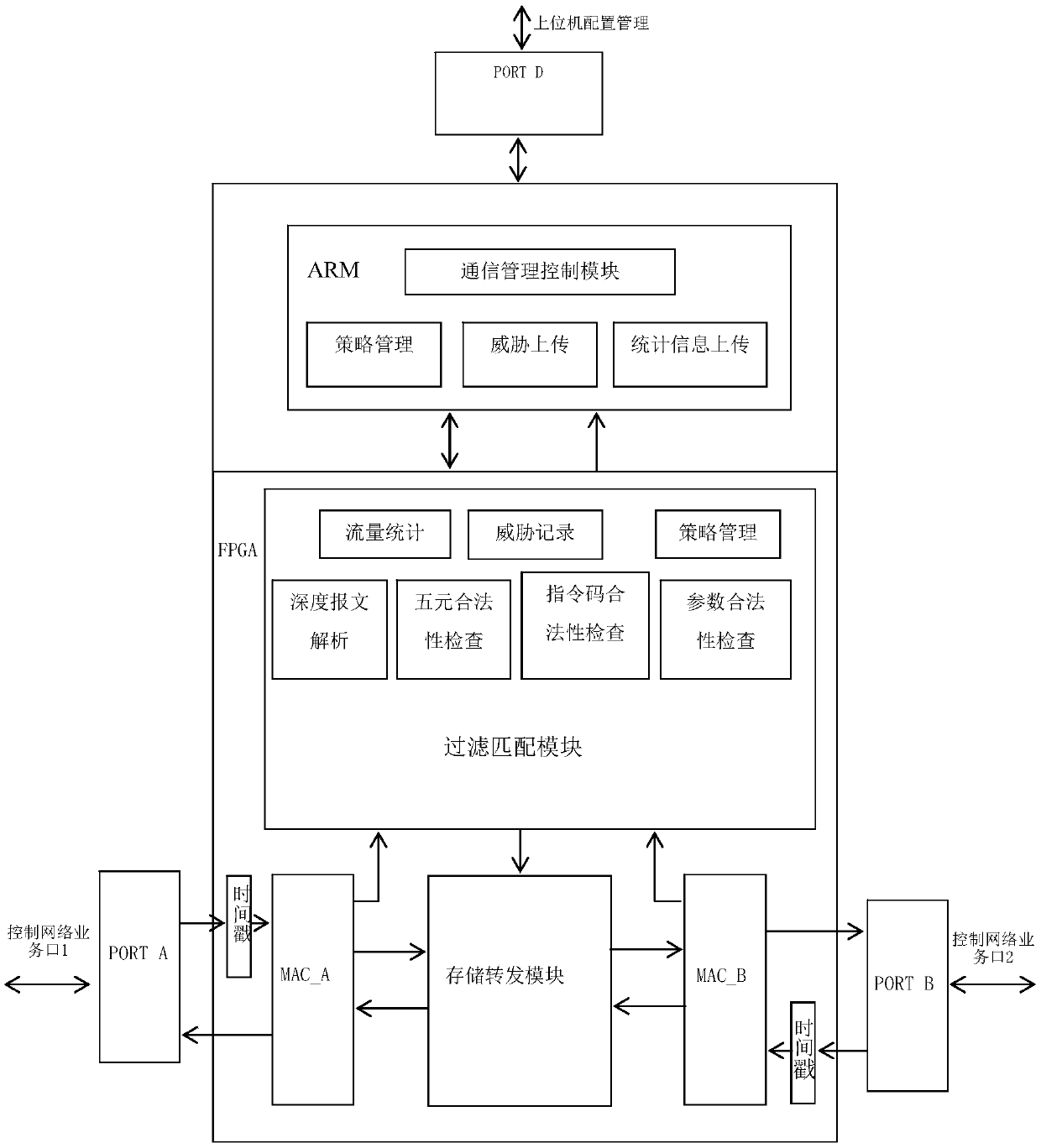
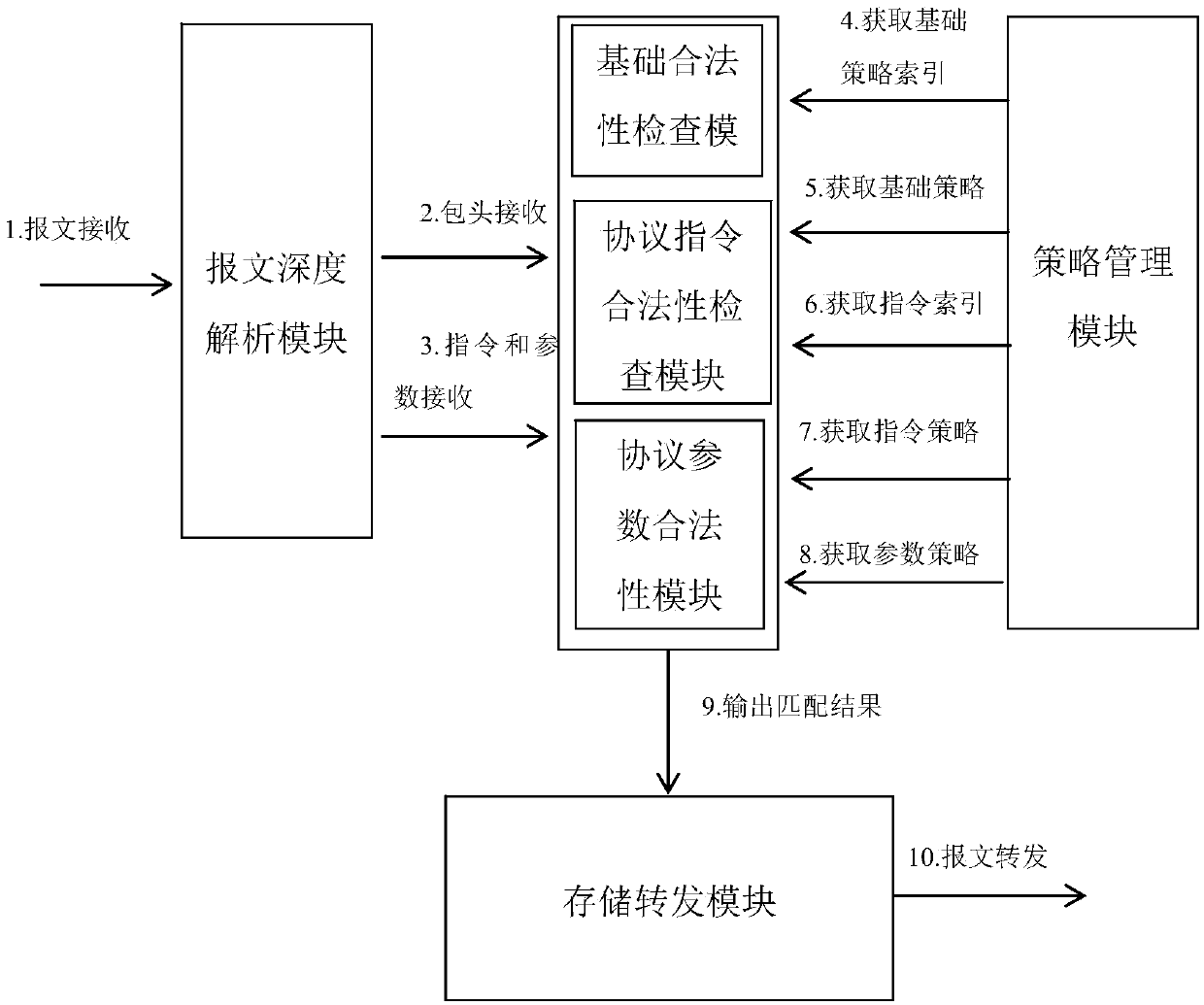
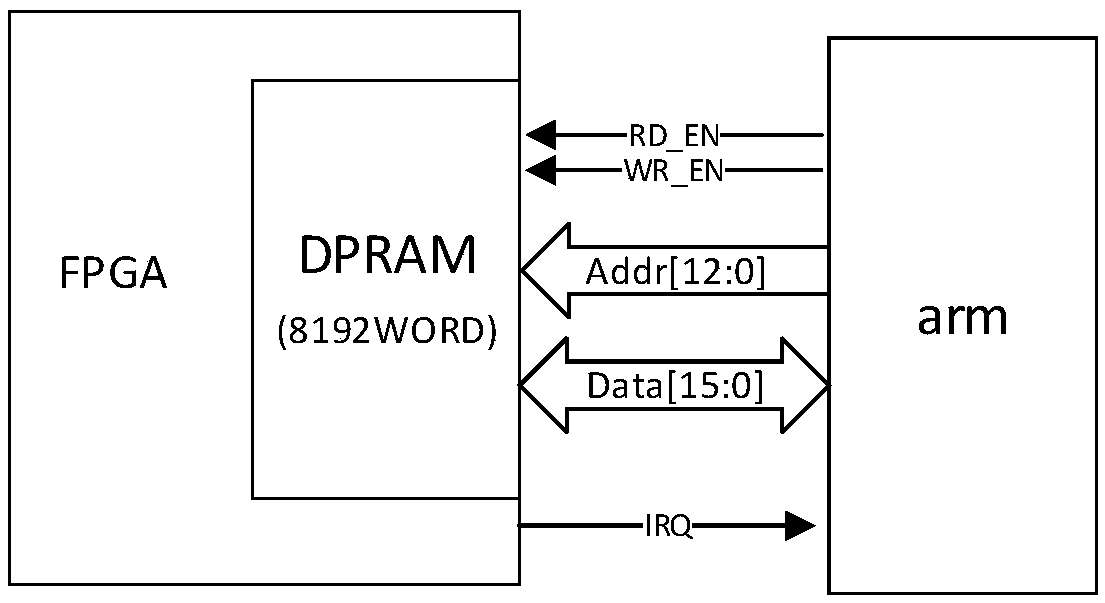
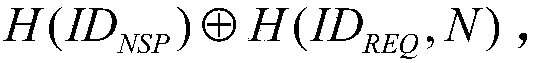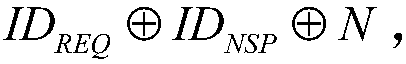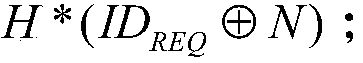Patents
Literature
178results about How to "Reduce security threats" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
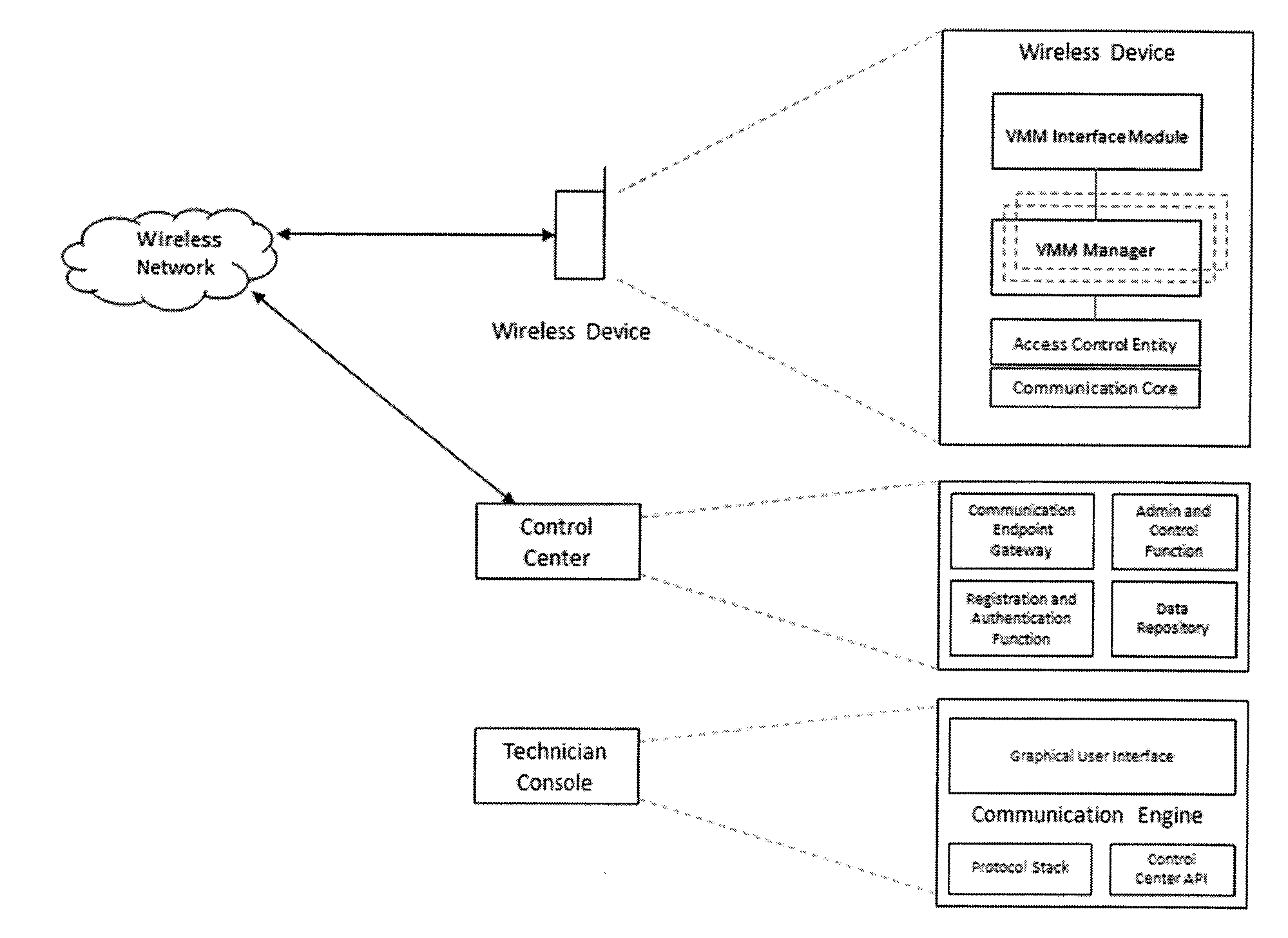
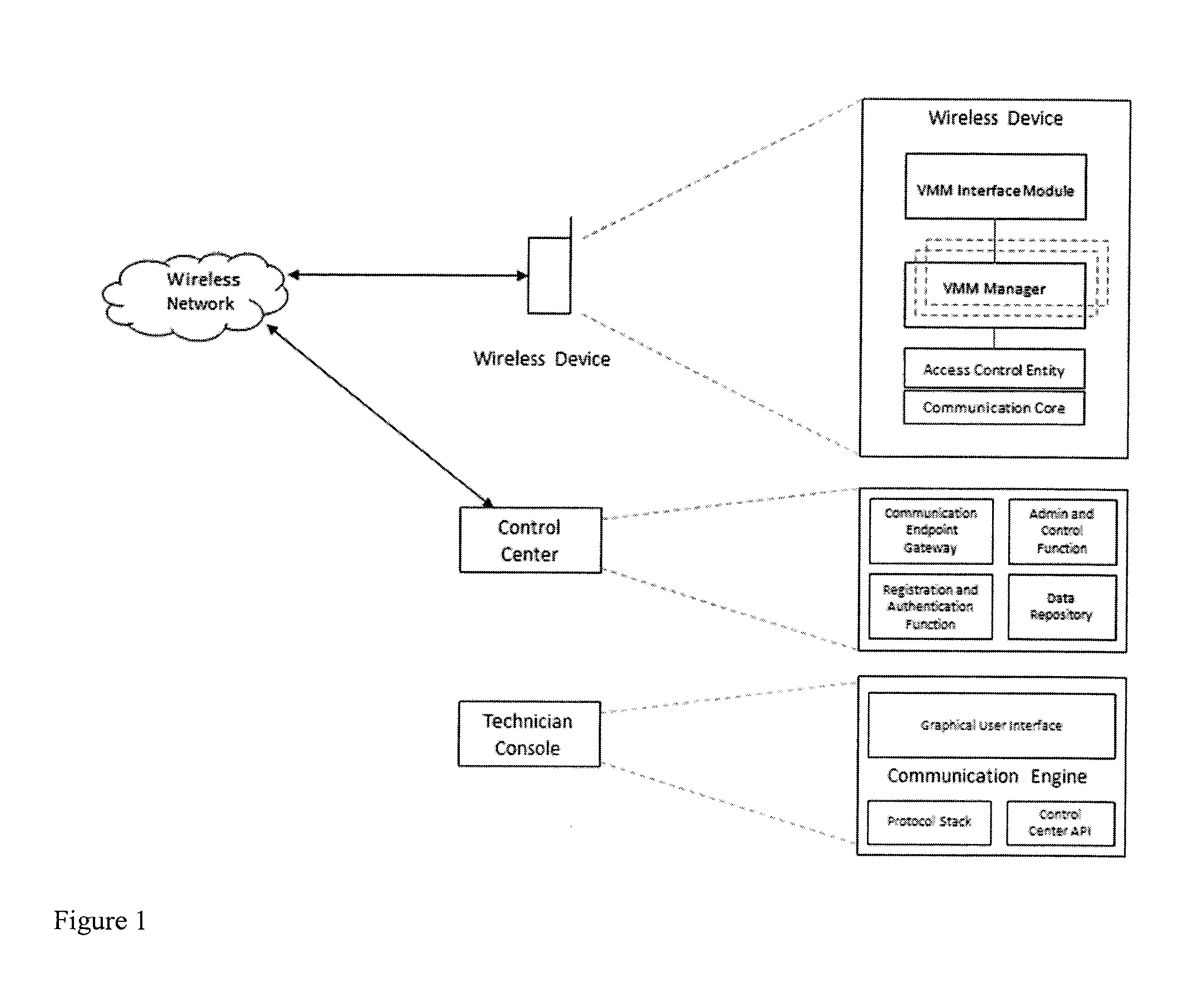
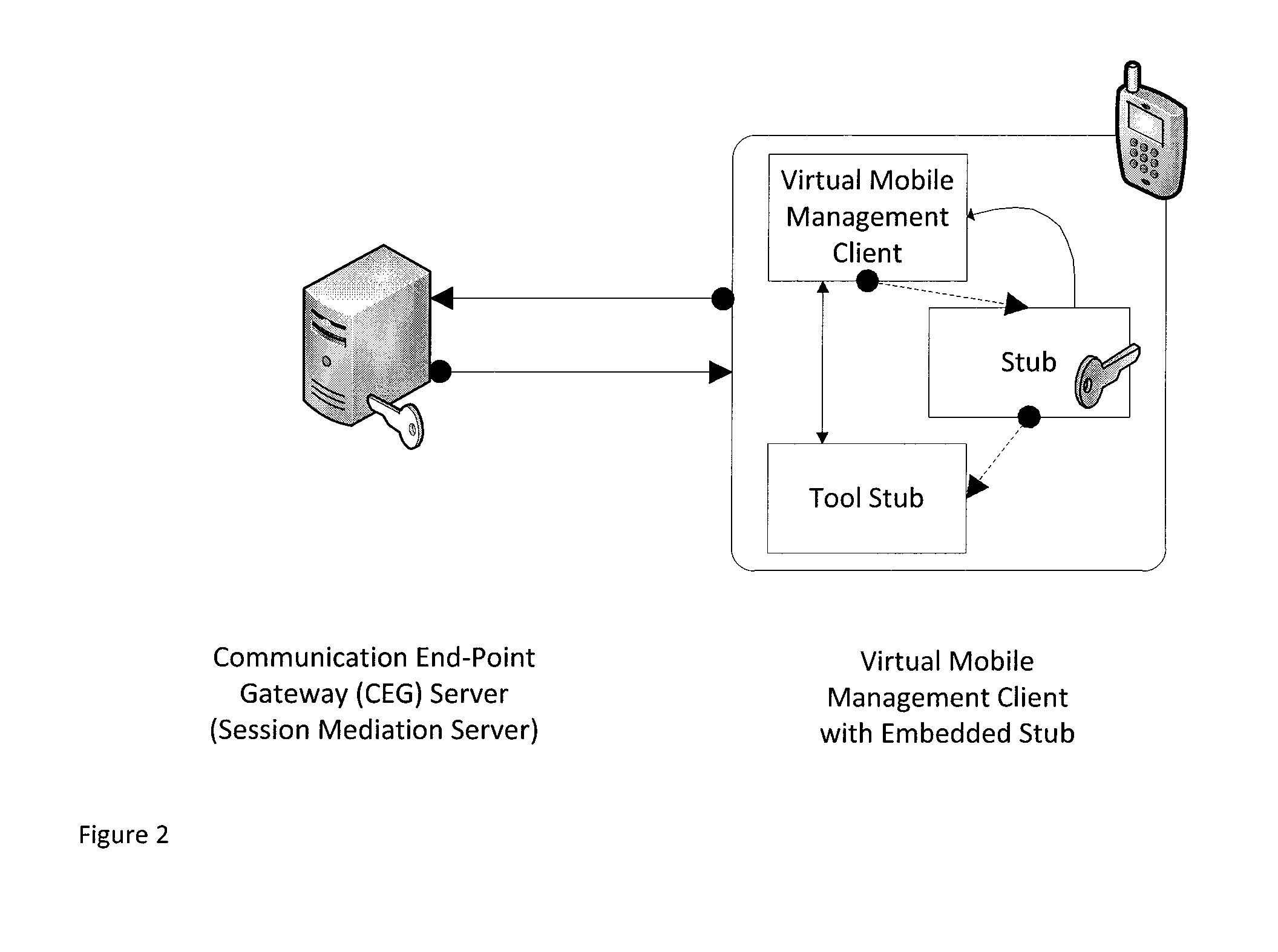
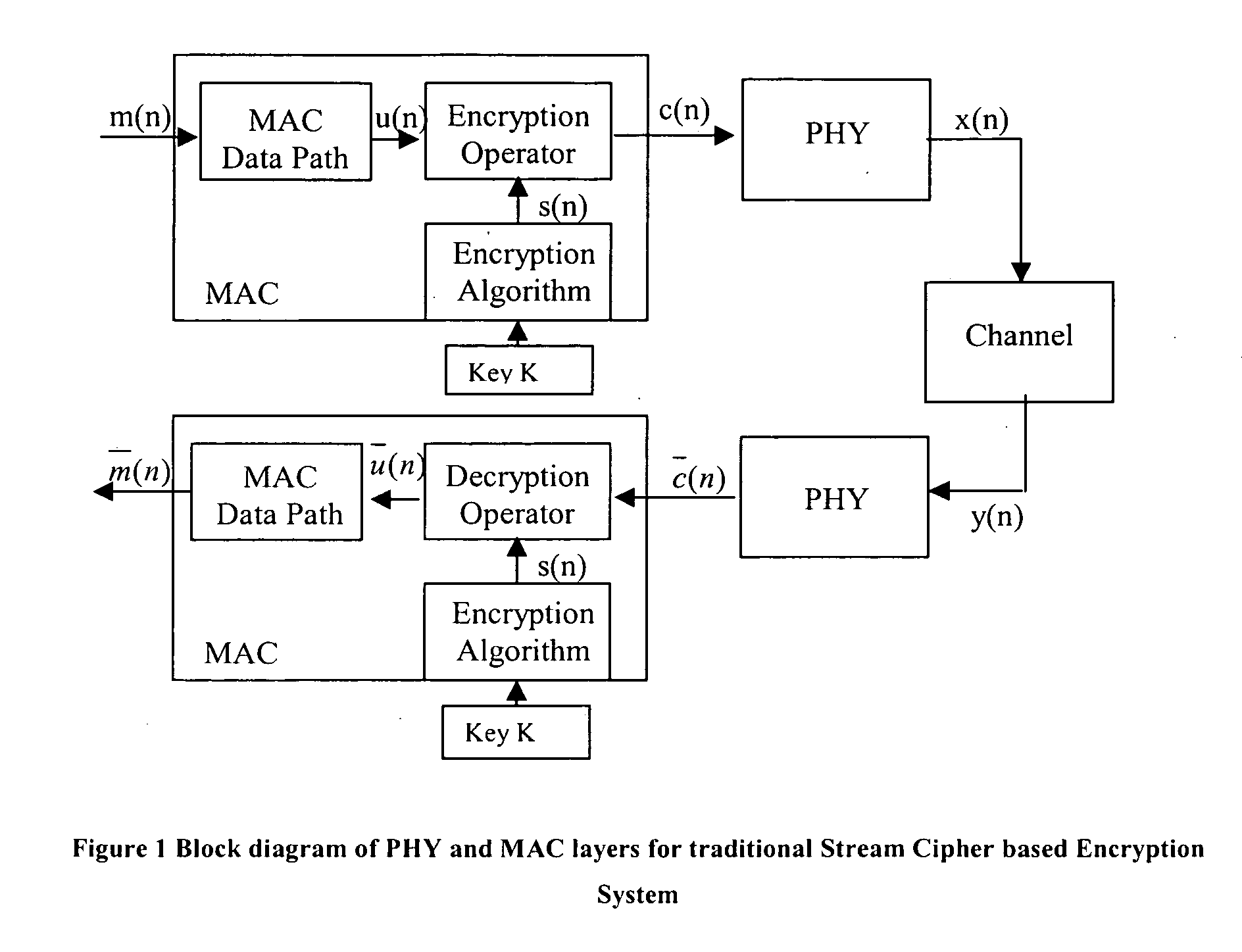
Connection authorization with a privileged access
InactiveUS20130067542A1Secure transmissionConnection securityDigital data processing detailsMultiple digital computer combinationsClient-sideSecret share
Owner:AETHERPAL
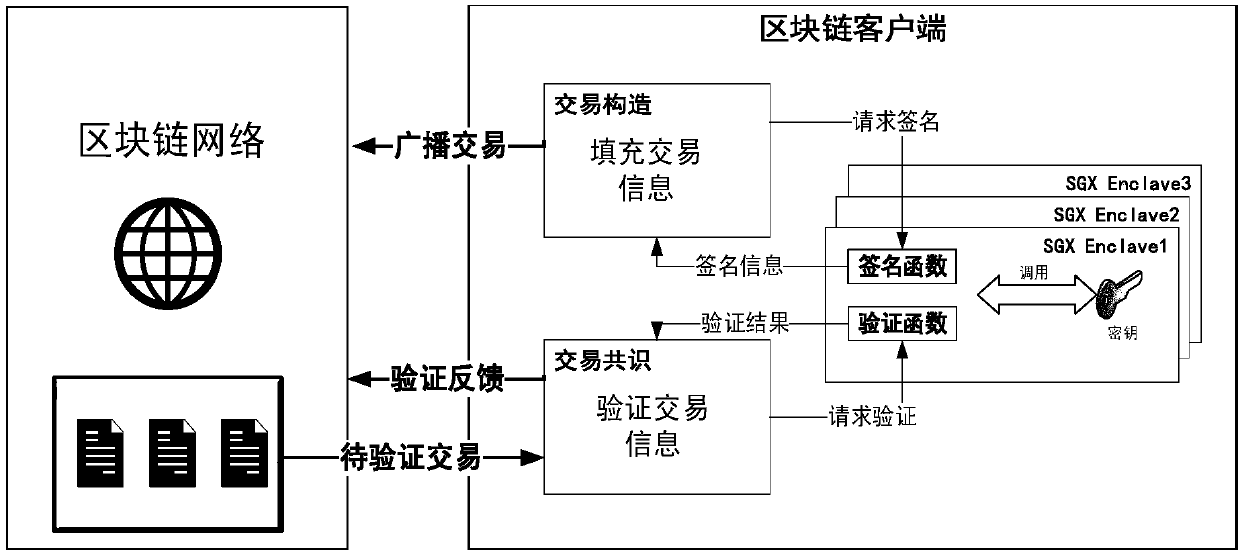
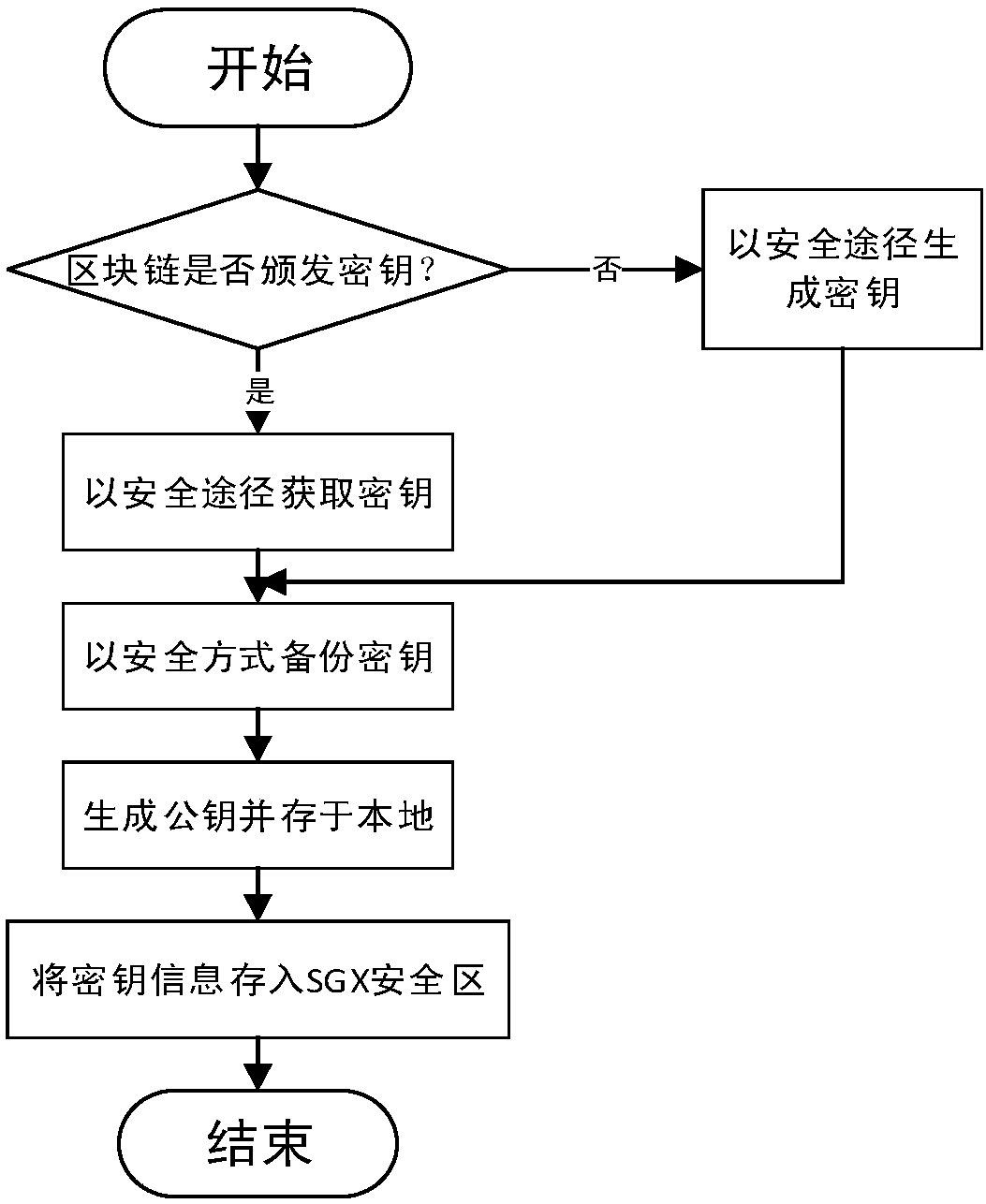
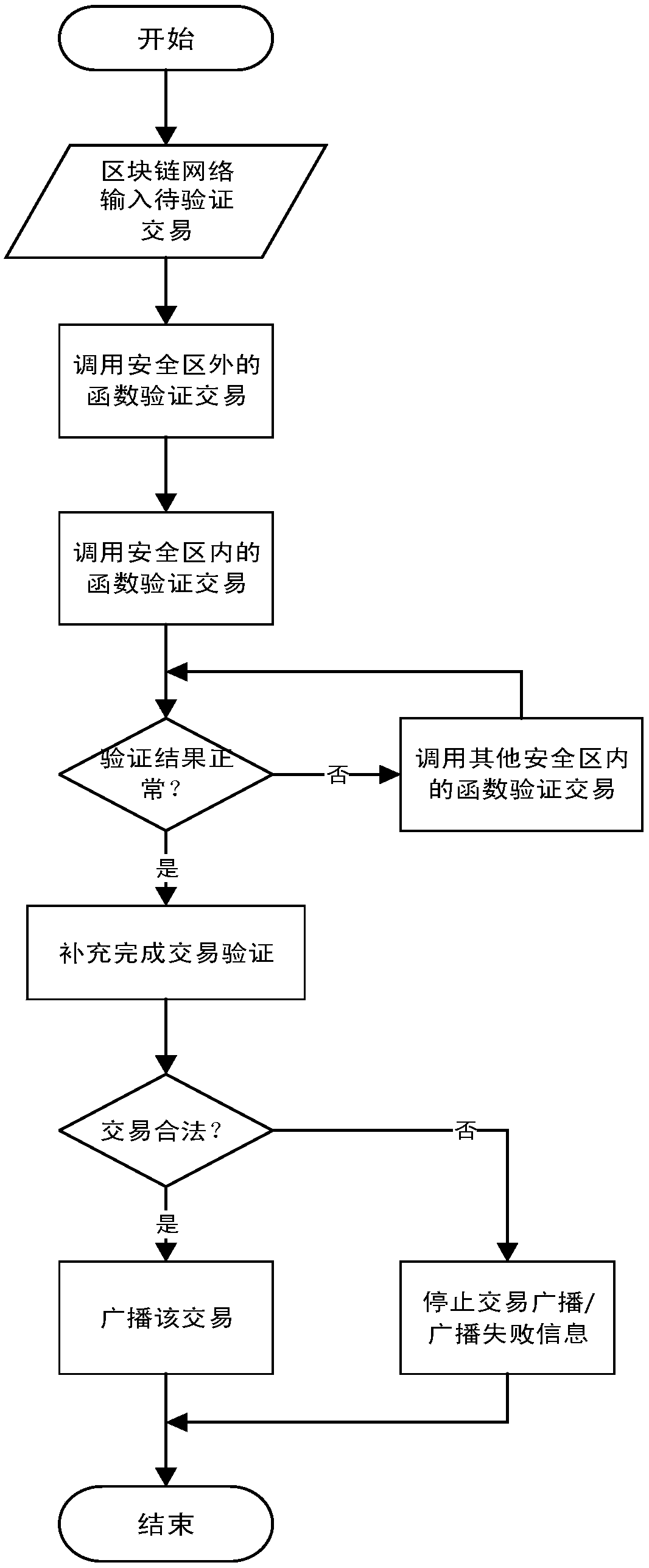
SGX-based secret key protection method and device for blockchain user
ActiveCN107919954AInviolableSafety and securityKey distribution for secure communicationPayment protocolsMalwareSoftware protection
The invention discloses an SGX-based secret key protection device for a blockchain user. The device comprises an SGX encryption module, a transaction common recognition module and a transaction construction module; the SGX encryption module generates a trustable space on the basis of a software protection expanded instruction, and generates an access secret key for verifying the access authority of the trustable space; the trustable space is used to store a user secret key and a secret key operation function of a blockchain network; the transaction common recognition module receives a transaction from the blockchain network, accesses the SGX encryption module via the access secret key, calls the secret key operation function, and realizes verification common-recognition of the transaction;and the transaction construction module initiates the transaction according to intention of the user, accesses the SGX encryption module via the access secret key, calls the secret key operation function, realizes filling and legalization of transaction information, and broadcasts the transaction to the blockchain network. The invention also discloses an SGX-based secret key protection method fora blockchain user. The method can be used to prevent malicious software from sniffing and cracking the local secret key of the user, and blockchain assets of the user are protected against intrusion.
