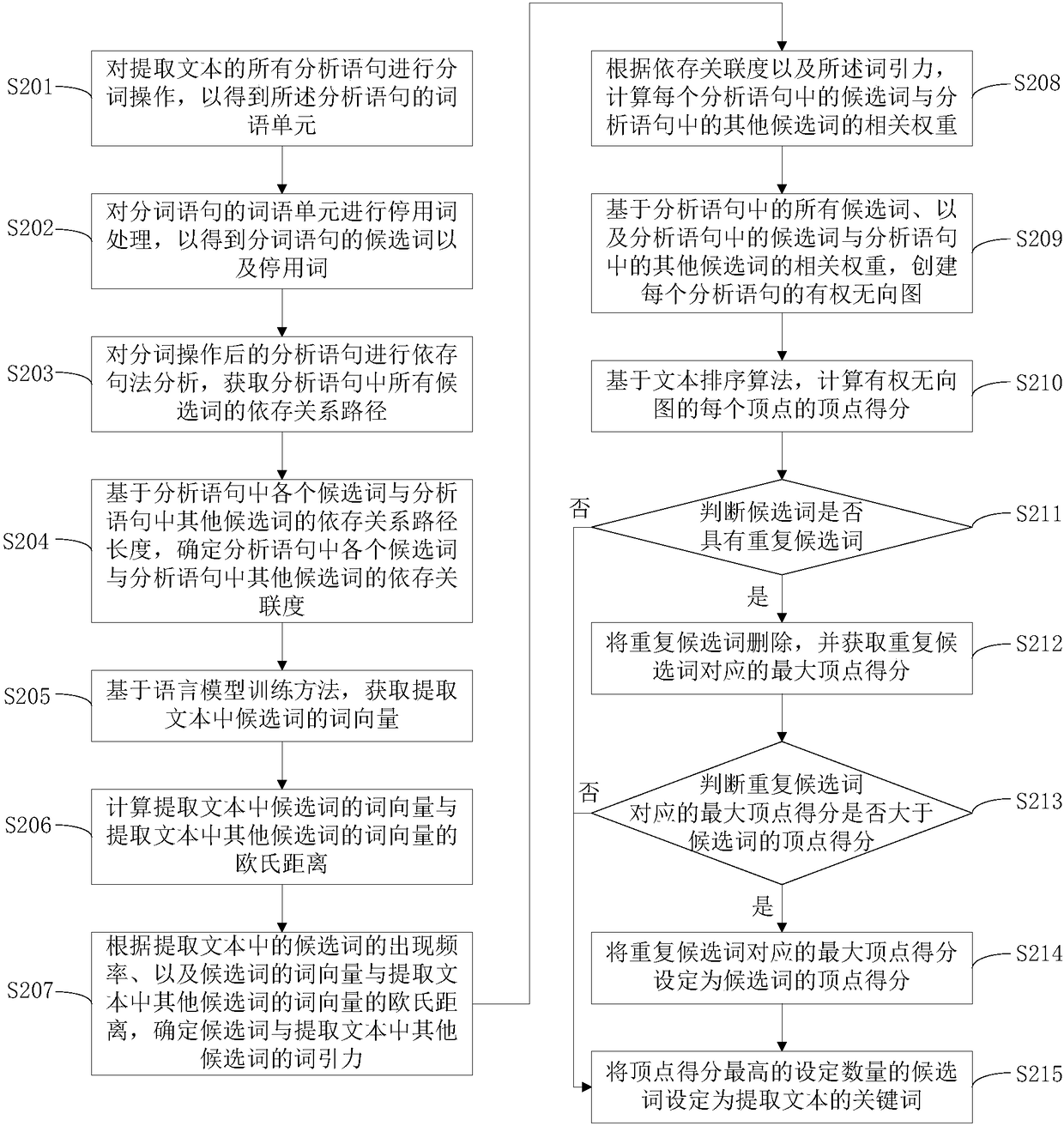
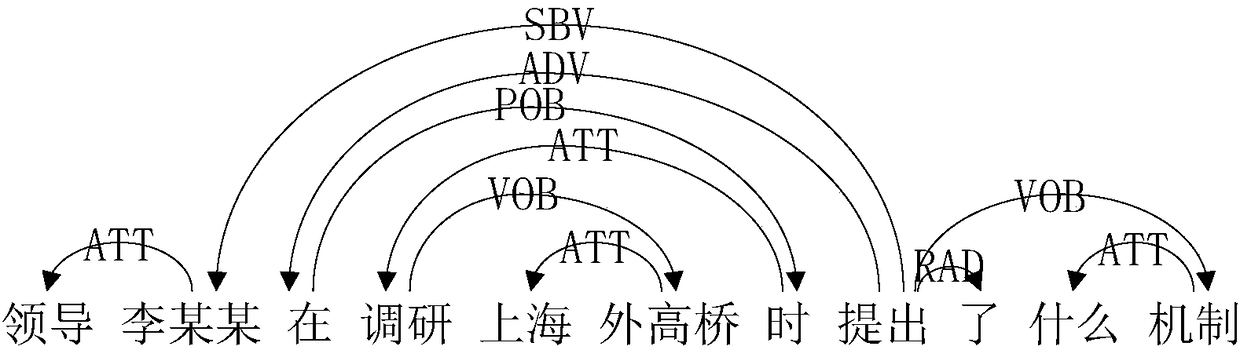
PendingCN108319627ASolve the technical problem of low extraction accuracyImprove calculation accuracyNatural language data processingSpecial data processing applicationsUndirected graphSorting algorithm
The invention provides a keyword extraction method. The method comprises the steps of performing word segmentation operation on all analysis statements of an extracted text to obtain word units of theanalysis statements; determining dependency association degrees between candidate words in the analysis statements and other candidate words in the analysis statements; determining word attraction between the candidate words and other candidate words in the extracted text; calculating related weights between the candidate words in the analysis statements and other candidate words in the analysisstatements; creating weighted undirected graphs of the analysis statements; based on a text sorting algorithm, calculating vertex scores of the vertexes of the weighted undirected graphs; and according to the vertex scores, sorting the candidate words corresponding to the vertexes, and extracting keywords in the candidate words. The invention furthermore