Malicious domain name infection host tracing method
A technology of host and domain name, applied in transmission systems, electrical components, etc., can solve the problems of low security and slow positioning of infected hosts, and achieve the effect of ensuring security and reducing security threats
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
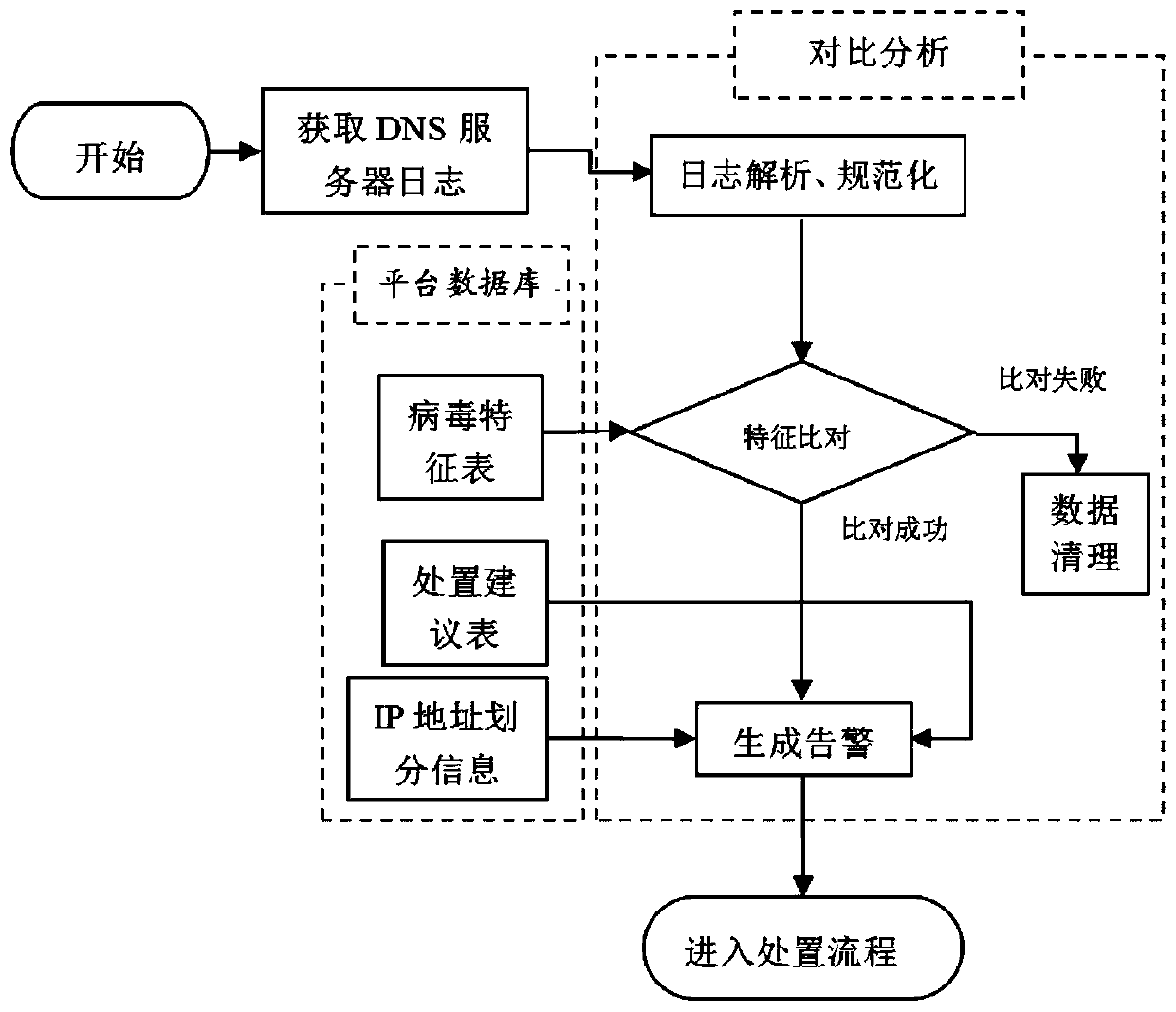
[0020] The present invention provides a method for tracing the source of a malicious domain name infected host, the method comprising:
[0021] Establish a platform, including acquisition server and big data analysis platform and establish a database,
[0022] The establishment of the database includes: collecting DNS server logs, anti-virus killing logs, virus access URL characteristic information, disposal knowledge base, and IP address division information of each associated host in the power grid system on the platform, and according to the collected virus access URL characteristic information Establish a virus signature table, establish a processing suggestion table according to the disposal knowledge base, and store IP address division information;
[0023] Obtain the DNS server logs from the accessed host through the collection server, use client access as the trigger condition, analyze and normalize the DNS server logs through comparative analysis, and then compare the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com