Patents
Literature
395 results about "Information dispersal" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
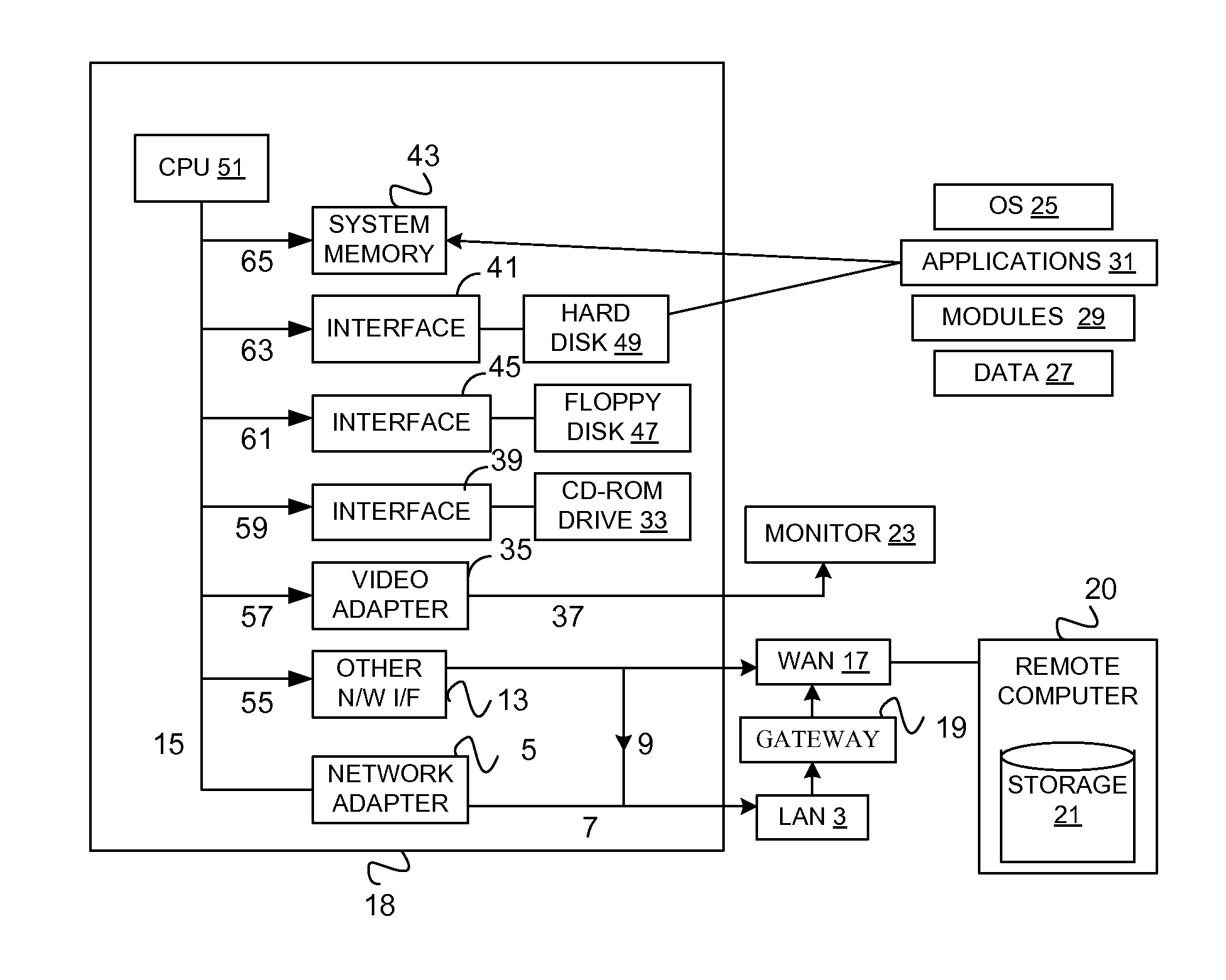
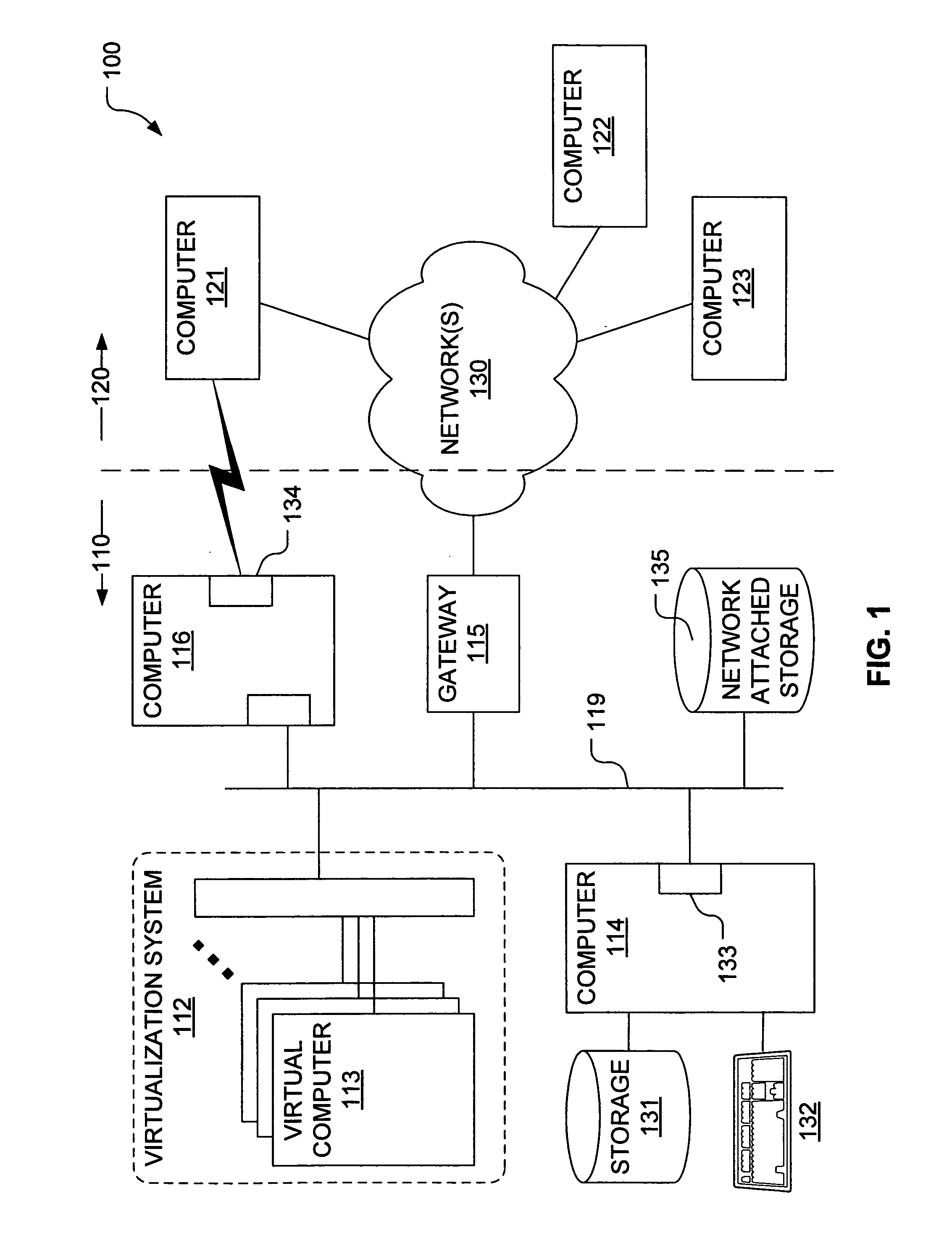
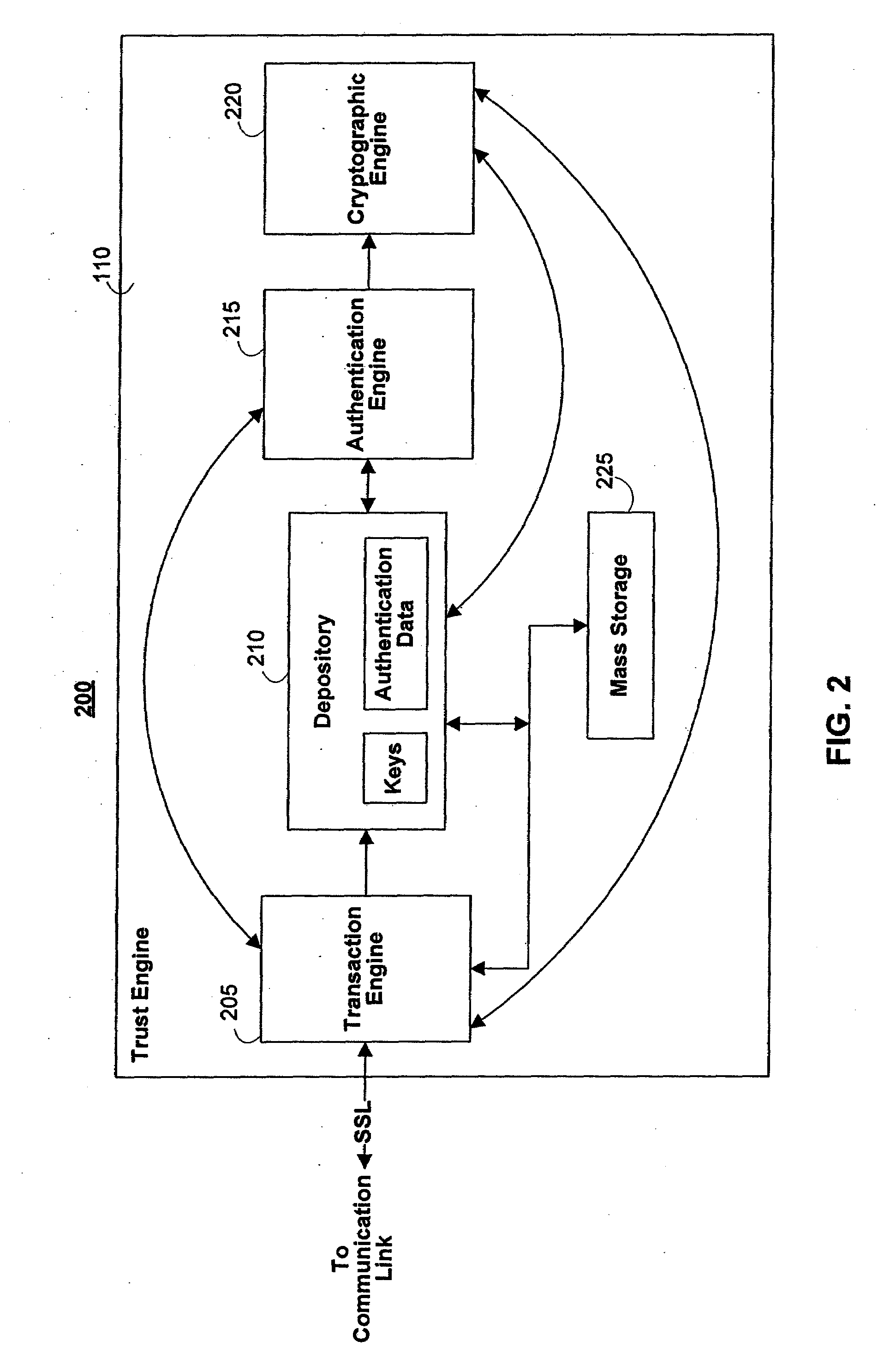
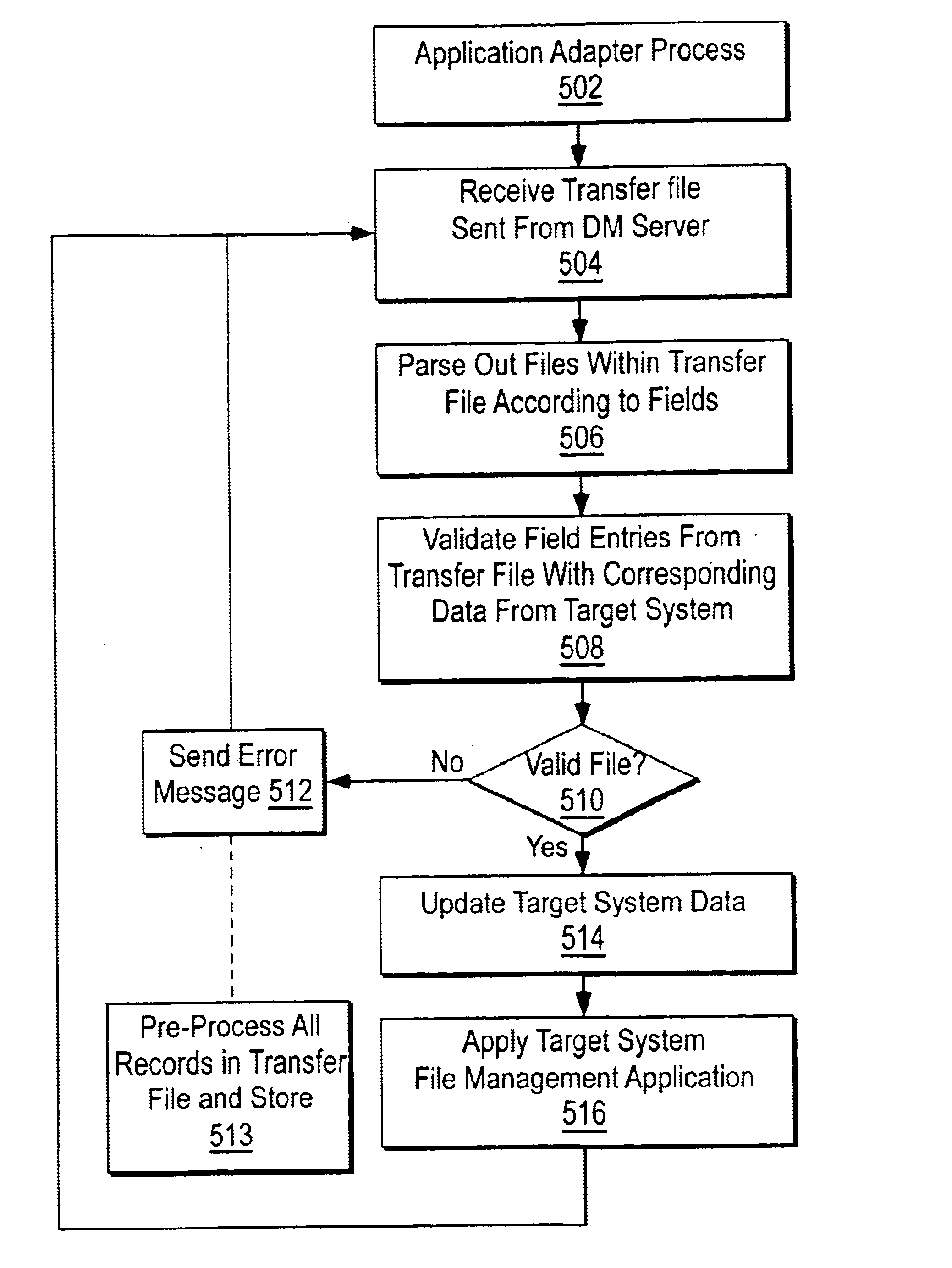
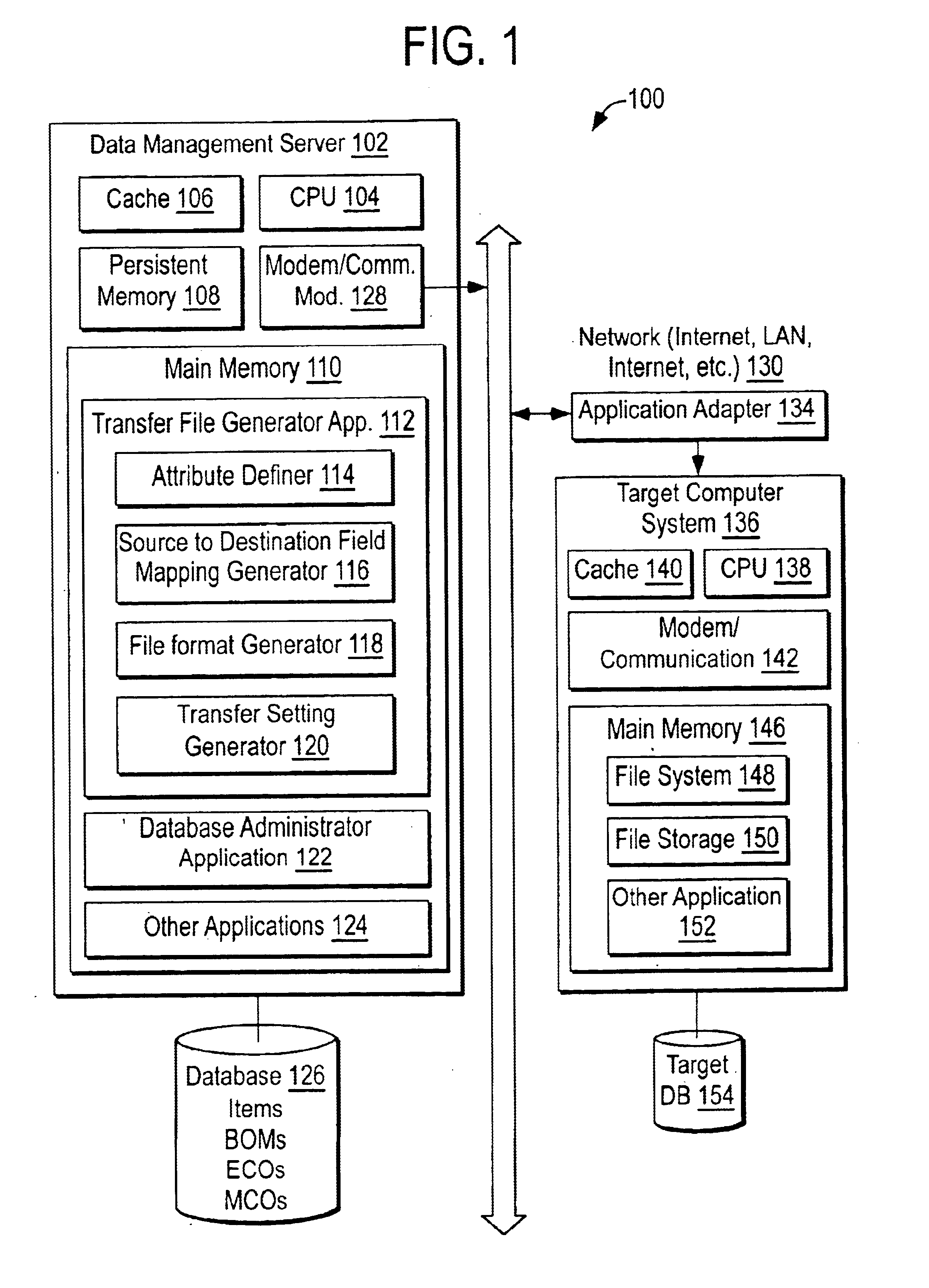
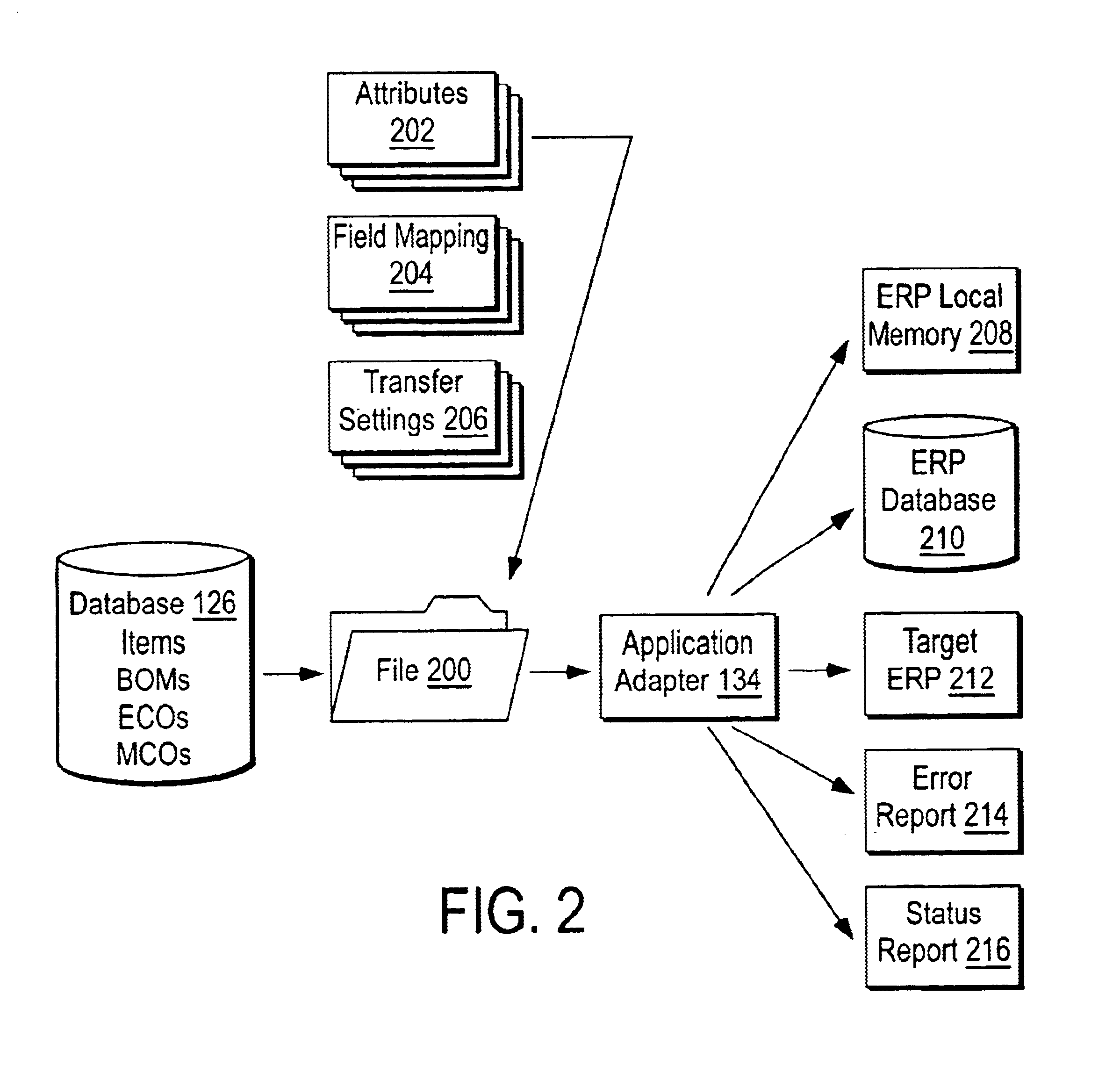
System for rebuilding dispersed data
ActiveUS20070079082A1Reliably and securely protectImprove privacyError detection/correctionDigital data protectionGrid resourcesInformation dispersal
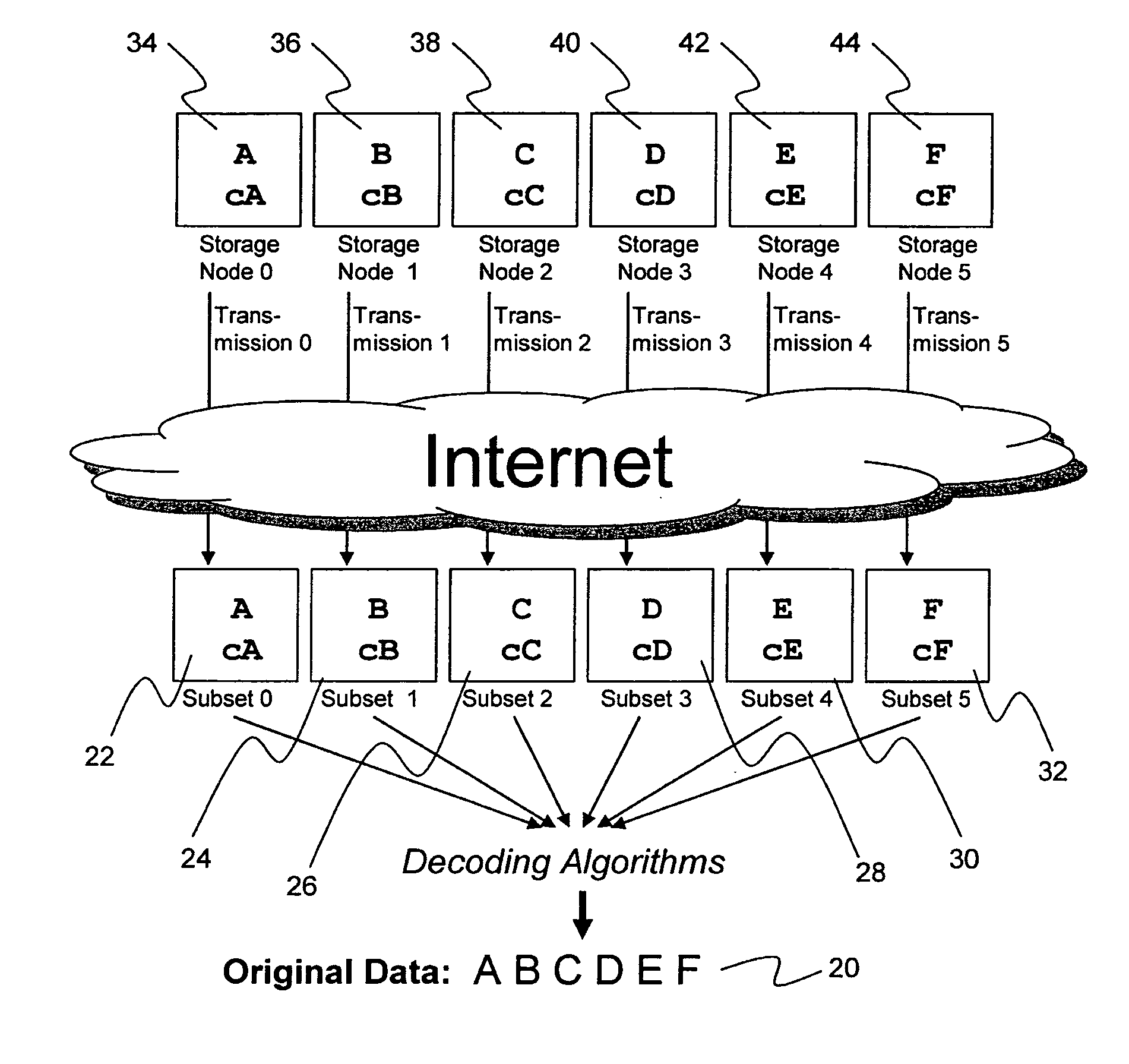
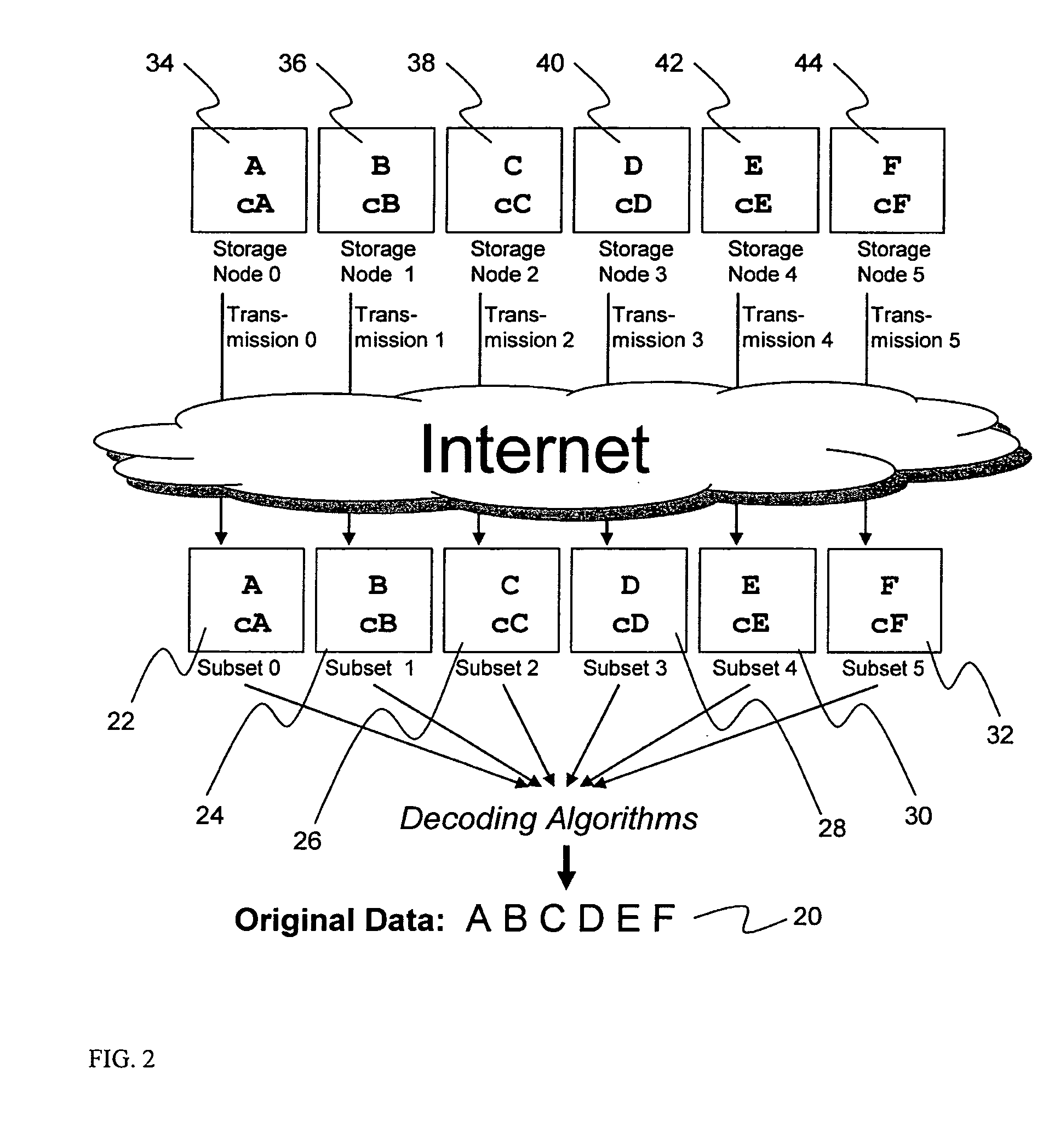
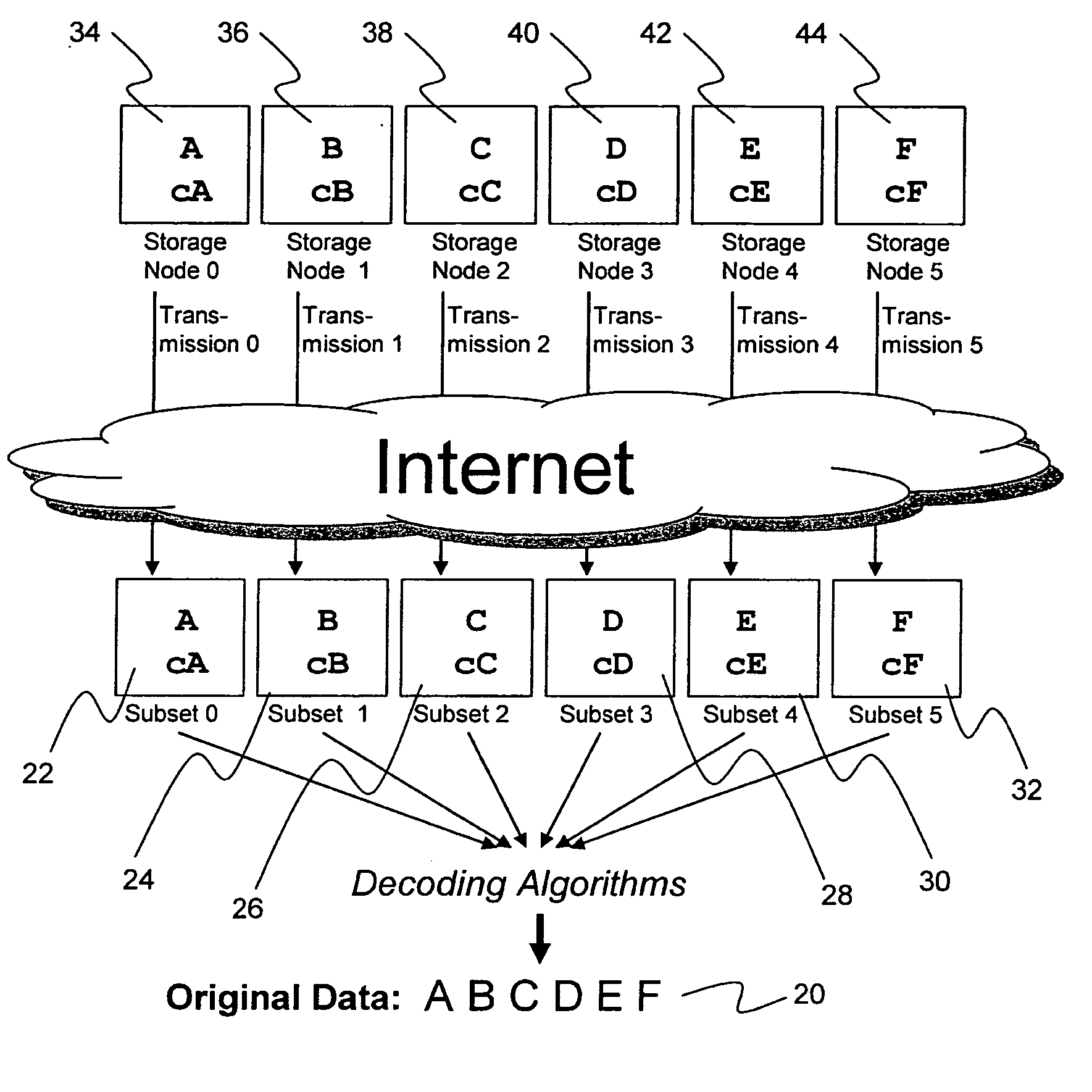
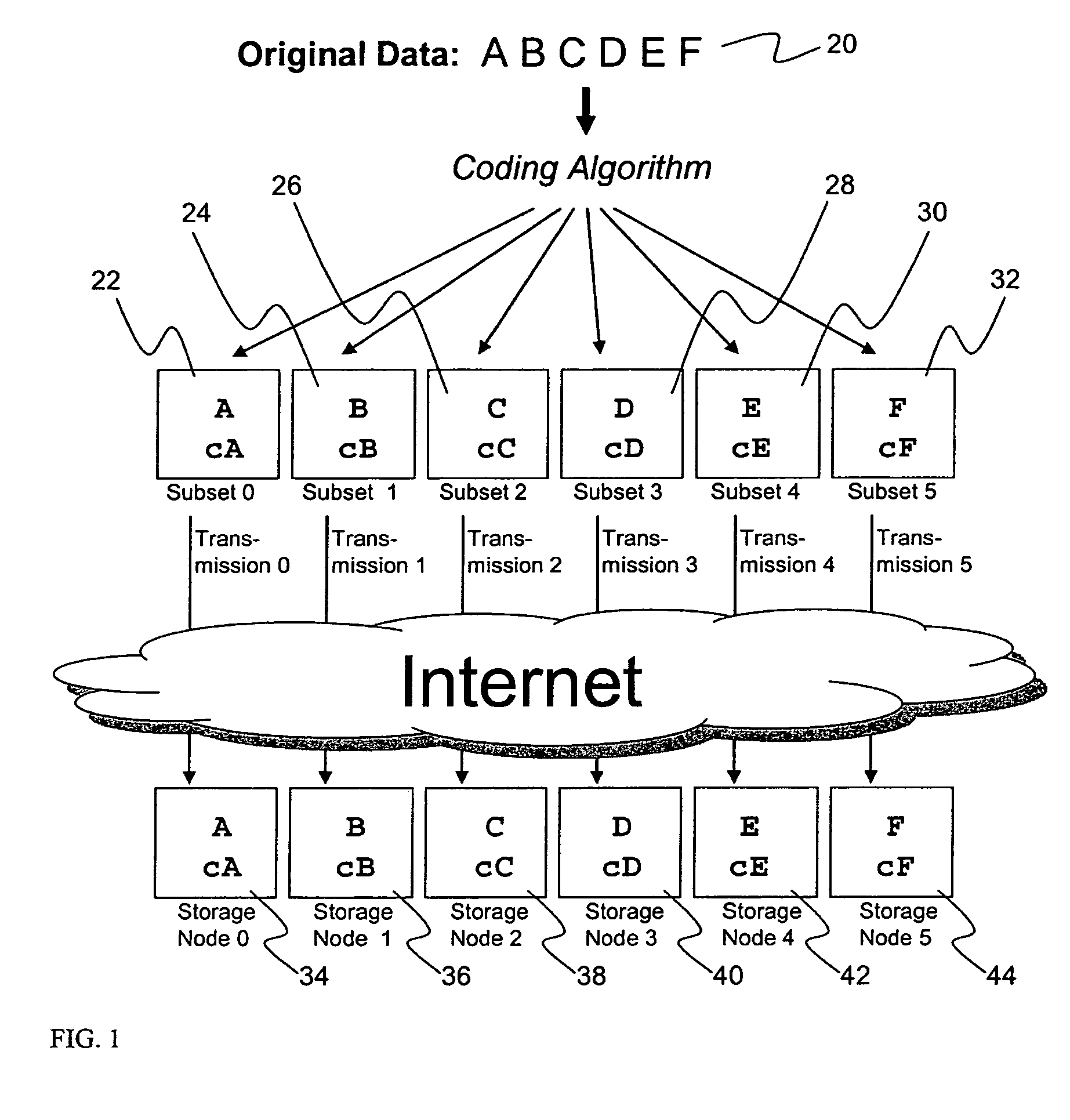
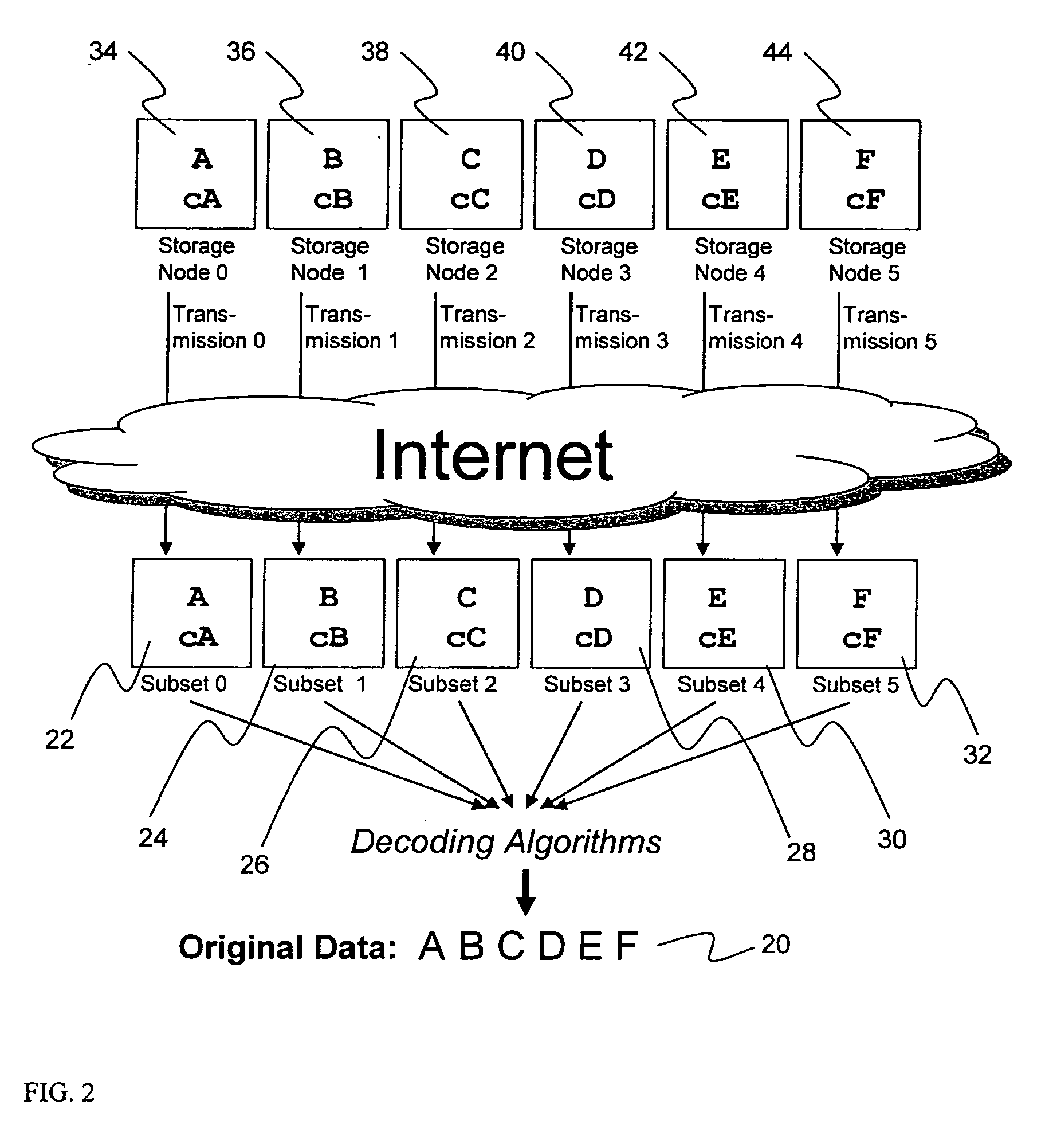
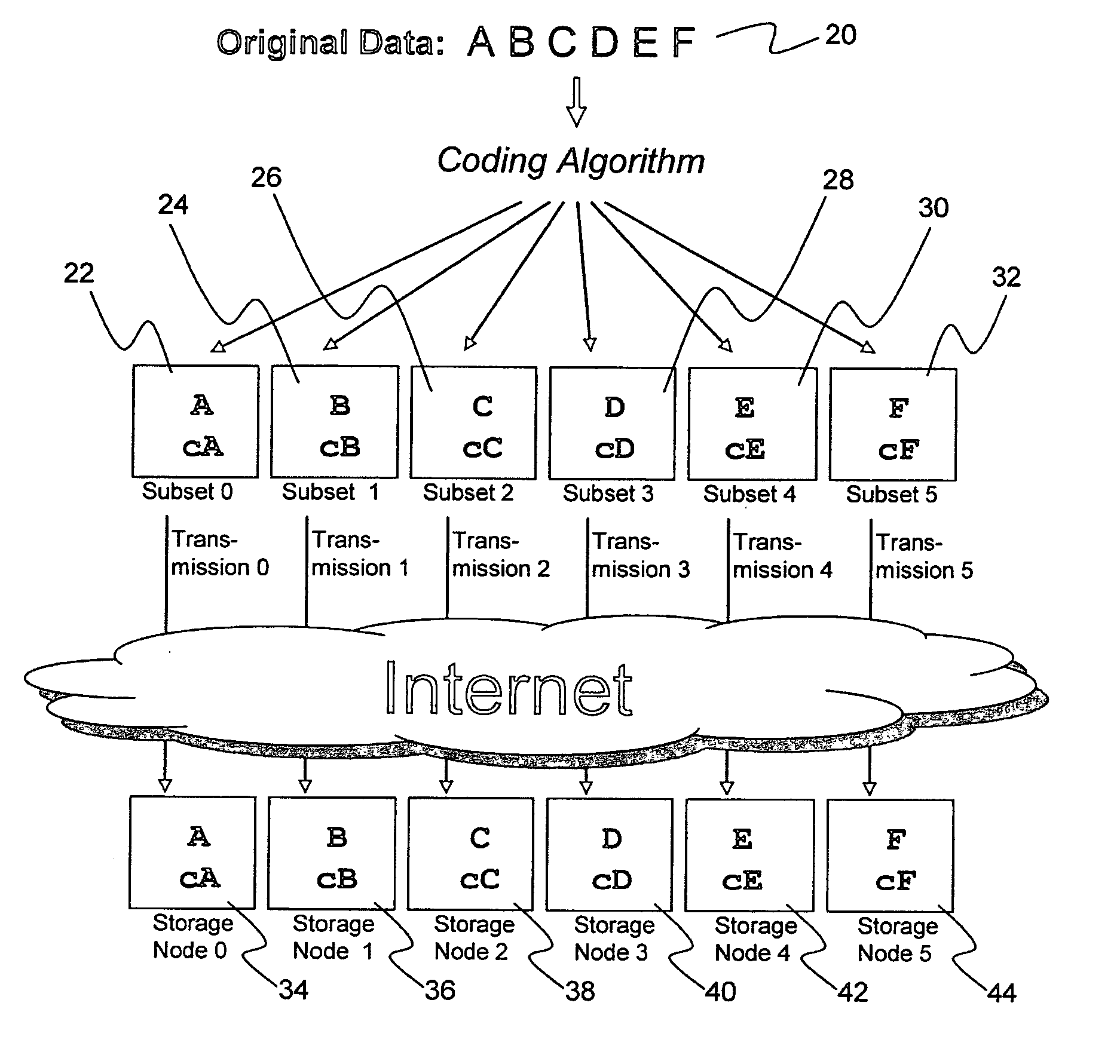
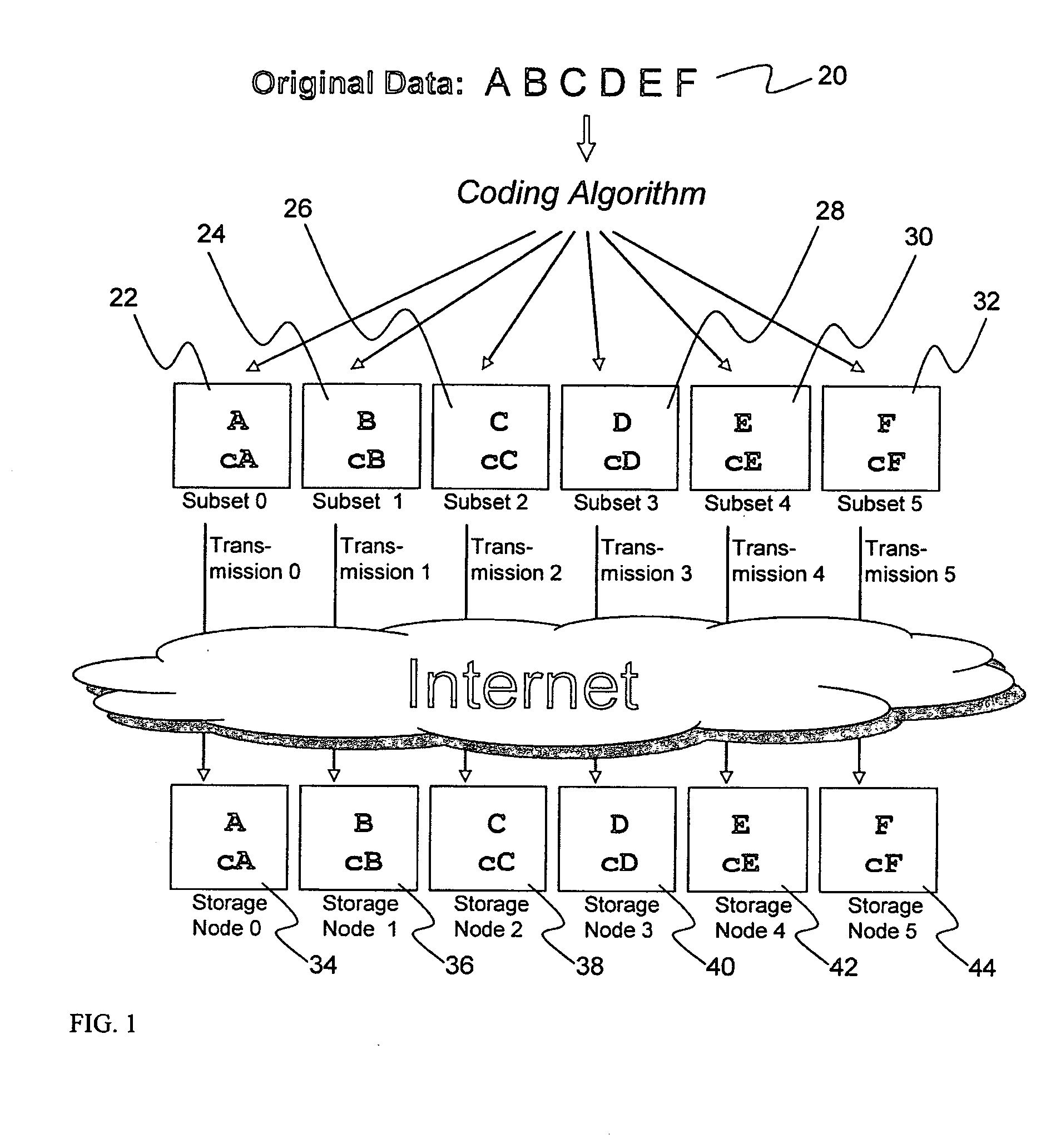
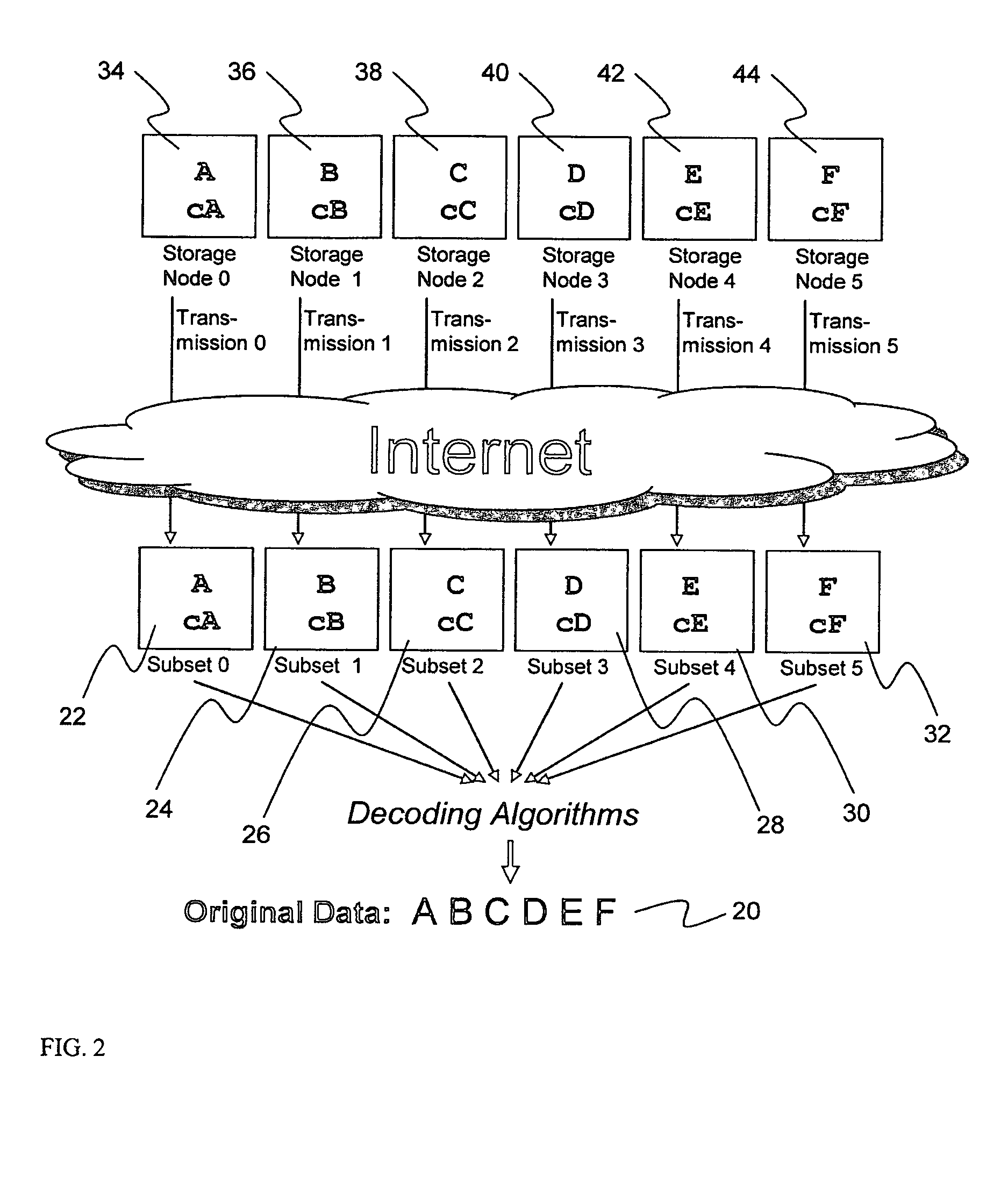
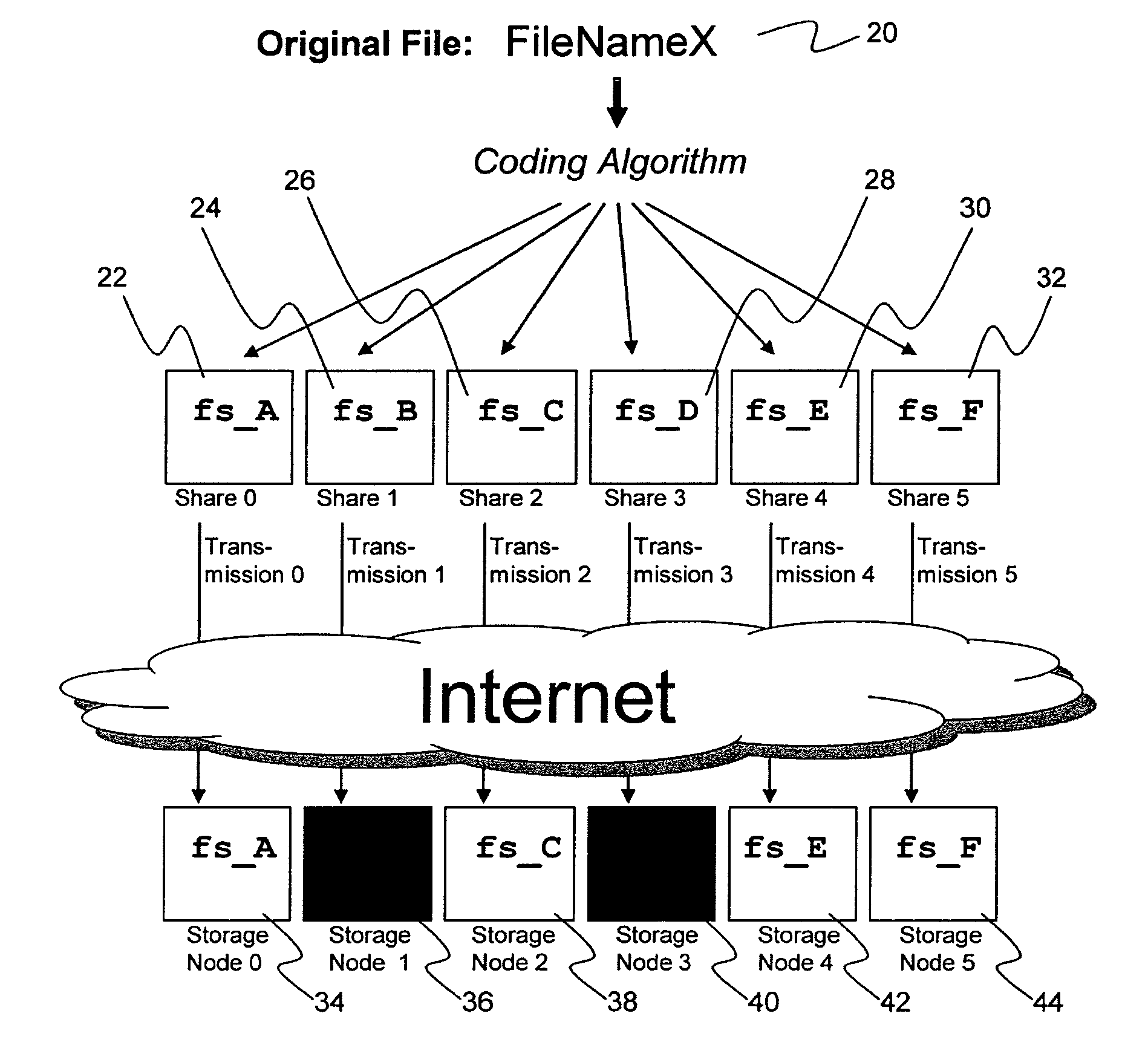
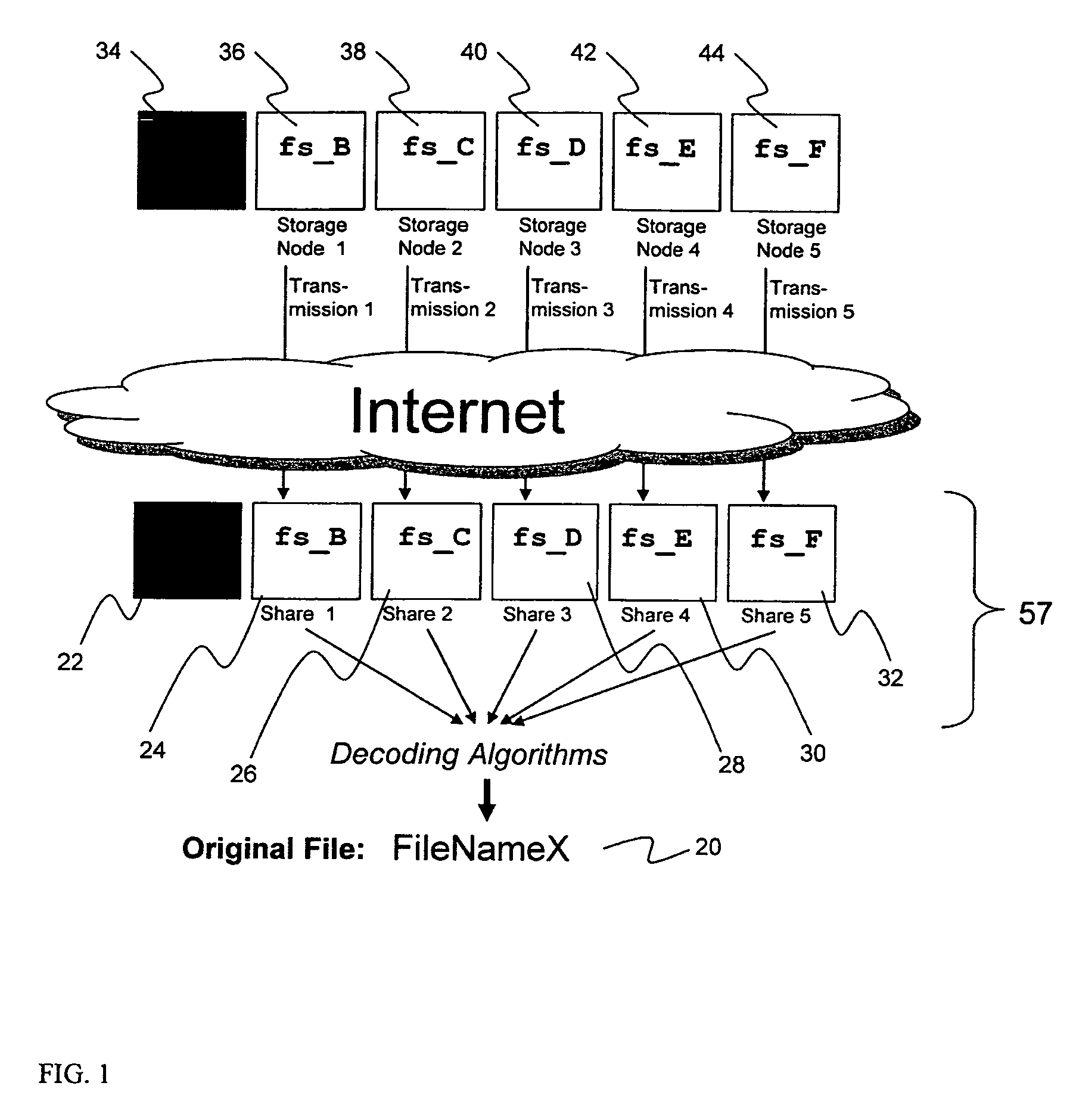
A digital data file storage system is disclosed in which original data files to be stored are dispersed using some form of information dispersal algorithm into a number of file “slices” or subsets in such a manner that the data in each file share is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other file shares. These file shares are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being transferred to or stored on a grid of distributed storage locations, various grid resources may become non-operational or may operate below at a less than optimal level. When dispersed file shares are being written to a dispersed storage grid which not available, the grid clients designates the dispersed data shares that could not be written at that time on a Rebuild List. In addition when grid resources already storing dispersed data become non-available, a process within the dispersed storage grid designates the dispersed data shares that need to be recreated on the Rebuild List. At other points in time a separate process reads the set of Rebuild Lists used to create the corresponding dispersed data and stores that data on available grid resources.