provides a keyword extraction apparatus. The related weight between the two candidate words serves as a weight edge in the text sorting algorithm, so that the calculation accuracy of the text sorting algorithm is improved and the keyword extraction accuracy is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
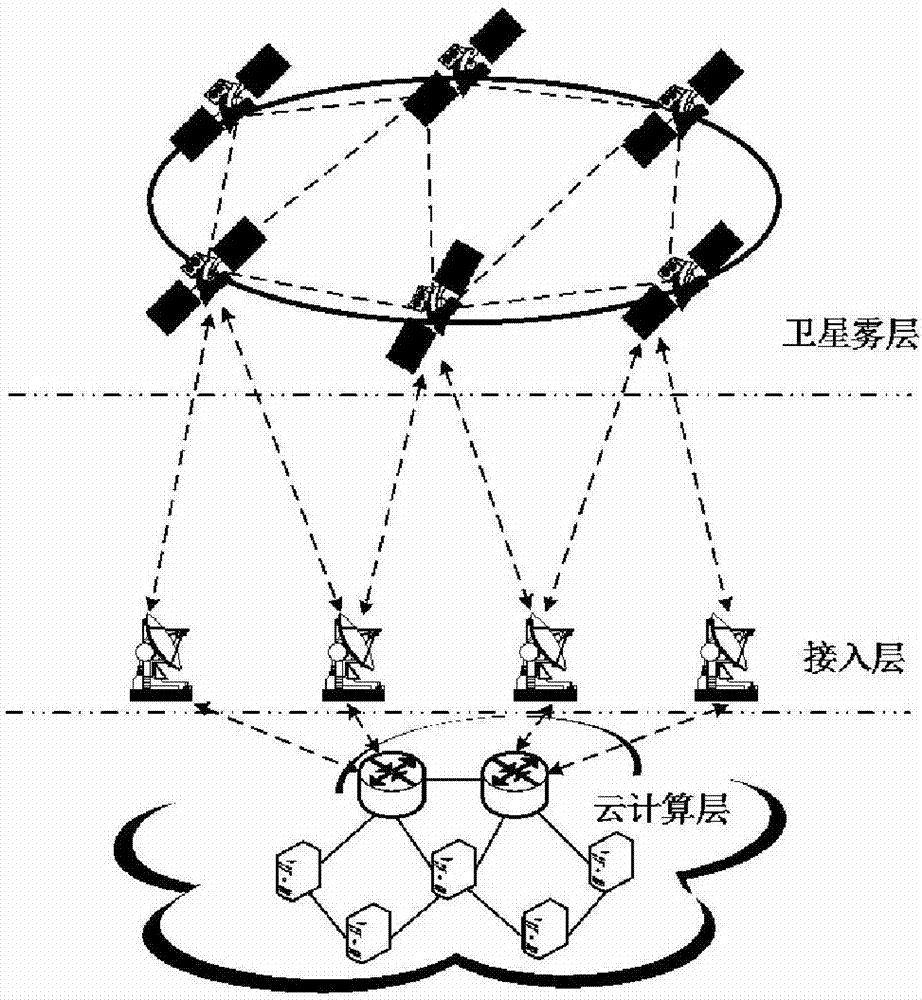
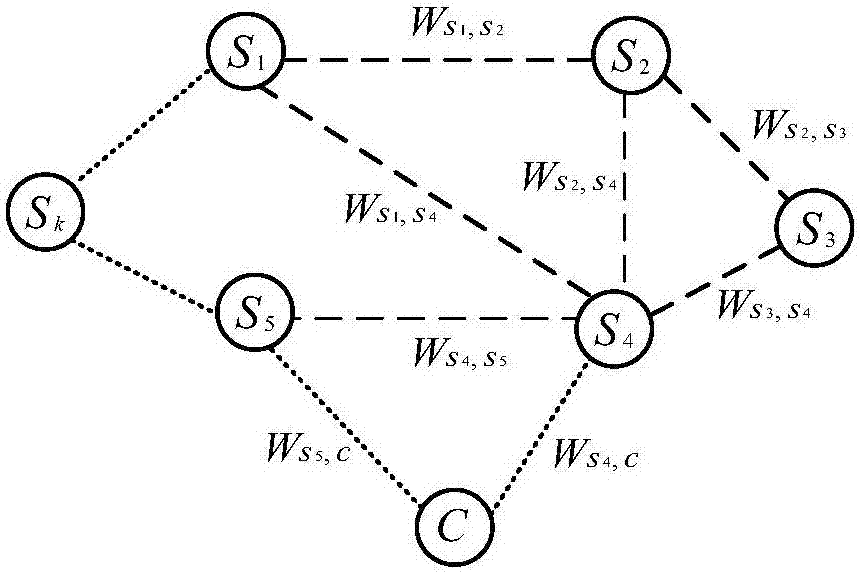
Distributed satellite cloud and fog network architecture and delay optimization method under energy-consumption constraint
ActiveCN107343025AReduce transmission delayImprove survivabilityNetwork traffic/resource managementNetwork topologiesUndirected graphNetwork architecture
The invention belongs to the technical field of communication, and in particular relates to a distributed satellite cloud and fog network architecture and a delay optimization method under energy-consumption constraint. The distributed satellite cloud and fog network architecture comprises a satellite fog layer, an access layer and a cloud computing layer. The delay optimization method under energy-consumption constraint comprises the steps of: (1), constructing an undirected graph G=(V,E) of the distributed satellite cloud and fog network architecture; (2), constructing a delay optimization model under energy-consumption constraint; and (3), determining a delay optimization strategy under an energy-consumption constraint condition.
