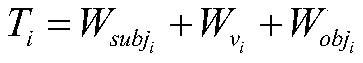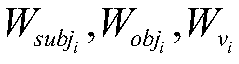Patents
Literature
92 results about "Event level" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
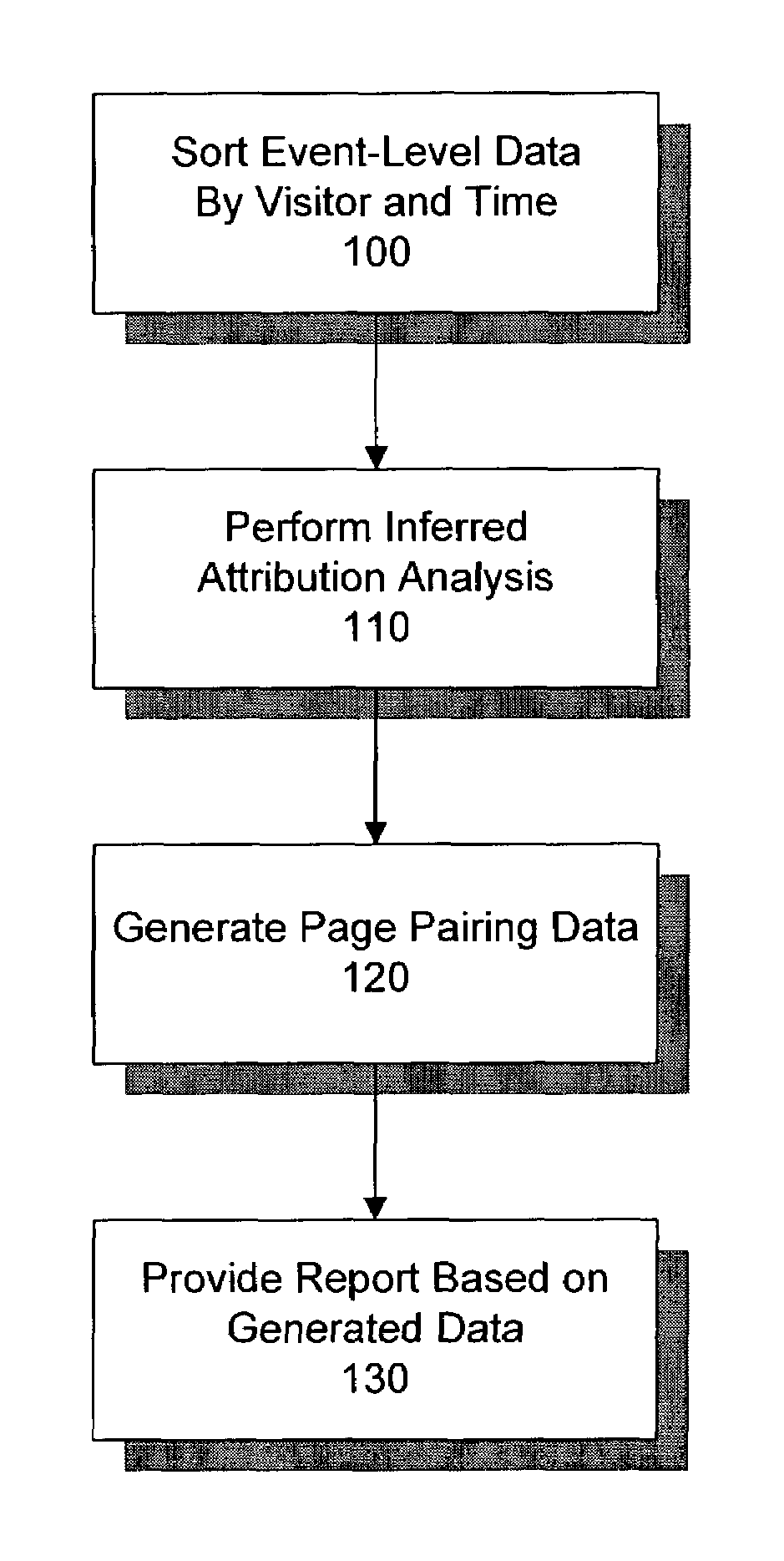
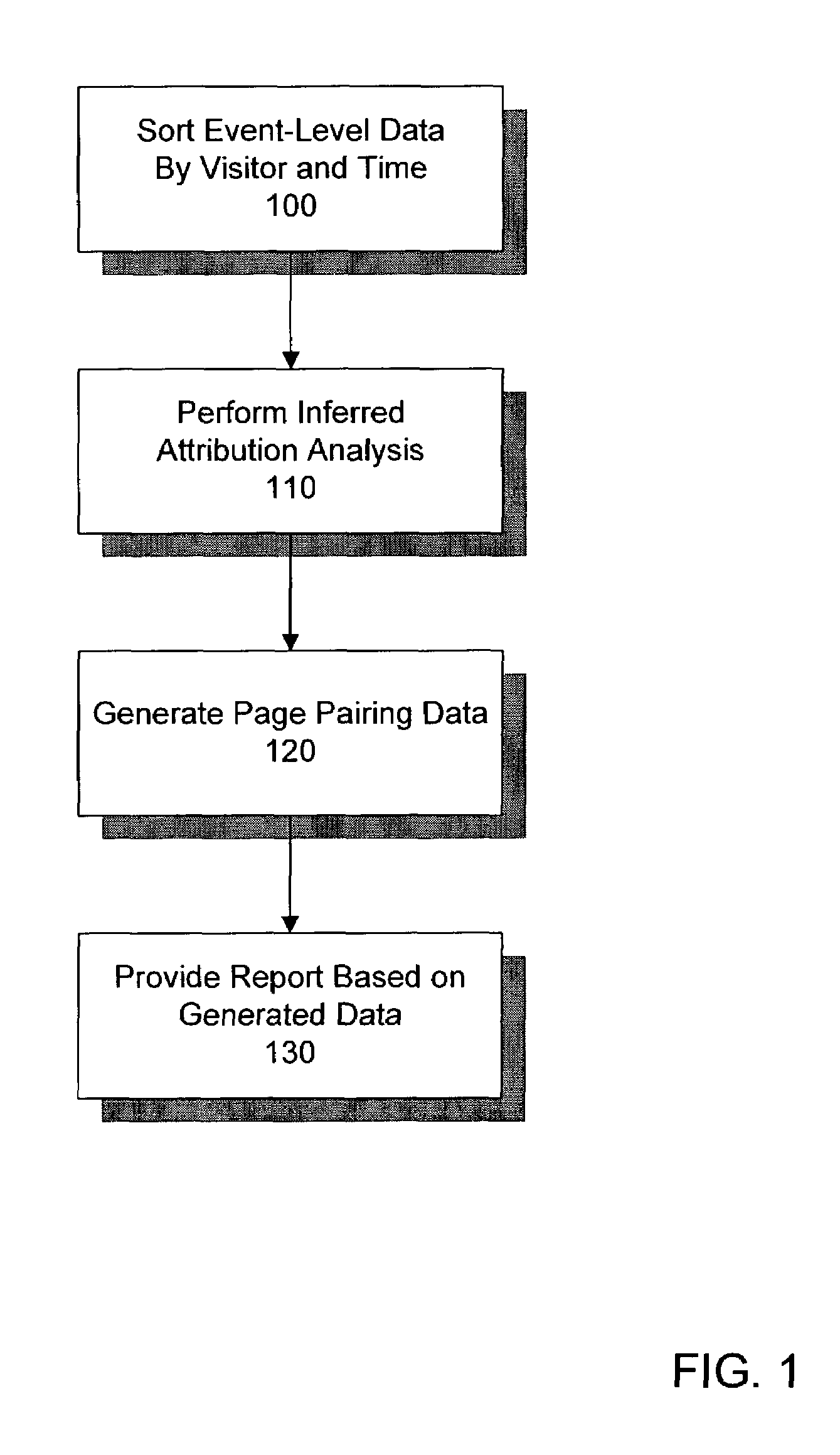
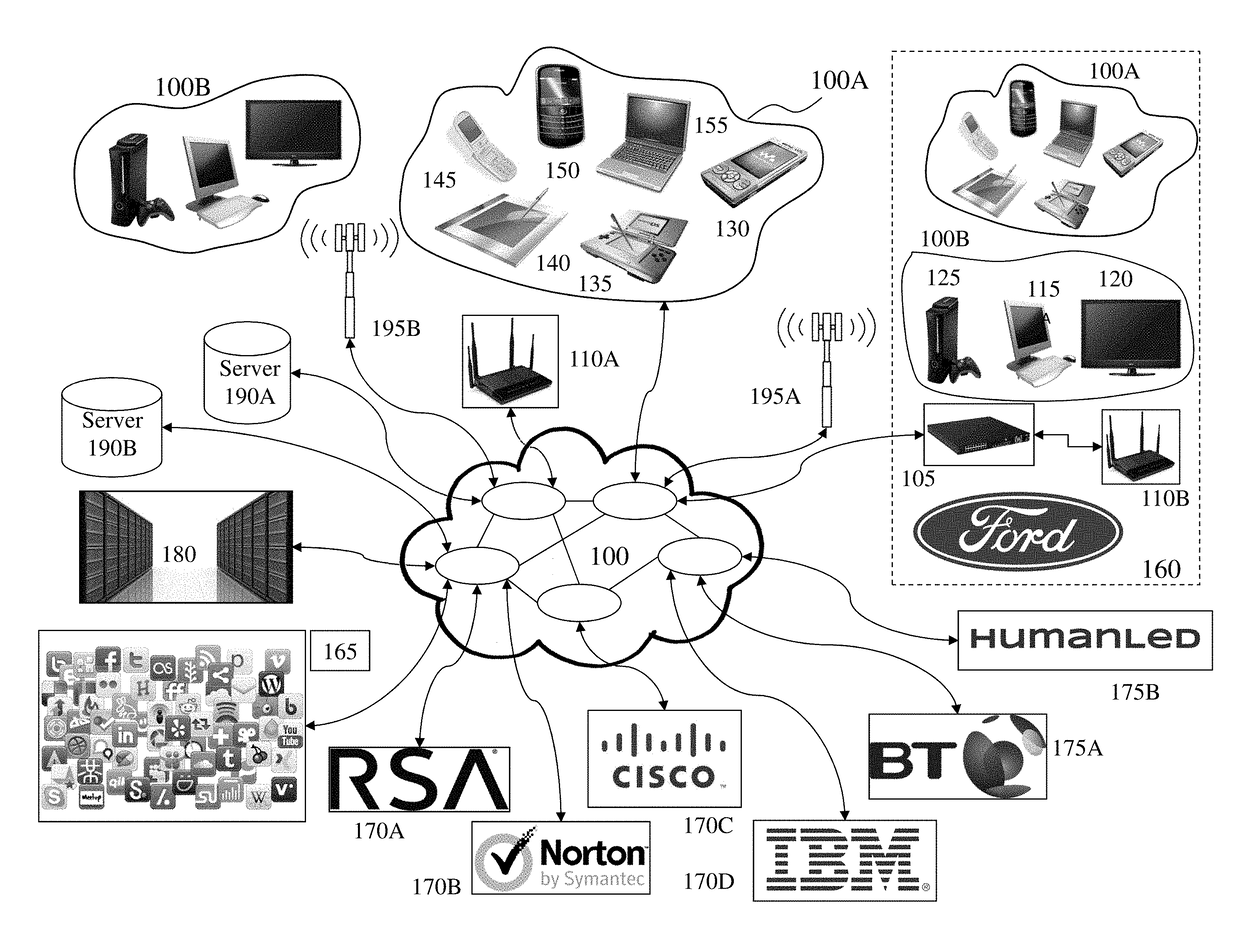
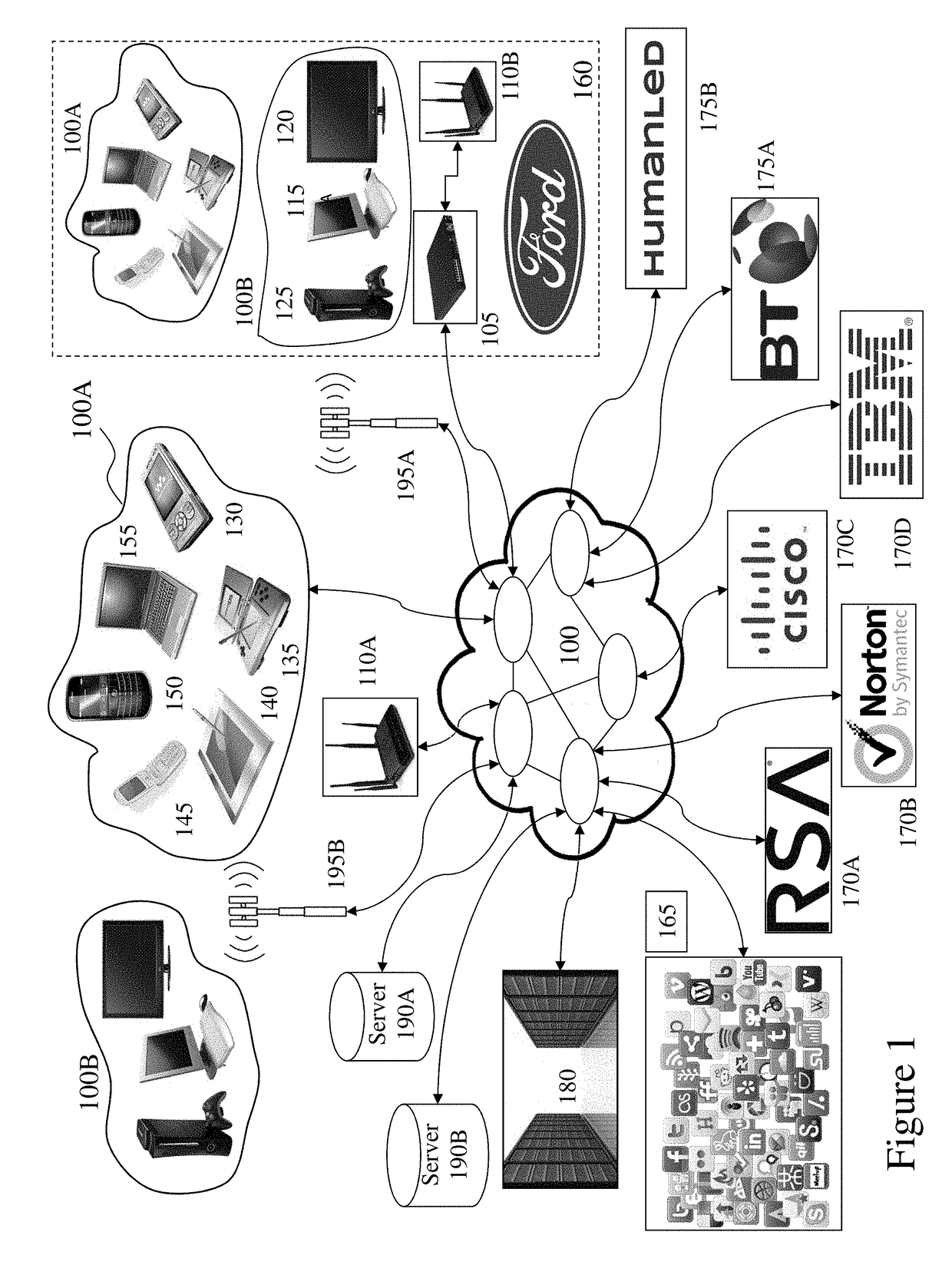
System and method for reporting website activity based on inferred attribution methodology
ActiveUS7349827B1Efficient and cost-effectiveEasy accessNuclear monitoringDigital computer detailsEvent levelClient-side
A method and system for reporting website activity. According to an example embodiment, the system receives event-level data representing visitor activity through navigation entities on a client website, infers attribution of one or more metrics to at least one navigation entity based on the visitor activity, and provides online reports to the client based on the inferred attribution.
Owner:GOOGLE LLC
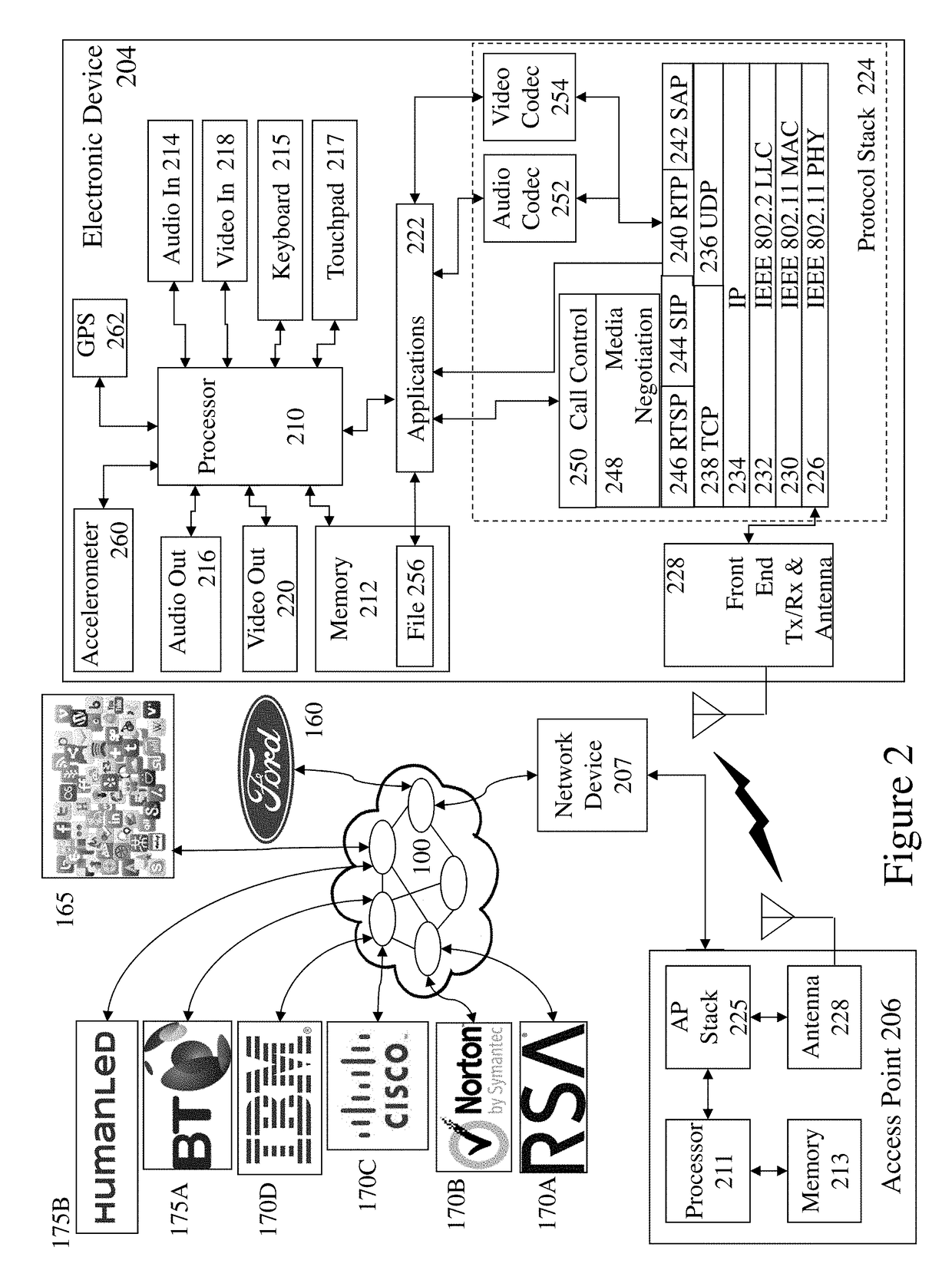
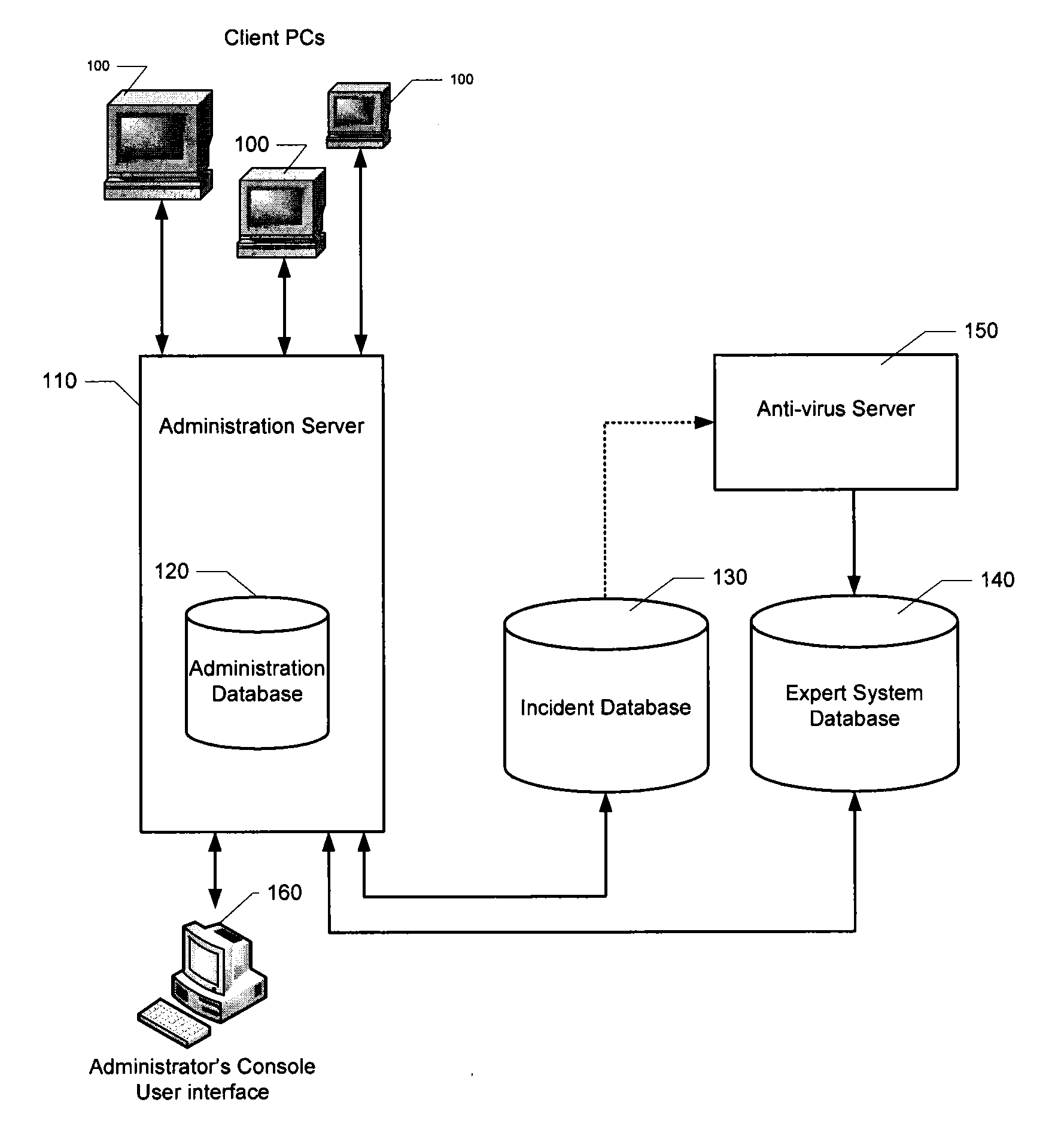
Automatic analysis of security related incidents in computer networks
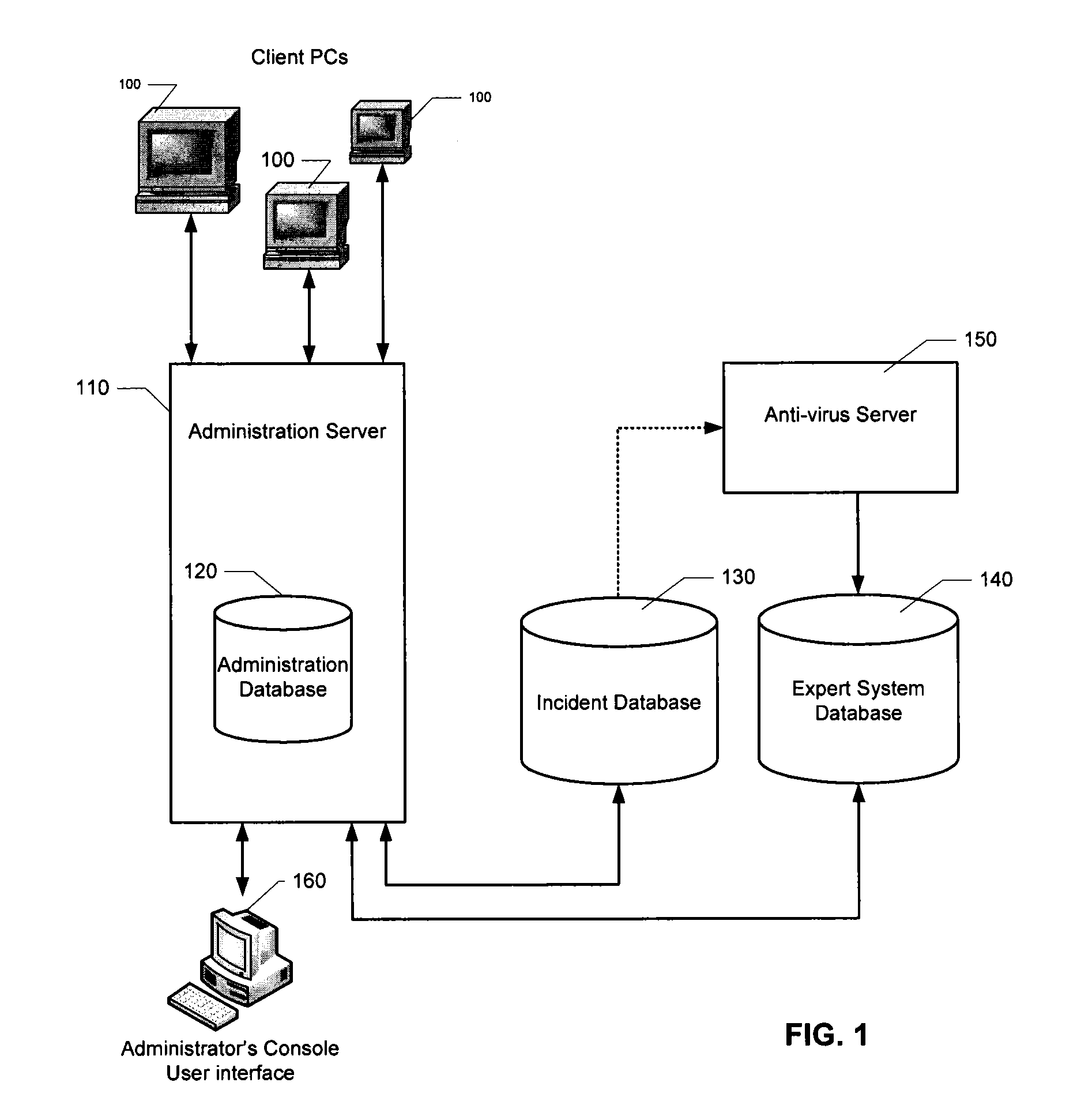
ActiveUS8776241B2Shorten the timePrevent relapseMemory loss protectionError detection/correctionEvent levelRelevant information
Owner:AO KASPERSKY LAB
Method for event-based semantic classification
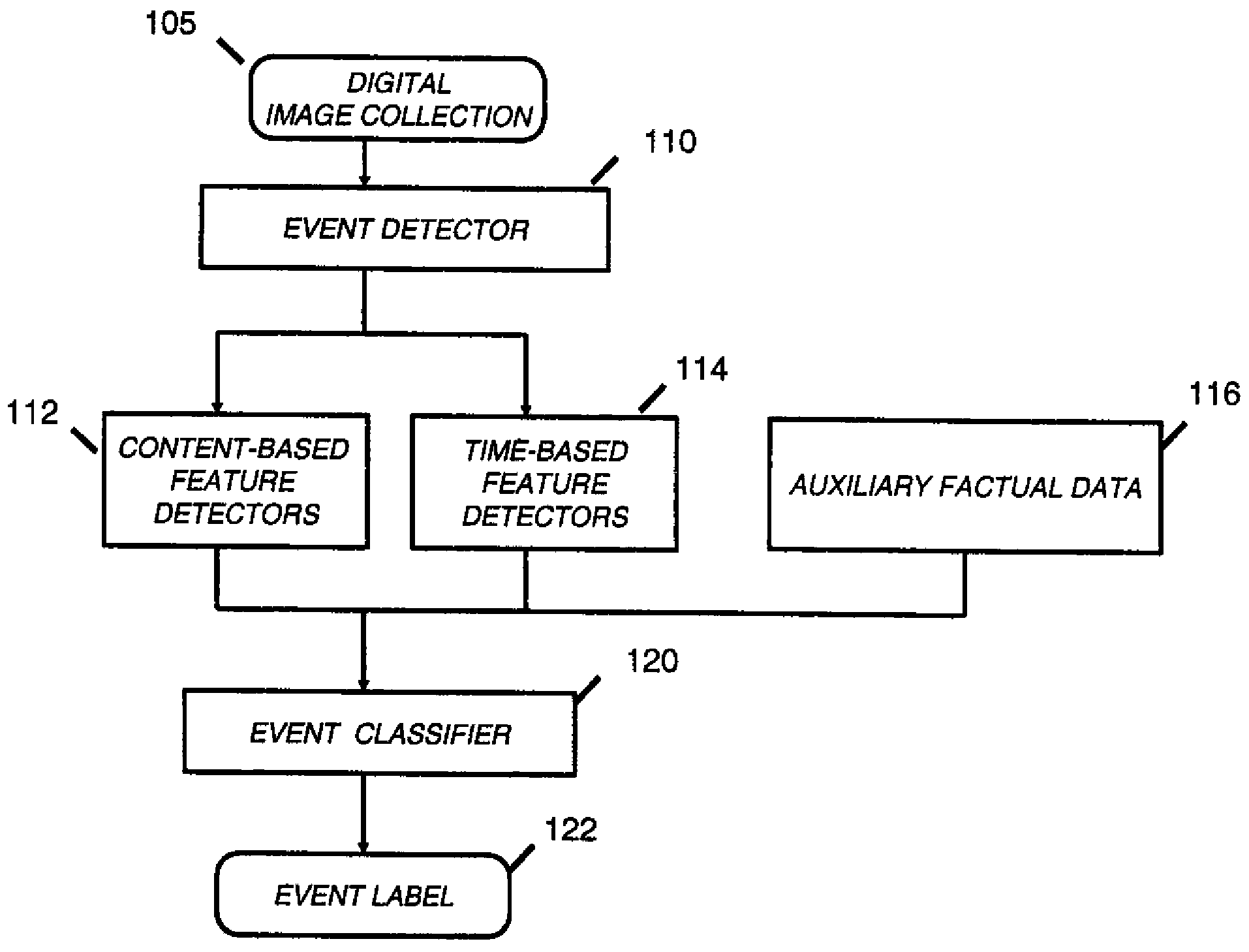
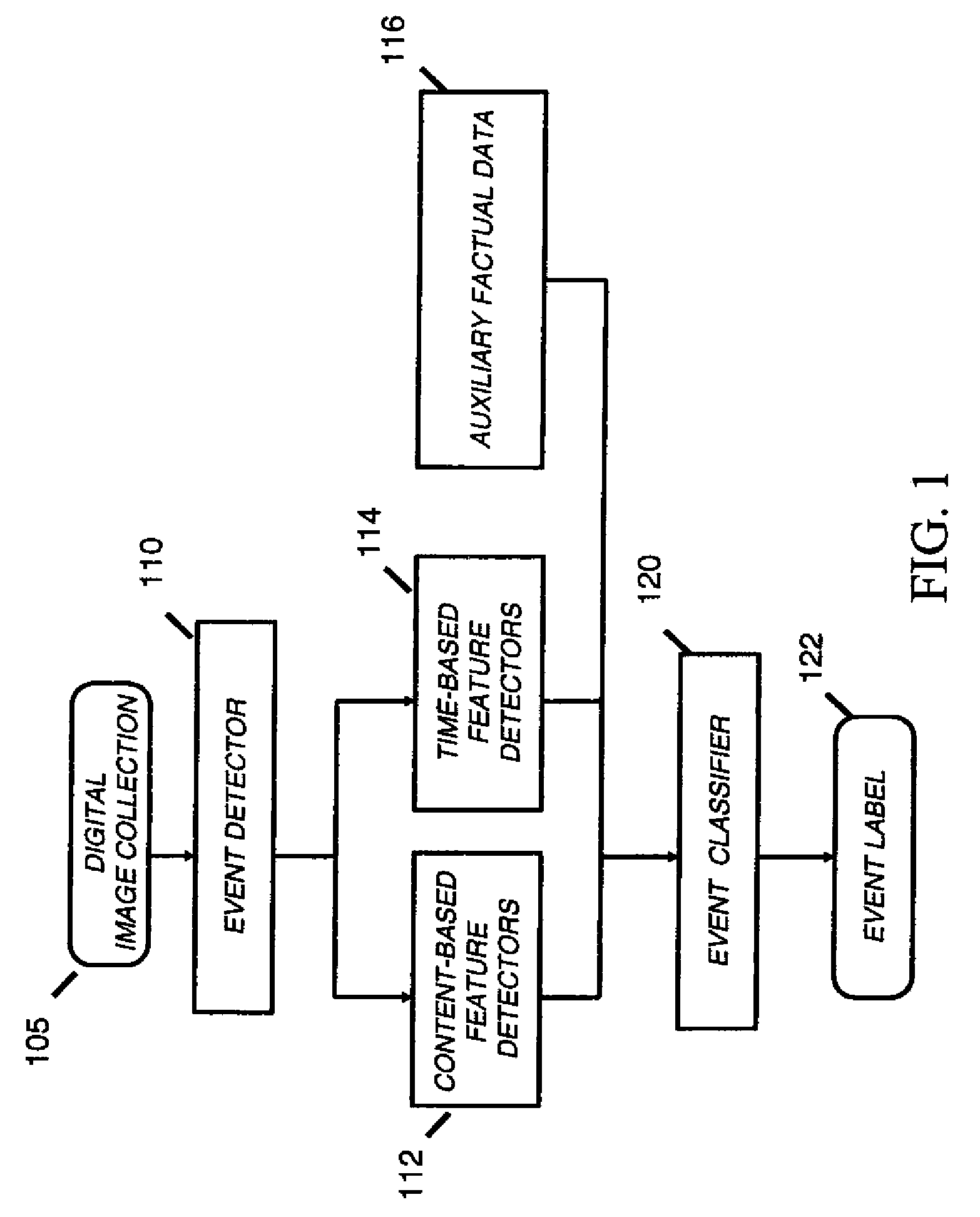
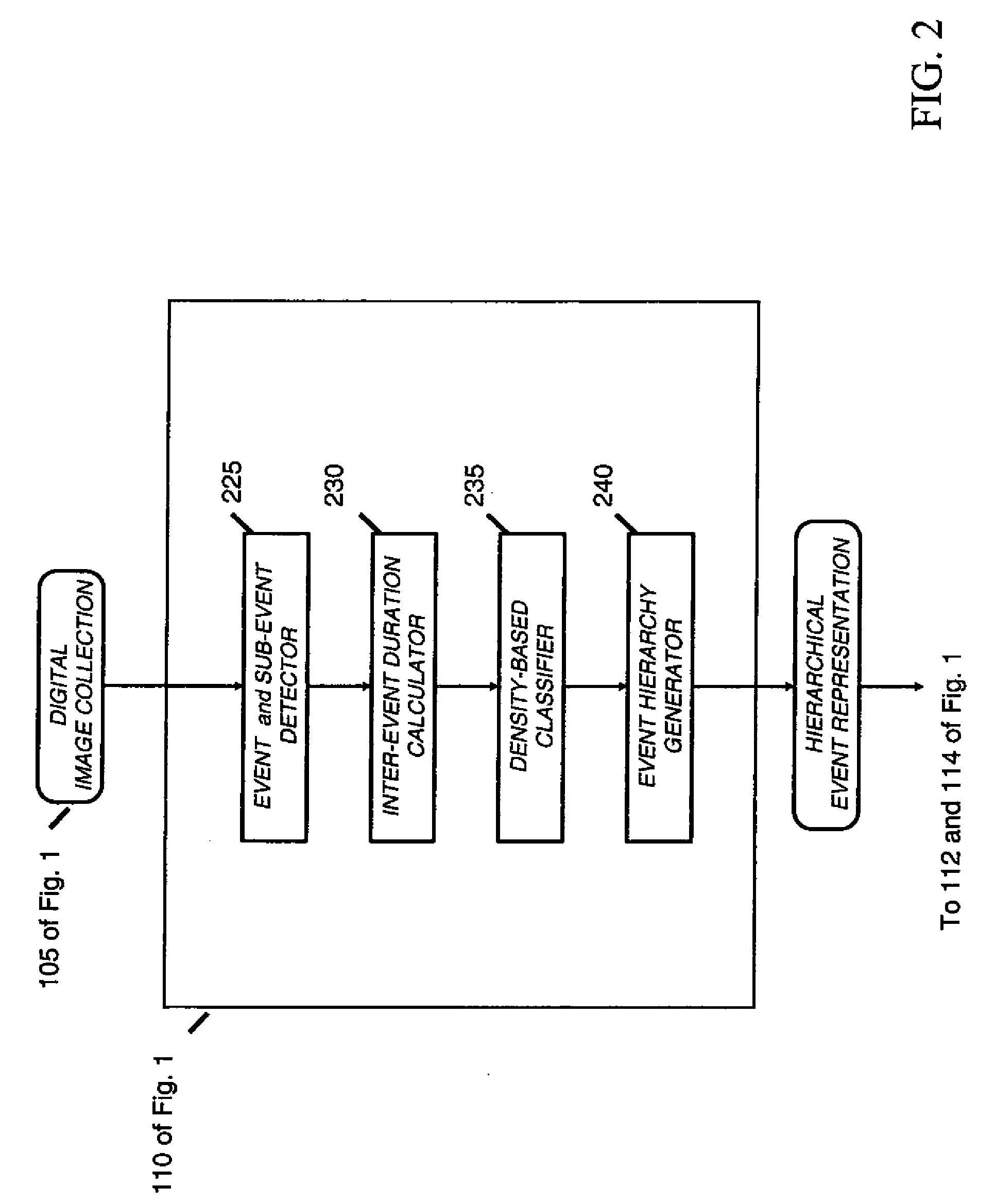
ActiveUS20100124378A1Digital data processing detailsRelational databasesEvent levelClassification methods
A method of automatically classifying images in a consumer digital image collection, includes generating an event representation of the image collection; computing global time-based features for each event within the hierarchical event representation; computing content-based features for each image in an event within the hierarchical event representation; combining content-based features for each image in an event to generate event-level content-based features; and using time-based features and content-based features for each event to classify an event into one of a pre-determined set of semantic categories.
