Patents
Literature
281 results about "Server log" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
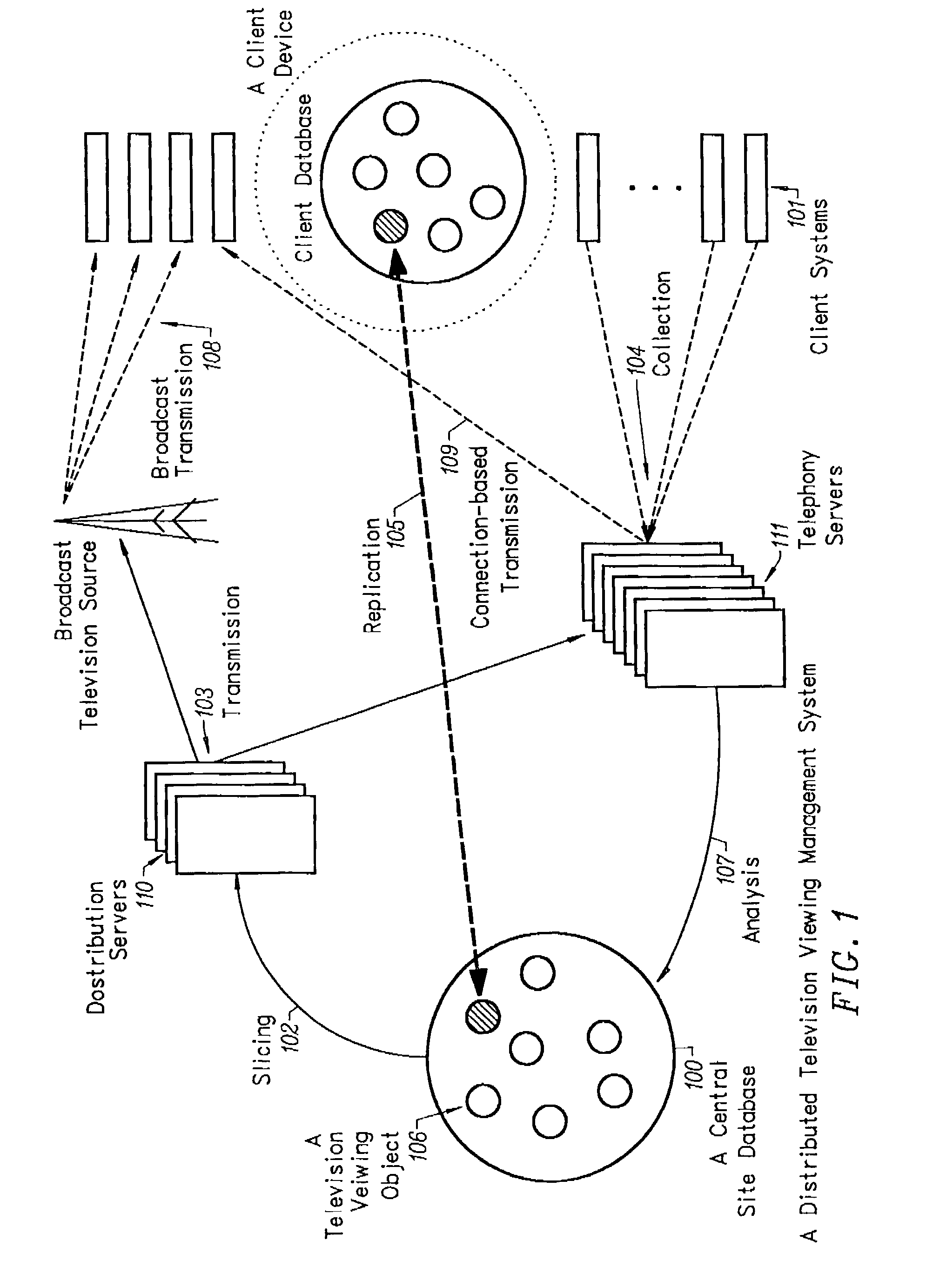
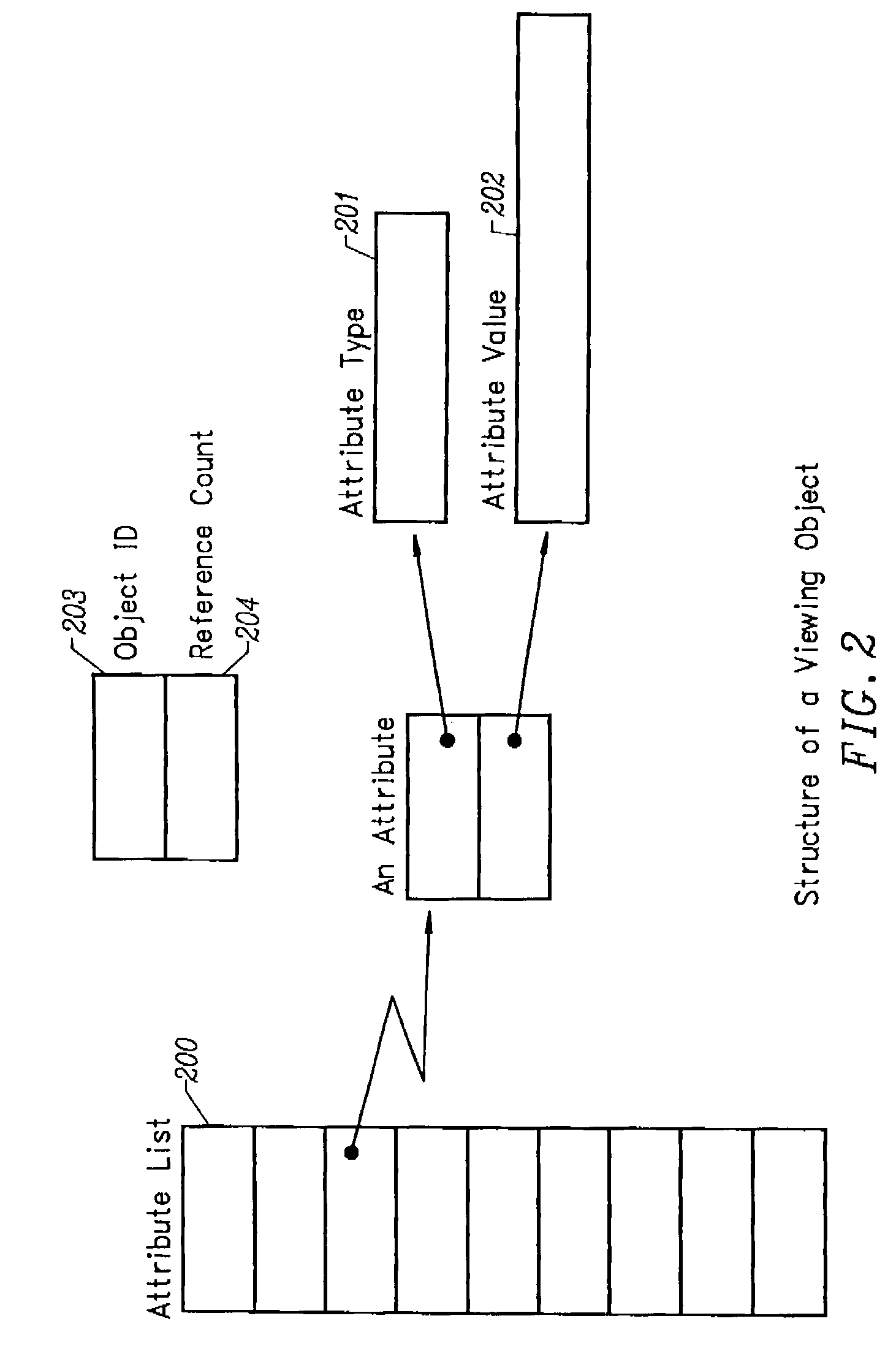
A server log is a log file (or several files) automatically created and maintained by a server consisting of a list of activities it performed. A typical example is a web server log which maintains a history of page requests. The W3C maintains a standard format (the Common Log Format) for web server log files, but other proprietary formats exist. More recent entries are typically appended to the end of the file. Information about the request, including client IP address, request date/time, page requested, HTTP code, bytes served, user agent, and referrer are typically added. This data can be combined into a single file, or separated into distinct logs, such as an access log, error log, or referrer log. However, server logs typically do not collect user-specific information.
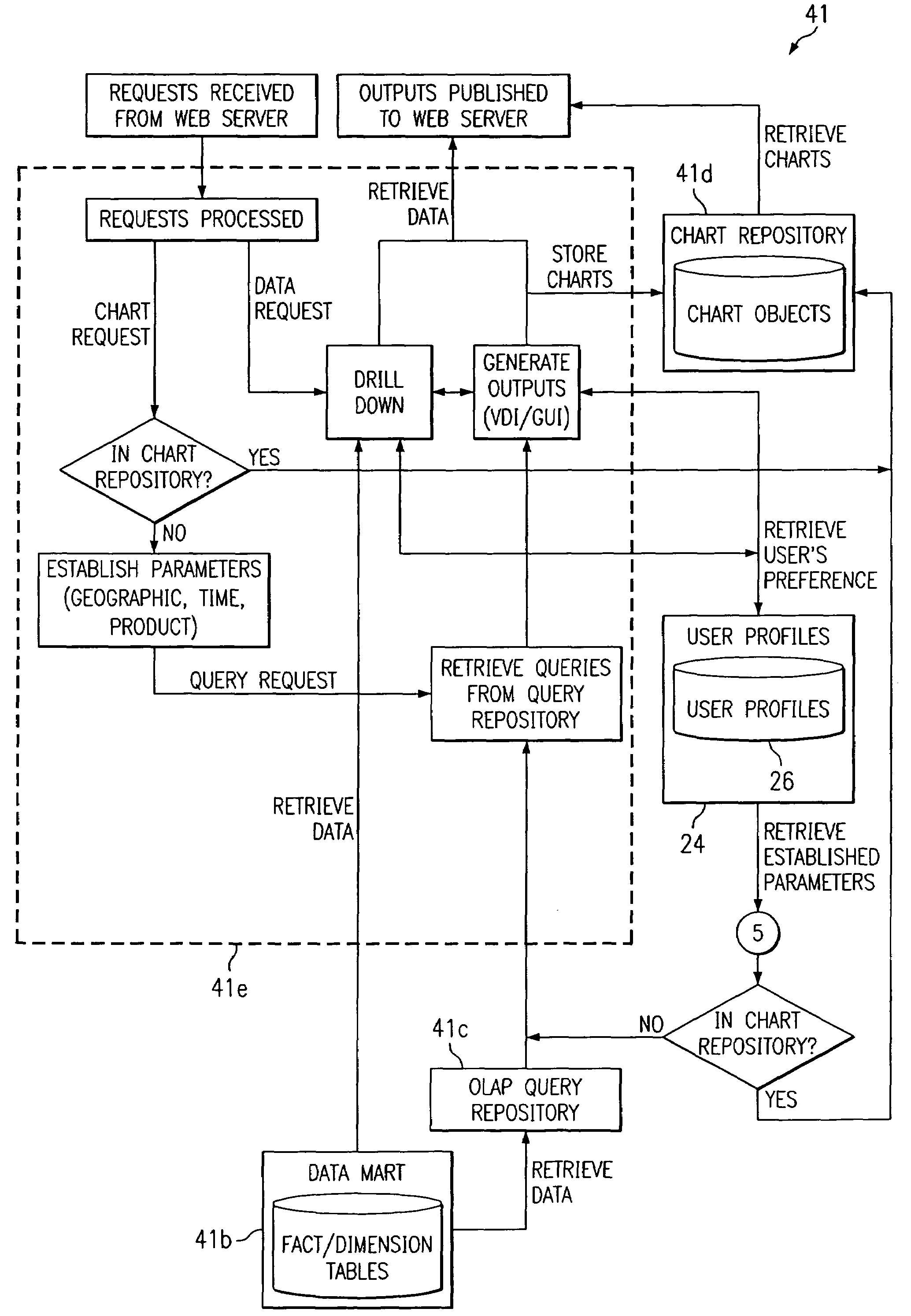
Text mining system for web-based business intelligence applied to web site server logs
InactiveUS7330850B1Data processing applicationsMultiple digital computer combinationsClustered dataWeb site
A text mining system for collecting business intelligence about a client, as well as for identifying prospective customers of the client, for use in a lead generation system accessible by the client via the Internet. The text mining system has various components, including a data acquisition process that extracts textual data from Internet web sites, including their logs, content, processes, and transactions. The system compares log data to content and process data, and relates the results of the comparison to transaction data. This permits the system to provide aggregate cluster data representing statistics useful for customer lead generation.
Owner:CALLAHAN CELLULAR L L C +1
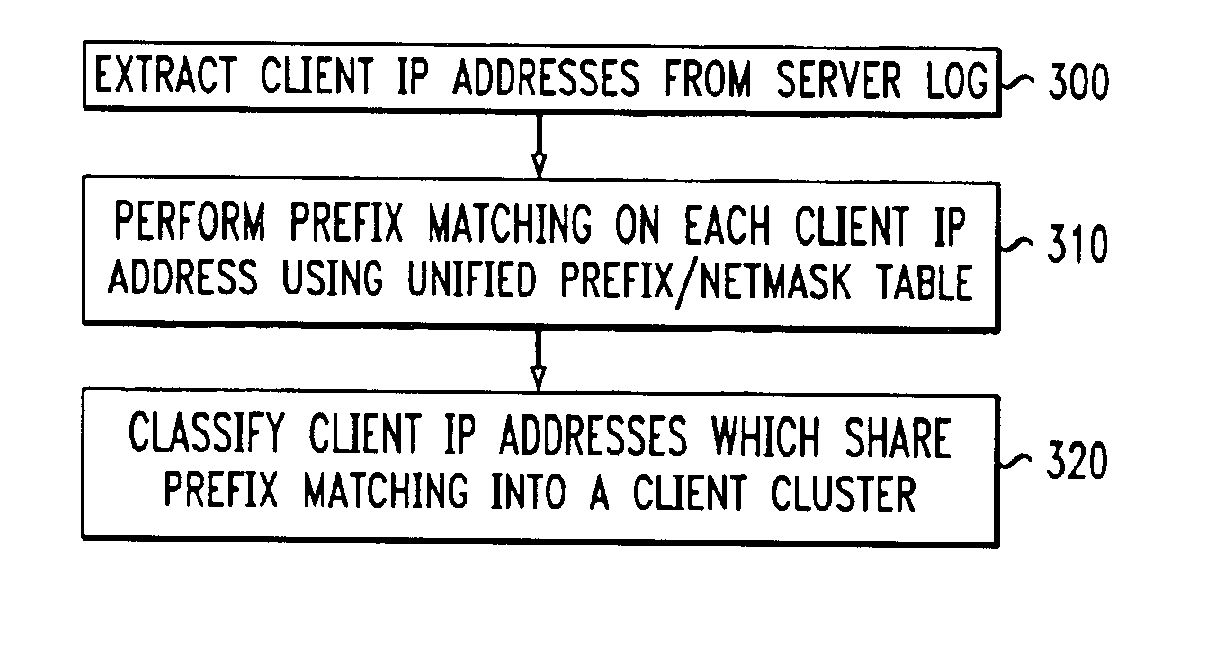
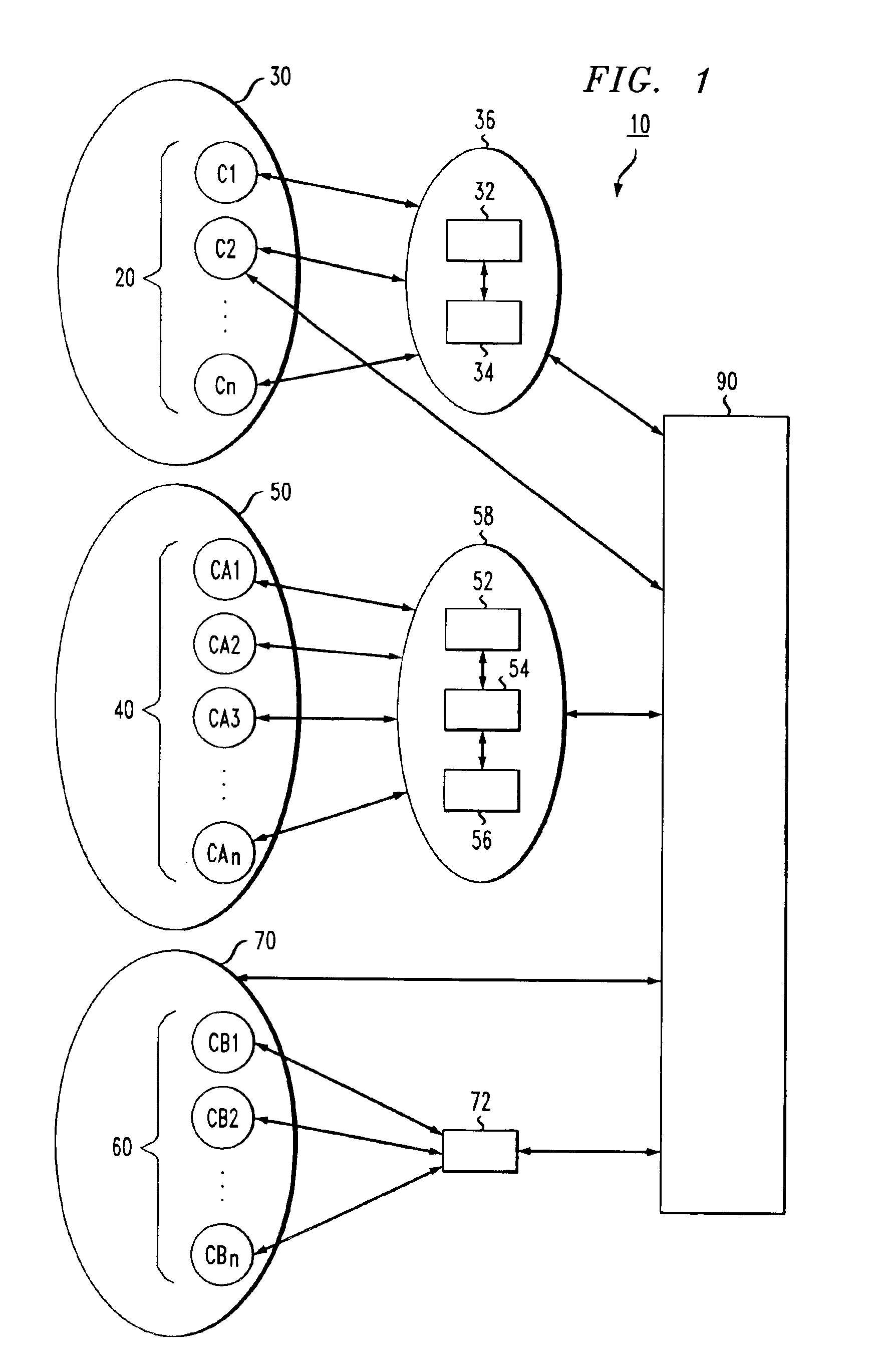
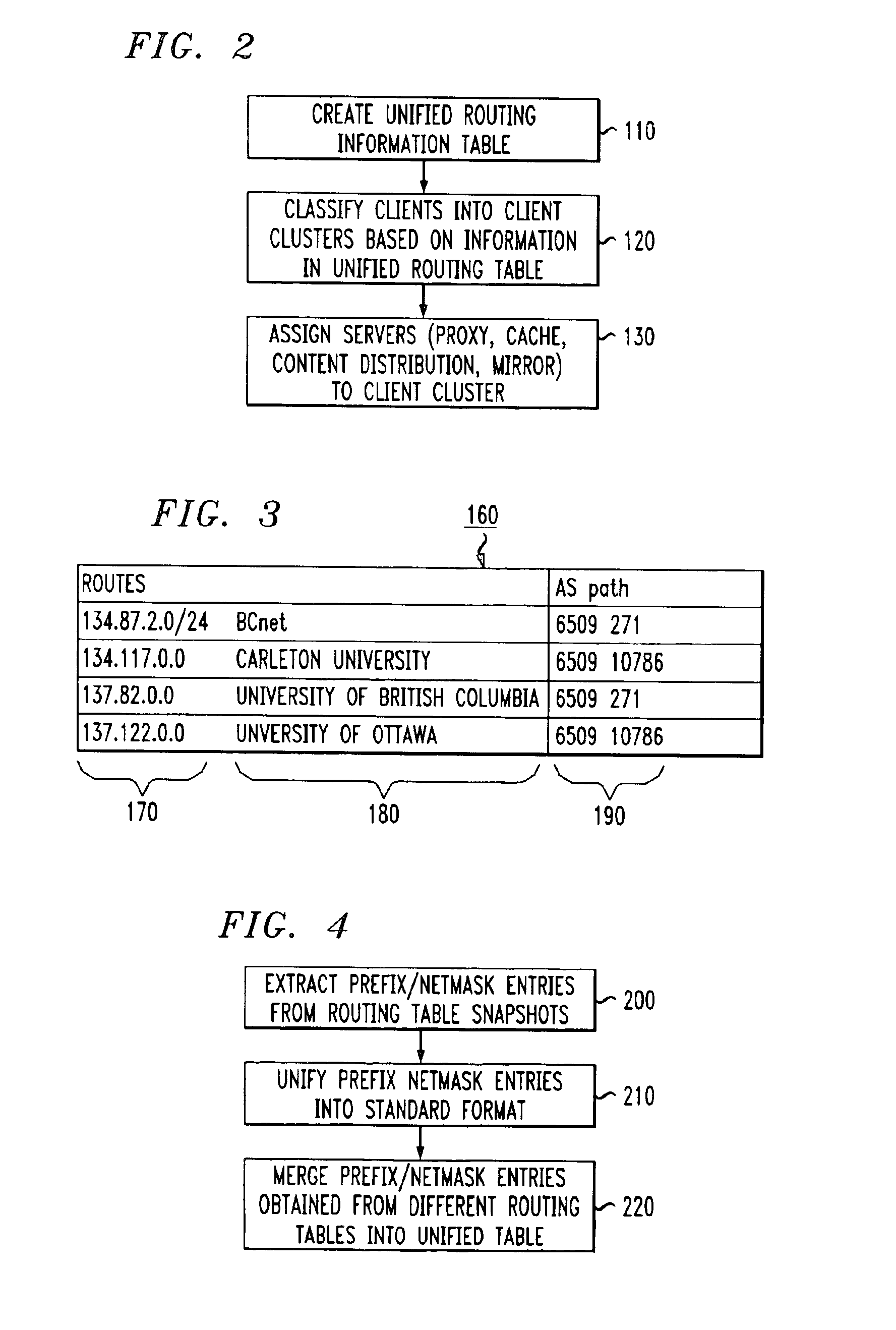
Method for network-aware clustering of clients in a network
InactiveUS6928485B1Relational databasesMultiple digital computer combinationsServer logContent distribution
A method for clustering together network clients for guiding of placement of network servers is disclosed. A number of routing table prefix / netmask entries are aggregated and unified into a tubular format. The routing table entries may be converted into a singular format. A network server log is used to extract a number of client IP addresses which are compared to the entries within the unified routing table. A common prefix shared by a number of the client IP addresses and an entry in the unified routing table is determined and used to cluster the clients together in a client cluster. Network servers, such as proxy server, cache servers, content distribution servers and mirror server may be placed in the network according to the client clusters.
Owner:AMERICAN TELEPHONE & TELEGRAPH CO
Method and system for monitoring performance of a client-server architecture
InactiveUS7933988B2Monitor performanceError detection/correctionDigital computer detailsServer logClient-side
An arrangement which jointly exploits an agent component installed in a server-side portion of client-server architecture for emulating requests of actual clients of the client-server architecture and measuring a server execution time indicative of a time elapsed between reception of an emulated end-user request at a server component and generation of a result of said emulated end-user request at said server component; information stored in a server log file about a hit end to end response time, i.e., the time elapsed between the instant in which the end-user sends a request to the server component and the instant in which result of the request reaches the end-user. From the server execution time and the hit response time, the delay due to the network connecting the server-side portion of the client-server architecture to a client-side portion may be determined. The network delay and the server execution time are then used for monitoring performance of the client-server architecture by distinguishing network related problems from server-related problems or even from client-related problems.
