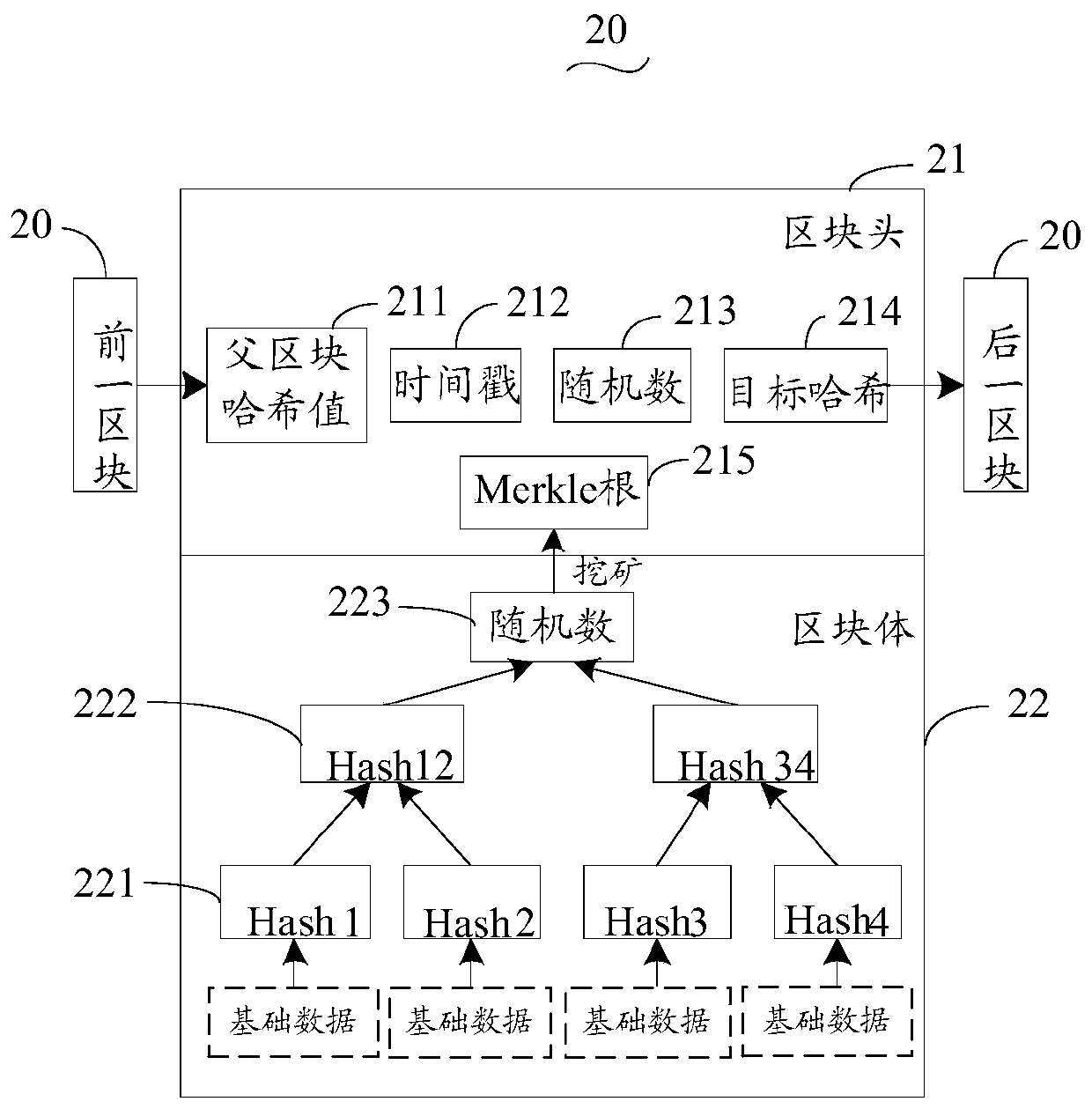
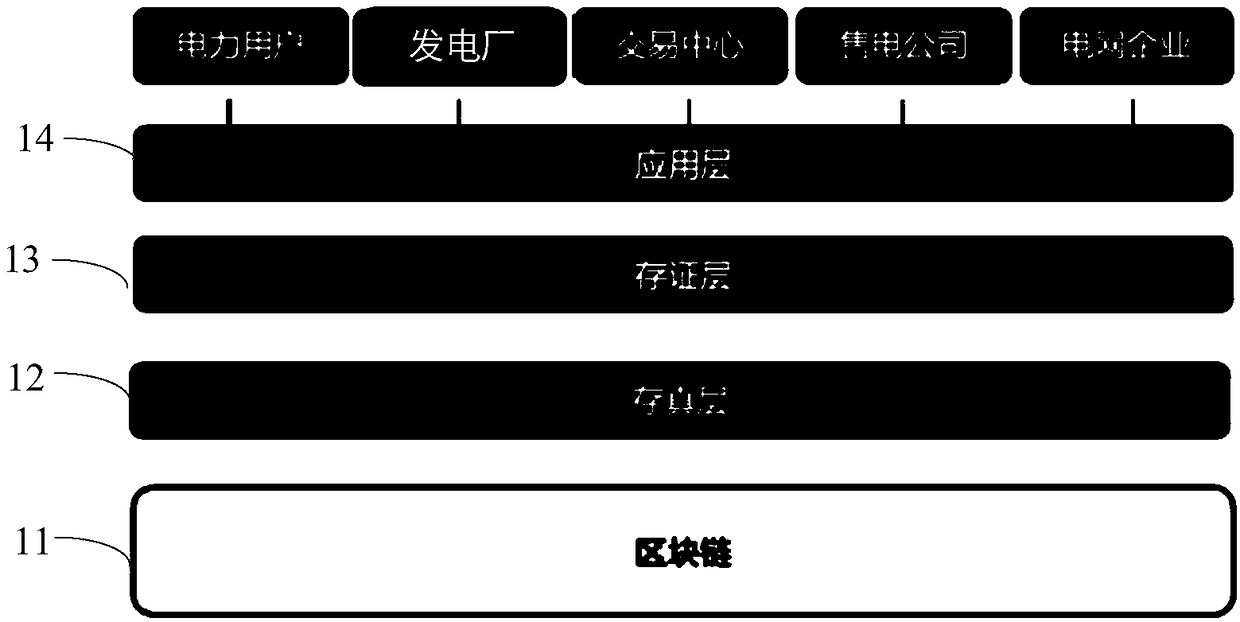
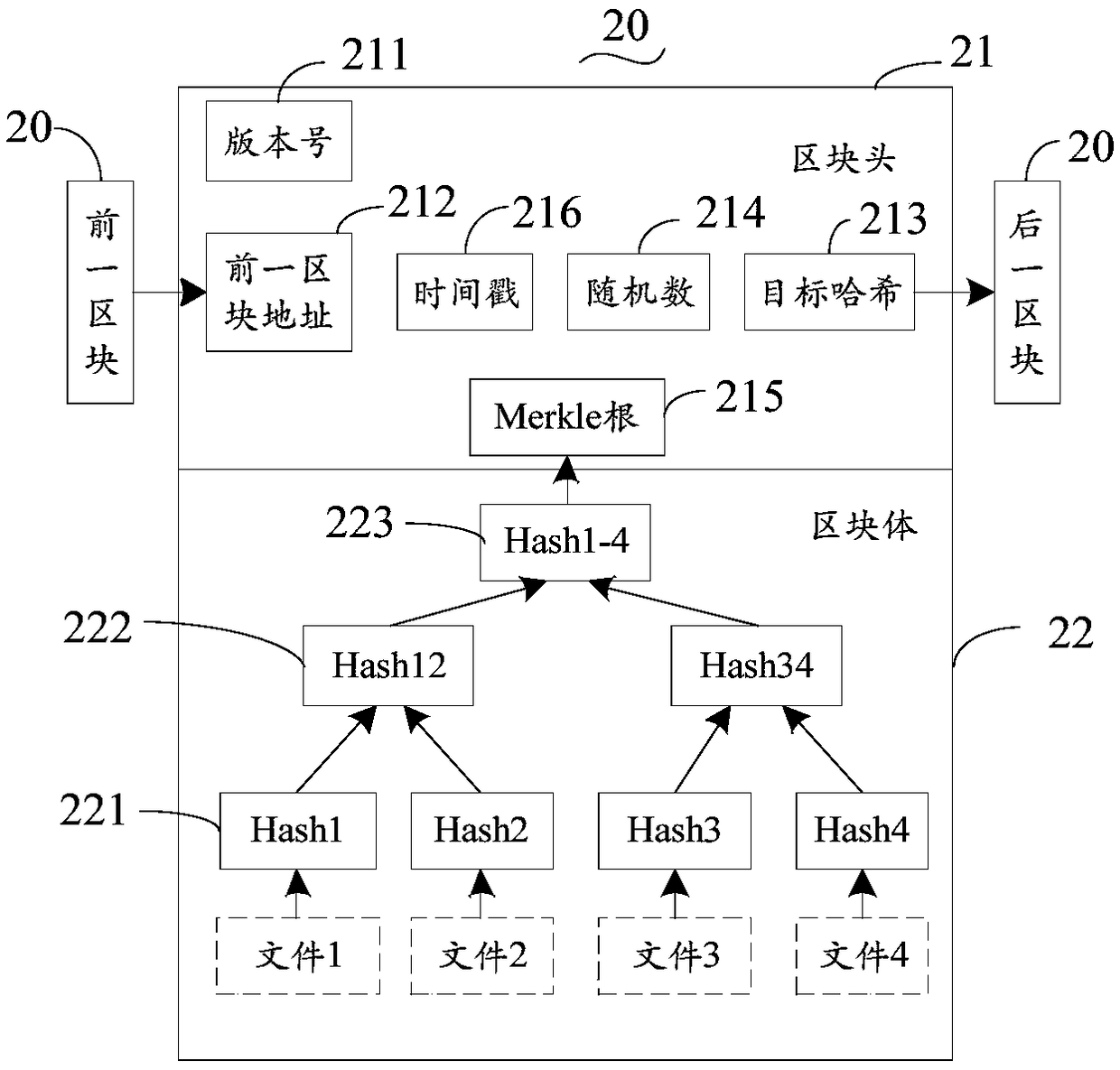
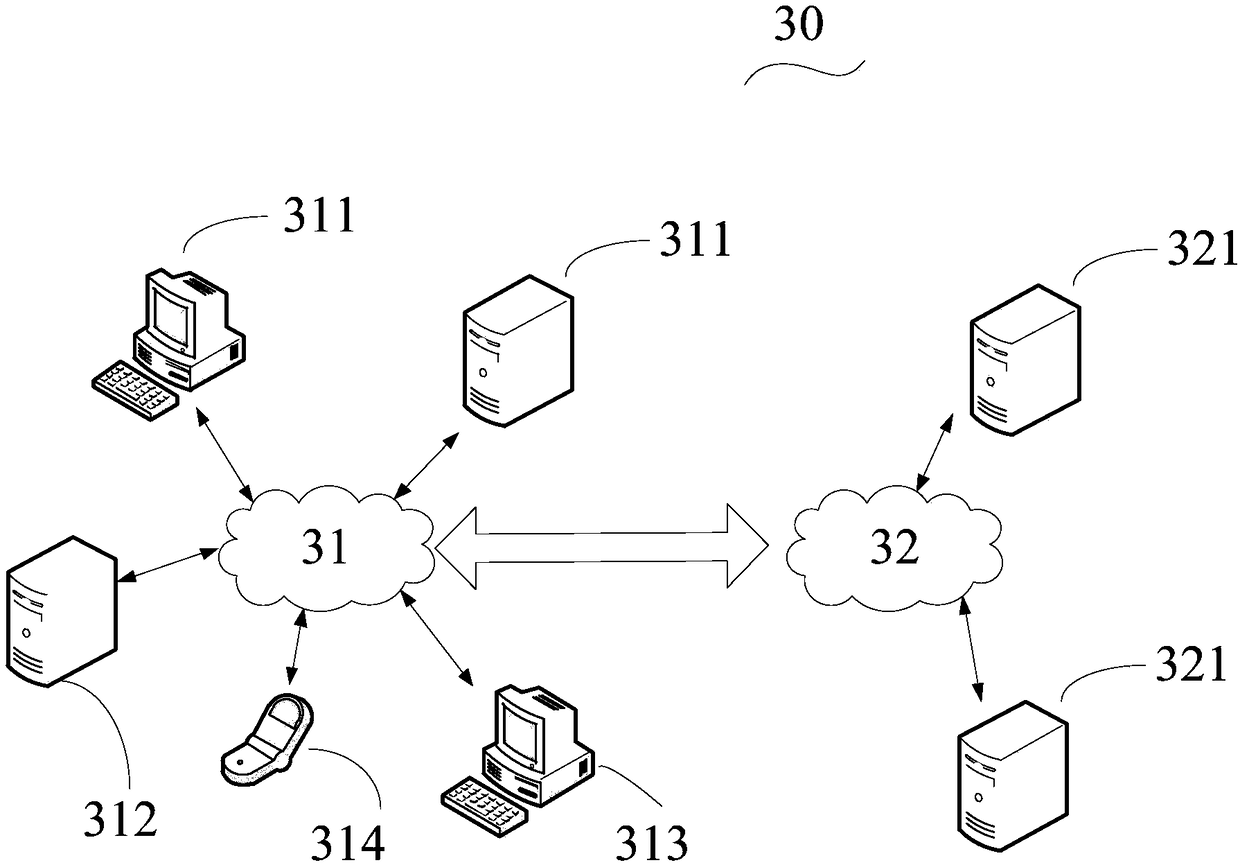
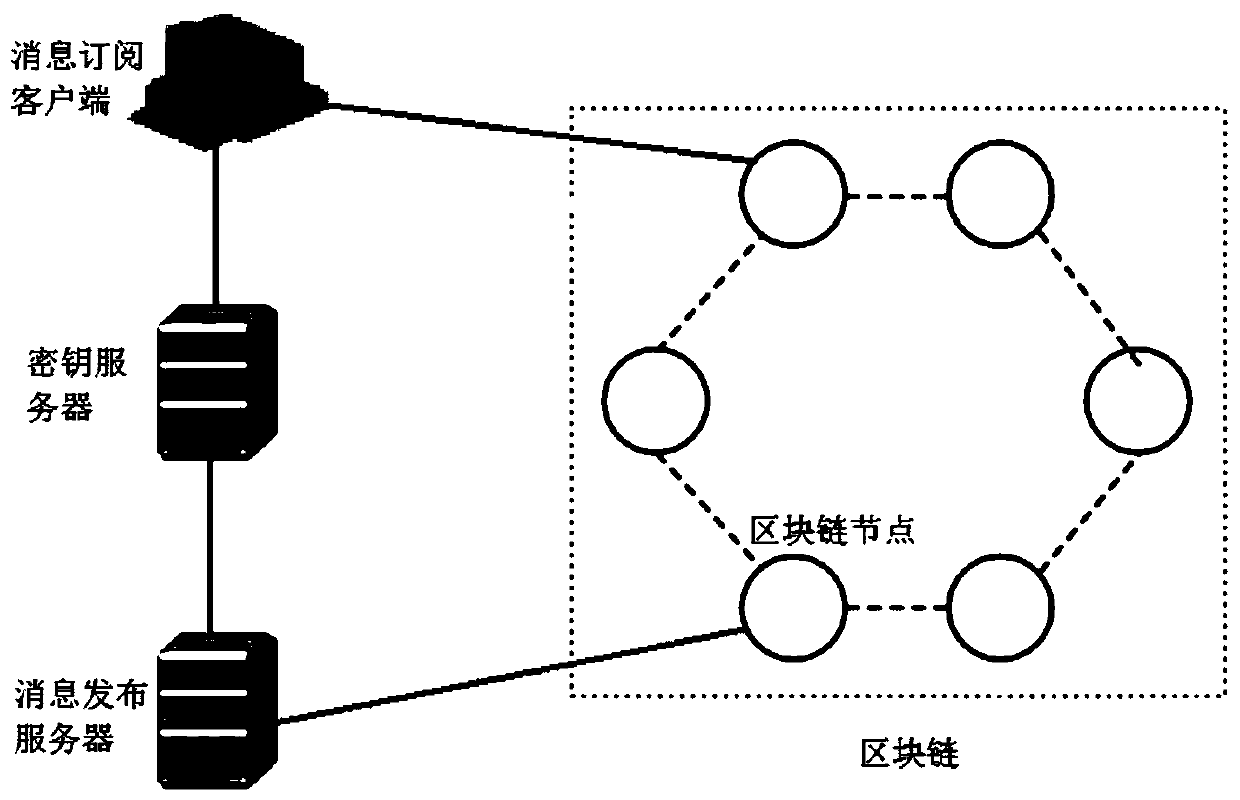
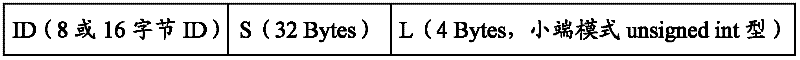Patents
Literature
299results about How to "Prevent malicious tampering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
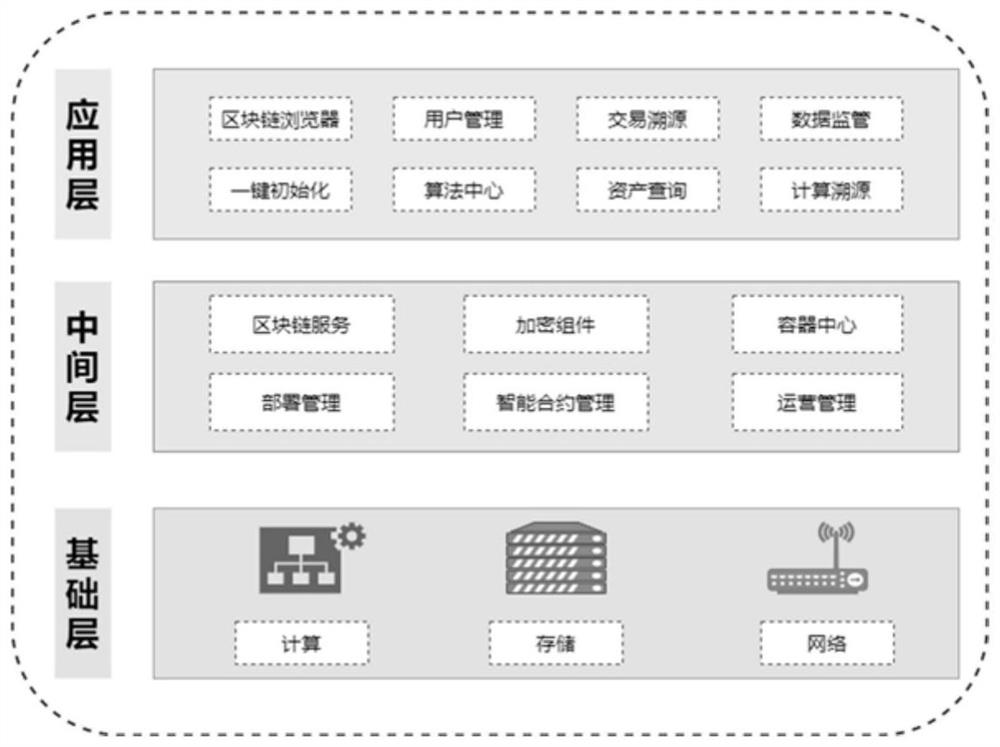
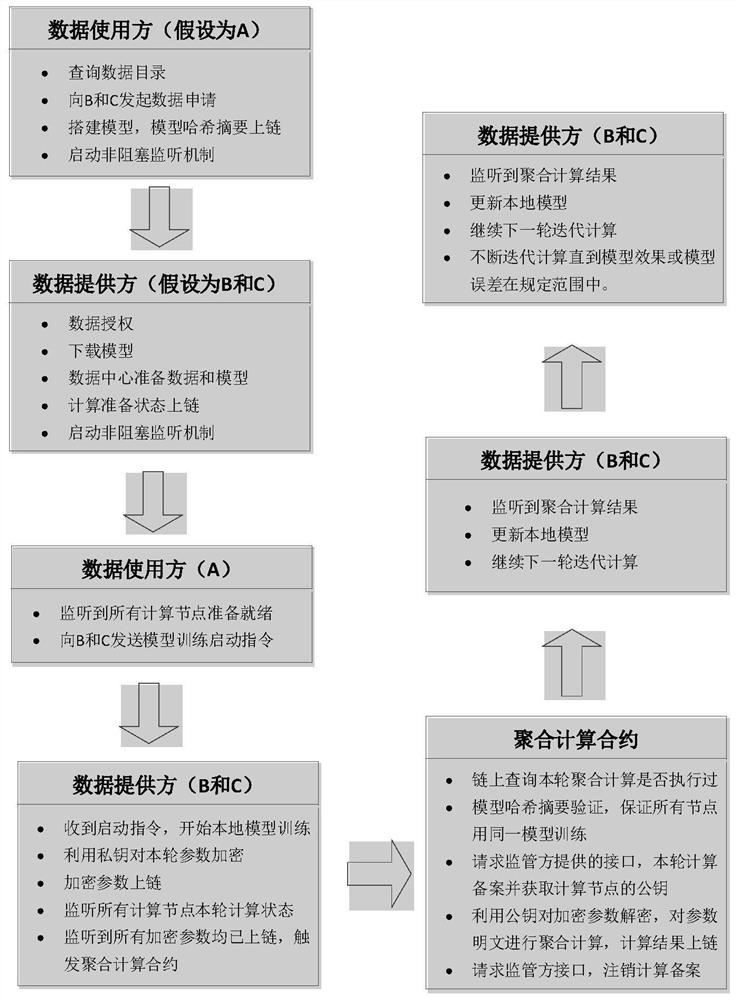
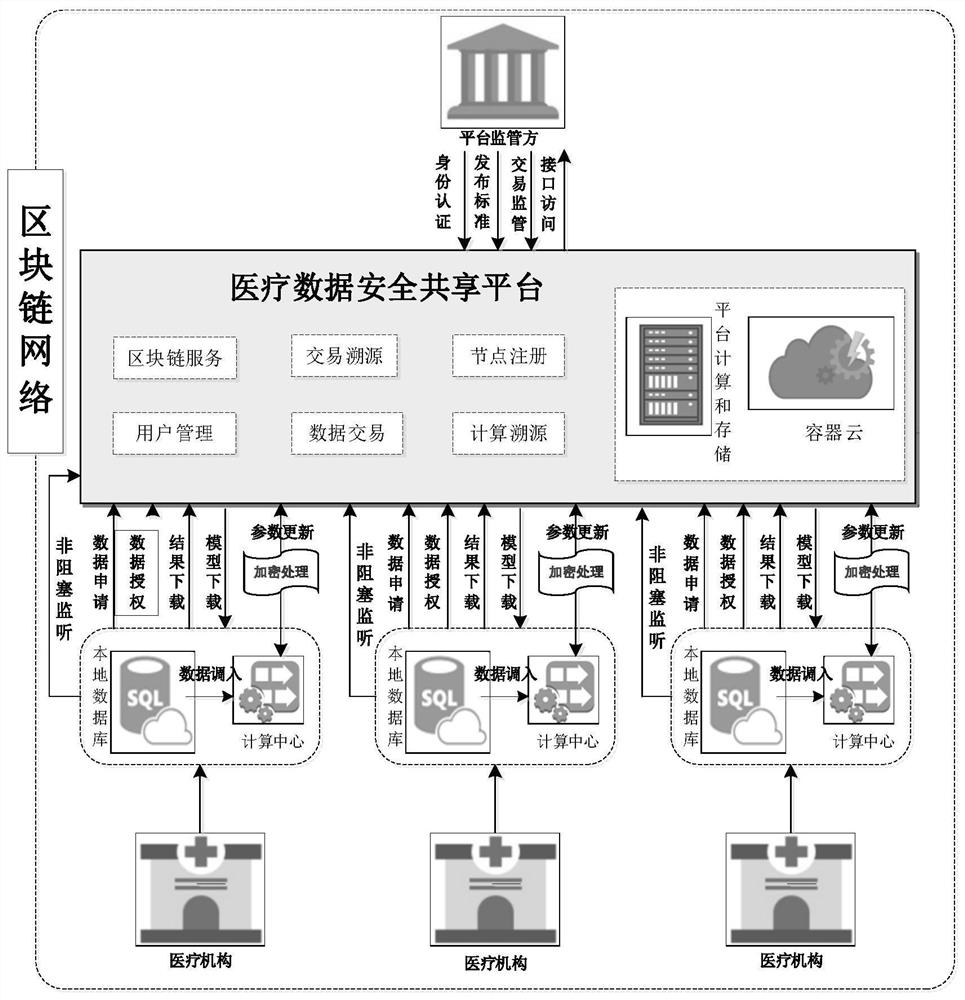
Medical data security sharing method based on block chain and federated learning
ActiveCN111698322APrevent malicious tamperingAvoid inconsistenciesMedical equipmentSecuring communicationData providerOriginal data
The invention discloses a medical data security sharing method based on a block chain and federated learning. The data applicant can use the data after being authorized on the chain of the data provider; the data fingerprint carries out hash abstract chaining on authorized data, the problem that the authorized data is maliciously tampered to cause data inconsistency is prevented, the use right ofthe original data is shared in the whole process, a data user cannot directly obtain the data, and the value of the data can be mined only through federated learning. In each round of iterative computation of federated learning, asset chaining is carried out on model parameters and aggregation results, and credible traceability of federated learning computation can be achieved. Each step of operation in the data sharing process is subjected to related auditing by a supervisor, such as identity auditing, data checking, transaction detail auditing and the like. According to the invention, aggregation calculation is carried out without the help of a central server, decentralized federated learning is realized, aggregation calculation is realized through an intelligent contract, and maliciousaggregation calculation results received by each node due to malicious control of the central server are avoided.