Owner:ZHEJIANG UNIV
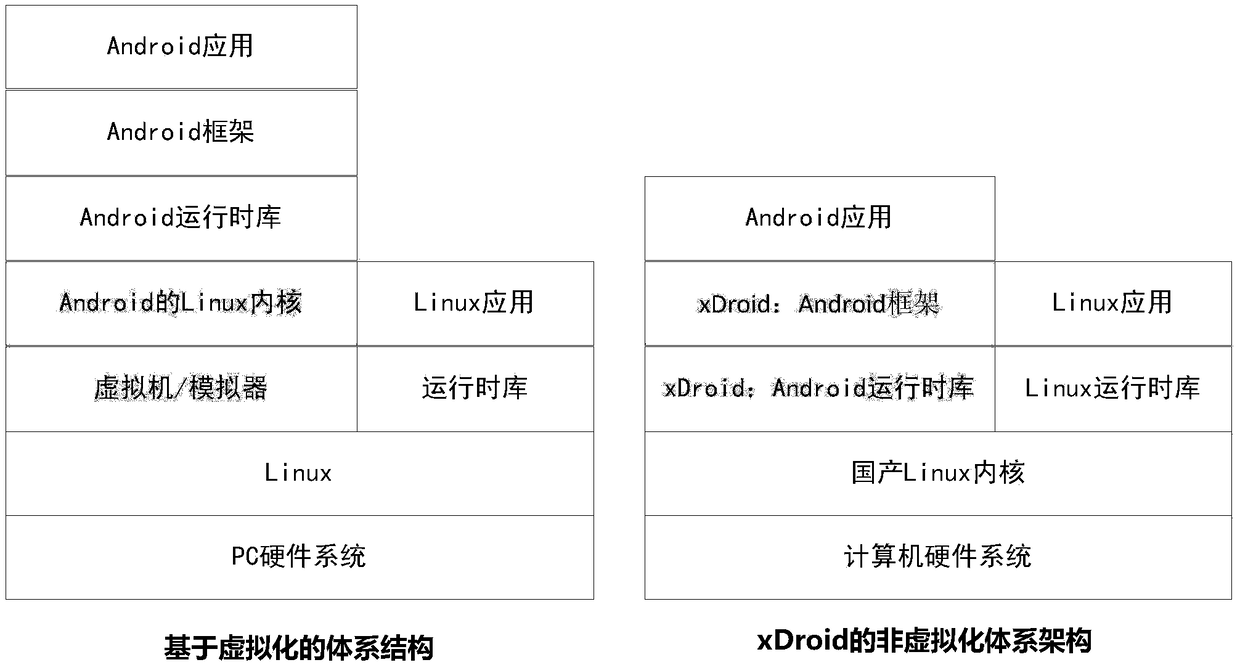
Android running environment realization method based on non-virtualized system architecture
The invention belongs to the field of computer basic software and relates to an Android running environment realization method based on a non-virtualized system architecture. According to the method,an Android running environment is constructed on an existing Linux kernel and recorded as xDroid, and an Android application framework and an Android running time library are migrated to a standard Linux kernel. The xDroid does not need the virtualization technology but stands from a basic library and a basic running mechanism provided by a desktop operating system kernel, an Android bottom running supporting library needed for Android application running is realized layer by layer from bottom to top, then efficient migration of the Android running time library is realized, and the Android running environment is realized on a desktop operating system platform. Compared with a virtualization-based technology, ecological complete fusion of desktop applications and Android applications is realized in a true sense through the xDroid, and the applications are high in starting speed and high in performance; and meanwhile realization is based on different platforms, so that cross-platform running is easy to realize.
Owner:北京麟卓信息科技有限公司
Means of mitigating denial of service attacks on IP fragmentation in high performance IPsec gateways
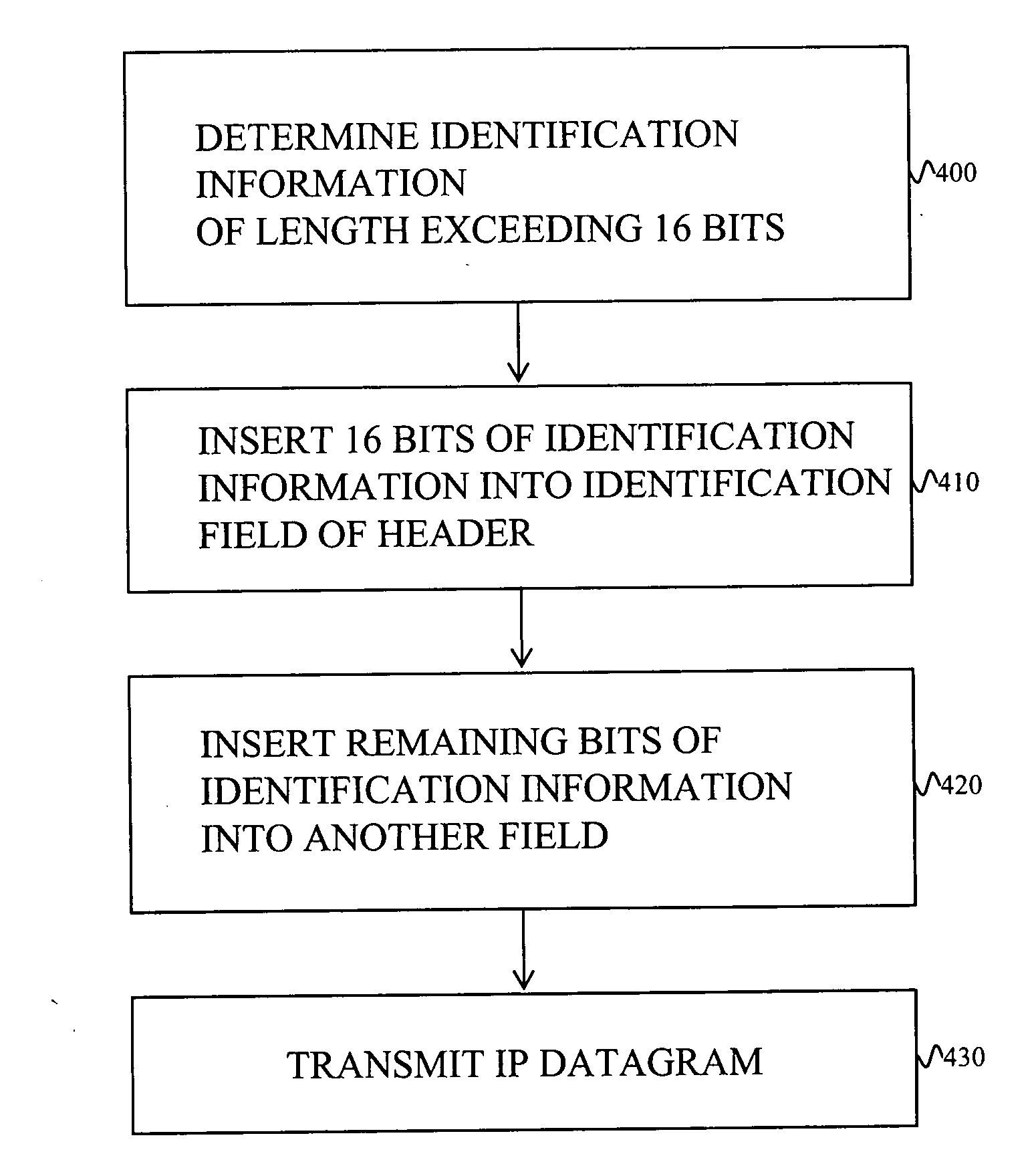
InactiveUS20070143598A1Lower success rateReduce probabilityMemory loss protectionError detection/correctionIPsecIP fragmentation
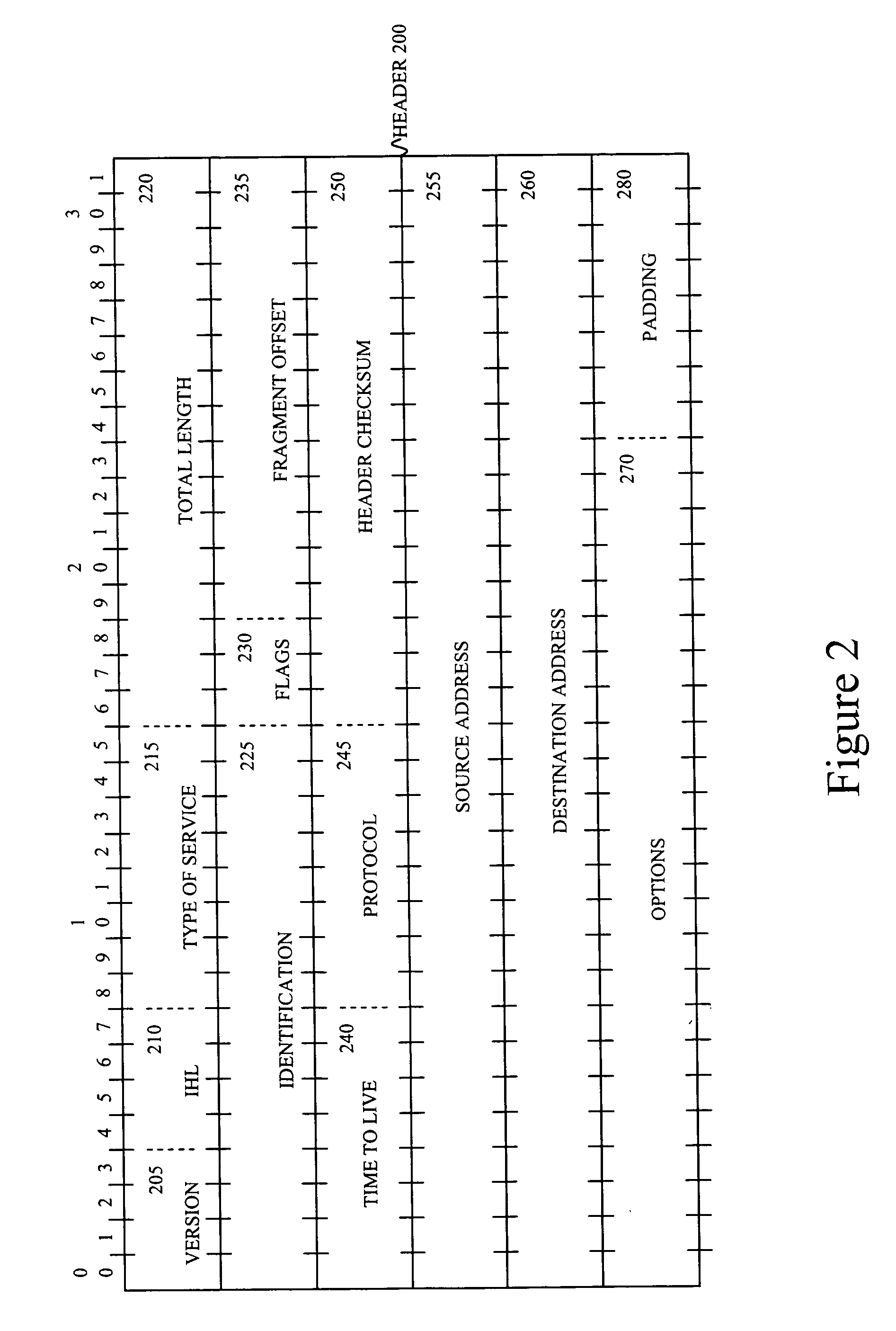
Embodiments of the invention reduce the probability of success of a DOS attack on a node receiving packets by decreasing the probability of random collisions of packets sent by a malicious user with those sent by honest users. The probability of random collisions may be reduced in one class of embodiments of the invention by supplementing the identification field of the IP header of each transmitted packet with at least one bit from another field of the header. The probability of random collisions may be reduced in another class of embodiments of the invention by ensuring that packets sent from a transmitting IPsec node to a receiving IPsec node are not fragmented.