Owner:TELECOM ITALIA SPA
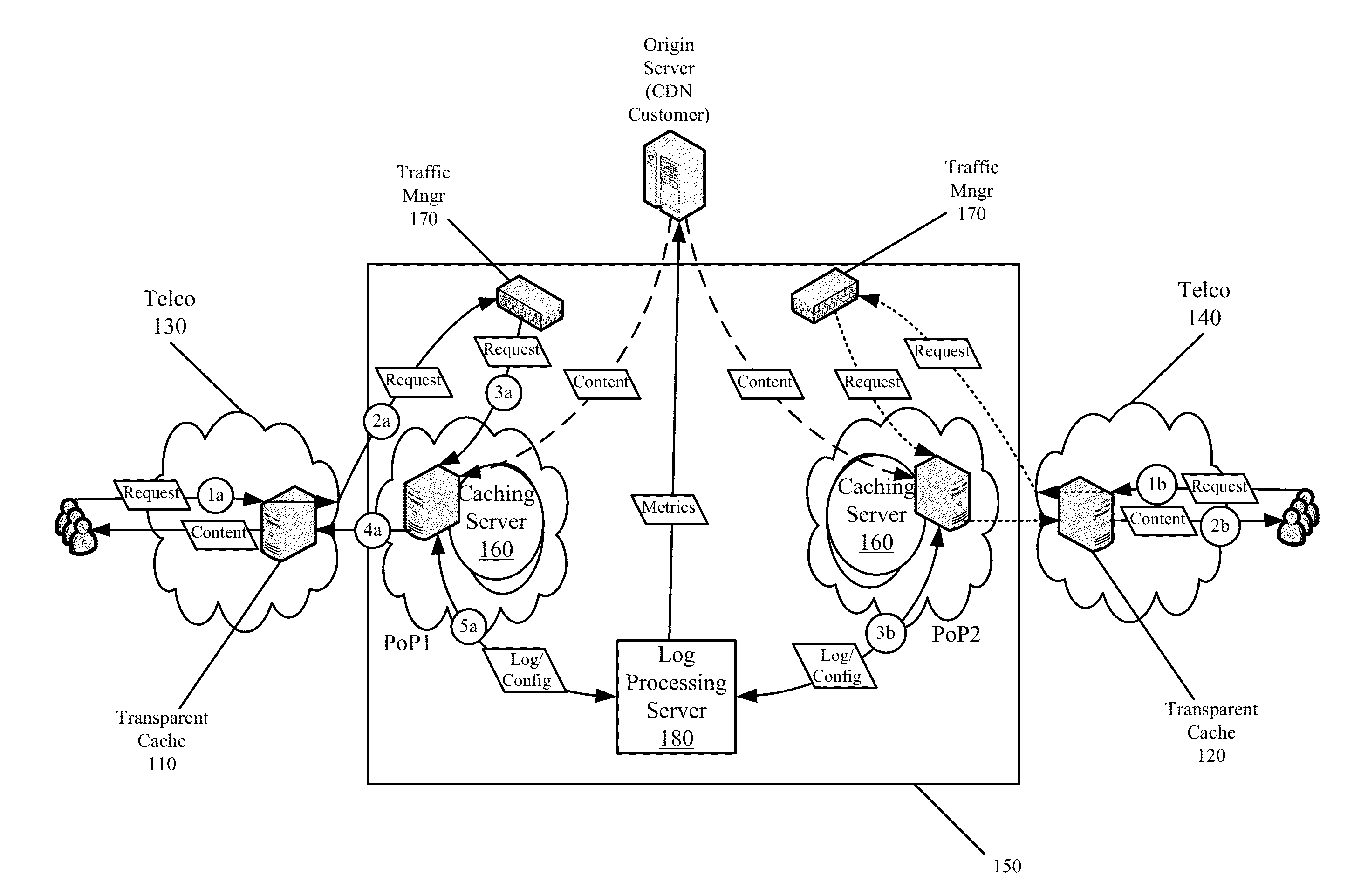
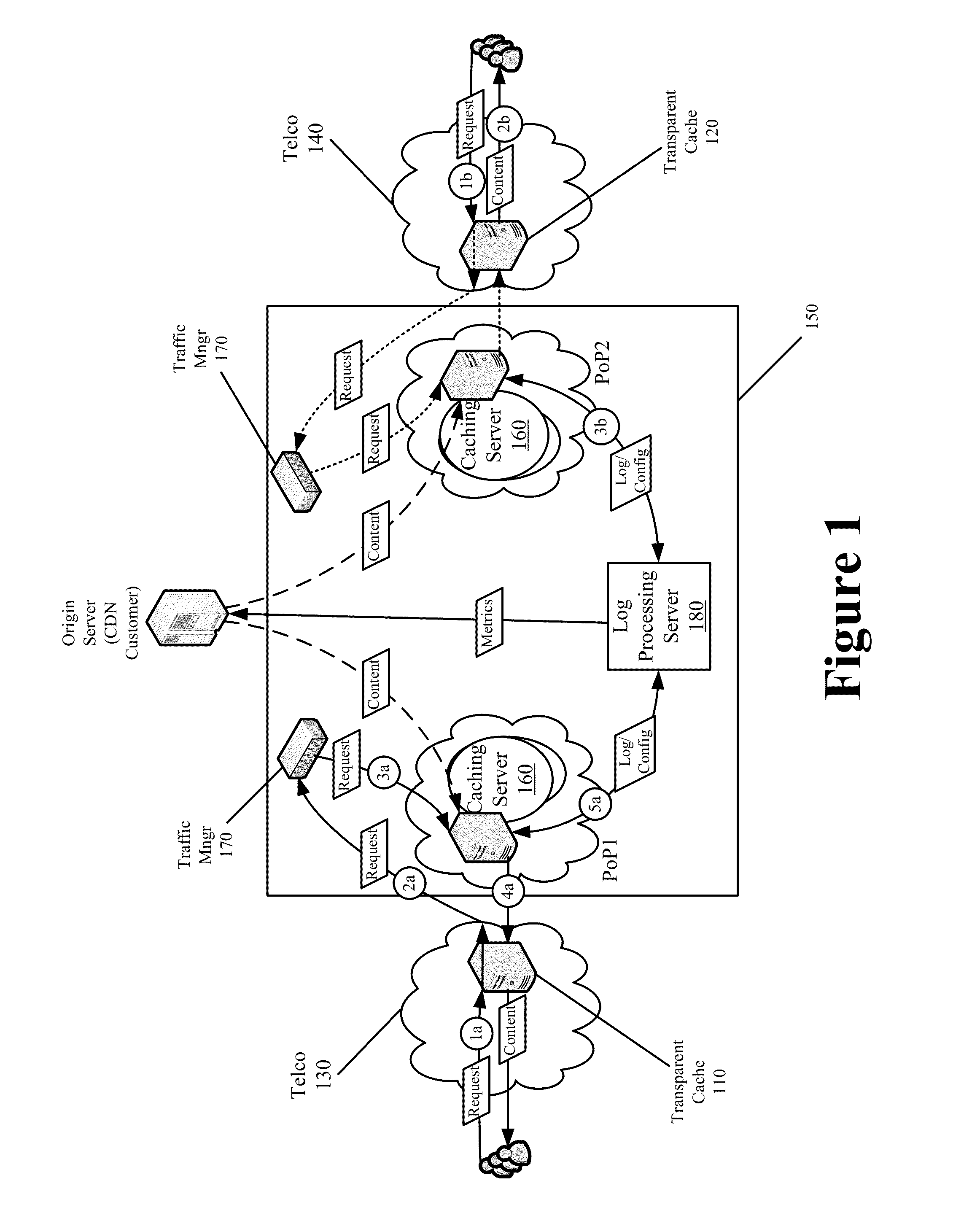
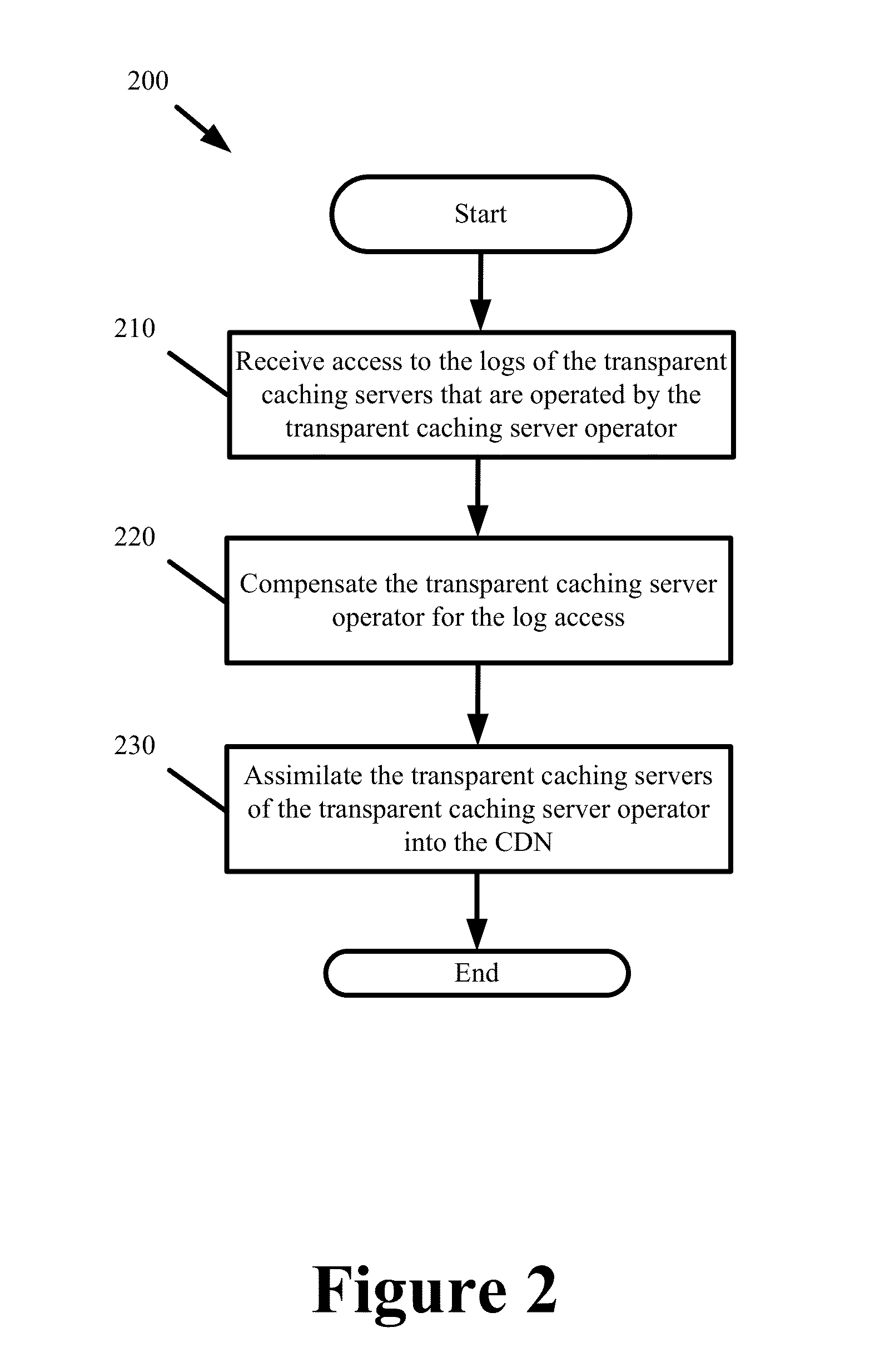
End-to-End Content Delivery Network Incorporating Independently Operated Transparent Caches and Proxy Caches
ActiveUS20130046883A1Accurately and comprehensively track and report metricImproves content deliveryDigital data information retrievalDigital computer detailsServer logCache server
Some embodiments provide an end-to-end federated CDN solution that assimilates a transparent caching server that is operated by a transparent caching server operator into a CDN that independently operates CDN caching servers. Specifically, the logs from the transparent caching server are assimilated into the CDN by aggregating the logs from the transparent caching server and processing the transparent caching server logs to identify network usage for content of a CDN content provider customer that is delivered by the transparent caching server. The network usage is then combined with the network usage that tracked by the CDN caching servers in order to provide comprehensive report metrics for the content provider customer and to bill the content provider customer for all network usage related to delivering the content provider customer's content irrespective of whether the content was delivered by a transparent caching server or a CDN caching server.
Owner:EDGIO INC
System for collecting, analyzing, and reporting high volume multi-web server usage
InactiveUS6789115B1Minimize data handledEfficient queryData processing applicationsDigital computer detailsServer logRelational database
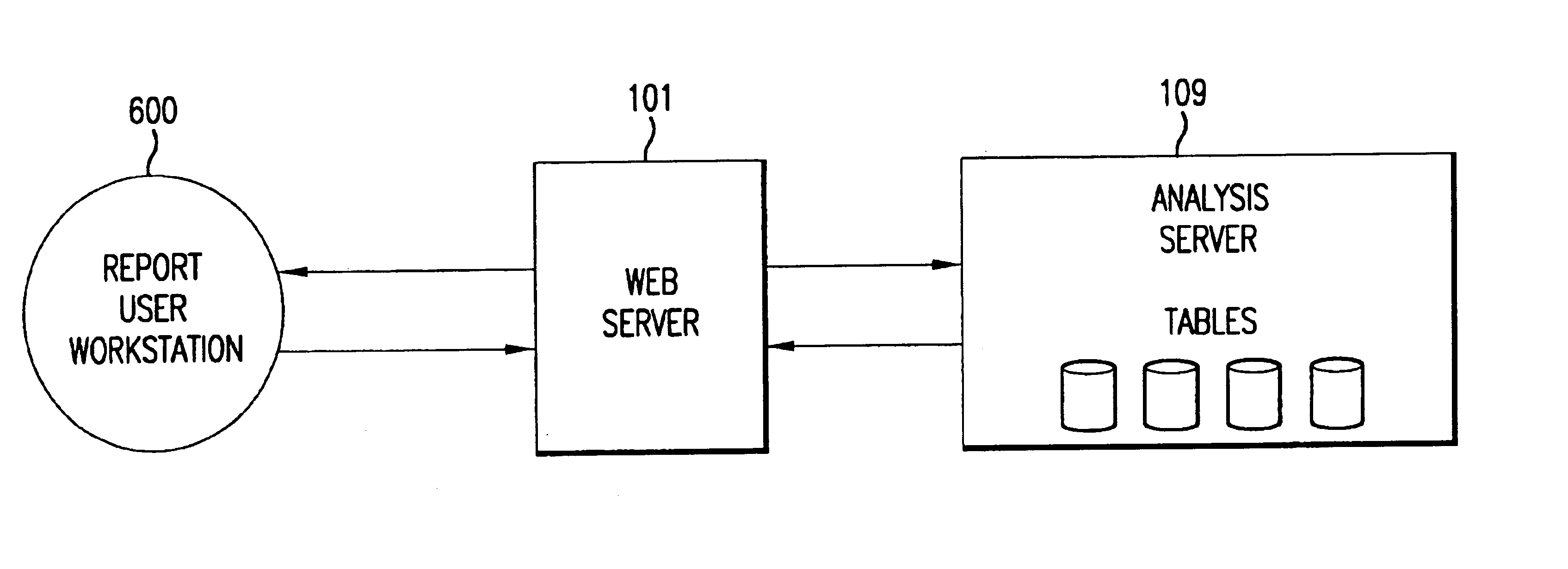
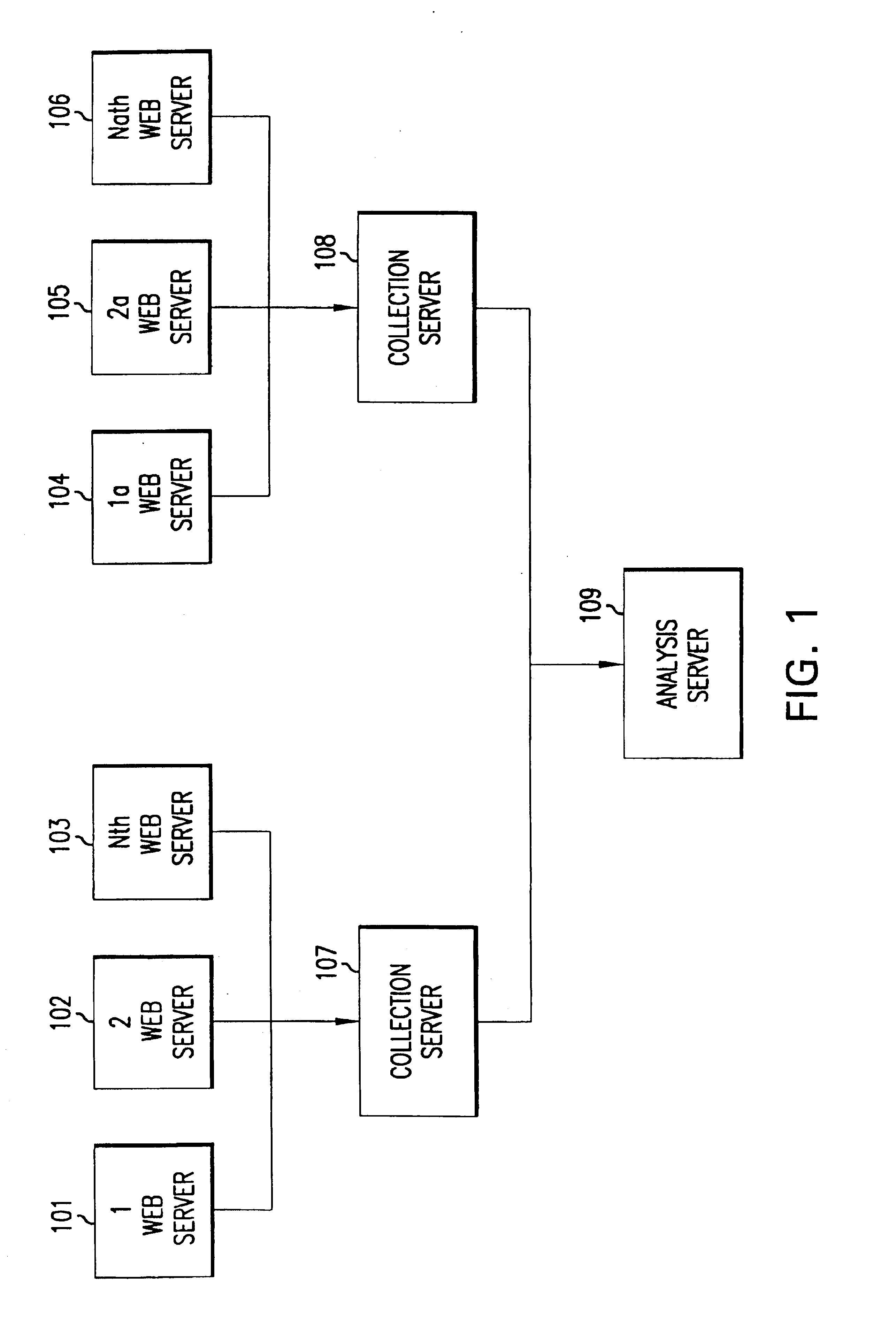
A system for capturing, analyzing, storing and reporting system-users' usage of multiple internet and / or intranet web servers. At each web server in the system, the actions by the system-user create a server log that is processed by the system on a continuous basis. The processing at the server may include, by way of illustration, filtering the logs of about 75 percent of the data and decrypting a system-user's cookie. On a periodic basis, one or more collection servers in the system copy the processed log files from each web server on the system, zip the files, and transfer the files to an analysis server. After the collection is complete, an analysis server processes the data and stores it in a relational database that supports various user specified daily, monthly and quarterly reports of the usage data.
Owner:BANK OF AMERICA CORP
Method of providing live feedback
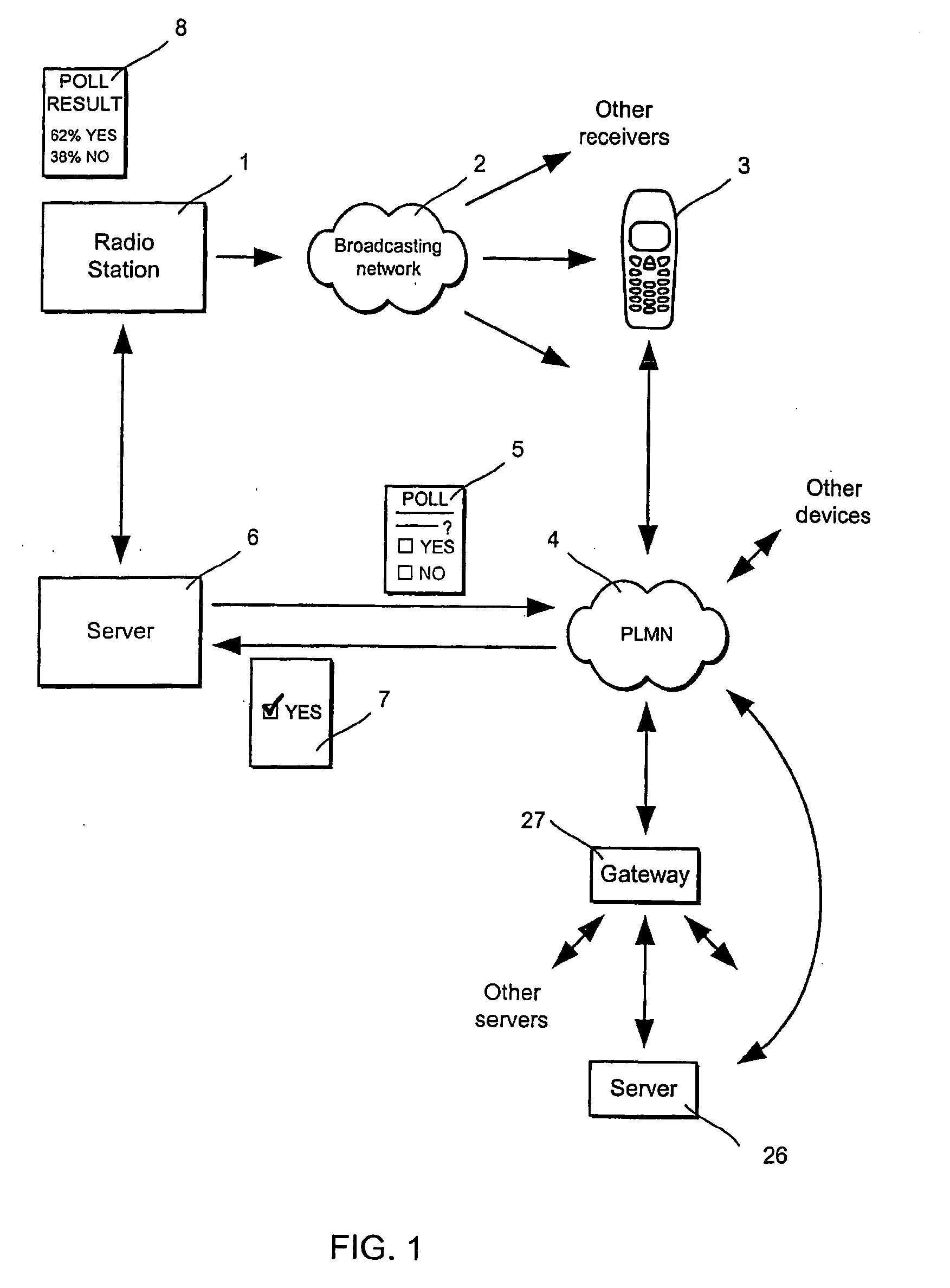
InactiveUS20050054286A1Broadcast information characterisationBroadcast transmission systemsWeb siteServer log
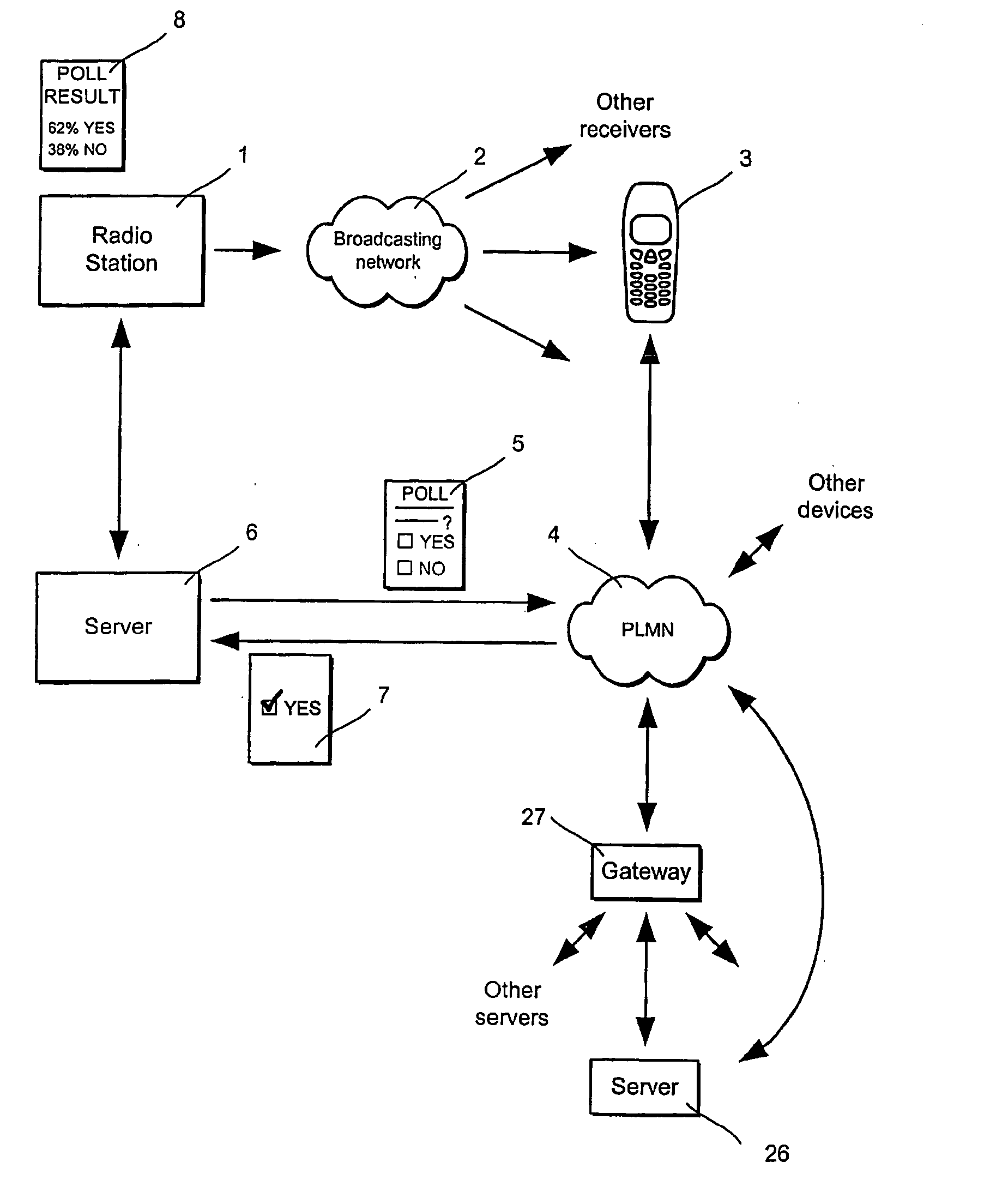
A radio station (1) transmits a radio programme using a VHF-FM singal which is received by a WAP-enabled mobile commnicaitons device (3). The signal includes radio datea service (RDS) data which includes the URL of a web-site associated with the radio station. The user accesses the web-page and participates in an opinion poll by casting a vote. The server logs the vote. The radio station counts the votes and announces the votes while the radio programme is still on air.
Owner:NOKIA CORP
Method of network merchandising incorporating contextual and personalized advertising
InactiveUS20080097843A1Improve Personalized ExperienceDiscounts/incentivesAdvertisementsServer logPersonalization
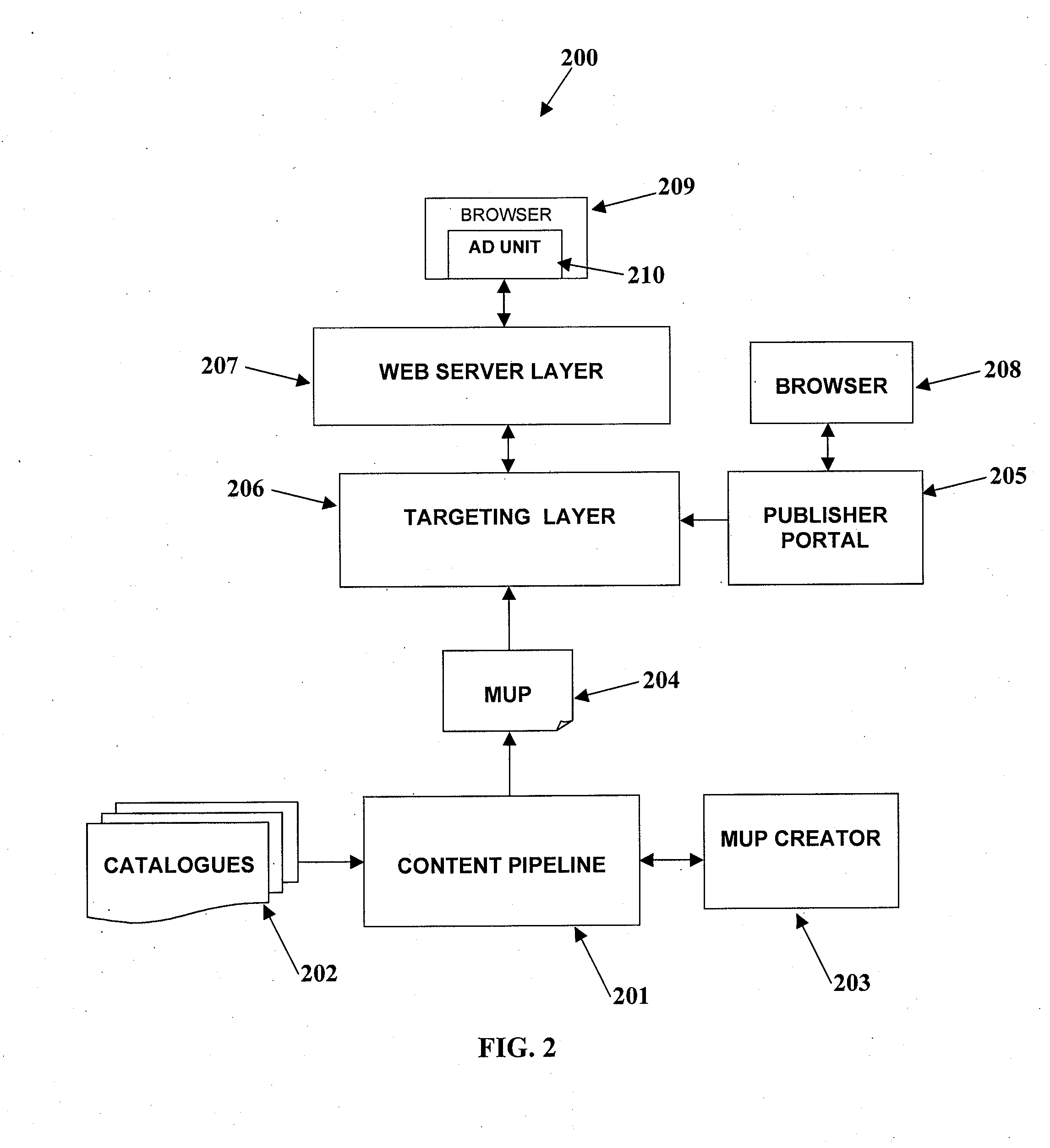
A method of network merchandising incorporates contextual and personalized advertising with human input to deliver relevant retail offers to interested online consumers efficiently and intelligently. Catalog content from retailers is downloaded, semantically analyzed and merged. The merged content is filtered using machine- and human-generated specifications to produce a merchandisable universe of products (MUP). Marketers and publishers create and modify corner store ad units and specify product offers from the MUP to display in those units. Publishers deploy the ad units on their web pages. Compensation of publishers by retailers can use a pay-for-performance model. Users visit the publisher's pages, viewing the product offers in the rendered ad unit. Performance data related to context, history, network and geo-location, product attributes and product combinations is derived from server log files is used to dynamically optimize and refine product placement in real time, providing a highly personalized experience for the user.