Owner:福州数据技术研究院有限公司
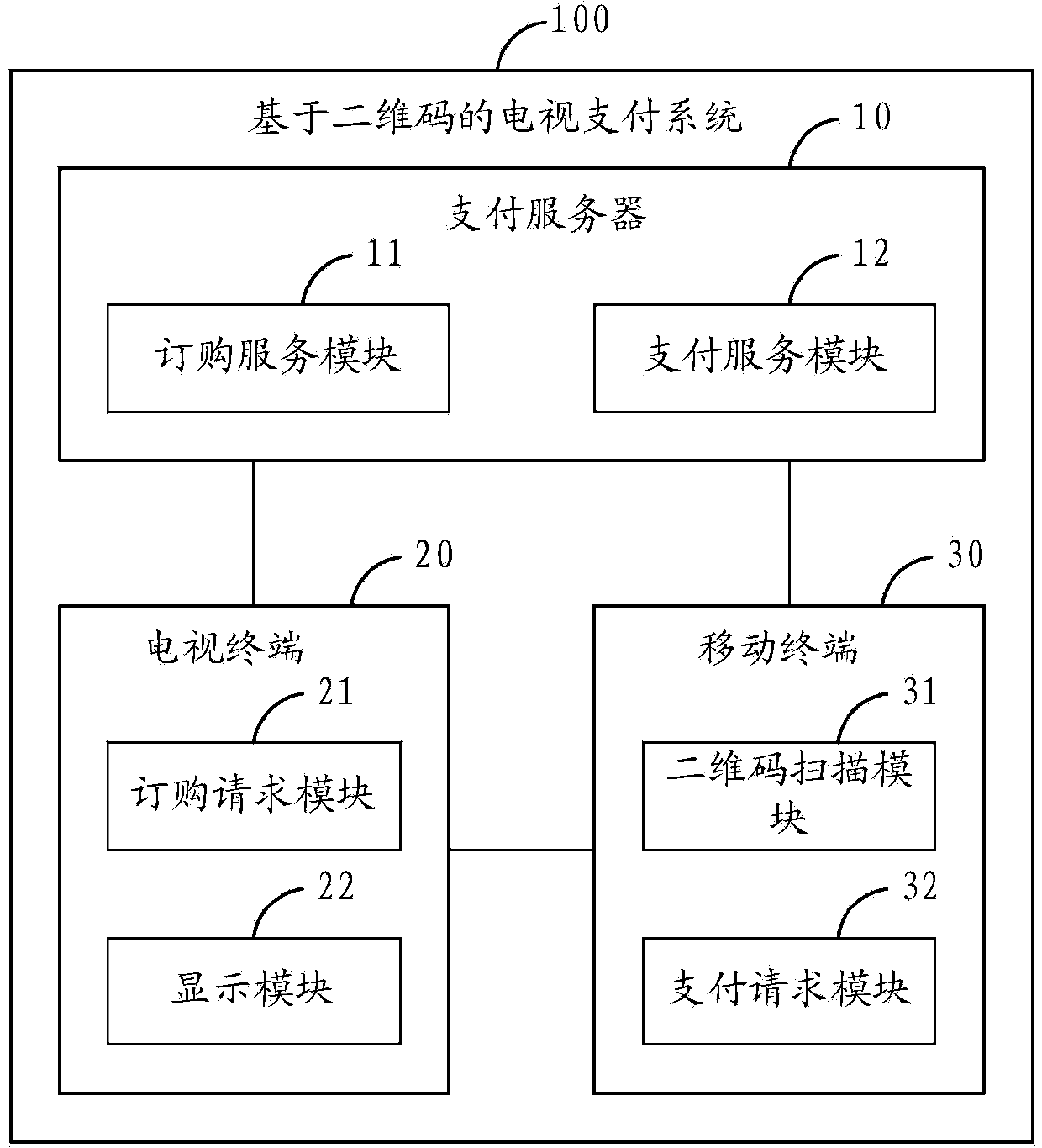
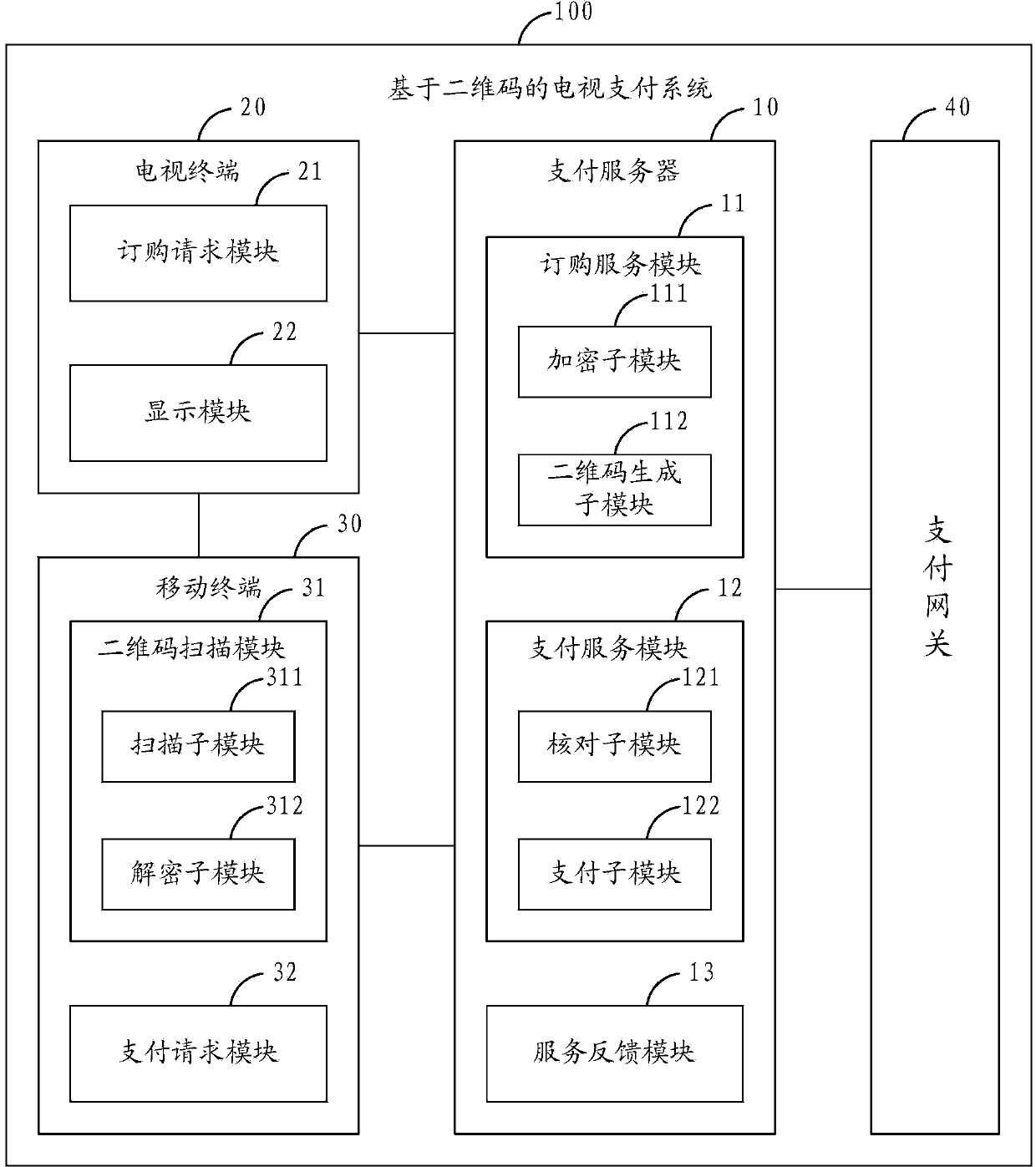
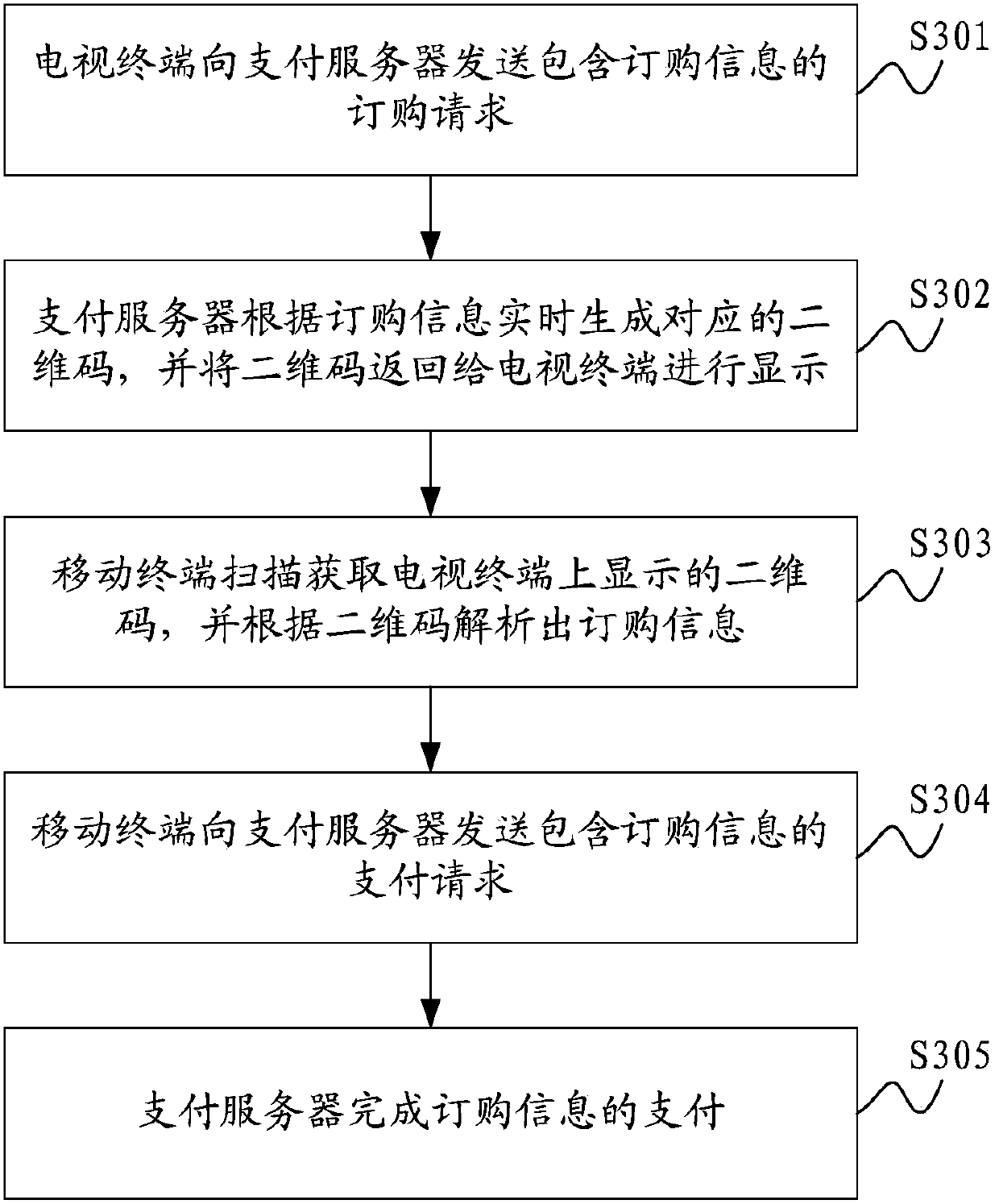
Television payment method and system based on two-dimensional codes
InactiveCN103426083AImprove experienceGuaranteed validityPayment architectureSelective content distributionPaymentPayment order
The invention belongs to the technical field of network televisions, and provides a television payment method and system based on two-dimensional codes. The television payment method comprises the steps that a television terminals sends an ordering request containing ordering information; a payment server generates corresponding two-dimensional codes in real time according to the ordering information and returns the two-dimensional codes to the television terminal to be displayed; a mobile terminal scans to obtain the two-dimensional codes displayed on the television terminal and analyzes the ordering information according to the two-dimensional codes; the mobile terminal sends a payment request containing the ordering information to the payment server; the payment server completes payment of the ordering information. Therefore, through the combination of the two-dimensional codes and the mobile terminal, the television payment method and system realize television payment, enable television payment to be more convenient and quicker, and user experience is improved accordingly.
Owner:百视通网络电视技术发展有限责任公司
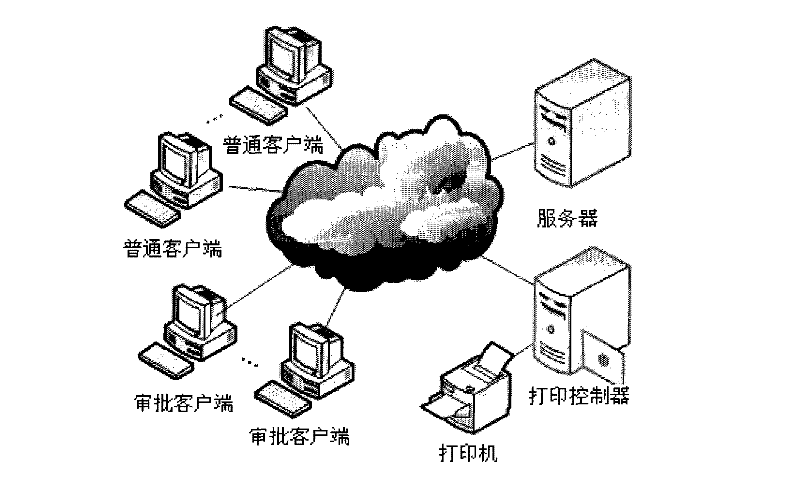
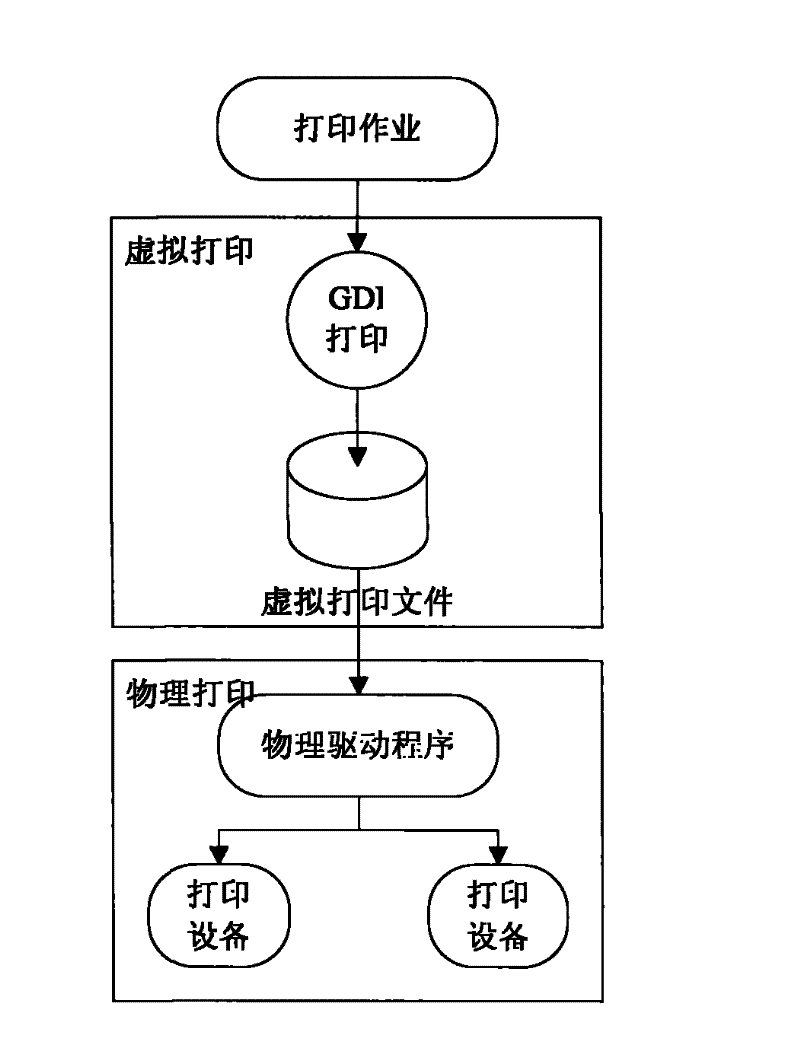
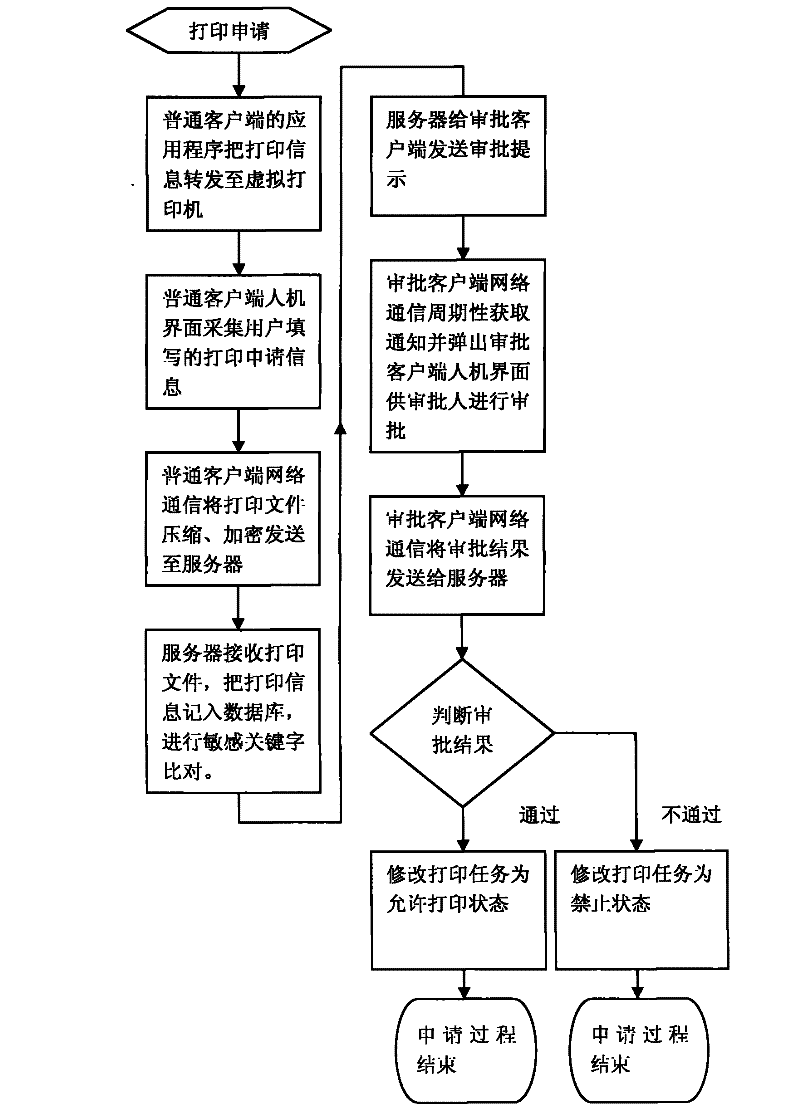
Printing security monitoring and auditing system based on virtual printing technique
ActiveCN102523255APrevent malicious tamperingImprove securityTransmissionDigital output to print unitsOptical character recognitionIntelligent control
The invention belongs to the field of information security techniques and provides a printing security monitoring and auditing system based on a virtual printing technique aiming at solving the problems that the printing behavior and the printing content are hard to monitor, unauthorized printing and skip-level printing cannot be prevented and the like in the existing printing management method. The printing security monitoring and auditing system comprises a server, at least one ordinary client, at least one approval client, a printing controller and a printing machine, wherein the clients are divided into the ordinary clients and the approval clients; and all ordinary clients and all approval clients are connected with the server, the printing controller is connected with the server and the printing machine is connected with the printing controller. By adopting the windows virtual printing technique, the optical character recognition (OCR) technique, the equipment intelligent control technique and the like, the printing security monitoring and auditing system realizes the monitoring and management of documents at a full life cycle which comprises printing application, approval, output, recovery, destruction and the like, and can form complete printing logs for review.
Owner:北京京航计算通讯研究所
File storage method and electronic device thereof, and storage medium
ActiveCN109409122AGuaranteed reliabilityImprove reliabilityDigital data protectionHash tableBlockchain
The present application discloses a file storage method, an electronic device and a storage medium thereof. The method comprises the following steps: a block chain accounting node receives the first file data; calculating the first file data by using a hash algorithm to obtain a first hash value; generating a second hash value using the first hash value and the second file data; the second hash value or both the first hash value and the second hash value are stored in a block chain for verifying whether the first file data has been tampered with. The scheme can avoid malicious tampering with the file data and ensure the reliability of the file data.