Owner:PURE STORAGE
Metadata management system for an information dispersed storage system
ActiveUS20070079083A1Less usableImprove privacyComputer security arrangementsMemory systemsInformation dispersalMetadata management
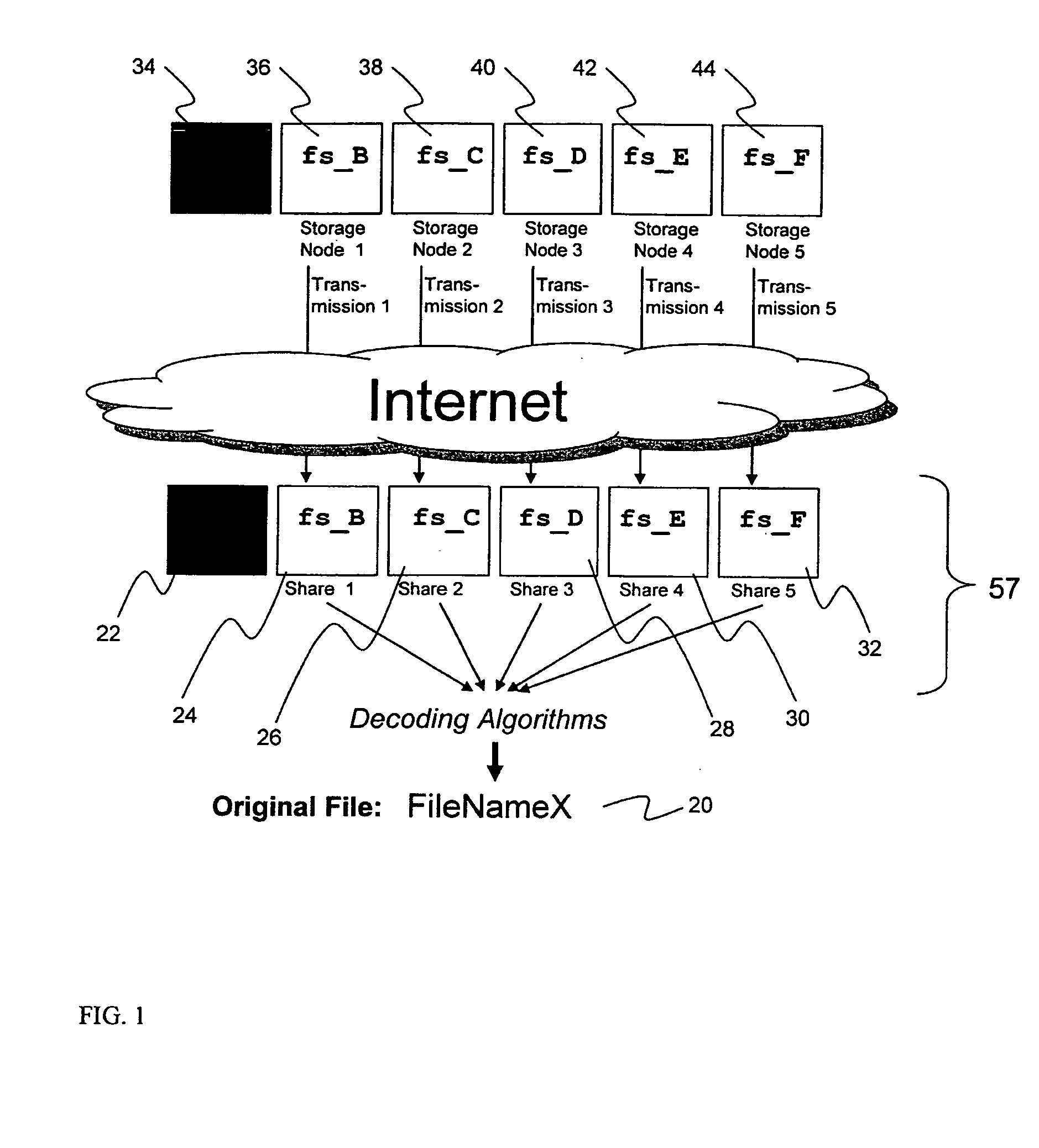
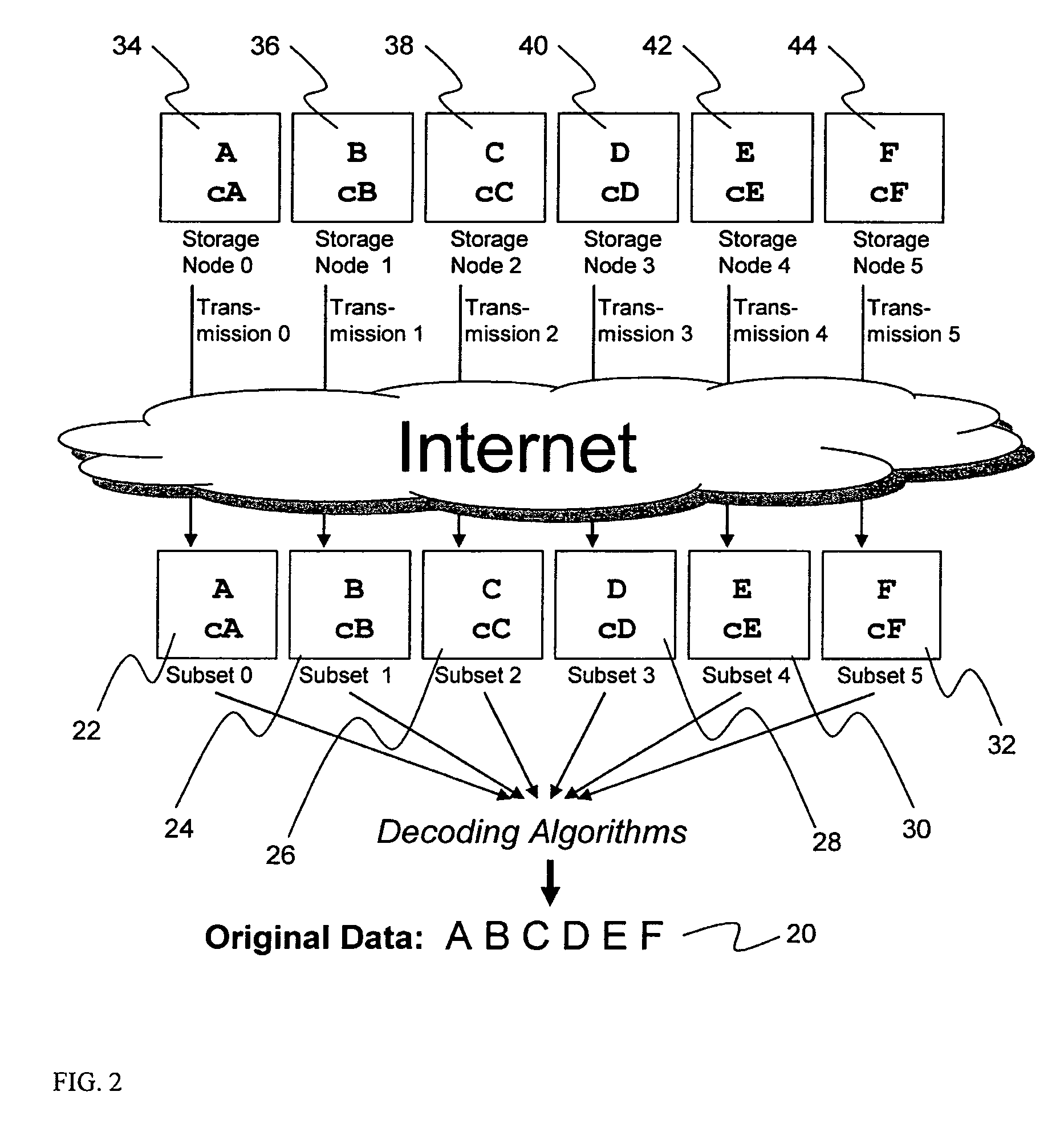
Briefly, the present invention relates to an information dispersal sytem in which original data to be stored is separated into a number of data “slices” in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate storage devices as a way of increasing privacy and security. In accordance with an important aspect of the invention, a metadata management system stores and indexes user files across all of the storage nodes. A number of applications run on the servers supporting these storage nodes and are responsible for controlling the metadata. Metadata is the information about the data, the data slices or data subsets and the way in which these data subsets are dispersed among different storage nodes running over the network. As used herein, metadata includes data source names, their size, last modification date, authentication information etc. This information is required to keep track of dispersed data subsets among all the nodes in the system. Every time new data subsets are stored and old ones are removed from the storage nodes, the metadata is updated. In accordance with an important aspect of the invention, the metadata management system stores metadata for dispersed data where: The dispersed data is in several pieces. The metadata is in a separate dataspace from the dispersed data. Accordingly, the metadata management system is able to manage the metadata in a manner that is computationally efficient relative to known systems in order to enable broad use of the invention using the types of computers generally used by businesses, consumers and other organizations currently.