Owner:XIDIAN UNIV
Target tracking method based on dynamic graph matching
ActiveCN102930539AEfficiently obtainedAccurately obtainedImage analysisStructural deformationUndirected graph
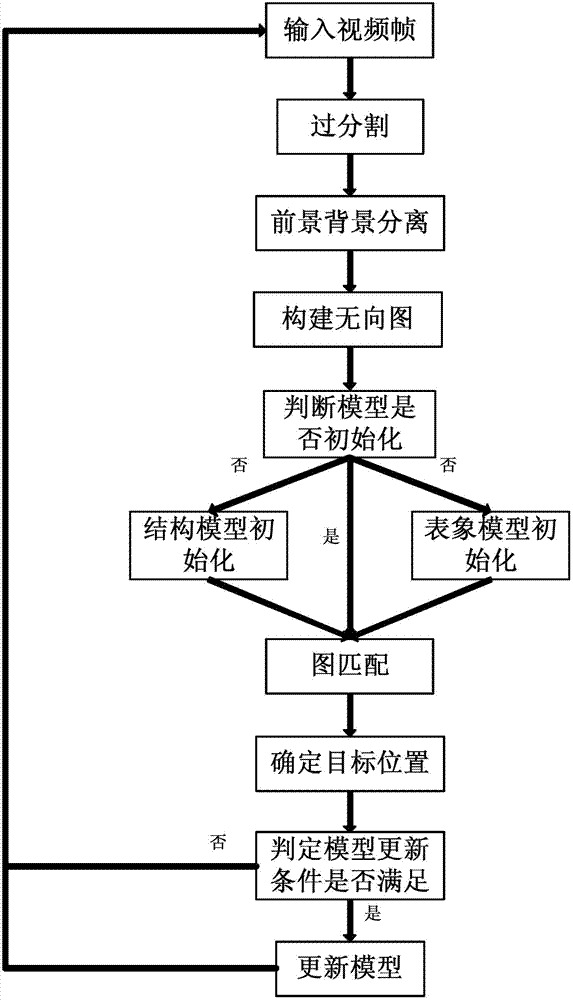
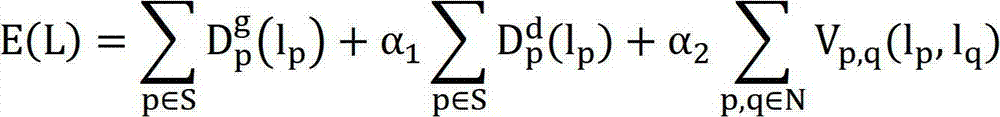
The invention discloses a target tracking method based on dynamic graph matching, which is characterized in that a structural model of a dynamic graph is used for effectively tracking a target. The target tracking method mainly comprises six steps of superpixel over-segmentation, extraction of candidate target blocks, creation of an undirected graph, matching of the undirected graph, determination of a target position and updating of a model. The target tracking method has the advantages that the internal structural information of the target can be effectively modeled by using a target tracking model structured with the method, so that the target position can be still precisely determined by the tracking method when the target has greater structural deformation or is severely shielded.