Owner:YGSOFT INC
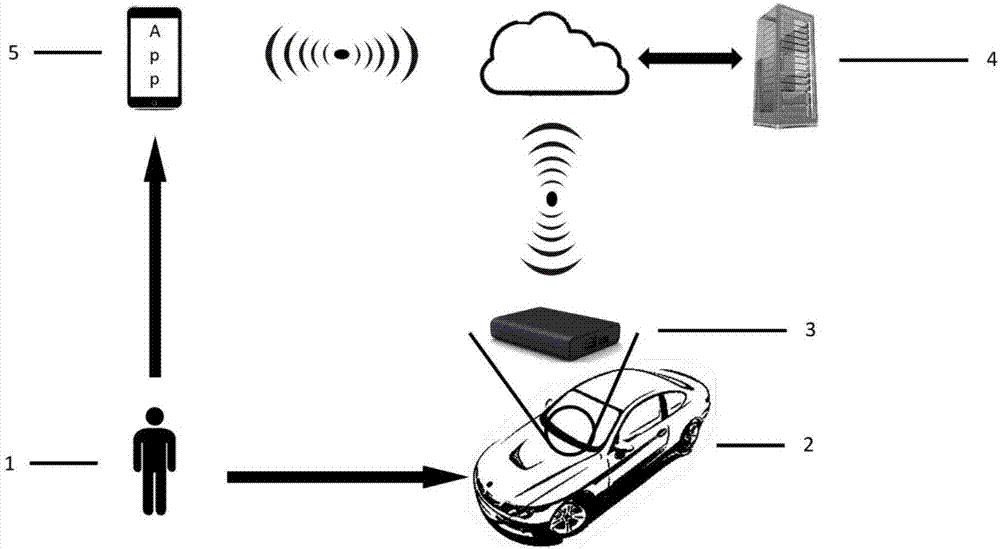
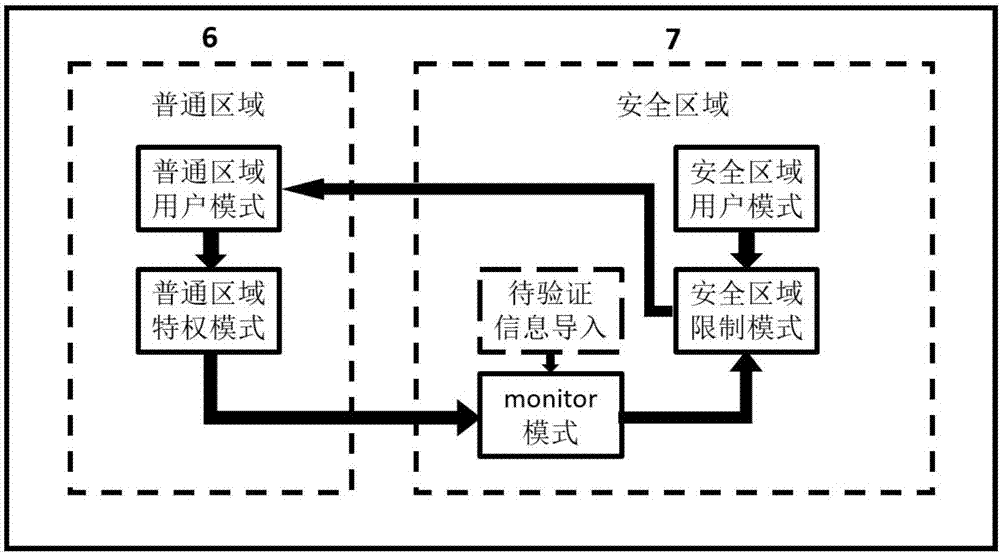
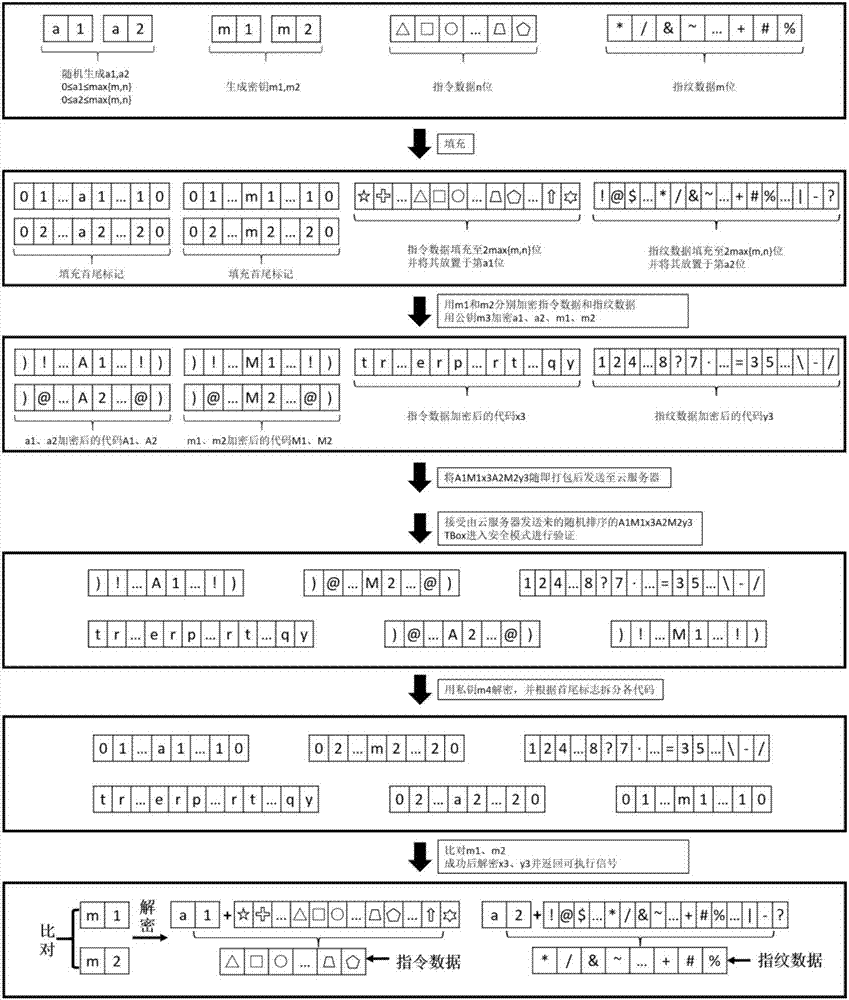
Safety certification system and method for information interaction between vehicle-mounted T-Box and user cellphone
ActiveCN106878008ASimple designProtection against intrusionKey distribution for secure communicationNormal modeSecure authentication
The invention discloses a safety certification system for information interaction between a vehicle-mounted T-Box and a user cellphone, and the system comprises a vehicle, the vehicle-mounted T-Box, a T-Box cloud server, and a mobile terminal. The invention also discloses a safety certification method for information interaction between the vehicle-mounted T-Box and the user cellphone, and the method comprises the following steps: 1, inputting the fingerprint of a user through the mobile terminal, enabling the mobile terminal to generate encryption data through the instruction data and fingerprint data and a downloaded APP, carrying out the random ordering of the encryption data, packaging the encryption data, and transmitting the packaged encryption data to a T-Box server; 2, enabling the T-Box server to search the corresponding vehicle-mounted T-Box according to a VIN code linked with an instruction source account, and then transmitting the information to the corresponding vehicle-mounted T-Box; 3, enabling the corresponding vehicle-mounted T-Box to carry out the authentication of the fingerprint information in the data in a safety mode: switching to a normal mode and carrying out the execution of the instruction if the authentication is successful, or else carrying out no operation.
Owner:BEIHANG UNIV
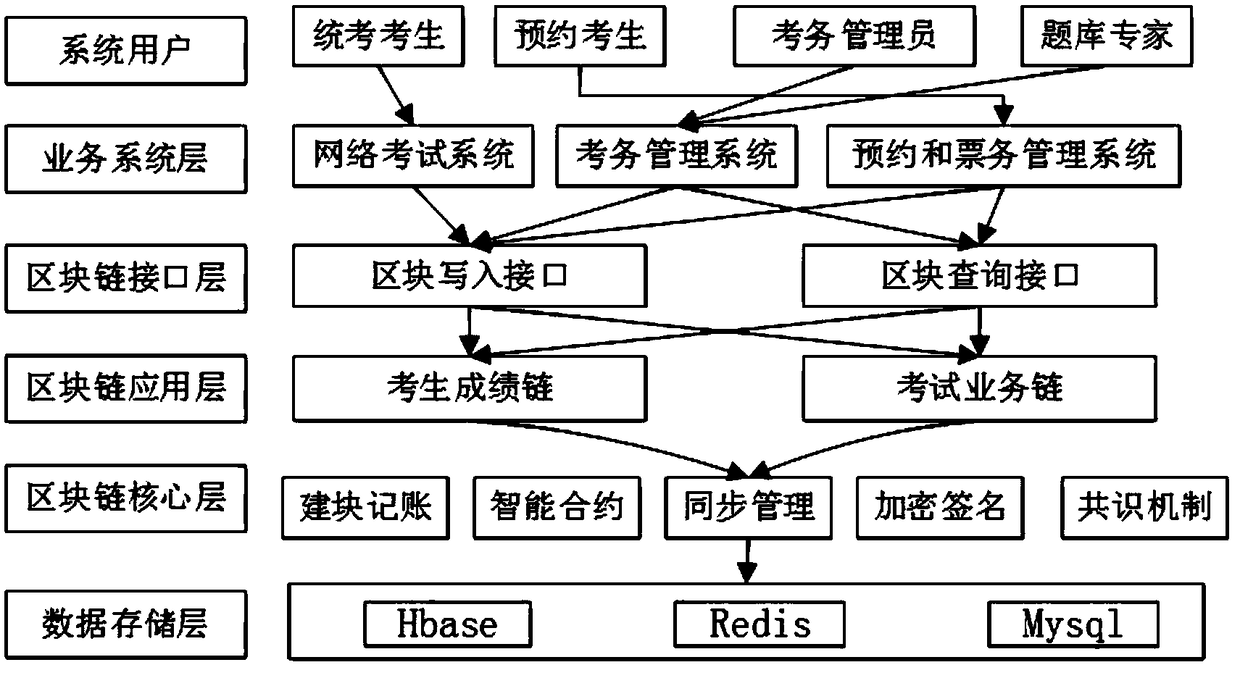
A network examination system based on a block chain and a method for managing the network examination by using the network examination system
ActiveCN109002527AAvoid lossPrevent malicious tamperingData processing applicationsSpecial data processing applicationsCredit systemManagement process
The invention relates to a network examination system based on a block chain and a method for managing the network examination by using the network examination system, belonging to the technical fieldof teaching management equipment. The system adopts double-block chain design, including a data storage layer, a block chain core layer, a block chain application layer, a block link interface layer,a business system layer and a system user layer. The API interface of the data storage layer is connected with the API interface of the core layer of the block chain, the core layer of the block chain is connected with the application layer of the block chain, and the application layer of the block chain is connected with the interface layer of the block link through the API interface. The blocklink interface layer is connected with the service system layer to realize the inquiry and writing of the block chain service. The business system layer is connected with the system user layer, whichprovides the interface between the user and the network examination service. The invention can prevent information from being lost or tampered with maliciously, construct a safe, reliable and non-tamper examination credit system, simplify the network examination management process, improve the network examination organization efficiency, and provide high-efficiency, convenient and humanized examination service for examinees.
Owner:JIANGSU OPEN UNIV
An enterprise resource management system based on a block chain
ActiveCN109698752AImprove management and operation efficiencyEnsure safetyFinanceUser identity/authority verificationResource Management SystemComputer module
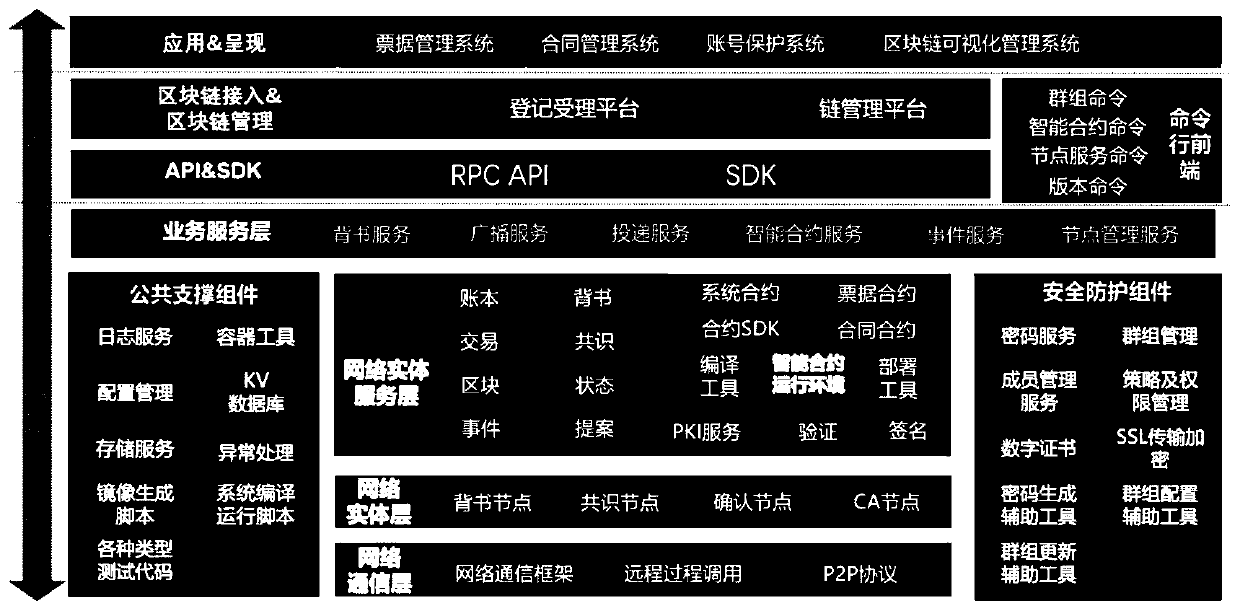
The invention discloses an enterprise resource management system based on a block chain. The enterprise resource management system includes a network communication layer, a network entity layer, a network entity service layer, a public support component, a security protection component, a business service layer, a command line front-end module, an API & SDK, a block link entry and management module and an application and presentation module. and various types of block chain platforms are developed and accessed based on the business service layer and the API & SDK. Compared with a traditional resource management system, the management operation efficiency can be greatly improved in the aspects of safety confirmation, input, management, query and the like, the safety of the system can be guaranteed, and the management operation efficiency can also be improved.
Owner:NARI INFORMATION & COMM TECH
Transaction storage method, storage network and electronic equipment
PendingCN109711836APrevent tamperingImprove storage reliabilityPayment protocolsStorage area networkTransaction data
The invention discloses a transaction storage method, a storage network and electronic equipment, and the method comprises the steps that a transaction node sends transaction data of a transaction toan information service processing node after the transaction initiated by the transaction node is completed; the information service processing node extracts characteristic data of the transaction byutilizing the transaction data; the transaction node calculates the characteristic data by using an irreversible encryption algorithm to obtain a first information abstract of the transaction, packages the first information abstract of the transaction into a storage request and sends the storage request; and the blockchain accounting node receives the storage request and stores the first information abstract in the blockchain. Through the scheme, the transaction can be prevented from being maliciously tampered, and the reliability of the transaction is ensured.
Owner:YGSOFT INC
Active defense method based on block chain intelligent contract, and node
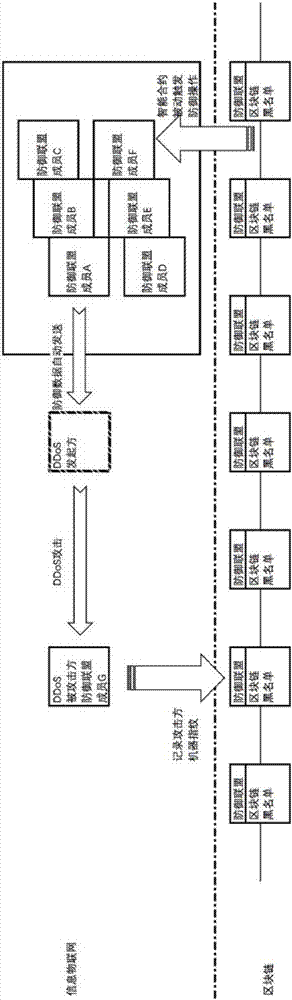
InactiveCN107172085APrevent malicious tamperingAvoid misjudgmentTransmissionNetwork packetThe Internet
The invention provides an active defense method based on a block chain intelligent contract, and the method comprises the following steps: enabling one defensive alliance member to judge whether a flow is an abnormal flow or not after the defensive alliance member is attacked: recording the attack side machine fingerprint if the flow is the abnormal flow, and notifying one of the remaining defensive alliance members or more of the abnormal flow, and requiring for the defense; executing a second intelligent contract after the remaining defensive alliance members receives the notification of defense requiring, i.e., transmitting a data package to an attack side, and quitting the active defense till a set quitting condition is met. According to the invention, equipment which supports the block chain intelligent contract is deployed on the Internet, and the intelligent contract will be automatically started after one server is attacked, and a data package is actively transmitted to the attack side, thereby enabling the attack side not to continue to attack, and achieving the purpose of protecting the server.
Owner:浙江华信区块链科技服务有限公司
Information processing method and electronic device
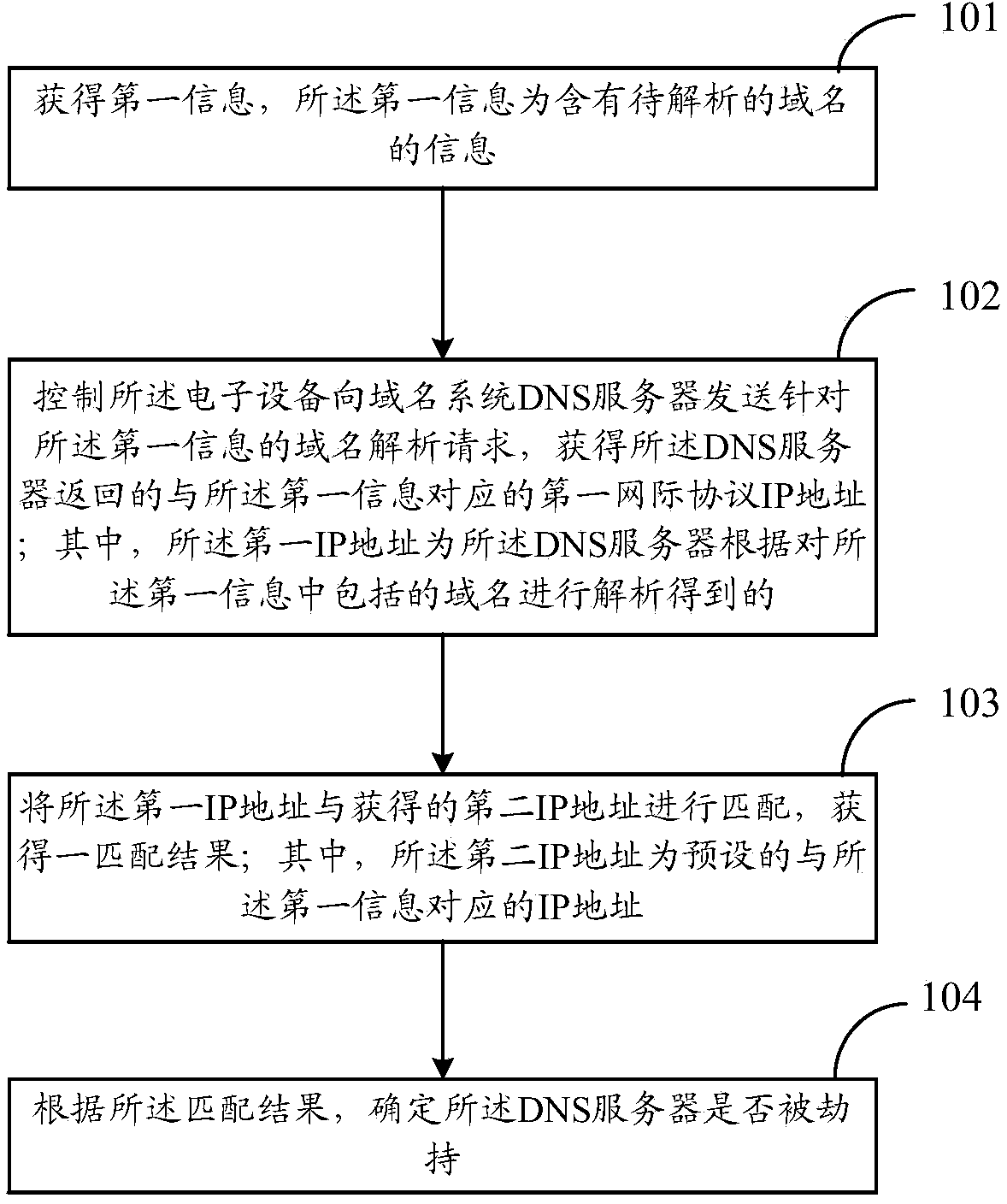
ActiveCN103825895APrevent malicious tamperingEnsure safetyTransmissionDomain nameInformation processing
The invention discloses an information processing method which is used for solving the technical problem that the network security of an electronic device is poor in the prior art. The information processing method is applied to an electronic device and comprises the steps that first information is obtained, wherein the first information contains the information of a domain name to be analyzed; the electronic device is controlled to send a domain name analysis request corresponding to the first information to a domain name system (DNS) server, and a first internet protocol IP address, corresponding to the first information, fed back by the DNS server is obtained; the first IP address is matched with an obtained second IP address, so that a matching result is obtained, wherein the second IP address is a preset IP address which corresponds to the first information; whether the DNS server is hijacked is determined according to the matching result. The embodiment of the invention further discloses the electronic device corresponding to the information processing method.
Owner:LENOVO (BEIJING) CO LTD
Block chain embedding method for wavelet domain watermark in image
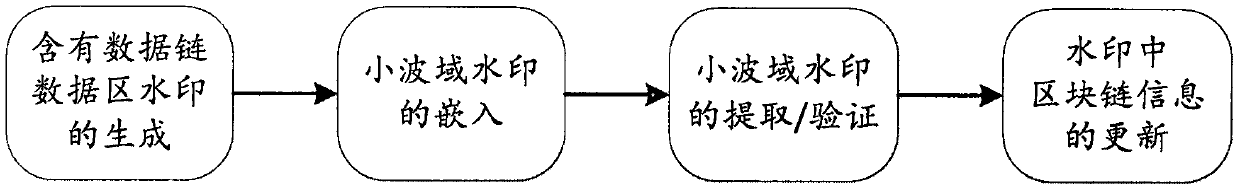
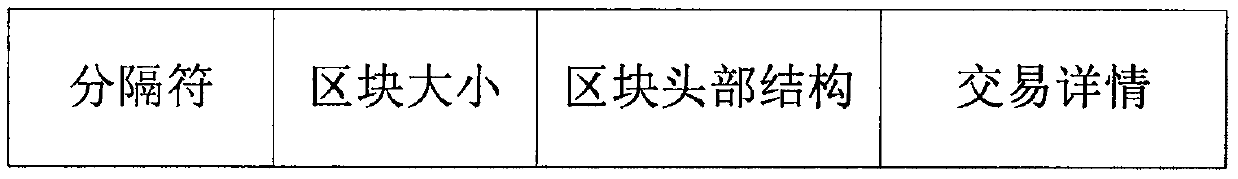
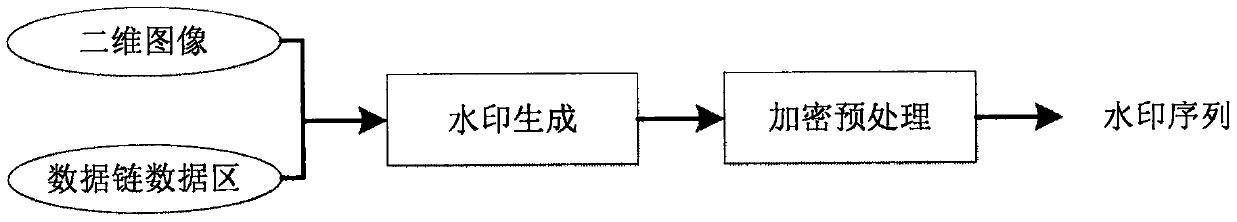
InactiveCN108053359AIntegrity guaranteedPrevent malicious tamperingImage enhancementImage analysisInformation securityDigital watermarking
The invention discloses a block chain embedding method for a wavelet domain watermark in an image. The method comprises the following steps of 1, generating a watermark containing data blocks of a block chain; 2, embedding the generated watermark containing the data blocks of the block chain into the wavelet domain watermark; 3, extracting and verifying the wavelet domain watermark; and 4, updating watermark information in the block chain. According to the block chain embedding method for the wavelet domain watermark in the image, a watermark sequence is generated by utilizing the data blocksof the block chain; a block chain technology is introduced in a digital watermark, so that the security of image information is ensured and the watermark information is prevented from being tampered by any attack means; and by updating the data blocks of the block chain in the watermark, the watermark is not modified at will in a network transmission process, attack in an invalid network is avoided, and the information security in the transmission process is ensured.