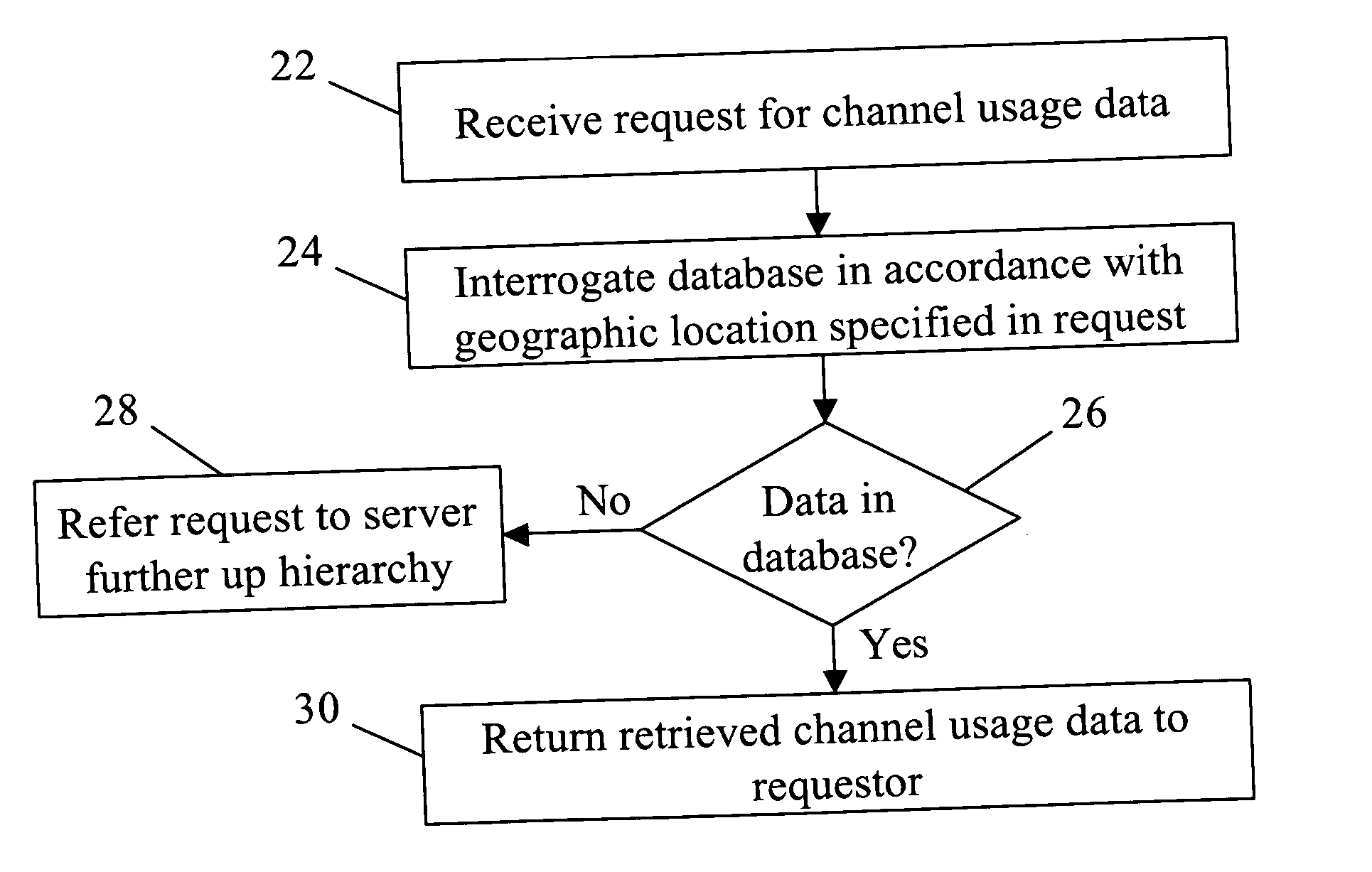
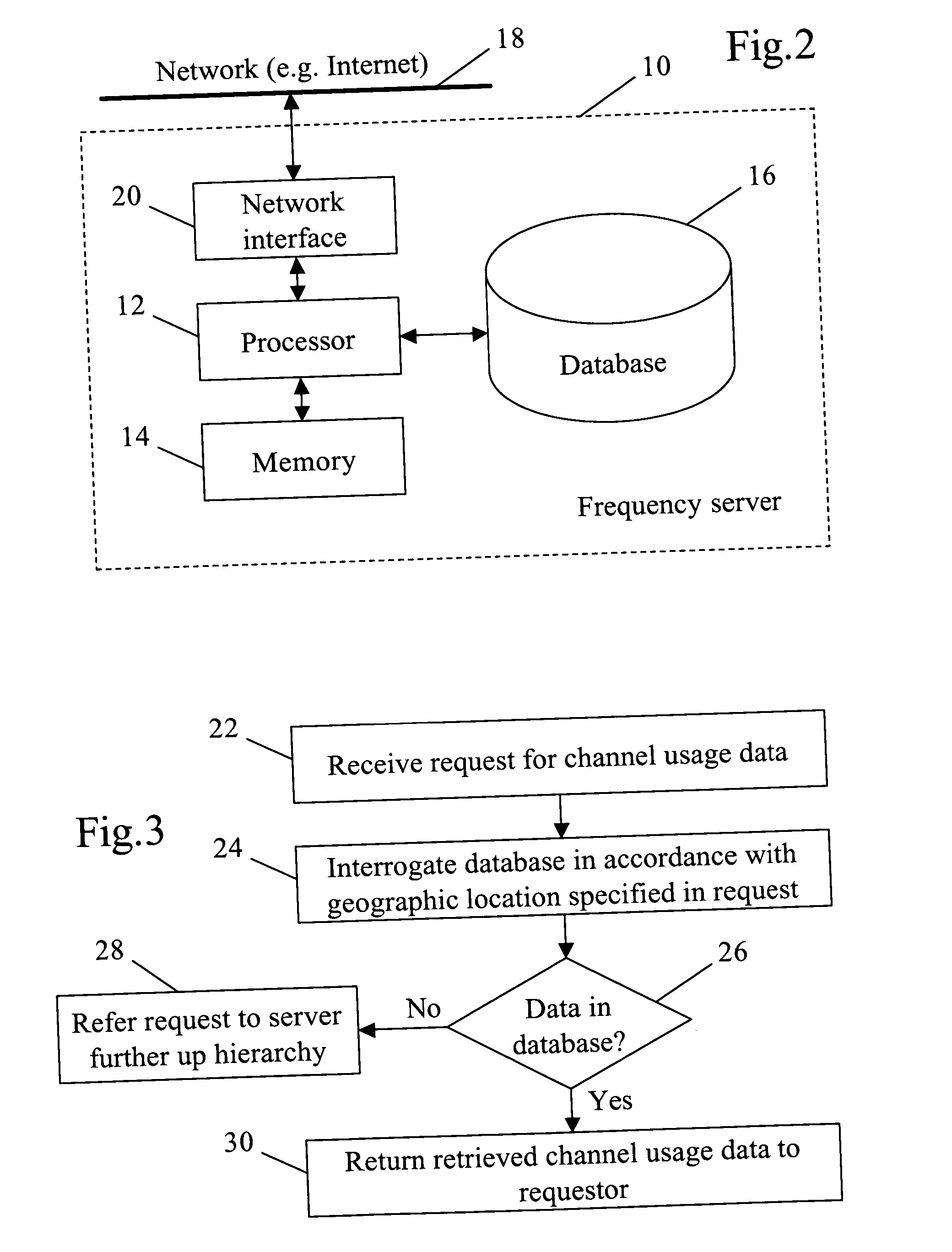
Owner:PURE STORAGE
Billing system for information dispersal system
ActiveUS20070174192A1Less usableLess recognizableFinanceComputer security arrangementsInformation dispersalOriginal data
A billing process is disclosed for a information dispersal system or digital data storage system. In one embodiment of the invention, the original data to be stored is separated into a number of data “slices” or shares in such a manner that the data in each subset is less usable or less recognizable or completely unusable or completely unrecognizable by itself except when combined with some or all of the other data subsets. These data subsets are stored on separate digital data storage devices as a way of increasing privacy and security. As dispersed file shares are being stored or removed from a grid of distributed storage locations, a set of metadata tables are created, separate from the dispersed file share storage, to maintain information about the original data size of each block, file or set of file shares dispersed on the grid. The original data size information in these separate metadata tables is used to determine usage information based upon the original file size even though the file has been dispersed onto a storage grid that contains file slices who size may not relate to the original file size and the file slices may have been compressed by the system in order to reduce storage space or improve transmission time. As such, the billing process is able to enable a broad range of commercial billing options for billing for commercial data services on an information dispersal grid.
Owner:PURE STORAGE
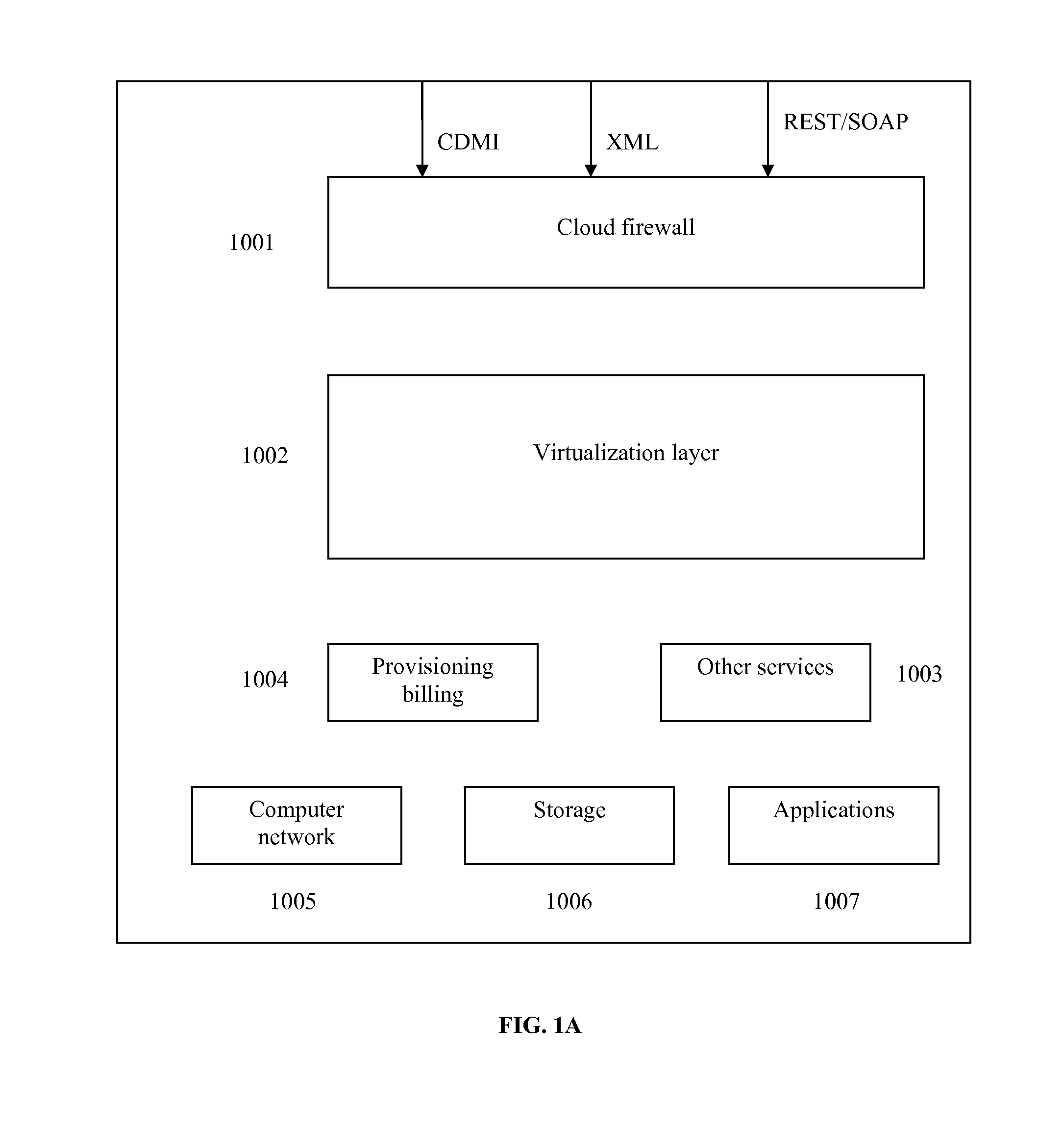
Virtualized data storage vaults on a dispersed data storage network
ActiveUS20090094251A1Efficient managementData processing applicationsDigital data processing detailsInformation dispersalVirtualization
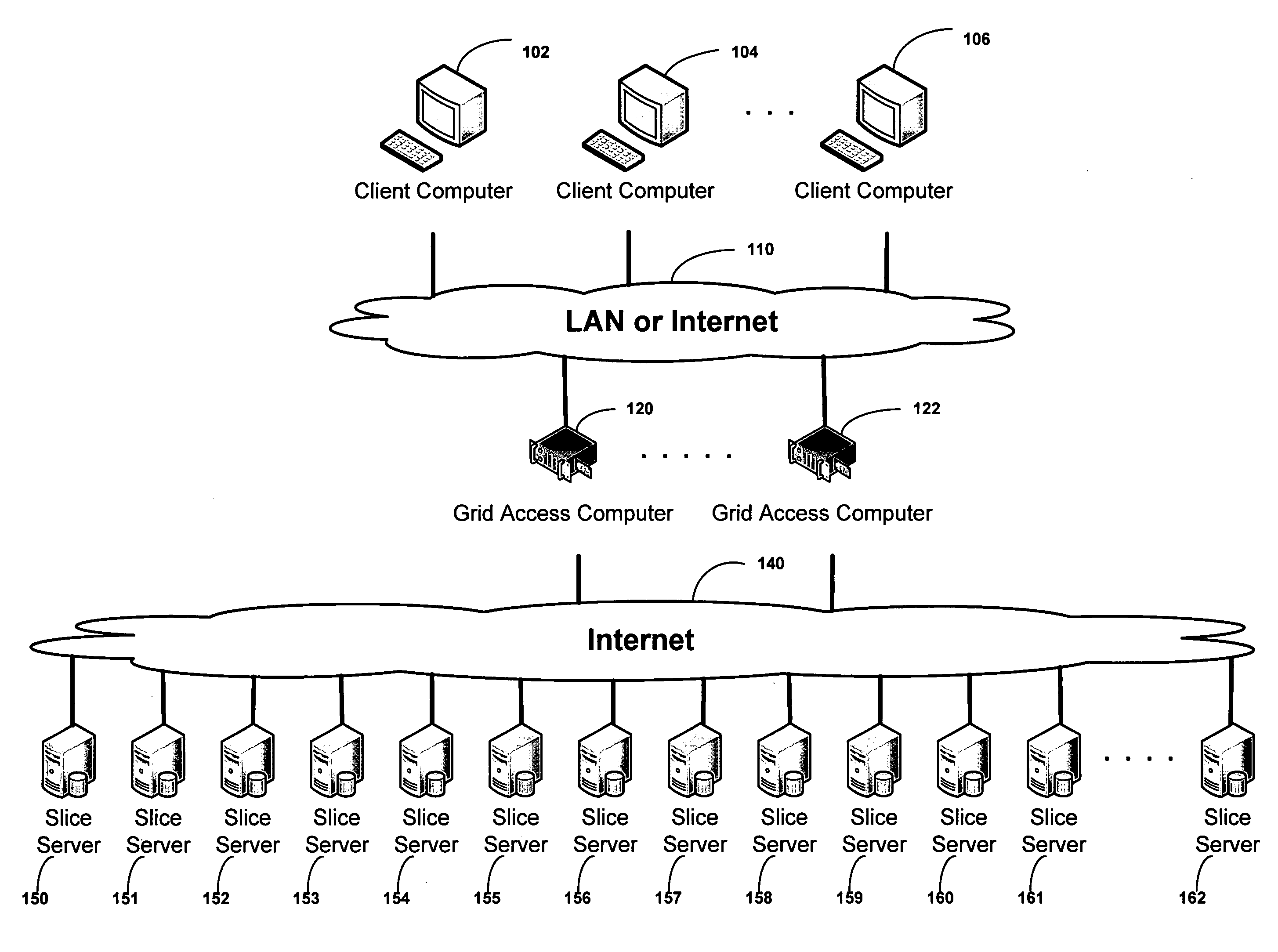
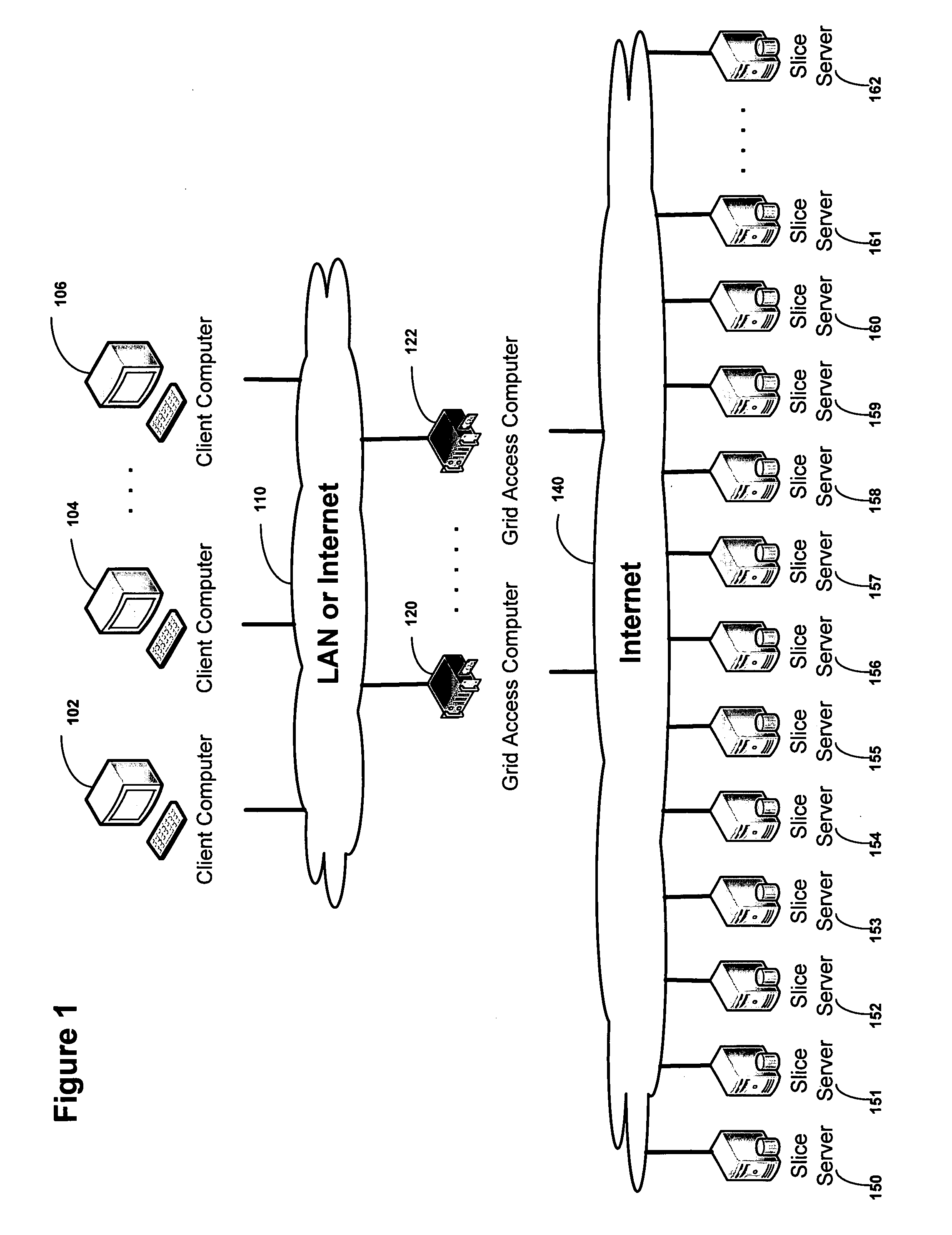
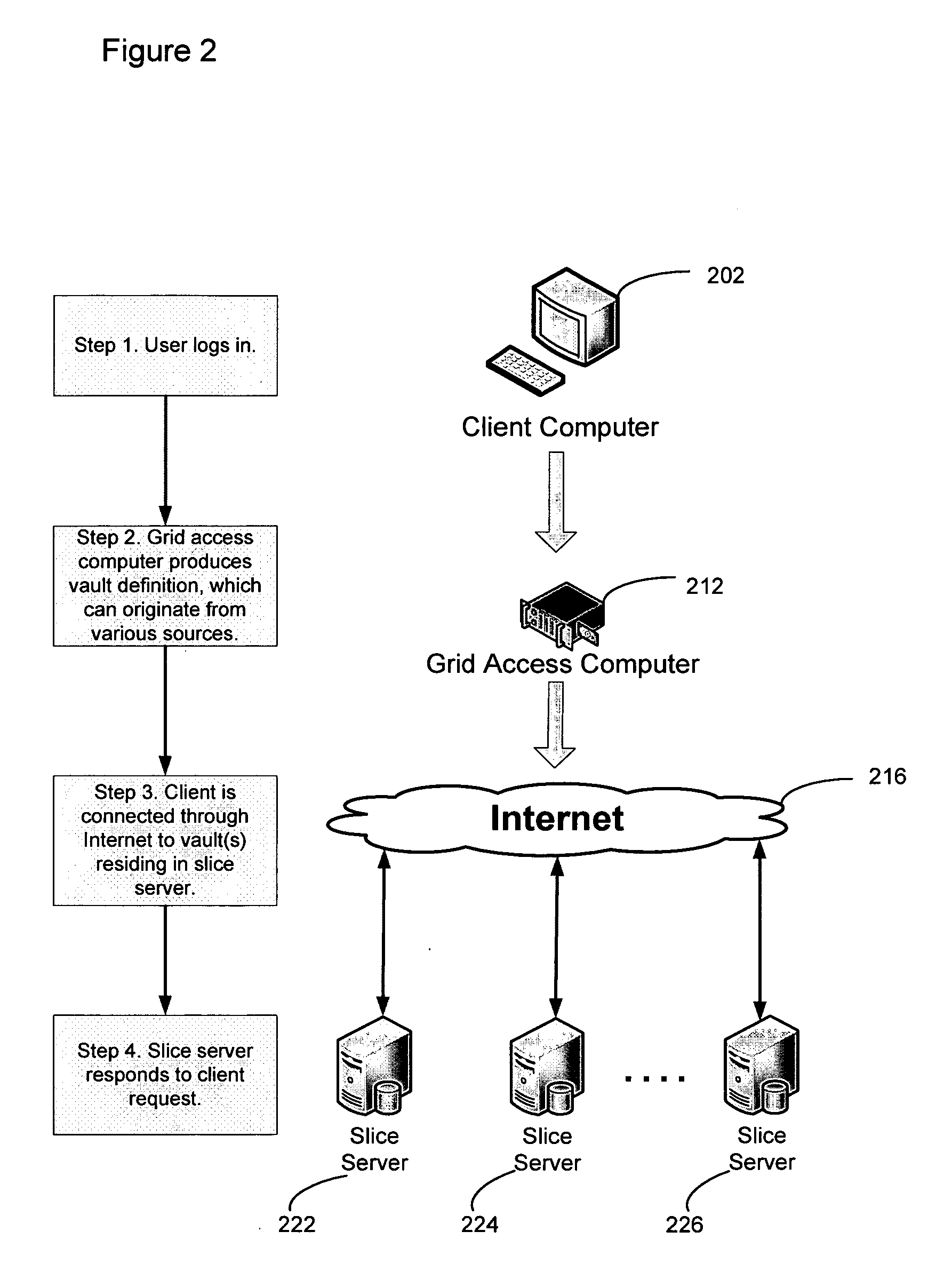
A system, method, and apparatus for implementing a plurality of dispersed data storage networks using a set of slice servers are disclosed. A plurality of information records are maintained, with each information record corresponding to a dispersed data storage network. The information record maintains what slice servers are used to implement the dispersed data storage network, as well as other information needed to administer a DDSN, such as the information dispersal algorithm used, how data is stored, and whether data is compressed or encrypted.
Owner:PURE STORAGE
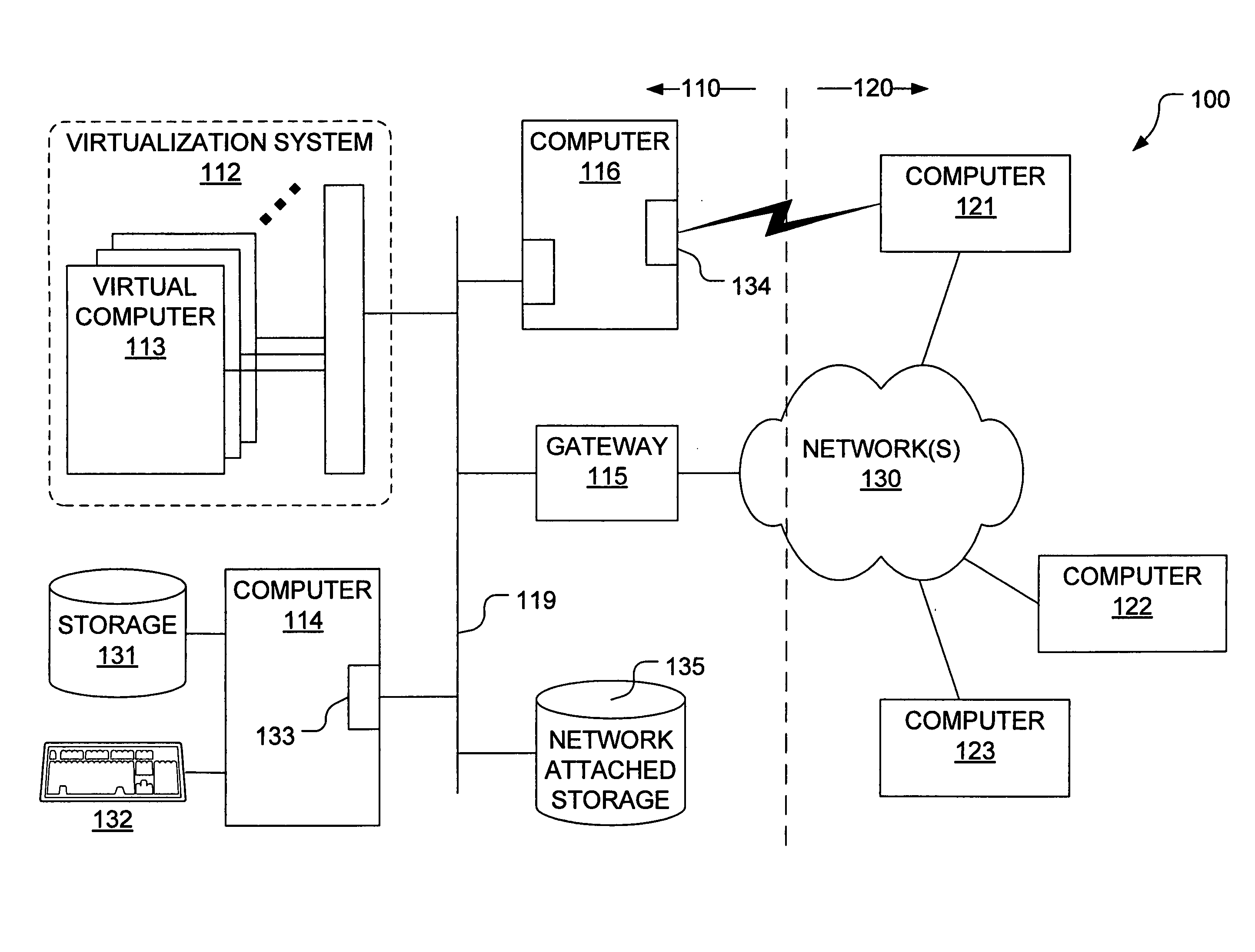
Distributed virtual storage cloud architecture and a method thereof
ActiveUS20130204849A1Prevent lockInput/output to record carriersDigital data information retrievalThird partyVirtualization
The present disclosure relates to a distributed information storage system which functions as virtual cloud storage overlay on top of physical cloud storage systems. The disclosure discloses transparently solving all the data management related security, virtualization, reliability and enables transparent cloud storage migration, cloud storage virtualization, information dispersal and integration across disparate cloud storage devices operated by different providers or on-premise storage. The cloud storage is owned or hosted by same or different third-party providers who own the information contained in the storage which eliminates cloud dependencies. This present disclosure functions as a distributed cloud storage delivery platform enabling various functionalities like cloud storage virtualization, cloud storage integration, cloud storage management and cloud level RAID.
Owner:CHACKO PETER
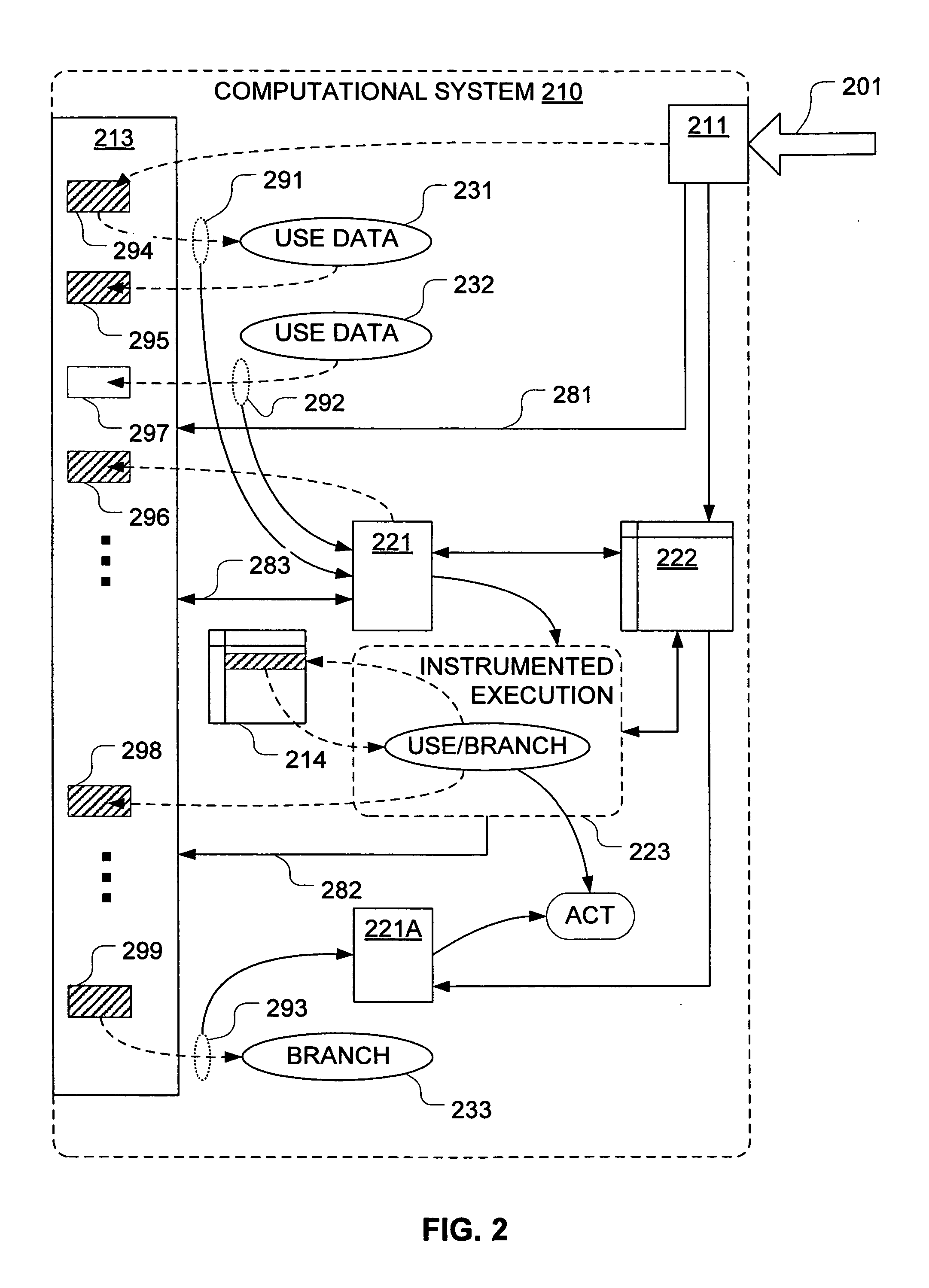
Taint tracking mechanism for computer security
ActiveUS8510827B1Easy to trackAvoid modificationMemory loss protectionDigital data processing detailsInformation dispersalOperation mode
Mechanisms have been developed for securing computational systems against certain forms of attack. In particular, it has been discovered that, by maintaining and propagating taint status for memory locations in correspondence with information flows of instructions executed by a computing system, it is possible to provide a security response if and when a control transfer (or other restricted use) is attempted based on tainted data. In some embodiments, memory management facilities and related exception handlers can be exploited to facilitate taint status propagation and / or security responses. Taint tracking through registers of a processor (or through other storage for which access is not conveniently mediated using a memory management facility) may be provided using an instrumented execution mode of operation. For example, the instrumented mode may be triggered by an attempt to propagate tainted information to a register. In some embodiments, an instrumented mode of operation may be more generally employed. For example, data received from an untrusted source or via an untrusted path is often transferred into a memory buffer for processing by a particular service, routine, process, thread or other computational unit. Code that implements the computational unit may be selectively executed in an instrumented mode that facilitates taint tracking. In general, instrumented execution modes may be supported using a variety of techniques including a binary translation (or rewriting) mode, just-in-time (JIT) compilation / re-compilation, interpreted mode execution, etc. Using an instrumented execution mode and / or exception handler techniques, modifications to CPU hardware can be avoided if desirable.
Owner:VMWARE INC
Systems and methods for securing data using multi-factor or keyed dispersal
ActiveUS20090177894A1Minimal compute resourceAvoid the needUnauthorized memory use protectionHardware monitoringInformation dispersalOriginal data
A secure data parser is provided that may be integrated into any suitable system for securely storing and communicating data. The secure data parser parses data and then splits the data into multiple portions that are stored or communicated distinctly. Encryption of the original data, the portions of data, or both may be employed for additional security. The secure data parser may be used to protect data in motion by splitting original data into portions of data, that may be communicated using multiple communications paths. A keyed information dispersal algorithm (keyed IDA) may also be used. The key for the keyed IDA may additionally be protected by an external workgroup key, resulting in a multi-factor secret sharing scheme.