Owner:TUMRI
Renewable energy certificate accumulating, distributing, and market making
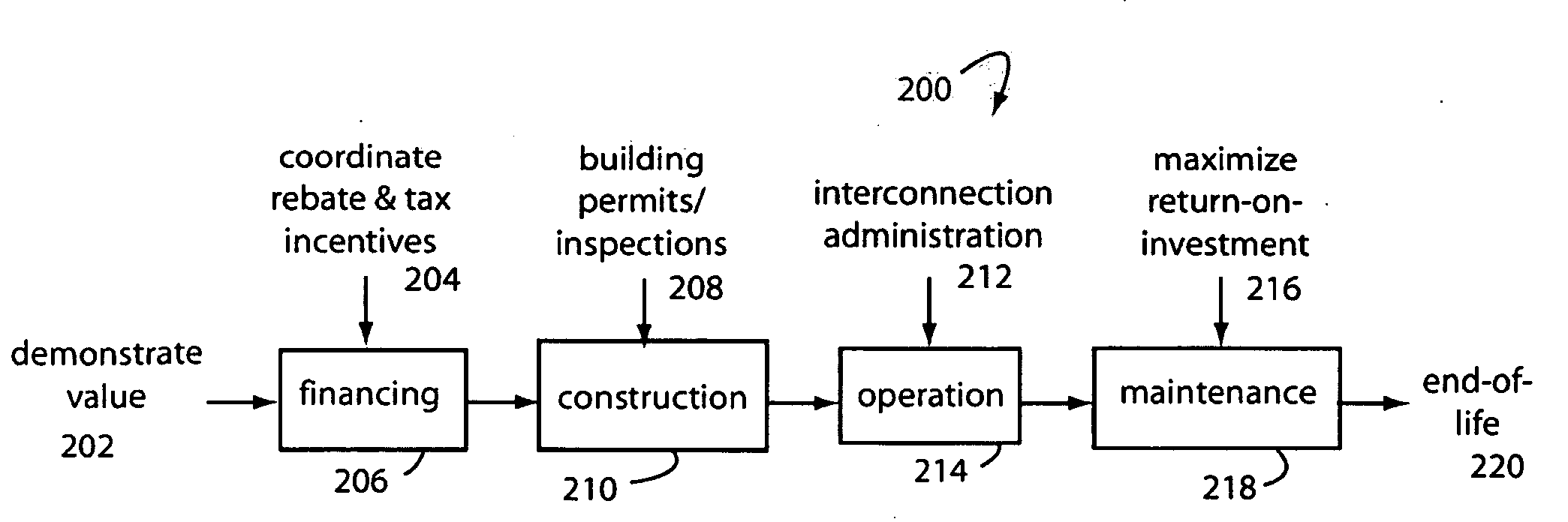
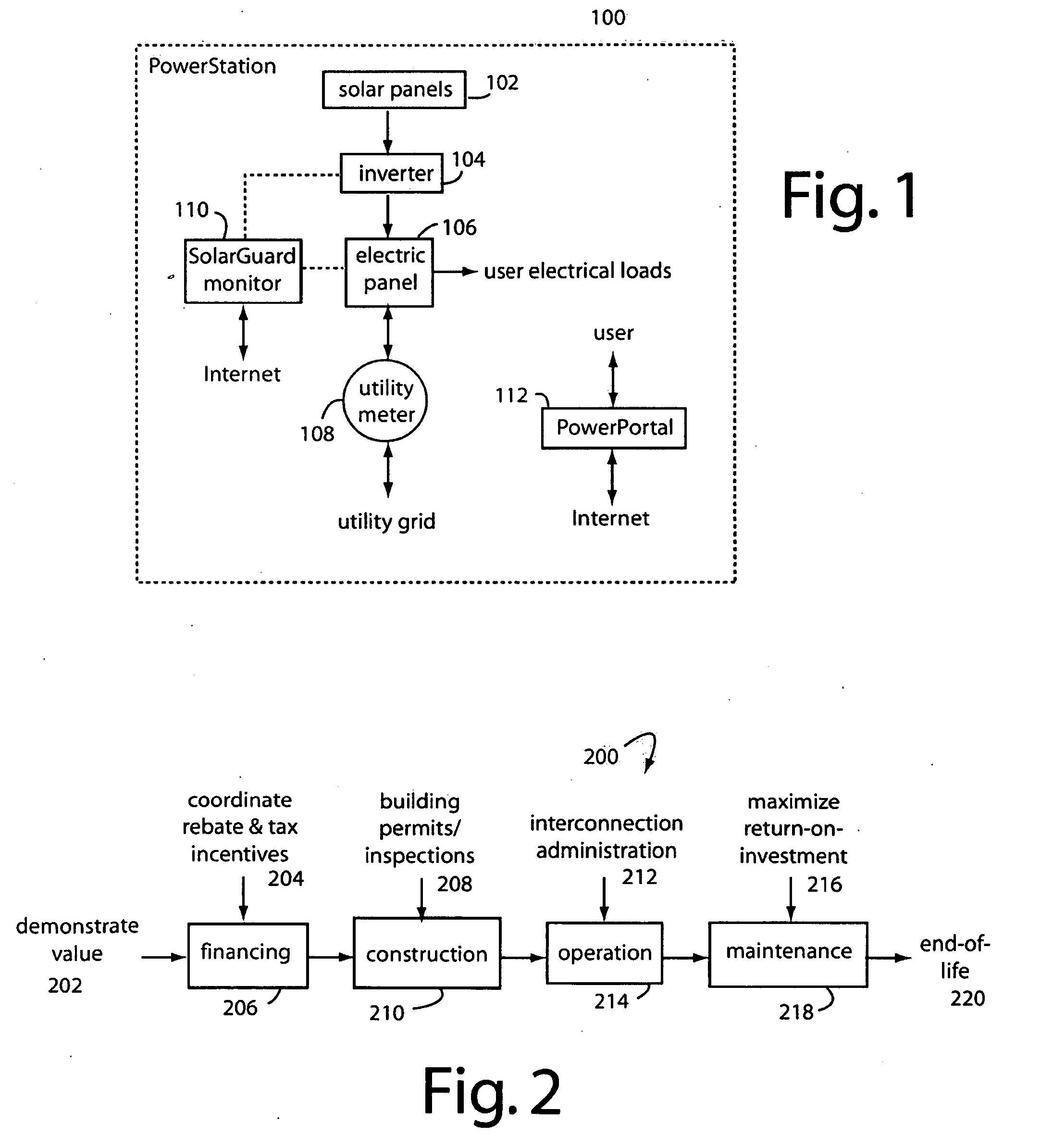
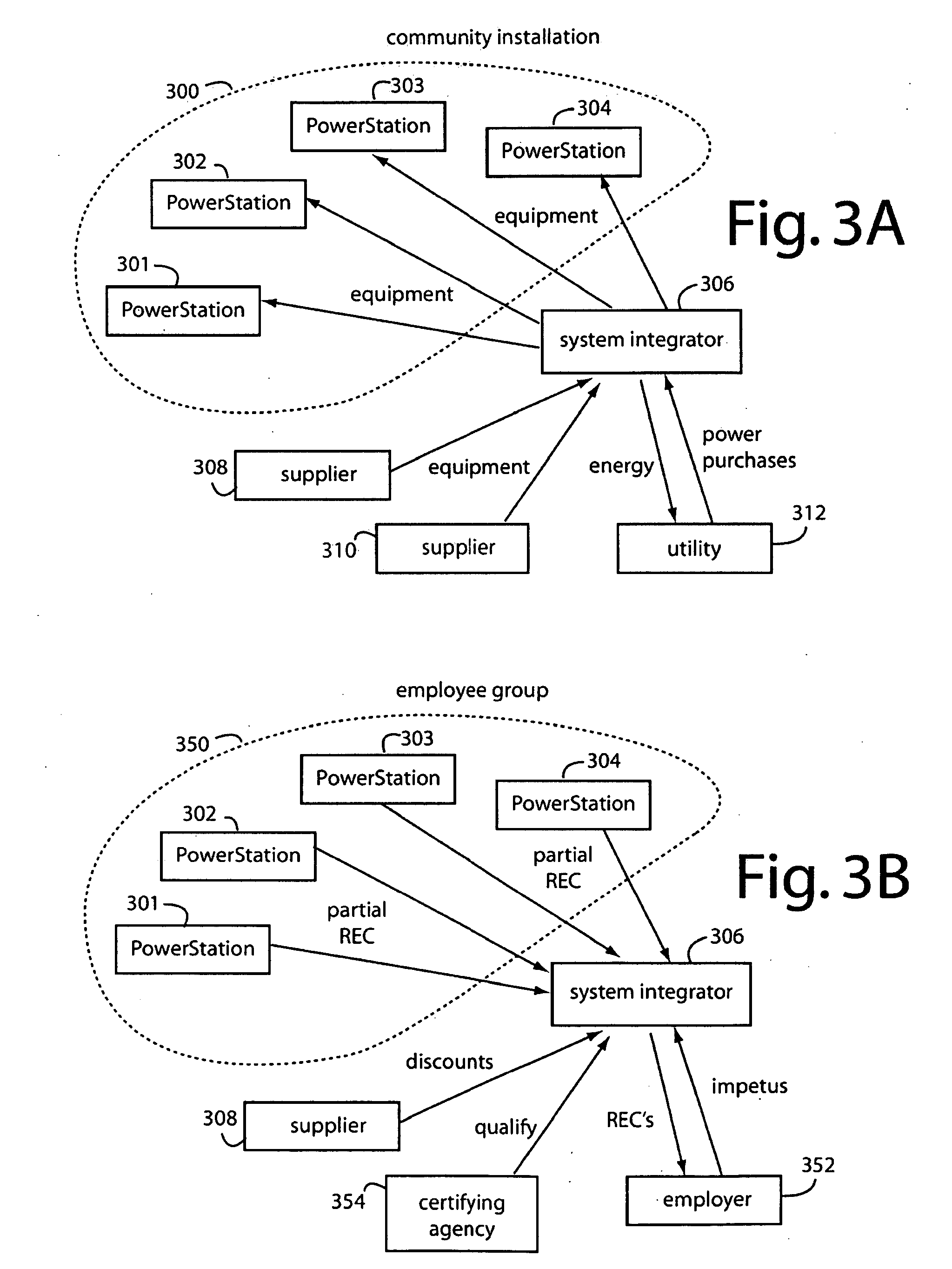
A renewable energy certificate business model embodiment of the present invention accumulates small shares of qualifying energy produced by many small solar installations into the minimum unit sizes that can be certified, traded and sold. Renewable energy generation and load control monitors are installed at hundreds and thousands of small installations to automatically report to centralized servers. These servers log and certify the production of renewable energy into the lot sizes needed for an efficient market. A system integrator provides the brokerage mechanisms needed for buyers and sellers to trade quickly and easily. In one aspect, an online auction website is constructed and maintained on the Internet as a centralized clearing house. The system integrator backs the quality of the lots and the trades with their large enterprise reputation and credit worthiness. The trading can be in renewable energy portfolios, emission offsets, carbon dioxide offsets, and other environmental attributes.
Owner:SOLARCITY
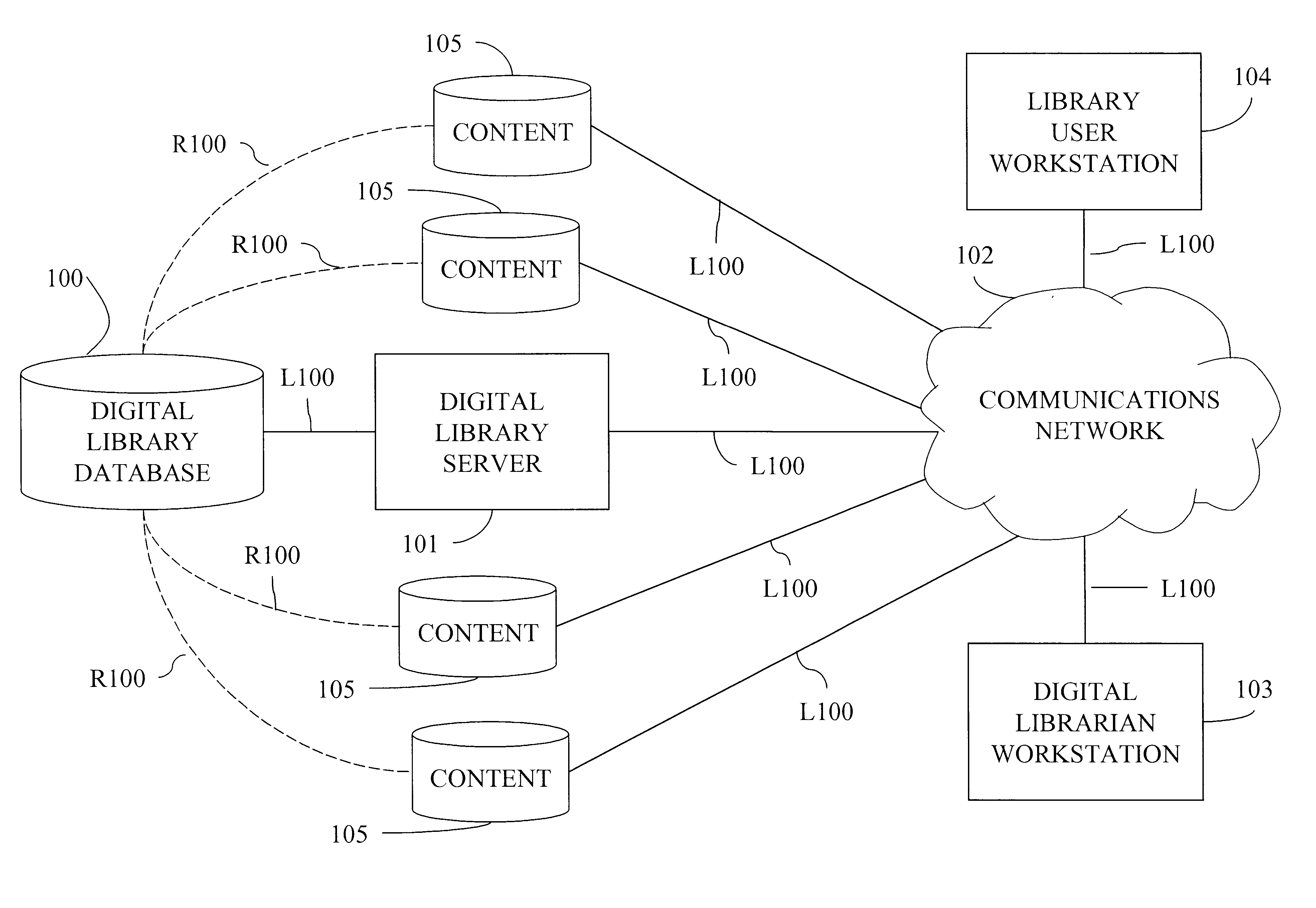
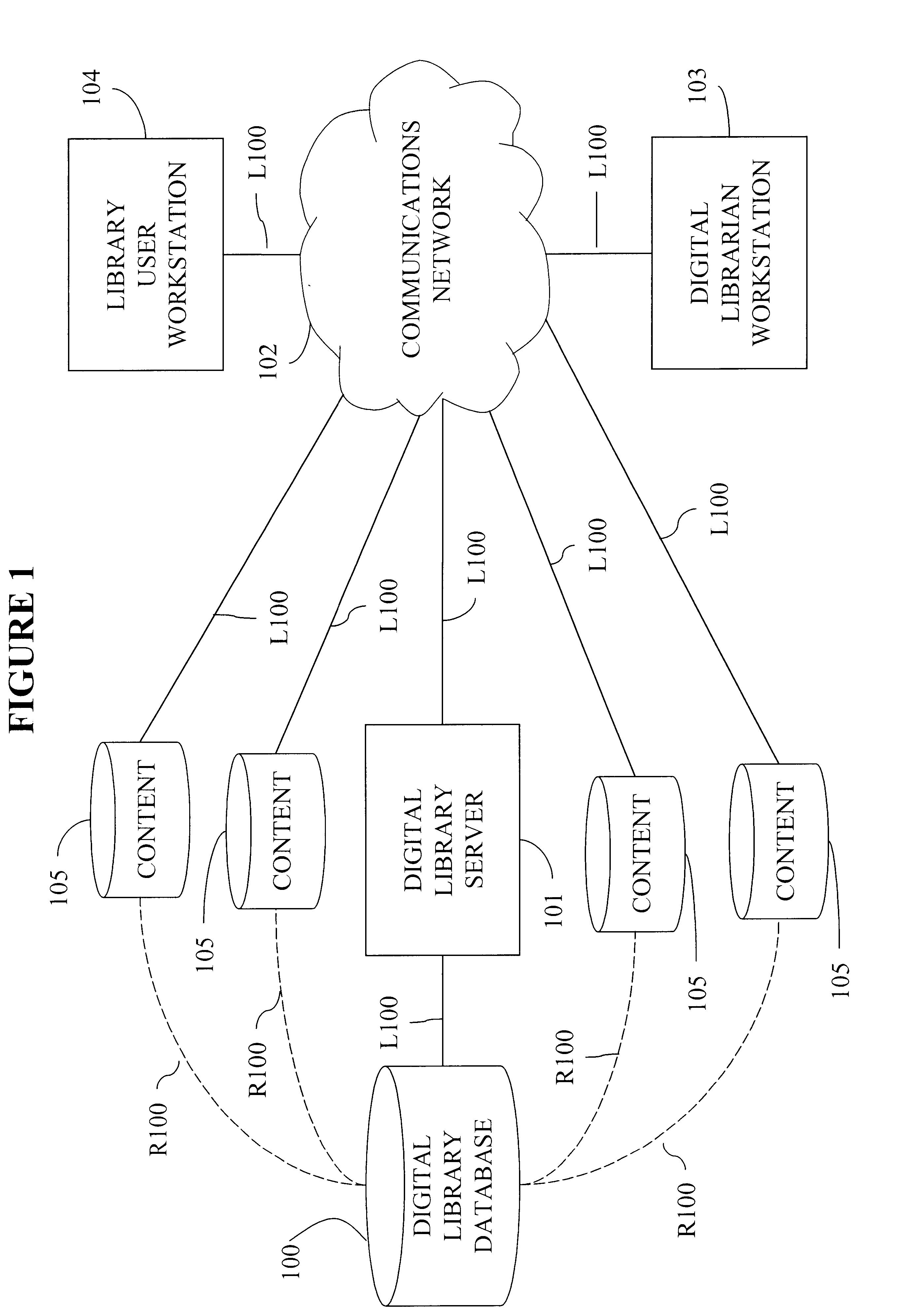
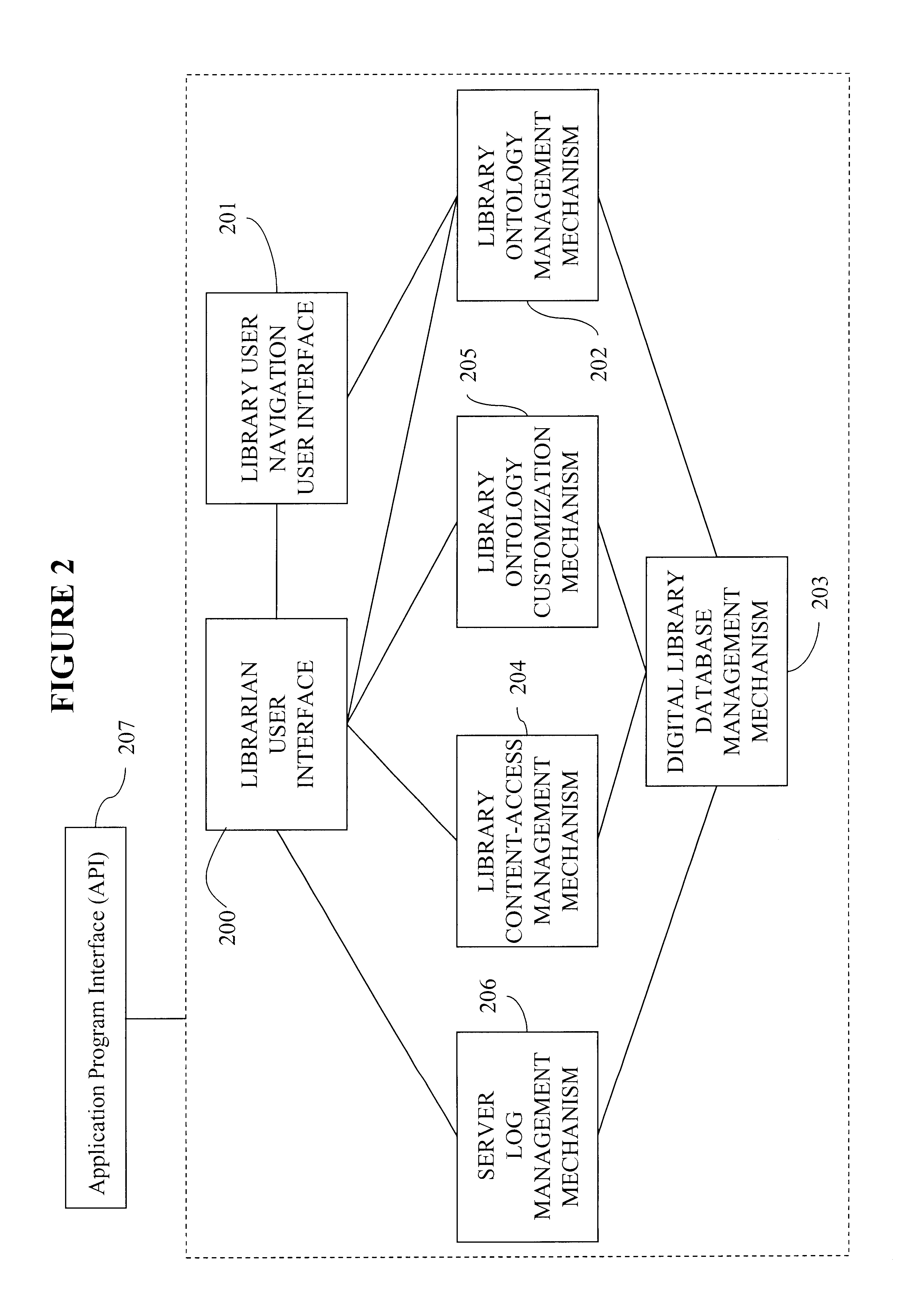
System, method, and computer program product for managing access to and navigation through large-scale information spaces
InactiveUS6850944B1Easy to addEasily cataloguedData processing applicationsDigital computer detailsServer logInformation space
A system, method and computer program product for managing access to and navigating through large-scale information spaces. A digital library is created by maintaining an ontological hierarchy in a database. Content is accessible through links to resources available over a communications network, such as the Internet. Librarians tailor the accessibility of content of the library as well as the view into the library that is presented to their user population to meet the specialized needs of their users. Content available via the library may be privileged according to qualitative feedback from users maintained within the digital library. An exactly-correct server log tracks the traversal of users through the digital library. The functionality of the digital library is accessible via an application program interface.