Owner:MONUMENT PEAK VENTURES LLC
System and method enabling multiple processes to efficiently log events
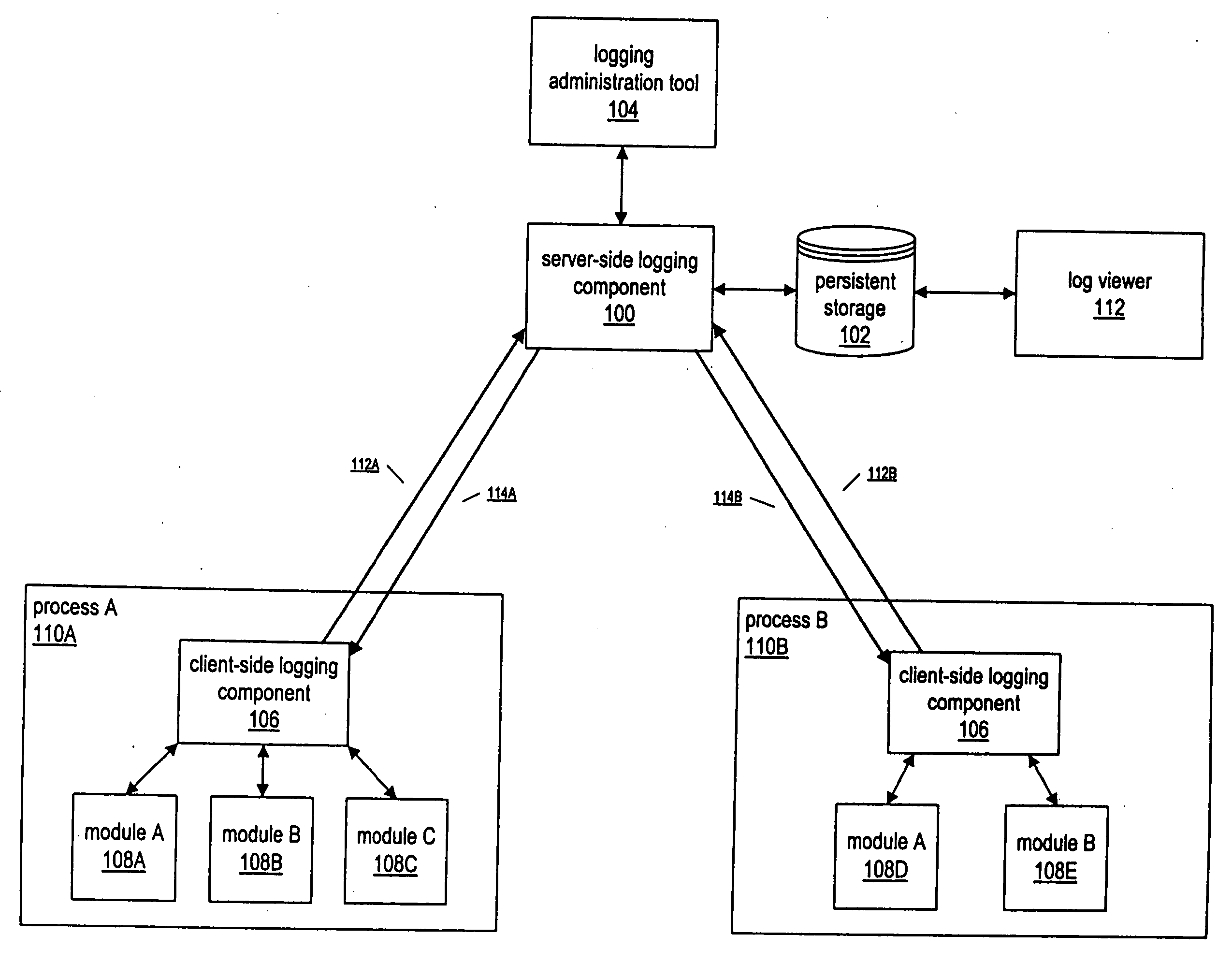
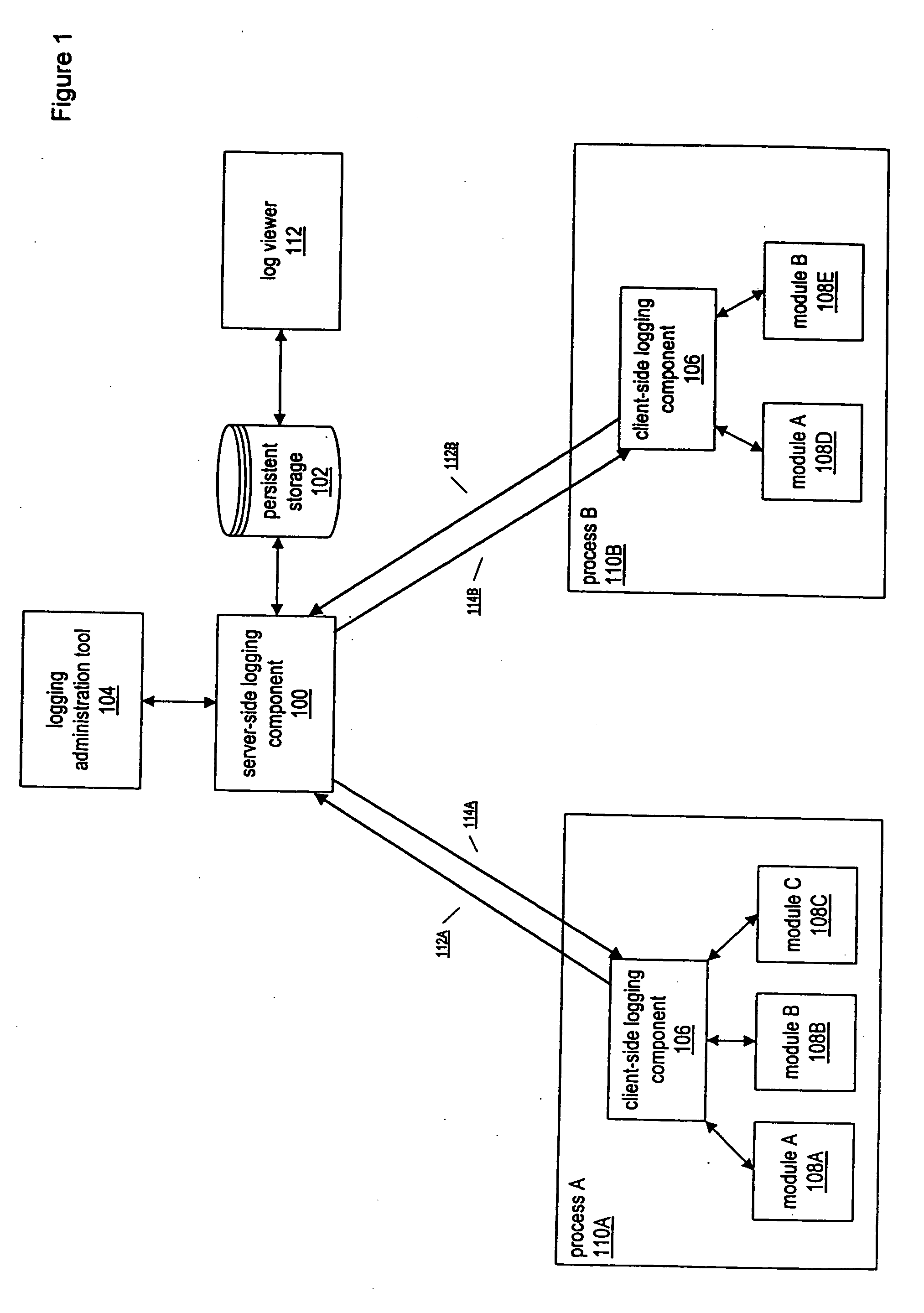
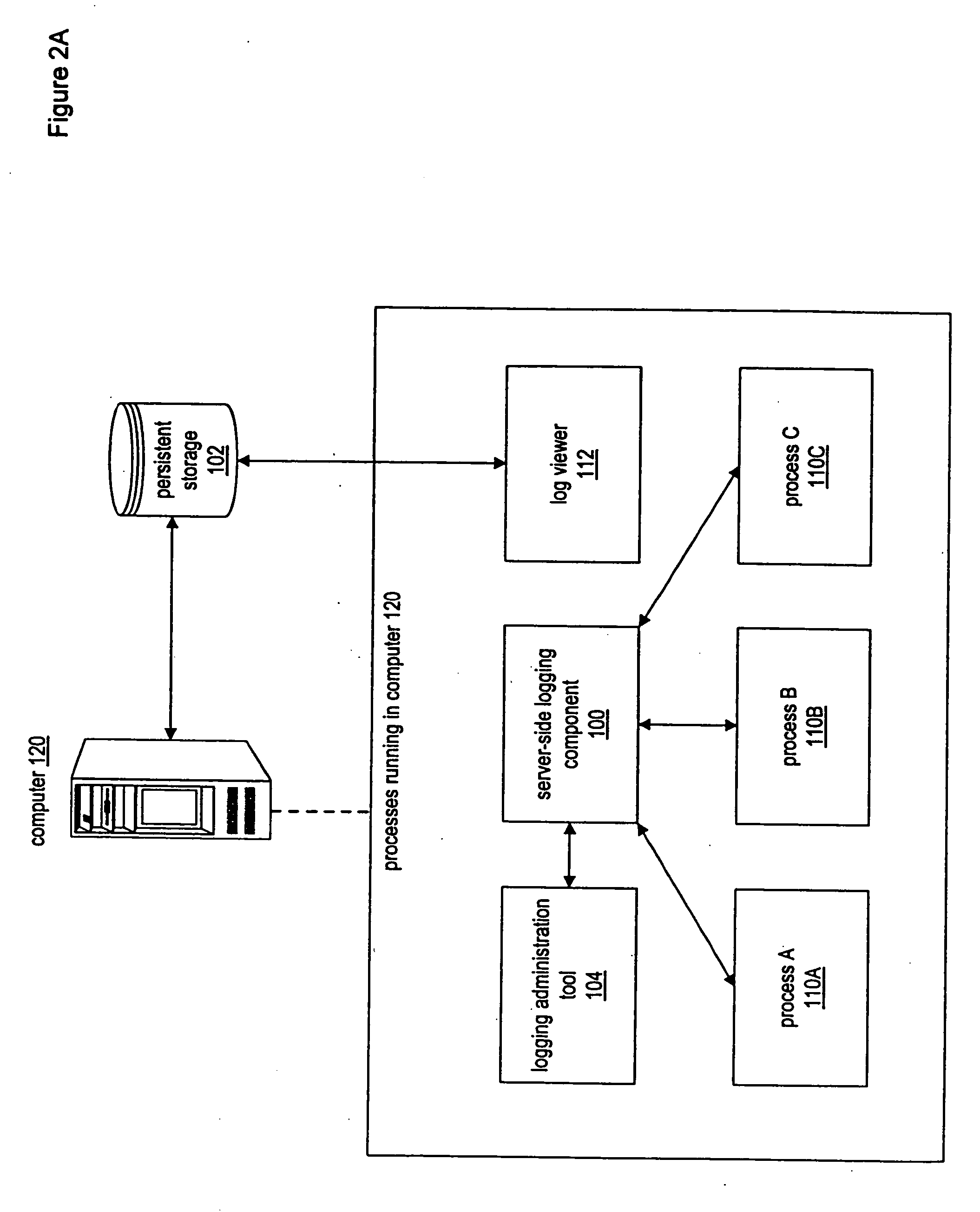
InactiveUS20050028171A1Efficiently log eventError detection/correctionProgram controlInformation dispersalEvent level
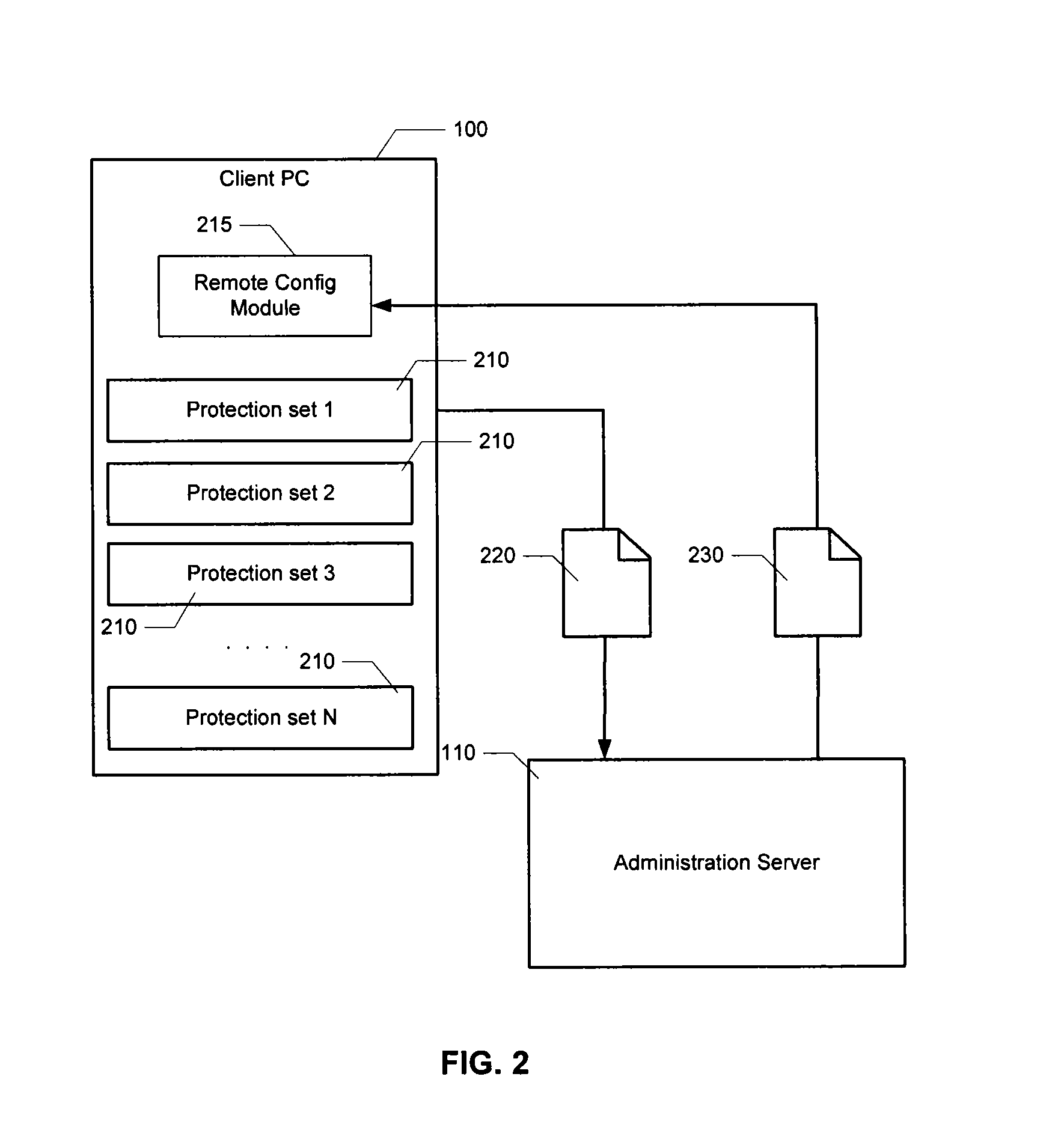
A system and method for enabling multiple processes to efficiently log events is described. A client executable module that needs to log an event may interface with a module or component referred to as a “client-side logging component”, passing various types of information regarding the event, such as an associated event level, one or more event associated event categories, an informational message, etc. The client-side logging component may maintain event logging criteria specifying which types of events should be logged. If the event should be logged, the client-side logging component may queue the event information and return execution control the client module. The event information may then be asynchronously retrieved from the event queue and sent to a server-side logging component. The server-side logging component may persistently log the event information in any of various ways, e.g., by storing it in a file, a database, etc. Processes running on multiple computers may call the server-side logging component to log events, via a client-side logging component instance associated with the process. A logging administration tool may be utilized in order to set event logging criteria. In response to being configured with new event logging criteria information, the server-side logging component may automatically propagate the logging criteria information to each of the client-side logging components. The client-side logging components may then being using the new logging criteria, dynamically changing the filtering of events that are sent to the server-side logging component.
Owner:KOUGIOURIS PANAGIOTIS +1
Security threat information gathering and incident reporting systems and methods
ActiveUS20170346846A1Improve the level ofEnhance client communicationTransmissionEvent levelCountermeasure
A common misconception equates information with intelligence. To transform information into intelligence a number of analytical steps must occur within a framework designed to yield very specific datum associable with other raw or formulated datum, that provides an answer or solution to a sub-problem. Every organization has threats and risks including cyber threats, threats to infrastructure, etc. that can impact the organization on many levels. However, most organizations do not understand how to quantify and assess these risks / threats yet alone assess different preemptive actions for mitigating impact. It would therefore be beneficial to provide organizations with a software based system that provides threat information gathering, incident reporting, and asset identification / valuation as part of its compounded intelligence and supports predictive context specific analysis of risks and countermeasures. Further, distributed countermeasure monitoring provides incident levels of known and unknown, or yet to be categorized threats.
Owner:FINDLAY VALERIE ANN
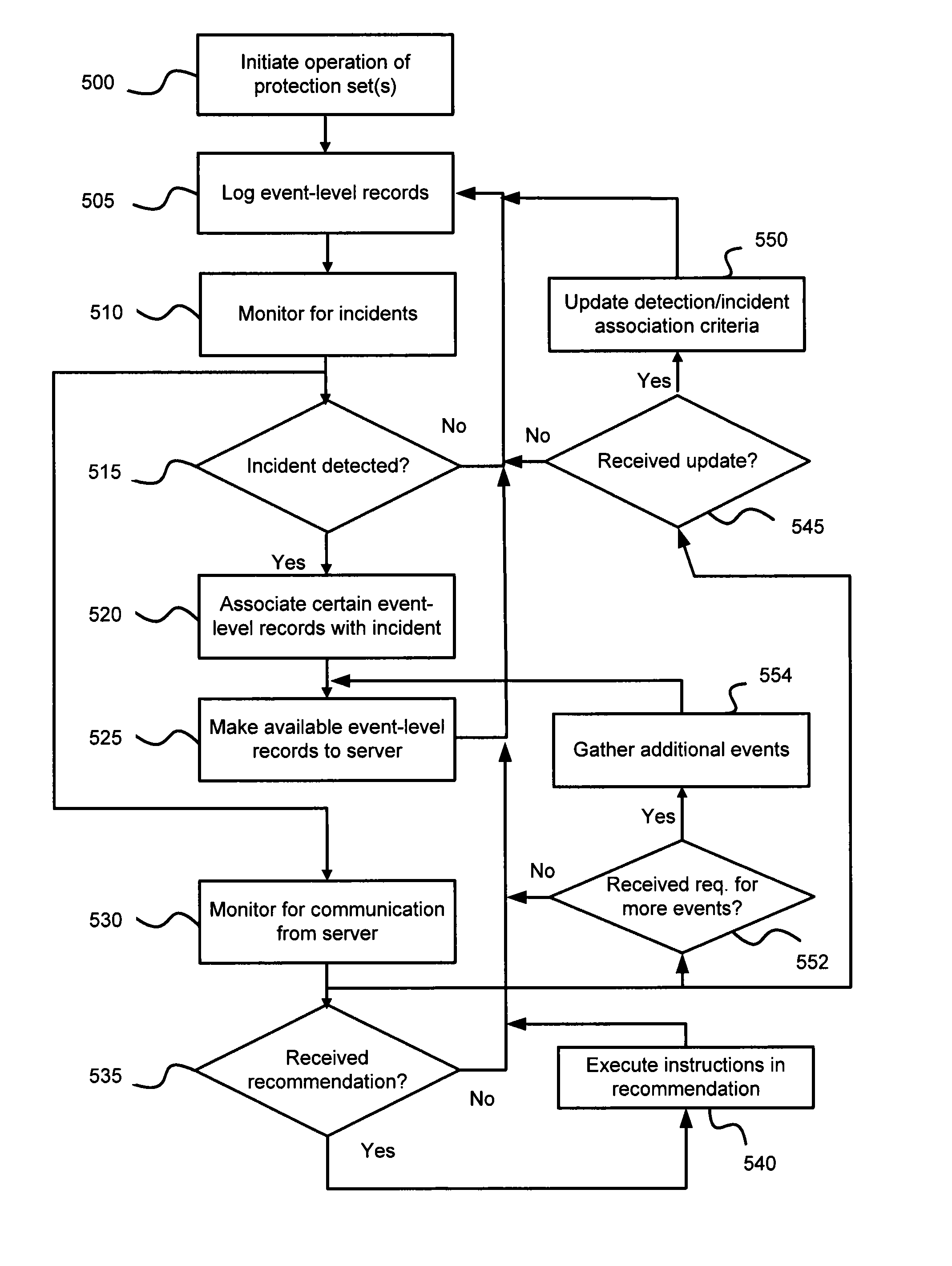
Automatic analysis of security related incidents in computer networks
ActiveUS20130055399A1Reduce time spent on investigatingEasy to detectMemory loss protectionError detection/correctionEvent levelChain of events
Solutions for responding to security-related incidents in a computer network, including a security server, and a client-side arrangement. The security server includes an event collection module communicatively coupled to the computer network, an event analysis module operatively coupled to the event collection module, and a solution module operatively coupled to the event analysis module. The event collection module is configured to obtain incident-related information that includes event-level information from at least one client computer of the plurality of client computers, the incident-related information being associated with at least a first incident which was detected by that at least one client computer and provided to the event collection module in response to that detection. The event analysis module is configured to reconstruct at least one chain of events causally related to the first incident and indicative of a root cause of the first incident based on the incident-related information. The solution module is configured to formulate at least one recommendation for use by the at least one client computer, the at least one recommendation being based on the at least one chain of events, and including corrective / preventive action particularized for responding to the first incident.