Owner:JIANGSU R & D CENTER FOR INTERNET OF THINGS
Traffic jam state propagation prediction and early warning system and method based on city portraits
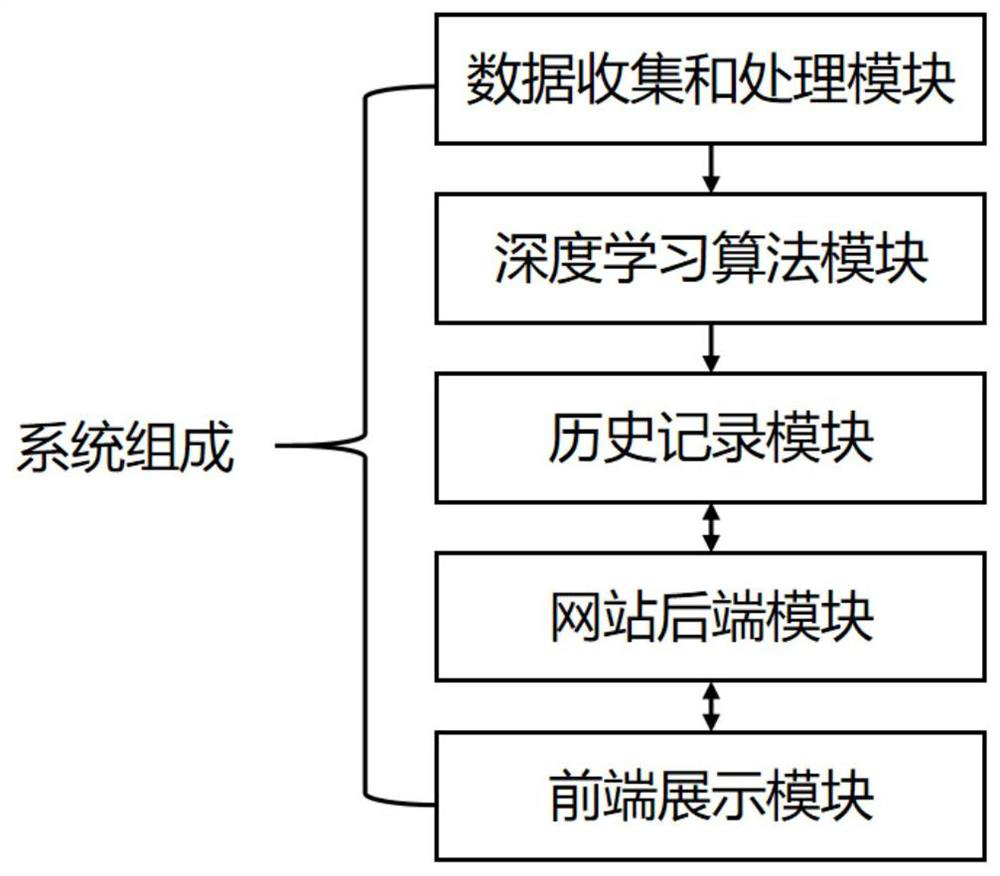
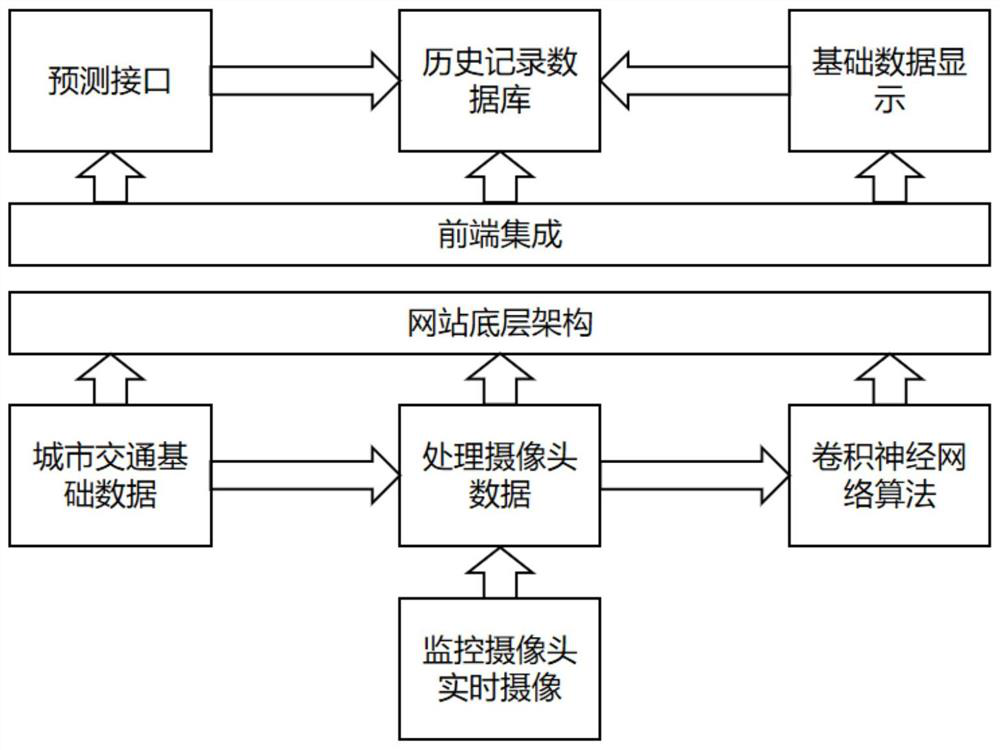
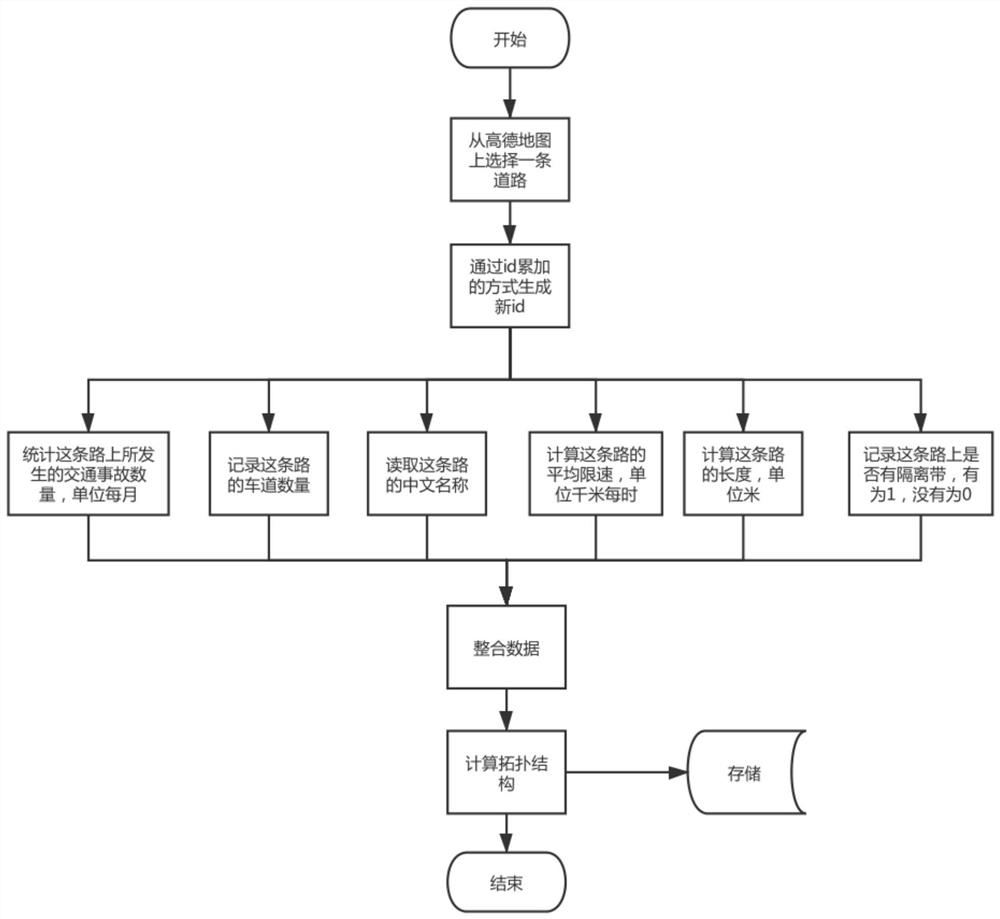
ActiveCN111768618ACongestion avoidanceImprove transportation efficiencyDetection of traffic movementTraffic control supervisionState predictionSimulation
The invention discloses a traffic jam state prediction and early warning system and method based on city portraits. The system comprises the following modules: a data collection and processing module,a deep learning module, a historical record module and a front-end display module. Recording road condition information of each street and intersection in real time by utilizing data provided by a traffic camera; streets are abstracted into edges in an undirected graph, intersections are abstracted into points in the undirected graph, road condition information of the streets and the intersections is sorted into edge weights and point weights, the edge weights and the point weights are input into a deep learning model of a dynamic graph, a real-time city portrait is constructed, city trafficcongestion state propagation at the next moment is predicted, and early warning information is reported to a congestion area.