Owner:ALABAMA THE UNIV OF +1
Log acquisition device and log acquisition method
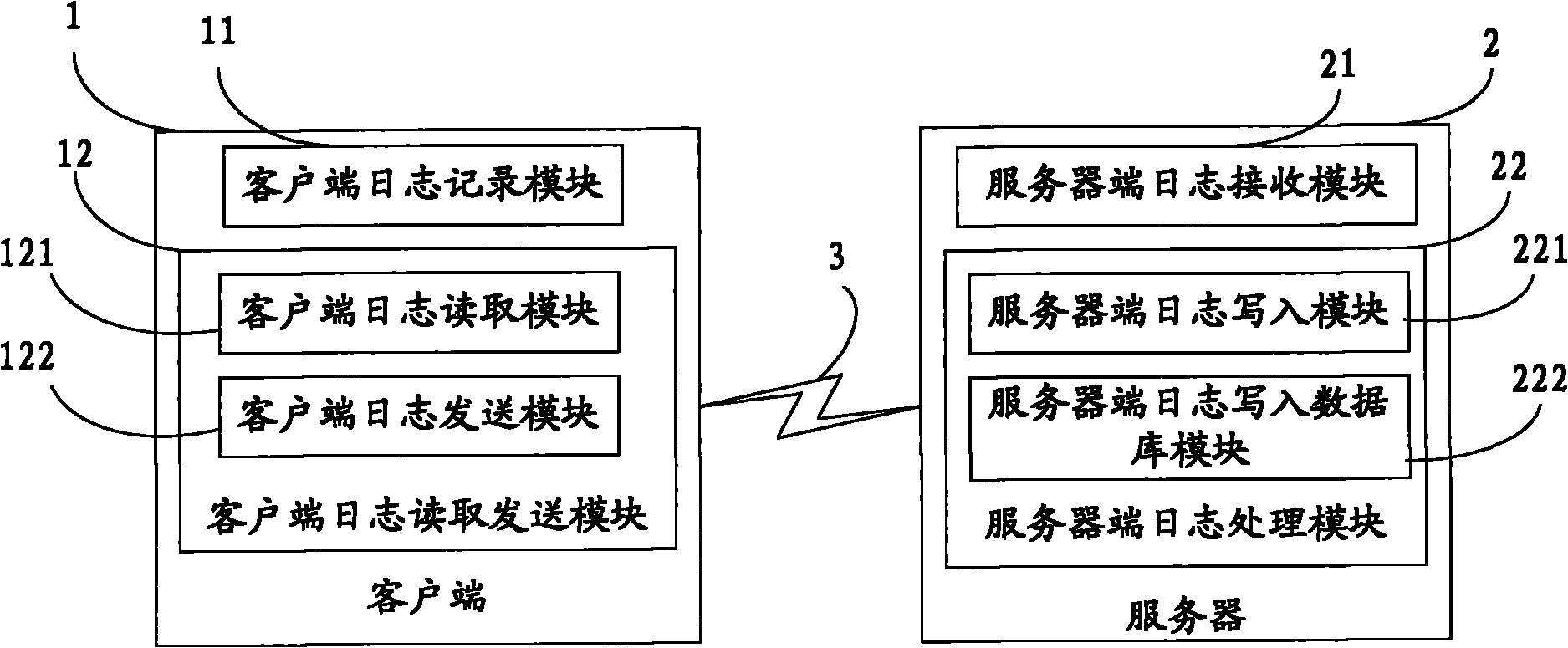
InactiveCN101969386AReal-time deliveryRealize distributed collectionData switching networksServer logNetwork connection
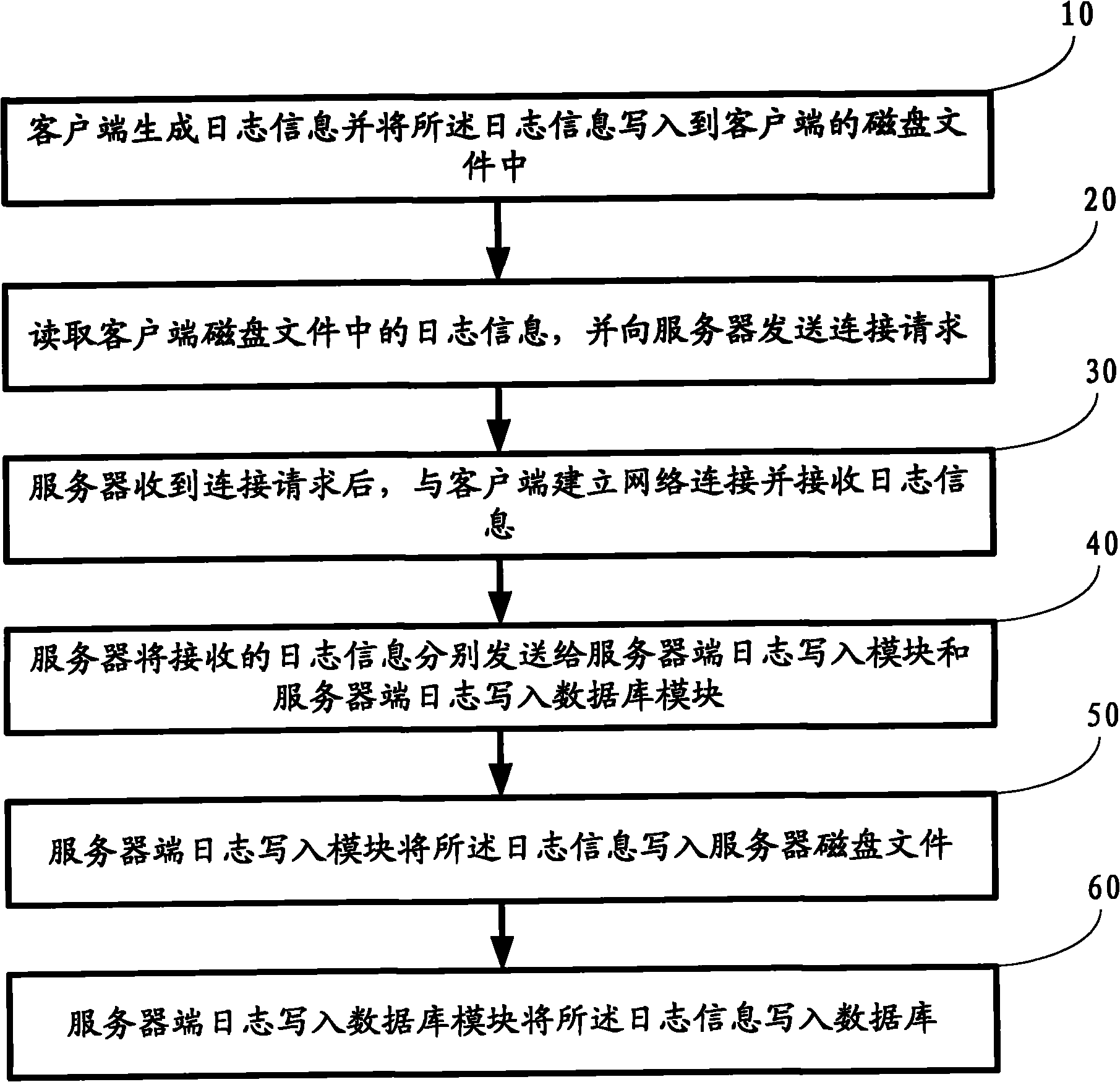
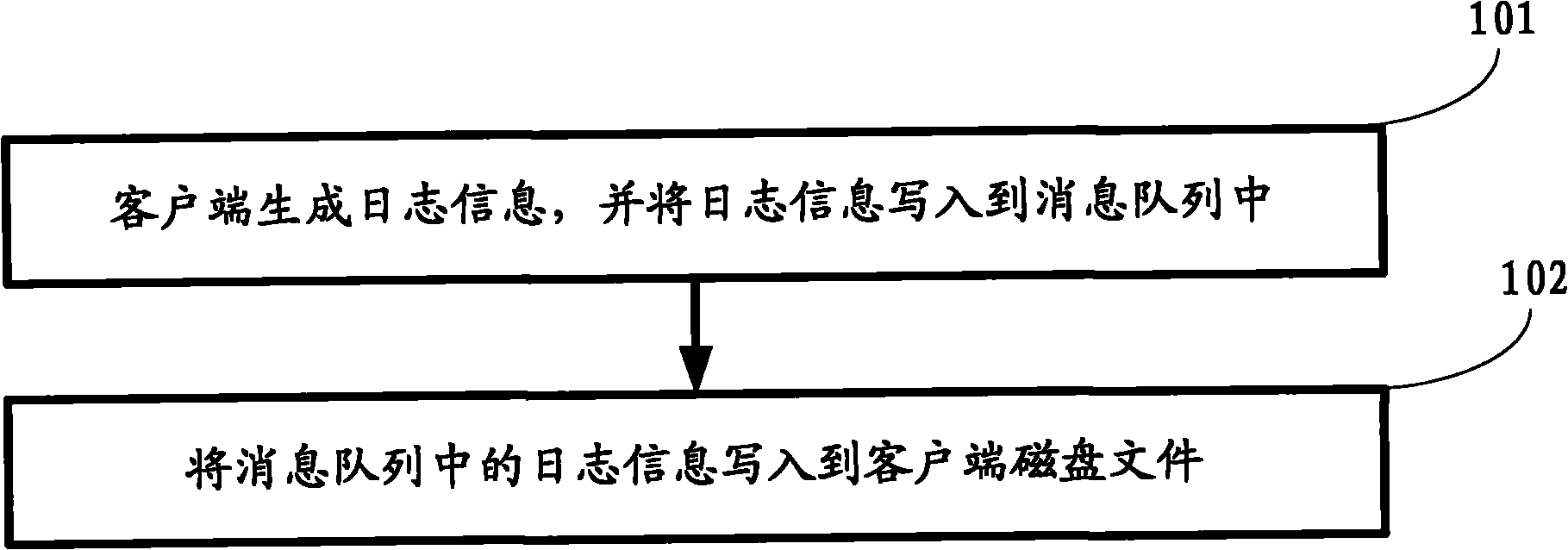
The invention relates to a log acquisition device and a log acquisition method. The device comprises at least one client for collecting logs and at least one server for recording the logs, wherein log information is transmitted between the client and the server through a network in real time. The method comprises that: the client generates the log information, writes the log information into a disk file of the client, reads the log information from the disk file of the client, and sends a connection request to the server; after receiving the request, the server establishes network connection with the client and receives the log information; the server sends the received log information to a server log writing module and a server log writing database module; the server log writing module writes the log information into the disk file of the server; and the server log writing database module writes the log information into the database. When the device and the method of the invention are used, the data analysis is more real-time, and the distributed acquisition of the logs is realized.
Owner:道有道科技集团股份公司 +1
Mobile Social Networking Platform
InactiveUS20080040437A1Mitigate text message costEasy to integrateMultiple digital computer combinationsData switching networksServer logClient-side
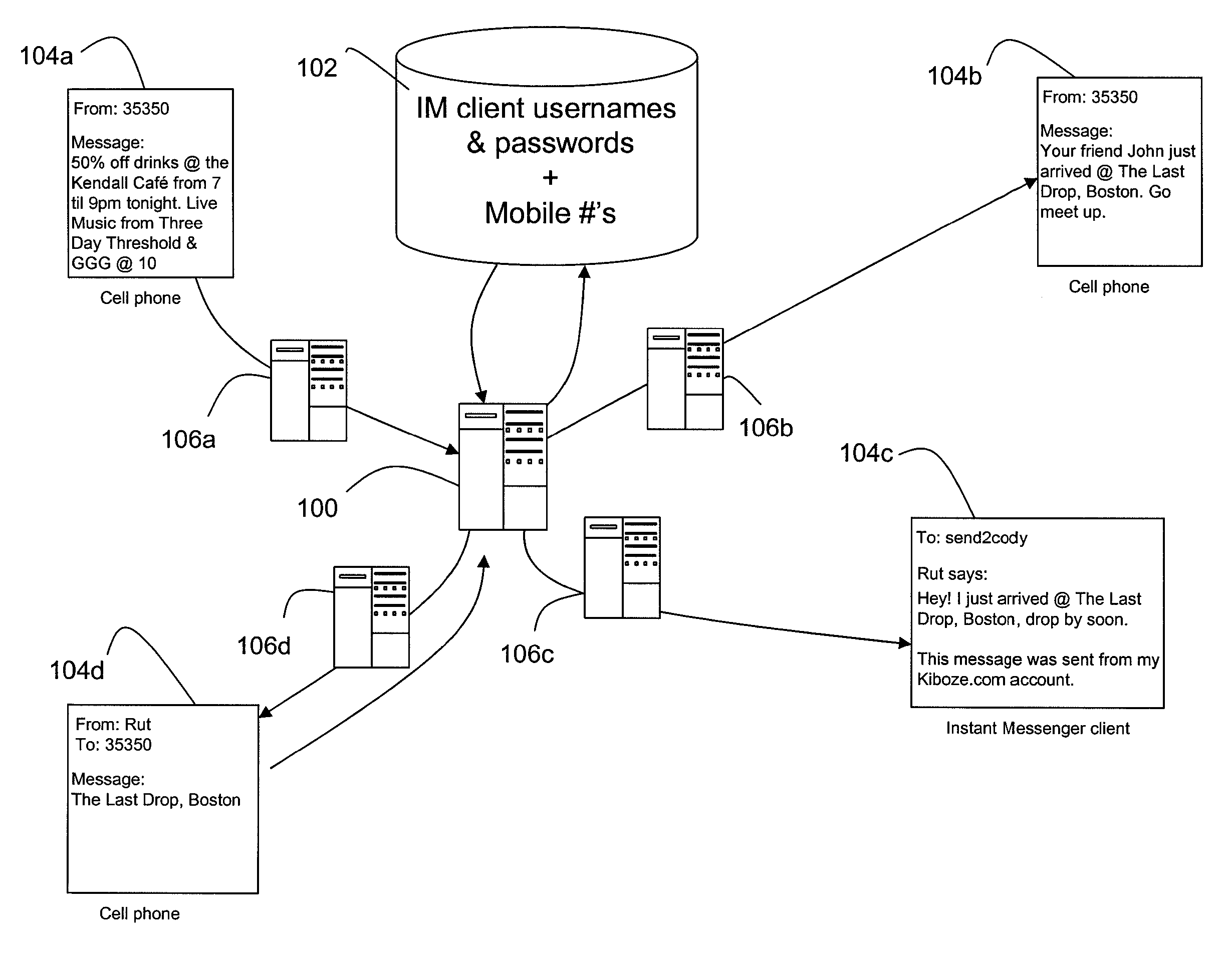
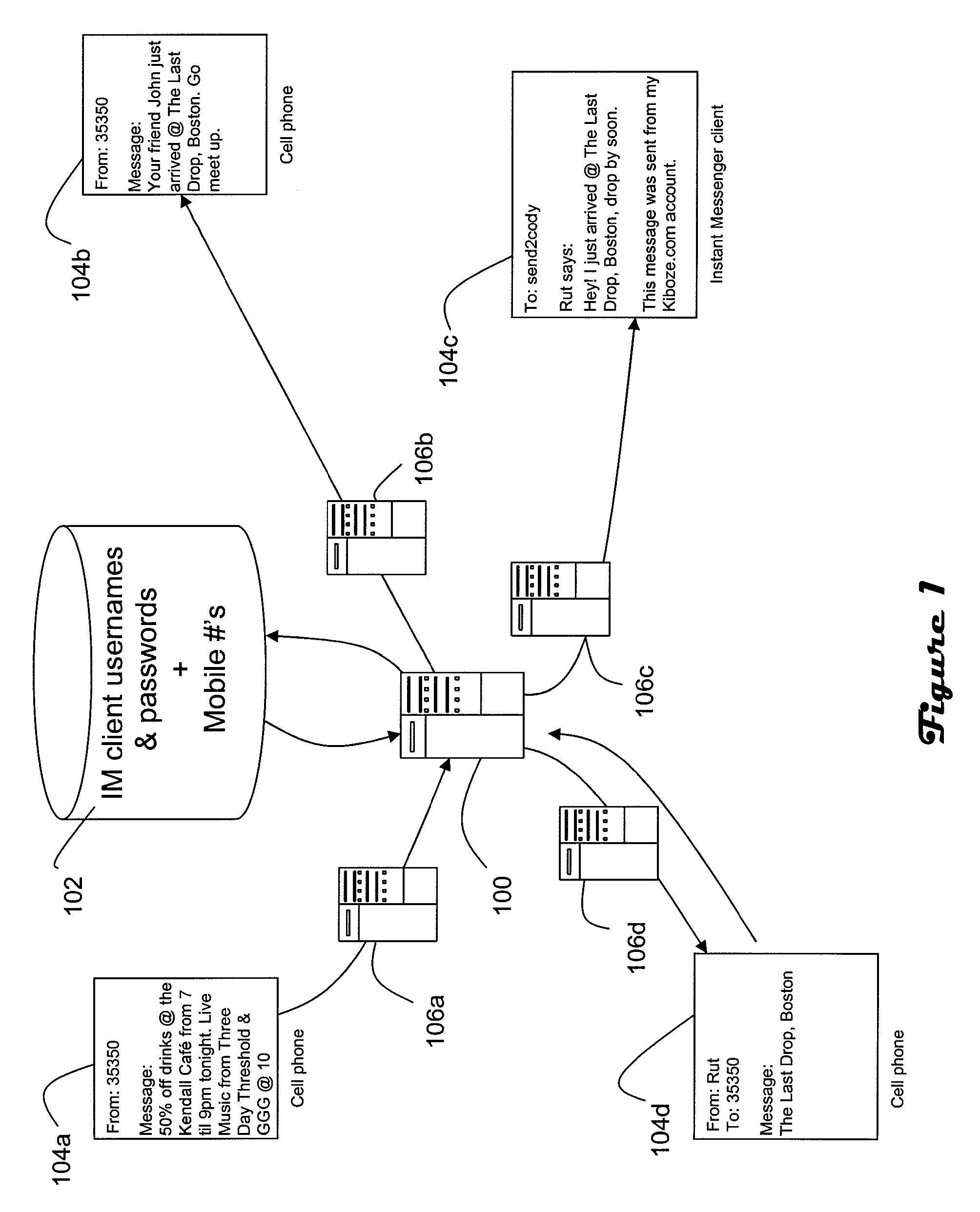
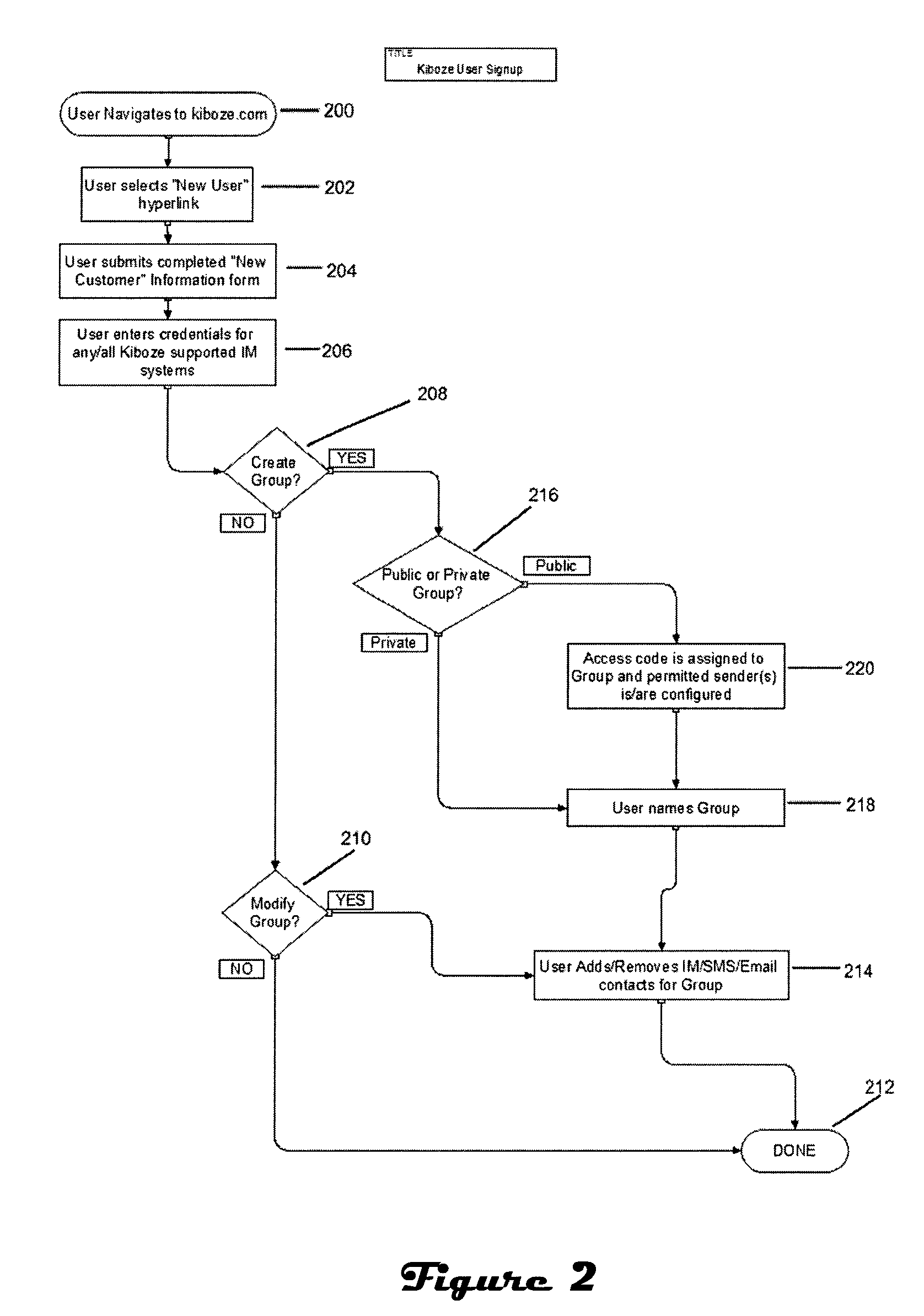
A mobile social networking platform integrates SMS (text messaging) services with Instant Messaging services so that cross-platform messages can be sent, e.g., text-to-IM and IM-to-text. In response to a text message sent by a user, an integration server prompts a corresponding IM message to be sent to the recipient. In one embodiment the integration server prompts transmission of the IM by logging into the user's IM account or accounts. An instant message corresponding to the text message is then sent to the recipient designated by the user via the user's IM account. After prompting transmission of the instant messages by the associated service, the integration server logs-off from the user's IM account or accounts. In an alternative embodiment the integration server itself generates the IM. In order to send an IM to text message a user logs onto an IM client, selects the integration server from a buddy list, composes the message for a particular group, then sends the message to the integration server. The integration server receives message and, based on the message content and the sender, the integration server identifies at least one of the user's ‘groups’ to which the message is to be sent. The group may comprise all subscribers of a group via IM, text and / or email. If a designated recipient is logged-in to the integration server via mobile phone, a corresponding text message is delivered to that mobile phone.
Owner:KIBOZE
Identity verification method, server and readable storage medium
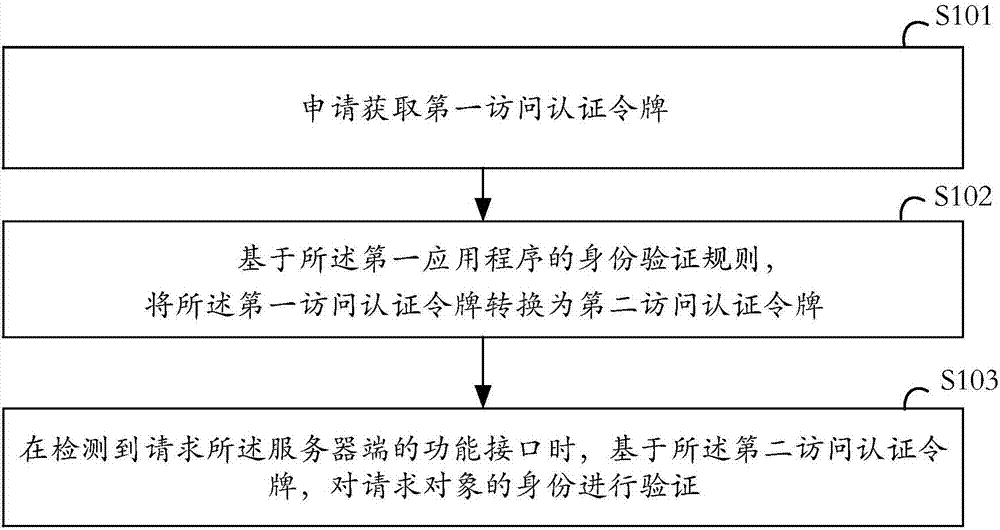
ActiveCN107483509APrevent malicious callsImprove securityUser identity/authority verificationServer logApplication software
The embodiment of the invention provides an identity verification method, a server and a readable storage medium. The identity verification method is used for preventing a function interface of the server from being called maliciously, and the resource safety of a server-side is improved. The method is applied to the server of a first application program. The method comprises the steps that a first access authentication token is acquired, and the first access authentication token is the access authentication token generated based on a rule corresponding to a second application program when the server logs into the first application program through a small program function of the second application program; based on an identity verification rule of the first application program, the first access authentication token is converted into a second access authentication token; when it is detected that the function interface of the server-side is requested, based on the second access authentication token, an identity of a request object is verified.