Owner:北京泛融科技有限公司
Disk array and its access right control method and device, server and server system
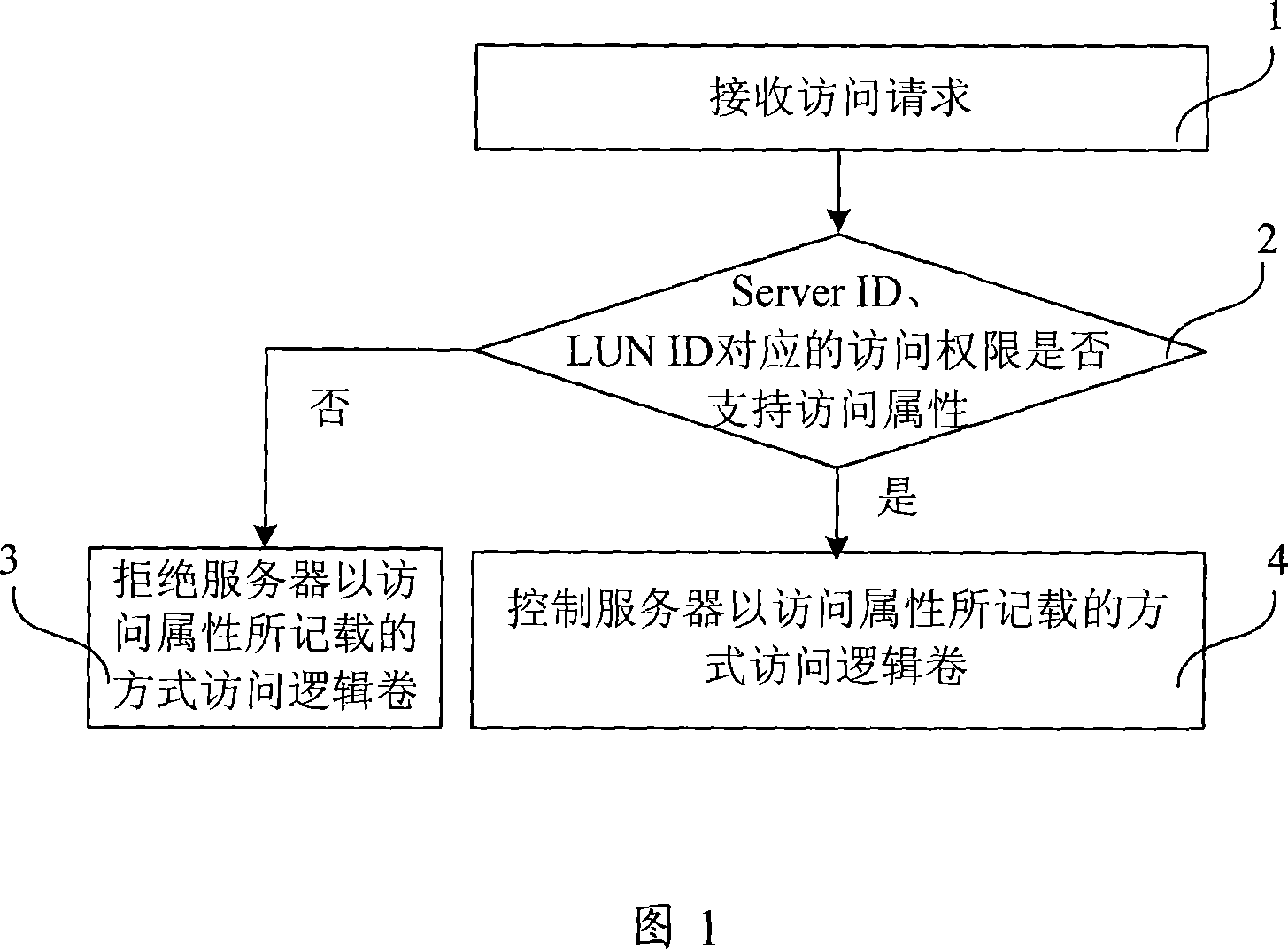
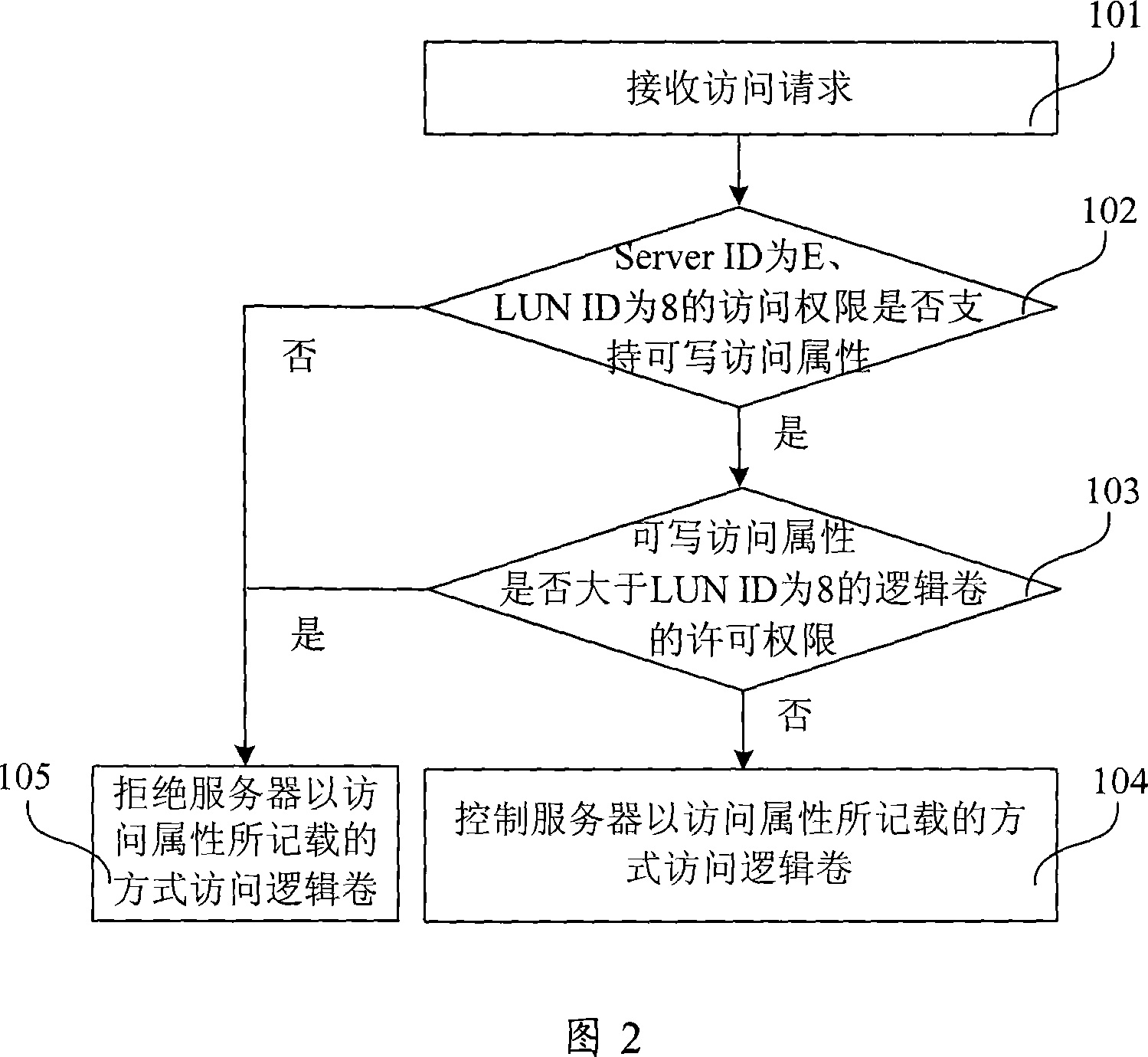
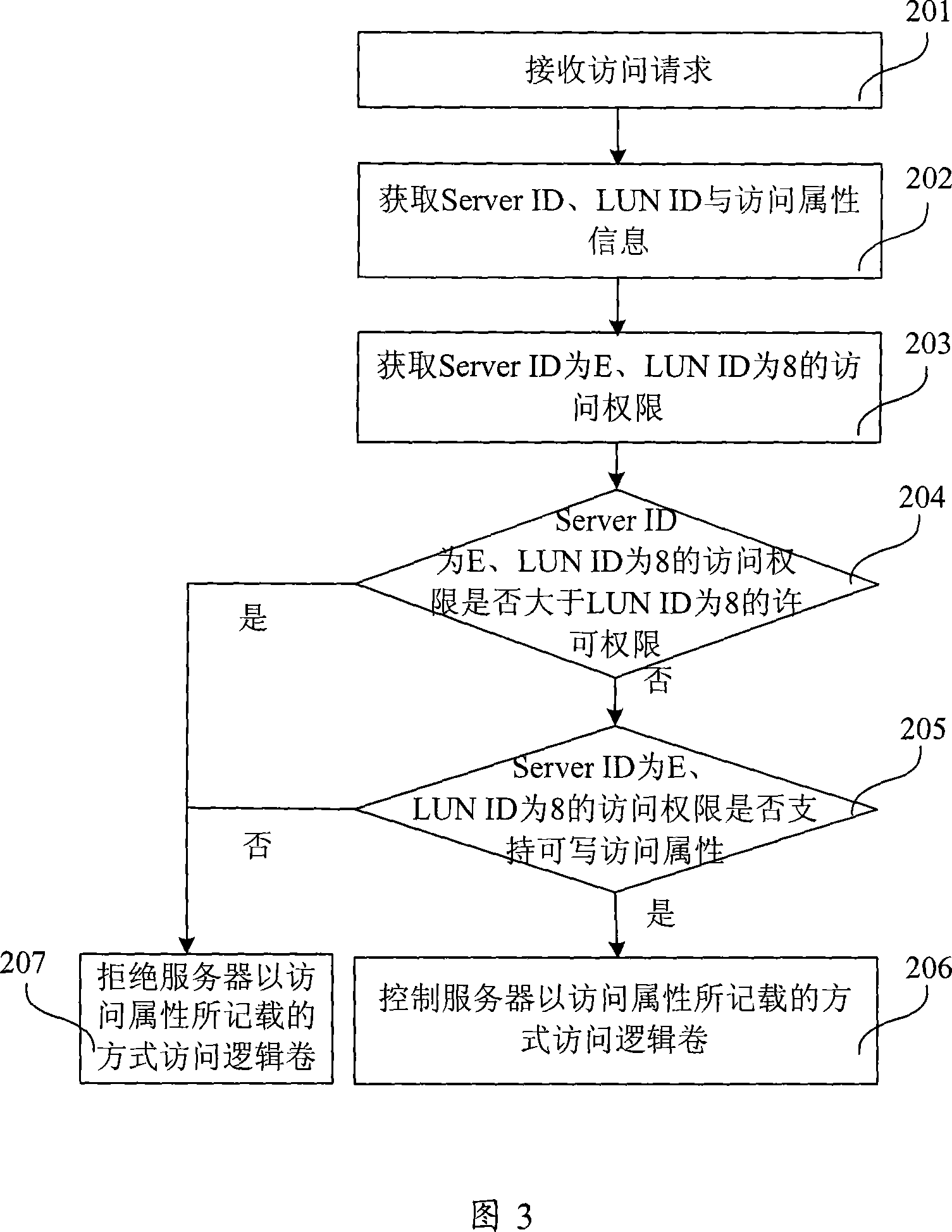
ActiveCN101056175APrevent intrusionPrevent malicious tamperingUser identity/authority verificationDisk arrayAuthority control
The invention provides a disk array and its access authority control method and devices, server and server system, in which, the method includes: the request for the access of logic volume sent by the disk array receiving server, this access request must have the server identifier, logic volume identifier and access attribute; the disk array query indicates the access authority list of logic volumes access authority for the disk array of servers; according to the access authority list, when the access authority corresponding to the server identifier and the logic volume identifier can't support the access attribute, the disk array refuses the server to access the logic volume in the mode recorded in the access attribute. The invention may effectively protect the disk array against the virus intrusion, avoid the malicious juggle of data saved on the disk array by Hacker, thus improve the safety of data on the disk array.
Owner:HUAWEI TECH CO LTD
Verification method of contract data and its network and electronic equipment
PendingCN109472164AImprove securityImprove storage reliabilityFinanceDigital data protectionValidation methodsDependability
The present application discloses a method for verifying contract data and a network and electronic equipment thereof. The method comprises the following steps: the verification node obtains a first digital fingerprint of the target contract data stored in the block chain; Acquiring the target contract data stored by the contract storage node, and calculating a second digital fingerprint using thetarget contract data; Judging whether the first digital fingerprint and the second digital fingerprint are consistent, and if so, determining that the target contract data in the contract storage node has not been tampered with. The scheme can avoid the contract being tampered with maliciously and guarantee the reliability of the contract data.
Owner:YGSOFT INC
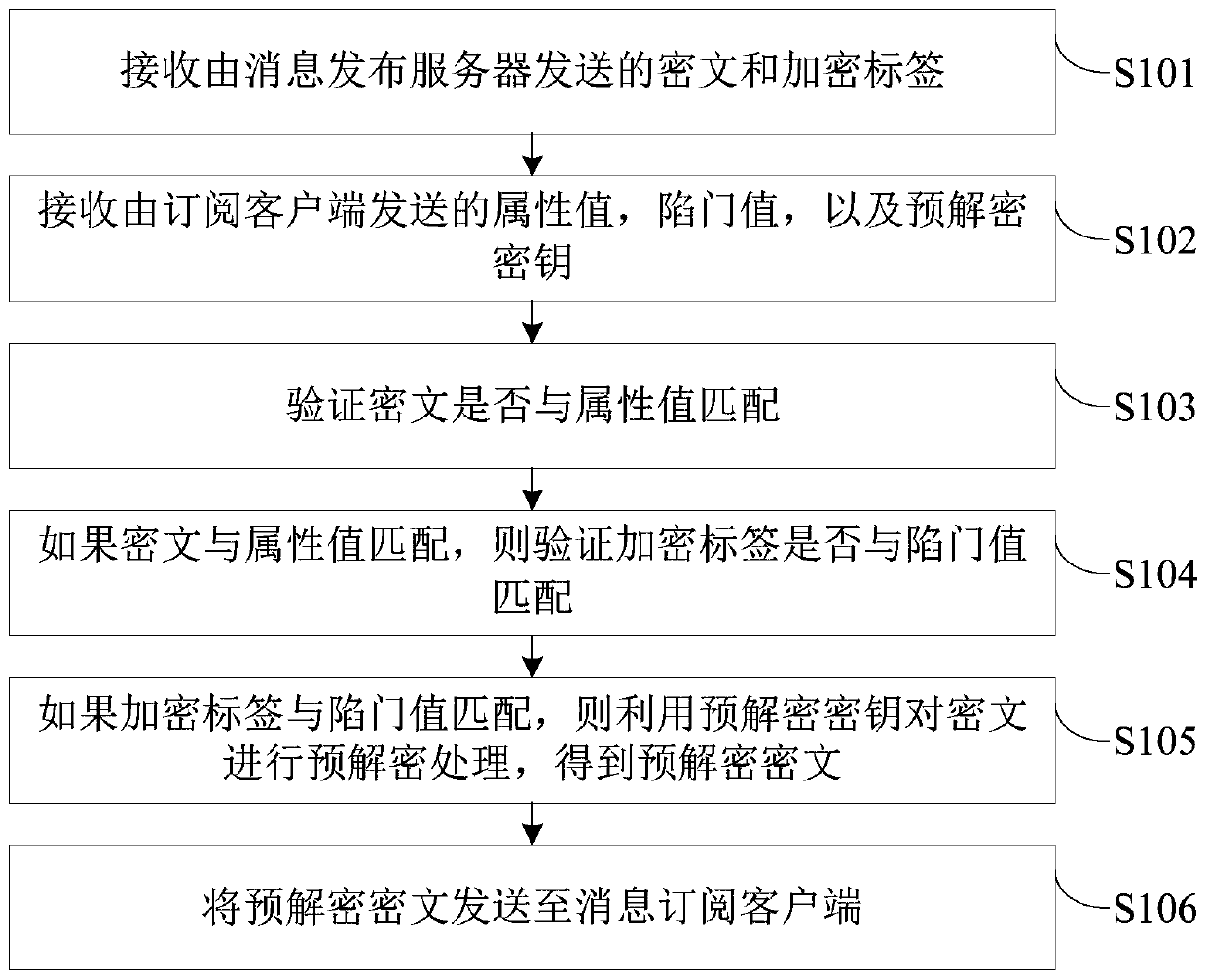
Security publishing and subscribing system and publishing and subscribing method based on block chain technology
ActiveCN109981641AImprove securityPrevent malicious tamperingKey distribution for secure communicationEncryption apparatus with shift registers/memoriesCiphertextClient-side
The embodiment of the invention provides a secure publishing and subscribing system and method based on a block chain technology. The system comprises a key server, a message subscribing client, a message publishing server and a block chain comprising a plurality of block chain nodes, the method comprises the following steps: receiving a ciphertext and an encryption tag sent by a message publishing server; receiving an attribute value, a trap door value and a pre-decryption key sent by the subscription client; verifying whether the ciphertext is matched with the attribute value or not; if yes,verifying whether the encryption tag is matched with the trap door value or not; if so, pre-decrypting the ciphertext by using the pre-decryption key to obtain a pre-decrypted ciphertext; and sendingthe pre-decrypted ciphertext to the message subscription client, so that the message subscription client decrypts to obtain a subscription message. According to the embodiment of the invention, the security of the stored data in the publishing and subscribing system can be improved.
Owner:BEIJING UNIV OF POSTS & TELECOMM
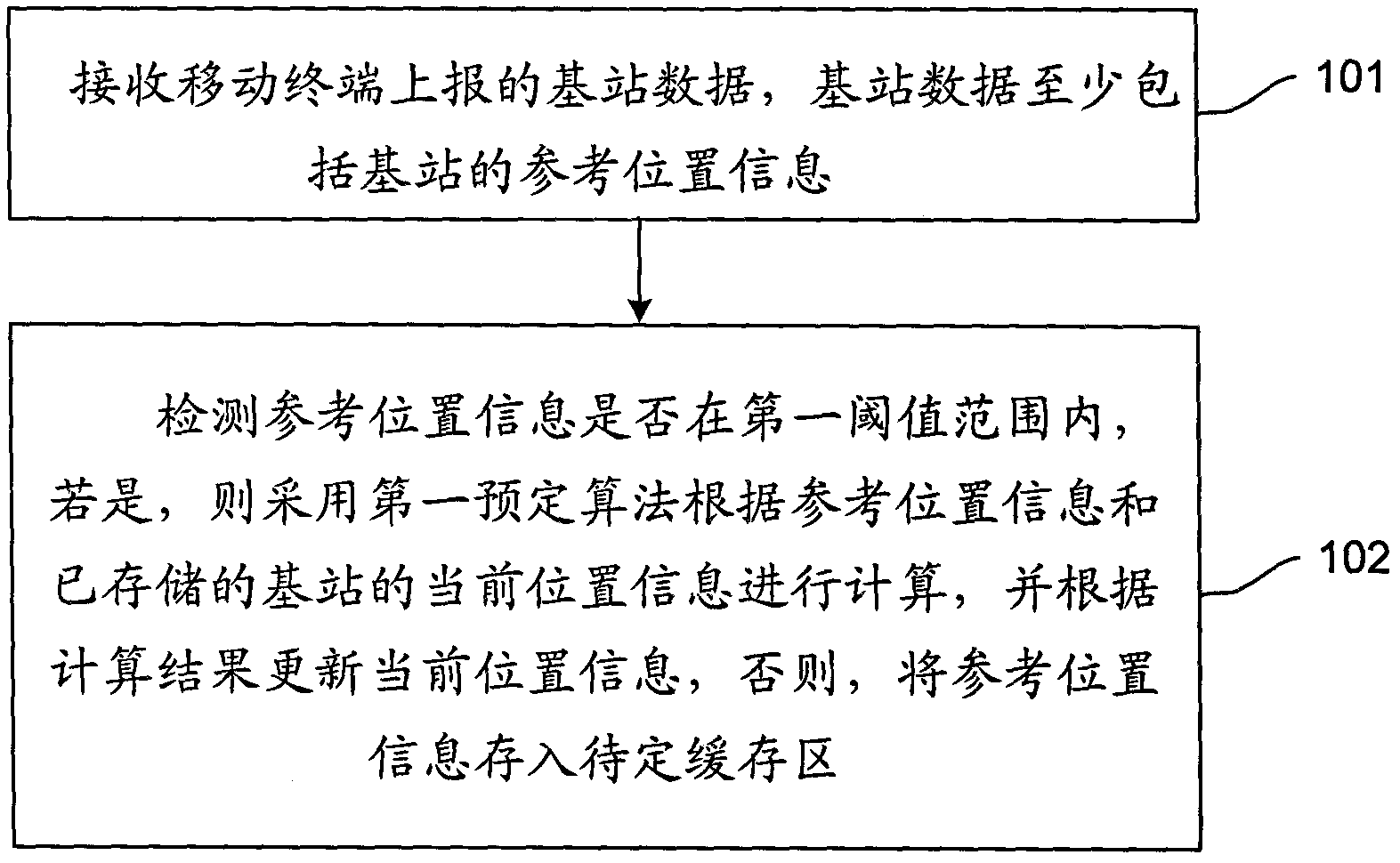
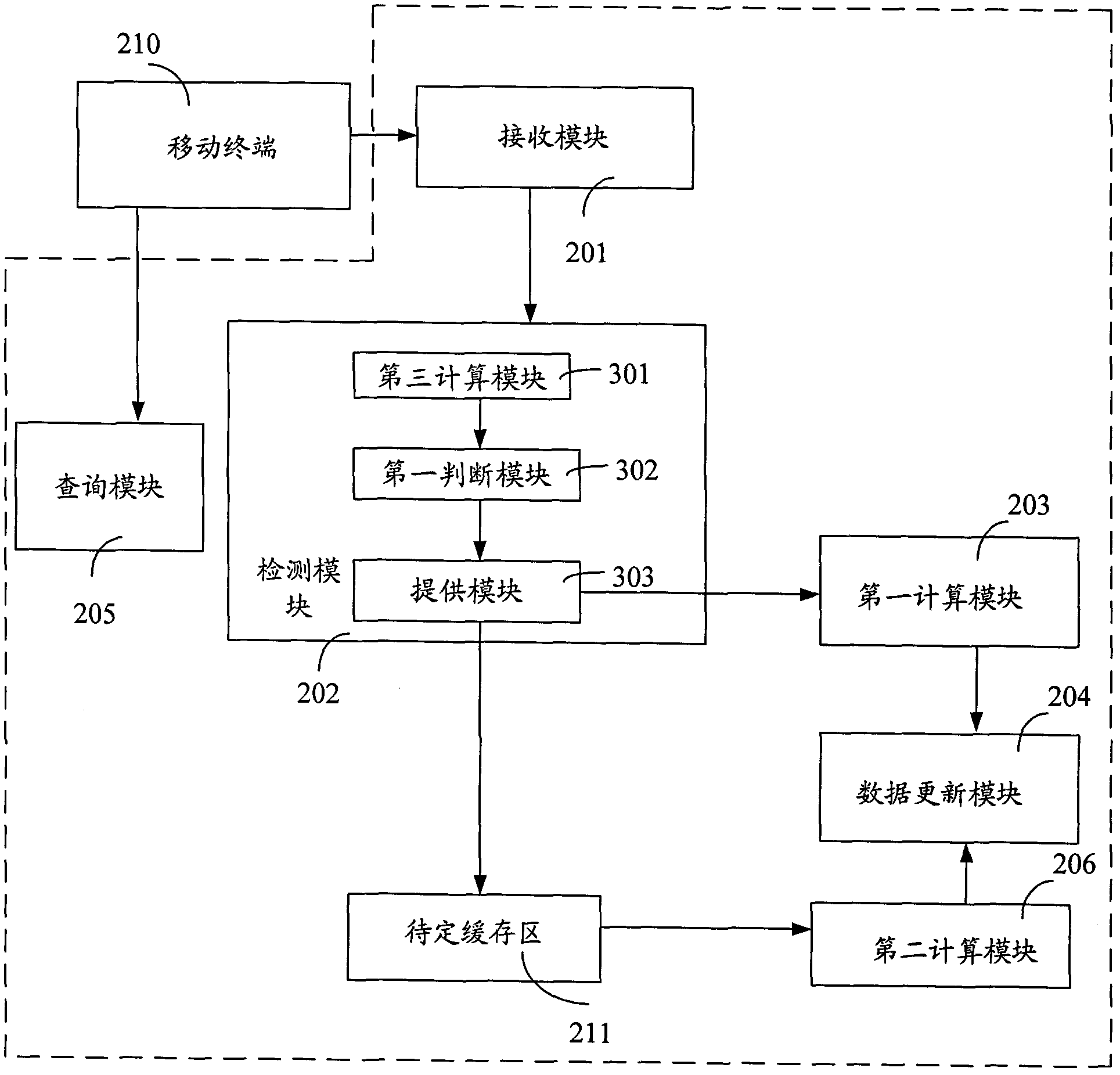
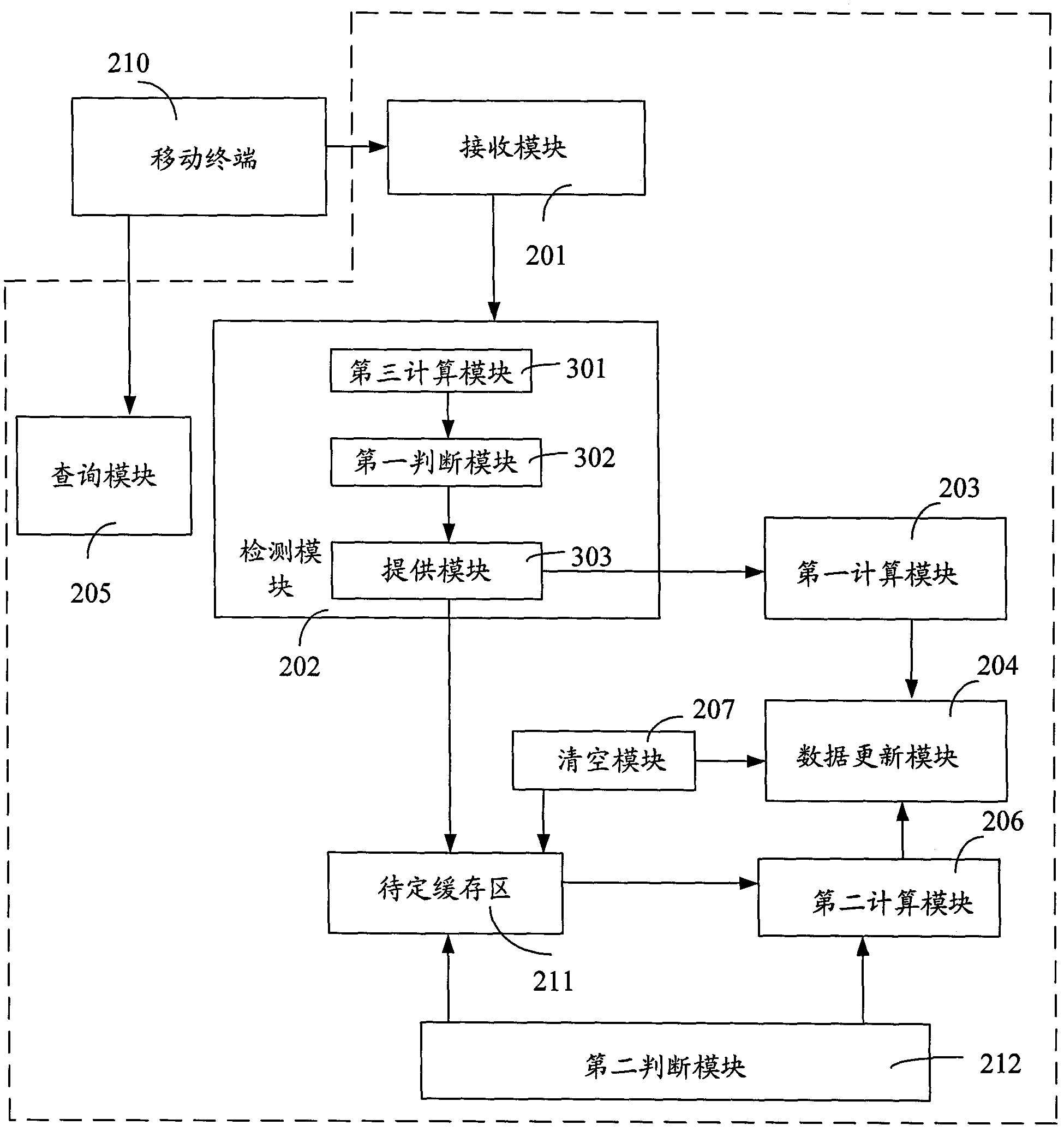
Method and system for updating position of base station
ActiveCN102158844APrevent malicious tamperingNetwork data managementComputer terminalReal-time computing
The invention discloses a method and a system for updating position of a base station. The method comprises the following steps: receiving a base station data reported by a mobile terminal; detecting if the reference position information is in a first threshold scope; if yes, updating the current position information; and if not, storing the reference position information into a to-be-determined cache region. The system comprises a receiving module, a detecting module, a first calculating module and a data updating module, wherein the receiving module is used for receiving the base station data reported by the mobile terminal; the detecting module is used for detecting if the reference position information is in the first threshold scope and supplying the reference position information to the first calculating module or the to-be-determined cache region according to a detection result; the first calculating module is used for calculating by the using of a first predetermining algorithm according to the reference position information and the stored current position information of the base station and supplying a calculation result to the data updating module; and the data updating module is used for updating the current position information according to the acquired calculation result. By the using of the method and system for updating position of base station provided by the invention, the operation of malevolently distorting the position of the base station in the data can be avoided.