Owner:AO KASPERSKY LAB
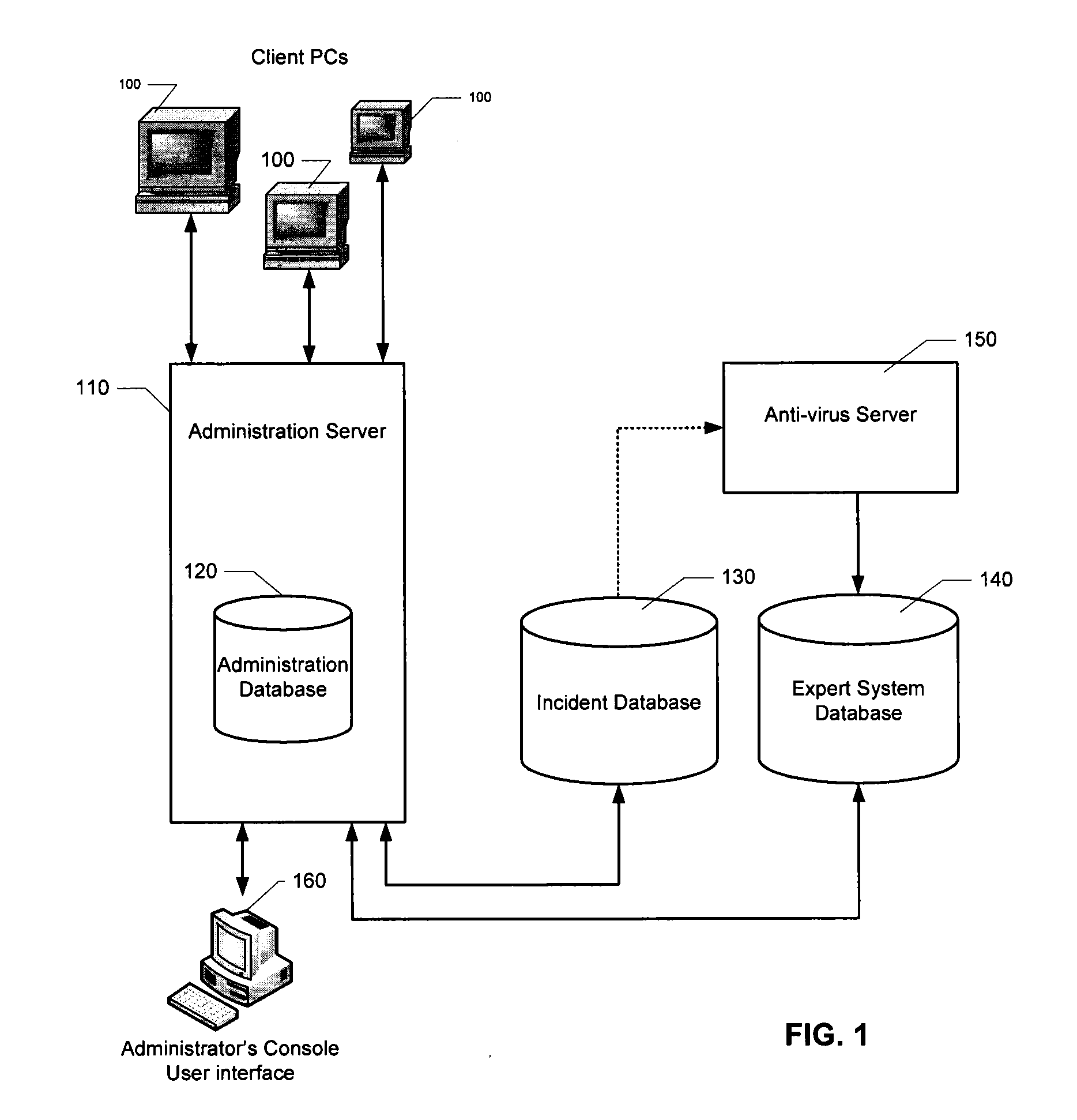
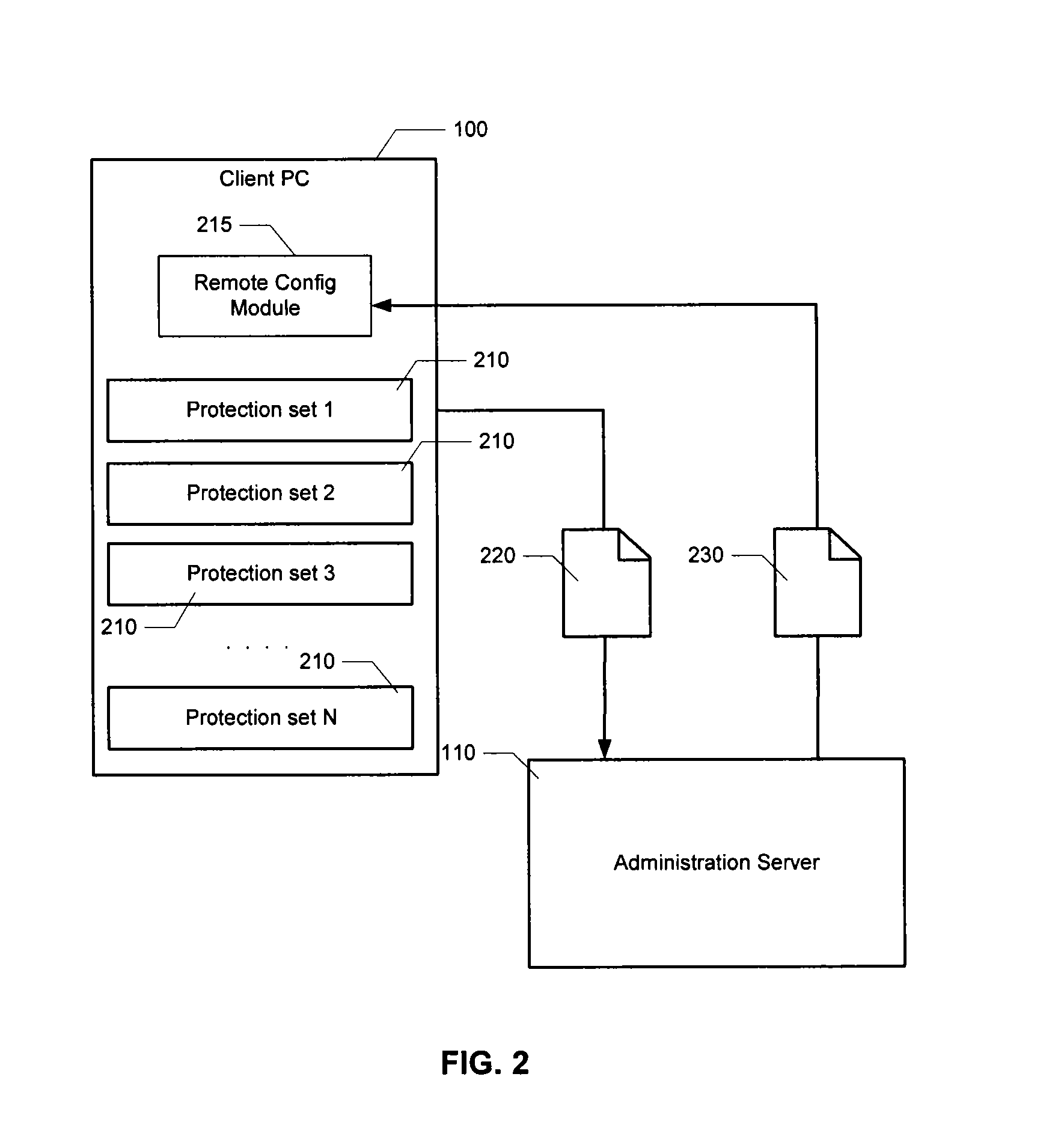
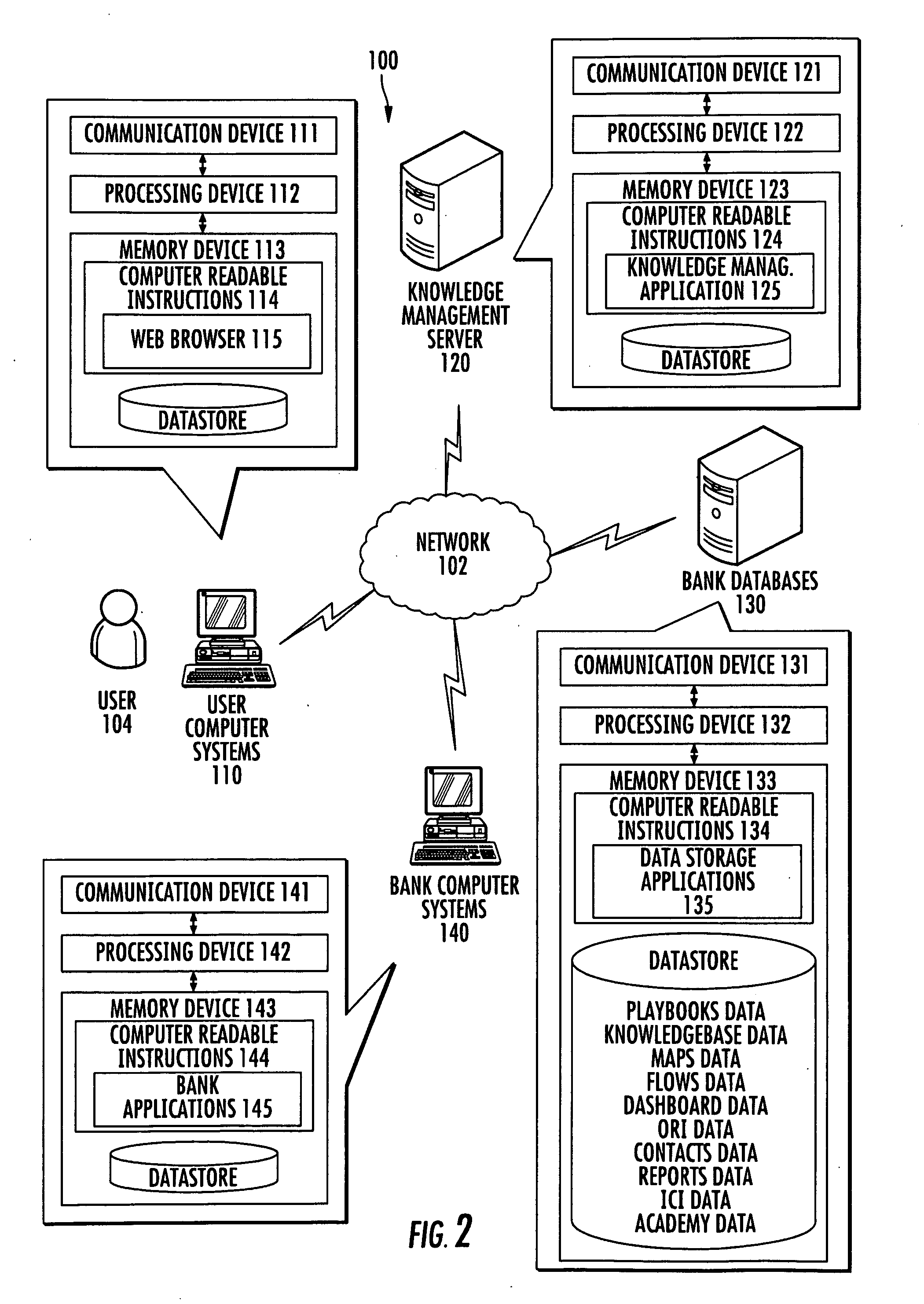
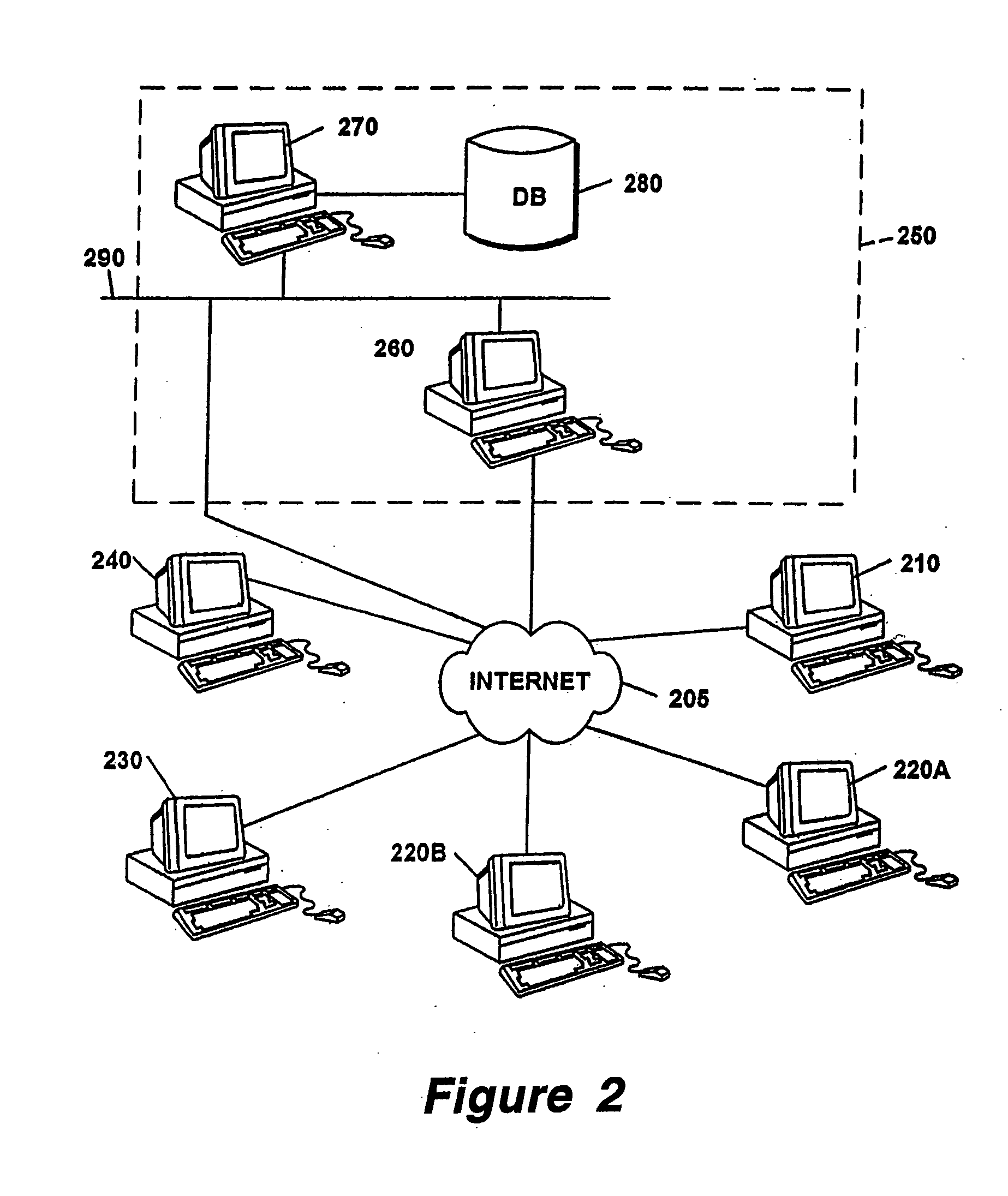
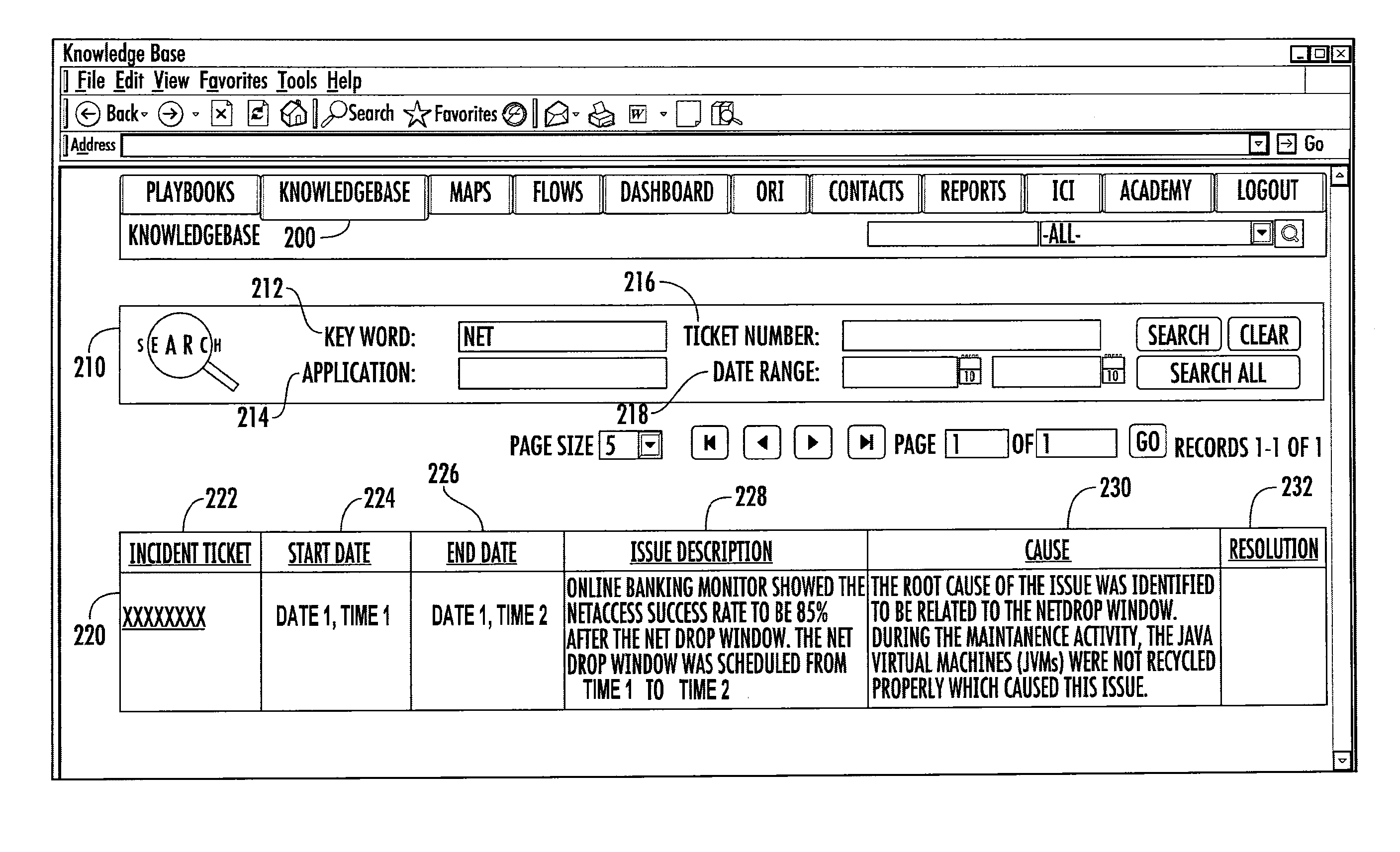
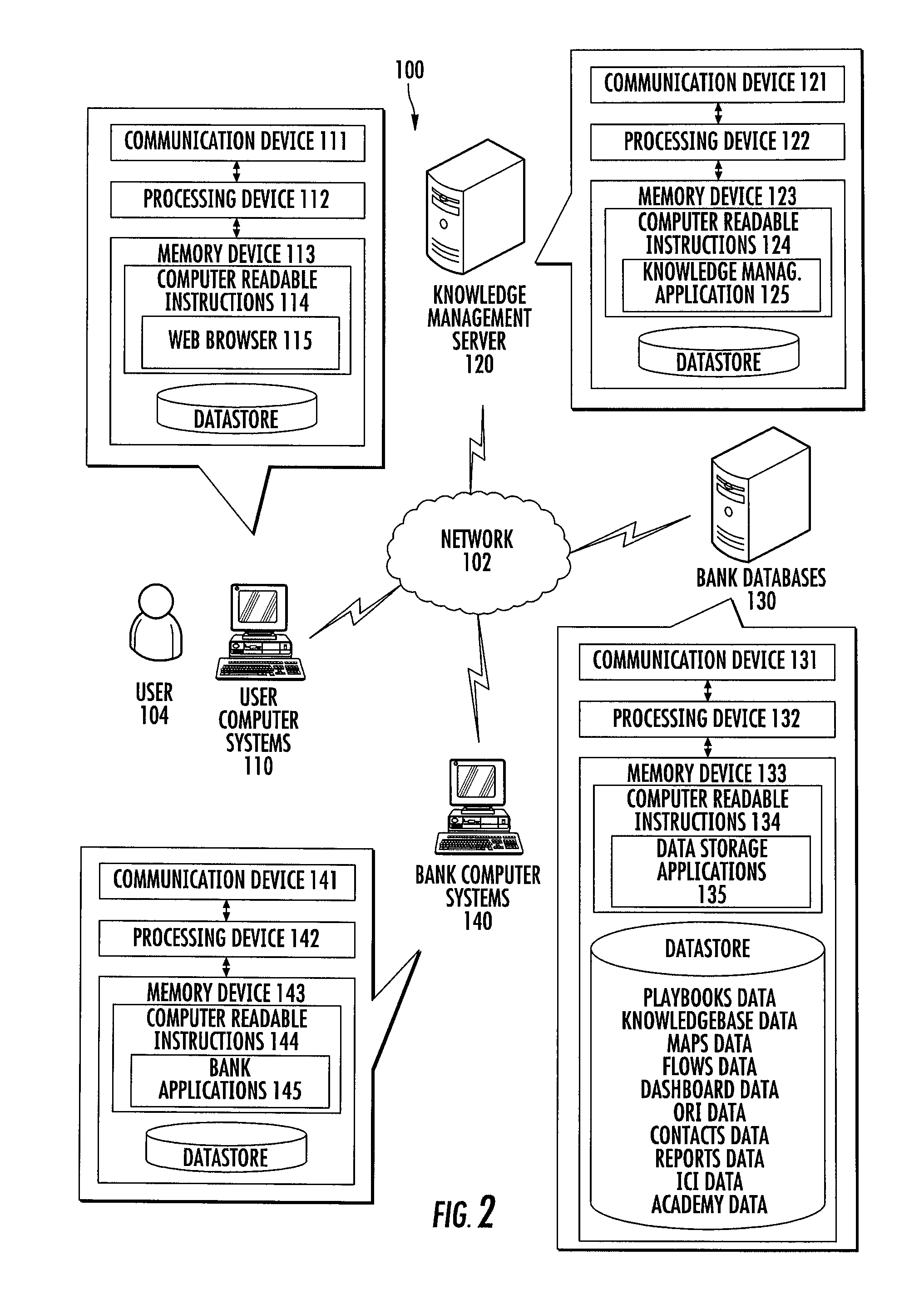
Performance dashboard monitoring for the knowledge management system
Embodiments of the present invention provide a method, system, computer program product, or a combination of the foregoing for creating a knowledge management system including a performance dashboard monitoring system that is standardized and centralized across the channels and sub-channels in an organization. The performance dashboard monitoring system is used to track, measure, and resolve incidents that occur throughout the channels, sub-channels, systems, and applications of an organization. The system receives information related to two or more incidents, where each incident is associated with one or more of a business channel, sub-channel, or application. The system stores the information on a memory device. The system tracks the status of at least one incident between the occurrence and the resolution of the incident. The system displays on a user interface the information related to the incident on a channel, sub-channel, application, or individual incident level.
Owner:BANK OF AMERICA CORP
Network failure real-time relativity analysing method and system
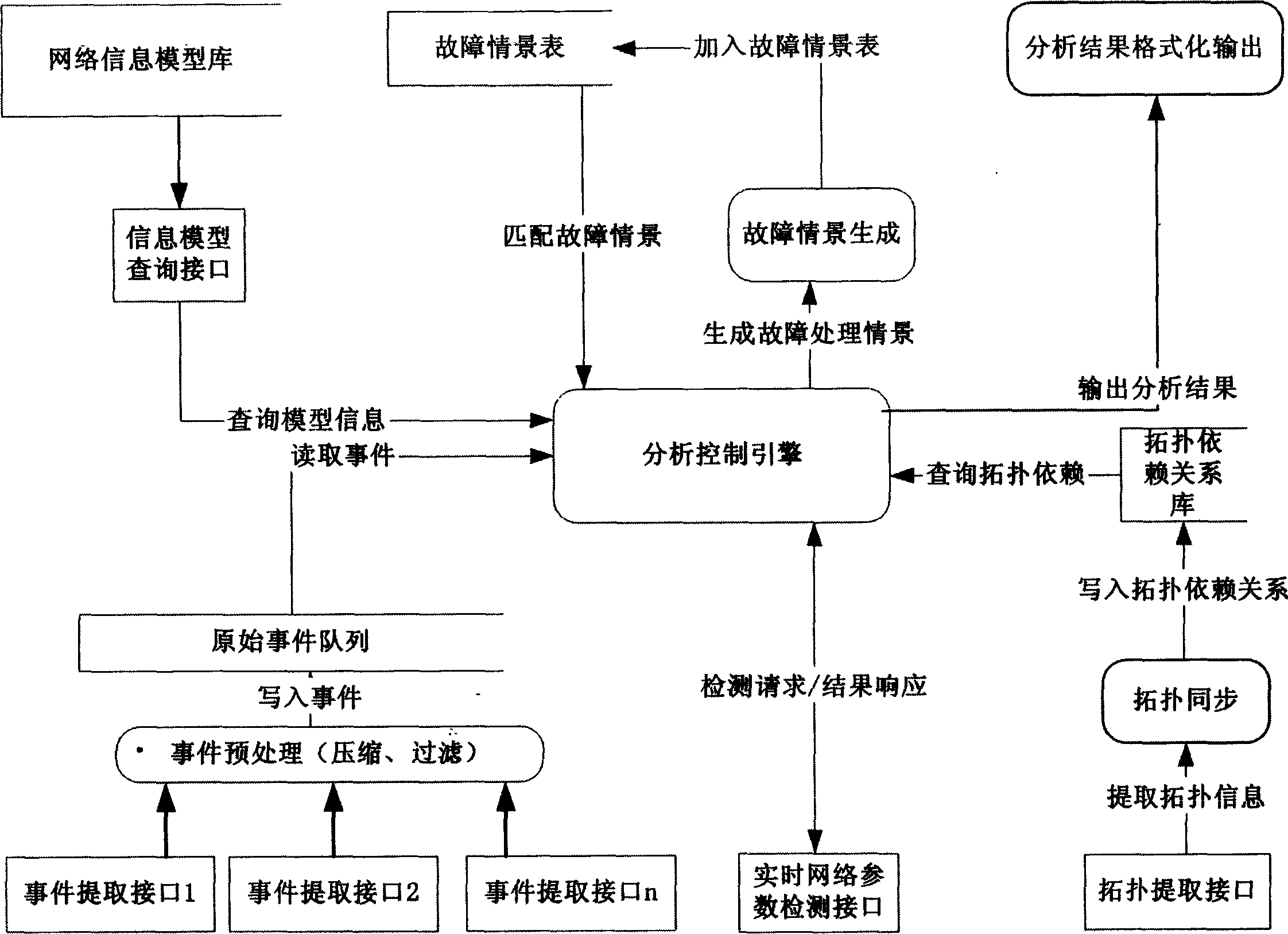
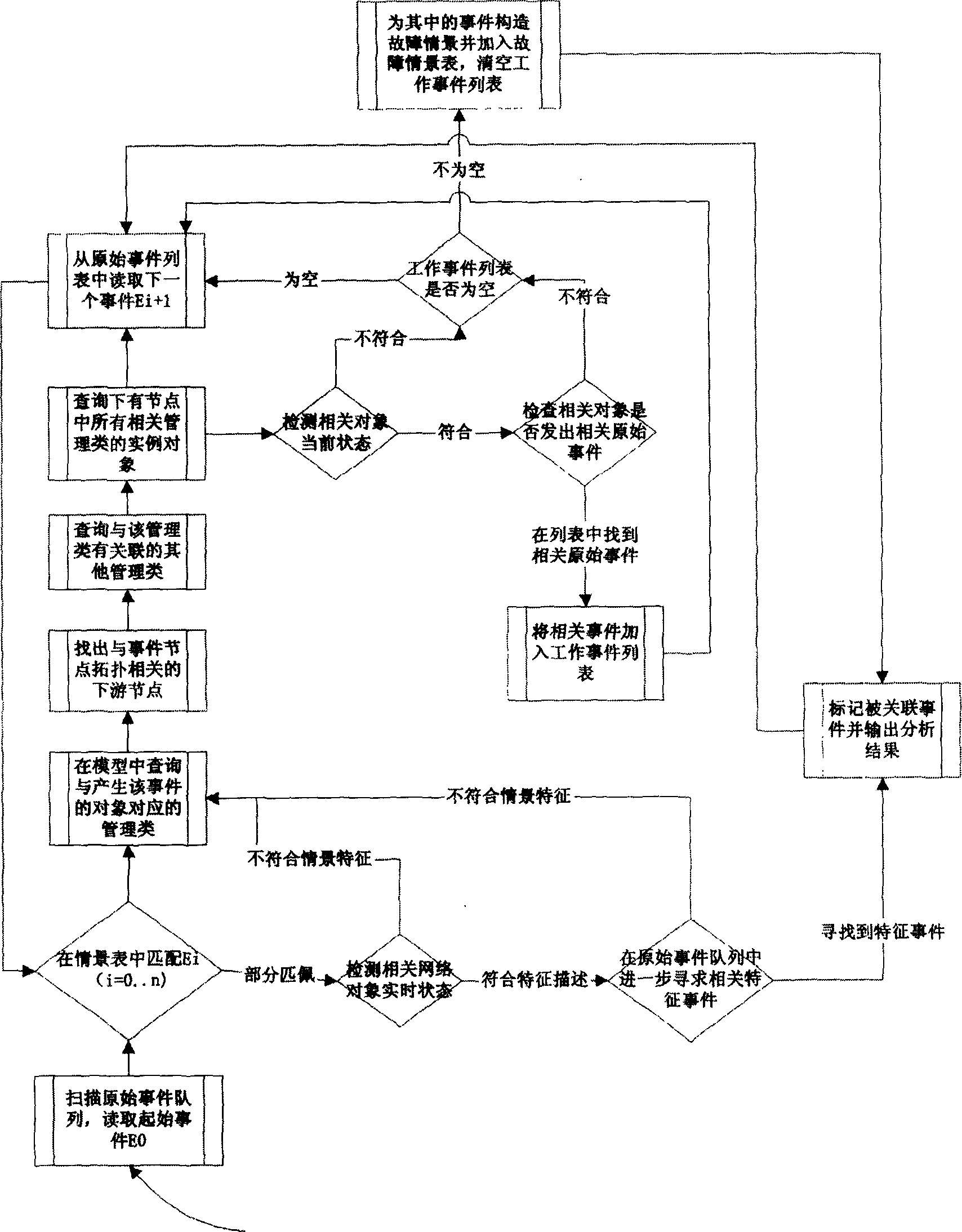
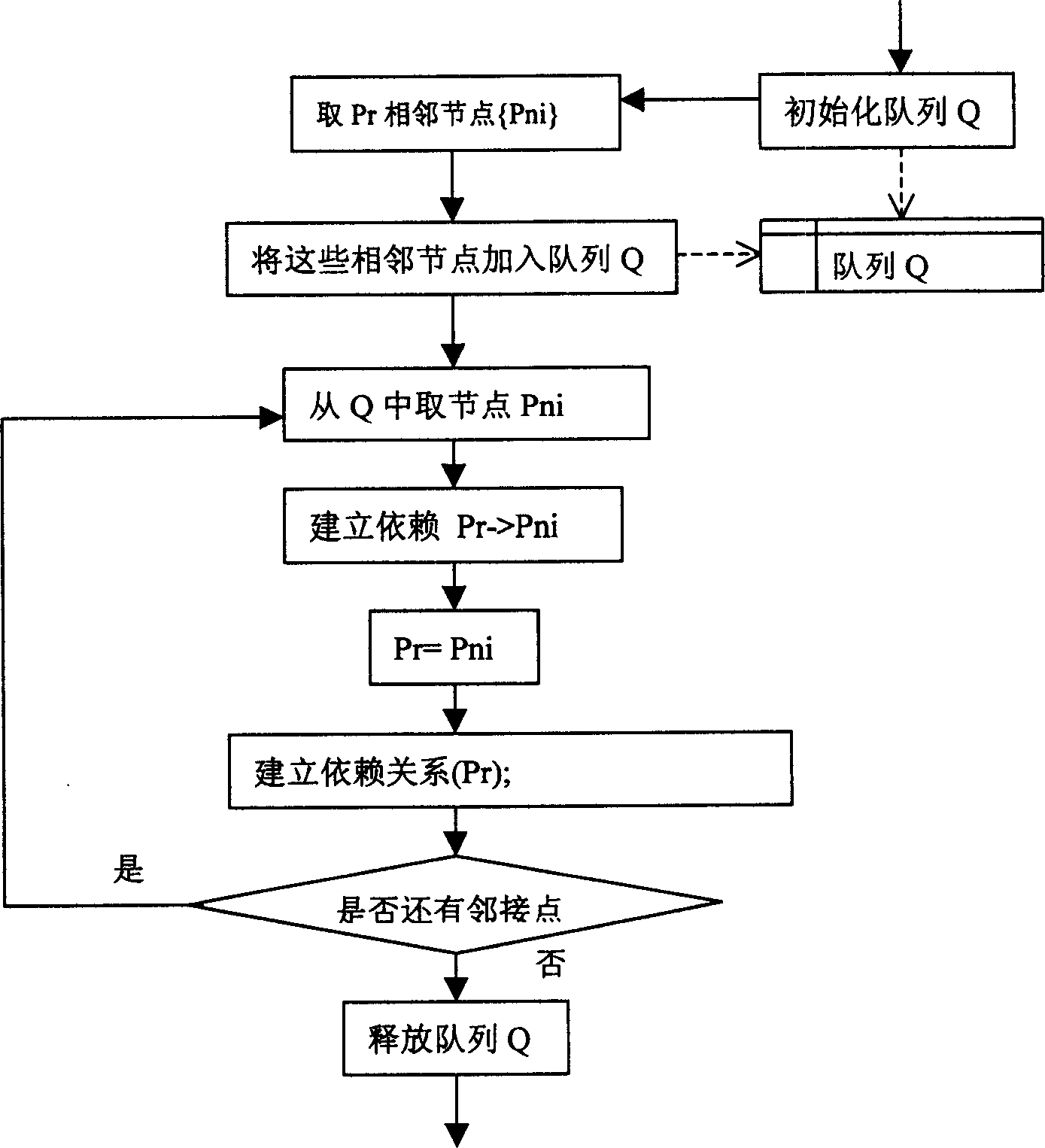
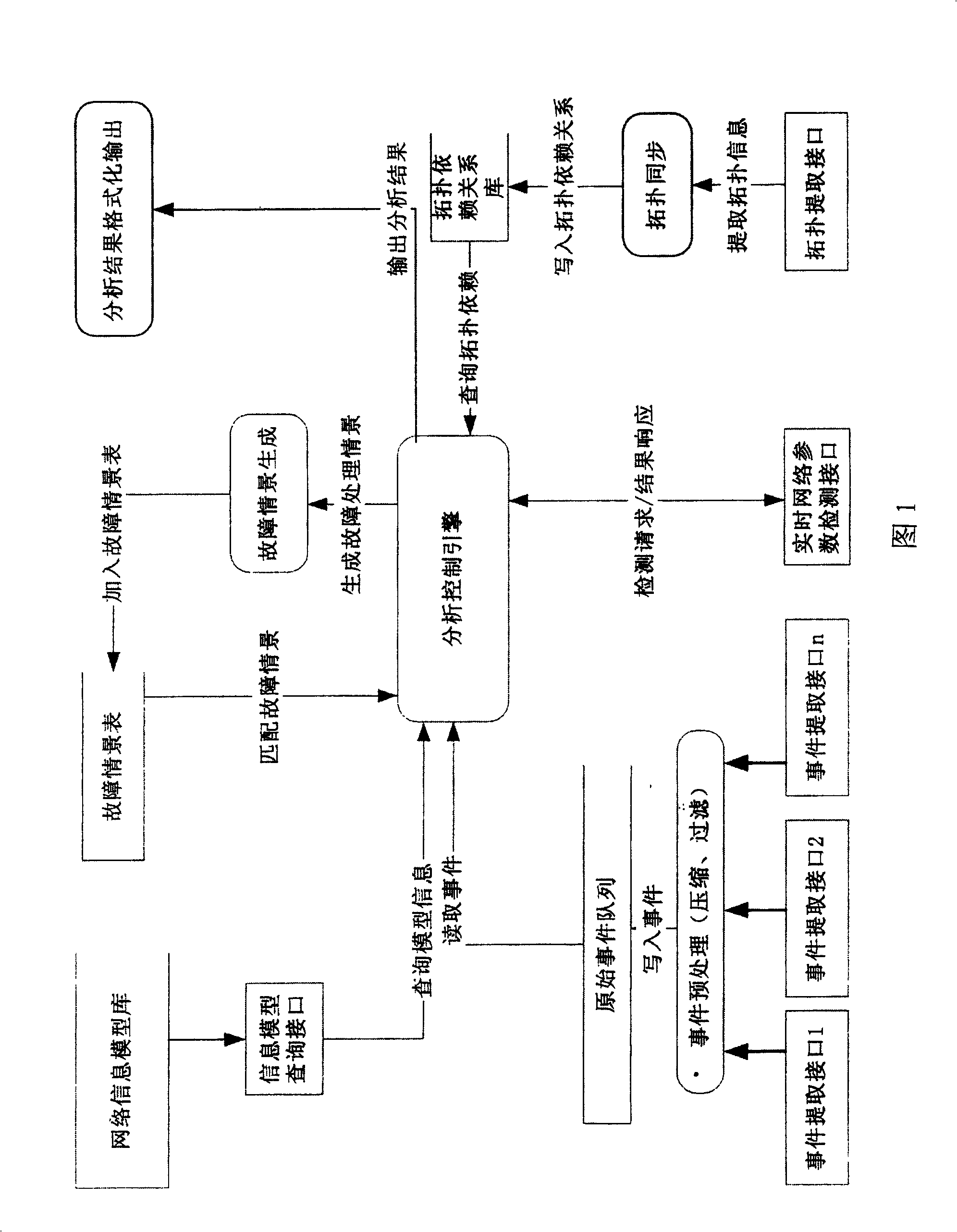
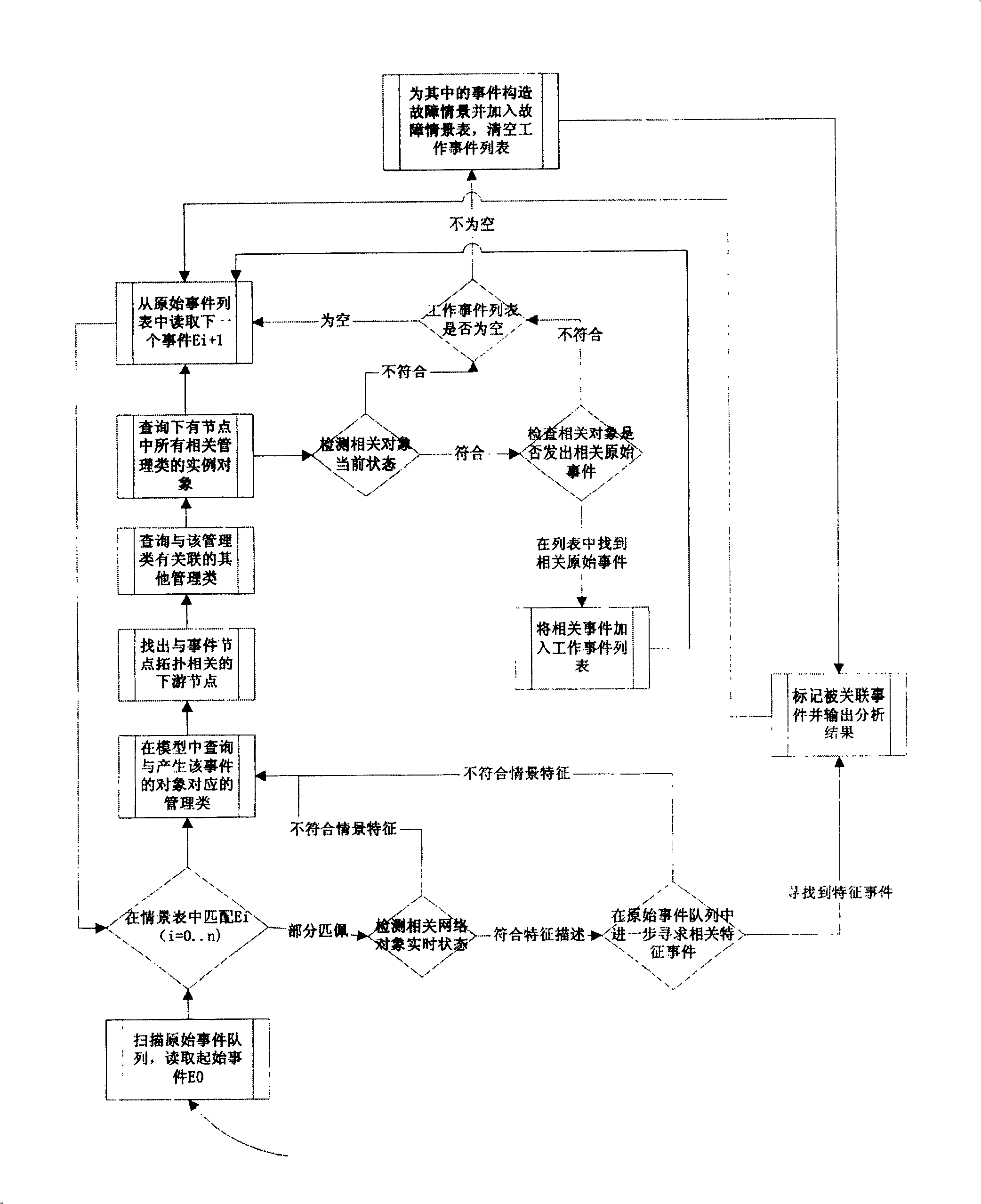
InactiveCN1529455AAvoid Correlation AnalysisEfficient identificationData switching networksTopology informationEvent level
Information of failure events from various network devices and service objects is written into original event list. Correlation analysis is carried out for events read by analyzing and controlling engine from the original event list according to levels of original event and selection of classes. The dynamic analytical algorithm synthetically handles information in each area such as scene of historical fault analysis, dynamic performance parameters of network, dynamic topology information and time character of event etc. comparing with prior art, the invention overcomes disadvantages of overlooking information of dynamic network state, dependent on preset rule and lack of auto study ability etc. The invented method provides effective correlation analysis, fault reason analysis and location in real time when storm of network fault happens.
