Linkage method for firewall and intrusion-detection system
An intrusion detection system and firewall technology, applied in the field of network security, can solve problems such as firewall and IDS not responding well, blocking normal communication, lack of correlation and merging of alarm information, etc., to meet the requirements of intelligent network security and improve effective Effects on Sex and Accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
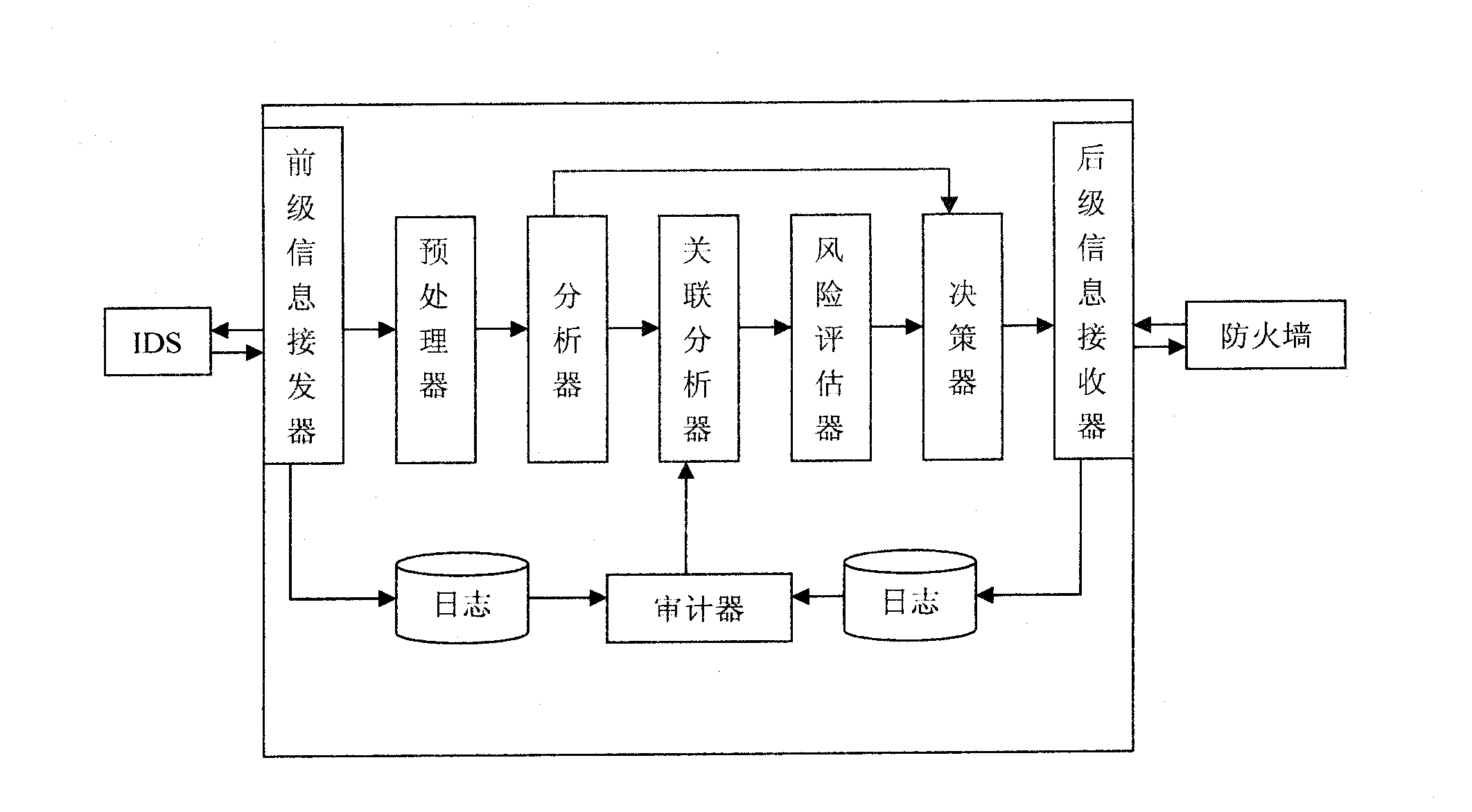
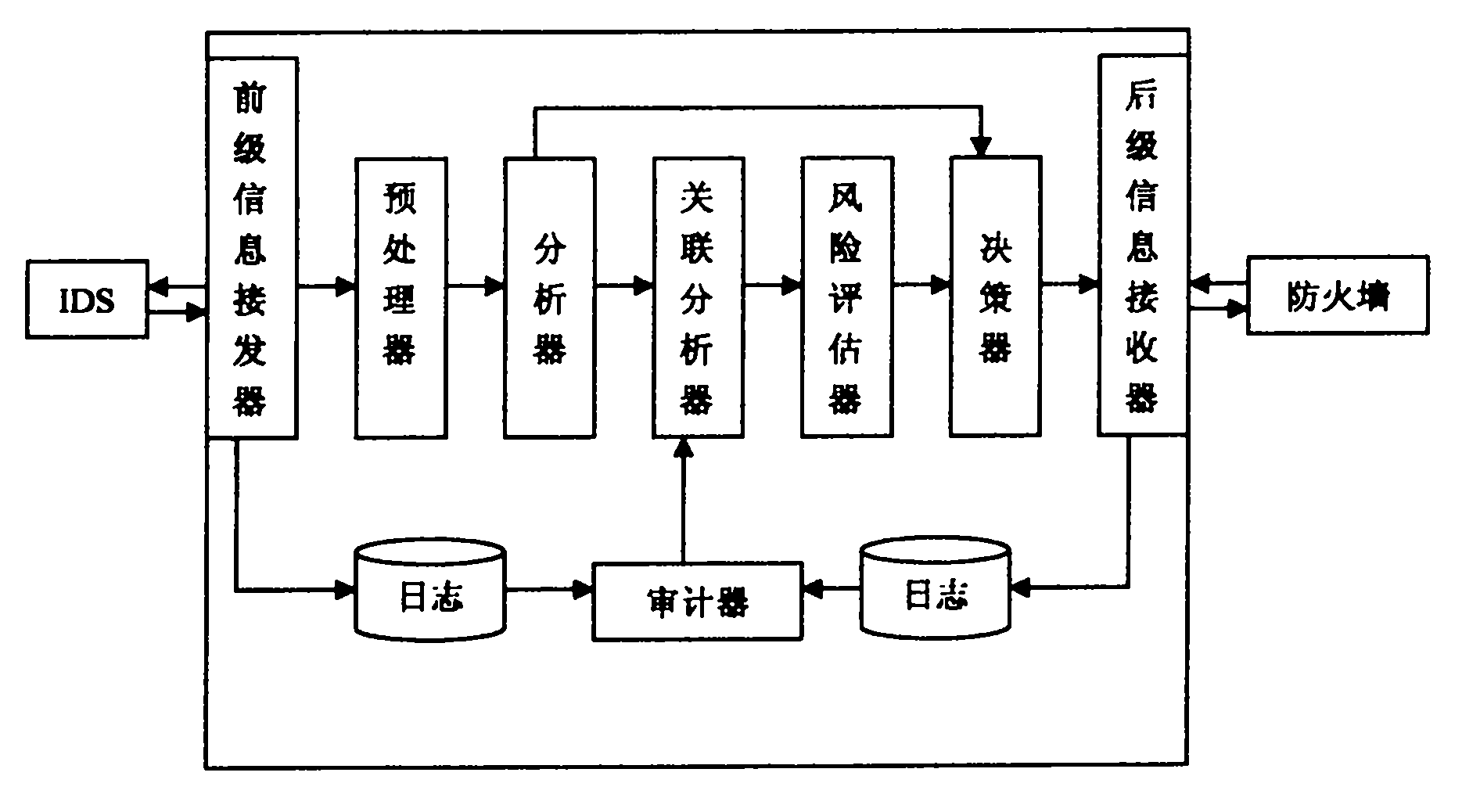
[0015] With reference to Fig. 1: the linkage method of firewall and intrusion detection system of the present invention comprises:
[0016] [1] The alarm information generated by the intrusion detection system is encrypted and transmitted to the front-level information transceiver, where it is decrypted and authenticated;
[0017] [2] Send the alarm information decrypted by the front-level information transceiver to the preprocessor for preprocessing, extract and clean the information records, and standardize the relevant data;
[0018] [3] Send the data preprocessed by the preprocessor to the analyzer for analysis. If the obtained security event level exceeds the predetermined threshold, the analyzer will send a command to the decision maker, otherwise the analysis result of the analyzer will be sent to the association Analyzer;
[0019] [4] Send the correlation analysis results of the correlation analyzer to the risk evaluator, carry out risk assessment on the current netwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com