Owner:CHINA UNITED NETWORK COMM GRP CO LTD
Image encoding method for preventing and identifying image tamper
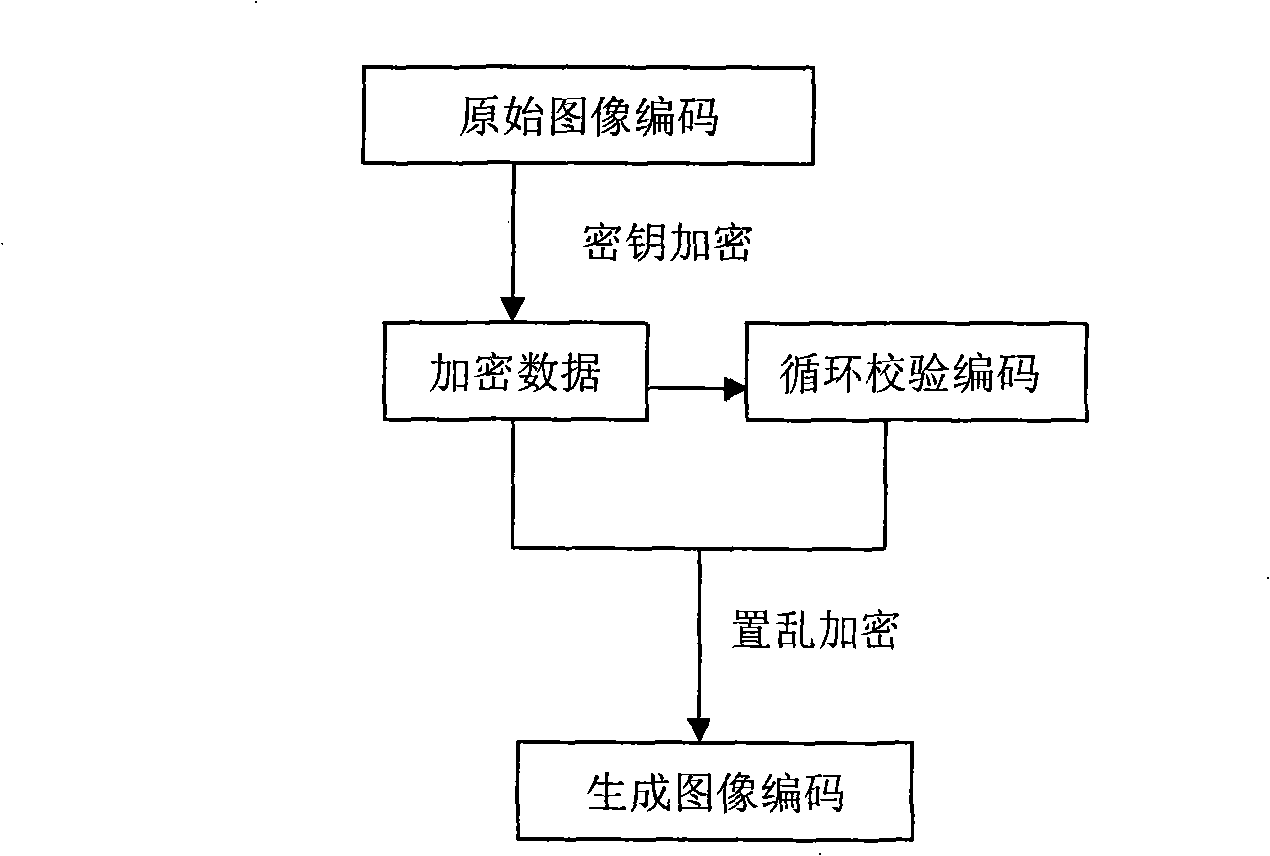
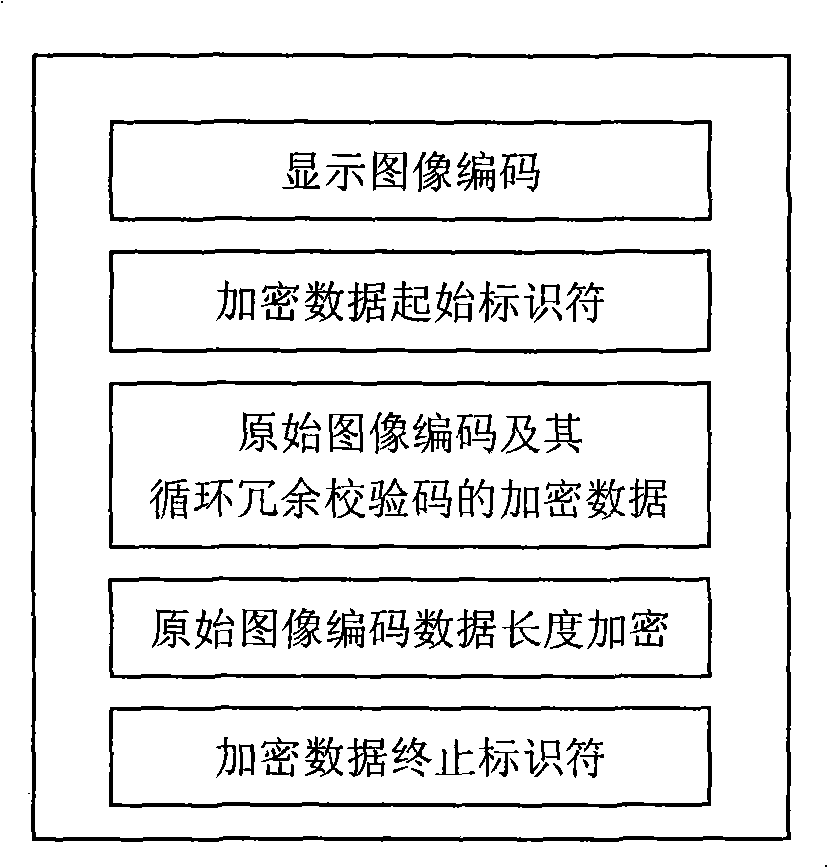
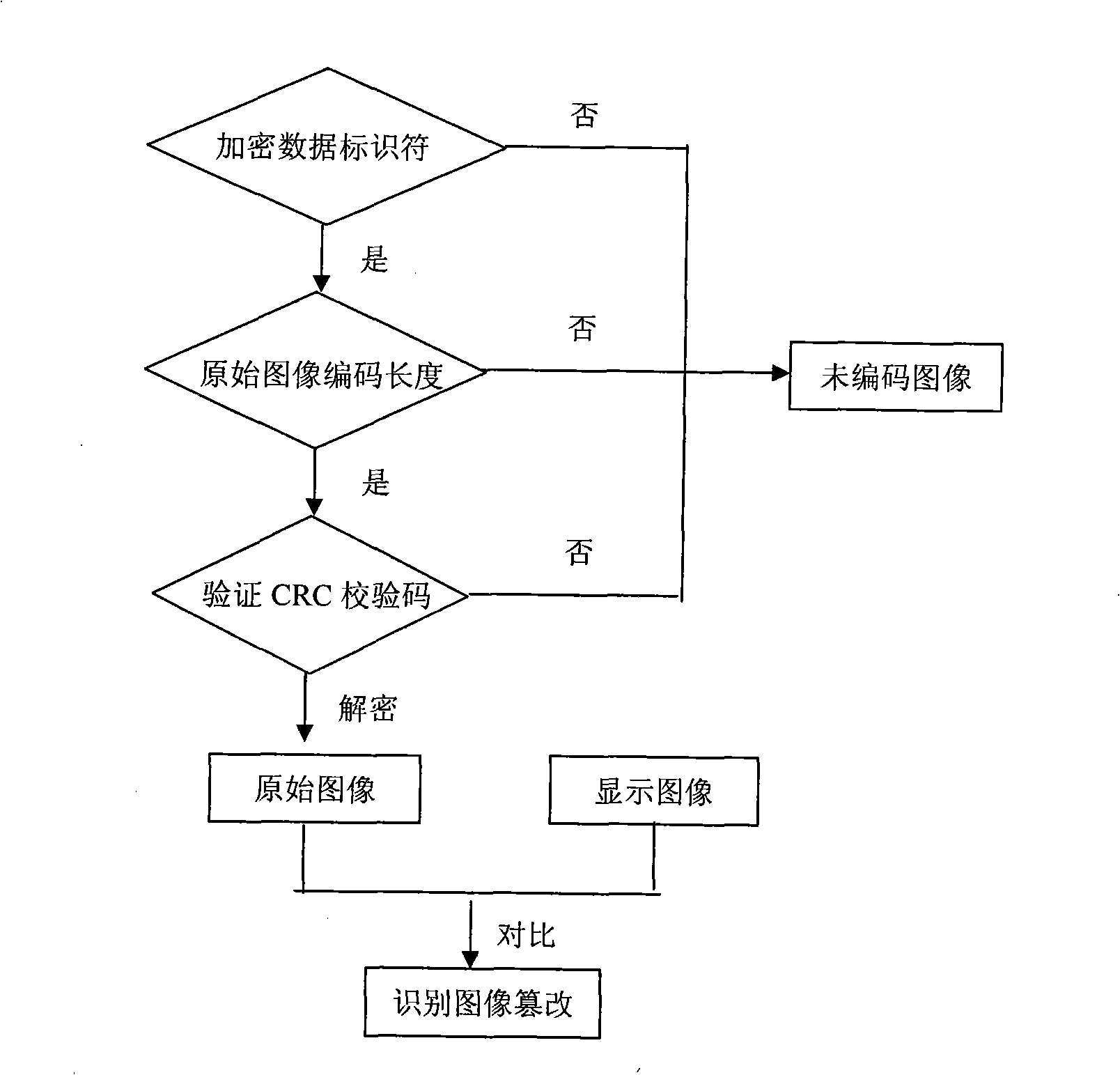
InactiveCN101409813APrevent malicious tamperingGuaranteed authenticity and securityTelevision system detailsColor television detailsImage compressionImage code
The invention discloses an image coding method for preventing and identifying image tampering. The data of original image coding is encrypted by a key and circulating redundancy check coding (CRC) is carried out on the encrypted data; then scrambling encryption is carried out the encrypted data of the original image coding and the circulating redundancy check coding by keys; and then the encrypted data of the original image coding and the circulating redundancy check coding are added to display image coding (non-encrypted image coding), thereby preserving the information of the safe and true original image into the image so as to prevent and identify image tampering, in this way, the coding of one image consists of two parts: the display image coding and the encrypted original image coding; the display image coding can be any form of image compression coding and allows any form of operation on the display image; the original image can be intuitively observed by carrying out decryption on the encrypted original image coding; comparison is carried out on the original image and the display image, thus being capable of intuitively observing the alternation carried out on the original image. The image coding method has the advantage of identifying the image tampering in direct contrast with the original image, thus being convenient for people to judge whether the correction on the image affects the authenticity of the content of the image or not and being capable of accurately resuming the image after tampering to the original image. The image coding method is simple in arithmetic, is easy to realize hardware coding and software coding, can be used for validating the authenticity of court evidence and e-business pictures as well as resuming the tampered image and image steganalysis.
Owner:陈诚
Method and device for reinforcing application program
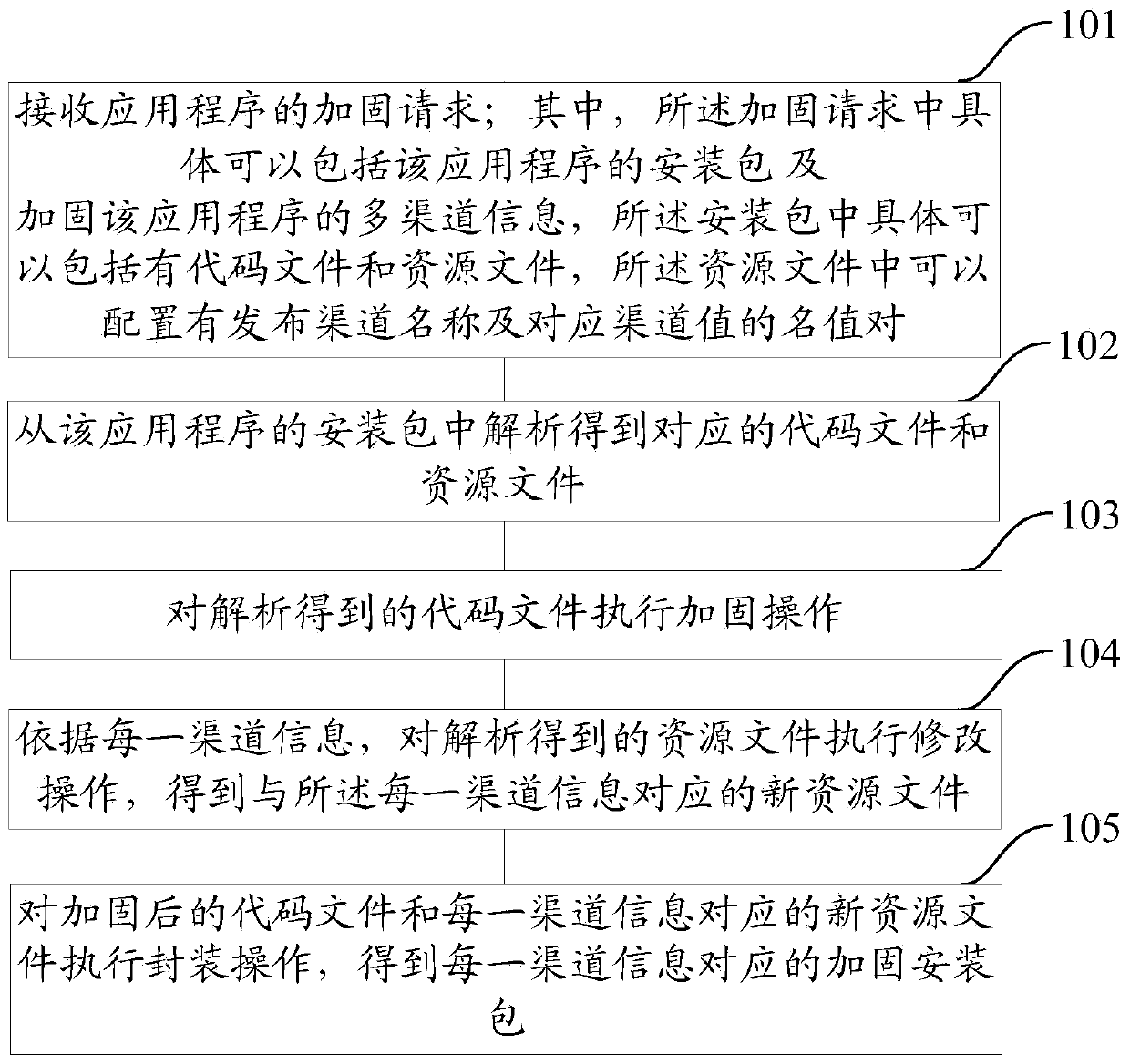
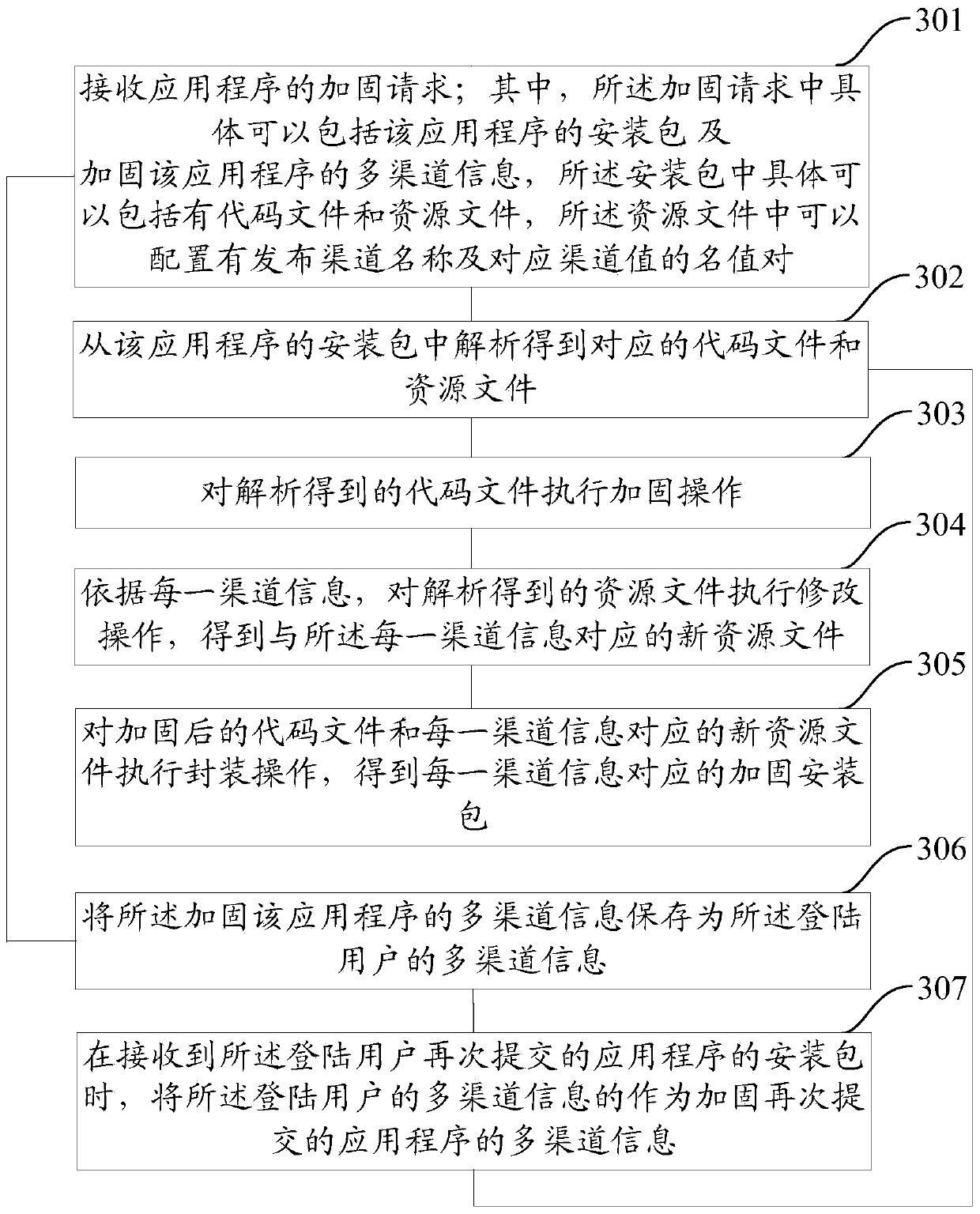
ActiveCN104217140AImprove securityPrevent decompilationProgram/content distribution protectionOperating systemResource file
The embodiment of the invention provides a method and a device for reinforcing an application program. The method comprises the following steps of receiving a reinforcing request of the application program, wherein the reinforcing request comprises an installation package of the application program and multi-channel information for reinforcing the application program, the installation package comprises code files and resource files, and release channel names and corresponding channel values are configured in the resource files; analyzing to obtain corresponding code files and resource files from the installation package of the application program; executing reinforcing operation on the code files obtained through analysis; executing retouching operation on the resource files obtained through analysis according to each piece of channel information to obtain a new resource file corresponding to each piece of channel information; executing packaging operation on the reinforced code files and the new resource file corresponding to each piece of channel information to obtain a reinforced installation package corresponding to each piece of channel information. According to the method and the device, the safety of the application program can be improved and the efficiency of reinforcing multiple release channels is improved.