Owner:HUAWEI TECH SERVICE
Method for event-based semantic classification
ActiveUS8611677B2Digital data processing detailsRelational databasesEvent levelClassification methods
A method of automatically classifying images in a consumer digital image collection, includes generating an event representation of the image collection; computing global time-based features for each event within the hierarchical event representation; computing content-based features for each image in an event within the hierarchical event representation; combining content-based features for each image in an event to generate event-level content-based features; and using time-based features and content-based features for each event to classify an event into one of a pre-determined set of semantic categories.
Owner:MONUMENT PEAK VENTURES LLC
Personalized automatic publishing extensible layouts
InactiveUS20050081148A1Natural language data processingSpecial data processing applicationsPersonalizationDocumentation generator
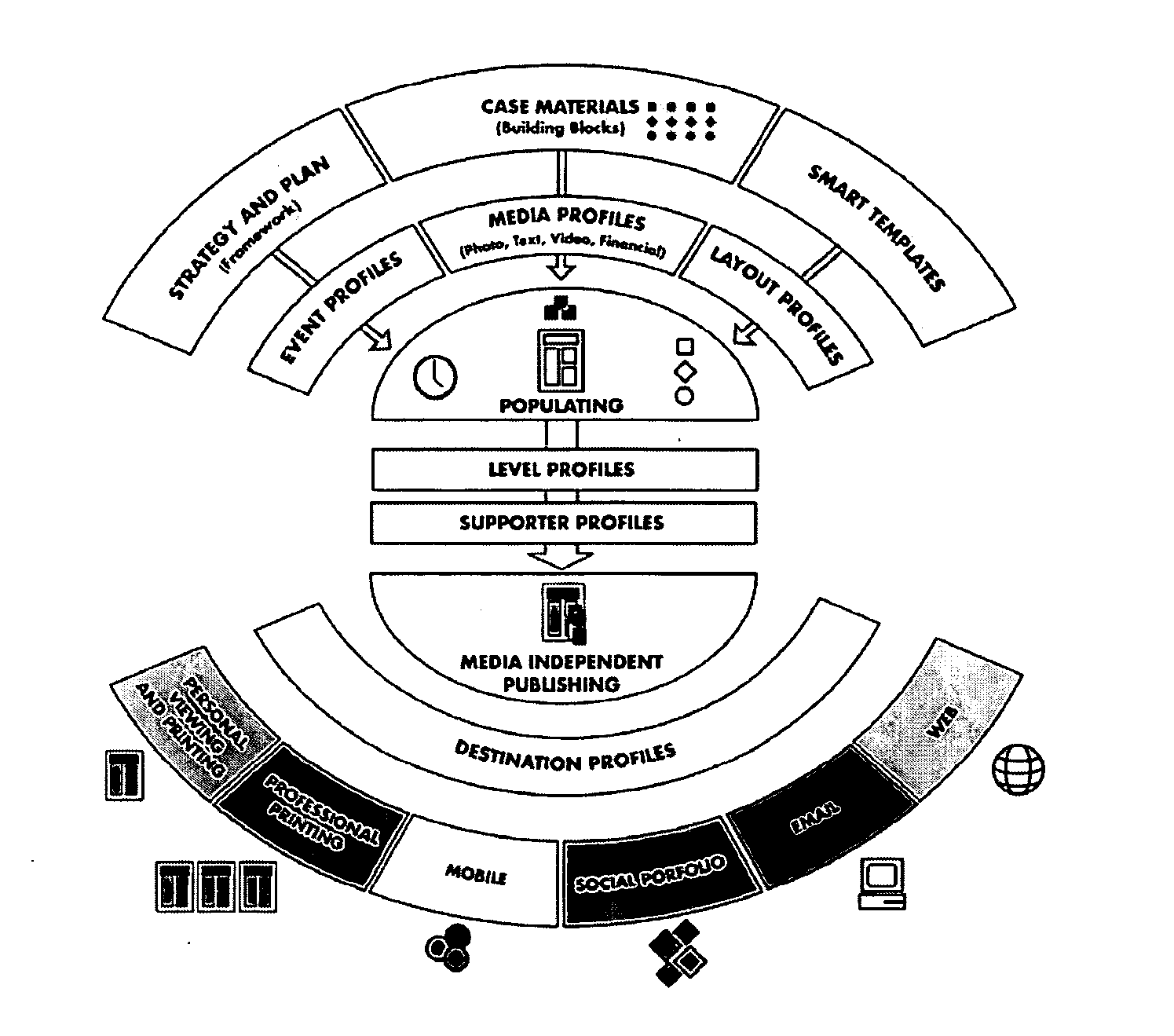
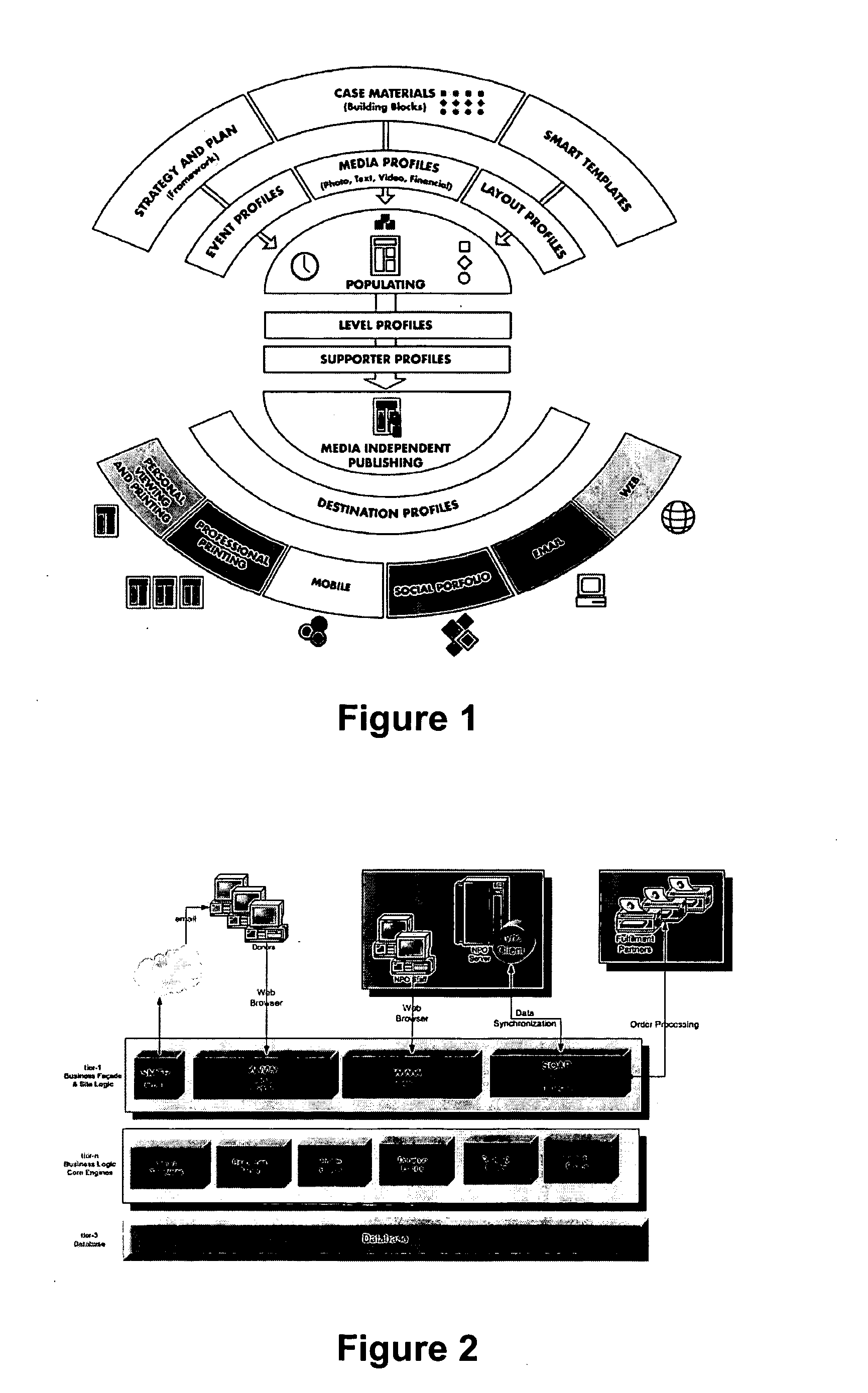
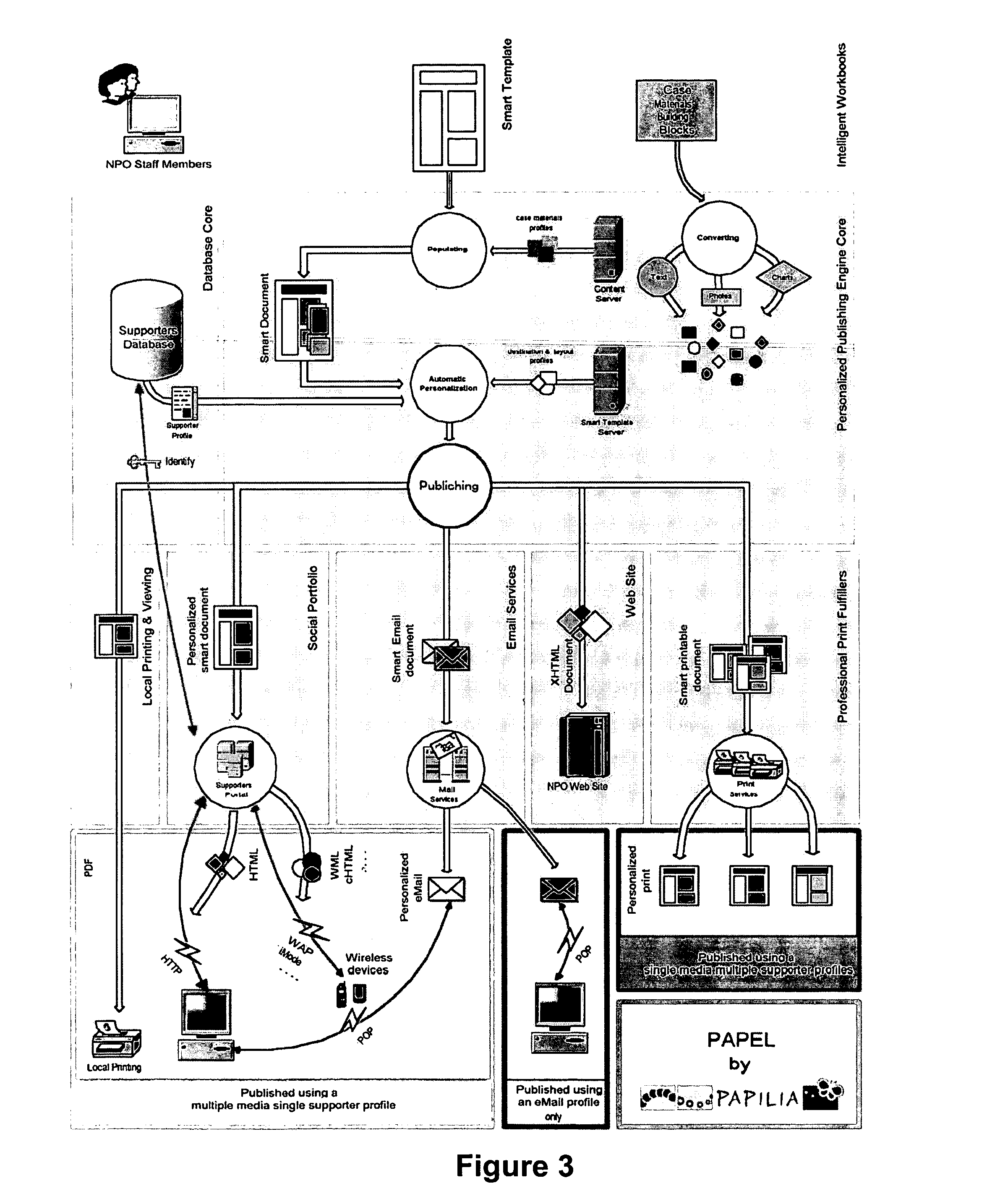
A software-based system automatically generates personalized communications including arrangements for communicating with various databases, servers and client systems. A smart templates document generator uses multiple categories and types of profiles such as case materials, destination and layout, and supporter profiles, as well as event, level and document profiles. The system further utilizes substantially or completely media independent communications of materials involving database and communications software architectures, input device / output display synchronization techniques, and graphics rendering software implementations.
Owner:PAPILIA PATENTS
Method and apparatus for assigning value to an item donated to an on-line charitable auction or fund raising event
The present invention discloses methods, systems, and program code that enable a nonprofit organization to manage its fundraising activities online. Disclosed are methods and systems for providing online hosting of fundraising auctions, and auction services such as maintaining donor / bidder registries, bid tracking, processing credit cards, and auction closeout activities. Also disclosed are a plurality of on-line, web-based tools, including tools for: 1) building a customized homepage reflecting the look and feel of the nonprofit organization; 2) building a customized catalog that allows for easy addition of items and pictures; and 3) enhanced email messaging that lets a nonprofit organization reach its constituents. According to the invention, the system enables an auction administrator to enable, at the global event level or on a per item basis, the ability for donors and / or buyers in an auction to assign either the value of an item or the final selling price of an item to a specific chapter of an organization or to a specific organization when multiple organizations are participating in a common auction. Alternatively, a buyer or donor can specify a fraction or percentage of the value or selling price such that multiple causes, chapters, or organizations may receive partial credit on the donation or sale of an item.
Owner:C-MARKET
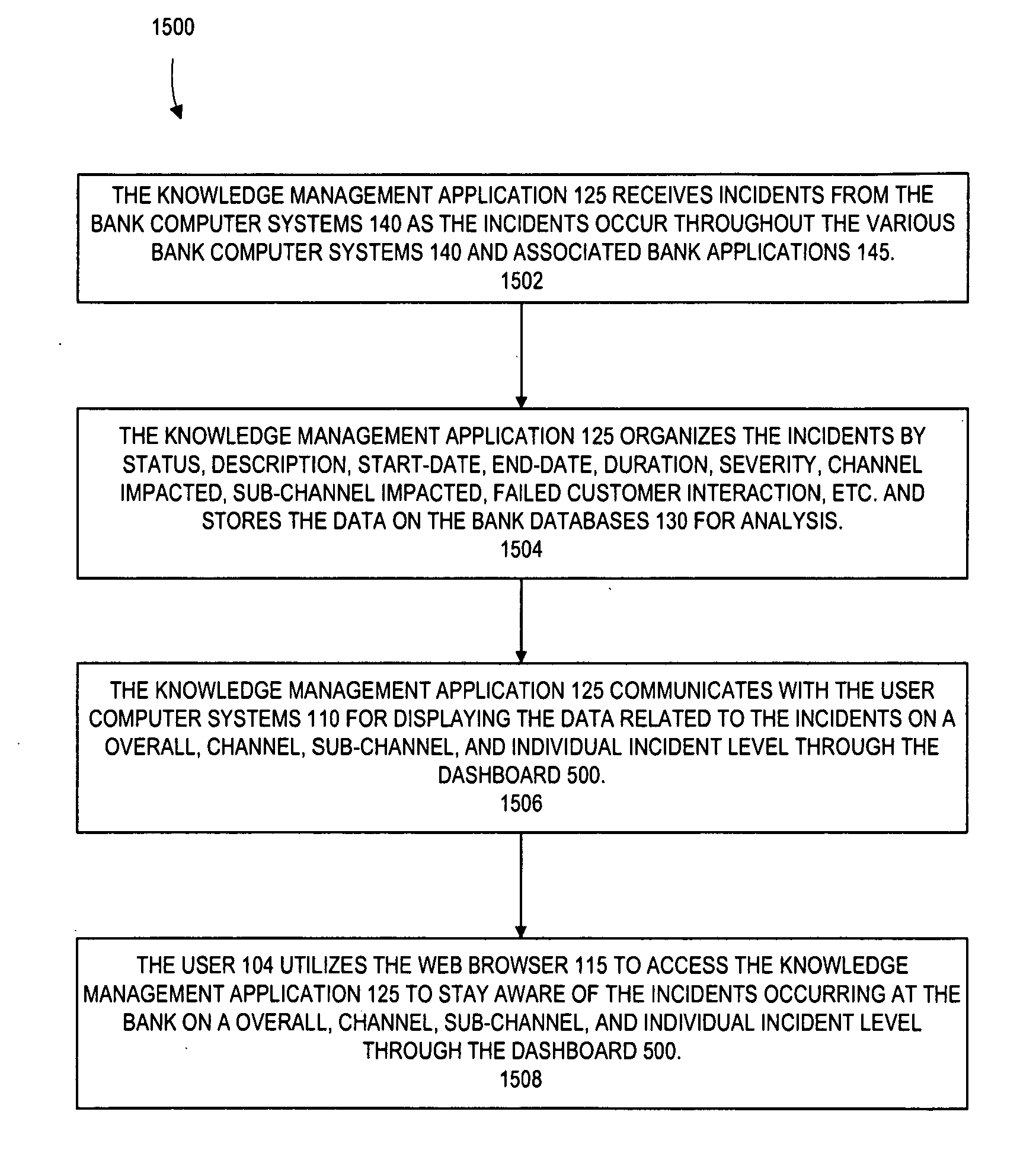
Performance dashboard monitoring for the knowledge management system
Embodiments of the present invention provide a method, system, computer program product, or a combination of the foregoing for creating a knowledge management system including a performance dashboard monitoring system that is standardized and centralized across the channels and sub-channels in an organization. The performance dashboard monitoring system is used to track, measure, and resolve incidents that occur throughout the channels, sub-channels, systems, and applications of an organization. The system receives information related to two or more incidents, where each incident is associated with one or more of a business channel, sub-channel, or application. The system stores the information on a memory device. The system tracks the status of at least one incident between the occurrence and the resolution of the incident. The system displays on a user interface the information related to the incident on a channel, sub-channel, application, or individual incident level.
Owner:BANK OF AMERICA CORP
Automatic Attribute Level Detection Methods
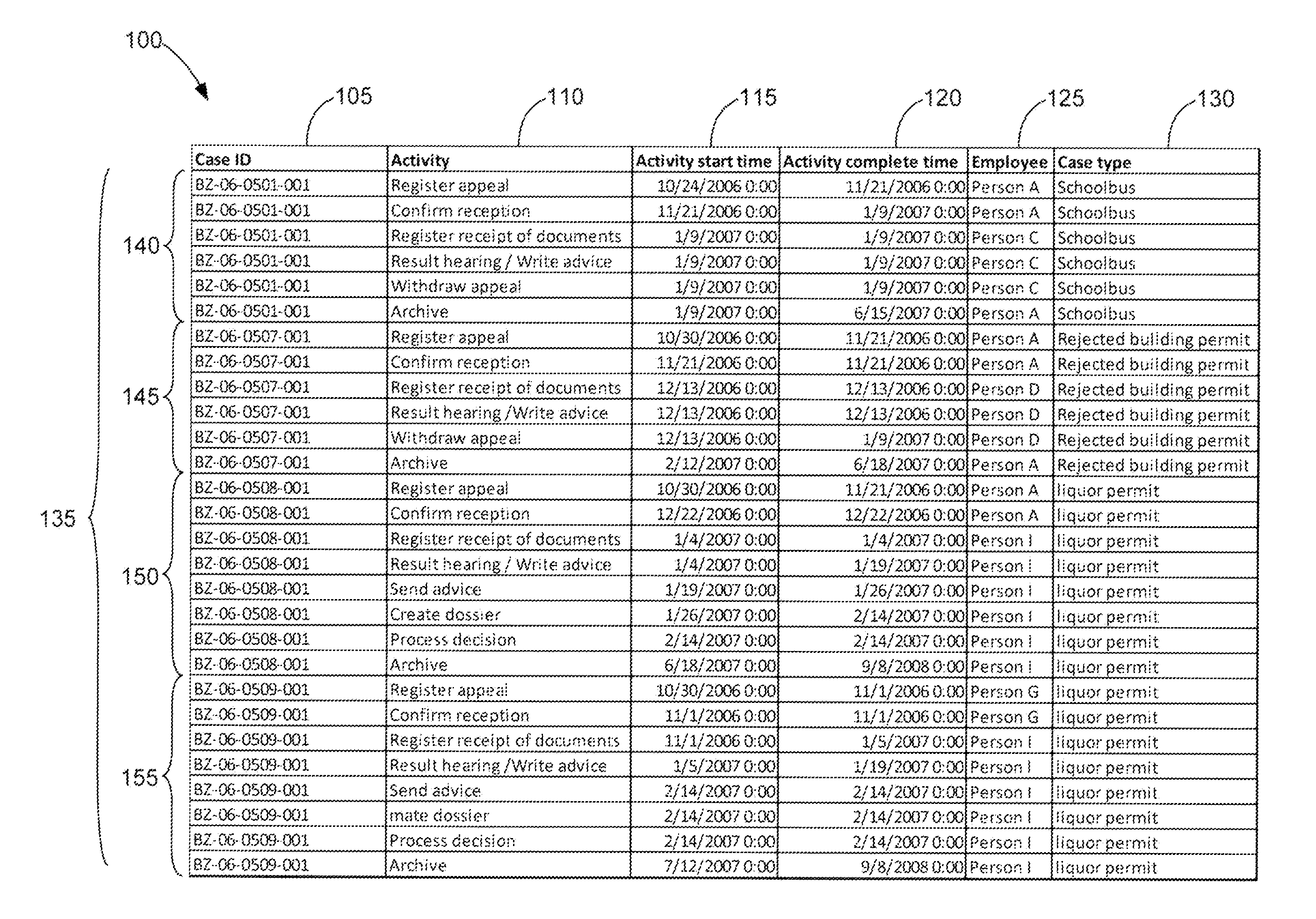
A method of detecting attribute levels in a dataset that includes determining whether column data in a column for a case identifier is the same, classifying the column data as case level attributes if all of the column data is identical, and classifying the column data as event level attributes if the column data is different for at least one data entry in the column.