Owner:RAYTHEON BBN TECH CORP +1
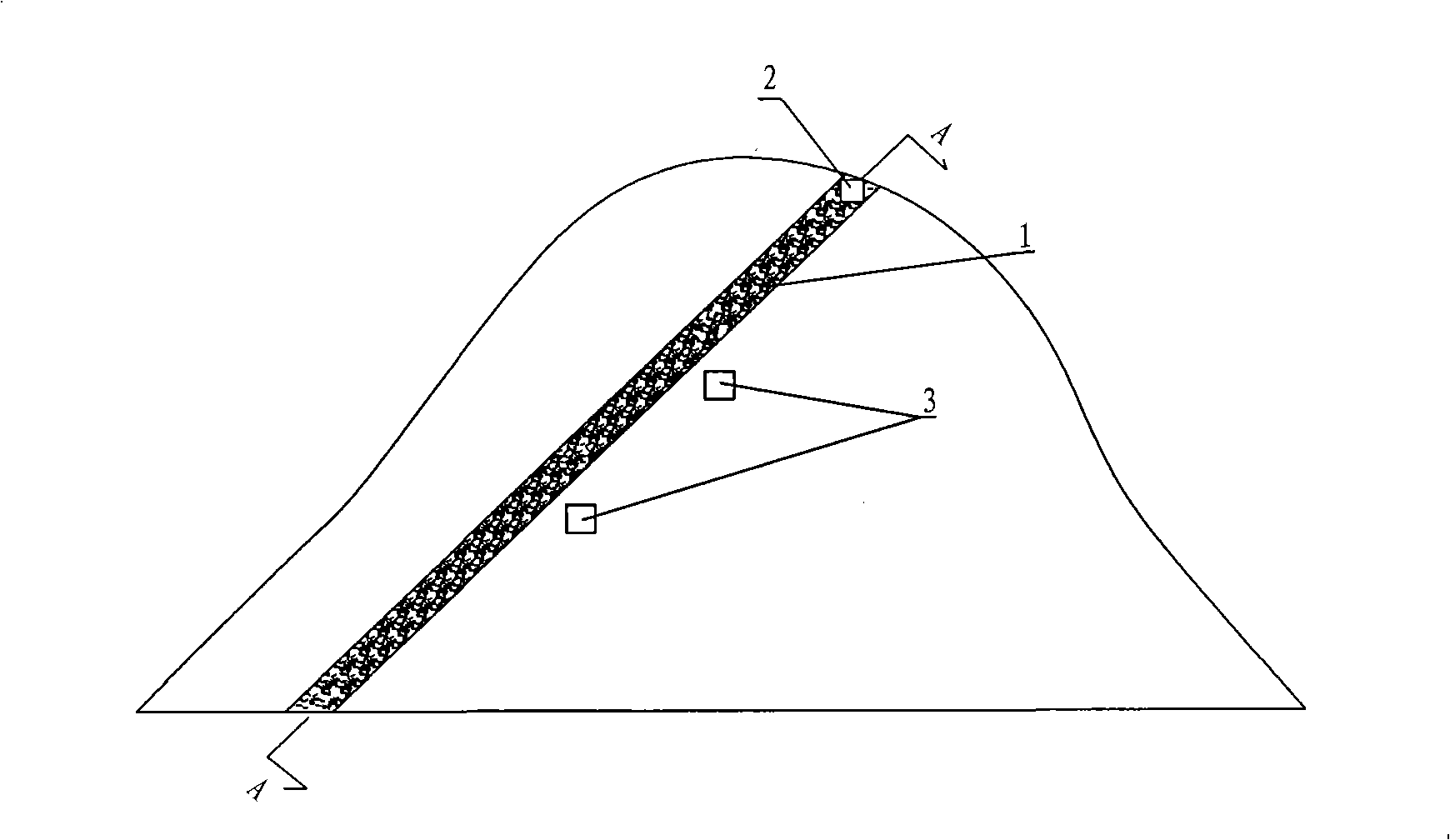
Sharply inclined coal seam mining method
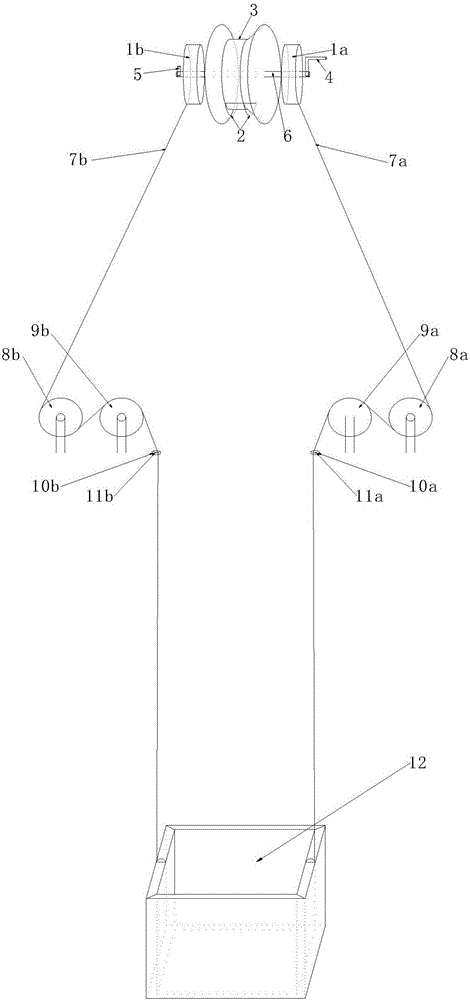
InactiveCN101307692AReduce security threatsSave support materialsUnderground miningSurface miningCoal miningEngineering
The invention discloses a method for mining a steeply inclined coal seam. The method comprises the following: step one, opening a return airway (2) and a first conveyor roadway (3) in the steeply inclined coal seam (1); step two, digging a first through cut (12), and placing a flexible shield support (5) on the first through cut (12) for roof control, thereby forming a false dip primary mining working surface (8); step three, starting coal mining on the primary mining working surface (8); step four, gradually extending the primary mining working surface (8) downwards to produce a second through cut (11) for the coal seam of the next section opposite to the inclined direction of the primary mining working surface (8), when the primary mining working surface (8) is propelled to the position of the second through cut (11) which is designed for the coal seam of the next section, and mining the coal seam of the next section; step five, mining the lower coal seam with the step four, and continuously and recurrently mining the whole steeply inclined coal seam (1) from the bottom to the top. The method has the advantages of high mining efficiency, safer mining and high percentage of recovery.
Owner:邹开科
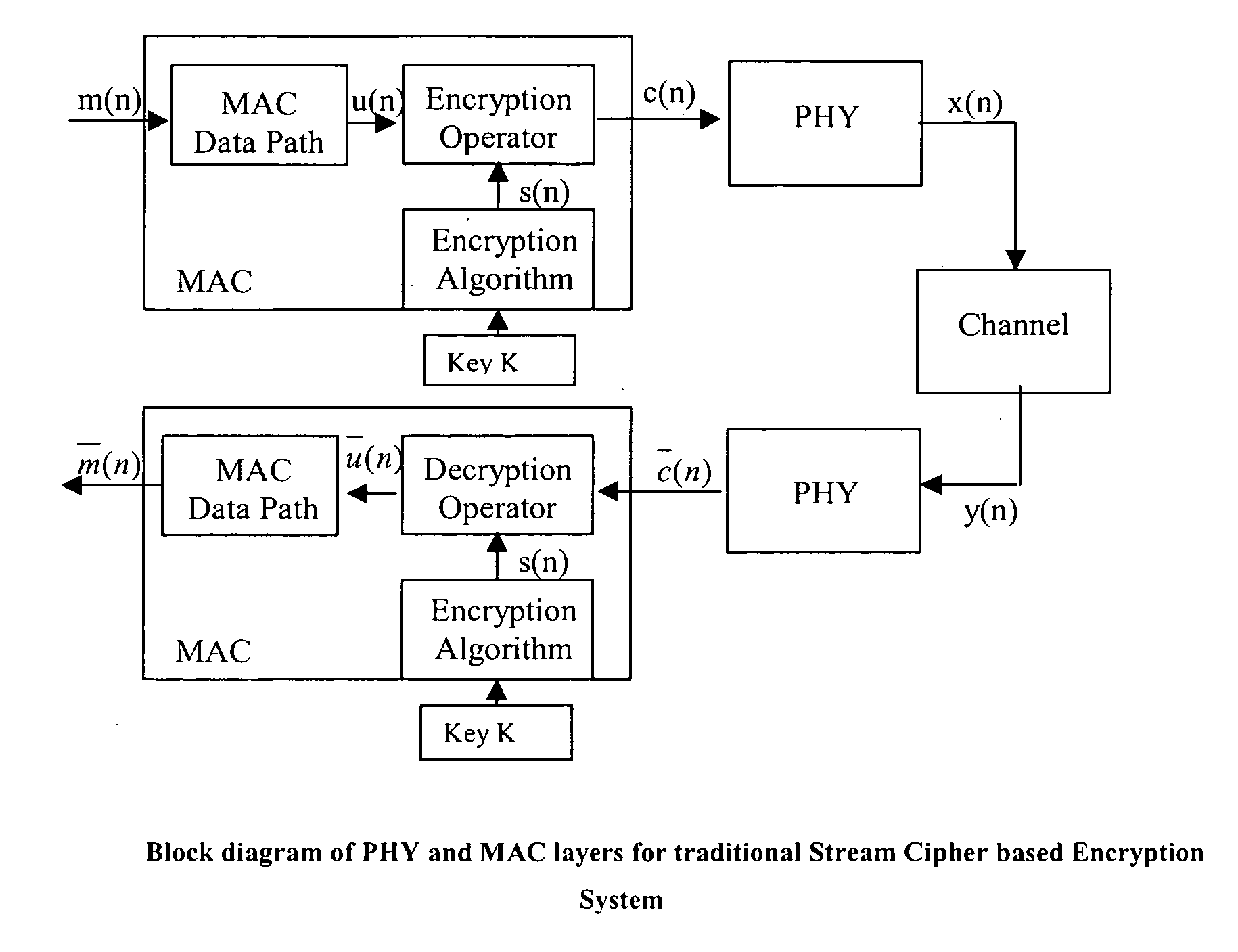
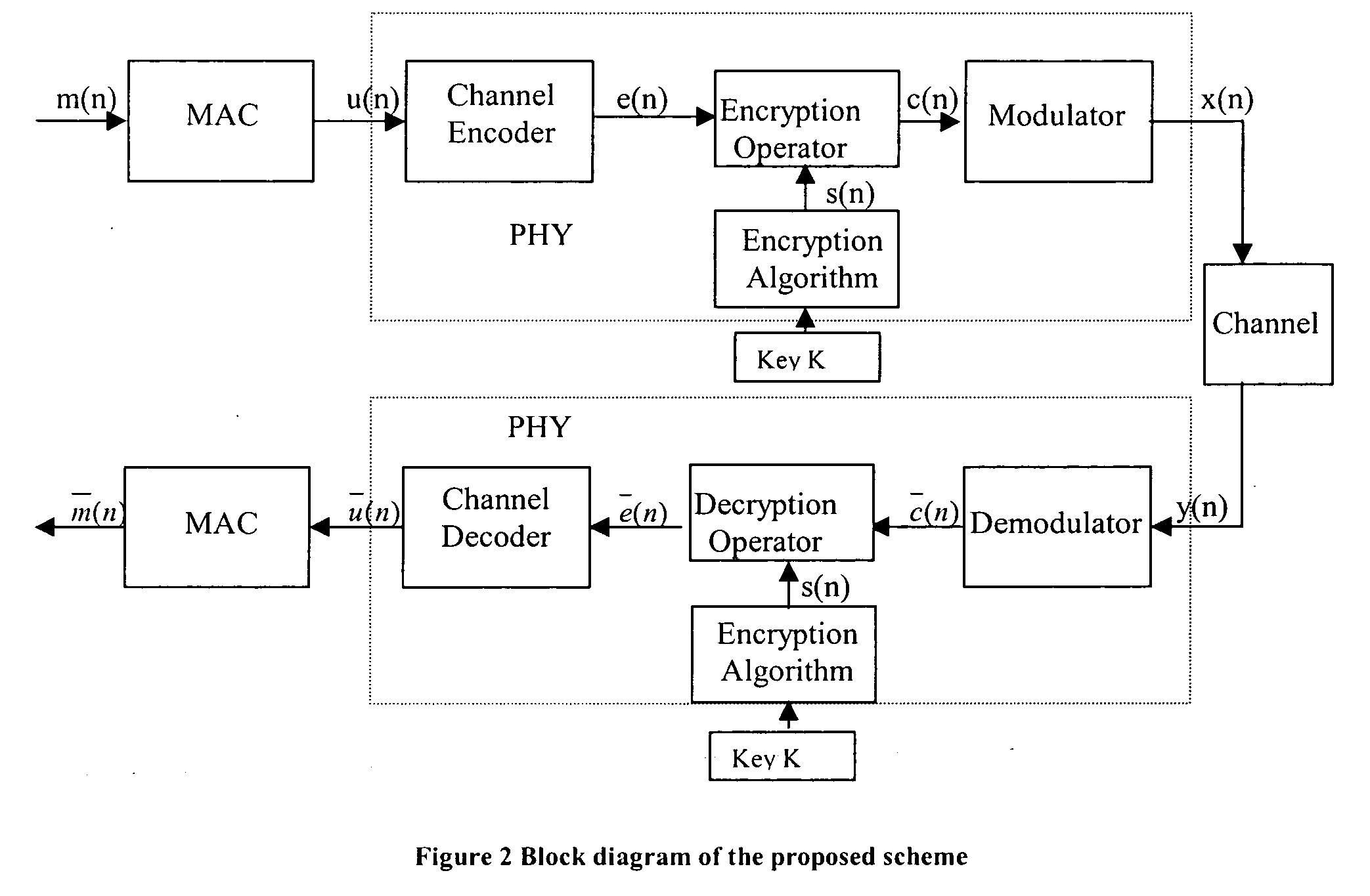
Method and apparatus for a security system for wireless networks
InactiveUS20060126841A1Avoid attackImprove communication performanceData stream serial/continuous modificationSecret communicationViterbi decoderCommunications system
A Method and Apparatus for a Security System for Wireless Networks is described. The technique involves encryption and decryption at the Physical layer. It also develops a criterion for choosing the encryption / decryption methodology for a particular embodiment for communication systems typically using a Viterbi Decoder and describes how the difficult-to-invert property of the Viterbi Decoder can be utilized to provide security against known-plaintext attacks. Some candidate encryption / decryption methodologies satisfying the developed criterion are also discussed.
Owner:TATA CONSULTANCY SERVICES LTD
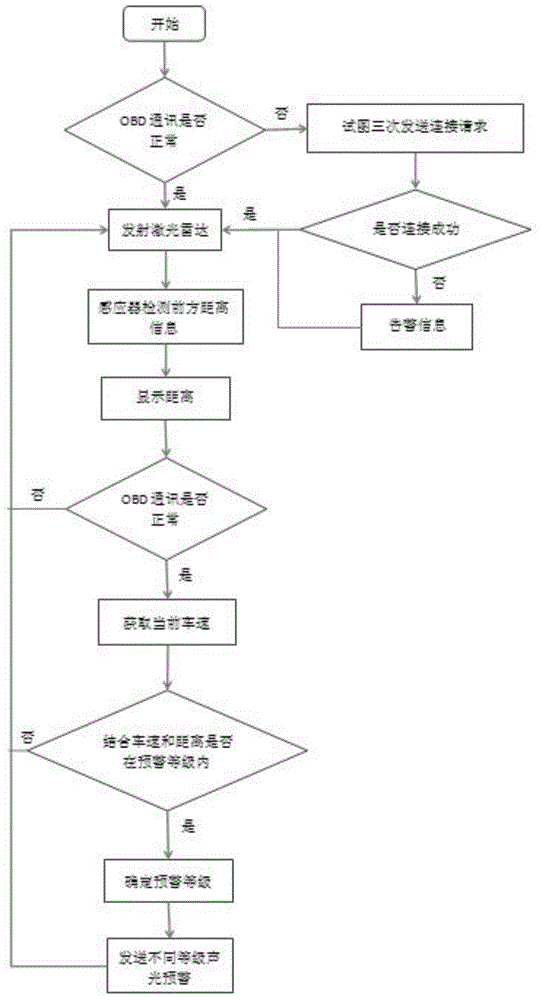
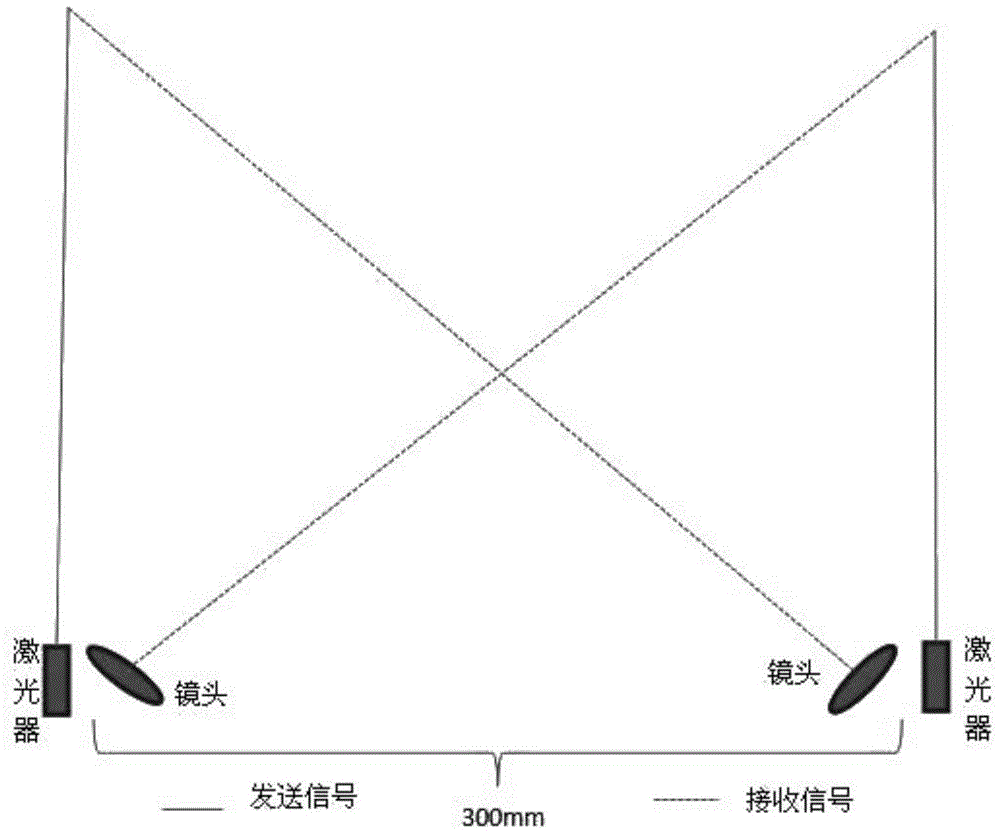
Vehicle anti-collision early warning system based on laser radar ranging
ActiveCN104808216AImprove experienceAccurate anti-collision active warning servicePedestrian/occupant safety arrangementElectromagnetic wave reradiationLaser rangingCamera lens
The invention discloses a vehicle anti-collision early warning system based on laser radar ranging. The vehicle anti-collision early warning system comprises 2n laser radar emitters and 2n optical lenses, wherein n is a natural number. Each laser radar emitter is paired with one optical lens to form a signal receiving and transmitting group. Each signal receiving and transmitting group is arranged along the central axis of a vehicle. An acute angle is formed between each optical lens and the vertical direction of the corresponding laser radar emitter. The laser radar emitters on one side of the central axis emit laser signals, and the laser signals are scattered after contacting with objects in places ahead and are received by the optical lenses at corresponding positions on the other side of the central axis. The vehicle anti-collision early warning system has the advantages that through intelligent anti-collision active early warning based on accurate laser radar ranging, users can get better experience effects; double-lens design is adopted, the lenses are treated specially in terms of optical design, and high-accuracy optical imaging and detecting and lens structure design applicable to complex in-vehicle environments can be guaranteed.
Owner:南京瞳乐信息科技有限公司
Dual-end recursive path computation element (PCE)-based computation method and device
InactiveCN102195869AReduce security threatsImprove business performanceData switching networksPath computation elementMulti protocol
The invention discloses a dual-end recursive path computation element (PCE)-based computation method. In the method, path computation is initiated at the same time at a source domain PCE and a destination domain PCE, and an intermediate domain PCE obtains the shortest path from a source node and a destination node by a result obtained by dual-end path computation. The invention also discloses a dual-end recursive PCE-based computation device. By the method and the device, time required by end-to-end path computation can be shortened maximally, thereby improving the performance of services transmitted by a network and simultaneously reducing security threats to the path computation. Particularly, more remarkable effects can be achieved in large-scale multi-domain multi-protocol label switching (MPLS) and generalized MPLS (GMPLS) networks.
Owner:ZTE CORP
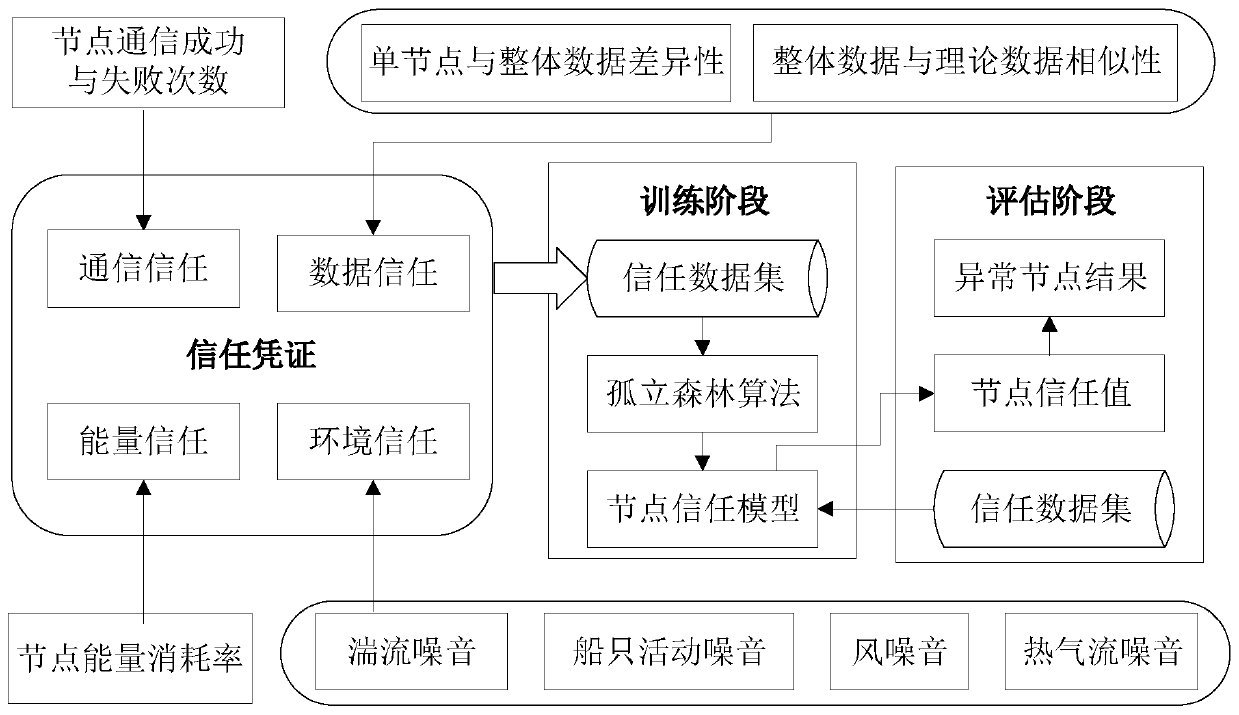
Trust model based on isolated forest in UASNs
ActiveCN110536258AImprove the detection rate of abnormal nodesReduce security threatsParticular environment based servicesSecurity arrangementEnvironmental noiseNODAL
The invention belongs to the technical field of wireless sensor network security, and discloses a trust model based on an isolated forest in UASNs. Firstly, trust items needing to be evaluated are divided into four types including communication trust, data trust, energy trust and environment trust, and particularly, in the data trust calculation process, the similarity between overall data distribution and theoretical data distribution in UASNs is considered besides the difference between a single node and overall data distribution. Due to the fact that environmental noise can influence communication and data transmission between nodes, energy changes are caused, evaluation errors of other trust items can be reduced by increasing environmental trust, and the accuracy of malicious detectionis improved. Then, the four trust items as a trust training set is taken, and a node trust model is established by adopting an isolated forest algorithm; and finally, reliability evaluation is performed on the nodes in the UASNs based on the node trust model, attacks of abnormal nodes and malicious nodes in the UASNs are effectively detected, and network security threats are reduced.