Owner:BEIJING QIHOO TECH CO LTD
Internet of ships intelligent shore-based interaction device based on Beidou
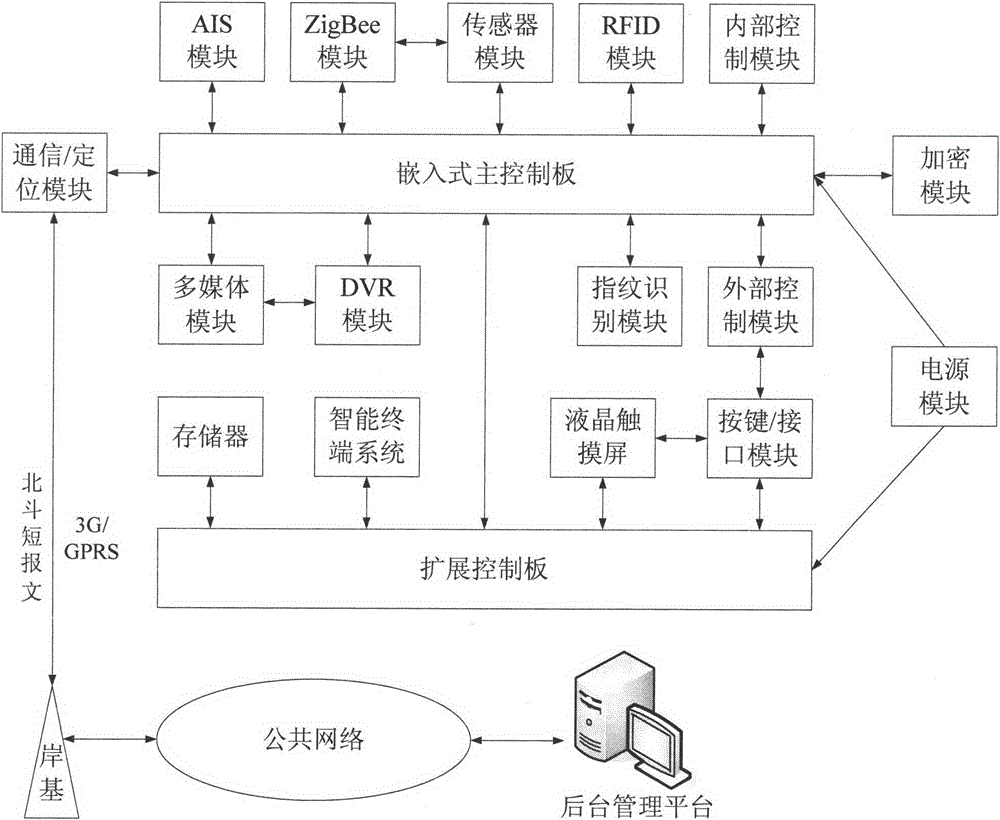
ActiveCN104933897ASimple internal structureLow failure rateTransmission systemsMarine craft traffic controlThe InternetInteraction device
The invention discloses an Internet of ships intelligent shore-based interaction device based on Beidou, and the device comprises an embedded-type main control board, an extended control board, a communication / positioning module, an AIS module, a ZigBee module, a sensor module, an RFID module, an internal control module, an encryption module, a power module, an external control module, a fingerprint recognition module, a DVR module, a multimedia module, a storage unit, an intelligent terminal system, a liquid crystal touch screen, and an interface module. The embedded-type main control board is connected with the extended control board. The power module is connected with the main control board and the extended control board. The communication / positioning module achieves interaction with shore-based equipment through a Beidou message or a 3G / GPRS signal. The device employs the technology of multimode positioning, the technology of sensing, the technology of wireless networking communication and the technology of safety encryption, achieves a function of inland river gate report, a function of visualized emergency command scheduling and a function of shipping electronic business, and prompts the building and development of inland river Internet of ships.
Owner:林兴志
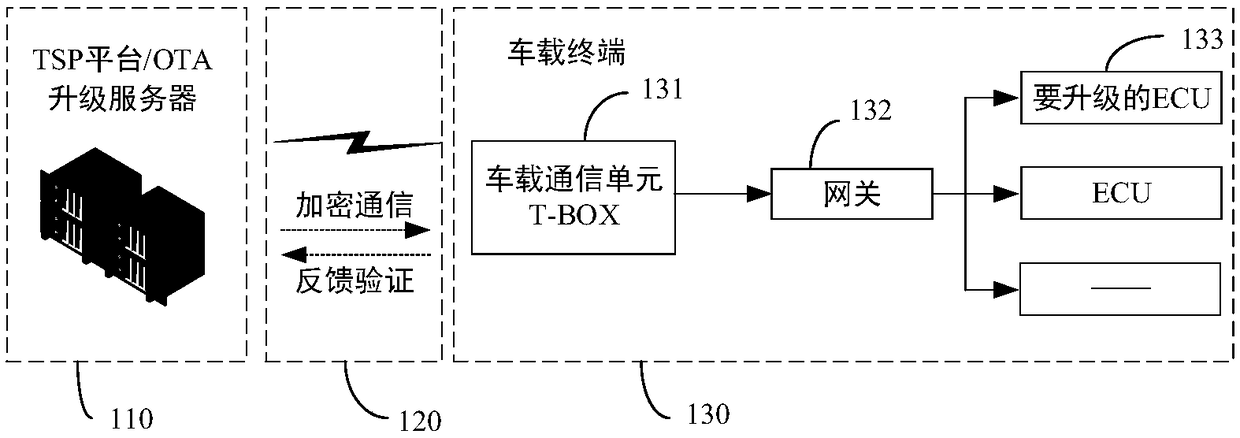
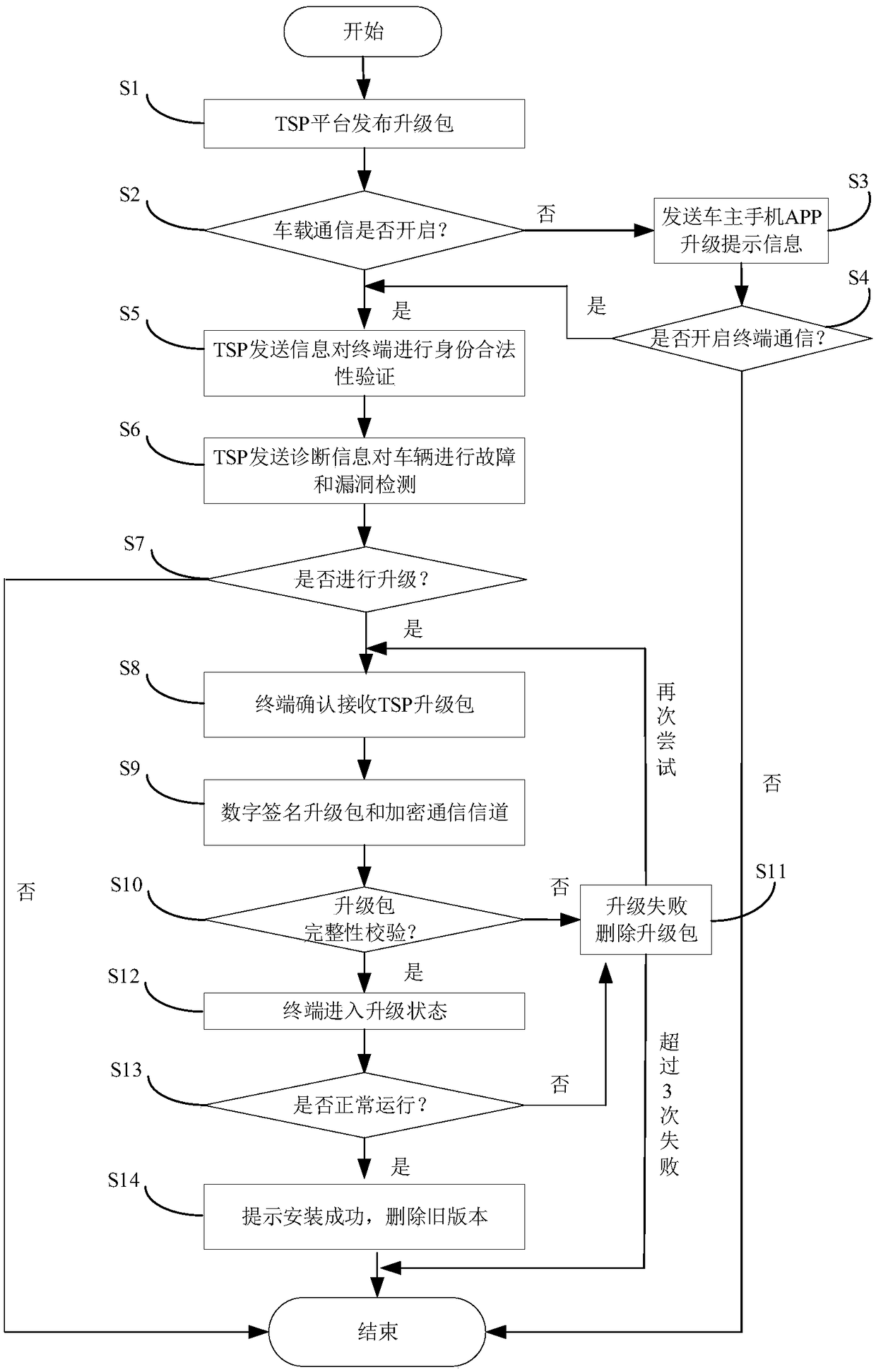
Working method of server, vehicle terminal upgrading method and vehicle terminal upgrading system
InactiveCN108923933APrevent malicious tamperingPrevent illegal intrusionUser identity/authority verificationSecure transmissionComputer module
The invention provides a working method of a server, and the working method comprises the following steps: the server issues an upgrading package; the server judges whether a communication channel ofa vehicle terminal is turned on; if the communication channel of the vehicle terminal is turned on, the server encrypts the upgrading package, and transmits the encrypted upgrading package to the vehicle terminal through the communication channel by a secure transmission mode. According to the method provided by the invention, by functions of an encrypted communication module and a feedback verification module, malicious tampering to the upgrading package or an installation package caused by illegal attacking is avoided, consequently, illegal invasion of the tampered upgrading package to the vehicle terminal, a power control unit, a vehicle owner personal privacy, an information entertainment system, and so on, can be avoided, a problem of existence of hidden security danger in a remote upgrading process of motor vehicles is eliminated, and security and reliability of downloading the upgrading package over the air is guaranteed.
Owner:BEIHANG UNIV
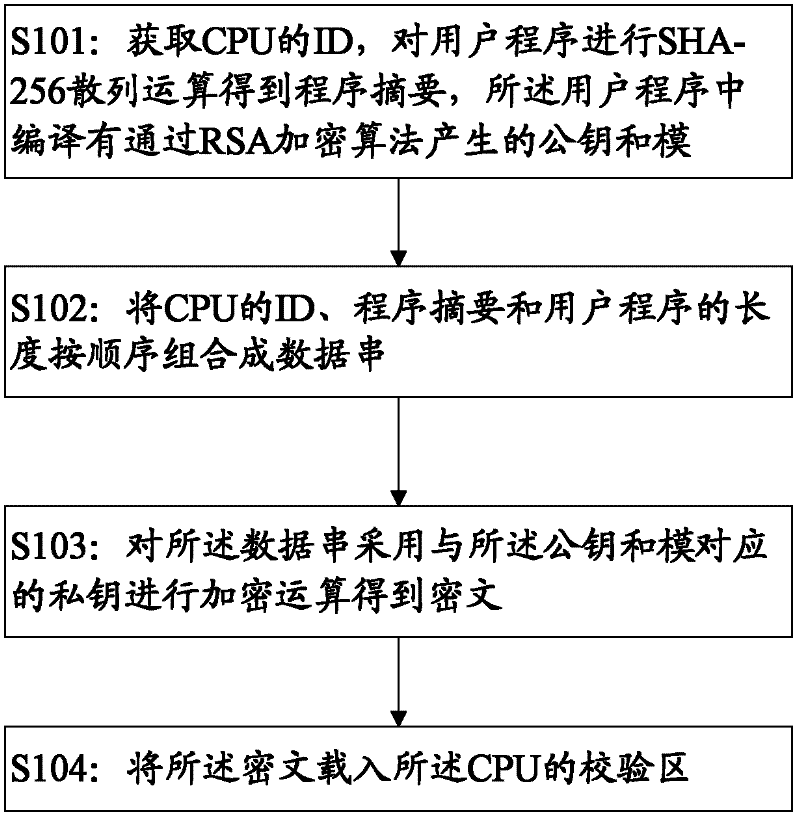
Method and device for signing user program and method and device for verifying signature of user program
ActiveCN102609665AReduce the risk of being brute-forcedPrevent malicious tamperingDigital data protectionProgram/content distribution protectionCiphertextBrute-force attack
The invention discloses a method and a device for signing a user program verifying signature of the user program. The method for signing the user program includes steps of acquiring ID (identity) of a CPU (central processing unit), computing the user program by SHA-256 hash operation to obtain a program digest, compiling a public key and a module generated through RSA (Ron Rivest,Adi Shamirh and Len Adleman) encryption algorithm into the user program; combining the ID of the CPU, the program digest and the length of the user program in sequence to form a data string; operating the data string by a private key corresponding to the public key and the module to obtain ciphertext; and loading the ciphertext into a check area of the CPU. By combining with the RSA algorithm and the SHA algorithm to process the user program and integrating with the ID of the CPU to be a part of the signature, the user program must be restarted by being strictly subjected to the signature verifying process matched with the signature, risk in brute force attack to the user program is greatly reduced, and the user program can be effectively protected from being tampered or stolen maliciously.
Owner:恒鸿达科技有限公司
Server log monitoring method and system based on block chain
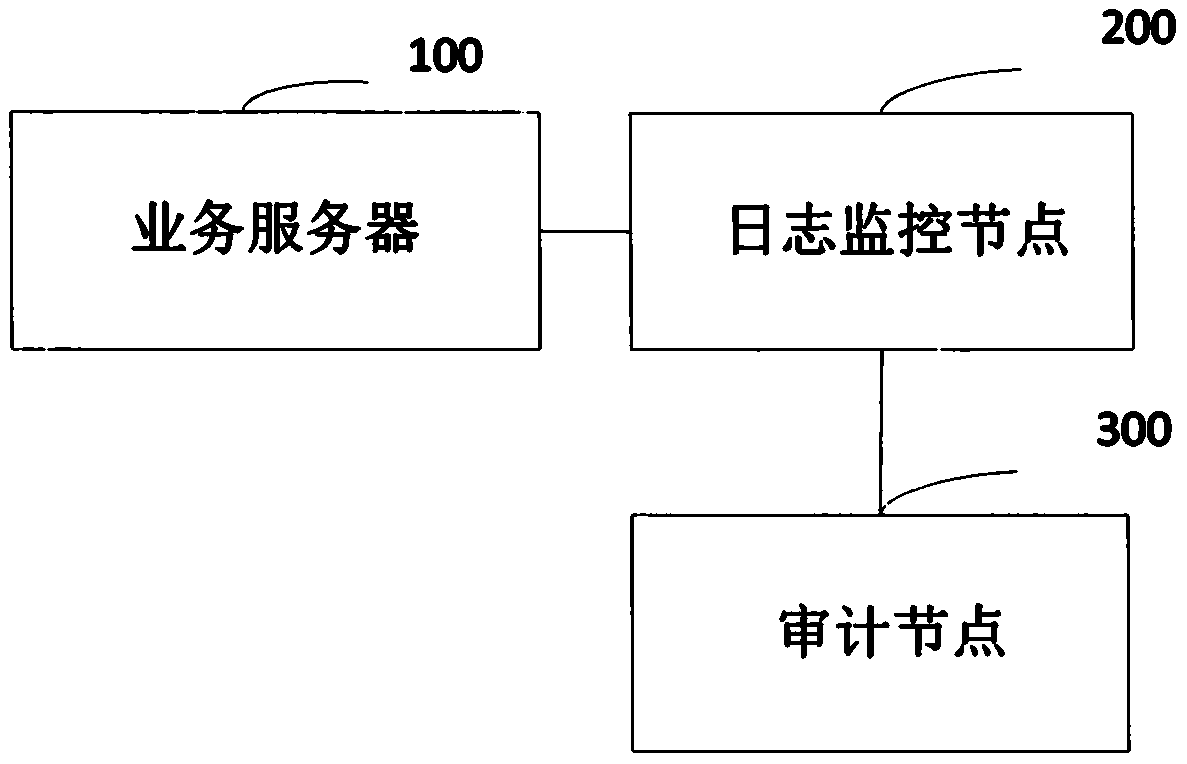
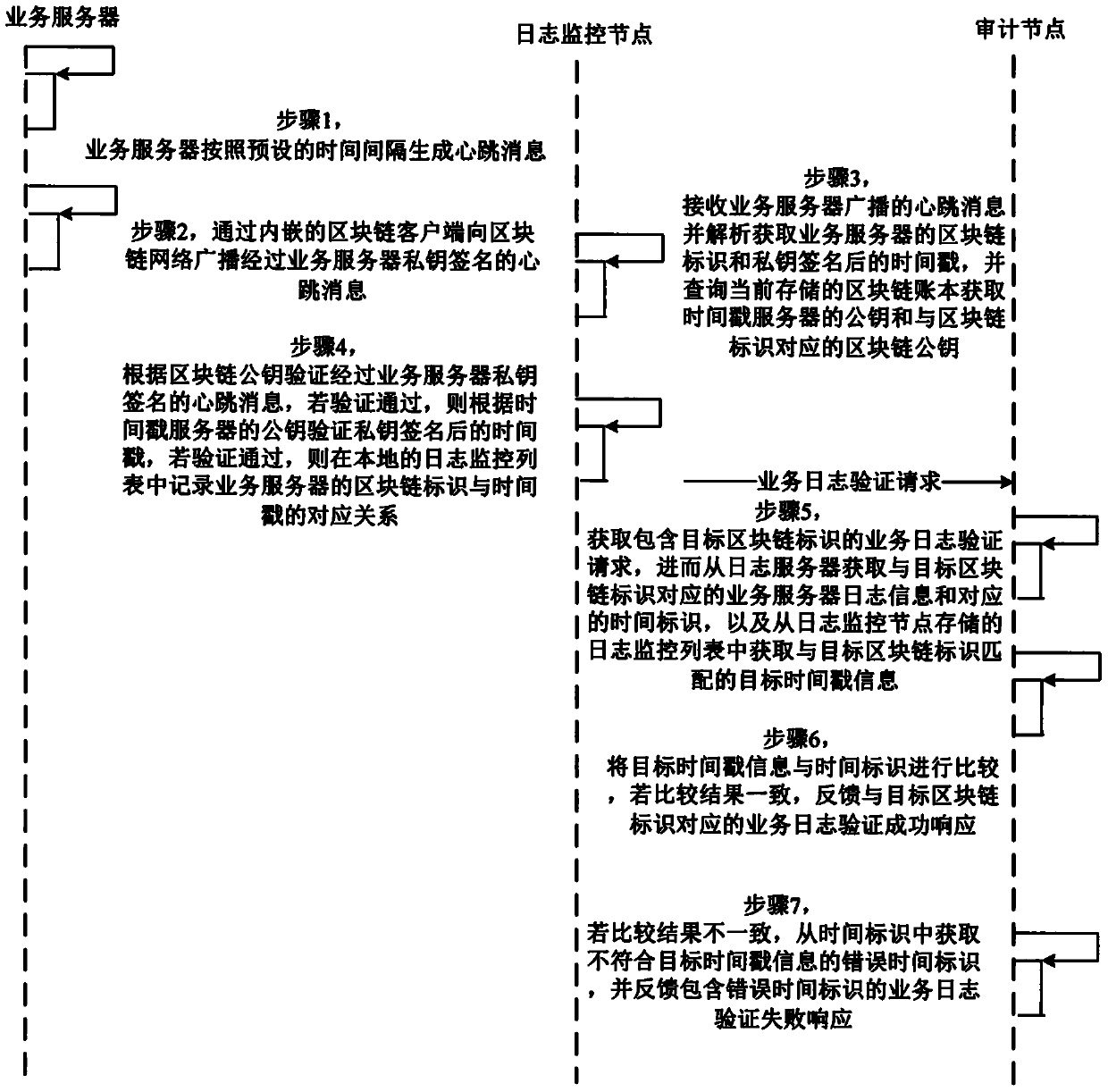
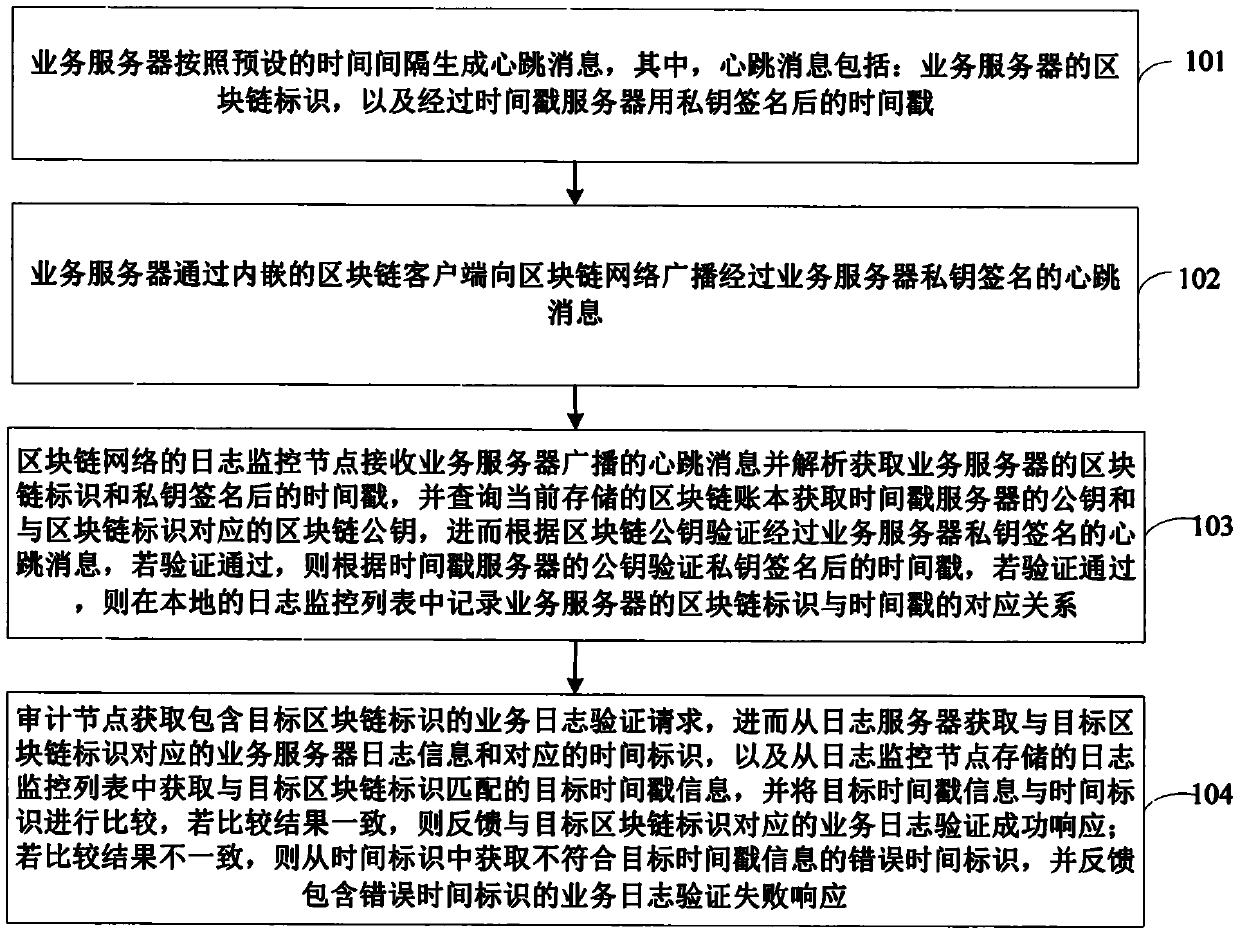
ActiveCN110049043APrevent malicious tamperingQuick recovery jobUser identity/authority verificationData switching networksServer logTime information
The invention provides a server log monitoring method and system based on a block chain, and the method comprises the steps that a service server generates a heartbeat message and broadcasts the heartbeat message signed by a private key of the service server to a block chain network; the log monitoring node of the block chain network receives the heartbeat message broadcasted by the service serverto verify the legality of the heartbeat message; and if the heartbeat message is legal, that the service server is online is determined, then a time mark corresponding to the service server is obtained by the auditing node, and the authenticity of the log information stored in the service server is detected based on the consistency of the time mark and the timestamp in the service server. Therefore, on one hand, the business server which is separated from control is found in time so as to recover the business server quickly, and on the other hand, the time information of the log is stored based on the decentralization mode, malicious tampering of the log is avoided, real-time log tampering risk monitoring is realized, and the security of the system is protected.
Owner:江苏全链通信息科技有限公司
Information sequence building method and system thereof
InactiveCN108471379APublish flexiblePost beautifulData processing applicationsData switching networksCommunications systemComputer science
The invention provides an information sequence building method and a system thereof, and belongs to the information sequence building field. The system comprises a publishing platform and an instant communication system. The publishing platform is used for editing, storage, calculation, and statistics of published information, and is used to transmit the edited information to the instant communication system. The instant communication system is used for the information sequence building. By setting the sequence building information in a collective and unified way, and counting the sequence building information, the sequence building information can be counted in a better way, and information of participants can be queried, and at the same time, the defect of the traditional sequence building can be solved, and a good popularization value is provided.