Owner:LEXMARK INT TECH
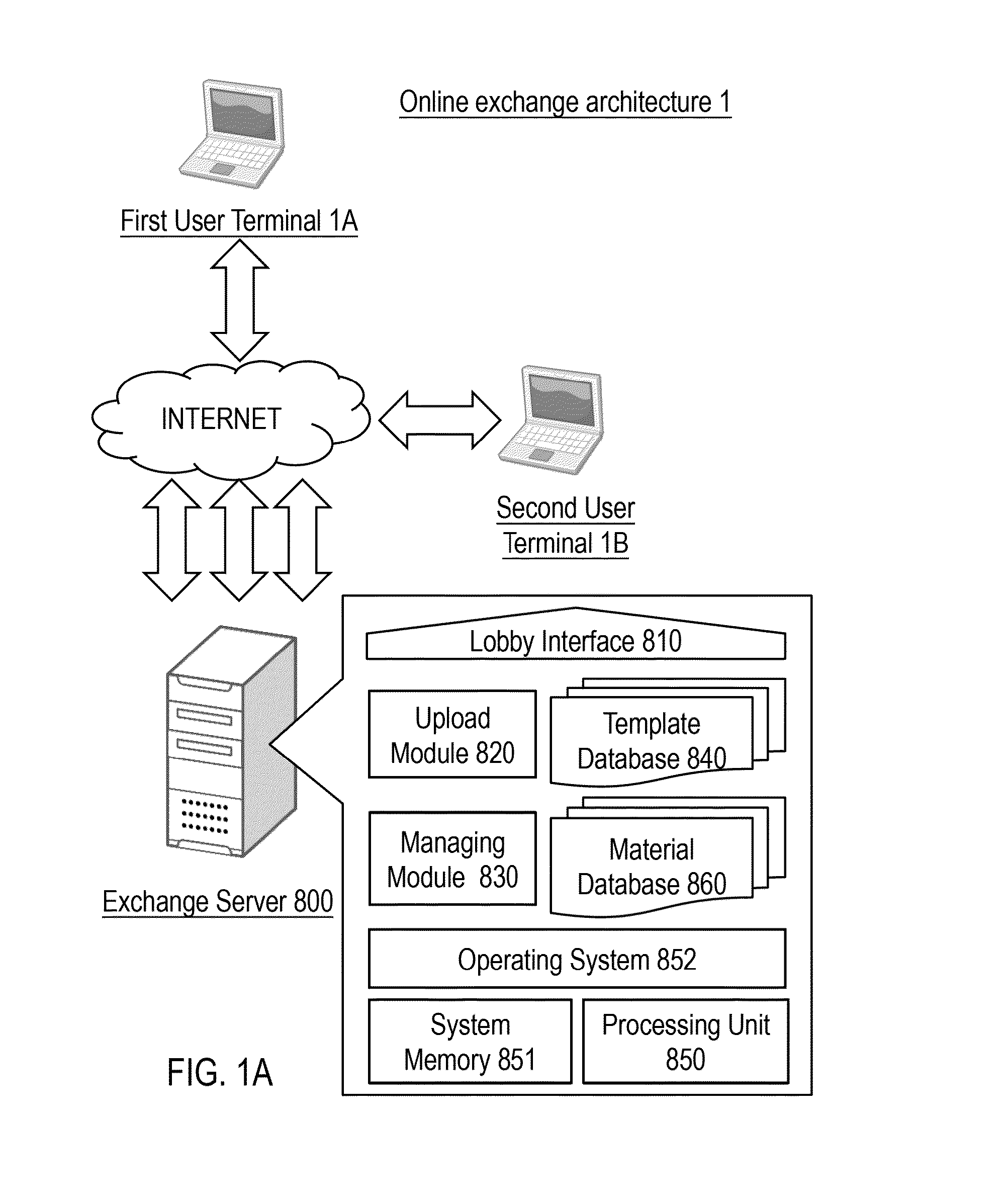
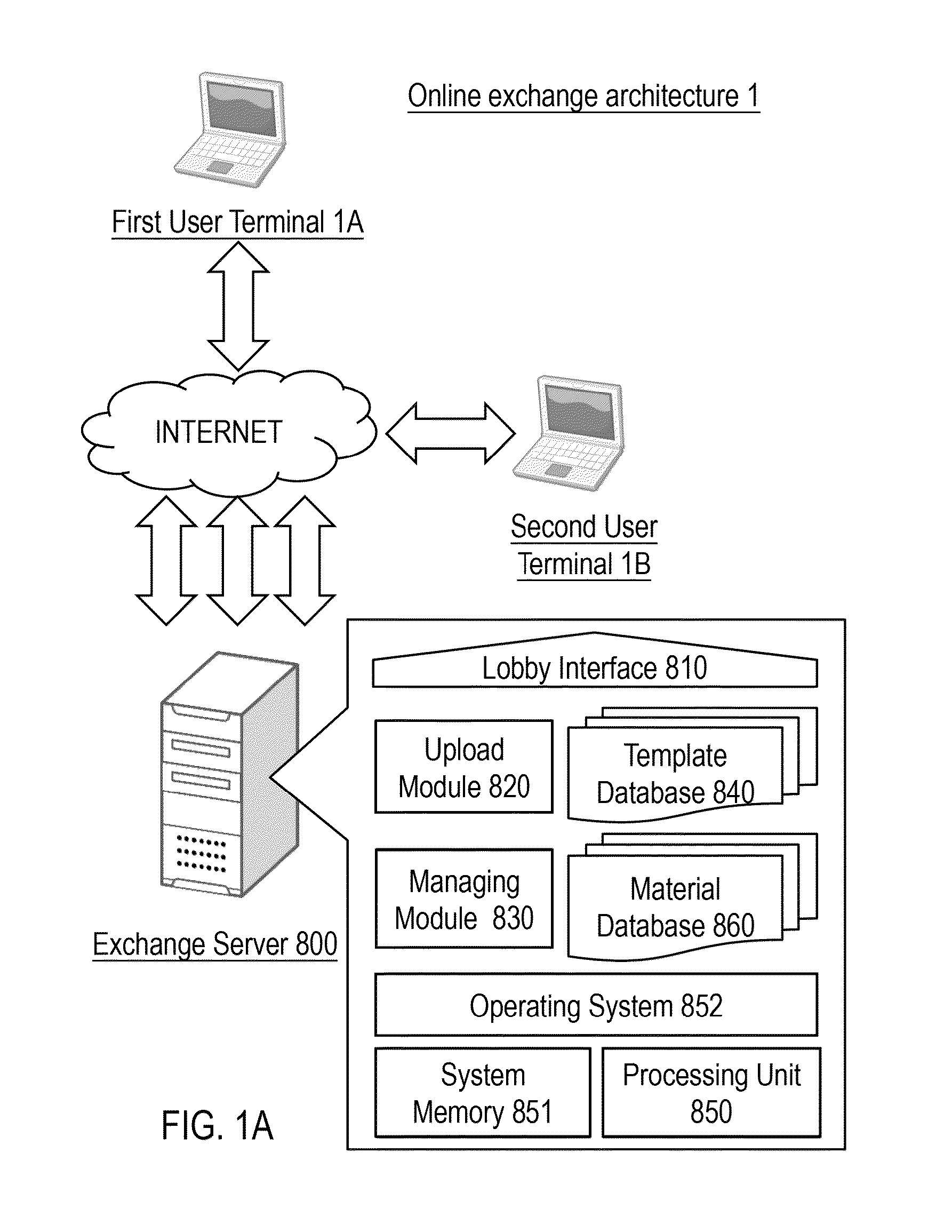
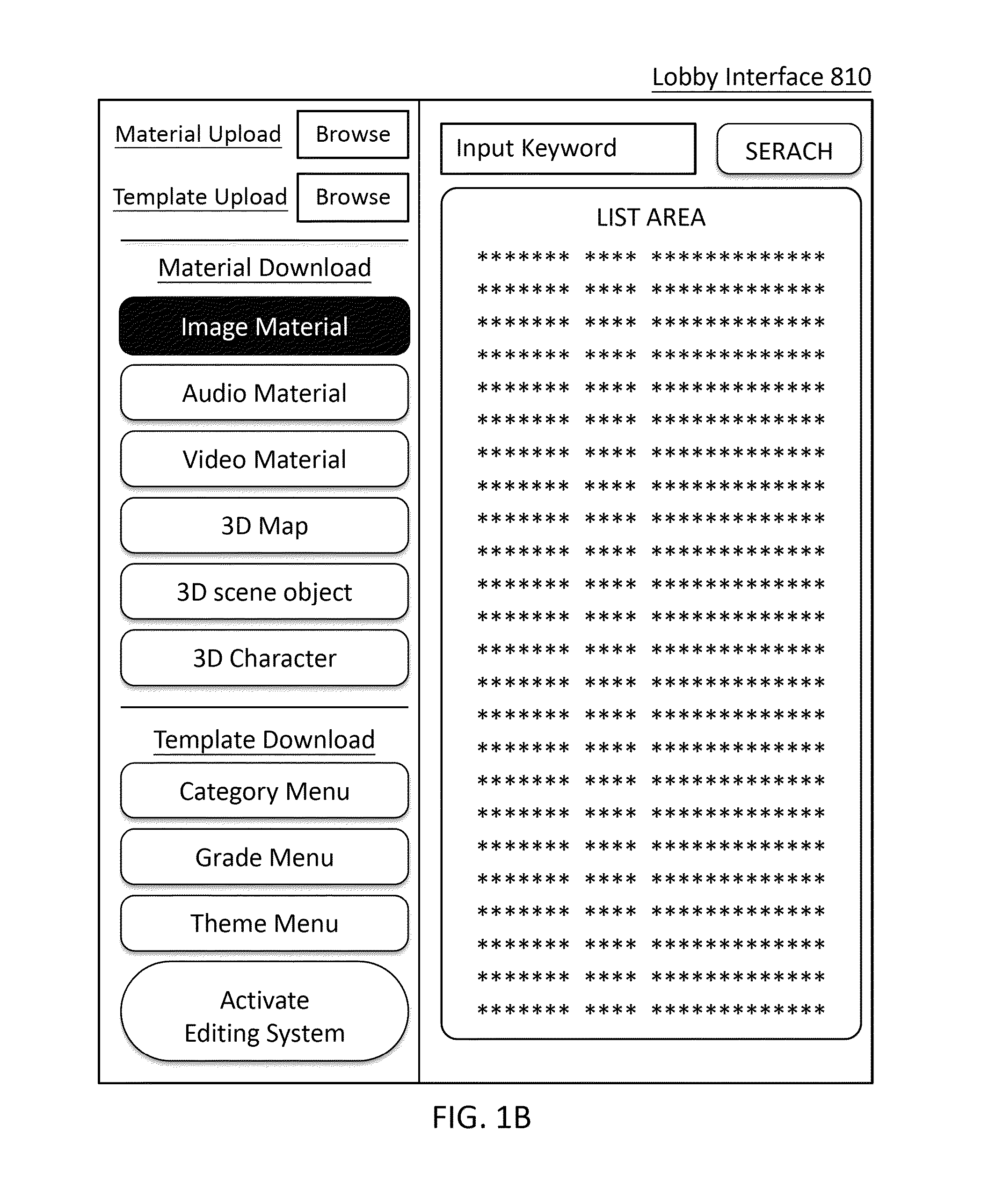
System and method for editing interactive three-dimension multimedia, and online editing and exchanging architecture and method thereof
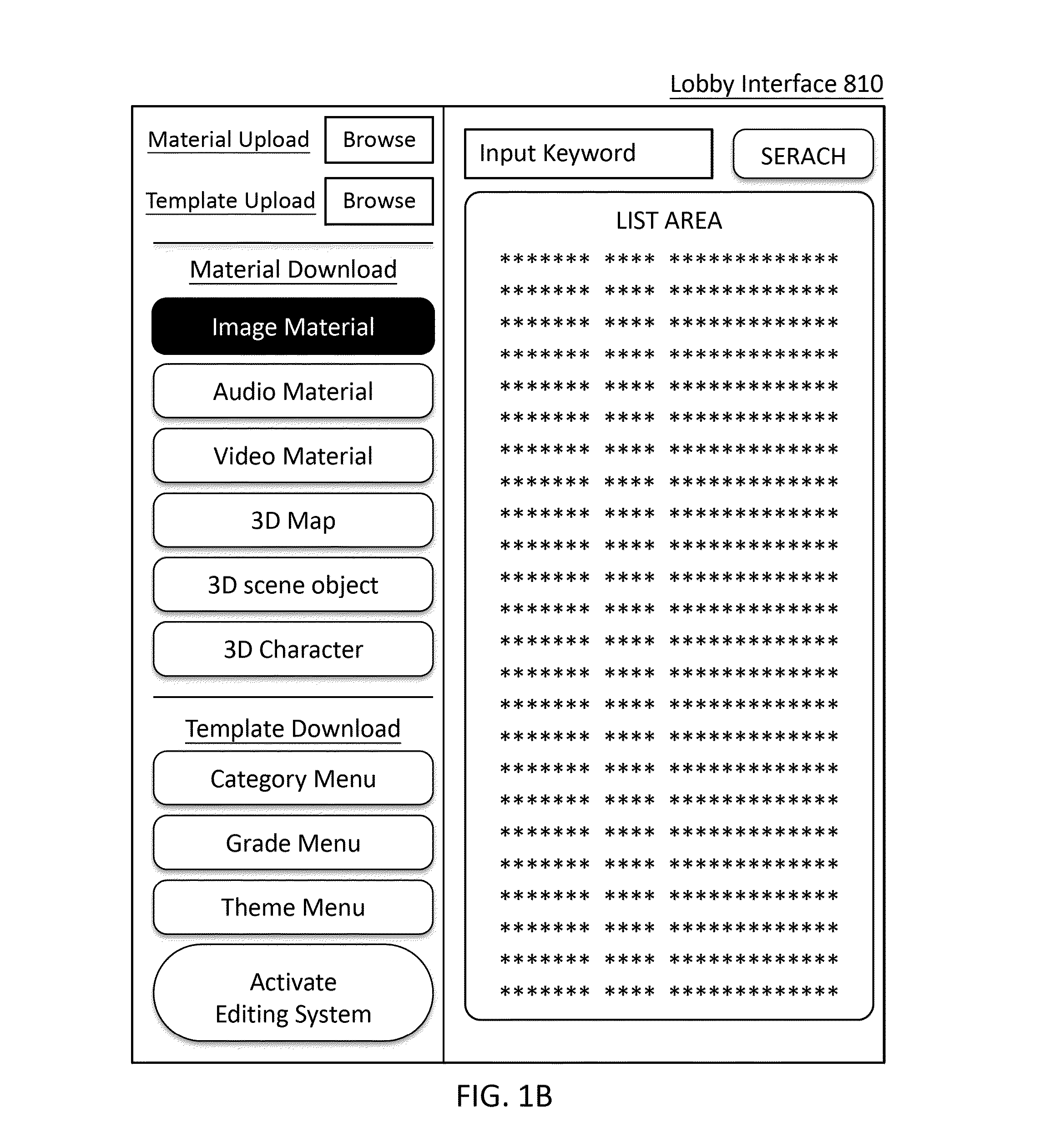
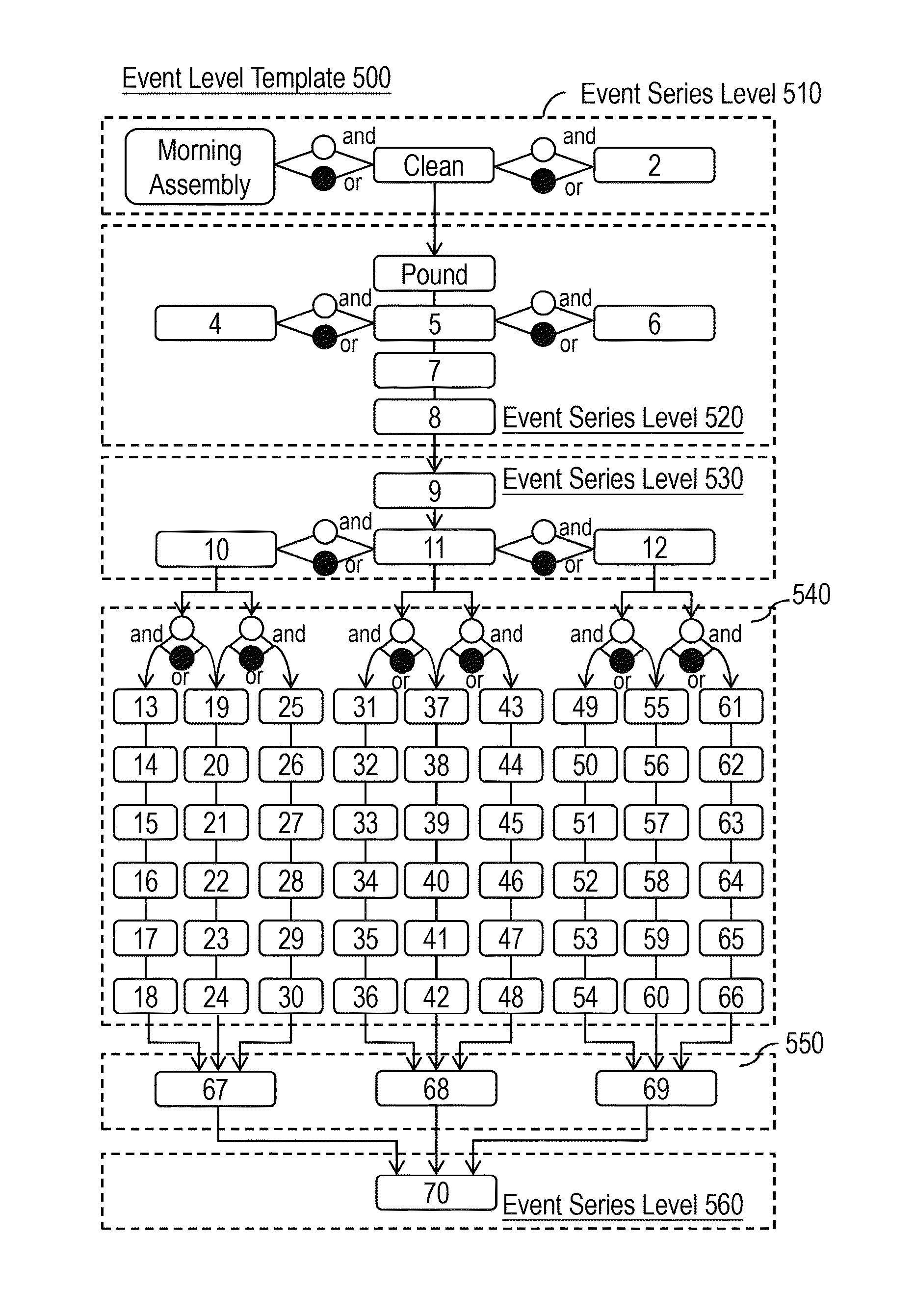
ActiveUS20130007669A1Indoor gamesElectronic editing digitised analogue information signalsEvent levelUser interface
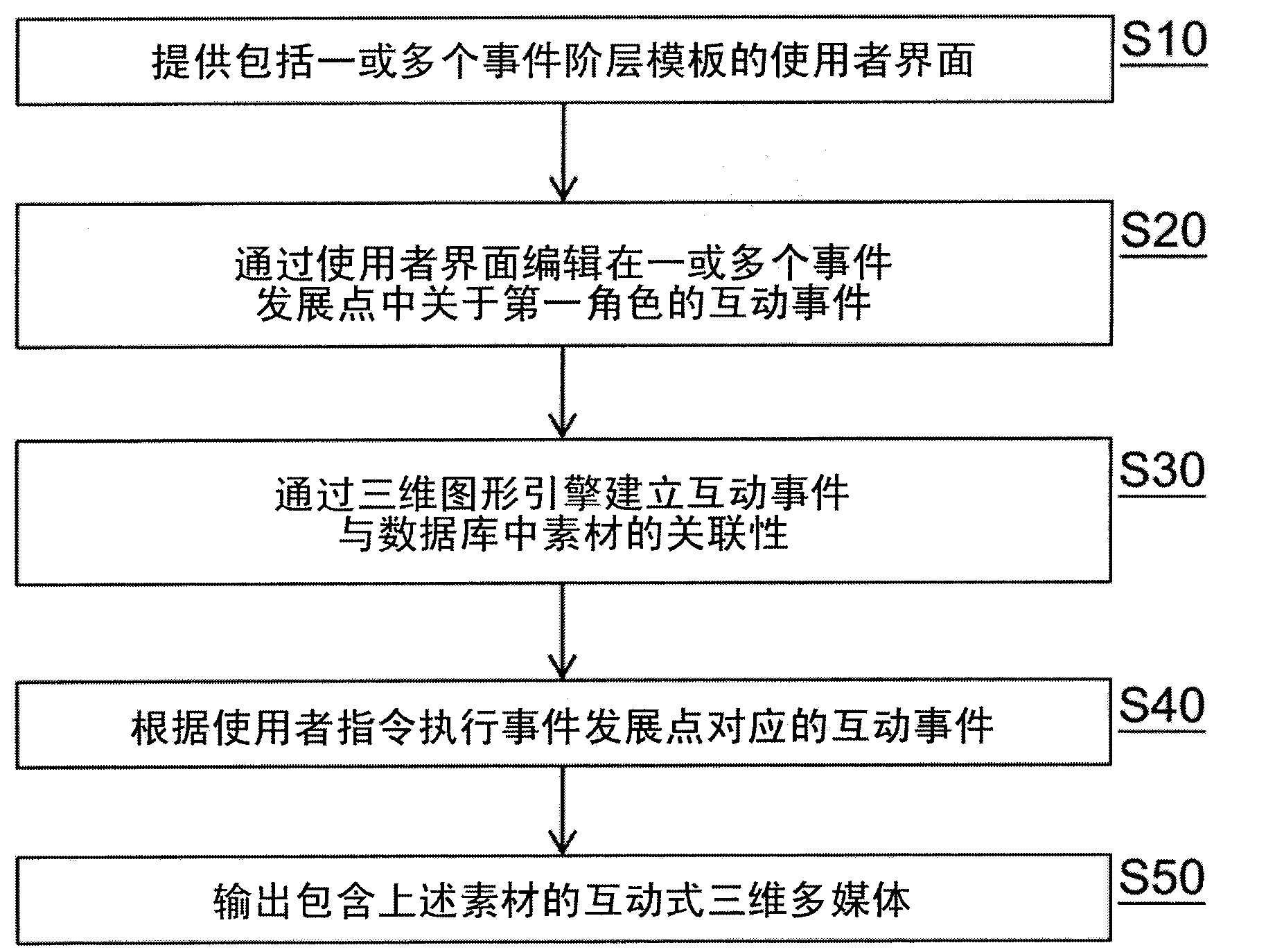
A system and method are provided to edit interactive three-dimensional multimedia. A user interface of the system is provided with an event level template that includes event series levels with multiple event developing points. Through the user interface, multiple interactive events related to a first character of the event developing point are edited. Through a three-dimensional engine, interactive relevances are built up between interactive events and multiple materials inside one or more database. When the interactive three-dimensional multimedia with multiple materials is output, the interactive events corresponding to the event developing points are performed according to a user command. An online editing and exchanging method integrated with the system and method is also provided to share pre-edited templates on an exchange server; each of the pre-edited templates is extracted from an interactive three-dimensional multimedia pre-edited by the system and method.
Owner:YU LING LU +1
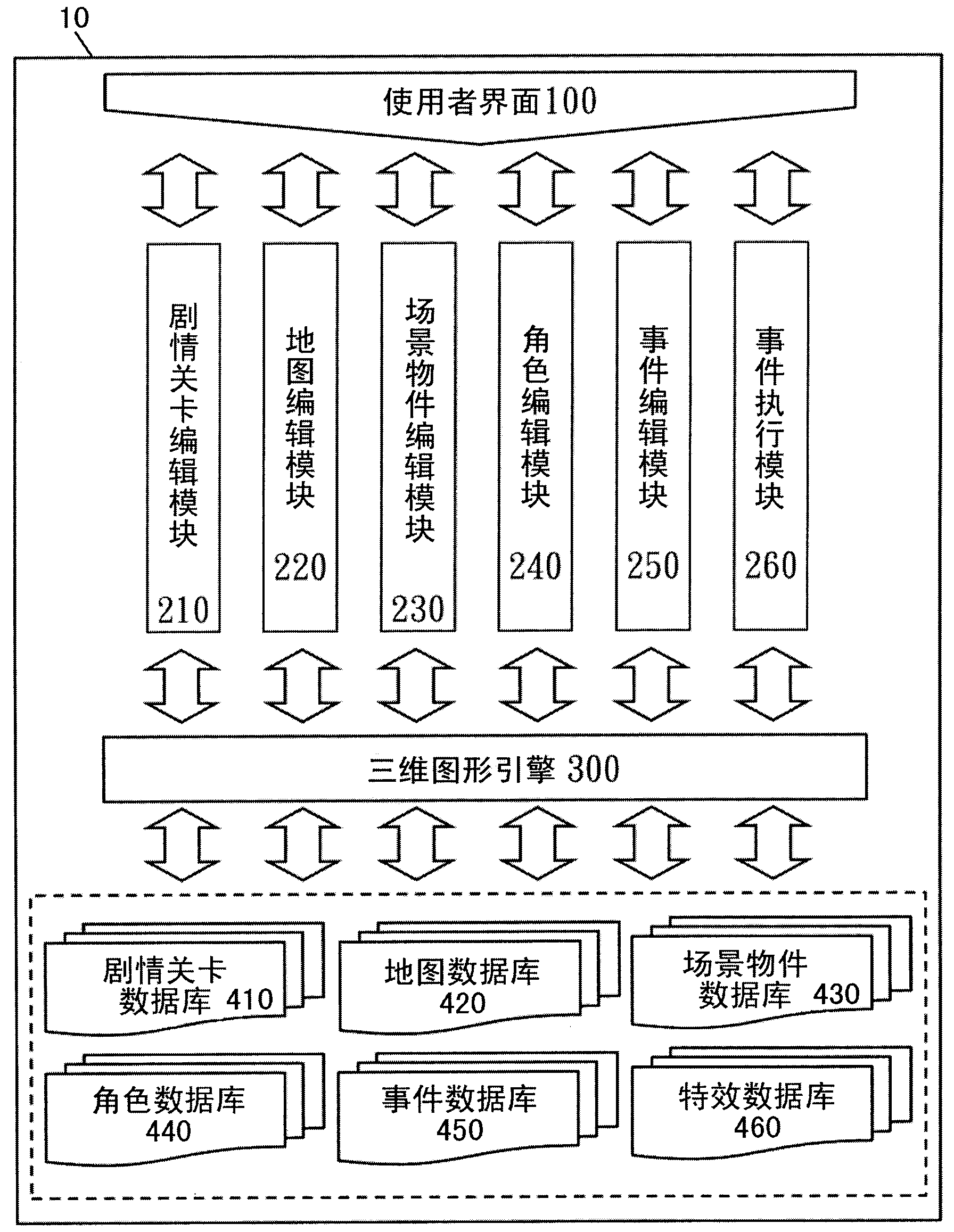
System and method for editing interactive three-dimension multimedia, and computer-readable medium
The invention relates to a system and a method for editing interactive three-dimension multimedia, and a computer-readable medium. A user interface is provided with an event level template that includes event series levels with multiple event developing points. Through the user interface, one or more interactive events related to a first character of the event developing point are edited. Through a three-dimensional image engine, interactive relevance is built up between the interactive events and multiple materials in multiple databases. When the interactive three-dimensional multimedia with the materials is output, the interactive events corresponding to the event developing points are performed according to a user command.
Owner:卢玉玲
Cloud computing cluster mixing job scheduling method and device, server and storage device
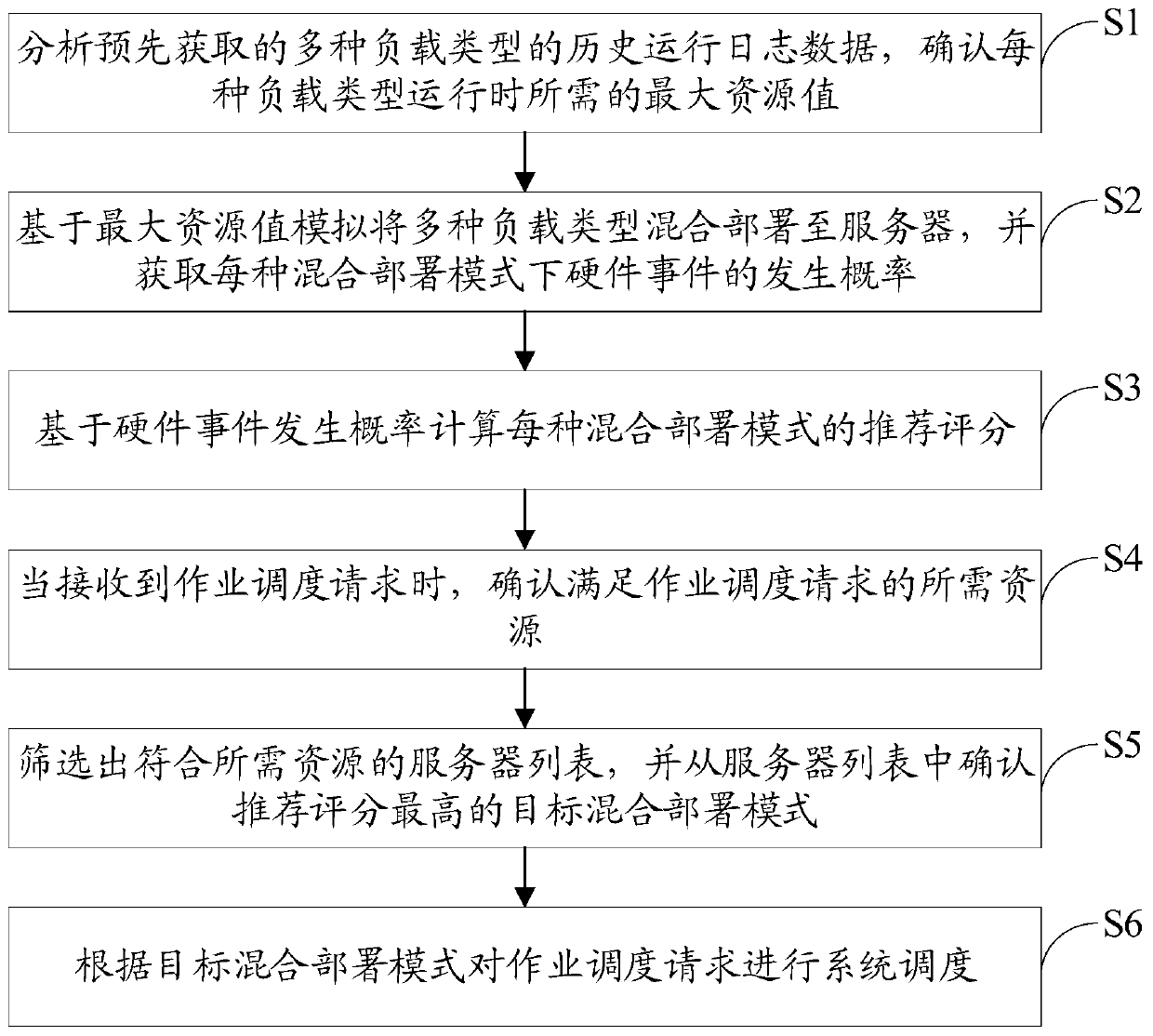
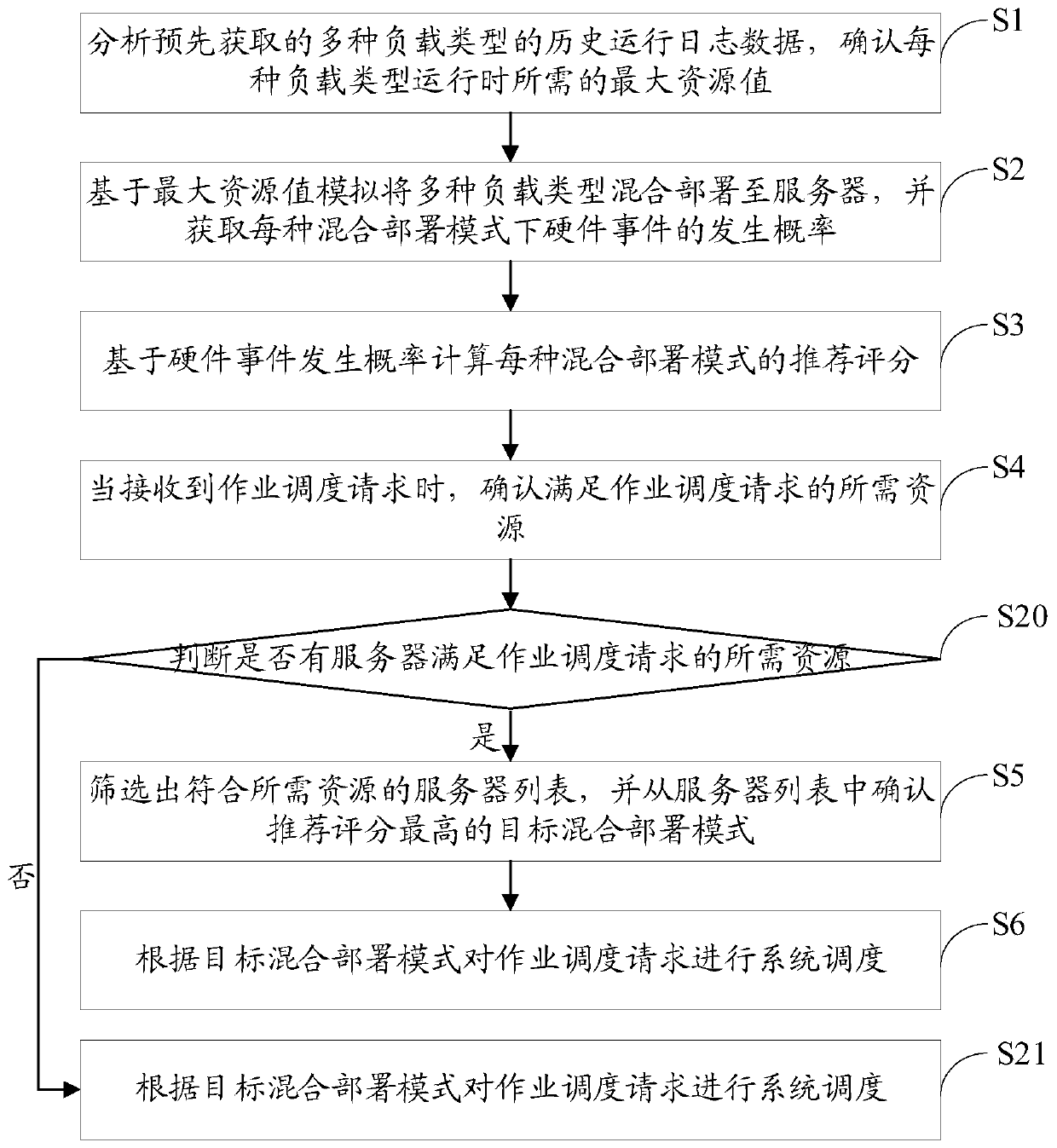
ActiveCN110908795AAvoid ability to declineImprove resource utilizationResource allocationEnergy efficient computingOperation schedulingEvent level
The invention discloses a cloud computing cluster hybrid job scheduling method and device, a server and a storage device, and the method comprises: analyzing the historical operation log data of a plurality of types of loads obtained in advance, and determining the maximum resource value needed during the operation of each load type; simulating and deploying multiple load types to a server in a mixed manner based on the maximum resource value, and obtaining the occurrence frequency of a hardware event in each mixed deployment mode; calculating a recommendation score of each hybrid deployment mode based on the occurrence frequency of the hardware event; when a job scheduling request is received, confirming required resources meeting the job scheduling request; screening out a server list conforming to the required resources, and determining a target hybrid deployment mode with the highest recommendation score from the server list; and performing system scheduling on the job scheduling request according to the target hybrid deployment mode. The job scheduling request is subjected to double-layer hybrid deployment on the resource level and the hardware event level, so that the overallresource utilization rate of the cloud server is improved.
Owner:SHENZHEN INST OF ADVANCED TECH
A text classification algorithm that combines statistical features and Attention mechanism
InactiveCN109325114ARich semantic featuresReduce training timeSemantic analysisSpecial data processing applicationsEvent levelComputation complexity
The invention relates to a text classification algorithm which combines statistical features and an Attention mechanism, and the Attention mechanism has been gradually applied to the field of naturallanguage processing. The prior method greatly increases the calculation amount when calculating the Attention weight value, and the invention proposes that the Attention weight value is calculated atthe structured event level. On the one hand, events contain richer semantics than words or phrases; On the other hand, the event-based Attention mechanism reduces computational complexity. At the sametime, statistical features are added to the calculation of Attention weights. Compared with the existing model, the semantic information contained in the event structure and the corresponding statistical features improve the quality of text vector representation and achieve better classification performance. The classification accuracy is evaluated, and the experimental results show that the model not only reduces the training time, but also achieves better results.