Owner:WUHAN DOUYU NETWORK TECH CO LTD
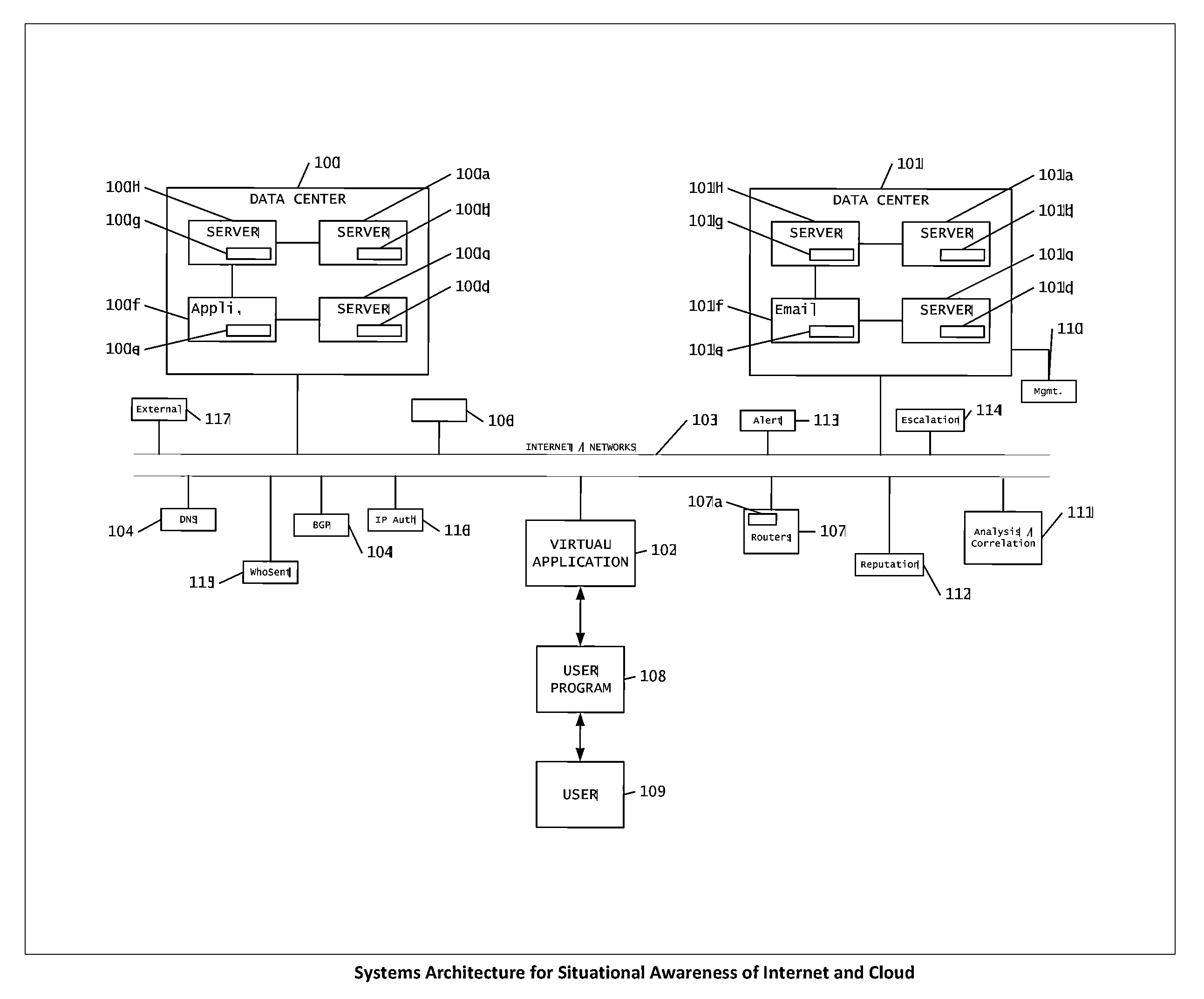
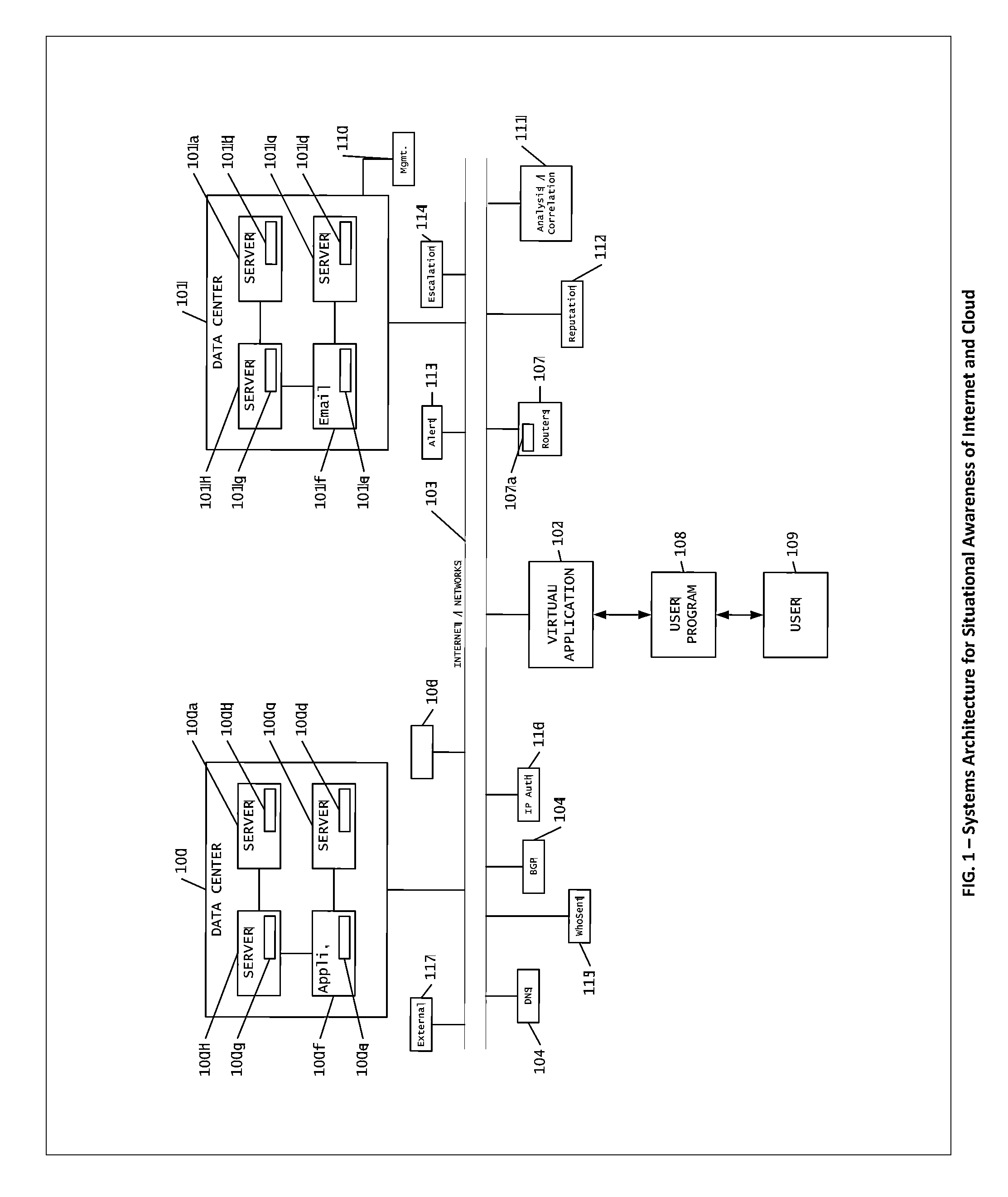
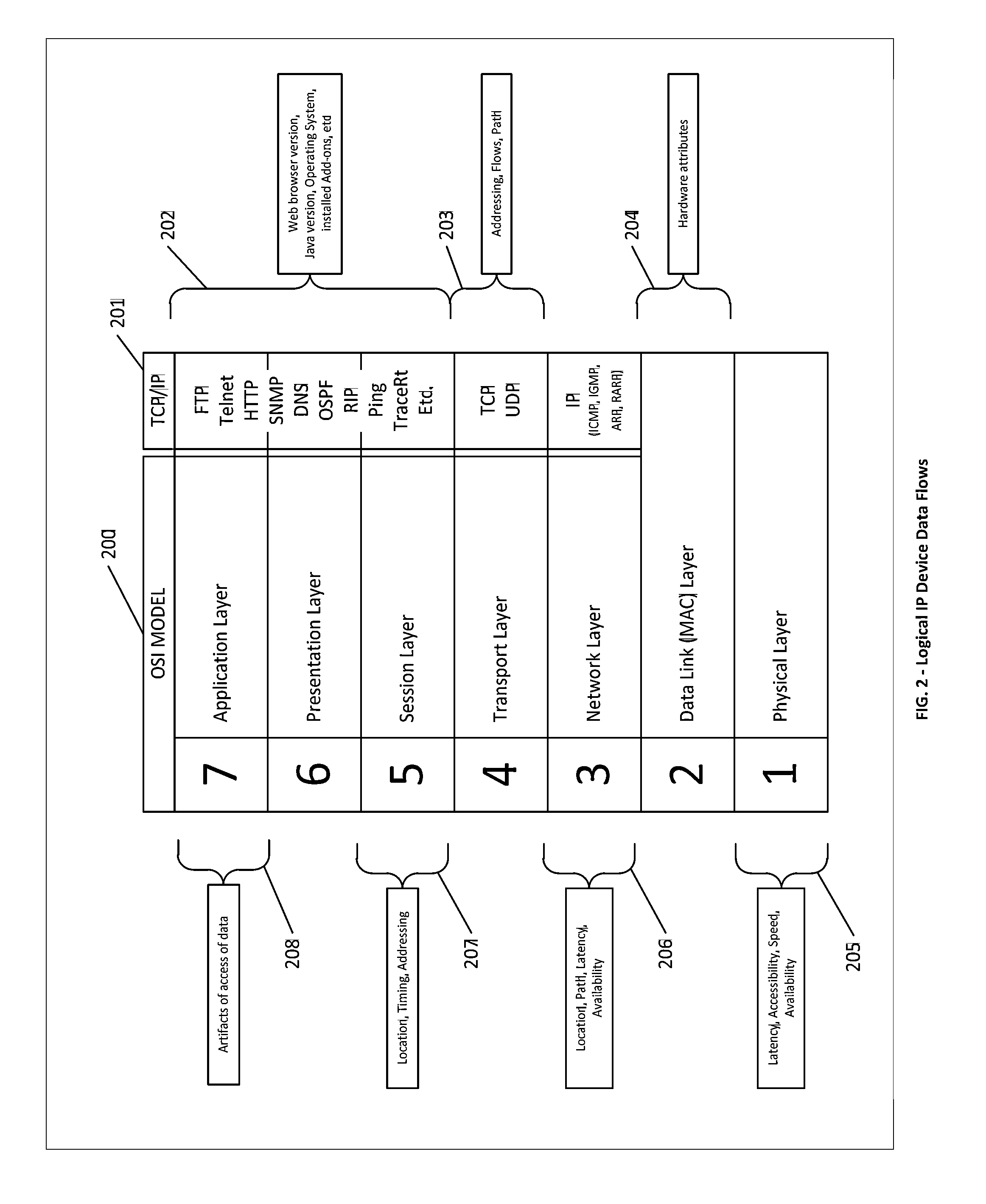
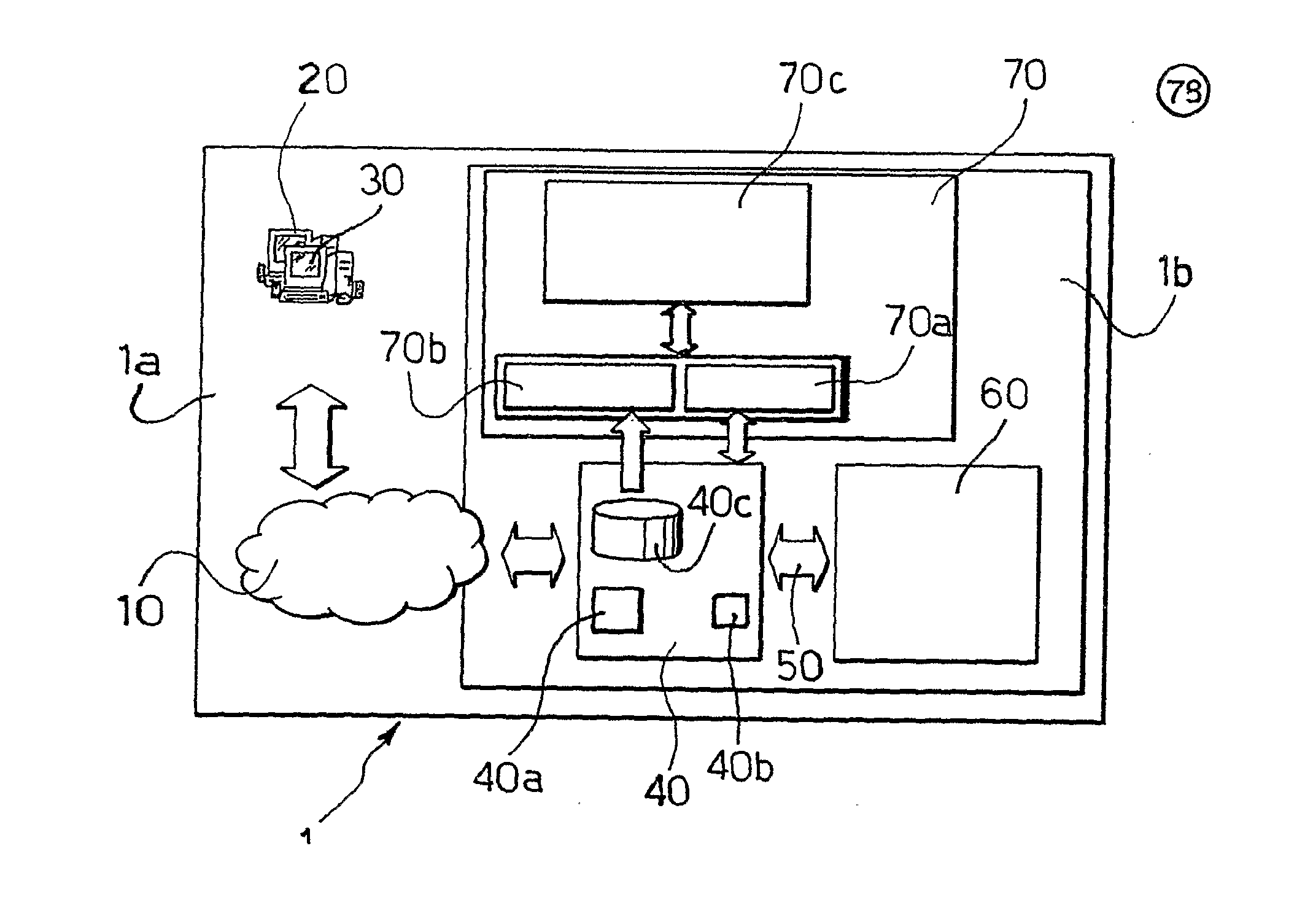
Systems, methods and devices for providing device authentication, mitigation and risk analysis in the internet and cloud
The present invention is a method to provide mechanisms and judgment to determine the ongoing veracity of “purported” devices (sometimes called spoofing) with such parameters as unique device ID, access history, paths taken and other environmental data (Device Authentication).This invention relies upon a previous invention “Reputation Database in the cloud and Internet”—the internet is comprised of collections of devices, data, applications and networks all dynamically exchanging information among users. We present a mechanism for real time observation, and putting or accessing those observations into a distributed virtual database for contextual evaluation and analysis of how the internet is being used or potentially subverted. This includes real time evaluation of DNS database changes, server logs, performance, path resolution, device logs, tip data and law enforcement data.This invention is particularly useful for helping detect and mitigate data compromises, networks, systems and other assets within the internet.
Owner:DONOVAN JOHN JOSEPH +2
Method And System For Monitoring Performance Of A Client-Server Architecture
InactiveUS20080104230A1Monitor performanceDigital computer detailsHardware monitoringServer logClient-side
An arrangement which jointly exploits an agent component installed in a server-side portion of client-server architecture for emulating requests of actual clients of the client-server architecture and measuring a server execution time indicative of a time elapsed between reception of an emulated end-user request at a server component and generation of a result of said emulated end-user request at said server component; information stored in a server log file about a hit end to end response time, i.e., the time elapsed between the instant in which the end-user sends a request to the server component and the instant in which result of the request reaches the end-user. From the server execution time and the hit response time, the delay due to the network connecting the server-side portion of the client-server architecture to a client-side portion may be determined. The network delay and the server execution time are then used for monitoring performance of the client-server architecture by distinguishing network related problems from server-related problems or even from client-related problems.
Owner:TELECOM ITALIA SPA
Internet website automatic classification method based on deep learning
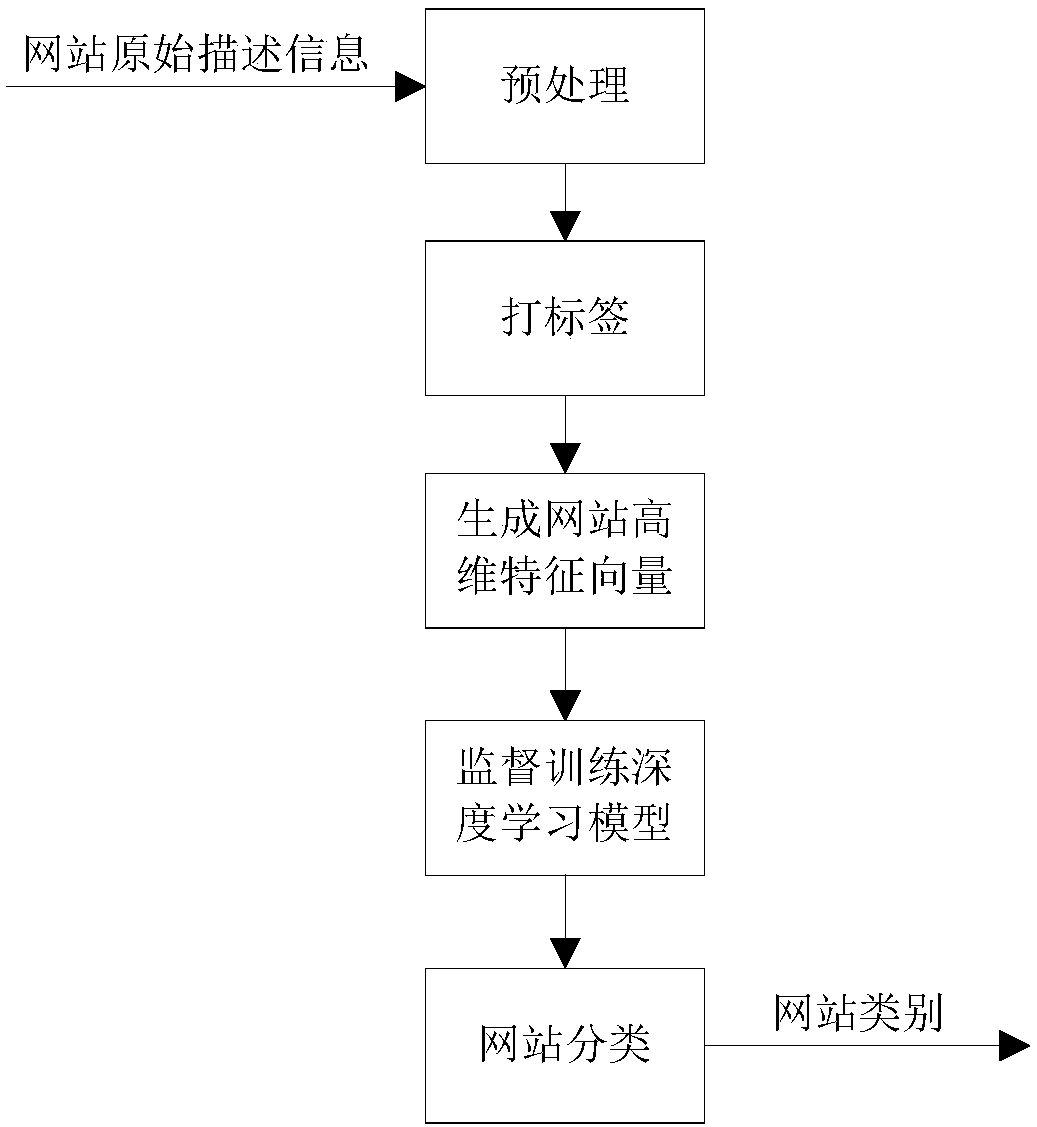
InactiveCN108364028AAvoid the problem of insufficient informationOvercome the problem of poor performance on high-dimensional large-sample multi-classification problemsCharacter and pattern recognitionWebsite content managementFeature vectorServer log
The present invention relates to an Internet website automatic classification method based on deep learning. The method comprises the steps of: collecting a lot of original description information ofan internet website according to a DNS server log as a website data set, and performing pre-processing and manual tagging; extracting high-dimensional feature vector representation, configured to input a deep learning model, of each website, increasing corresponding website category tags for each website, and converting the corresponding website category tags to type vectors; taking high-dimensional feature vectors as input of the deep learning model, taking the category vectors as output of the deep learning model, and employing an Adam gradient descent algorithm optimizer to supervise and train a recurrent neural network deep learning model based on the LSTM; increasing one layer of SoftMax regression behind the trained LSTM recurrent neural network deep learning model; and taking the website category corresponding to the dimension of the maximum probability value in the probability distribution vector as a website category, and comparing the output network category with the actual category of the website to obtain a classification accuracy of an Internet website.
Owner:INST OF INFORMATION ENG CAS
Electronic content distribution and exchange system
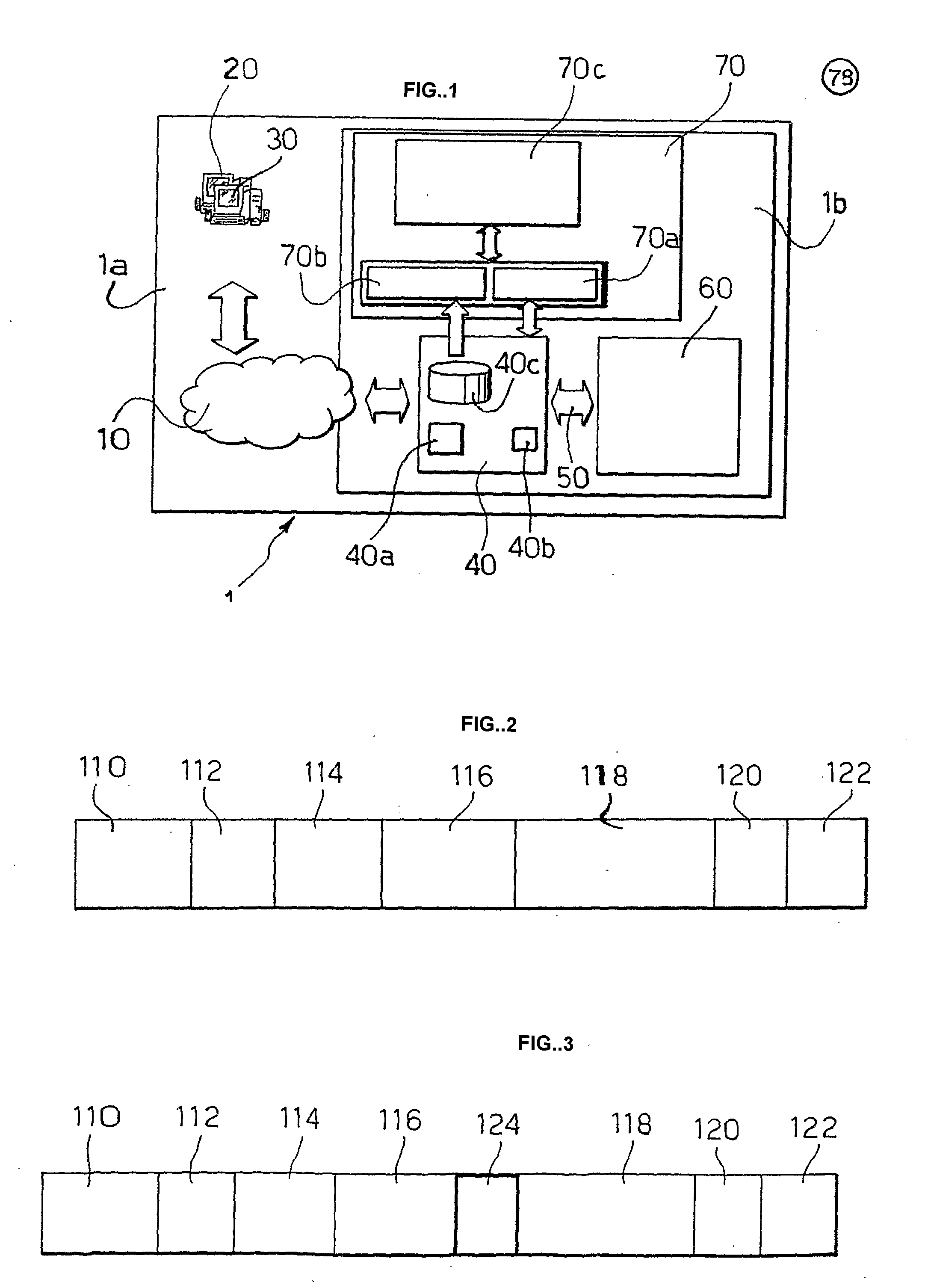
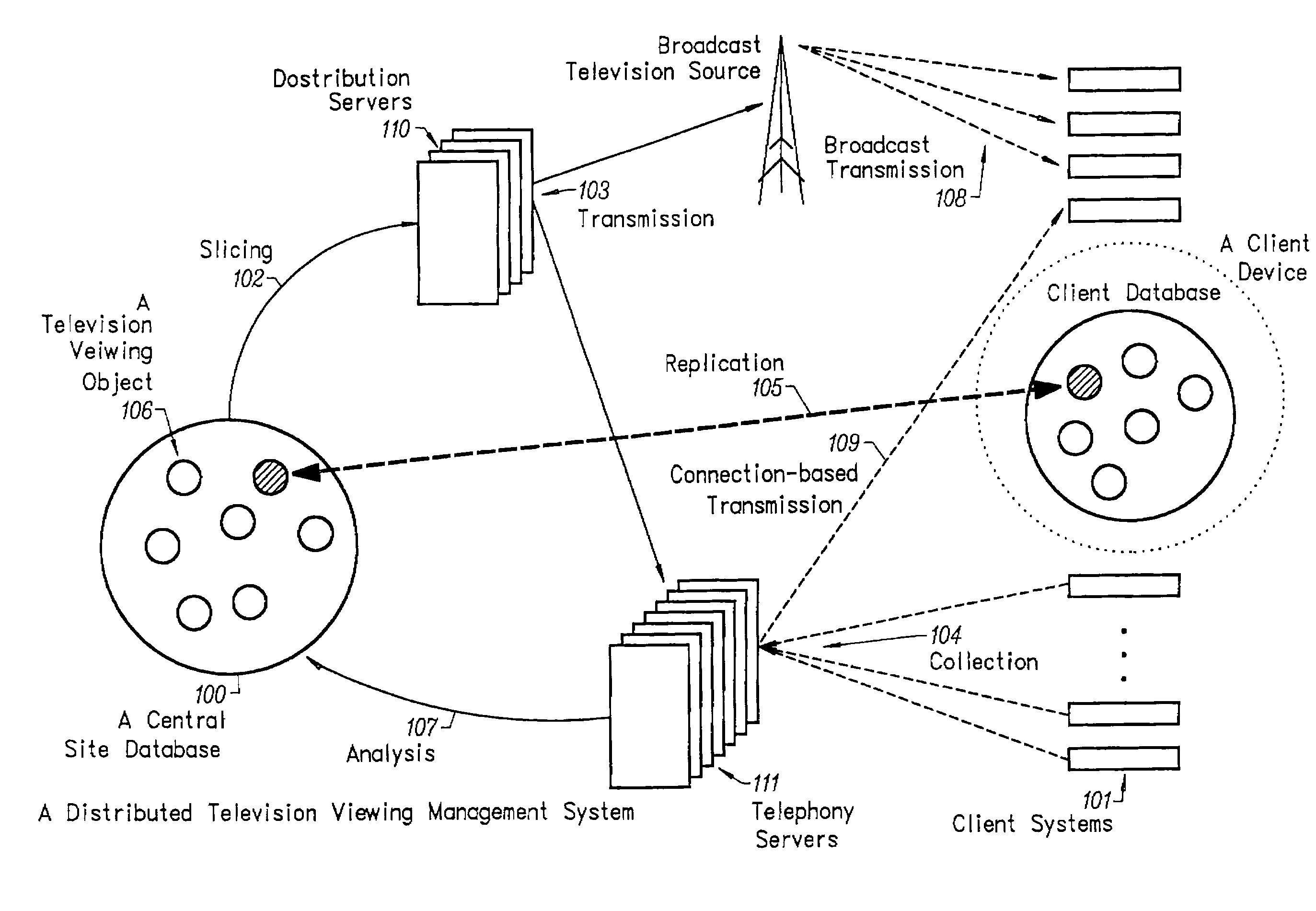
InactiveUS8131648B2Secure distributionTelevision system detailsAnalogue secracy/subscription systemsBroadcast channelsServer log
An electronic content distribution and exchange system provides authenticated, reliable content downloads and tracking capabilities. Content is distributed to users through the invention's architecture. A user registers for the purchase of content through an interface on a client system or via a Web site. The purchase is for a license to the content, not for the content itself. A list of available content is displayed to the user through the client system or the Web site. The invention's central servers log the purchase of the content into a license database. The electronic copy of the song may be already resident on the client system in a hidden area, carouseled in a protected broadcast channel, in the central database ready to be sent out in slices, or resident on a secure server on the Internet. The user accesses content through the client system's user interface where the user plays the content and controls its playback. The invention's service provides an exchange capability similar to stock trading whereby owners offer licenses to various electronic for sale. A seller places his license for a particular content up for sale on the central server where a buyer that is interested in the license places a bid. When a price is agreed to, the invention's central server transfers license ownership in the license database to the new owner.
Owner:TIVO SOLUTIONS INC
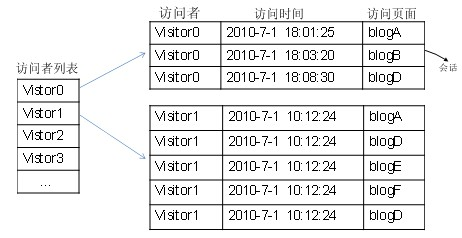
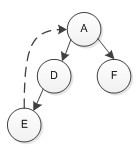
Blog friend recommendation method based on tree log pattern analysis
InactiveCN102122291AImprove visit rateImprove experienceSpecial data processing applicationsServer logData mining
The invention discloses a blog friend recommendation method based on tree log pattern analysis. An offline digging method is adopted, a server log is analyzed to extract the access record of a visitor on a blog page; an access log tree which takes a blog to be recommended as a root is further constructed by the technologies of grouping, sorting, loop-back removal and the like; the constructed access log tree is frequently dug to find a frequent subtree conforming to a preset requirement; nodes in the frequent subtree serves as candidate blog friends; a recommendation degree is calculated according to the set formula; and friends with highest scores are recommended. An algorithm in the method is different from the traditional algorithm based on frequent item digging or frequent sequence digging; a frequent tree structure digging method is adopted for fully digging aiming at the specific parallel link relationship and indirect access characteristic of the blogosphere; and potential access contact among blogs is extracted and is recommended to an access user, thereby improving user experience. The blog friend recommendation method is an efficient and practical blog recommendation method.