Owner:广西中科万宏信息科技有限责任公司
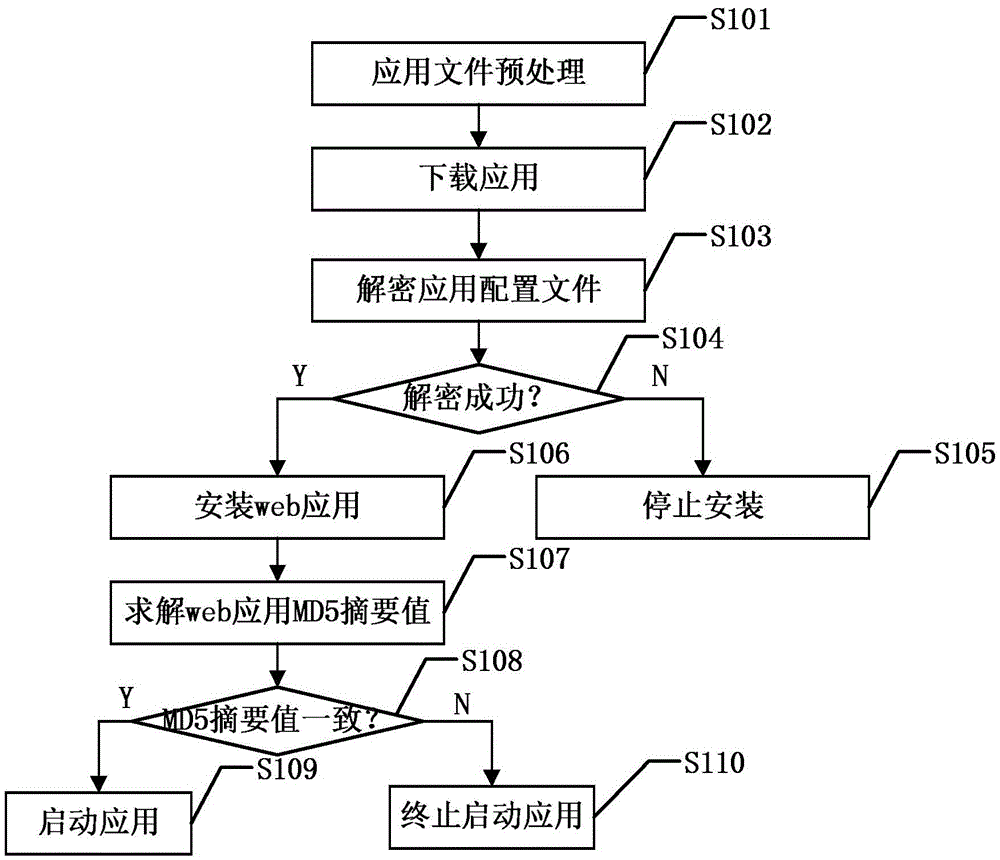
Method for guaranteeing security of source of web application in mobile terminal
InactiveCN105554091APrevent phishing malicious behaviorPrevent malicious tamperingPlatform integrity maintainanceTransmissionApplication serverSource code file
The invention discloses a method for guaranteeing the security of the source of a web application in a mobile terminal. The method includes the following steps that: as for a web application stored on an application server, encryption processing is performed on a configuration file, the MD5 abstract value of a source code file is solve and is stored, and the web application and the MD5 abstract value are downloaded through the mobile terminal; the configuration file is decrypted, if the configuration file is successfully decrypted, the web application is installed; after the web application is installed, every time a user starts the web application, MD5 abstract value solving is performed on the source code file, an obtained MD5 abstract value is compared with the downloaded MD5 abstract value, if the obtained MD5 abstract value is consistent with the downloaded MD5 abstract value, the application is started, otherwise, the application is not started. According to the method of the invention, the configuration file of the web application is encrypted, so that malicious behavior of network phishing can be prevented; when the application is started, the obtained MD5 abstract value is compared with the downloaded MD5 abstract value, so that the source code file of the web application can be prevented from being maliciously tampered; and therefore, the security of the source of the web application in the mobile terminal can be guaranteed.
Owner:UNIV OF ELECTRONICS SCI & TECH OF CHINA
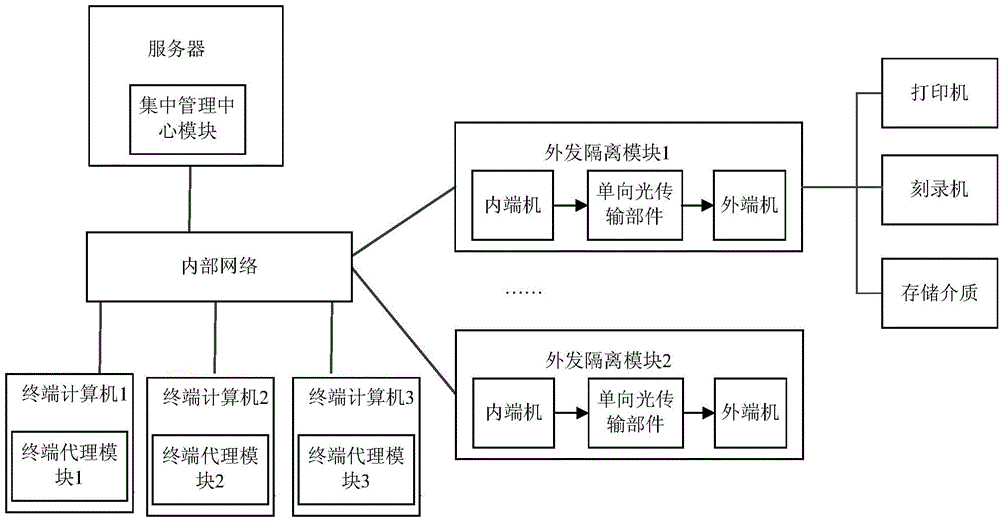
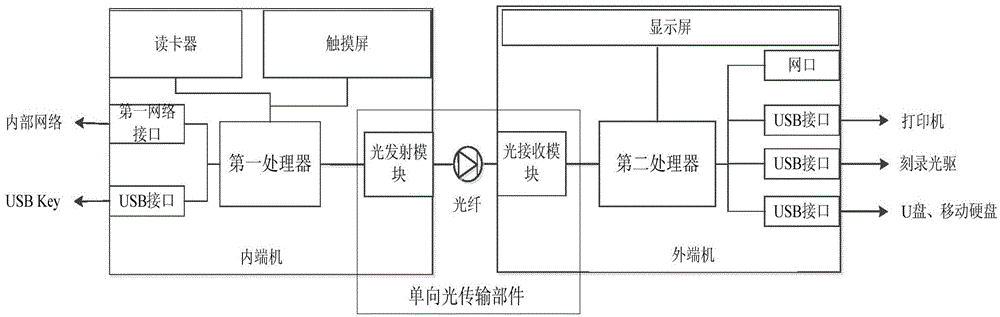
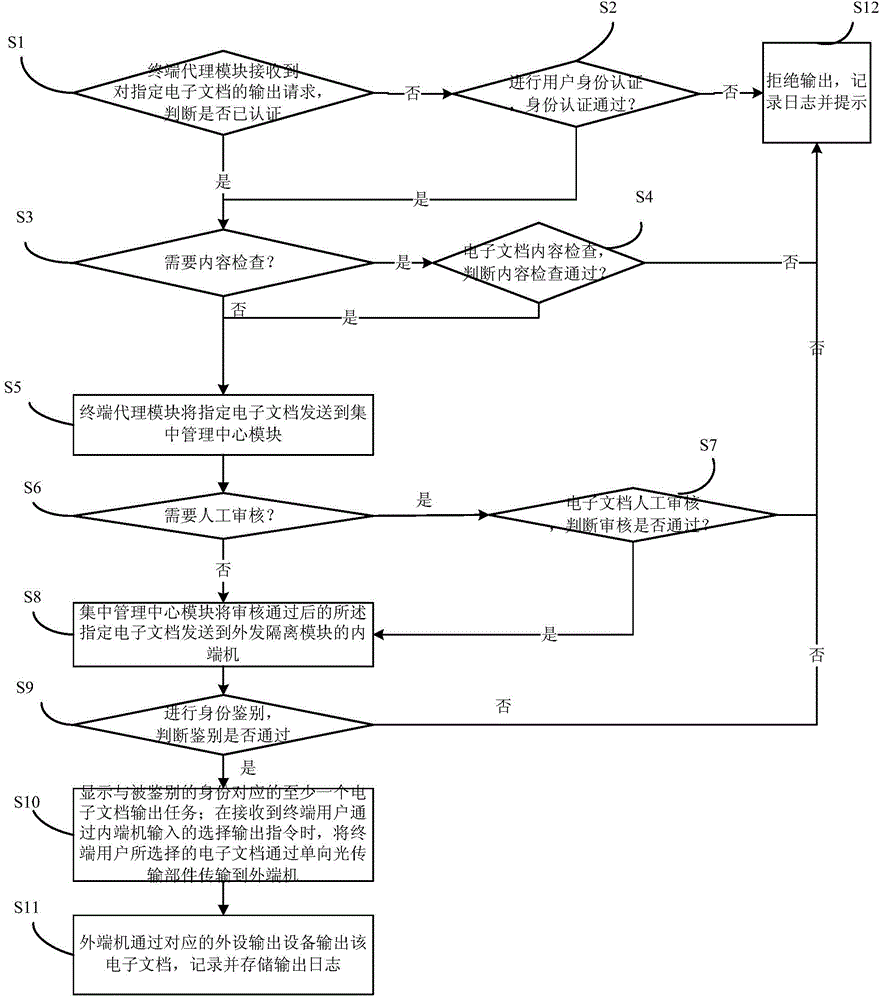
Unidirectional transmission based electronic document output management and control system and method
ActiveCN104579626AEffective isolationAvoid accessDigital data protectionPlatform integrity maintainanceElectronic documentControl system
The invention provides a unidirectional transmission based electronic document output management and control system and method. The system comprises a terminal proxy module, a centralized management center module and an outgoing isolation module, wherein both-way communication is performed between the terminal proxy module and the centralized management center module and between the centralized management center module and the outgoing isolation module. The system has the following advantages: (1) through the unidirectional transmission technology, an in-house network is connected with peripheral output device through the outgoing isolation module, so that unidirectional output of an electronic document can be ensured, and effective isolation between peripheral output risk devices such as a printer and the sensitive in-house network is realized; (2) safe identity authentication ensures credibility of an outgoing source of the electronic document, security check ensures content controllability and manageability of the outgoing electronic document, and execution of a security policy ensures that only authorized electronic document can be sent outward; (3) multiple output modes such as printing output, optical disk burning output, storage medium output and the like are supported, and the system can be widely applied to various security output occasions of the electronic document.
Owner:ZHONGTIE XINAN BEIJING INFORMATION SECURITY TECH
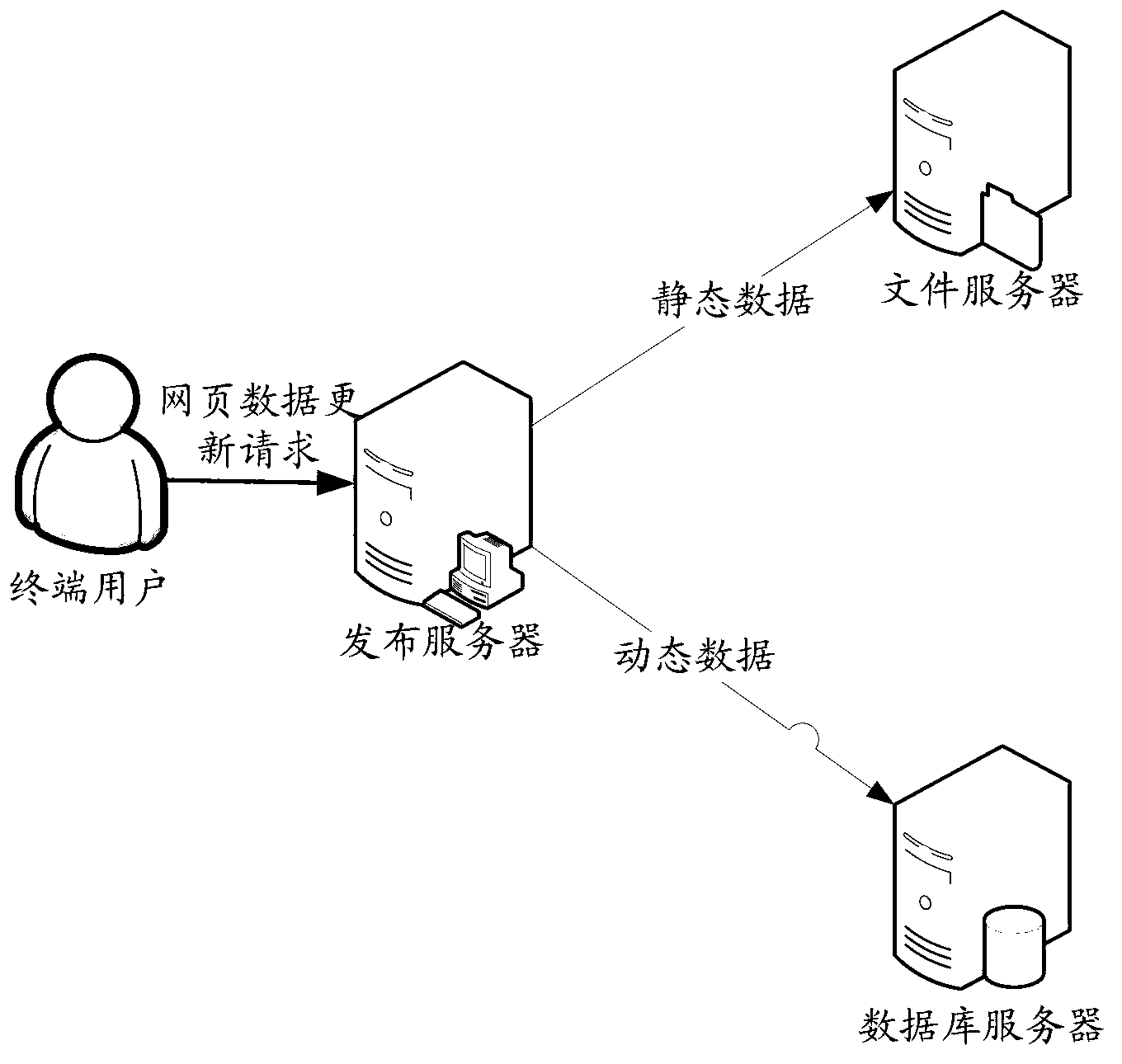
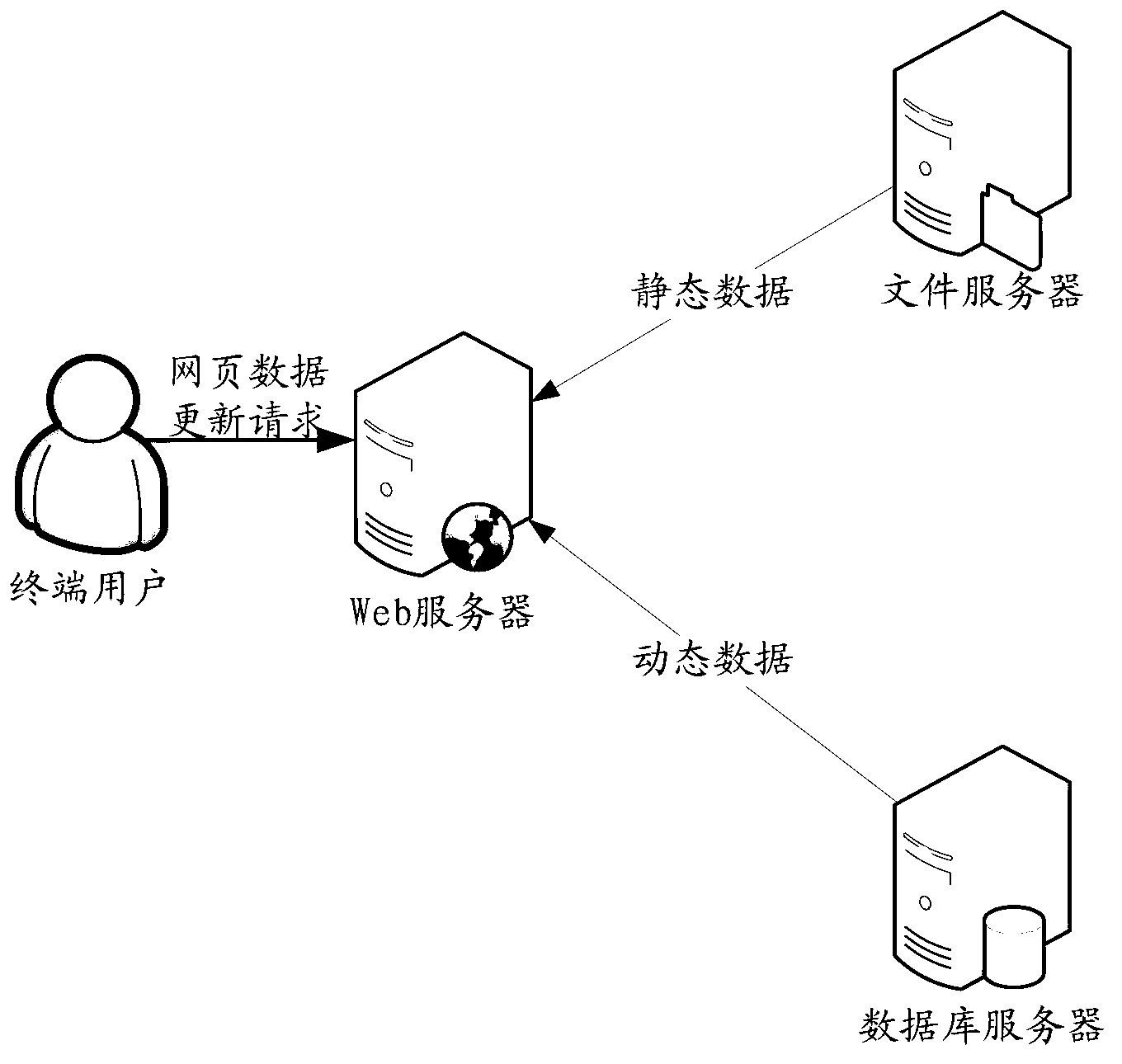
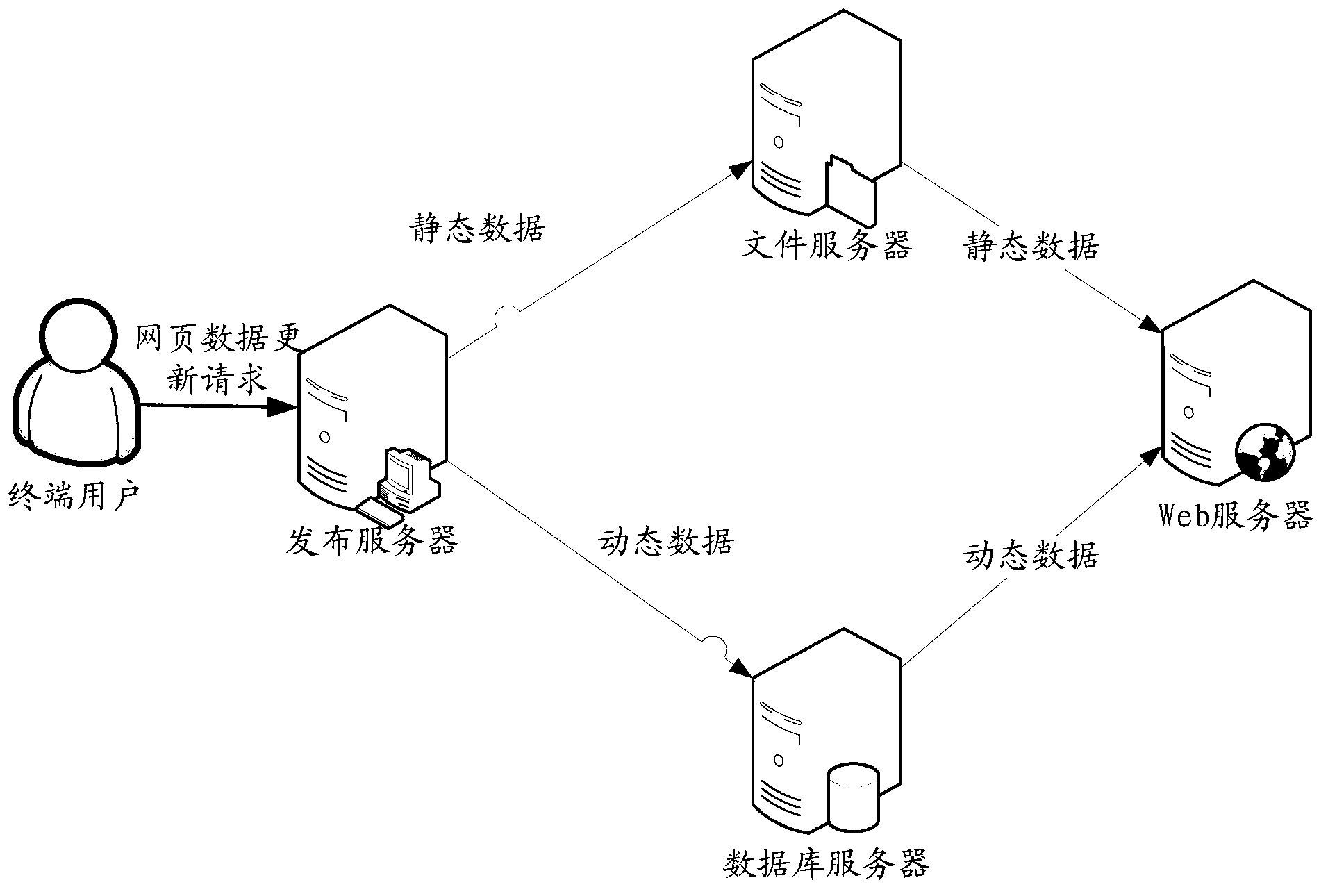
Method, system and device for preventing webpage from being tampered with
ActiveCN103310160APrevent malicious tamperingImprove securityUser identity/authority verificationDigital data protectionSQLDatabase server
The invention discloses a method, a system and a device for preventing a webpage from being tampered with. The method, the system and the device can authenticate webpage data effectively and improve the safety of the webpage data. The method comprises the steps of receiving a webpage data updating request from a terminal user, when the webpage data updating request is to request to update static data, signing the updated static data with a key, and transmitting to a file server in a network system, and / or when the webpage data updating request is to request to update dynamic data, signing values of fields in an SQL (Structured Query Language) for updating the dynamic data with the key and transmitting to a database server in the network system, and executing the SQL to update the dynamic data when the database server determines that signatures of the values of the fields in the SQL are valid.
Owner:NSFOCUS INFORMATION TECHNOLOGY CO LTD +1
Storage method for power purchase and sale contract and network and electronic device thereof
PendingCN109491965AImprove securityEnsure safetyData processing applicationsDigital data protectionElectricitySmart contract
The present application discloses a storage method for a power purchase and sale contract, a network and an electronic device thereof. The method comprises the following steps: a contract management node sends a first storage request after a purchase and sale power contract is signed, wherein the first storage request is used for requesting to store a digital fingerprint of the purchase and sale power contract data, and the digital fingerprint of the purchase and sale power contract data is generated based on the content of the purchase and sale power contract data; the block chain accountingnode receives the first storage request and stores a digital fingerprint of the purchase and sale contract data in the block chain. The scheme can avoid malicious tampering with the power purchase andsale contract and guarantee the reliability of the power purchase and sale contract.