Owner:WUHAN UNIV OF TECH
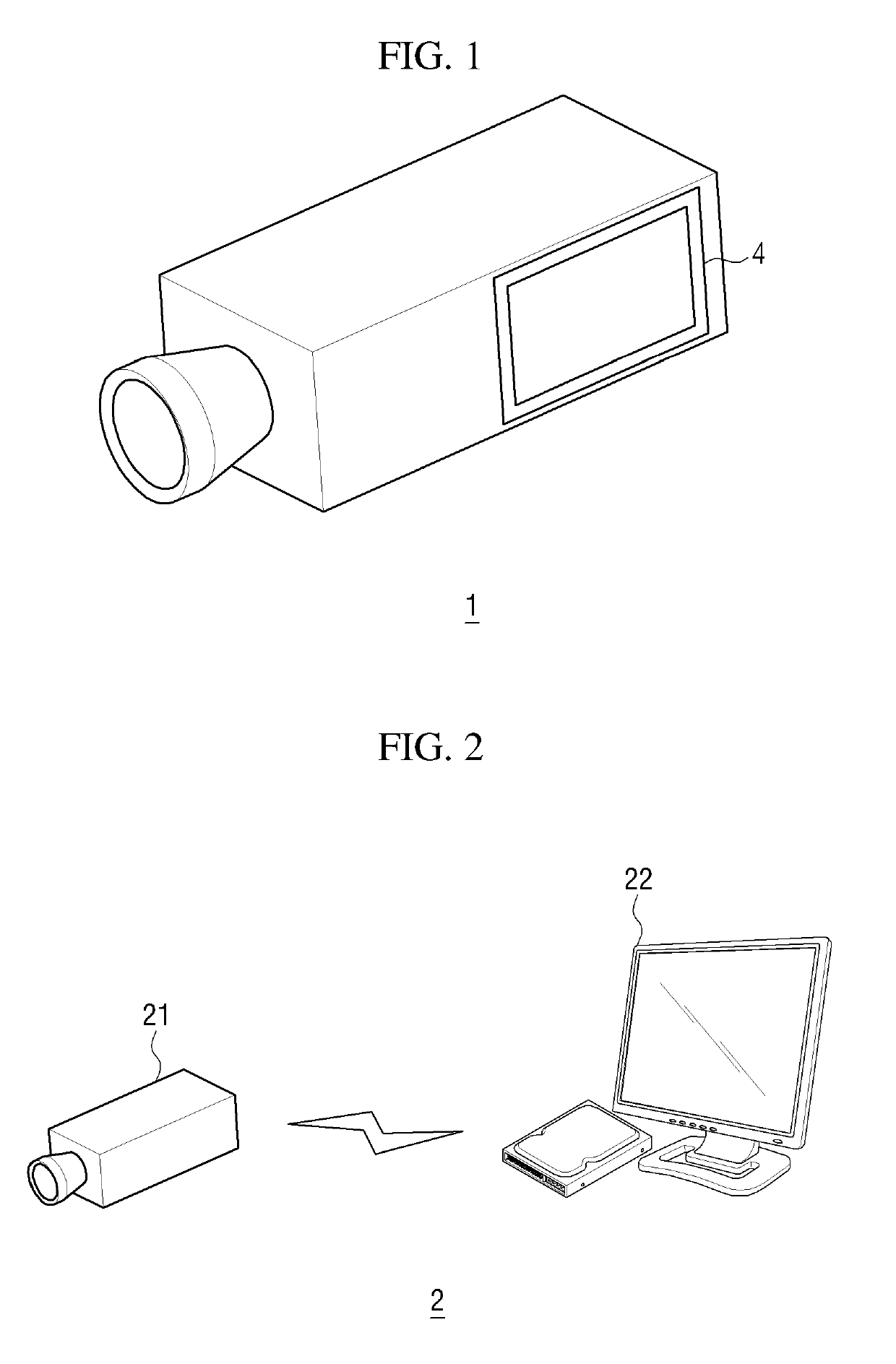
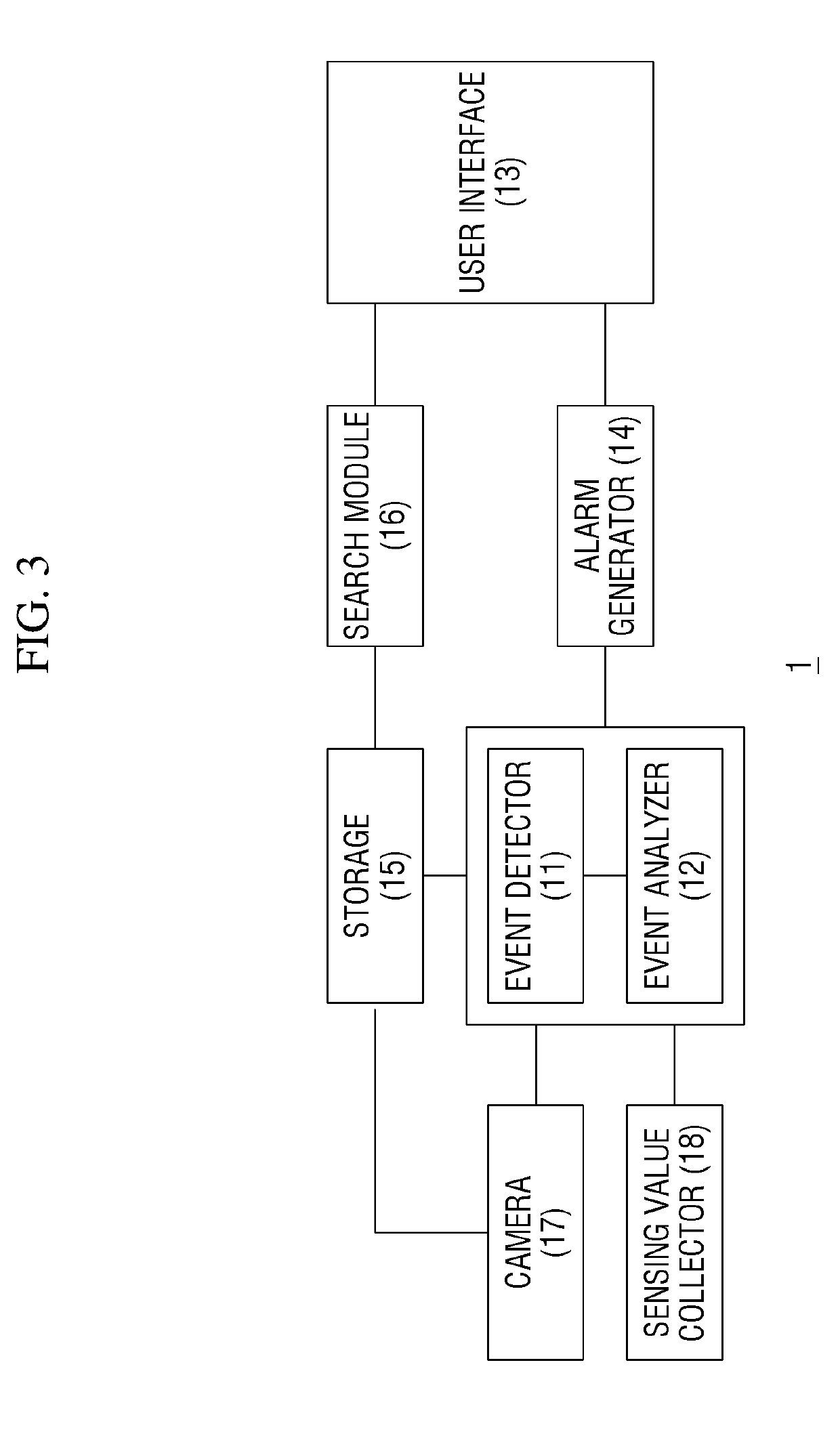
Image capturing apparatus with variable event detecting condition
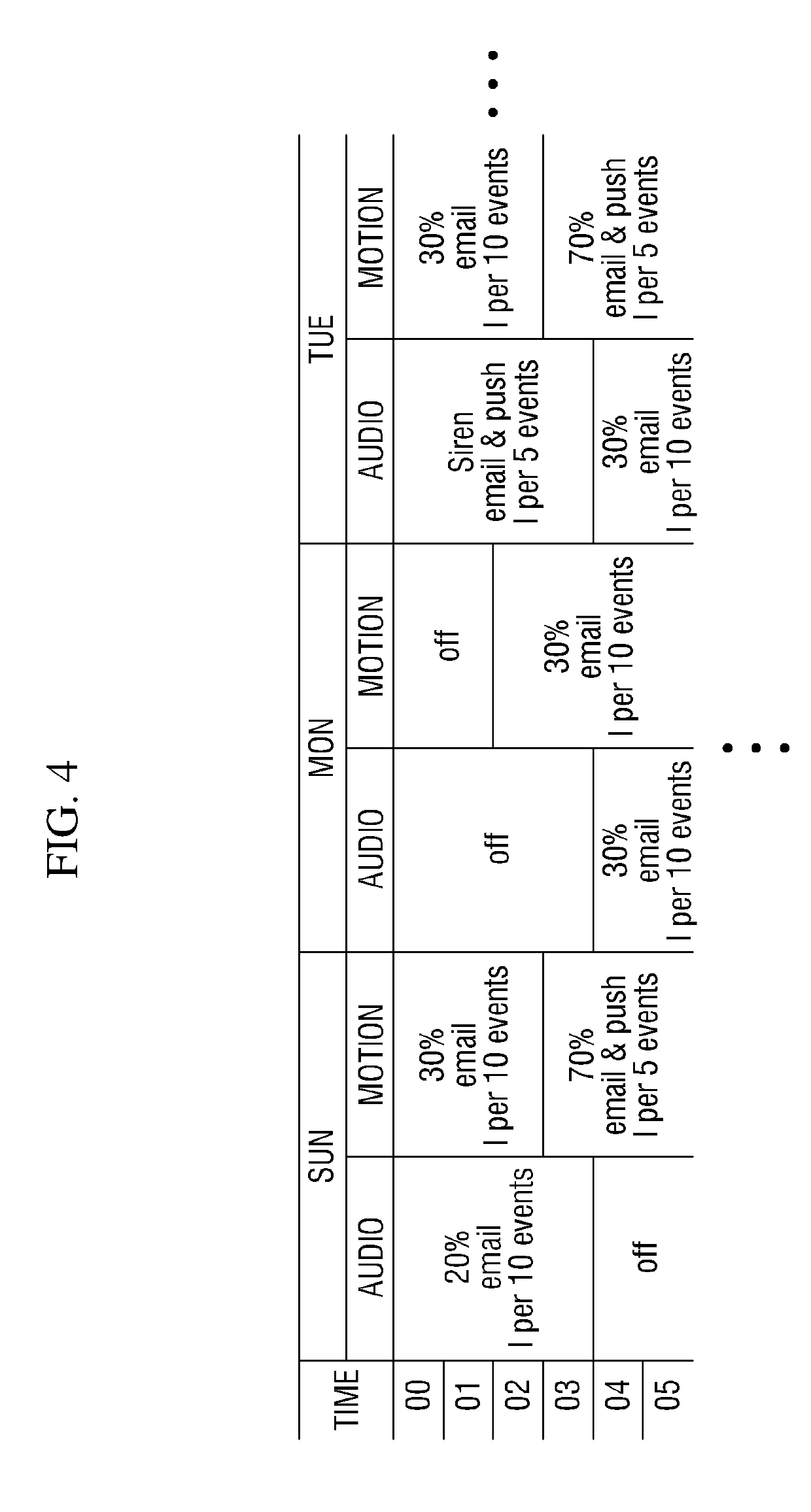
ActiveUS20190295393A1Prevent excessive numberAdjustable frequencyTelevision system detailsVideo data queryingEvent levelImage capture
Provided are an event storage device, an event search device, and an event alarm device for an event occurring in a surveillance area. The event storage device includes a processor and a memory and its operation is controlled by the processor. The processor is configured to receive images captured in a surveillance area, detect an event generated in the surveillance area, storing, in the memory, an image related to the event, among the captured images, and storing an event level of the detected event along with the stored image.
Owner:HANWHA VISION CO LTD
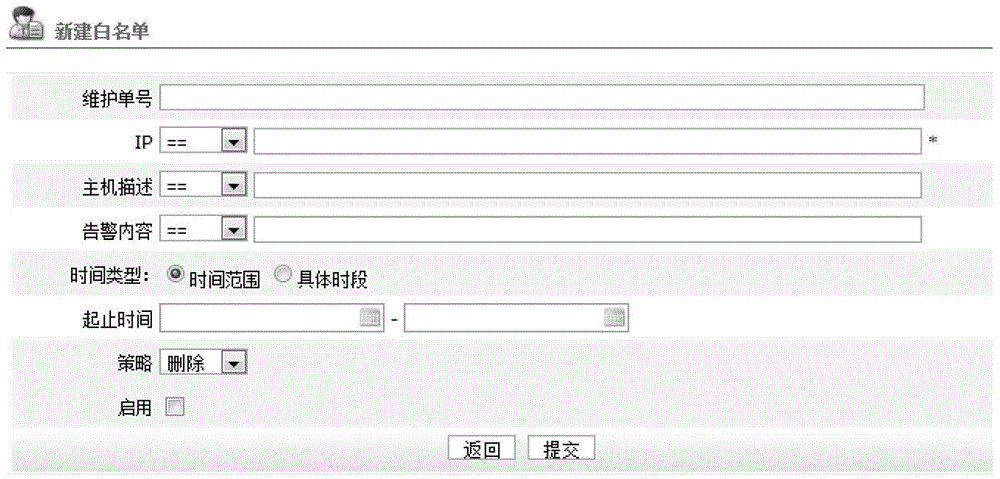
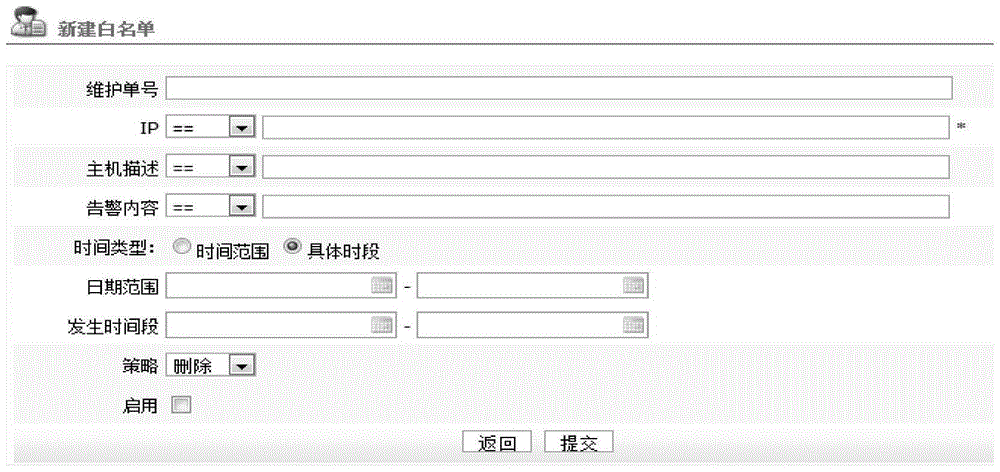
Data center operation and maintenance monitoring and alarming white list system
The invention provides a data center operation and maintenance monitoring and alarming white list system, which comprises an IP module, an alarming content module, a time type module and a strategy module, wherein the IP module is provided for a user to fill alarming event IP addresses in need of filtering and screen alarming events in need of filtering; the alarming content module is provided for the user to fill alarming contents of the alarming events in need of filtering and screen alarming events comprising the filled alarming contents; the time type module is provided for the user to select a time range or a particular time period, a white list system validation time period is set, and the alarming events in need of filtering which are screened in the validation time period are always shielded; and the strategy module is provided for the user to set an event level for the alarming events in need of filtering and adopt a corresponding filter strategy. The system of the invention has the advantages that one white list system only needs to be set, alarming shielding can be realized, alarming records can be stored for enabling the user to check, the operation is convenient and quick, and the data processing pressure is lessened.
Owner:长威信息科技发展股份有限公司
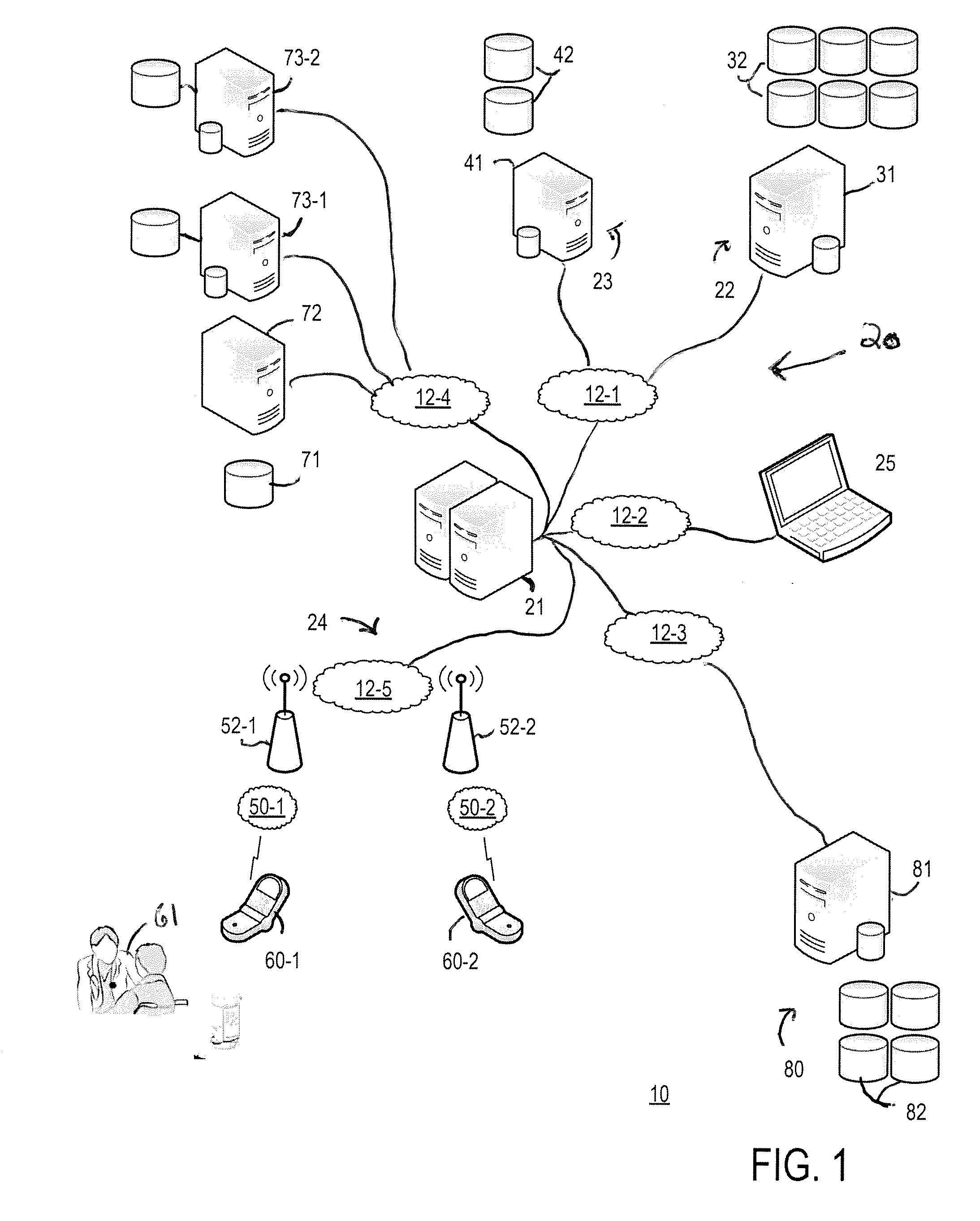
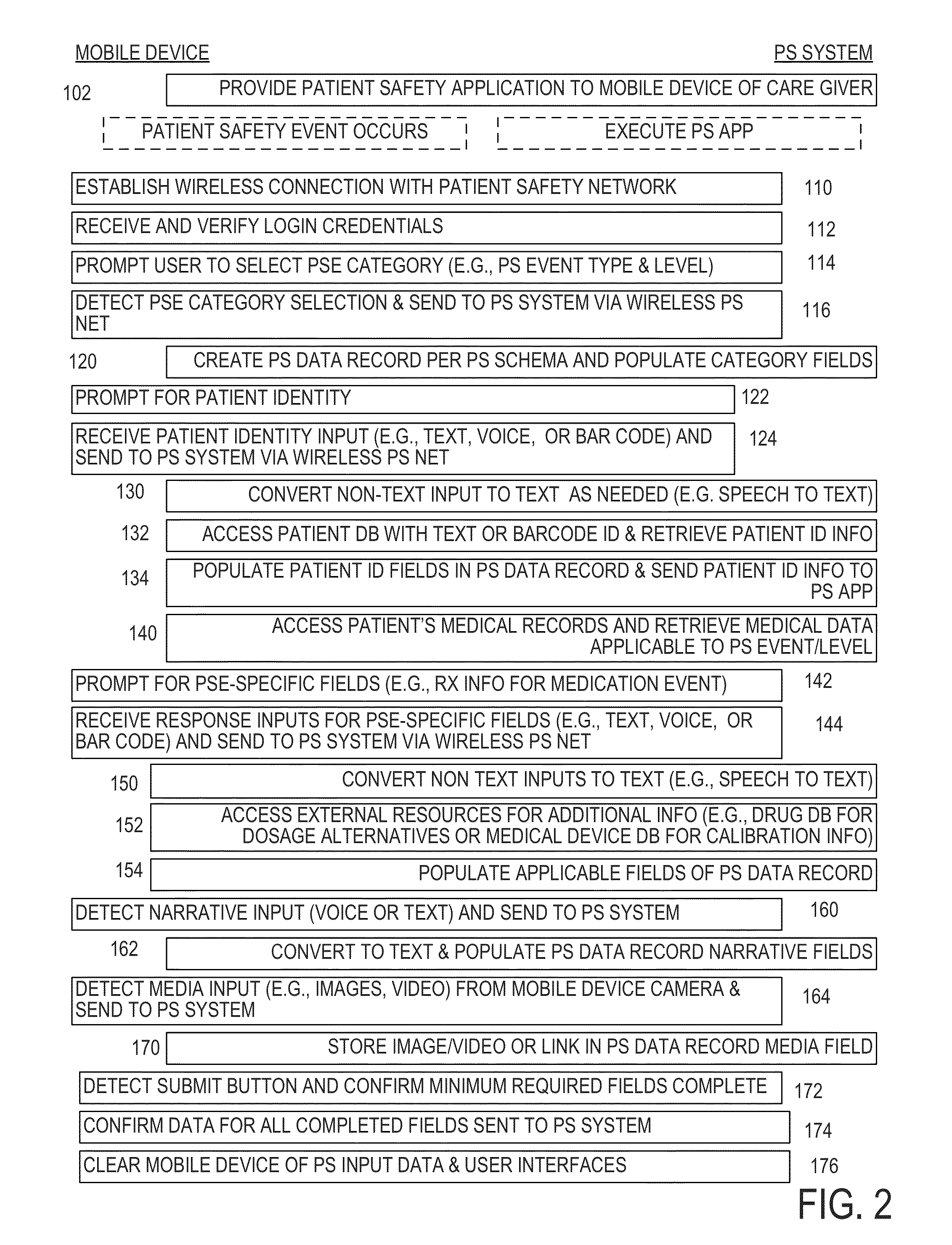
Healthcare hazard detection and early warning system
InactiveUS20160070864A1Data processing applicationsPatient personal data managementEarly warning systemEvent level
A patient safety system receives remote inputs wirelessly transmitted by a mobile device over a wireless network referred to herein as a patient safety network. The remote inputs indicate information, obtained by the patient safety application, pertaining to a patient safety event. Responsive to receiving remote input indicating a patient safety event category, the patient safety system creates a patient safety data record, comprising a set of predefined fields, corresponding to the patient safety event. In one non-limiting application applicable to patient safety events defined in the AHRQ Common Formats, the mobile device user may initiate the generation of a patient safety database record simply by selecting from a mobile device user interface one of nine patient safety event types defined by the Common Formats and one of three patient safety event levels of severity defined by the Common Formats.
Owner:DOTAN DOUGLAS BERNARD +1
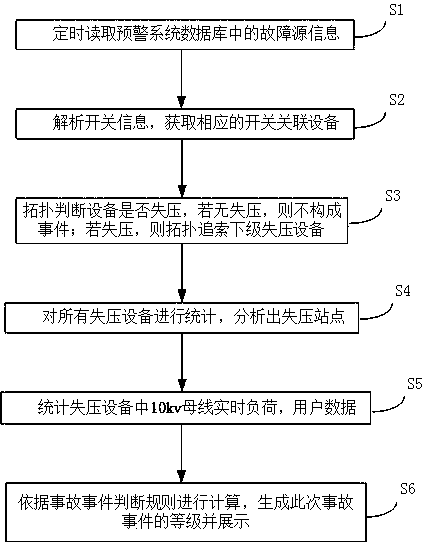
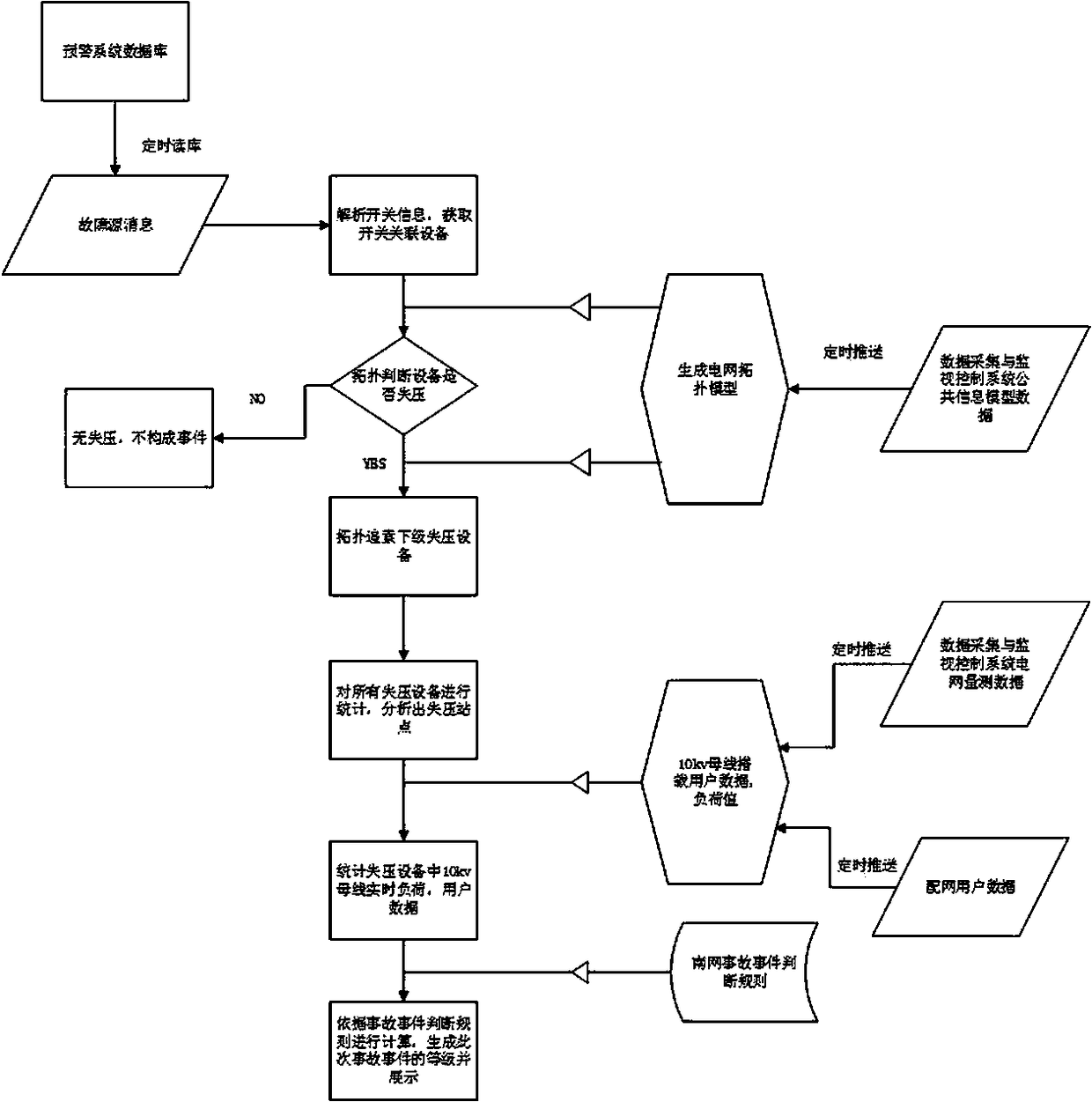
Power grid fault event level automatic identification method
InactiveCN108061841AShorten the timeGuaranteed timelinessFault location by conductor typesEvent levelCalculation error
The invention belongs to the power grid fault identification field and relates to a power grid fault event level automatic identification method. The method comprises the following steps: S1, fault source information in an alarm system database is regularly read; S2, switch information is parsed, so that corresponding switch associated equipment can be obtained; S3, a topologic model determines whether devices undergo voltage loss, if no devices undergo voltage loss, no events are generated; if voltage loss occurs, the topologic model traces lower-level voltage-loss devices; S4, all voltage-loss devices are put into statistics, and voltage-loss stations are obtained through analysis; S5, the real-time load of 10kv bus-bars in the voltage-loss devices and user data are put into statistics;and S6, calculation is performed according to accident event judgment rules, and the level of a current accident event is generated and displayed. With the method adopted, fault risk information can be automatically generated; high efficiency can be realized; time can be saved for a dispatcher; the dispatcher can obtain risk reference information immediately; and automatic calculation can be realized, and therefore, manual calculation errors can be avoided, and a misjudgment rate can be reduced.
Owner:广东电网有限责任公司惠州供电局
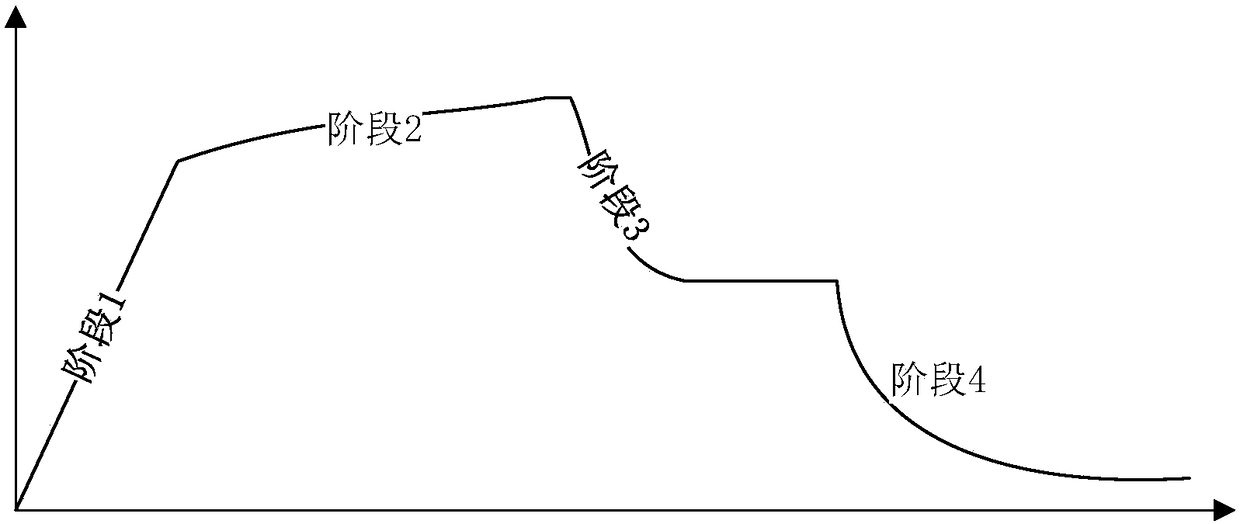
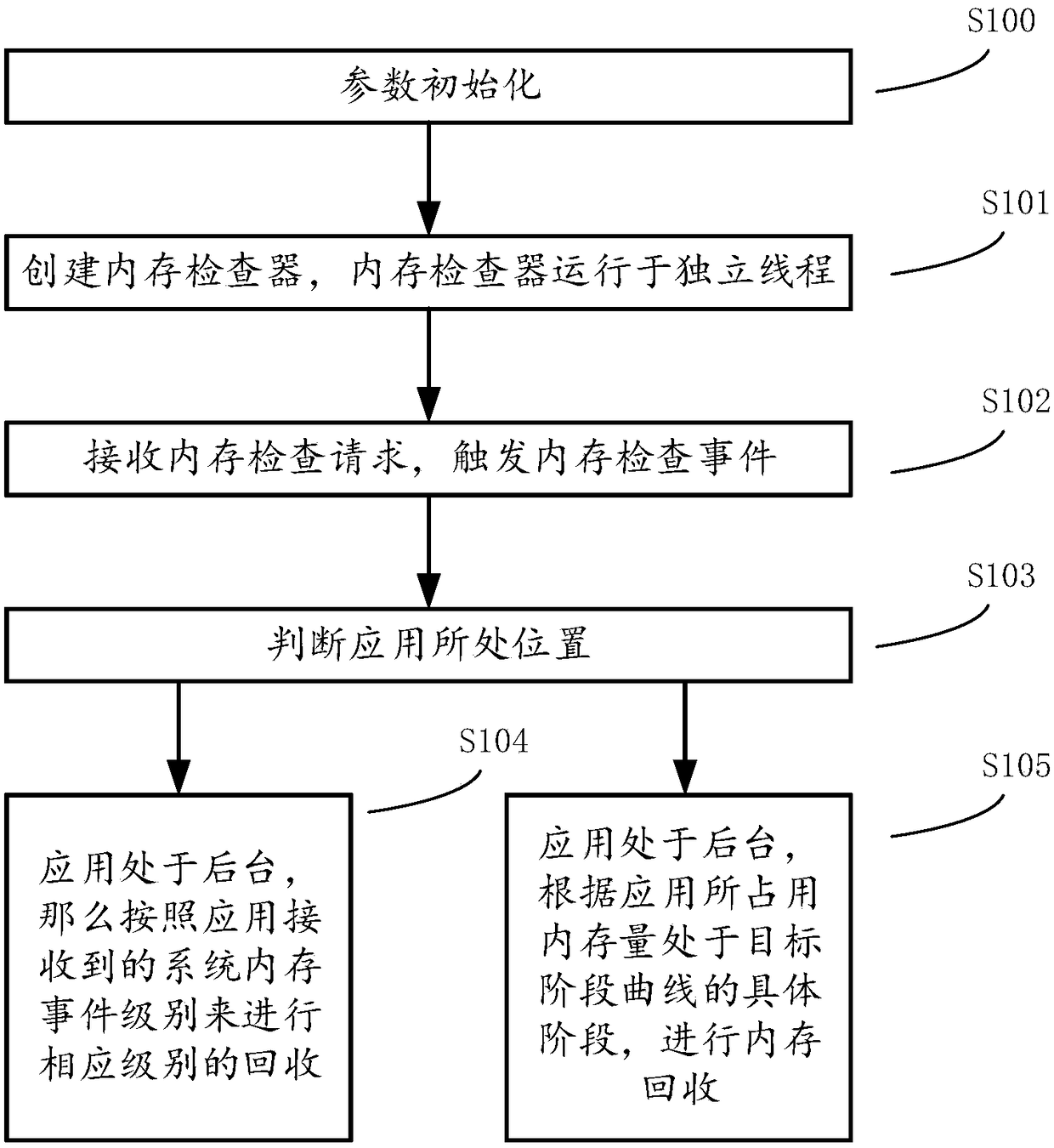
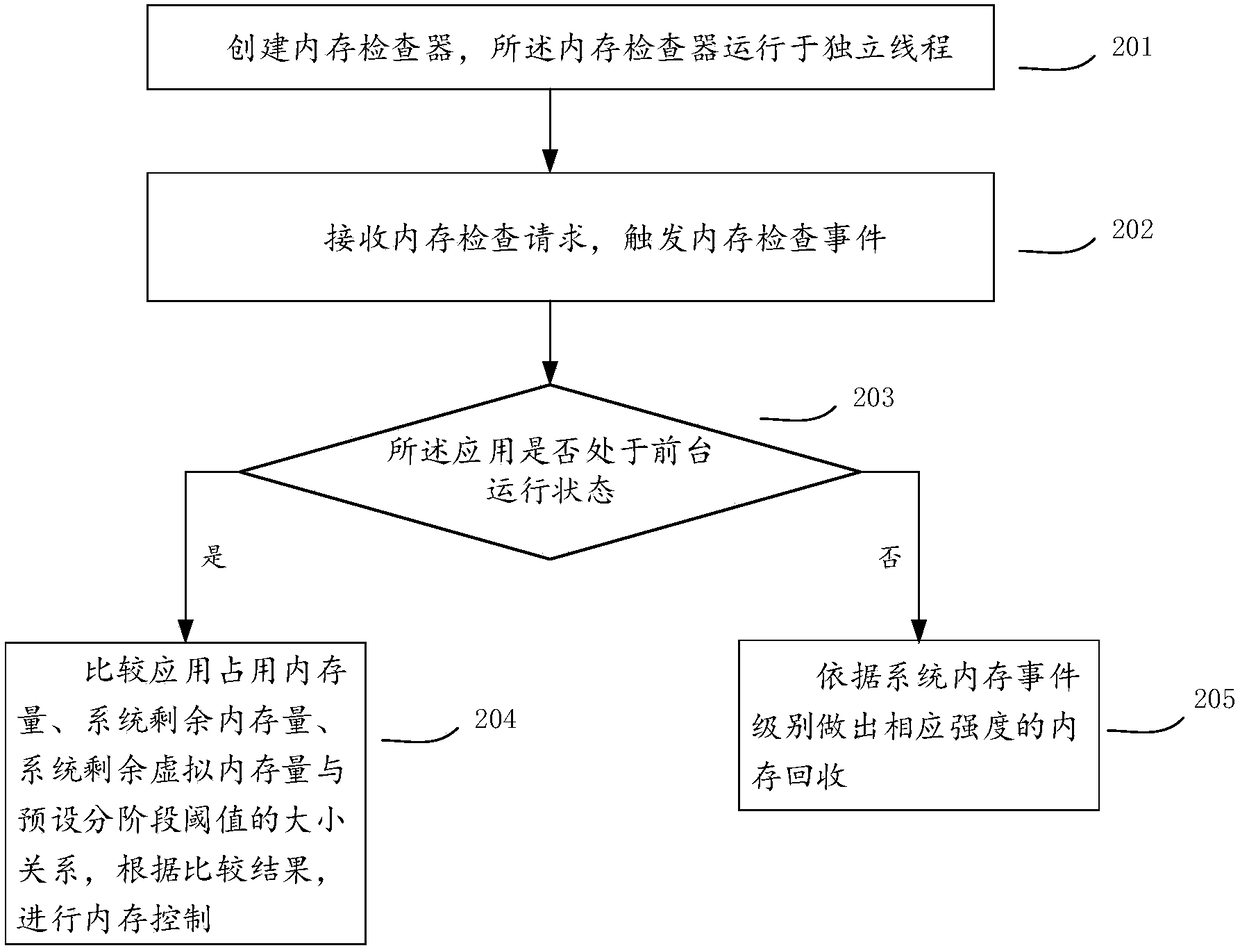
Memory control method and device
ActiveCN108073520AEfficient use ofImprove experienceResource allocationMemory adressing/allocation/relocationVirtual memoryEvent level
The invention provides a memory control method and device. The method includes: creating a memory checker, wherein the memory checker is run in an independent thread; receiving a memory checking request, and triggering a memory checking event; judging whether an application is in a foreground running state, if yes, obtaining size relationships of an application memory-occupancy amount, a remainingsystem memory amount, a remaining system virtual-memory amount and preset phased threshold values by comparison, and carrying out memory control according to comparison results, wherein the preset phased threshold values are set on the basis of an application memory target-phase curve; and if not, carrying out corresponding-intensity memory recovery according to a system memory event level. According to the method, more elaborate memory management can be realized for the foreground application according to the application memory target-phase curve, contradiction of ceaseless system memory claiming of the application and the limited system memory total-amount can be solved on an application layer, hardware resources can be effectively utilized, and user experience can be improved at the same time.