Owner:ZHEJIANG UNIV
Method and system for obtaining server logs
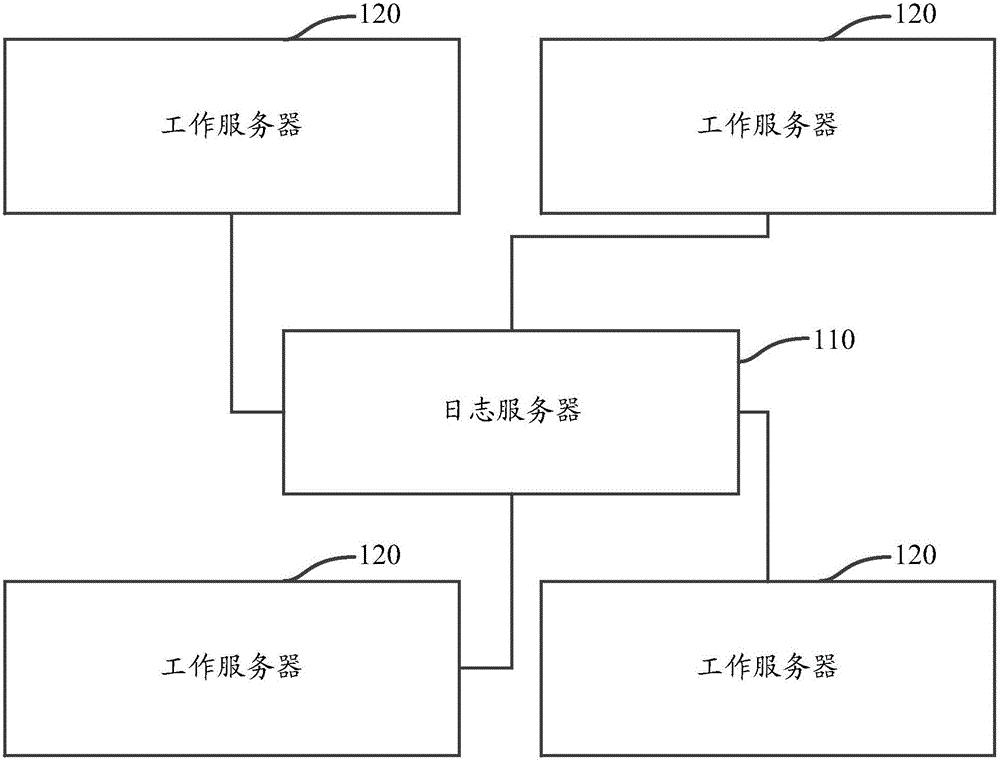
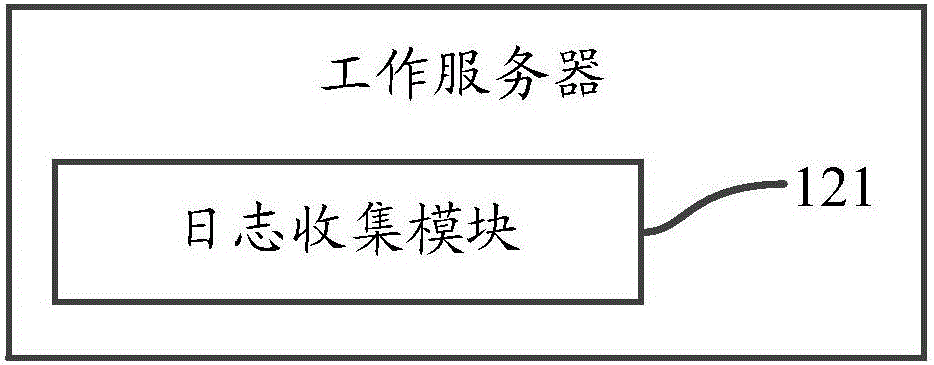
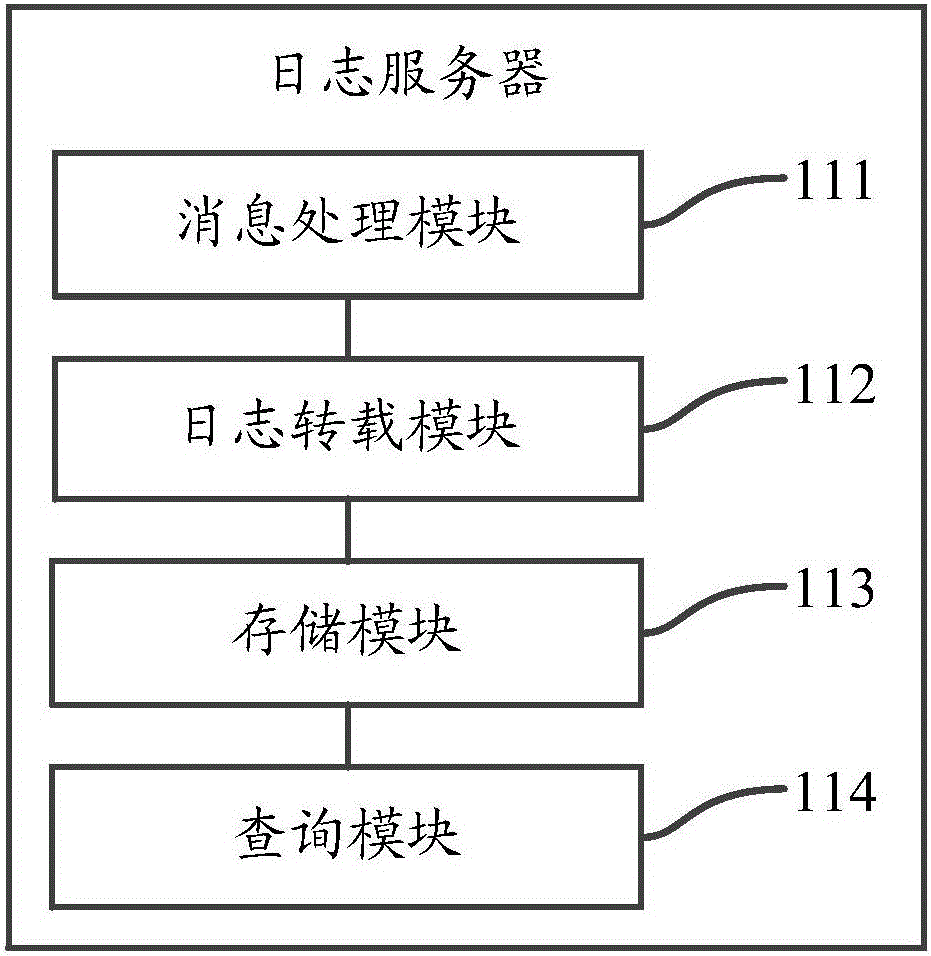
InactiveCN106130782ASimple processImprove the efficiency of mistakesData switching networksServer logSoftware bug
The invention discloses a method and a system for obtaining server logs. The system comprises at least one log server and multiple working servers, wherein the working servers are used for sending generated server logs to the log server; and the log server is used for receiving the server logs from the working servers, storing the server logs locally, and when receiving a query request from a client, obtaining corresponding server logs locally and returning the obtained server logs to the client. According to the system, by collecting the server logs on the multiple working servers, intensively storing the collected server logs to one log server, and providing a query module for a user to view the server logs, the optimization on a procedure of querying the server logs is realized, and the efficiency of troubleshooting server program error is improved.
Owner:NUBIA TECHNOLOGY CO LTD
Information individualized recommendation method based on Web log data
ActiveCN103678652AAccurate recommendationPersonalized recommendationHardware monitoringSpecial data processing applicationsInformatizationPersonalization
The invention discloses an information individualized recommendation method based on Web log data, and belongs to the technical field of electronic information. The method is used for an information mode of a server plus a broadband network plus a multimedia thin client side. The method includes the steps that users have access to internet sources through the multimedia thin client side, and theserver records the behaviors of the users into server log files; clean, regular and accurate data sources are extracted through analysis and preprocessing of data of the Web log files in the server; a user interest matrix is built through a collaborative filtering technology, similarity between the users is calculated, and the users with large similarity are selected as similar users; a recommendation resource pool is built according to hobbies and interests of the similar users; the server selects and recommends pages of which the recommendation value is larger than the threshold value in the recommendation resource pool to the users. The method has the advantages that the data in the Web log files are preprocessed to acquire the clean and regular data sources, and accurate and individualized information recommendation is provided for the users by the cooperation of the hobbies and the interests of the similar users.
Owner:SHANDONG UNIV
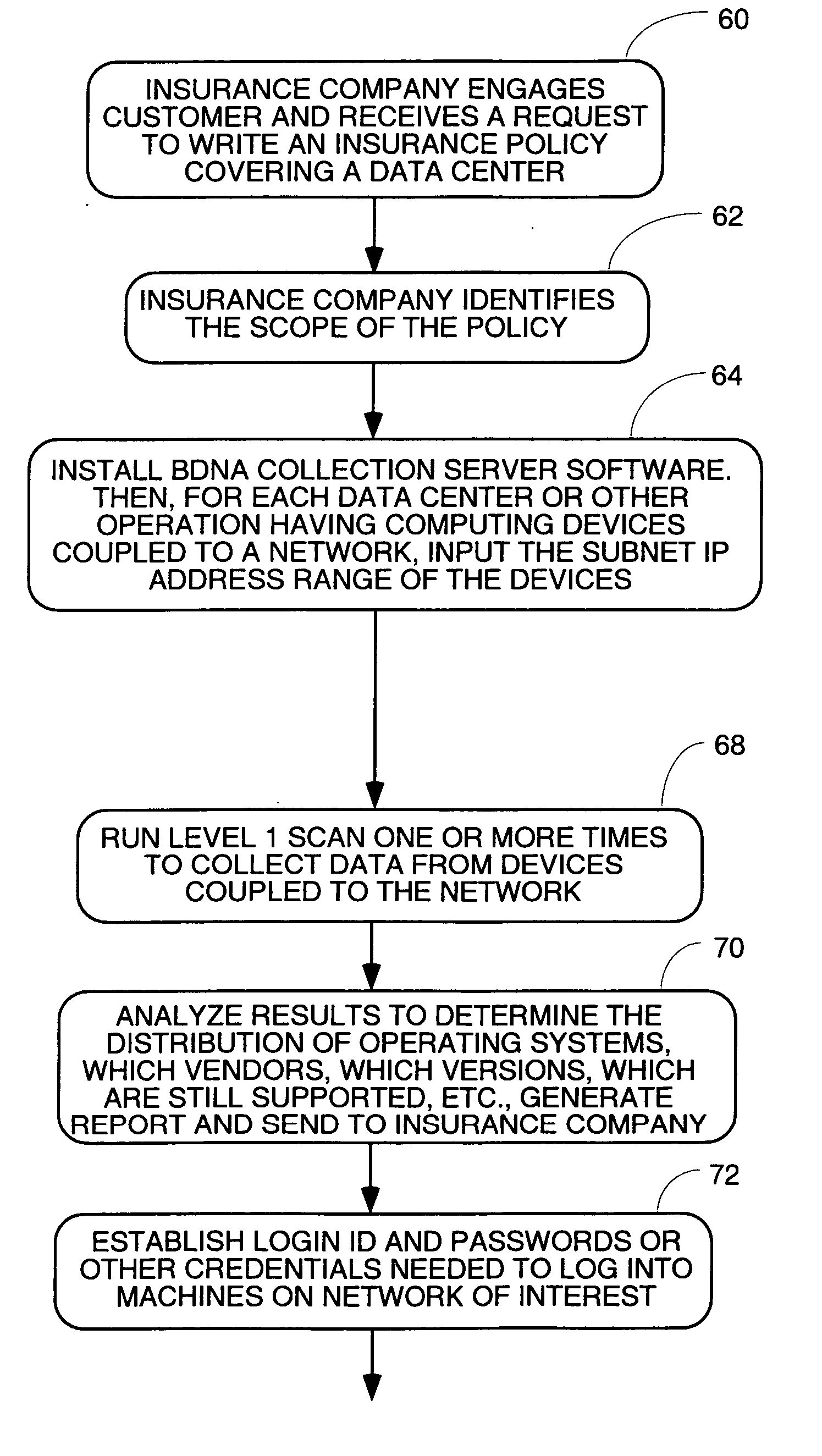
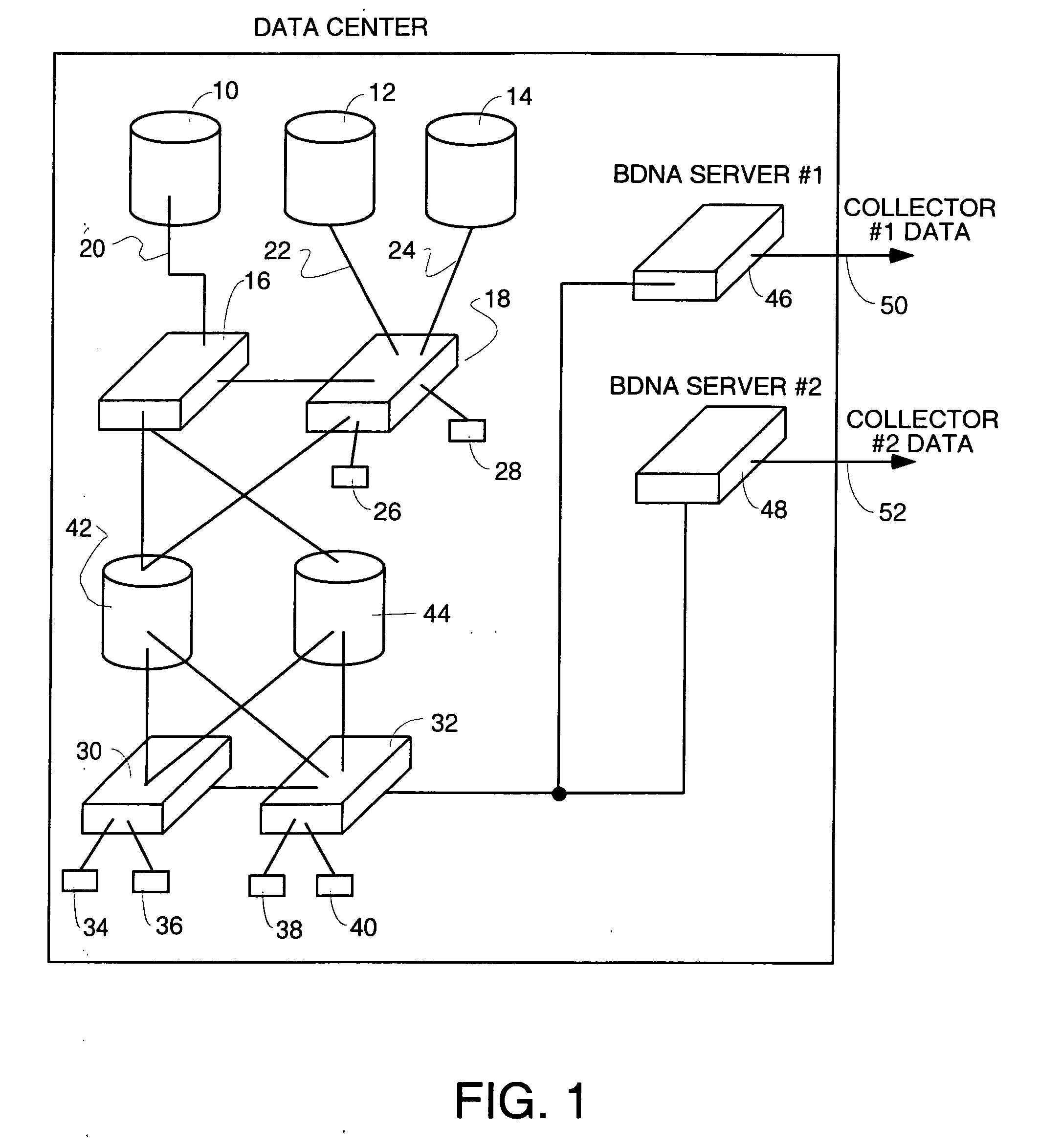
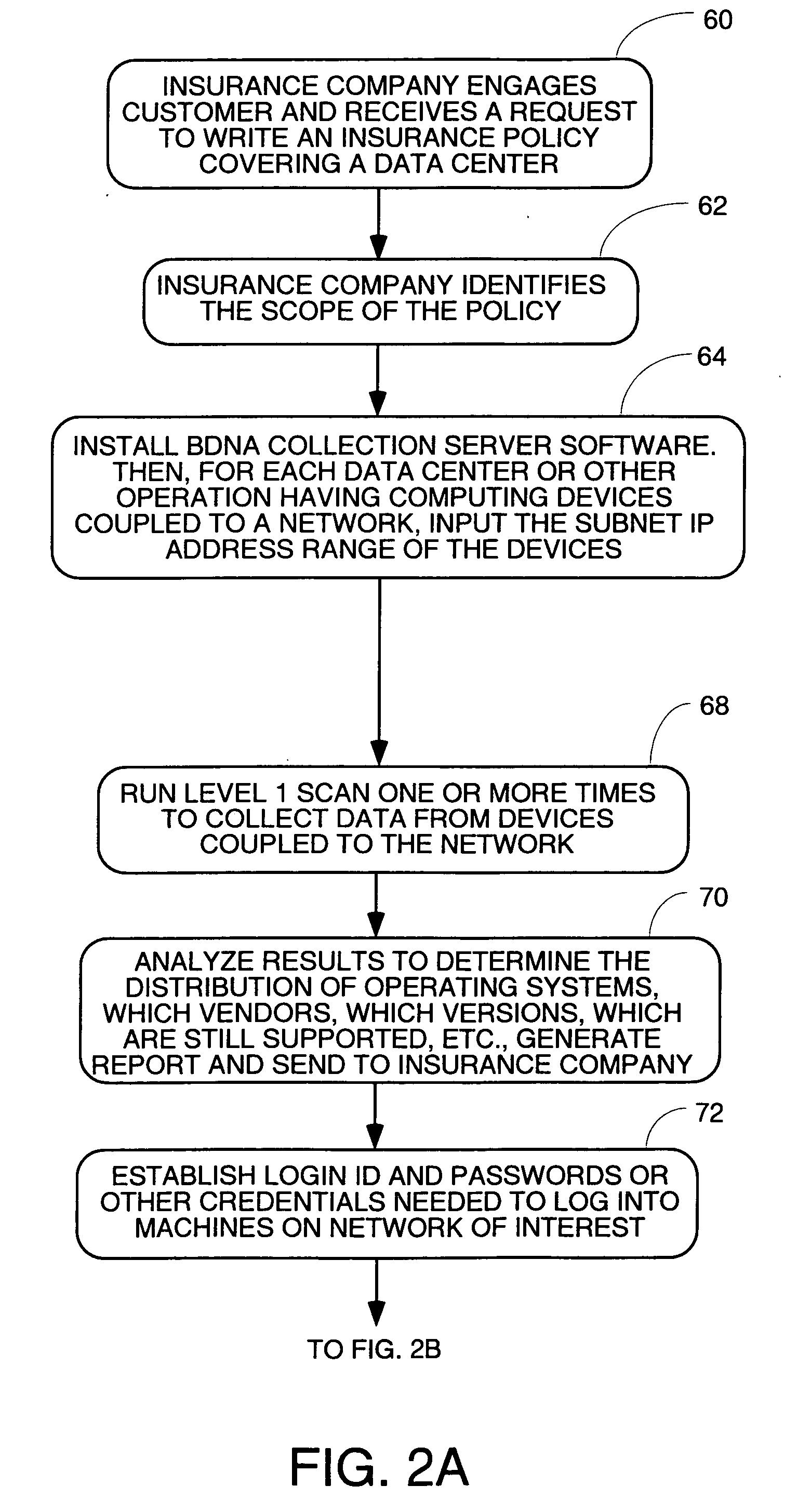
Method and apparatus for collecting inventory information for insurance purposes
A method and appartus for automatically gathering data about assets of a data center for use in assessing risks in writing insurance policies. The method uses collection servers coupled to the network or networks of the data center. The collection servers are informed of the IP address range and ping all addresses to find addresses at which active machines reside. Then a plurality of protocols are executed to send packets to the active IP addresses in accordance with a plurality of different protocols in an attempt to elicit meaningful responses. If a meaningful packet arrives back from a machine, the protocols try to decipher it to determine what protocols the machine understands. Once the protocol(s) the machine understands are known, packets are sent to invoke function calls of known APIs of that protcol to extract information about the machine. If more information is needed, login ID and passwords are obtained for the machines of interest, and the collection servers log into the machine of interest, and invoke function calls of the known APIs of the operating system of the machine to extract more data about the machine. The gathered data is analyzed and sent to the insurance company.
Owner:BNDENA
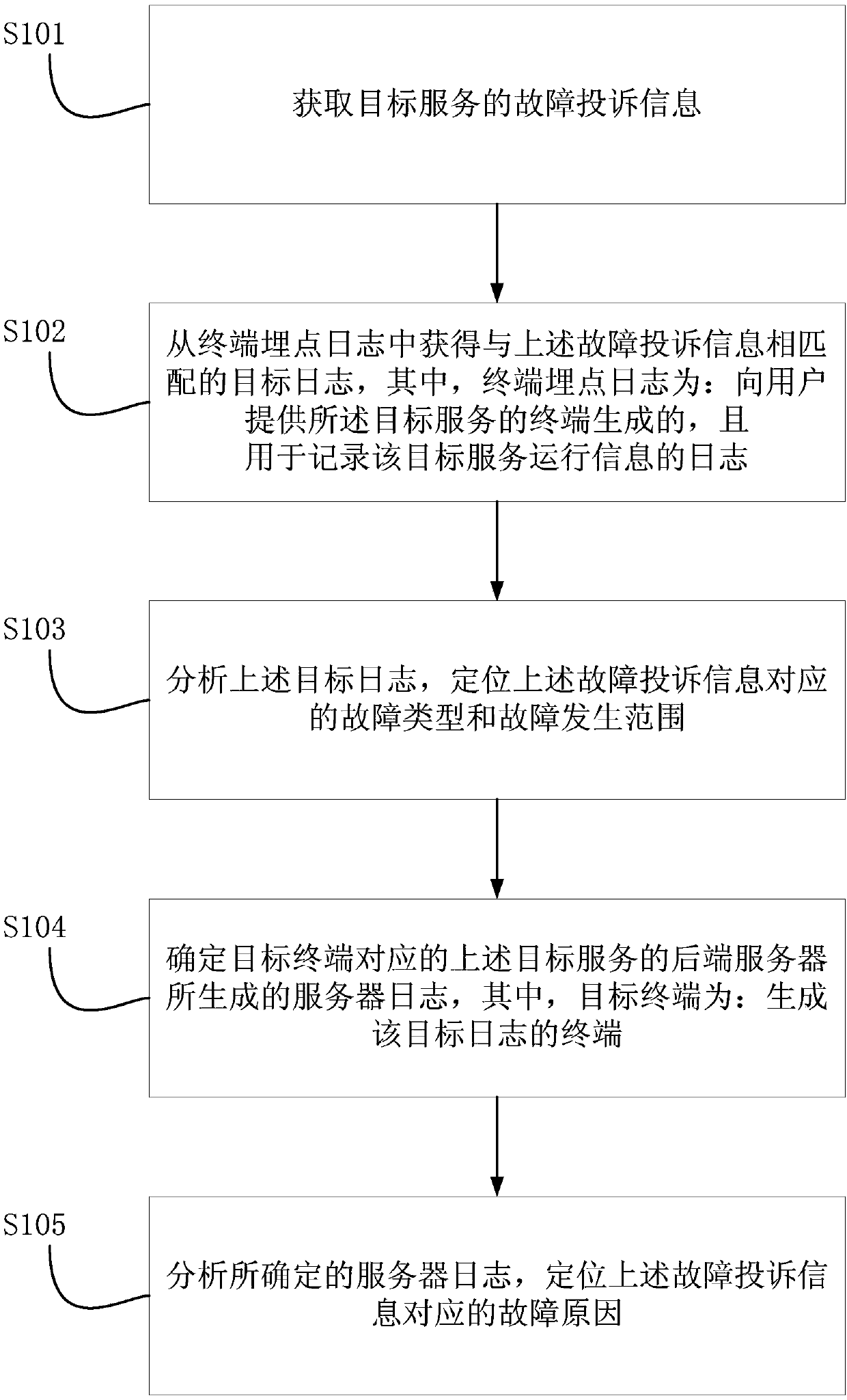
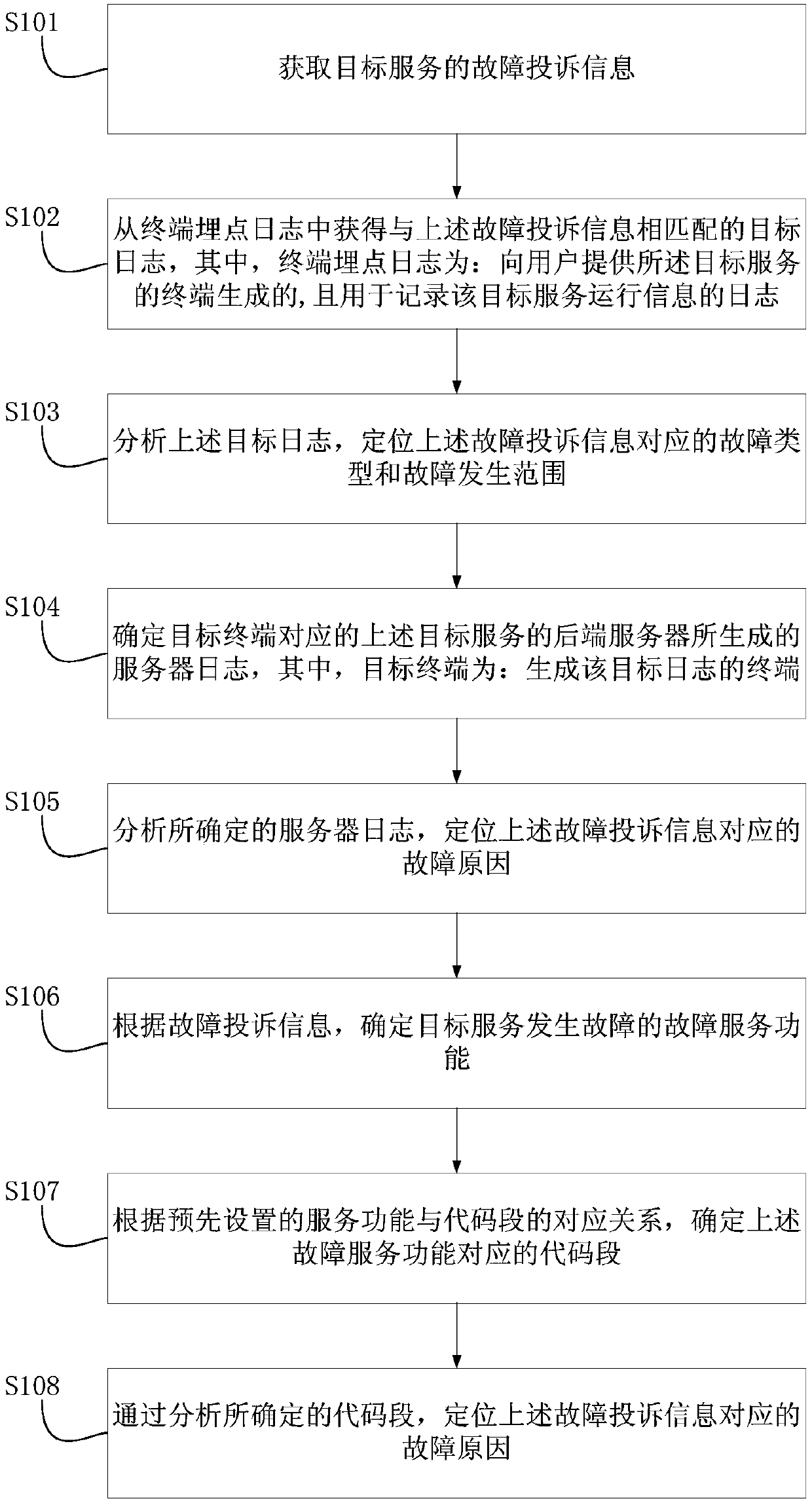
Failure positioning method and device
InactiveCN107872353AReduce the impactImprove experienceData switching networksServer logThe Internet
The embodiment of the invention provides a failure positioning method and a failure positioning device, and relates to the technical field of internet. The failure positioning method comprises the following steps: acquiring failure complaining information of target service; acquiring a target log matched with the failure complaining information from a terminal burying point log, wherein the terminal burying point log is generated by a terminal for providing the target service to a user and is used for recording the operating information of the target service; analyzing the target log and positioning the failure type and the failure occurrence range corresponding to the failure complaining information; determining a server log generated by a back-end server of the target service corresponding to the target terminal, wherein the target terminal is the terminal which generates the target log; and analyzing the determined server log and positioning the failure reason corresponding to the failure complaining information. Compared with the prior art, the scheme provided by the embodiment of the invention has the following advantages: the hidden danger that the failure is difficult to position rapidly can be eliminated, the duration of the influence on users by the failure can be reduced and the user experience can be improved.
Owner:BEIJING QIYI CENTURY SCI & TECH CO LTD
Server logging module
InactiveUS20130290441A1Error detection/correctionMultiple digital computer combinationsWorld Wide WebServer log
Techniques are described herein for logging messages at a server. In some embodiments, a plurality of client request messages from one or more client machines may be received at a server logging module in a server. The received client request messages may be parsed to extract one or more request headers and an request body from each received client request message. Request body characterization information may be created based on the parsed request body. Message information may be stored in a server log in accordance with a standard log format. The message information may include the one or more request headers and the request body characterization information associated with each received client request message.