Owner:DALIAN UNIV OF TECH
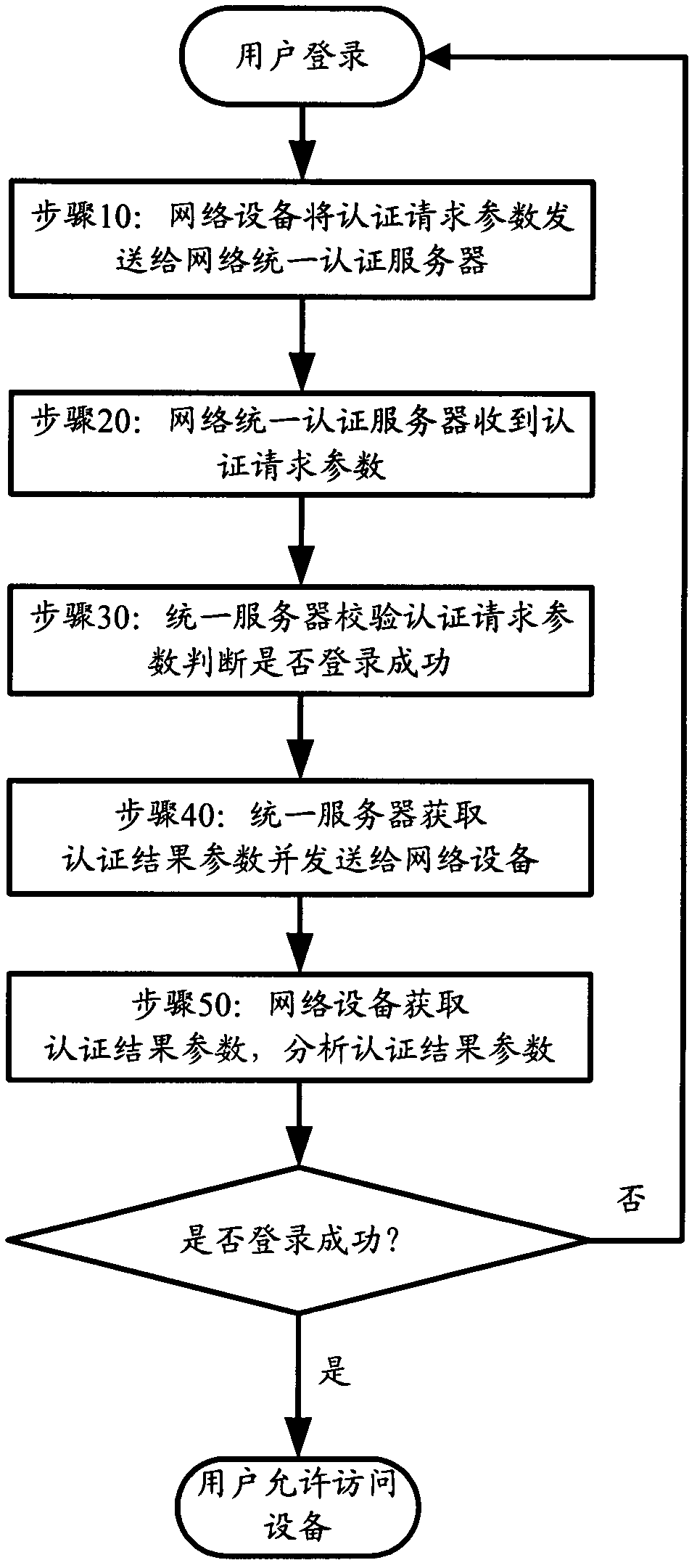
User identity authentication method and system
InactiveCN102307097ARealize centralized managementIncrease flexibilityUser identity/authority verificationUser authenticationAuthentication server
The invention provides a user identity authentication method, which comprises the following steps of: uniformly storing and recording authentication parameters of user identity into a unified authentication server, and uniformly authenticating the legality of the user identity by using the unified authentication server when a user logs in network equipment. The invention also provides a user identity authentication system. By the user identity authentication method and the user identity authentication system, security-policy-based unified user management and authentication can be realized, the unified authentication of a plurality of pieces of network equipment over the user identity is realized and the maintenance difficulties and complexity of a network equipment manager are reduced simultaneously, thereby reducing production cost and threats to information security.
Owner:ZICT TECH CO LTD
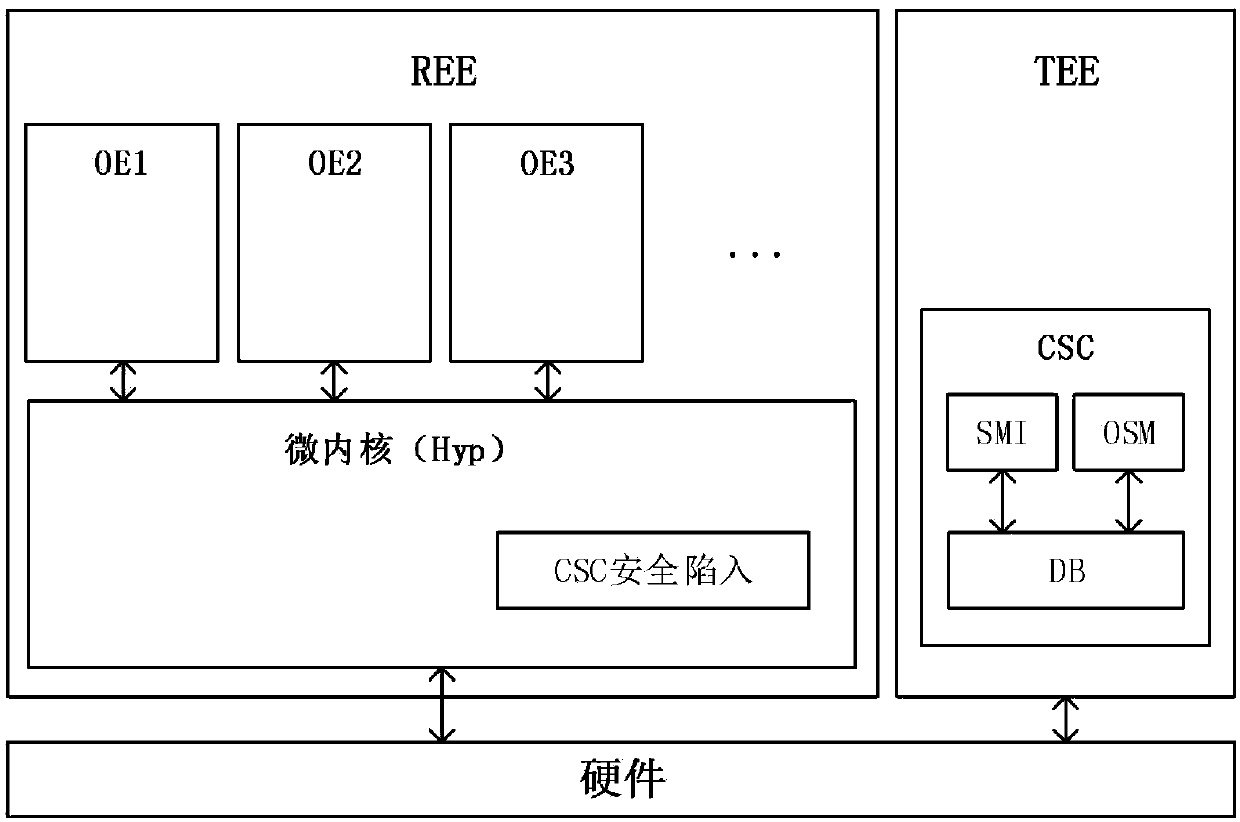
Mobile terminal trusted isolation environment core control method
ActiveCN109522754AImprove security featuresReduce security threatsInternal/peripheral component protectionProgram controlSecurity domainTerm memory
The invention discloses a mobile terminal trusted isolation environment core control method, and aims to solve the trusted isolation problem of different operation environments in a mobile terminal, and a core controller CSC in a security domain is realized based on a TrustZone technology, so that the trusted isolation security among different operation environments is enhanced. According to control of the fine-grained security policy library, memory access behaviors of different operation environments are supervised, and it is ensured that codes and data cannot be accessed by different operation environments; And the operation states of different operation environments are supervised to ensure that illegal operations cannot obtain corresponding authorities.
Owner:INST OF INFORMATION ENG CAS
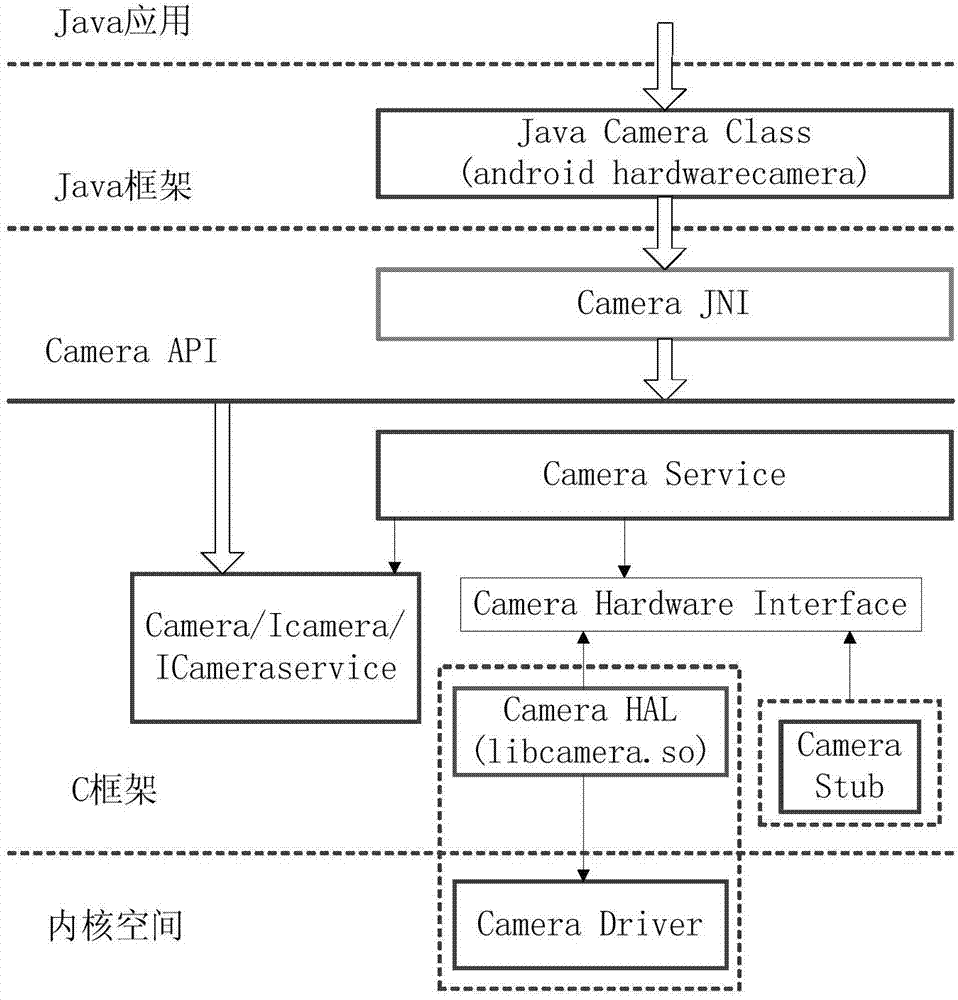
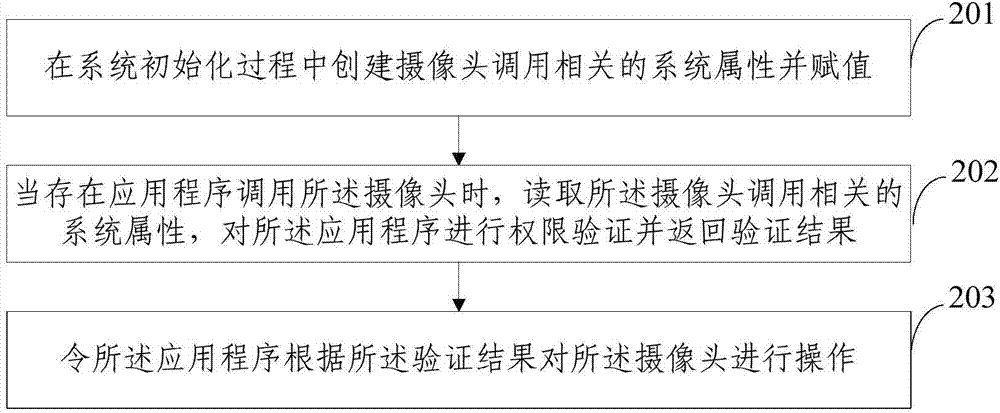
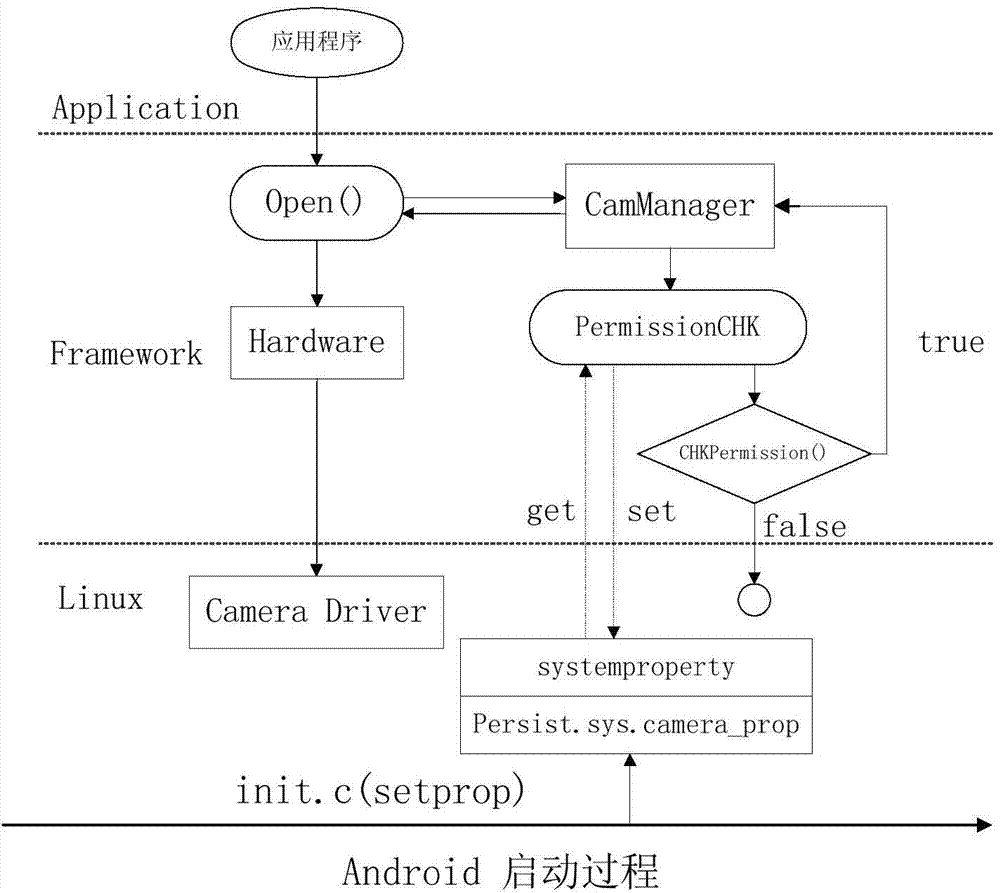
Method and device for managing calling authority of camera
InactiveCN104268463AImprove securityEnsure safetyComputer security arrangementsSubstation equipmentApplication softwareComputer science
The invention provides a method and a device for managing the calling authority of a camera. The method comprises the following steps of: creating system attributes related to calling for the camera and assigning during a system initialization process; when an application program calls the camera, reading the system attributes related to calling for the camera, carrying out authority verification on the application program and returning a verification result; enabling the application program to operate the camera according to the verification result. The method and the device provided by the invention are capable of reducing the security threats of the application program on a system platform from a system level, and controlling and managing the camera resources of the system, thus ensuring the security of data during the calling process for the camera, and effectively preventing privacy disclosure.
Owner:INST OF INFORMATION ENG CHINESE ACAD OF SCI
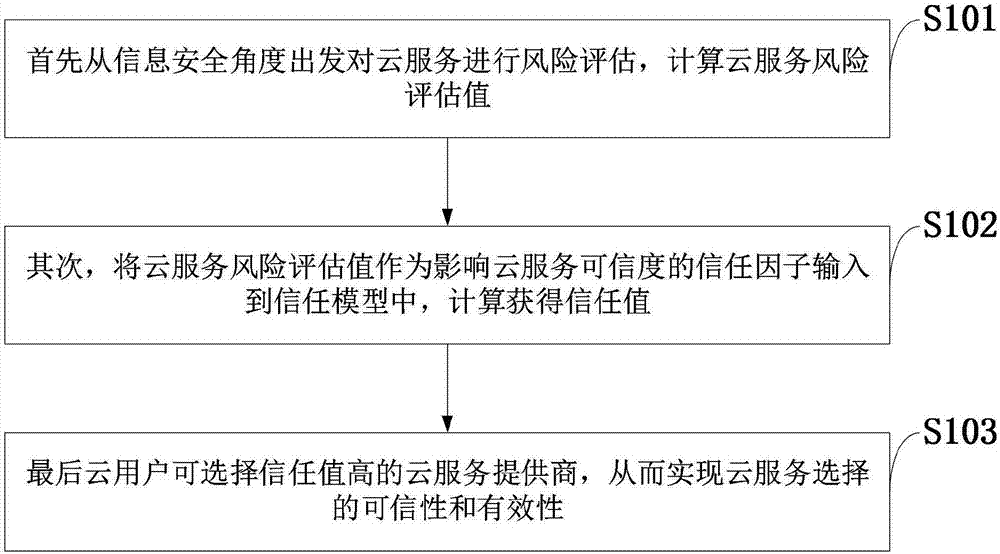
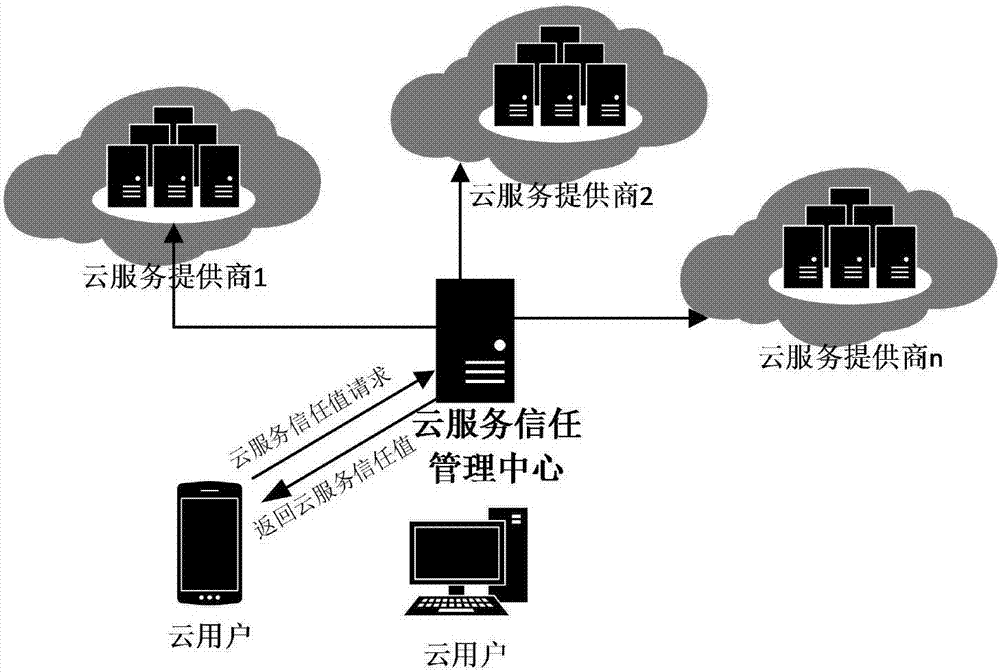
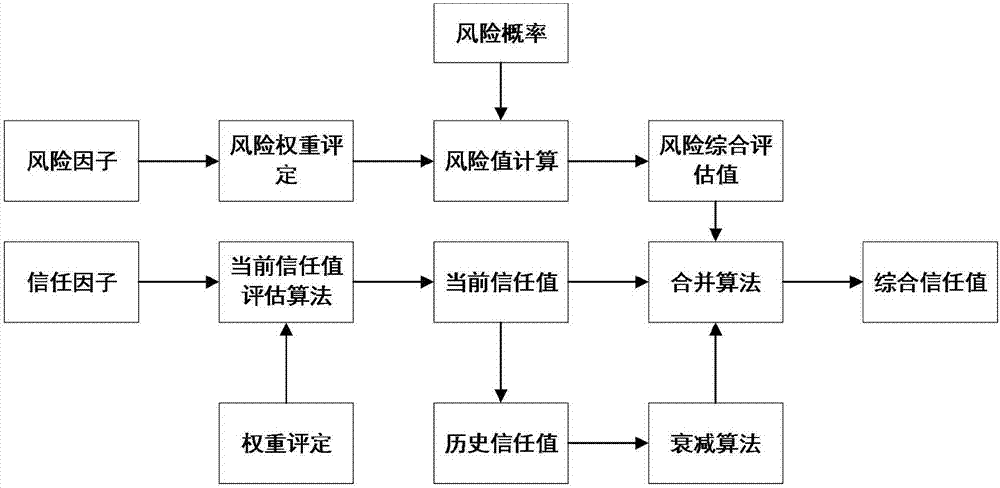
Trusted cloud service selection method based on risk assessment, cloud system, and cloud server
InactiveCN107249015ACredibility measurementImprove securityResourcesTransmissionCloud userConfidentiality
The invention belongs to the technical field of cloud service security, and discloses a trusted cloud service selection method based on risk assessment, a cloud system, and a cloud server. Starting from the perspective of risk assessment, the confidentiality, integrity, availability and controllability indexes of a cloud service are input as risk factors to calculate the risk assessment value of the cloud service. The risk assessment value is input to a trust model as one of evaluation indexes affecting the credibility of the cloud service to calculate the trust value of the cloud service. Risk assessment is introduced to a cloud service trust model. On one hand, the security of cloud services can be measured, and the credibility of cloud service providers can be assessed more comprehensively. On the other hand, cloud service providers can develop effective strategies according to the risk assessment results in order to reduce the possibility of security threats, improve the security and credibility of cloud services, and increase the trust degree of cloud users to cloud services, and cloud users can select more credible cloud service providers according to the trust values to realize credible and effective cloud service selection.