Owner:BEIHANG UNIV
Formation satellite finite-time configuration containment control method
ActiveCN104898691AIncrease speedReliable controlPosition/course control in three dimensionsRelative orbitDirected graph
The invention relates to a formation satellite configuration containment control method, in particular, a formation satellite finite-time configuration containment control method. The objective of the invention is to solve the problem of low robustness of an existing multiple-satellite system formation control method and the problem of incapability of completely adapting to a practical application environment which is caused by a situation that inter-satellite communication topology is an undirected graph in the existing multiple-satellite system formation control method. The formation satellite finite-time configuration containment control method includes the following steps that: a relative orbit dynamic model of formation satellites i of a satellite formation system and relative reference points is established according to an established relative motion dynamic equation of reference satellites and accompanying satellites, and is simplified as an expression described in the descriptions; a weighted adjacent matrix A and a Laplacian matrix in the graph theory of a directed graph in the satellite formation system are provided according to the formation types of the formation satellites i; and a distributed finite-time configuration containment control laws of the multi-dynamic-pilot-satellite satellite formation system are designed, and therefore, each following satellite can achieve at a configuration convex hull formed by pilot satellites in finite time, and formation satellite finite-time configuration containment control can be realized. The formation satellite finite-time configuration containment control method of the invention is applicable to the control field of formation satellite configuration.