Owner:深圳市雅阅科技有限公司
System and method for editing interactive three-dimension multimedia, and online editing and exchanging architecture and method thereof
ActiveUS8966402B2Indoor gamesElectronic editing digitised analogue information signalsEvent levelUser interface
A system and method are provided to edit interactive three-dimensional multimedia. A user interface of the system is provided with an event level template that includes event series levels with multiple event developing points. Through the user interface, multiple interactive events related to a first character of the event developing point are edited. Through a three-dimensional engine, interactive relevances are built up between interactive events and multiple materials inside one or more database. When the interactive three-dimensional multimedia with multiple materials is output, the interactive events corresponding to the event developing points are performed according to a user command. An online editing and exchanging method integrated with the system and method is also provided to share pre-edited templates on an exchange server; each of the pre-edited templates is extracted from an interactive three-dimensional multimedia pre-edited by the system and method.
Owner:YU LING LU +1
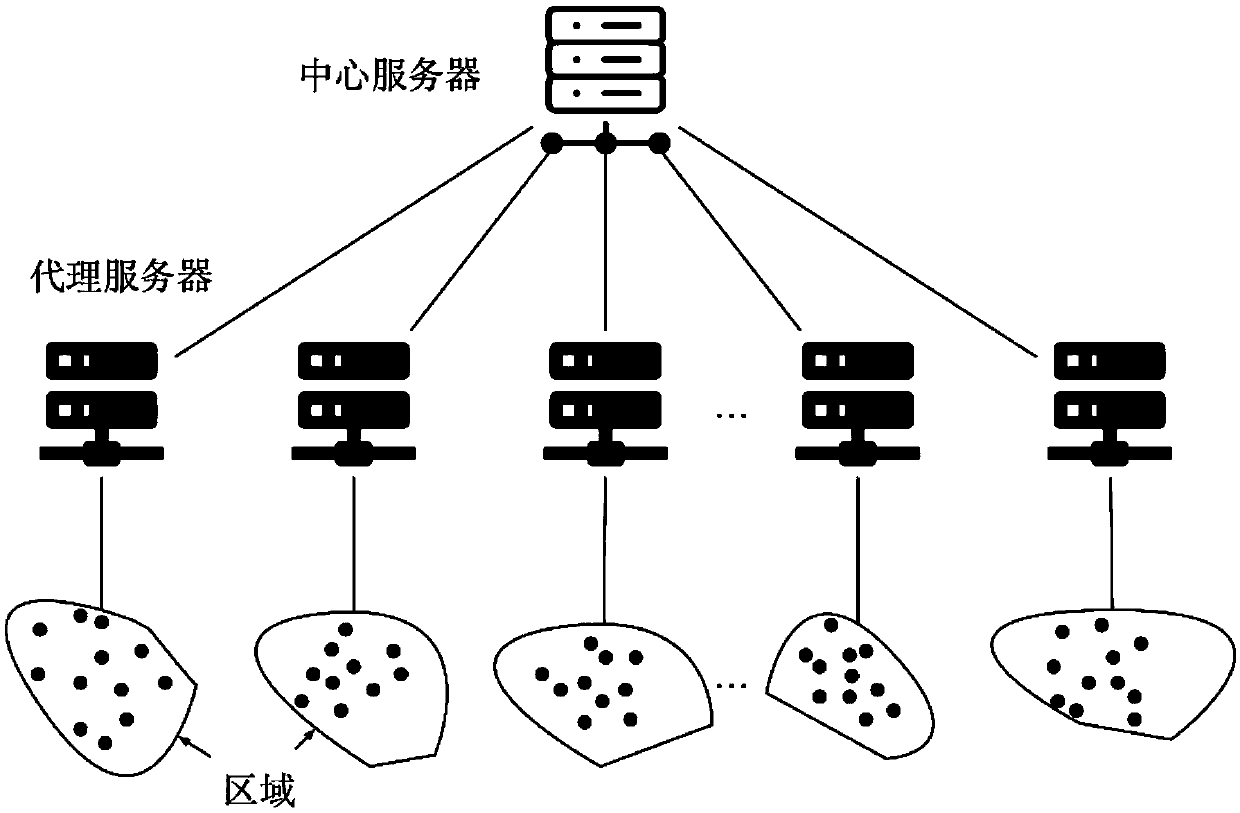
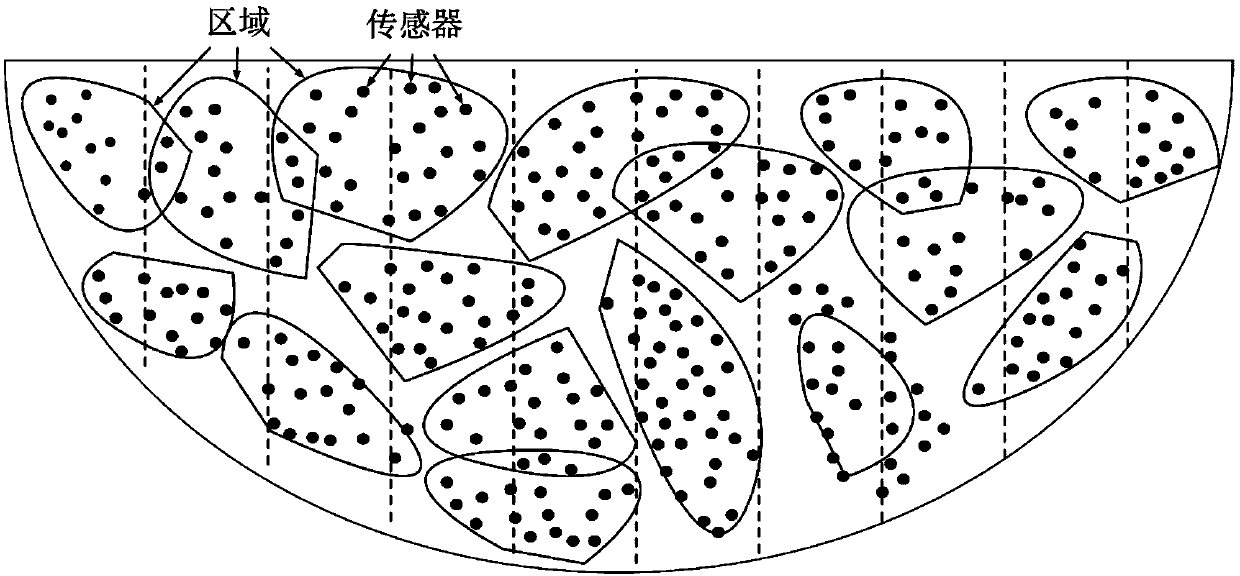
A sensor network event fusion and decision method based on node reliability
ActiveCN109543746AGuaranteed real-timeCharacter and pattern recognitionNeural architecturesNODALEvent level
The invention discloses a sensor network event fusion and decision method based on node reliability. The sensor network is used to judge and decide the structural engineering operation conditions, including event classification and event decision fusion.. In the phase of event classification, the sensor network detects and classifies abnormal events in structural engineering, and reflects the changes of physical state in local area. Considering the reliability difference of nodes, the classification error can be reduced by cooperating with each other. In the event decision fusion stage: abnormal event level changes can reflect the operation state of the structure, and different event classification results are combined to evaluate and make decisions on the structural engineering conditions. Using event fusion model based on depth learning, data enhancement method is used to solve the problem of small training samples, update model parameters dynamically, and assist the evaluation of structural engineering operating conditions.
Owner:HOHAI UNIV
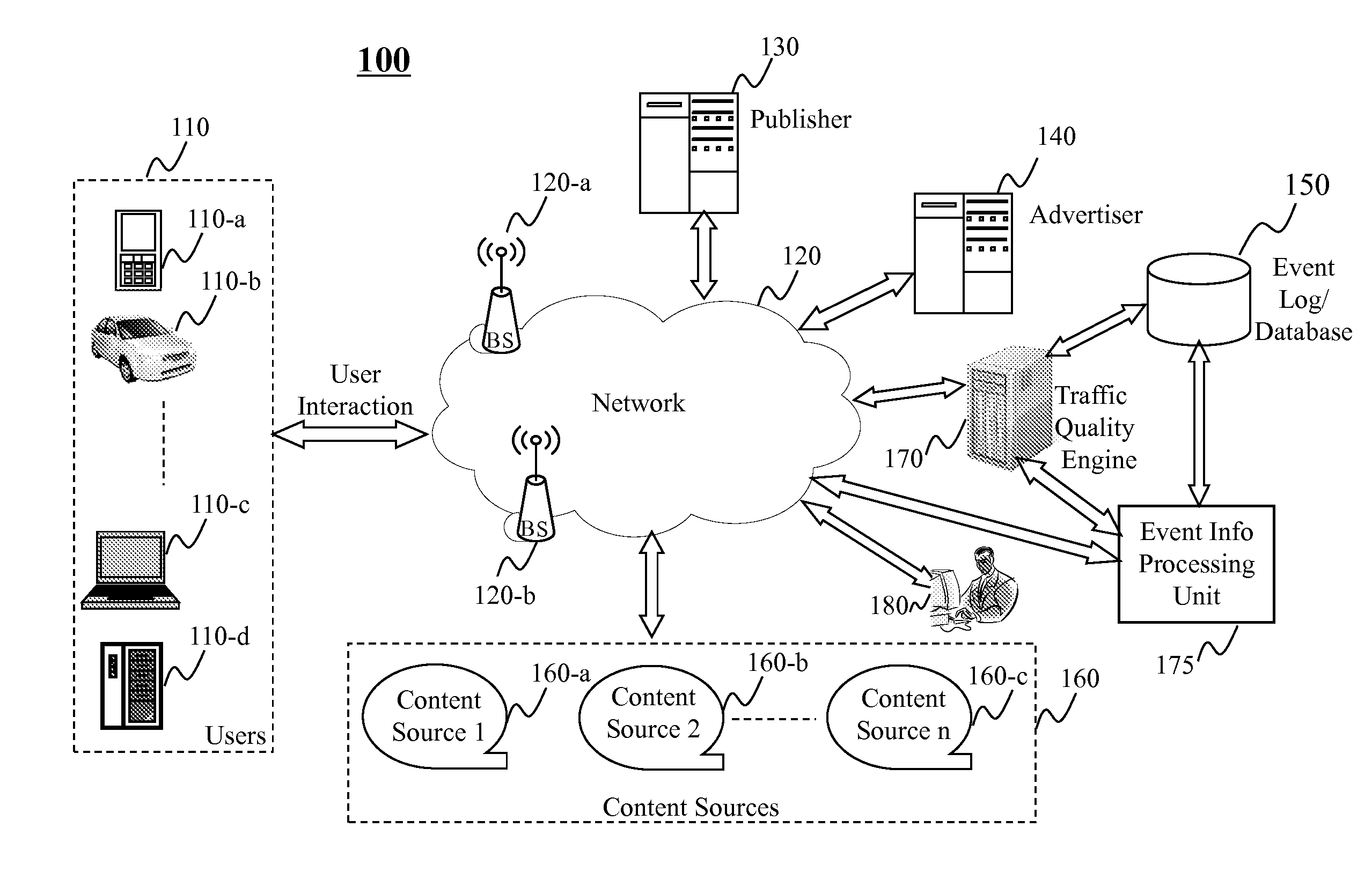
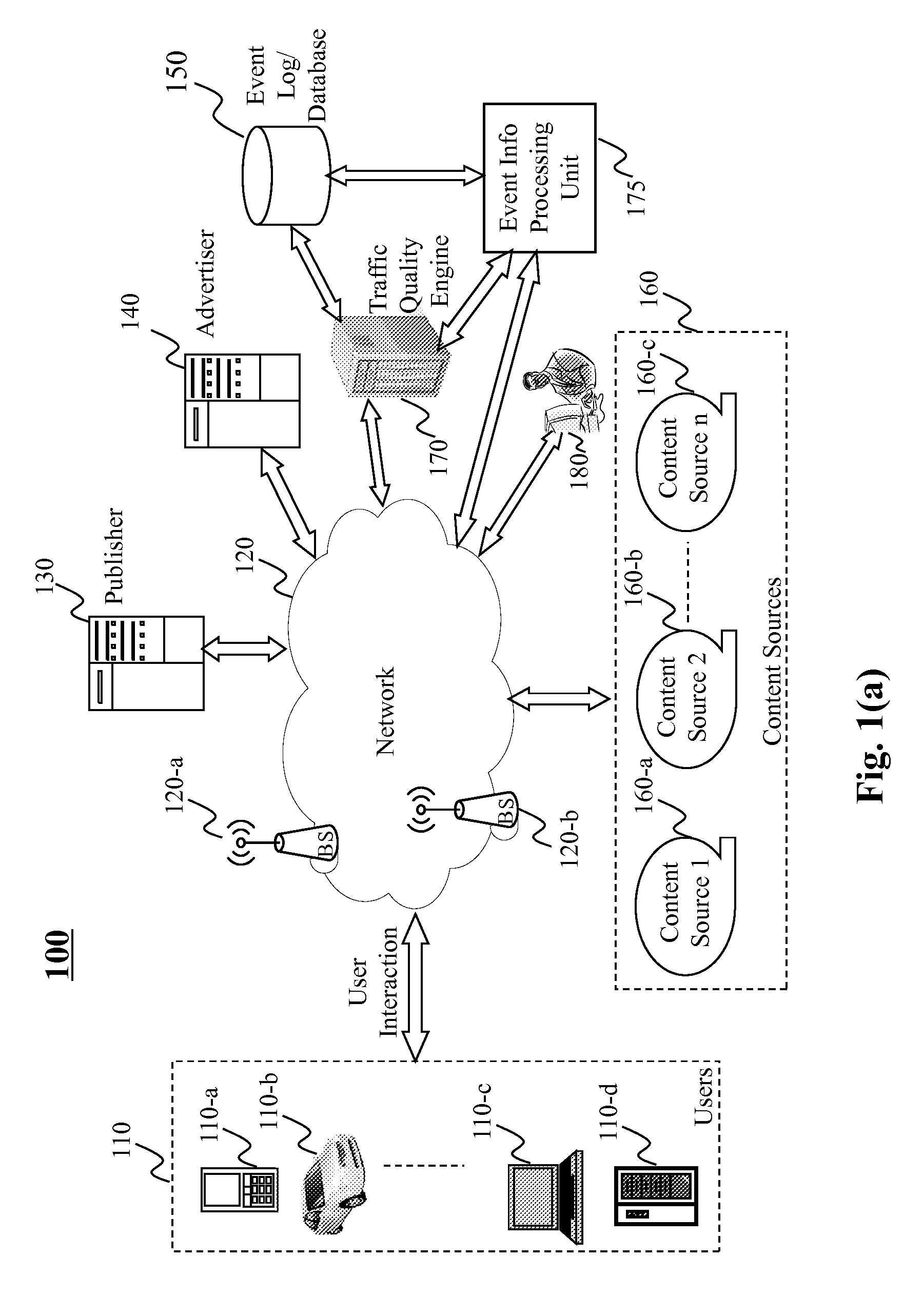
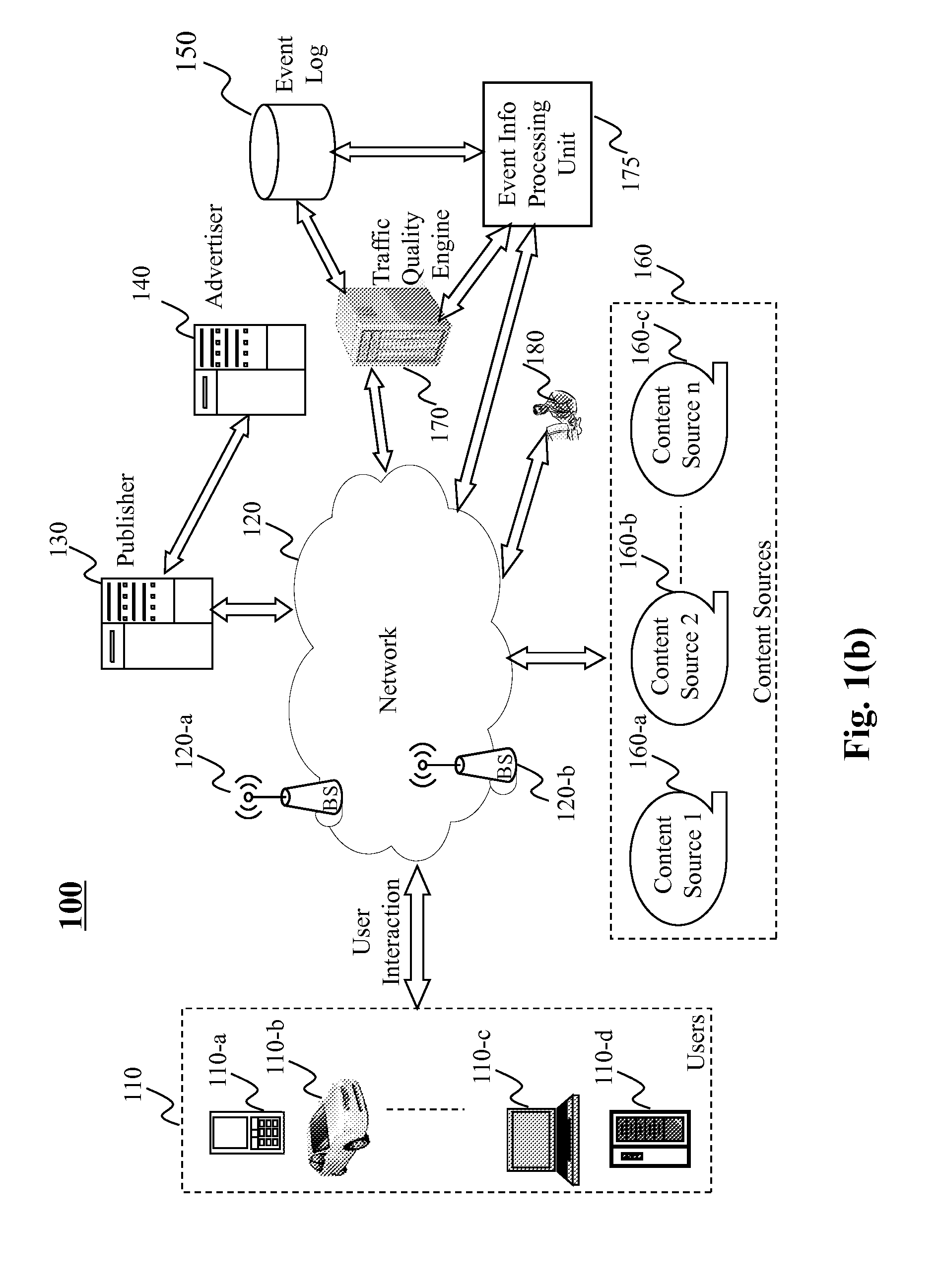
Determining traffic quality using event-based traffic scoring
Methods, systems, and programs are provided to determine event-level traffic quality for event(s) related to user interaction with online content (e.g., via a webpage, a mobile application, etc.). Data related to a current user event and past user events may be received, where such data may include information regarding a set of entities associated with each respective user event. A feature value set for the current user event is generated based on the information regarding the respective sets of entities associated with the current user event and the past user events. Based at least on such feature value set, a traffic quality score for the current user event may be determined, e.g., based on a weighted combination of elements of the feature value set. An entity-level traffic quality score for an entity may be determined based on event-level traffic quality scores of user events that involve that entity.
Owner:R2 SOLUTIONS
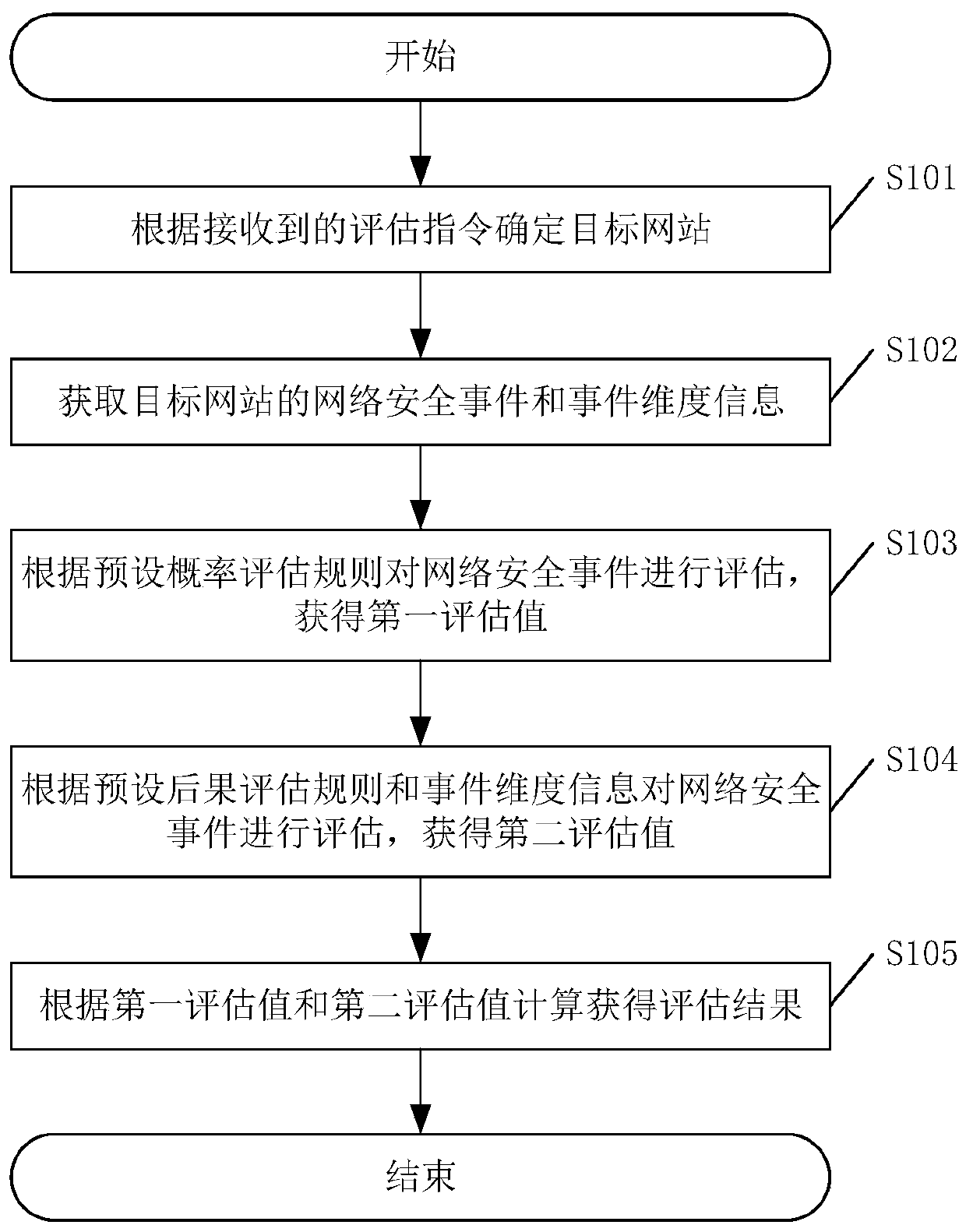
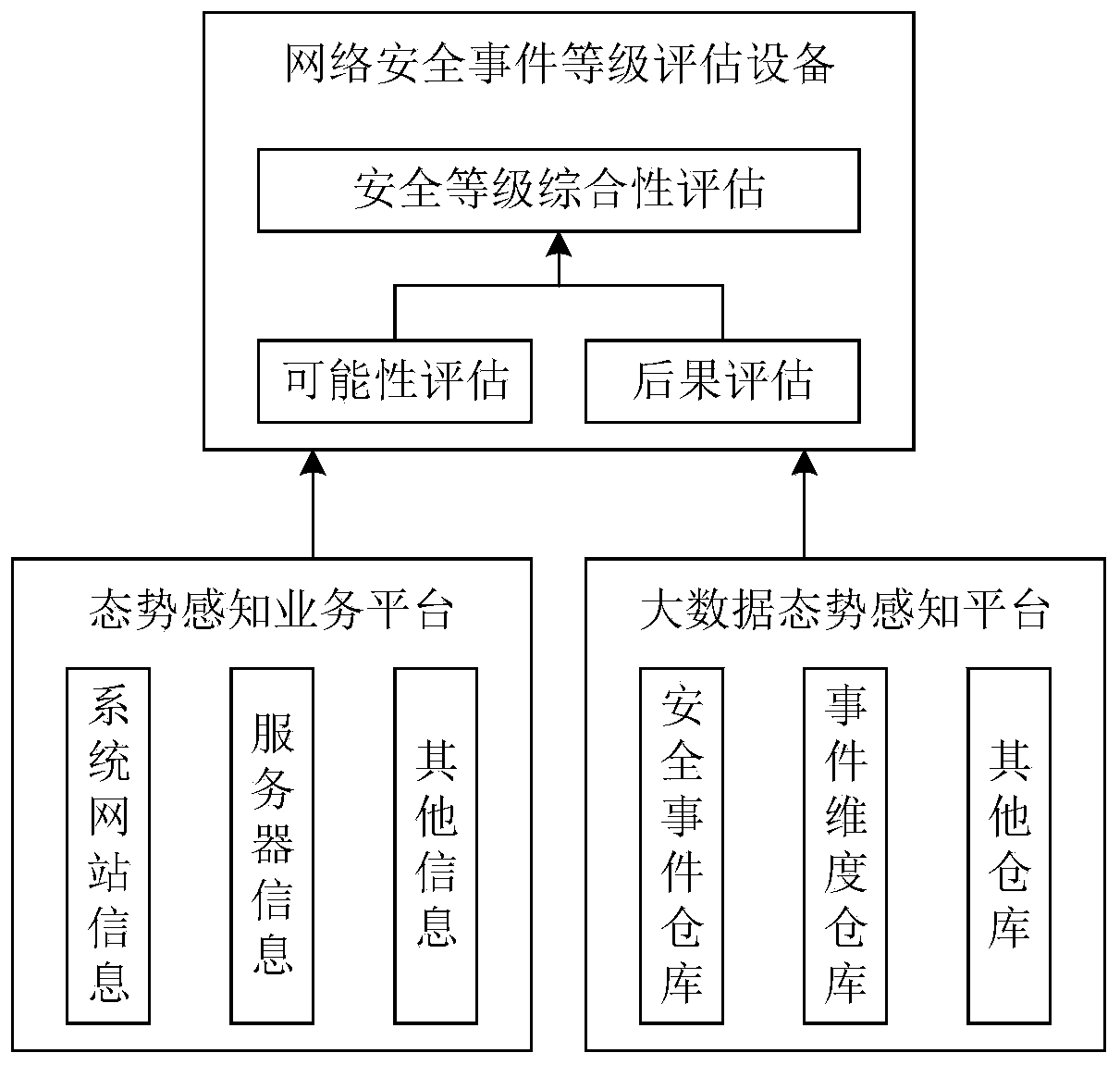
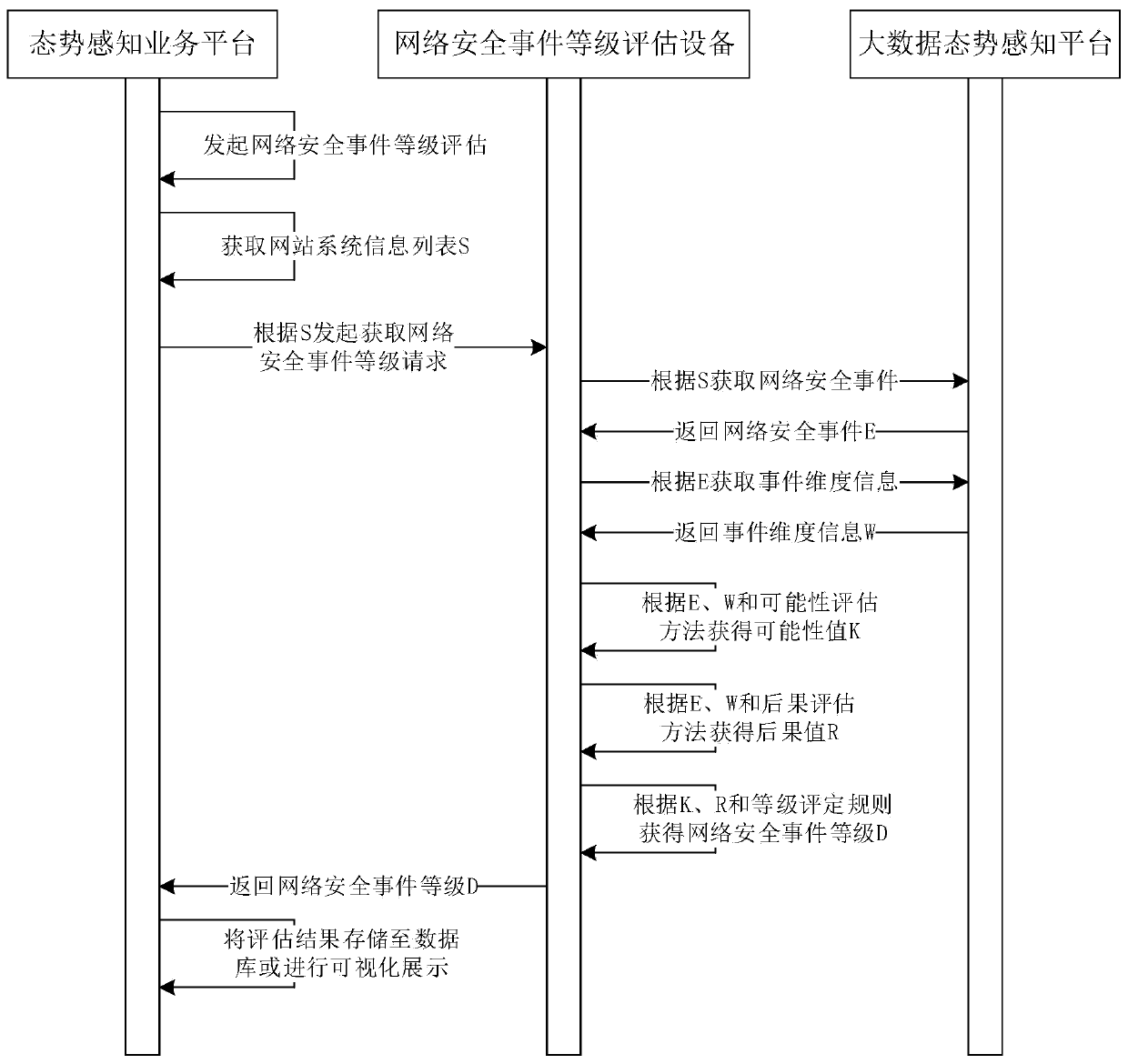
Network security event level evaluation method and equipment and related equipment thereof
ActiveCN111600897AGuaranteed accuracyImprove grade evaluation efficiencyTransmissionWeb siteEvaluation result
The invention discloses a network security event level evaluation method. The method comprises the steps of determining a target website according to a received evaluation instruction; obtaining a network security event and event dimension information of the target website; evaluating the network security event according to a preset probability evaluation rule to obtain a first evaluation value; evaluating the network security event according to a preset consequence evaluation rule and the event dimension information to obtain a second evaluation value; calculating according to the first evaluation value and the second evaluation value to obtain an evaluation result; according to the network security event level evaluation method, the accuracy of the network security event level evaluationresult can be ensured, the security level evaluation efficiency is greatly improved, and the labor cost is effectively saved. The invention further discloses a network security event level evaluationdevice and equipment and a computer readable storage medium, which all have the above beneficial effects.