Owner:SECURITY FIRST INNOVATIONS LLC
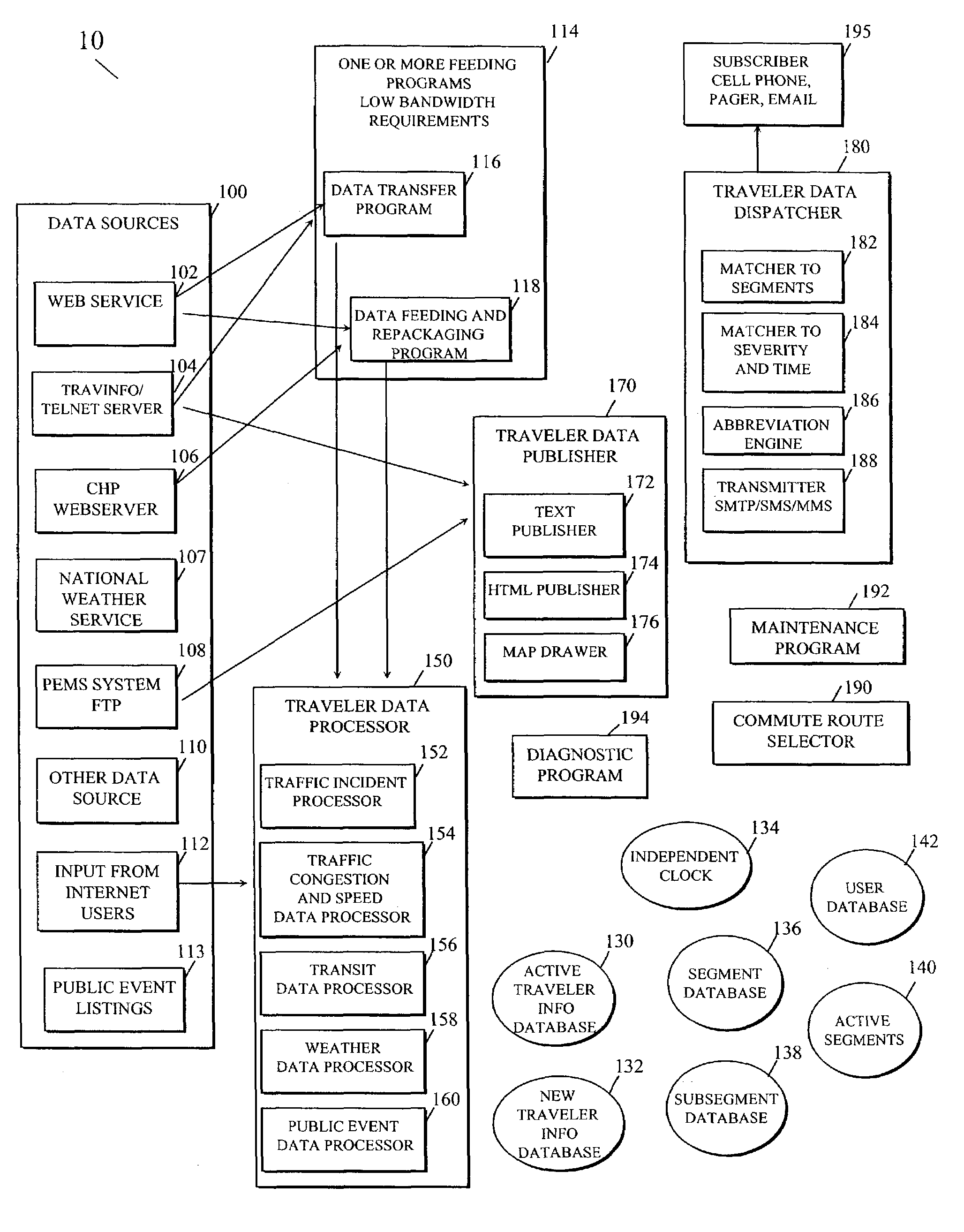
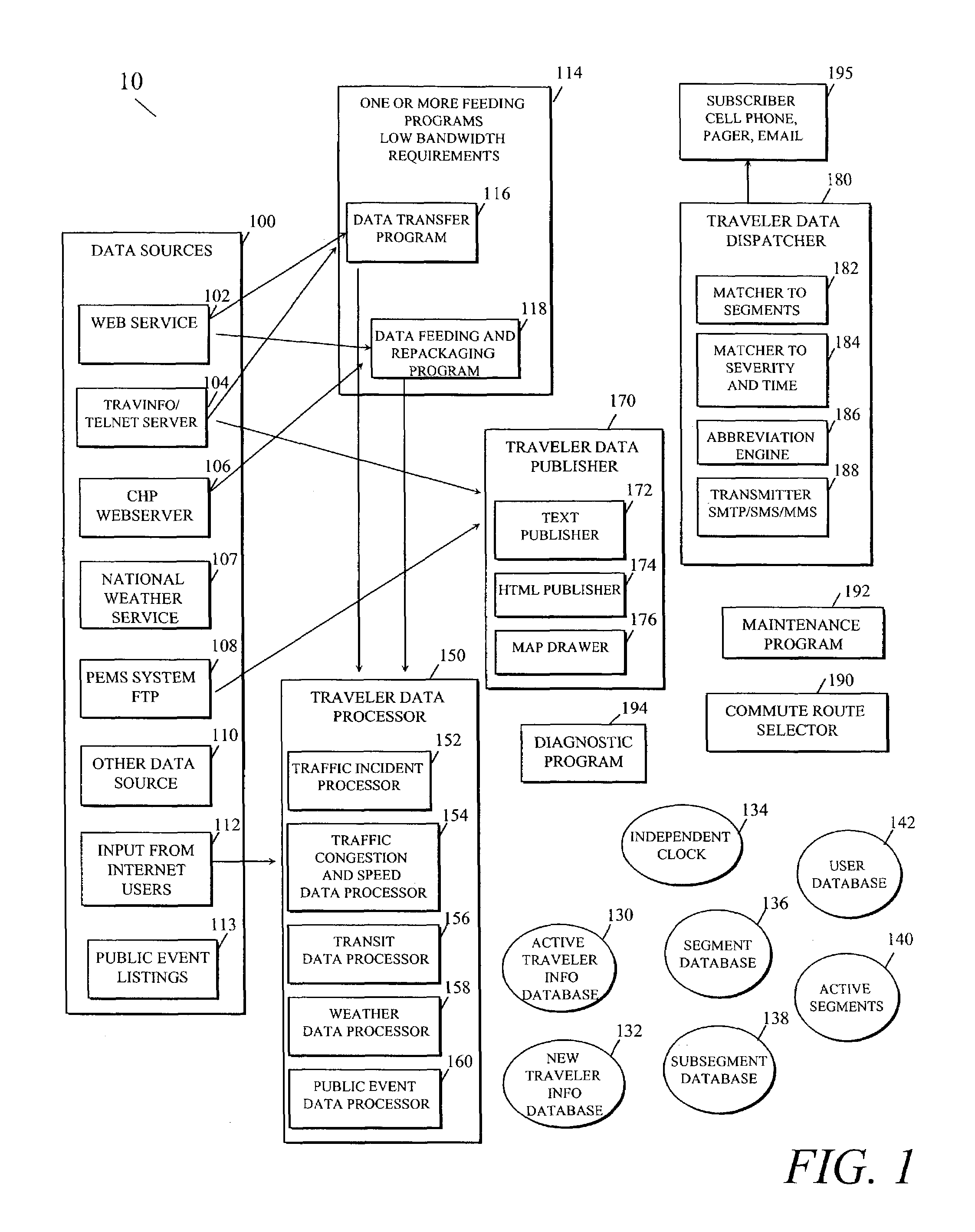
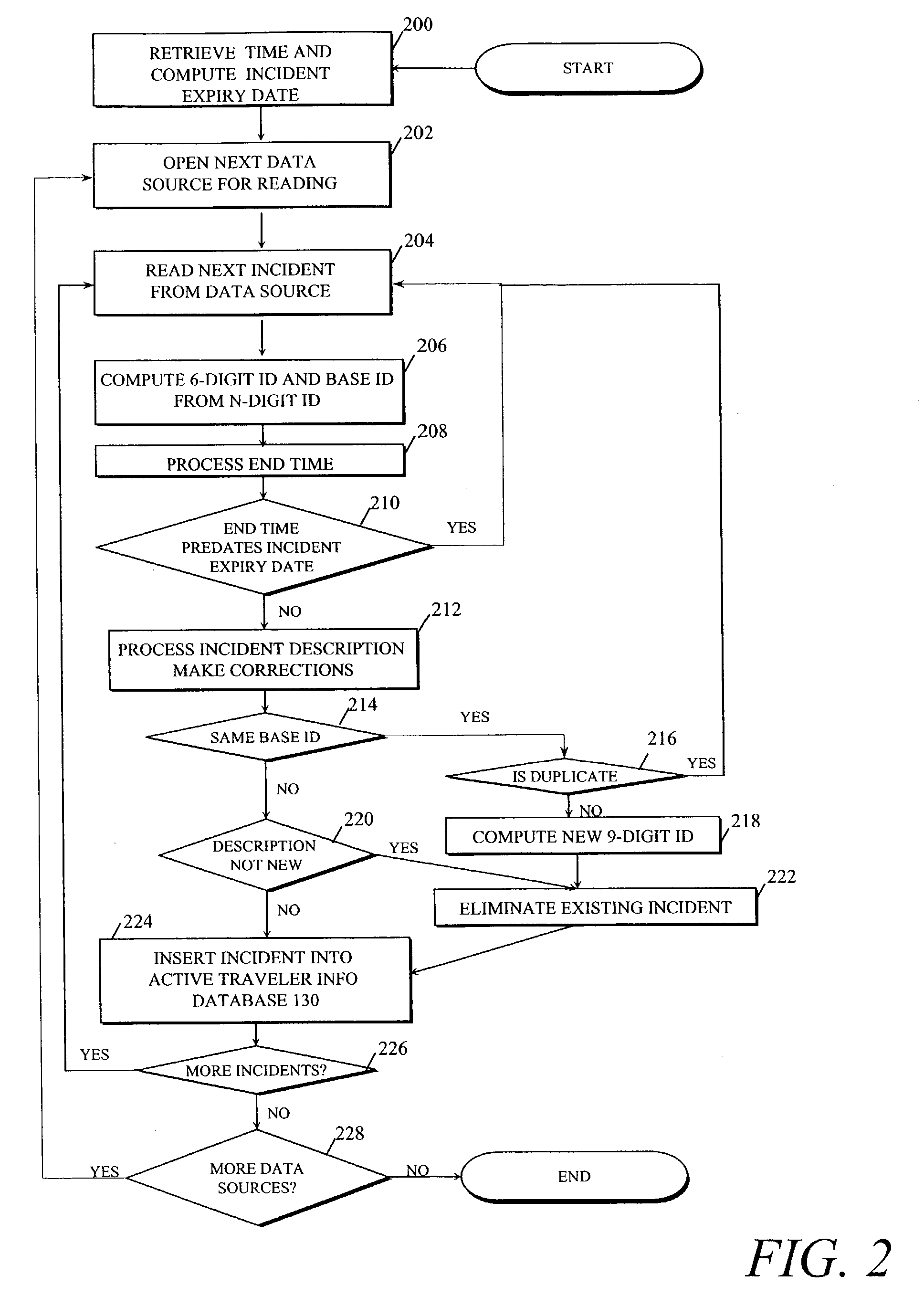
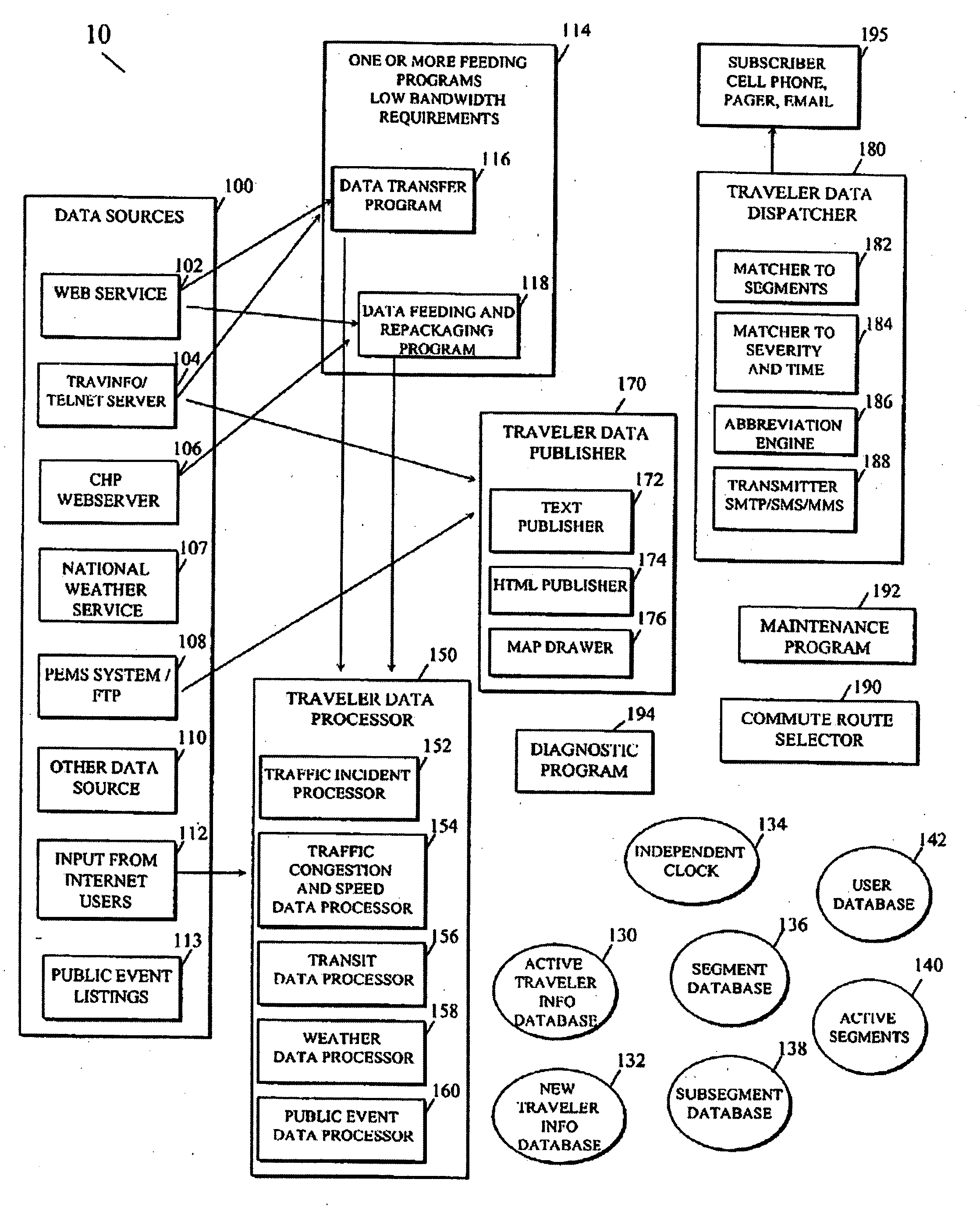
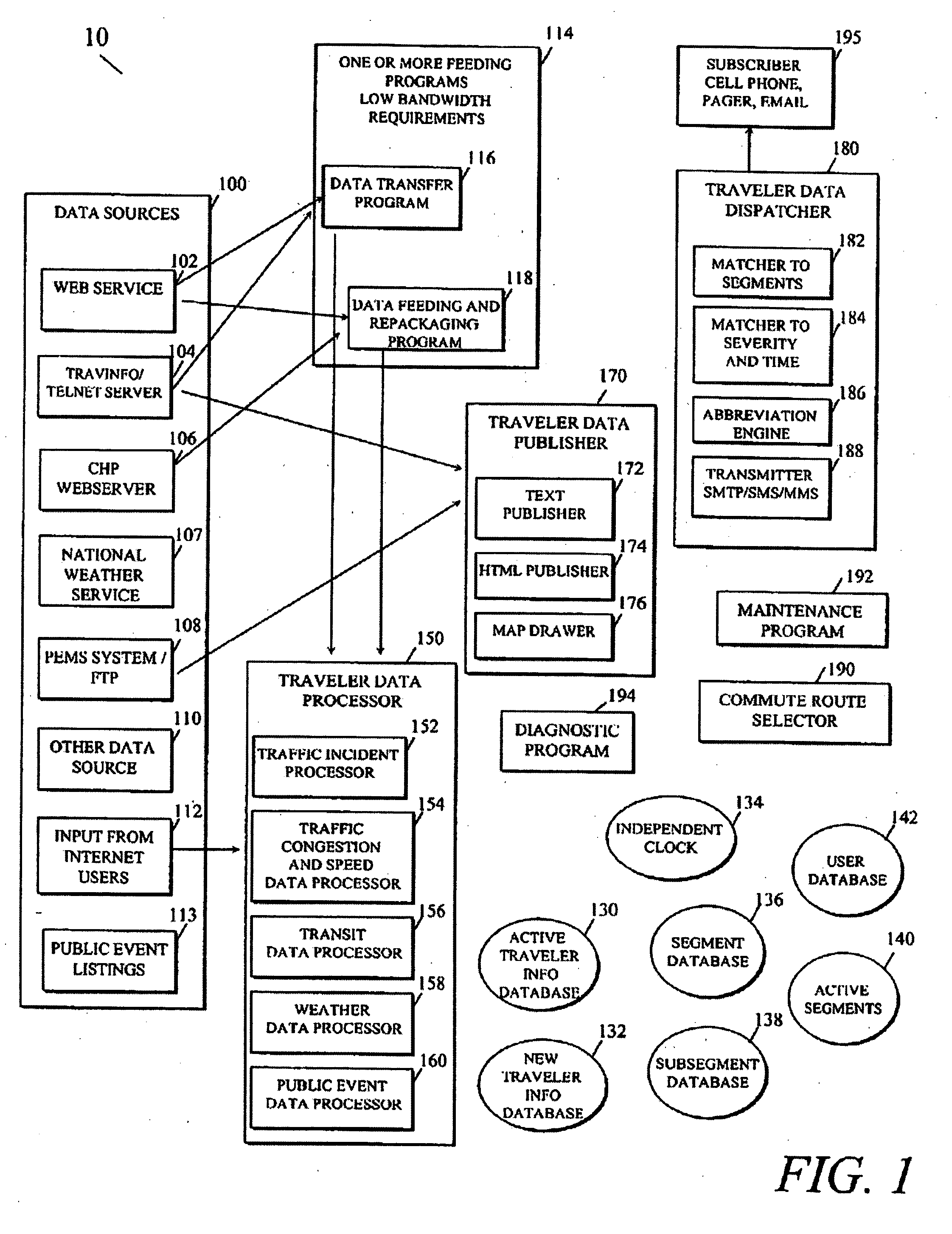
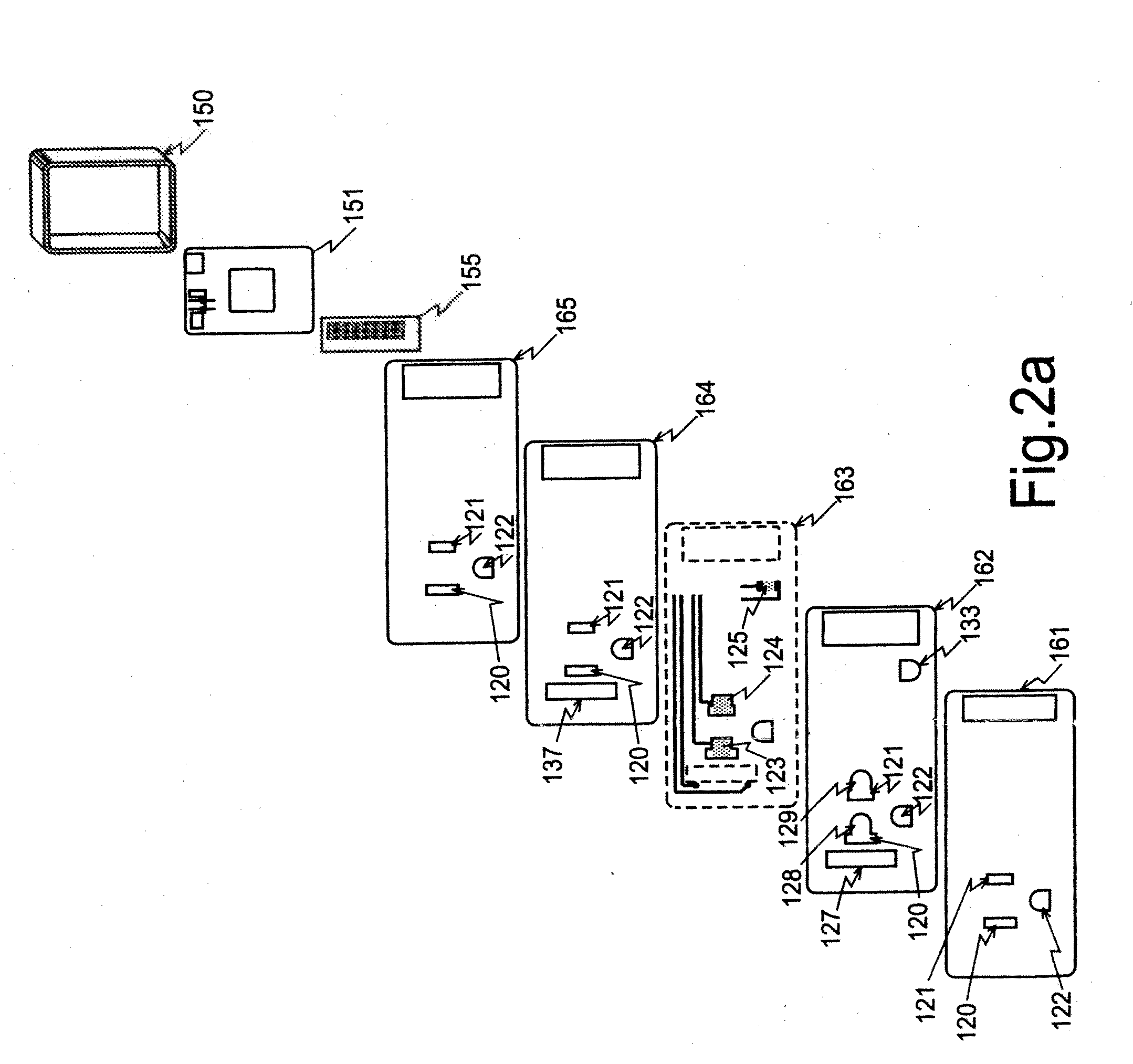
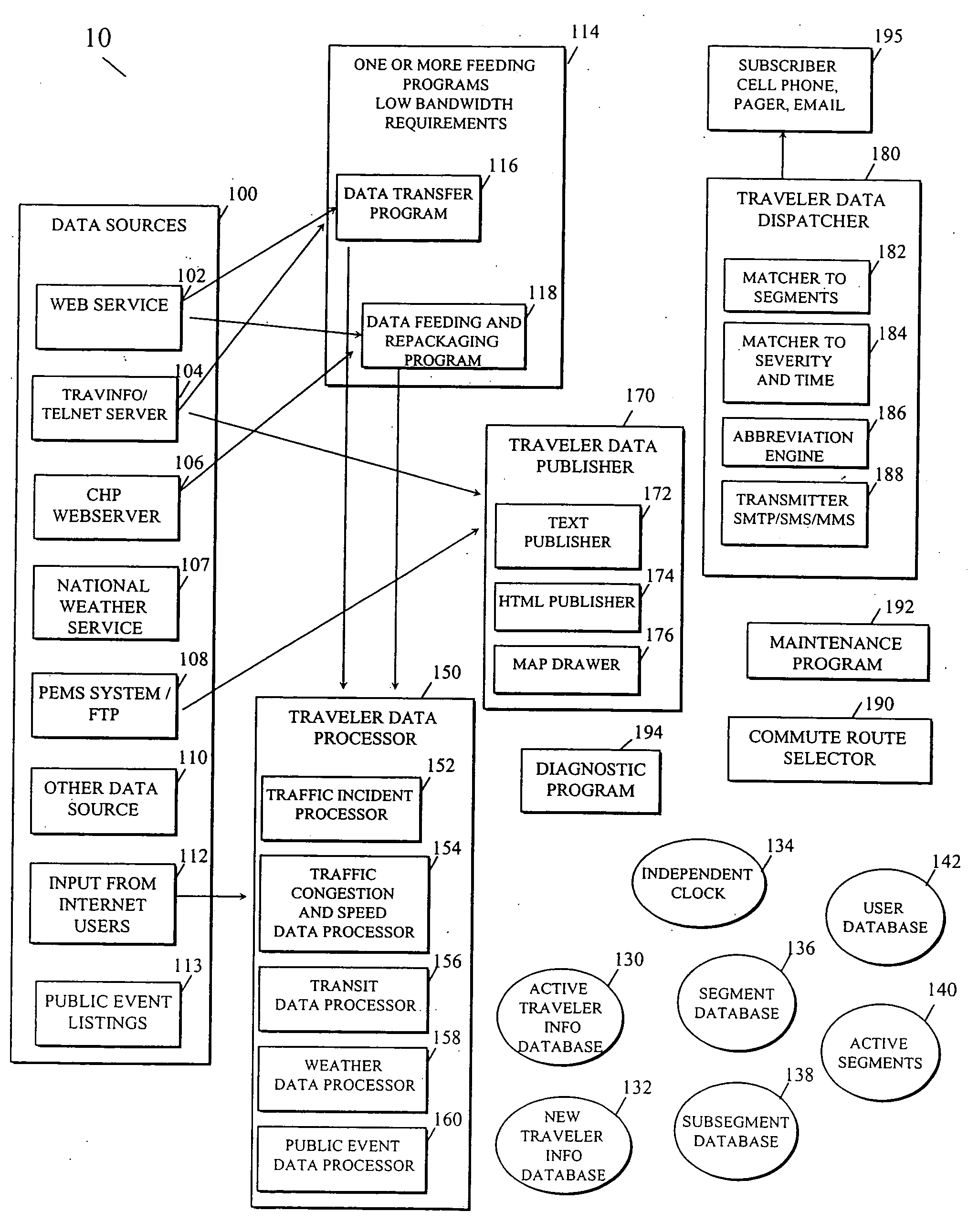
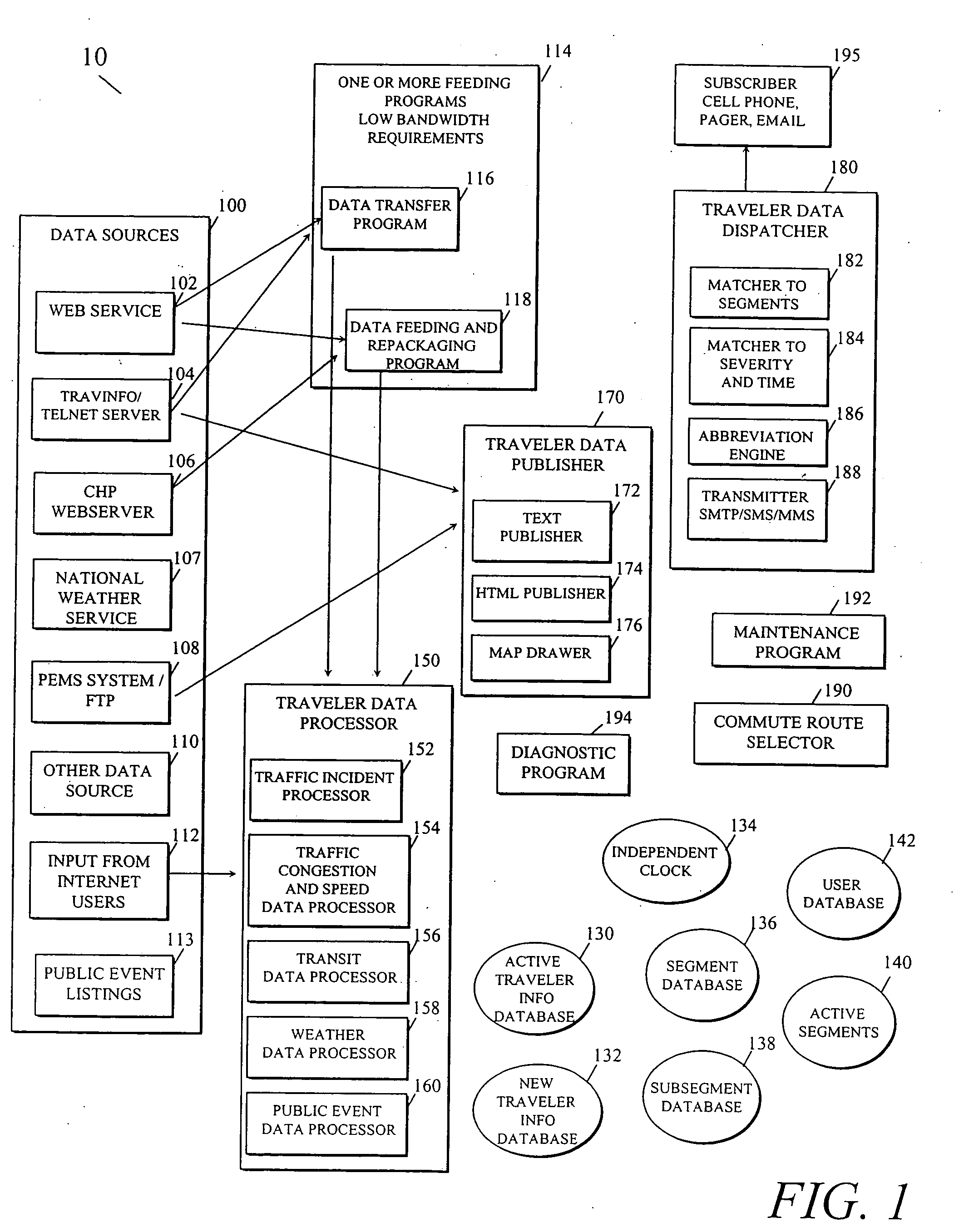
Personalized traveler information dissemination system
ActiveUS6989765B2Short system delayElimination of outdated informationElectric signal transmission systemsInstruments for road network navigationInformation dispersalPersonalization
Disclosed herein is a traveler information monitoring and dissemination system. The system disclosed herein provides real time information to a traveler, wherein the real time information may be pre-selected by the traveler. The system ensures consistent and quality data are produced and issued to the traveler.
Owner:UBER TECH INC
Systems and methods for gslb mep connection management across multiple core appliances
ActiveUS20110153840A1Improve performanceAvoid any of the servers being overburdened or crashingMultiple digital computer combinationsTransmissionInformation dispersalTransport layer
The present disclosure presents systems and methods for obtaining metric information by a multi-core GSLB intermediary device and providing global server load balancing services using the obtained information. A first core of a multi-core GSLB appliance establishes a transport layer connection to a remote load balancer at a site of a plurality of sites. The first core transmits a message to each of the other cores of the multi-core GSLB appliance that that the first core is a master core for receiving metric information from the load balancer. The first core receives metric information of the remote site from the load balancer. The first core propagates the metric information to each of the other cores of the GSLB appliance. A GSLB virtual server on a slave core receives a DNS request. The GSLB virtual server determines a DNS resolution for the DNS request based on the metric information.
Owner:CITRIX SYST INC
Hierarchical system and method for centralized management of thin clients
InactiveUS20030061323A1Digital computer detailsData switching networksInformation dispersalInformation transmission
A system and method for managing a network of thin clients is disclosed. The thin clients may be organized into a hierarchy with multiple administrative servers in a hierarchy, each managing one or more thin clients. Updates to thin client configurations may be performed by propagating update information to a top-level master administrative server, which in turn conveys the update information to one or more lower-level remote administrative servers, which in turn convey the update information to their managed thin clients. To simplify network management, the thin clients may be organized into arbitrary clusters, regardless of their position within the hierarchy structure. The hierarchy may also be used to control the propagation of error messages from thin clients. The hierarchy may be implemented using a thin client management program that configures thin clients according to their position within the hierarchy.
Owner:EAST KENNETH H +4
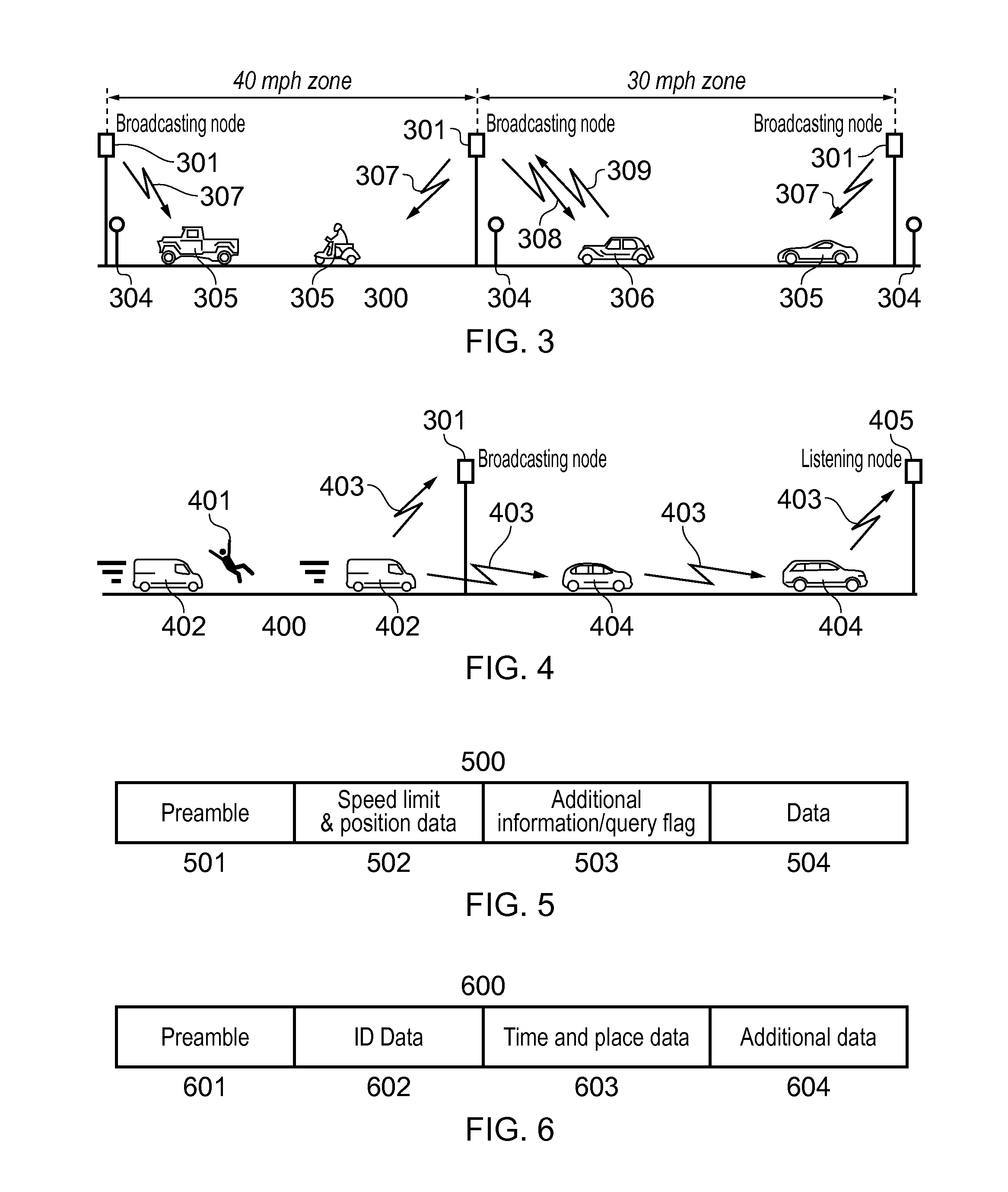
Vehicular safety system
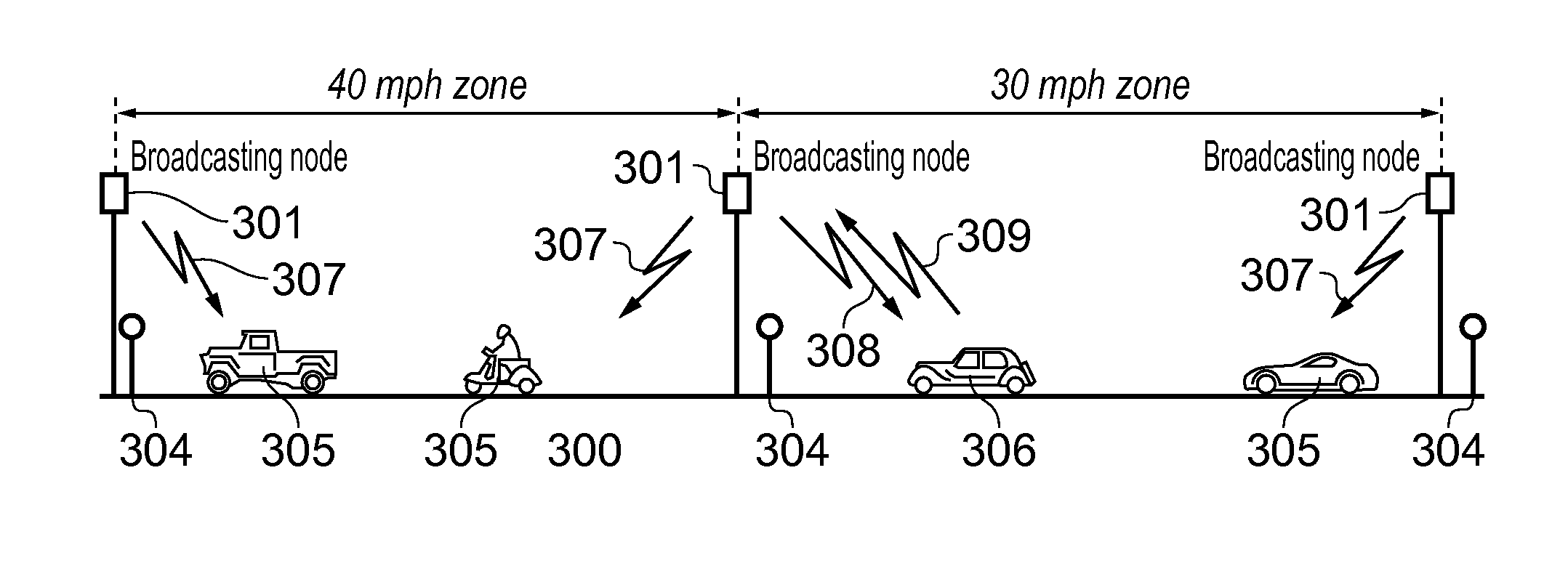
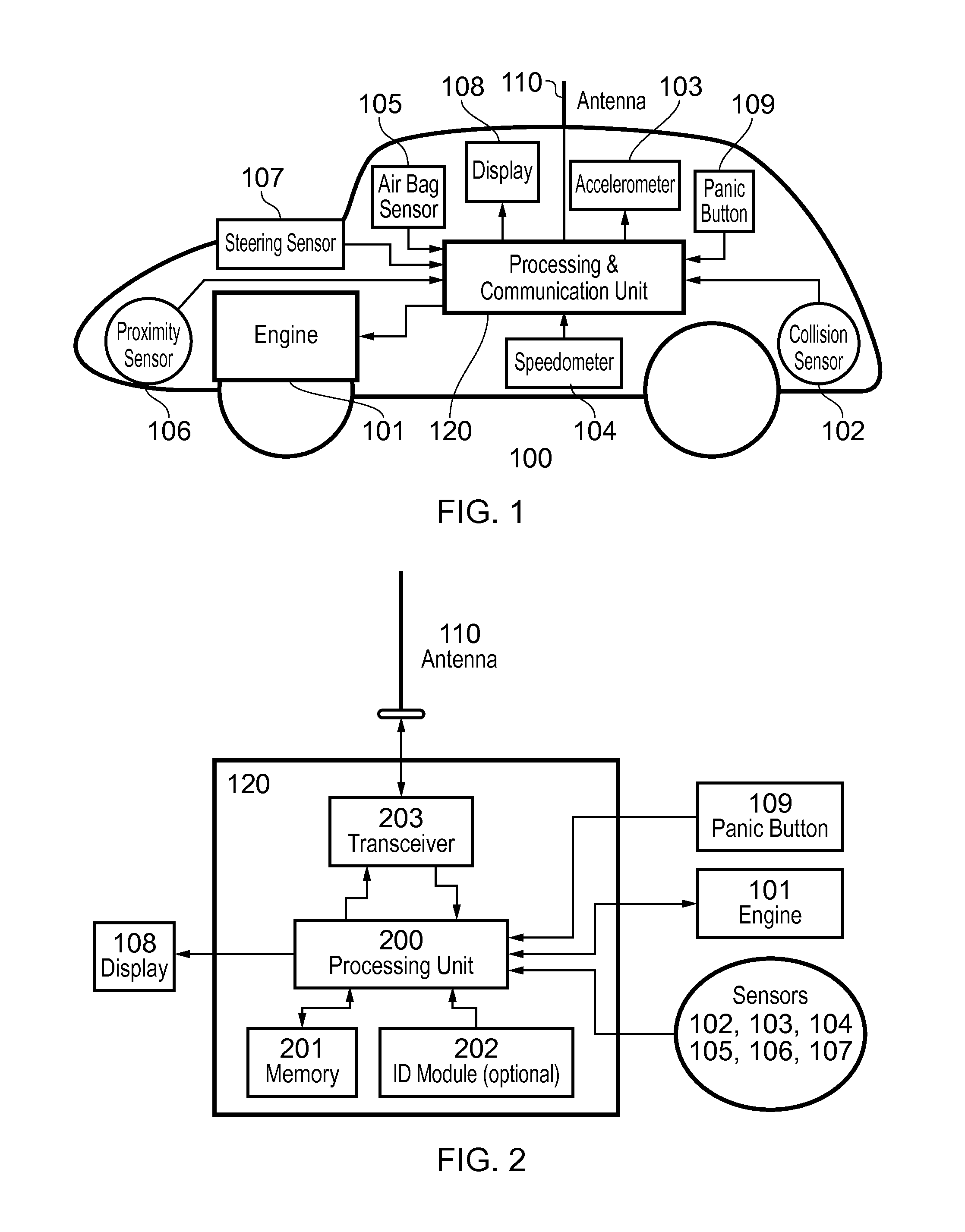
ActiveUS20150310742A1Curb number of fatalityImprove road safetyArrangements for variable traffic instructionsAlarmsInformation dispersalEvent type
A vehicular safety system employing an adaptive epidemic information dissemination protocol running on a wireless ad-hoc network composed by neighboring vehicles and roadside stations. The protocol is based on storage and re-transmission of messages by vehicle on-board units; both storage time and re-transmission period are adaptively adjusted to make information spread through the network reasonably certain. An on-board vehicle system monitors a speed and acceleration to detect collisions or any other dangerous situations that might compromise the safety; when such an event is detected a time-stamped message identifies the vehicle and approximate location and event type. A panic button can trigger an emergency message in an immediate threat situation. Roadside stations add their location to the messages they relay; they also receive messages transmitted from passing vehicles, relaying them to law-enforcement agencies. Roadside stations can also broadcast messages aimed at locating and safely disabling stolen vehicles.