Owner:XIAN UNIV OF FINANCE & ECONOMICS
Mimicry switch judgment system and method based on trusted measurement
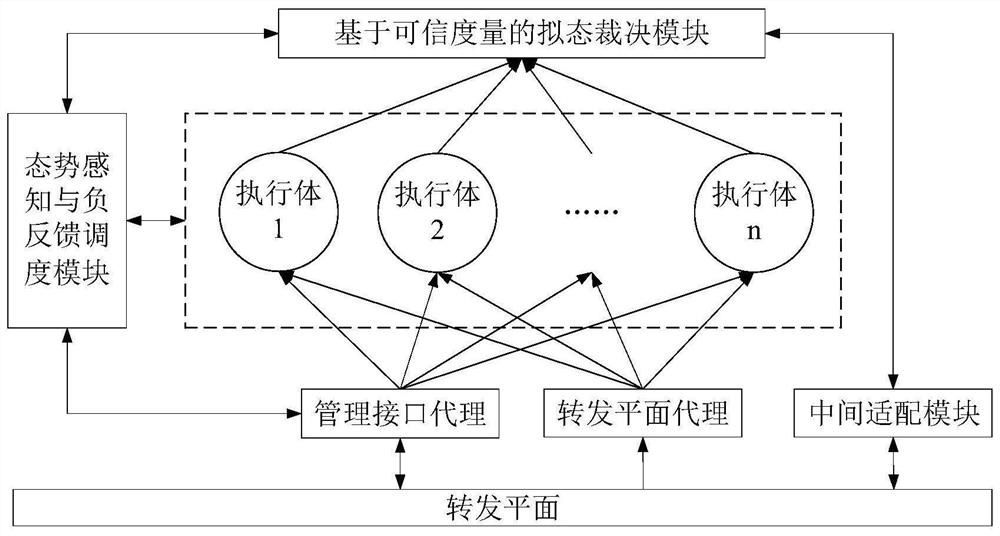
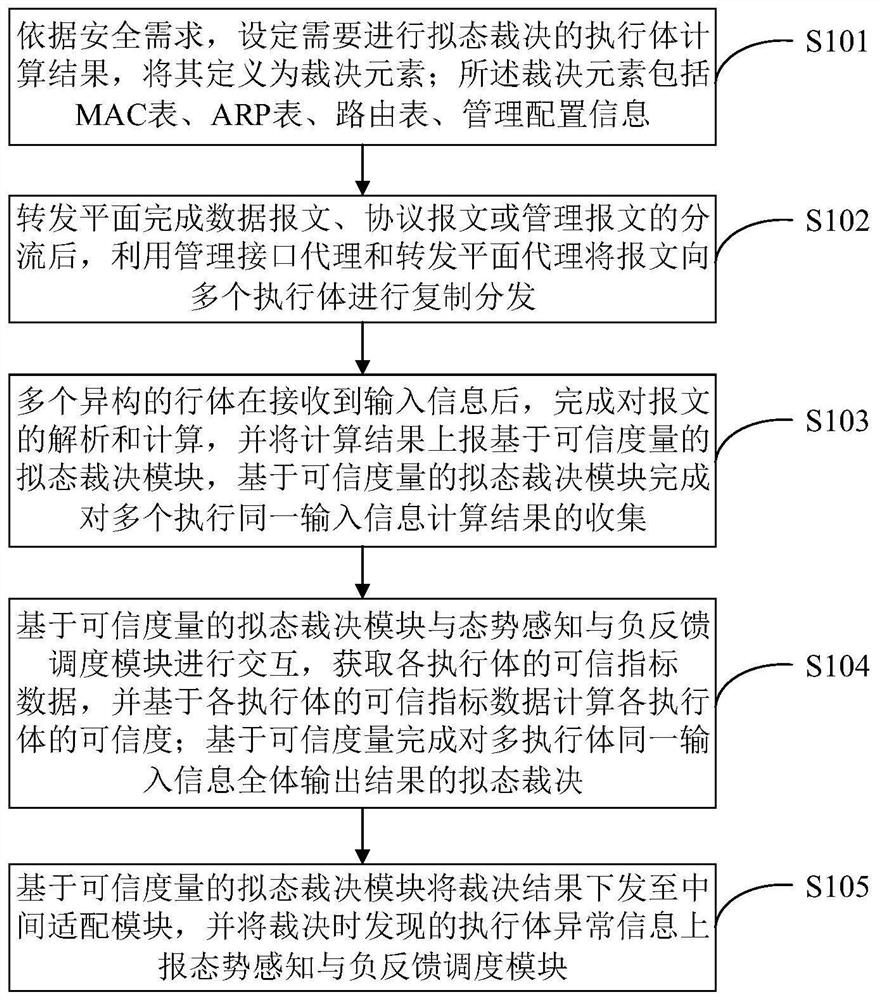
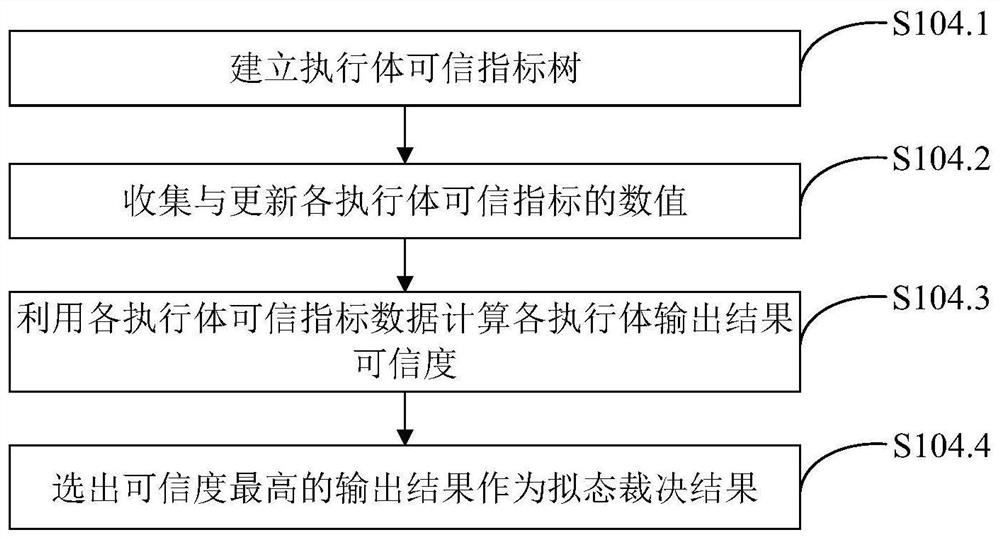
ActiveCN111884996AReduce security threatsImprove the level of security protectionData switching networksComplex mathematical operationsDecision systemInformation Harvesting
The invention belongs to the technical field of network security, and discloses a mimicry switch decision system based on trusted measurement, and the system comprises a forwarding plane, a managementinterface agent, an intermediate adaptation module, a forwarding plane agent, a plurality of heterogeneous actuators, a trusted measurement-based mimicry decision module and a situation awareness andnegative feedback scheduling module. The invention further discloses a mimicry switch judgment method based on trusted measurement. The mimicry switch judgment method comprises the steps: setting mimicry switch judgment elements; distributing input information; collecting output information; carrying out mimicry decision based on credibility measurement; issuing a judgment result, sensing the threat situation of the switch, and scheduling an executor; the mimicry decision based on credibility measurement comprises the following steps: establishing an executive credible index tree; collectingand updating the credible index data of the executive body; calculating the credible weight of the output result of each executive body; and calculating the credibility of each output result. The method can effectively reduce the influence of unknown loopholes and potential backdoors, and improves the safety protection level of a local area network.
Owner:PLA STRATEGIC SUPPORT FORCE INFORMATION ENG UNIV PLA SSF IEU +1
Preparation method, application and using process of floating agent prepared from drainage oil
The invention relates to a preparation method, application and using process of a floating agent prepared from drainage oil, wherein the preparation method of the floating agent comprises the following steps of: (a) purifying the drainage oil; (b) carrying out hydrolysis reaction on the purified drainage oil obtained from the step (a) to obtain the floating agent used for floating ores. When the floating agent used by the invention and prepared from the drainage oil is used as a collecting agent for floating the ores, the selectivity of the collecting agent can be enhanced, and the technical indicator and the economic indicator of flotation are enhanced favorably; and in addition, because a raw material used for the preparation of the floating agent is the drainage oil, the technical scheme provided by the invention has important significance on the aspects of preventing environmental pollution, simplifying production process, reducing food security threat, and the like.
Owner:鄂尔多斯市君致清环境科技有限公司
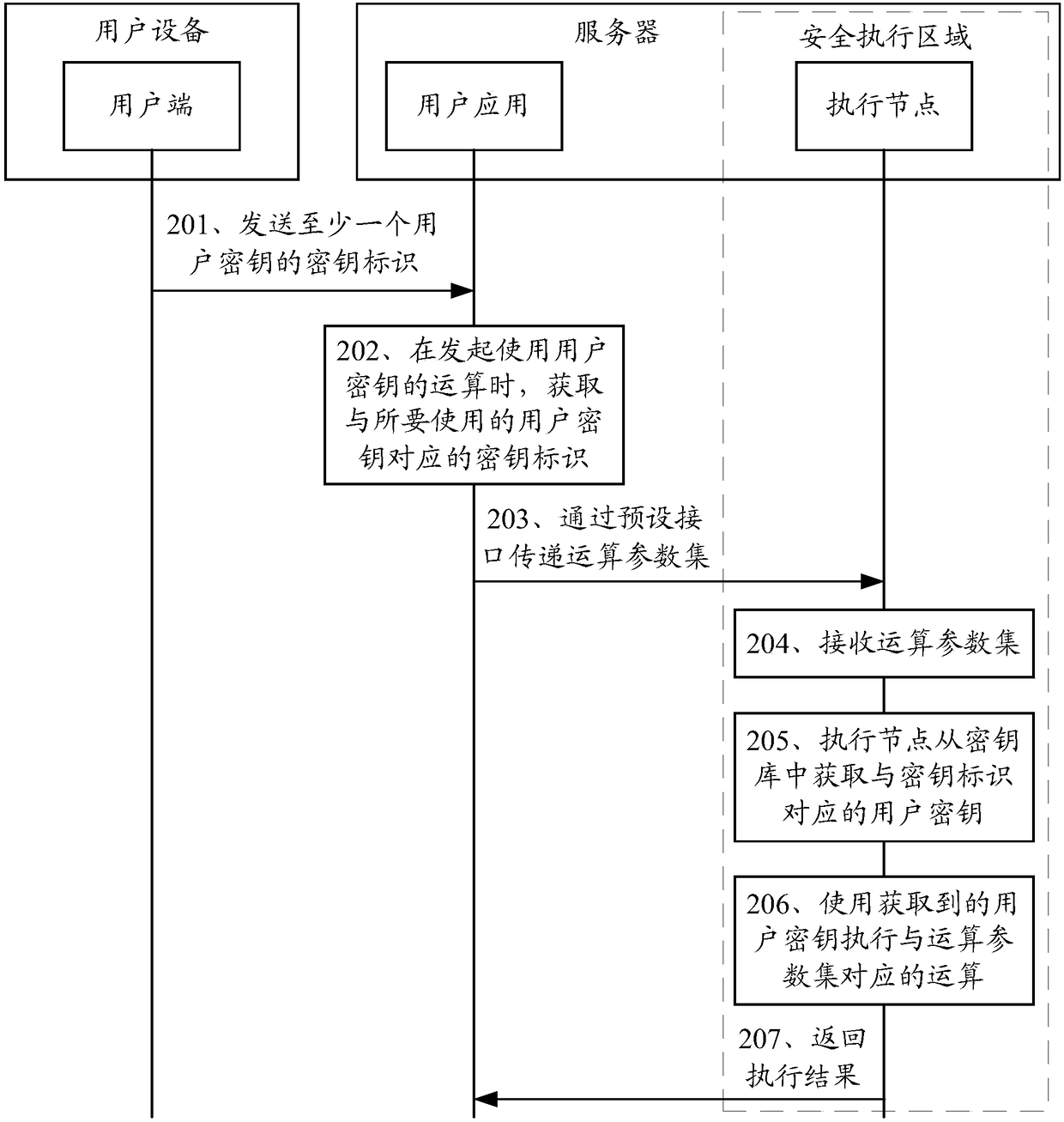
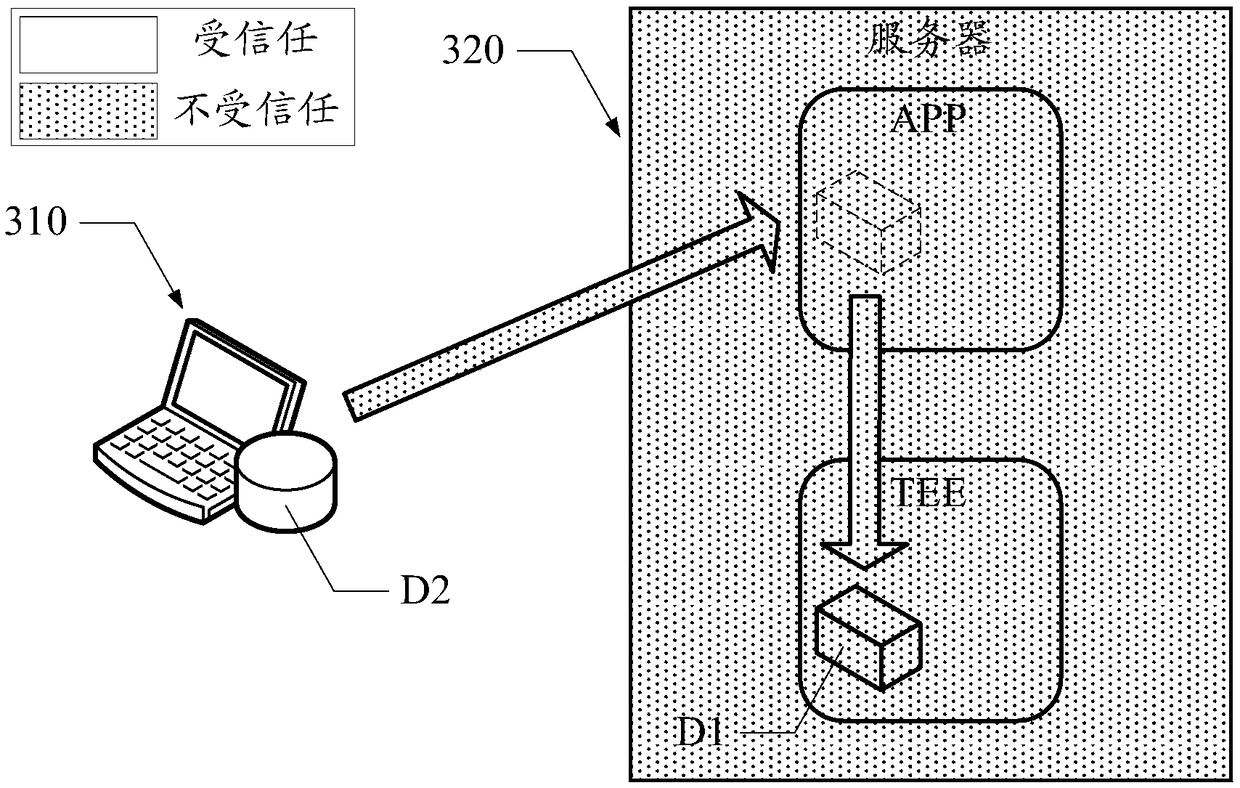
Key protection method and device
ActiveCN108429719AReduce security threatsIntegrity guaranteedDigital data protectionProgram/content distribution protectionUser equipmentPrivilege level
The application discloses a key protection method and device, and belongs to the technical field of network security. In the application, user equipment sends a key identifier of at least one user keyto a server, so that a user application running on the server can transmit an operation parameter set including a corresponding key identifier to an execution node in a secure execution space when anoperation using the user key is initiated. The secure execution space is configured to be capable of preventing external access to a privilege-level code, so that an internal execution node can acquire the user key in a key library through the key identifier when the privilege-level code is invisible so as to perform the abovementioned operation using the user key and return an execution result.The user key and a key operation process are packaged within the secure execution space, so that the security threat to the user key caused by privileged software in a cloud server can be lowered.
Owner:HUAWEI TECH CO LTD
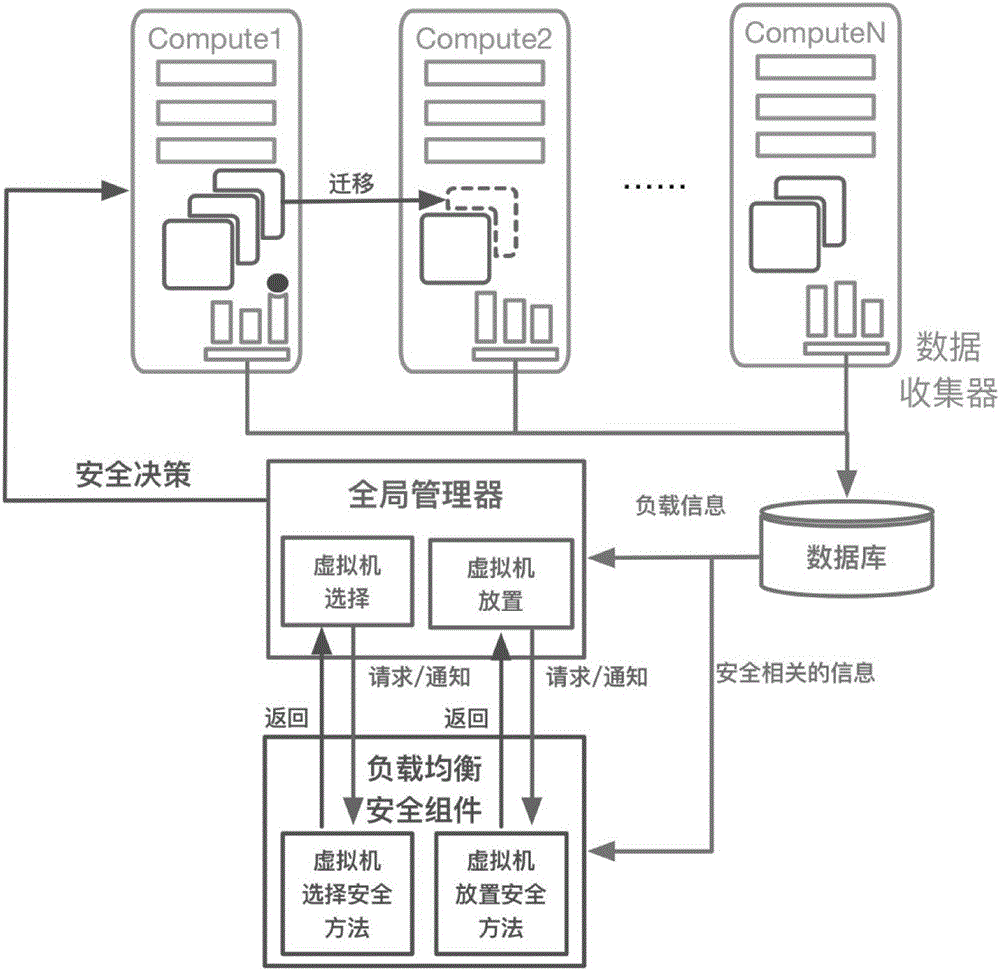
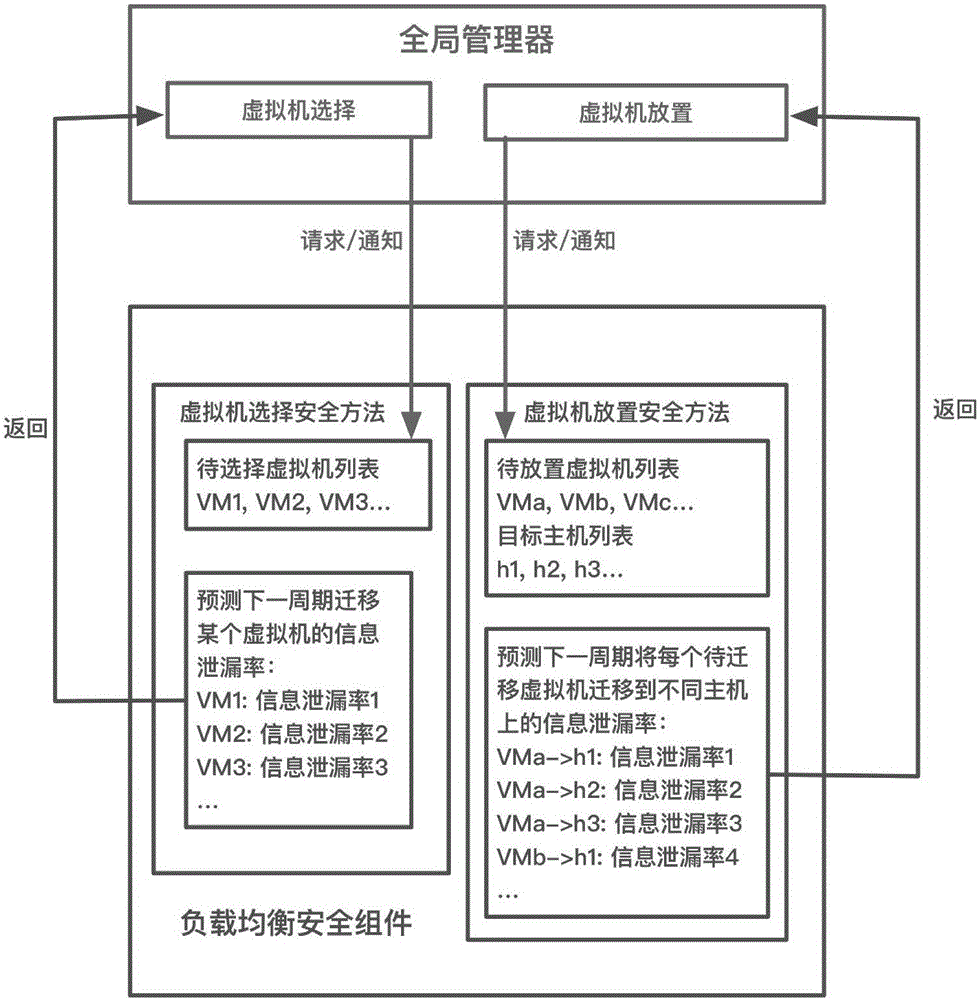
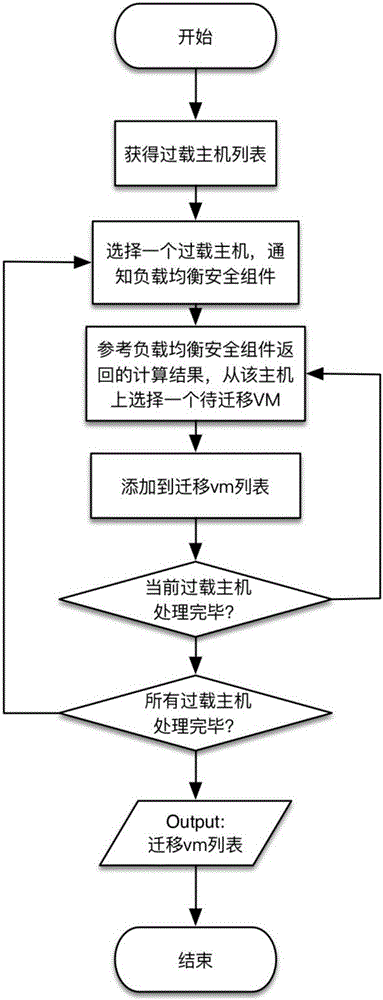
Virtual machine load balancing security dispatching method in cloud environment
ActiveCN106095532AIncrease profitReduce energy consumptionProgram initiation/switchingSoftware simulation/interpretation/emulationInformation leakageVirtual machine
The invention discloses a virtual machine load balancing security dispatching method in a cloud environment. The method includes the steps that 1, an ID list of virtual machines on an overload host in the cloud environment is sent to a security assembly through a load balancer; 2, the security assembly sequentially calculates the information leakage rate of a next period after each virtual machine in the list is deleted, and then the obtained information leakage rates are returned to the load balancer; 3, the load balancer determines the candidate virtual machines needing to be migrated in the list according to the information leakage list; 4, the load balancer sends each candidate virtual machine ID and virtual machine IDs on an underload host to the security assembly; 5, the security assembly calculates the information leakage rate of a next period after each virtual machine is migrated to different hosts according to the sent virtual machine IDs, and the information leakage rates are returned to the load balancer; 6, the load balancer makes a virtual machine placement decision according to the calculation result. The migration security of the virtual machines is enhanced.