Owner:MOBITV
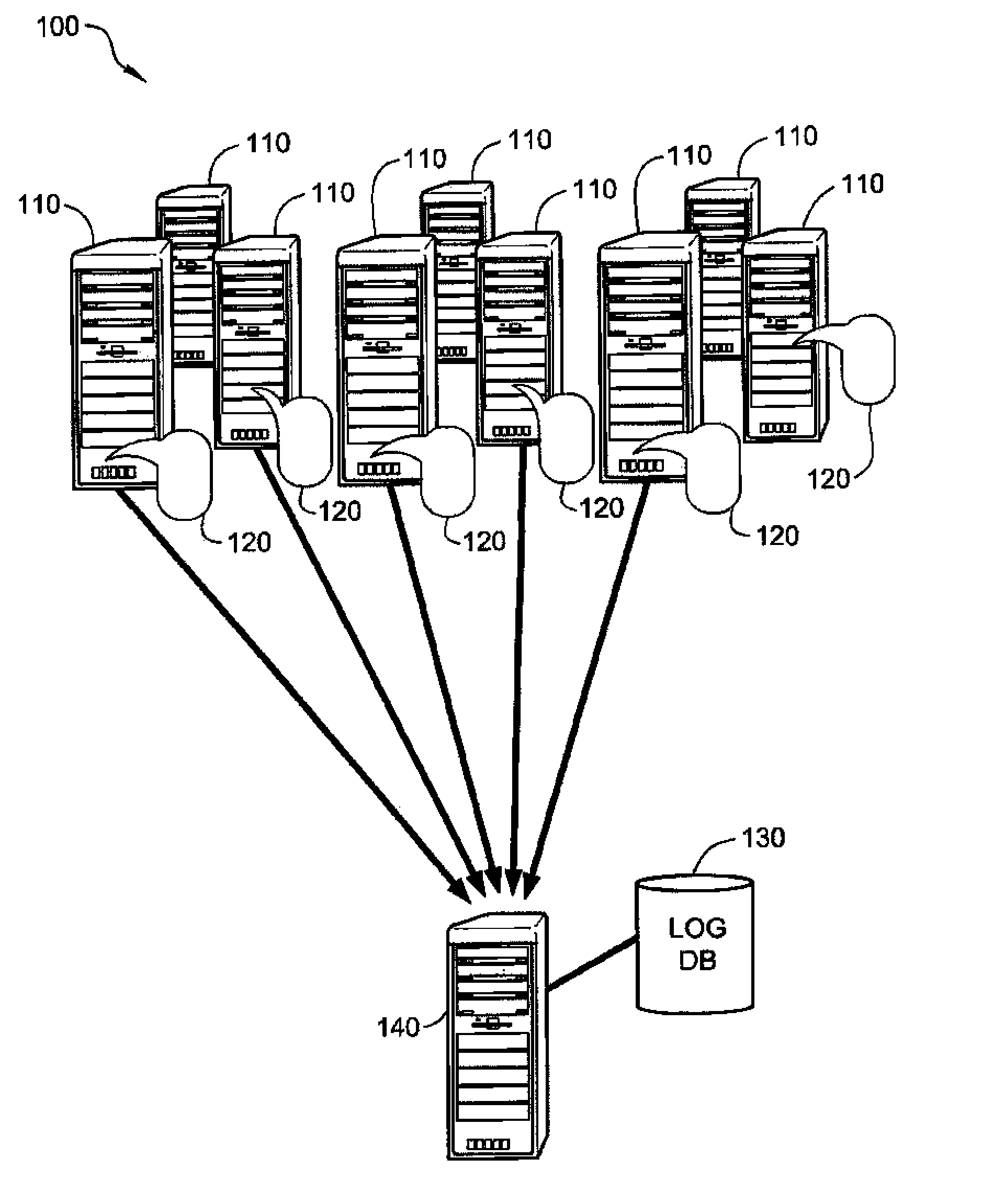
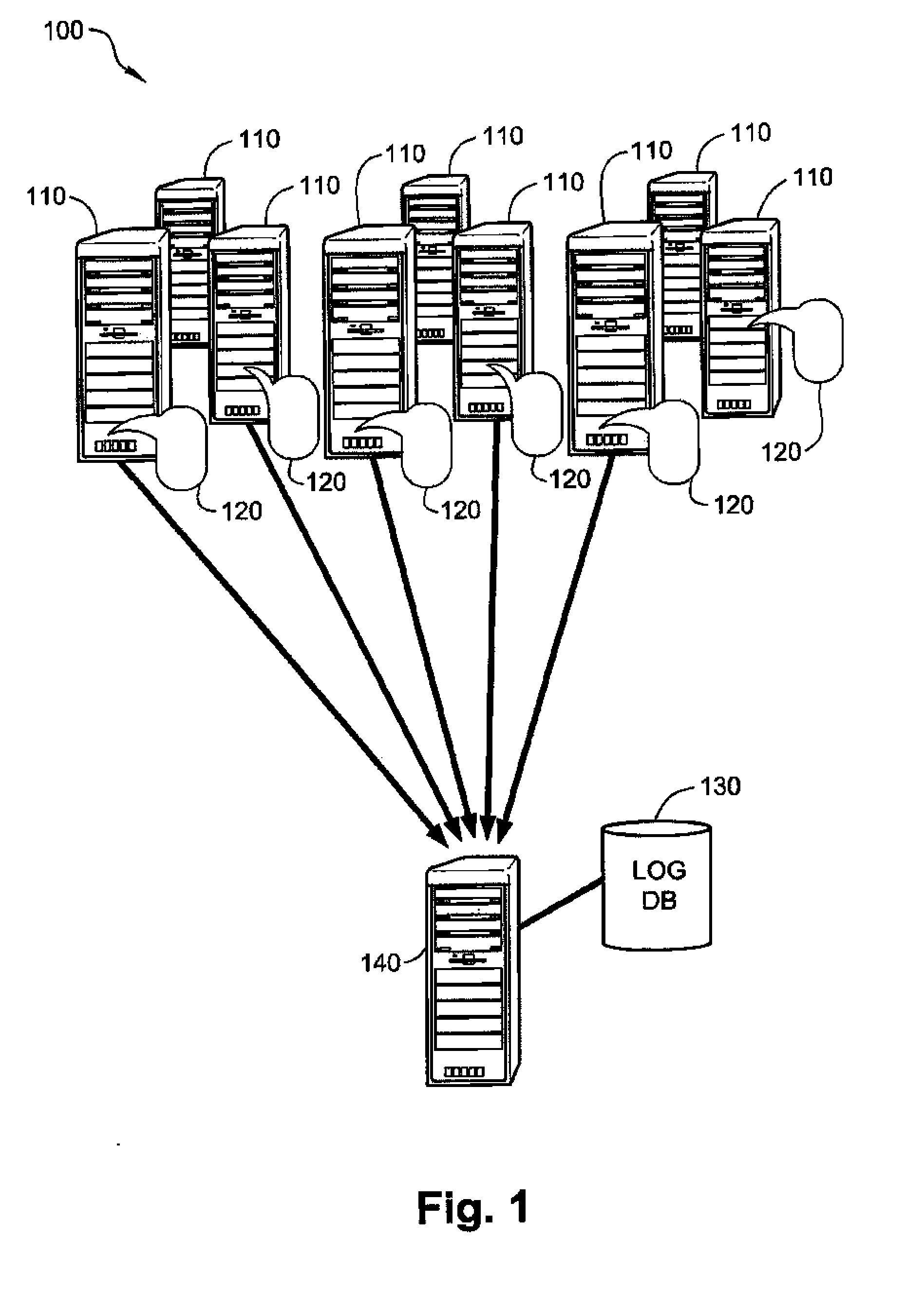
System and Method for Collection and Analysis of Server Log Files
InactiveUS20090013007A1Improve scalabilityTransmissionSpecial data processing applicationsServer logApplication software
A method of handling log files in a network with multiple servers, including, installing an agent application on each server in the network, collecting log files on each server by the agent application, defining a uniform format for providing the log files to a central server, transforming the log files to the defined uniform format, transmitting the transformed log files to a central server, storing the log files in an archive by the central server, analyzing the log files received by the central server, producing reports responsive to the analysis of the log files.
Owner:INTERWISE CO LTD
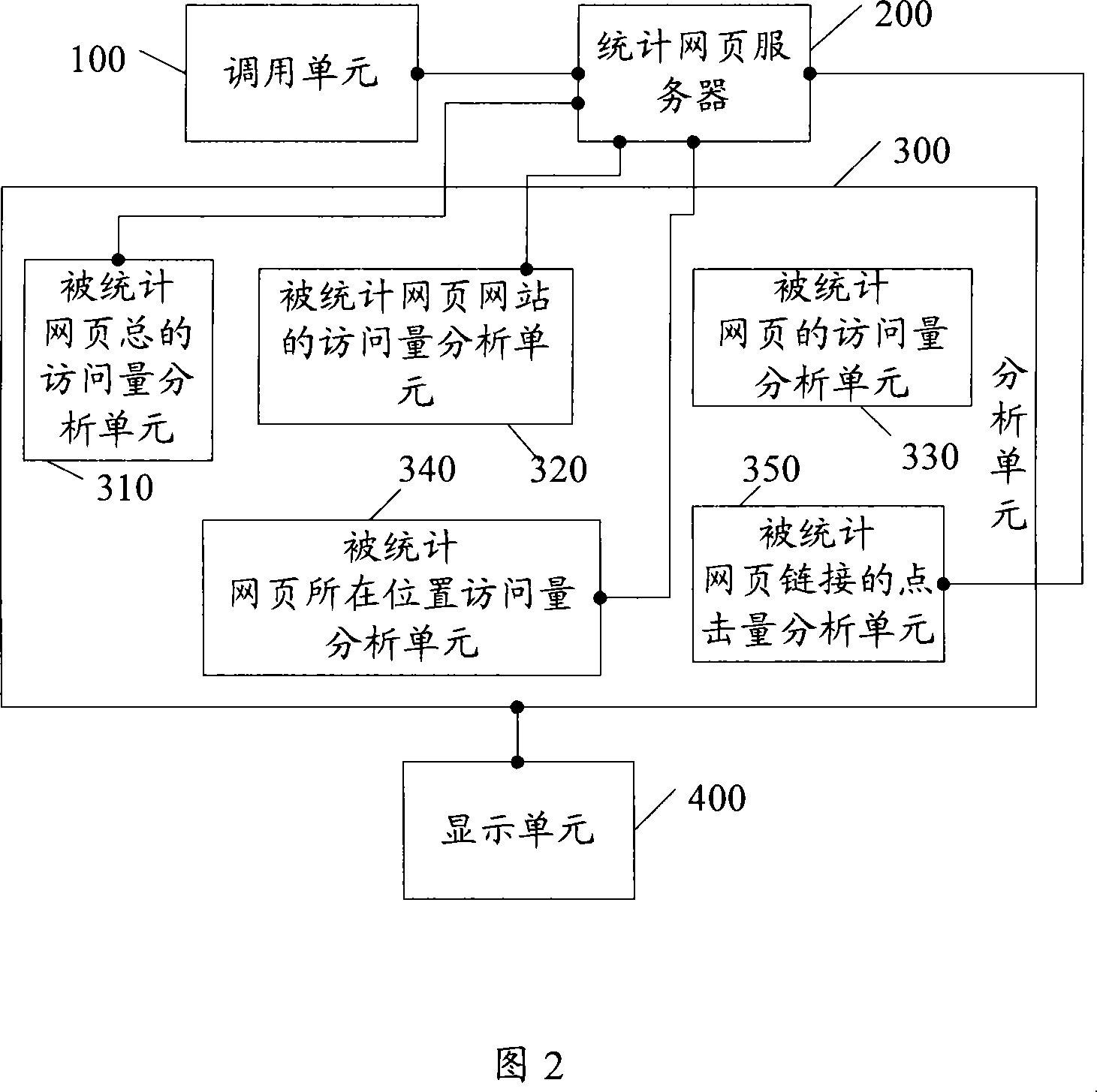
Method and system of statistical web page access data
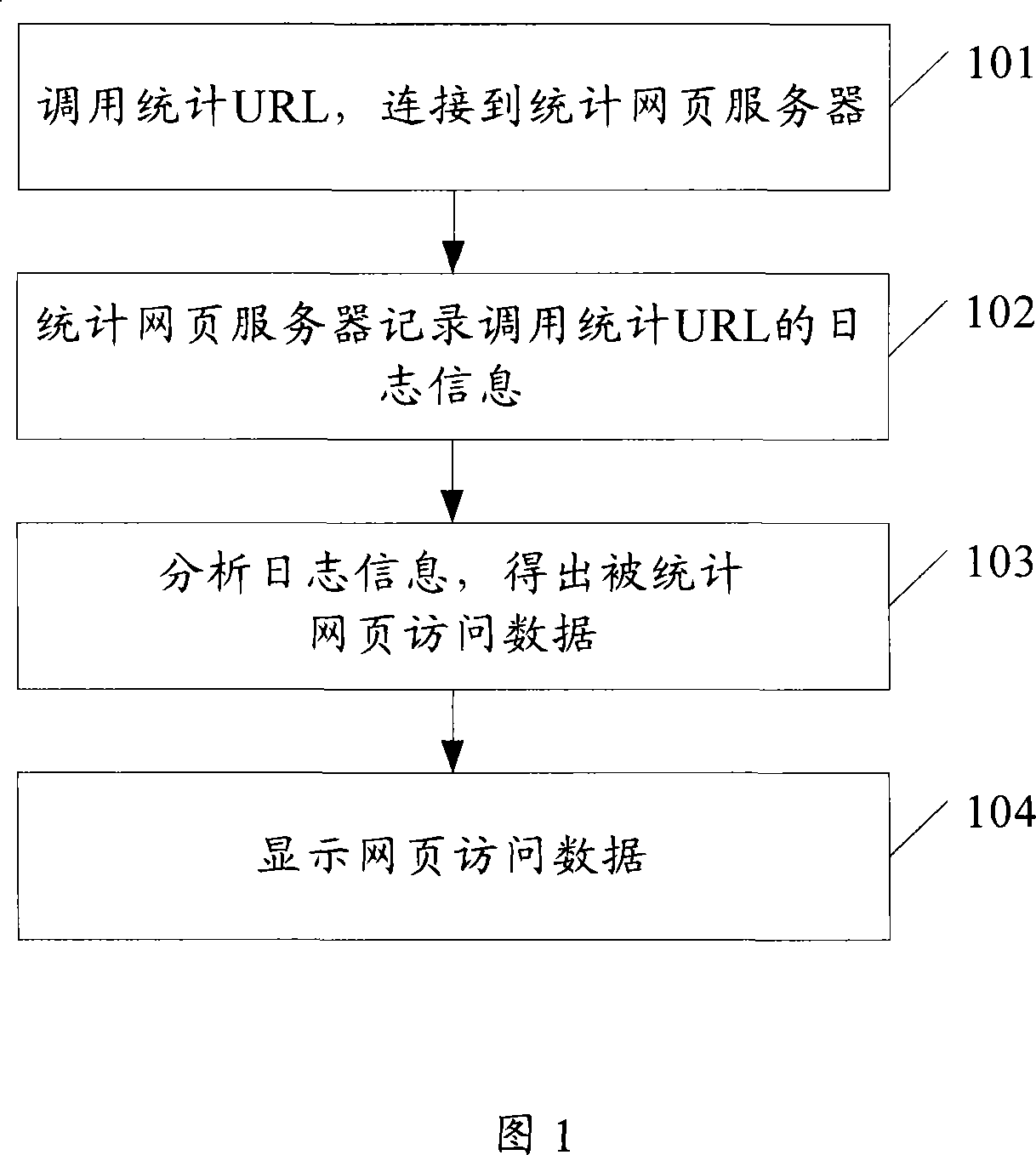
ActiveCN101163045ASave resourcesShorten the timeData switching networksSpecial data processing applicationsServer logUniform resource locator
The invention discloses a method and a system for statistics of web access data. The method of the invention comprises that when a statistical web is clicked by consumers, a uniform resource locator URL is transferred and counted and is connected with a statistical web server. The statistical web server records the log information of the transferred and counted URL. The log information is analyzed so that the access data of the statistical web is worked out. The invention has the following effects: the invention is capable of realizing the accurate statistics of web access data; the log of the server is used and the resource of the server is saved, which facilitates consumers to visit object web.
Owner:BEIJING KINGSOFT OFFICE SOFTWARE INC
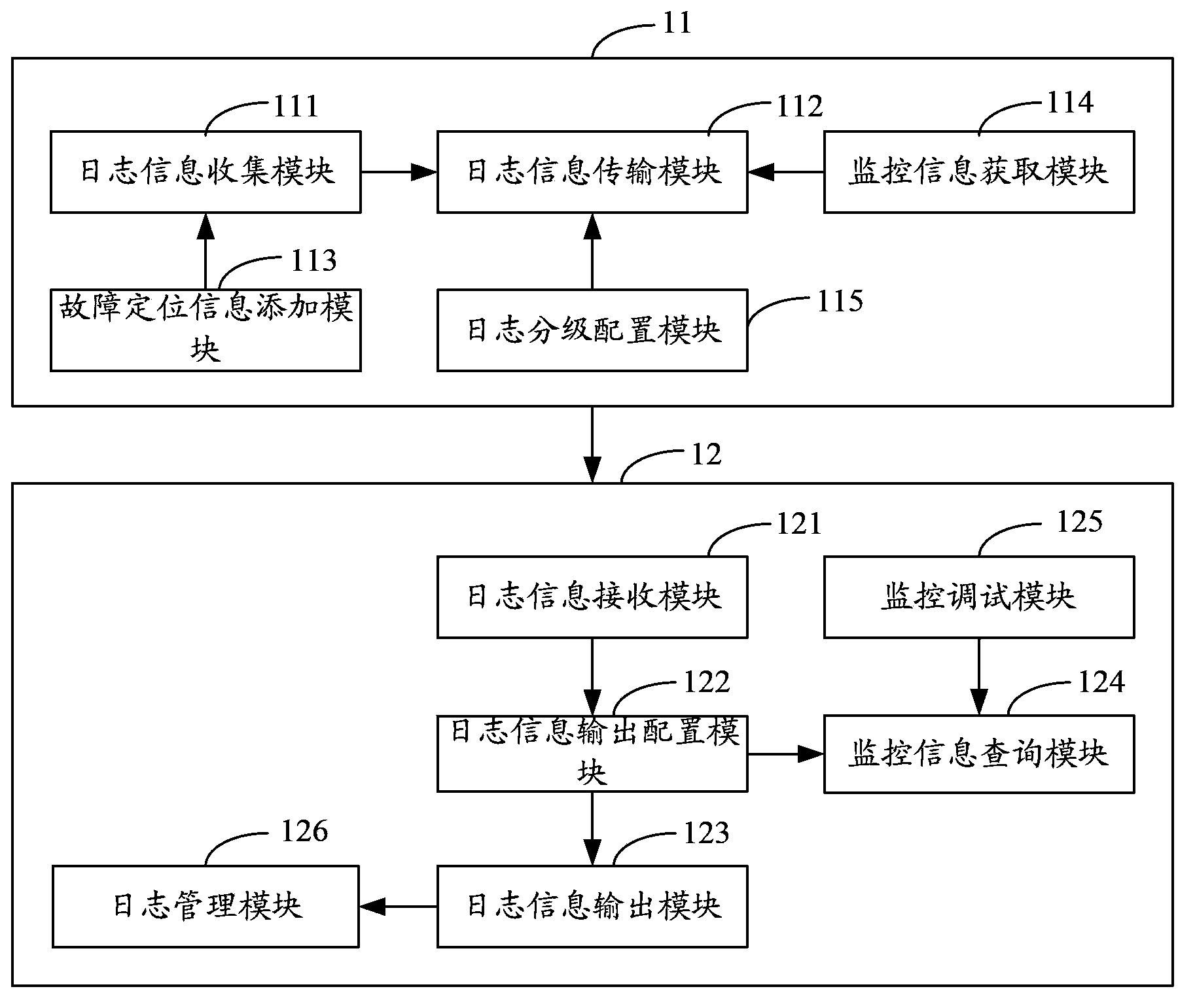
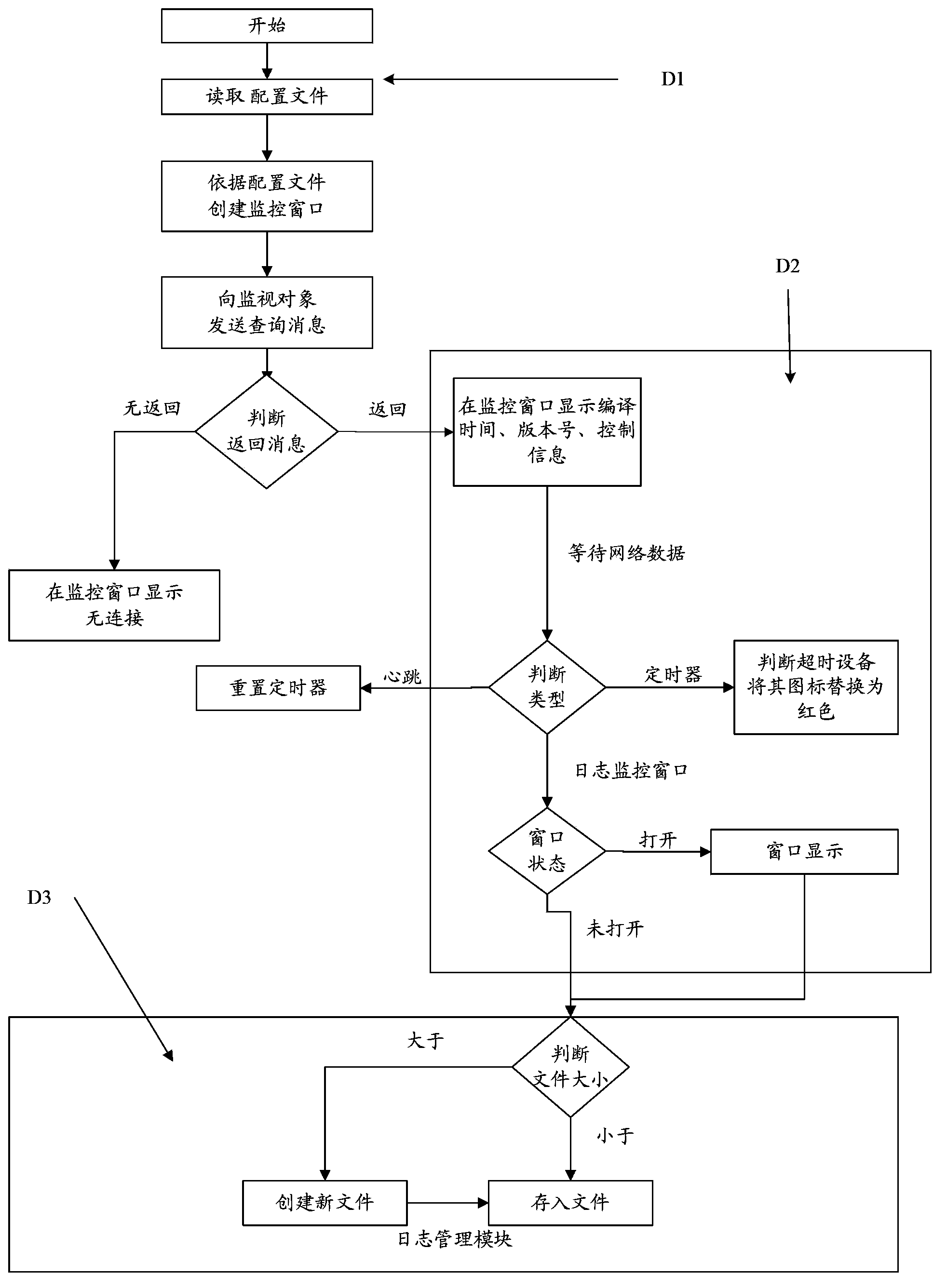
Embedded system development log system
InactiveCN103778049AMultiplayer supportSupports modularityHardware monitoringData switching networksServer logSoftware development
The invention is applicable to the field of embedded systems and provides an embedded system development log system. The embedded system development log system comprises a device log unit embedded in device application software, and a server log unit arranged in a server and communicated with the device log unit, wherein the device log unit is used for generating the log information of the device log application software and transmitting the log information to the server log unit in real time; the server log unit is used for receiving and storing the log information transmitted by the device log unit and outputting the log information according to configuration files. The embedded system development log system can meet the requirements on real-time checking and storing of the log information during the developing and debugging process of an embedded system, and meanwhile, a single developer can develop and debug multiple embedded devices in the working station, so that the embedded system development log system can well support multi-individual and modularized software development.