Owner:HARBIN INST OF TECH
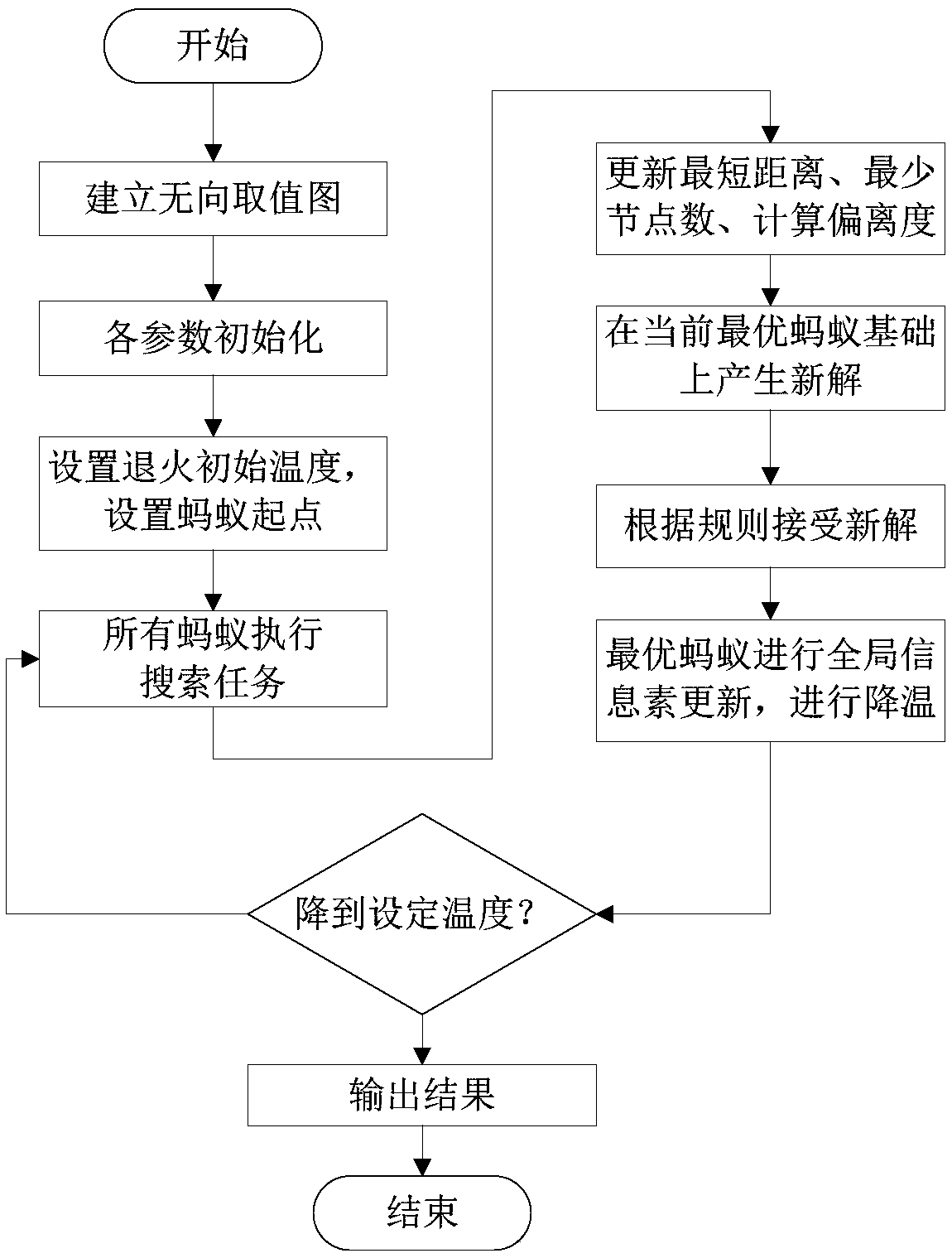
Electric power inspection robot path planning method based on simulated annealing ant colony algorithm
ActiveCN109141430AIncrease speedGuaranteed feasibilityNavigational calculation instrumentsPath lengthTransformer
The invention discloses an electric power inspection robot path planning method based on a simulated annealing ant colony algorithm. The method includes the steps: building a map according to an outdoor transformer substation environment, planning the running path and stop points of an electric power inspection robot and building a topological map according to coordinate information of the stop points; acquiring the local shortest path of two optional inspection points by the aid of a classical Dijkstra algorithm according to inspection tasks, and building an undirected graph; transforming a global optimal path planning problem into a multi-target traveling salesman problem according to path lengths and the number of passing stop points, and planning a global optimal path on the basis of the undirected graph by the simulated annealing ant colony algorithm; replacing a local path in the global optimal path by the local shortest path to obtain a complete final path. The method is high inconvergence rate and global searching ability and has the advantages of low complexity, high feasibility and high speed.
Owner:NANJING UNIV OF SCI & TECH
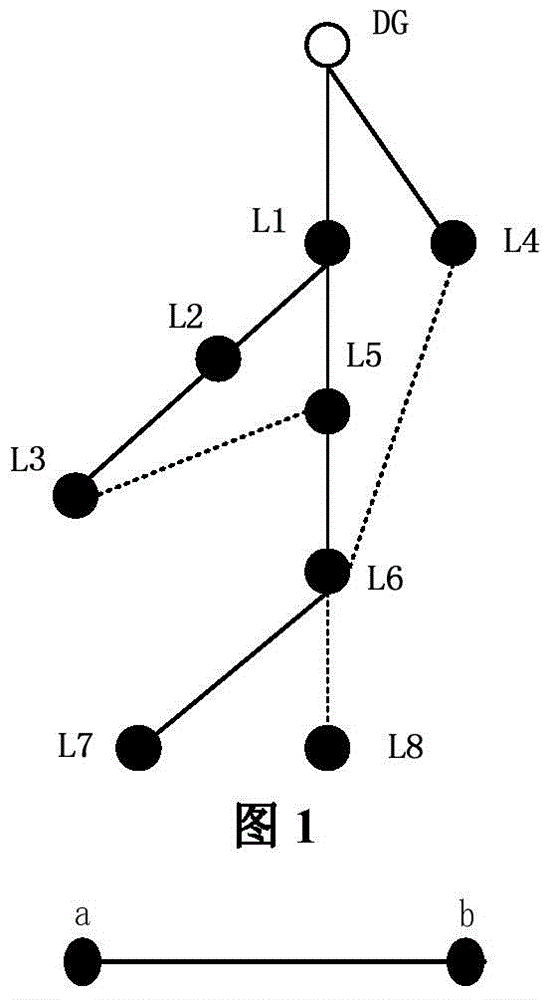
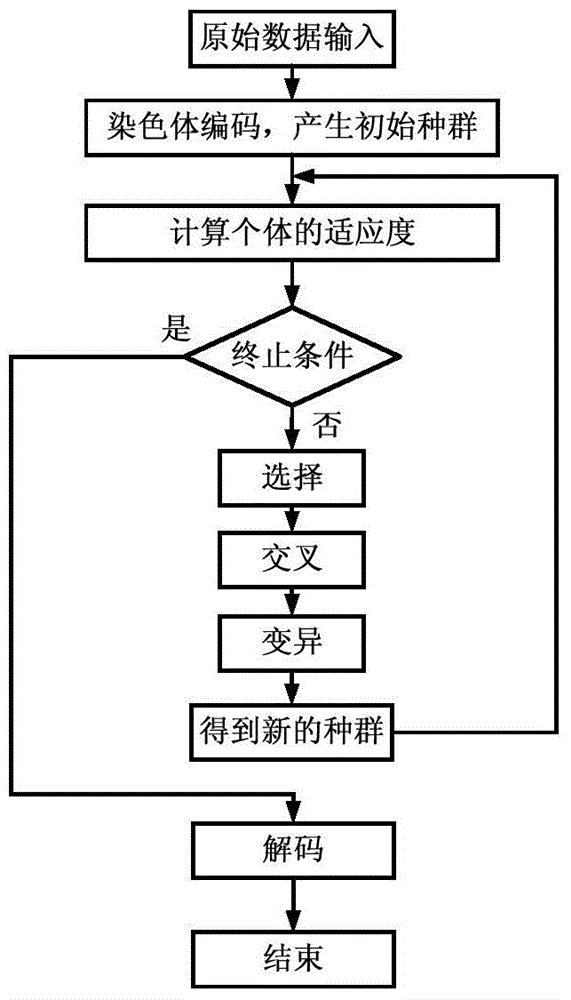