Owner:FUJITSU LTD
Systems and methods for distributing and securing data
ActiveUS20080137857A1Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
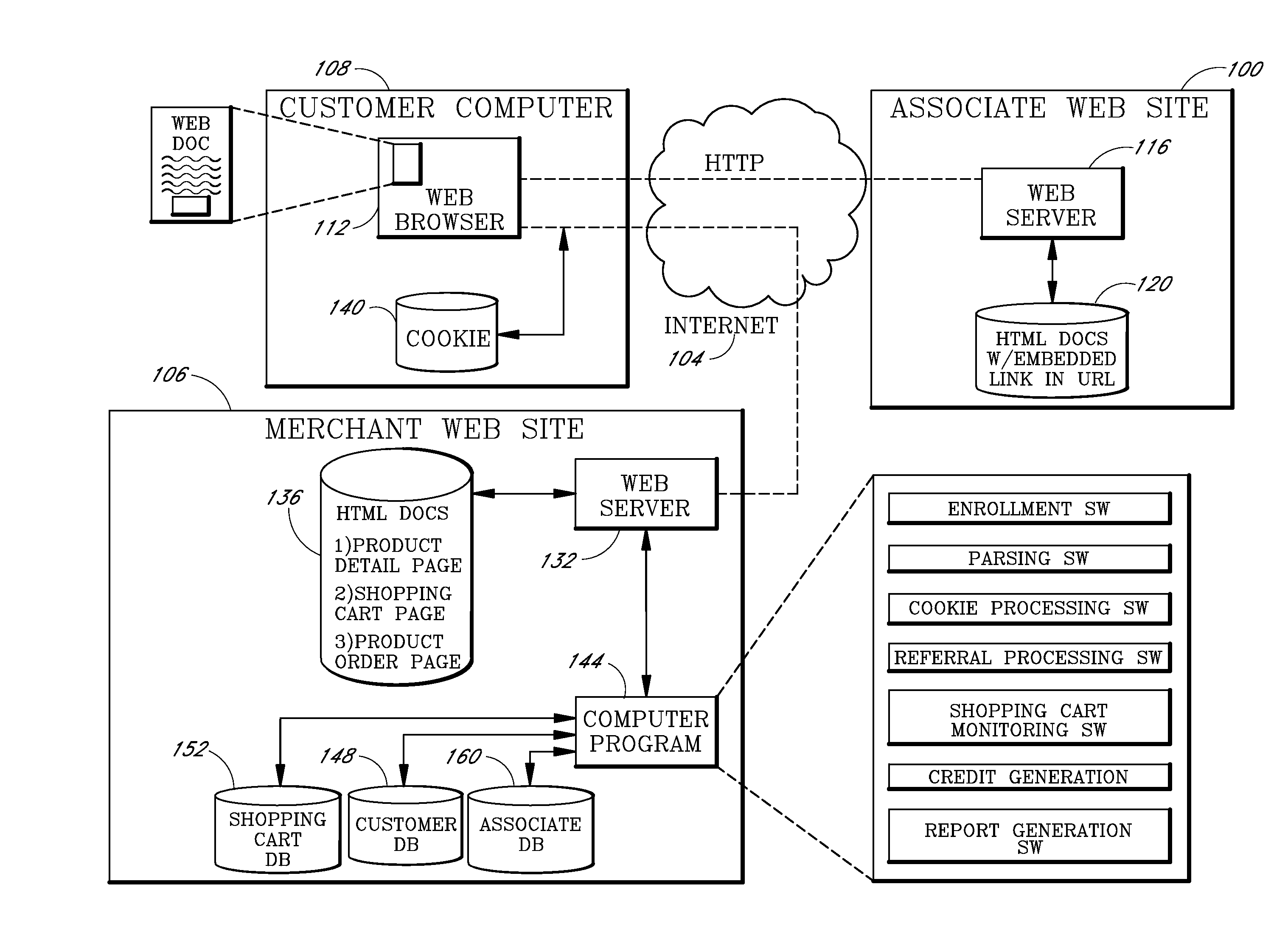
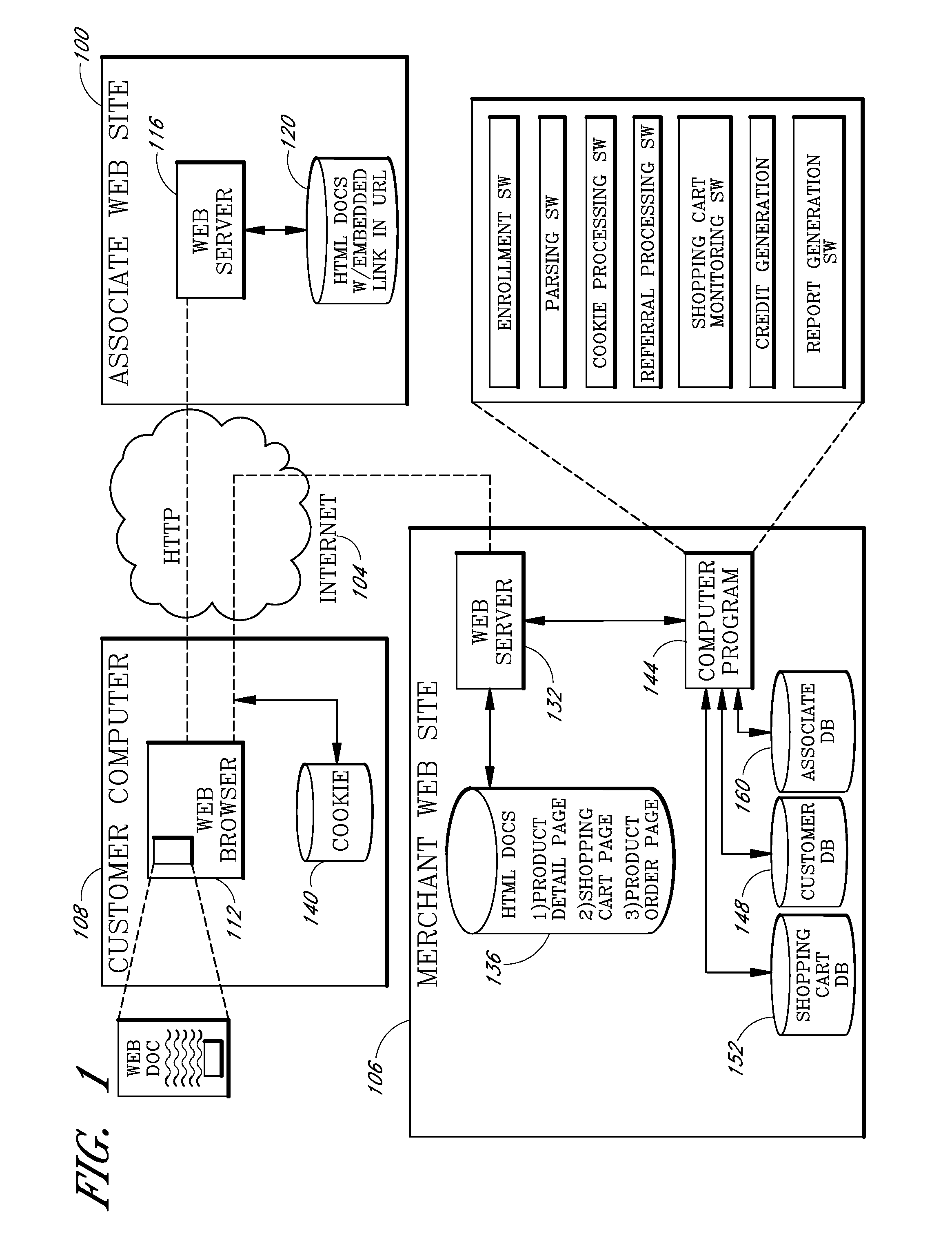
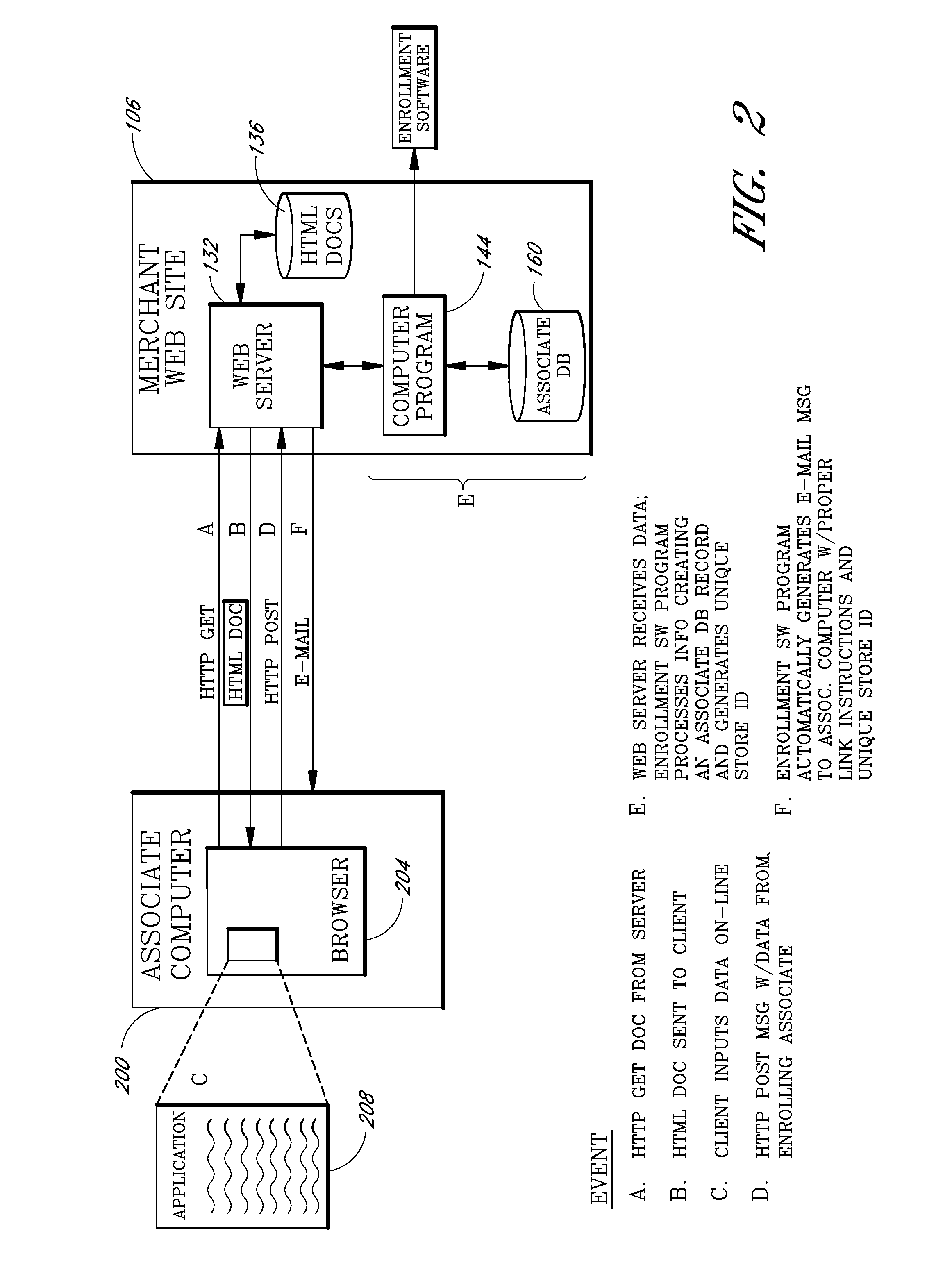
Internet-based customer referral system
InactiveUS20080167946A1Efficient mechanismEffective distributionMarket predictionsPayment architectureInformation dispersalWeb site
An Internet-based customer referral system enables individuals and other business entities (“associates”) to market products sold on a merchant web site in return for commissions. Following registration, the associate sets up a web site (or other information dissemination system) to distribute hypertextual catalog documents that include marketing information (product reviews, recommendations, etc.) about selected products of the merchant. In association with each such product, the catalog document includes a hypertextual “referral link” that allows a user / customer to access the merchant web site and purchase the product. When a customer selects a referral link, the customer's computer transmits unique IDs of the selected product and of the associate to the merchant's site, allowing the merchant to identify the product and the referring associate. If the customer subsequently purchases a product from the merchant's site, a commission is automatically credited to an account of the referring associate.
Owner:AMAZON TECH INC
Traffic information dissemination
InactiveUS20060158330A1Ensures relevanceImprove accuracyInstruments for road network navigationArrangements for variable traffic instructionsInformation dispersalTime information
Disclosed herein is a traveler information monitoring and dissemination system. The system disclosed herein provides real time information to a traveler, wherein the real time information may be pre-selected by the traveler. The system ensures consistent and quality data are produced and issued to the traveler.
Owner:UBER TECH INC
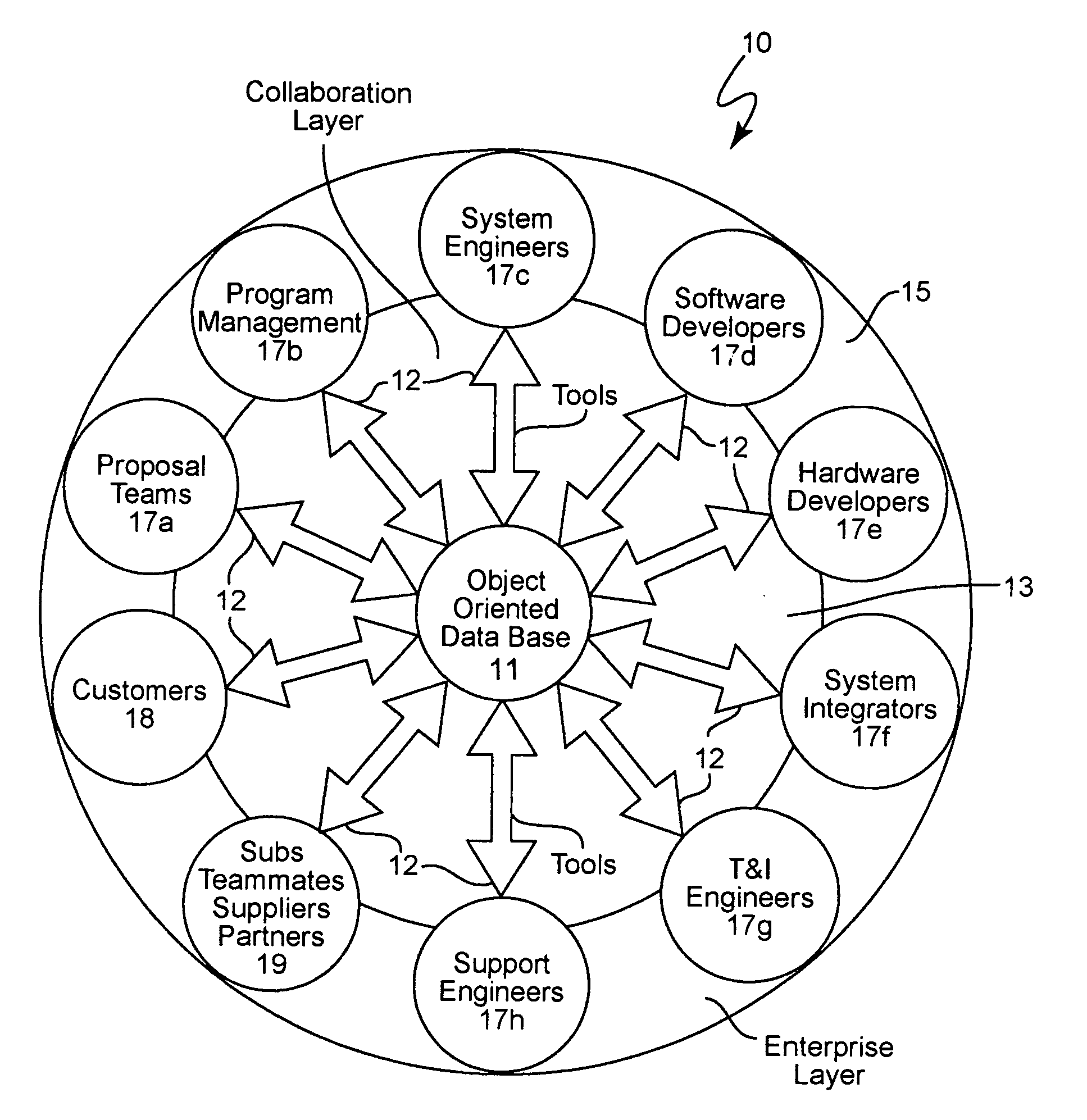
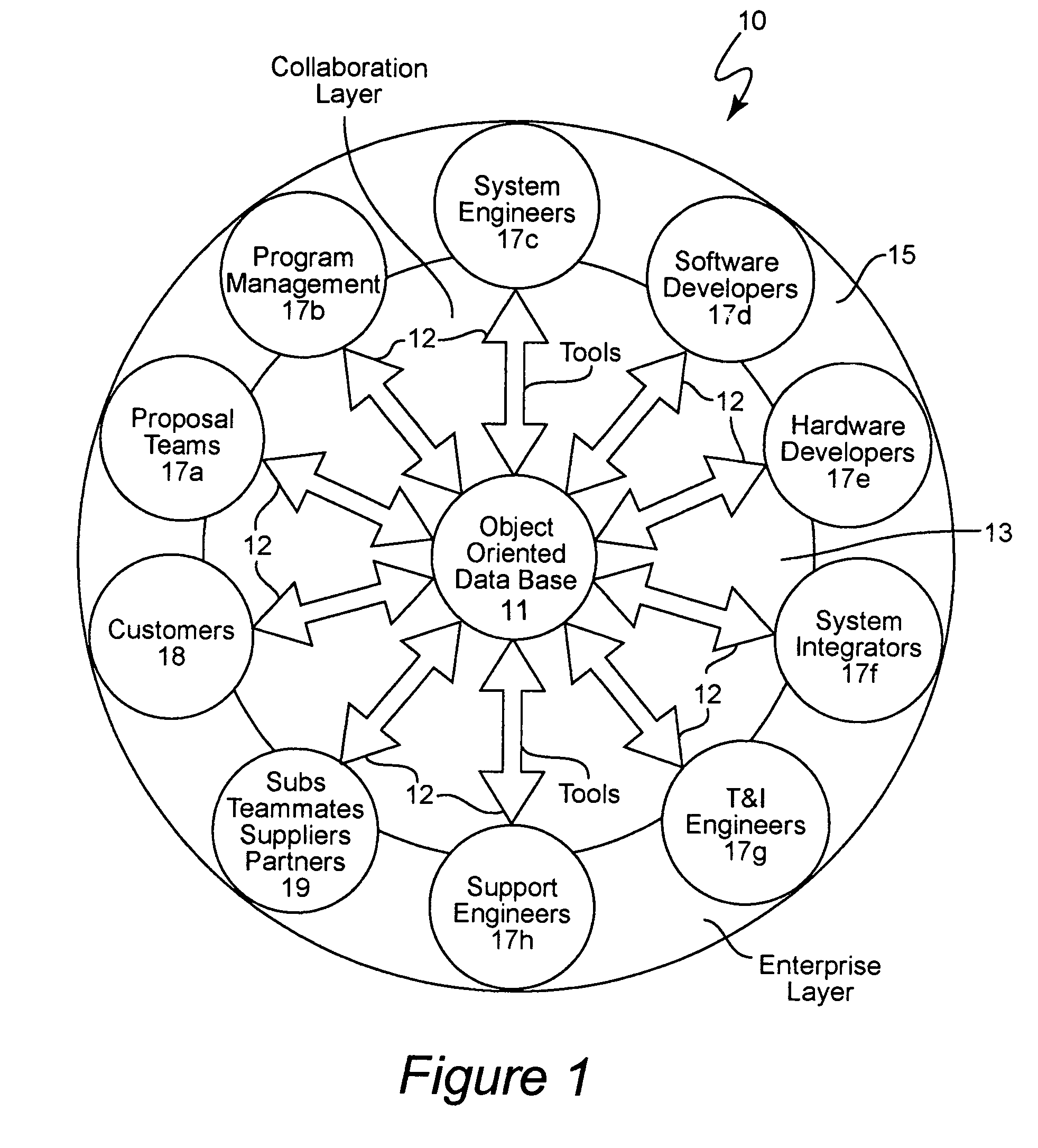
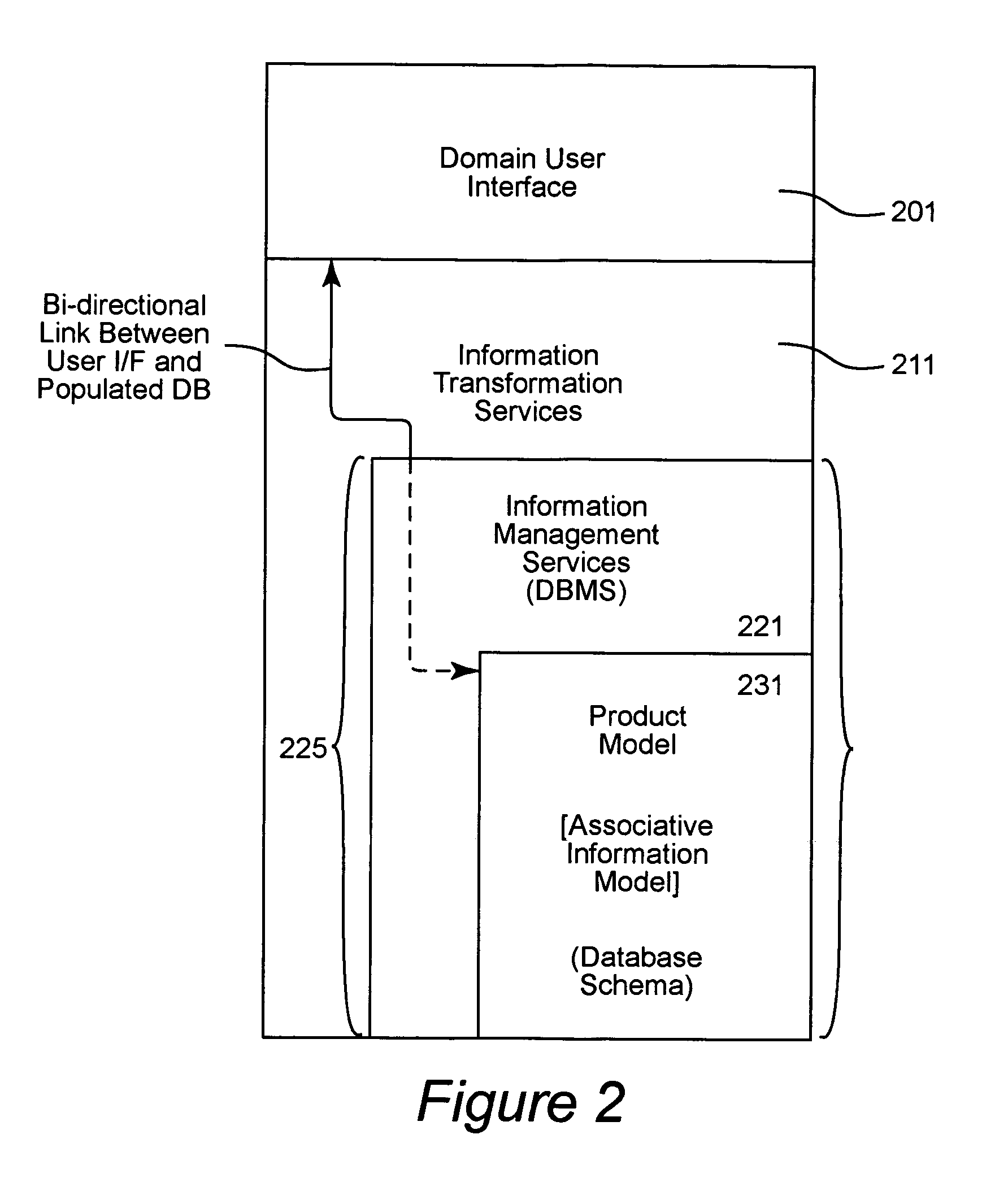
Product catalog for use in a collaborative engineering environment and method for using same
InactiveUS6959268B1Easy to useImprove visibilityMultiple digital computer combinationsOffice automationInformation dispersalSubject-matter expert
A collaborative engineering environment (CEE) enables the effective capture, management, communication, and exploitation of all product related information to a project team. The systematic employment of this information offers substantial improvements in productivity, cost savings, cycle time reductions, product integrity, and lifetime supportability of the system. Advanced CEE capabilities exploit and leverage the engineering, architectural and technological expertise of enterprise subject matter experts (domain experts) across multiple complex systems development and integration activities. The CEE provides a tightly coupled process automation using reusable product elements for coupling information with engineering processes and ensuring adherence to repeatable and traceable engineering processes. A product catalog provides a single information management point for intrinsic complex product characteristics and facilitates the propagation of that information to engineering teams incorporating the complex product into their system designs. The intrinsic complex product characteristics are augmented with implementation specific information to fully describe the complex product in the system design.
Owner:LOCKHEED MARTIN CORP
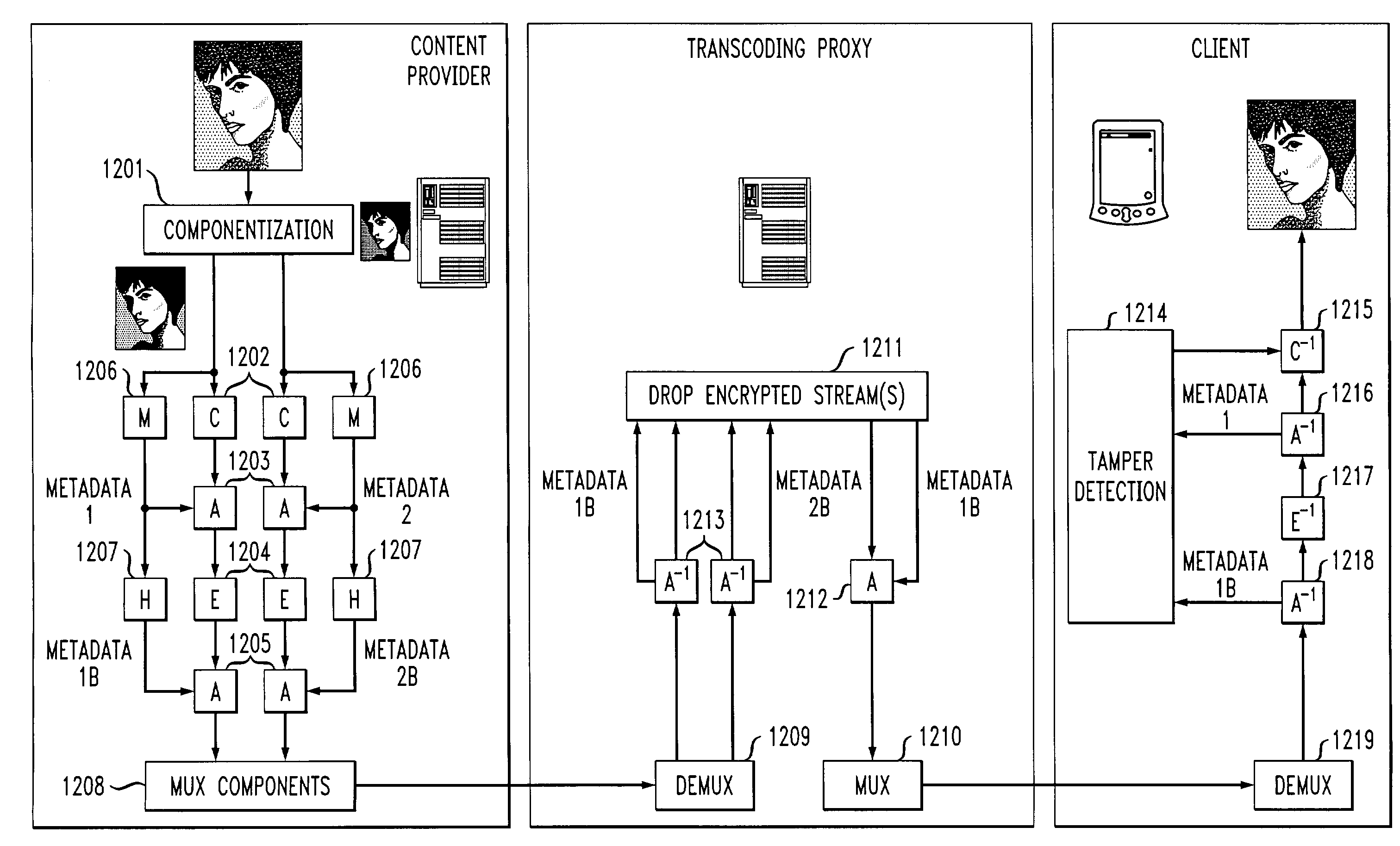
Method and apparatus for networked information dissemination through secure transcoding
ActiveUS6963972B1Improve speedIncrease speedUnauthorized memory use protectionHardware monitoringClient-sideMetadata
A method and system enables network intermediaries such as proxies to transcode multimedia data without violating end-to-end security guarantees. In one embodiment, a content provider decomposes a data stream into a plurality of components, each of which are independently encrypted. In a preferred embodiment, an intermediary or proxy performs transcoding of the components by prioritizing and dropping predetermined components, in accordance with unencrypted clear-text metadata associated with each component, without the need for decrypting the components. Clear-text metadata preferably provides a semantic understanding of the absolute or relative importance / priority of the components with respect to each other, thereby facilitating the transcoding process. The destination / client device can subsequently decrypt the components transmitted by the transcoding proxy and reassemble them into a representation of the original data content.