Owner:PEKING UNIV
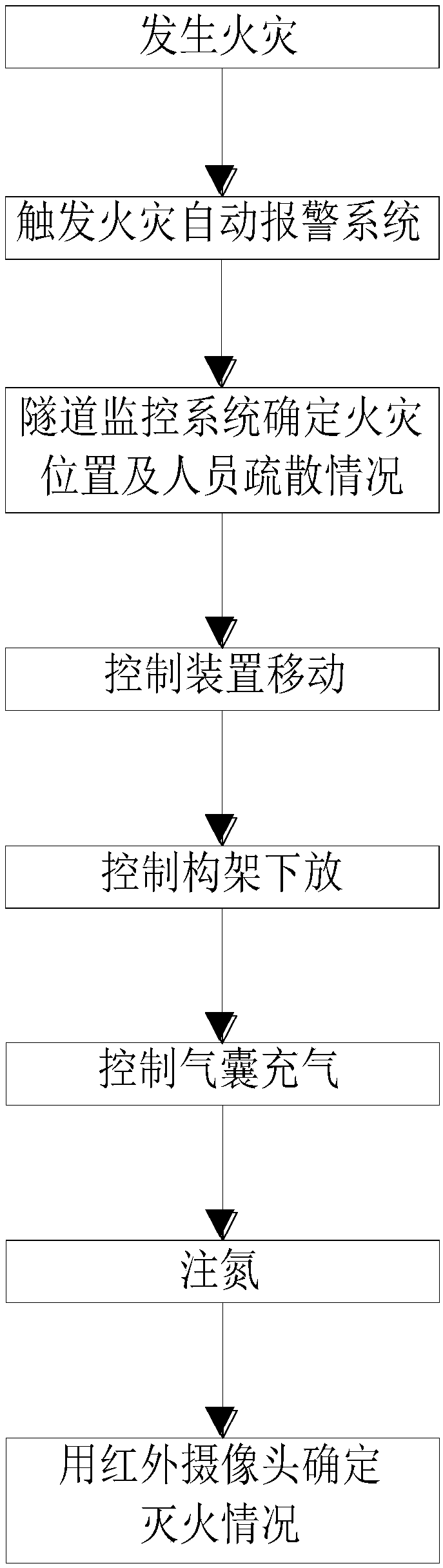
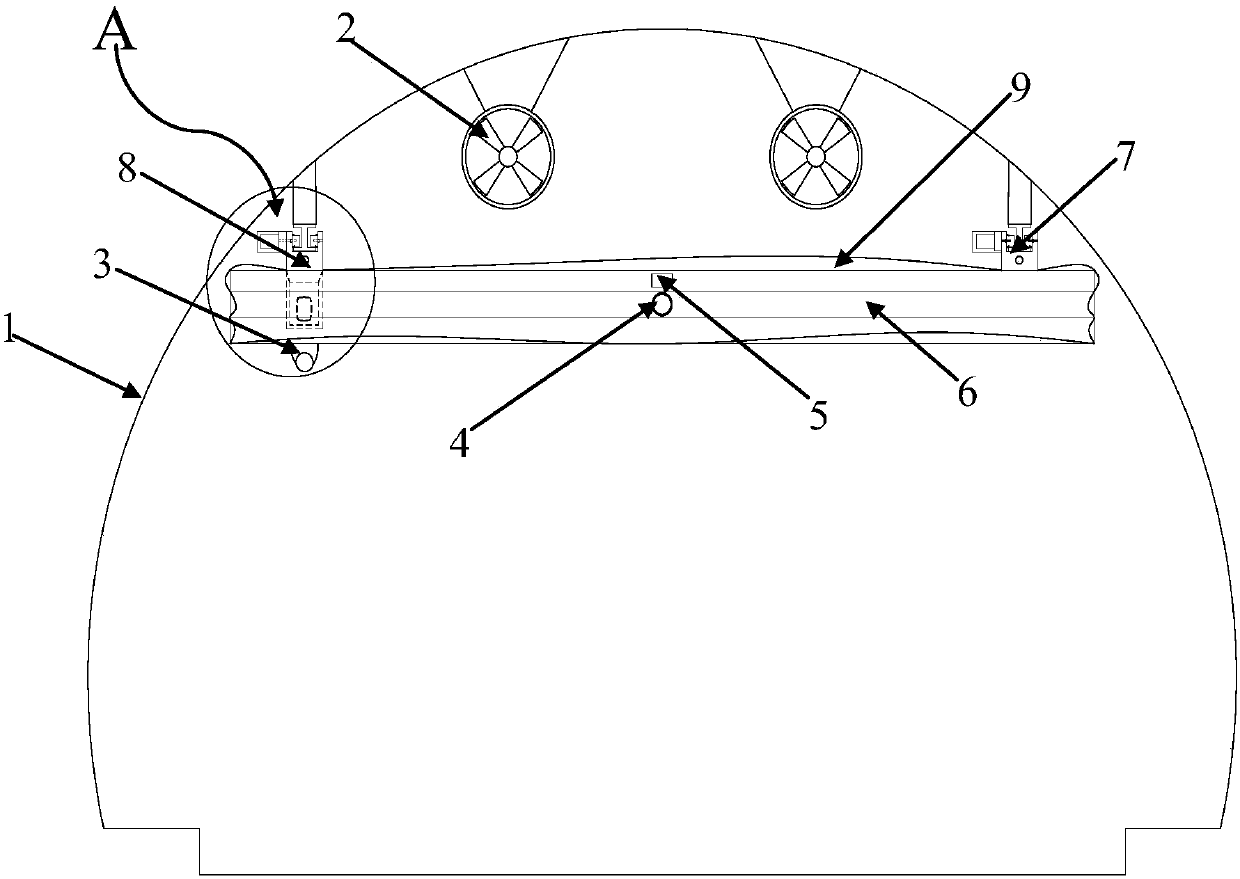
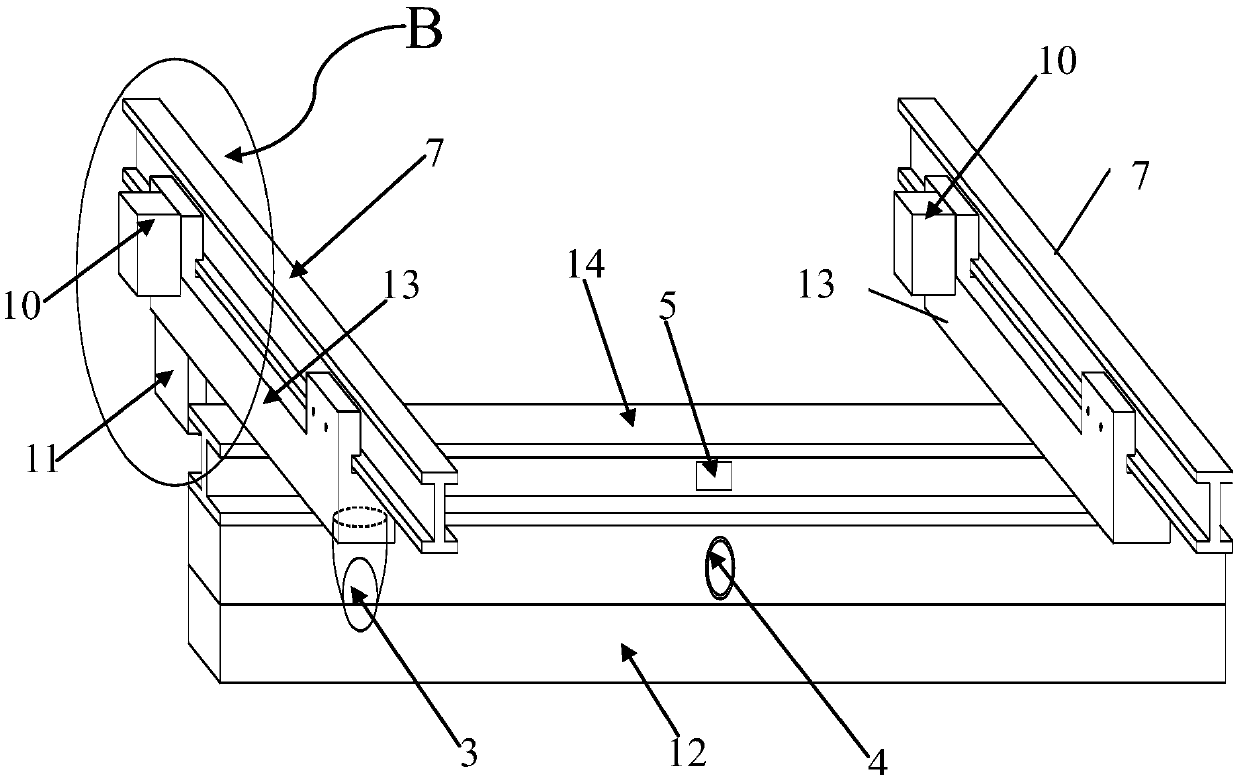
Suffocation type movable tunnel fire extinguishing device
InactiveCN108245807AOvercoming the inability to automatically extinguish a fireOvercoming the difficulty of disaster relief workers entering the fire sceneFire rescueBoring toolsToxic gasFire - disasters
A suffocation type movable tunnel fire extinguishing device comprises a high-temperature-resisting air bag and a movable bridge. A top beam is arranged at the upper portion of the inner wall of a tunnel. Two end beams are arranged on the top beam and are parallel. The end beams are perpendicular to the top beam. A main beam is arranged between the two end beams. The movable bridge comprises guiderails, the end beams are arranged on the guide rails and can move along the guide rails, and the high-temperature-resisting air bag is arranged on the beam. According to the suffocation type movable tunnel fire extinguishing device, the highway tunnel operation safety performance is improved, and security threats to personnel left in the tunnel and damage to tunnel electromechanical and civil engineering facilities from the fire disaster are reduced. An inflation type air bag device is adopted for sealing the tunnel sections at the two ends of a fire source, high-temperature gas and a large amount of smoke generated by the fire disaster are isolated, and fire disaster spreading and toxic gas diffusion can be effectively controlled.
Owner:CHANGAN UNIV
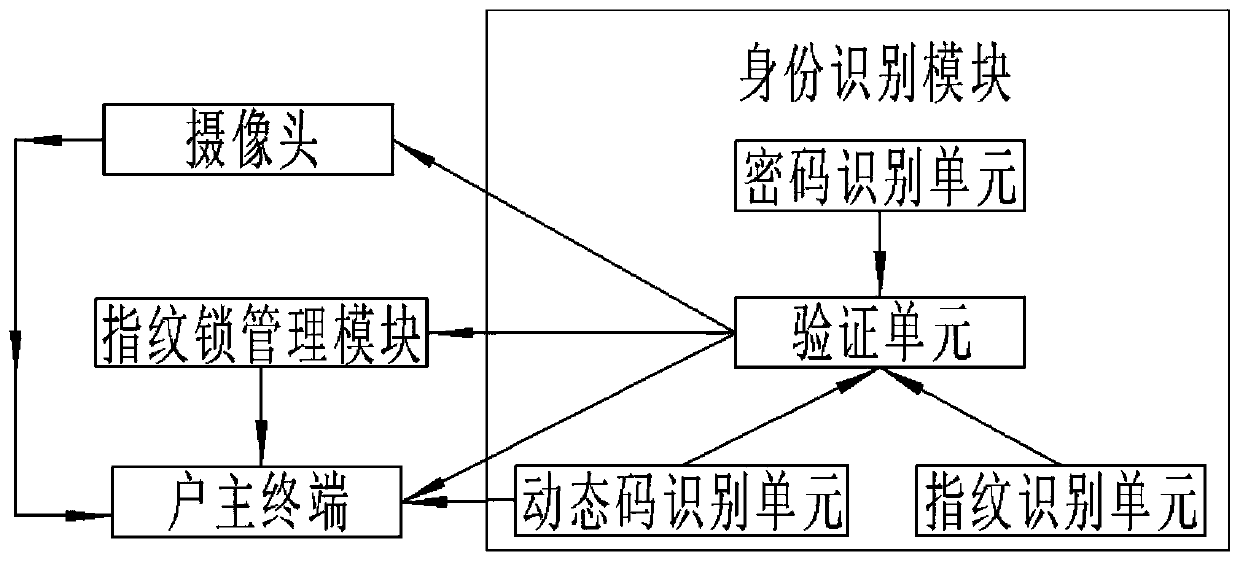
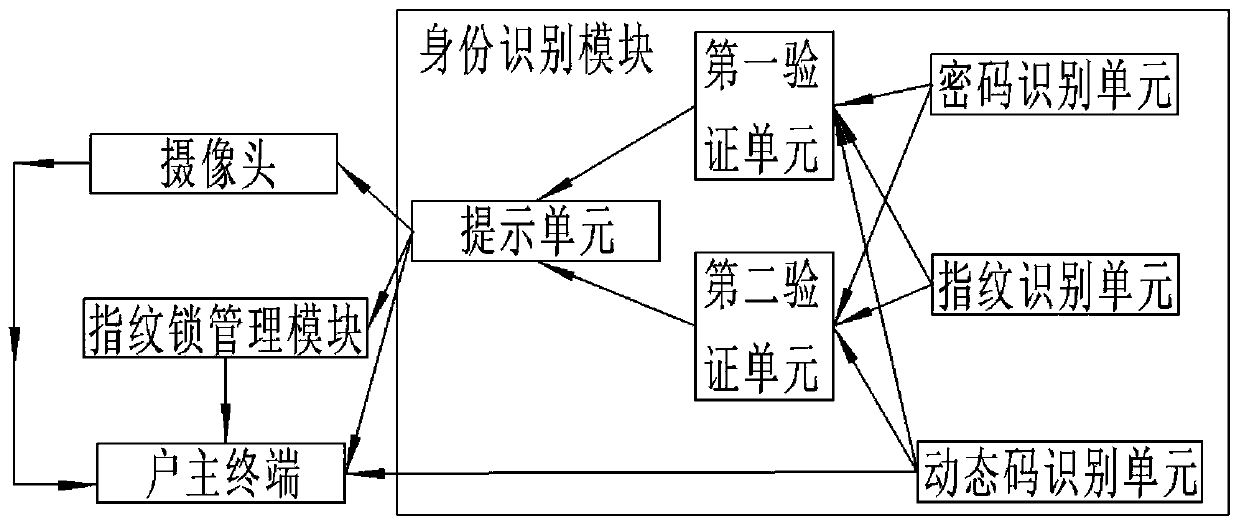
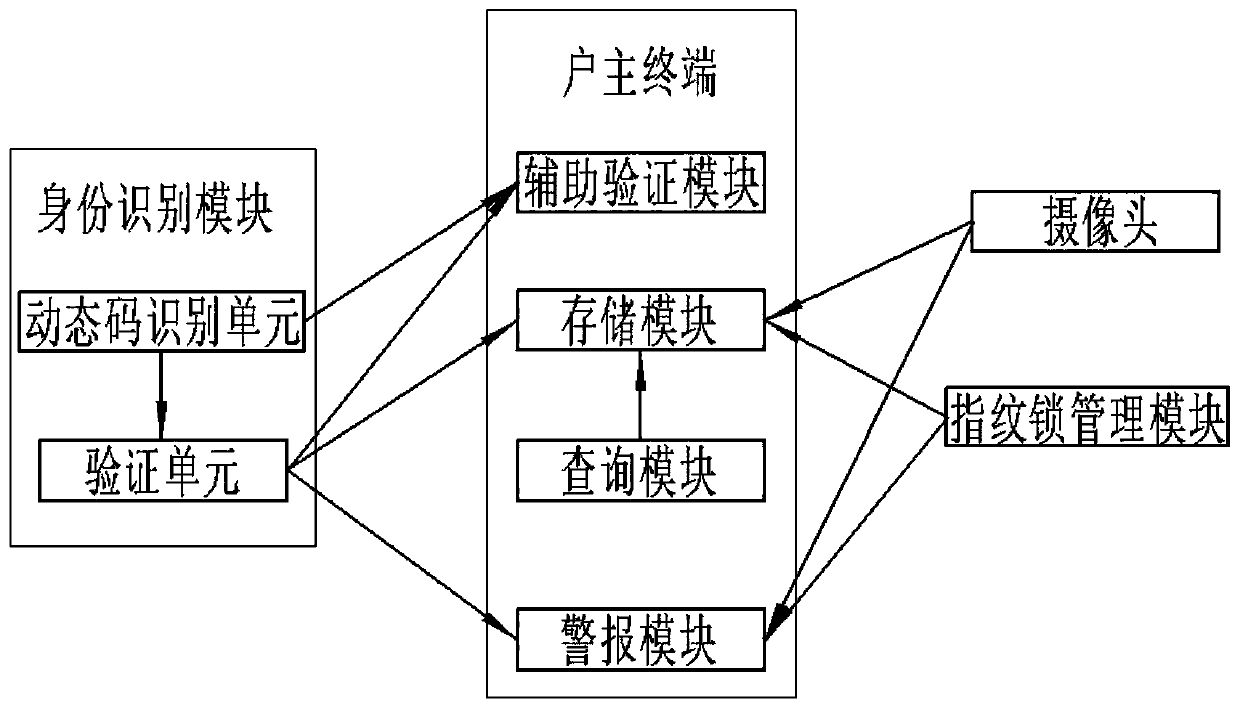
Fingerprint lock control system and method based on blockchain technology
InactiveCN110349311AReduce security threatsRealize control managementIndividual entry/exit registersBlockchainElectricity
The invention discloses a fingerprint lock control system and method based on blockchain technology, and the fingerprint lock control system comprises an identity recognition module, a fingerprint lock management module and a household owner terminal, wherein the identity recognition module comprises a password recognition unit, a fingerprint recognition unit, a dynamic code identifying unit and averifying unit, and the password identifying unit, the fingerprint identifying unit and the dynamic code identifying unit are electrically connected to the verifying unit, respectively. The fingerprint lock control system provided by the invention is reasonable in module design and simple in operation. By combining the blockchain and the fingerprint lock technology, the fingerprint lock control system and method provided by the invention not only effectively realize the control and management of the fingerprint lock, but also ensure the safety of the house of the household owner, and at the same time greatly reduce the threat of the house. In the technical solution, presets and corresponding module settings are made for various situations that may occur in the house, so that the householdowner can understand and carry out effective treatment in the first time in the case of house theft to reduce the property loss, thereby having high practicability.
Owner:江苏橙贝科技有限公司
Method for using collector prepared from illegal cooking oil in fluorite flotation
The invention relates to a method for using a collector prepared from illegal cooking oil in fluorite flotation. The collector is prepared by the following steps: (a) purifying and extracting illegal cooking oil; and (b) subjecting the purified and extracted illegal cooking oil obtained by the step (a) to a hydrolysis reaction and thus obtaining the collector for use in ore floatation. When the collector prepared from the illegal cooking oil, which is used in the invention, is used in fluorite flotation, the selectivity of the collector is improved, and the technical index and economic index of the flotation can be improved. As the illegal cooking oil is used as the raw material for preparing the collector, the technical scheme adopted by the invention has a great significance for avoiding environment pollution, simplifying production process, reducing food safety threats and the like.
Owner:BEIJING JUNZHIQING SCI & TECH
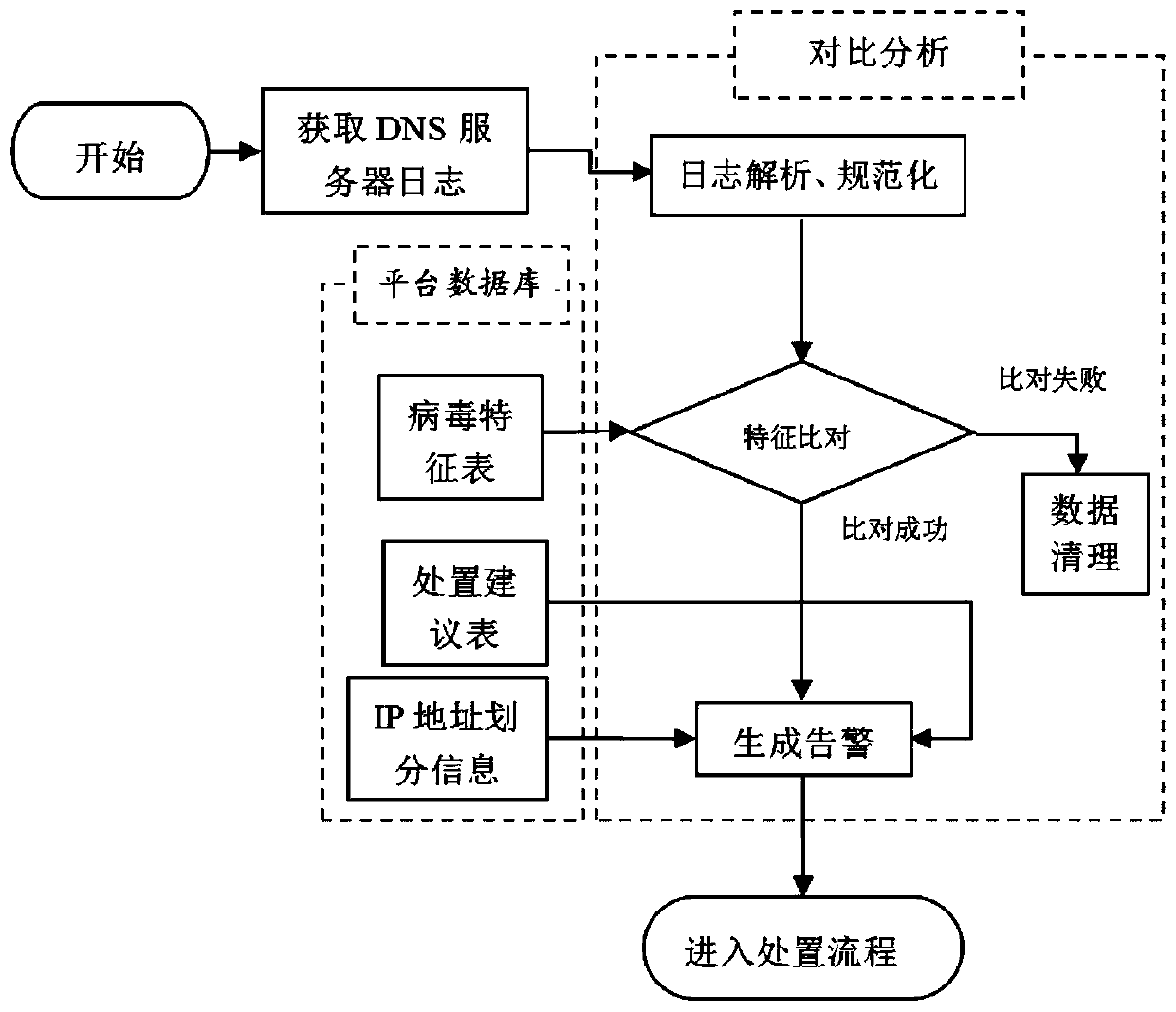
Malicious domain name infection host tracing method
The invention belongs to the field of power system computers. The method is a malicious domain name infected host tracing method. The method comprises: establishing a database on a platform, collecting DNS server logs, anti-virus searching and killing logs, virus access URL feature information, a disposal knowledge base and IP address division information of all associated hosts in a power grid system on a platform; establishing a virus feature table according to the collected virus access URL feature information, establishing a processing suggestion table according to a processing knowledge base, and storing IP address division information; and obtaining a DNS server log from a host, analyzing and normalizing the DNS server log through comparative analysis, then performing feature comparison with the virus feature table, generating an alarm according to suggestions corresponding to virus features compared in the virus feature table in the processing suggestion table, and then enteringa processing flow. According to the invention, the attacked host is disposed in time according to the disposal suggestions, thereby achieving the purposes of ensuring the security of the informationintranet and reducing the security threat.
