Security information duplicate checking method and system based on semantic analysis
A semantic analysis and information technology, applied in the security information plagiarism check method and system field based on semantic analysis, can solve the problems of difficult to locate sentences, consume large resources, etc., and achieve the effect of improving the accuracy and efficiency of plagiarism check
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
[0055] see Figure 1-2 .
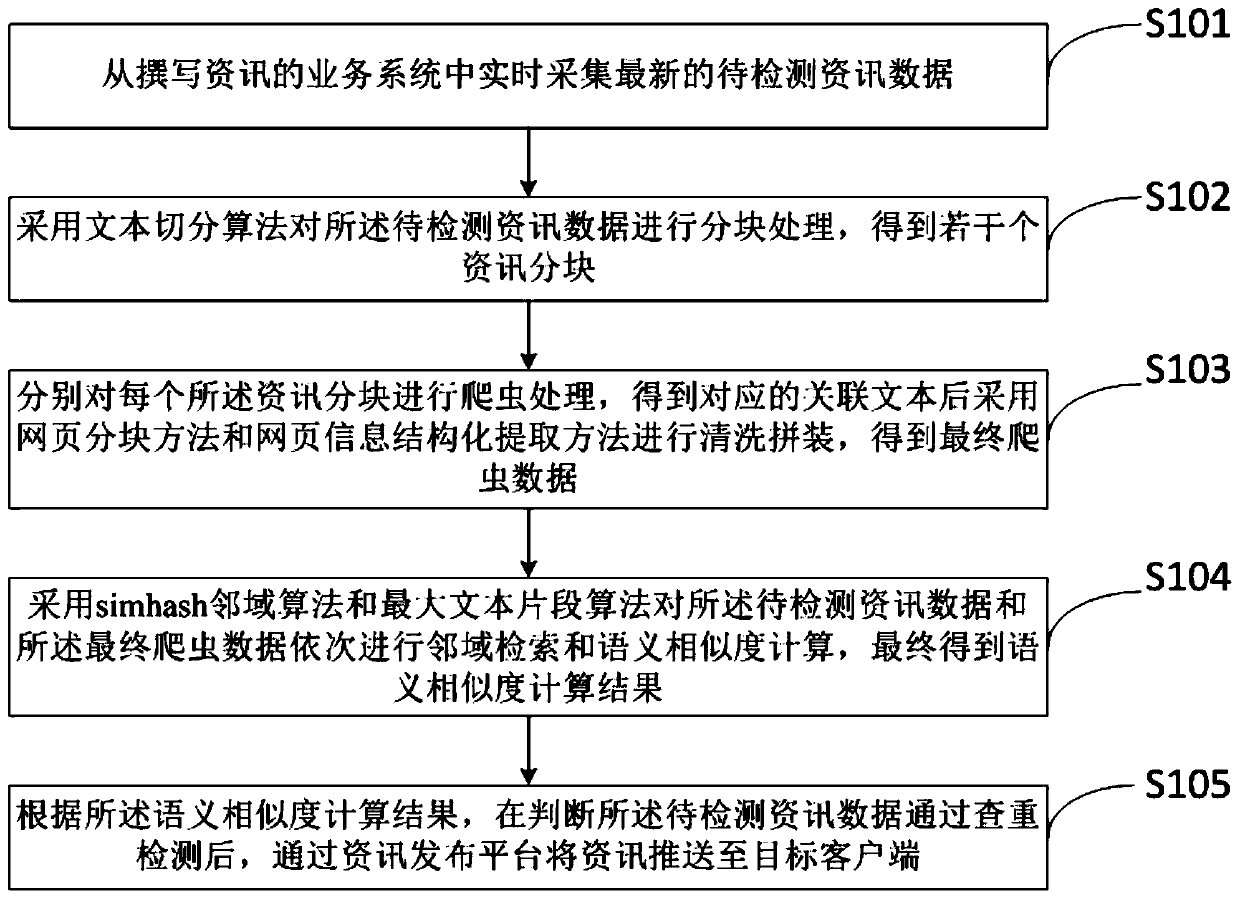
[0056] Such as figure 1 As shown, a semantic analysis-based securities information plagiarism checking method provided by an embodiment of the present invention is suitable for execution in a computing device, and at least includes the following steps:
[0057] S101. Collect the latest information data to be detected in real time from the business system for writing information;
[0058] Specifically, for step S101, the latest information is mainly collected in real time from multiple business systems to the plagiarism checking system. In this embodiment, the latest information written by investment consultants is mainly collected from the business systems through Kafka, and stored in Oracle, Mysql, etc. type database.
[0059] S102. Using a text segmentation algorithm to perform block processing on the information data to be detected to obtain several information blocks;
[0060] Specifically, for step S102, the received information is divided i...
no. 2 example
[0098] see Figure 3-7 .
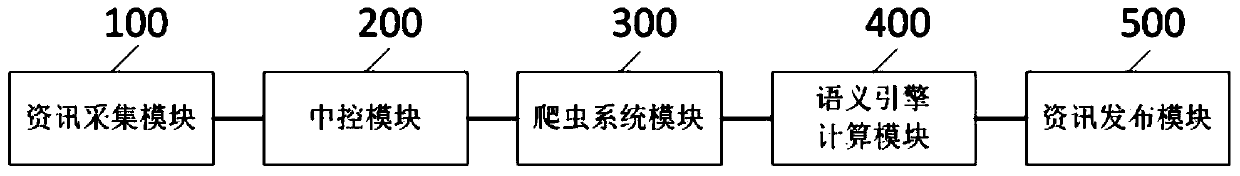
[0099] Such as image 3 As shown, another embodiment of the present invention also provides a security information plagiarism checking system based on semantic analysis, including:
[0100] The information collection module 100 is used to collect the latest information data to be detected in real time from the business system for writing information;
[0101] Specifically, the information collection module 100 mainly collects the latest information to be checked in real time from multiple business systems to the plagiarism checking system, including author information, investment certificate number, information review object, information review basis, information review text and other information. In this embodiment, the latest information written by investment consultants is mainly collected from the business system through Kafka, and stored in relational databases such as Oracle and Mysql.
[0102] The central control module 200 is used to block...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com