Owner:AWEMANE LTD
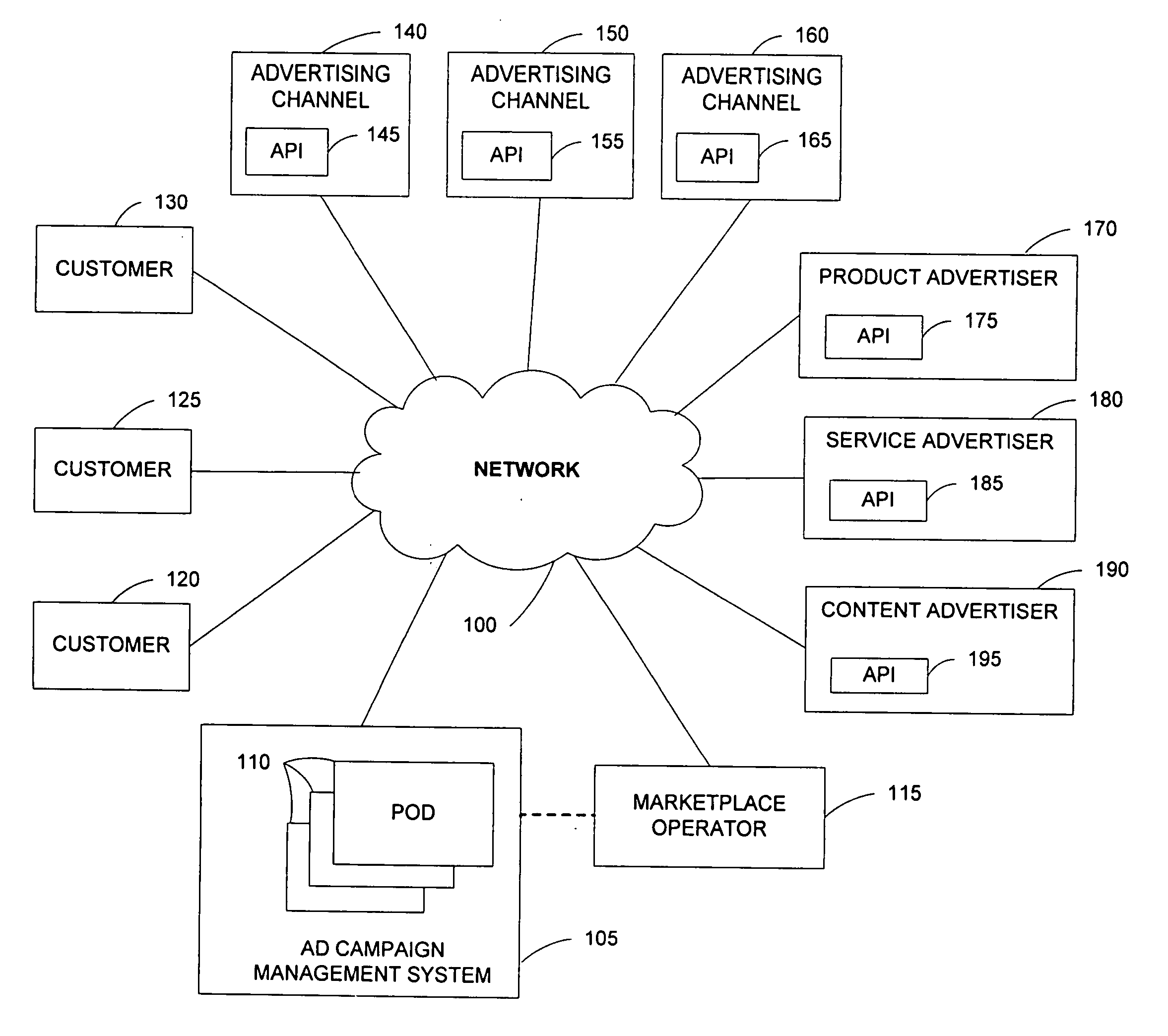
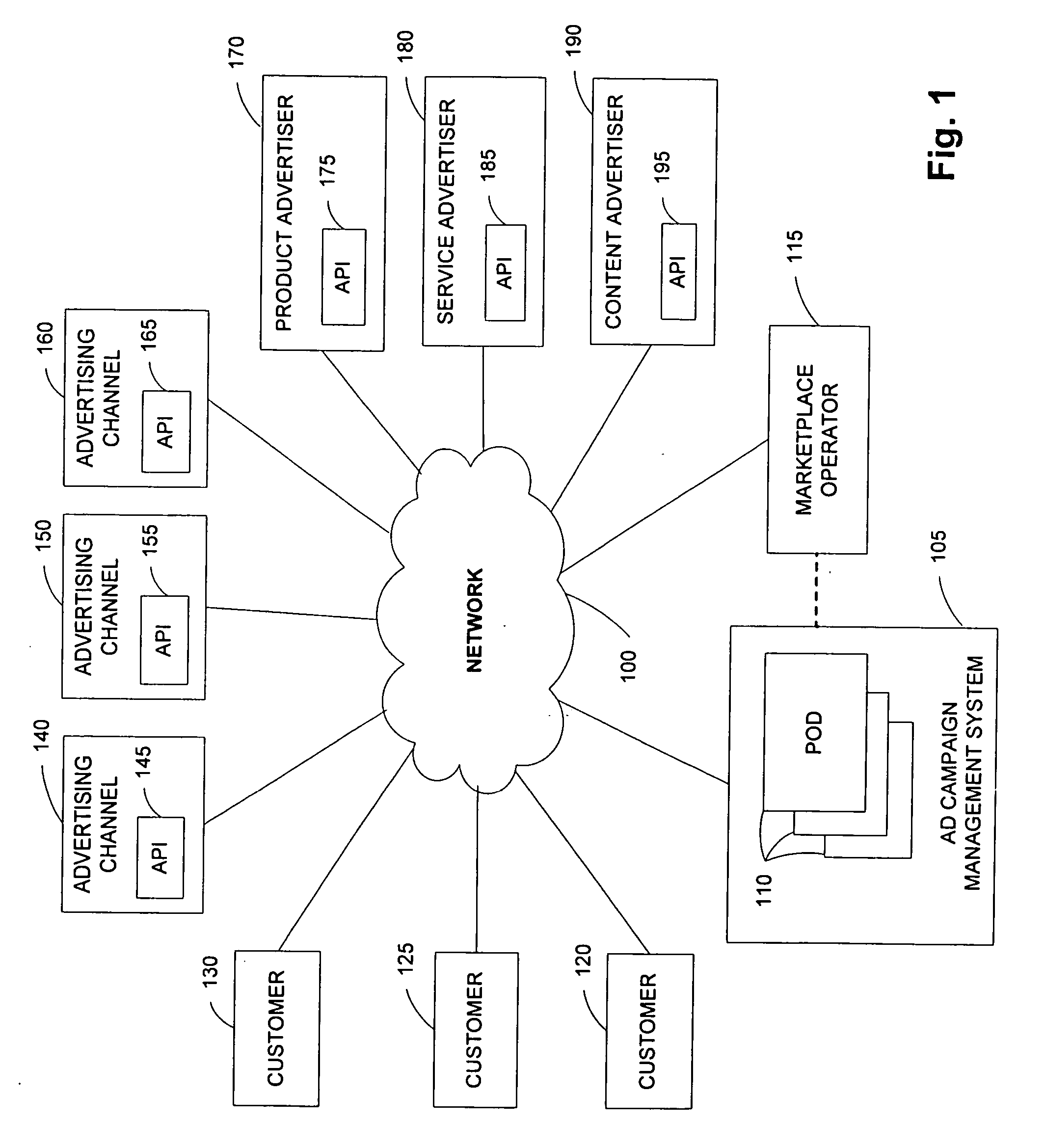
Architecture for distribution of advertising content and change propagation
A system comprises an interface for enabling a user having a web property to input advertisement information including a web property advertisement, criteria indicating when presentation of the advertisement is desired by the user, a bid for the presentation of the advertisement when the criteria are met, and subsequent modifications to the advertisement information; geographically distributed servers, a plurality of the geographically distributed servers for storing the advertisement information, at least one of the geographically distributed servers for receiving a request for advertisement content from an advertising channel, at least one of the geographically distributed servers for determining whether the request meets the criteria, and at least one of the geographically distributed servers for forwarding the advertisement to the advertising channel in response to the request when the criteria have been met; and a distribution component for propagating the advertisement information to the geographically distributed servers according to an arrangement.
Owner:R2 SOLUTIONS
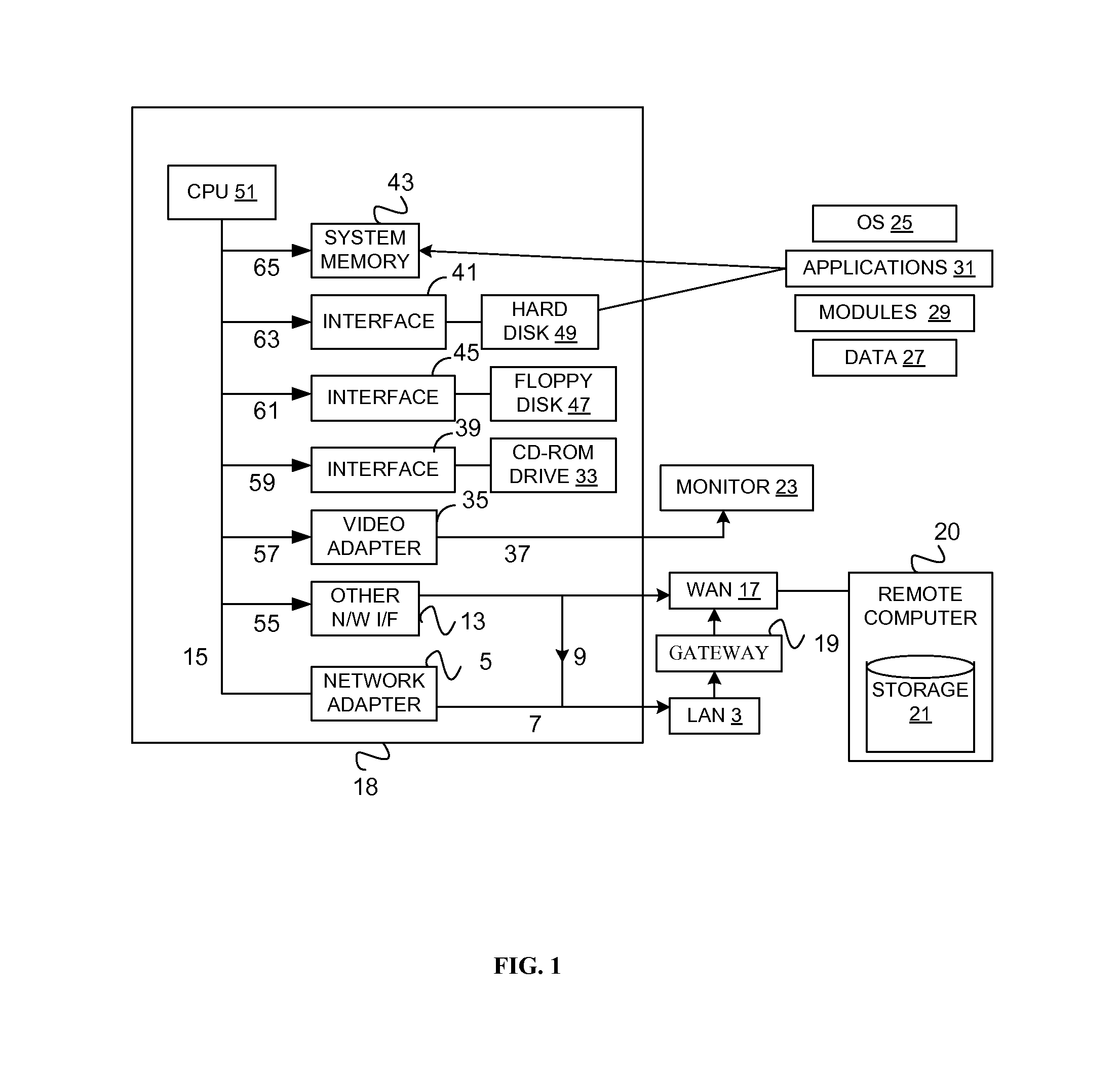
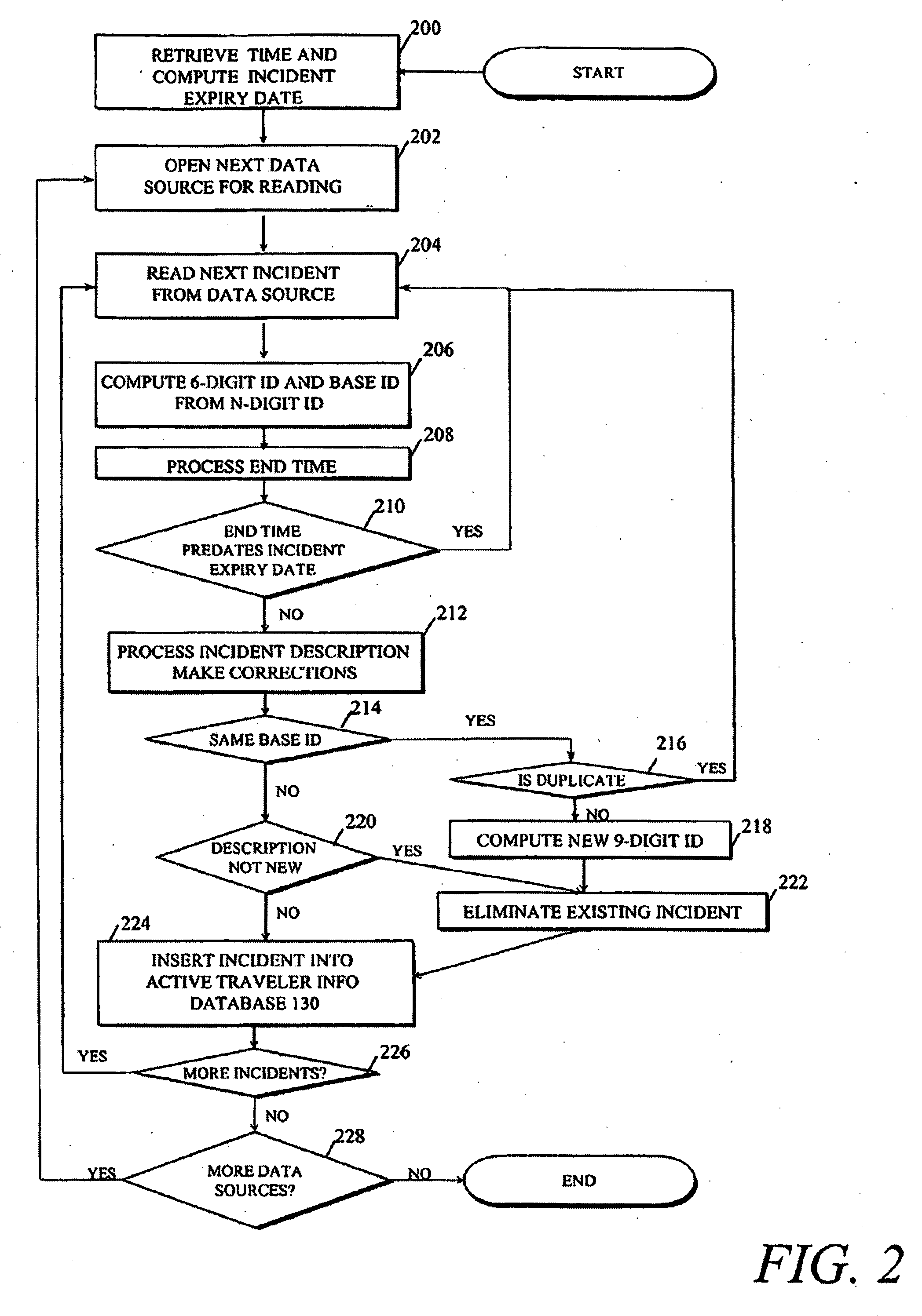
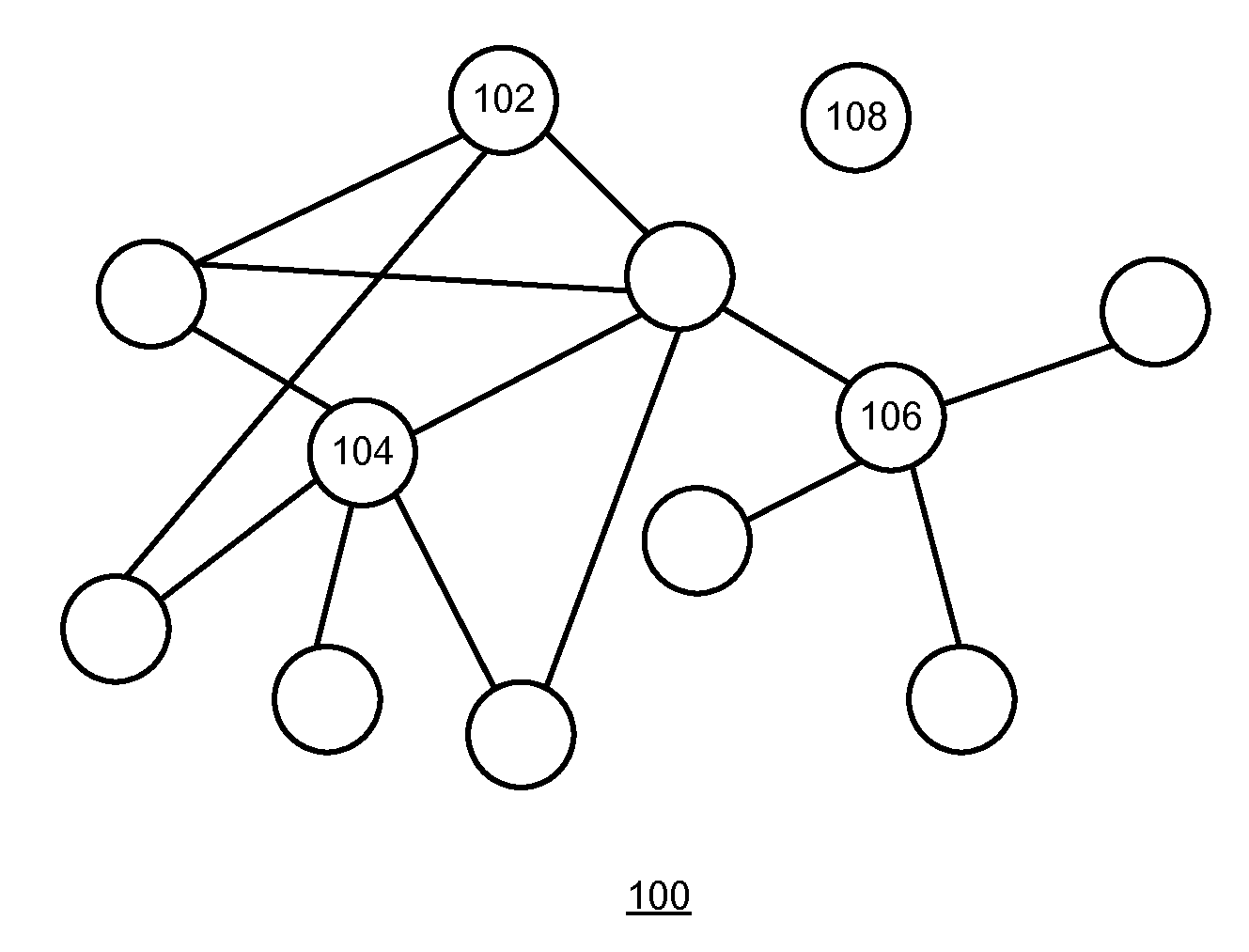
System for rebuilding dispersed data
ActiveUS7546427B2Improve privacyImprove securityError detection/correctionMemory adressing/allocation/relocationDigital dataInformation dispersal
Owner:PURE STORAGE
Electricity energy monitor
InactiveUS20090079416A1Current/voltage measurementSpecial tariff metersInformation dispersalElectrical conductor
An electric energy monitor or meter for efficient measuring and recording electrical energy usage data relating to a particular appliance or circuit. One embodiment comprises a thin-profile monitoring device through which an electrical conductor, for example the normal line cord plug of an appliance or the output wire from a circuit breaker to the load, is inserted. A display may be provided to show the accumulated energy usage. In other embodiments a device of the invention can be installed in a light switch, appliance, plug, or receptacle. Data can also be transmitted by various means to a computing device such as a personal computer or the like. The device of the invention allows for interaction with Internet-based information dissemination or gathering, meter distribution by means of incentive or promotional give-away, and control of energy usage through connection to an energy management system.
Owner:VINDEN JONATHAN PHILIP +1
System and method enabling multiple processes to efficiently log events
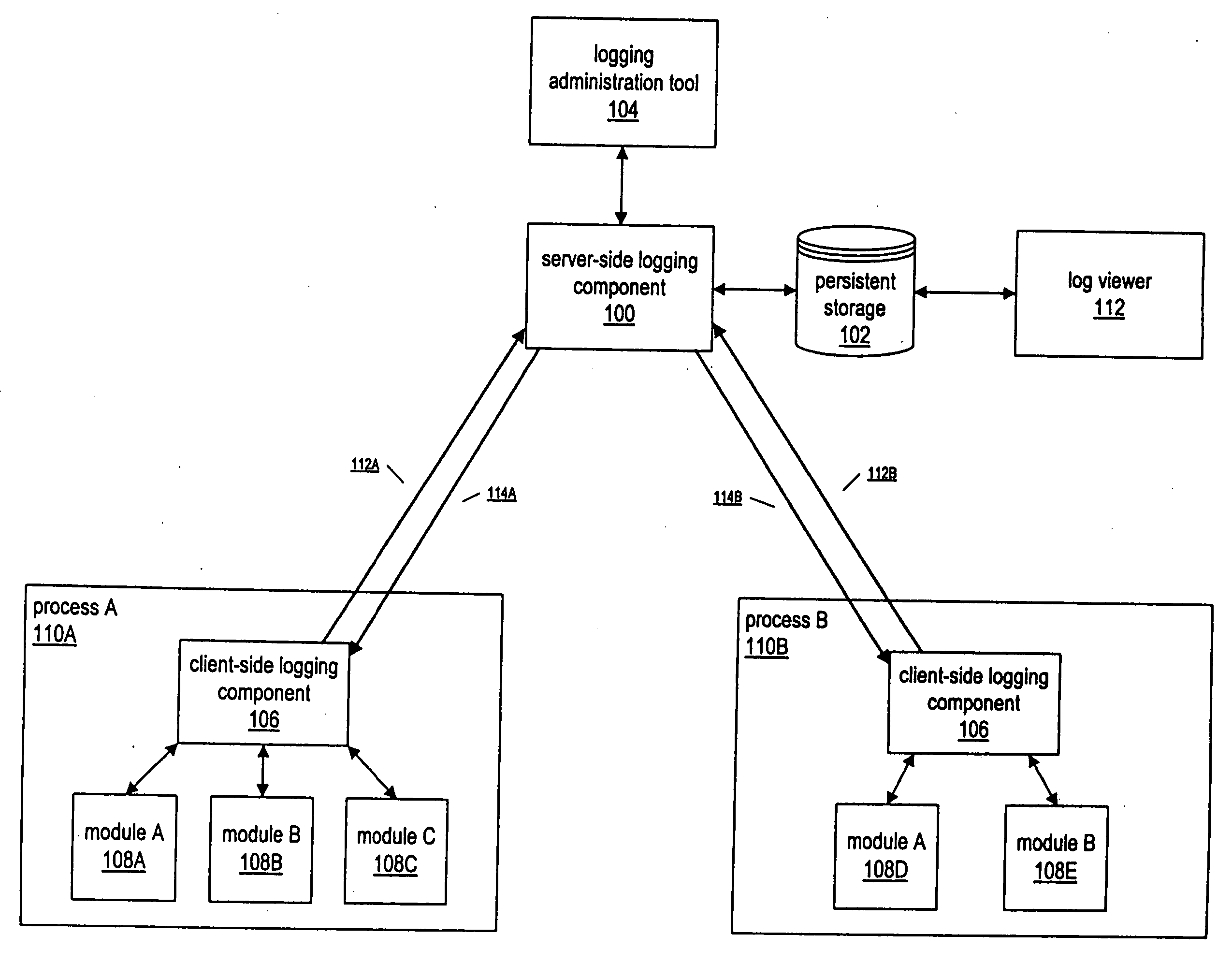
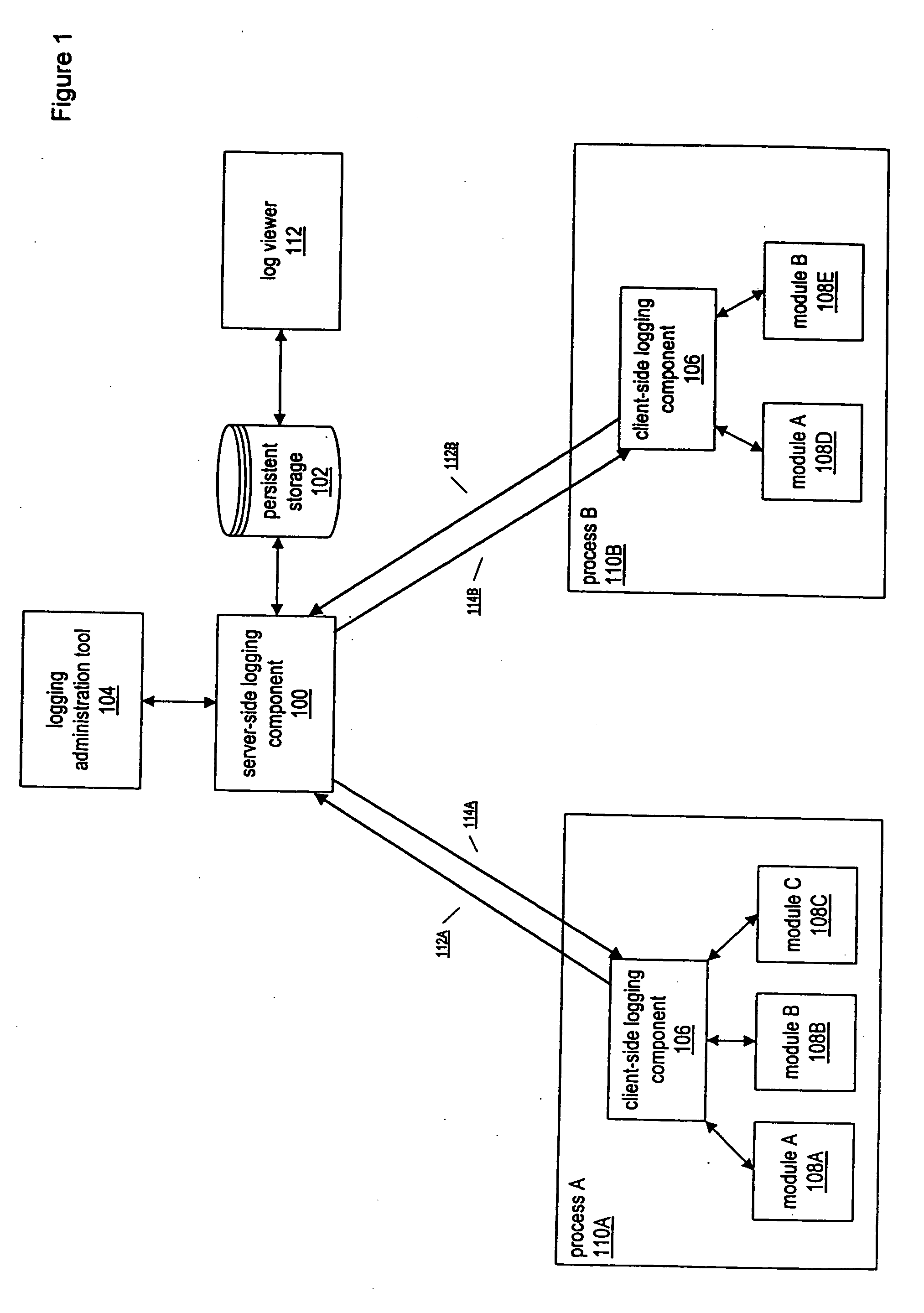
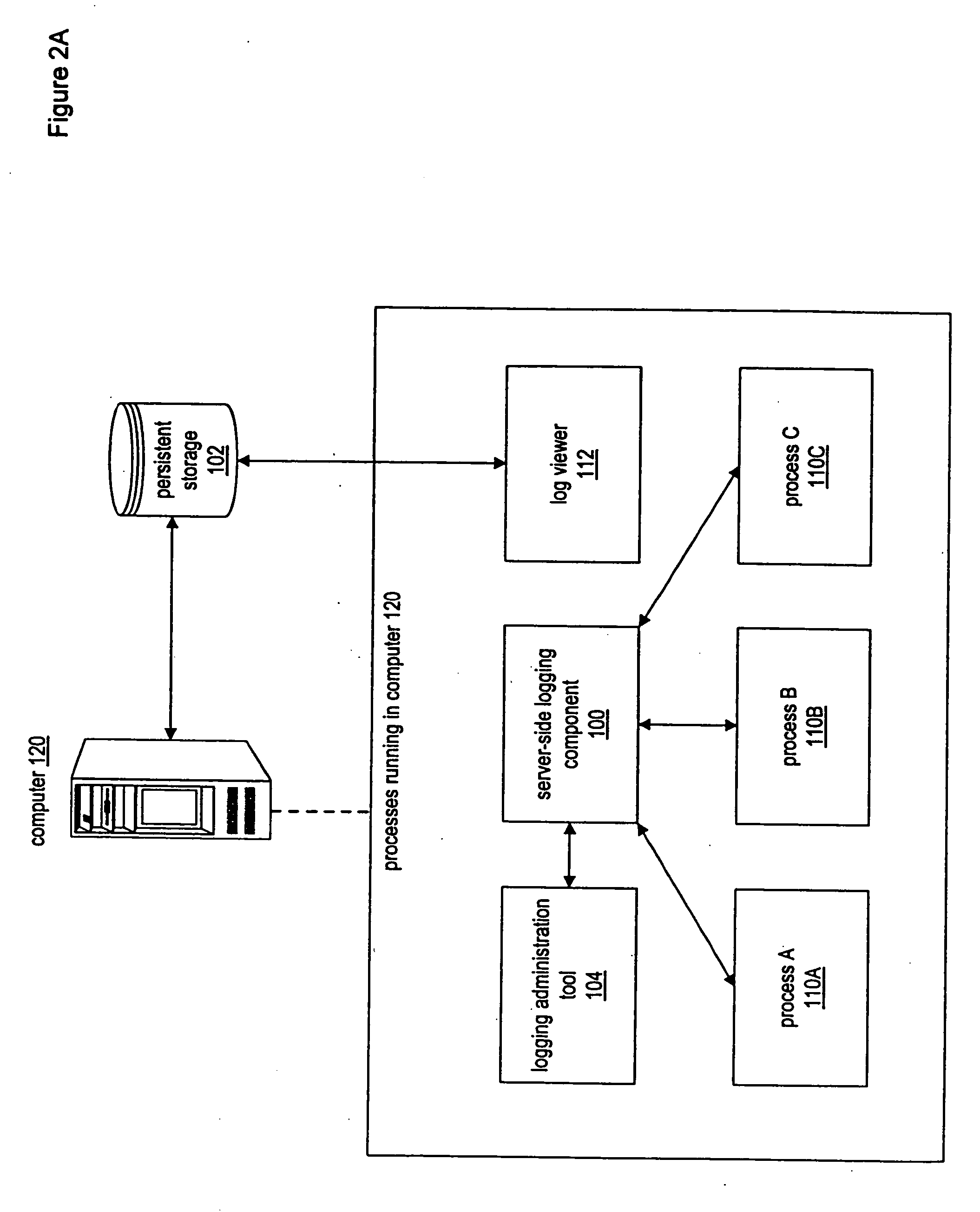
InactiveUS20050028171A1Efficiently log eventError detection/correctionProgram controlInformation dispersalEvent level
A system and method for enabling multiple processes to efficiently log events is described. A client executable module that needs to log an event may interface with a module or component referred to as a “client-side logging component”, passing various types of information regarding the event, such as an associated event level, one or more event associated event categories, an informational message, etc. The client-side logging component may maintain event logging criteria specifying which types of events should be logged. If the event should be logged, the client-side logging component may queue the event information and return execution control the client module. The event information may then be asynchronously retrieved from the event queue and sent to a server-side logging component. The server-side logging component may persistently log the event information in any of various ways, e.g., by storing it in a file, a database, etc. Processes running on multiple computers may call the server-side logging component to log events, via a client-side logging component instance associated with the process. A logging administration tool may be utilized in order to set event logging criteria. In response to being configured with new event logging criteria information, the server-side logging component may automatically propagate the logging criteria information to each of the client-side logging components. The client-side logging components may then being using the new logging criteria, dynamically changing the filtering of events that are sent to the server-side logging component.
Owner:KOUGIOURIS PANAGIOTIS +1
Data management system and method for automatically propagating information to disparate information systems from a central location
InactiveUS6873997B1Data processing applicationsDatabase management systemsInformation dispersalInformation Dissemination
A data management system for automatically propagating changes in information related to a product being designed or manufactured from a central location to remote and disparate user information systems includes a central data base for storing and maintaining data, an administration module communicating with the central database and having software code that can configure the administration module to validate data related to a product; a product change module communicating with the central data base and having software code that can configure the product change module to poll the central data base to determine whether a change has been made to data related to a product; and a data server having code that extracts, formats and transmits changes in data stored in the central data base to a user system, the data being transferred according to predetermined data requirements of the disparate information system.