Owner:BEIJING SANXI ELECTRONICS TECH DEV
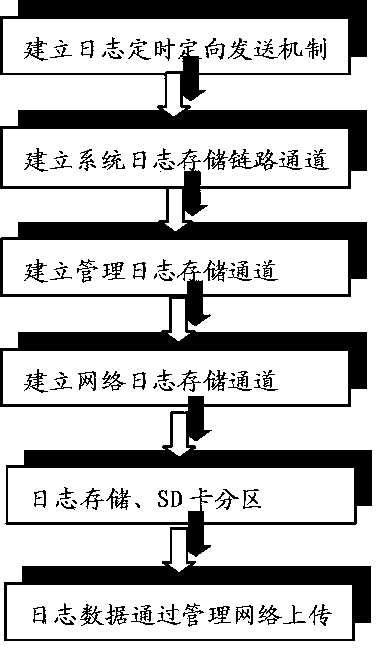
Server log information acquisition method
InactiveCN104268068AAvoid reading and writing conflictsEfficient designInput/output to record carriersHardware monitoringServer logLog management
The invention discloses a server log information acquisition method and relates to the computer communication field. The server log information acquisition method includes that adding a regular and directed key log information sending mechanism to a BIOS, wherein the BIOS continuously sends the key log information from the system starting to the stable system running; building a log information acquisition control board, and connecting the control board with a south bridge of the main board to build a system log storage link channel; connecting the log information acquisition control board with an on-board BMC chip and network chip through an I2C bus to build a log and network log management storage channel; dividing a medium storage SD card on the log information acquisition control board into three zones, connecting the SD card port with an on-board BMC management control system, and transmitting the log information in each zone to a user through management network.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
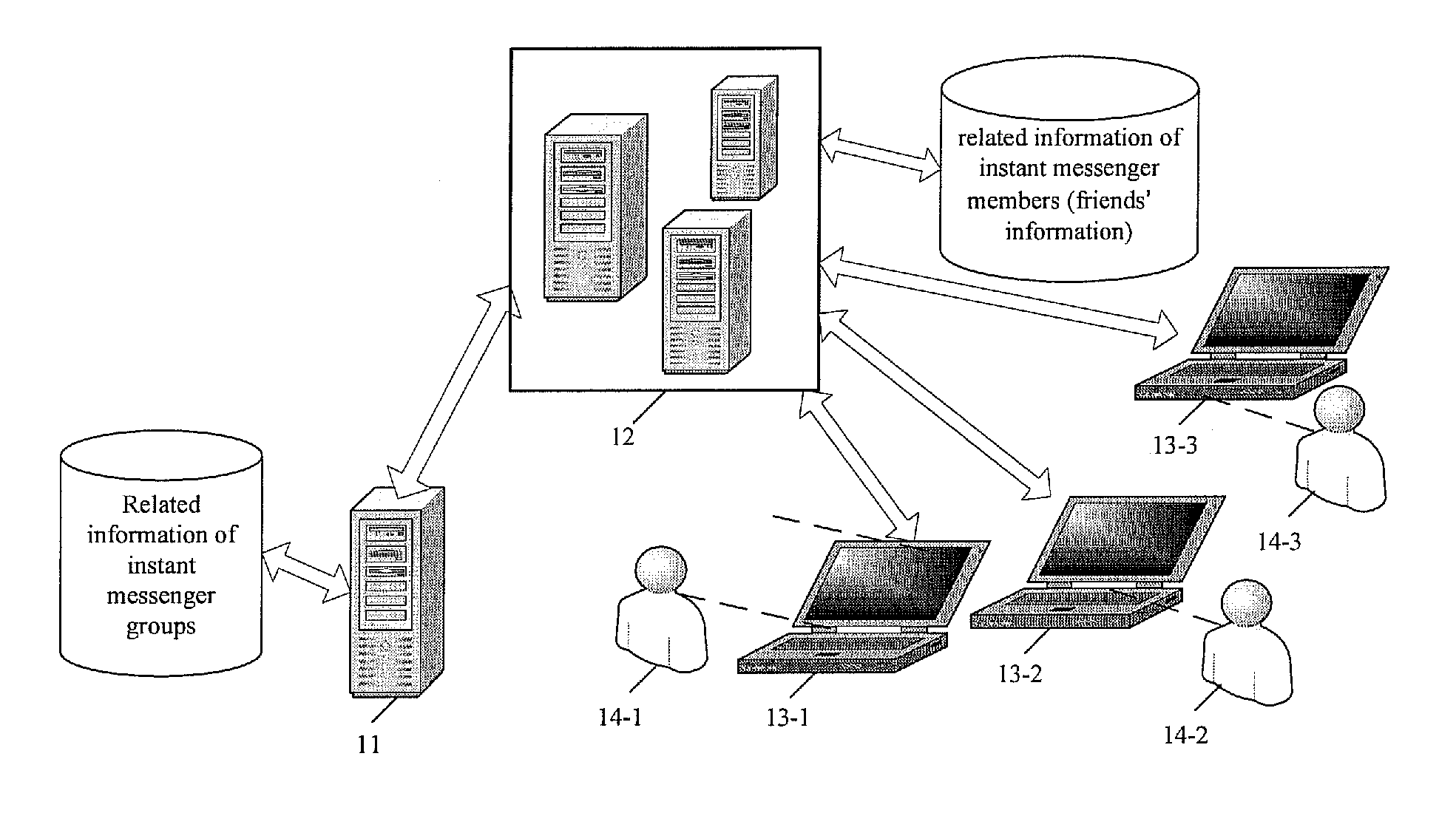
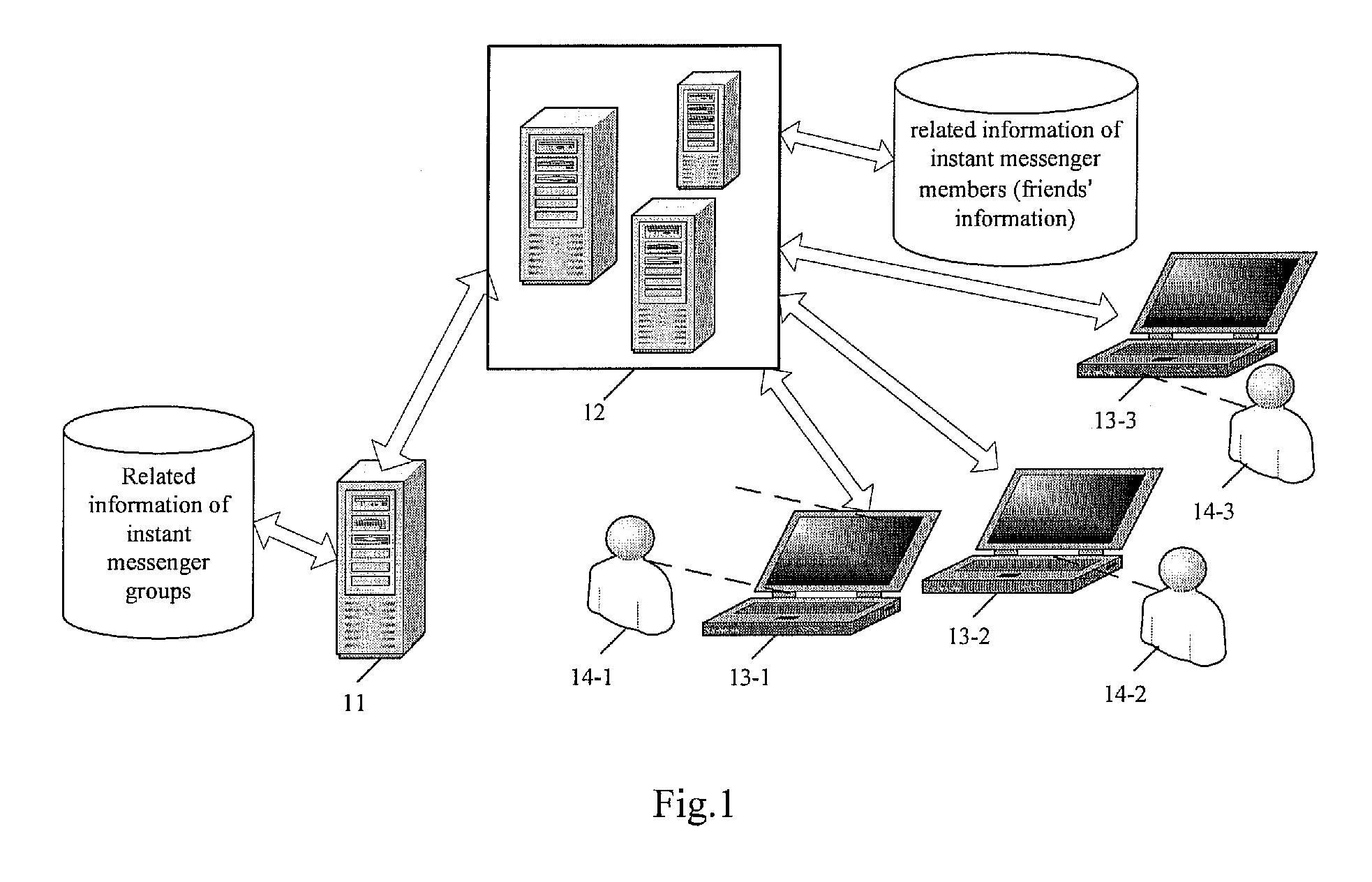
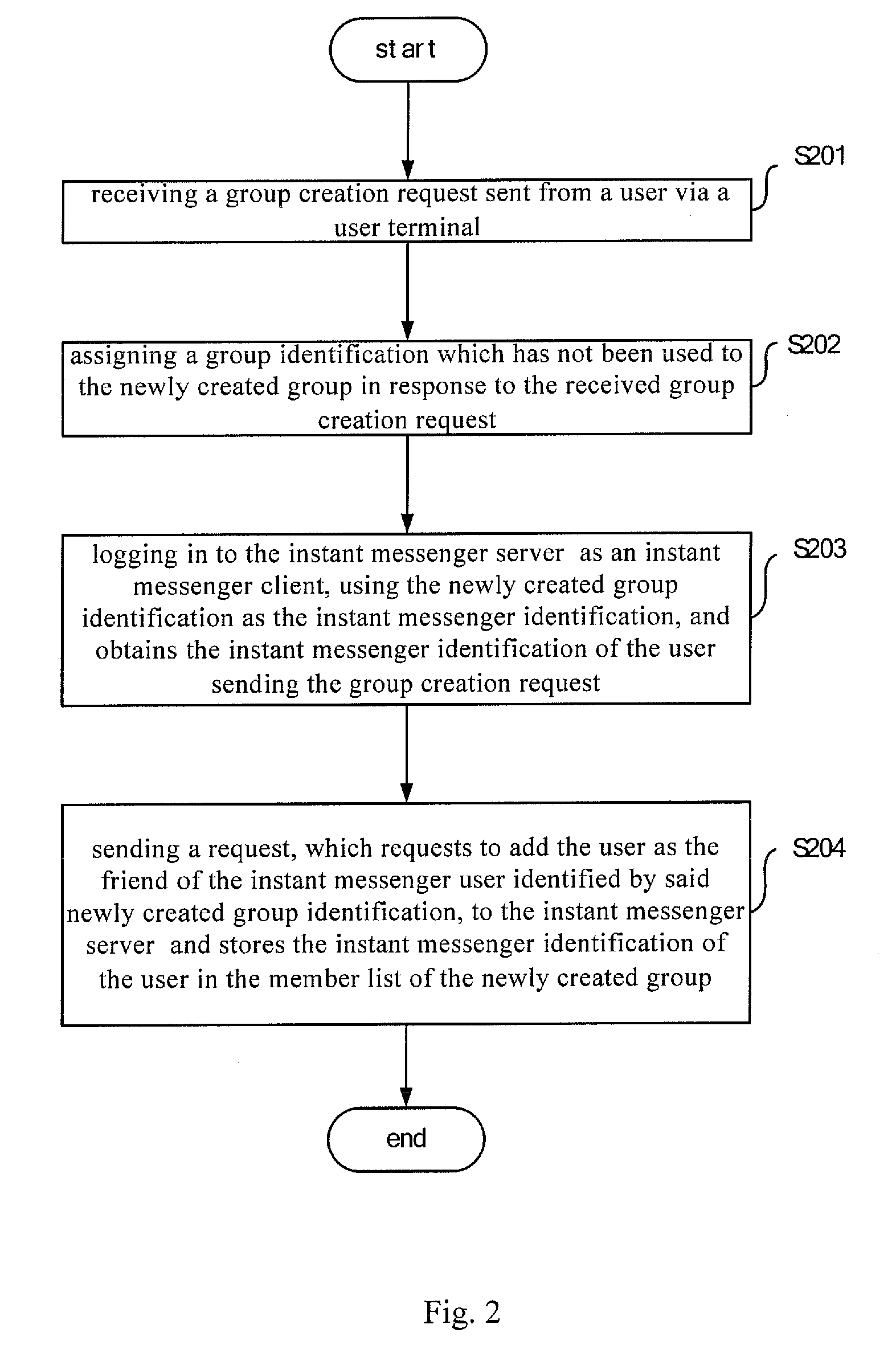
Method and apparatus for realizing instant messaging between a plurality of members in an instant messenger group
InactiveUS20100146065A1Implementation is simple and convenientSimple and efficient implementationMultiple digital computer combinationsTransmissionServer logClient-side
The invention provides a technical solution for instant messaging among multiple members of an instant messenger group. An instant messenger group server is independent of an instant messenger server. At least one group identification and a member list of each group identified by the corresponding group identification are prestored in the group server. The instant messenger group server logs in to the instant messenger server as an instant messenger client, using each of said at least one group identification as an instant messenger identification, and receives instant messages sent by an instant messenger client and sends the instant messages respectively to each of the instant messenger clients corresponding to the instant messenger identifications of other members the instant messenger server. Since the instant messenger group server is independent of the instant messenger server, the instant messenger group server can support multiple instant messenger platforms.
Owner:INCESOFT
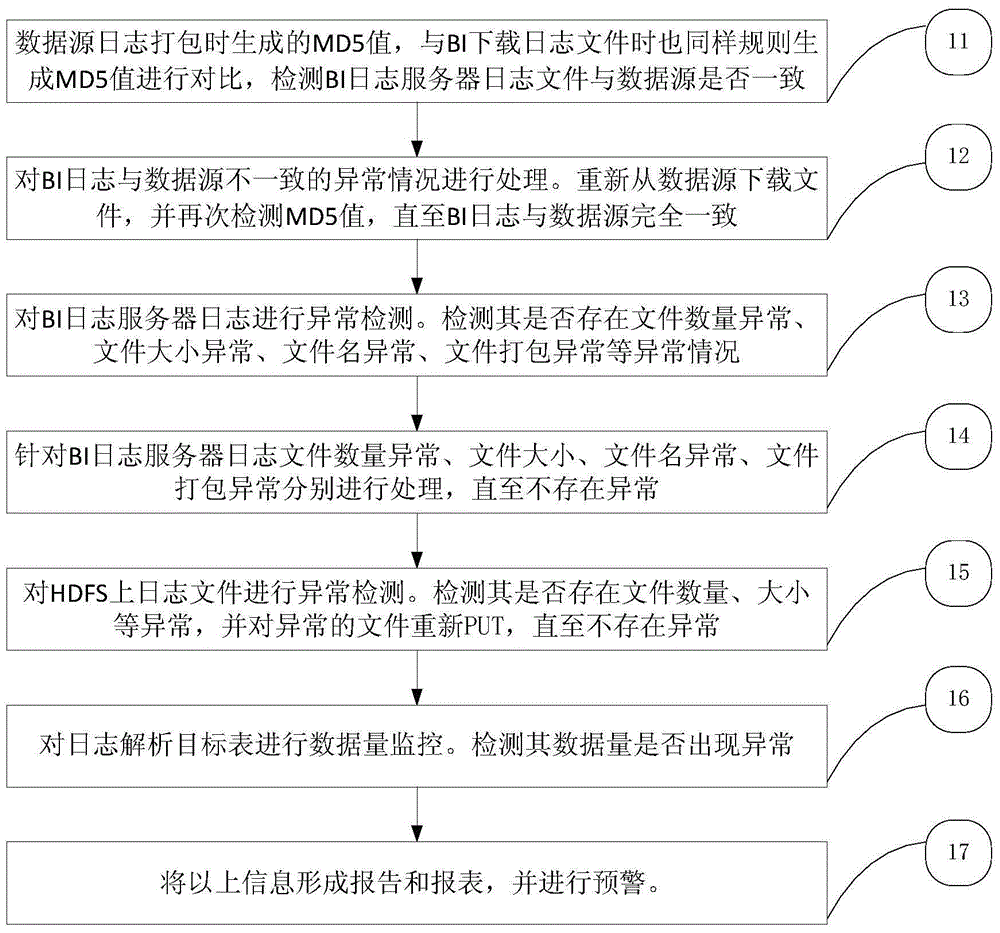
Method and device for abnormity detection and processing of log files
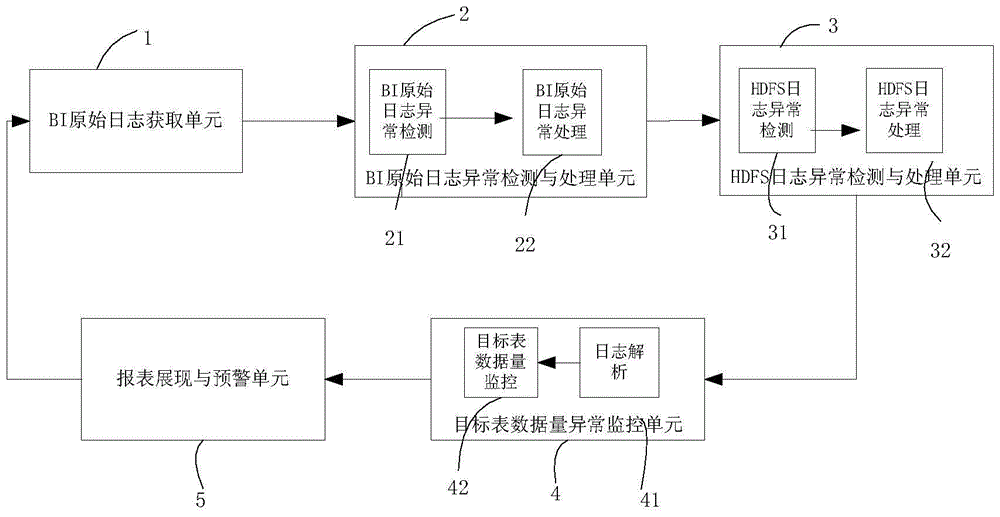
ActiveCN105700989AImprove analytical performanceComplete and accurate analysisHardware monitoringServer logAnomaly detection
The invention discloses a method for abnormity detection and processing of log files. The method comprises the following steps: 1) abnormity monitoring and processing of a BI log server log and a data source MD5: (1) comparing the BI log server log with the data source MD5 and detecting whether the BI log server log and the data source MD5 are abnormal, and (2) processing the abnormal condition that a BI log server log file is inconsistent with a data source MD5 file; 2) abnormity monitoring and processing of the BI log server log file and the data source MD5 file: (1) detecting whether the BI log server log file is abnormal, (2) identifying content in the file, and when records not under the date of a folder exist in the file under the folder or records under the date and records not under the date coexist in the file, considering that the log file has packaging error, and (3) abnormity processing of the BI log server log file: carrying out abnormity detection on the BI log server log file and carrying out processing after abnormity is found; and 3) abnormity detection and processing of an HDFS file.
Owner:FOCUS TECH
Server log monitoring method and system based on block chain
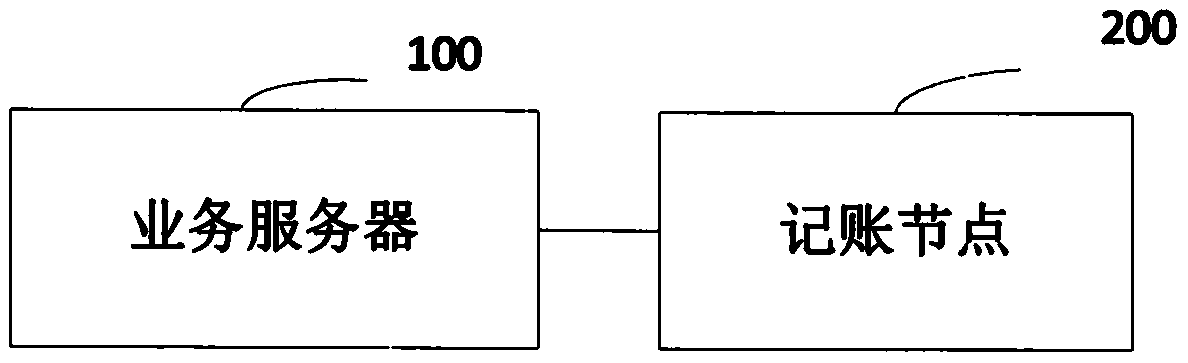
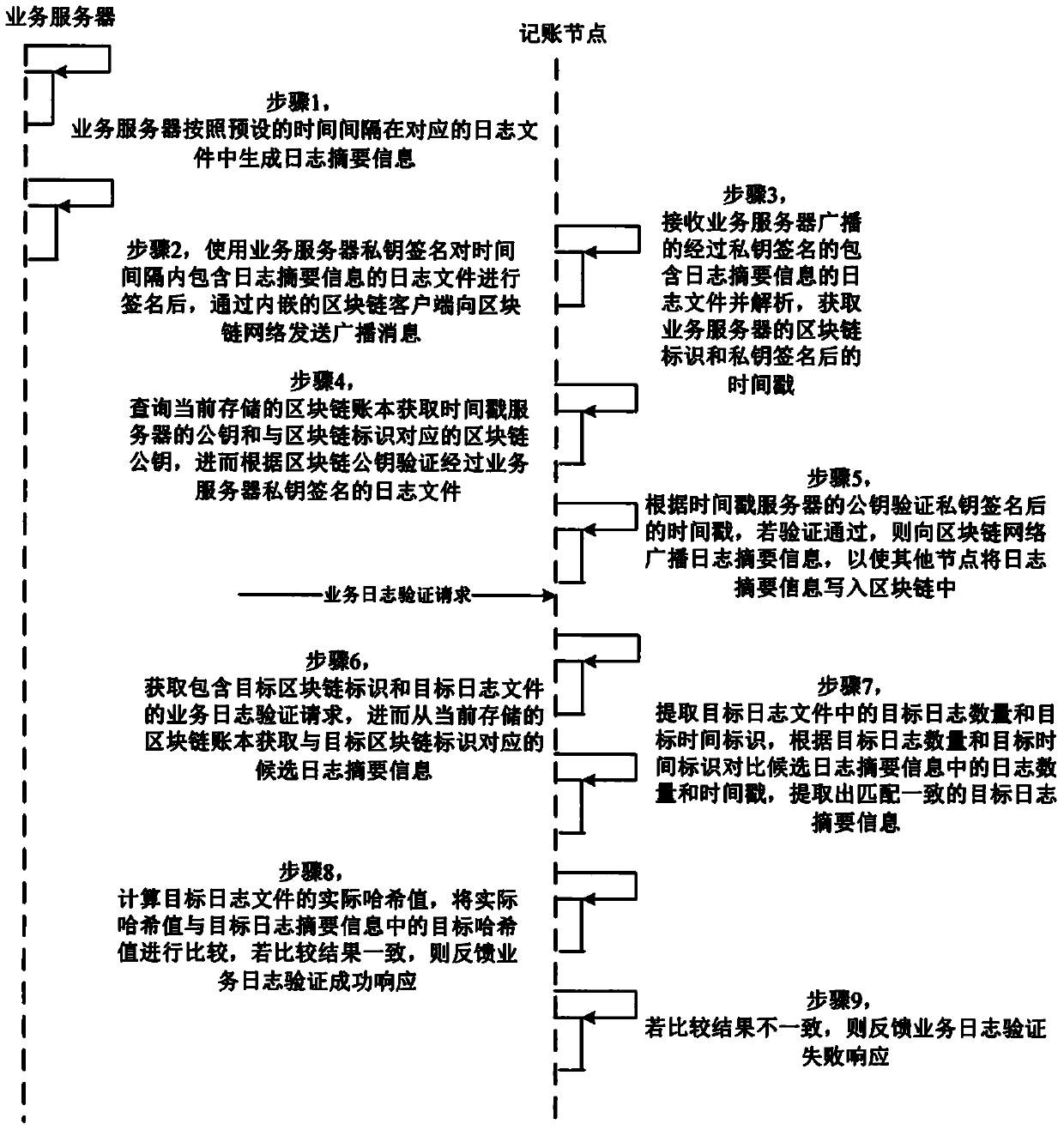
ActiveCN110084069APrevent malicious tamperingReal-time log tampering risk monitoringHardware monitoringDigital data protectionServer logChain network
The invention provides a server log monitoring method and system based on a block chain. The method comprises the following steps that a service server generates log summary information in a log file;the log file is sent to the block chain network; and the accounting node in the block chain network analyzes the log file to verify the authenticity of the sender identity of the log file and the reliability of the content, and if the verification is passed, the log summary information in the log file is written into the block chain, so that the reliability of the target log file is verified according to the written log summary information. Therefore, the authenticity of the log file is verified based on the decentralized block chain network, the log is prevented from being maliciously tampered, real-time log tampering risk monitoring is realized, and the security of the system is protected.
Owner:江苏全链通信息科技有限公司
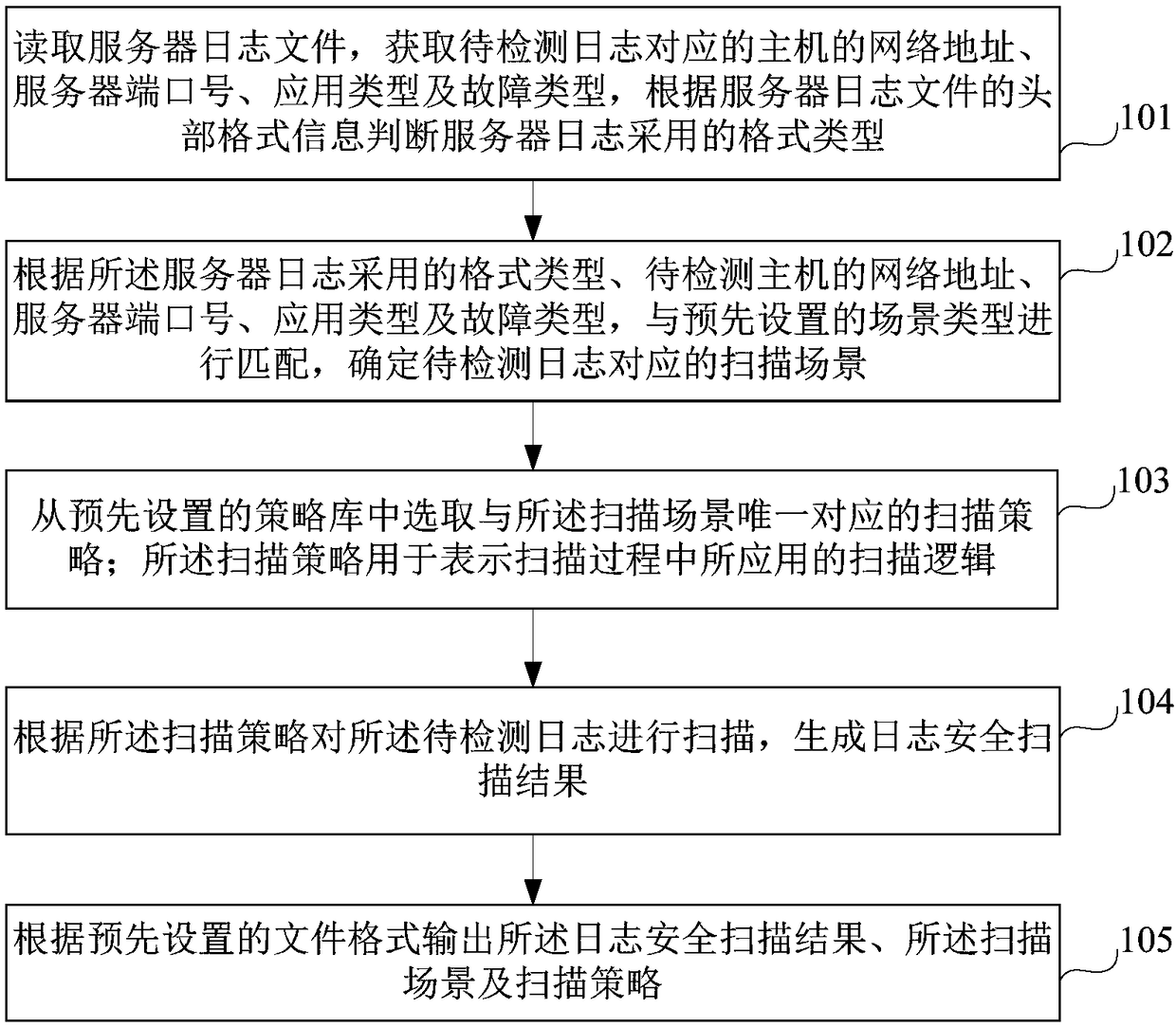
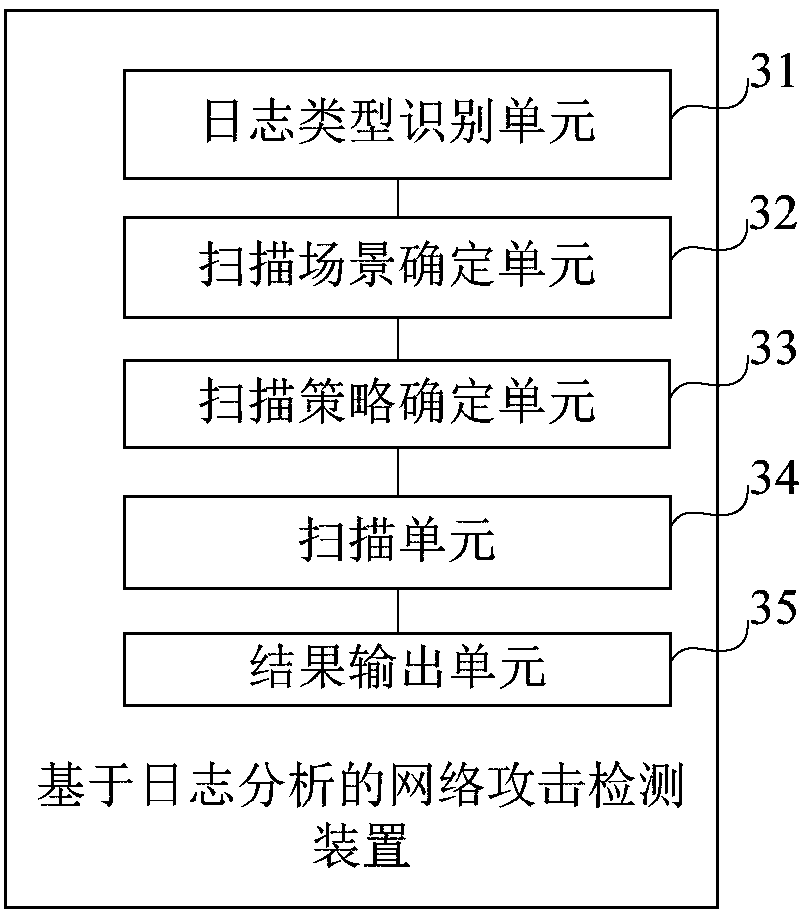
Network attack detection method and device based on log analysis
The invention provides a network attack detection method and device based on log analysis, and relates to the technical field of network information security. The method comprises the following steps:reading a server log file, obtaining a network address, a server port number, an application type and a fault type of a host corresponding to a to-be-detected log, and judging a format type adopted by the server log according to header format information of the server log file; performing matching with a preset scene type according to the format type adopted by the server log, and the network address, the server port number, the application type and the fault type of the to-be-detected hot to determine a scanning scene corresponding to the to-be-detected log; selecting a scanning strategy uniquely corresponding to the scanning scene from a preset strategy library; scanning the to-be-detected log according to the scanning strategy to generate a log security scanning result; and outputtingthe log security scanning result, the scanning scene and the scanning strategy according to a preset file format.
Owner:NORTH CHINA ELECTRICAL POWER RES INST +2
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com