Owner:STATE GRID LIAONING ELECTRIC POWER RES INST +1
Firewall based on multiprocessor architecture
ActiveCN109558366AResist attackReduce security threatsMultiple digital computer combinationsPlatform integrity maintainanceService flowByte
A firewall based on a multiprocessor architecture comprises a main processor for processing a management flow of the firewall and a coprocessor which is used for carrying out parallel processing on the service flow of the firewall, and the main processor and the coprocessor are independent of each other and communicate with each other through a communication interface. The firewall provided by theinvention adopts a double-processor architecture, the two processors are independent of each other and are in limited communication through the communication interface, and when the main processor isattacked by a network or the main processor cannot work normally, the service processing unit of the coprocessor can still process the service flow normally. Compared with other industrial control firewalls, the firewall disclosed by the invention has the advantages that the reduced processing time reaches several orders of magnitudes, and the 100% throughput is achieved under the conditions of gigabit rate linear speed and 64-byte Ethernet message through the modules such as message deep analysis, basic strategy matching, industrial control protocol function code matching, industrial controlprotocol parameter matching, alarm information uploading and the like.
Owner:浙江国利网安科技有限公司
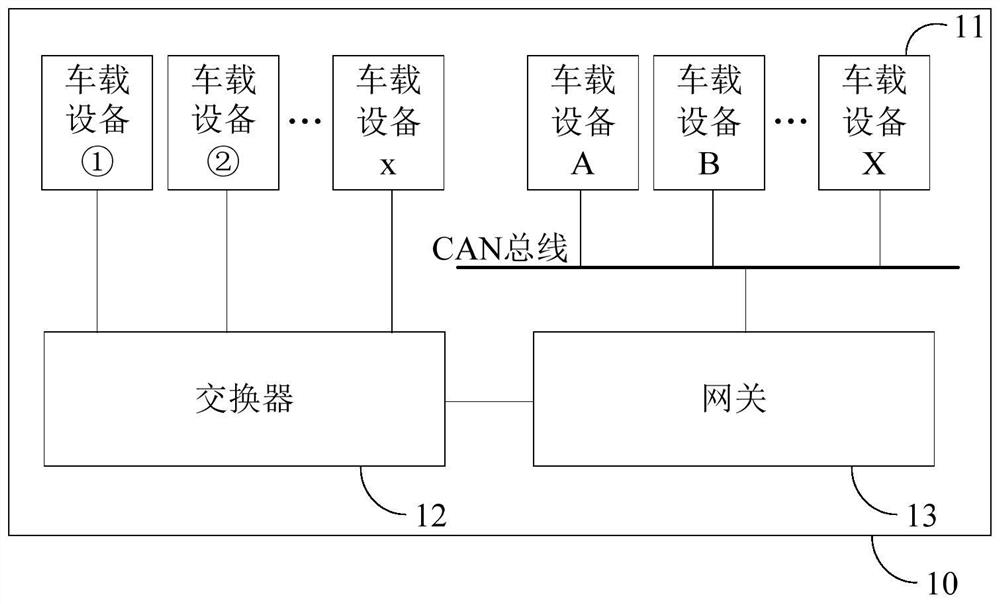
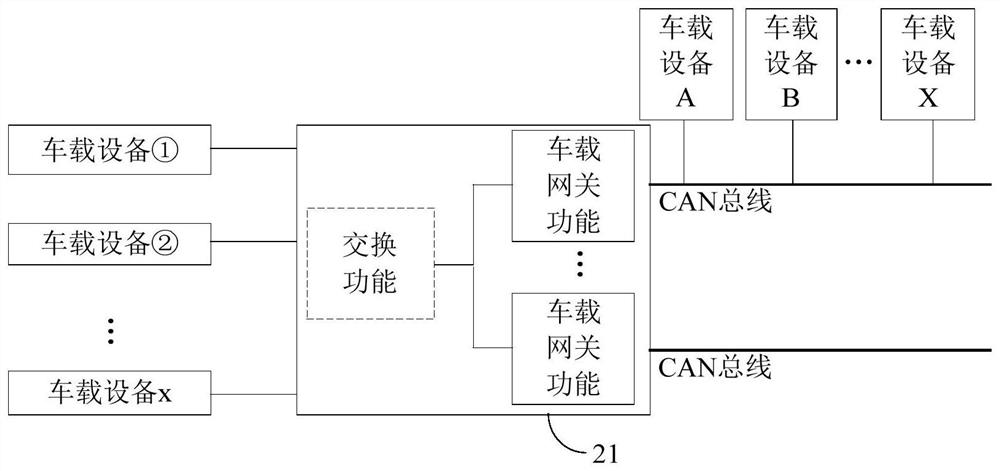
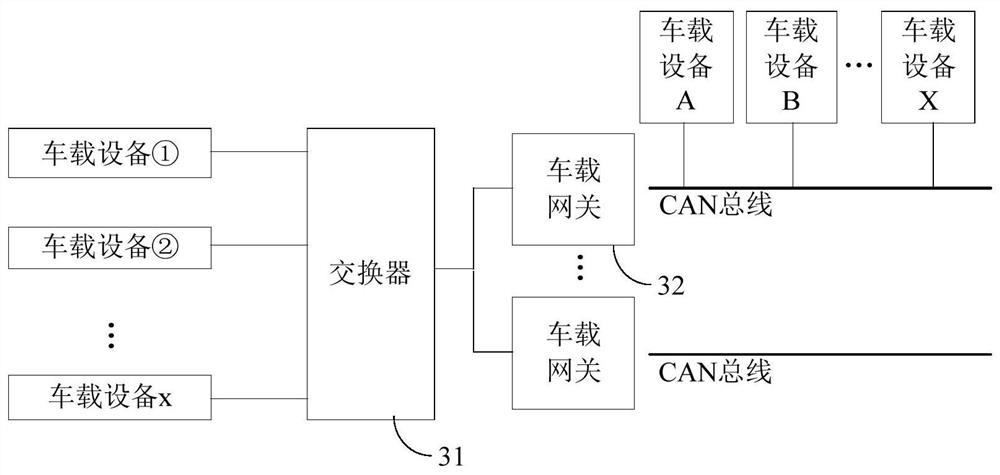
Communication method of vehicle-mounted gateway, vehicle-mounted gateway and intelligent vehicle
ActiveCN111835627AReduce security threatsImprove securityNetwork connectionsWireless communicationIn vehicleEngineering
The invention provides a communication method of a vehicle-mounted gateway, the vehicle-mounted gateway and an intelligent vehicle. When receiving a first message from a first vehicle-mounted device,the vehicle-mounted gateway identifies identification information in the first message, matches the identification information with preset identification information stored in the vehicle-mounted gateway, and does not send a second message unless matching is successful, and thus, the second message indicates a target operation executed by a second vehicle-mounted device. When the identification information of the first message cannot be matched with the preset identification information stored in the gateway, the vehicle-mounted gateway does not send the second information to control the second vehicle-mounted equipment to execute the target operation. Therefore, through the identification information of the first message set in the vehicle-mounted gateway of the automobile, the security threat brought to the vehicle-mounted network is reduced, and the security performance of the vehicle-mounted network of the automobile is improved.
Owner:HUAWEI TECH CO LTD
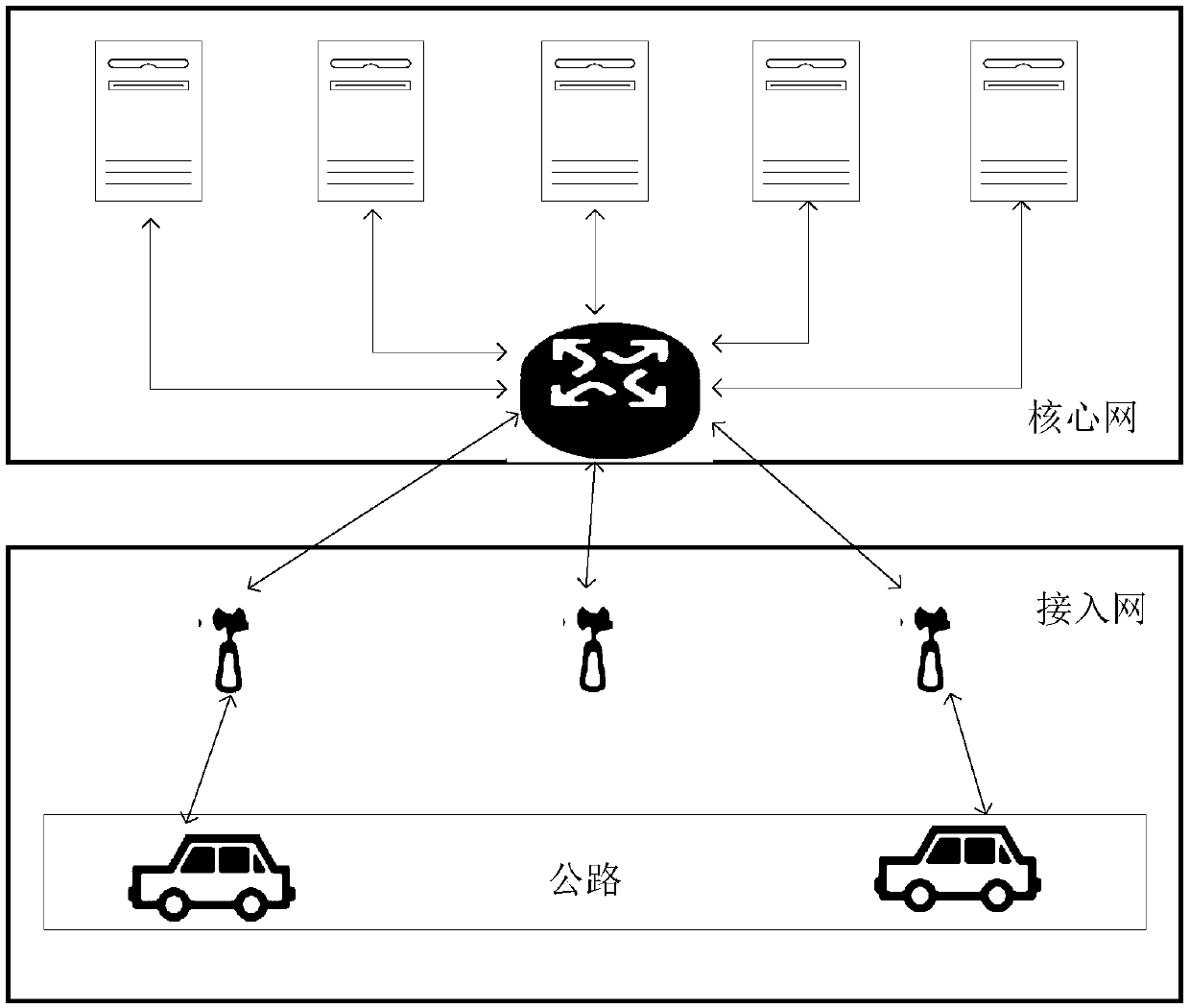
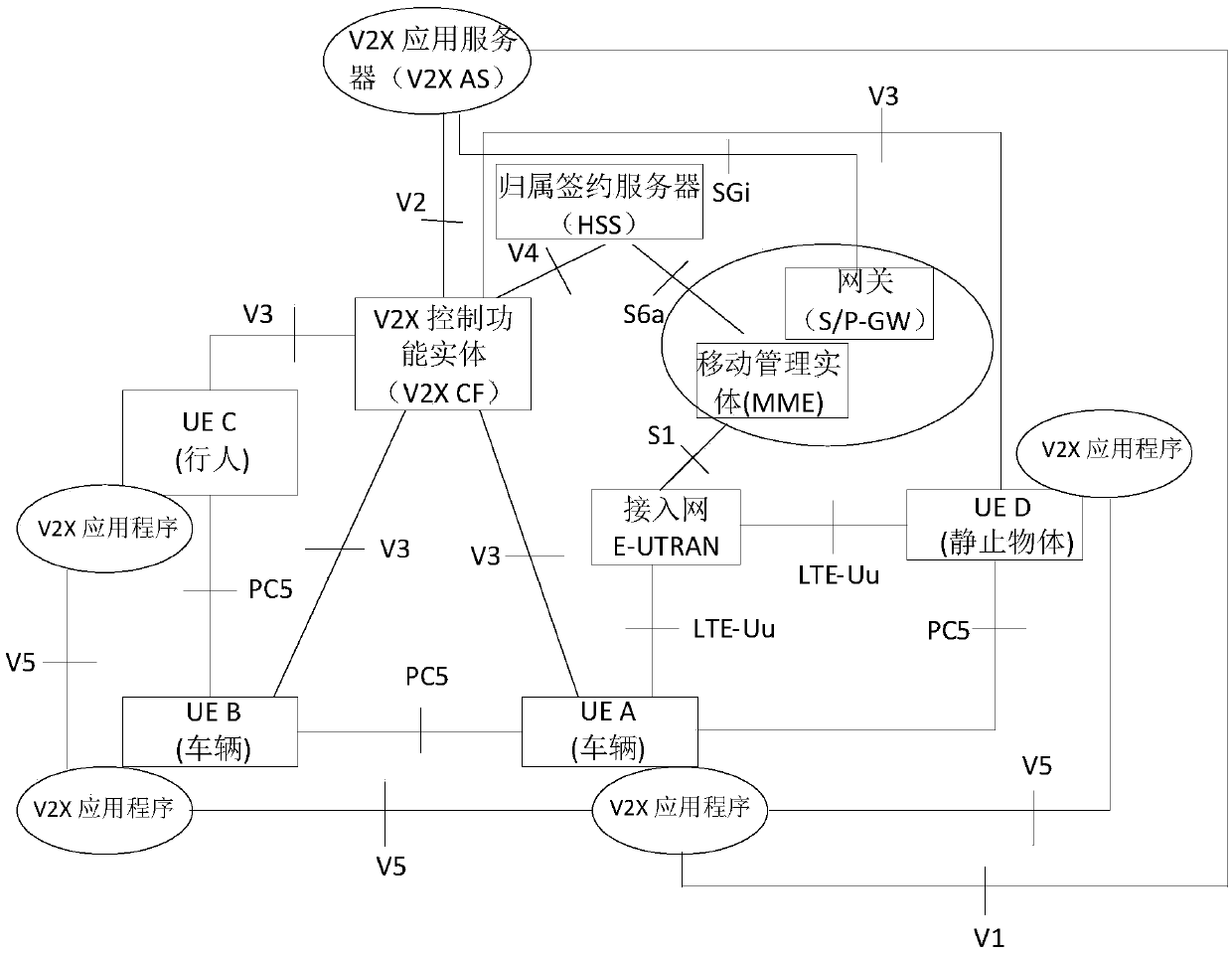
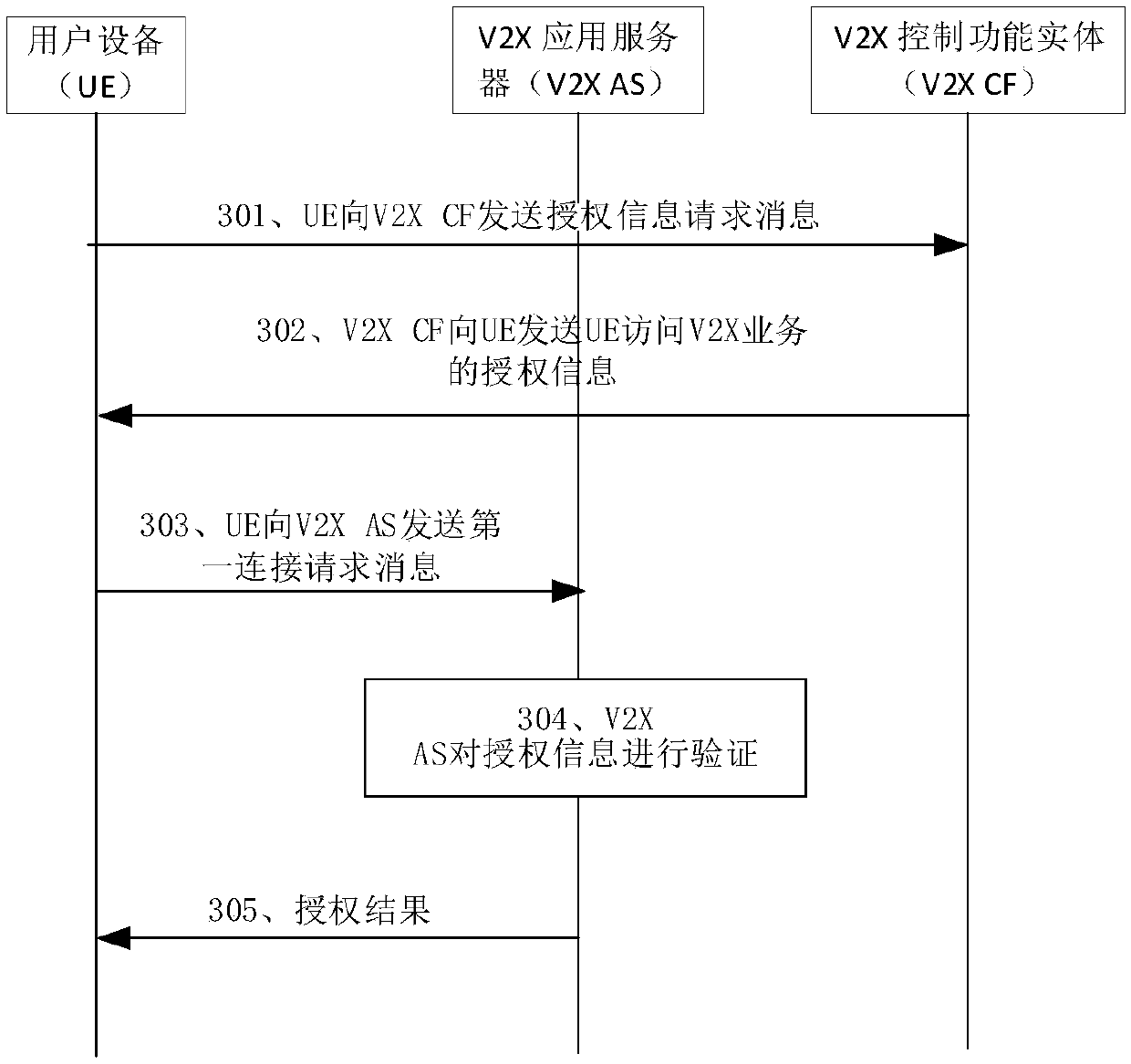
V2X service authorization method, device and equipment
ActiveCN110366130AReduce security threatsImprove securityParticular environment based servicesVehicle wireless communication serviceAuthorization
The embodiment of the invention discloses a V2X service authorization method, a device and equipment, for improving the security of V2X service access. The V2X service authorization method comprises the steps: UE receives authorization information sent by a V2X CF, wherein the authorization information comprises a V2X service identifier; and the UE sends authorization information to network side equipment, and the authorization information is used for authorizing the UE to access the V2X service corresponding to the V2X service identifier after the network side equipment verifies the authorization information successfully. In the embodiment of the invention, after the network side equipment verifies and authorizes the authorization information of the UE, the UE can access the V2X service,so that the security threat caused by the access of unauthorized equipment can be reduced, and the security of V2X service access can be improved.
Owner:HUAWEI CLOUD COMPUTING TECH CO LTD
Fire scene sampling device and sampling method thereof
PendingCN111829839AReduce security threatsGuaranteed to workWithdrawing sample devicesAnalysing gaseous mixturesElectric machineryEnvironmental engineering
The invention discloses a fire scene sampling device and a sampling method thereof. The fire scene sampling device comprises a control box and a sampling trolley, wherein the sampling trolley is driven by a driving motor and a driving bottom plate, a gas sampler and a gas storage tank are further fixedly arranged on the sampling trolley, the control box is in communication connection with the sampling trolley through a wireless communication module, a control module used for controlling the sampling trolley is arranged in the control box, the control module is connected with the wireless communication module, and a detection unit is further arranged on the sampling trolley. The device is advantaged in that the sampling equipment is conveyed into a high-risk fire scene through the samplingtrolley which can be infinitely and remotely controlled, gas samples are collected, unmanned sampling of a fire scene is achieved, safety threats to workers are greatly reduced, and rapid gas samplingwork in complex and dangerous environments such as a fire scene is achieved.
