Identity verification method, server and readable storage medium
An identity verification method and identity verification technology, applied in the fields of identity verification methods, servers and readable storage media, can solve the problems of resource security on the server side, malicious calls, etc., to prevent malicious calls and improve security sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
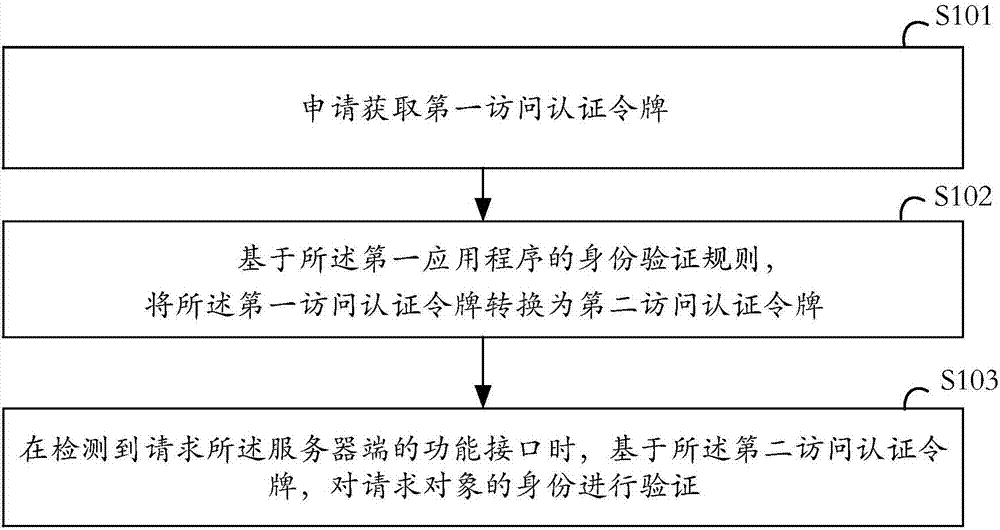
[0049] Please refer to figure 1 , the first embodiment of the present invention provides an identity verification method, which is applied to the server of the first application program, and the identity verification method includes the following steps:
[0050]S101: Apply for a first access authentication token, the first access authentication token is applied by the server to the second application when logging in to the first application through the applet function of the second application An access authentication token generated based on the corresponding rules of the second application;
[0051] S102: Convert the first access authentication token into a second access authentication token based on the identity verification rule of the first application;
[0052] S103: Verify the identity of the request object based on the second access authentication token when it is detected that the functional interface of the server is requested.
[0053] Specifically, in this embodi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com