Owner:AGILE SOFTWARE CORPORATION
Personalized traveler information dissemination system
InactiveUS20060145892A1Improve accuracyMatching of incidents becomes increasingly flexibleControlling traffic signalsAnalogue computers for vehiclesPersonalizationTime information
Owner:UBER TECH INC
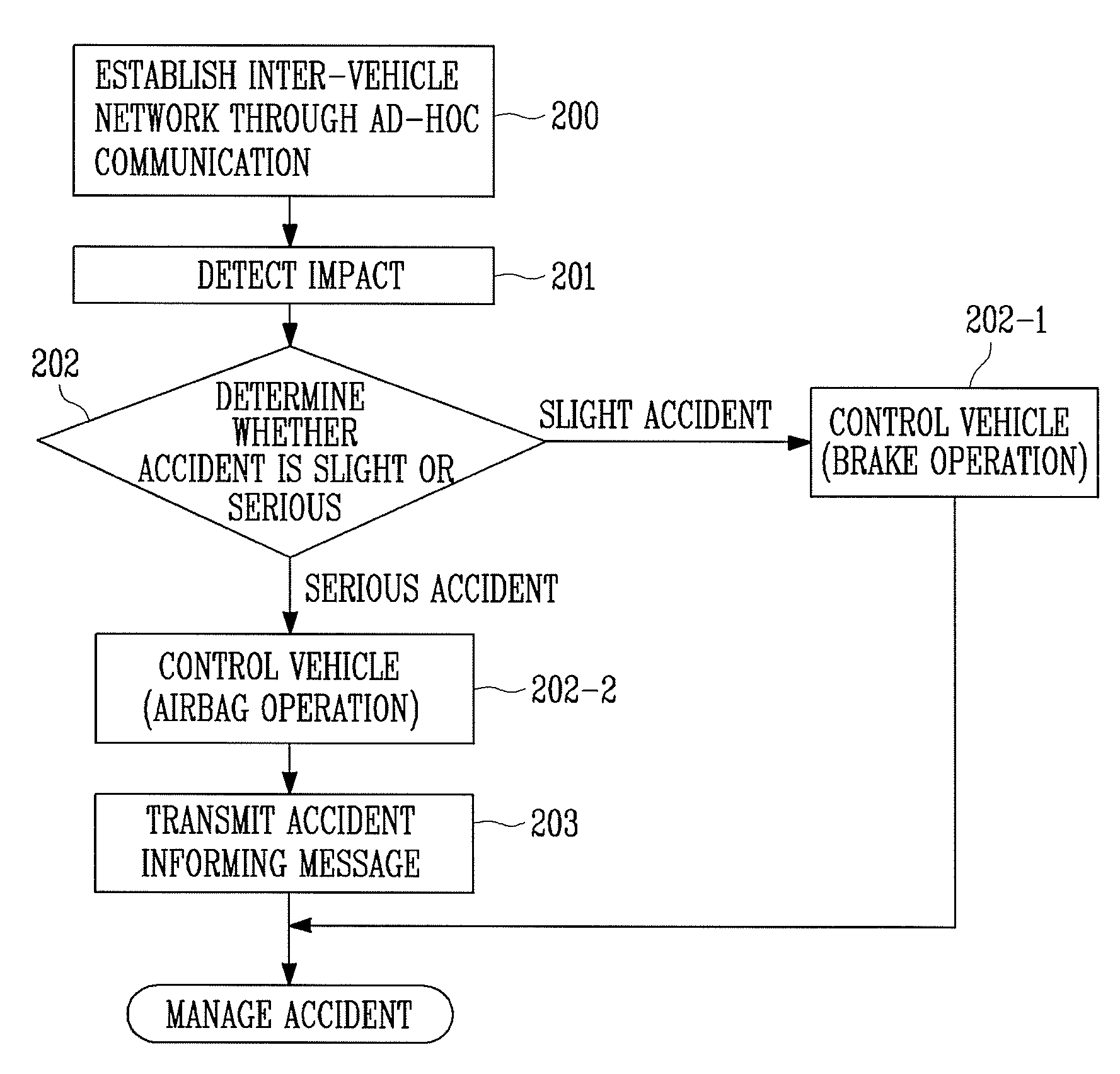
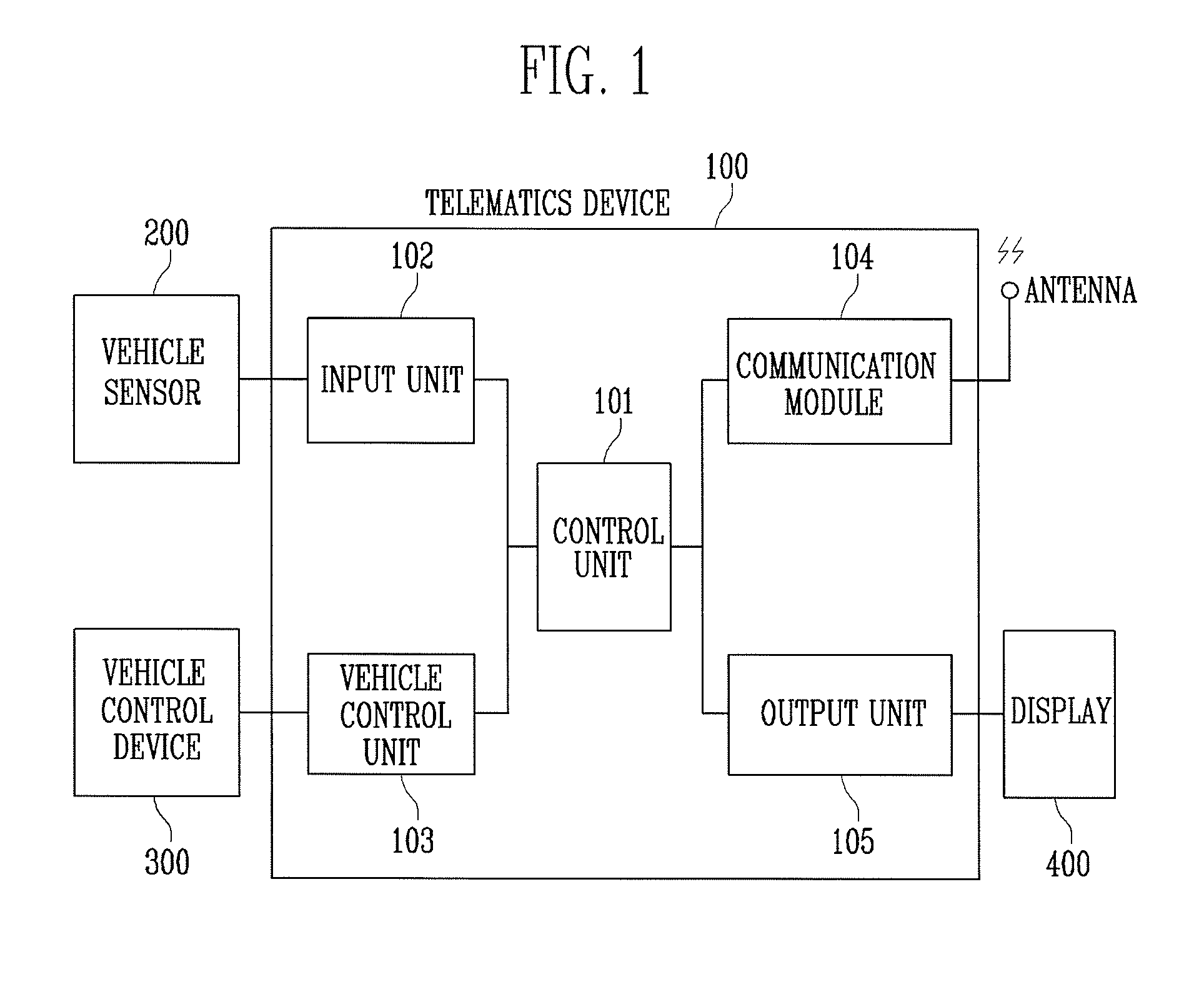
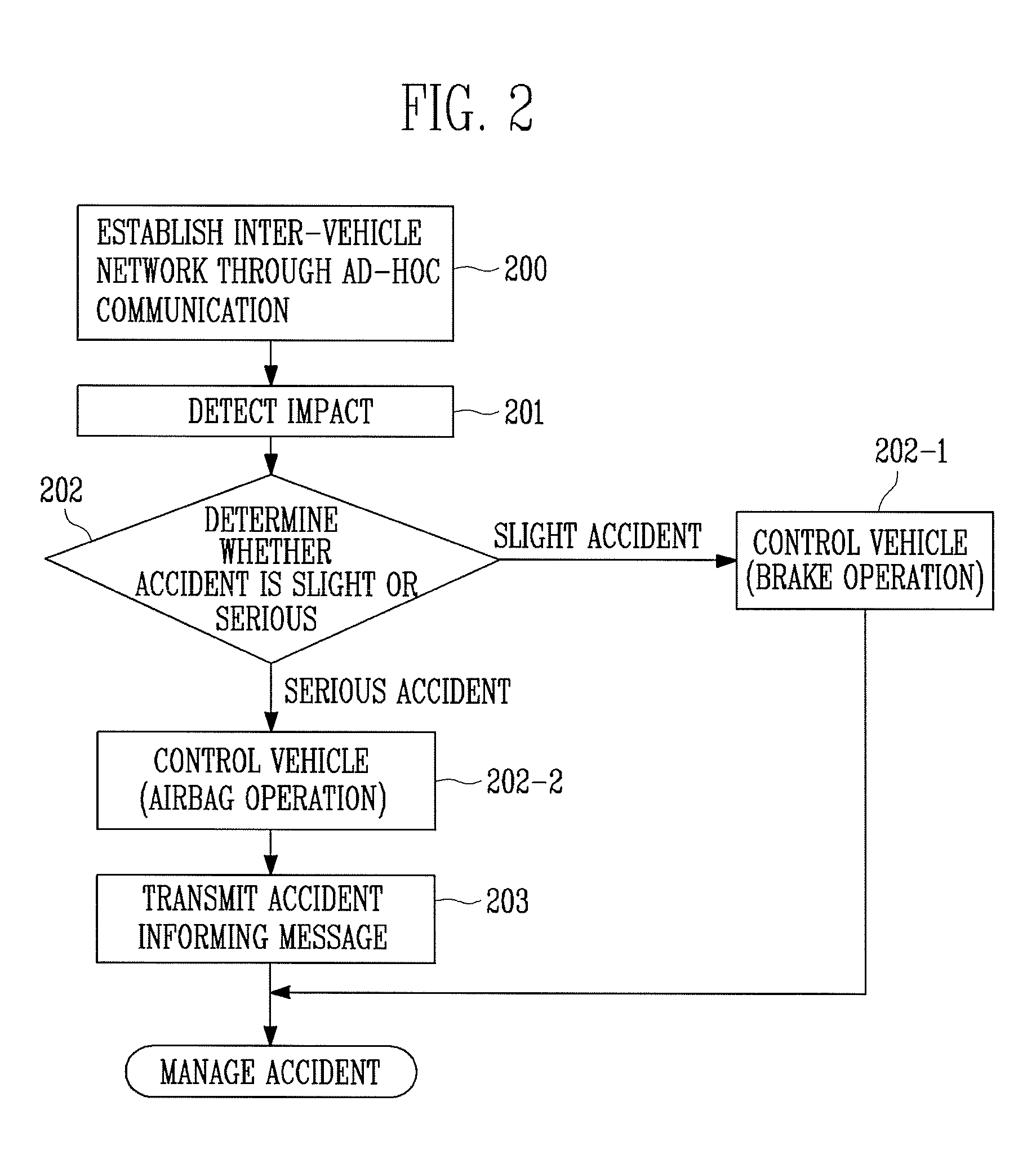
System and method for informing vehicle accident using telematics device
InactiveUS20080140287A1Analogue computers for vehiclesInstruments for road network navigationInformation dispersalTraffic congestion
Provided are a system and method for informing a vehicle accident using a telematics device. In an emergency, such as vehicle collision, etc., the system and method propagate information on the accident to vehicles around the accident scene, thereby informing the vehicles of traffic congestion. Since the vehicles continuously inform the same to vehicles behind through ad-hoc communication, a vehicle guided by a telematics device can recognize the traffic congestion ahead, re-search for a path, and thereby make a detour. Therefore, although vehicles behind the accident scene cannot see the occurrence of the accident on a foggy highway, etc., the risk of a chain-reaction crash is reduced. In addition, it is possible to avoid traffic congestion due to an accident in downtown.
Owner:ELECTRONICS & TELECOMM RES INST
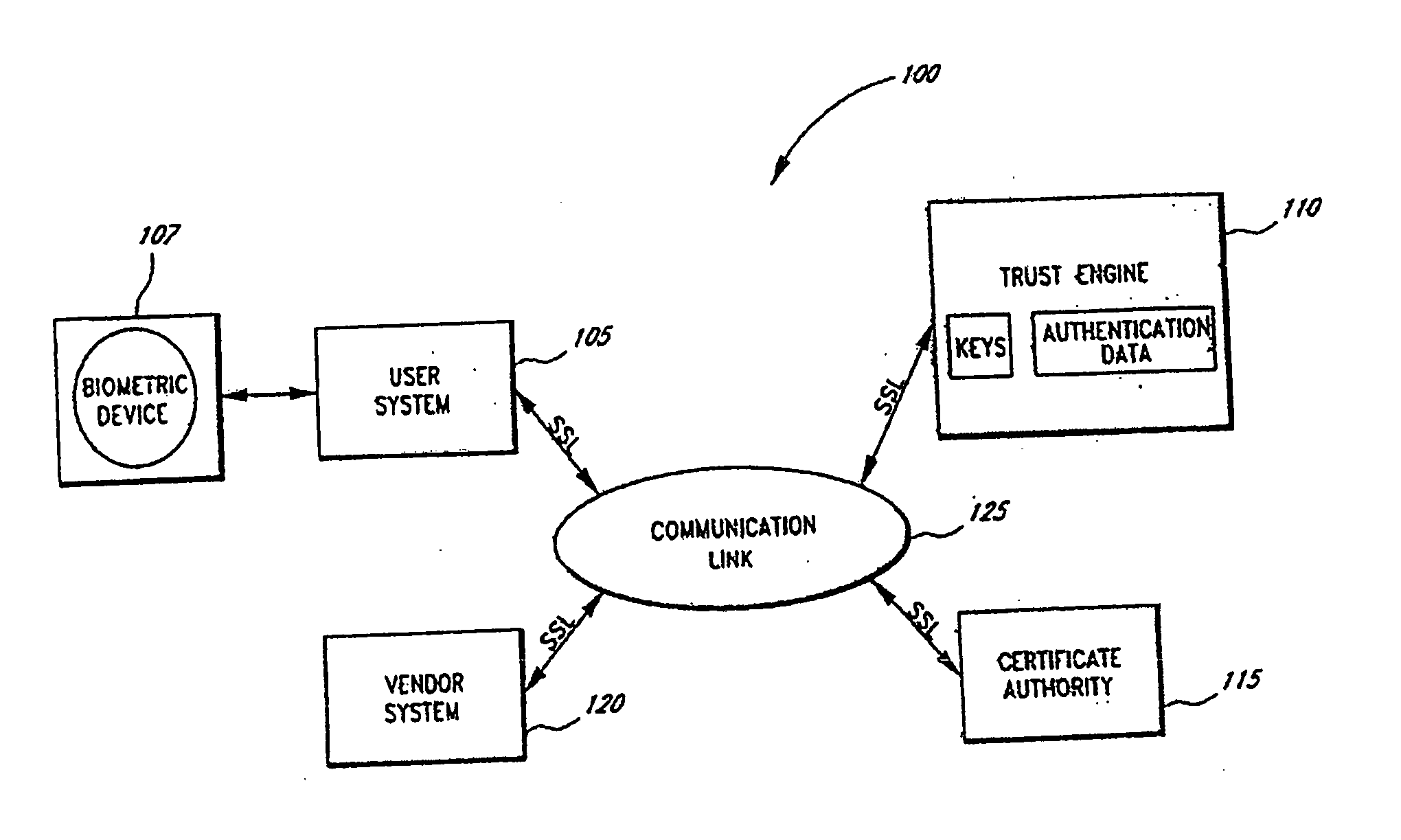
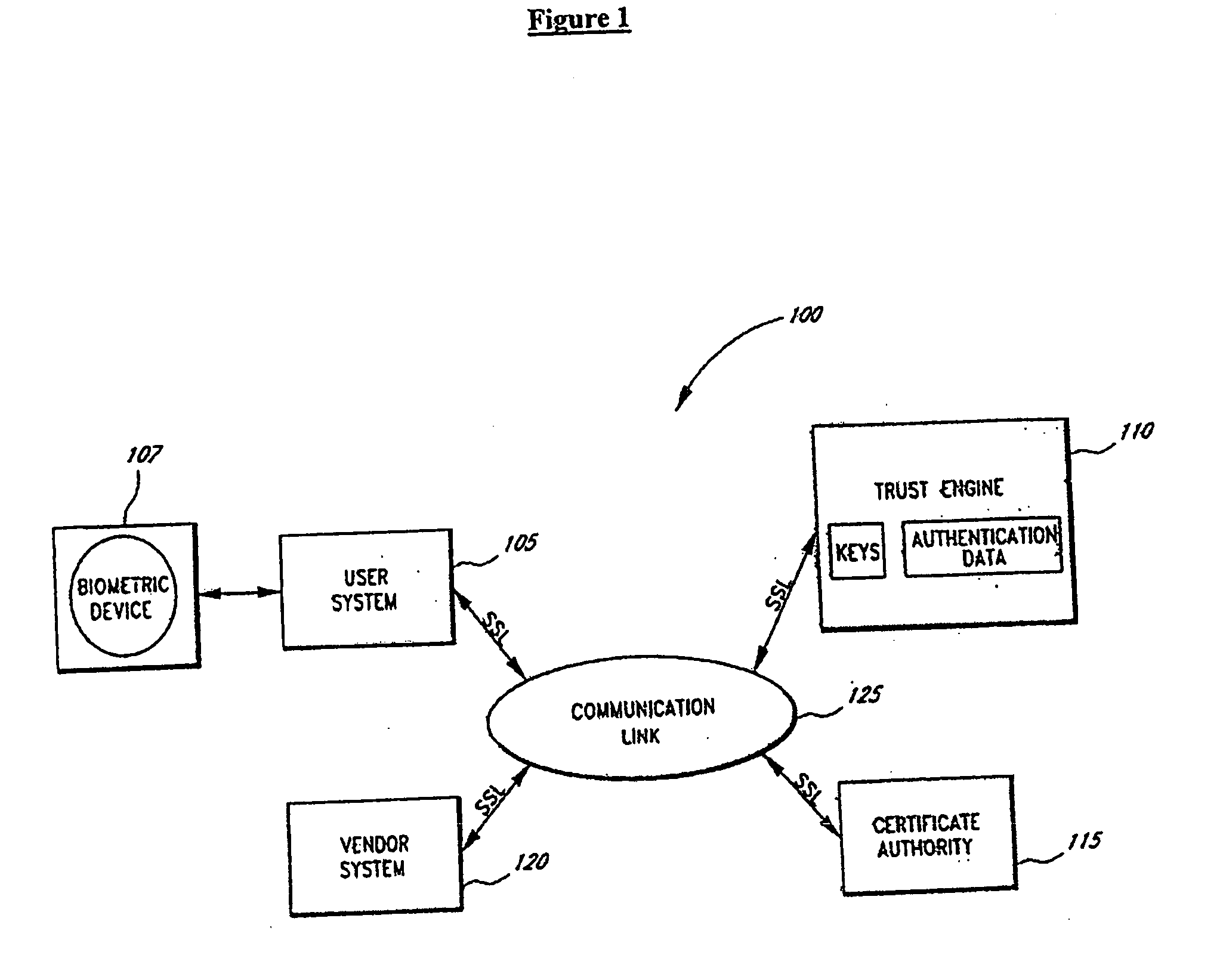
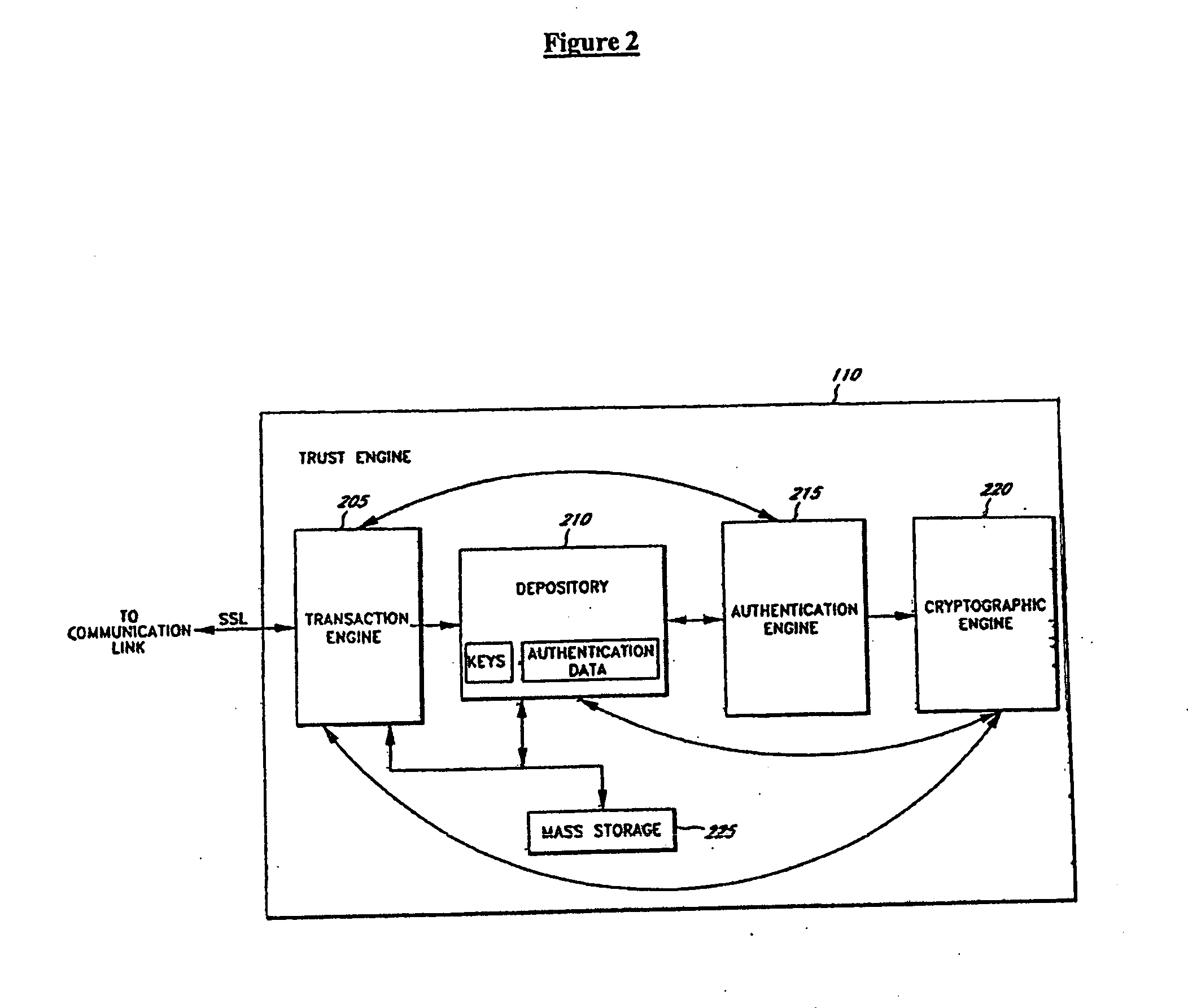
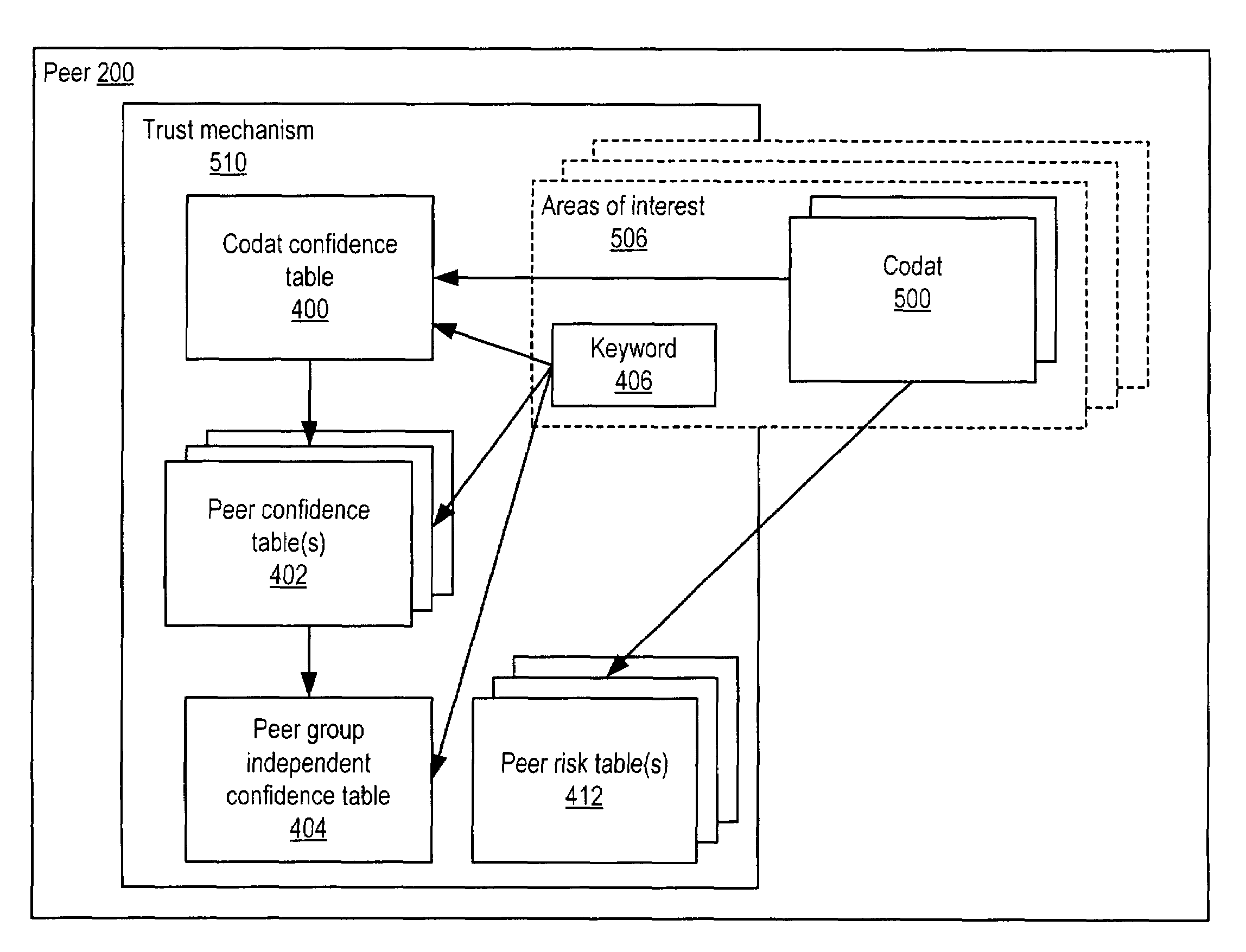
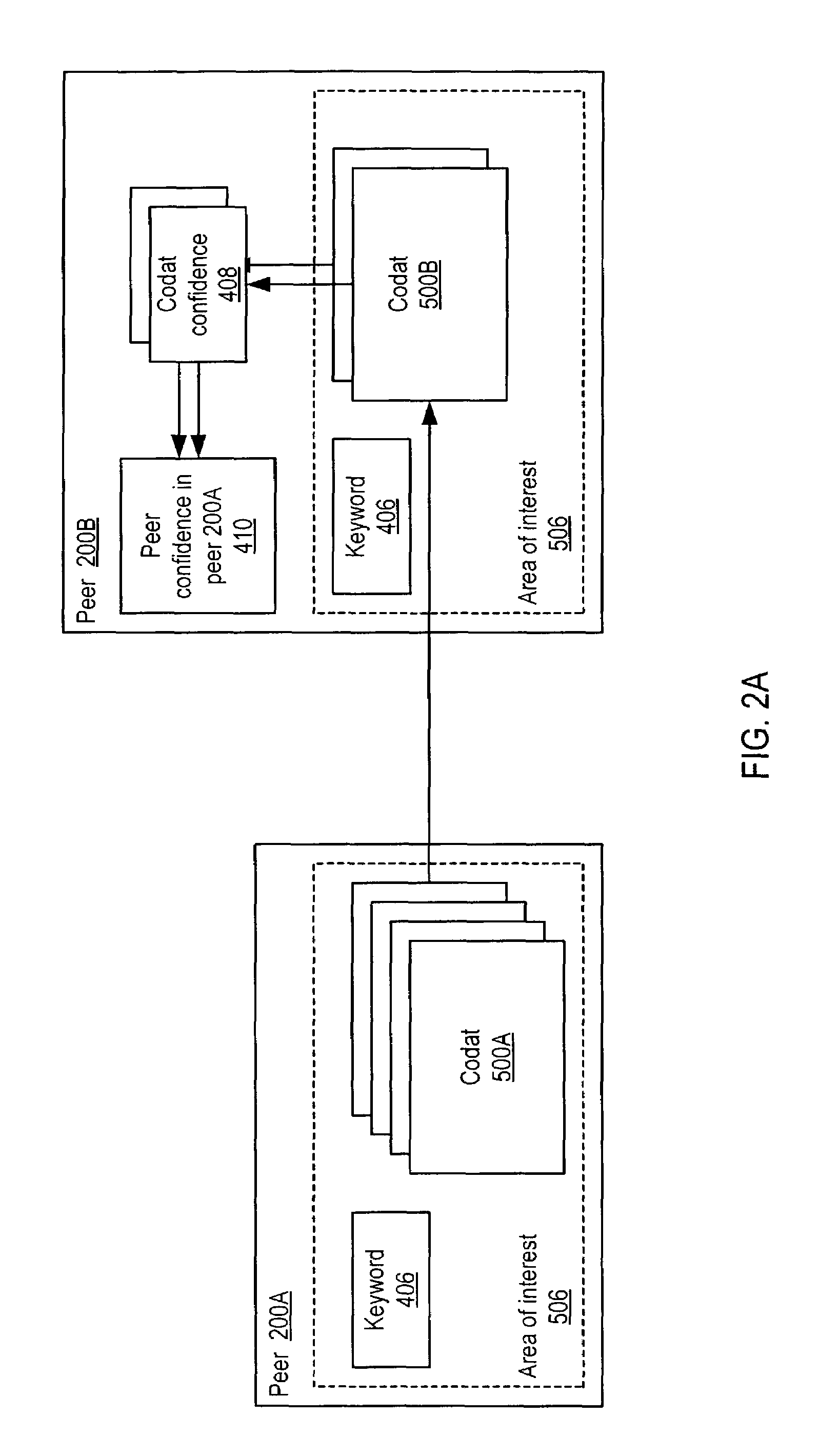
Representing trust in distributed peer-to-peer networks
ActiveUS7308496B2Multiprogramming arrangementsMultiple digital computer combinationsInformation dispersalInternet privacy
Embodiments may provide mechanisms for representing trust between peers or systems in decentralized networking environments including peer-to-peer networking environments. Trust may include both direct trust between two peers and trust in a pipeline of peers along which codat may be passed. Embodiments may provide a mechanism for a peer to represent and rate the trustworthiness of other peers as providers of codat relevant to the peer's interest. To evaluate trust in another peer as a provider of codats in the area of interest, trust may be represented with two components, confidence and risk. Embodiments may provide mechanisms for measuring the components and determining trust from the components. Embodiments may also provide mechanisms for feeding back trust information to the providing peer and for propagating trust information to other peers.
Owner:ORACLE INT CORP
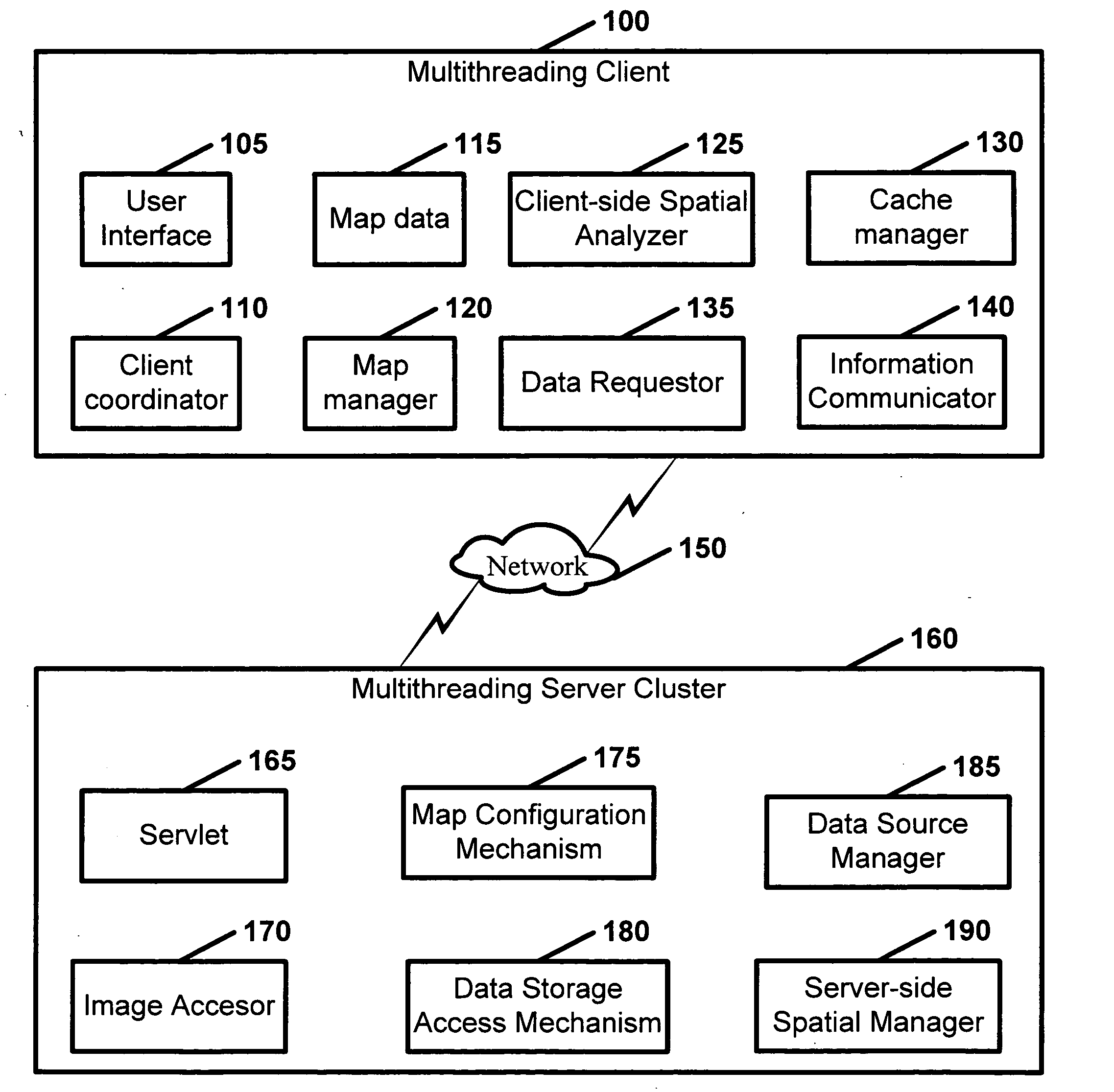
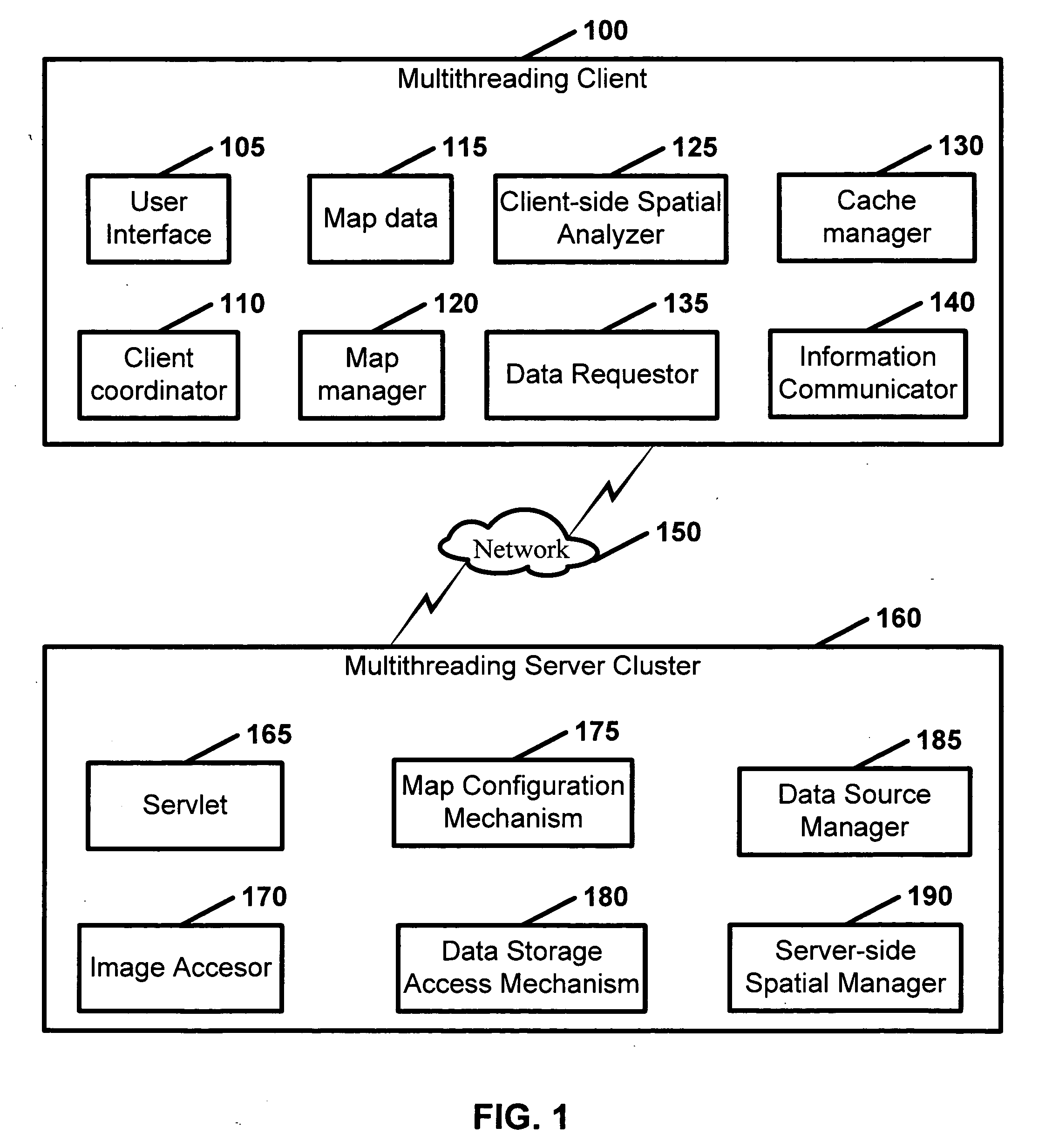
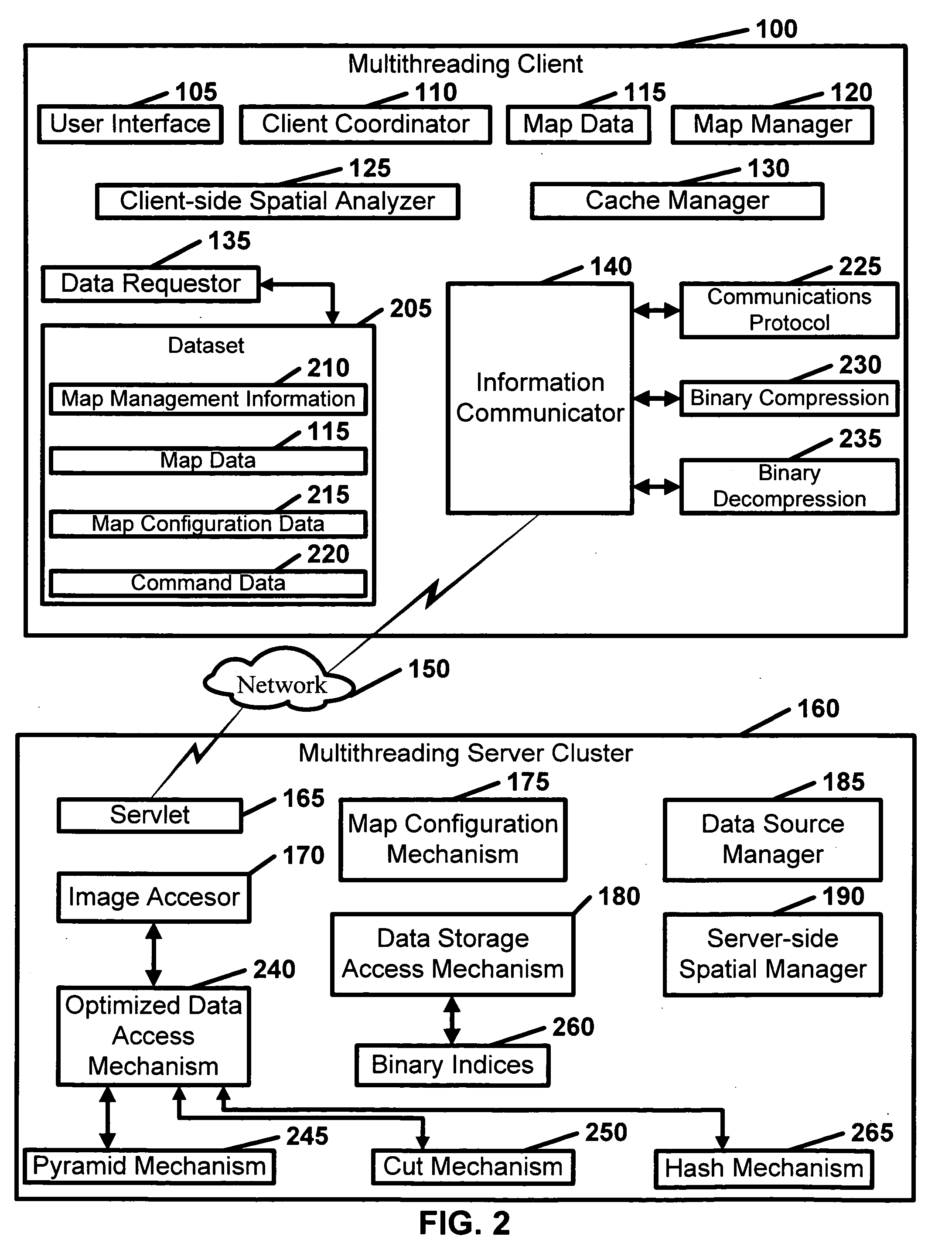
Geographic information system
InactiveUS20050165788A1Multiple digital computer combinationsGeographical information databasesInformation dispersalData source
Disclosed is a geographic information system which comprises a multithreading client and a multithreading server cluster. The multithreading client includes at least one user interface, at least one client coordinator, map data, at least one map manager, at least one client-side spatial analyzer, at least one cache manager, at least one data requester, and at least one information communicator. The multithreading server cluster includes: at least one servlet, at least one image accessor, at least one map configuration mechanism; at least one data storage access mechanism, at least one data source manager, and at least one server-side spatial manager.