Owner:应急管理部四川消防研究所
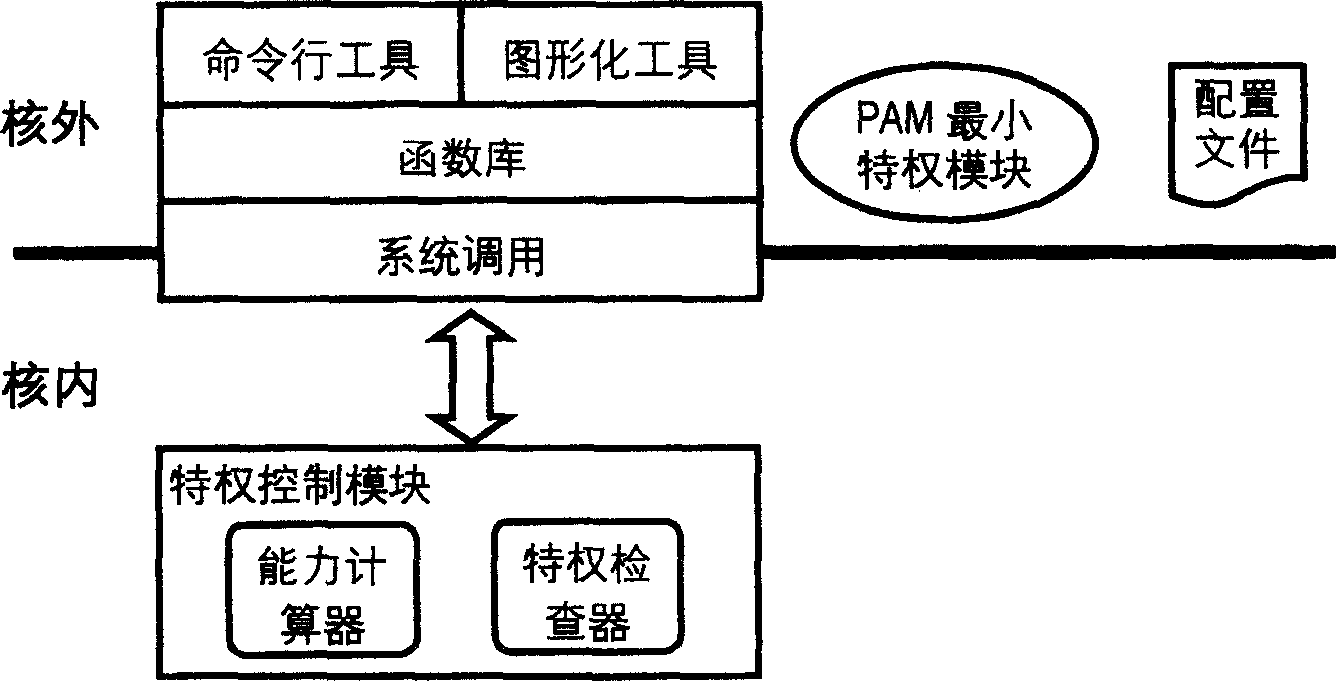
Privilege minimizing method based on capability
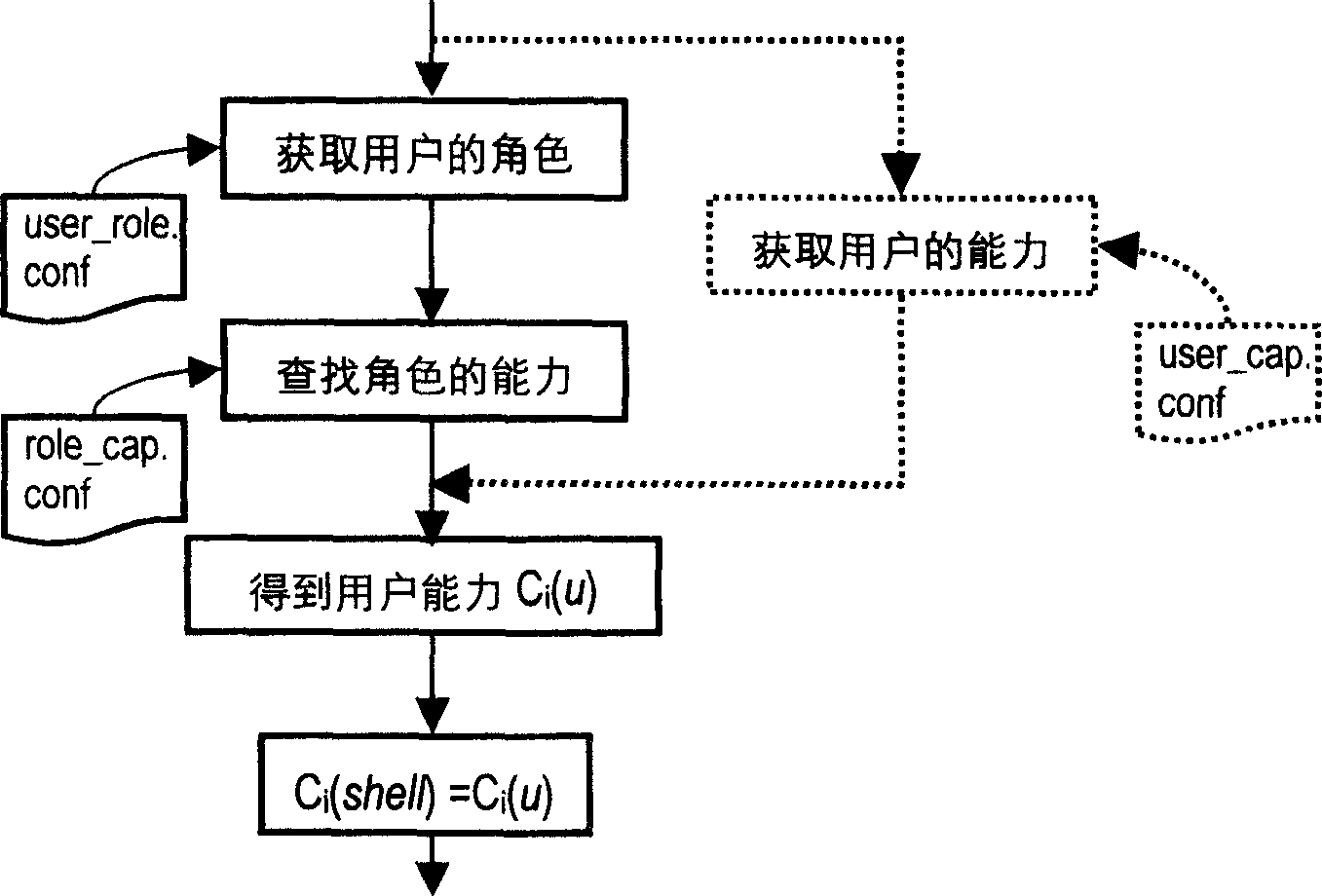
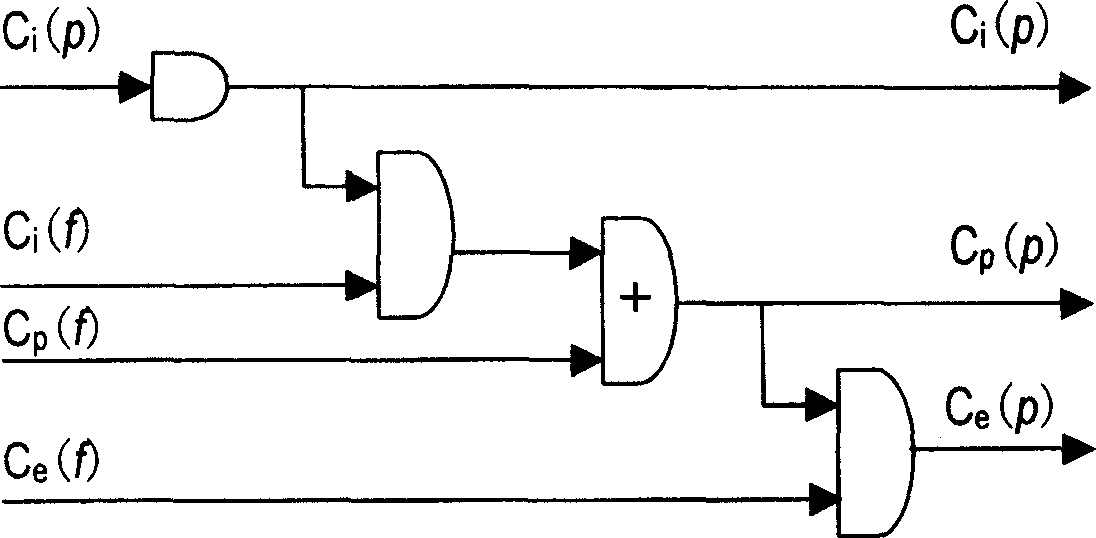
InactiveCN1763710AReduce security threatsPerformance is not affectedSpecific program execution arrangementsOperating pointOperational system
The invention discloses a privilege minimum method based on the power, which is characterized by the following: inheriting the power mechanism of draft standard POSIX1003.1e; defining role power, user power and power logical relationship; designing a privilege minimum model based on the power through dynamic mode pattern, wherein the privilege control mode contains power calculator and privilege examiner; the power calculator computes the course final privilege according to the power logical relationship; the privilege examiner judges the corresponding invitation privilege in each privilege operation.
Owner:NAT UNIV OF DEFENSE TECH
Multifunction wing tip turbine engine having fore-lying impellers
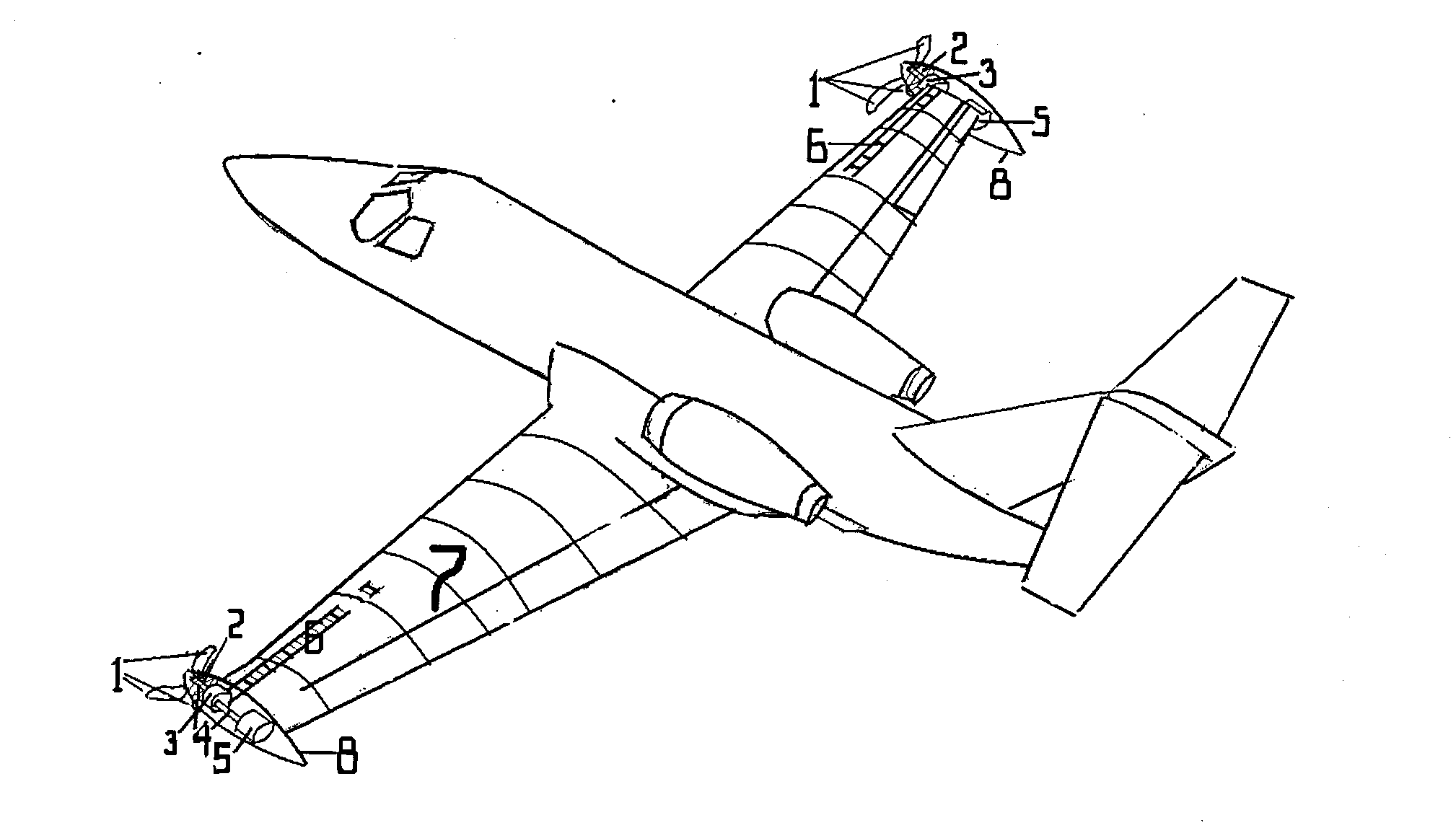
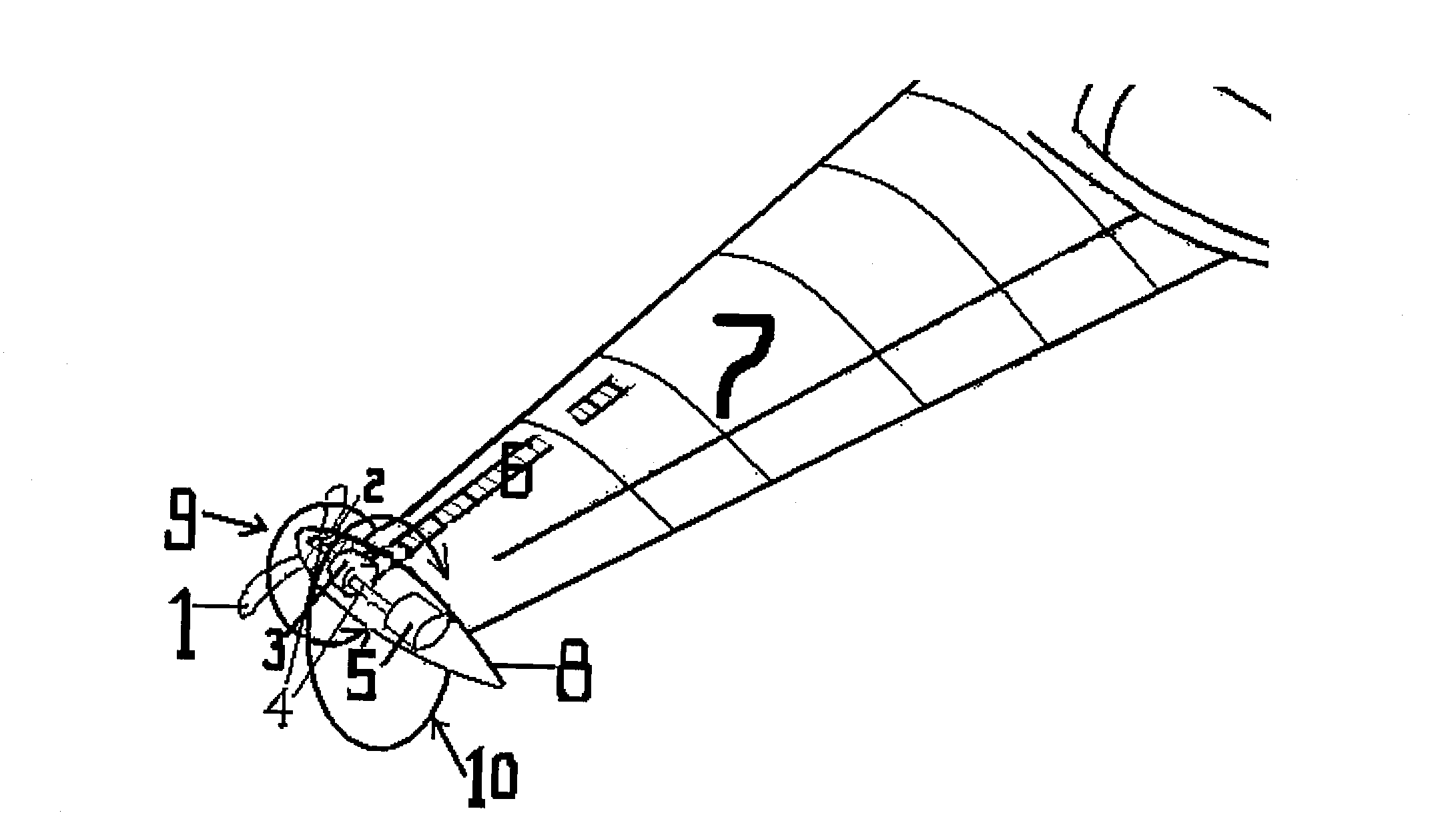
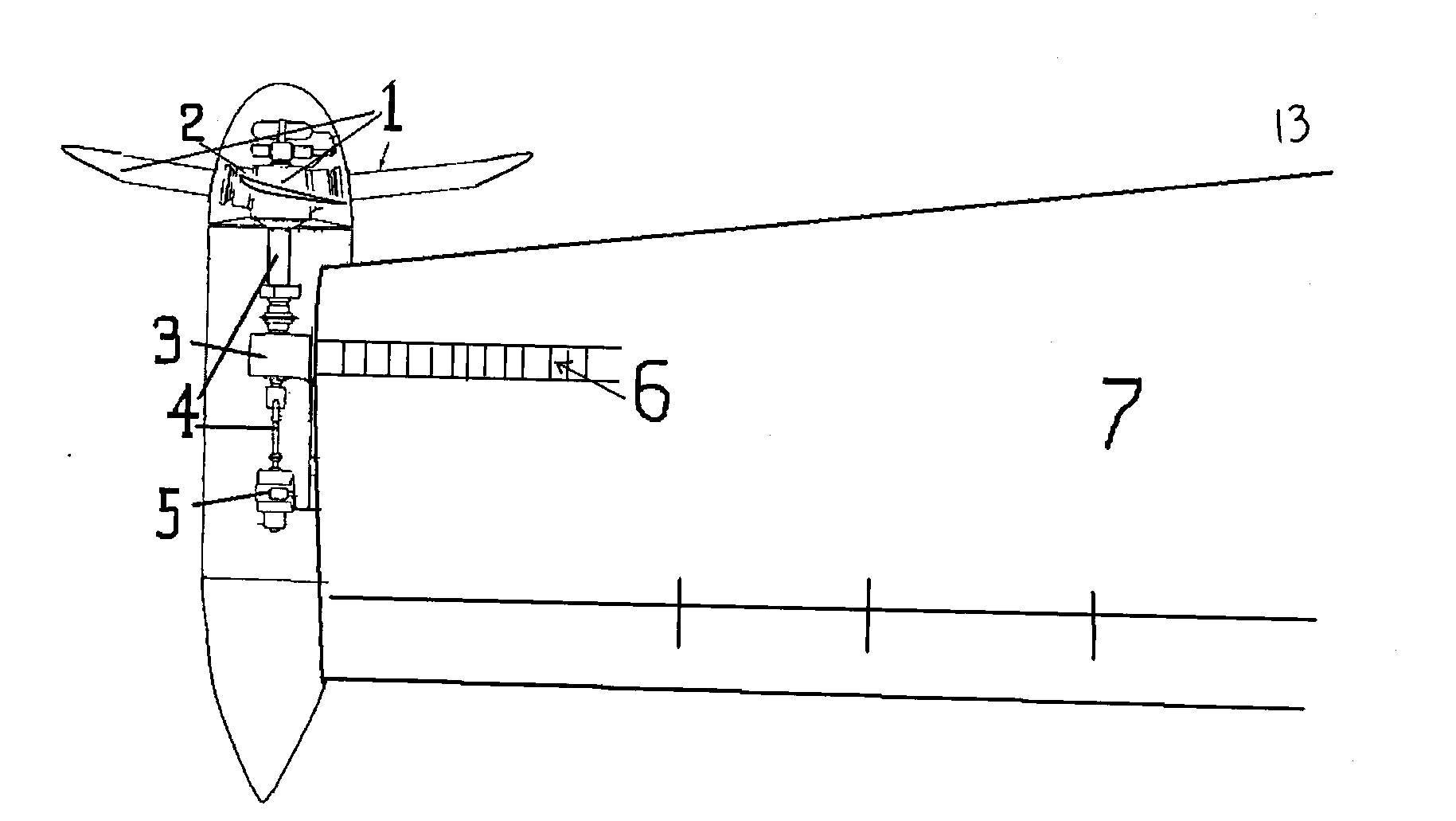
InactiveCN102975851AEasy to liftIncreased benign effectsWind motor combinationsMachines/enginesAviationImpeller
The invention relates to completely-new wing auxiliary equipment or a novel wing. According to the present invention, the front part of a wing tip is provided with a circle or a plurality of circles of impellers, a fairing is arranged on the front and the rear of a shaft disc of the impeller and extends to the whole wing tip, variable pitch blades are arranged in front of the wing tip through a wheel hub, a gear and a rotation shaft, and drive an electricity generation device arranged on the wing tip position or other transmission devices, the impeller is driven to rotate through facing airflow, the blade can rotate in a direction against an upward turning eddy flow of the wing tip under pushing of the incoming flow with an installation angle ( as shown in Figure 1) of the blade, such that right wing tip counterclockwise rotation wing tip eddy flow generated in the normal wing profile is previously decreased, rotation airflows generated by the impellers on both edges upward impact the wings from the bottom of the wings so as to further increase lifting force, and substantial lifting increase and resistance reduction are achieved with the benign effects. The multifunction wing tip turbine engine even can replace an electromotor driven by the aircraft motor part or generate auxiliary power, such that safety threat on the back flying aircraft by the wing tip wake of the front flying aircraft can be decreased, and aviation industry safety can be improved.
Owner:刘婉婷 +2
Grouping cluster and master key based key management method
ActiveCN103813320AEnsure safetyGuaranteed confidentialitySecurity arrangementConfidentialityStructure of Management Information
The invention relates to a grouping cluster and master key based key management method and relates to the technical field of a wireless sensor network (WSN). According to the grouping cluster and master key based key management method, the WSN needs secure channels during a communication key transmission process, so that an elliptic curve encryption method is used; a master key is used for encrypting and distributing group keys, and the group keys are used for encrypting data, so that data transmission channels are separated from key transmission channels, and key distribution security is guaranteed; by means of difficulties in solving a discrete logarithm problem on an elliptic curve, group key distribution confidentiality is guaranteed; by means of a grouping cluster network structure, a large-scale network is partitioned into small logic cluster groups, and each group shares one group key so as to reduce stored keys; a key distribution method is improved on the basis of clustering and in combination with the idea of master key management, and network work efficiency is effectively improved.
Owner:NORTHEASTERN UNIV
Identity authentication method and device of equipment and computer storage medium
ActiveCN109446788AReduce security threatsImprove efficiency and safetyDigital data authenticationInformation transmissionInformation transfer
The invention discloses an identity authentication method and device of equipment and a computer storage medium. The method comprises that in response to an inquiry instruction sent by a management platform, the device calculates a first hash value according to the device identity information and a received random number, and sends the first hash value to the management platform; the device sendsthe first hash value to the management platform according to the first hash value; the random number is generated by the management platform after the device joins the network; in response to a queryresponse instruction sent by the device, the management platform calculates the received first hash value, obtains a second hash value and sends it to the server; the server performs legitimacy authentication on the device according to the first hash value, obtains authentication information corresponding to the device and returns the authentication information to the management platform, so thatthe management platform calculates a third hash value according to the authentication information; according to the received third hash value, the device authenticates the validity of the management platform, which can effectively improve the efficiency and security of identity authentication, and effectively improve the efficiency and security and reliability of equipment information transmission.
Owner:GCI SCI & TECH
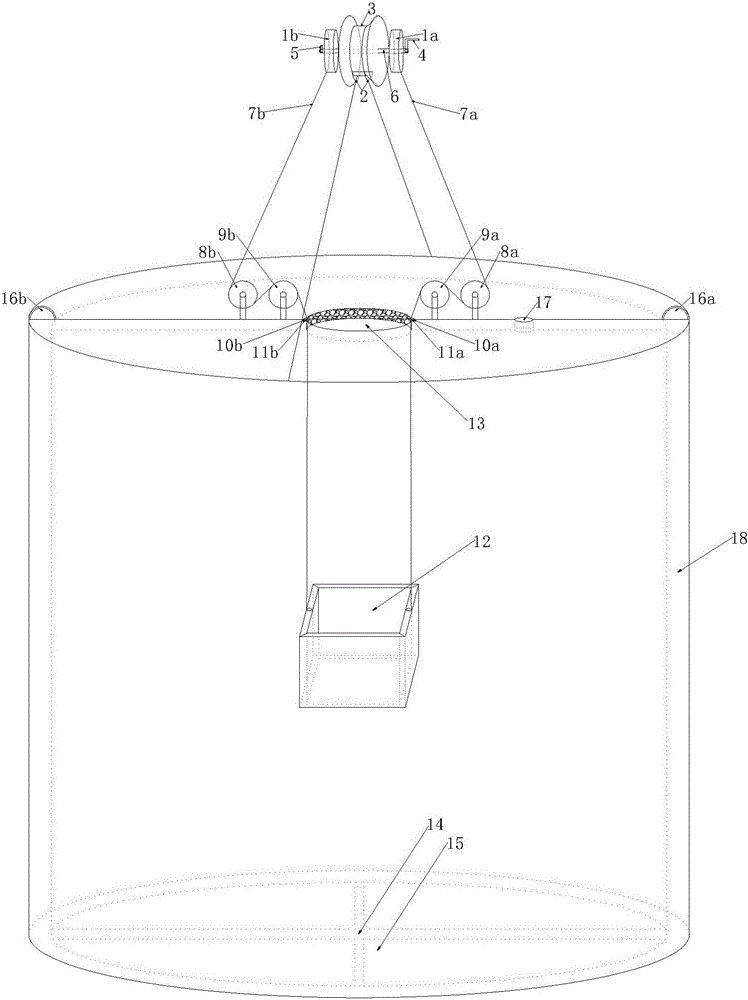
Civil explosive article destroying device and method
The invention discloses a civil explosive article destroying device and method. The civil explosive article destroying device comprises a wire control device body, an explosion steel drum and a monitoring port. The lower end of the wire control device body of the destroying device is fixed to the upper edge of the explosion steel drum through supporting rods, and the two sides of the wire control device are provided with a first wire coil and a second wire coil correspondingly. According to the civil explosive article destroying device and method, explosion vibration can be remarkably reduced, and explosion noise is lowered; fragments produced through explosion and remaining explosives are collected to the bottom of the steel drum so that collecting, processing and analyzing can be convenient, and pollution to the environment of a destroying site is reduced; nearby arrangement can be conducted, so that the safety and the convenience of explosive articles in the destroying process are improved; the temperature and the toxic gas content in the explosion steel drum are detected in time through the monitoring port, and the situation that the temperature is too high due to multiple times of explosion, and the safety of operation personnel is threatened due to the fact that the toxic gas content is too high is avoided; the excavation number and time of explosion tunnels are decreased, and resources are saved; and the labor cost is reduced, and the working efficiency is improved.
Owner:ANHUI UNIV OF SCI & TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com