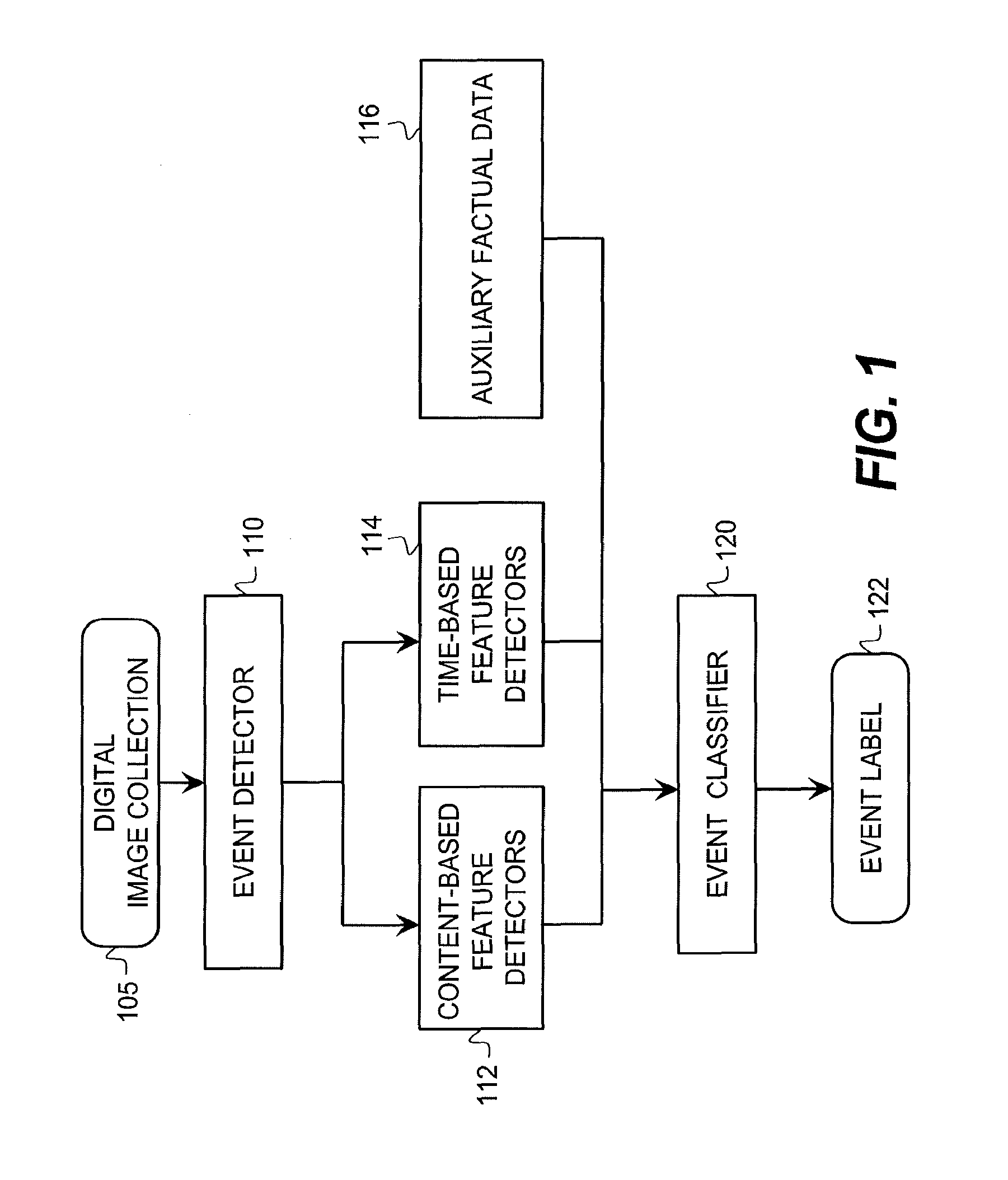
Owner:HANGZHOU ANHENG INFORMATION TECH CO LTD
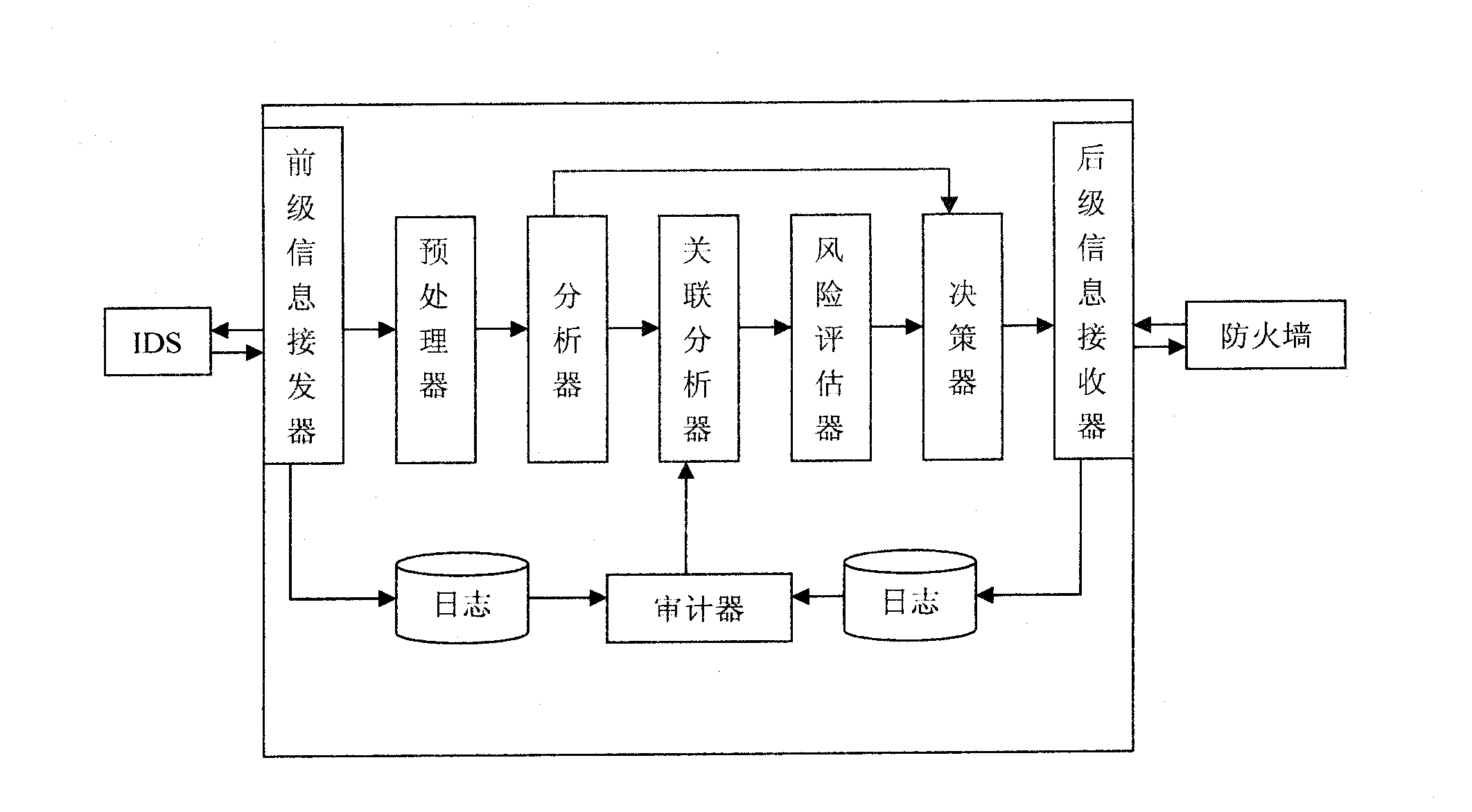
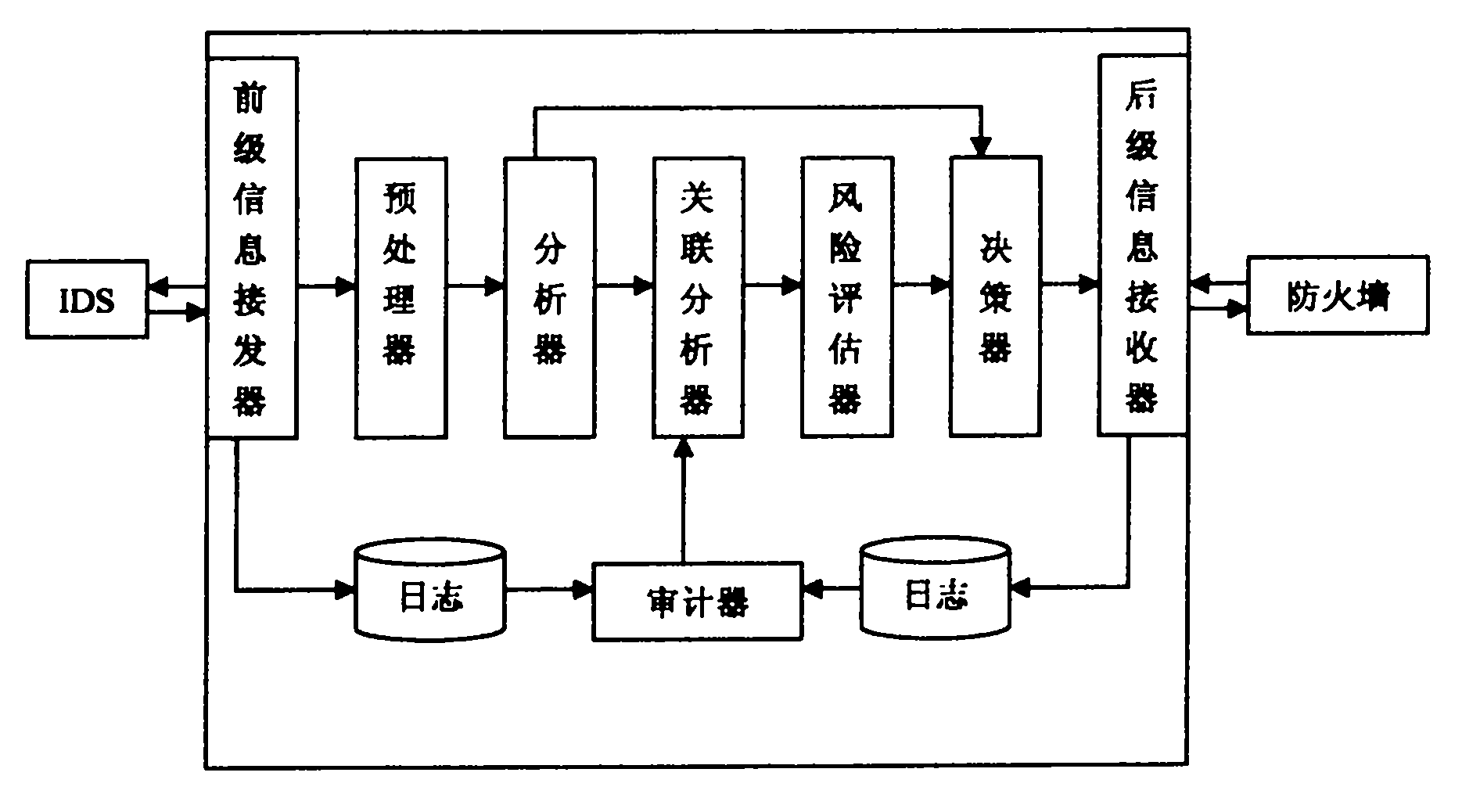
Linkage method for firewall and intrusion-detection system
The invention relates to a linkage method for a firewall and intrusion-detection system, and the method is used for network protection and is characterized by comprising the following steps: encrypting and transmitting the alarm information generated by the intrusion-detection system to a forestage information receiver and then sending the alarm information to a preprocessor after decrypting and authenticating the alarm information by the forestage information receiver; performing the preprocessing of extracting and cleaning the information record by the preprocessor and then sending to an analyzer; sending an order to a decider by the analyzer if the acquired safety event level exceeds a preset threshold value, otherwise, sending an analyzed result to a relevance analyzer; performing the relevance analysis by the relevance analyzer and then sending a result to a risk evaluator; performing the risk evaluation on the current network state by the risk evaluator and then sending the acquired risk level of the current network and the network running state parameters to the decider; sending the linked specific information to a backstage information receiver by the decider, performing the related treatment and then sending the result to the firewall for implementing linkage; and centrally auditing an intrusion-detection log of the forestage information receiver and a firewall log of the backstage information receiver and then sending to the relevance analyzer.
Owner:NORTHEAST DIANLI UNIVERSITY
Airborne distributed node debugging method based on event level
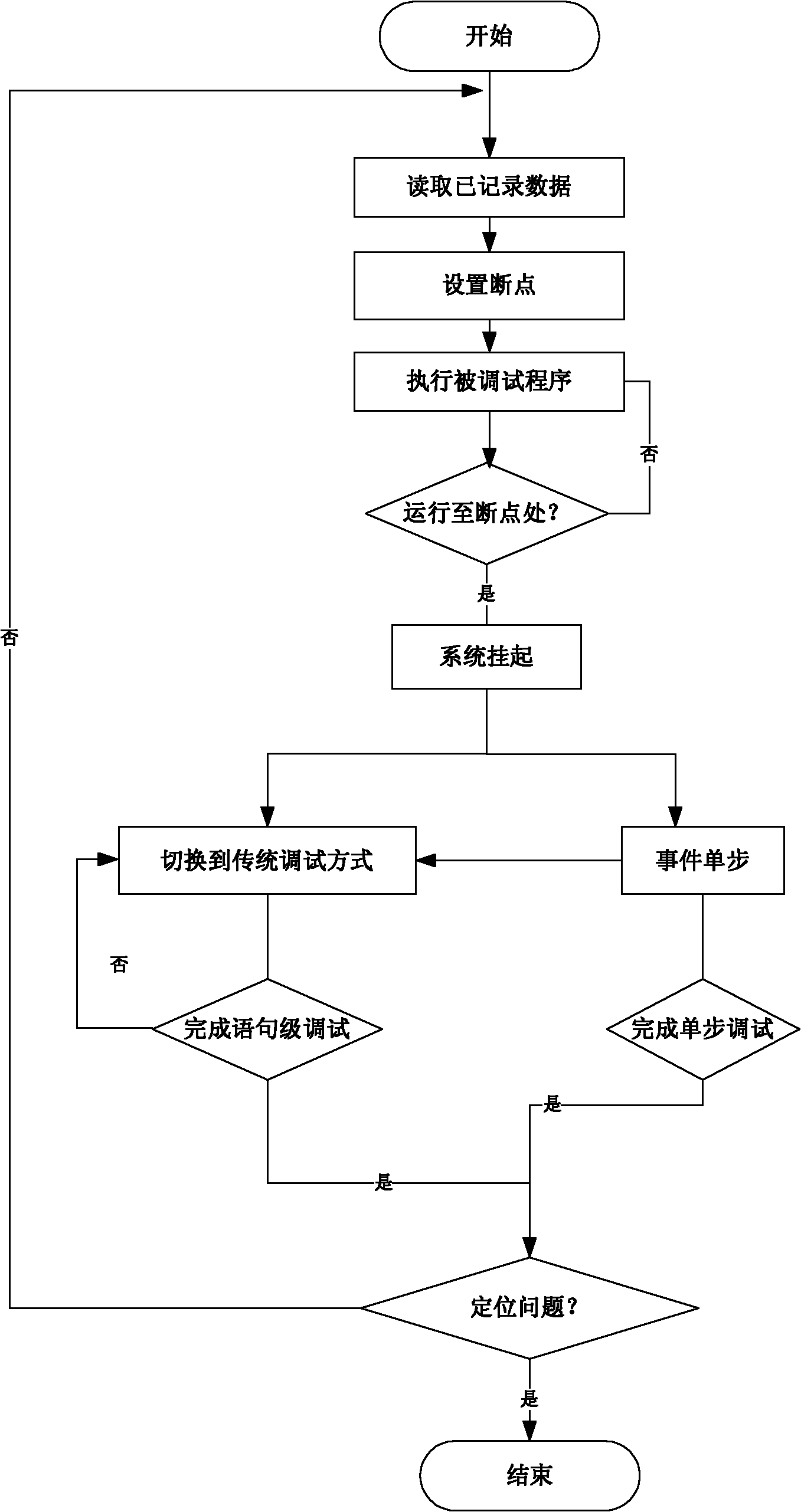
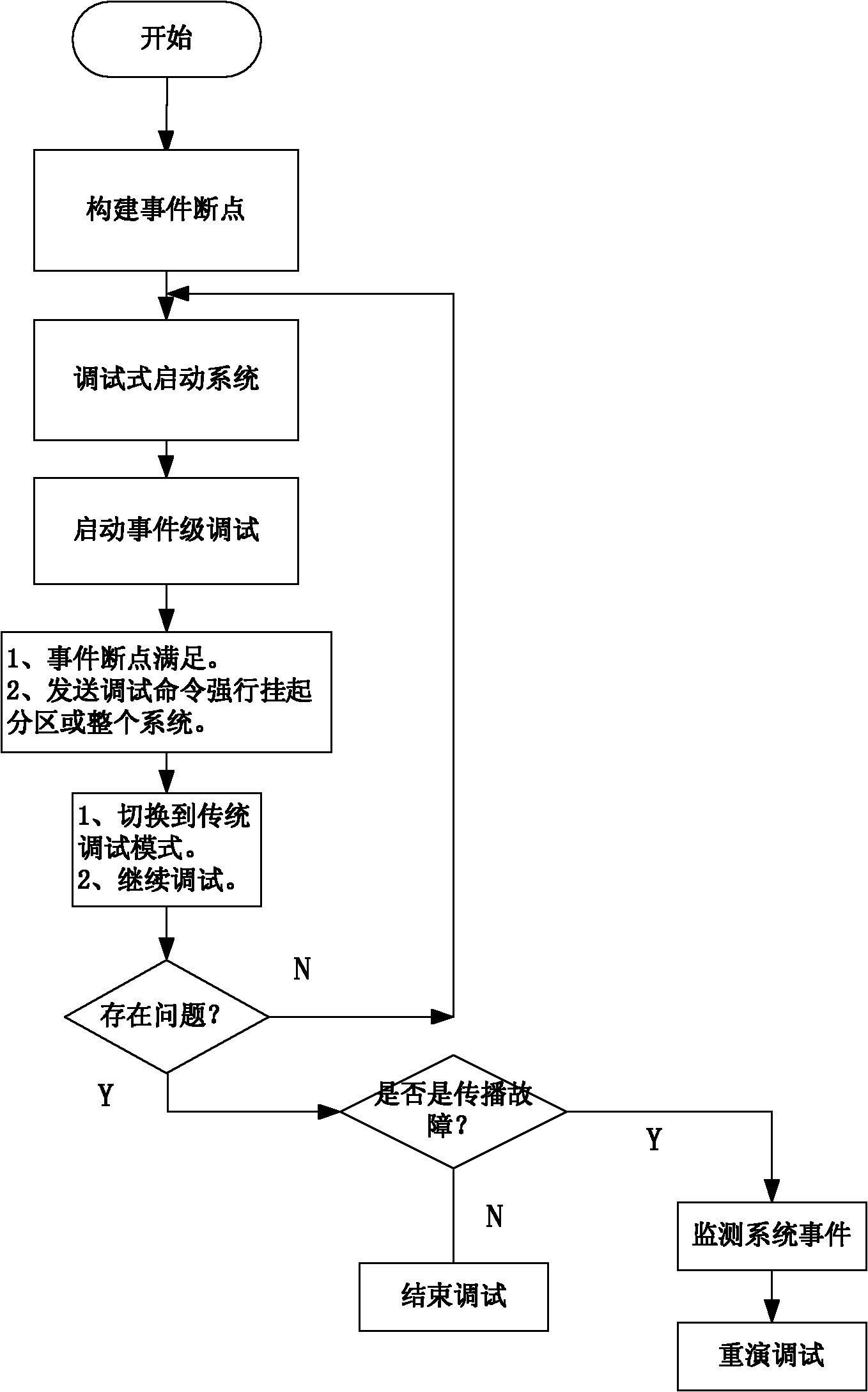
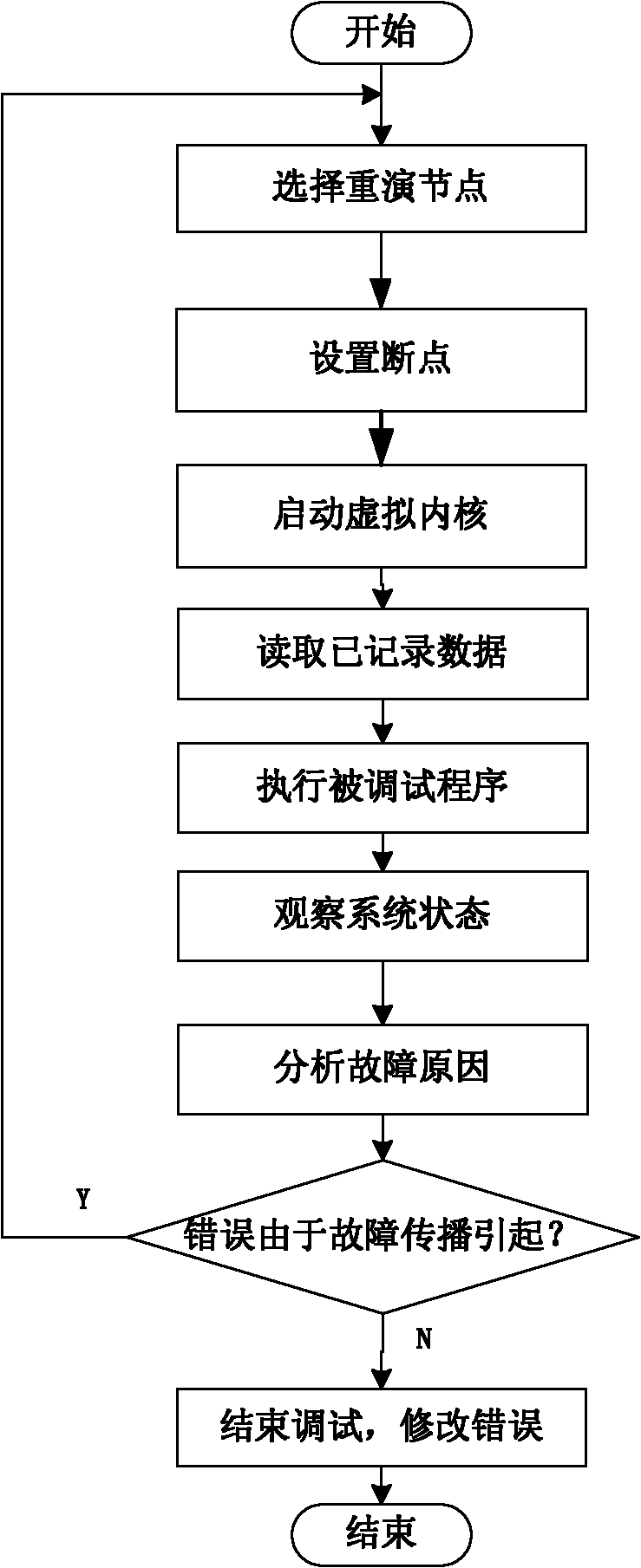
InactiveCN102096634AImprove debugging efficiencySoftware testing/debuggingEvent levelEmbedded system
The invention discloses an airborne distributed node debugging method based on an event level. The method comprises the following steps: (1) constructing an event breakpoint; (2) debugging a start-up system; (3) switching the system to the conventional debugging mode to diagnose the trouble source; (4) debugging by monitoring; and (5) repeating the debugging, and stopping the repeated debugging if the fault is not caused by propagation. The invention solves the technical problems of the conventional debugging system, such as complex structure, no fault recurrence, and large cost on the space and the time of the system, and the event-based debugging method pays more attention on the interaction behavior between the nodes so as to reduce the concern on the internal state of a program.
Owner:AVIC NO 631 RES INST
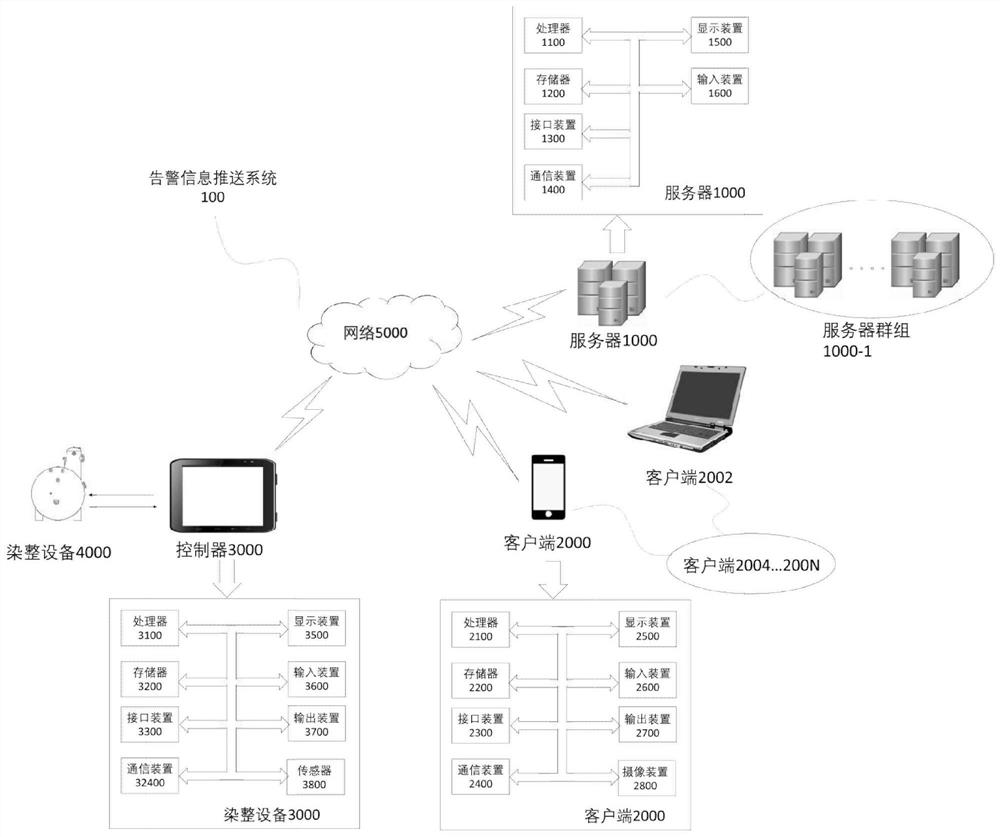
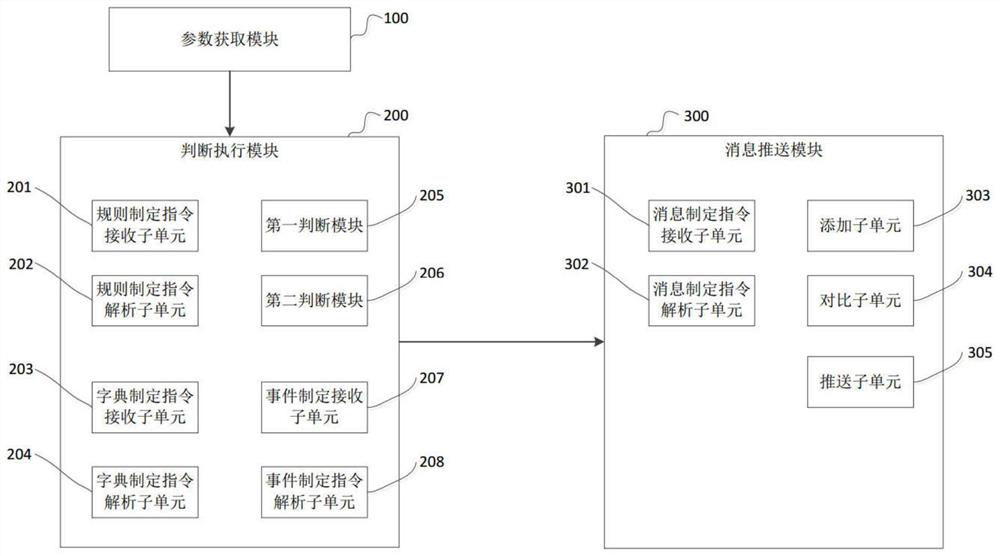
Alarm message pushing method and device, equipment and storage medium
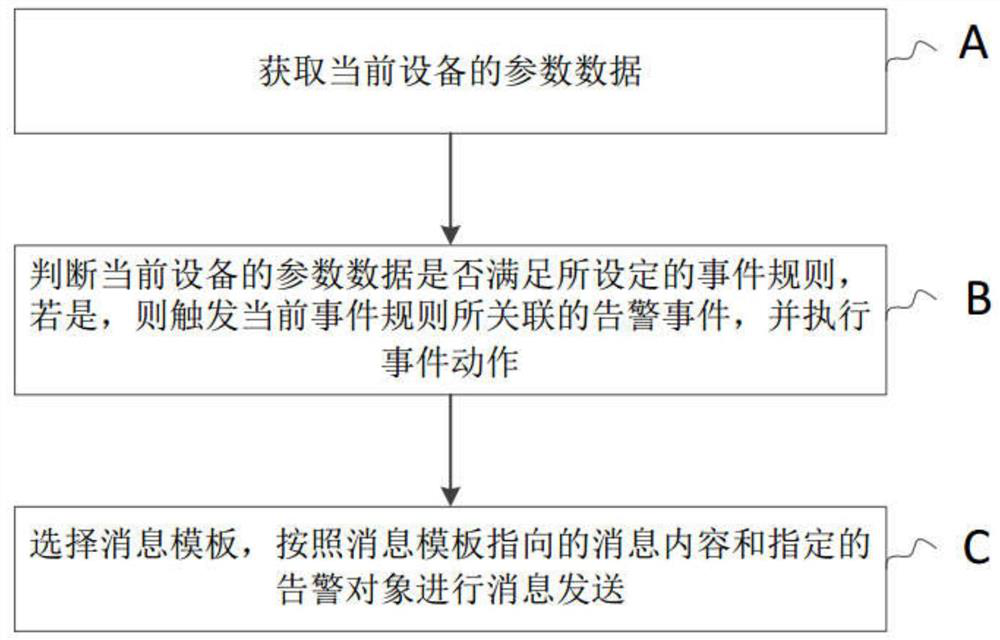
The invention discloses an alarm message pushing method and device, equipment and a storage medium. The method comprises the following steps: acquiring parameter data of current equipment; judging whether the parameter data of the current equipment meets a set event rule, if so, triggering an alarm event associated with the current event rule, and executing an event action; wherein the event action comprises the steps of selecting a message template, and sending a message according to the message content pointed by the message template and a specified alarm object. According to the invention, the data cloud storage is operated through the equipment, the abnormal condition of the data is determined according to the rule definition of the event, the alarm information is sent to the specific receiving end and the receiving object according to the message preset template, the event level and the determination strategy are pre-defined for the abnormal condition of the data, and different terminals are selected for sending. Meanwhile, the user object permission is formulated, so that the message can be sent to a specific object, and the problems that the content viewing permission of the existing alarm information is not graded, and the sending object and the sending form are single are solved.
Owner:佛山技研智联科技有限公司
Network failure real-time relativity analysing method and system
InactiveCN100456687CAvoid Correlation AnalysisEfficient identificationData switching networksTopology informationEvent level
Information of failure events from various network devices and service objects is written into original event list. Correlation analysis is carried out for events read by analyzing and controlling engine from the original event list according to levels of original event and selection of classes. The dynamic analytical algorithm synthetically handles information in each area such as scene of historical fault analysis, dynamic performance parameters of network, dynamic topology information and time character of event etc. comparing with prior art, the invention overcomes disadvantages of overlooking information of dynamic network state, dependent on preset rule and lack of auto study ability etc. The invented method provides effective correlation analysis, fault reason analysis and location in real time when storm of network fault happens.
Owner:HUAWEI TECH SERVICE
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com