Owner:GEORGE MASON INTPROP INC
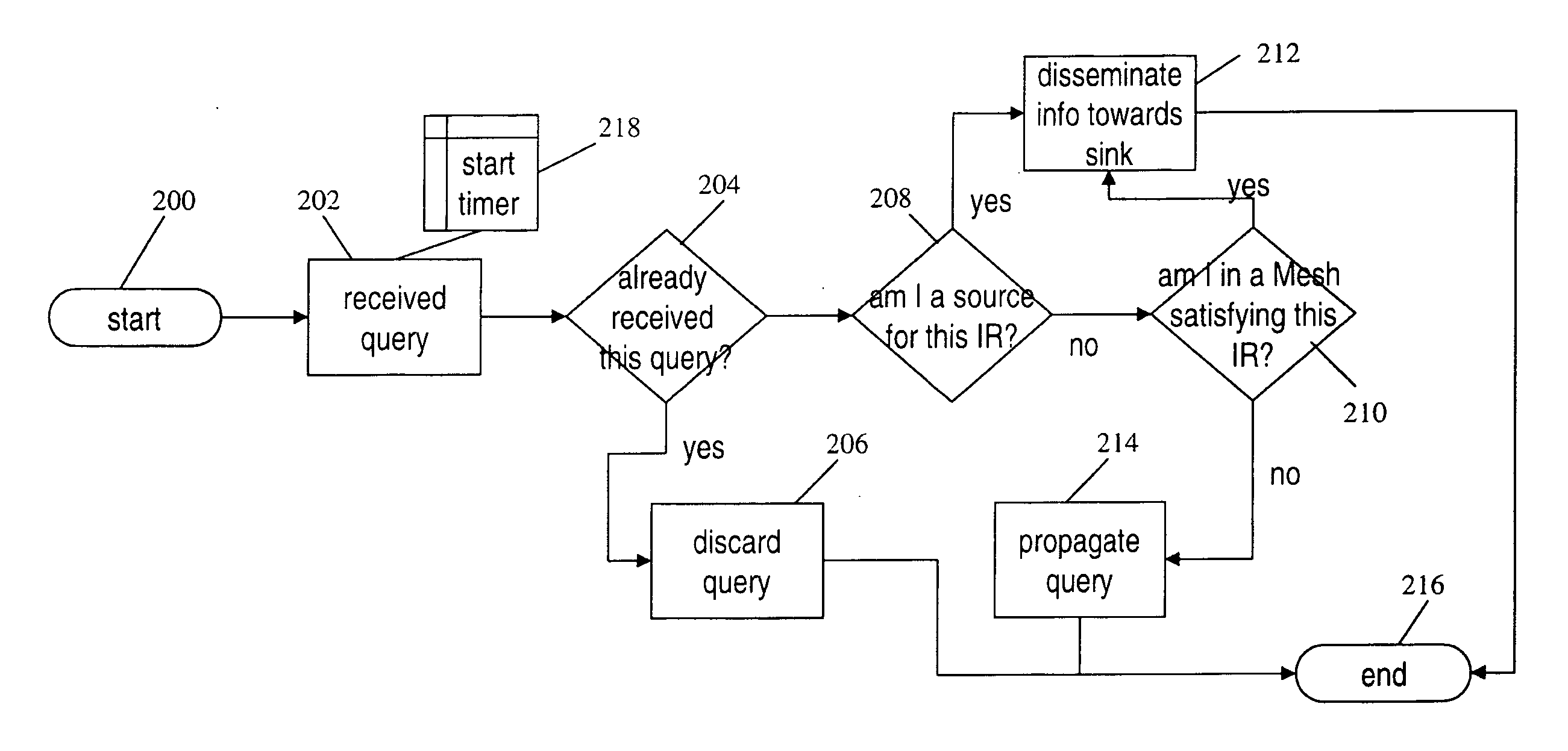
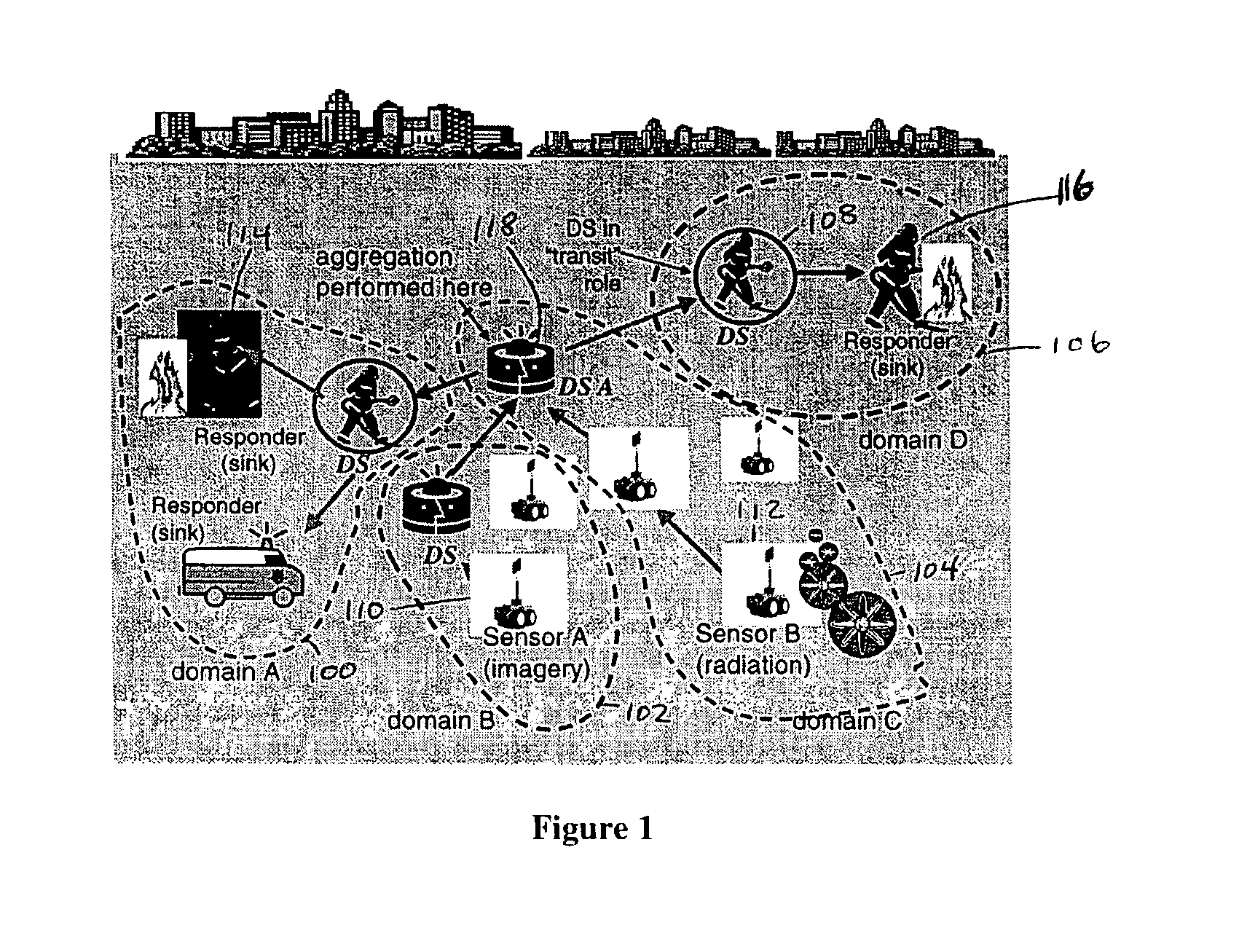
Architecture for information dissemination in wireless mobile ad hoc networks
In future large-scale Emergency Response / Management (ER / EM) to terrorism and natural disasters, sharing the so-called common operational picture amongst dynamic task groups provides immediate advantages. In an ER / EM scenario, dissemination of the right data to the right person at the right time has a direct benefit. Timely and bandwidth efficient dissemination of sensor and Command and Control data remains a challenge. For example, dynamically changing mobile teams, information-needs profiling, information routing based upon information needs (not on IP address) are all complex issues. Accordingly, a protocol, called dissemination mesh, for constructing and reconfiguring network paths for disseminating information from sources to sinks, a software architecture for multi-domain wireless network information dissemination in the context of emergency response (resting above existing MANET protocols), supports needs-based dissemination, node mobility, rapidly changing groups (information sinks) and sensor networks (sources) is provided. The protocol includes: exploitation of Semantic Web and collaborative agent technologies, novel subscription-based information dissemination, intelligent networked information intermediaries, smart dissemination mesh forming and management. Together these technologies provide information dissemination management in the wireless setting. Application realms other than ER / EM can also be supported.
Owner:TELCORDIA TECHNOLOGIES INC
Systems and methods for distributing and securing data
ActiveUS8155322B2Key distribution for secure communicationRandom number generatorsInformation dispersalCiphertext
A robust computational secret sharing scheme that provides for the efficient distribution and subsequent recovery of a private data is disclosed. A cryptographic key may be randomly generated and then shared using a secret sharing algorithm to generate a collection of key shares. The private data may be encrypted using the key, resulting in a ciphertext. The ciphertext may then be broken into ciphertext fragments using an Information Dispersal Algorithm. Each key share and a corresponding ciphertext fragment are provided as input to a committal method of a probabilistic commitment scheme, resulting in a committal value and a decommittal value. The share for the robust computational secret sharing scheme may be obtained by combining the key share, the ciphertext fragment, the decommittal value, and the vector of committal values.
Owner:SECURITY FIRST INNOVATIONS LLC
Disseminating control information to a wireless communications device
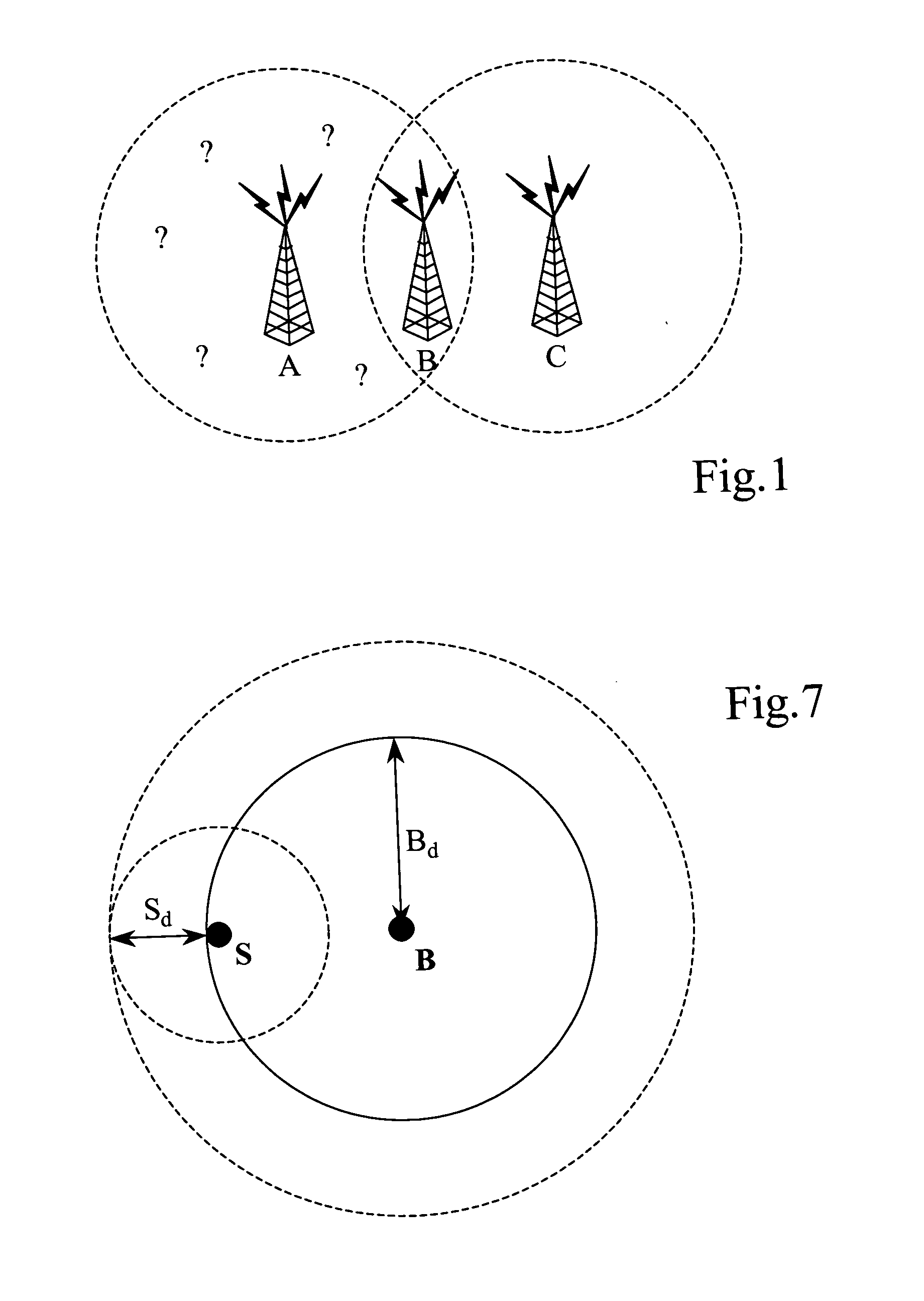
InactiveUS20050197118A1Easy to useAssess restrictionSpecial service for subscribersInformation dispersalFrequency spectrum
Information for coordinating use of wireless spectrum resources is disseminated from a frequency server in accordance with the geographic location of wireless devices intending to use the spectrum. The information may be disseminated via a beacon station that communicates with the frequency server to obtain spectrum usage information for the location of the beacon and broadcasts it to wireless devices in the vicinity of the beacon.
Owner:AGILENT TECH INC
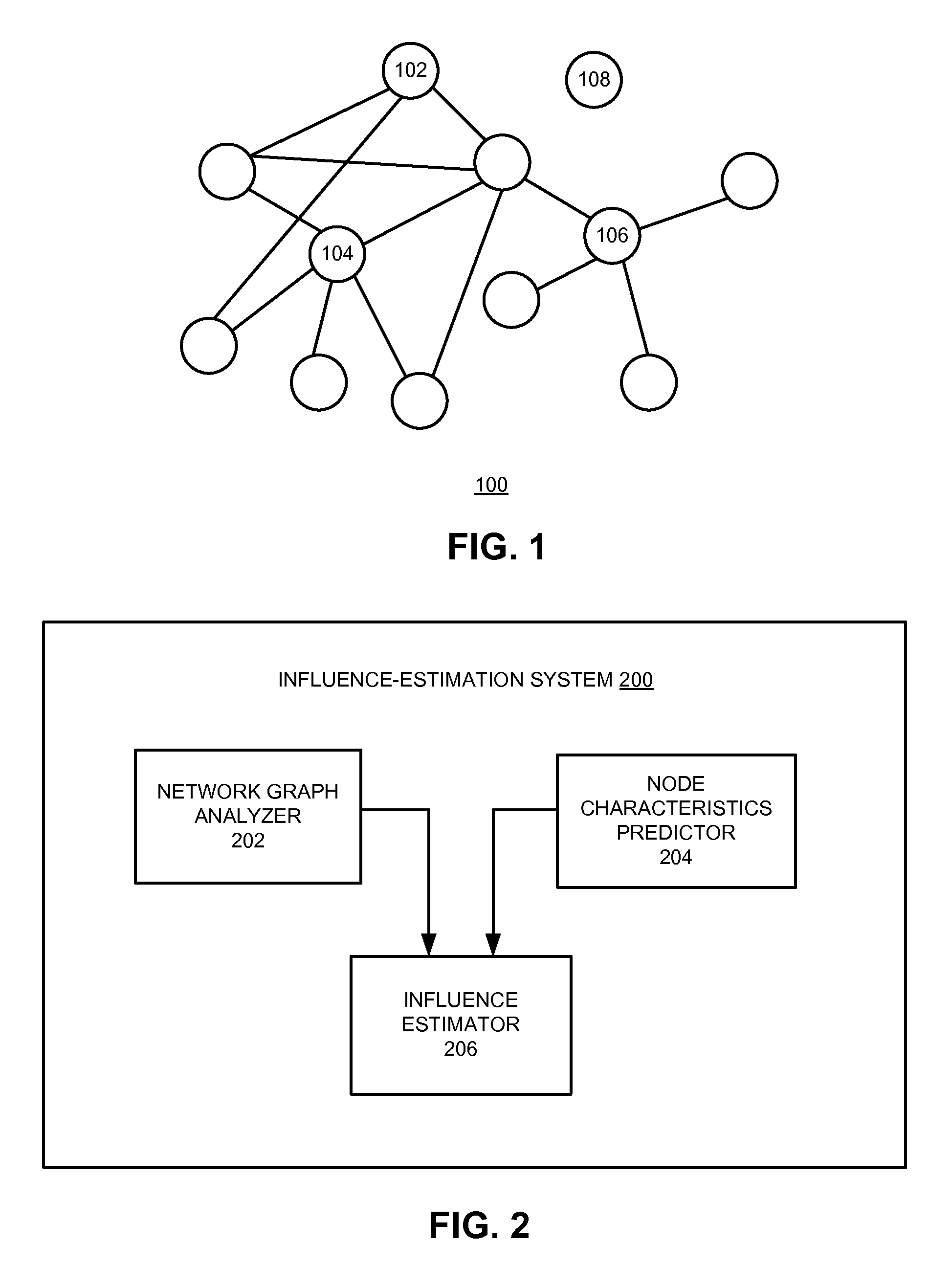
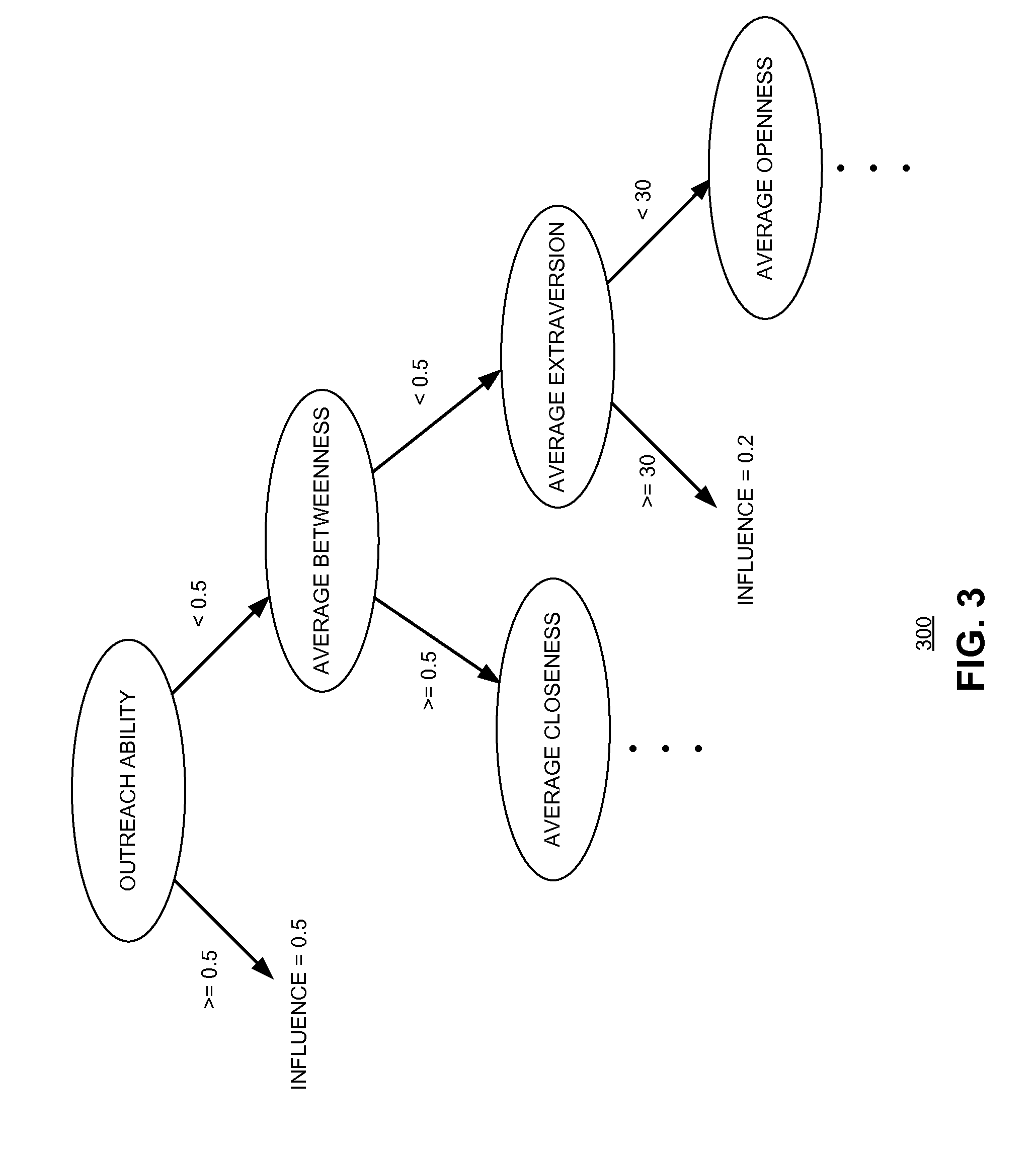
System and method for identifying key targets in a social network by heuristically approximating influence
ActiveUS20150170295A1Maximize information spreadingMaximizes information spreadingData processing applicationsInformation dispersalPopulation sample
One embodiment of the present invention provides a system for selecting a set of nodes to maximize information spreading. During operation, the system receives a budget constraint and a population sample, constructs a social network associated with the population sample, analyzes a network graph associated with the social network to obtain structural information associated with a node within the social network, estimates characteristics associated with the node, and selects the set of nodes that maximizes the information spreading under the budget constraint based on the structural information and the characteristics associated with the node.
Owner:XEROX CORP
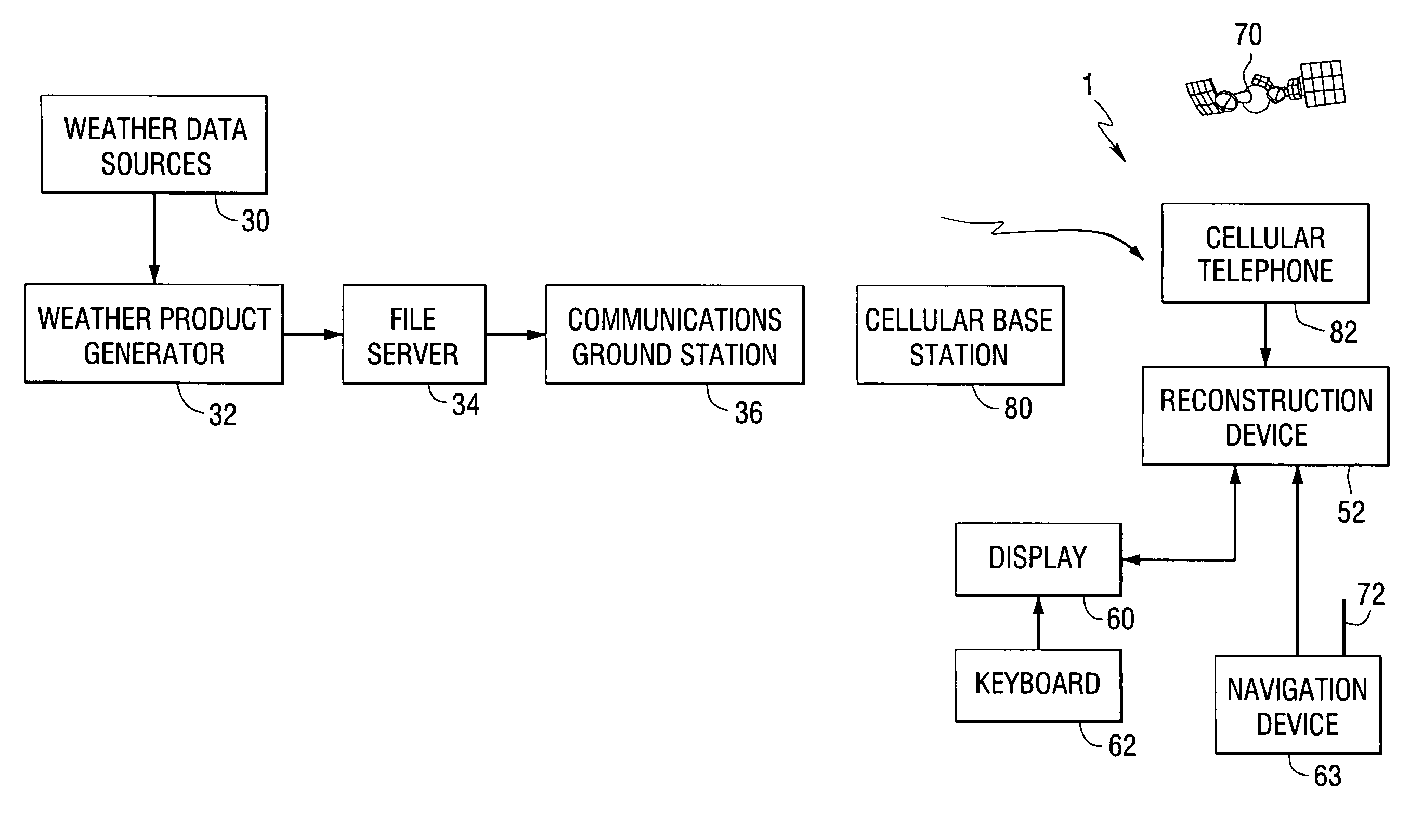
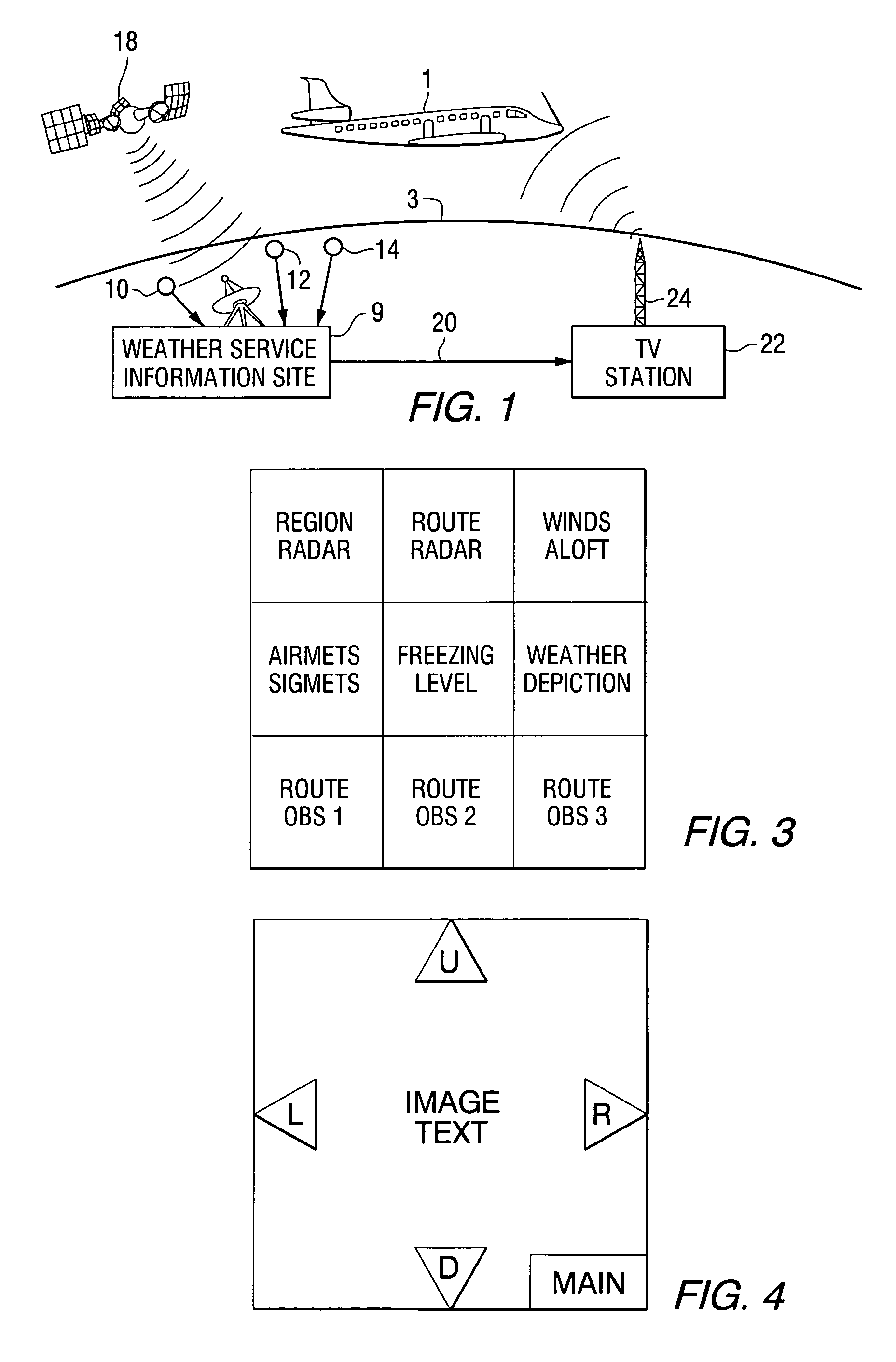
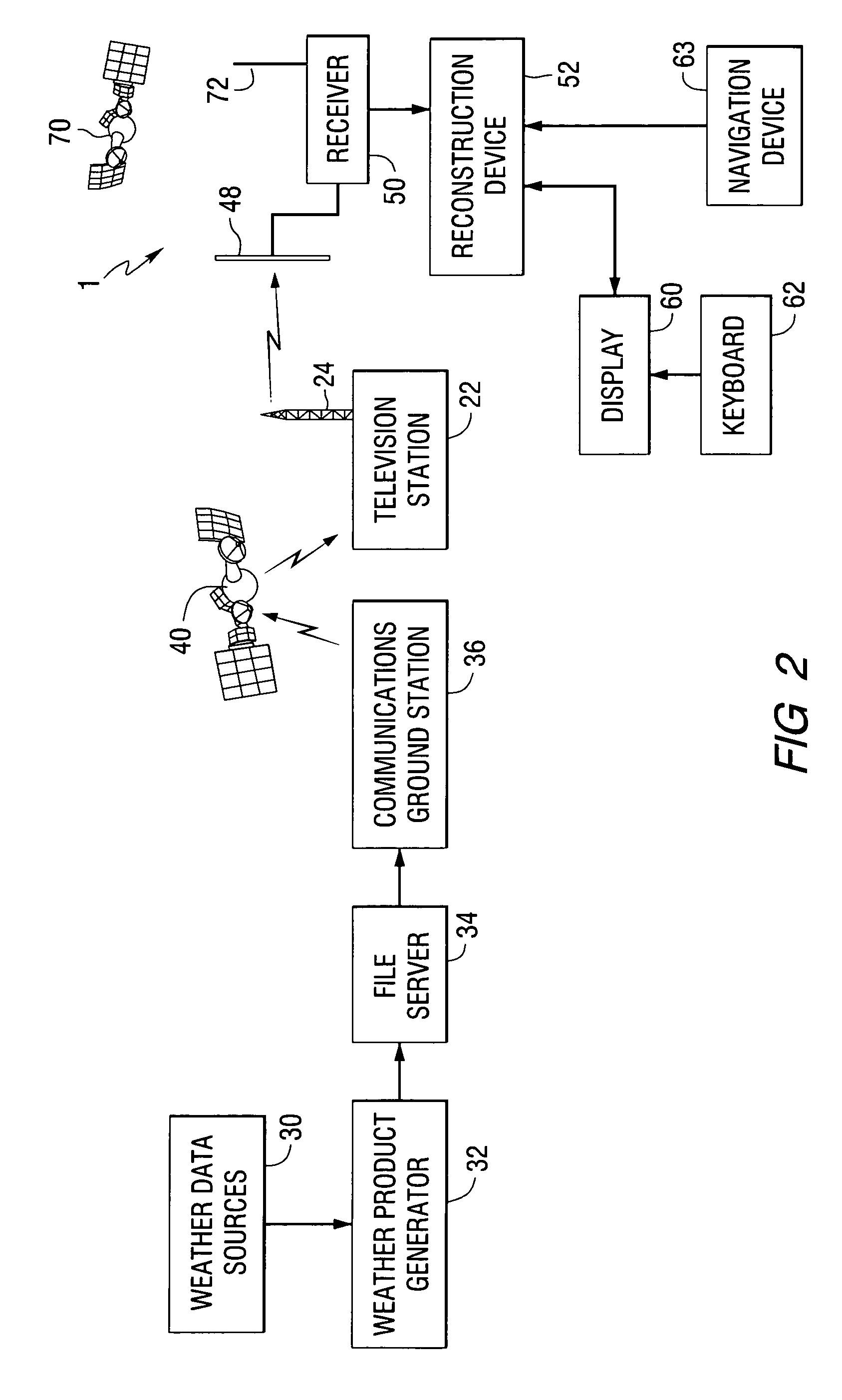
Weather information dissemination system for mobile vehicles
InactiveUS6995686B2Arrangements for variable traffic instructionsSpecific information broadcast systemsMobile vehicleInformation dispersal
A method and apparatus for disseminating weather products, based on raw weather data provided by various weather condition sensors, to a mobile vehicle. The weather products are formed as web pages and transmitted to the mobile vehicle during the vertical blanking interval of a broadcast television signal. The weather products are received and displayed within the vehicle under control of a web browser.
Owner:HARRIS CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com