Owner:YGSOFT INC
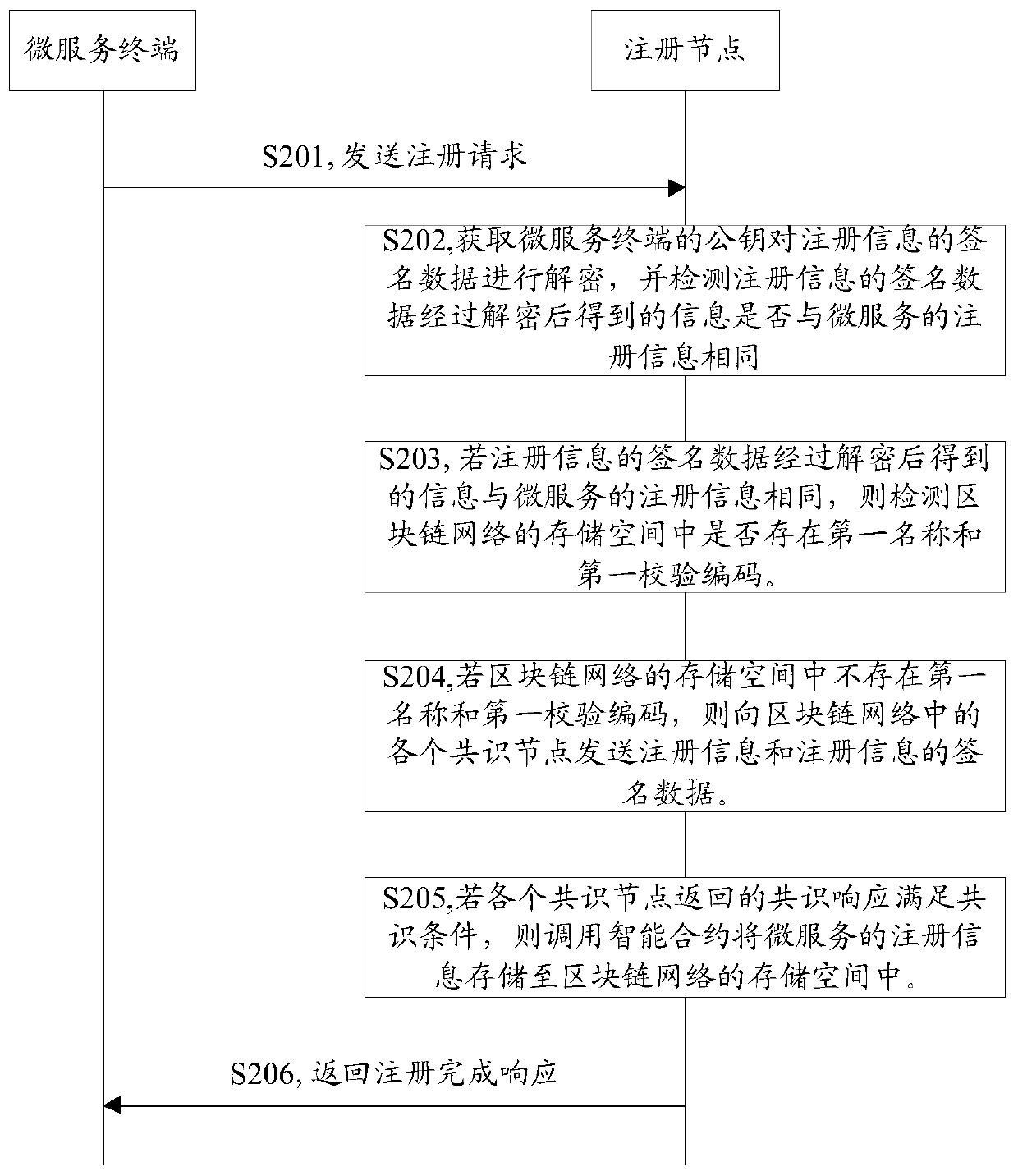
Micro-service registration method and device
ActiveCN110839029AImprove securityPrevent malicious tamperingUser identity/authority verificationComputer networkEngineering
The embodiment of the invention discloses a micro-service registration method and device. The method comprises the following steps: receiving a registration request sent by a micro-service terminal; obtaining a public key of the micro-service terminal to decrypt signature data of the registration information, and detecting whether the information obtained by decrypting the signature data of the registration information is the same as the registration information of the micro-service or not; if yes, detecting whether a first name and a first check code exist in a storage space of the blockchainnetwork or not; if not, sending registration information and signature data of the registration information to each consensus node in the blockchain network; and if the consensus response returned byeach consensus node satisfies the consensus condition, calling the smart contract to store the registration information in the storage space of the blockchain network, and returning a registration completion response to the micro-service terminal for the registration request. By adopting the embodiment of the invention, the address of the micro-service can be prevented from being maliciously tampered, and the safety of the micro-service and the stability of the provided service are improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD
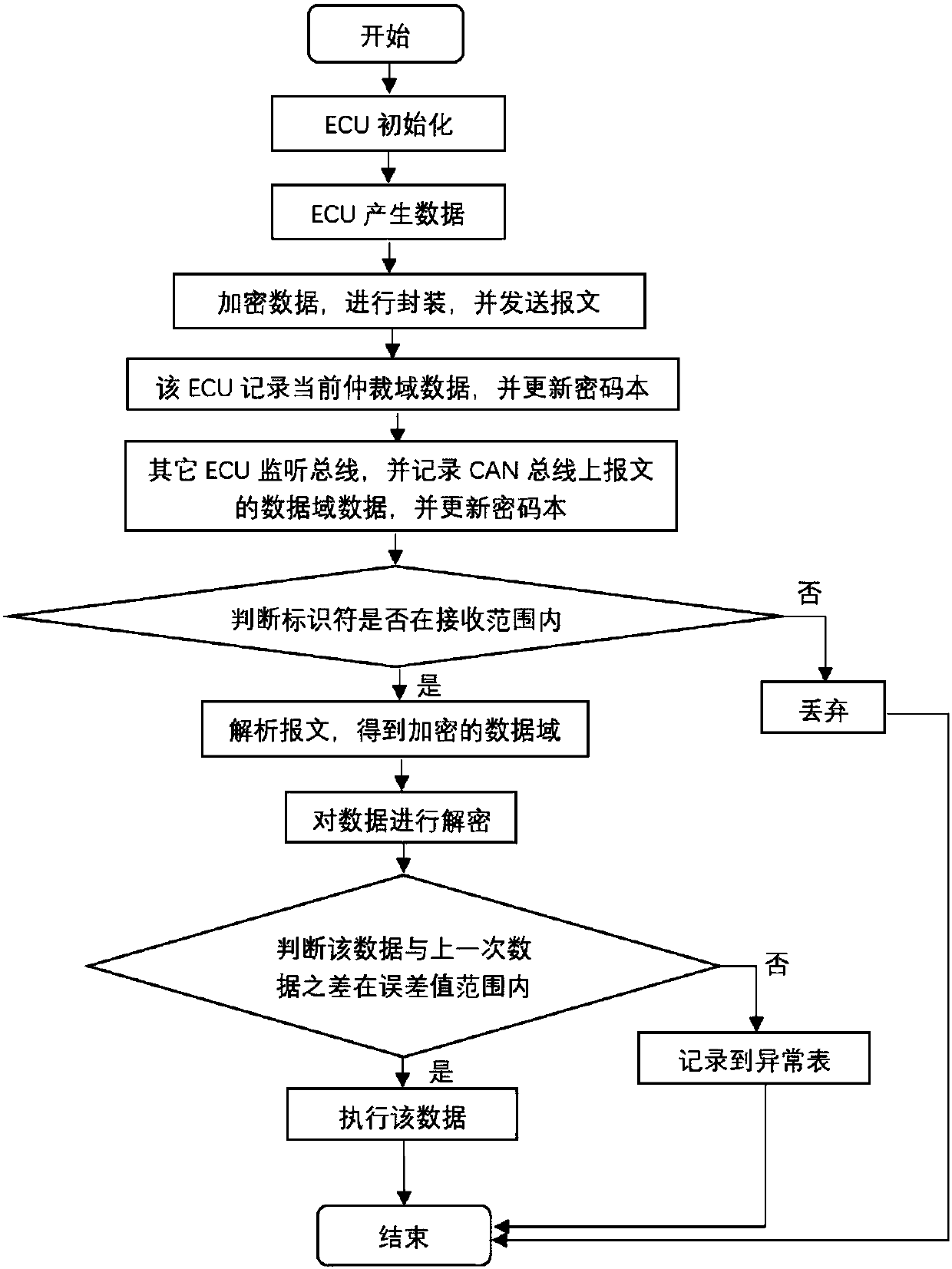
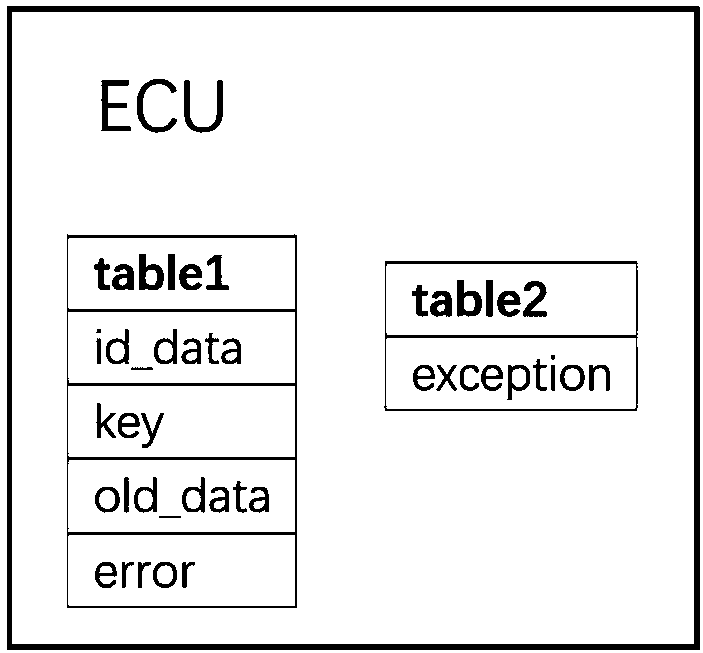
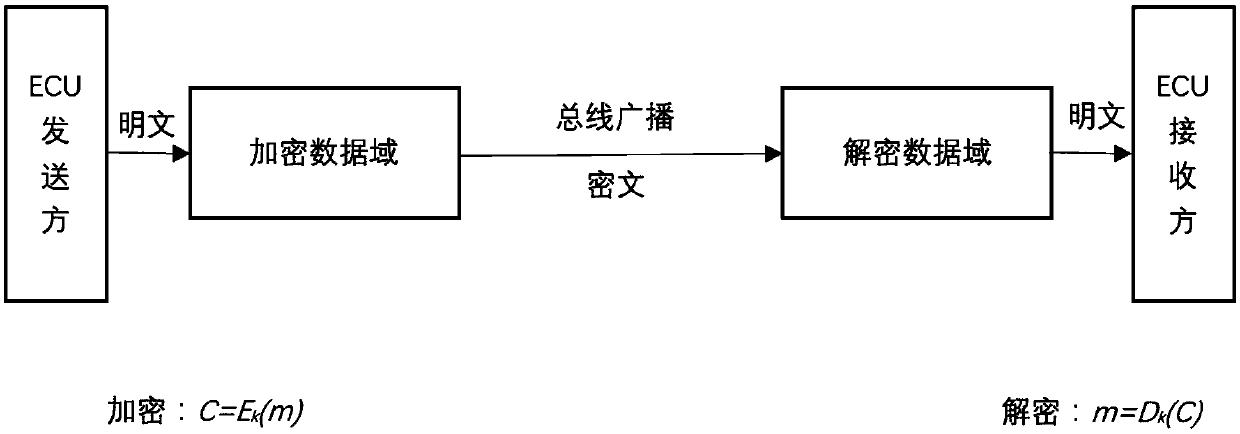
Anti-attack method and system of CAN bus message based on block chain technology
ActiveCN107749845AImprove securitySolving Difficult Management ProblemsBus networksAttack modelCode book
The invention belongs to the technical field of anti-attack of messages, and discloses an anti-attack method and system of a CAN bus message based on the block chain technology. The method comprises the following steps: improving an account book generated in a block chain, generating a password with a fixed length and updating the password in real time; performing, by each ECU, encryption processing on arbitration domain data monitored every time and a code book to obtain a new code book; before a message is sent, encrypting the data domain information via the latest code book to obtain an encrypted data domain, and finally sending the data domain; filtering, by the ECU, an identifier in the arbitration domain to obtain the necessary message, analyzing the message to obtain the encrypted data domain, and decrypting the encrypted data domain by using own code book; then judging the validity of the data obtained by decryption; and if the data are valid, executing the data, and otherwise,discarding the data. By adoption of the anti-attack method and system, the counterfeit, replay and other attacks can be defended, and the security of the vehicle is enhanced.
Owner:CHENGDU UNIV OF INFORMATION TECH
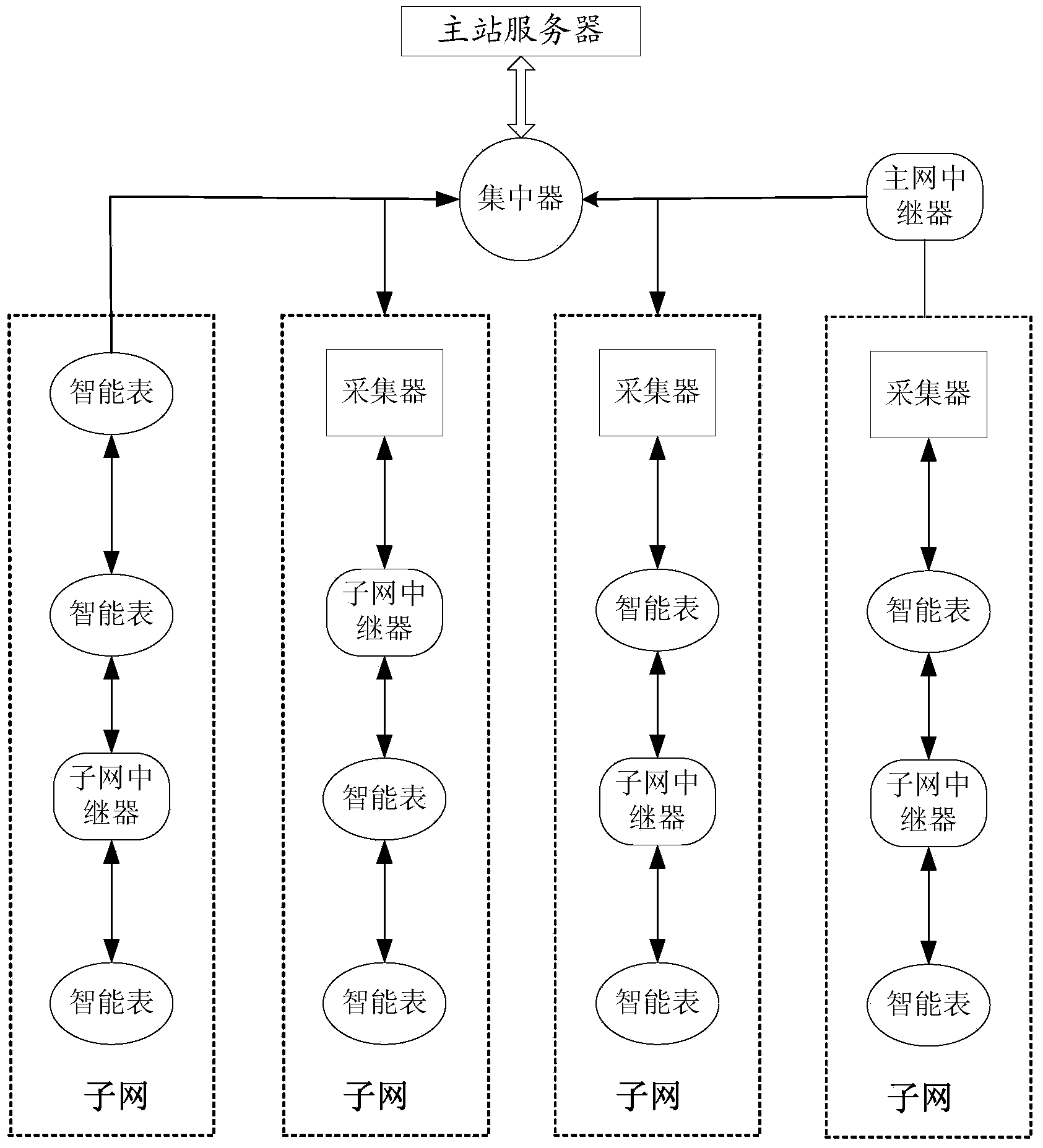
Meter reading system of wireless intelligent meter
PendingCN103632526AEasy to loseEfficient managementTransmission systemsNetwork topologiesMaster stationComputer science
The invention relates to a meter reading system of a wireless intelligent meter. The system comprises the intelligent meter, a subnet relay, a collector, a concentrator and a master station server, wherein the intelligent meter collects and sends data of use levels of intelligent meter users, the subnet relay transmits a reading management command and the data of the use levels of the intelligent meter users, the collector establishes a subnet, collects the data of the use levels of the intelligent meter users, and transmits the reading management command, the subnet relay transmits an ultrashort management command and the use levels of the intelligent meter users, the concentrator establishes a main network, collects the data of the use levels of the intelligent meter users and transmits the reading management command, the master station server generates and sends the reading management command, receives the data of the use levels of the intelligent meter users and analyzes and manages the data. The subnet relay provided by the invention can relay and transmits the data of the use levels of the intelligent meter users, sent by the intelligent meter, when the number of the intelligent meters is great, so that the problem that in the subnet, the volume of the data of the use levels of the intelligent meter users, sent by the intelligent meter farther from the collector, is easy to lose is effectively solved. The system has the advantage of strong reliability.
Owner:STATE GRID JIANGSU ELECTRIC POWER CO ELECTRIC POWER RES INST +2
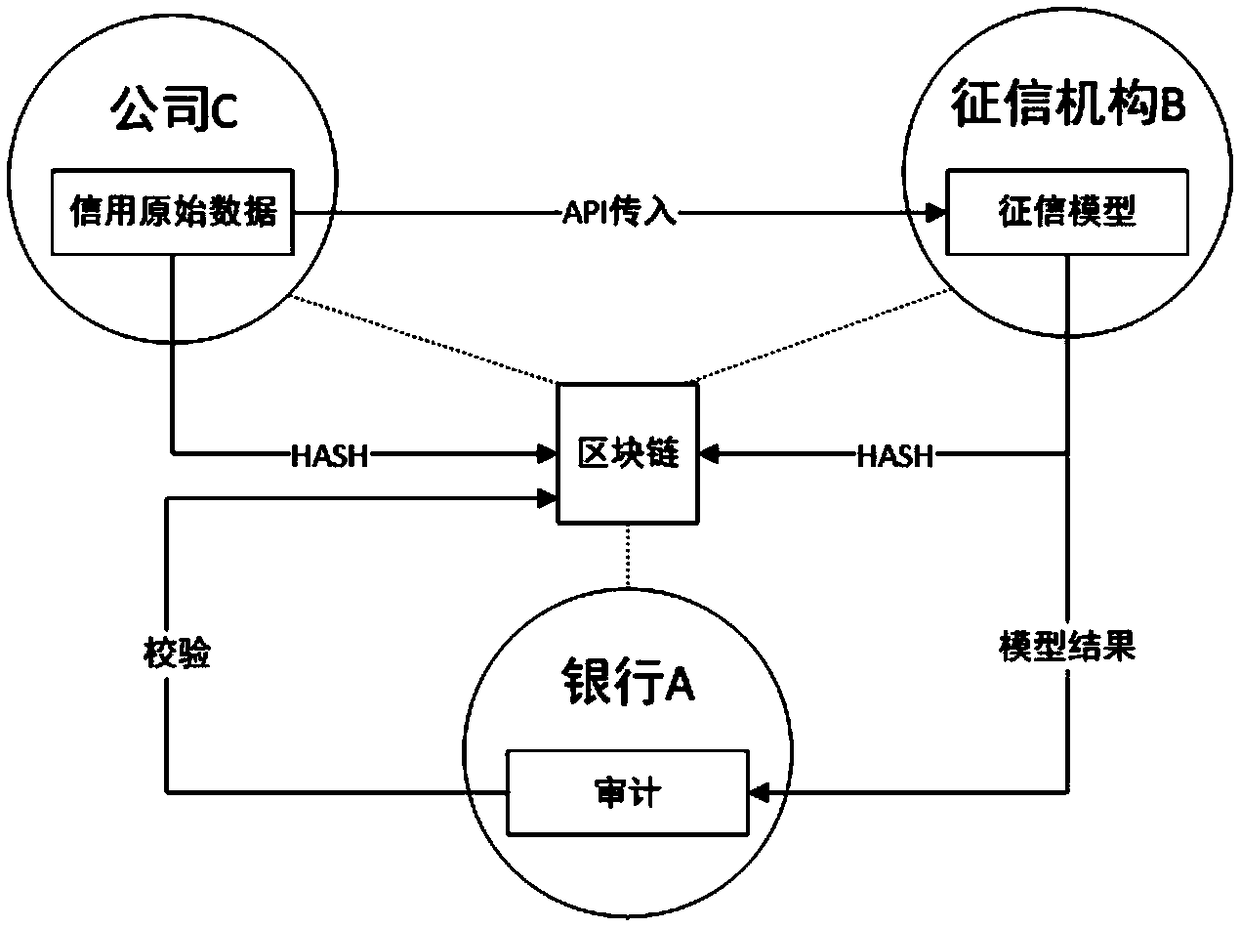
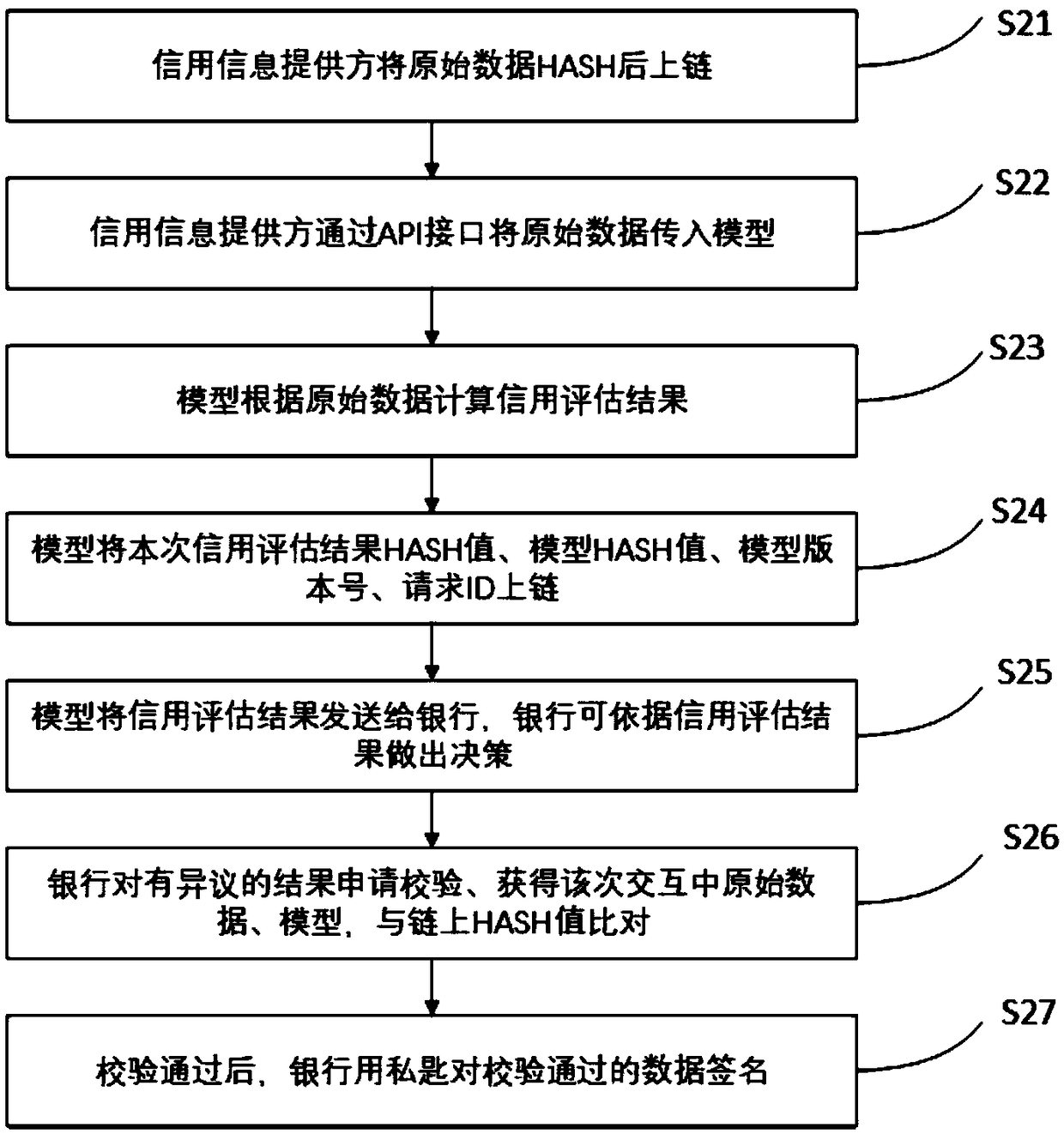
Credit Data, Model Guarantee and Verification Method Based on Block Chain
InactiveCN109118355AAvoid lostPrevent malicious tamperingFinanceDigital data protectionOriginal dataEvaluation data
The invention discloses a warranty and verification method of credit data and credit model based on block chain. The method comprises the following steps: (1) a provider of credit data links the HASHvalue of the original data; (2) the HASH value of the model, the HASH value of the model result data, the model version and the request ID are recorded on the link; (3) bank or other personal information users audit the data, that is, compare the data on the chain with the original data, audit and verify the evaluation data and model. The invention guarantees the safety, reliability, traceabilityand verifiability of the credit evaluation data, thereby effectively reducing the disputes caused by the information opacity in the credit investigation process, preventing the damage caused by malicious tampering of the credit investigation data, and meeting the actual use demand.
Owner:南京安链数据科技有限公司
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com