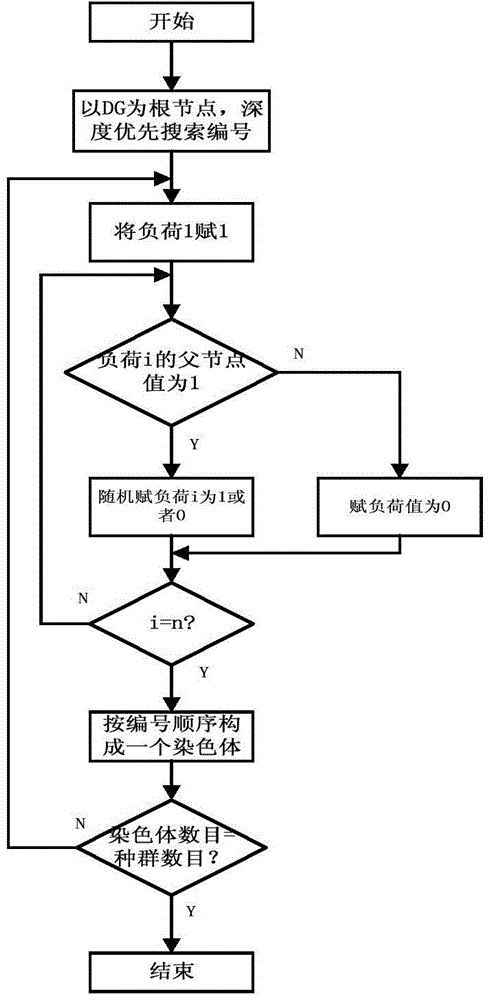
Island dividing method for power distribution network having distributed power sources
ActiveCN105098762APrevent overloadAvoid overvoltageSpecial data processing applicationsAc network circuit arrangementsElectric power systemStructure of Management Information
The invention relates to an island dividing method for a power system and an island dividing method for a power distribution network having distributed power sources. The method includes steps of (1) modeling aiming at the island dividing problem; (2) undirected graph weight setting for the power distribution network; (3) formation of a radiation power distribution network based on a minimum spanning tree algorithm; (4) island division, based on an improved genetic algorithm, for the power distribution network having the distributed power sources; (5) island division for the power distribution power network having the plurality of distributed power sources. According to the invention, island division problem of the power distribution network is solved by the combination of the minimum spanning tree algorithm and the improved genetic algorithm. The power distribution network model is simplified based on features of the power distribution network. The power distribution network with a looped network structure is simplified to a radiation power distribution network with the optimal load restoration sequence and then the optical island is obtained by adopting the improved genetic algorithm. The searching efficiency is improved and the optimal solution can be obtained quickly and effectively. The method provided by the invention has good practicability.
Owner:STATE GRID CORP OF CHINA +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com